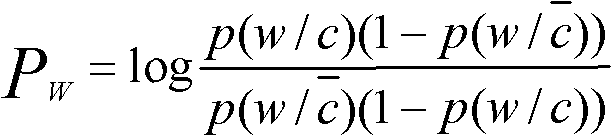Method for obtaining software security defects based on vertical search and semantic annotation
A vertical search and semantic annotation technology, applied in special data processing applications, instruments, electrical digital data processing, etc., can solve the problems of expensive software maintenance and fault recovery, heavy computer losses, etc.
Active Publication Date: 2010-08-25
江苏永达电力电信安装工程有限公司
View PDF3 Cites 7 Cited by
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Computer systems are destroyed and paralyzed, key information leaks lead to huge economic losses and other intangible losses, and software maintenance and fault recovery costs become more and more expensive. It can be seen that the losses caused by computer attacks are very heavy.
Method used
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
View moreImage
Smart Image Click on the blue labels to locate them in the text.
Smart ImageViewing Examples
Examples
Experimental program
Comparison scheme
Effect test
Embodiment Construction
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More PUM
 Login to View More
Login to View More Abstract
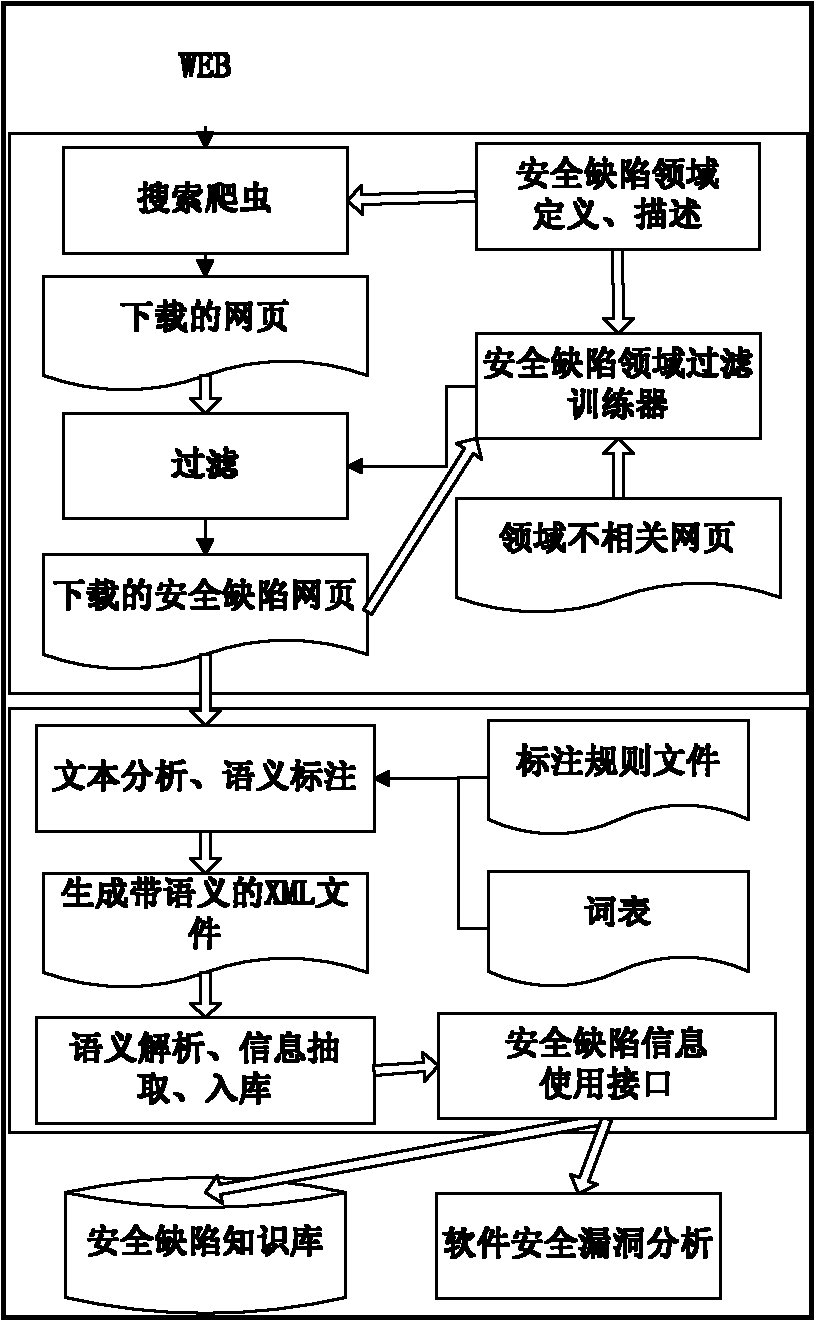
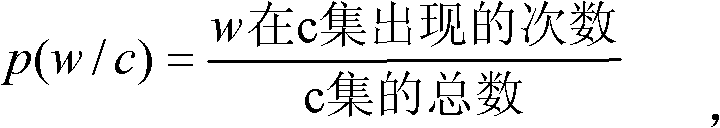
The invention belongs to the field of dependable computing, in particular to a method for obtaining software security defects based on vertical search and semantic annotation, which comprises the steps of: firstly, creeping a security defect information webpage published on a World-Wide-Web by using a field search creeper, providing a forceful filter support for the search creeper completing the task by a security defect filed filter trainer; secondly, carrying out semantic annotation on downloaded webpages to enable the webpages to be carried out with semantic information and allow a machine to be understood; thirdly, designing an annotation analysis tool for further carrying out information extraction on the annotated information; and fourthly, providing an interface for carrying out a software security knowledge base and a software security hole analysis by using the information. The invention can provide a large quantity of data and the forceful support for the software security knowledge base and the software security hole analysis.
Description
technical field The invention belongs to the field of trusted computing and relates to a method for acquiring software safety defects. Background technique Today, with the rapid development of computers, the security features of computer software are not only additional attributes of software, but also essential features. Moreover, with the rapid development of today's network, the requirements for software reliability and security are getting higher and higher. This is because the network makes computer applications and computer systems show a trend of highly interconnected development. This trend is bringing IT industry Astonishing opportunities come, but also means that these highly interconnected computers are more likely to be attacked. Computer systems are destroyed and paralyzed, key information leaks lead to huge economic losses and other intangible losses, and software maintenance and fault recovery costs become more and more expensive. It can be seen that the loss...
Claims
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More Application Information
Patent Timeline
 Login to View More
Login to View More Patent Type & Authority Applications(China)
IPC IPC(8): G06F17/30
Inventor 李晓红刘丰煦杜洪伟许光全徐超
Owner 江苏永达电力电信安装工程有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com