Text deep learning-based software security vulnerability prediction method
A deep learning and software security technology, applied in computer security devices, special data processing applications, instruments, etc., can solve the problems of insufficient vulnerability prediction effect and poor feature learning effect, and achieve high accuracy, false alarm rate and missed alarm rate. The effect of low and improved performance indicators
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0031] The present invention will be further described below in conjunction with the accompanying drawings.
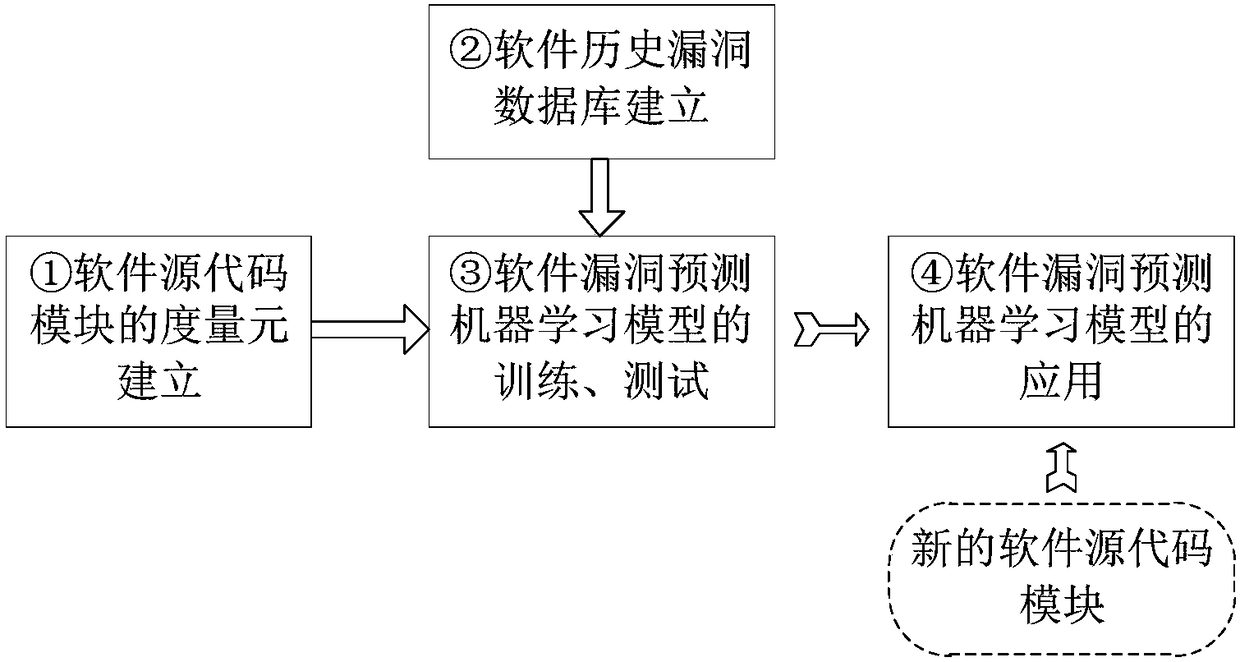
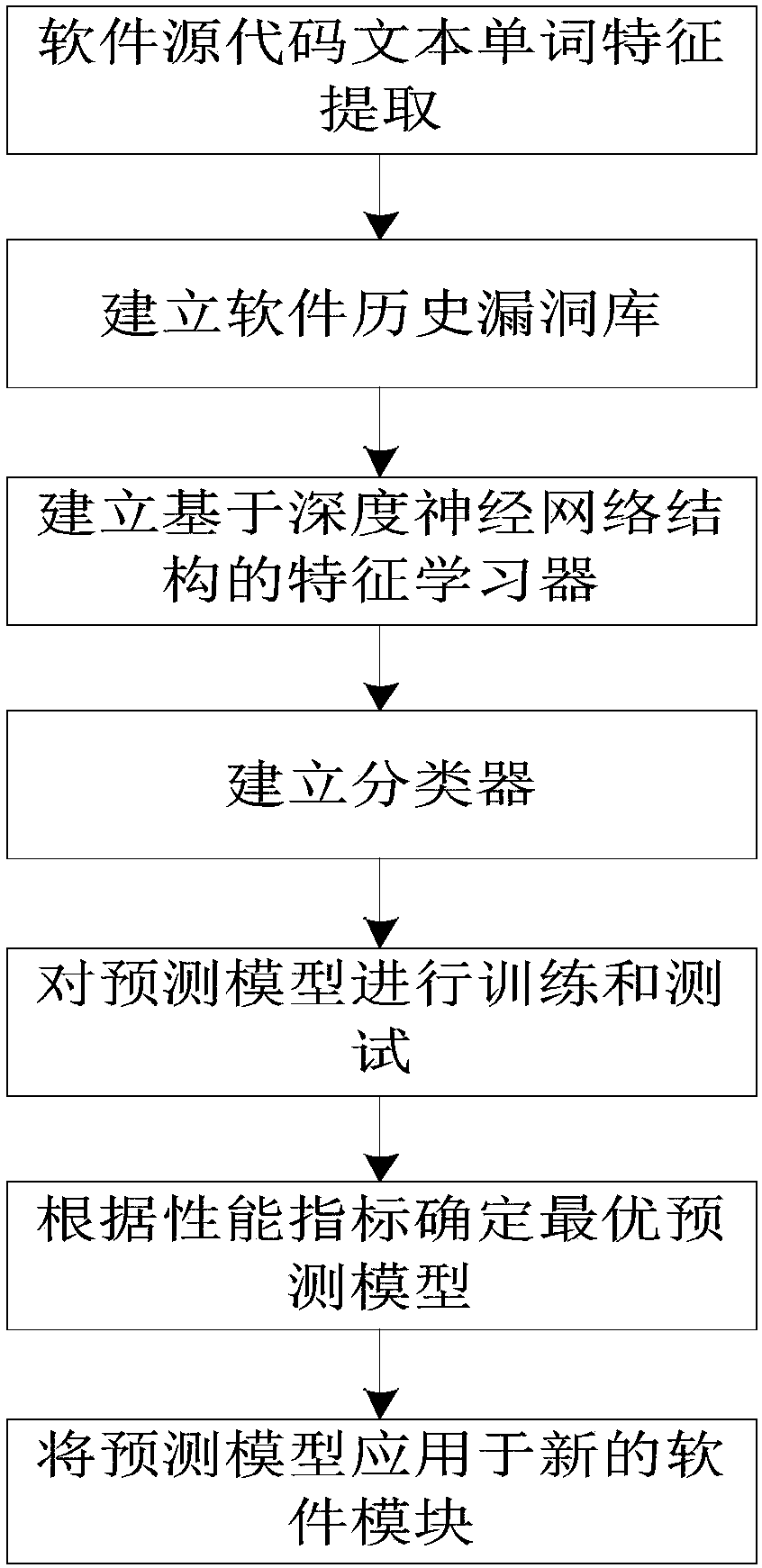
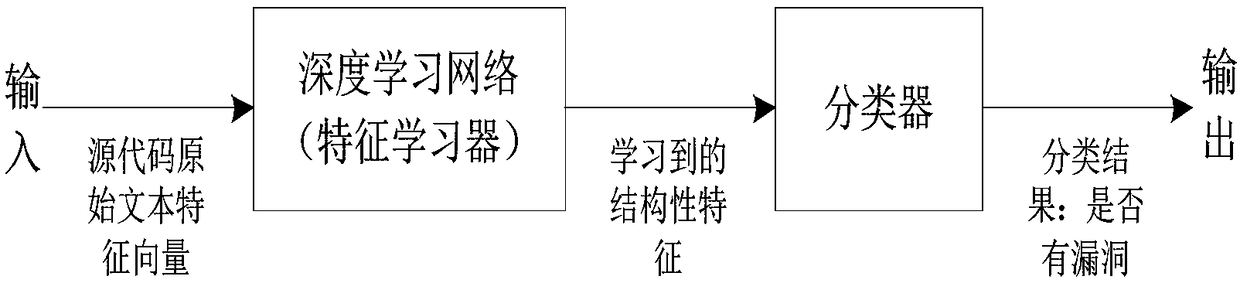
[0032] Such as figure 2 As shown, the software security vulnerability prediction method based on text deep learning of the present invention comprises the following steps:
[0033] Step 1, software source code text word feature extraction
[0034] For the source code of a software project (that is, the prediction object), take the software module in it as the processing unit, first remove the punctuation marks and code comments that appear in the module source code text, and use spaces as separators for the remaining text Extract each word, and count the number of occurrences of each word in the entire text, and finally normalize the number of occurrences. The result of the processing is the frequency of occurrence of the word, thus obtaining the source code text for this module. The eigenvectors, set to the following representation:
[0035] ComponentName: (Item_1...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com