Computer software security loophole repairing apparatus and method
A software security and vulnerability repair technology, applied in the computer field, can solve problems such as difficulty in ensuring normal use of the network, inability to play a decisive role, and harm
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
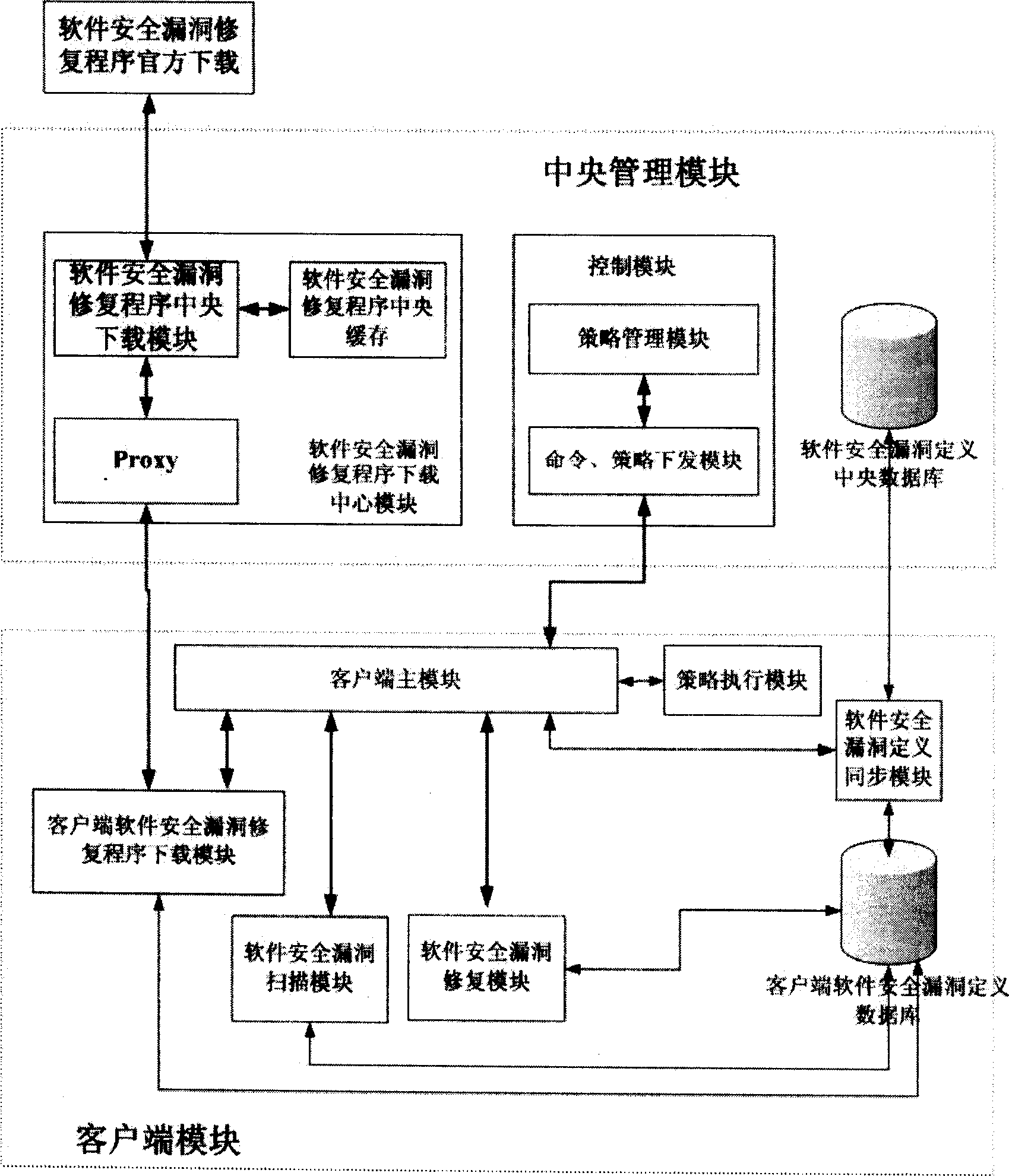
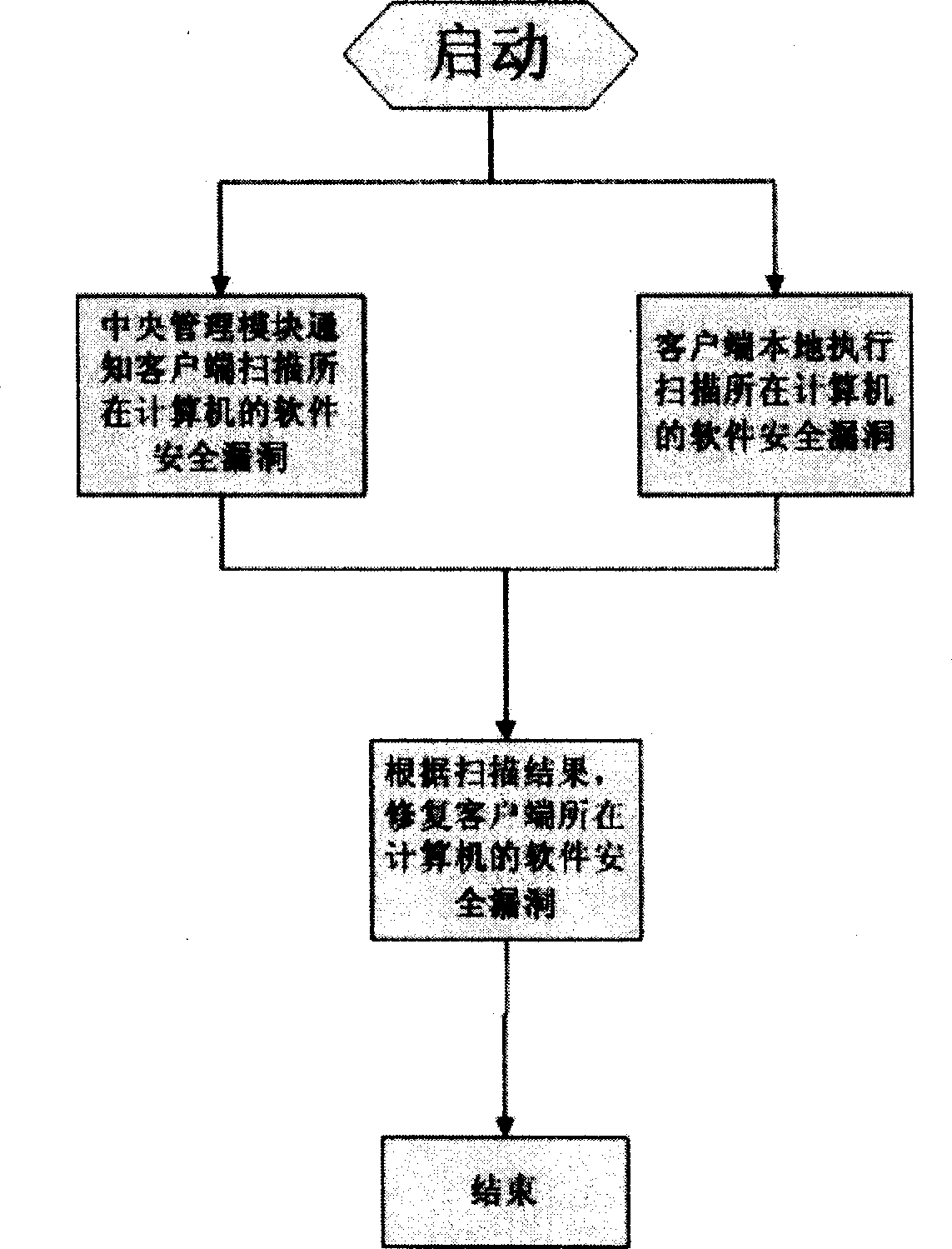
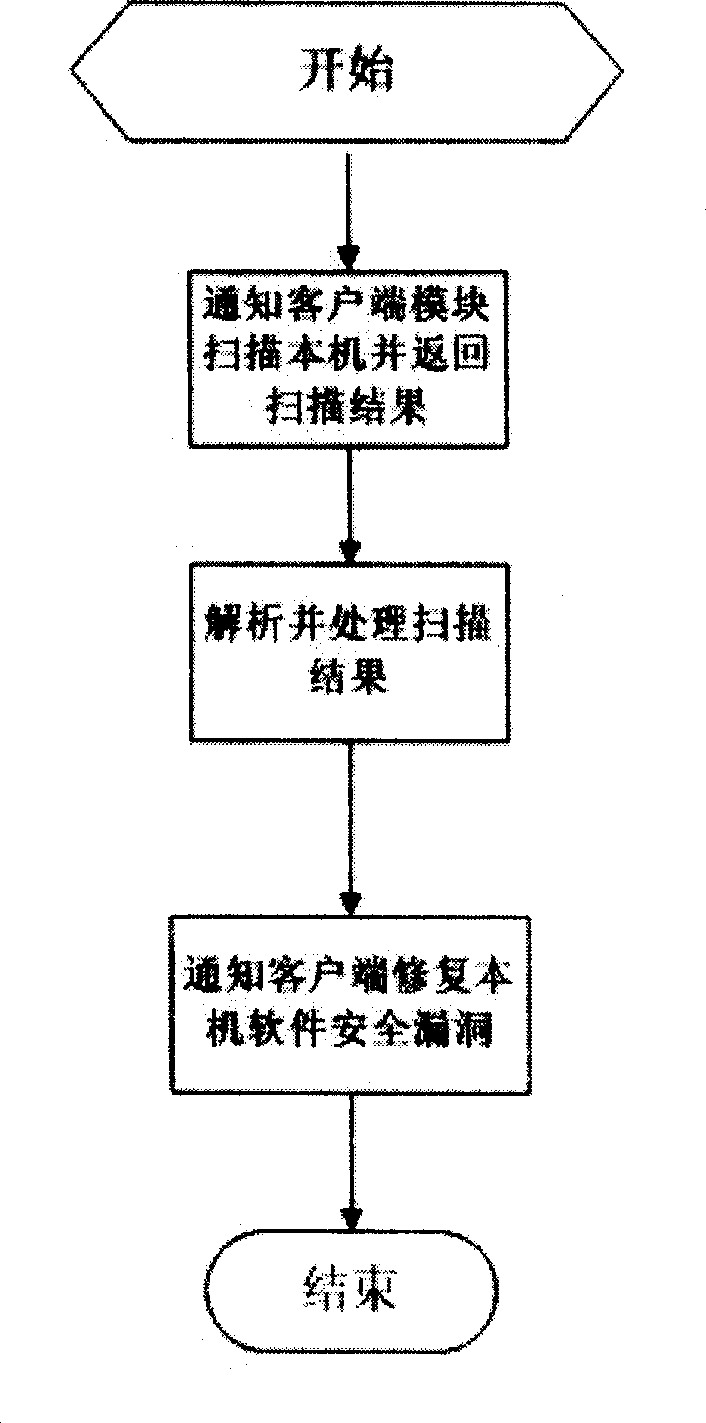
[0011] Such as figure 1 As shown, a computer software security vulnerability repairing device includes a central management module and at least one client module; the central management module contains a software security vulnerability repair program download center module, a control module and a software security vulnerability definition central database; The client module includes a client main module, a policy execution module, a software security vulnerability definition synchronization module, a client software security vulnerability definition database, a software security vulnerability repair module, a software security vulnerability scanning module, and a client software security vulnerability repair program download module ; The client software security loophole repair program download module and the software security loophole patch download center module in the central management module, the client main module and the control module in the central management module, t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com