Compiler security test method based on system structure cross check
An architecture and cross-checking technology, applied in the field of compiler security testing, which can solve the problems of unable to find the architecture, unable to find unknown types, difficult to be migrated, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
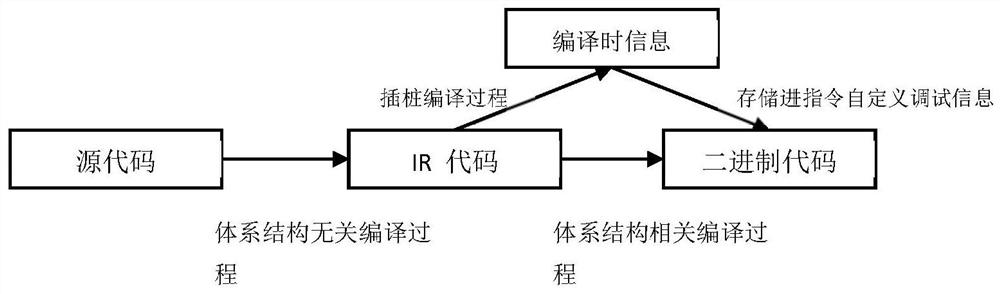
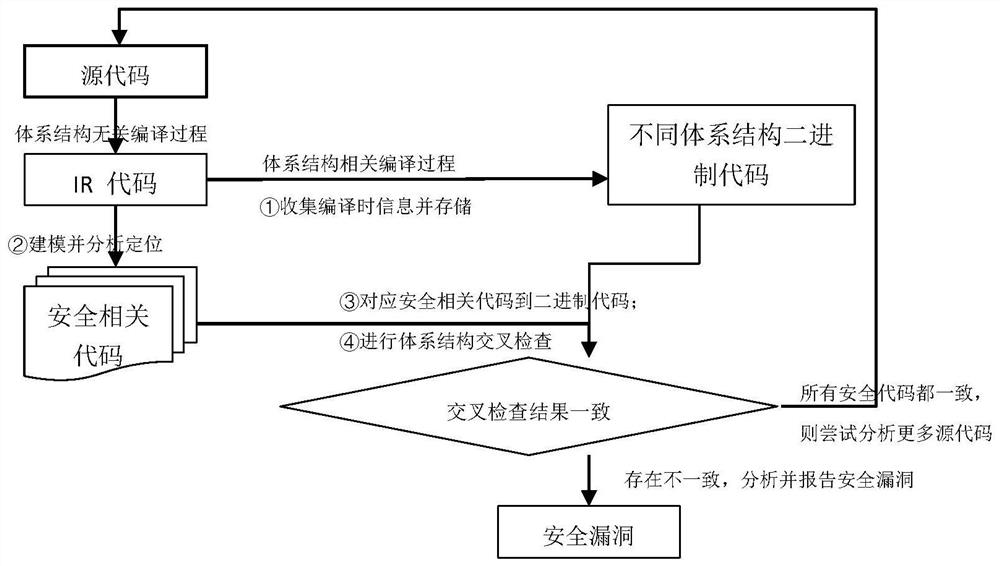
[0078] like figure 1 As shown, it is the compilation process of the pile compiler. Collect representative instruction information, IR level control flow information, IR and binary code basic block level corresponding information, and store this information into the customization of the relevant instructions. Debug information.
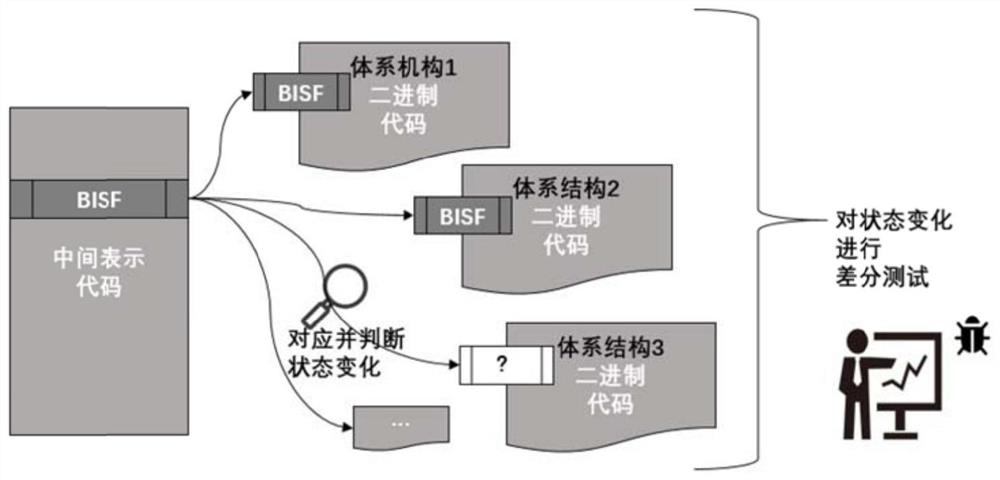
[0079] like figure 2 As shown, discriminate the change in the semantic state of the security-related instructions and the cross-check of the architecture. The BISF (Back-Endependent Semantic Fragment) is modeled and positioned in accordance with the method of the present invention. On the basis of being positioned to security related code, the security related code is correspondingly related to the secure correlation code in the binary code of different architectures. Finally, cross-check and analyze confirmation of real security issues.
[0080] The test case of the test compiler of the present invention is the source code of common large-scale open sourc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com