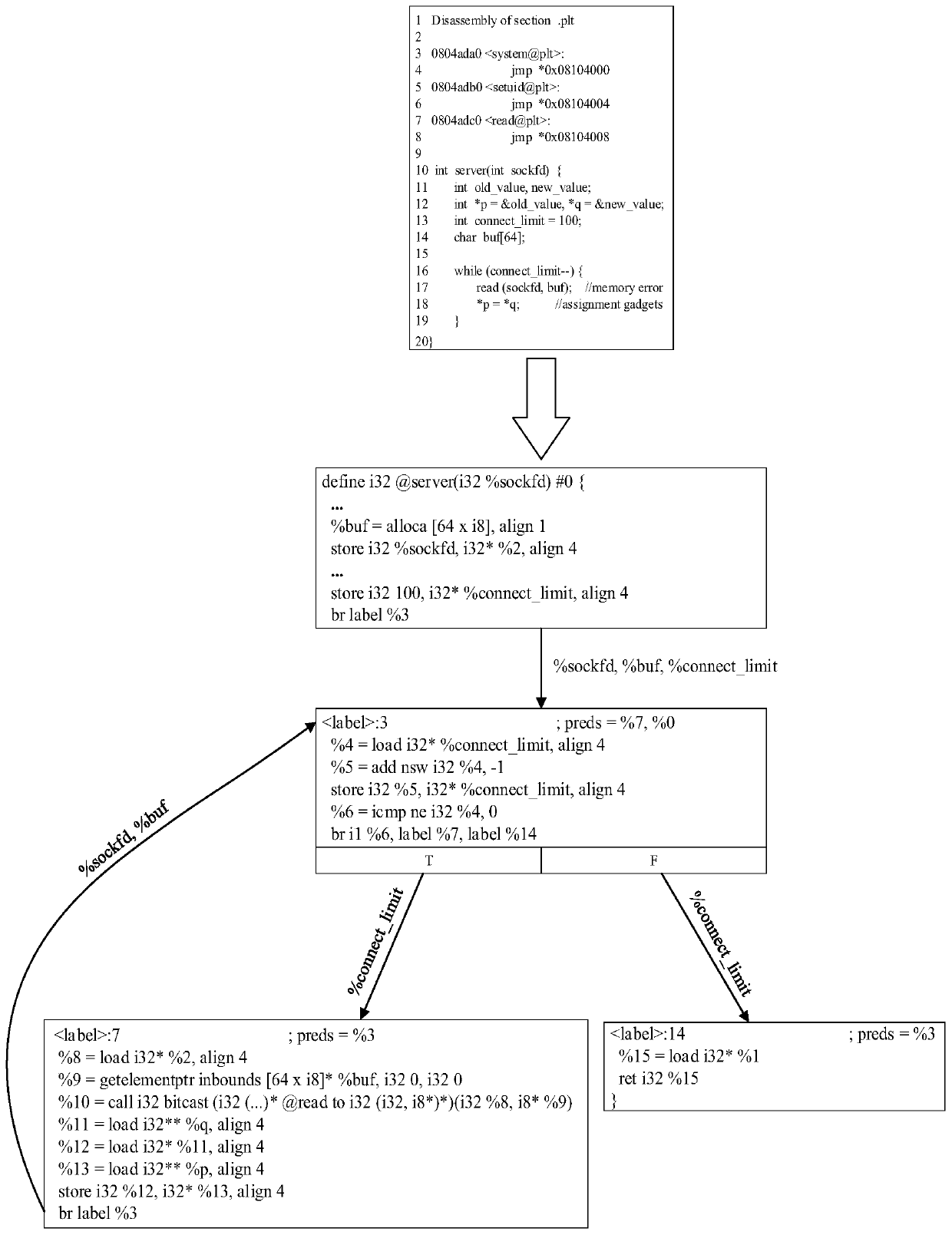
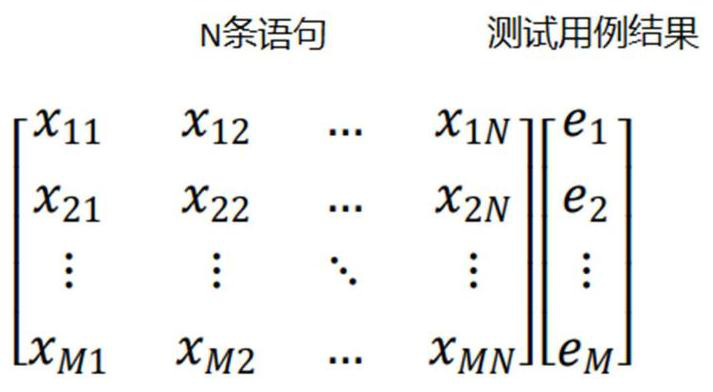
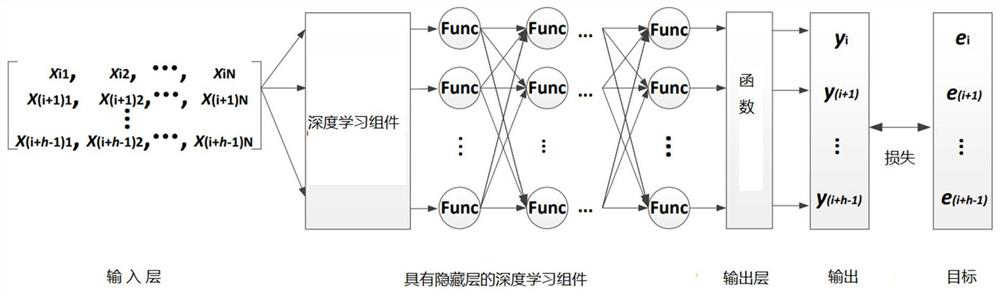
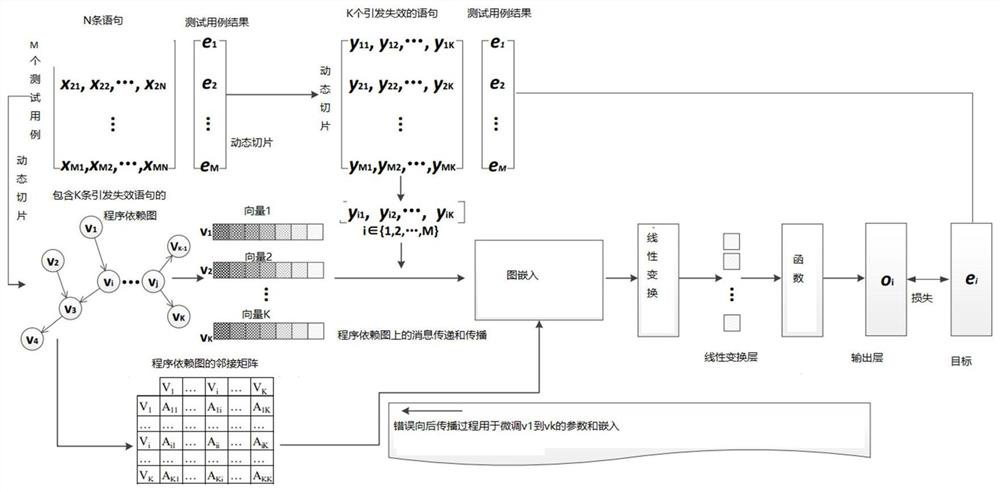
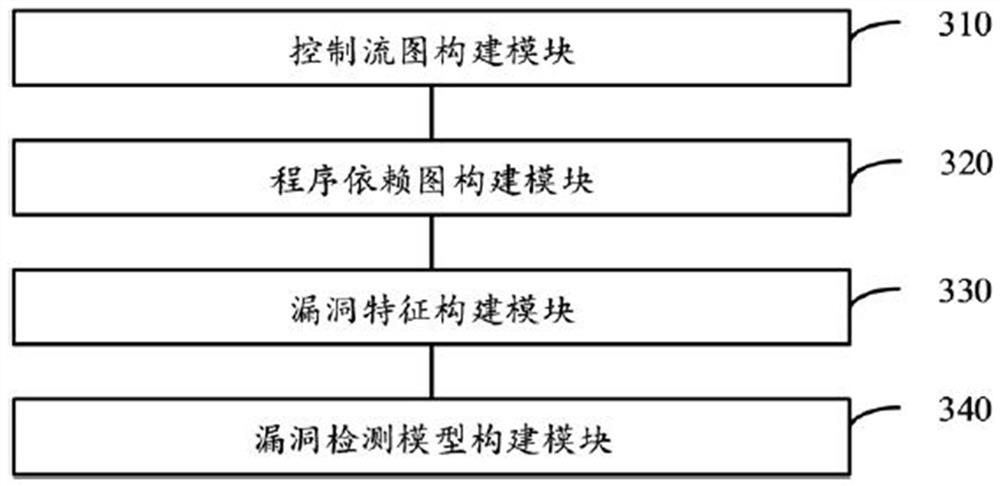
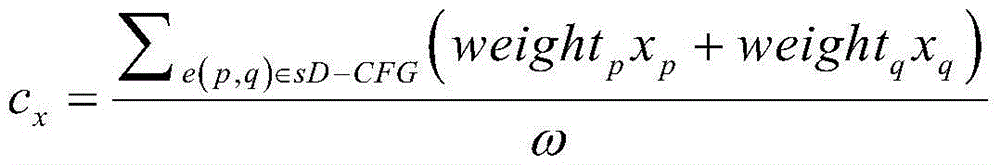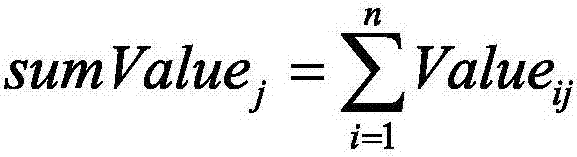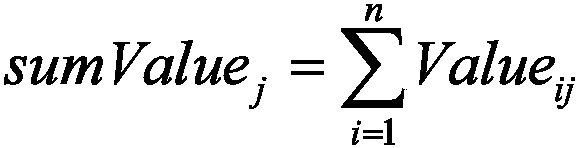Patents
Literature
44 results about "Program Dependence Graph" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
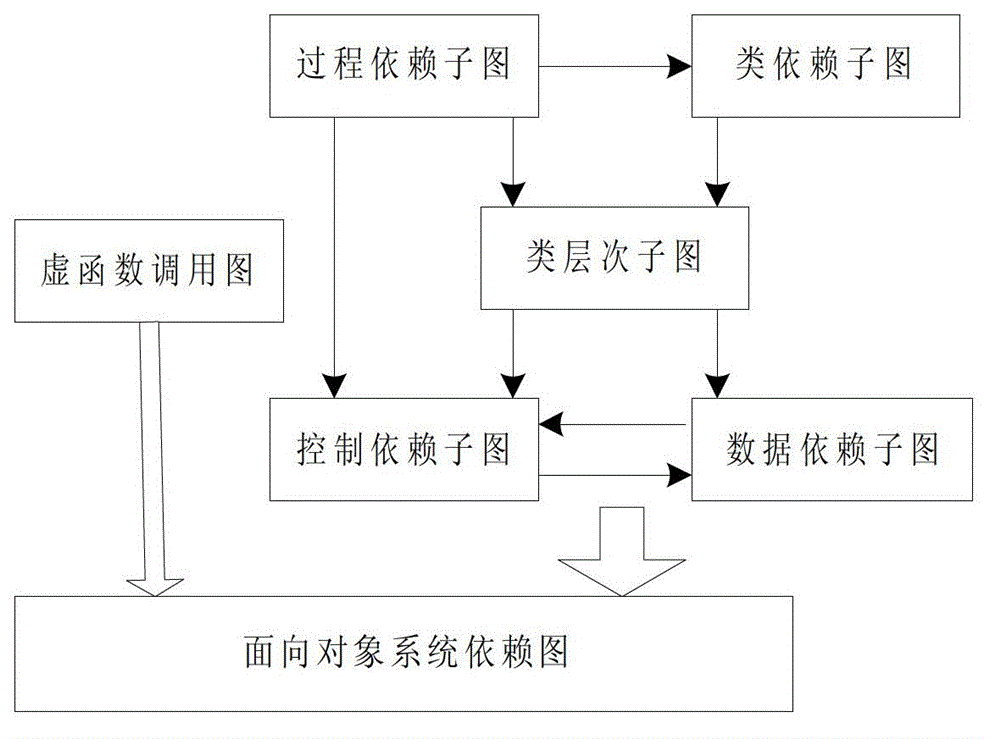
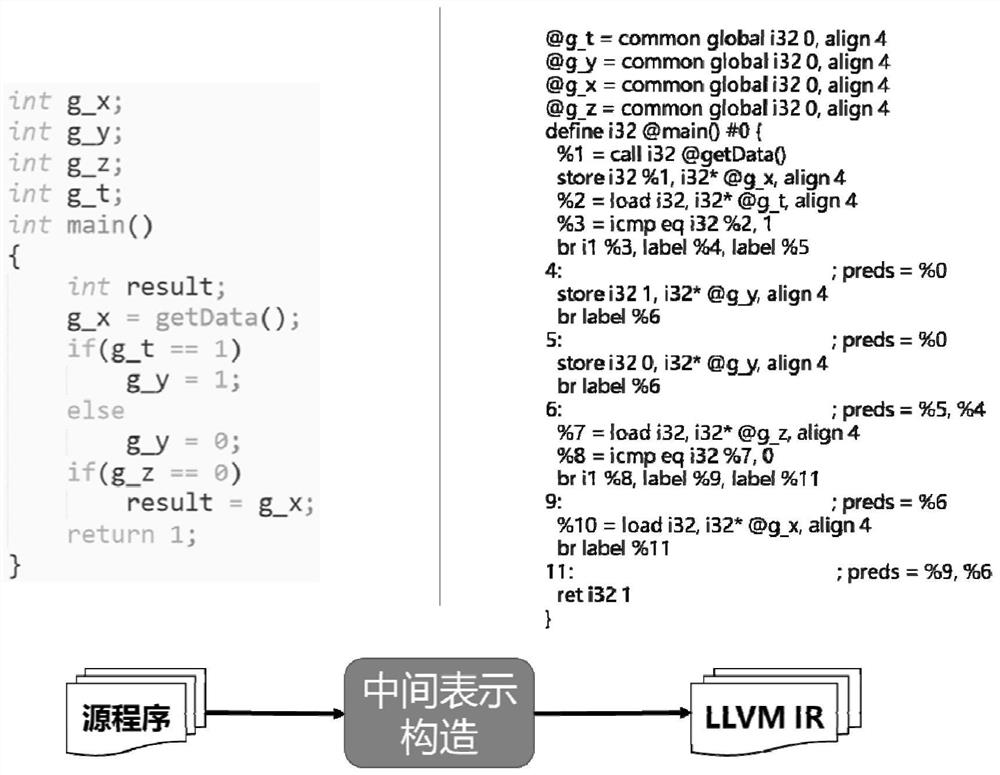
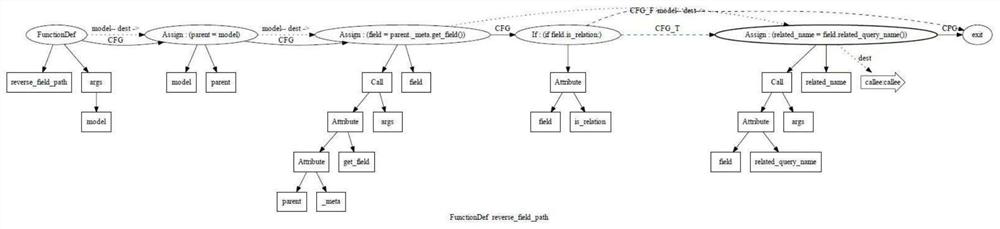
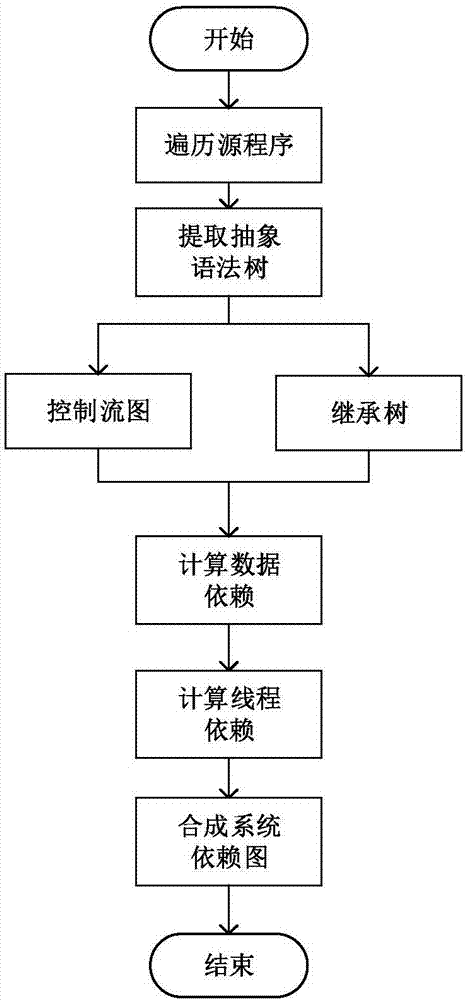
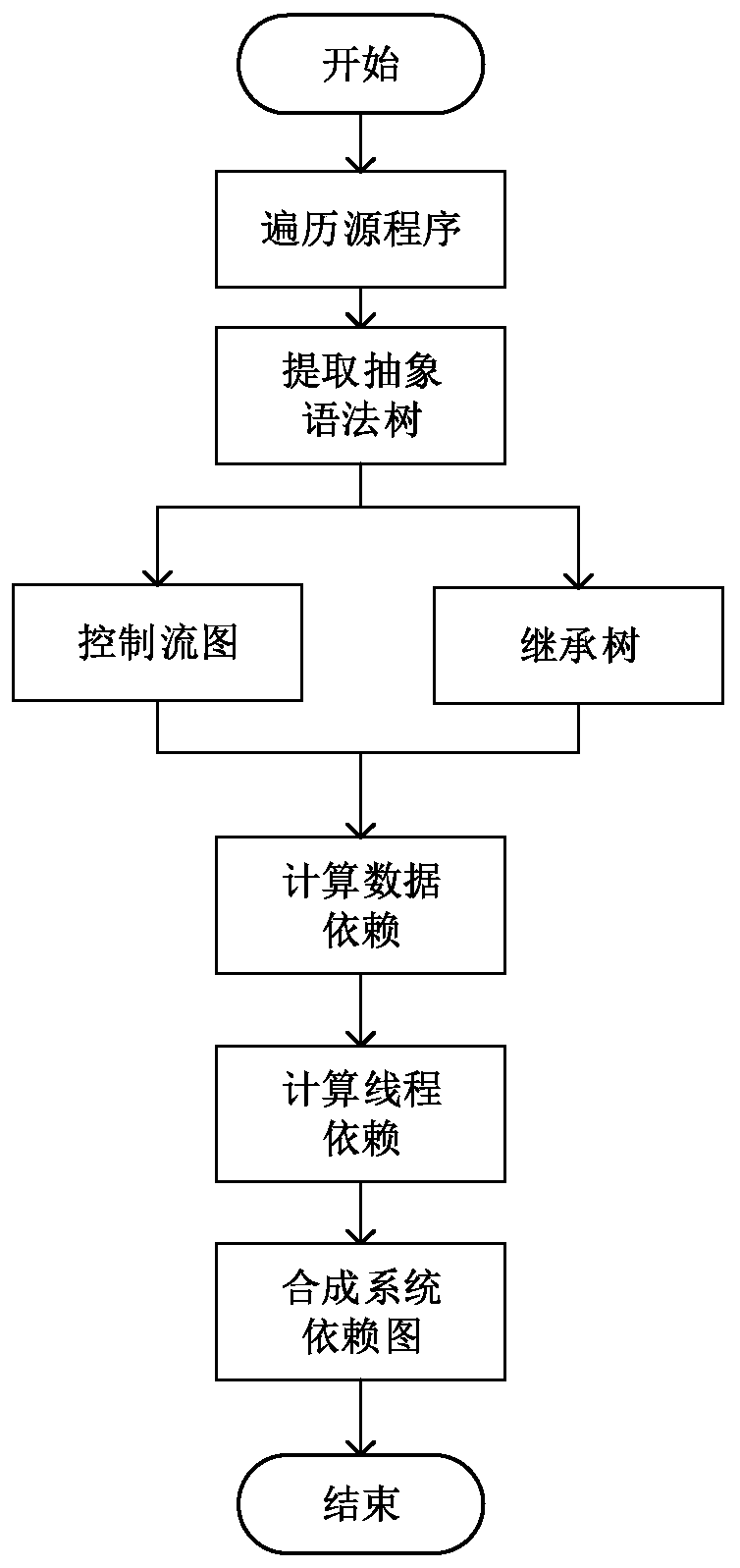
In computer science, a program dependence graph (PDG) is a representation, using graph notation, that makes data dependencies and control dependencies explicit. These dependencies are used during dependence analysis in optimizing compilers to make transformations so that multiple cores are used, and parallelism is improved.
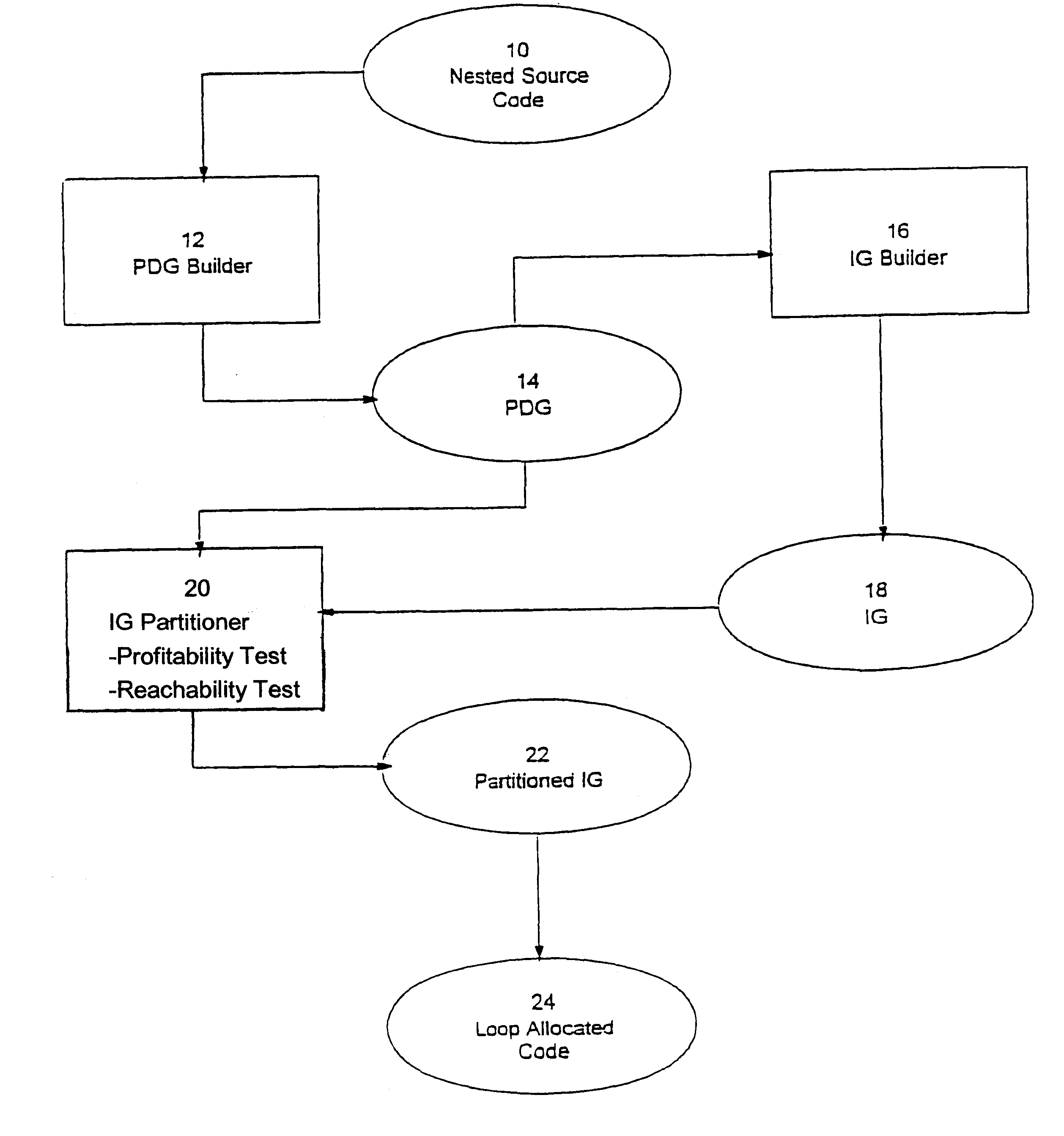
Loop allocation for optimizing compilers
Loop allocation for optimizing compilers includes the generation of a program dependence graph for a source code segment. Control dependence graph representations of the nested loops, from innermost to outermost, are generated and data dependence graph representations are generated for each level of nested loop as constrained by the control dependence graph. An interference graph is generated with the nodes of the data dependence graph. Weights are generated for the edges of the interference graph reflecting the affinity between statements represented by the nodes joined by the edges. Nodes in the interference graph are given weights reflecting resource usage by the statements associated with the nodes. The interference graph is partitioned using a profitability test based on the weights of edges and nodes and on a correctness test based on the reachability of nodes in the data dependence graph. Code is emitted based on the partitioned interference graph.
Owner:IBM CORP
Method for detecting redundant code defects based on static analysis
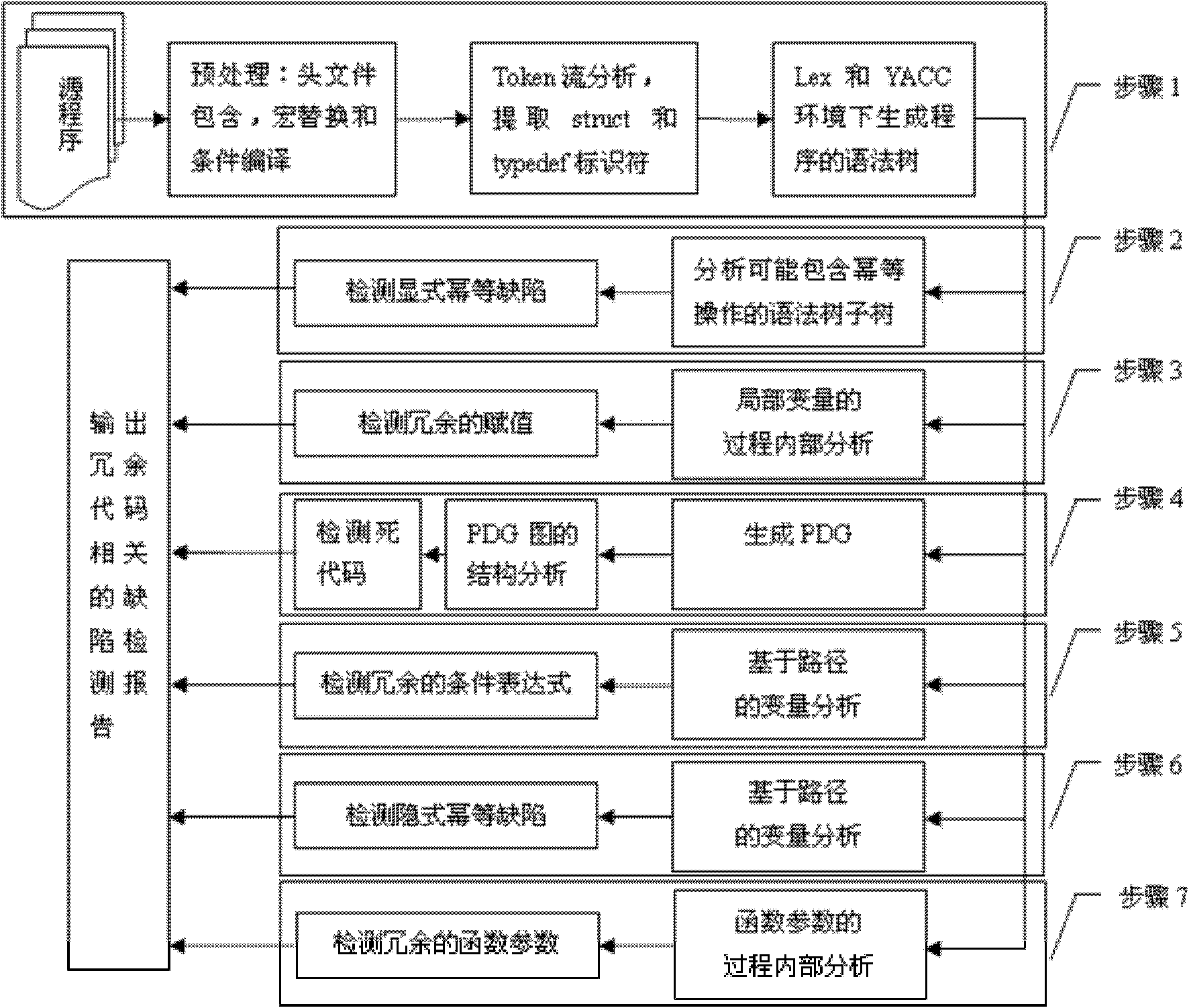
InactiveCN102231134AReduce false detection rateReduce missed detection rateSoftware testing/debuggingStatic timing analysisAbstract syntax tree
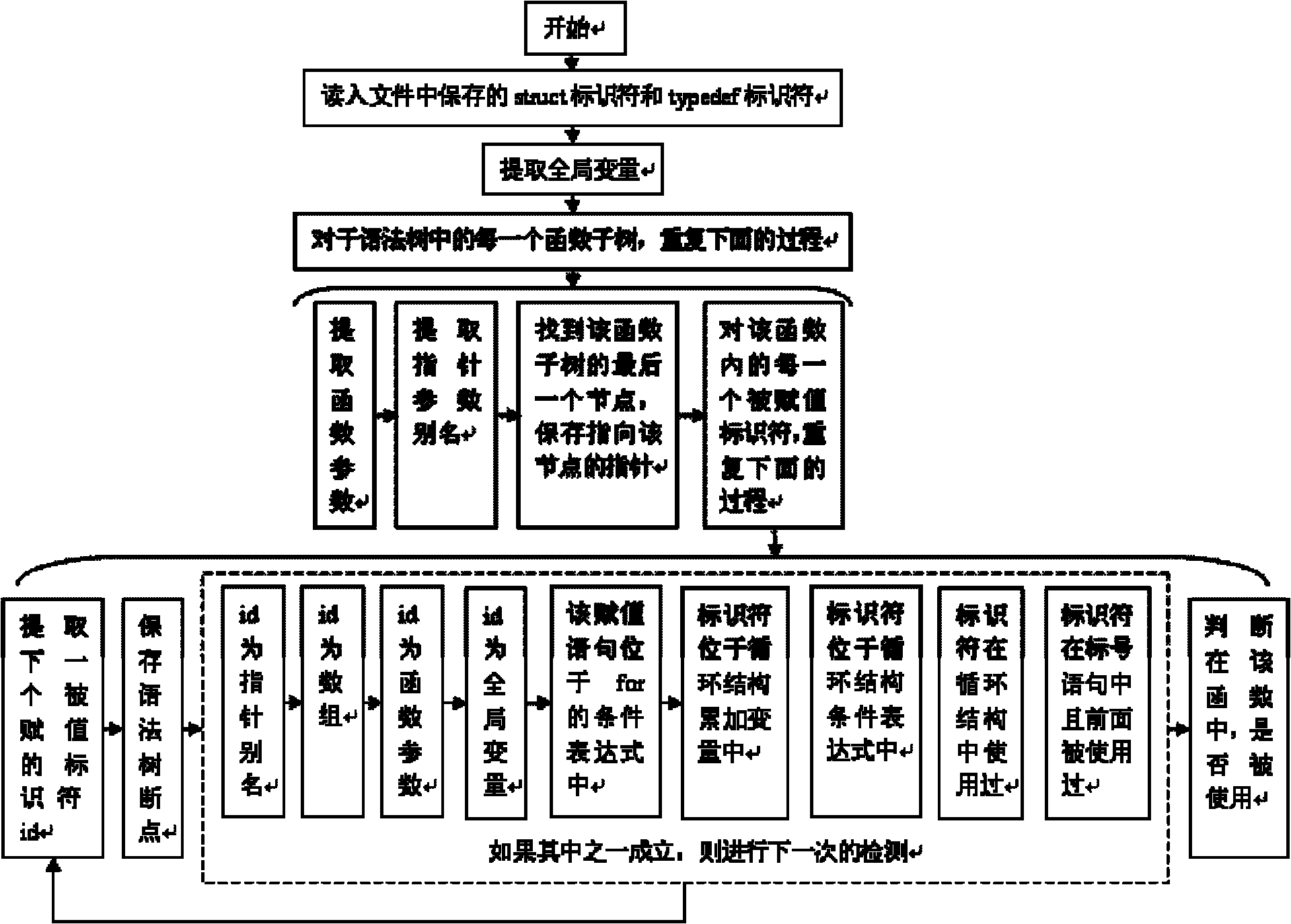
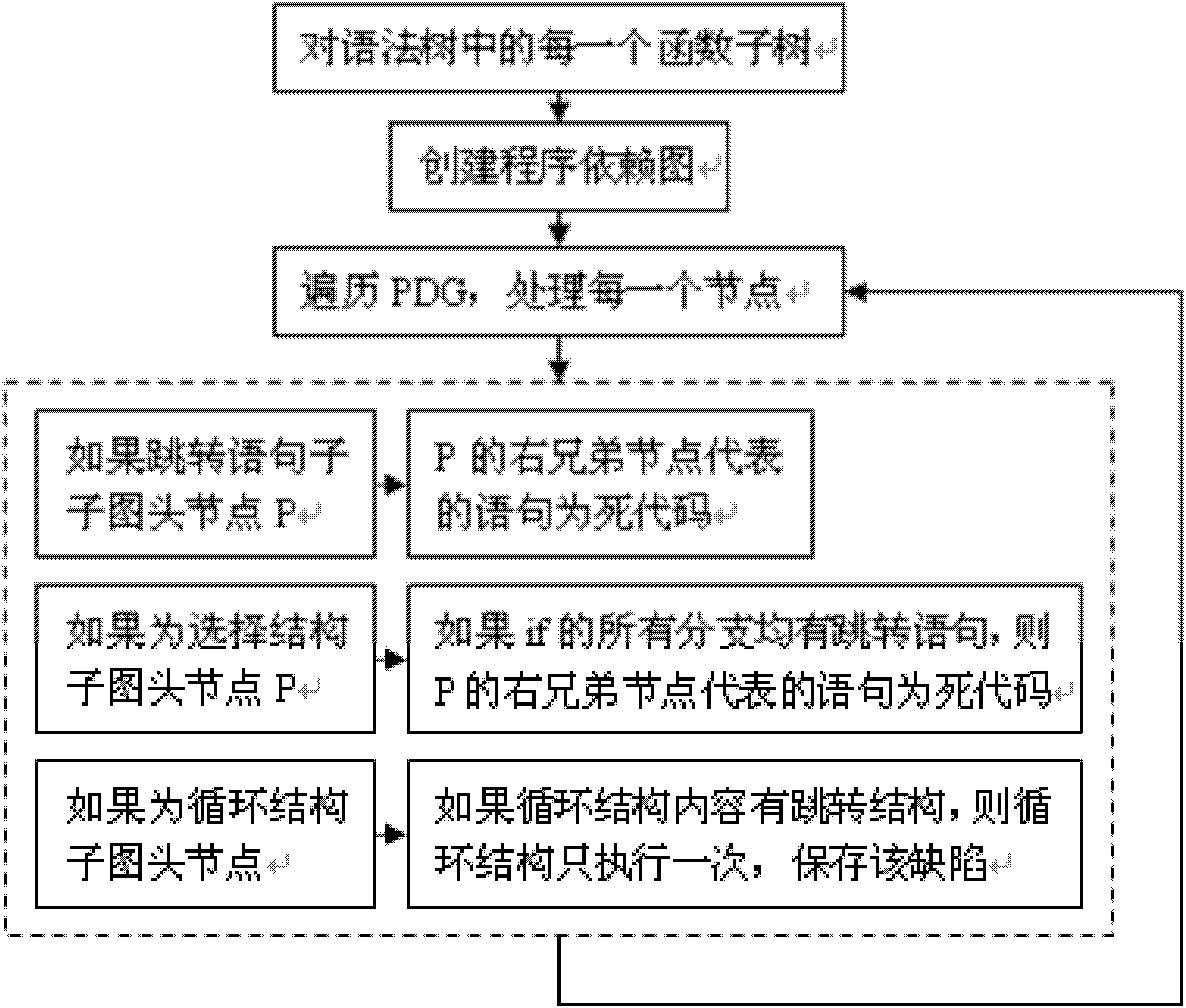
The invention discloses a method for detecting redundant code defects based on static analysis, for solving the problem lacking of a mature method for detecting redundant codes and related defects currently. The method comprises the following steps of: 1, inputting a program to be tested; analyzing the program into an abstract syntax tree; 2, analyzing statements possibly including operations of explicit power and the like; detecting the operations of the explicit power and the like; 3, for locally defined variables, detecting redundant assignment statements by using an internal process analysis method; 4, traversing the abstract syntax tree of the program; searching structures including the defects on the basis of a standardized program dependency graph; detecting dead codes; 5, detecting redundant conditional expressions; 6, detecting operations of implicit power and the like; and 7, detecting redundant function parameters; and giving a defect detection report according to the six defect detection results obtained in the steps 2-7. The method disclosed by the invention is applicable for analyzing large-scale program codes.
Owner:HARBIN INST OF TECH
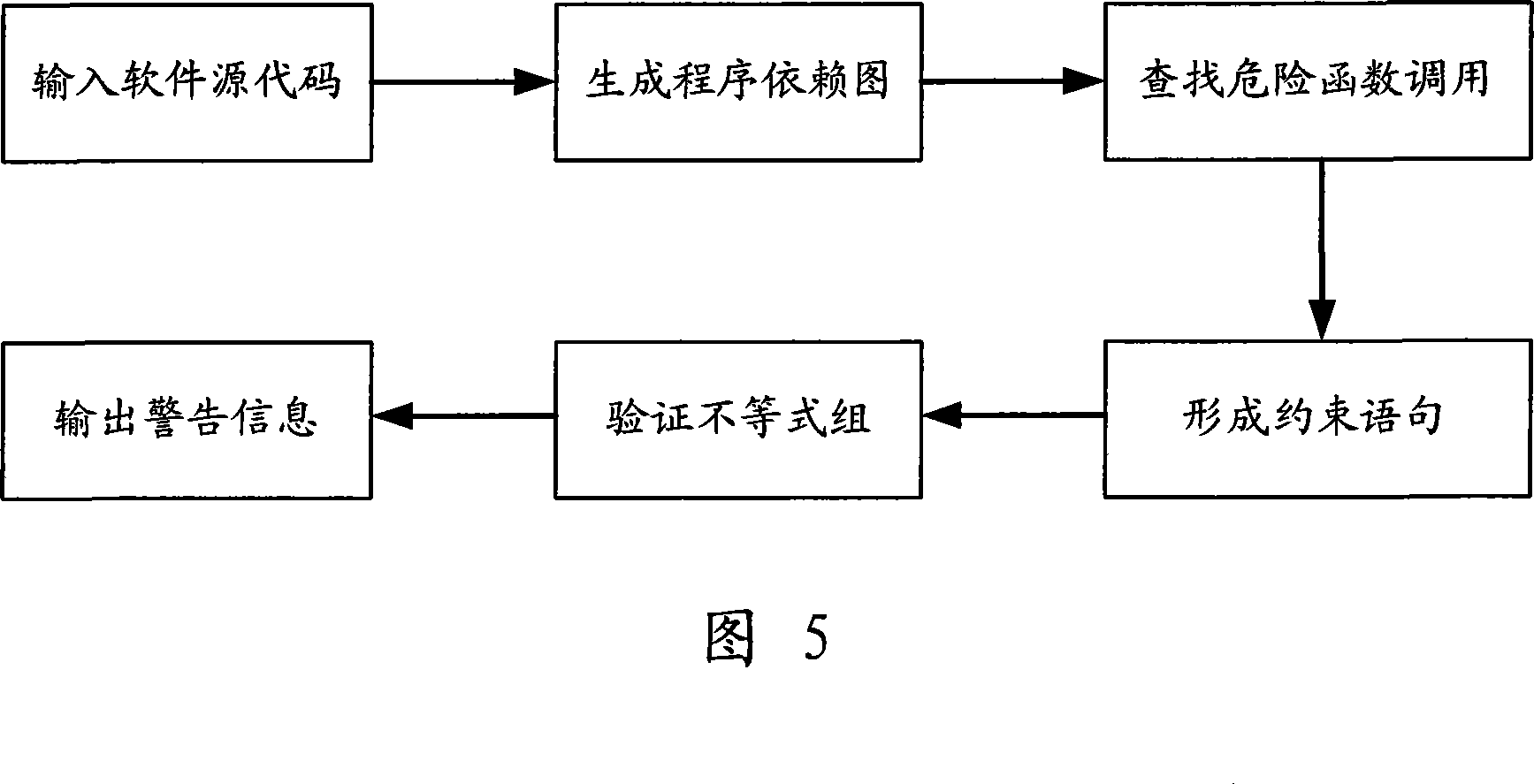
Source code facing buffer overflow detection method based on inequalities solving
InactiveCN101241532ASolve defects that cannot be accurately graspedReduce false alarm rateProgram/content distribution protectionData dependentLength property
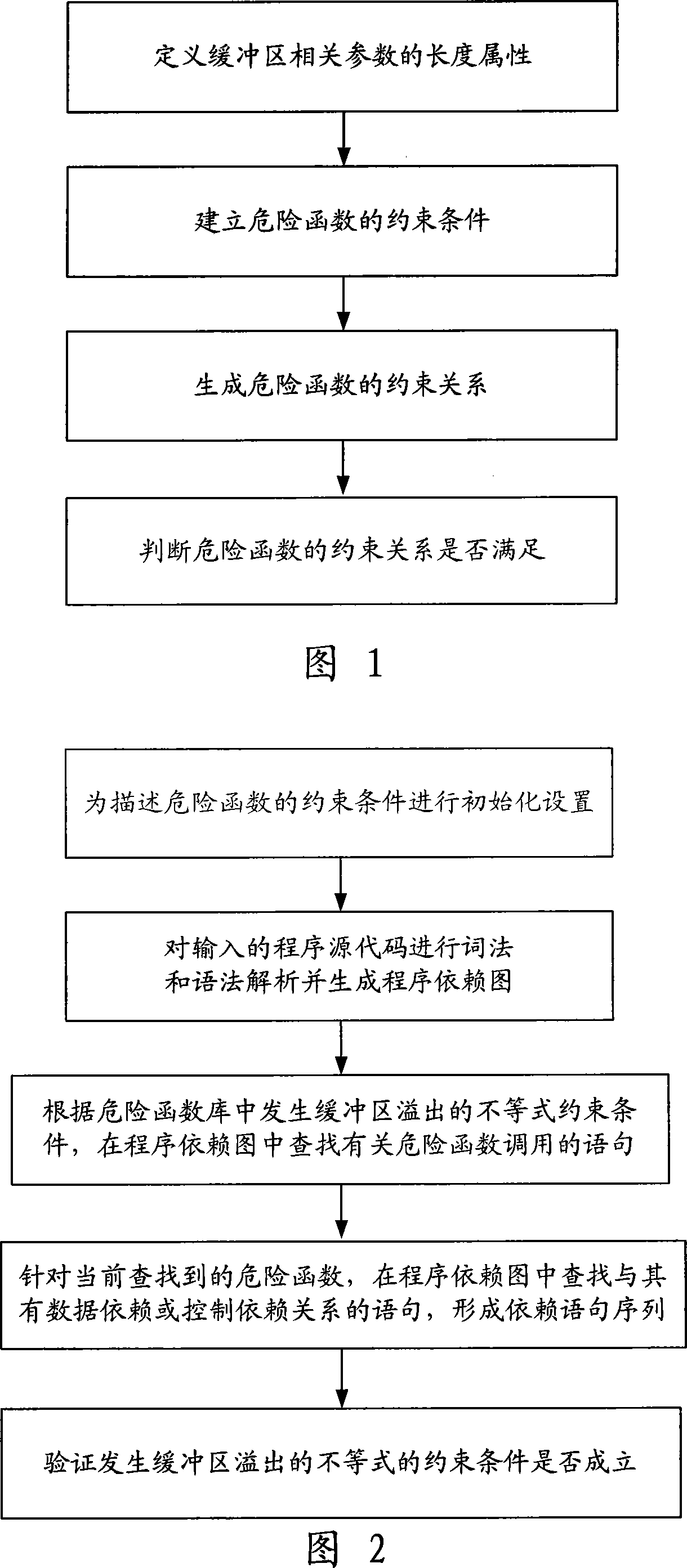
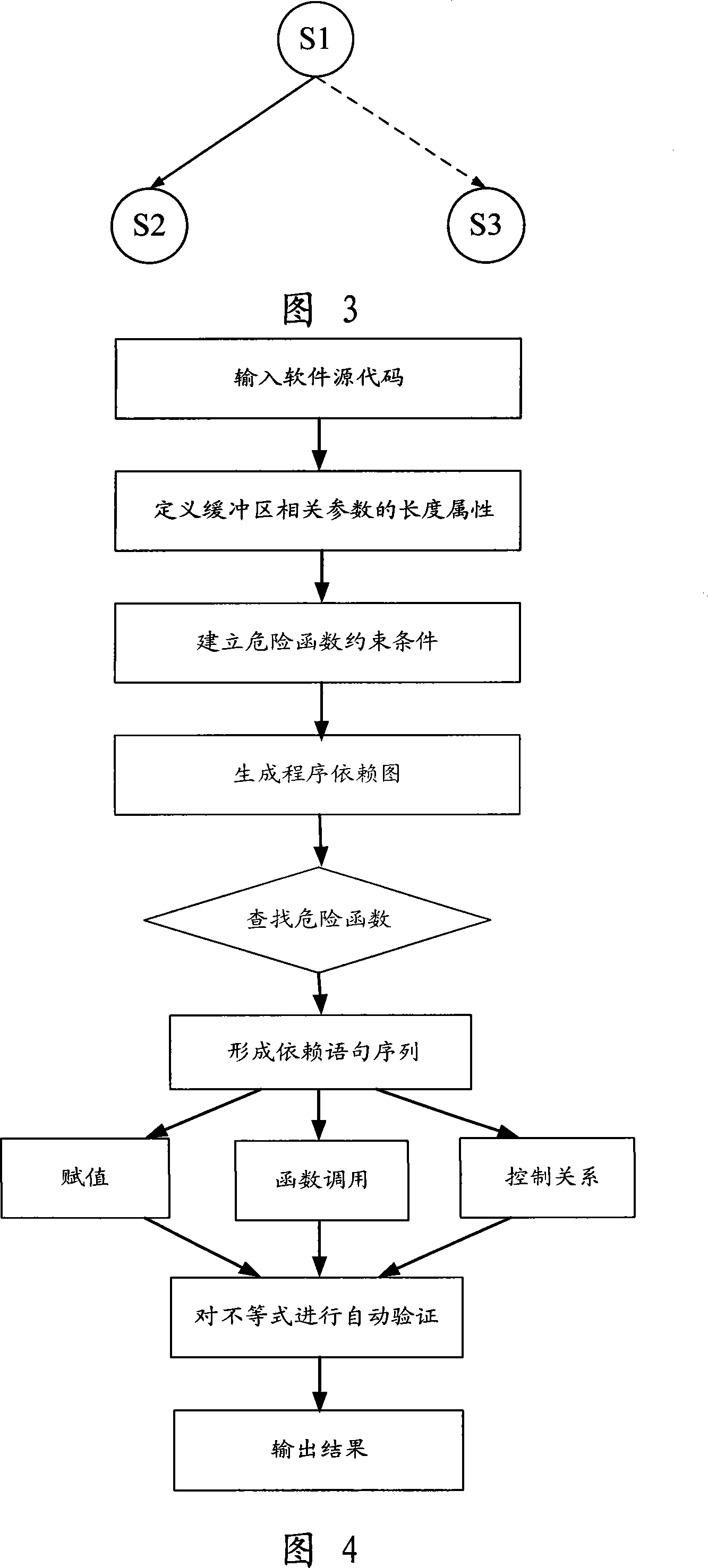
The present invention provides a overflow detecting method of buffer solving based on the set of inequalities faced to the source code, including following steps: (1) processing initialization set in order to describe constraint condition of the risk function; (2) processing morphology and grammar analysis to the input program source code to generate a program dependency graph; (3) finding relative risk function callable statement in the program dependency graph according to inequality constraint condition of the buffer overflow in the risk function base; (4) finding sentence having data dependent or control relation with the risk function in the program dependency graph aimed to the found risk function to form dependent sentence sequence, in other words a set of inequalities; (5) verifying constraint condition of the inequality in the buffer overflow whether establishing or not. The method can greatly resolve the problems of inaccurate grasp fault of the impact of the length property of the buffer variable or parameter when processing program control relation in the present static code analyzing technology, effectively reduces the rate of false alarm of the buffer overflow exploit code.
Owner:BEIJING UNIV OF POSTS & TELECOMM
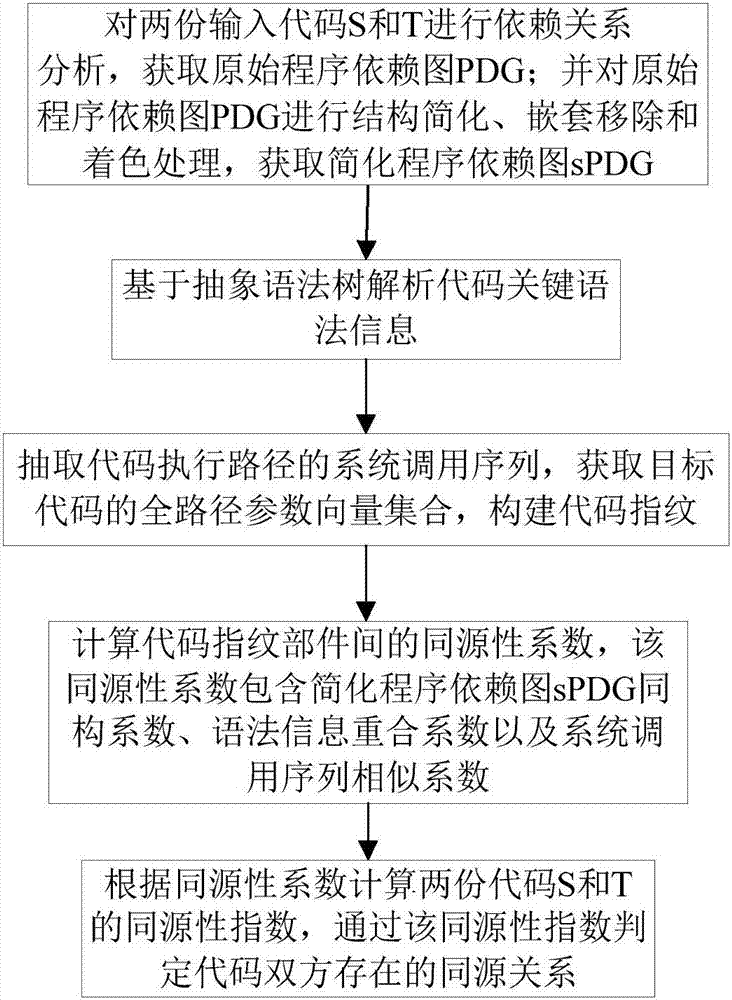
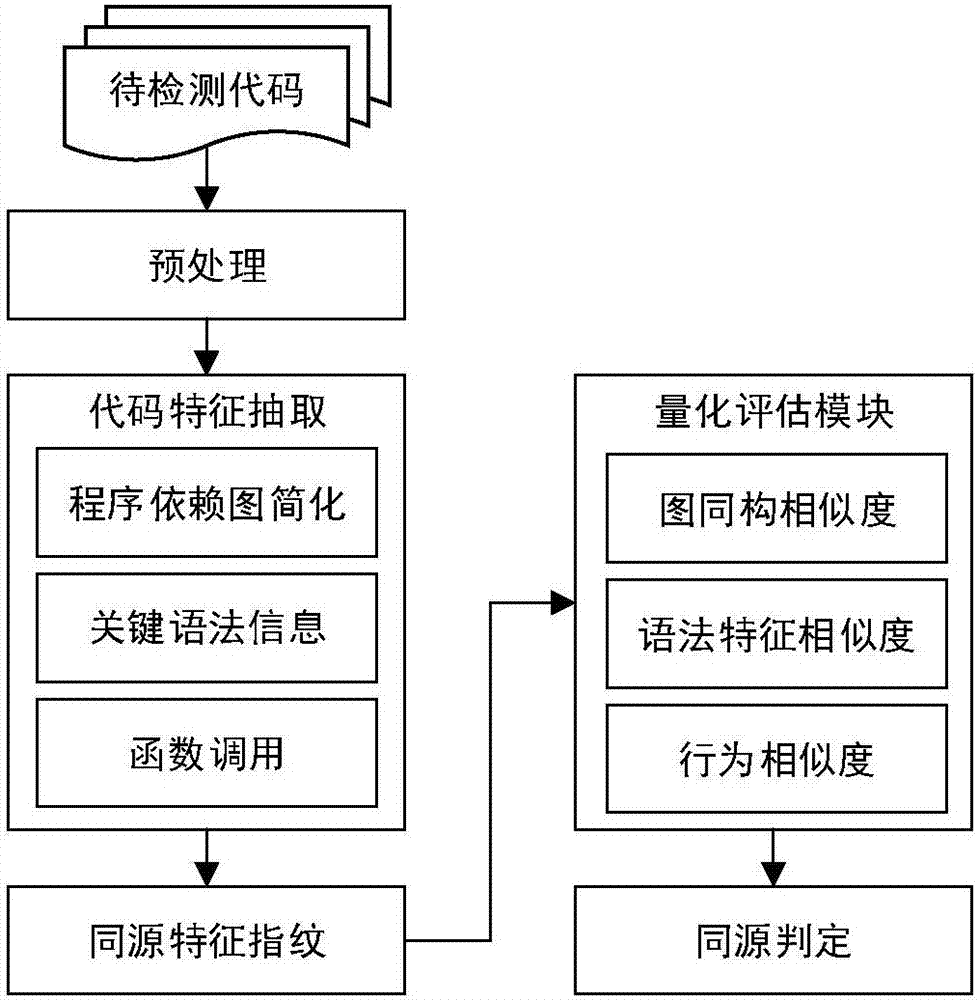
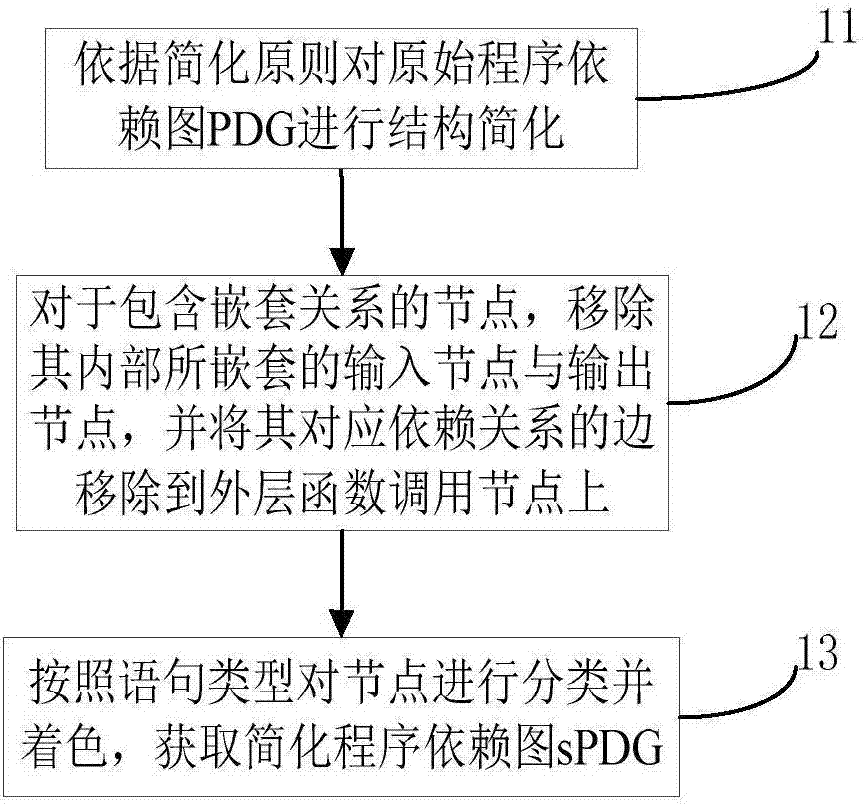
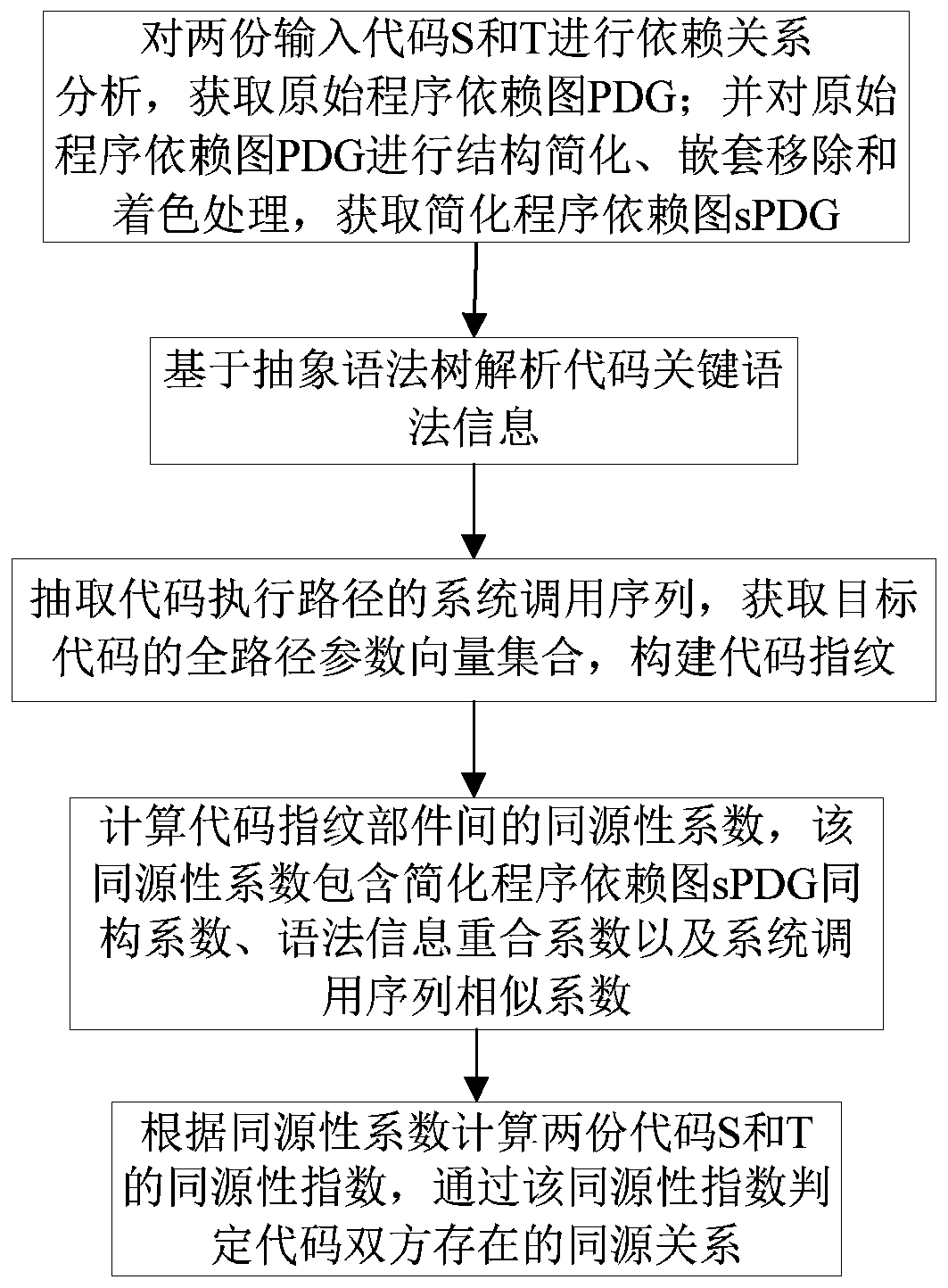
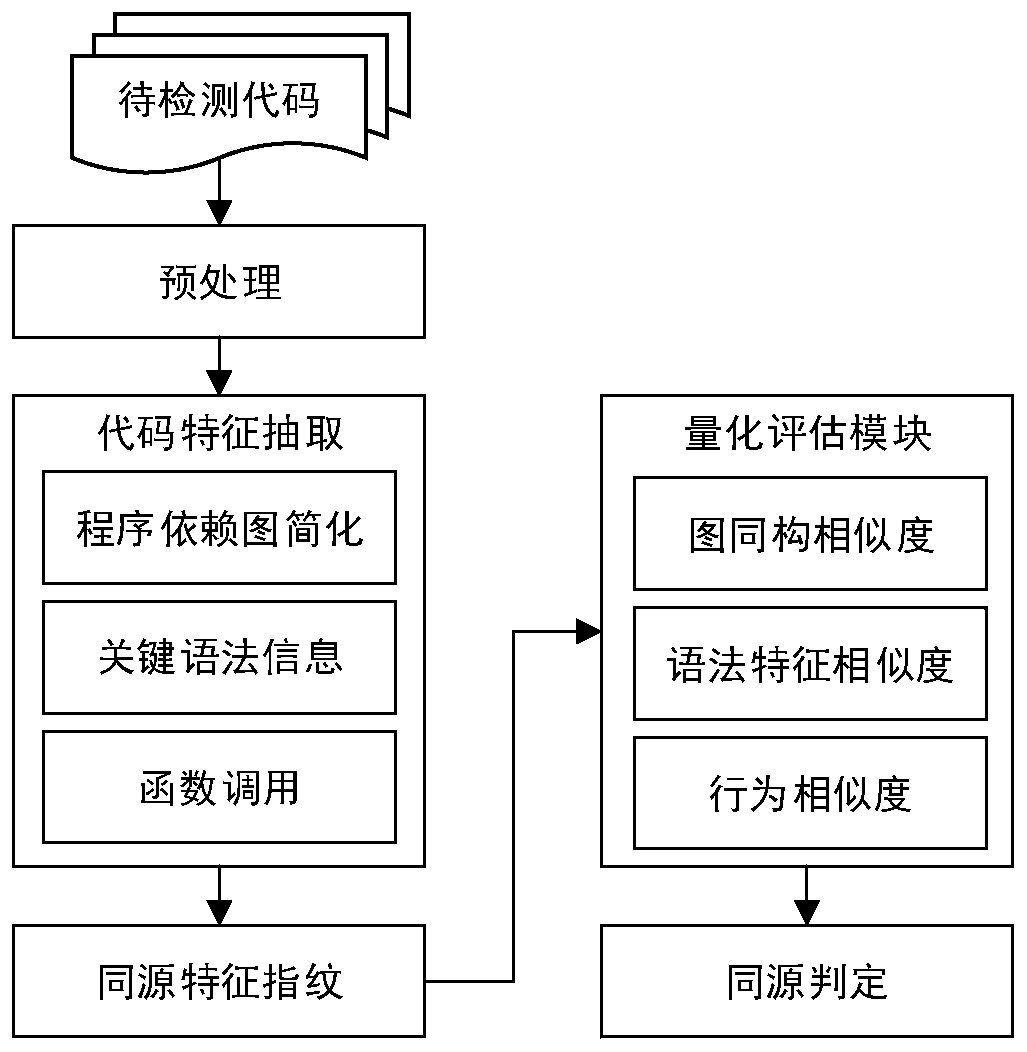
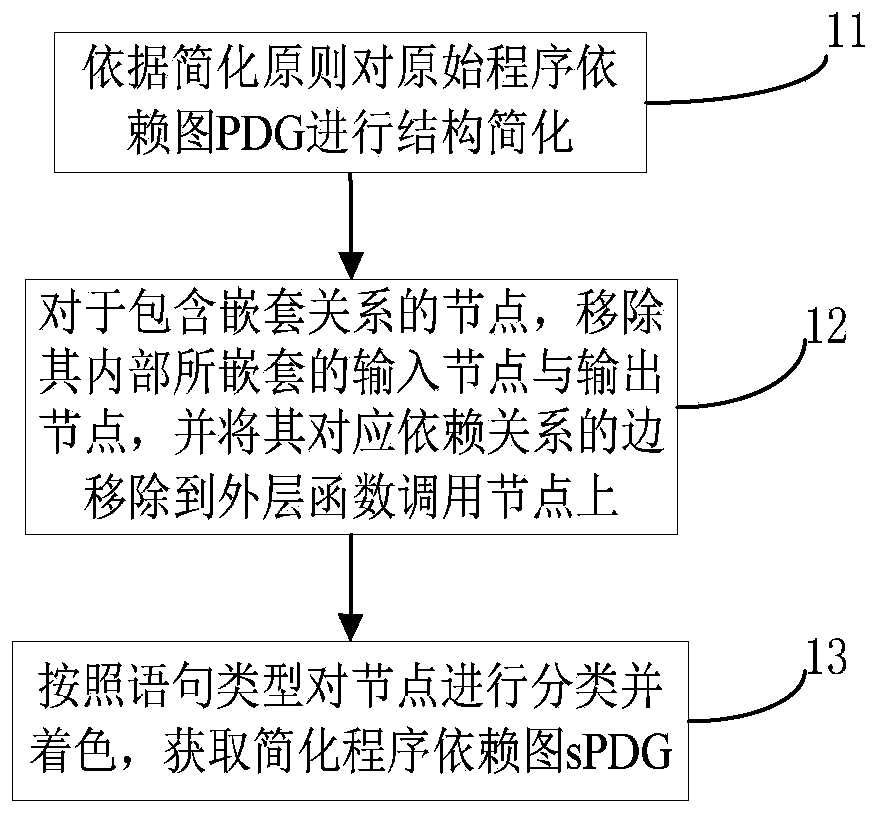
Code homology detection method based on code fingerprint and device thereof
ActiveCN107169358AImprove detection efficiencyImprove accuracyPlatform integrity maintainanceProgram controlObject codeSemantics
The invention relates to a code homology detection method based on code fingerprint and a device thereof. The method comprises: performing dependence analysis on input codes, obtaining an original program dependence graph PDG; performing structure simplification, removing nesting and performing shading on the original program dependence graph PDG, to obtain a simplified program dependence graph sPDG; based on an abstract syntax tree, analyzing code key grammar information; extracting a system call sequence of a code execution path, to obtain a full path parameter vector assembly of an object code, to build code fingerprint; calculating a homology coefficient of code fingerprint components; according to the homology coefficient, calculating a homology index of two codes S and T, and through the homology index, determining a homologous relation exists in the both codes. The method can give consideration to code semantics and behaviors on the basis of similarity, and improves detection efficiency by using a lightweight characteristic and simplified mechanism, and measures homologous relations among codes in a multi-angle manner, and improves detection efficiency while ensuring accuracy.
Owner:THE PLA INFORMATION ENG UNIV +1
Fine-grained vulnerability detection method based on depth features
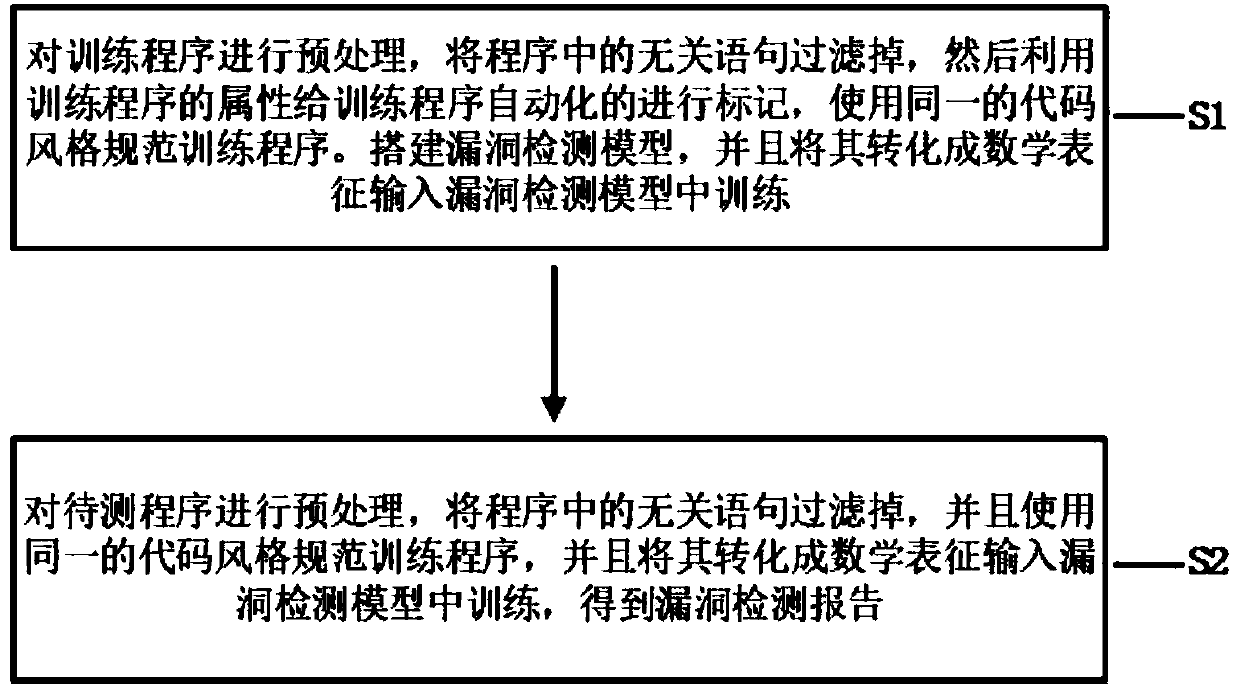
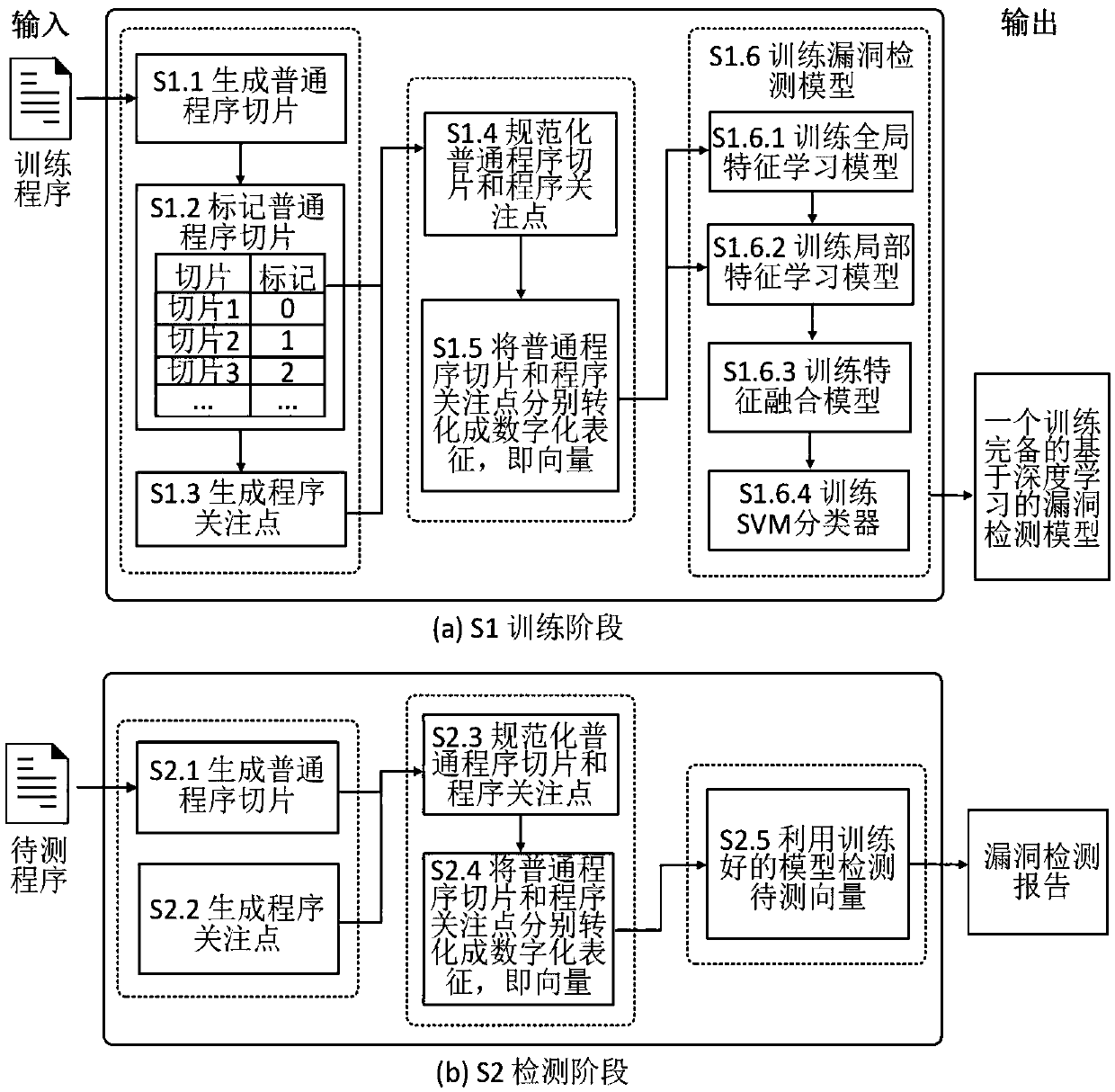
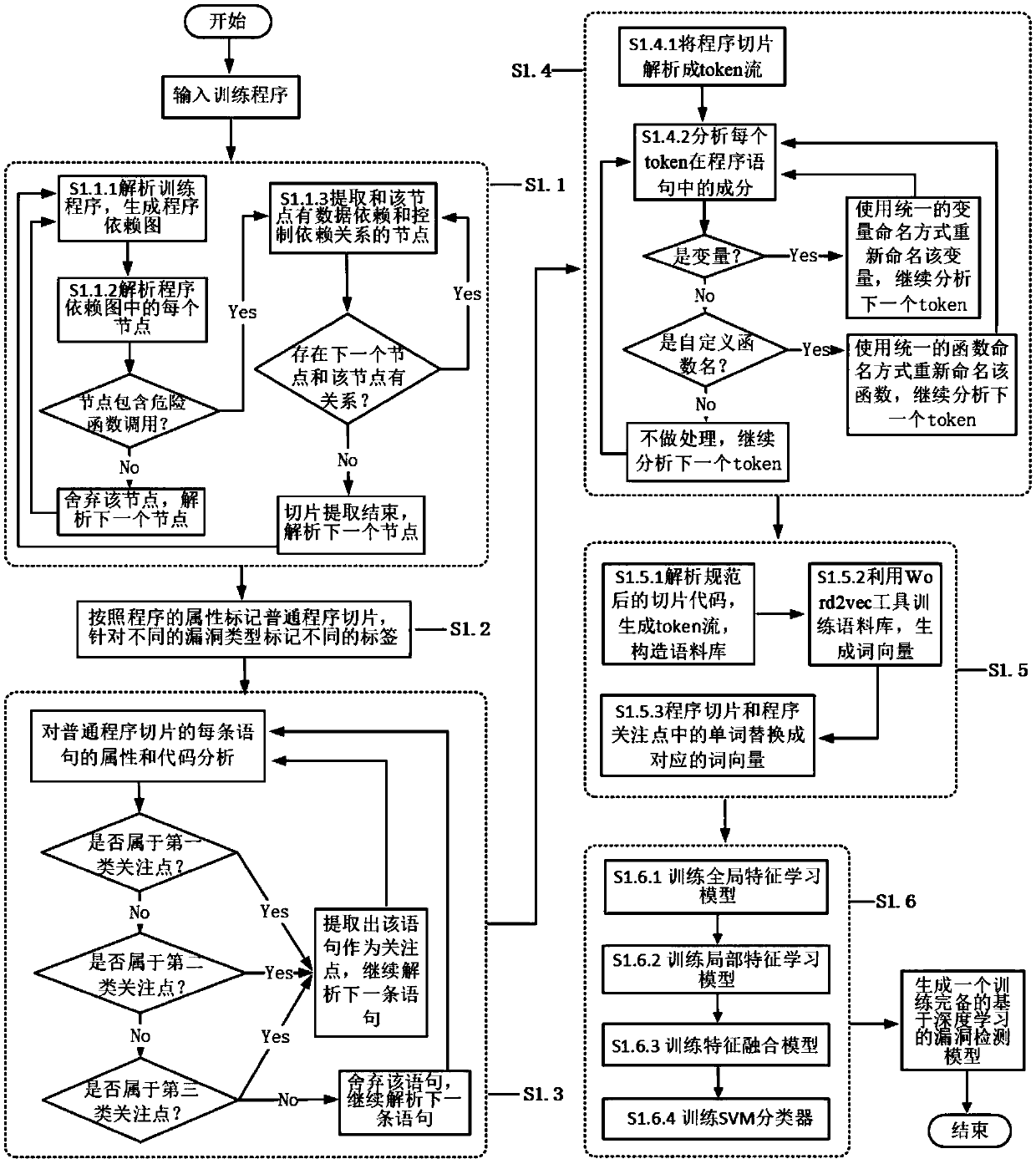
ActiveCN109657473AImprove accuracyRapid positioningNatural language data processingPlatform integrity maintainanceAlgorithmTheoretical computer science
The invention discloses a fine-grained vulnerability detection method based on depth characteristics. The fine-grained vulnerability detection method comprises the following two stages: a training stage and a detection stage. The training stage comprises the steps that a large number of programs with vulnerabilities and without vulnerabilities are collected; Preprocessing the programs, and extracting program slices from the program dependency graph; Labeling the generated program slice according to the vulnerability type; Extracting a program focus point from the program slice according to a security analysis rule; Converting the program slice and the program focus point into vectors; Building a vulnerability detection model based on deep learning, and using vectors to train model parameters to be optimal; And finally, a trained vulnerability detection model based on deep learning is obtained. The detection stage comprises the following steps: extracting a program slice and a program focus point from a program to be detected according to a source code processing mode of the training stage, and respectively converting the program slice and the program focus point into vectors; And classifying the vectors by using the trained vulnerability detection model, and finally generating a vulnerability detection report according to a classification result.
Owner:HUAZHONG UNIV OF SCI & TECH
Error positioning method based on object-oriented program slice spectrum
InactiveCN102750223AImprove the efficiency of error positioning searchSmall scaleSoftware testing/debuggingError locationComputer engineering
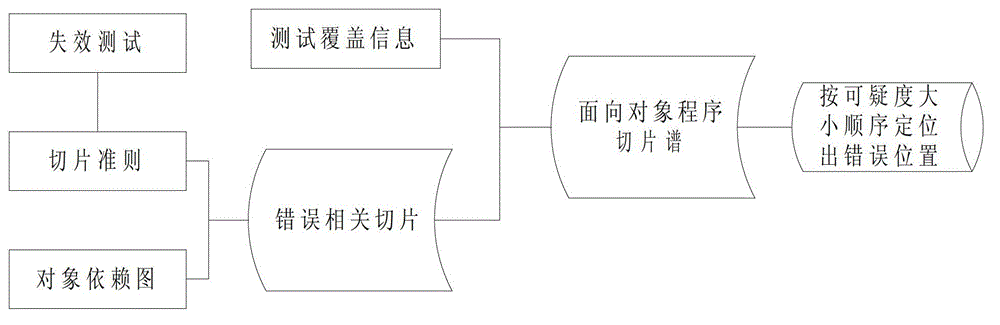
The invention discloses an error positioning method based on an object-oriented program slice spectrum. The error positioning method comprises the following steps of: at first, constructing an object-oriented program dependence graph according to a source program, and extracting slices relative to an error by combining failure test information extracted from a test history; secondly, constructing an object-oriented program slice spectrum matrix according to the slices relative to the error and test coverage information extracted from test history information; and finally, scaling equivocation of each element of the slices relative to the error based on the object-oriented program slice spectrum matrix, and positioning a position of the error according to an equivocation sequence. The error positioning method based on the object-oriented program slice spectrum provided by the invention has higher efficiency.
Owner:SOUTHEAST UNIV
Method, device and system for detecting the safety of terminal source codes
ActiveCN106033516AAutomate analysisImprove detection efficiencyPlatform integrity maintainanceControl flowComputer terminal
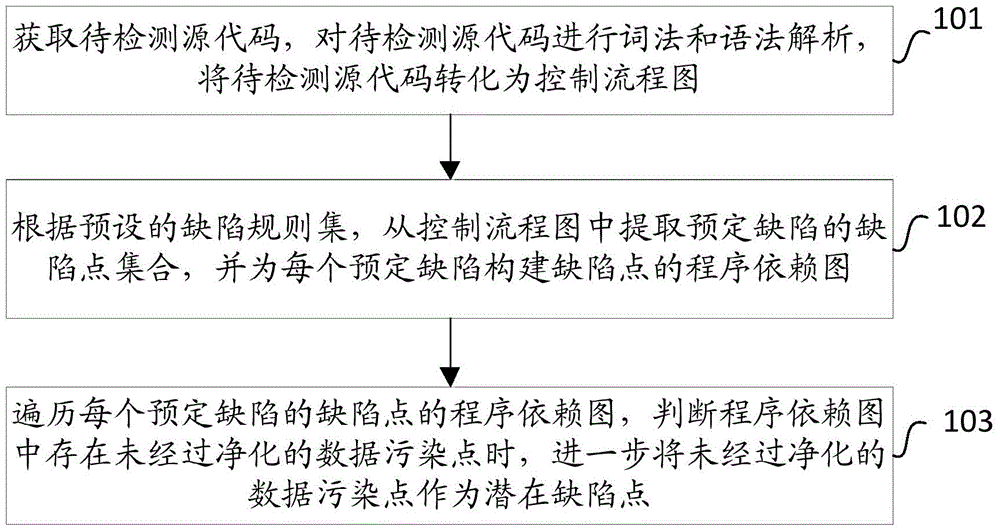
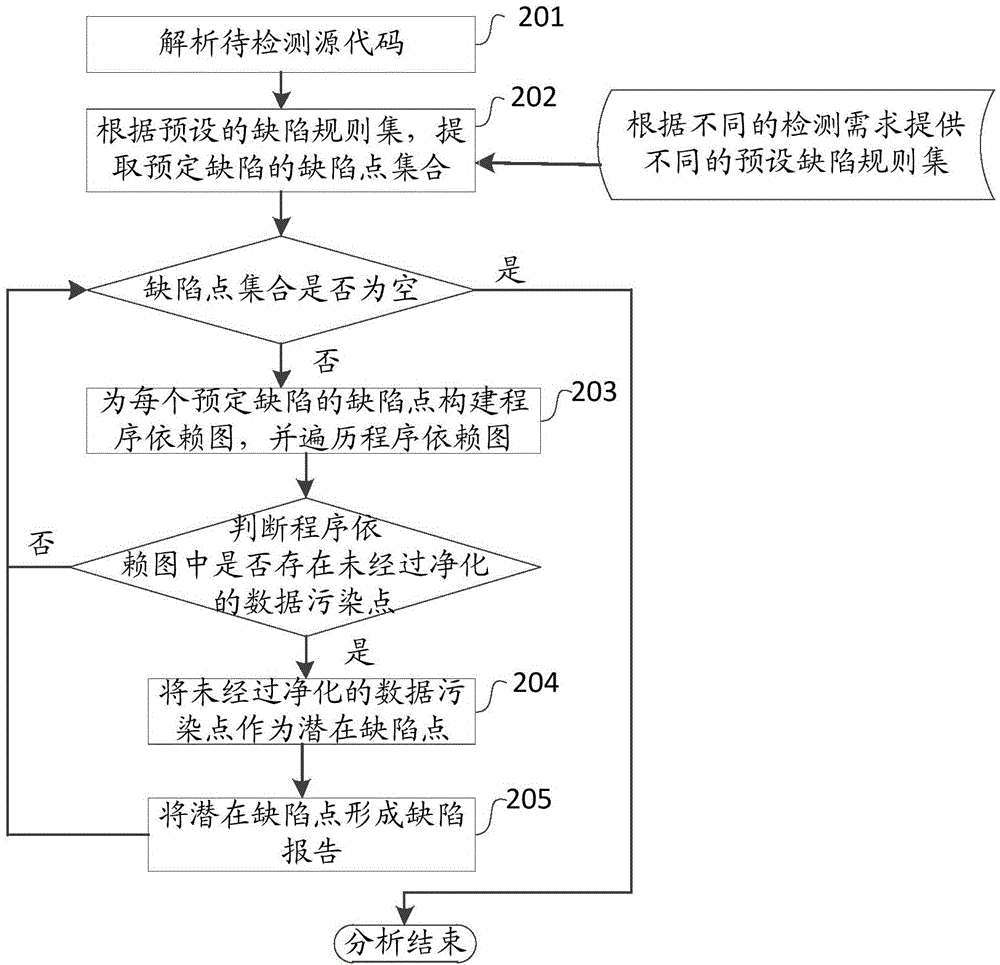
The invention provides a method, device and system for detecting the safety of terminal source codes. The method comprises following steps: obtaining source codes to be detected, performing morphology and grammar analysis on the source codes to be detected and converting the source codes to be detected into a control flow chart; according to a preset defect rule set, extracting defect point set of the preset defect from the control chart and establishing a program dependence chart for defect point of each preset defect; traversing the program dependence chart of defect point of each preset defect, determining that when unpurified data polluted points exist in the program dependence chart, further regarding the unpurified data polluted points as potential defect points. By means of the method, automatic analysis on source codes to be detected is fulfilled to detect existing and potential safety problems of application systems; the defect analysis false report rate is effectively reduced and the detection efficiency is increased.
Owner:中国移动通信集团陕西有限公司
Software security vulnerability detection method based on grammatical features and semantic features
ActiveCN112541180AHigh precisionImprove accuracySoftware testing/debuggingPlatform integrity maintainanceTheoretical computer sciencePerformance index
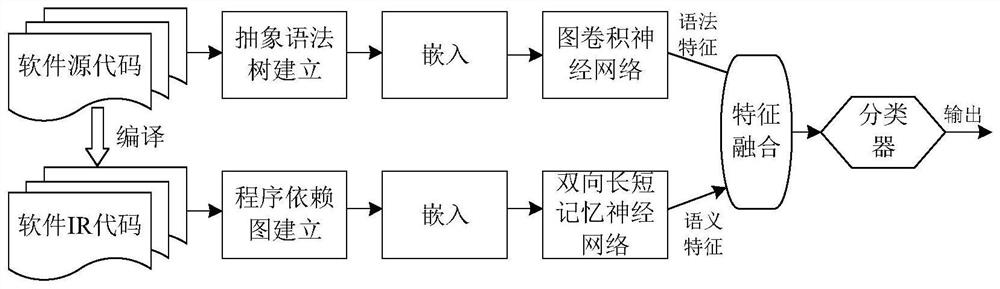
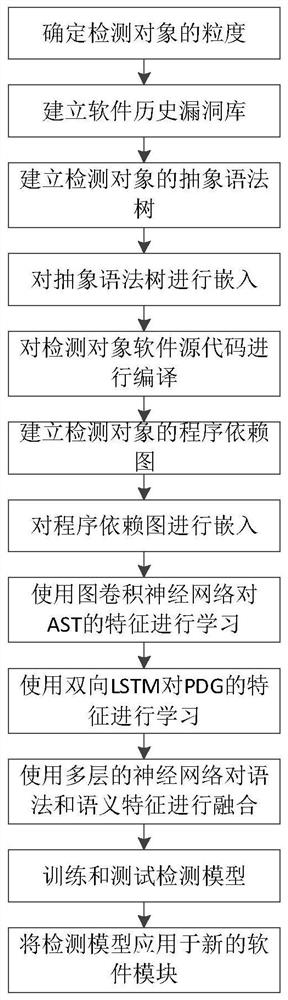
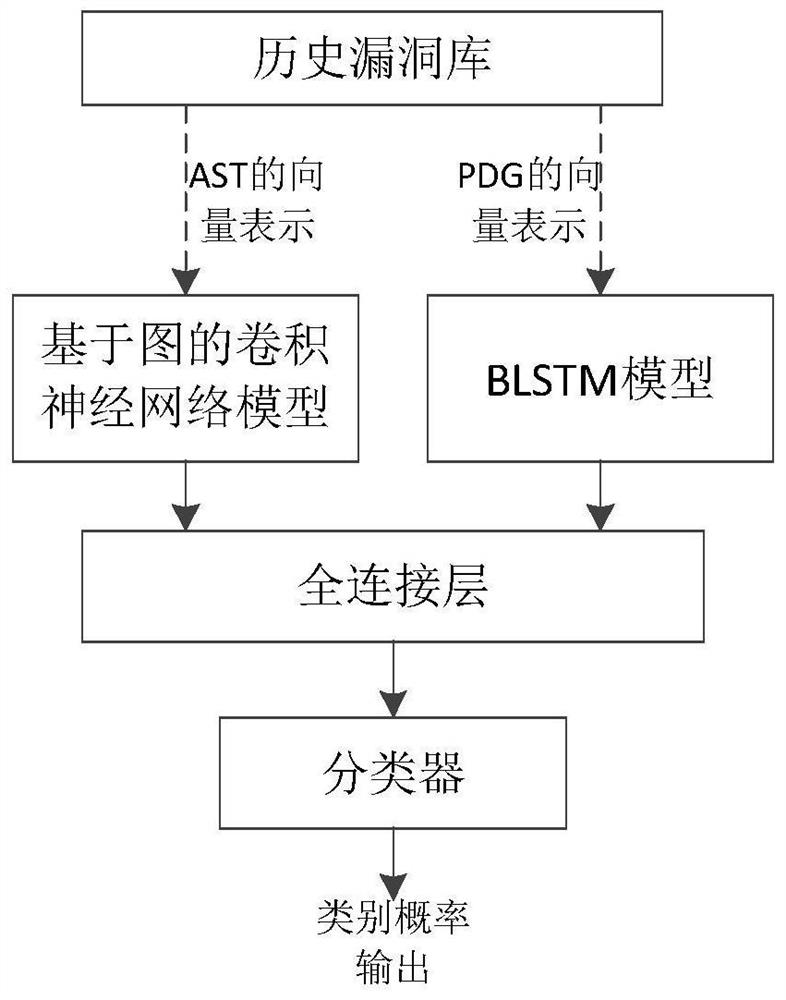
The invention discloses a software security vulnerability detection method based on grammatical features and semantic features. The method comprises the following steps: 1, determining the granularityof a detection object; 2, establishing a software historical vulnerability library; 3, establishing an abstract syntax tree of the detection object; 4, embedding the abstract syntax tree; 5, compiling the source code of the detection object software; 6, establishing a program dependence graph of the detection object; 7, embedding the program dependence graph; 8, learning the features of the AST by using a graph convolutional neural network; and 9, learning the features of the PDG by using a bidirectional LSTM. The method has the advantages that the performance indexes of precision, accuracy and recall rate of the detection model are improved; and an AST tree structure is directly learned by adopting a graph neural network, so that any information is not lost, and the detection performanceof the model can be greatly improved by adopting a feature direct extraction mode based on the graph neural network.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY +1
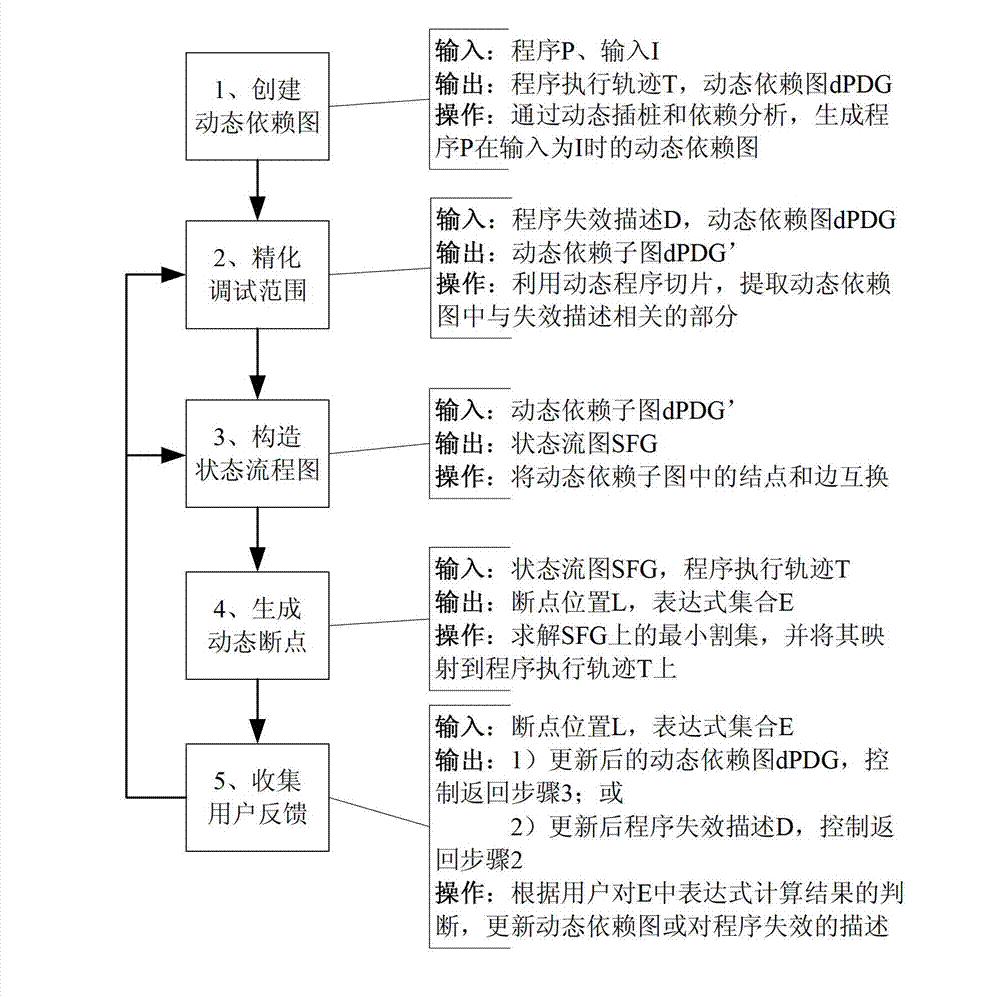
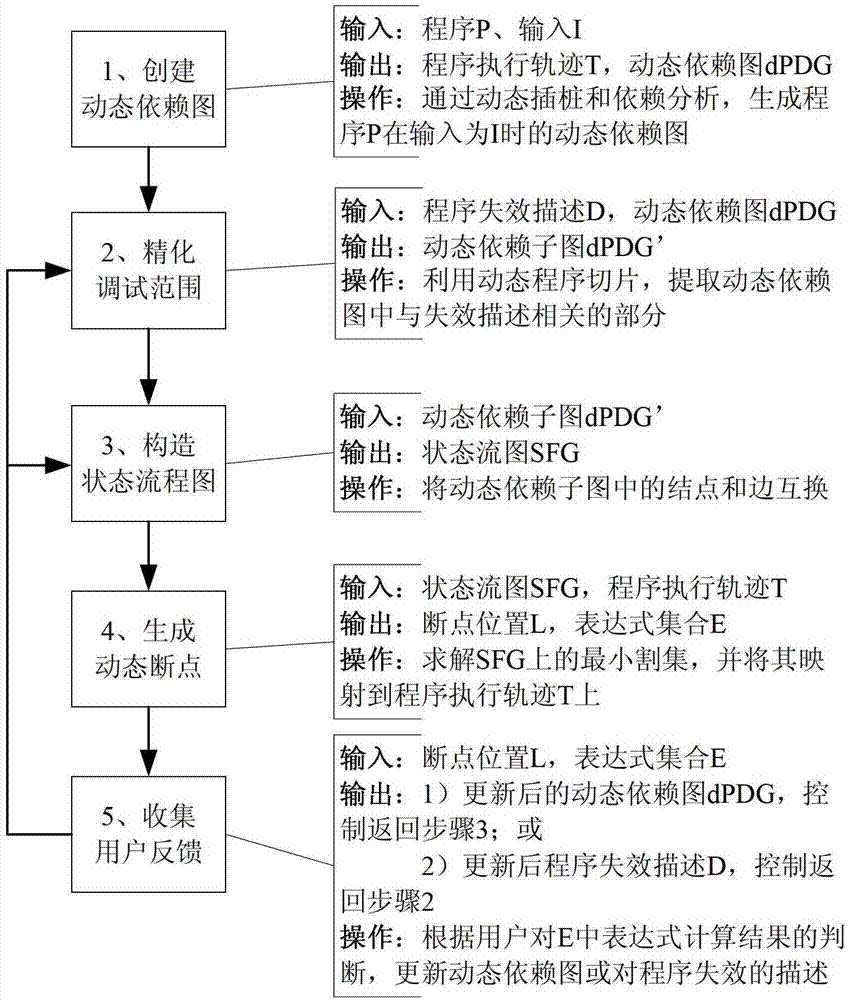
Method and system for automatically generating dynamic breakpoints
ActiveCN102968369AReduce the burden onLess interactive informationSoftware testing/debuggingProgramming languageDynamic instrumentation
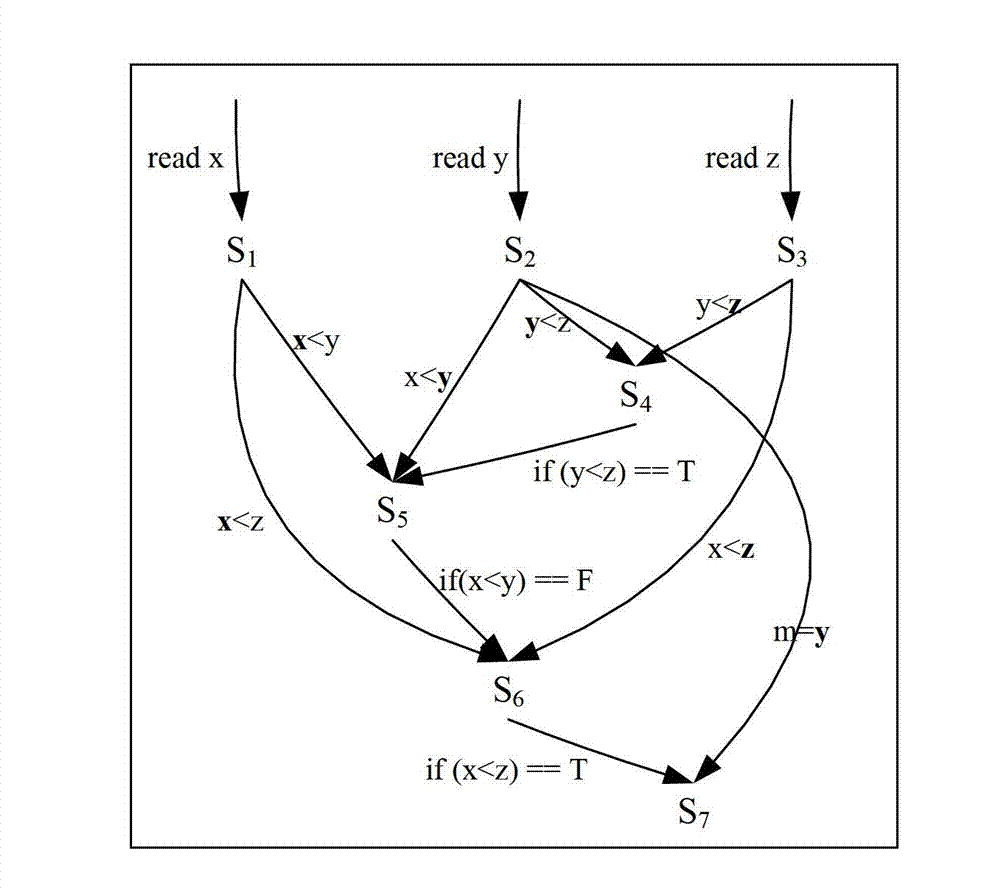
The invention discloses a method and system for automatically generating dynamic breakpoints, wherein the system comprises a dynamic dependence graph creation module, a debugging range refinement module, a state-flow graph creation module, a dynamic breakpoint generation module and a debugging feedback collection module, wherein the dynamic dependency graph creation module is used for not only collecting execution examples of program statements, but also collecting execution sequences and dependency relationship between the examples by utilizing a dynamic instrumentation technique during the program execution process, so as to create a dynamic program dependence graph on the bases; the debugging range refinement module is used for extracting parts of the dynamic program dependence graph relevant with program failure descriptions by utilizing a program dynamic-slicing technique; the state-flow graph creation module is used for interchanging connection points and sides in the dynamic dependence graph output by the debugging range refinement module and transforming a debugging range into a state-flow graph; the dynamic breakpoint generation module is used for generating dynamic breakpoints and aggregations of expressions required being inspected at the breakpoints; and the debugging feedback collection module is used for collecting the results of judgments made by a user about the provided breakpoints and the aggregations of the expressions required being inspected at the breakpoints.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
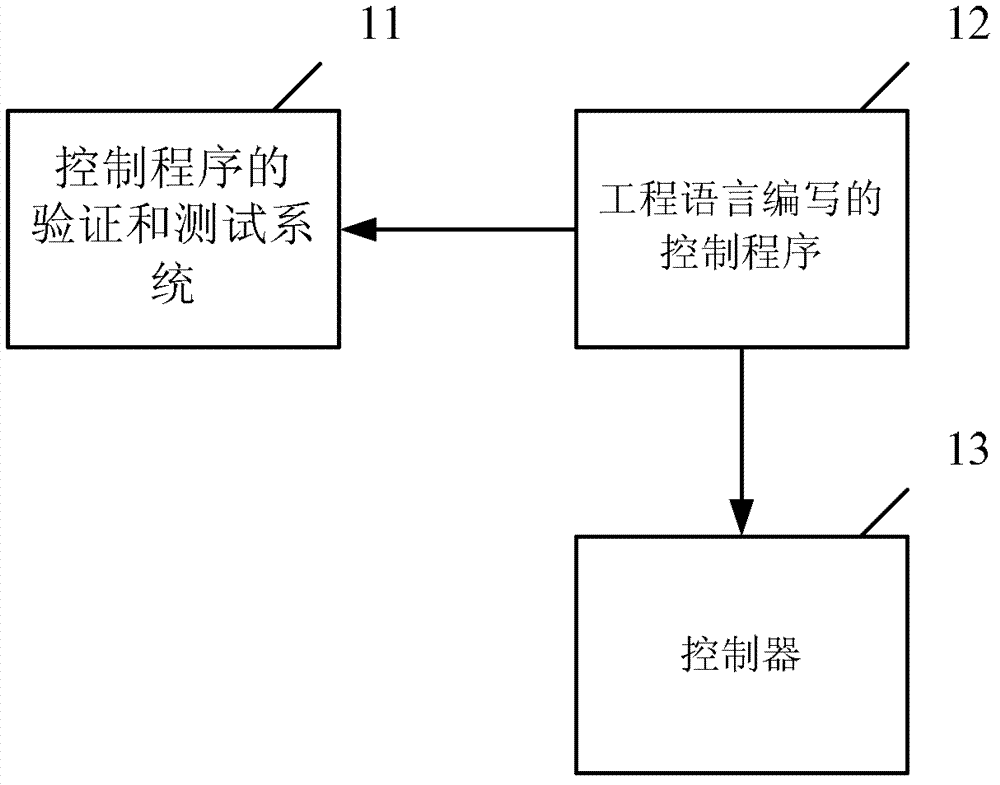
Controlling program verifying and testing method and system thereof
ActiveCN103092747AGuaranteed performanceImprove Simulation EfficiencySoftware testing/debuggingTest performanceComputer module
The invention provides a controlling program verifying and testing method which is used for directly verifying and testing controlling programs compiled in engineering languages so as to improve simulating efficiency and accuracy. The controlling program verifying and testing method includes: an analysis step, performing semantic analysis on a first controlling program compiled in engineering languages, and building a program dependency graph; a transformation step, according to the program dependency graph, transforming the first controlling program to a second controlling program which is supported by a simulation module and represented in general middle level languages; and a simulation step, performing simulation of the second controlling program based on the simulation module to verify and test performance of the second controlling program. The invention further provides a controlling program verifying and testing system.
Owner:SIEMENS AG
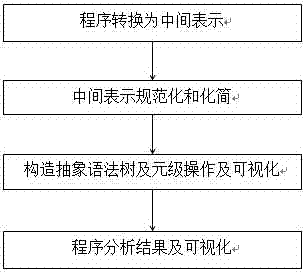
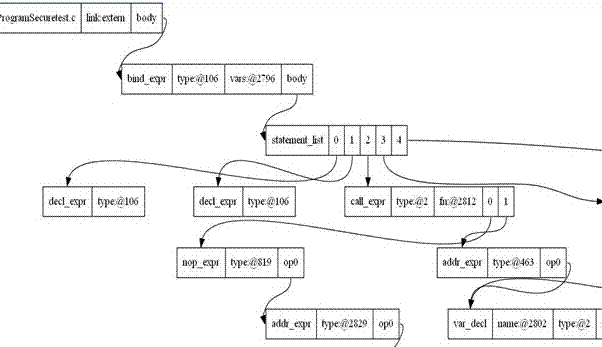
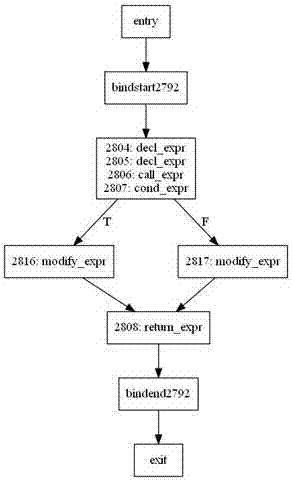
Visualization method and system for program analysis processes
The invention discloses a visualization method and system for program analysis processes. The method includes a program switch module, a standardized processing module, a meta-level operation module and a graphical display module, wherein the program switch module generates intermediate representation of a computer program; the standardized processing module normalizes and simplifies the intermediate representation of the program; the meta-level operation module provides the intermediate representation with a primary program modification mode; the graphical display module extracts information of data flows and control flows of the program, and displays an abstract syntax tree, a control flow diagram and a program dependence graph in a graphical mode. The visualization method and system for program analysis processes have the advantages of visually showing the whole processes of a program analysis, using a graph to demonstrate the result of the program analysis, and helping students better understand analysis processes and analysis methods of programs.
Owner:郭德贵
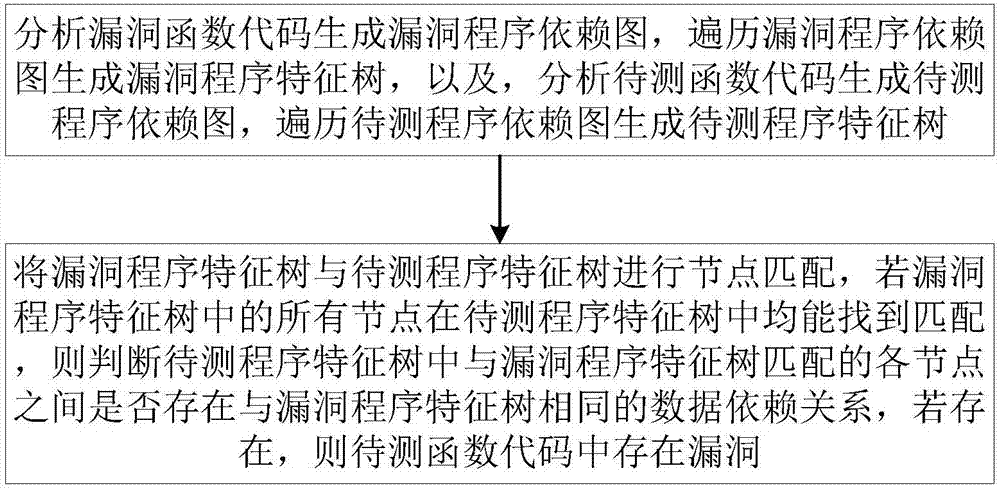
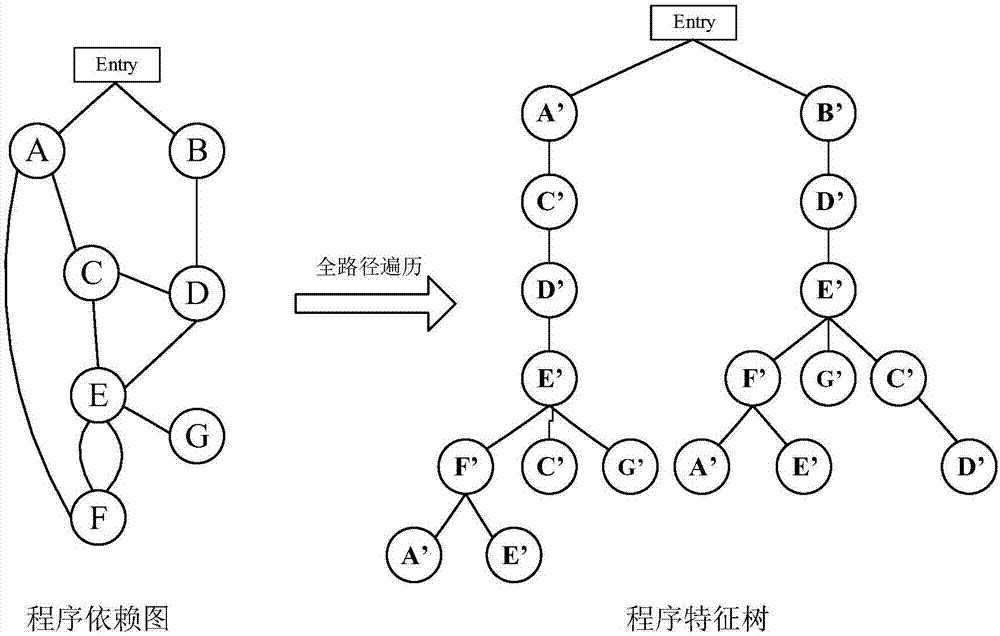
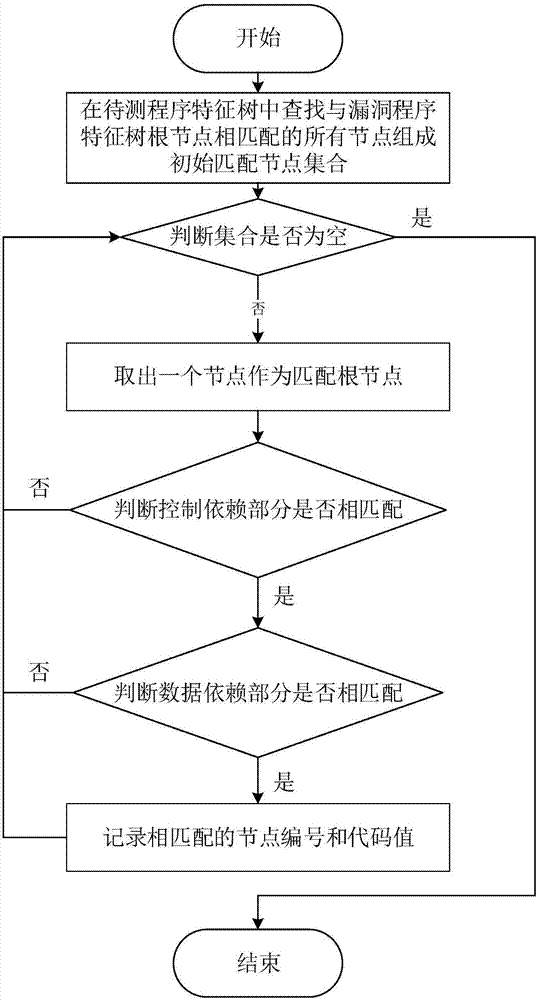
Bug detection method and system based on program characteristic tree
ActiveCN107038380AFully consider semantic featuresReduce false alarm rateSoftware testing/debuggingPlatform integrity maintainanceTheoretical computer scienceData dependence
The invention discloses a bug detection method and a bug detection system based on a program characteristic tree. The implementation method comprises the steps of analyzing a bug function code to generate a bug program dependence graph, traversing the bug program dependence graph to generate a bug program characteristic tree; analyzing a to-be-detected function code to generate a to-be-detected program dependence graph, traversing the to-be-detected program dependence graph to generate a to-be-detected program characteristic tree; carrying out node matching on the bug program characteristic tree and the to-be-detected program characteristic tree; if all nodes in the bug program characteristic tree can be matched with the nodes in the to-be-detected program characteristic tree, judging whether a data dependence relation of the to-be-detected program characteristic tree which is the same as that of the bug program characteristic tree exists between the matched nodes in the bug program characteristic tree and the to-be-detected program characteristic tree; and if so, judging that a bug exists in the to-be-detected function code. According to the method and the system, the execution efficiency of bug detection can be remarkably improved while guaranteeing the detection accuracy.
Owner:HUAZHONG UNIV OF SCI & TECH
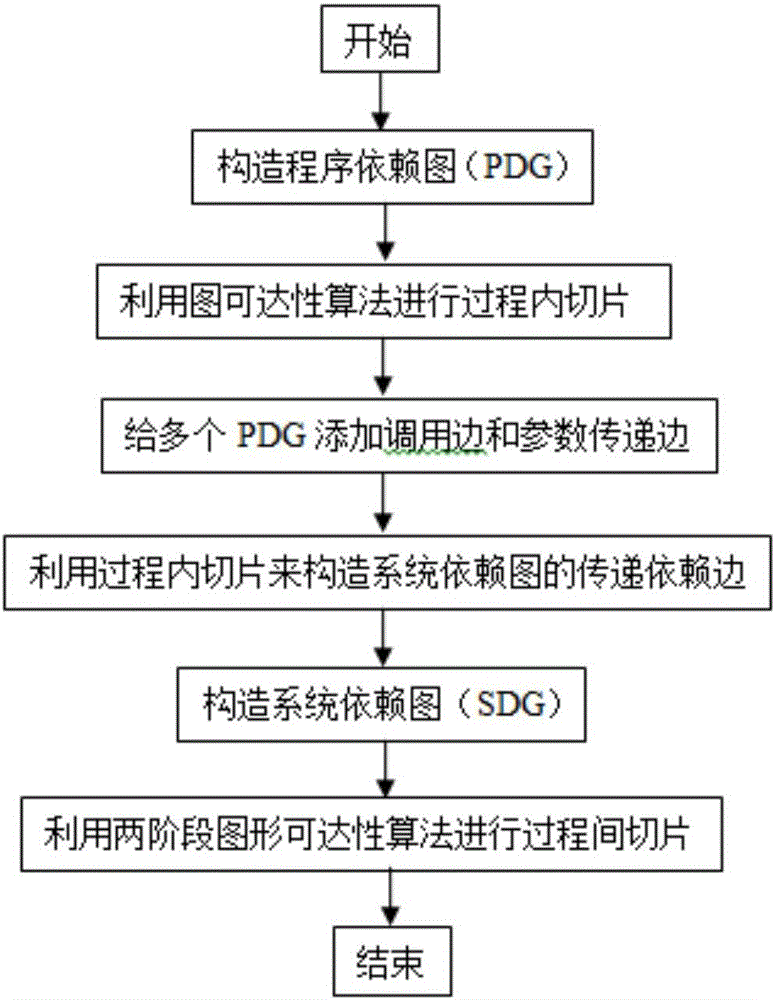
LLVM IR program slicing method based on improved system dependence graph
InactiveCN105700893AHigh precisionImprove general performanceReverse engineeringSoftware testing/debuggingGraphicsRound complexity
The invention discloses an LLVM IR program slicing method based on an improved system dependency graph. First, construct a program dependency graph; then use the graph reachability algorithm to slice the LLVM IR statement of a single program; and then expand the analysis of a single program according to the calling relationship between programs and the corresponding relationship between actual parameters and formal parameters Go to multiple programs; then use a new method to construct transitive dependency edges, and then complete the construction of the system dependency graph; finally, use the two-stage graph reachability algorithm to traverse the system dependency graph to complete the slicing of multiple programs. . The present invention greatly reduces the time complexity of slicing.
Owner:NANJING UNIV OF POSTS & TELECOMM
Communication device and method for updating software thereof
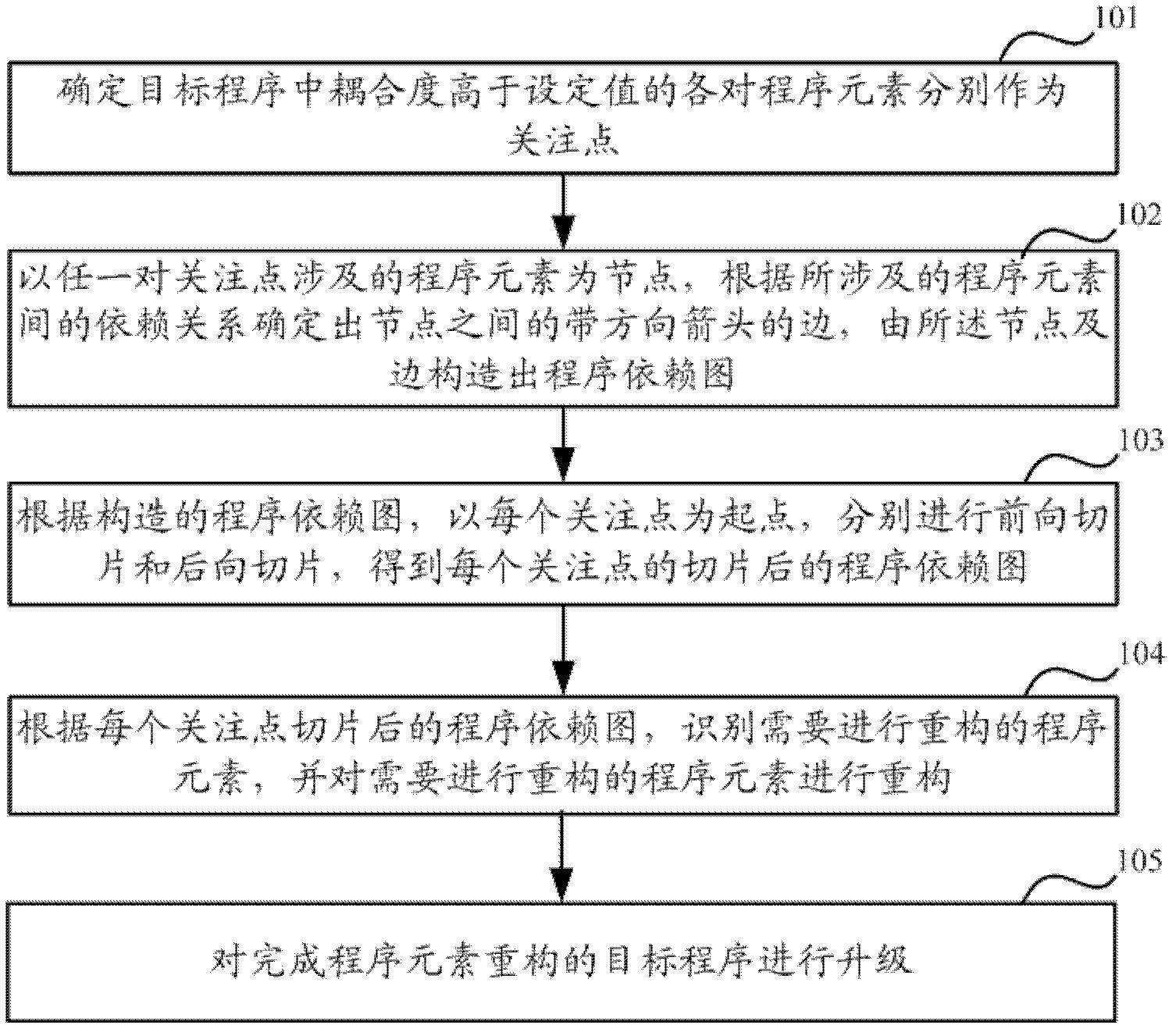
ActiveCN102541592AEasy to refactorImprove upgrade efficiencyProgram loading/initiatingEntry pointCoupling
The invention discloses a communication device and a method for updating software thereof. The method comprises determining each pair of program elements with coupling degree higher than a set value in a target program to respectively serve as focus points; enabling the relevant program elements of any pair focus points to serve as nodes, determining the edges of arrows with directions between the nodes according to the dependent relations between the relevant program elements, and constructing a program dependent graph through the nodes and the edges; performing forward slicing and backward slicing according to a slicing principle with each focus point serving as a starting point respectively according to the constructed program dependent graph, and acquiring the program dependent graph after slicing of the corresponding focus points; and identifying the program elements needing to be reconstructed according to the program dependent graph after slicing. The communication device and the method for updating the software of the communication device construct the dependent graph with the coupling degree serving as an entry point. Compared with cohesion, the coupling degree can reflect the interaction relation between the elements in the program so as to facilitate the reconstruction between analysis classes. The slicing technology is introduced so as to increase the accuracy of measurement.
Owner:DATANG MOBILE COMM EQUIP CO LTD +1
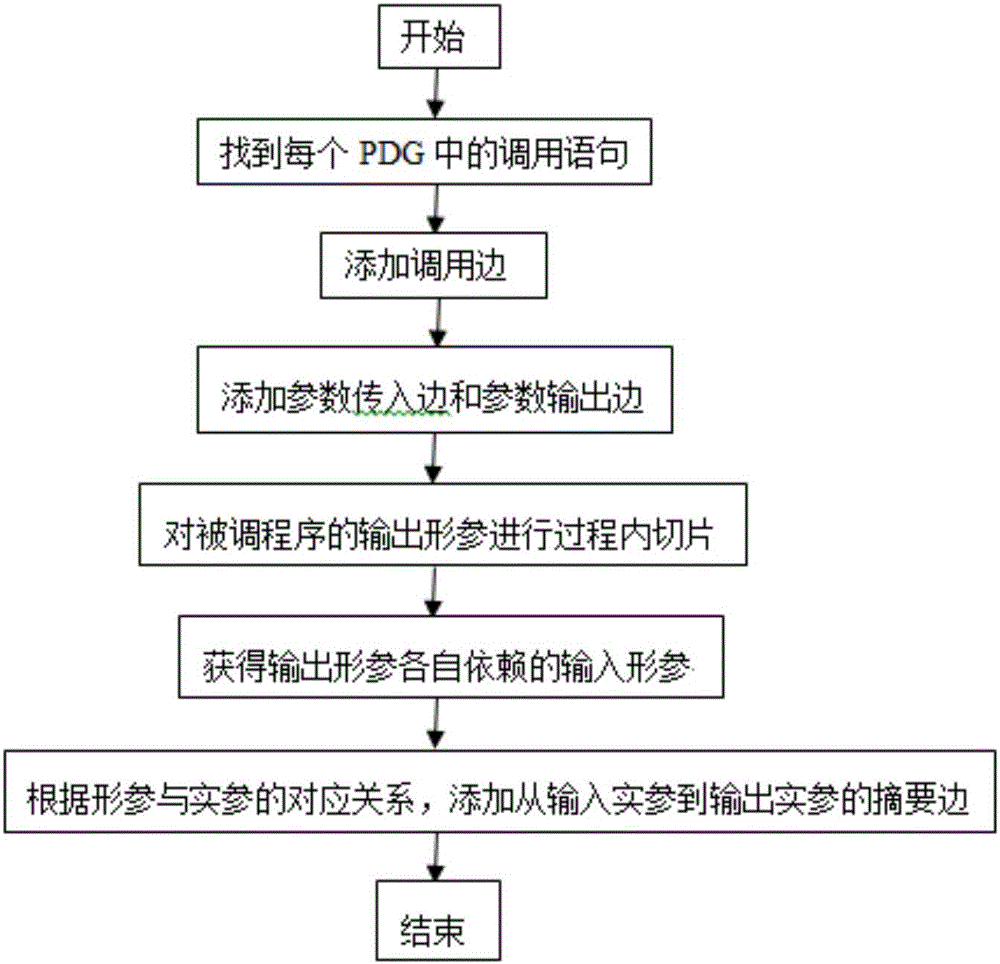
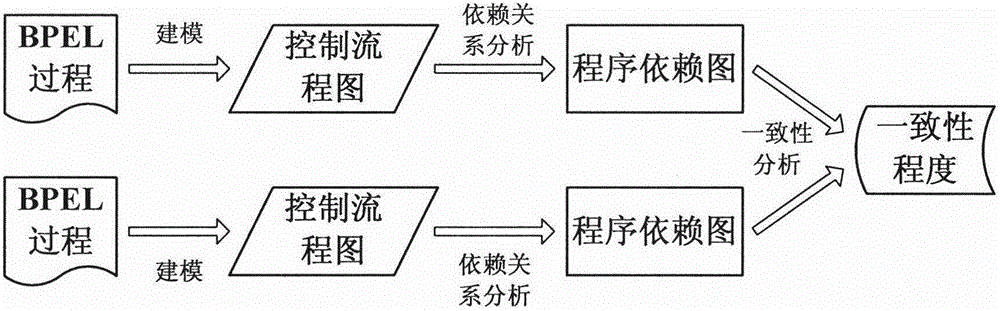
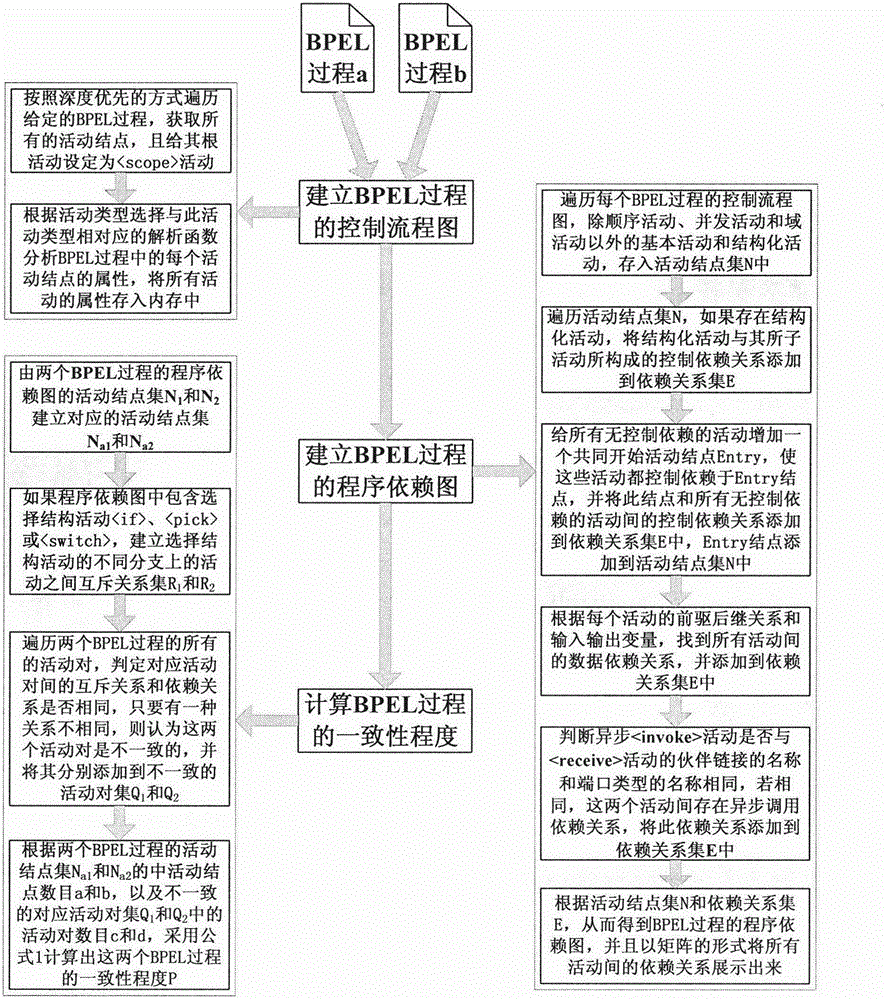
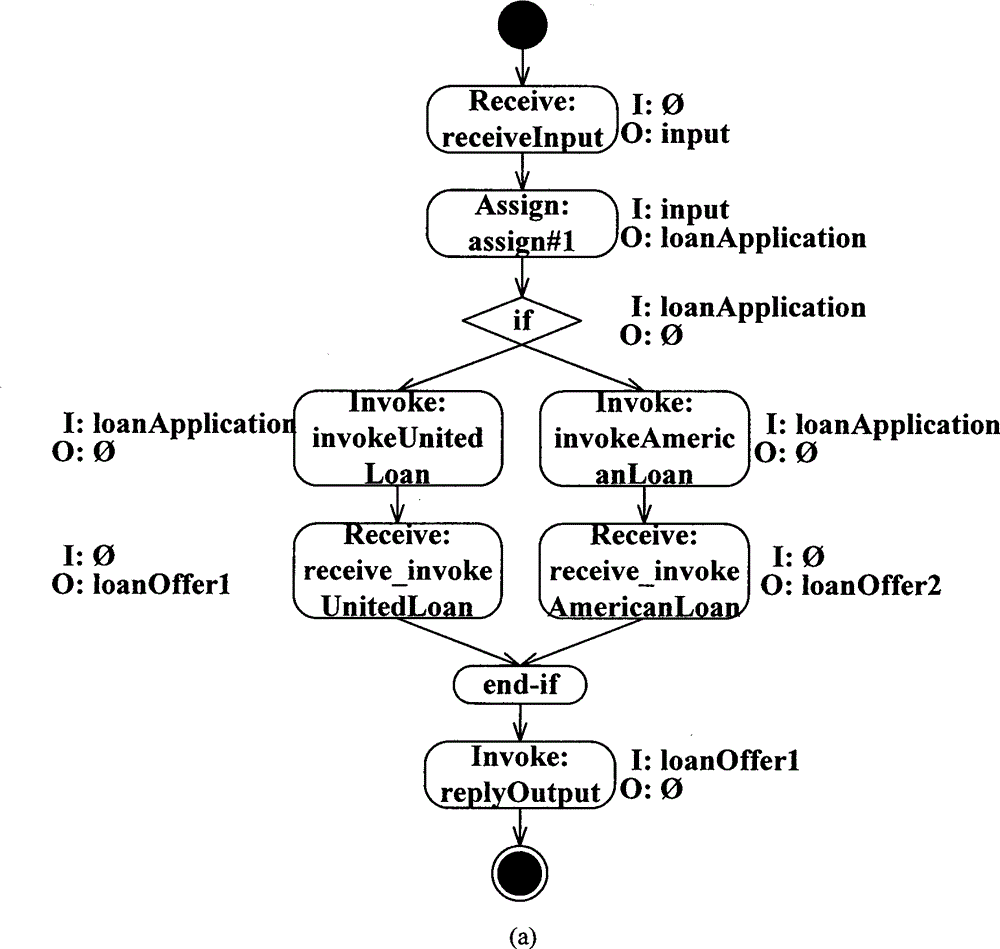
Program dependence graph-based BPEL (Business Process Execution Language) process consistency measurement method
The invention discloses a program dependence graph-based BPEL process consistency measurement method. Two BPEL processes are inputted, and the consistency degree of the two BPEL processes is an output result; the BPEL processes used by the method need to strictly come up to the WS-BPEL2.0 specifications, and moreover, the processes do not contain (link) activities; according to the characteristics of the BPEL, the two BPEL processes are respectively converted into control flow diagrams; according to the control flow diagram of each BPEL process, three dependencies between activities are analyzed, and a program dependence graph (PDG) is generated; and on the basis of the program dependence graphs of the two BPEL processes, the consistency degree of the two BPEL processes is worked out. The method provided by the invention can provide a value from 0 to 1 for the consistency of the two BPEL processes, unlike the conventional method which only provides a qualitative conclusion (consistency or inconsistency), and thereby different degrees of BPEL process consistency can be effectively differentiated.
Owner:NANJING UNIV OF SCI & TECH
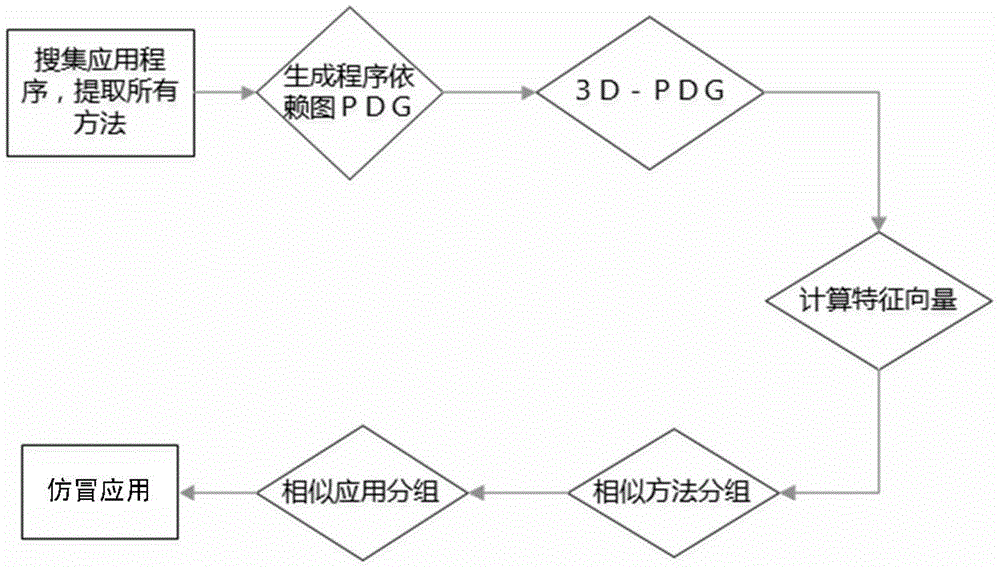
Android platform counterfeit application detection method based on program dependency graph
Owner:INST OF INFORMATION ENG CAS
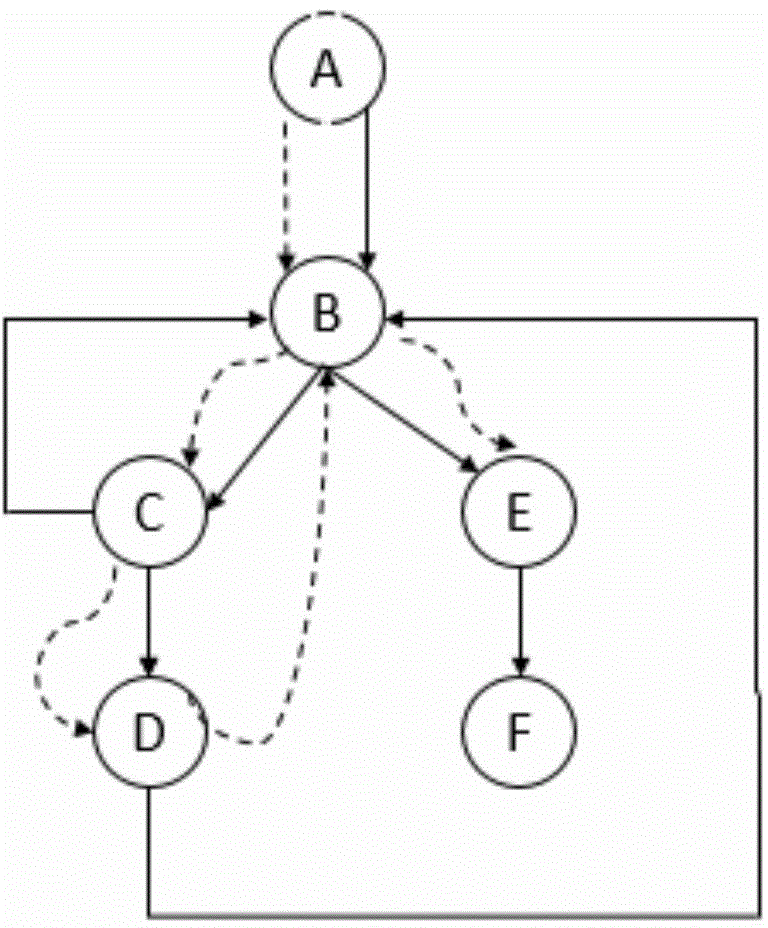
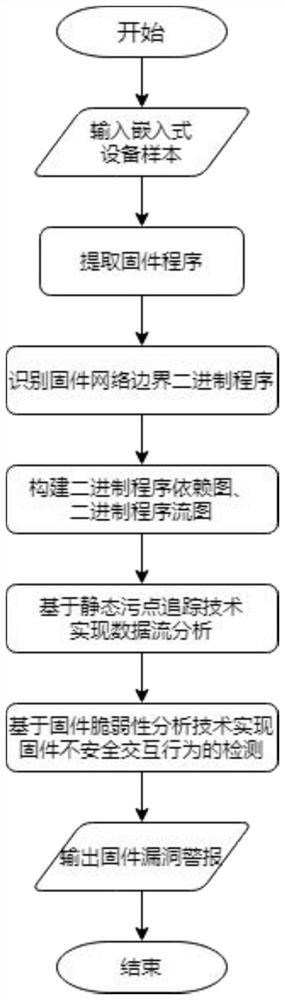
Firmware unknown vulnerability detection method based on vulnerability analysis
The invention discloses a firmware unknown vulnerability detection method based on vulnerability analysis. The method comprises the following steps: step 1, collecting a target binary program of Internet of Things equipment firmware; 2, based on the target binary program of the firmware of the Internet of Things device obtained in the step 1, determining an interactive binary program in a firmware sample of the Internet of Things device; 3, based on the interactive binary program in the firmware sample of the Internet of Things equipment in the step 2, constructing a program dependence graph; 4, based on the program dependence graph in the step 3, data flow tracking of the Internet of Things equipment firmware binary program is conducted; 5, binary program unsafe interaction behavior detection is achieved based on data flow tracking and firmware vulnerability analysis in the step 4, and unknown vulnerabilities in the firmware of the Internet of Things device are determined; and 6, verifying and detecting unknown vulnerabilities in the binary program with vulnerability. The method is used for overcoming the defects of an existing networking device firmware vulnerability detection method based on static analysis.
Owner:HARBIN INST OF TECH
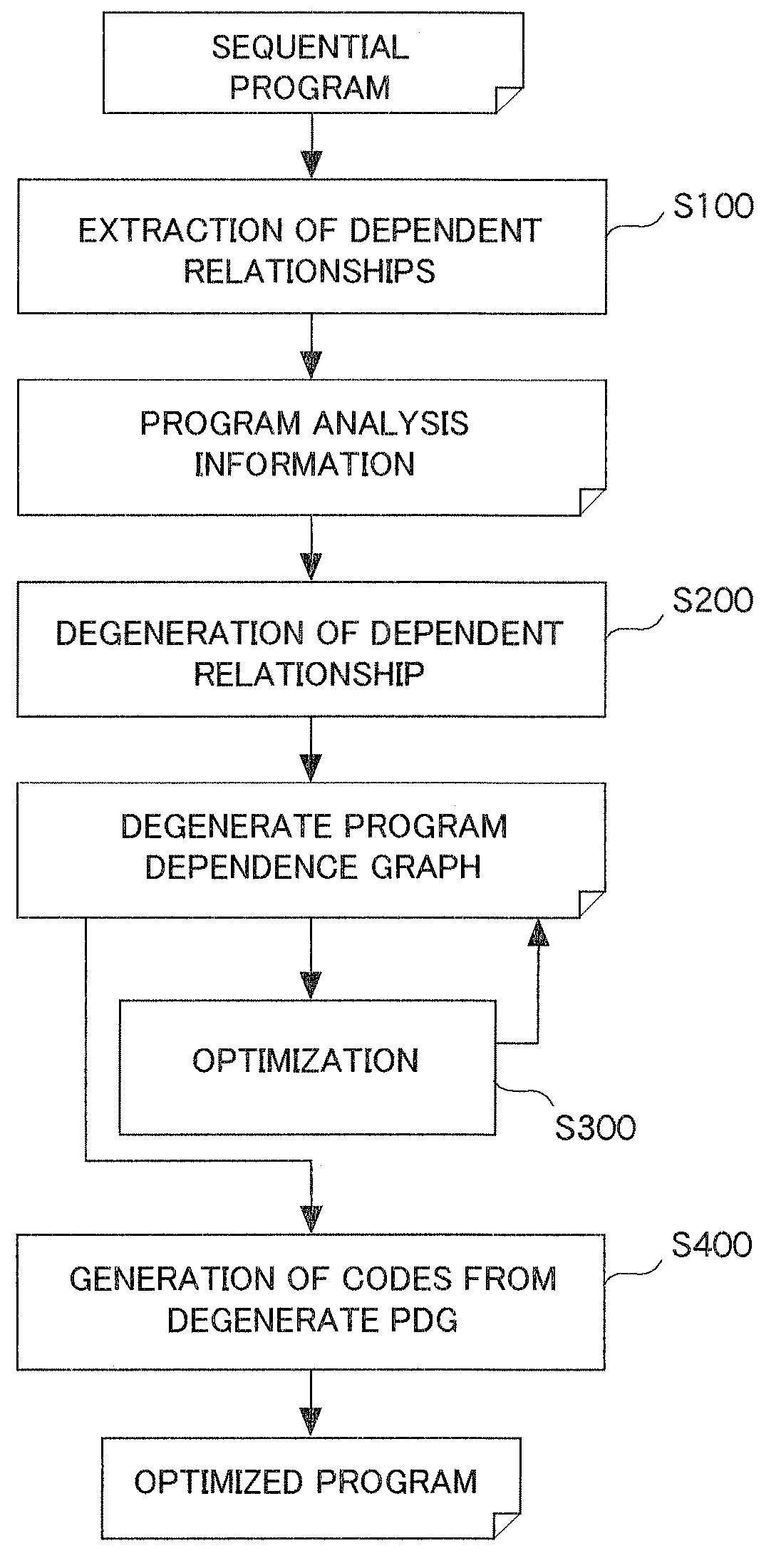
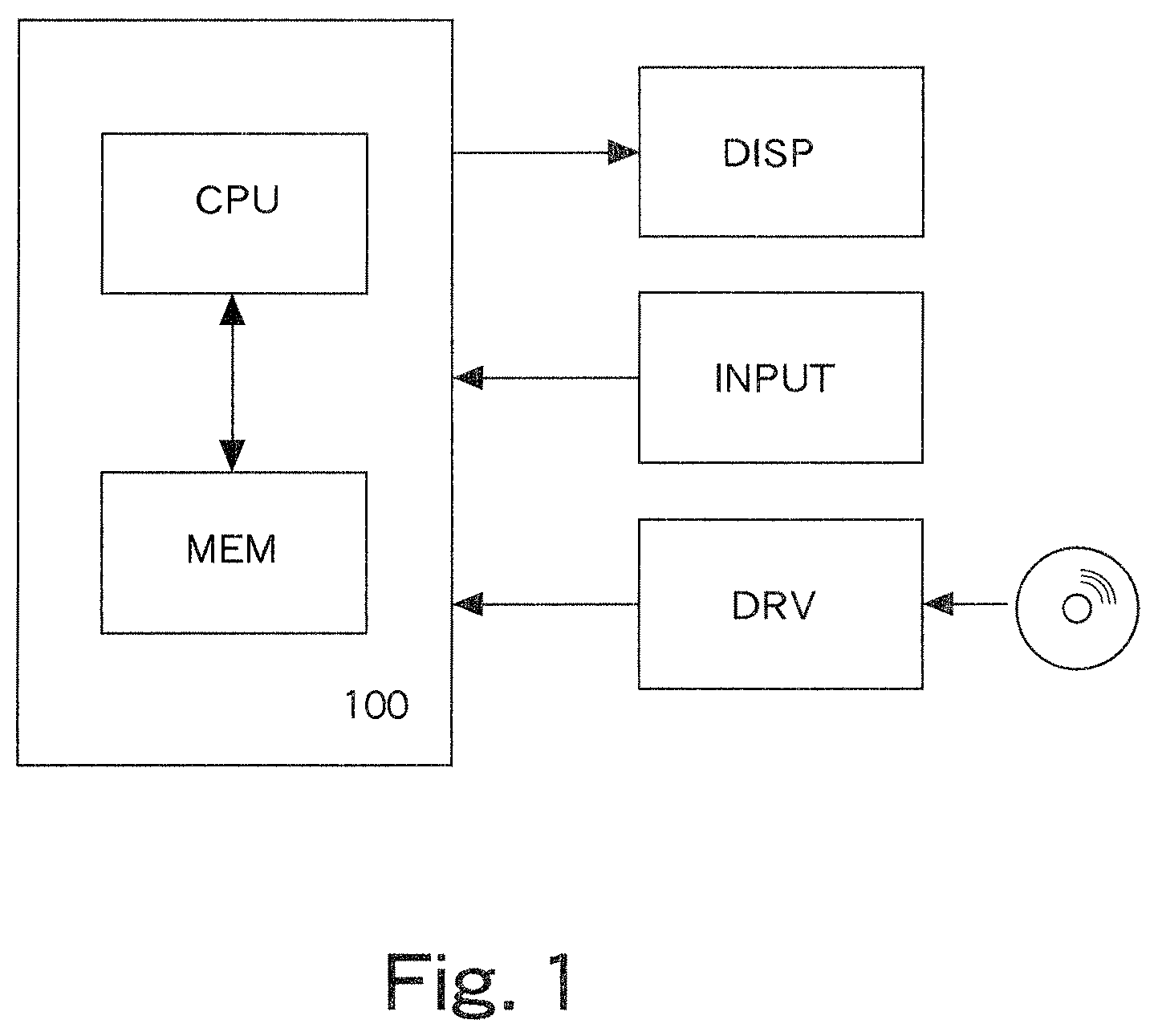
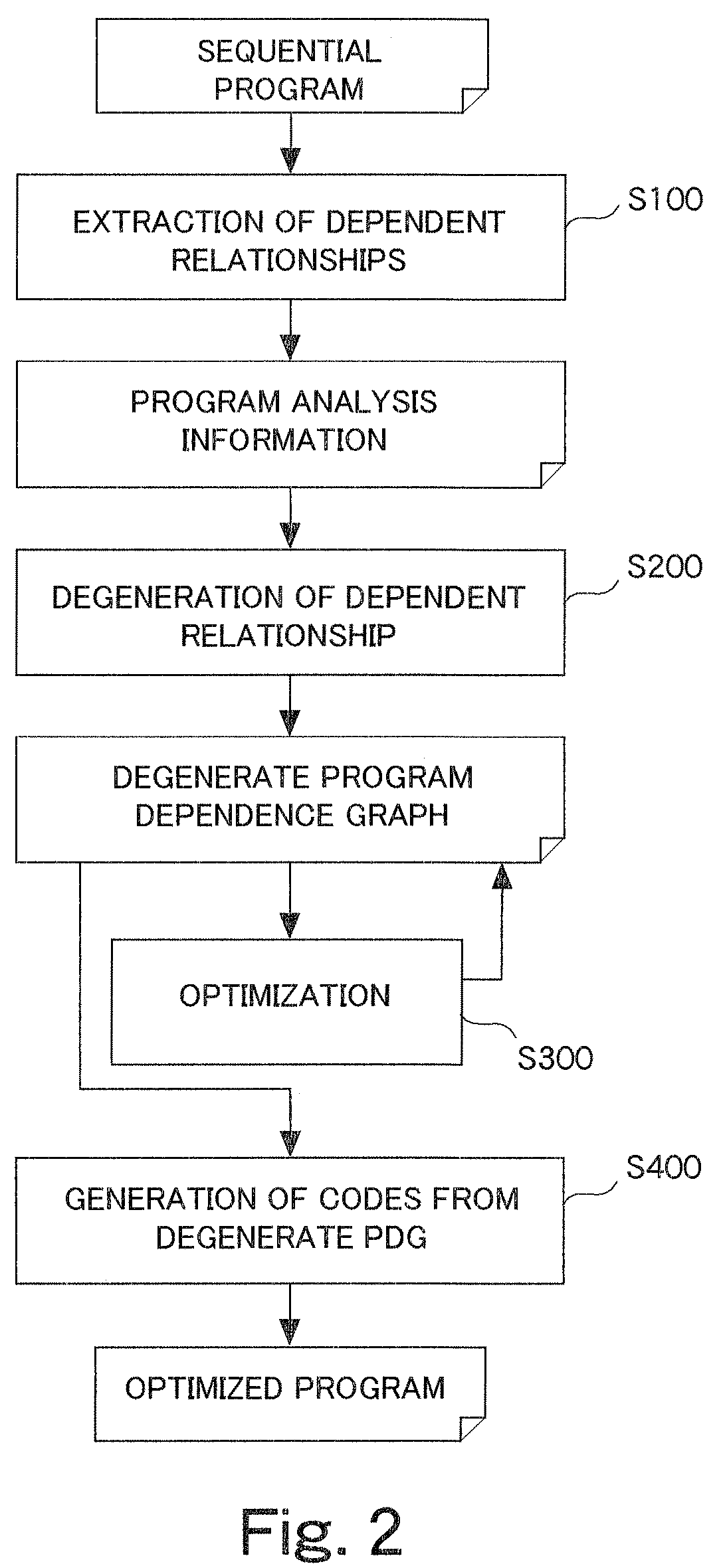
Method and apparatus for analyzing large scale program and generation of code from degenerated program dependence graph
InactiveUS8181171B2Error detection/correctionSpecific program execution arrangementsGranularityProgram analysis
A dependent element group which is invertibly contractible is found by using program analysis information including a plurality of dependent elements representing dependent relationships of statement and control, the statement and the control being included in a program. Next, a program dependence graph in which dependent elements are made to be contracted is generated by contracting the found dependent element group. The number of vertices and the number of edges of the program dependence graph are reduced by the contraction of the dependent elements, so that a program dependence graph with a rough granularity can be generated. As a result, a calculation amount (calculation time) necessary for optimization processing such as parallel processing of the program can be reduced. That is, by generating the contracted program dependence graph having invertibility, it is possible to realize the analysis and optimization of large-scale software in a realistic time.
Owner:FUJITSU LTD
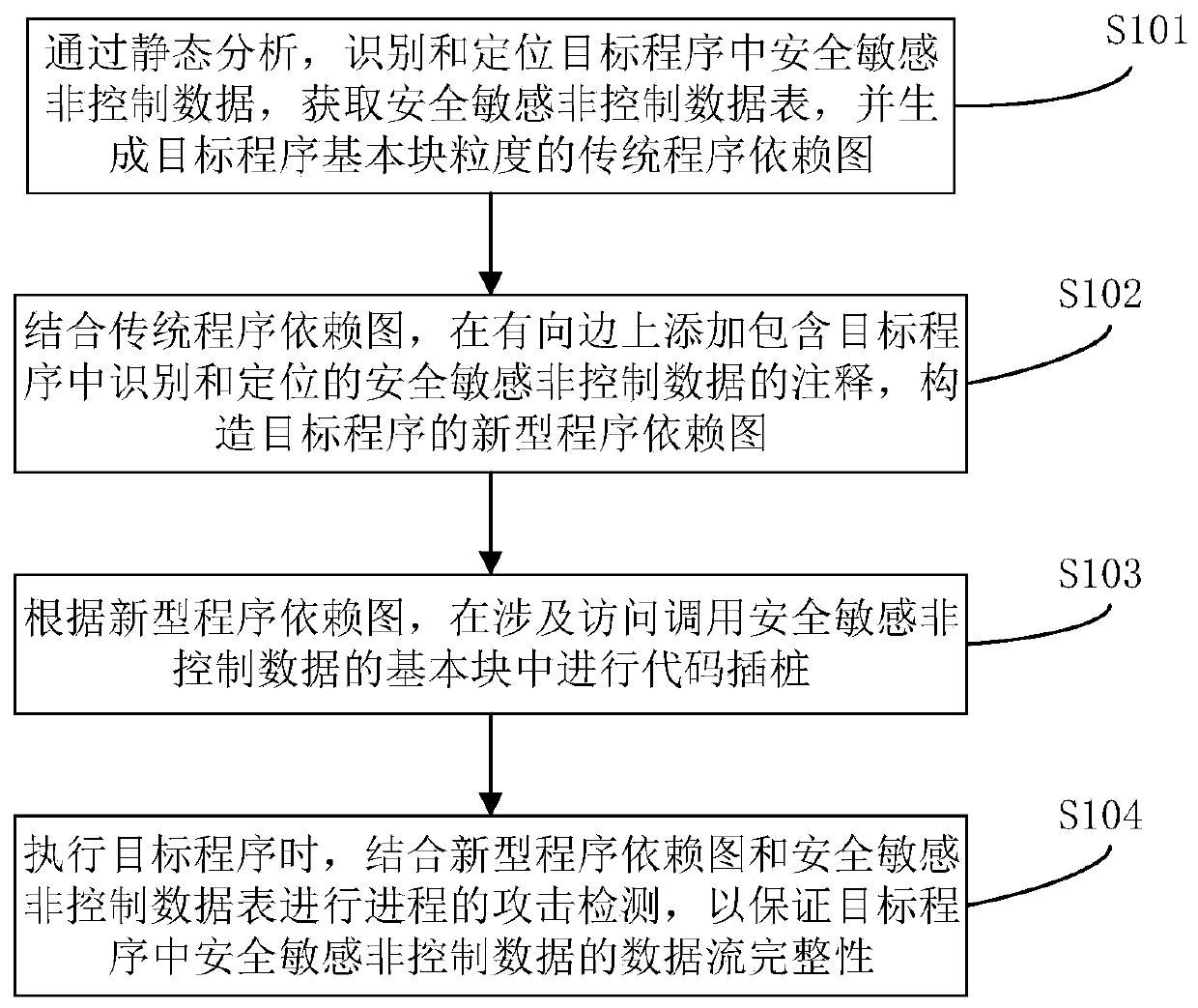
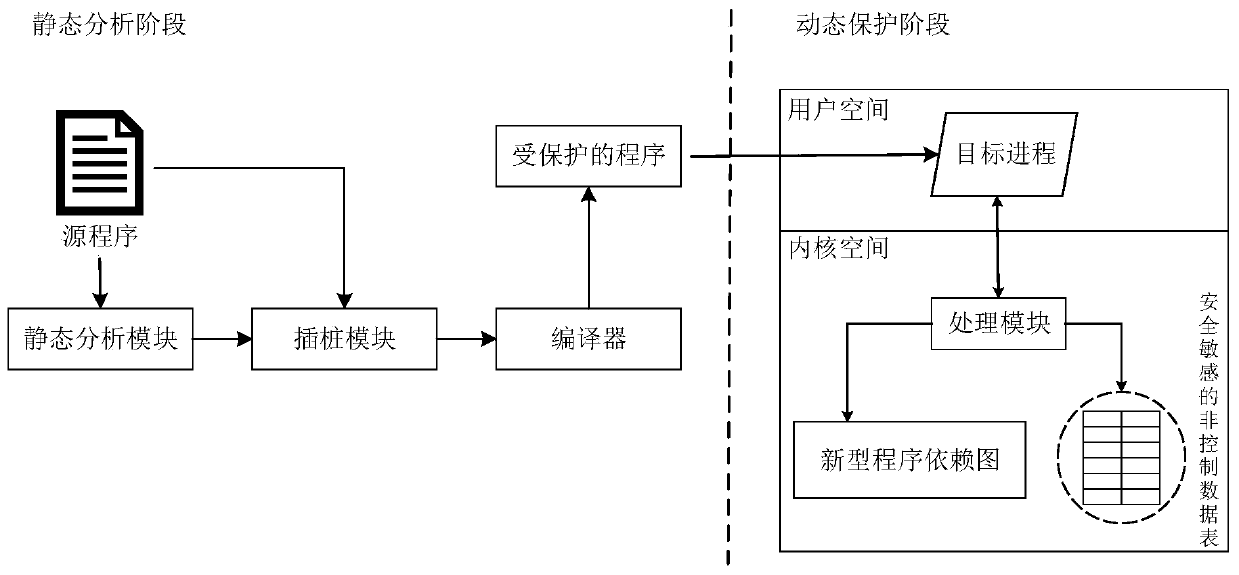
Non-control data attack detection method and device based on novel program dependence graph
ActiveCN110717181AIntegrity guaranteedGuaranteed normal executionPlatform integrity maintainanceData streamData set
The invention belongs to the technical field of network security space, and particularly relates to a non-control data attack detection method and device based on a novel program dependency graph, andthe method comprises the steps: constructing a security-sensitive non-control data set in a program and the novel program dependency graph of basic block granularity through static analysis, and carrying out instrumentation of the LLVM intermediate language representation of the program; in the running process, access and calling operation of the safety-sensitive non-control data in the program is verified, and therefore the data flow integrity of the safety-sensitive non-control data is protected. The control flow and the data flow of the program are combined, and data flow integrity protection of safe and sensitive non-control data in the target program is realized according to the novel program dependency graph during running. The protected non-control data is shrunk to a safe and sensitive non-control data set, analysis and instrumentation processing are carried out on the granularity of the basic block, the running efficiency of a program is guaranteed, safety and performance expenditure are balanced, good universality is achieved, and a new solution is provided for non-control data attack detection.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
Defect positioning method based on context awareness
ActiveCN112965894AImprove effectivenessSoftware testing/debuggingNeural architecturesDirected graphAlgorithm
The invention relates to a defect positioning method based on context awareness, which is characterized in that a program slicing technology is utilized to construct a defect context, the context can be expressed as a directed graph expressed by a program dependency graph, nodes in the graph are statements having a direct or indirect association relationship with failures, and edges are association relationships among the statements. On the basis of the graph, the CAN embeds each node in the graph into a node representation vector by adopting one-hot coding, a dependency relationship between statements is obtained by utilizing GNN, and the CAN is trained by utilizing a test case on the basis of the node representation vectors, so that a more accurate node representation vector can be obtained. And finally, a virtual test case set is constructed through a method that each statement in the defective context statements of the defective target program is covered by only one test case and only one defective context statement is covered by one test case. The test case set is input into the trained GNN to obtain a suspicious value of each statement. According to the method, defect context is analyzed and incorporated into suspicious evaluation to improve defect positioning, and experimental analysis shows that the method can obviously improve the effectiveness of defect positioning.
Owner:CHONGQING UNIV
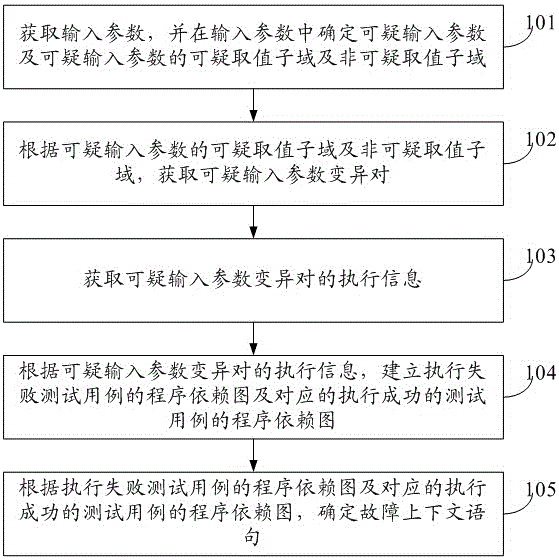
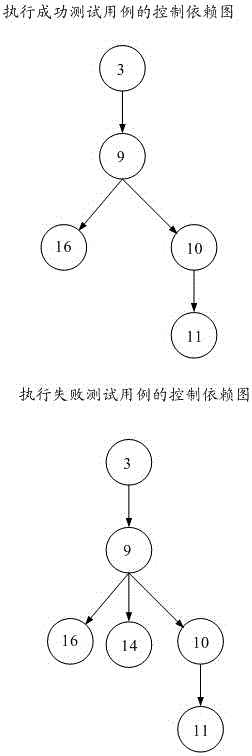
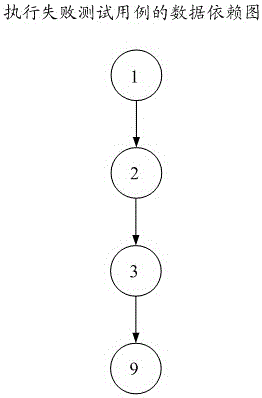
Method and device for carrying out context positioning on software fault
The embodiment of the invention provides a method and a device for carrying out context positioning on a software fault, relates to the technical field of software testing, and is used for providing a context environment where the software fault is generated for a programmer and improving accuracy of positioning the software fault. The method comprises: acquiring input parameters, and determining doubtful input parameters in the input parameters and doubtful value subdomains and non-doubtful value subdomains of the doubtful input parameters; according to the doubtful value subdomains and the non-doubtful value subdomains of the doubtful input parameters, acquiring doubtful input parameter variation pairs; acquiring execution information of the doubtful input parameter variation pairs; according to the execution information of the doubtful input parameter variation pairs, establishing a program dependency graph of an execution failure test case and a program dependency graph of a corresponding execution success test case; according to the program dependency graph of the execution failure test case and the program dependency graph of the corresponding execution success test case determining fault content statements.
Owner:SHANGHAI DIAN TECH INC
Vulnerability detection method for Android application program and related device
ActiveCN113468534AEfficient detectionPlatform integrity maintainanceContext awarenessDependency graph
The invention provides a vulnerability detection method for an Android application program and a related device. The method comprises the following steps of constructing a control flow diagram of a target Android application program, constructing a program dependency graph of the target Android application program based on the control flow graph, according to the program dependency graph, establishing vulnerability features of the target Android application program, and training a pre-constructed machine learning model by utilizing the vulnerability features to obtain a vulnerability detection model, and detecting vulnerabilities of the target Android application program based on the vulnerability detection model. According to the vulnerability detection method for the Android application program and the related device provided by the invention, the vulnerability detection model with context awareness is obtained through training according to the obtained vulnerability features of the Android application program with semantics, and the vulnerability of the Android application program can be quickly and effectively detected.
Owner:BEIJING UNIV OF POSTS & TELECOMM +1
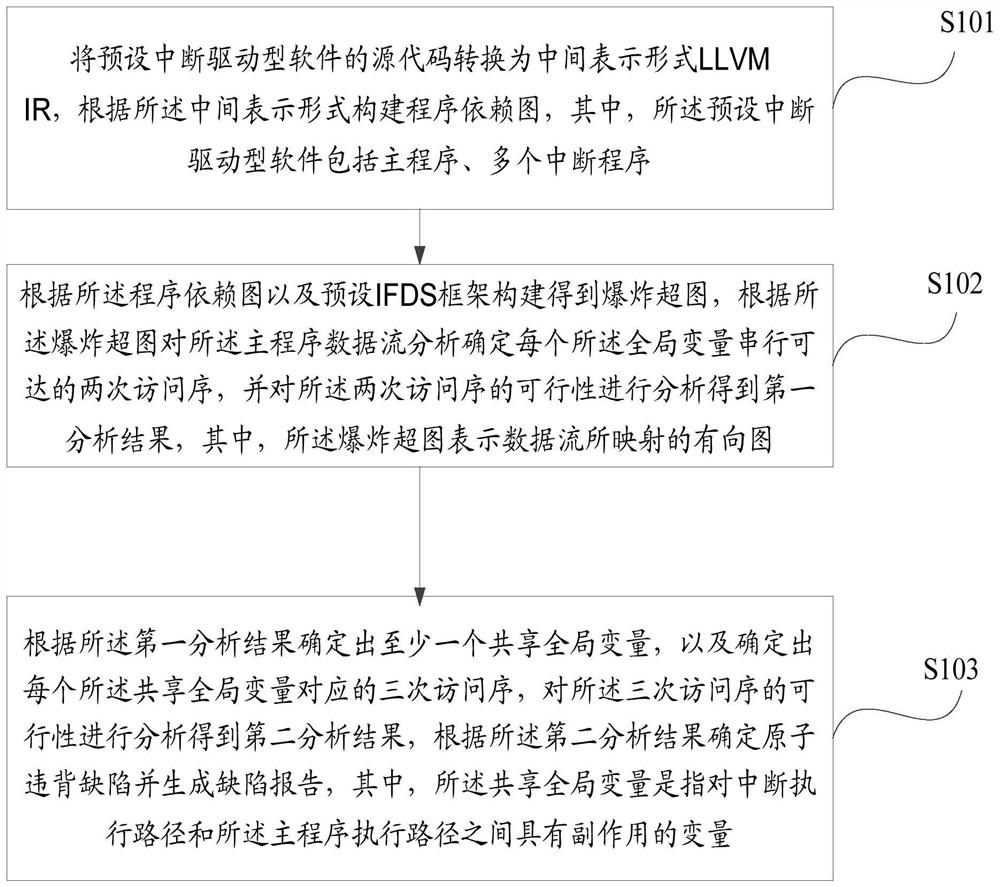
Method for detecting single-variable atom violation defects
PendingCN112631925AImprove accuracyImprove the efficiency of defect detectionSoftware testing/debuggingData streamAlgorithm
The invention discloses a method for detecting single-variable atomic violation defects, and the method comprises the following steps: converting a source code of preset interrupt-driven software into an intermediate representation form LLVM IR, and constructing a program dependency graph according to the intermediate representation form; constructing an explosion hypergraph according to the program dependence graph and a preset IFDS framework, analyzing the main program data flow according to the explosion hypergraph to determine two accessible access sequences of each global variable serial, and analyzing the feasibility of the two access sequences to obtain a first analysis result; determining at least one shared global variable according to the first analysis result, determining a three-time access sequence corresponding to each shared global variable, analyzing the feasibility of the three-time access sequence to obtain a second analysis result, determining atomic violation defects according to the second analysis result, and generating a defect report. According to the invention, the technical problems of low accuracy and low efficiency of single-variable atomicity violation defect detection in the prior art are solved.
Owner:北京轩宇信息技术有限公司
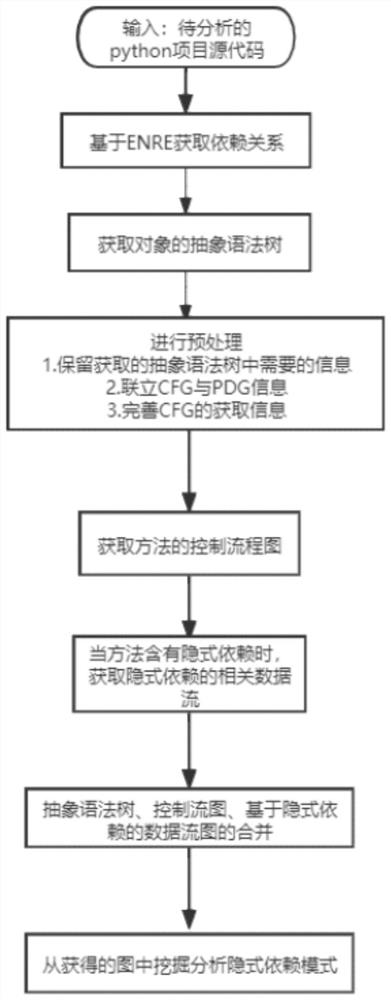
Implicit dependency mode analysis method based on CPG + graph
PendingCN114879974ASolve the problem that implicit dependencies are still unknownReduce complexityCode compilationControl flowAlgorithm
The invention discloses an implicit dependency mode analysis method based on a CPG + graph, which is used for conditionally acquiring a program dependency graph so as to reduce the complexity of an intermediate representation form of a graph structure for generating codes, and can be used for mining an implicit dependency mode from the graph due to the addition of implicit dependency information. By analyzing and analyzing source codes, an abstract syntax tree, a control flow graph and a program dependency graph are generated, and a CPG + graph is jointly constructed, so that the complexity of an intermediate representation form of a graph structure for generating codes is reduced. According to the method, the project file can be quickly and effectively analyzed, the specific implicit dependency mode is mined from the project file, the problem that the current implicit dependency mode is still unknown is solved, and the specific implicit dependency mode and the number can be quickly obtained from the project.
Owner:XI AN JIAOTONG UNIV
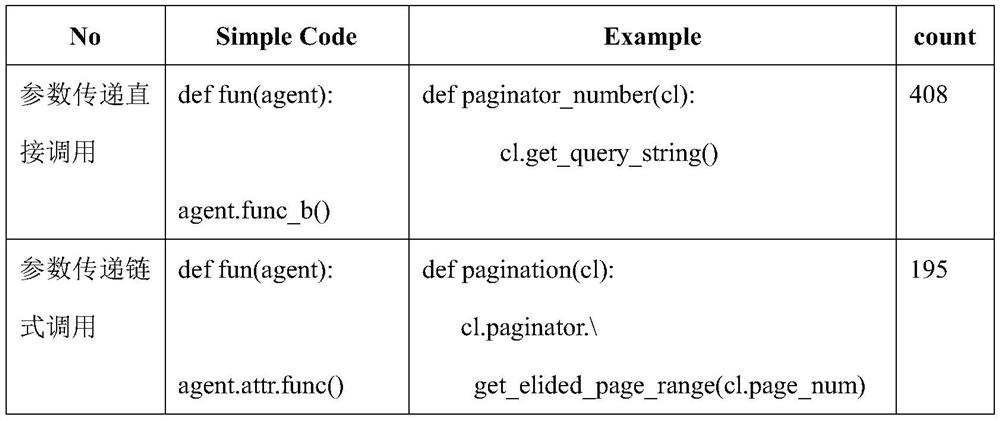
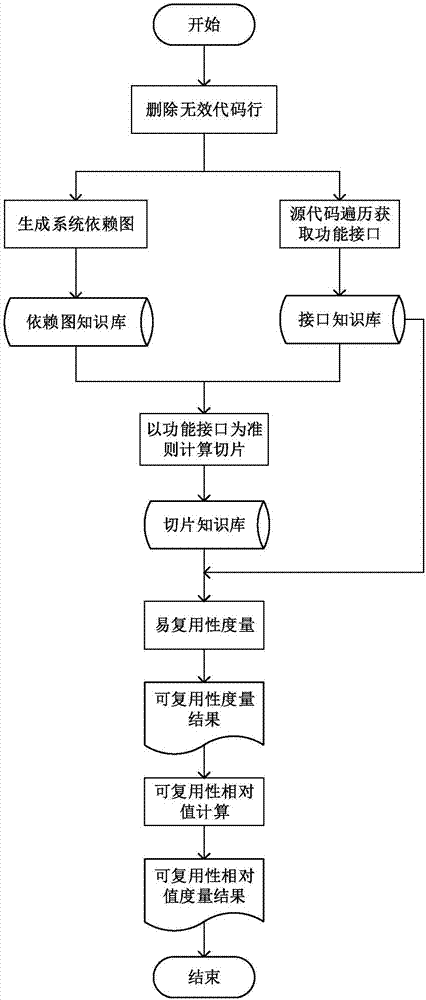
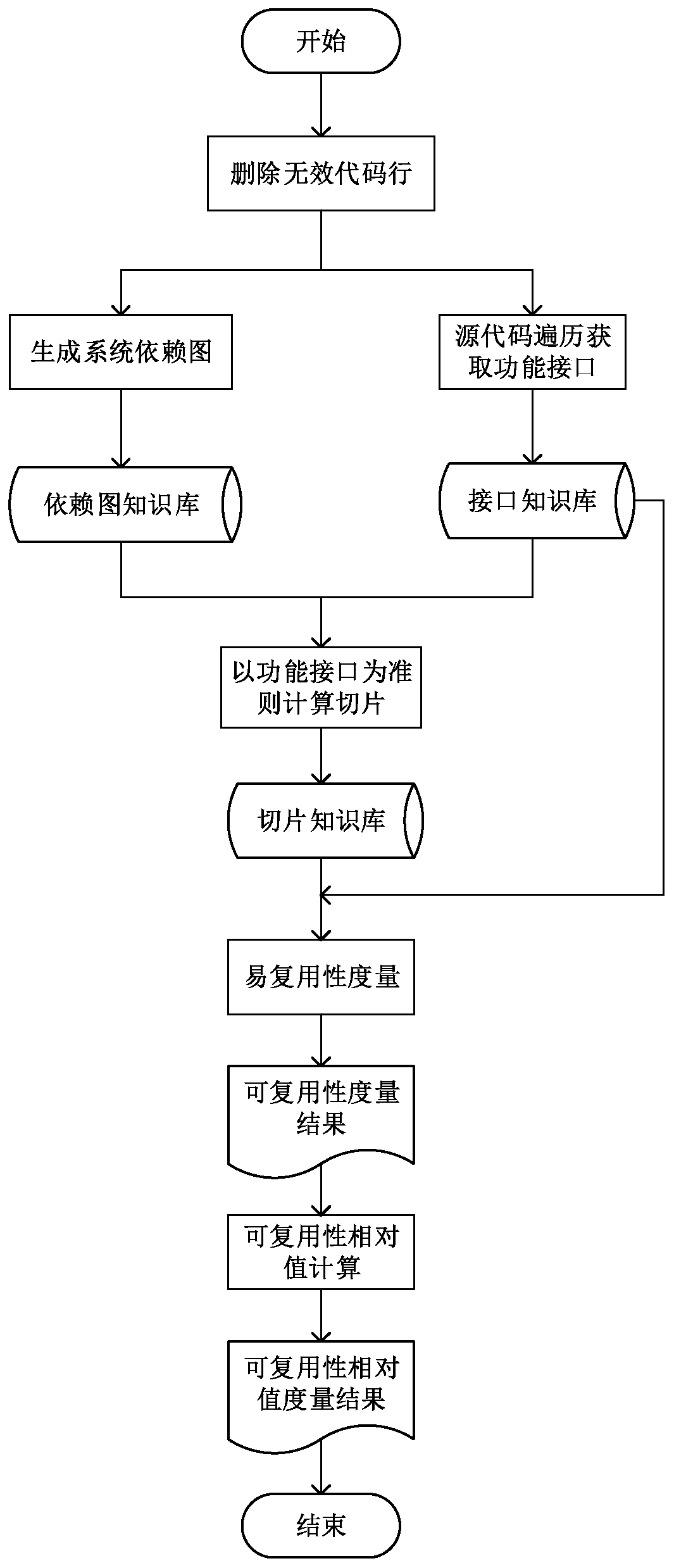
Program slicing-based function reusability measurement method
ActiveCN106980495ARealize analysisApplicable Reusability MetricsSoftware reuseSpecific program execution arrangementsCouplingReusability
The invention discloses a program slicing-based function reusability measurement method. The method comprises the following steps of: constructing a program dependence graph for a source program, and calculating slicing results by taking a code behavior slicing criterion where a functional interface is located, wherein each slicing result is a statement associated with a corresponding functional module; constructing measurement indexes of the functional modules on the basis of the slicing results, wherein the measurement indexes comprise a clustering degree, a cohesion degree, a cyclomatic complexity, a public method number, a maximum nesting layer number and a coupling degree average value of the functional modules; and constructing a functional module reusability measurement value calculation formula according to the measurement indexes, and obtaining reusability relative values of the functional modules so as to screen the functional modules with relatively high reusability.
Owner:SOUTHEAST UNIV
A Functional Reusability Measurement Method Based on Program Slicing
ActiveCN106980495BRealize analysisApplicable Reusability MetricsSoftware reuseRound complexityTheoretical computer science
The invention discloses a program slicing-based function reusability measurement method. The method comprises the following steps of: constructing a program dependence graph for a source program, and calculating slicing results by taking a code behavior slicing criterion where a functional interface is located, wherein each slicing result is a statement associated with a corresponding functional module; constructing measurement indexes of the functional modules on the basis of the slicing results, wherein the measurement indexes comprise a clustering degree, a cohesion degree, a cyclomatic complexity, a public method number, a maximum nesting layer number and a coupling degree average value of the functional modules; and constructing a functional module reusability measurement value calculation formula according to the measurement indexes, and obtaining reusability relative values of the functional modules so as to screen the functional modules with relatively high reusability.
Owner:SOUTHEAST UNIV
Vulnerability detection method and related device for Android applications
ActiveCN113468534BEfficient detectionPlatform integrity maintainanceTheoretical computer scienceContext awareness
The present disclosure provides a vulnerability detection method for Android applications and related devices, including: constructing a control flow graph of the target Android application; building a program dependency graph of the target Android application based on the control flow graph; The vulnerability characteristics of the target Android application; use the vulnerability characteristics to train the pre-built machine learning model, obtain the vulnerability detection model, and detect the vulnerability of the target Android application based on the vulnerability detection model. The vulnerability detection method and related devices for Android applications provided by the present disclosure, according to the acquired vulnerability characteristics of Android applications with semantics, train a vulnerability detection model with context awareness, which can quickly and effectively detect vulnerabilities of Android applications .
Owner:BEIJING UNIV OF POSTS & TELECOMM +1
Method and system for automatically generating dynamic breakpoints
ActiveCN102968369BReduce the burden onLess interactive informationSoftware testing/debuggingProgramming languageDynamic instrumentation
The invention discloses a method and system for automatically generating dynamic breakpoints, wherein the system comprises a dynamic dependence graph creation module, a debugging range refinement module, a state-flow graph creation module, a dynamic breakpoint generation module and a debugging feedback collection module, wherein the dynamic dependency graph creation module is used for not only collecting execution examples of program statements, but also collecting execution sequences and dependency relationship between the examples by utilizing a dynamic instrumentation technique during the program execution process, so as to create a dynamic program dependence graph on the bases; the debugging range refinement module is used for extracting parts of the dynamic program dependence graph relevant with program failure descriptions by utilizing a program dynamic-slicing technique; the state-flow graph creation module is used for interchanging connection points and sides in the dynamic dependence graph output by the debugging range refinement module and transforming a debugging range into a state-flow graph; the dynamic breakpoint generation module is used for generating dynamic breakpoints and aggregations of expressions required being inspected at the breakpoints; and the debugging feedback collection module is used for collecting the results of judgments made by a user about the provided breakpoints and the aggregations of the expressions required being inspected at the breakpoints.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
Method for acquiring signals
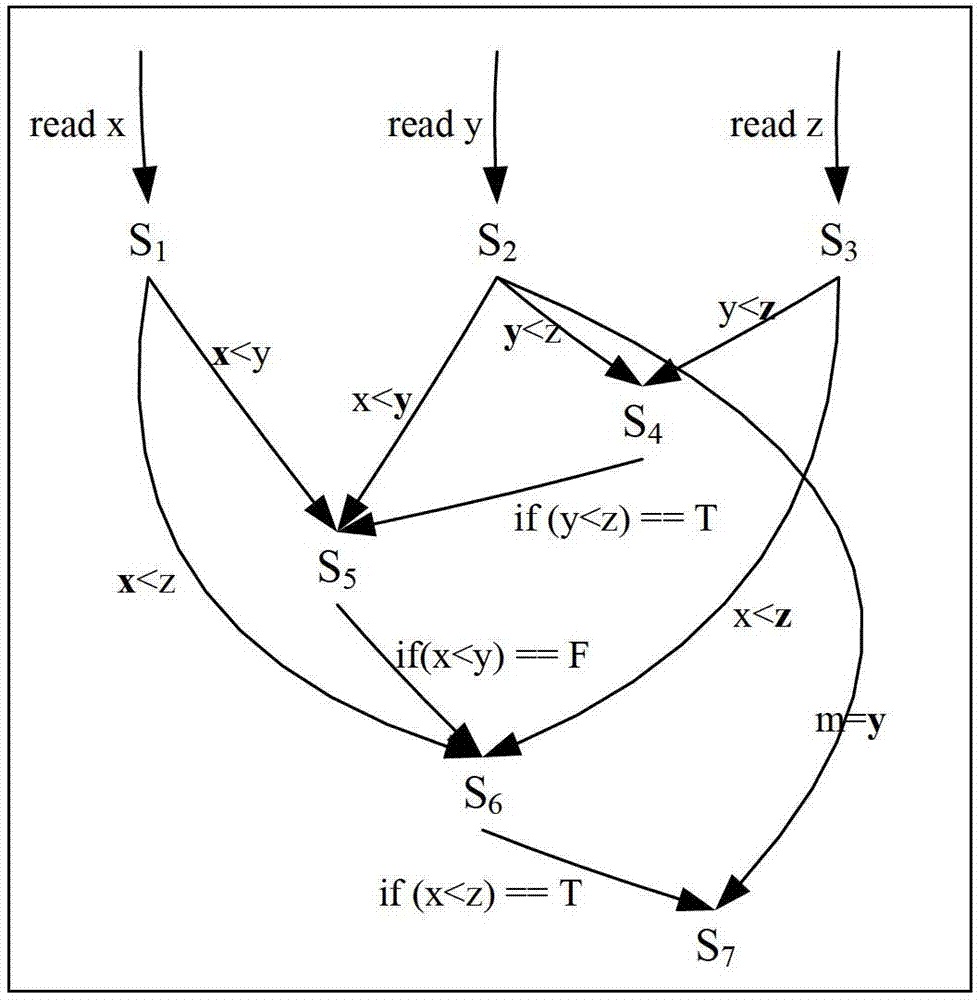
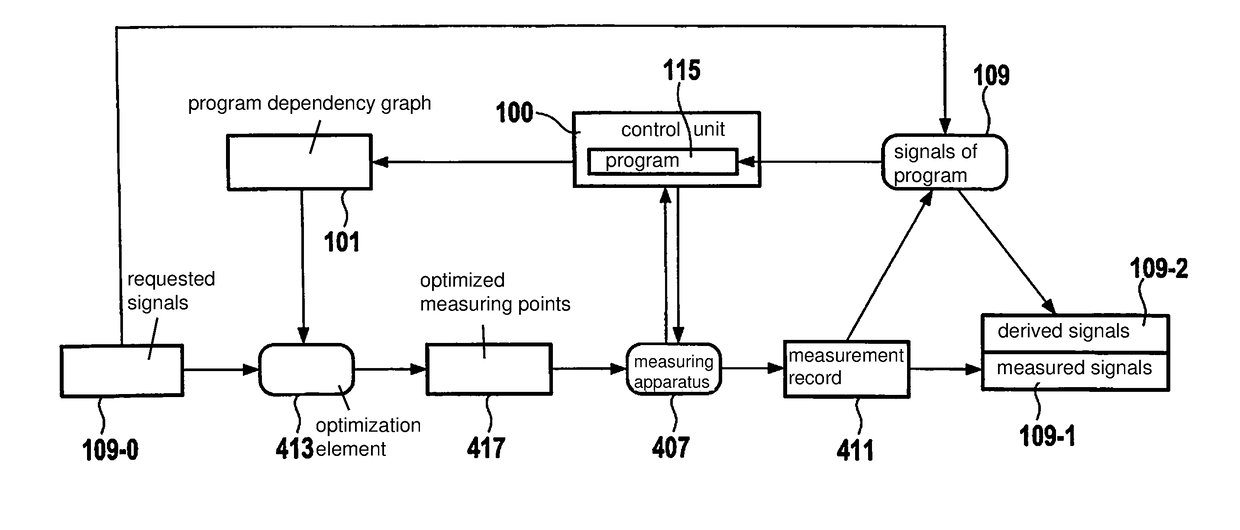
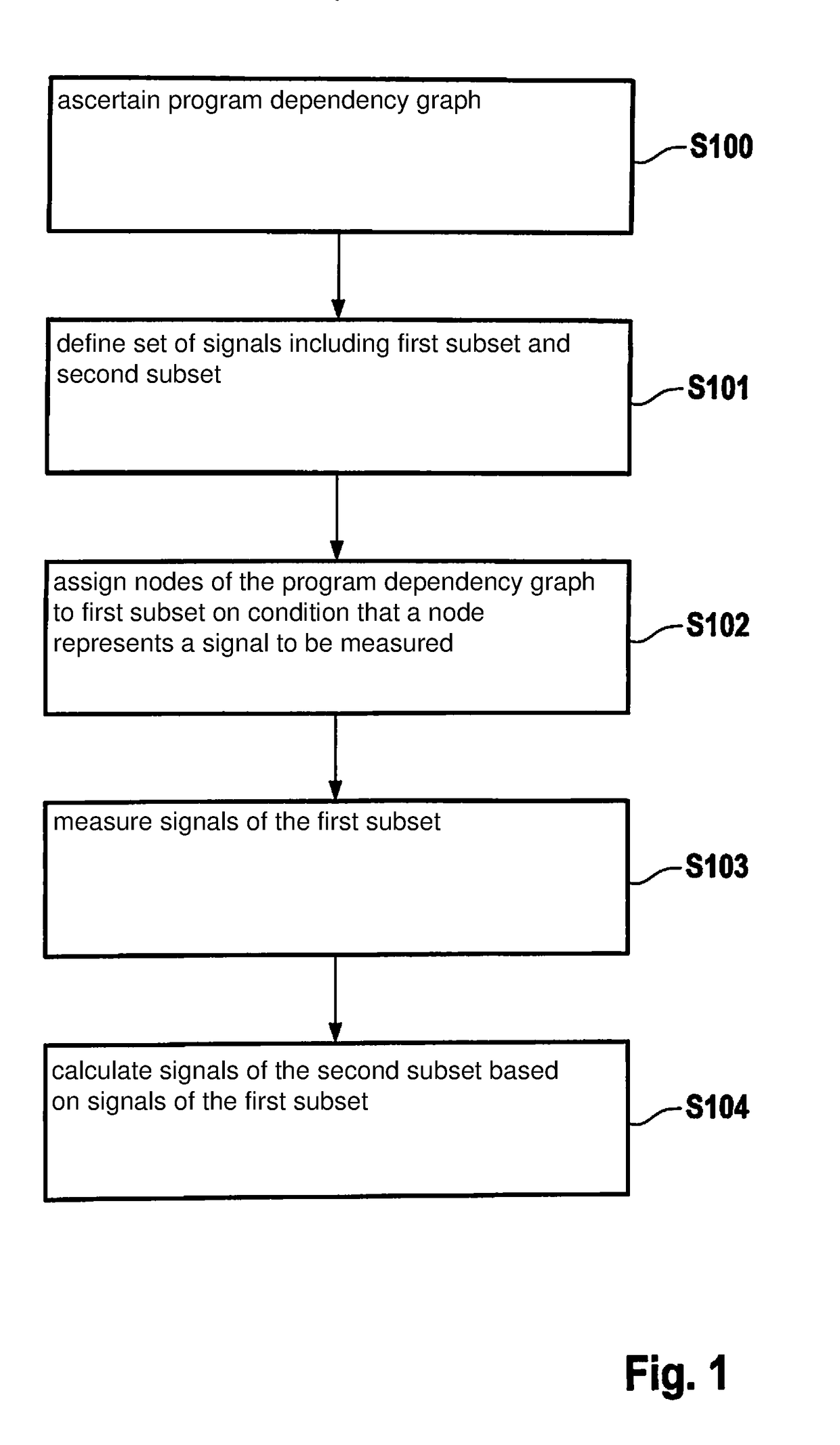
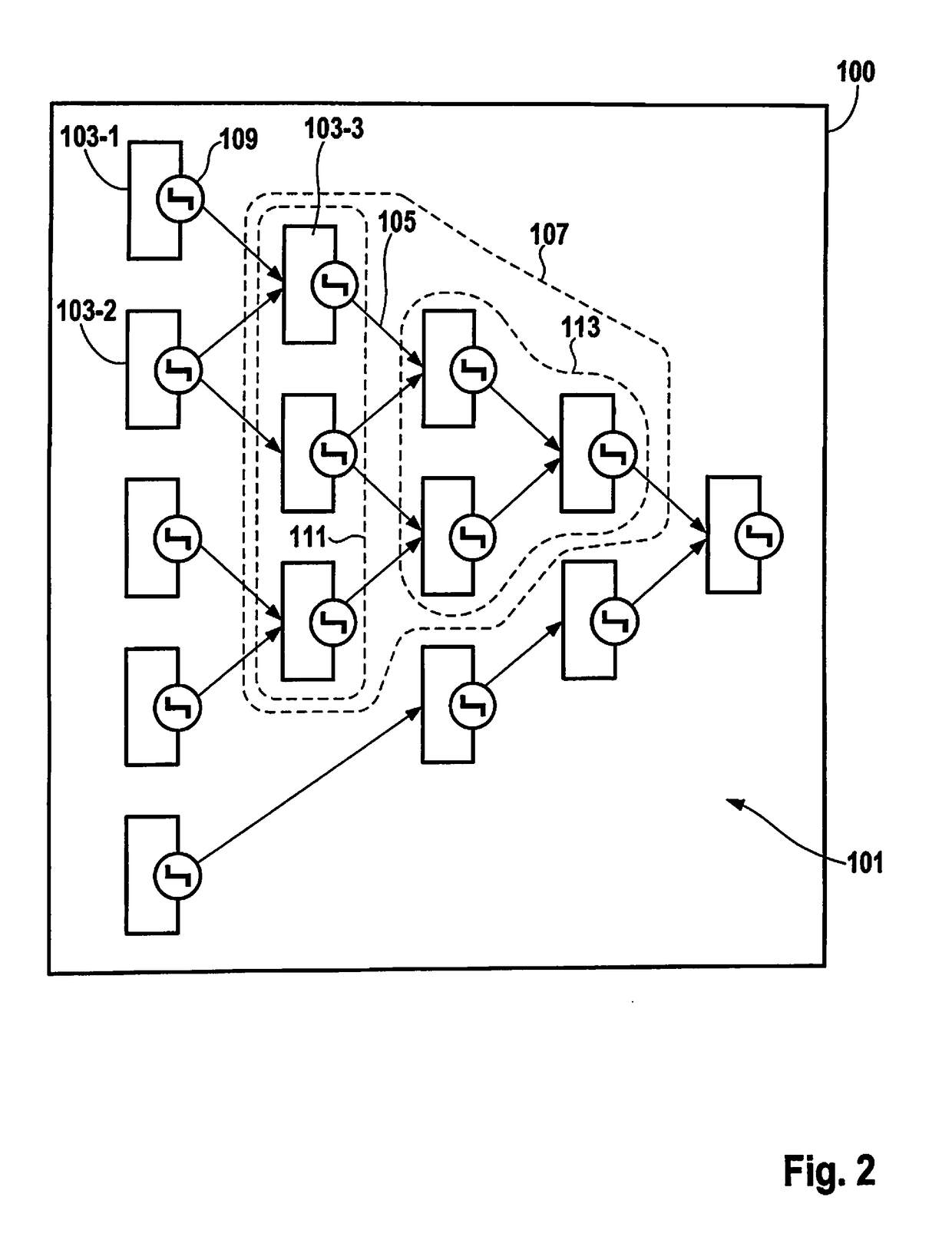
InactiveUS20180196090A1Reduce data volumeReduce in quantitySoftware designMeasurement using digital techniquesTheoretical computer scienceDependency graph
A method for acquiring signals of a control unit, including the steps of ascertaining a program dependency graph from a program of the control unit, the nodes of the program dependency graph being the computational steps of the program, from which signals are obtained, and whose segments are the data and / or control dependencies between the computational steps; defining a set of signals, which includes a first subset of signals to be measured and a second subset of dependent signals; assigning nodes to the first subset on condition that a node represents a signal to be measured, if a node is situated at an incoming segment of the node, outside of the set of signals; measuring the signals of the first subset; and calculating the signals of the second subset on the basis of the measured signals of the first subset.
Owner:ROBERT BOSCH GMBH
Code homology detection method and device based on code fingerprint
ActiveCN107169358BImprove detection efficiencyImprove accuracyPlatform integrity maintainanceCode compilationObject codeSemantics
The invention relates to a code homology detection method based on code fingerprint and a device thereof. The method comprises: performing dependence analysis on input codes, obtaining an original program dependence graph PDG; performing structure simplification, removing nesting and performing shading on the original program dependence graph PDG, to obtain a simplified program dependence graph sPDG; based on an abstract syntax tree, analyzing code key grammar information; extracting a system call sequence of a code execution path, to obtain a full path parameter vector assembly of an object code, to build code fingerprint; calculating a homology coefficient of code fingerprint components; according to the homology coefficient, calculating a homology index of two codes S and T, and through the homology index, determining a homologous relation exists in the both codes. The method can give consideration to code semantics and behaviors on the basis of similarity, and improves detection efficiency by using a lightweight characteristic and simplified mechanism, and measures homologous relations among codes in a multi-angle manner, and improves detection efficiency while ensuring accuracy.
Owner:THE PLA INFORMATION ENG UNIV +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com