Source code facing buffer overflow detection method based on inequalities solving
A technology of buffer overflow and detection method, which is applied in the detection of buffer overflow in source code and the field of buffer overflow detection, which can solve the problem that the influence of buffer variables or parameter length attributes cannot be accurately grasped.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0060] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be further described in detail below in conjunction with the accompanying drawings.
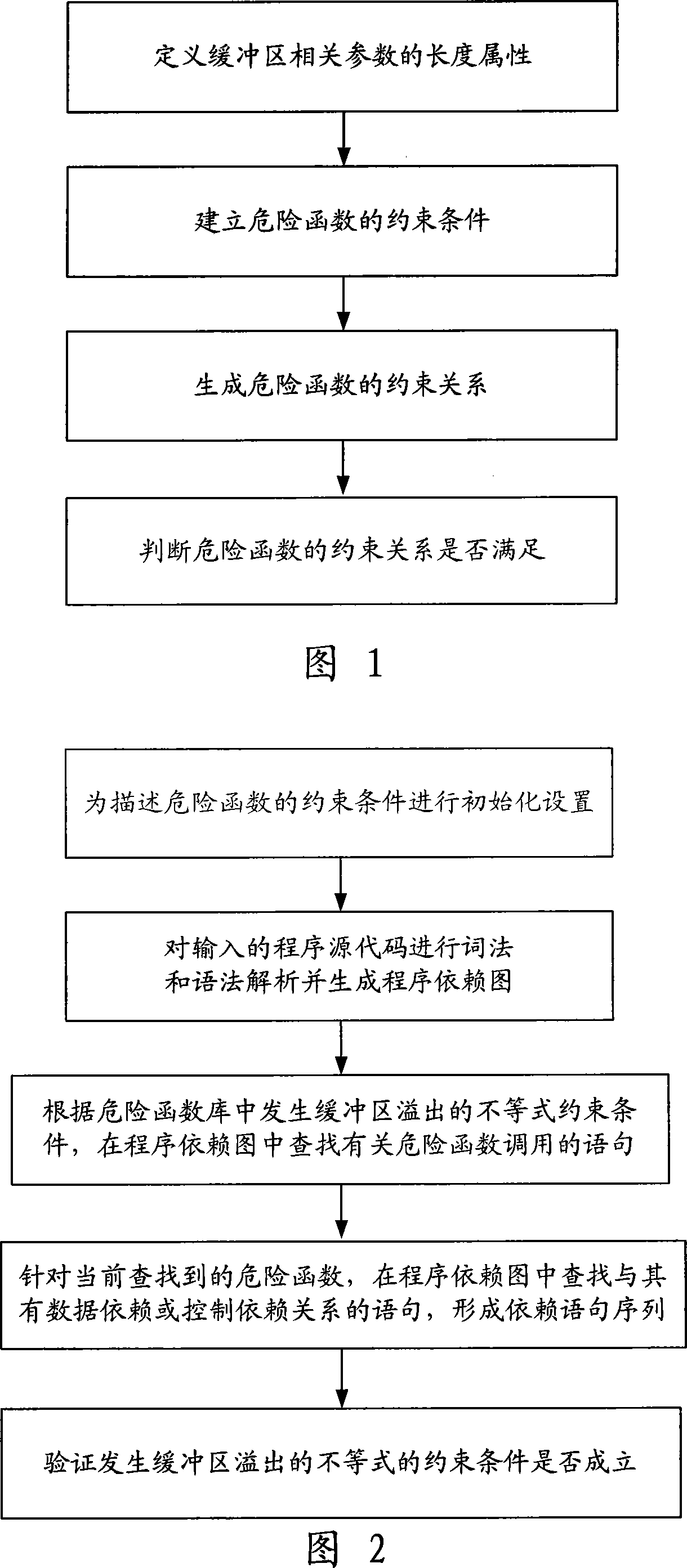
[0061] Referring to Fig. 2, specifically introduce the buffer overflow detection method that the present invention is oriented to the source code and solve based on the group of inequalities, the method comprises the following steps:
[0062] (1) Initialize the constraints describing the dangerous function;
[0063] The specific operation content of this step is: define the length attribute of buffer related parameters, specify the expression method of parameters or variables in the buffer area, and define multiple C / C ++ The library functions respectively establish the inequality constraints for which buffer overflows occur. Because the operation content of this step is basically the same as step 1 and step 2 of the traditional method, it will not be repeated he...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com