Non-control data attack detection method and device based on novel program dependence graph
A program dependency graph and attack detection technology, applied in the fields of electrical digital data processing, computer security devices, instruments, etc., can solve problems such as inability to effectively detect attacks and difficult deployment of applications
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0044] In order to make the purpose, technical solution and advantages of the present invention more clear and understandable, the present invention will be further described in detail below in conjunction with the accompanying drawings and technical solutions.
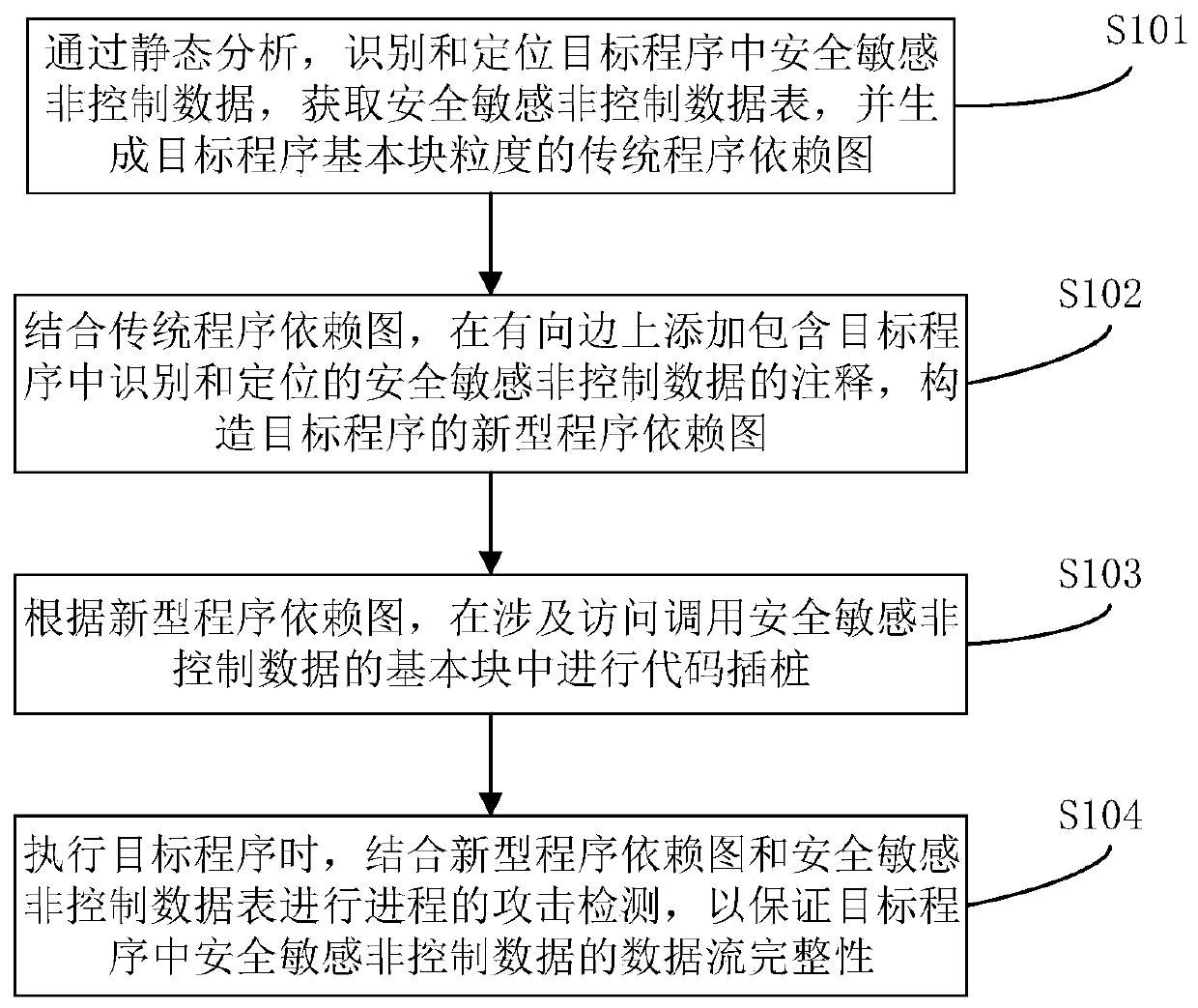
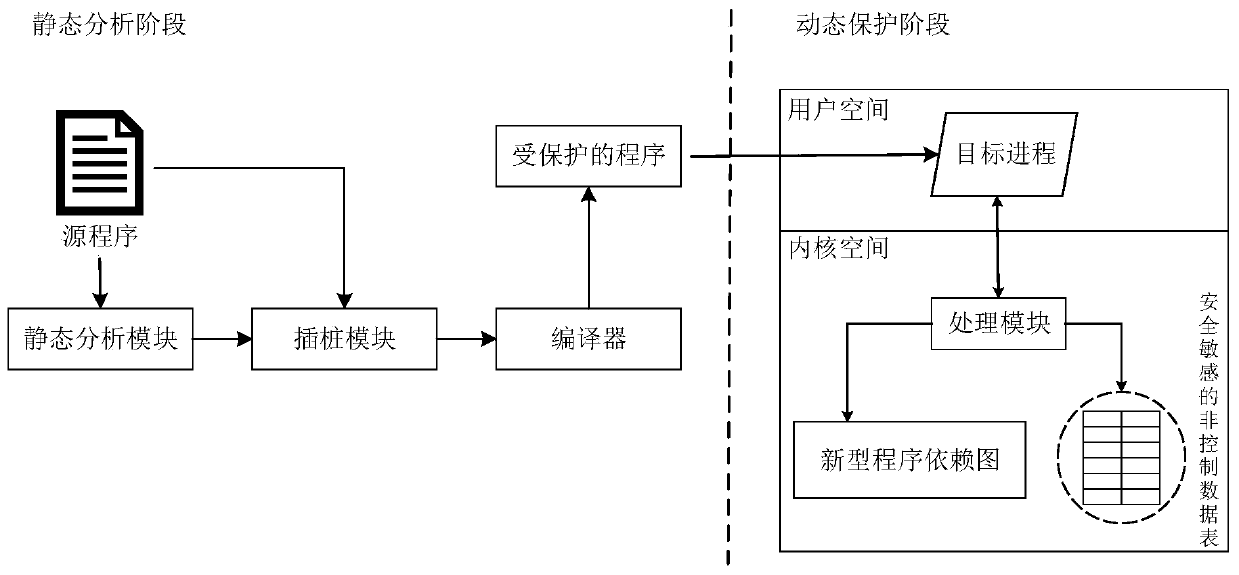
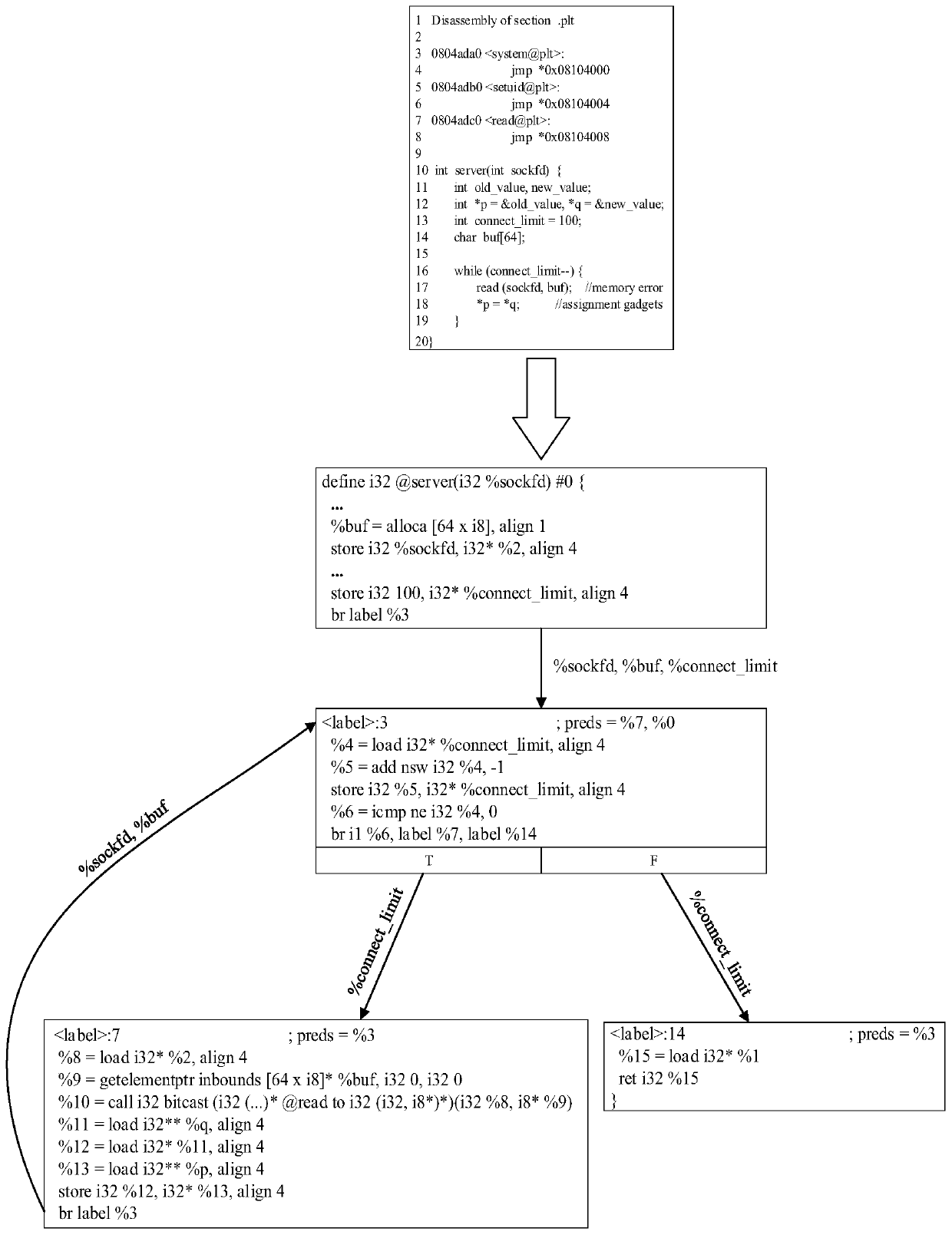
[0045] The existing non-control data attack detection technology (DFI) realizes the defense against non-control data attacks by verifying whether the operation on variables conforms to the data flow graph (Data Flow Graph, DFG). However, DFI needs to perform reachability analysis on each operation of variables. Because reachability analysis may be redundant and complicated for some read operations, it will cause DFI false positives and protect the data flow integrity of all variables. It also introduces a lot of overhead, making it difficult to deploy applications in real environments. Embodiment of the present invention, see figure 1 As shown, a non-control data attack detection method based on a new program depende...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com