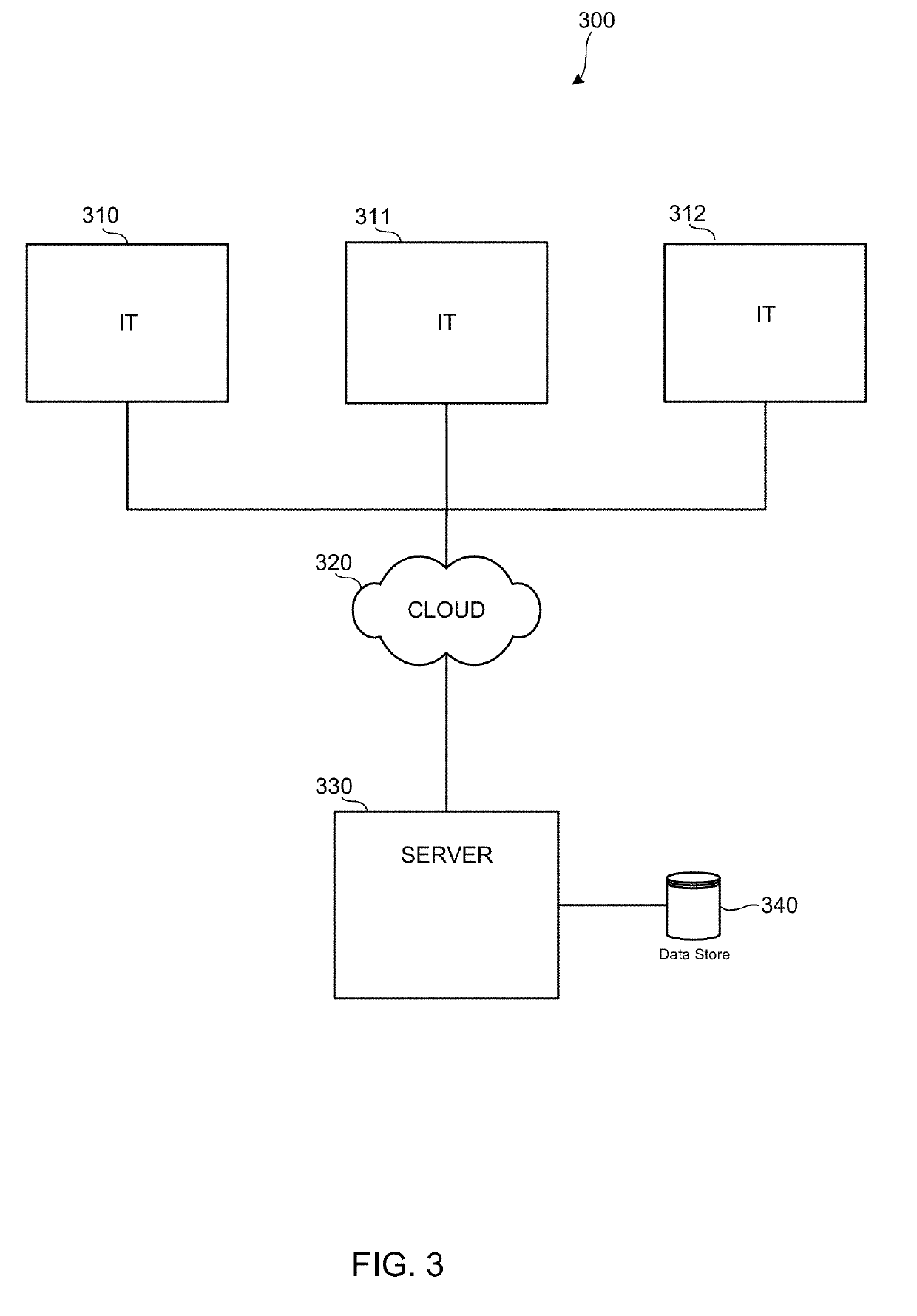
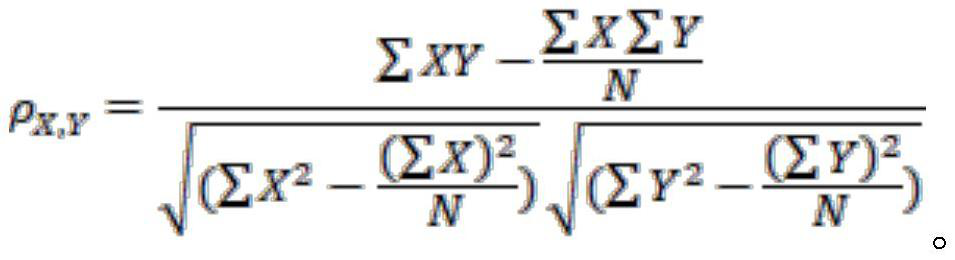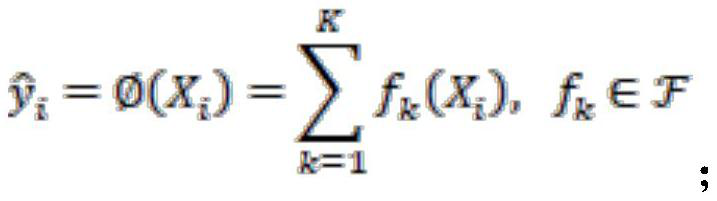Patents
Literature
117 results about "Dependence analysis" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In compiler theory, dependence analysis produces execution-order constraints between statements/instructions. Broadly speaking, a statement S2 depends on S1 if S1 must be executed before S2. Broadly, there are two classes of dependencies--control dependencies and data dependencies.
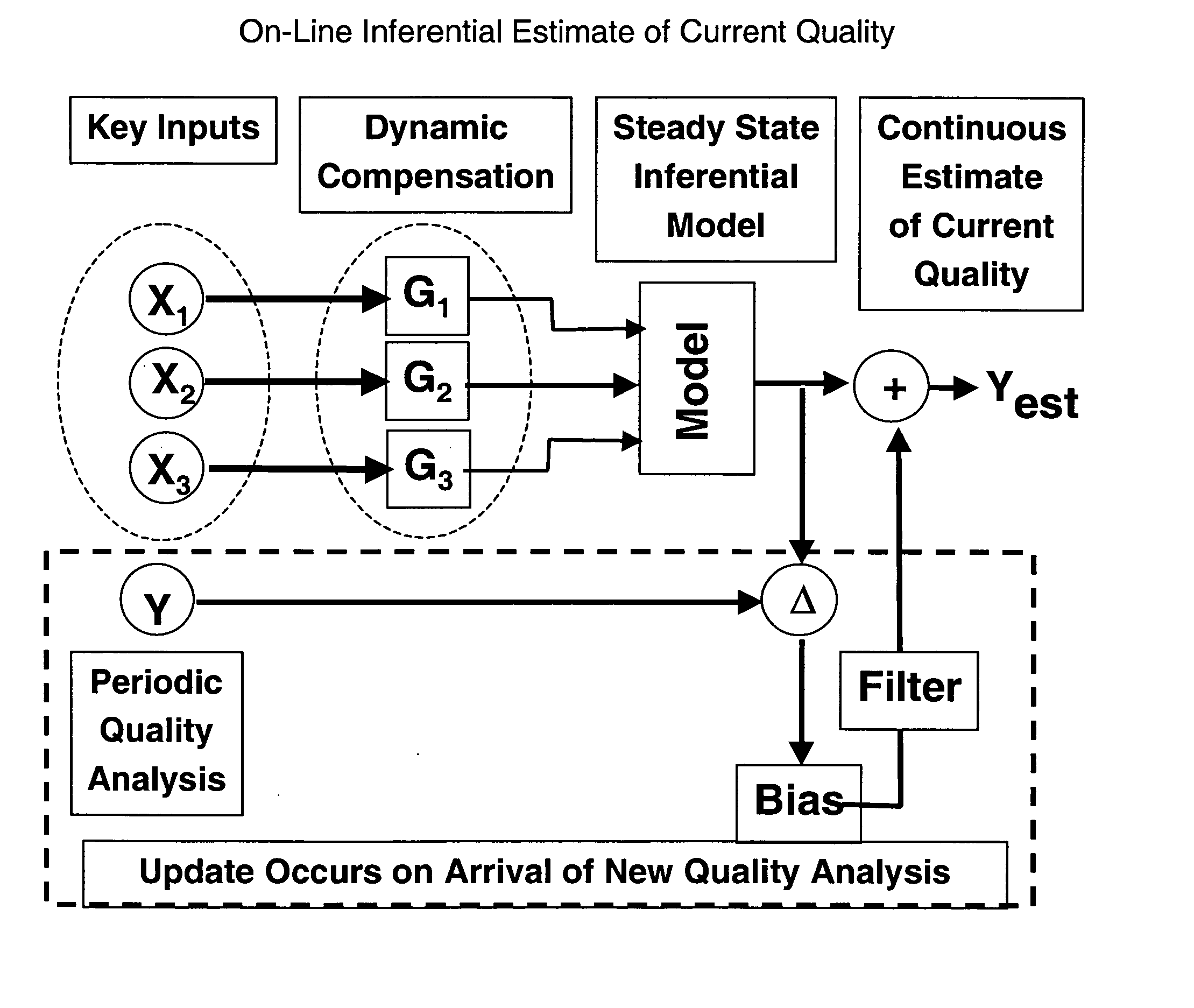
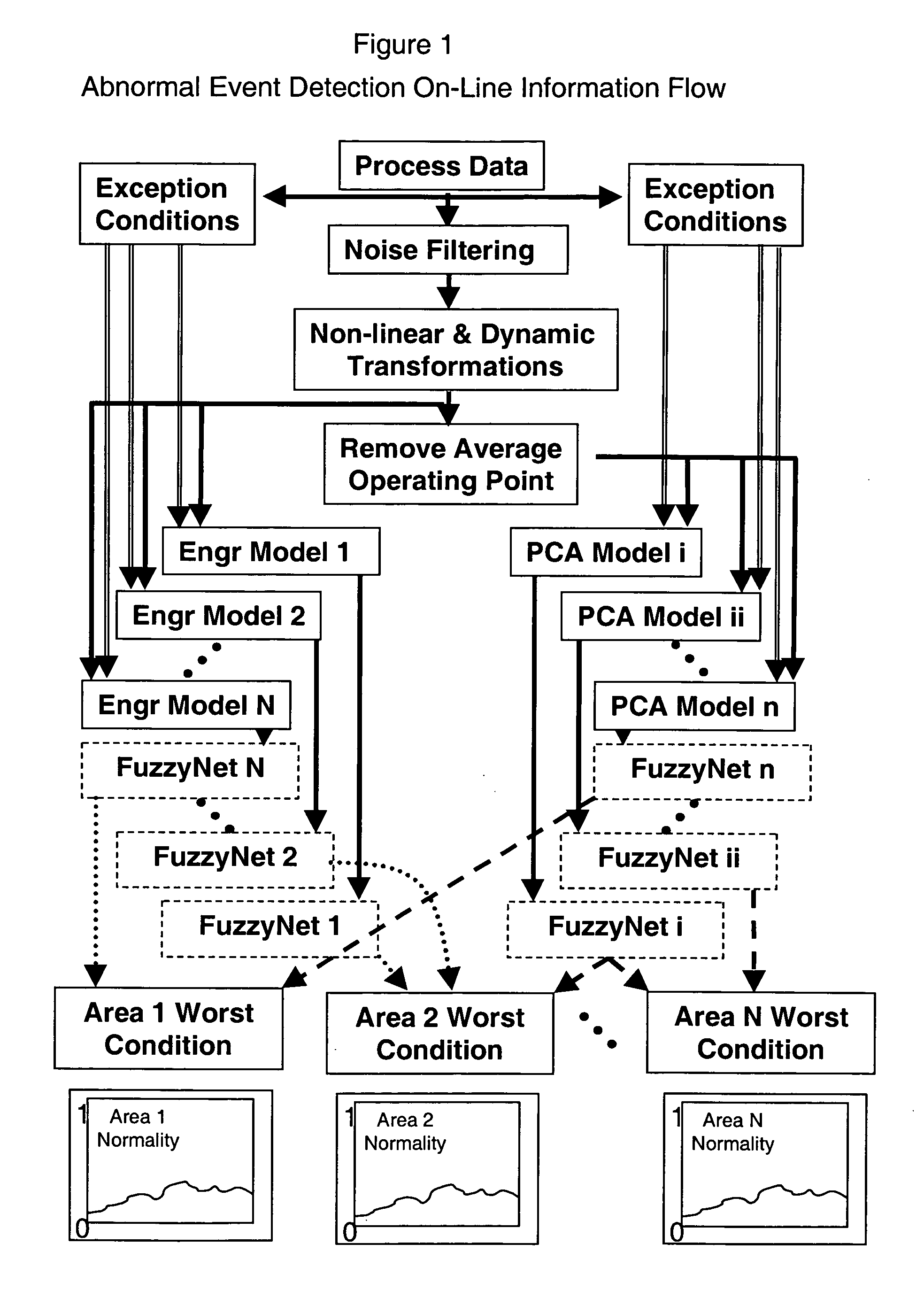
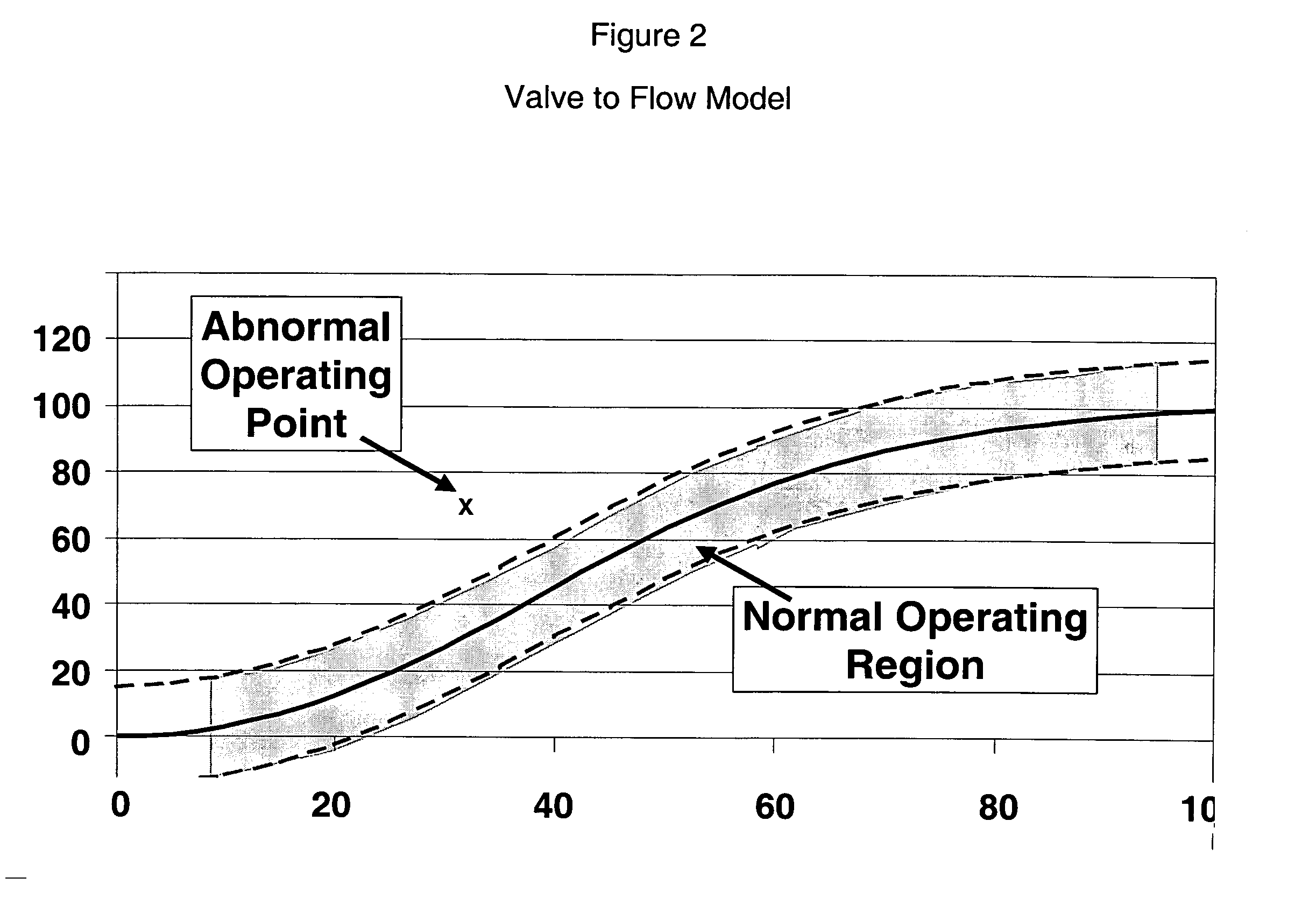
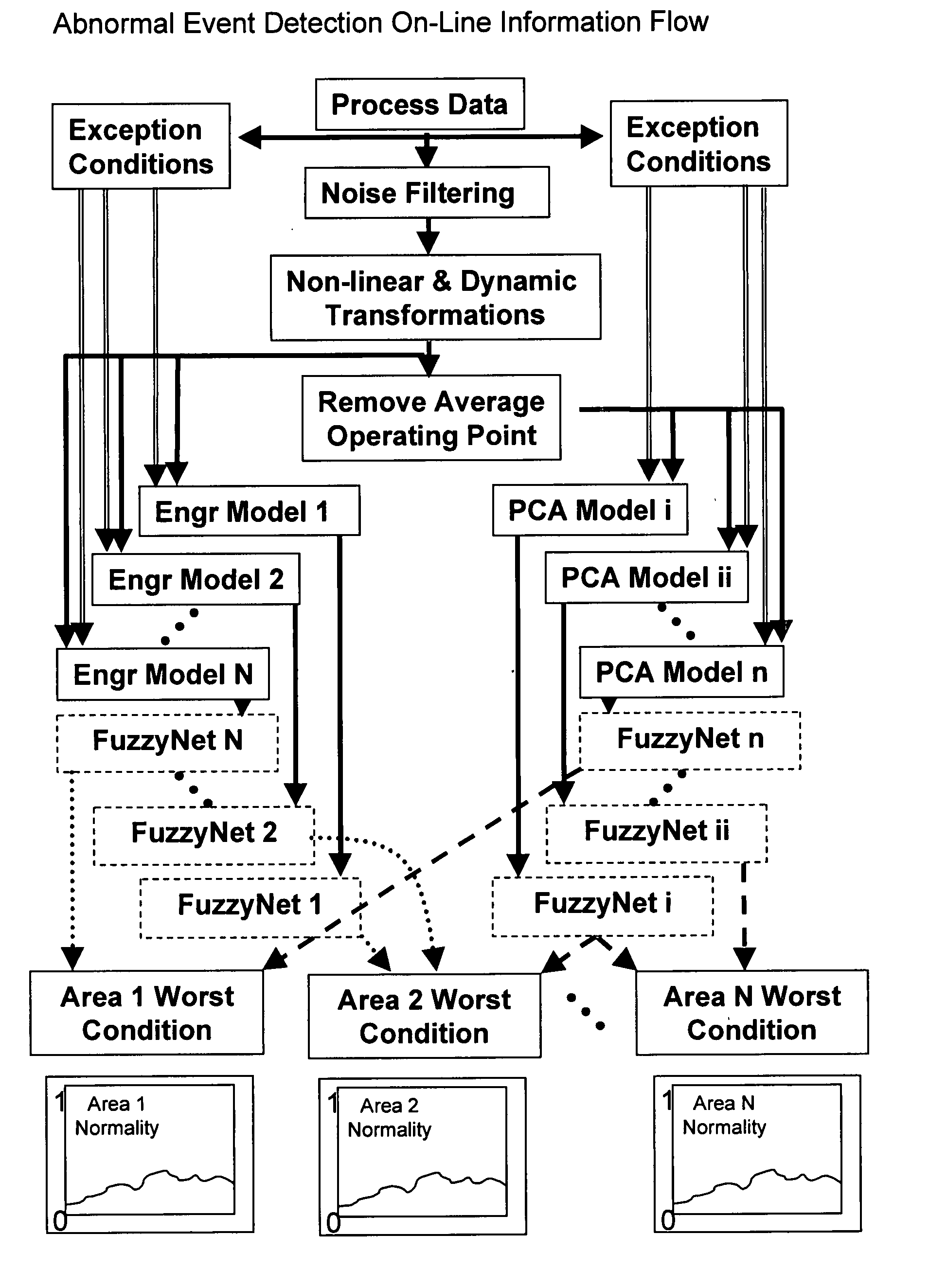
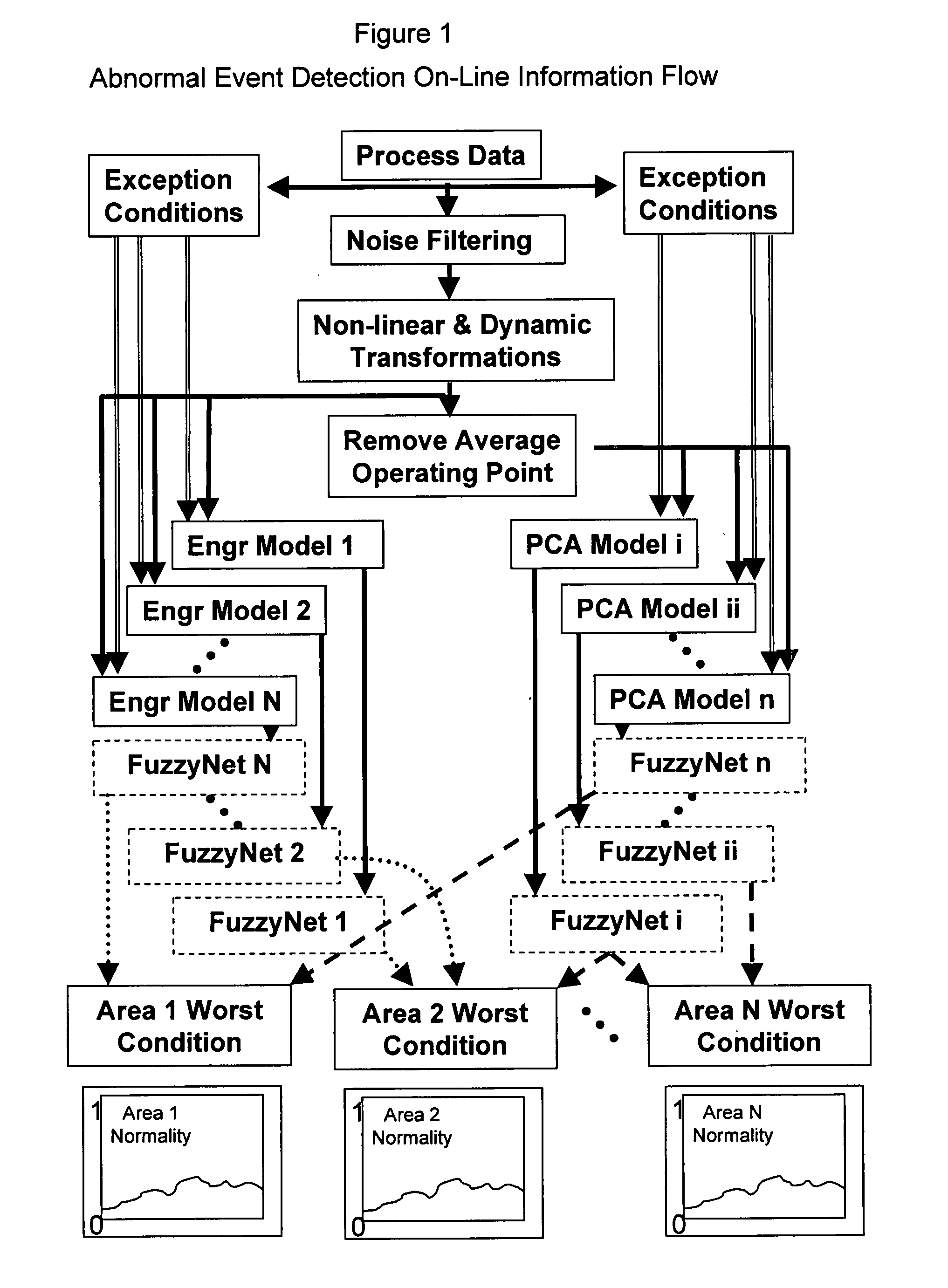
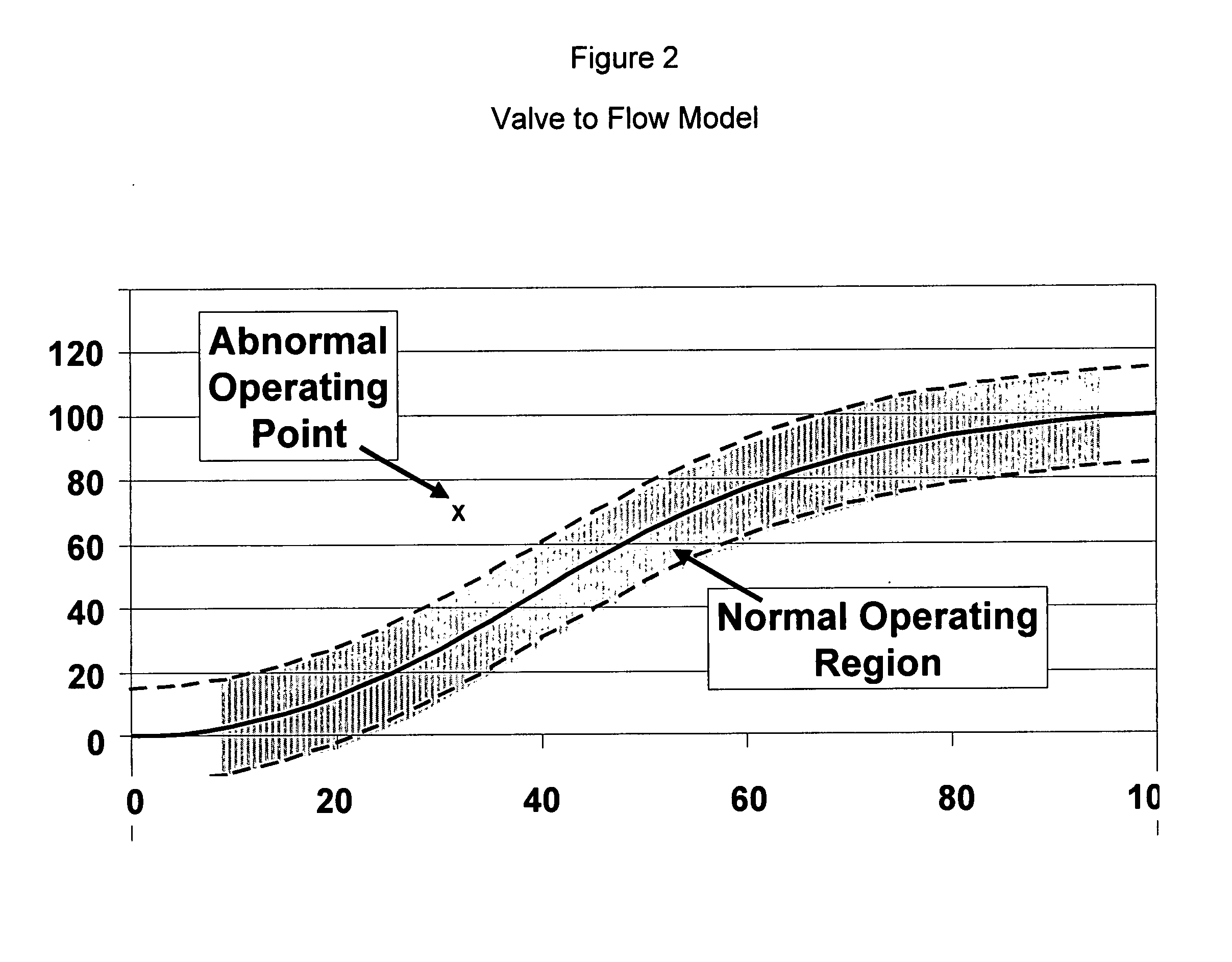
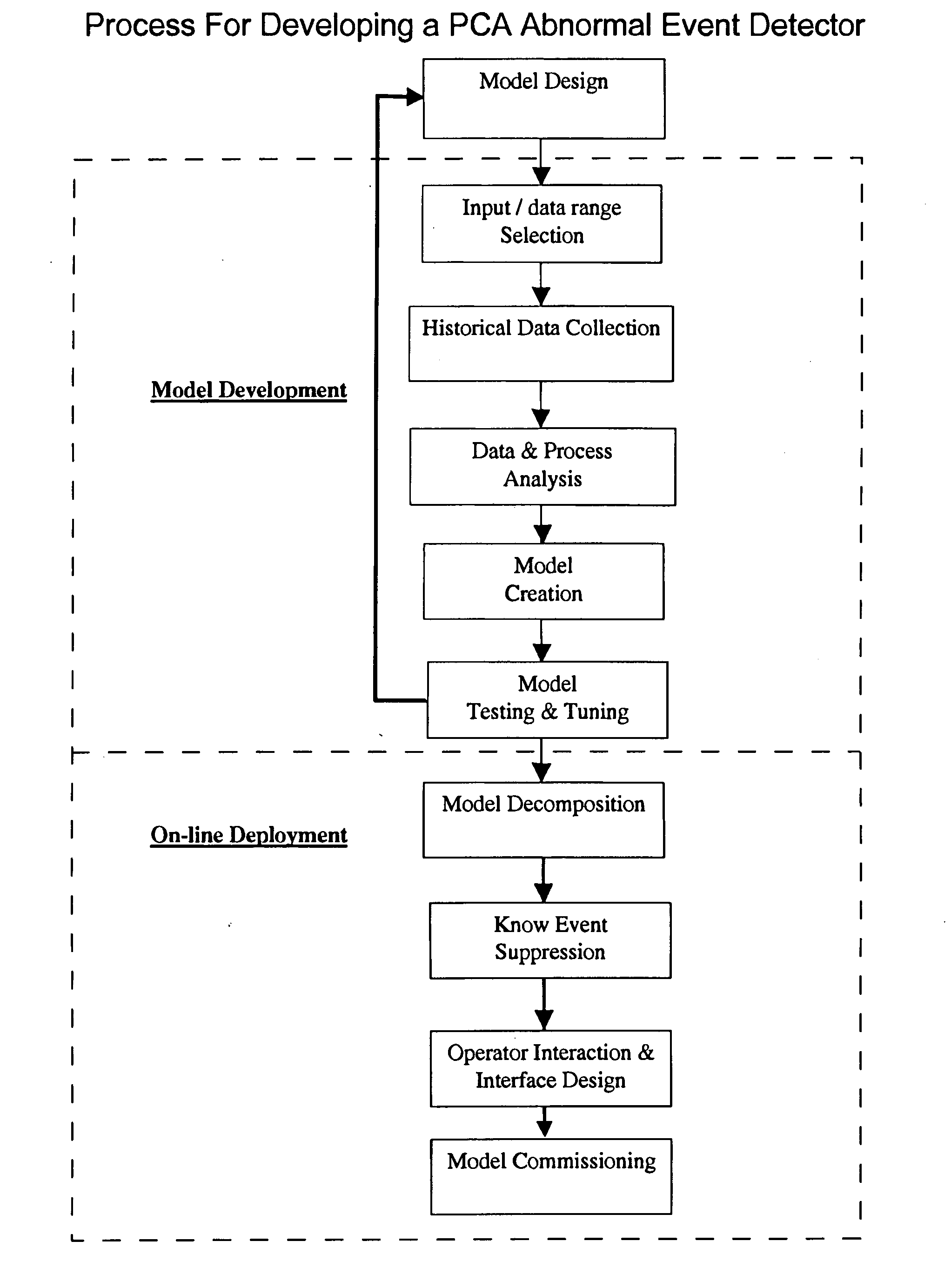
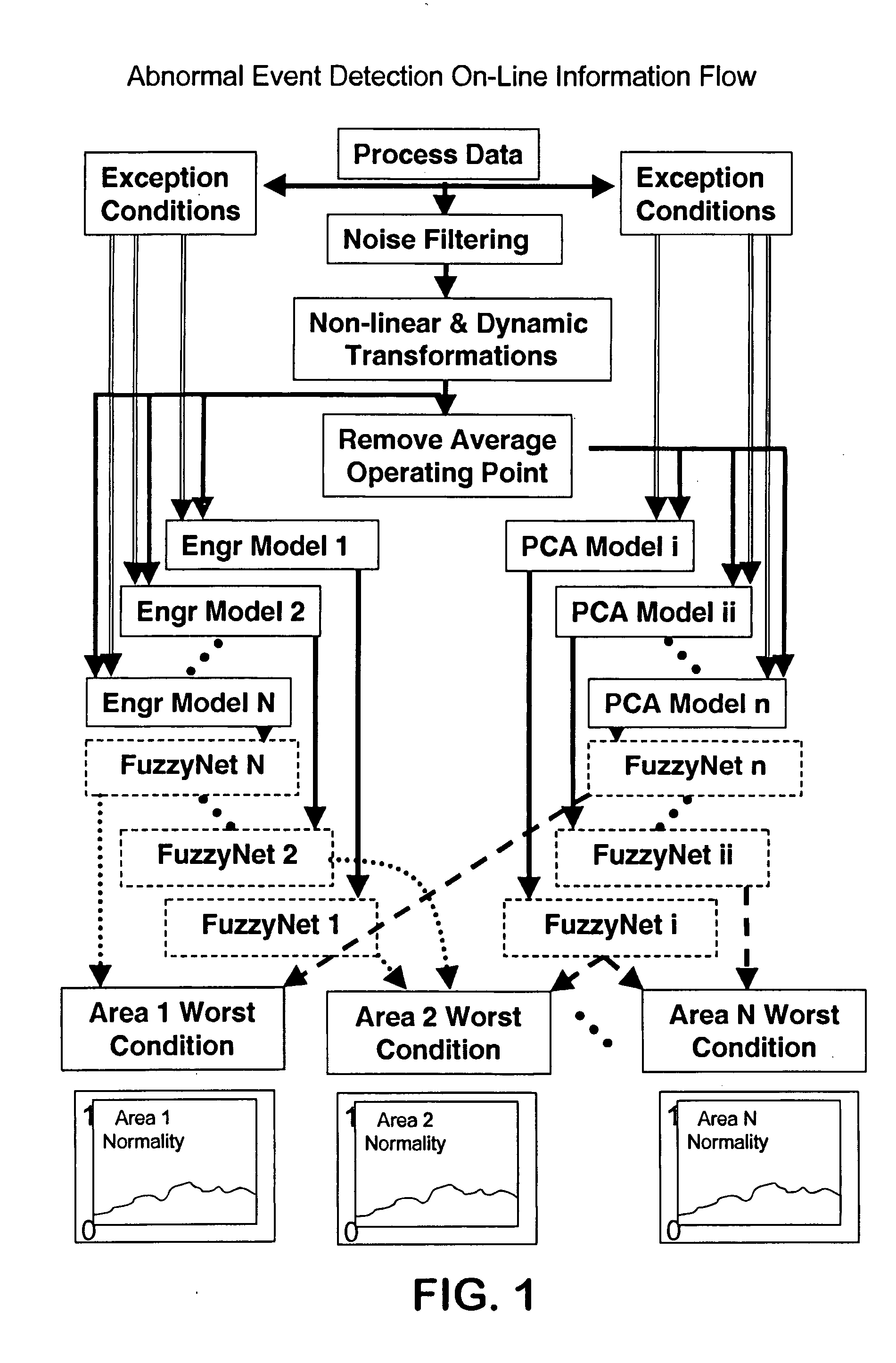
Application of abnormal event detection technology to fluidized catalytic cracking unit
ActiveUS20060073013A1PropellersSpecial data processing applicationsPrincipal component analysisCorrelation analysis
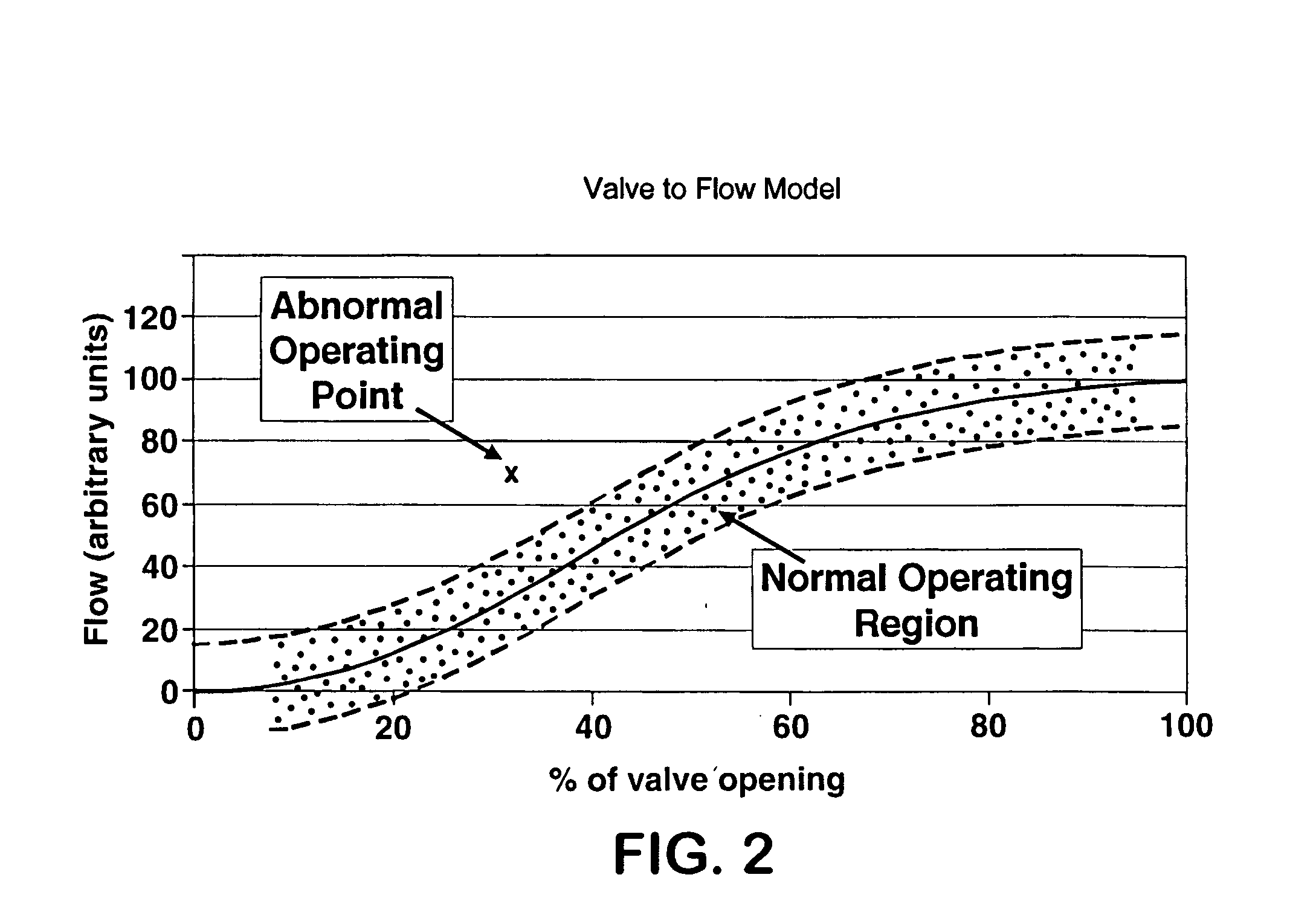
The present invention is a method for detecting an abnormal event for process units of a Fluidized Catalytic Cracking Unit. The method compares the operation of the process units to a statistical and engineering models. The statistical models are developed by principle components analysis of the normal operation for these units. In addition, the engineering models are based on partial least squares analysis and correlation analysis between variables. If the difference between the operation of a process unit and the normal model result indicates an abnormal condition, then the cause of the abnormal condition is determined and corrected.
Owner:EXXON RES & ENG CO
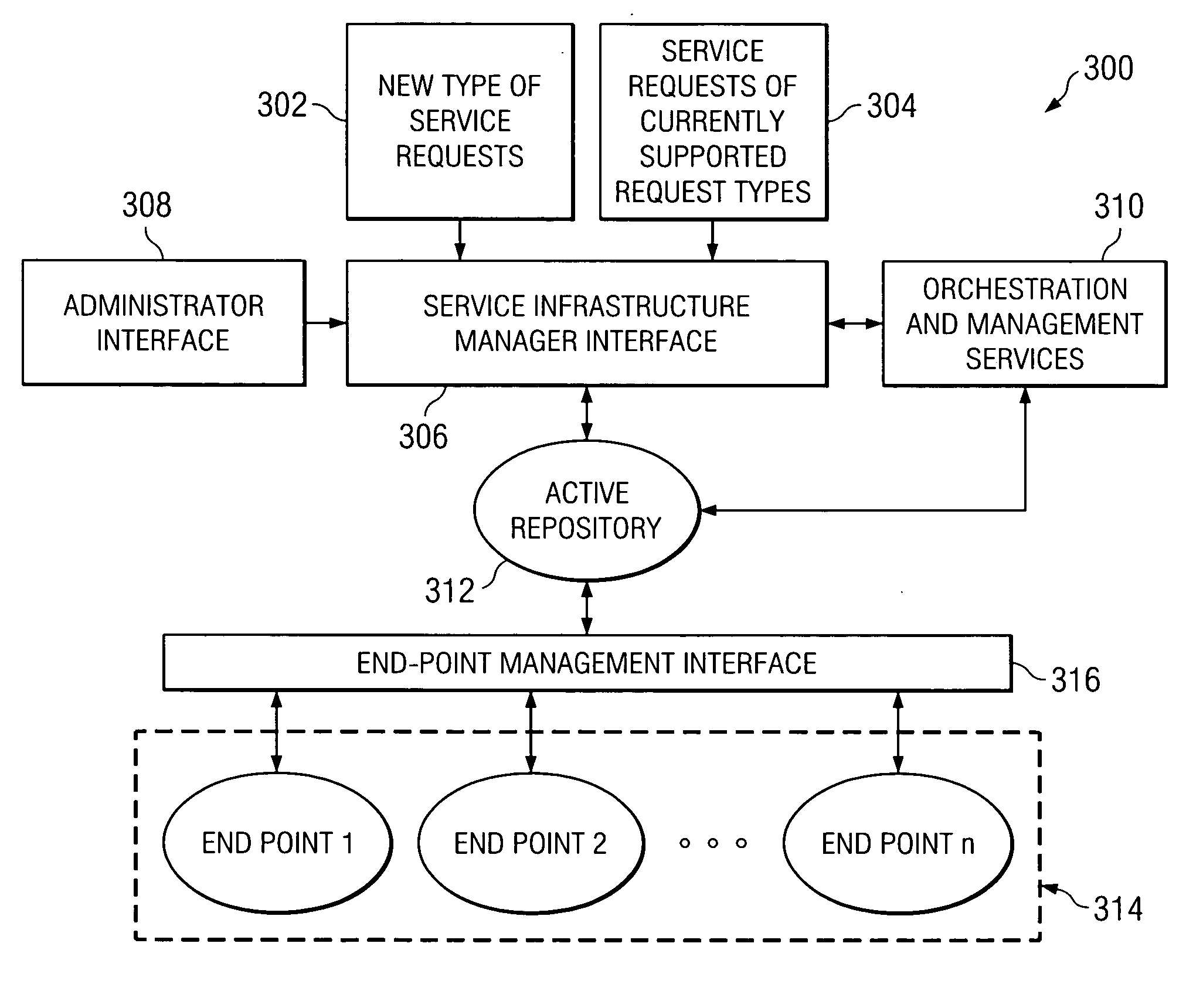
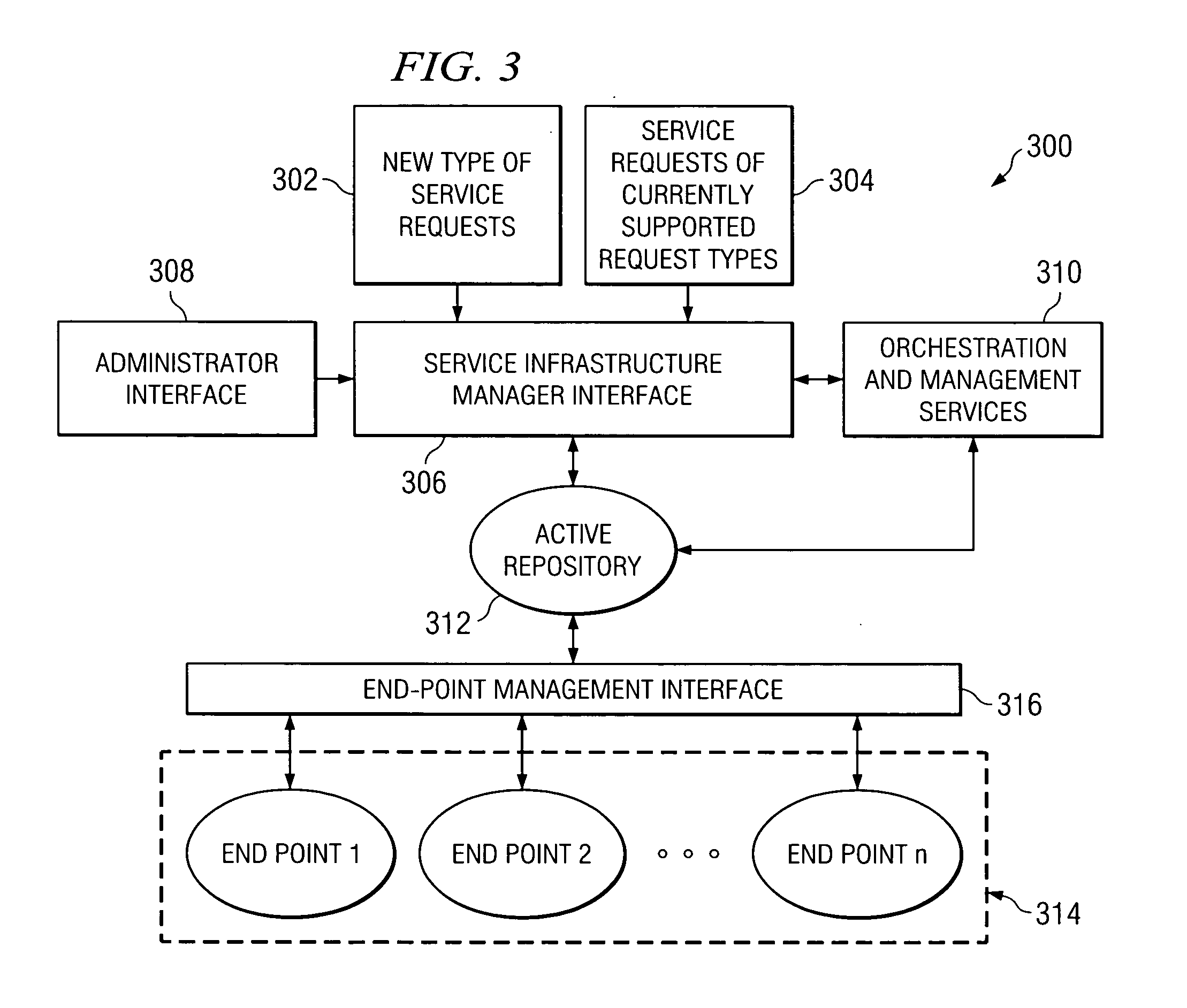
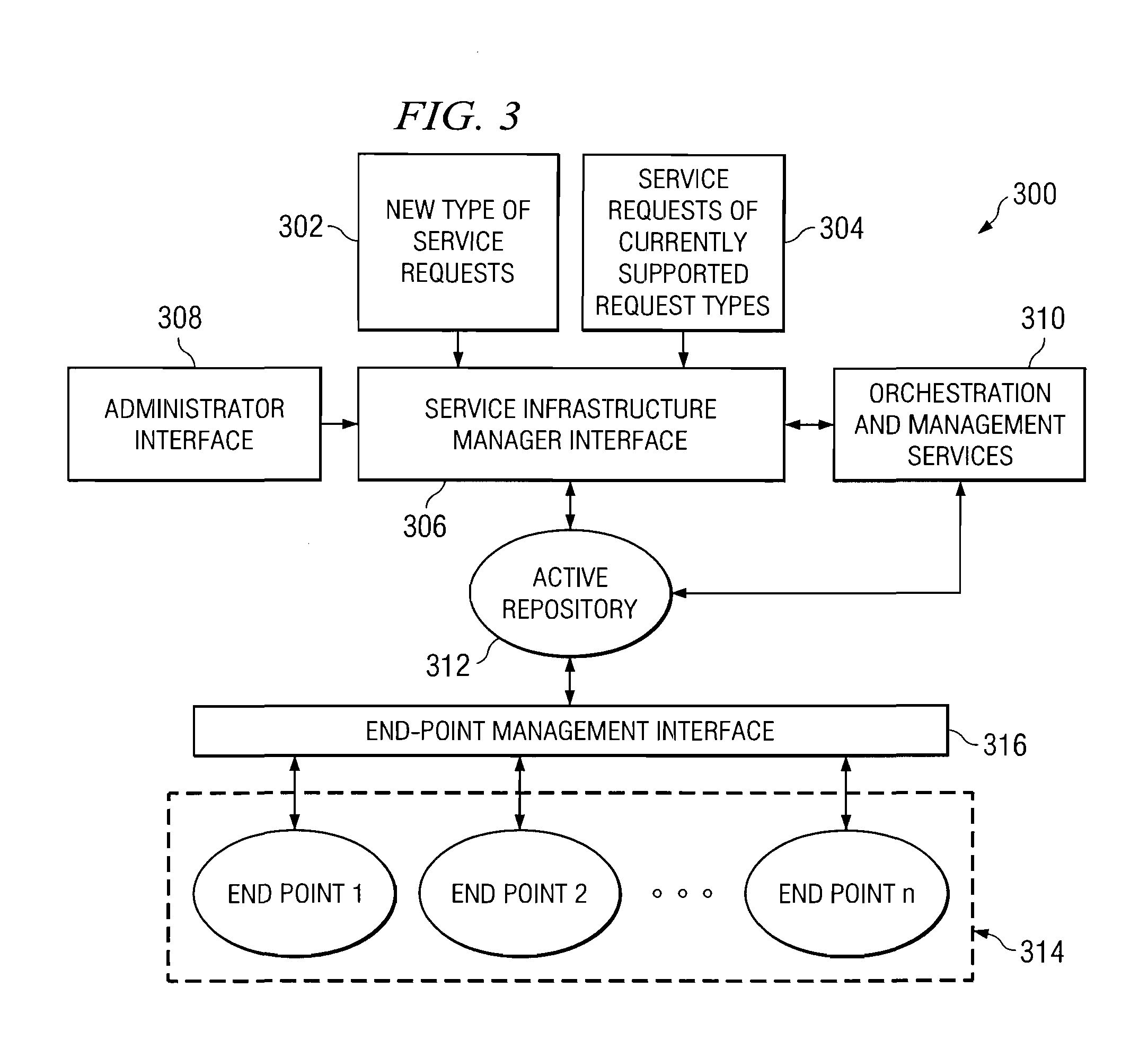
Management of composite software services
InactiveUS20070294364A1Multiple digital computer combinationsProgram controlData processing systemTemplate based
A computer implemented method, data processing system, computer usable program code, and active repository are provided for management of a software service. A request is received to deploy the software service in a computer network. A dependency analysis is performed for the requested software service to determine component software services and physical resources necessary to deploy and manage new software service as a composite in responsive to the software service being the new software service. An active object is created to manage the new software service using an active template based on the analysis. The new software service is deployed in the computer network using the active object. The new software service is managed using the active object.
Owner:IBM CORP
Application of abnormal event detection technology to delayed coking unit
ActiveUS20070250292A1Efficiently presentedPlug gaugesMeasurement arrangements for variablePrincipal component analysisCorrelation analysis
The present invention is a method for detecting an abnormal event for process units of a Delayed Coking Unit. The method compares the operation of the process units to statistical and engineering models. The statistical models are developed by principal components analysis of the normal operation for these units. The engineering models are based statistical and correlation analysis between variables. If the difference between the operation of a process unit and the normal model result indicates an abnormal condition, then the cause of the abnormal condition is determined and corrected.
Owner:EXXON RES & ENG CO
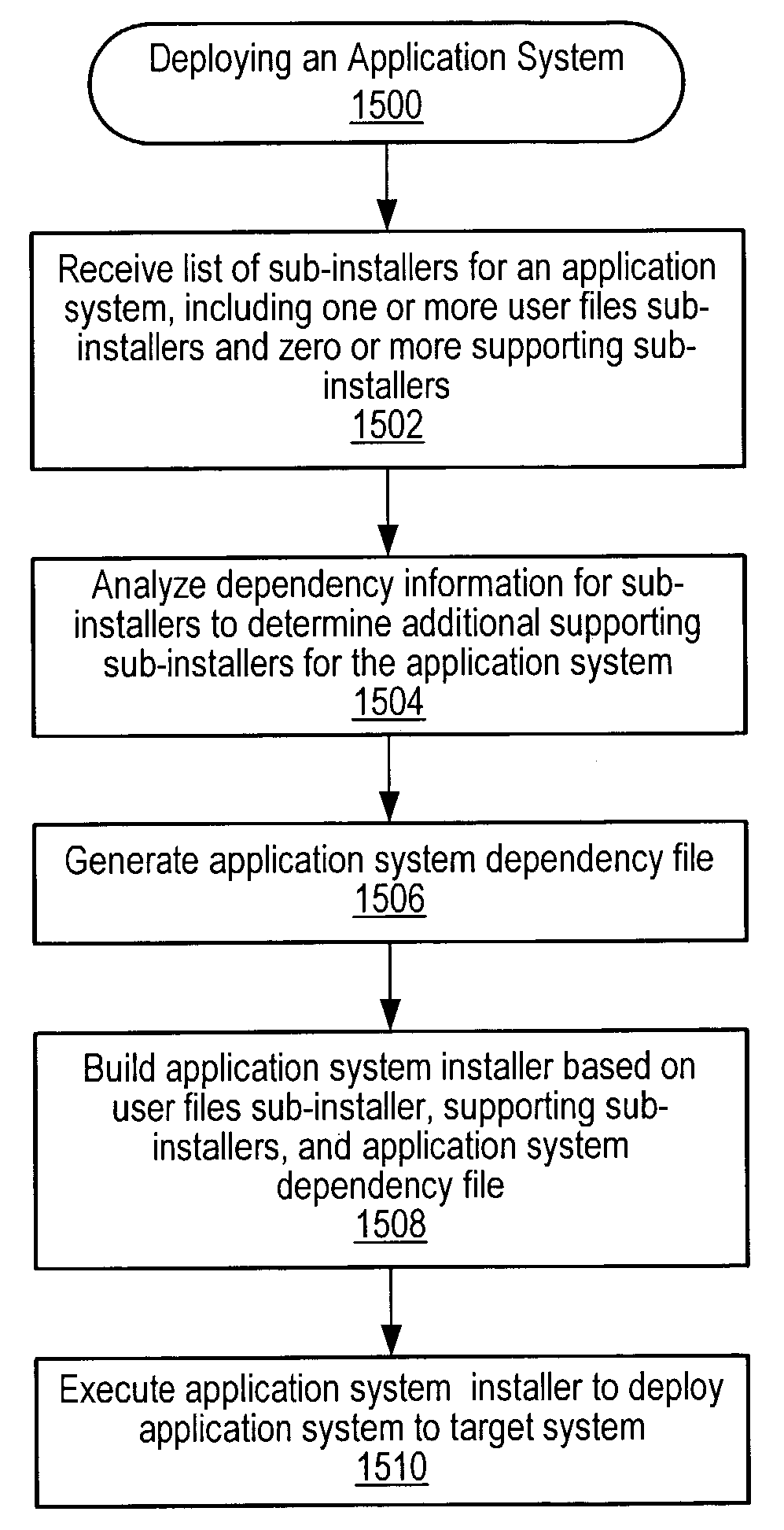
Installing software using programmatic component dependency analysis
ActiveUS7478385B2Maximum flexibilityChoose simpleProgram loading/initiatingMemory systemsGoal systemApplication software
System and method for installing software using component dependency analysis. A list indicating an initial set of sub-installers is received, each sub-installer including respective software components and installation software for deploying the components onto a target system. The initial set of sub-installers includes one or more user-files sub-installers and one or more supporting sub-installers. The initial set of sub-installers is programmatically analyzed (e.g., re dependencies) to determine additional sub-installers. An application system dependency file is generated based on the analysis, and an application system installer generated based on the sub-installers and the application system dependency file. The installer is executed to programmatically deploy the application system onto the target system, where executing includes programmatically analyzing the target system, application system dependency file, and user-specified deployment options (entered via a user-interface) to determine an installation set of sub-installers, each of which is executed to deploy respective components onto the target system.
Owner:NATIONAL INSTRUMENTS
Iterative software development environment with prioritized build rules
ActiveUS6922827B2Version controlSpecific program execution arrangementsSoftware developmentBuilt environment
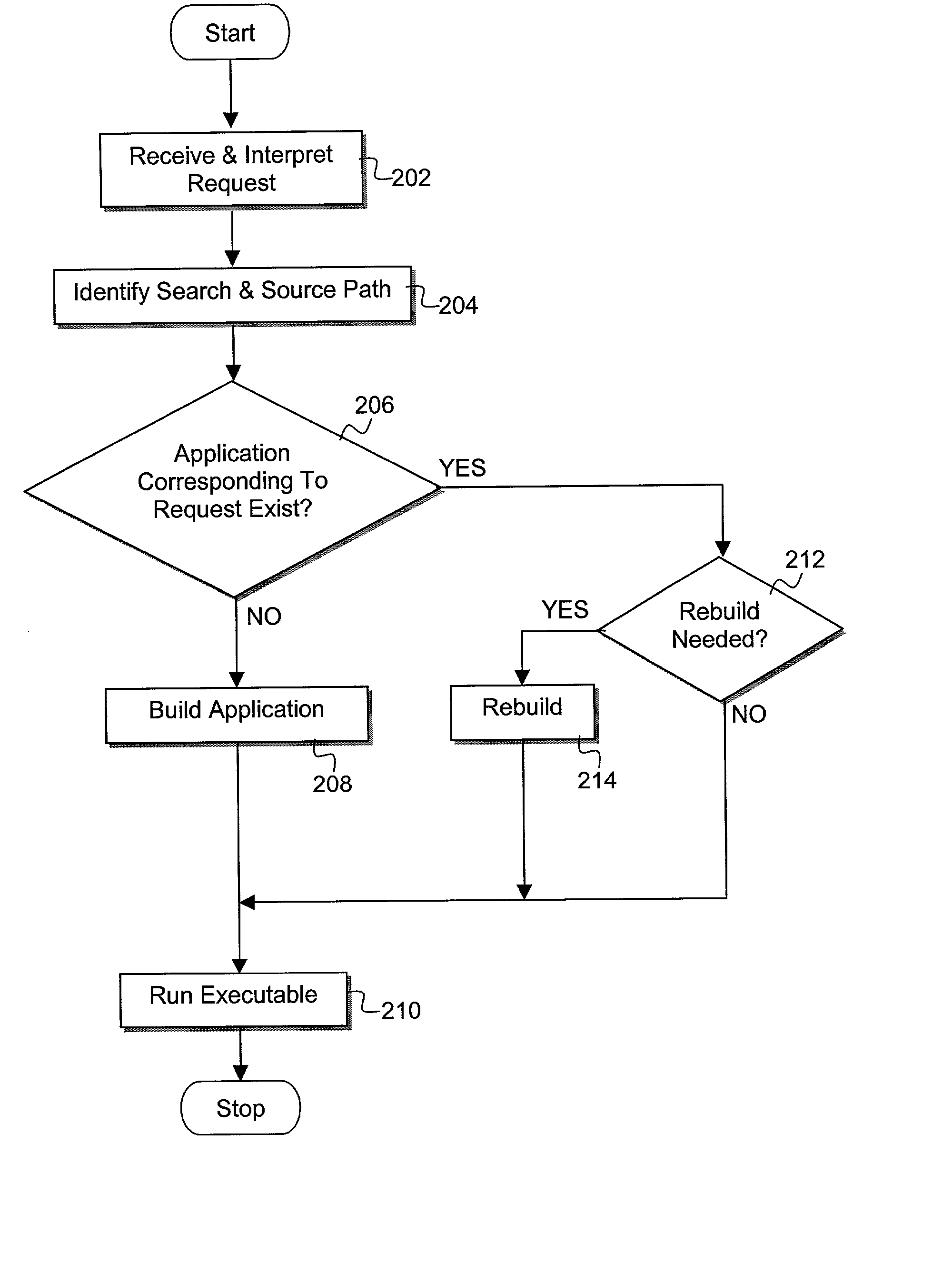
An iterative software development environment is provided to perform modified dependency analyses for use in building a target file and all the files on which it depends from one or more source files using a set of prioritized build rules. In one embodiment, the build rules indicate how different types of target files can be generated from different source file types. A given target file type may be associated with several rules, each having a different priority, for building the target from different source file types. In one embodiment, if more than one source file exists that can be used to generate a given target file, the rule with the highest priority is used. In one embodiment, the build environment identifies how to generate a particular target file by identifying the highest priority rule for which an associated source file type exists. Moreover, the development environment identifies the presence of a new source file having a corresponding build rule with a higher priority than that of the source file type(s) previously used in the generation of the target file. In one embodiment of the invention, the target file is rebuilt if such a new source file is identified, or if one or more source files previously used to build the target file are determined to have been modified more recently than that indicated by the build date / time of the target file itself.
Owner:ORACLE INT CORP
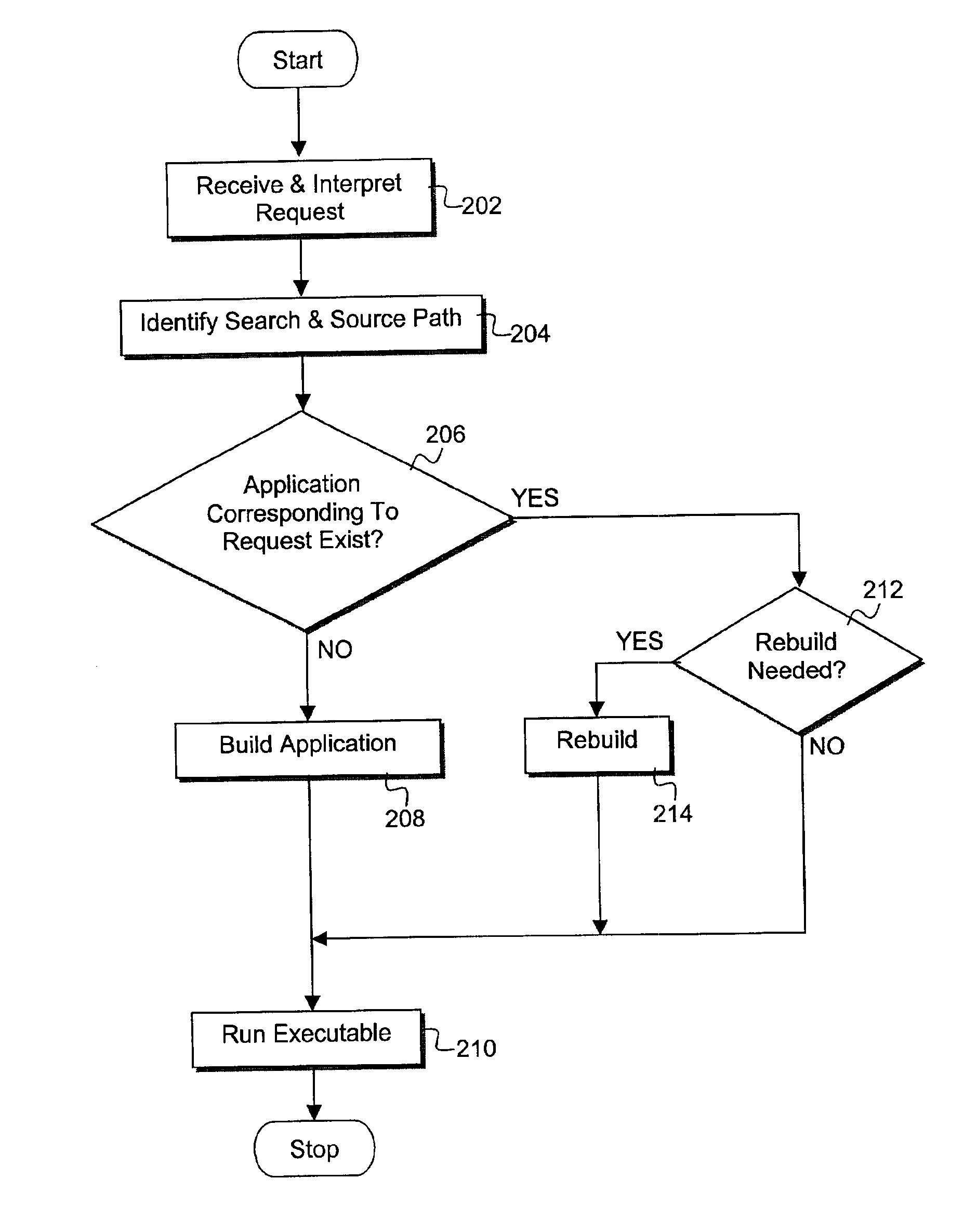
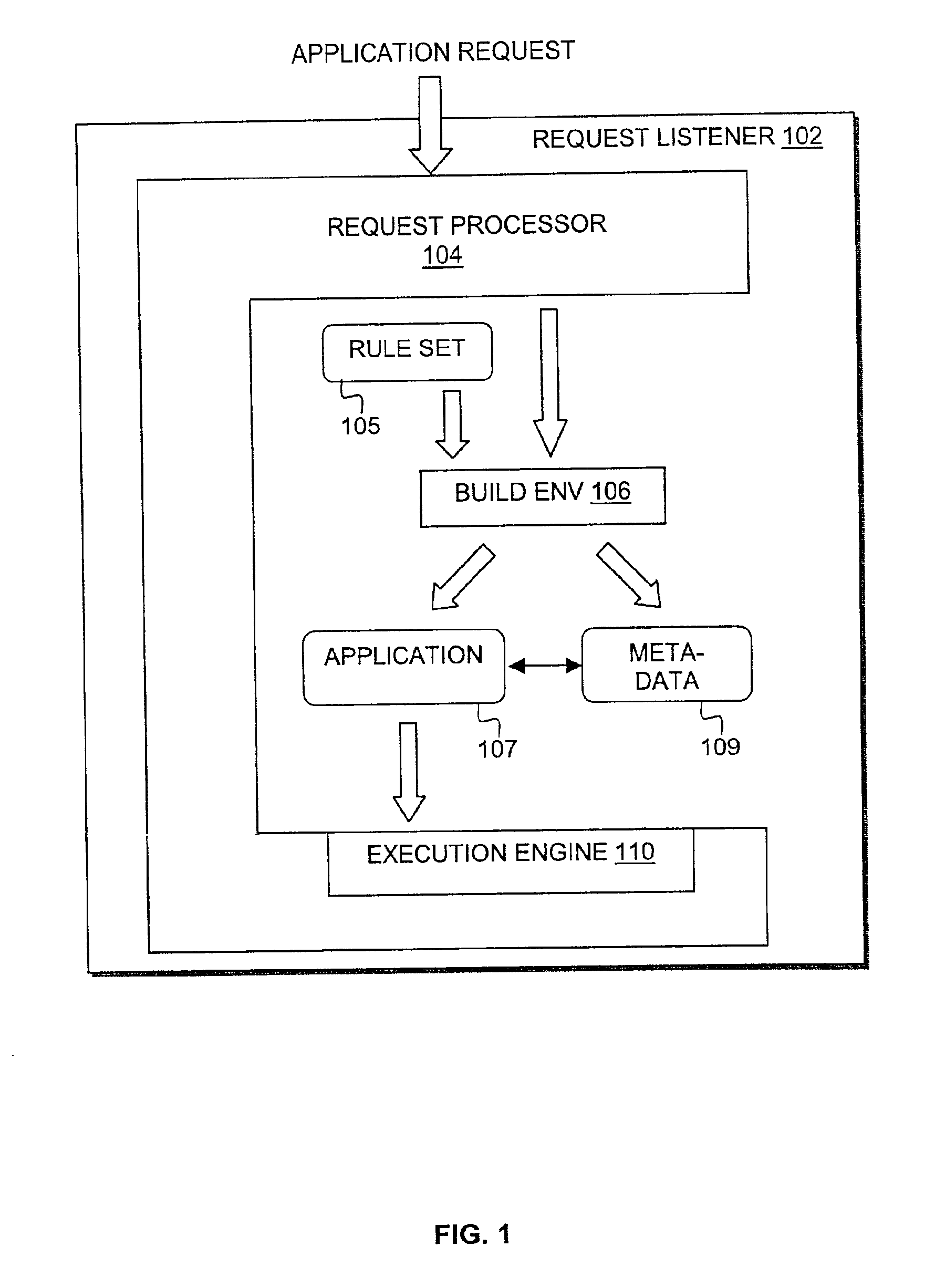
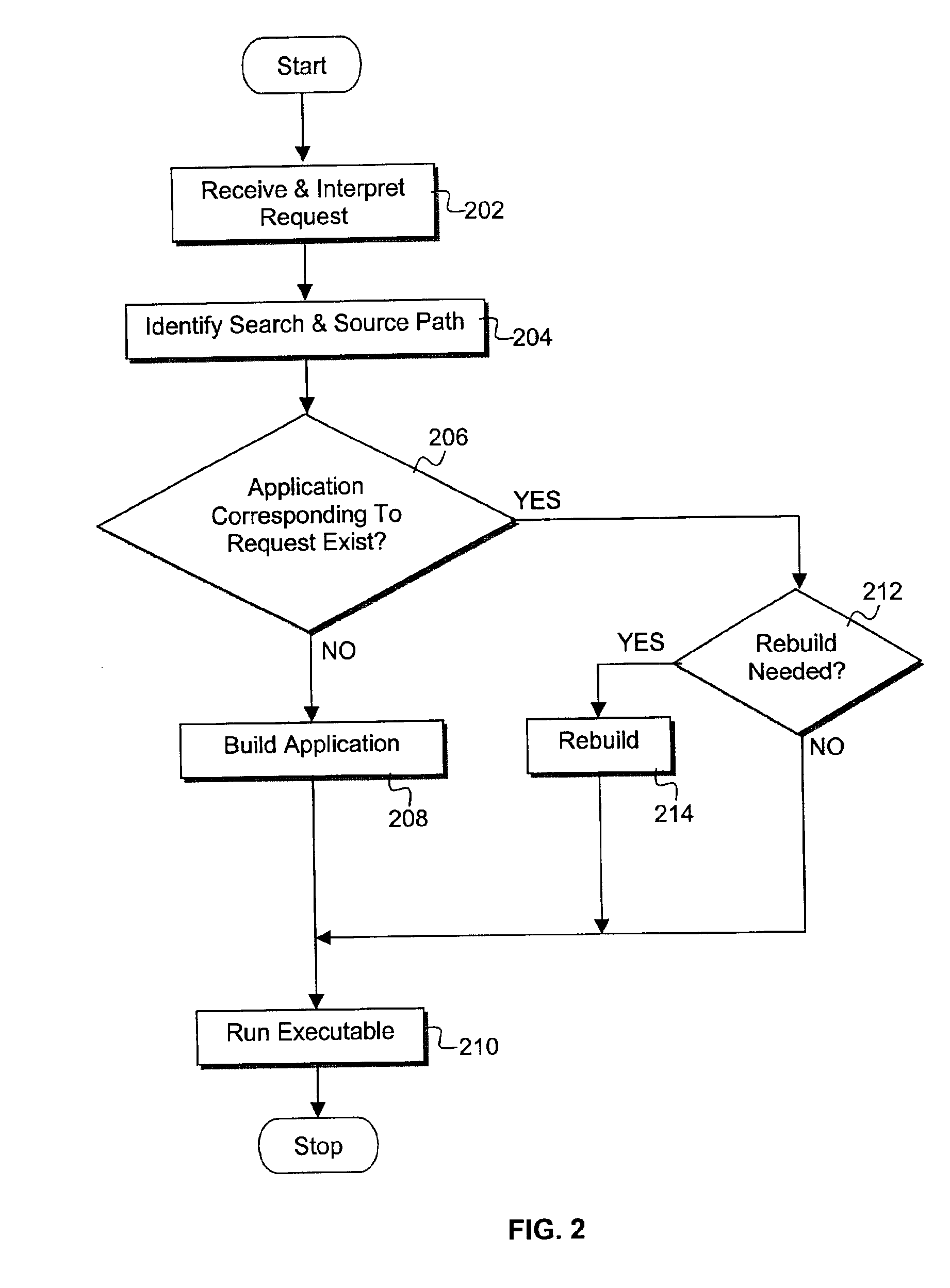
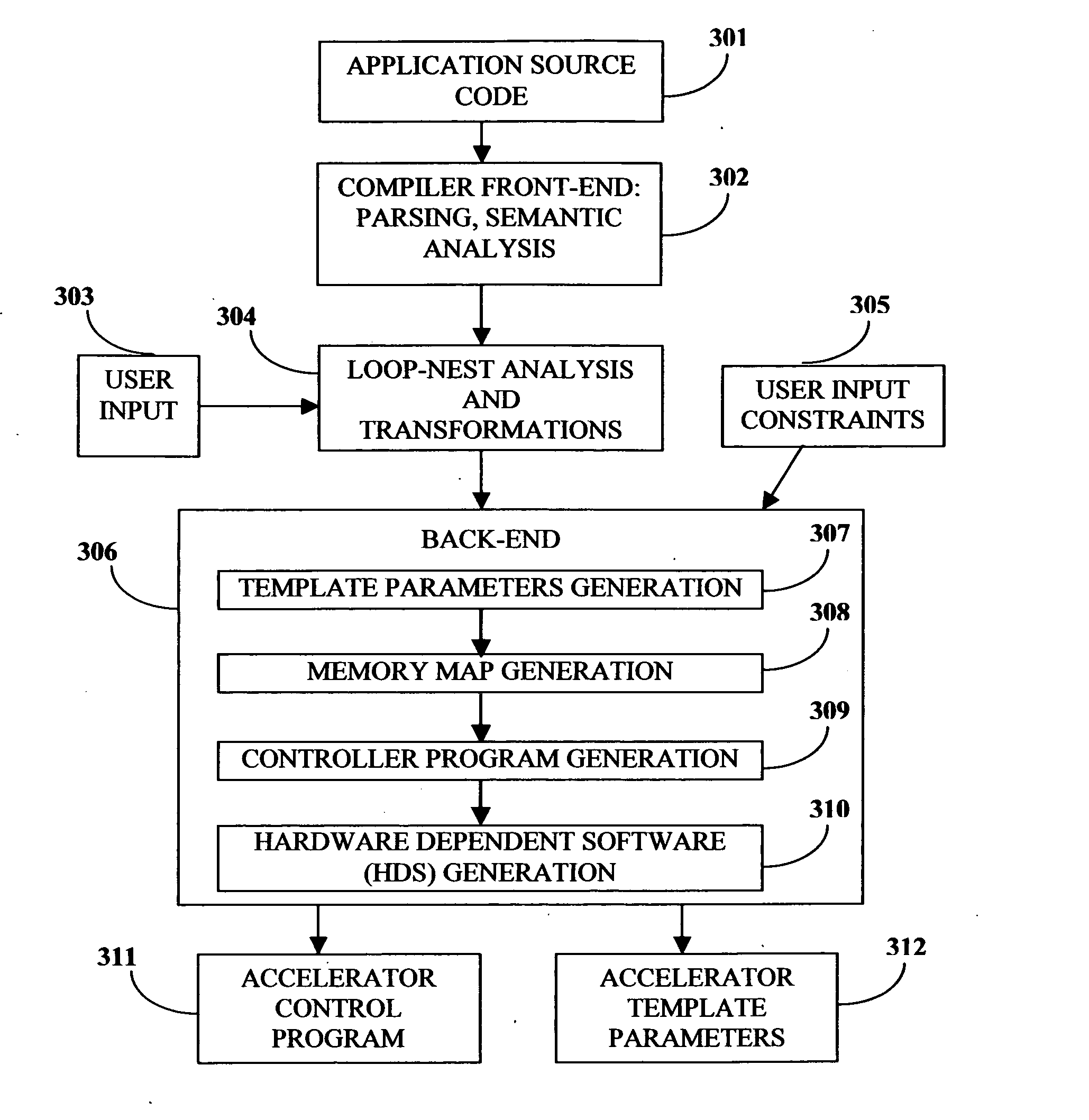
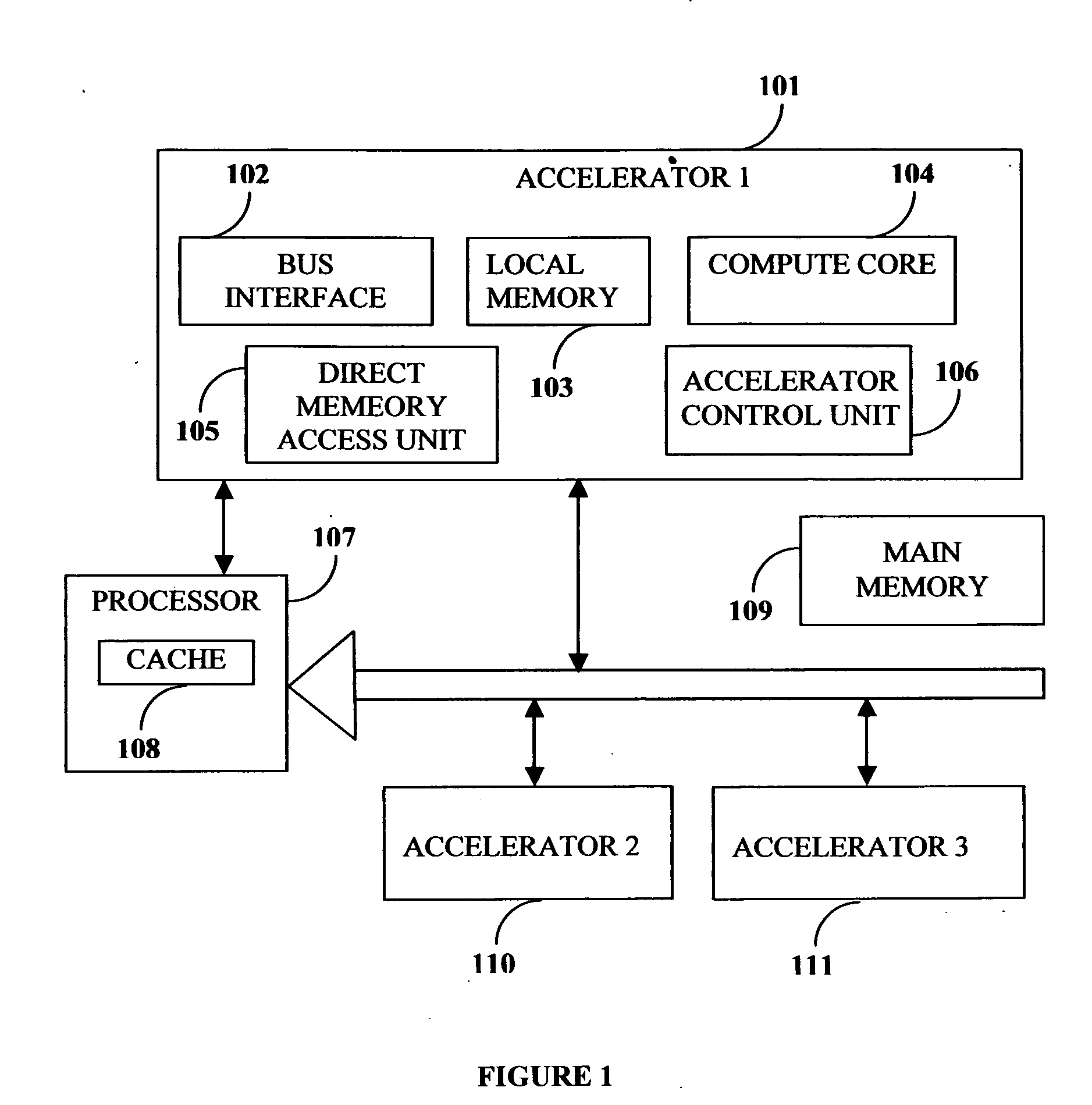
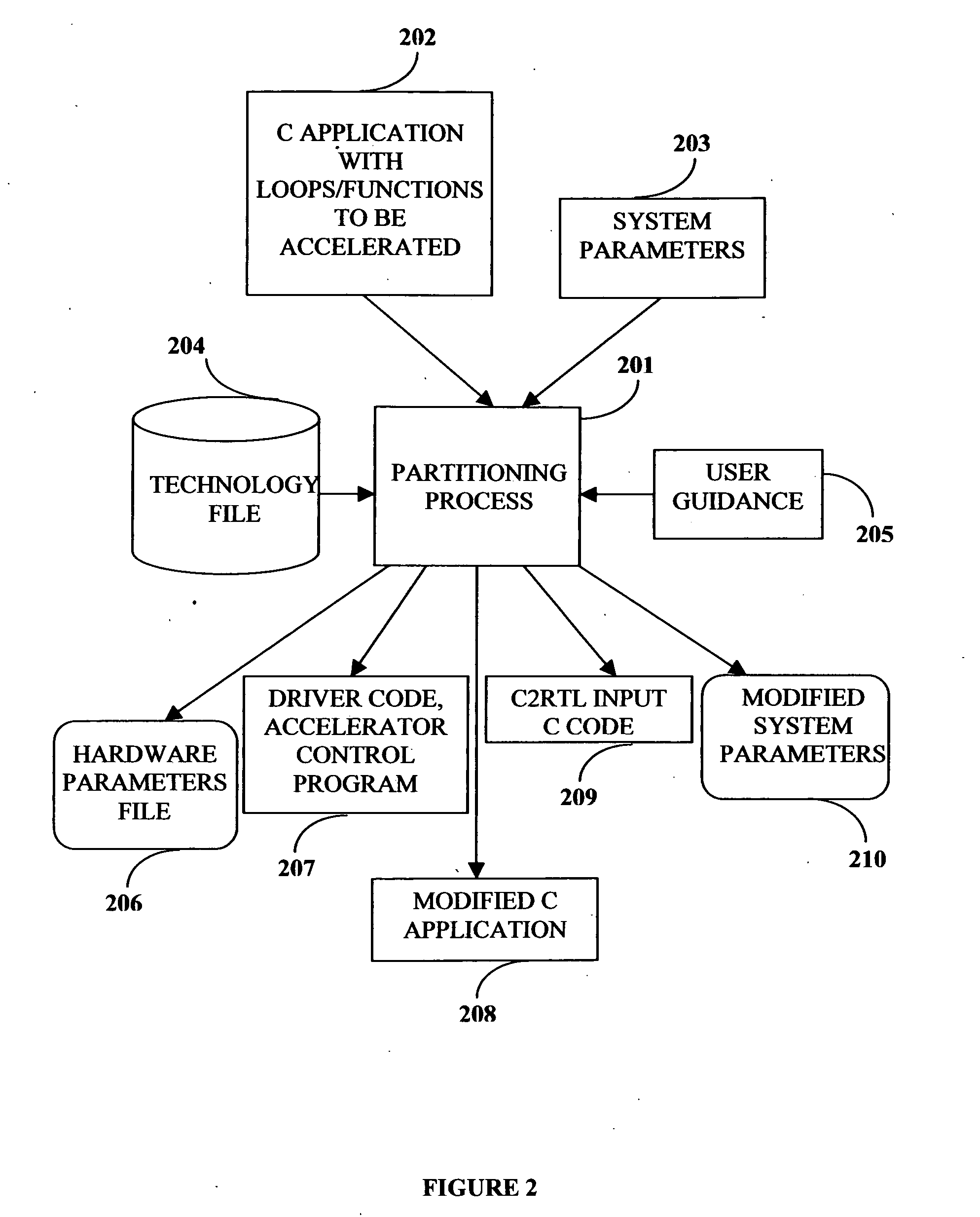
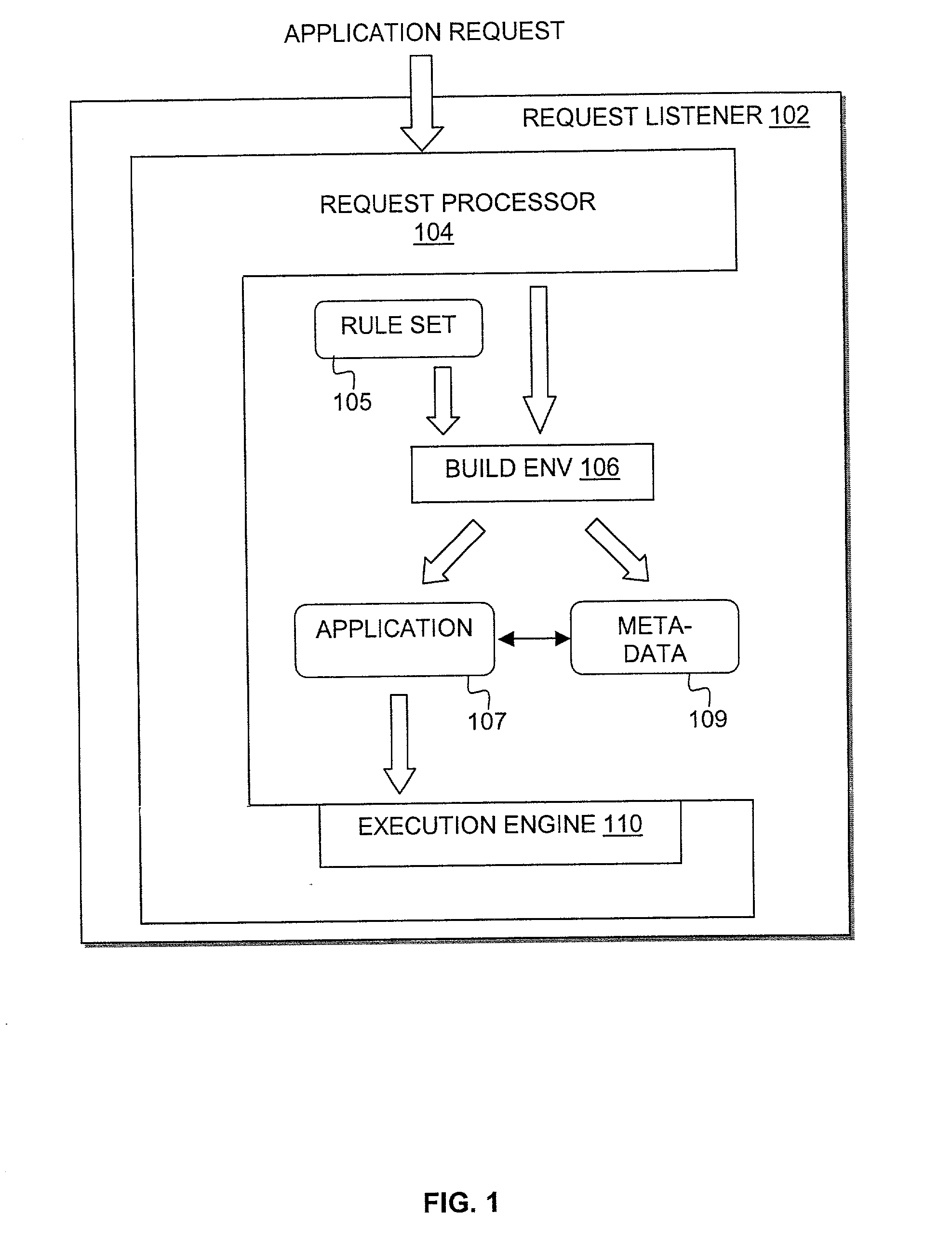
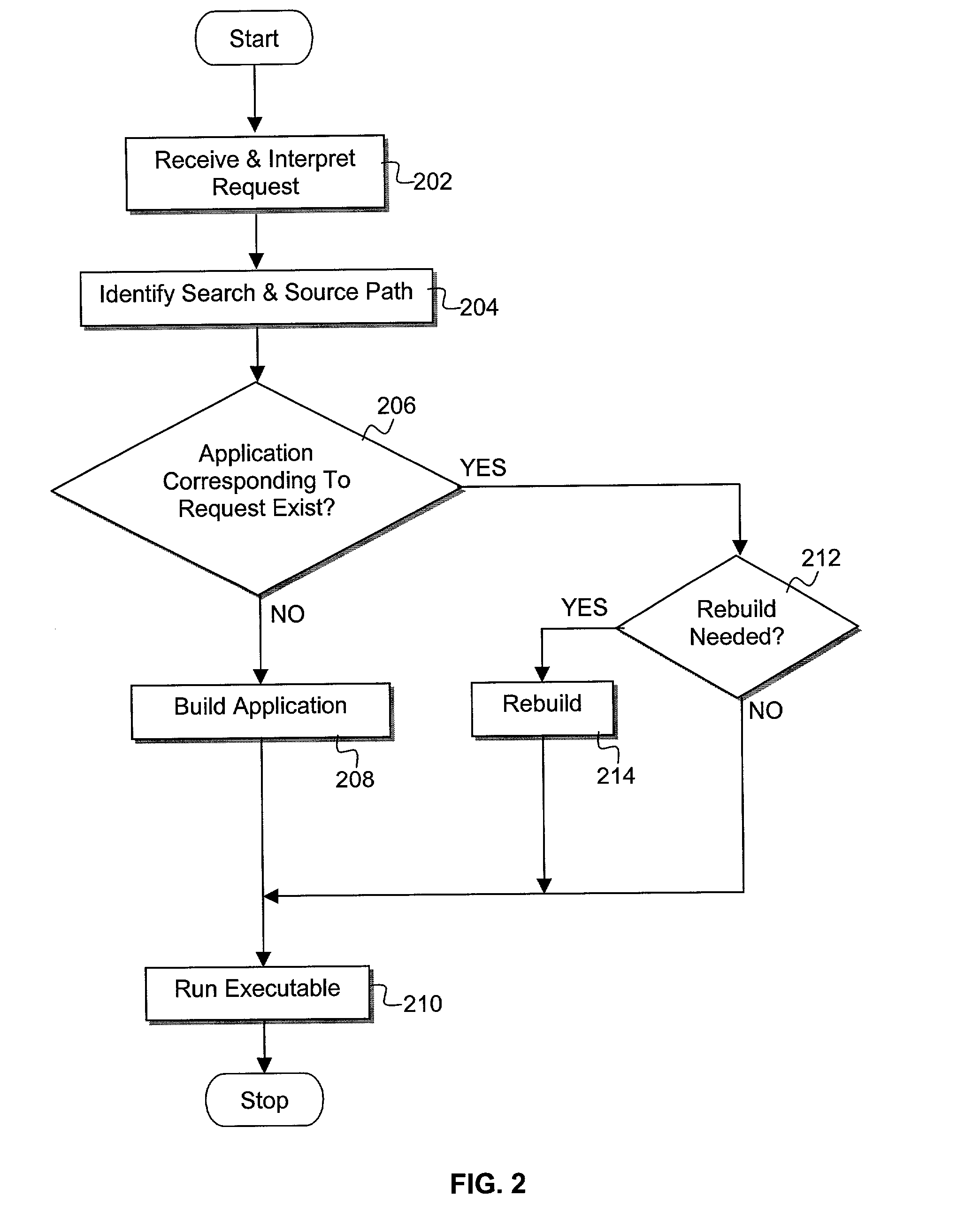
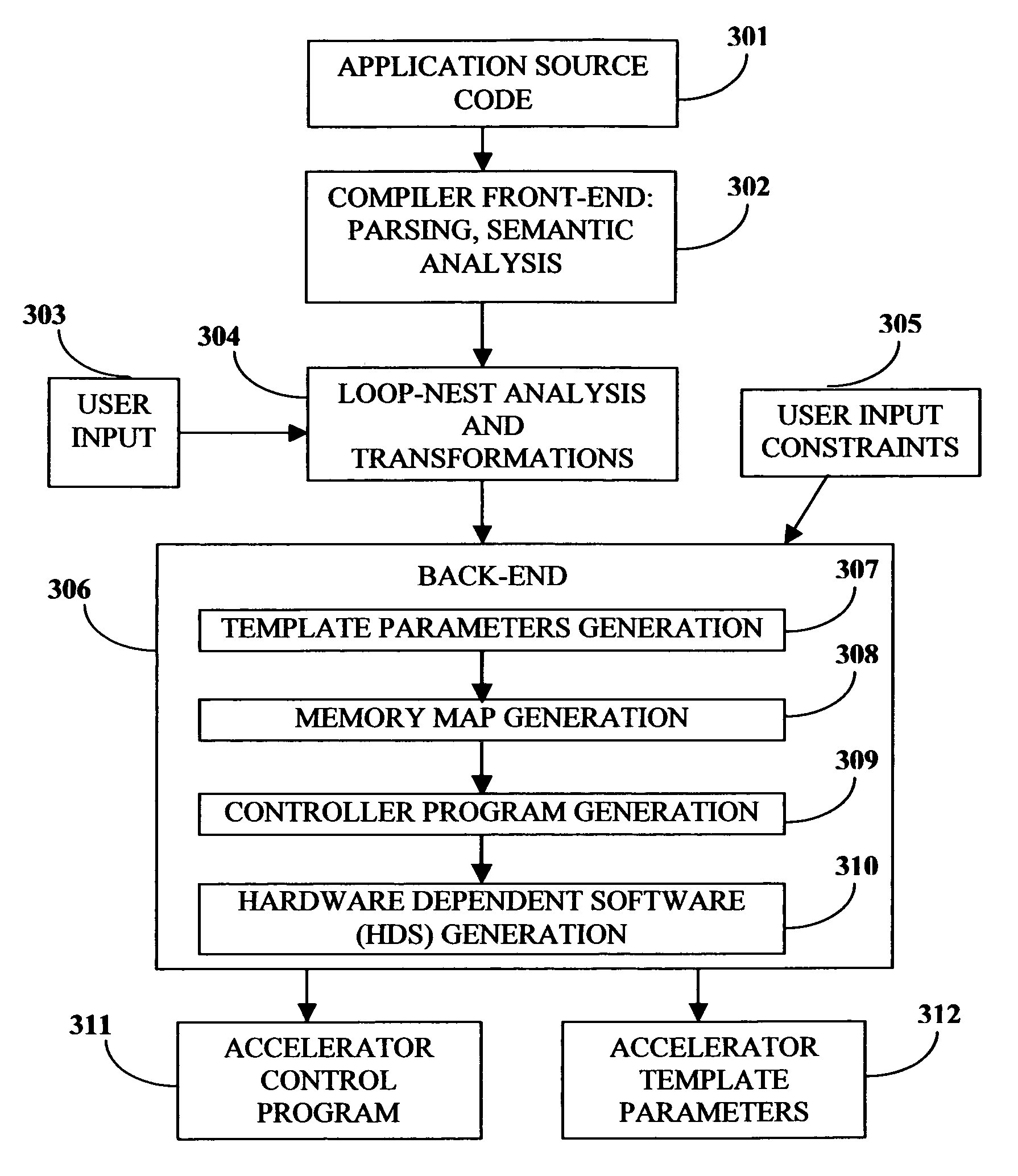
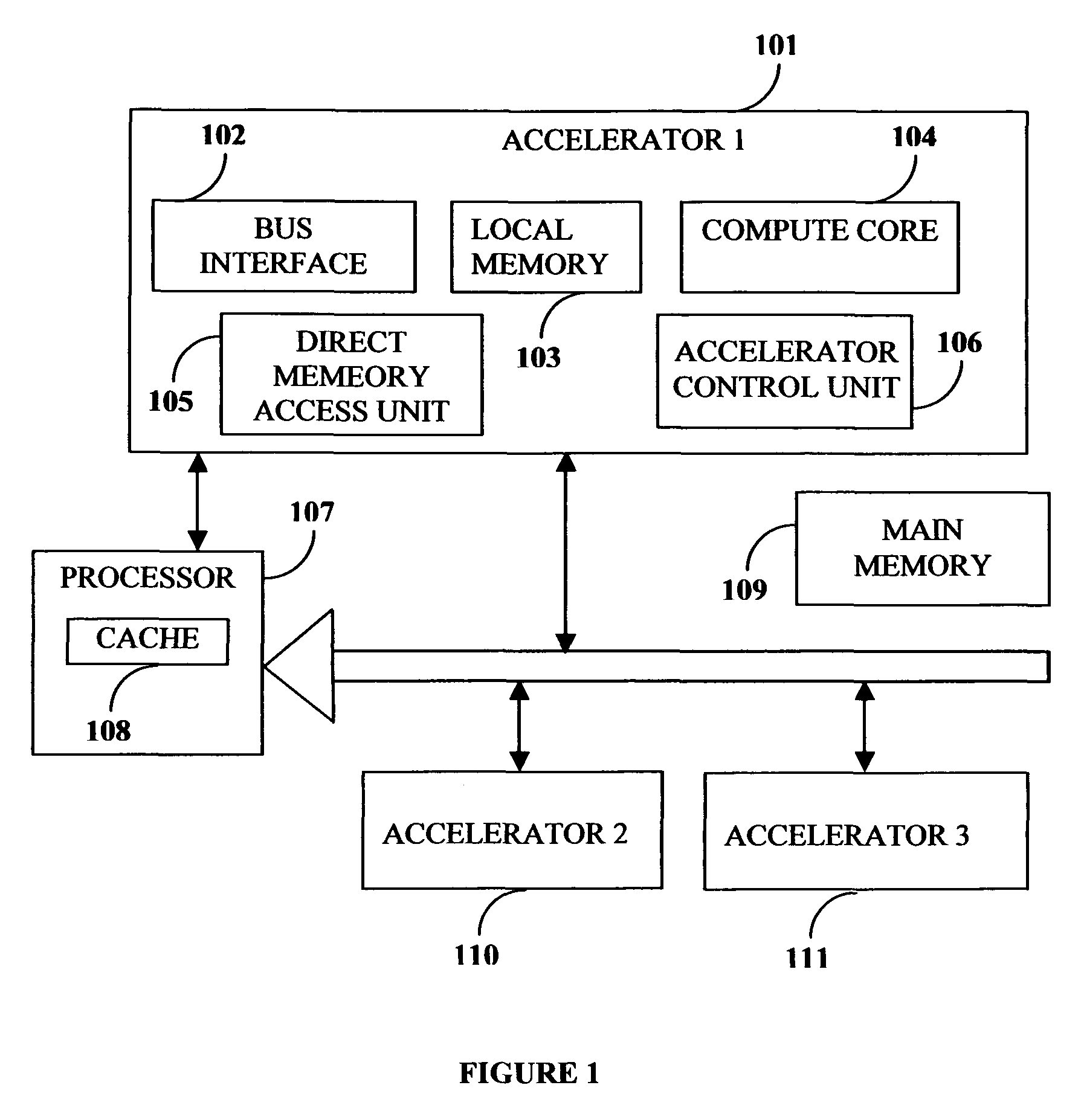
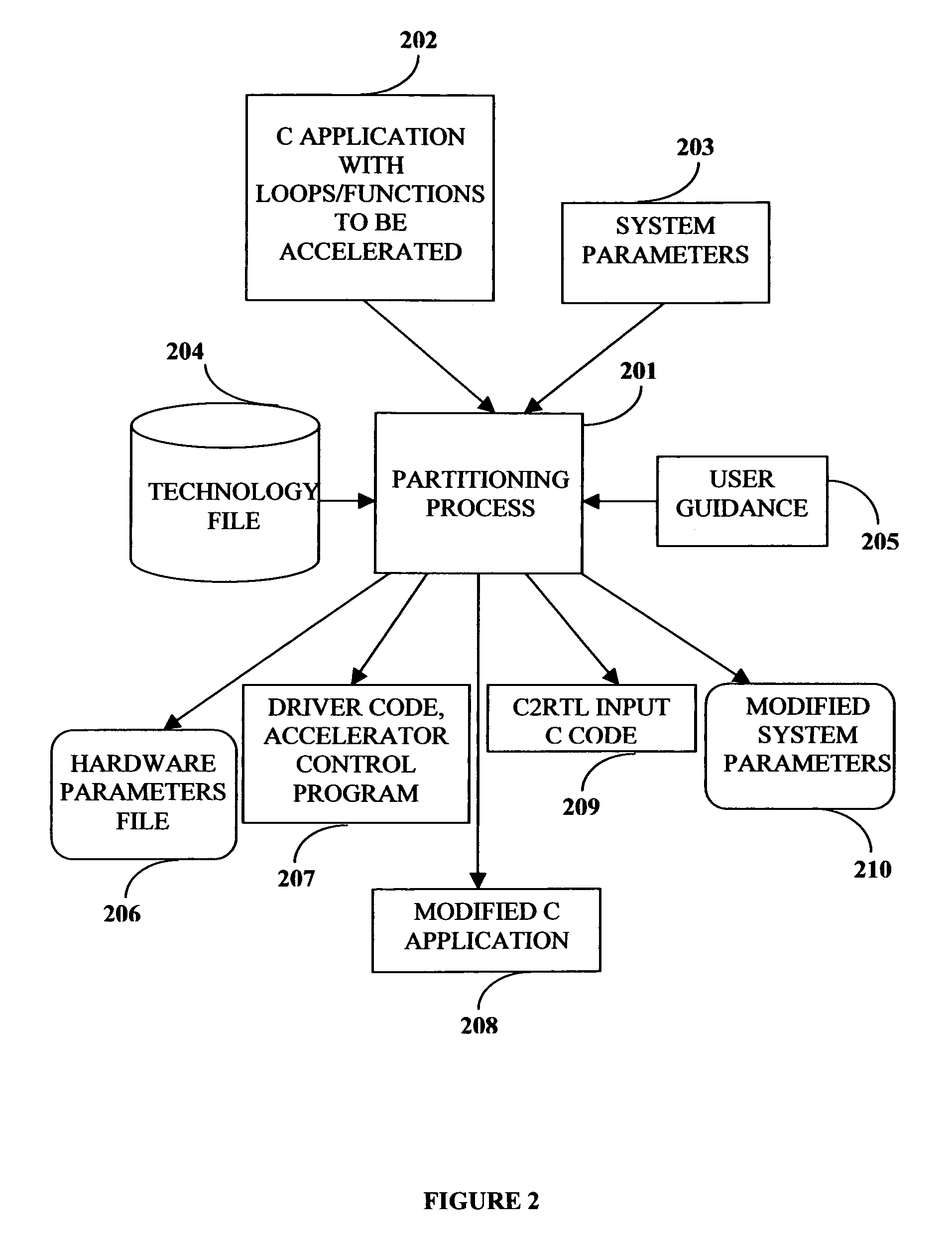
Compiler method for extracting and accelerator template program
InactiveUS20070169059A1Software engineeringSpecific program execution arrangementsSemantic translationSemantics
This invention describes a compilation method of extracting and implementing an accelerator control program from an application source code in a processor based system. The application source code comprises arrays and loops. The input application source code is sequential, with loop, branch and call control structures, while the generated output of this invention has parallel execution semantics. The compilation method comprises the step of performing loop nest analysis, transformations and backend processes. The step of loop nest analysis consists of dependence analysis and pointer analysis. Dependence analysis determines the conflicts between the various references to arrays in the loop, and pointer analysis determines if two pointer references in a loop are in conflict. Transformations convert the loops from their original sequential execution semantics to parallel execution semantics. The back-end process determines the parameters and memory map of the accelerator and the hardware dependent software.
Owner:POSEIDON DESIGN SYST
Application of abnormal event detection (AED) technology to polymers process
ActiveUS20080097637A1Efficiently presentedSimulator controlTesting/monitoring control systemsPrincipal component analysisCorrelation analysis
The present invention is a method and system for detecting an abnormal event for process units of a Polymers Unit. The method compares the operation of the process units to statistical, engineering or heuristic models. The statistical models are developed by principle components analysis of the normal operation for these units. In addition, the engineering models are based on correlation analysis between variables or simple engineering calculations. If the difference between the operation of a process unit and the normal model result indicates an abnormal condition, then the cause of the abnormal condition is determined and corrected.
Owner:EXXON RES & ENG CO
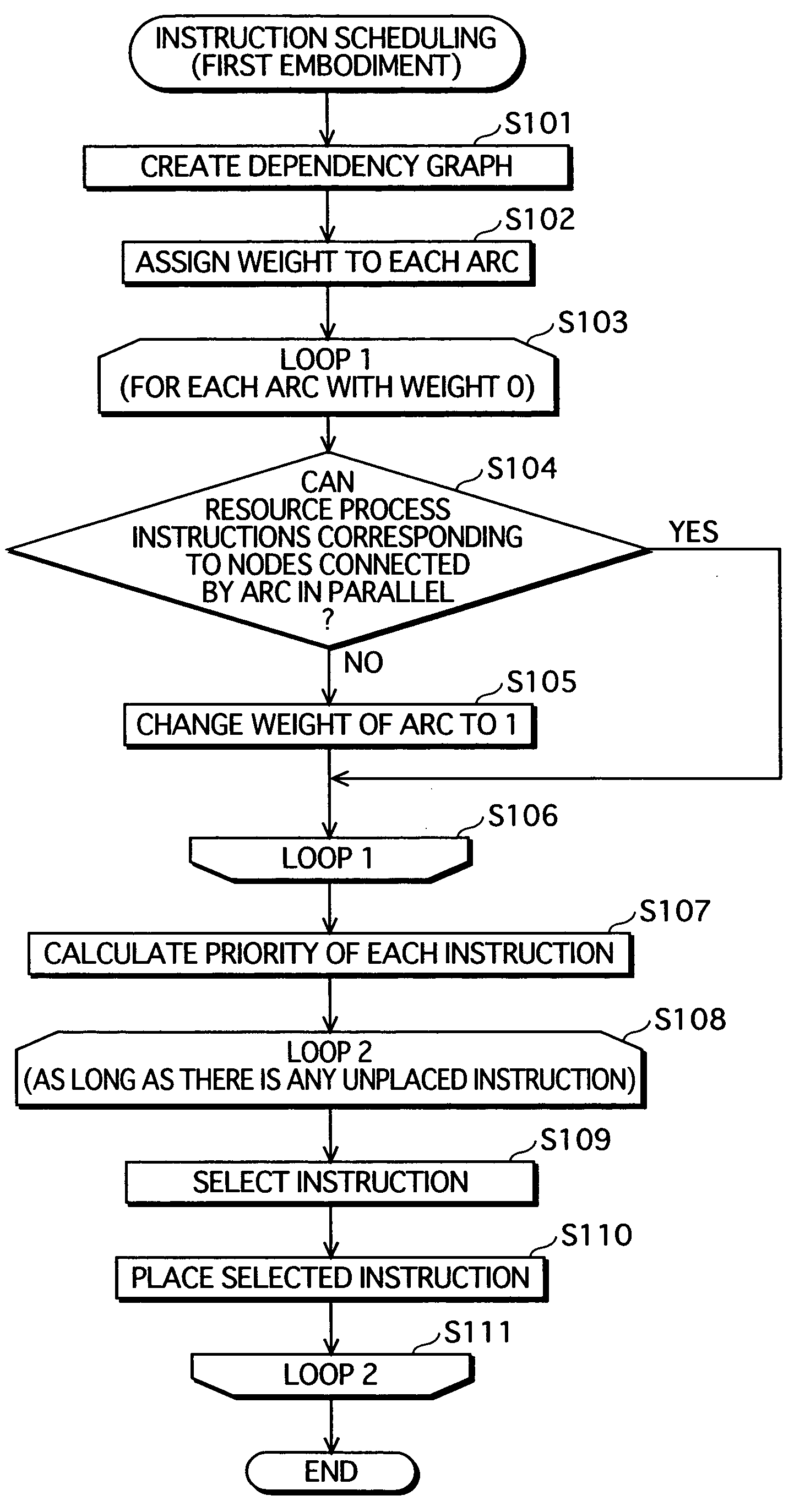
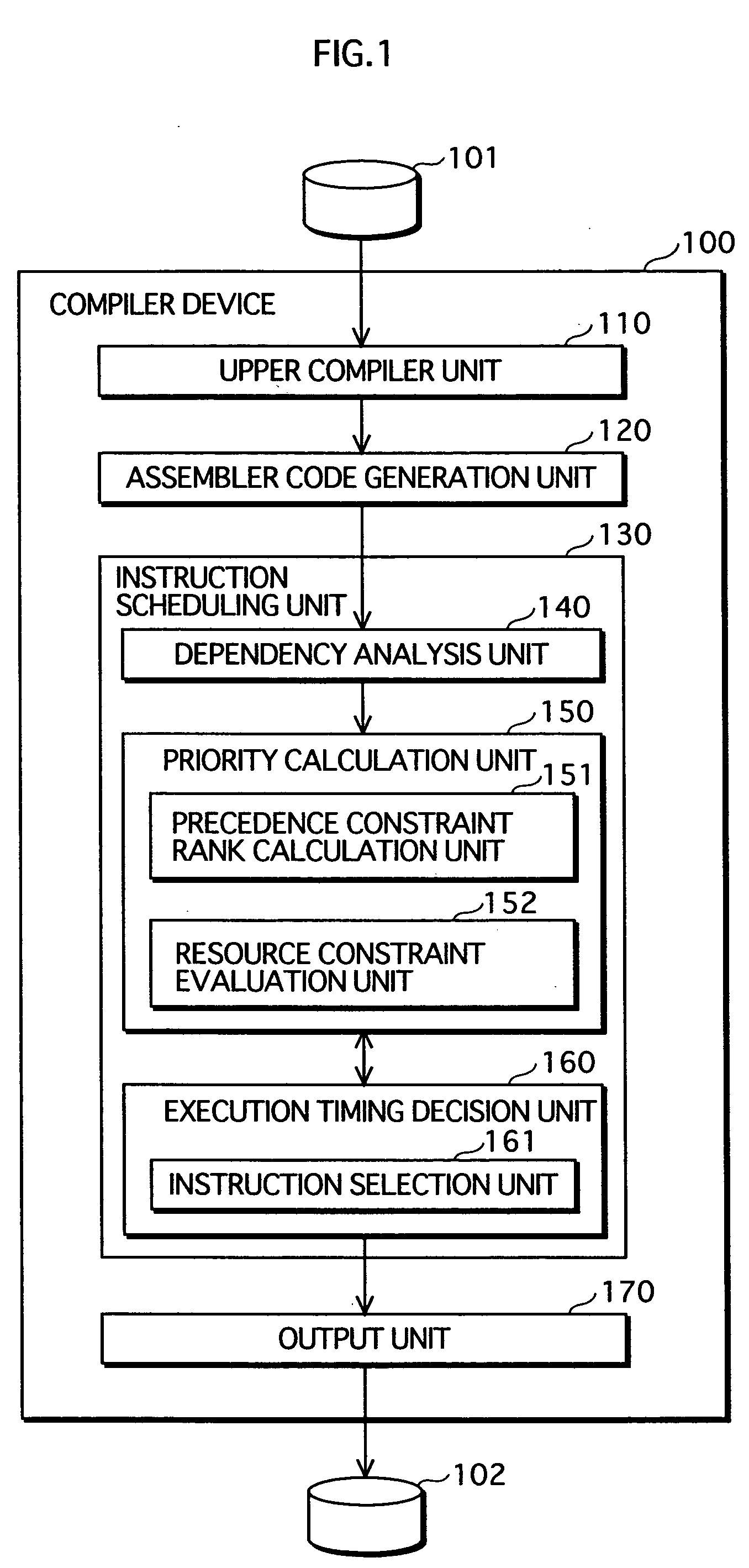
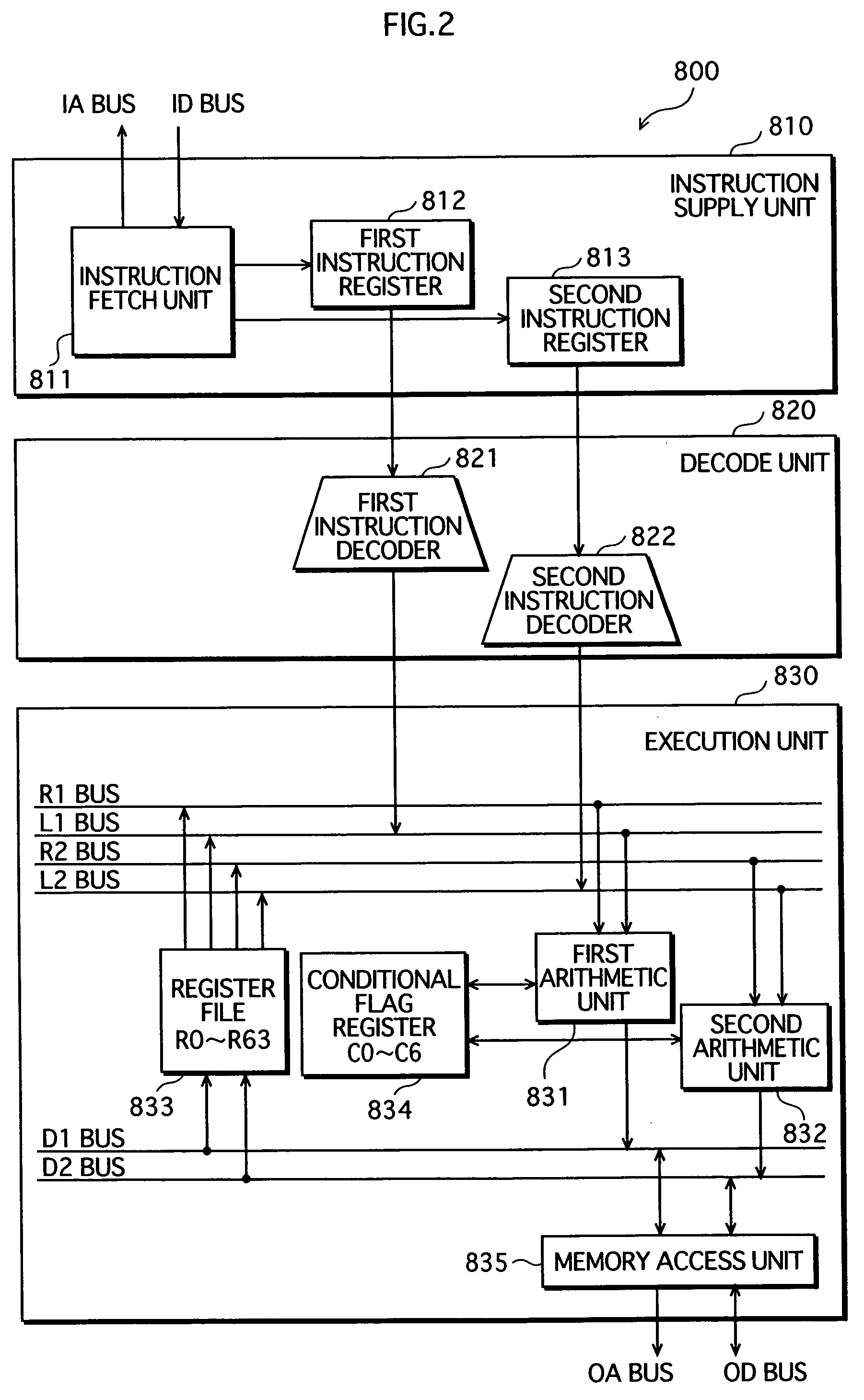
Instruction scheduling method, instruction scheduling device, and instruction scheduling program
InactiveUS20040083468A1Software engineeringProgram controlScheduling instructionsParallel processing
A dependency analysis unit creates a dependency graph showing dependencies between instructions acquired from an assembler code generation unit. A precedence constraint rank calculation unit assigns predetermined weights to arcs in the graph, and adds up weights to calculate a precedence constraint rank of each instruction. When a predecessor and a successor having a dependency and an equal precedence constraint rank cannot be processed in parallel due to a resource constraint, a resource constraint evaluation unit raises the precedence constraint rank of the predecessor. A priority calculation unit sets the raised precedence constraint rank as a priority of the predecessor. An instruction selection unit selects an instruction having a highest priority. An execution timing decision unit places the selected instruction in a clock cycle. The selection by the instruction selection unit and the placement by the execution timing decision unit are repeated until all instructions are placed in clock cycles.
Owner:PANASONIC CORP
System and method for computer-aided graph-based dependency analysis
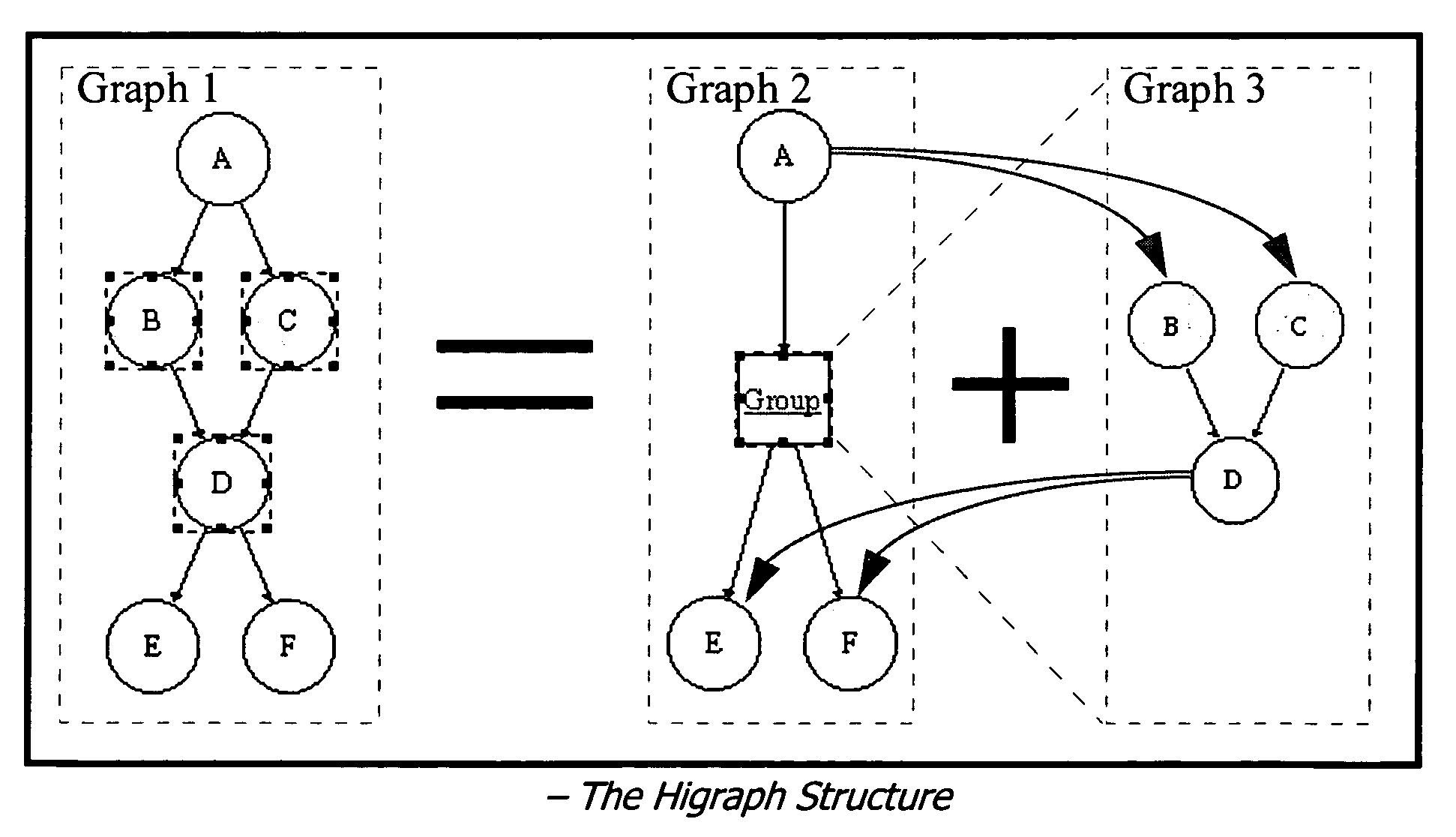
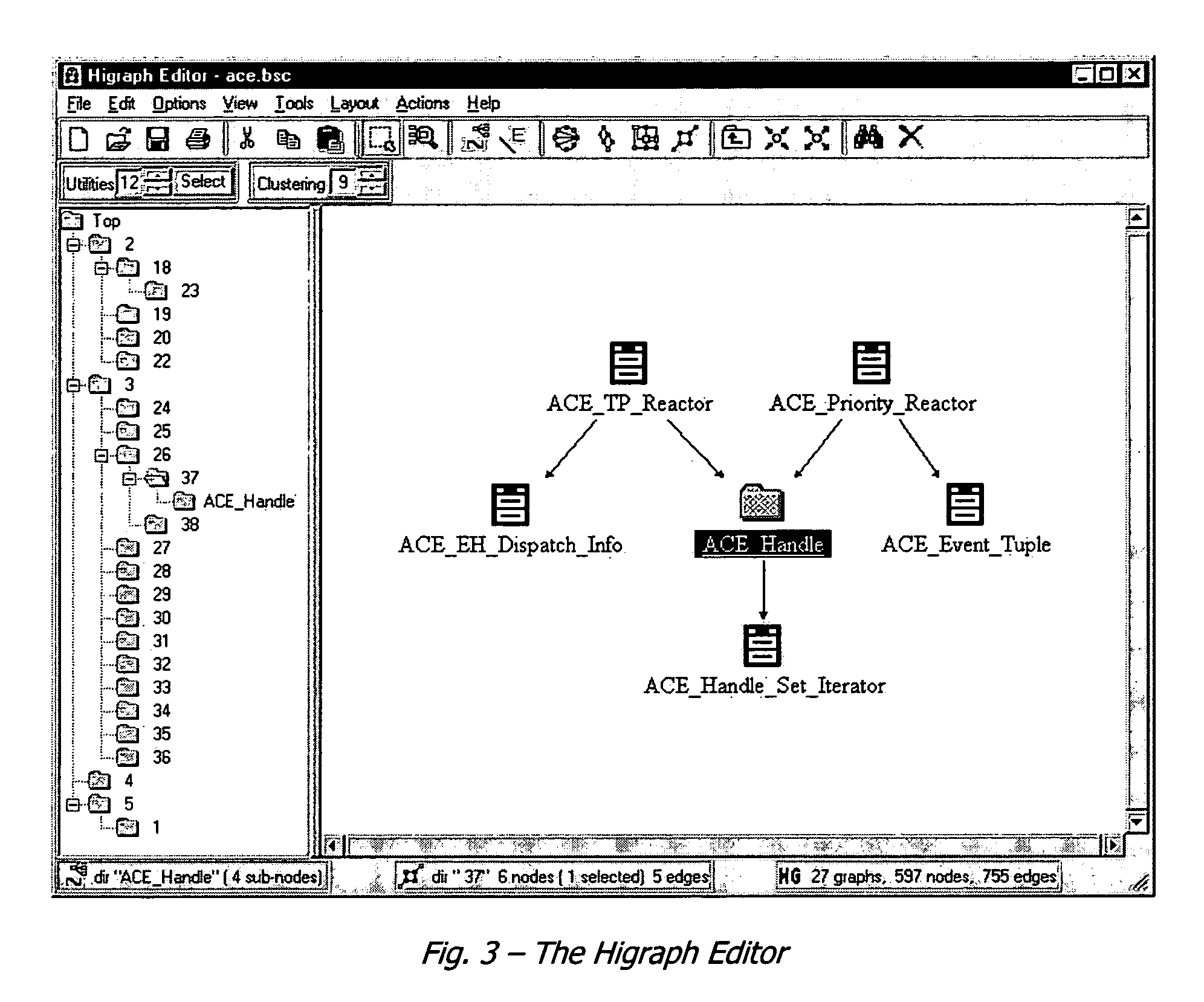
The present invention is directed to a system and methods for analyzing dependencies. The dependencies that may be analyzed include, for example, dependencies among methods or procedures in software source code, or in system configuration or deployment. A layered system is provided, comprising a back-end layer, abstraction layer and user interface layer are used to derive dependency information from third-party tools, and present the information through uniform interfaces to a user-interface layer. The system maintains a dependency model as a hierarchical graph structure in computer memory, and provides a plurality of user views which may be manipulated actively or passively by the user. Active manipulations are propogated through the back-end layer to modify the system analyzed, and passive manipulations affect the user views without changing the analyzed system. The system provides advantages to users seeking to understand complex systems with many dependencies.
Owner:HEADWAY RES
Iterative software development environment with prioritized build rules
ActiveUS20030163799A1Version controlSpecific program execution arrangementsSoftware developmentBuilt environment
An iterative software development environment is provided to perform modified dependency analyses for use in building a target file and all the files on which it depends from one or more source files using a set of prioritized build rules. In one embodiment, the build rules indicate how different types of target files can be generated from different source file types. A given target file type may be associated with several rules, each having a different priority, for building the target from different source file types. In one embodiment, if more than one source file exists that can be used to generate a given target file, the rule with the highest priority is used. In one embodiment, the build environment identifies how to generate a particular target file by identifying the highest priority rule for which an associated source file type exists. Moreover, the development environment identifies the presence of a new source file having a corresponding build rule with a higher priority than that of the source file type(s) previously used in the generation of the target file. In one embodiment of the invention, the target file is rebuilt if such a new source file is identified, or if one or more source files previously used to build the target file are determined to have been modified more recently than that indicated by the build date / time of the target file itself.
Owner:ORACLE INT CORP
Compiler method for extracting and accelerator template program
InactiveUS7926046B2Software engineeringSpecific program execution arrangementsArray data structureSemantic translation
This invention describes a compilation method of extracting and implementing an accelerator control program from an application source code in a processor based system. The application source code comprises arrays and loops. The input application source code is sequential, with loop, branch and call control structures, while the generated output of this invention has parallel execution semantics. The compilation method comprises the step of performing loop nest analysis, transformations and backend processes. The step of loop nest analysis consists of dependence analysis and pointer analysis. Dependence analysis determines the conflicts between the various references to arrays in the loop, and pointer analysis determines if two pointer references in a loop are in conflict. Transformations convert the loops from their original sequential execution semantics to parallel execution semantics. The back-end process determines the parameters and memory map of the accelerator and the hardware dependent software.
Owner:POSEIDON DESIGN SYST
Management of composite software services
InactiveUS20080168424A1TransmissionSpecific program execution arrangementsData processing systemTemplate based
A computer implemented method, data processing system, computer usable program code, and active repository are provided for management of a software service. A request is received to deploy the software service in a computer network. A dependency analysis is performed for the requested software service to determine component software services and physical resources necessary to deploy and manage new software service as a composite in responsive to the software service being the new software service. An active object is created to manage the new software service using an active template based on the analysis. The new software service is deployed in the computer network using the active object. The new software service is managed using the active object.
Owner:IBM CORP
System and method for extracting Chinese event trigger words
ActiveCN104331480AImprove performanceNatural language data processingSpecial data processing applicationsFeature extractionEvent trigger
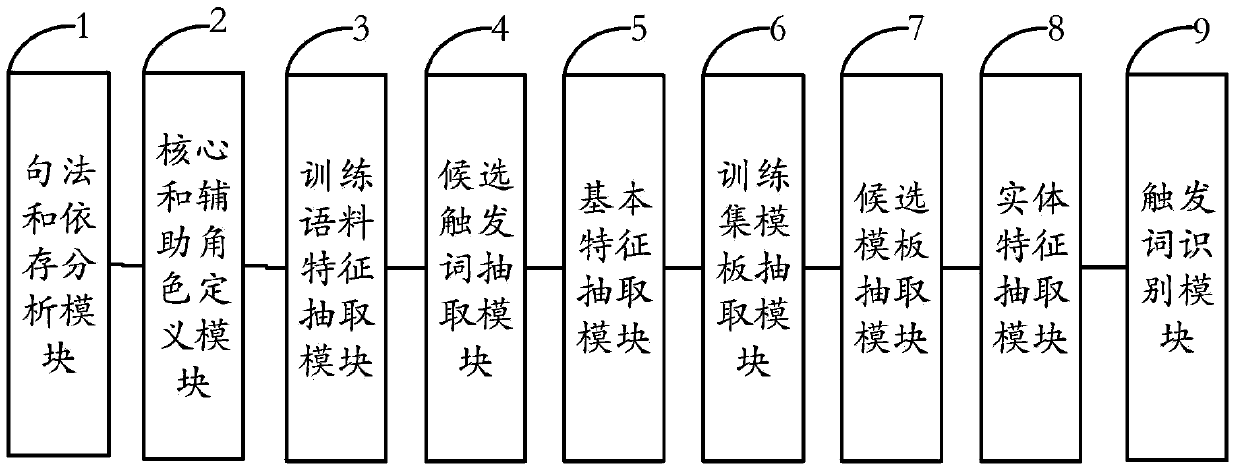
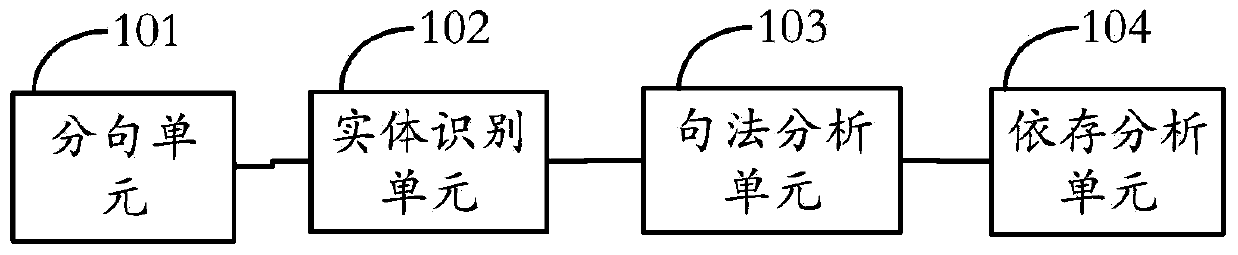
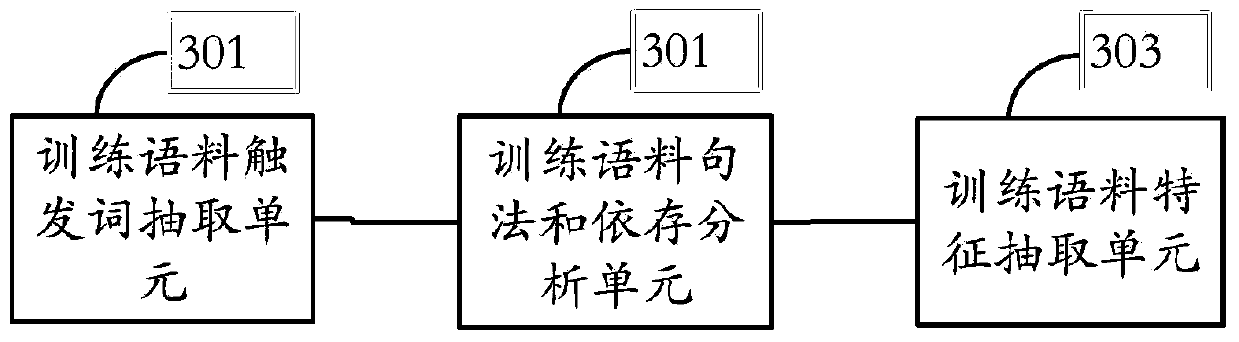
The invention provides a system and a method for extracting Chinese event trigger words. The system comprises a syntax and dependence analysis module, a core and auxiliary role definition module, a training corpus feature extraction module, a candidate trigger word extraction module, a basic feature extraction module, a training set template extraction module, a candidate template extracting module, a solid feature extraction and a trigger word recognition module. According to the fact that a role semantics is one event semantics expression form, the invention provides a method for expressing the role semantics by use of a core role and auxiliary roles, and the method is used for extracting the Chinese event trigger words. Compared with the best existing method and system for extracting a Chinese event, the method provided by the invention has the advantage that the Chinese event trigger word extraction performance is obviously improved.
Owner:SUZHOU UNIV
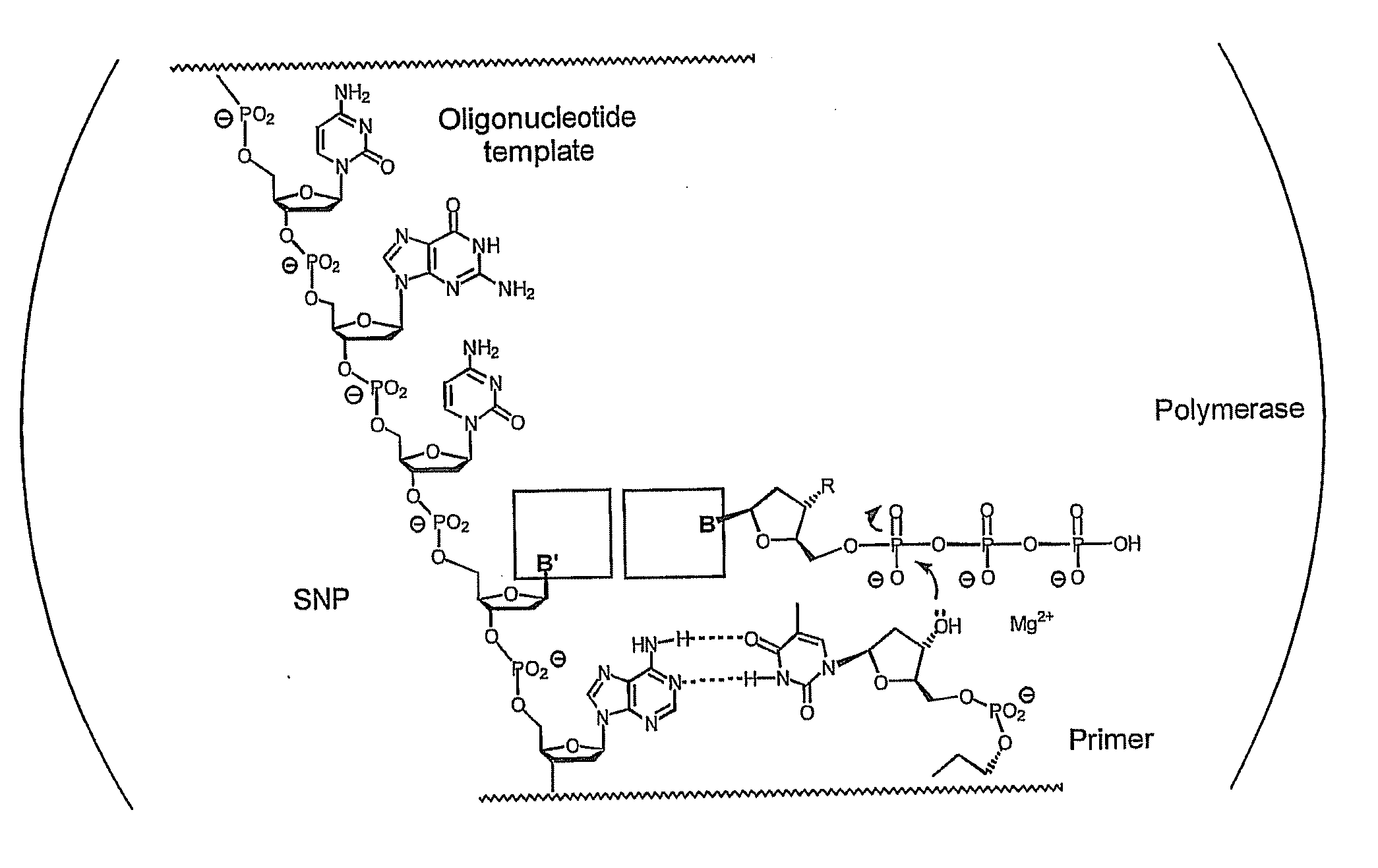
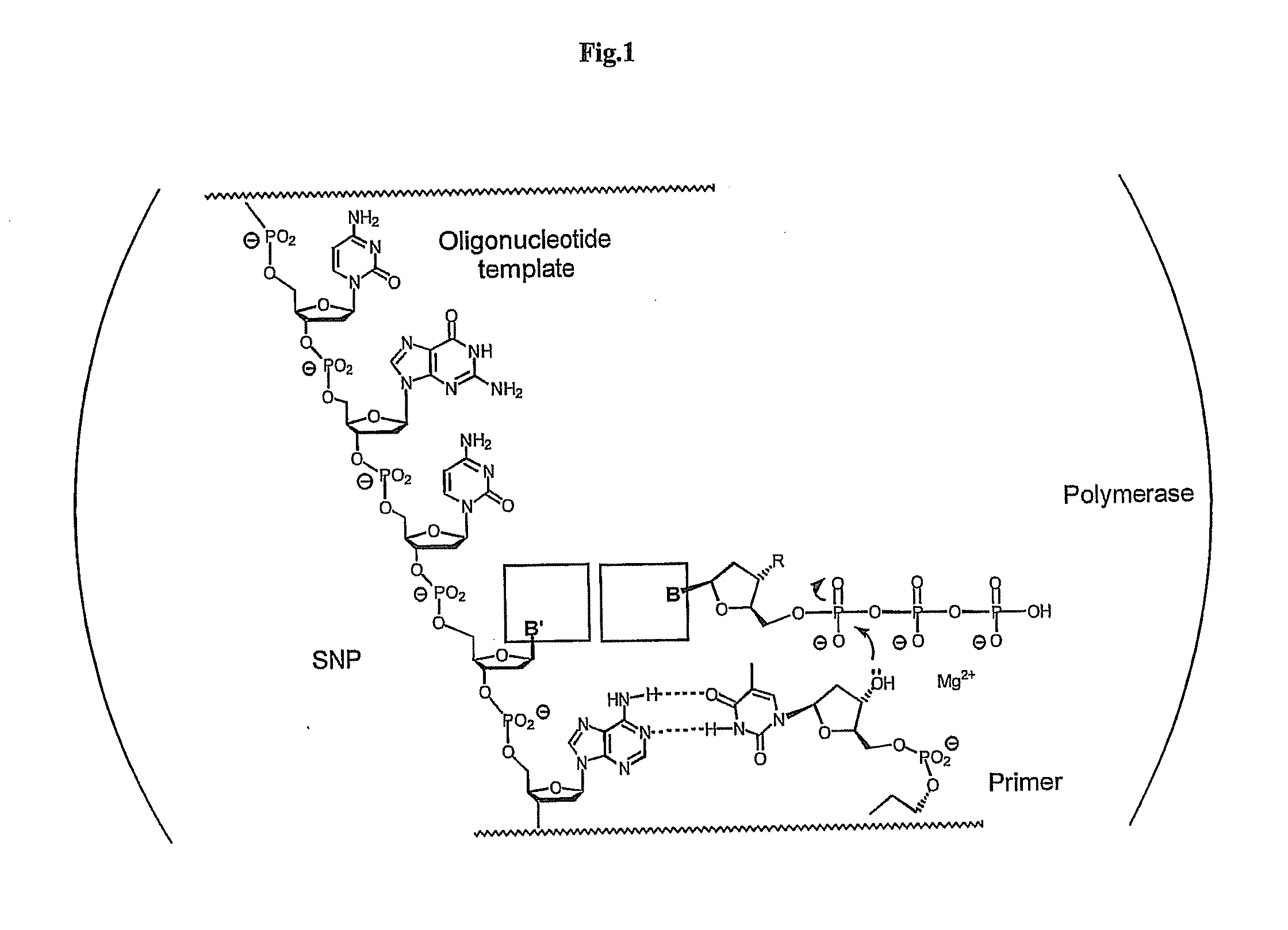
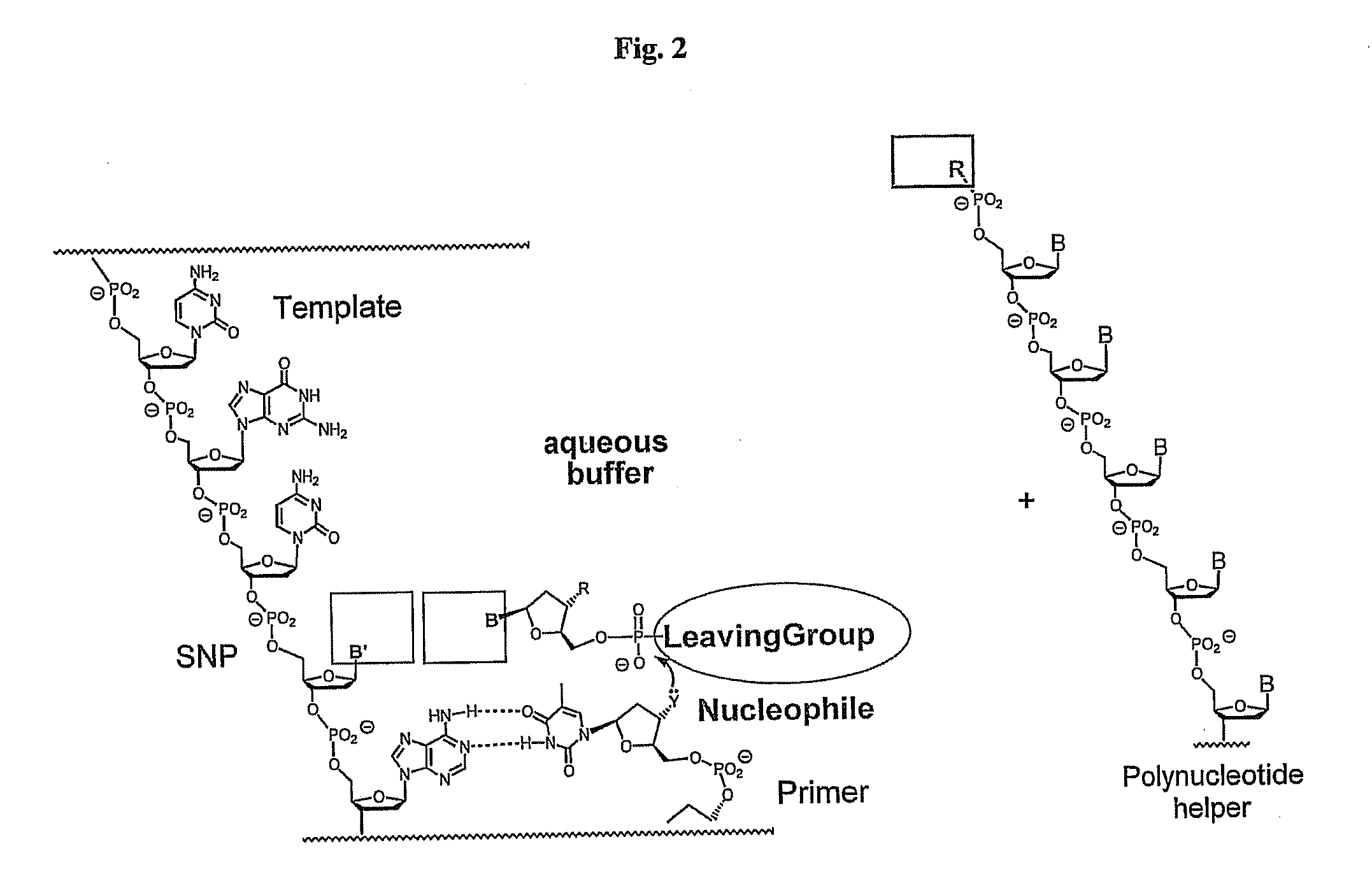
Polymerase-independent analysis of the sequence of polynucleotides
InactiveUS20100029008A1Increase flexibilityQuick analysisSugar derivativesBiological testingNucleotide sequencingPolynucleotide
The present invention concerns methods of polymerase independent template directed elongation of polynucleotides, nucleotide building blocks used in these methods as well as the use of the methods and building blocks for the determination of nucleotide sequences, in particular for the determination of SNPs, base modifications, mutations, rearrangements and methylation patterns.
Owner:FEBIT HOLDING GMBH
Data warehouse data model adapters
InactiveUS20120054249A1Digital data processing detailsMulti-dimensional databasesGraphicsData warehouse
In the context of data administration in enterprises, an effective manner of providing a central data warehouse, particularly via employing a tool that helps by analyzing existing data and reports from different business units. In accordance with at least one embodiment of the invention, such a tool analyzes the data model of an enterprise and proposes alternatives for building a new data warehouse. The tool, in accordance with at least one embodiment of the invention, models the problem of identifying fact / dimension attributes of a warehouse model as a graph cut on a Dependency Analysis Graph (DAG). The DAG is built using existing data models and the report generation scripts. The tool also uses the DAG for generation of ETL (Extract, Transform Load) scripts that can be used to populate the newly proposed data warehouse from data present in the existing schemas.
Owner:IBM CORP
Code homology detection method based on code fingerprint and device thereof
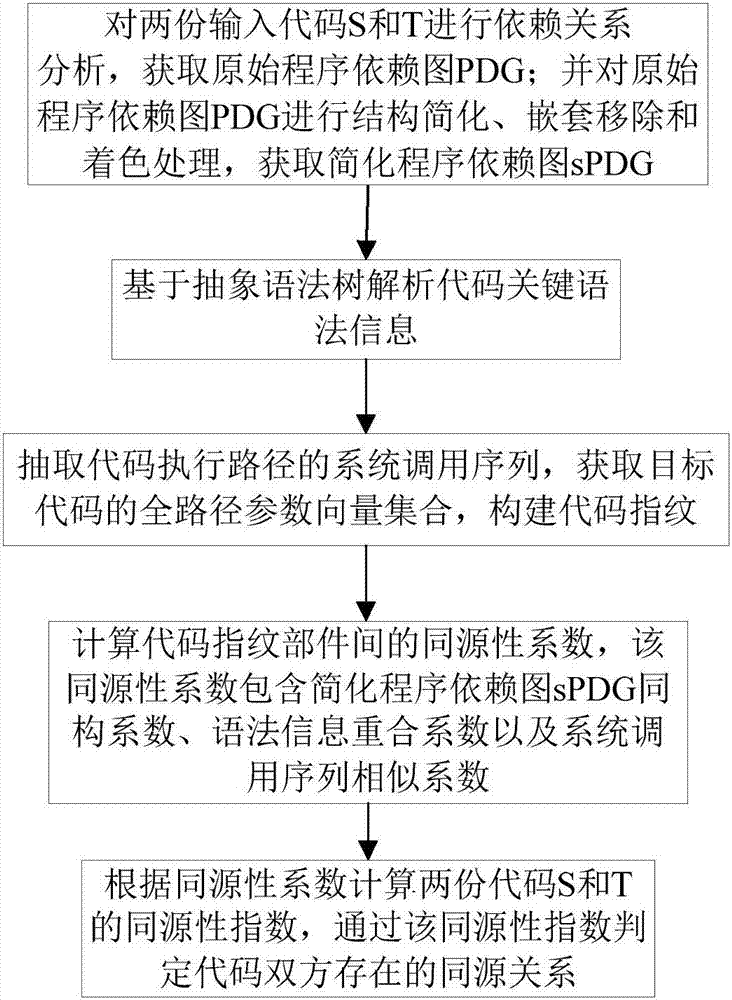
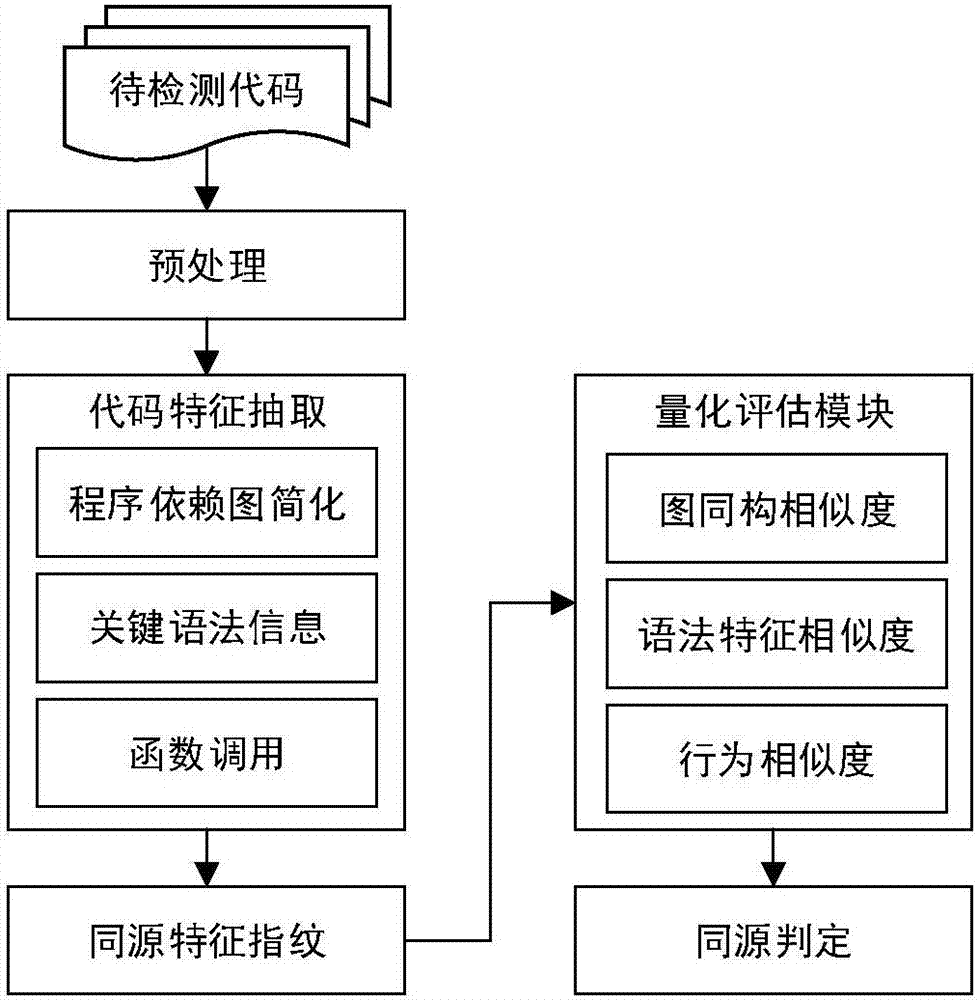
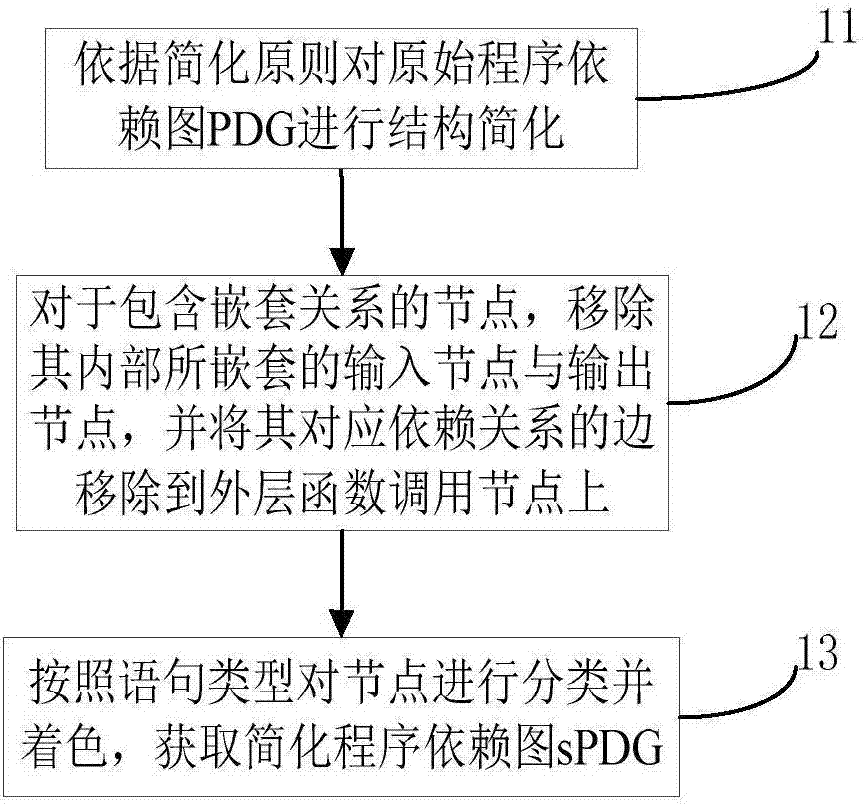
ActiveCN107169358AImprove detection efficiencyImprove accuracyPlatform integrity maintainanceProgram controlObject codeSemantics
The invention relates to a code homology detection method based on code fingerprint and a device thereof. The method comprises: performing dependence analysis on input codes, obtaining an original program dependence graph PDG; performing structure simplification, removing nesting and performing shading on the original program dependence graph PDG, to obtain a simplified program dependence graph sPDG; based on an abstract syntax tree, analyzing code key grammar information; extracting a system call sequence of a code execution path, to obtain a full path parameter vector assembly of an object code, to build code fingerprint; calculating a homology coefficient of code fingerprint components; according to the homology coefficient, calculating a homology index of two codes S and T, and through the homology index, determining a homologous relation exists in the both codes. The method can give consideration to code semantics and behaviors on the basis of similarity, and improves detection efficiency by using a lightweight characteristic and simplified mechanism, and measures homologous relations among codes in a multi-angle manner, and improves detection efficiency while ensuring accuracy.
Owner:THE PLA INFORMATION ENG UNIV +1
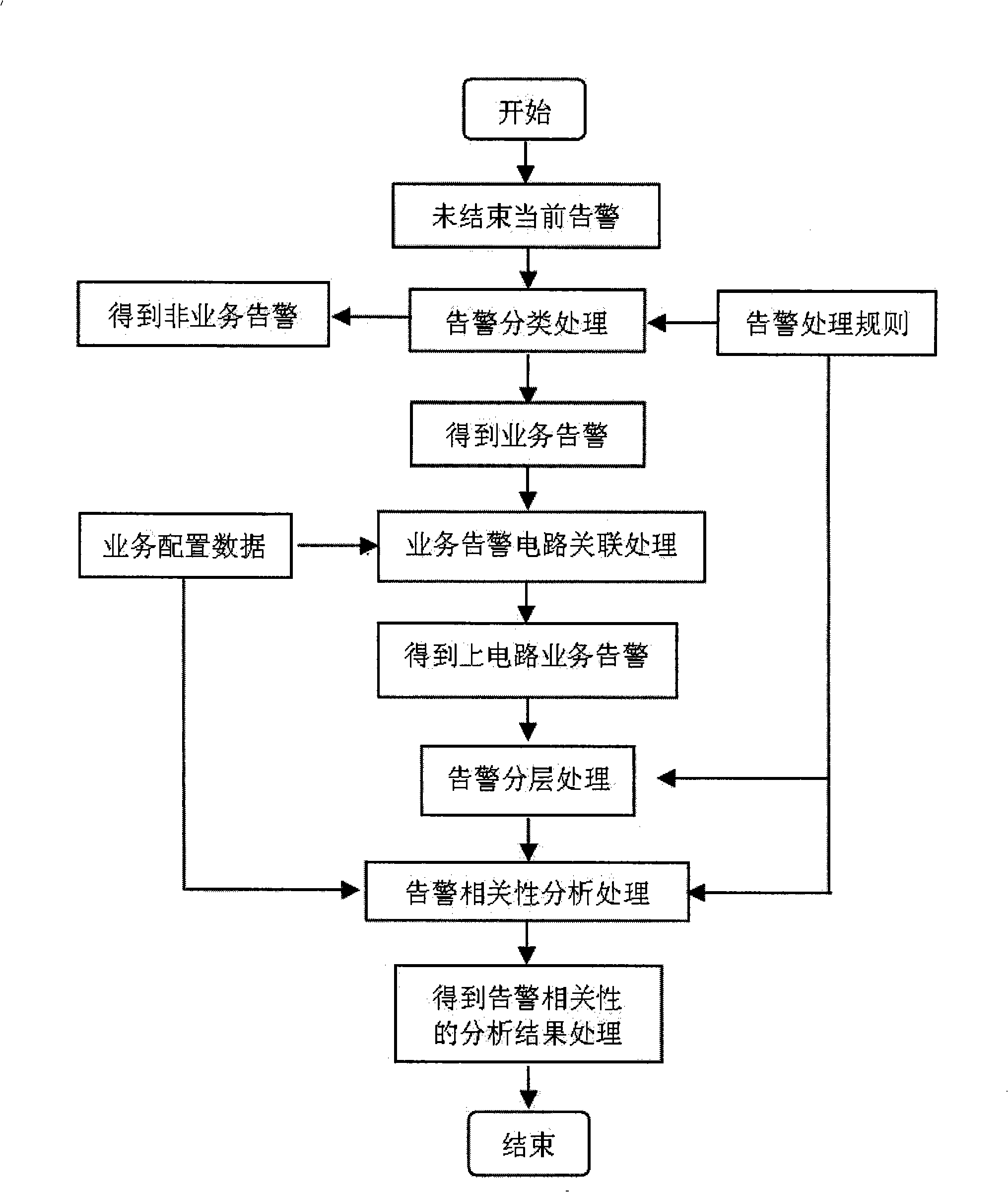
Method and apparatus for SDH equipment alarm correlativity analysis
InactiveCN101335643AImprove execution efficiencyQuick fixTime-division multiplexData switching networksData modelingAnalysis of algorithms
The invention relates to a method which is used for the alarm correlation analysis of SDH equipment, and a device thereof. The method and the device consider the order of severity of SDH business impact caused by different faults in terms of an SDH transmission system, and differentiate a business alarm and a non-business alarm; a reasonable alarm processing rule is provided so as to satisfy the complexity and flexibility of the maintenance of a signal processing by the SDH business alarm; the self-learning processing of an alarm controlling rule is introduced and diversities related to equipment alarm in different periods are compatible; an alarm correlation analysis algorithm works closely with SDH business operation and maintenance experience to lead to the partitioning operation of a algorithm control logic and operational data. High-efficiency date modeling is combined to improve the execution efficiency of an algorithm analysis, thereby being beneficial to the determination of a source alarm fast carried out by a user.
Owner:FENGHUO COMM SCI & TECH CO LTD
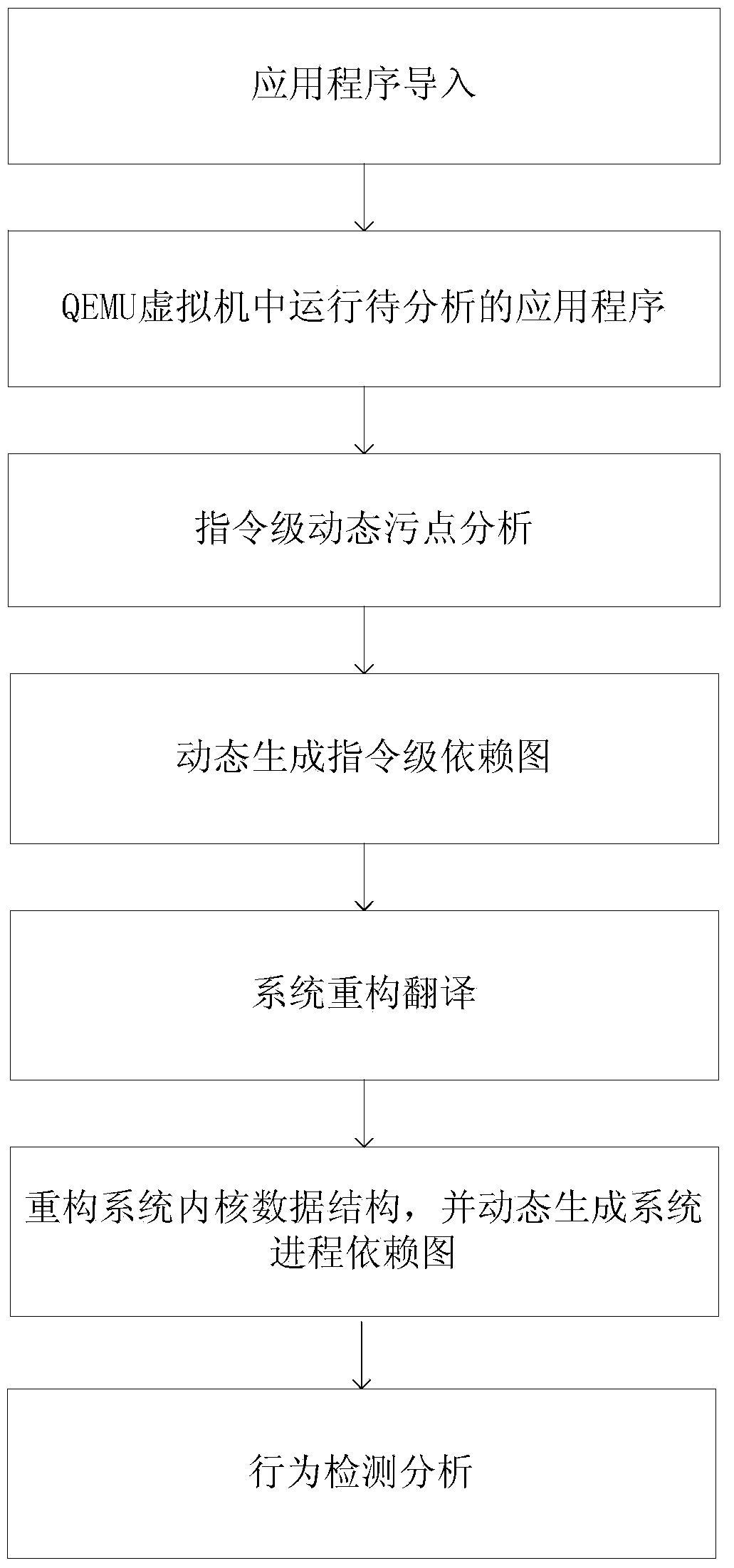
Software privacy leak behavior detection method and system based on virtualization technology
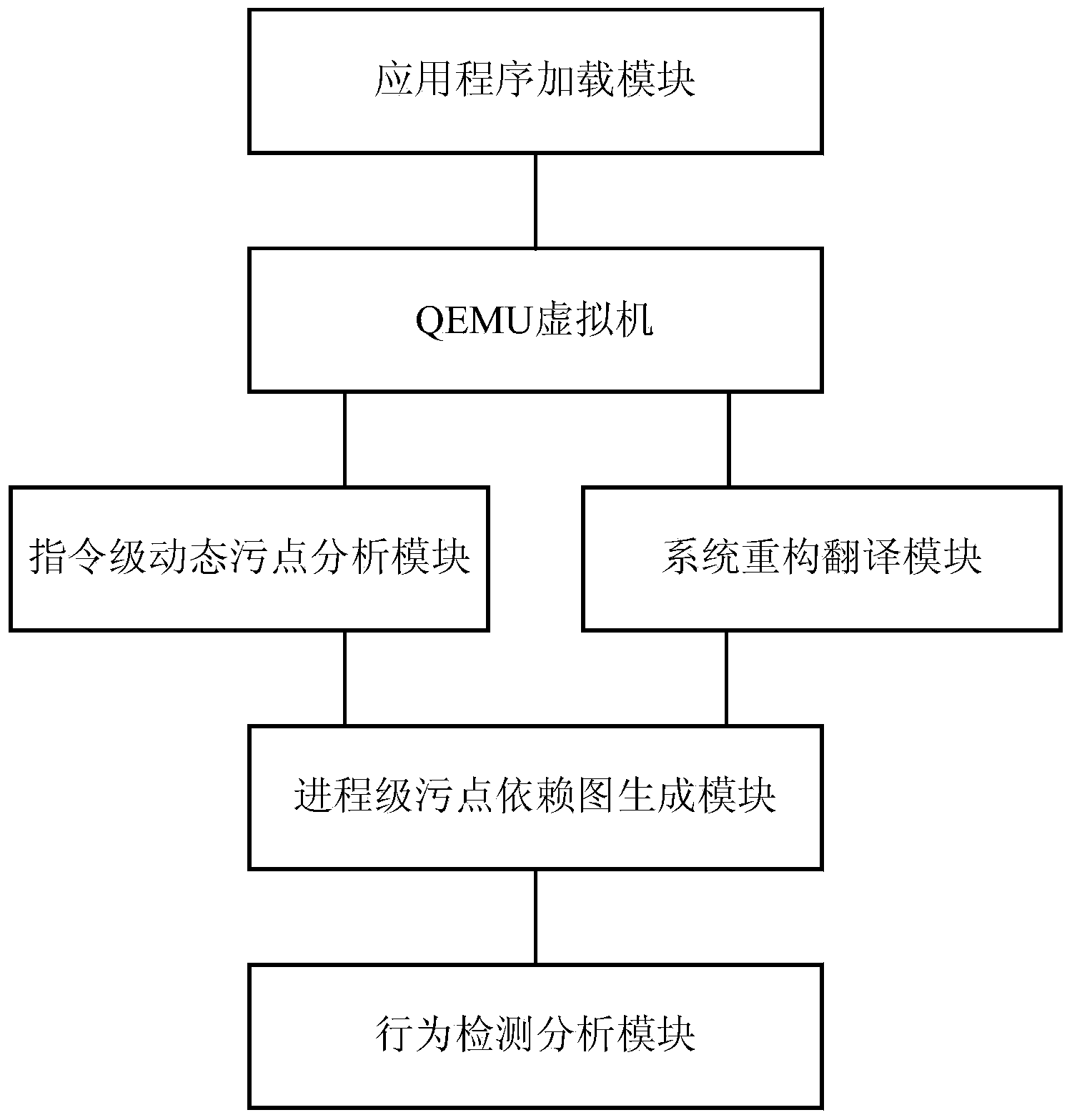
ActiveCN104008329AEfficient analysisEffective detectionPlatform integrity maintainanceVirtualizationInternet privacy
The invention relates to a software privacy leak behavior detection method and system based on the virtualization technology. The software privacy leak behavior detection method includes the steps of loading software to be analyzed into a modified virtual machine for operation; then monitoring execution of instructions in the software operation process, when an application accesses a sensitive resource, signing related taint data, making a related taint propagation rule, on the premise, dynamically generating an instruction-level taint dependence graph, reconstructing translation according to the system, and dynamically generating a system process-level taint dependence graph; analyzing software privacy leak behaviors through a fine-grit taint dependence analysis graph. According to the software privacy leak behavior detection method and system, the fine-grit taint dependence analysis graph is obtained through an instruction-level and process-level combined multi-level dynamic taint analysis method, information of a system pollution path and high-level semantic information such as information leak can be accordingly obtained, and effective analysis and effective detection of the software privacy leak behaviors are achieved.
Owner:INST OF INFORMATION ENG CAS
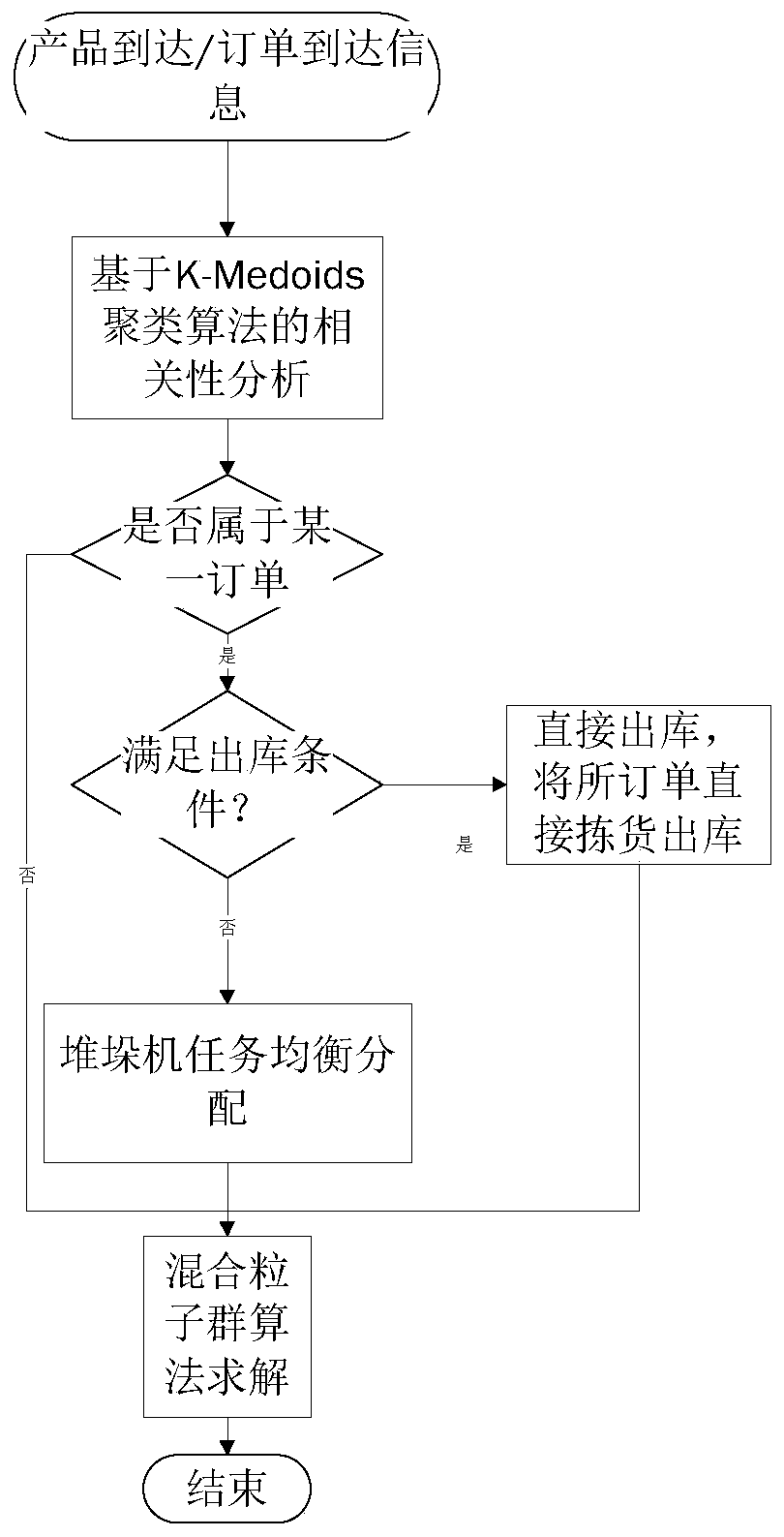
Integrated scheduling method for multi-roadway automatic stereoscopic warehouse based on mixed integer programming model
ActiveCN110084545AReduce complexitySuccessfully Solve Integration Scheduling ProblemsCharacter and pattern recognitionLogisticsOperation schedulingProduct order
The invention discloses an integrated scheduling method for a multi-roadway automatic stereoscopic warehouse based on a mixed integer programming model which comprises the steps that step 1, a tray / order arrives so as to perform step 2; if no tray / order arrives, performing the step 5; step 2, carrying out correlation analysis based on a K-Medoids clustering algorithm on arrived tray products making clustering analysis on arrived tray products, finding class clusters where tray products are located, solving an initial goods allocation range, wherein correlation analysis implementation process based on K-Medoids clustering algorithm is as follows: K-Medoids clustering algorithm is used for carrying out correlation analysis: step3, directly warehousing products ordered the same day and performing the step 6; if not, skipping to the step 4, directly warehousing products ordered the same day; step 4, stacking machine task distribution based on operation balance, step 5: distributing a sorting mode, and step 6: performing goods allocation and operation scheduling distribution; step 7, generating a stacking machine operation list until an optimal solution is not changed, otherwise, repeating the step 5 -step 7.
Owner:ZHEJIANG UNIV OF TECH
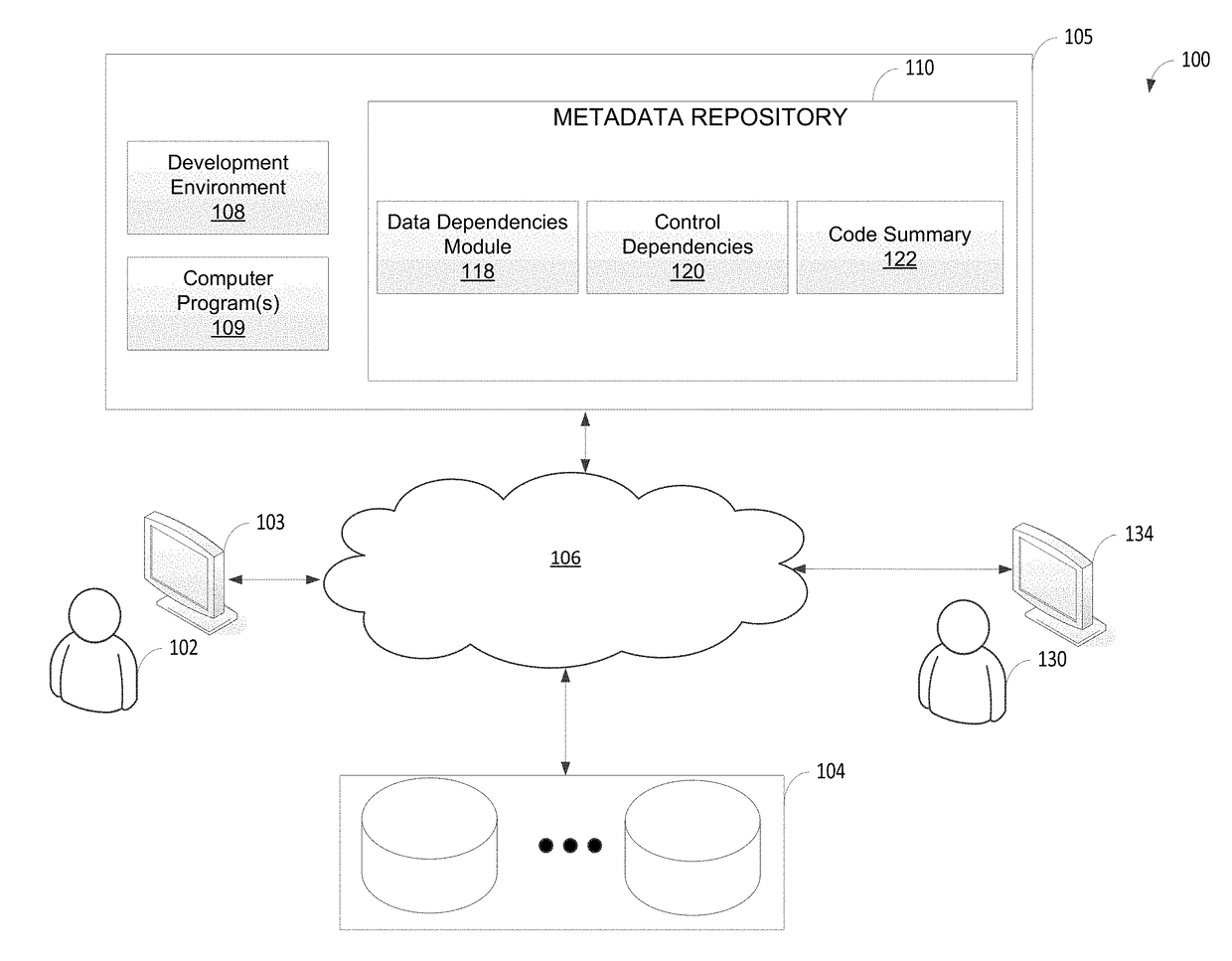
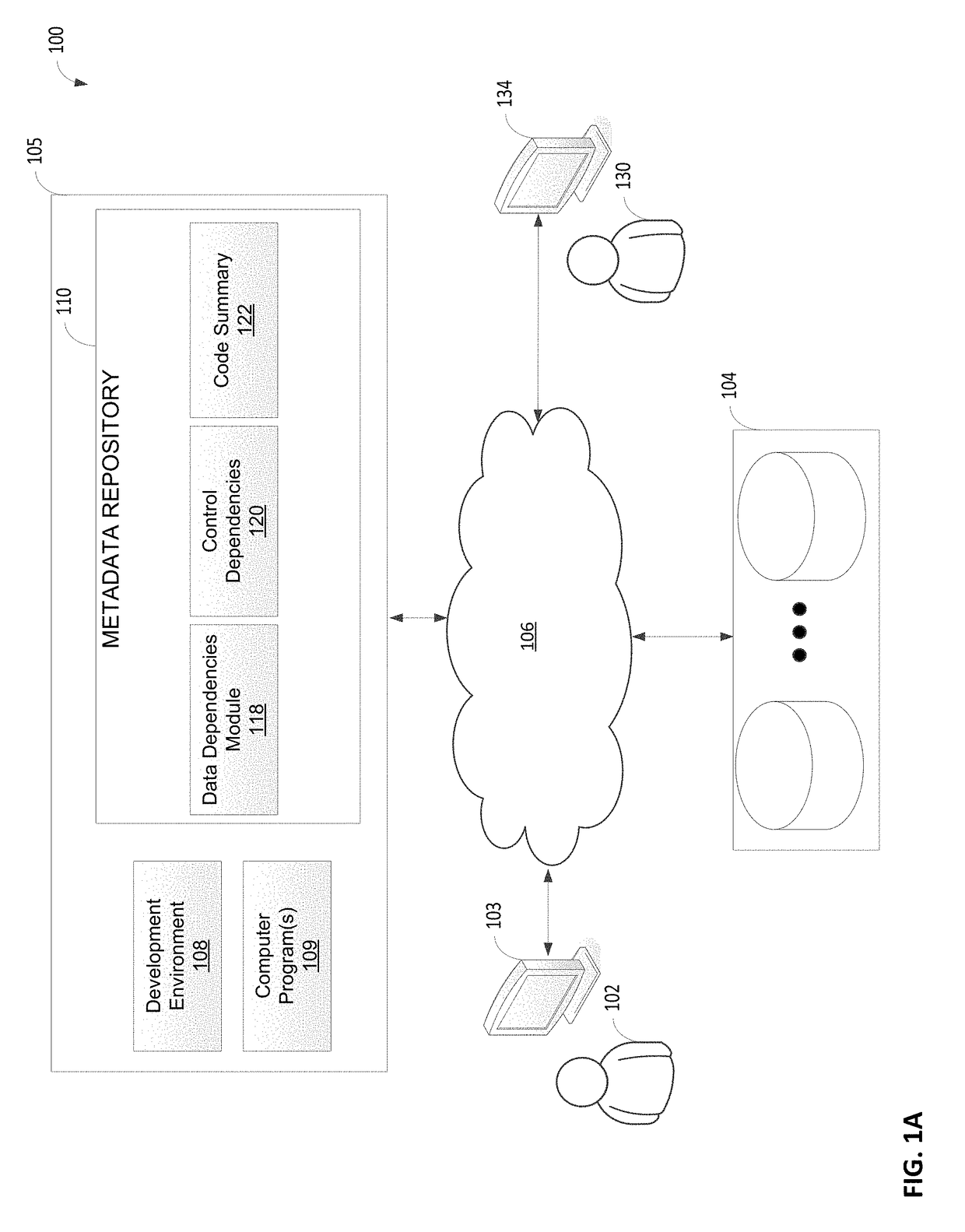
Automated dependency analyzer for heterogeneously programmed data processing system
ActiveUS20180336020A1Digital data information retrievalSoftware engineeringData processing systemChange control
A dependency analyzer for a data processing system comprising at least one computer hardware processor configured to generate dependency information among variables, which may appear in any of multiple programs written in different source languages. The data processing system may parse each program, regardless of the language in which the module was written. Parsed information about each program may be recorded in a first-type data structure and then may be converted to a format representing dependencies among variables. Dependency information for each of the plurality of programs may be expressed as a combination of language independent constructs, which may be processed together, to generate dependency information for the data processing system. The dependency information may be recorded in a dependency data structure and further used for operations, such as data quality checking and change control for the data processing program.
Owner:INITIO TECH
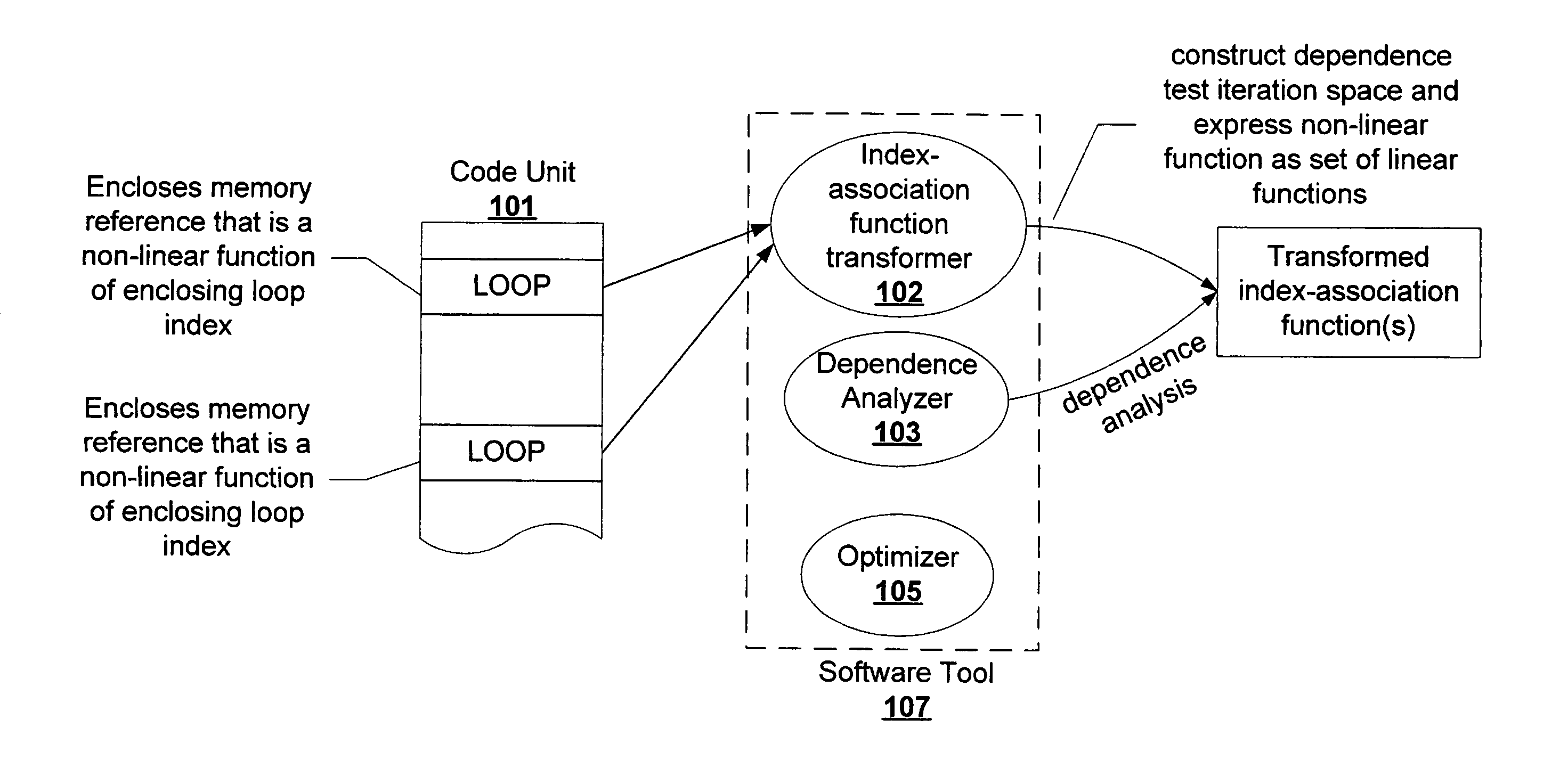
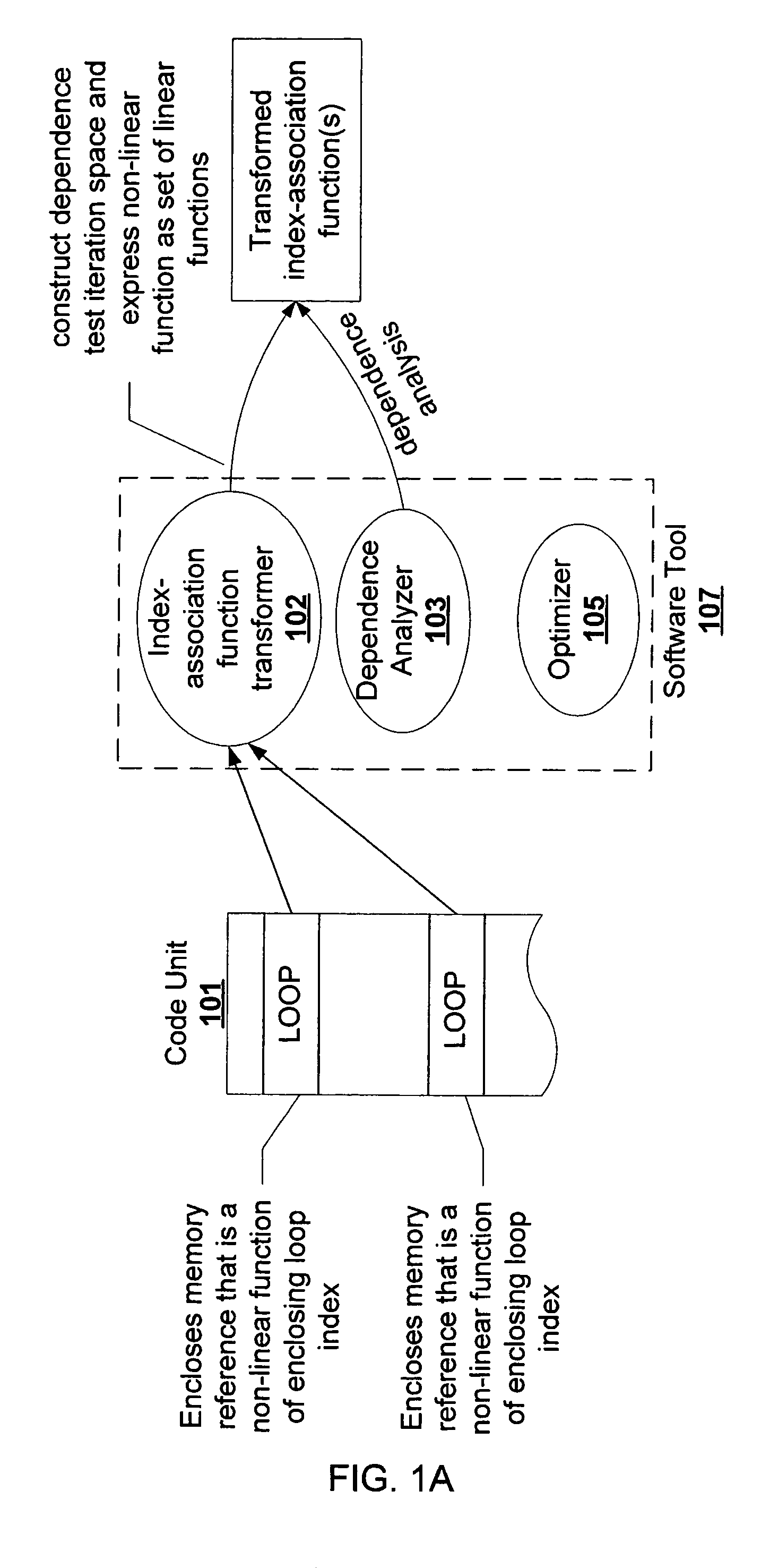
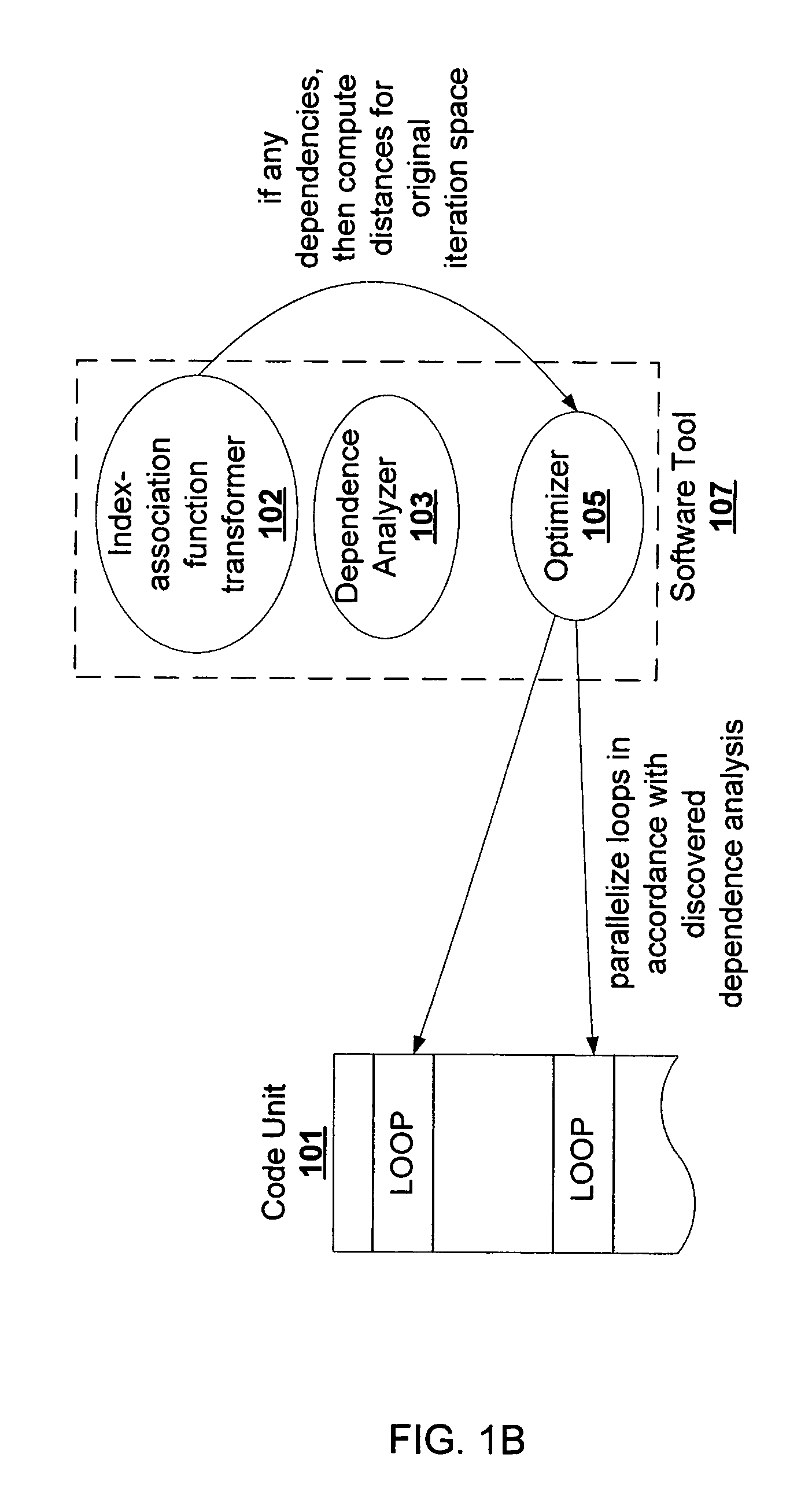
Dependency analysis system and method
We present a technique to perform dependence analysis on more complex array subscripts than the linear form of the enclosing loop indices. For such complex array subscripts, we decouple the original iteration space and the dependence test iteration space and link them through index-association functions. The dependence analysis is performed in the dependence test iteration space to determine whether the dependence exists in the original iteration space. The dependence distance in the original iteration space is determined by the distance in the dependence test iteration space and the property of index-association functions. For certain non-linear expressions, we show how to transform it to a set of linear expressions equivalently. The latter can be used in dependence test with traditional techniques. We also show how our advanced dependence analysis technique can help parallelize some otherwise hard-to-parallelize loops.
Owner:ORACLE INT CORP
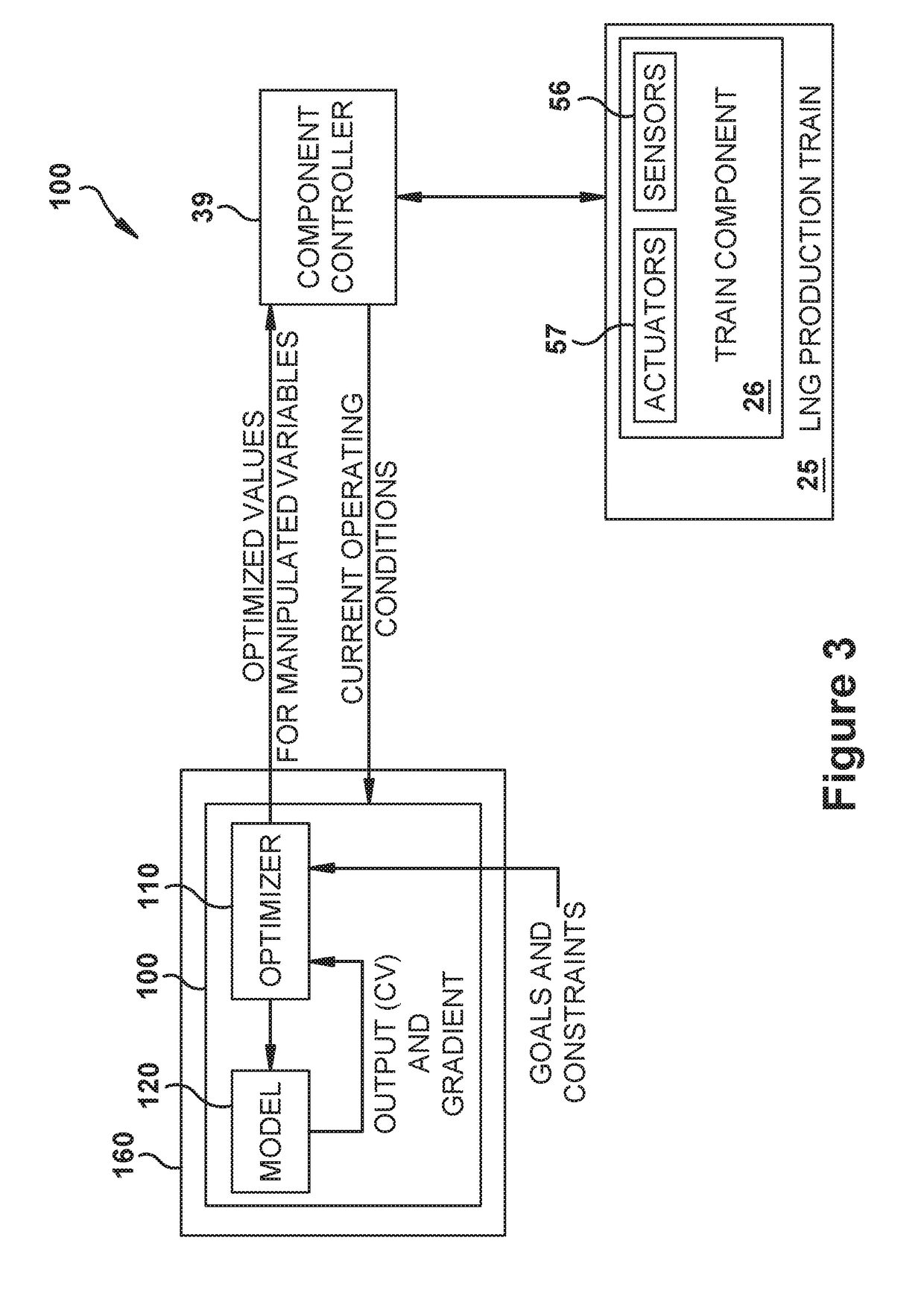
Methods and systems for enhancing production of liquefied natural gas
ActiveUS20180356151A1Improve performanceProgramme controlSolidificationIntegrated monitoringEvent data
A method for enhancing a LNG production train that includes connected train components. The method may include steps of: constructing an integrated surveillance system for monitoring operation of the train components; using the integrated surveillance system to measure and record operational data and event data related to, respectively, the operation and a failure event of the train components over a historical operating period; performing a correlation analysis that calculates a correlation between the occurrences of the failure event and the operational data; given results of the correlation analysis, deriving a prognostic rule that indicates a likelihood of the failure event occurring based on values of the operating parameters of the operational data; applying the prognostic rule to current values of the operating parameters and determining therefrom the likelihood of the failure event occurring; determining an advisory related to the determined likelihood of the failure event occurring; and issuing the advisory.
Owner:GENERAL ELECTRIC CO
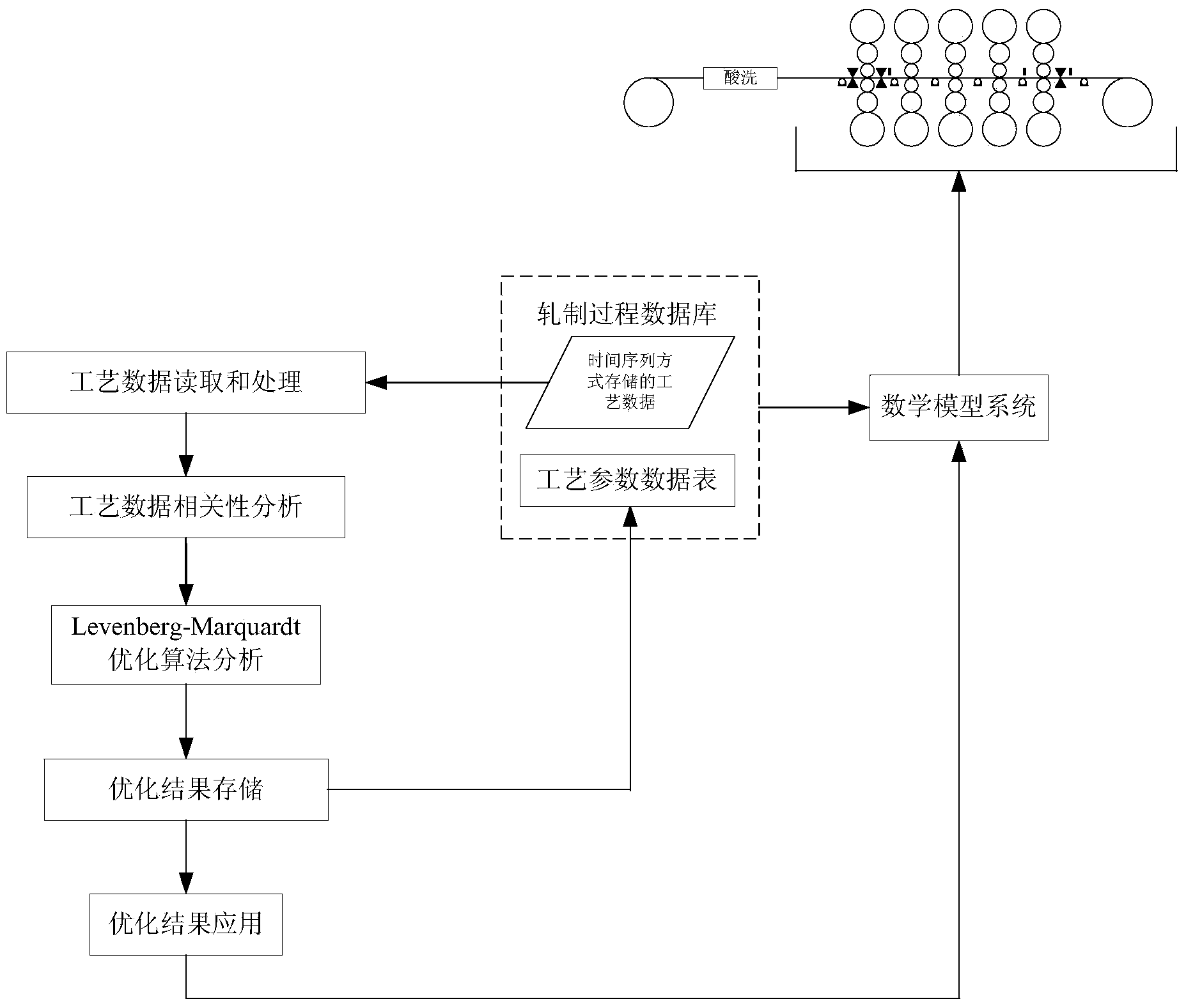
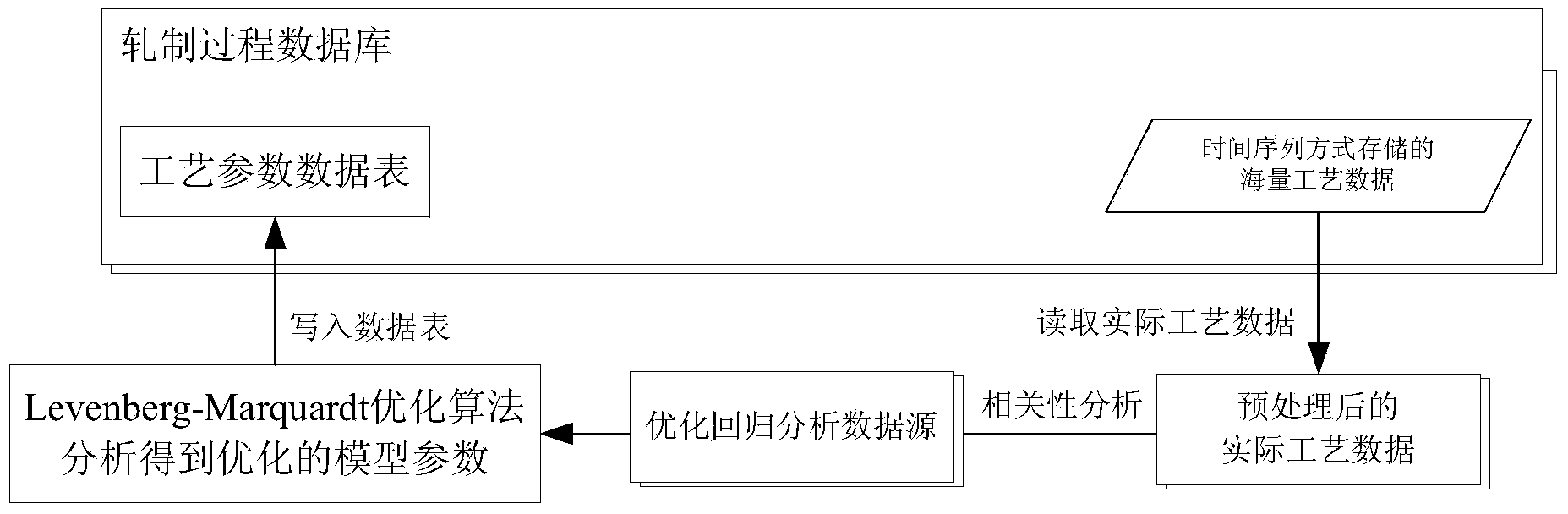
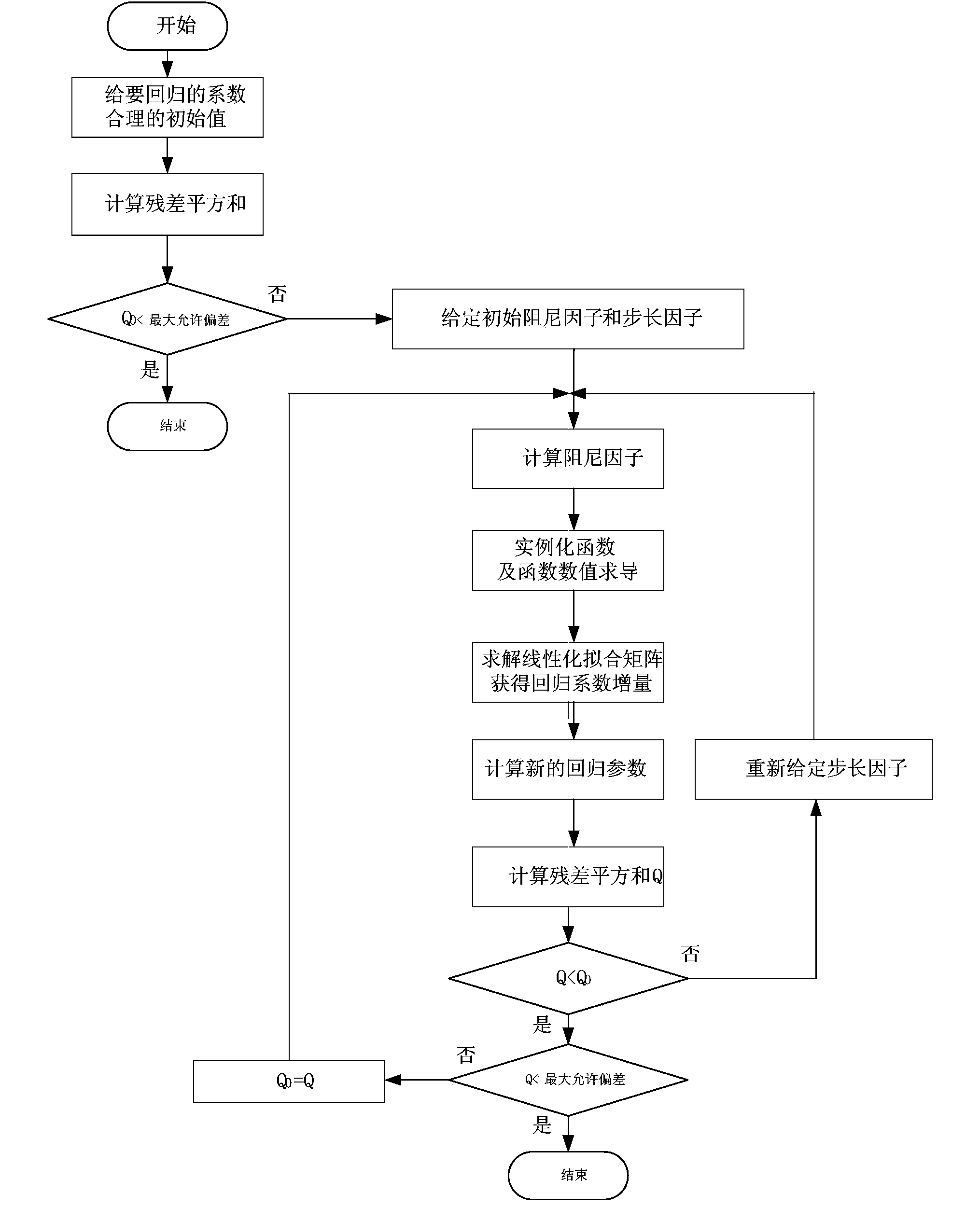
Friction coefficient model optimizing system and method in rolling process
ActiveCN103722022AImprove execution efficiencySuperiorRoll mill control devicesMetal rolling arrangementsMathematical modelData dependency analysis
The invention discloses a friction coefficient model optimizing system and method in the rolling process, and belongs to the technical field of control mathematical models in the rolling process. The Levenberg-Marquardt optimization algorithm is adopted to optimize friction coefficient model parameters in the rolling process. The friction coefficient model optimizing system is characterized by comprising a rolling process database, a rolling process technological parameter data sheet and following function modules which are a technological data reading and processing module, a technological data dependency analysis module, a Levenberg-Marquardt optimization algorithm analysis module, an optimization result storage module and an optimization result application module. The friction coefficient model optimizing system has the advantages that on the premise that key technological parameters are fully considered, the method can effectively process redundant parameters, actual rolling parameters on the site are utilized for directly conducting regression optimization on parameters of a nonlinear polynomial rolling process friction coefficient model, the linear processing process is prevented from being carried out on the complex friction coefficient model, the actual rolling situation on the site can be better reflected, friction coefficient setting computational accuracy is improved, the requirement for high-accuracy rolling is met, and therefore the product quality and yield are improved.
Owner:BEIJING SHOUGANG AUTOMATION INFORMATION TECH
Download server and method for installing and updating application program using partitioning of shared library
InactiveUS20100017503A1Reduce download trafficSave memory spaceVersion controlMultiple digital computer combinationsObject codeApplication software
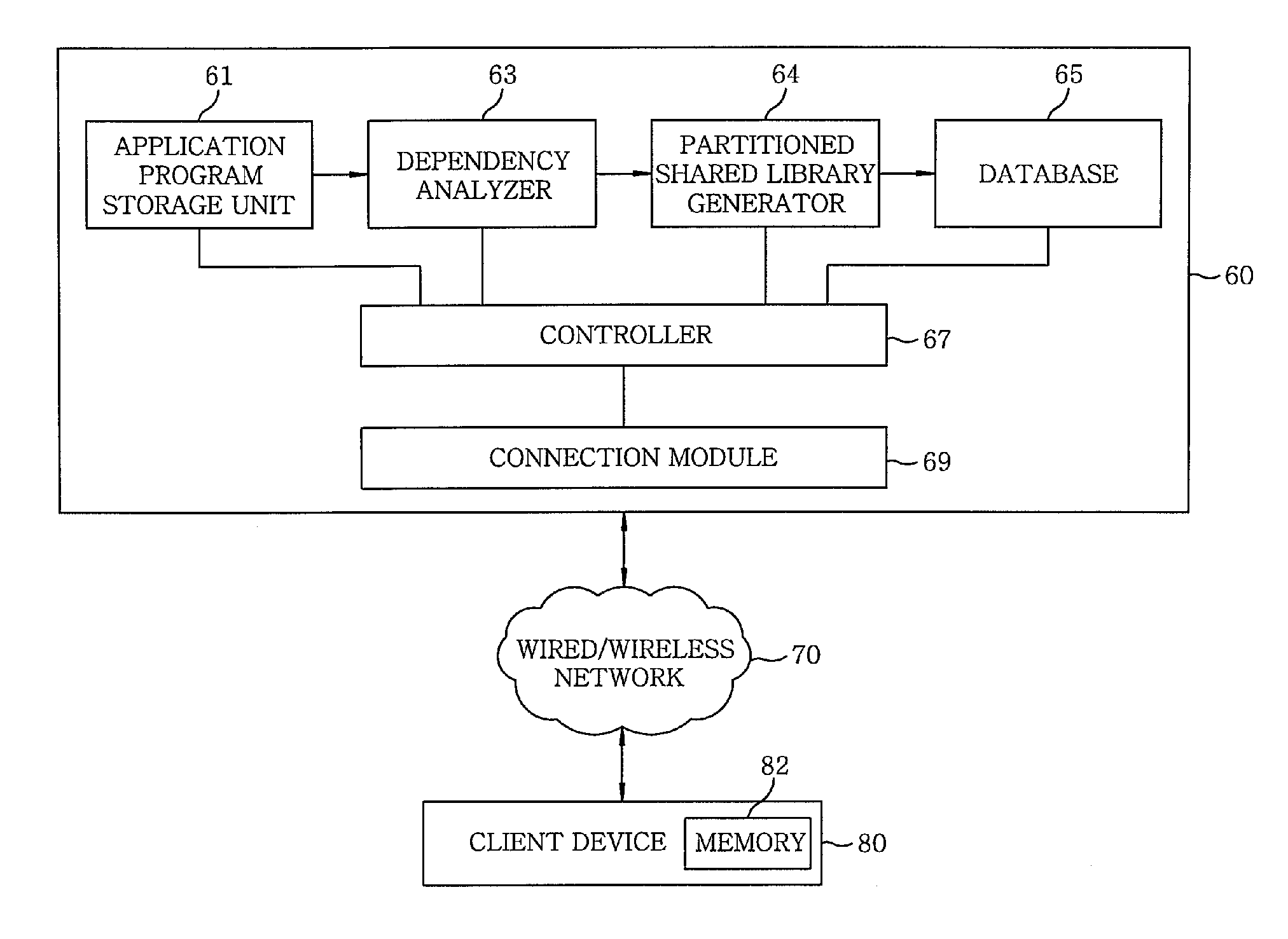
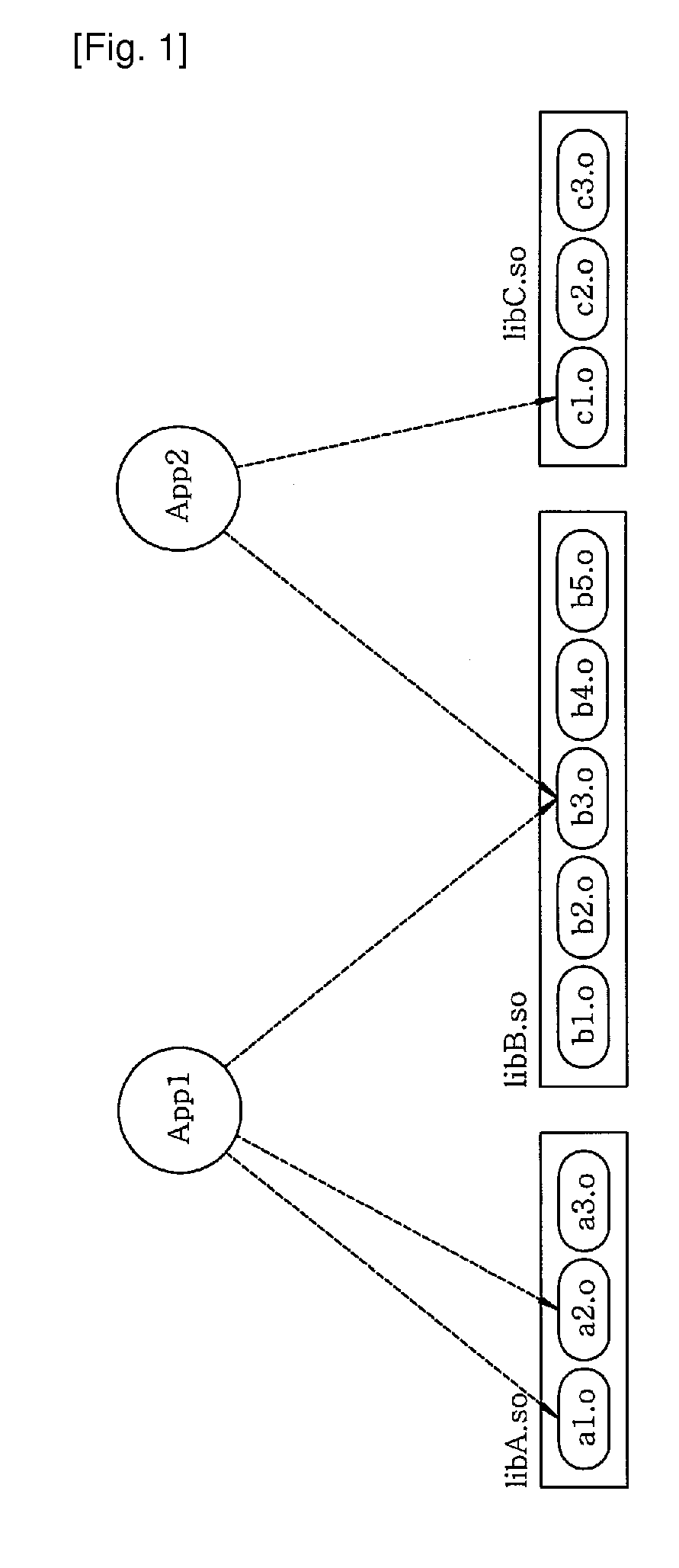
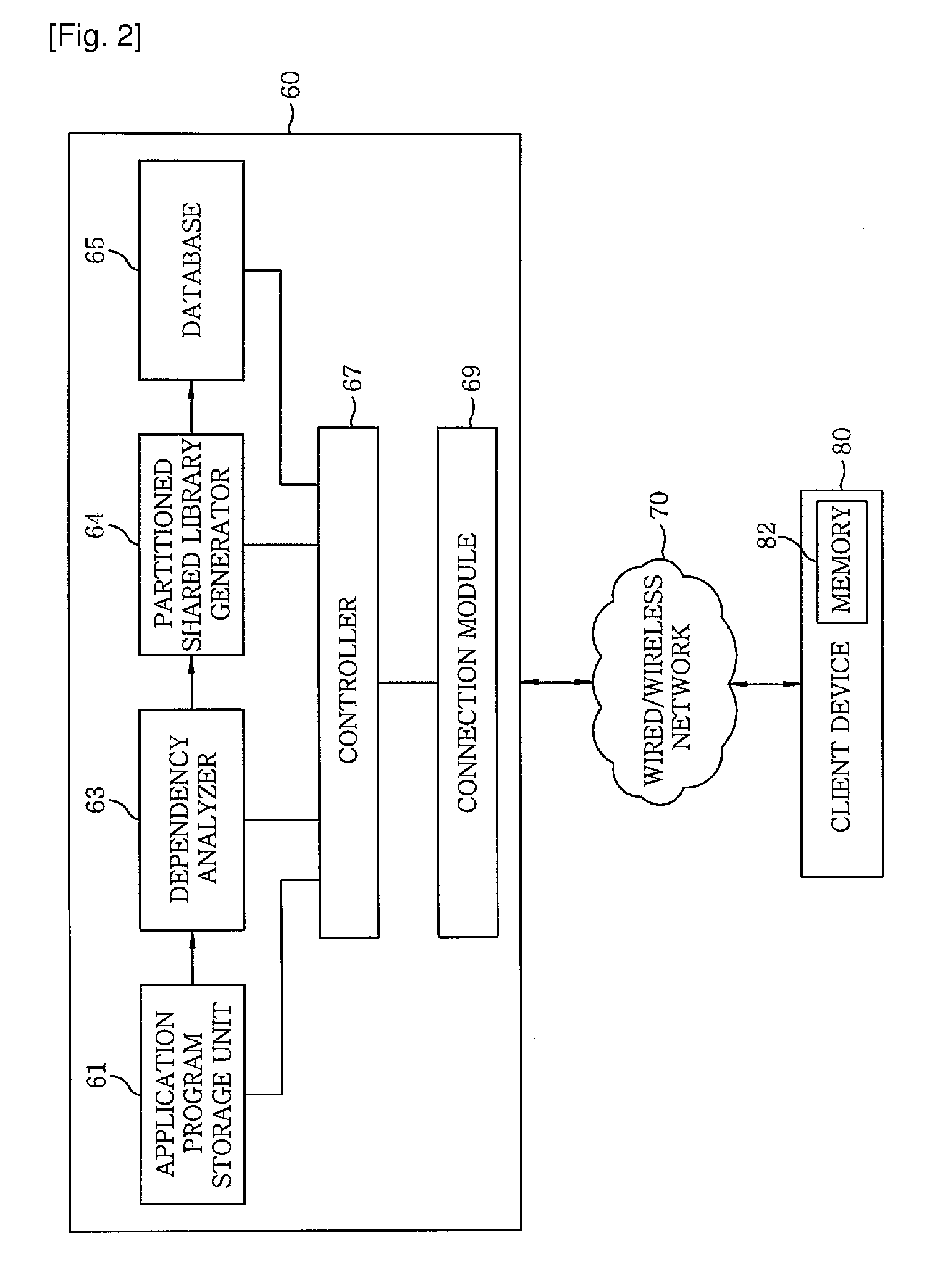
A download server that transmits, when it receives a request of one or more application programs from a client device, to the client device connected to the download server via a wired or wireless network the application programs includes a dependency analyzer, a partitioned shared library generator and a controller. The dependency analyzer that analyzes a dependency of each of the application programs on existing shared libraries to detect object codes, which are actually used by corresponding application program, in the existing shared libraries; the partitioned shared library generator that generates, based on the analyzing result of the dependency analyzer, partitioned shared libraries having only the actually-used object codes; and the controller that transmits, by using a connection module, partitioned shared libraries selected from the generated partitioned shared libraries, and the application programs linked thereto to the client device via the network.
Owner:ELECTRONICS & TELECOMM RES INST
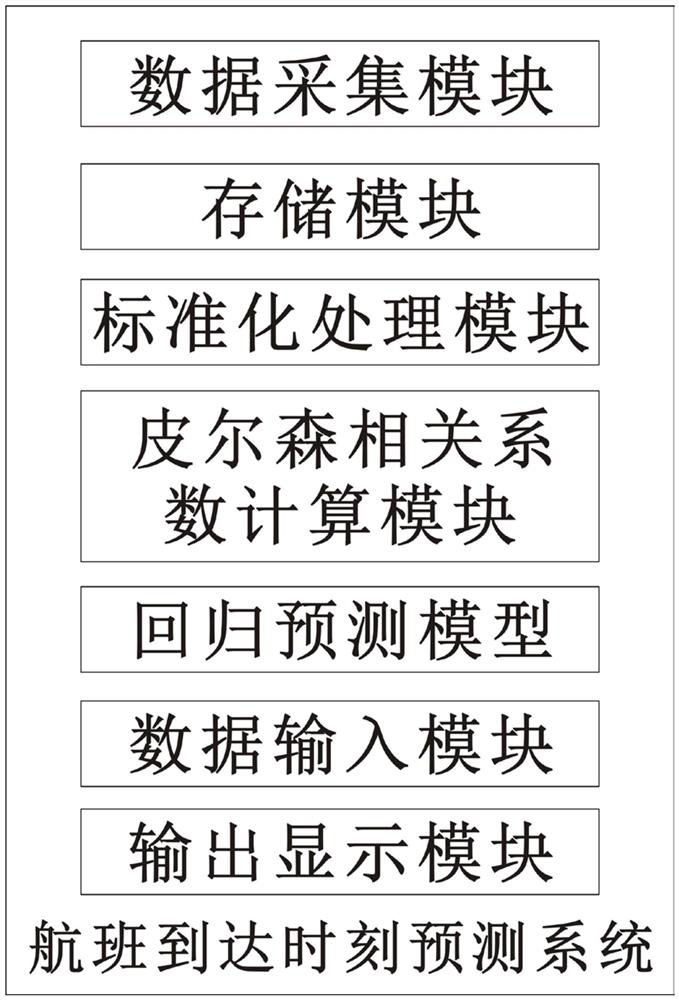
Flight arrival time prediction method and system based on data mining analysis
PendingCN111652427AImprove accuracyImprove forecast accuracyForecastingMachine learningData matchingCorrelation coefficient
The invention discloses a flight arrival time prediction method and system based on data mining analysis. The flight arrival time prediction method comprises the steps of S1, carrying out flight historical operation data matching fusion and standardization processing; s2, carrying out historical operation data feature screening and correlation analysis; 3, constructing a prediction model; and S4,inputting the characteristic variable data of the predicted flight into the regression prediction model, and performing calculation to obtain a prediction value of the remaining flight time of the flight. According to the invention, flight historical data is collected from an ADS-B system, an ACARS system and other devices; firstly, data is subjected to association and standardization processing;Pearson correlation coefficient calculation is performed according to feature variable screening and feature value calculation, and a regression prediction model based on an XGBoost algorithm is constructed; the parameter optimization model is continuously adjusted to obtain the regression prediction model with the optimal accuracy, the predicted arrival time of the flight can be predicted after the characteristic variable data of the predicted flight is input into the model, and the prediction precision of the arrival time of the flight is improved.
Owner:航科院中宇(北京)新技术发展有限公司
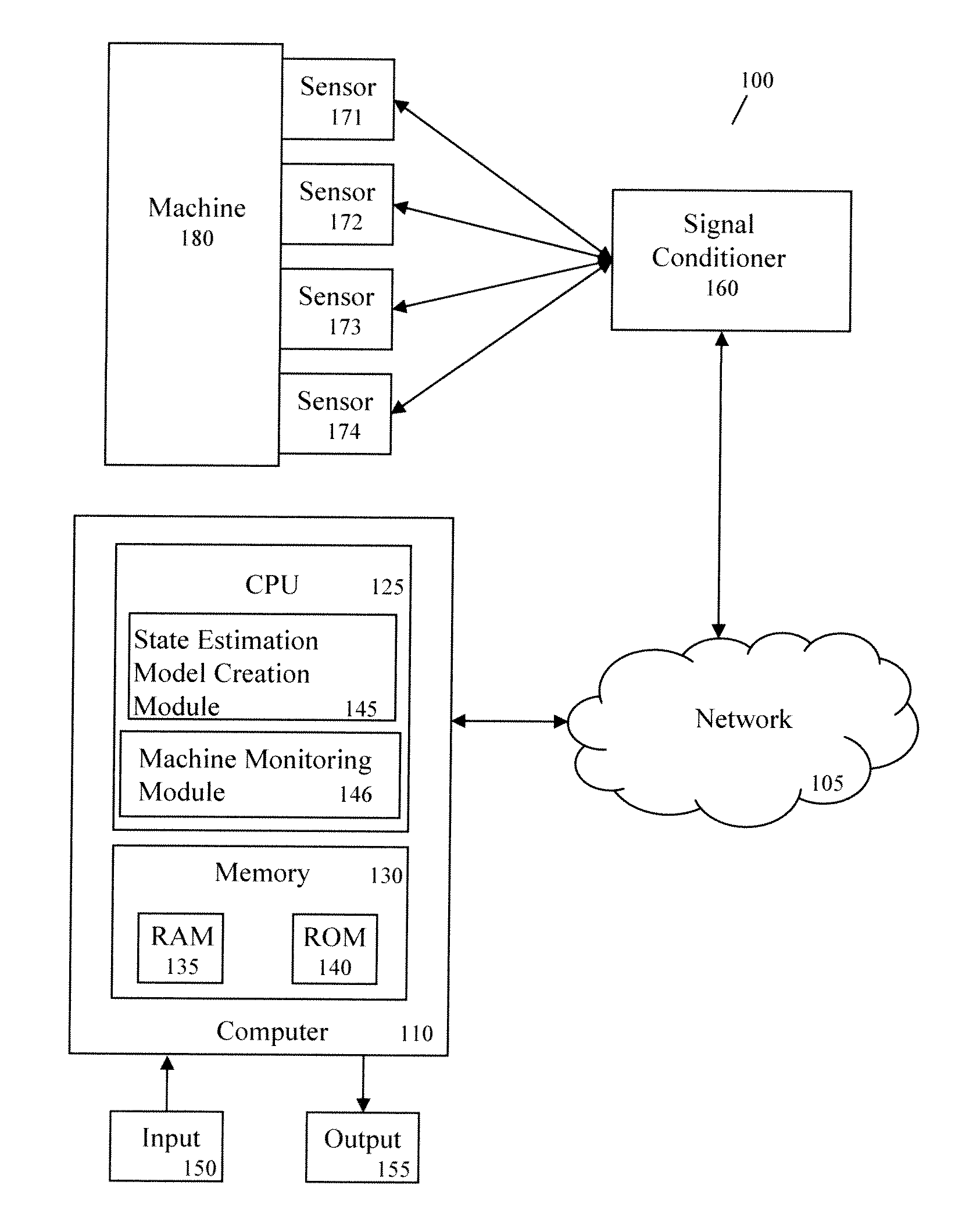
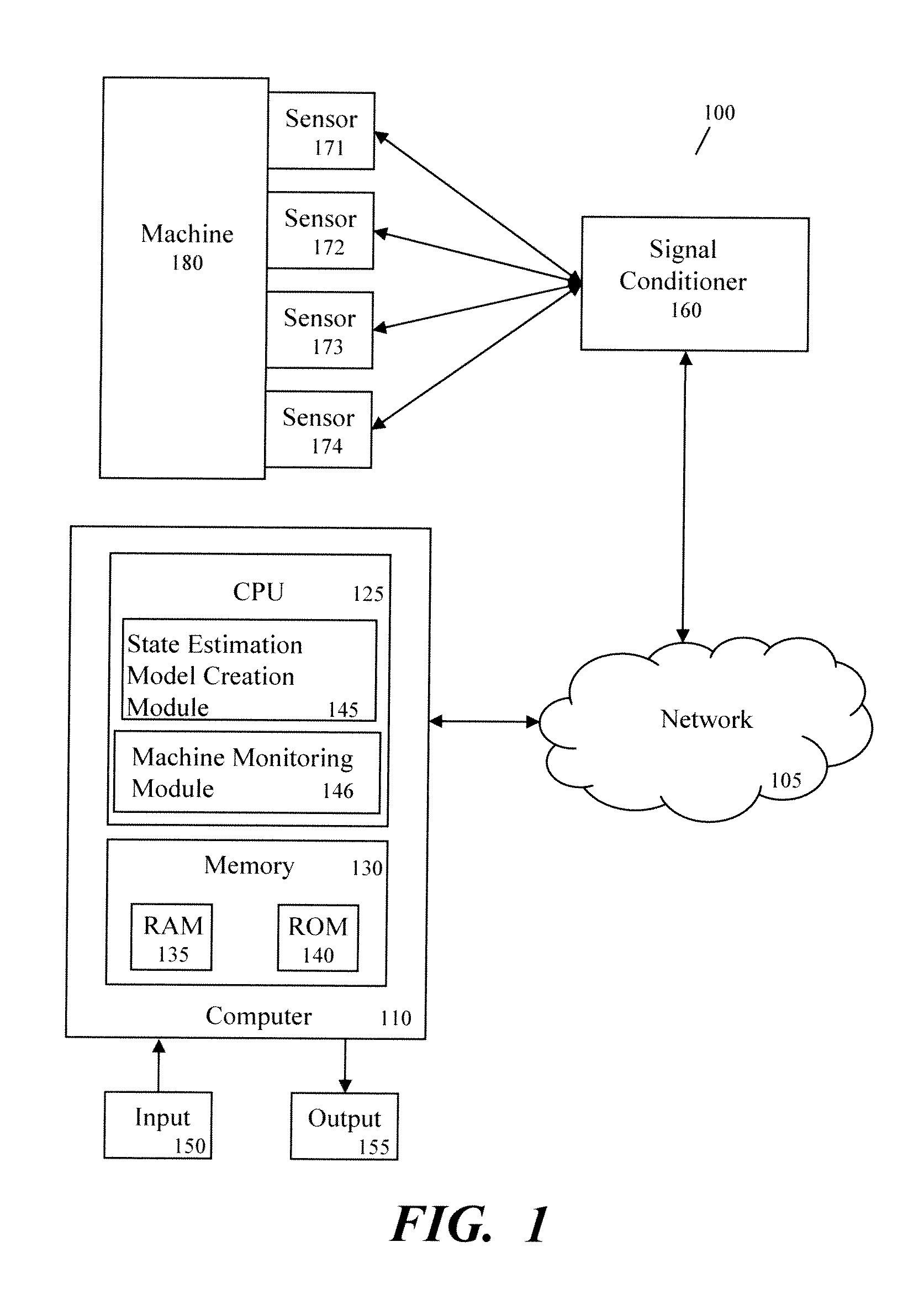
Method And Apparatus For Creating State Estimation Models In Machine Condition Monitoring
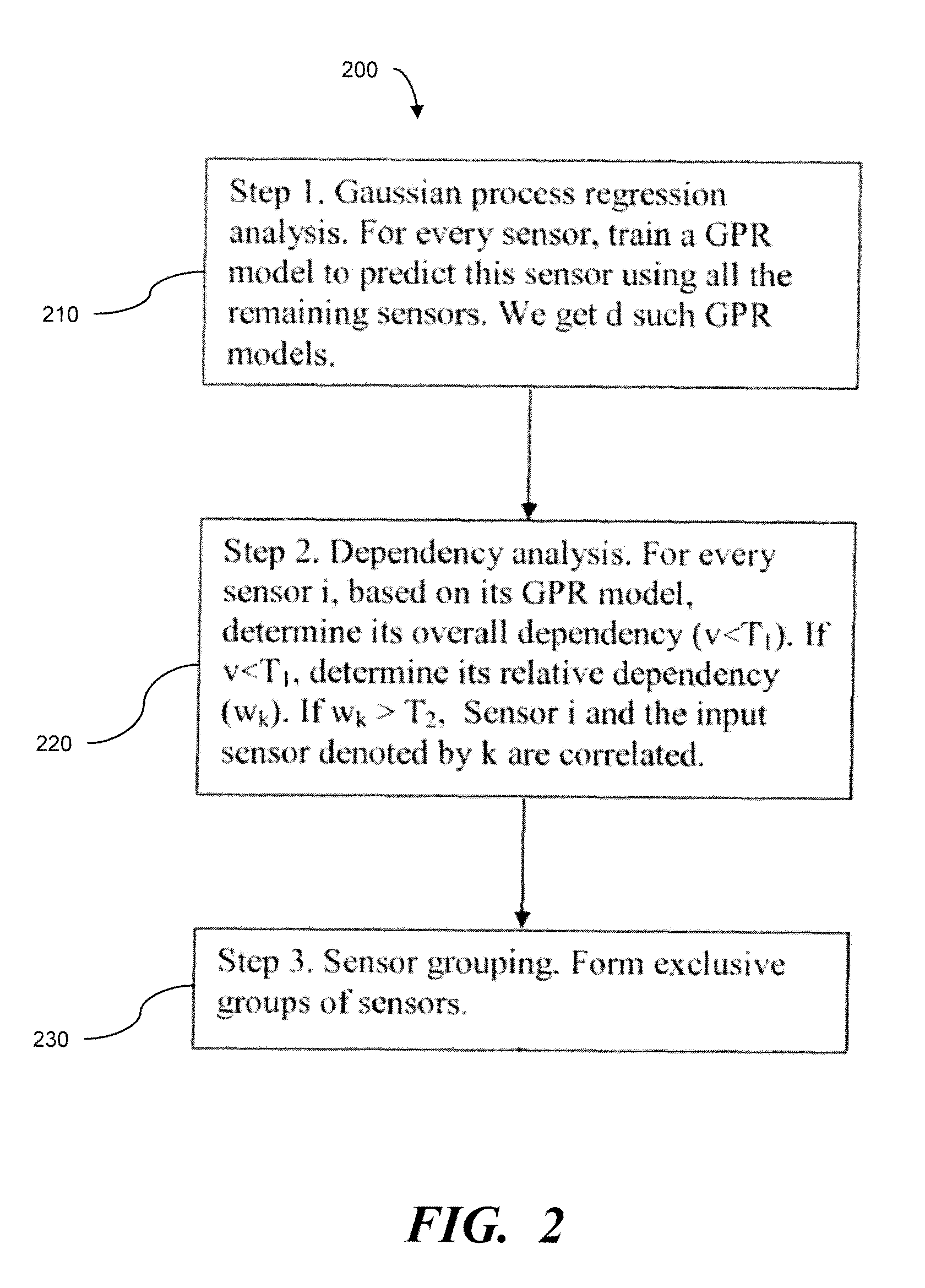
In a machine condition monitoring technique, related sensors are grouped together in clusters to improve the performance of state estimation models. To form the clusters, the entire set of sensors is first analyzed using a Gaussian process regression (GPR) to make a prediction of each sensor from the others in the set. A dependency analysis of the GPR then uses thresholds to determine which sensors are related. Related sensors are then placed together in clusters. State estimation models utilizing the clusters of sensors may then be trained.
Owner:SIEMENS AG
Method for analyzing taint propagation path
InactiveCN103729295AEasy to analyzeEliminate dependenciesSoftware testing/debuggingAnalysis methodBasic block
The invention provides a method for analyzing the taint propagation path to achieve the technical purpose of analyzing the taint propagation path based on the program dependence. The method comprises the steps that firstly, a program is analyzed through the LLVM compiler architecture, a source code is converted into an IR expression, and the IR expression of the LLVM is based on the static single assignment form; secondly, the variable data dependence analysis in a basic block is carried out on the IR expression obtained in the first step; thirdly, the control dependence analysis among basic blocks is carried out on the IR expression obtained in the first step; fourthly, the dependence of a PHI node at the aggregation position of the basic blocks is processed, the PHI function is placed at the aggregation position of the basic blocks in the static single assignment form expression and used for selecting different living examples of the variables in different branches, the dependence relation of the left variable of the PHI function is worked out according to the analysis result of the second step and the analysis result of the third step, the dependence of the basic blocks to the basic block aggregation position is linked, and therefore the taint propagation path can be analyzed.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
Integrated circuit, computer system, and control method
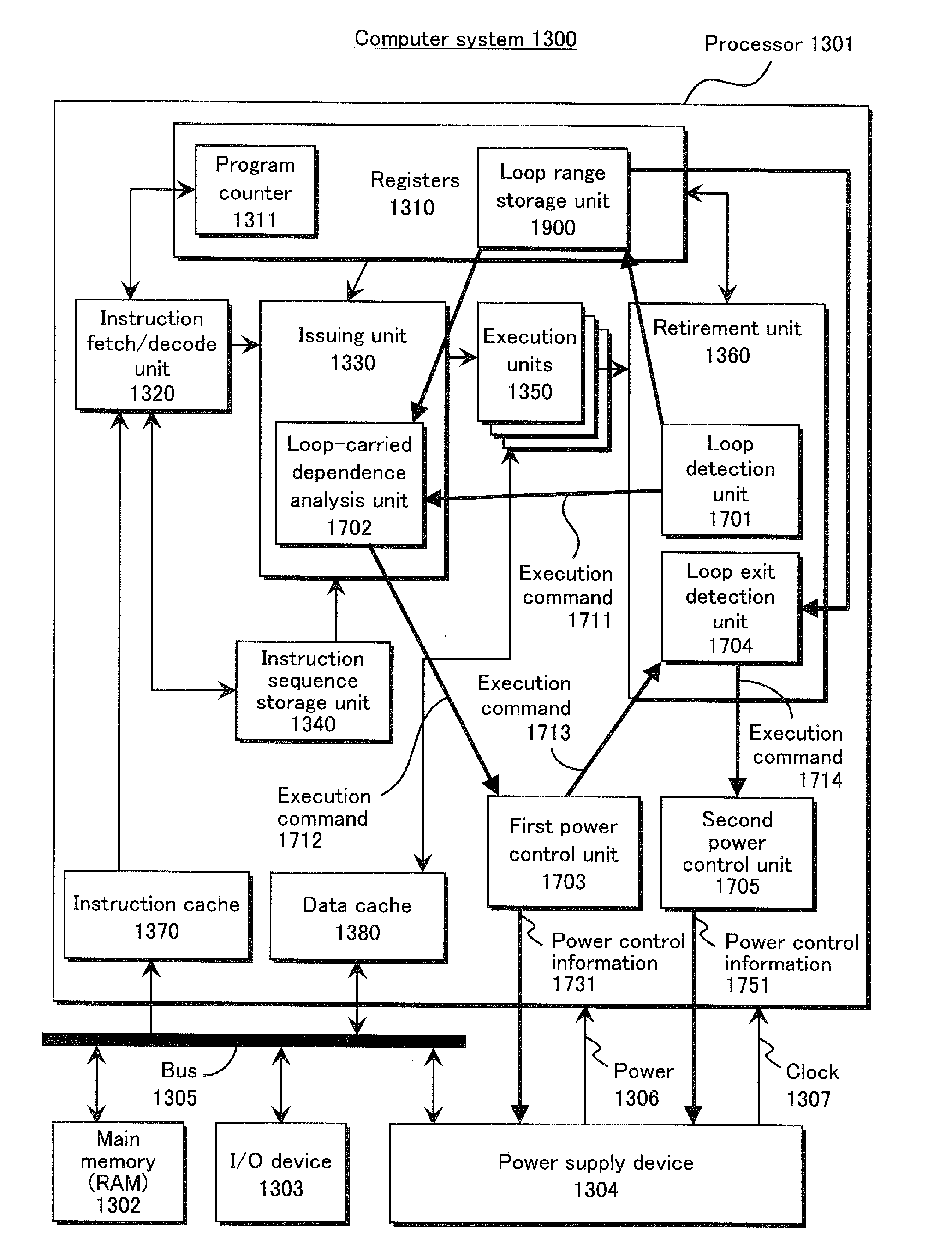
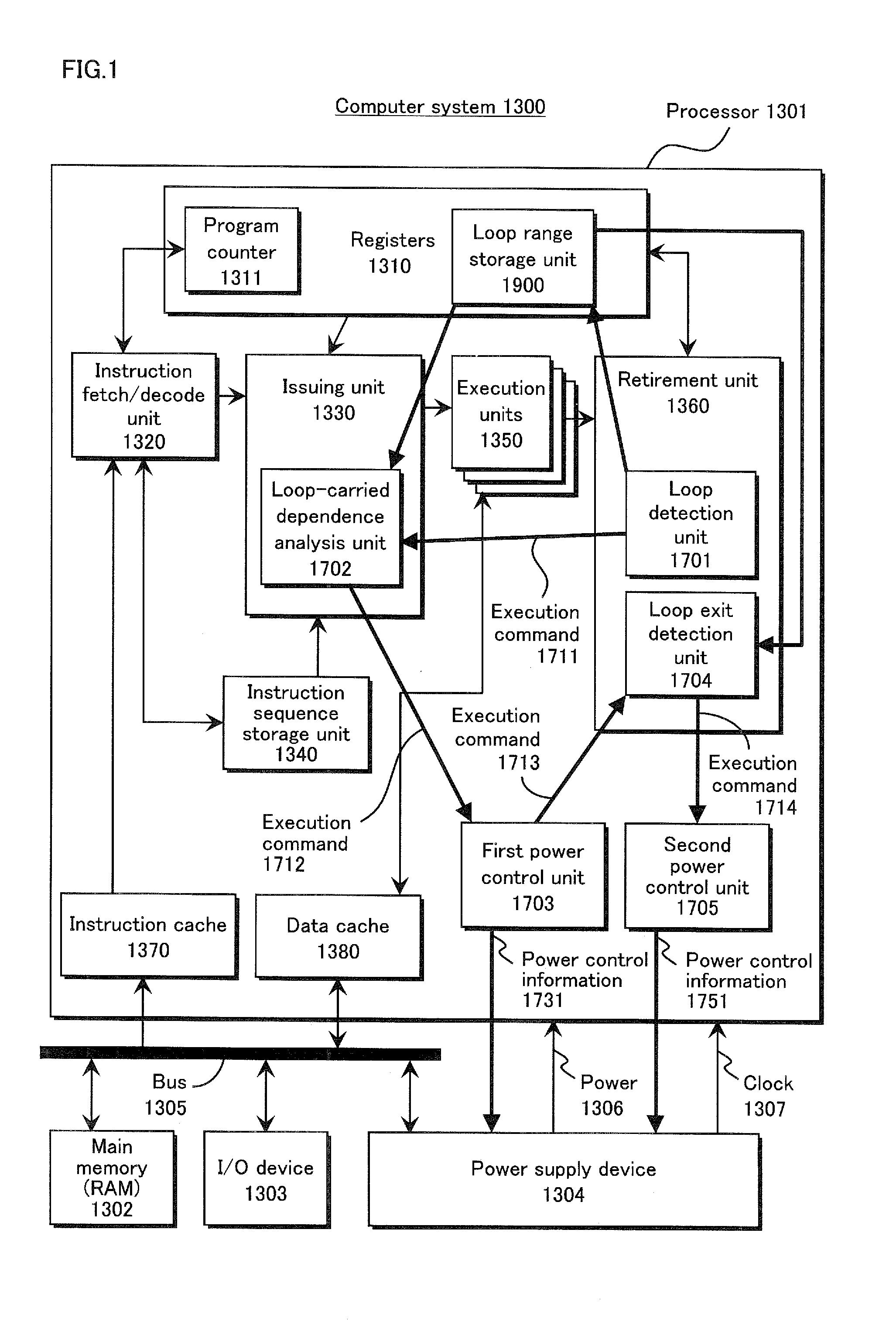
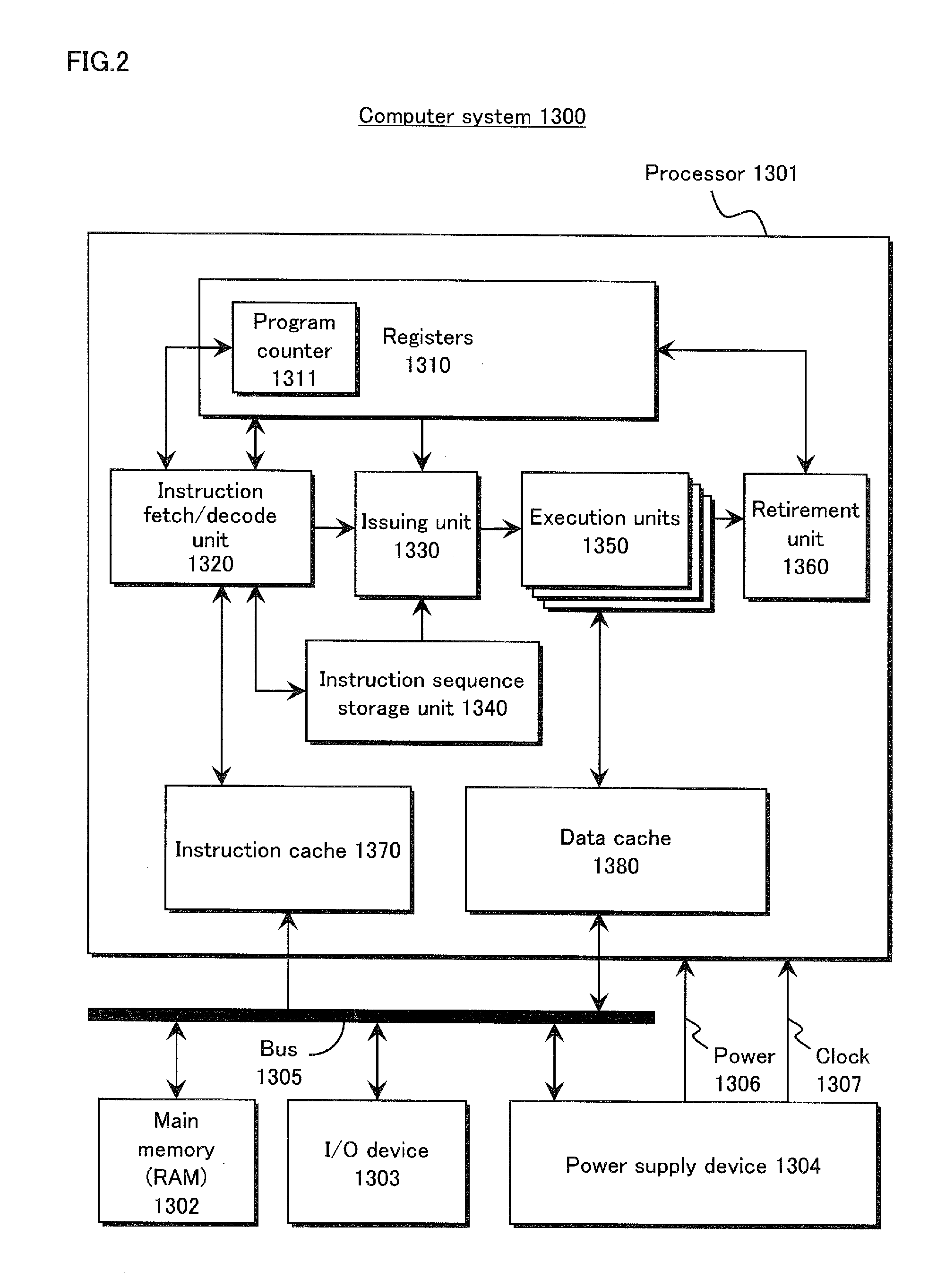
InactiveUS20120179924A1Easily detect loopReduce the amount of powerVolume/mass flow measurementConcurrent instruction executionComputerized systemEngineering
An integrated circuit provided with a processor includes a loop detection unit that detects execution of a loop in the processor, a loop-carried dependence analysis unit that analyzes the loop in order to detect loop-carried dependence, and a power control unit that performs power saving control when no loop-carried dependence is detected. By detecting whether a loop has loop-carried dependence, loops for calculation or the like can be excluded from power saving control. As a result, a larger variety of busy-waits can be detected, and the amount of power wasted by a busy-wait can be reduced.
Owner:PANASONIC INTELLECTUAL PROPERTY MANAGEMENT CO LTD
Imaging related clinical context apparatus and associated methods
ActiveUS20190156921A1Natural language translationMedical data miningPaper documentDocument preparation
Systems, methods, and apparatus provide facilitate detection, processing, and relevancy analysis of clinical data including imaging related clinical context are disclosed and described herein. An example imaging related clinical context apparatus includes a processor to: analyze a plurality of documents to identify a subset of relevant documents in the plurality of document by: applying natural language processing to identify terms in the plurality of documents, a subset of the identified terms forming tagged concepts; processing the identified terms using a machine learning model with respect to a relevancy criterion for an examination to select the subset of relevant documents; and adding an emphasis to the tagged concepts found in the subset of relevant documents. The processor is to output the subset of relevant documents including emphasized tagged concepts.
Owner:GENERAL ELECTRIC CO
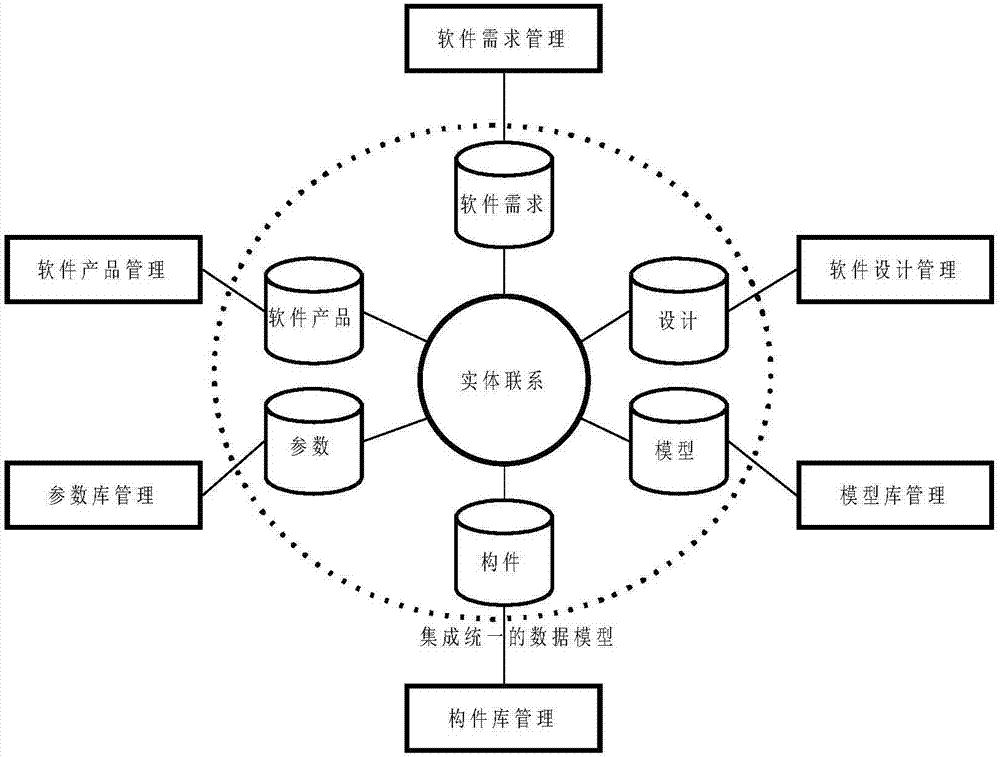
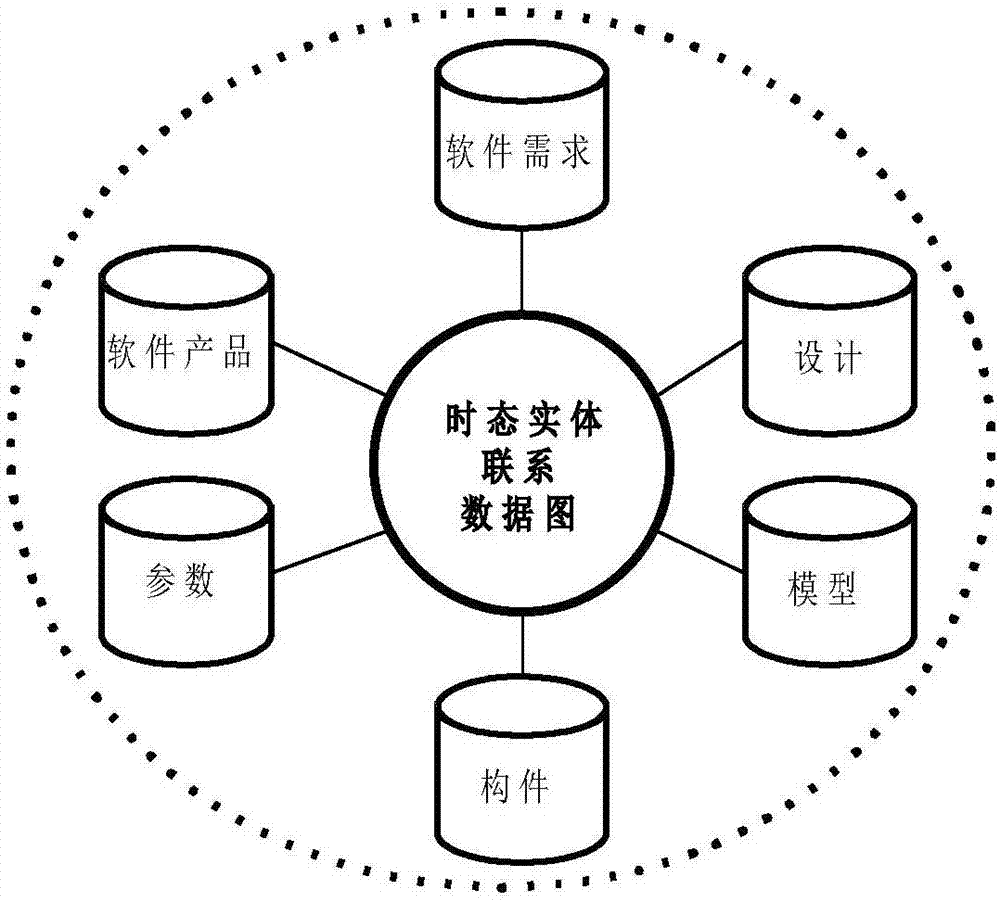
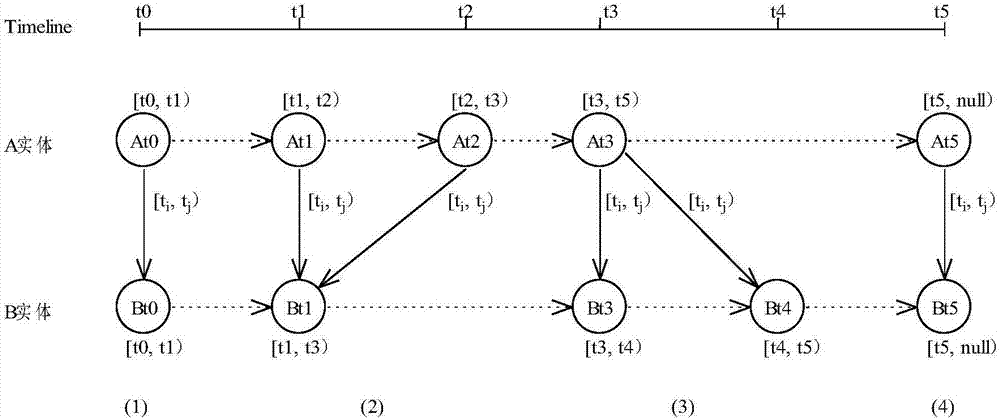
Temporality-based object dependency discovery method and system
ActiveCN106970788AImprove maintainabilitySoftware designSpecific program execution arrangementsSoftware configuration managementStored procedure
The invention relates to a temporality-based software configuration management object dependency discovery system and method. According to the method, time-varying software development factors, including at least one of software demands, design, models, components, parameters, software products, development units and developers, are defined as temporal entities; database modes of tables, views, storage processes, etc. corresponding to the temporal entities and a temporal entity relationship are established, and each database mode at least comprises a time property field, a temporal entity internal dependency field and a temporal entity external dependency field; and access is made to all the database modes, a Multilayer Temporal Dependency Graph (MTDG) is established, and needed analysis about internal and external dependency of the temporal entities is obtained according to the MTDG. The method is beneficial for timely discovering influences on other modules or a whole software system after a certain part of the software system is changed (version upgrade and version change) during software configuration management, so that software development and maintenance cost is lowered, and software configuration efficiency is improved.
Owner:PLA DALIAN NAVAL ACADEMY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com