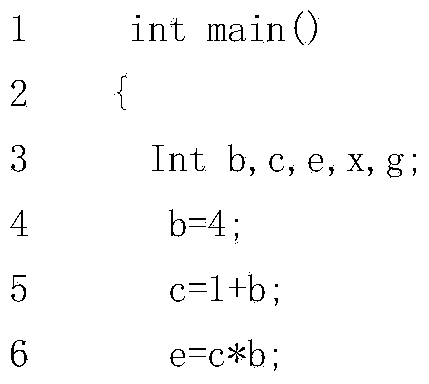Method for analyzing taint propagation path
A technology of taint propagation and path analysis, applied in the field of taint propagation path analysis, can solve the problems of less research, time-consuming, and performance-consuming, and achieve the effect of simple data flow analysis, eliminating redundant dependencies, and eliminating control dependencies
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] The present invention will be further described below in conjunction with the drawings and specific embodiments.
[0021] At first term among the present invention is set forth:
[0022] Static single assignment: Static Single-Assignment, which is an intermediate representation. It is called single assignment because each name is only assigned once in SSA.
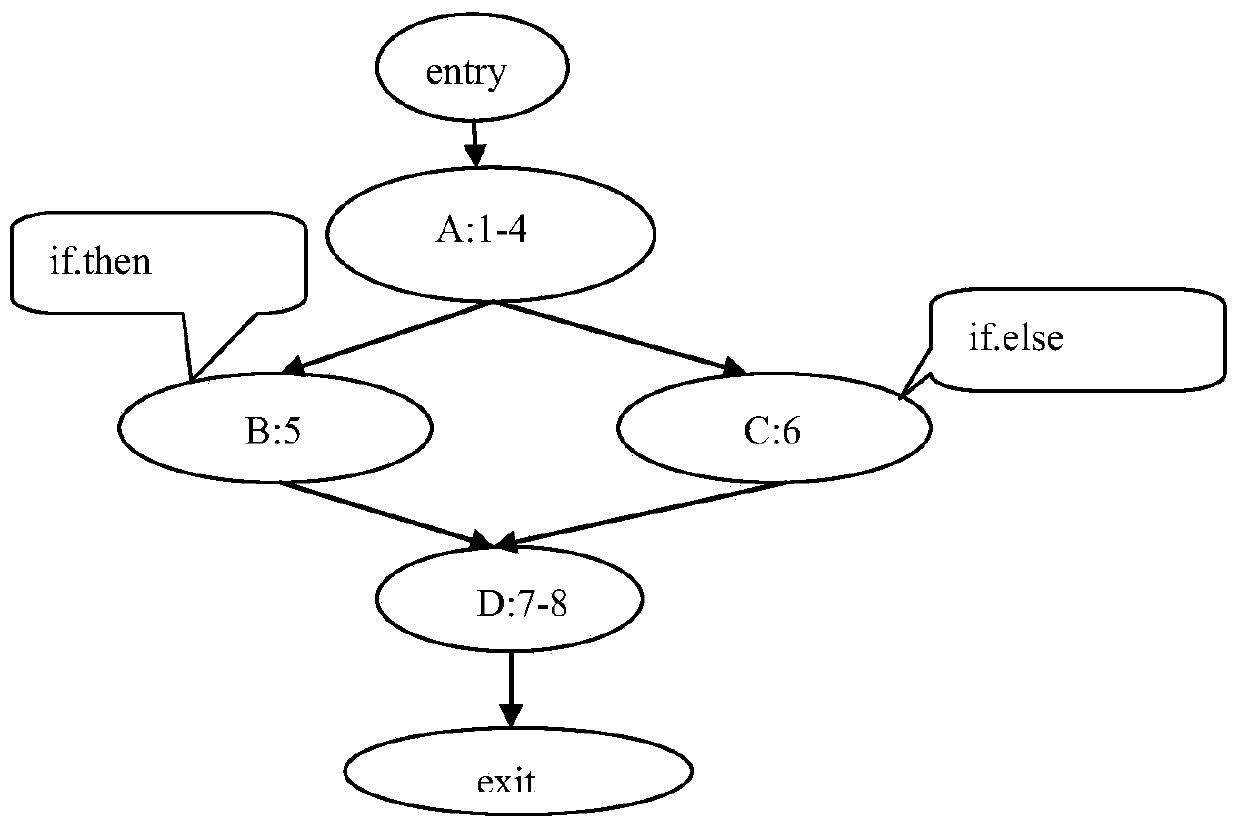
[0023] Postdomination: We say that the basic block Y postdominates the basic block X, if every path P from X to the program Exit contains Y, it is recorded as Y PDom X. That is, Y is a necessary node of X.
[0024] Post dominance frontier (Post dominance frontier): DF(Y)={X|Z is the successor node of X so that Y post-dominates Z and Y does not post-dominate node X, that is, Z∈succeed(X) makes Y PDom Z and Y┐ (PDom)X}.
[0025] Branch control variable: Assume that the basic block B contains the definition of variable v or the use statement, and the bounding set of B’s necessary nodes is DF(B). For any Bi∈DF(B), i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com