Software privacy leak behavior detection method and system based on virtualization technology
A virtualization technology and privacy leakage technology, applied in the direction of platform integrity maintenance, etc., can solve problems such as pollution, inability to obtain the precise location of polluted data from data analysis results, lack of upper-level information in instruction-level data, etc., to achieve effective analysis and detection Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] The present invention will be further described below through specific examples and accompanying drawings.
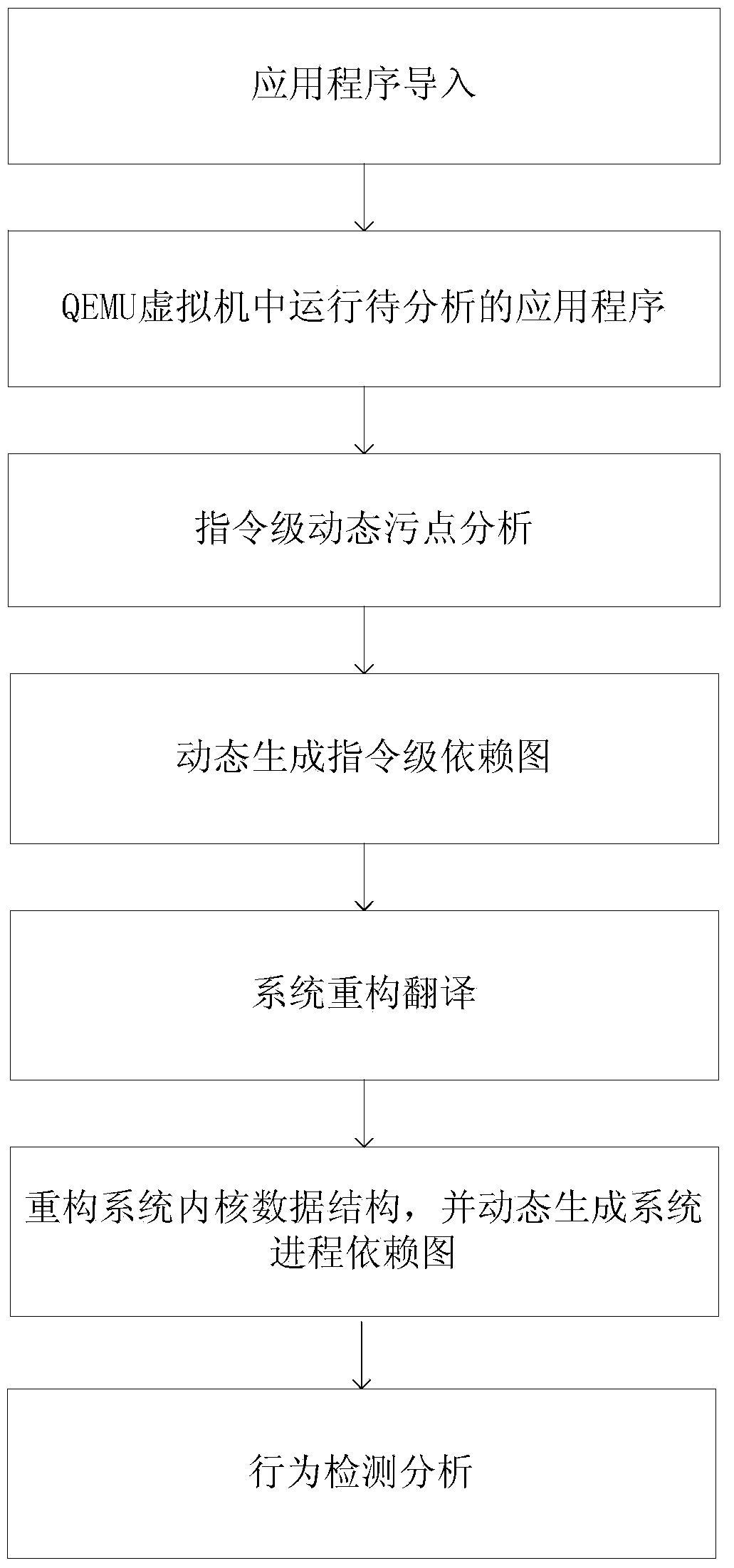
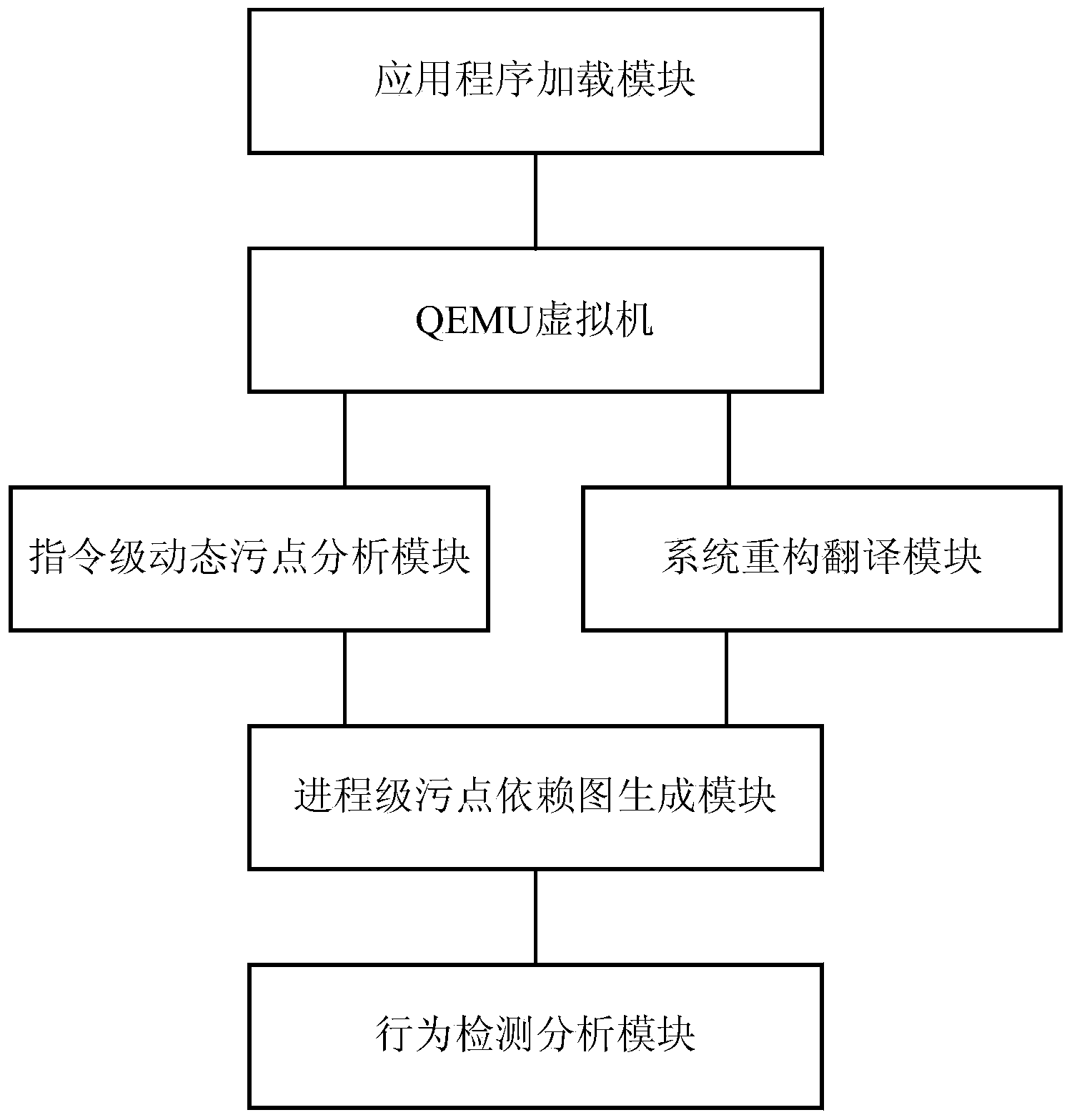
[0030] This embodiment adopts linux software, and the steps of the linux software privacy leakage behavior detection method are as follows: figure 1 As shown, the corresponding system module composition is as follows figure 2 As shown, the specific description is as follows:
[0031] 1. Import the application to be analyzed into the virtual machine and run it.
[0032] By running the application program to be detected in a virtual machine (such as a QEMU virtual machine), the information of each executed instruction is monitored, and each module performs corresponding processing as required before the instruction is translated.
[0033] Specifically, by modifying its hardware simulation program in the virtual machine, taint tags can be added to the privacy-sensitive information of the user host, and the memory unit where the taint data is stored can be located...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com