Patents
Literature
749 results about "Stored procedure" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A stored procedure (also termed proc, storp, sproc, StoPro, StoredProc, StoreProc, sp, or SP) is a subroutine available to applications that access a relational database management system (RDBMS). Such procedures are stored in the database data dictionary.
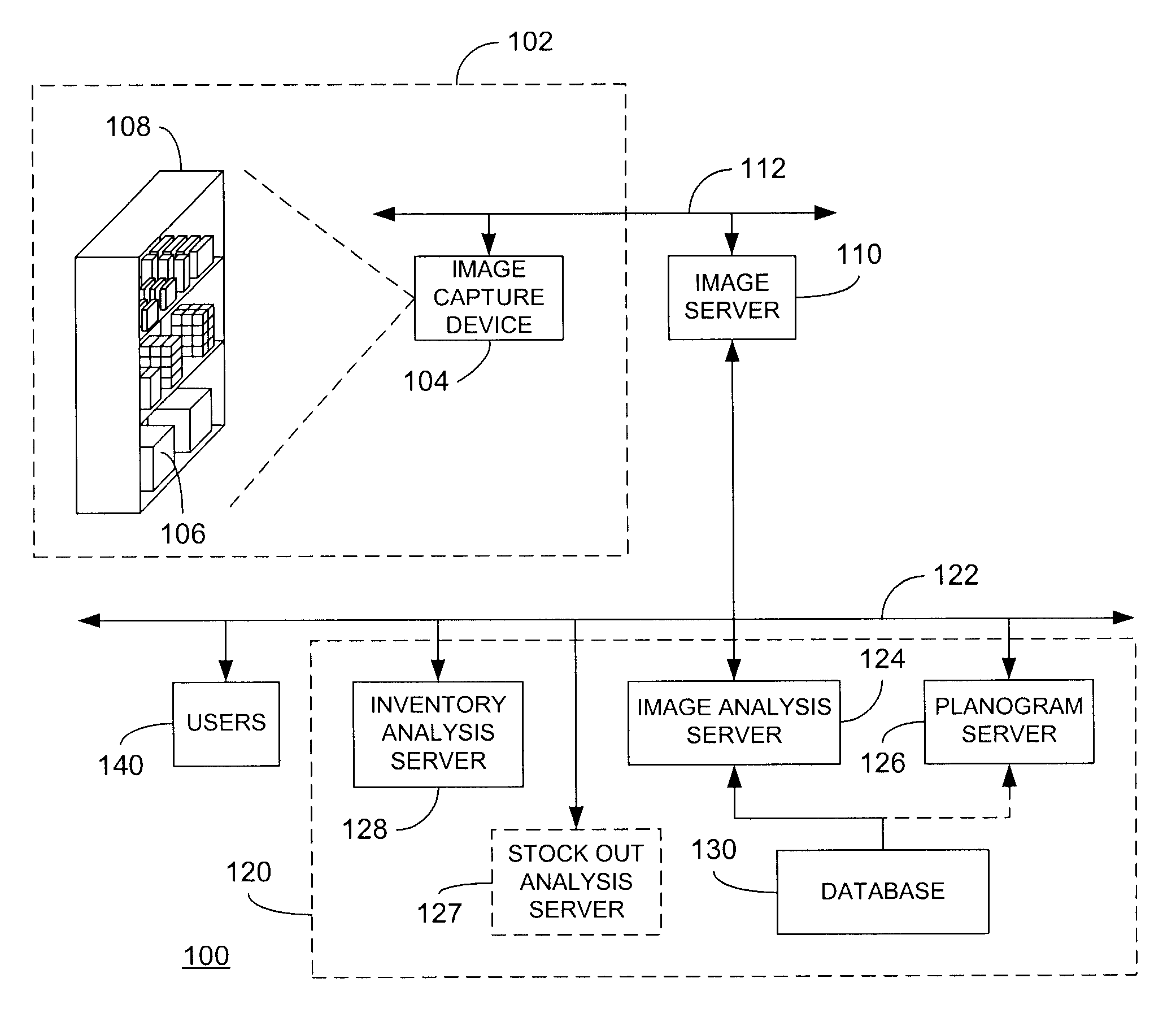
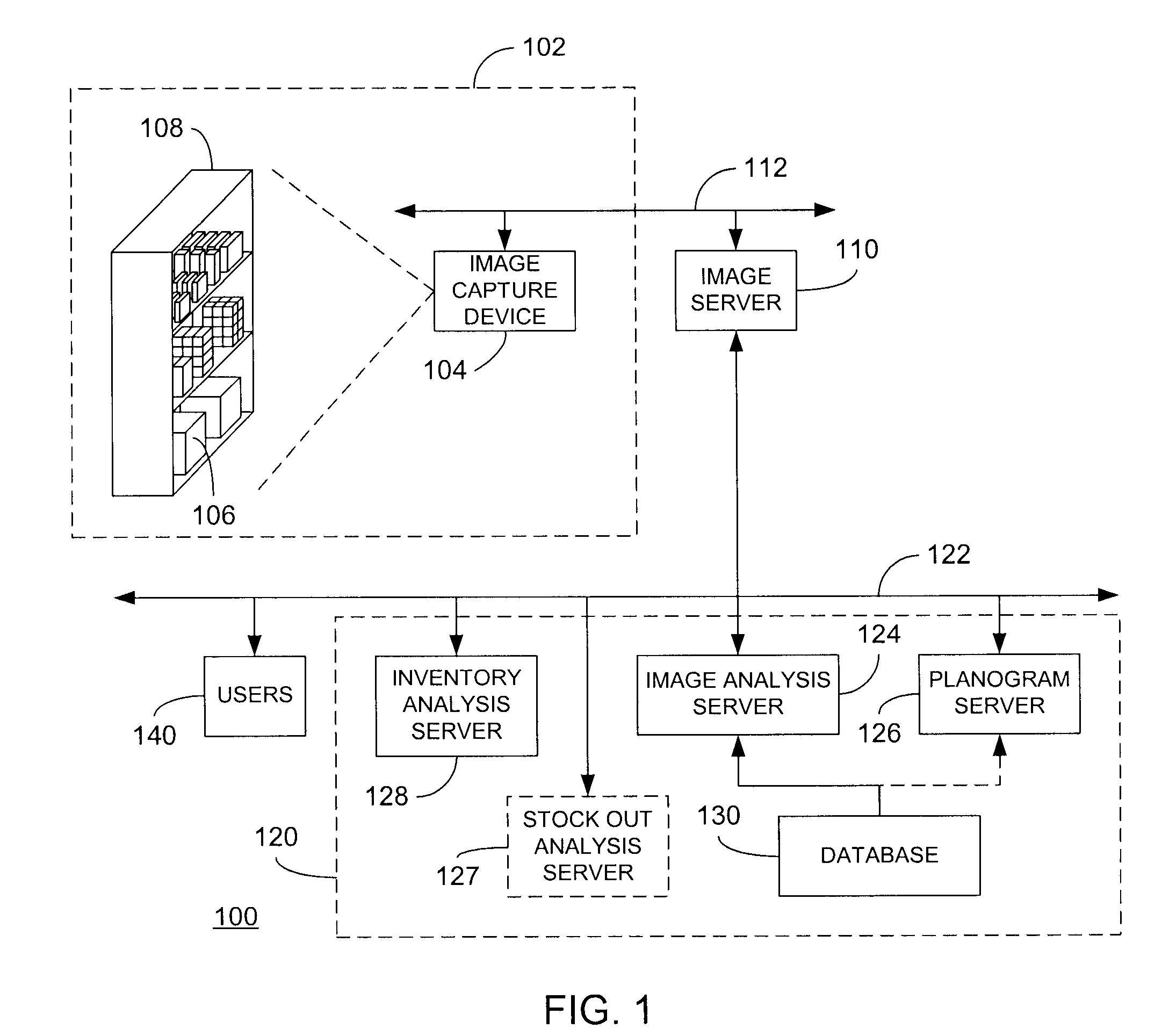
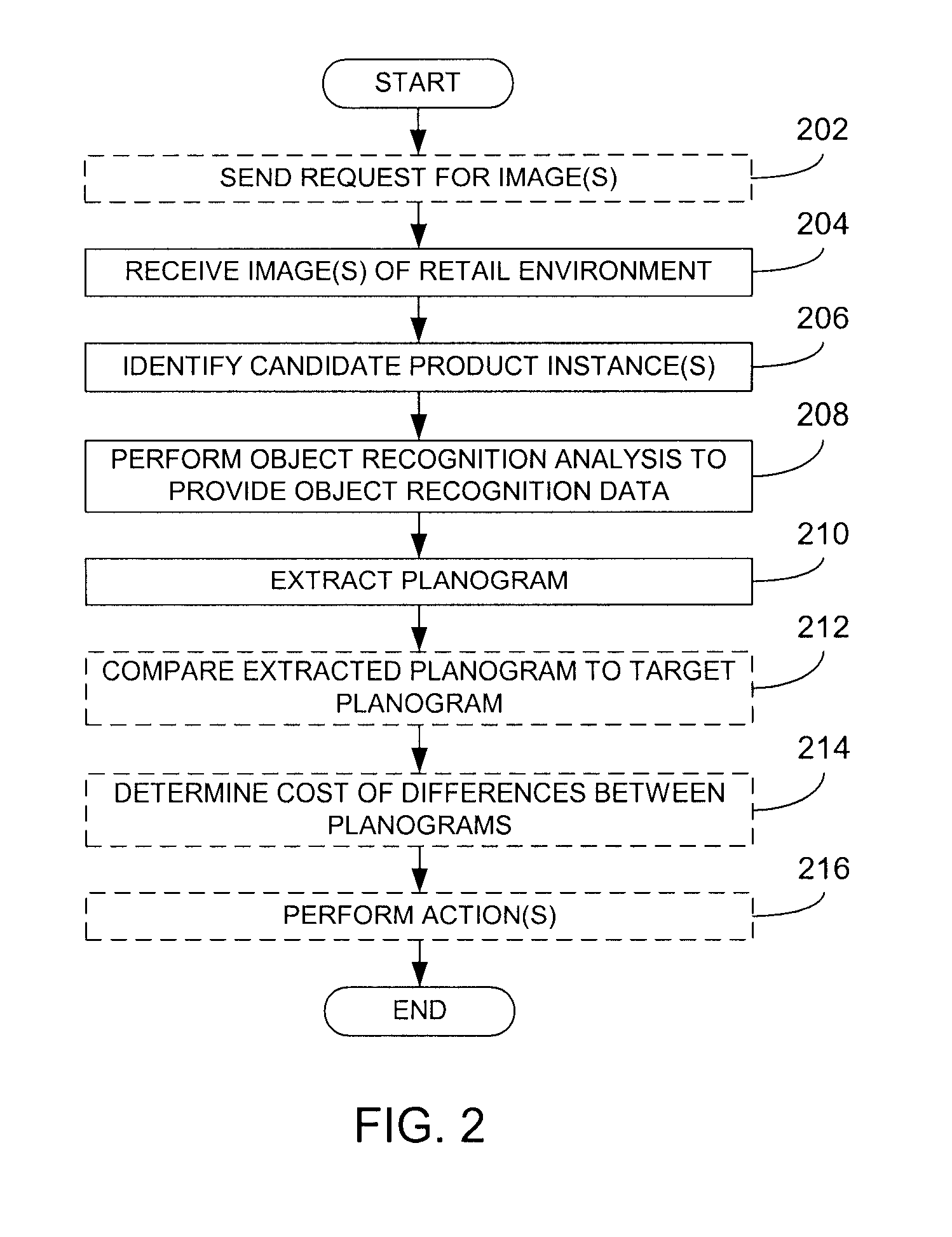
Planogram extraction based on image processing
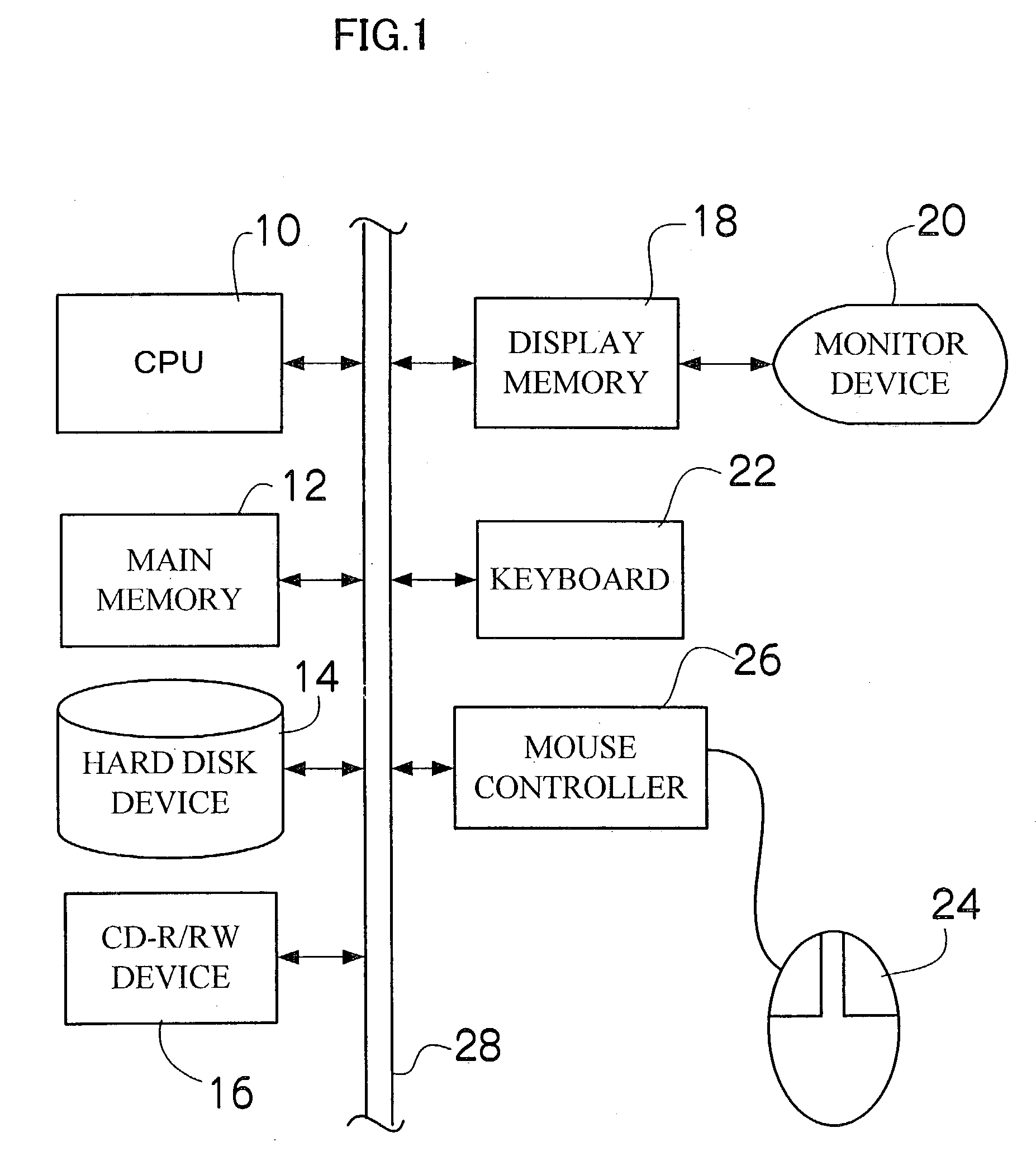
ActiveUS8189855B2Enhancing efficiency and effectivenessQuick checkDigital output to print unitsThree-dimensional object recognitionPattern recognitionObject based
Image analysis techniques, including object recognition analysis, are applied to images obtained by one or more image capture devices deployed within inventory environments. The object recognition analysis provides object recognition data (that may include one or more recognized product instances) based on stored product (training) images. In turn, a variety of functionalities may be enabled based on the object recognition data. For example, a planogram may be extracted and compared to a target planogram, or at least one product display parameter for a product can be determined and used to assess presence of the product within the inventory environment, or to determine compliance of display of the product with a promotional objective. In yet another embodiment, comparisons may be made within a single image or between multiple images over time to detect potential conditions requiring response. In this manner, efficiency and effectiveness of many previously manually-implemented tasks may be improved.
Owner:ACCENTURE GLOBAL SERVICES LTD
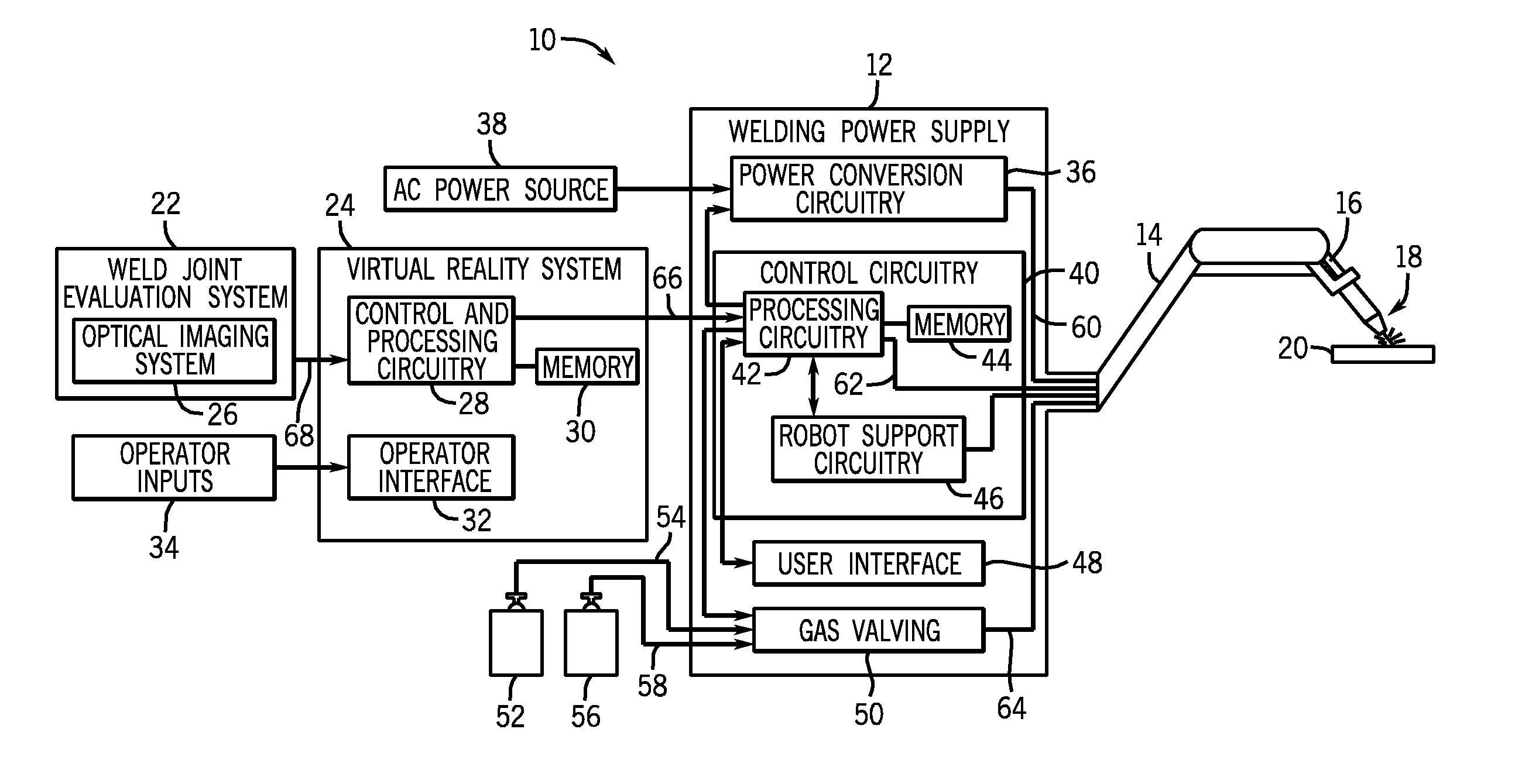
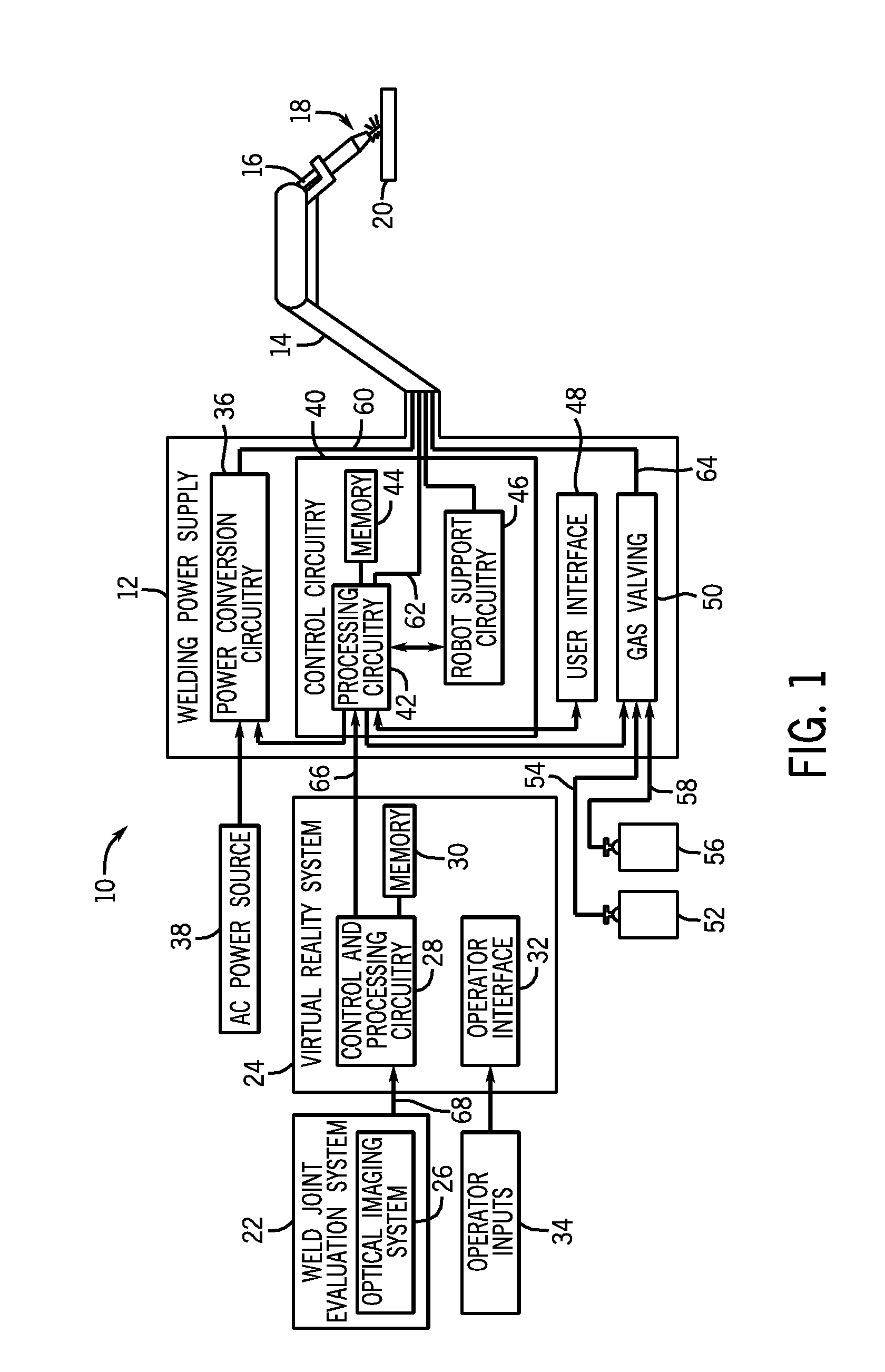
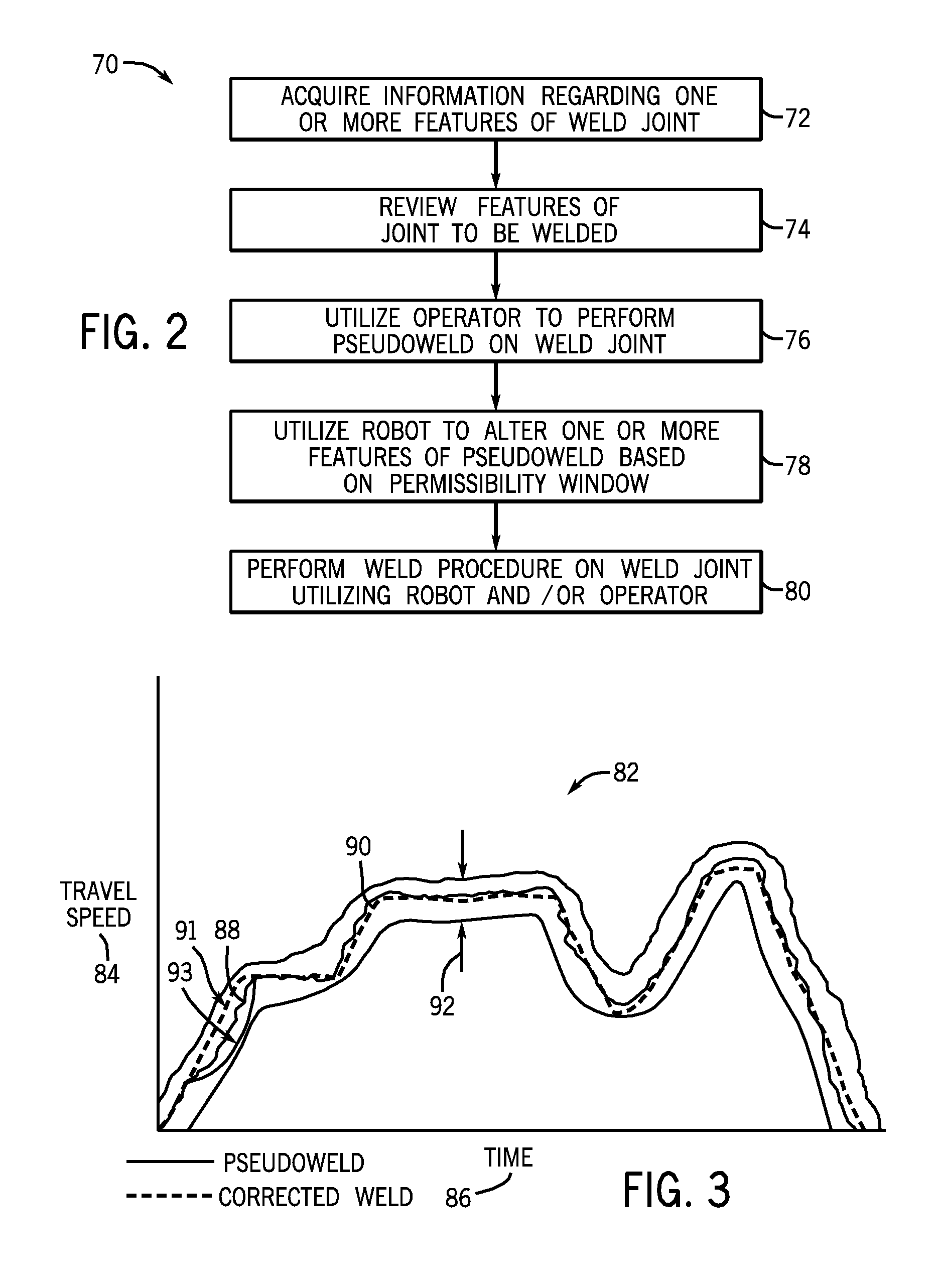
Automatic and semi-automatic welding systems and methods
Methods and devices for control for an automated welding system are provided. Disclosed control methods may include receiving a data set including one or more features of a joint to be welded and receiving a weld procedure for the joint to be welded. The weld procedure for the joint is determined based on a sample virtual weld performed by an operator, a stored procedure developed for a substantially similar weld joint, or a combination thereof. The method may further include determining one or more desired changes to the weld procedure based on the received features of the joint to be welded and generating an updated weld procedure by altering one or more parameters of the received weld procedure in accordance with the one or more desired changes, wherein the one or more parameters are included within a predetermined allowable data set.
Owner:ILLINOIS TOOL WORKS INC
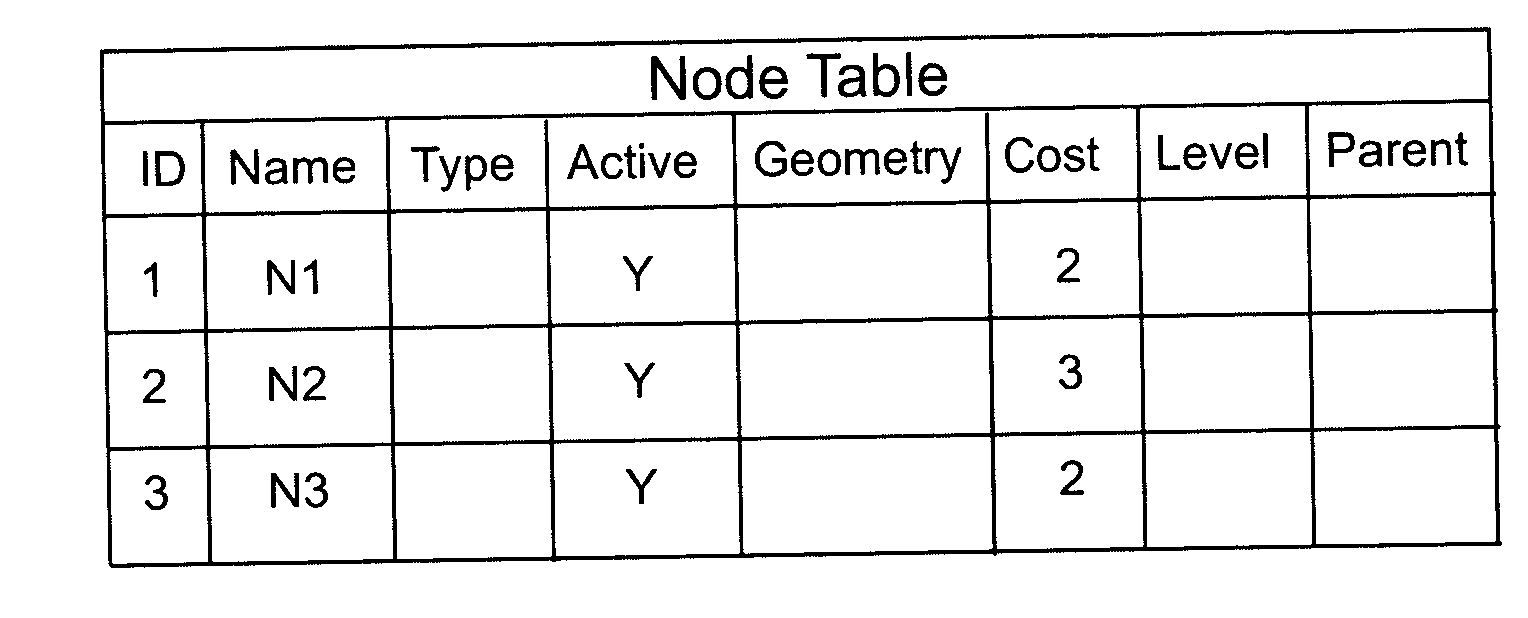
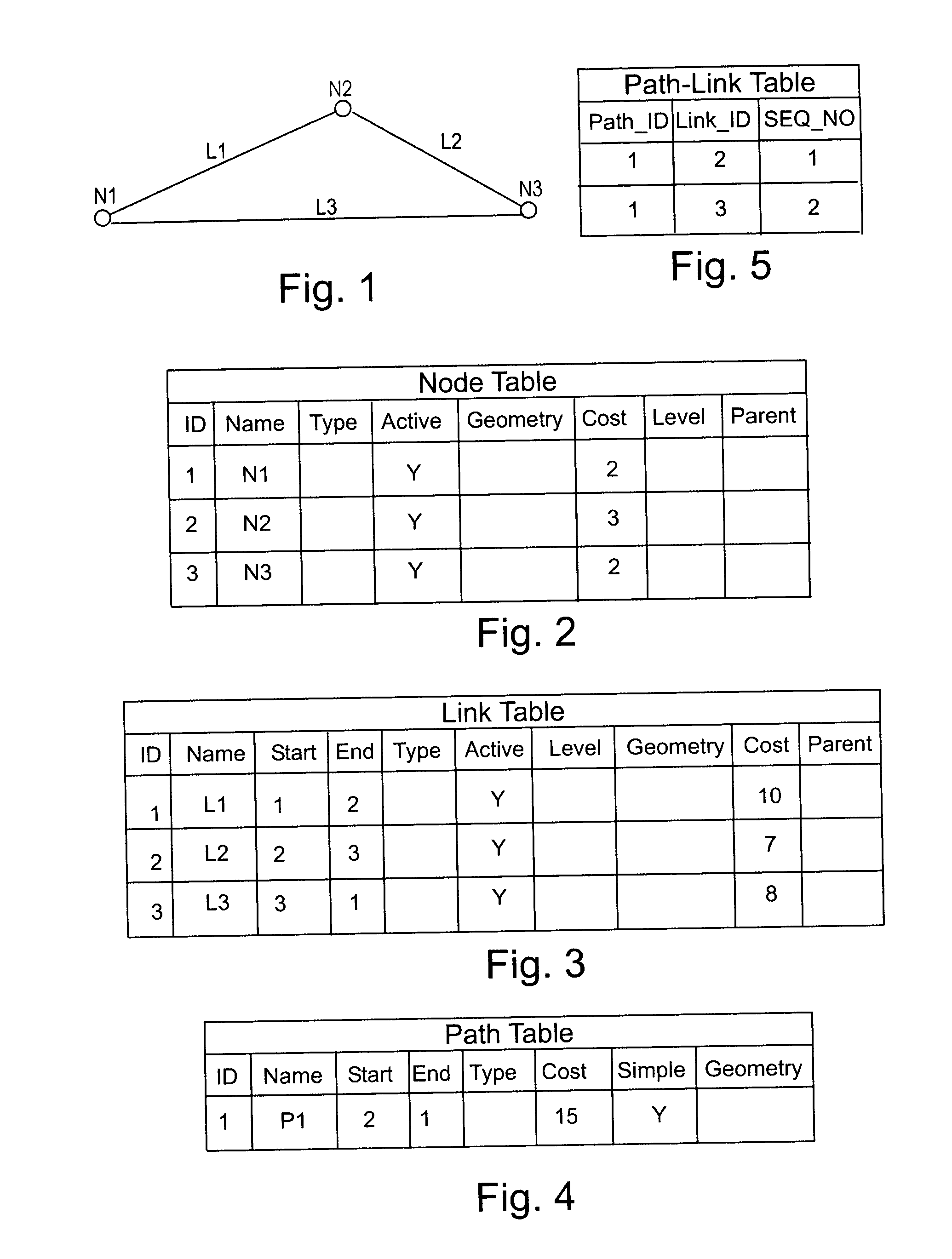
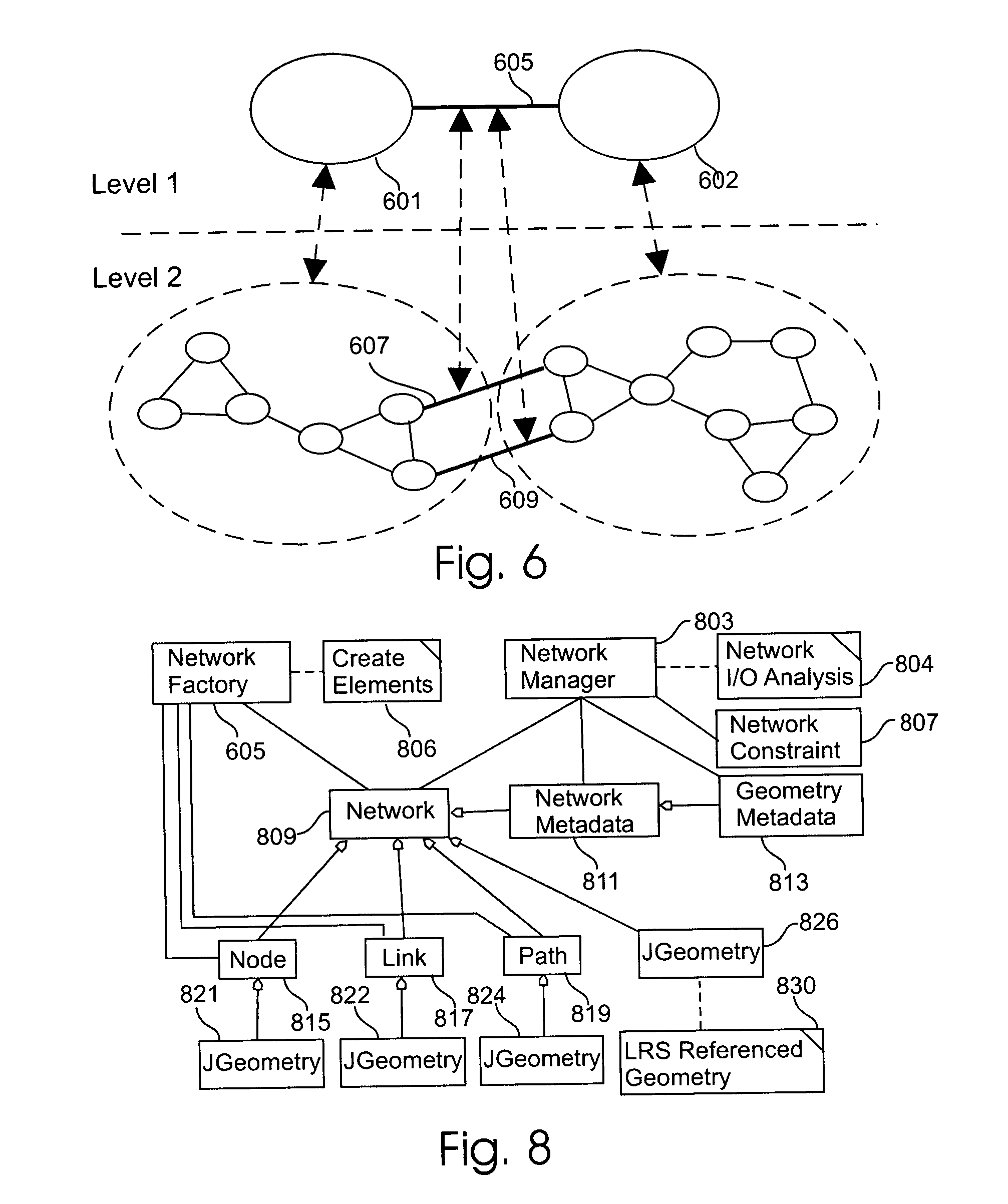
Network data model for relational database management system
ActiveUS20050097108A1Reduce maintenance costsSimplified managementDigital data processing detailsRelational databasesRelational database management systemNetwork data
A shareable application program interface (API) and network data model infrastructure which is used in combination with a relational database to provide data storage and processing functions for network data. The network data model is stored in relational tables that describe a set of nodes and links forming a network wherein each of node represents an object of interest and link represents a relationship between two nodes. A generic node table contains a row describing each node in the network, and a generic link table contains row data describing each link. In addition, a path table whose contents are commonly generated by network analysis procedures contains rows which describe corresponding paths each consisting of an alternating sequence of nodes and links. The sequence of links in each path are identified in a separate path-link table. The system provides two application program interfaces, a PL / SQL API and a Java API, which executing application programs to use stored procedures for creating the node and link tables, store data describing nodes and links in the tables, and perform standard operations on the network data.
Owner:ORACLE INT CORP
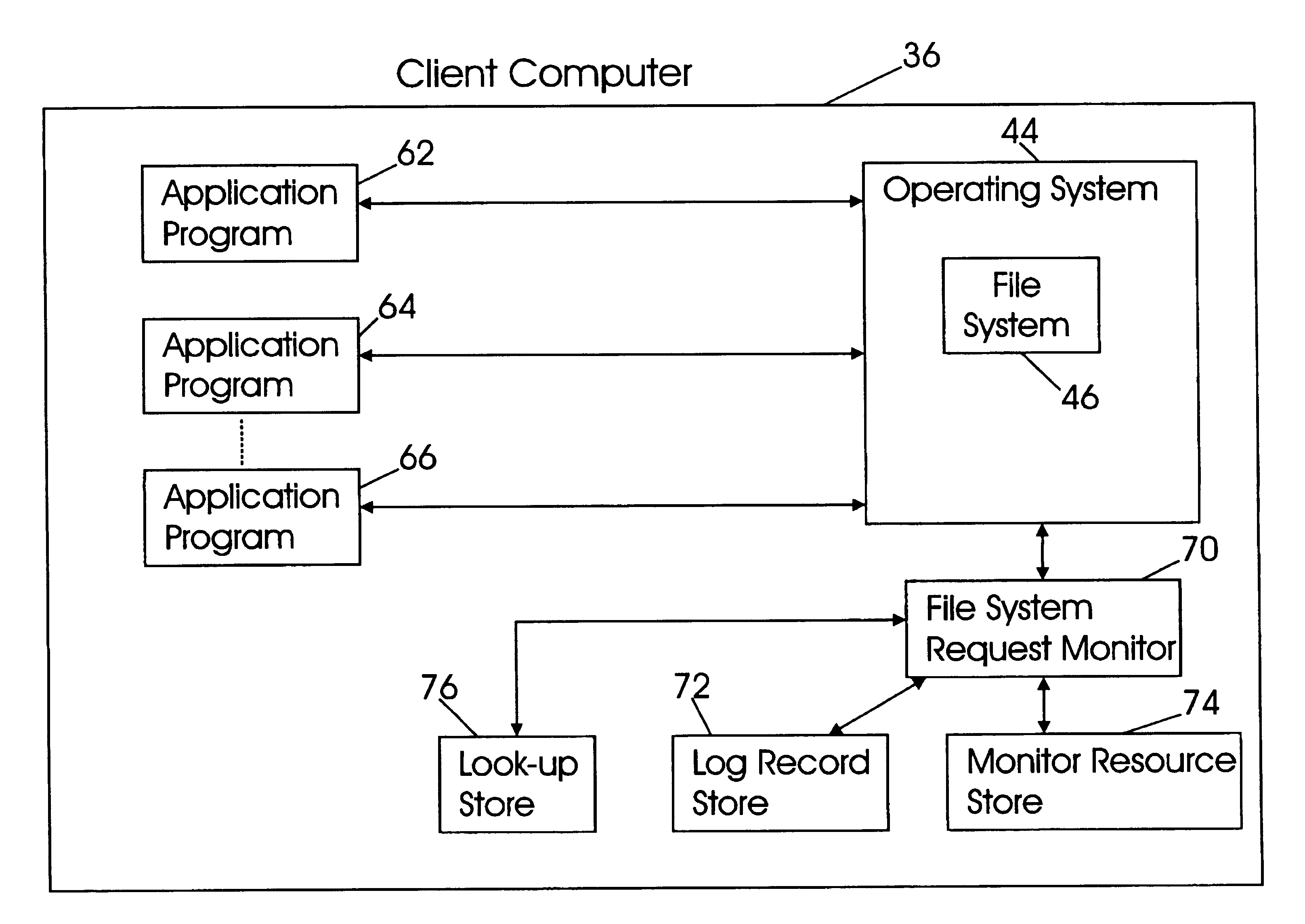
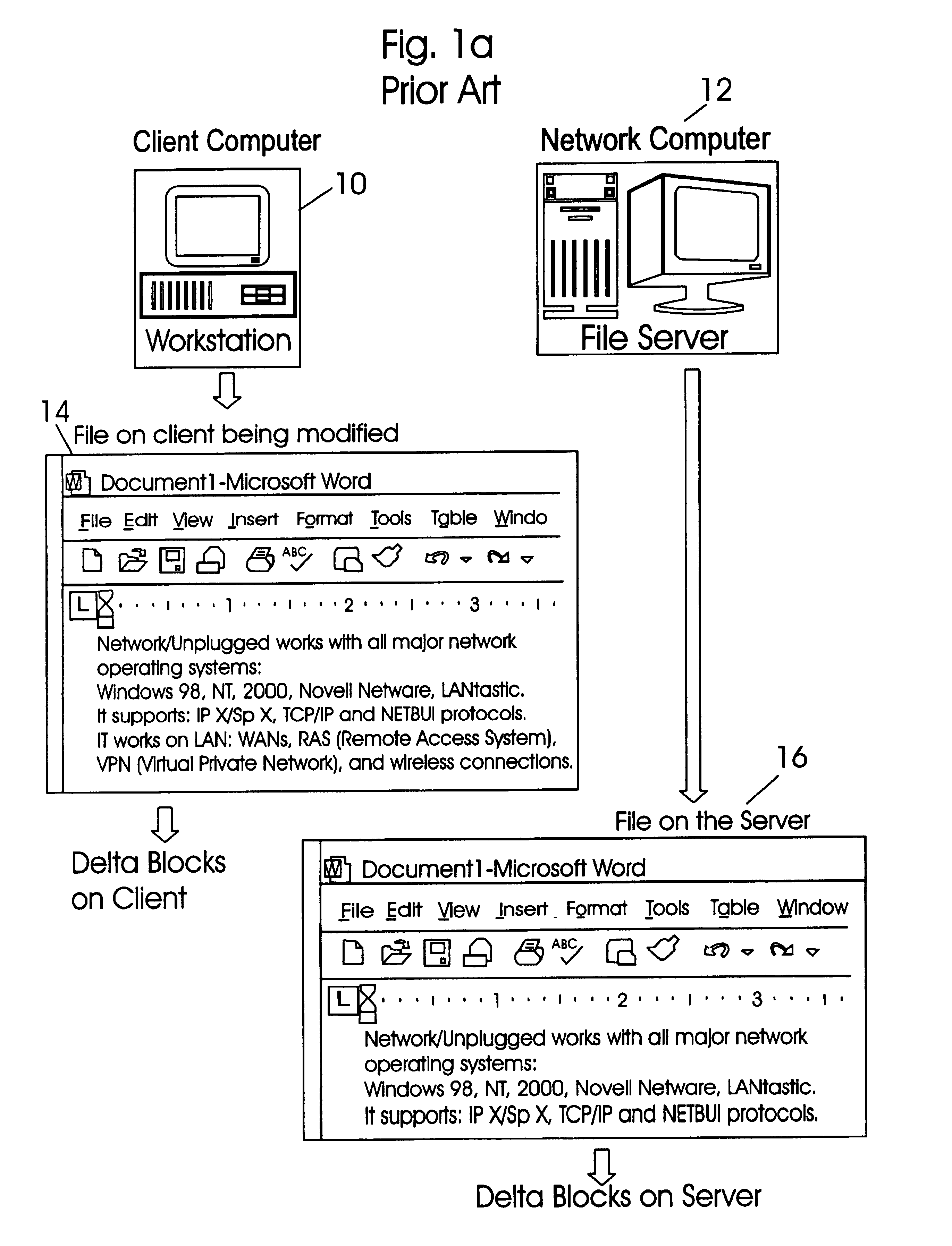
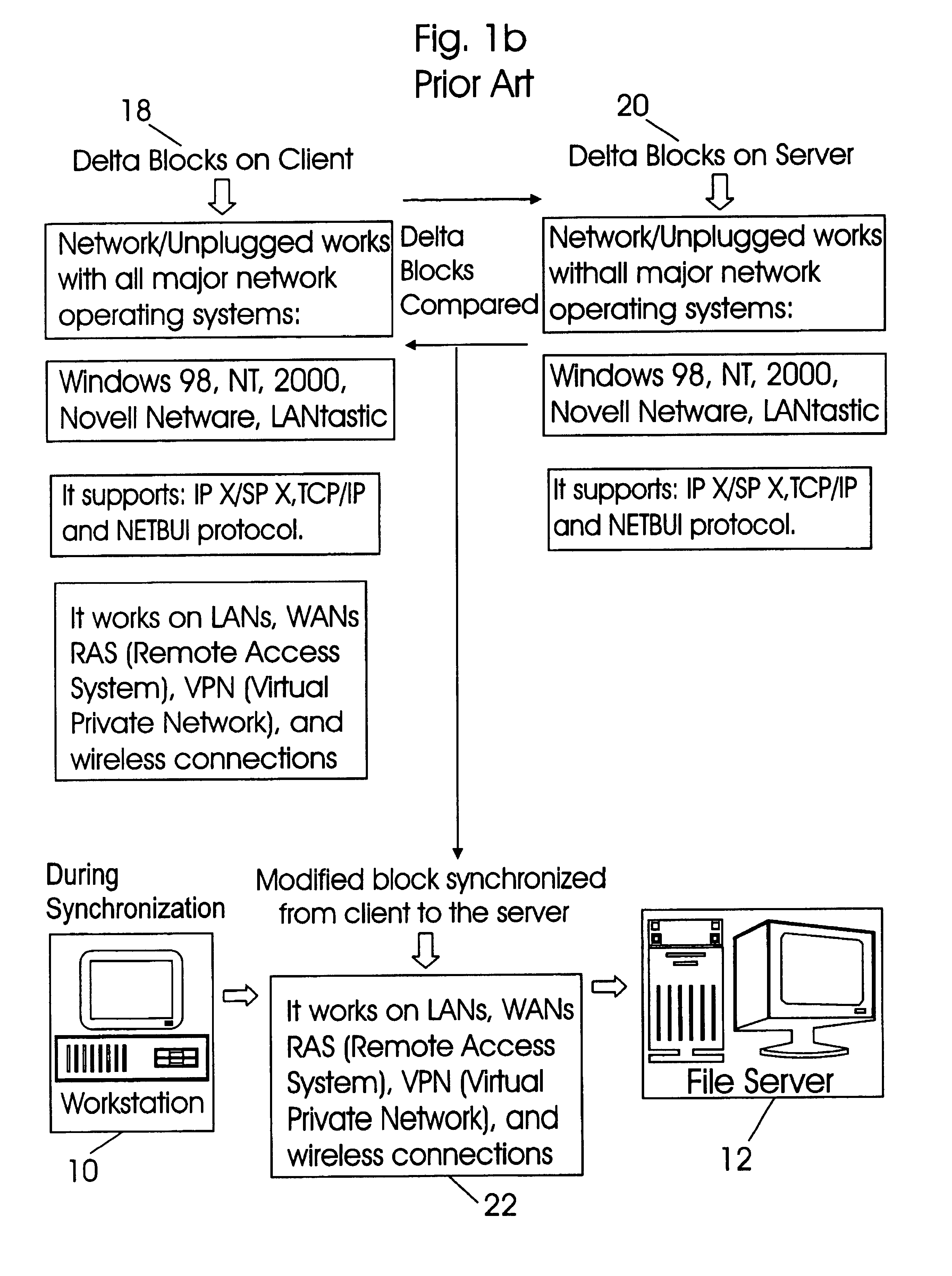
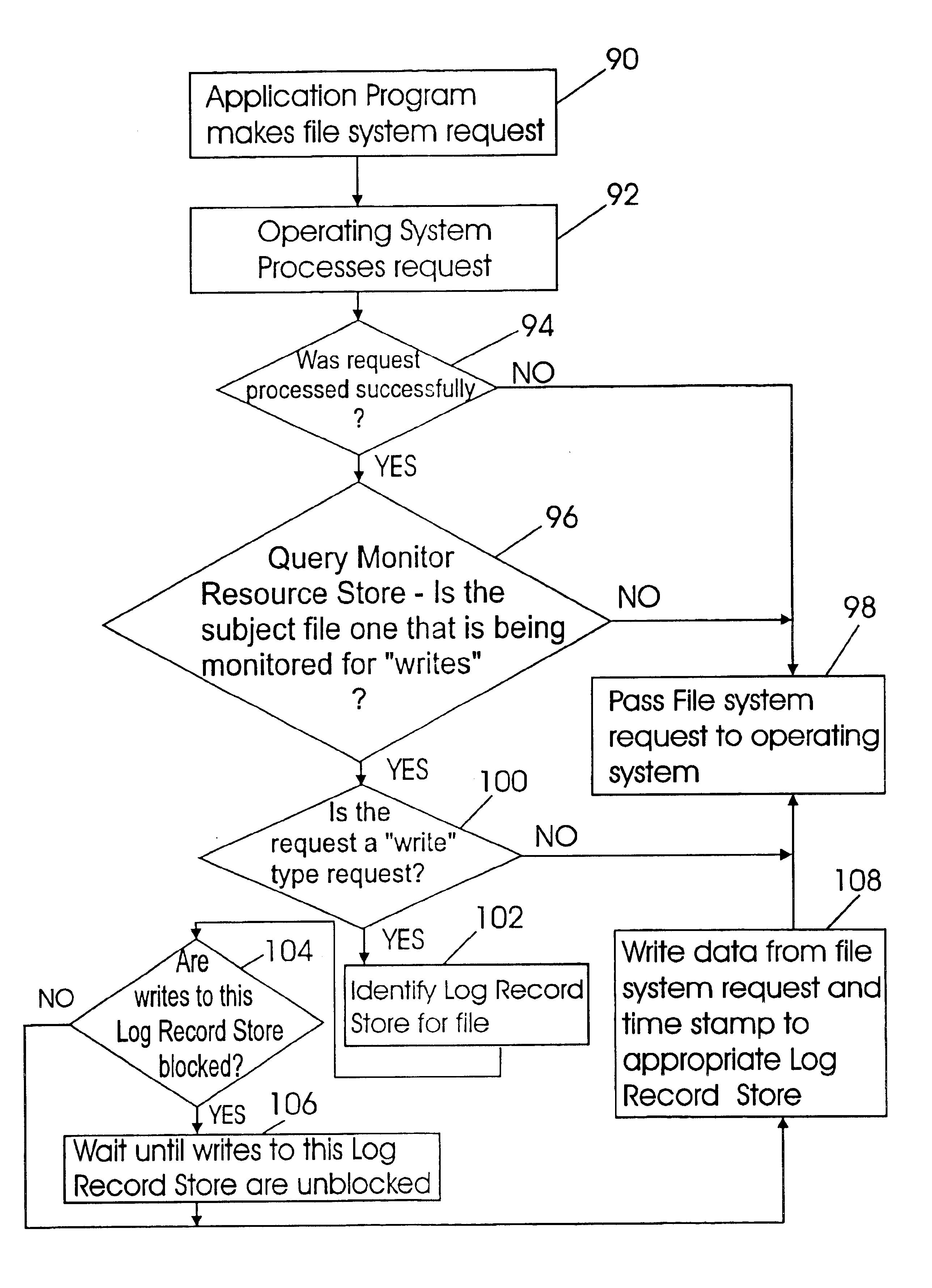
Application independent write monitoring method for fast backup and synchronization of files
InactiveUS6985915B2Reduce data transferReduce unit loadData processing applicationsDigital data information retrievalOperational systemFile system
A method for monitoring file system requests made by an application program, storing changes made to a first copy of a selected file by the application program into a first file and synchronizing the changes made to the selected file with a second copy of the selected file. The monitoring and storing process is application independent in that it is utilized by the operating system for all file system requests made by any application program. The monitoring and storing process is repeated each time a file system request is made by the application program to track changes made to the selected file. At the time of synchronization, if the application program is no longer modifying the selected file and the selected file is closed, all entries in the first file are applied to the second copy of the selected file. As a result, synchronization of both copies of the selected files is achieved.
Owner:CA TECH INC
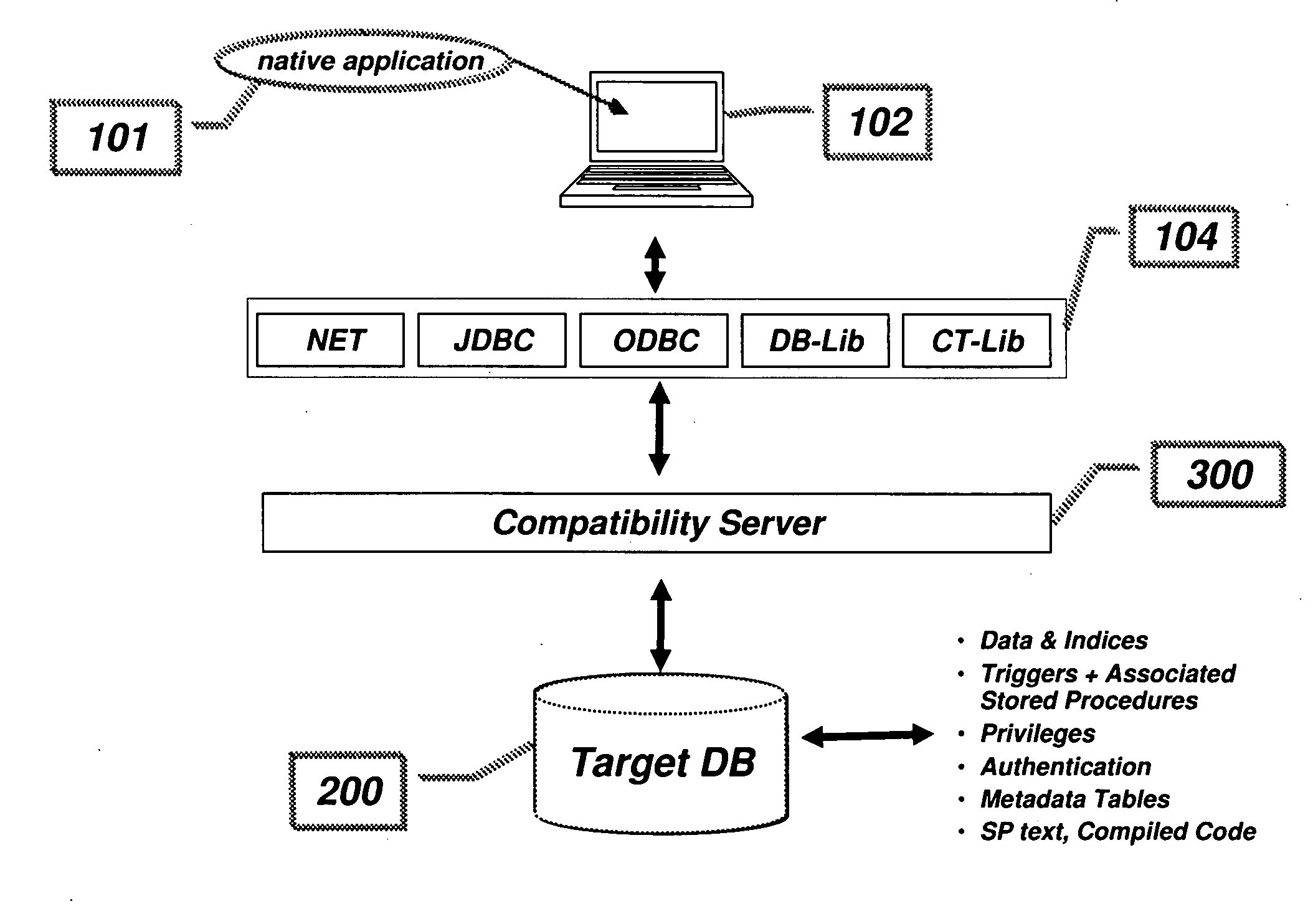
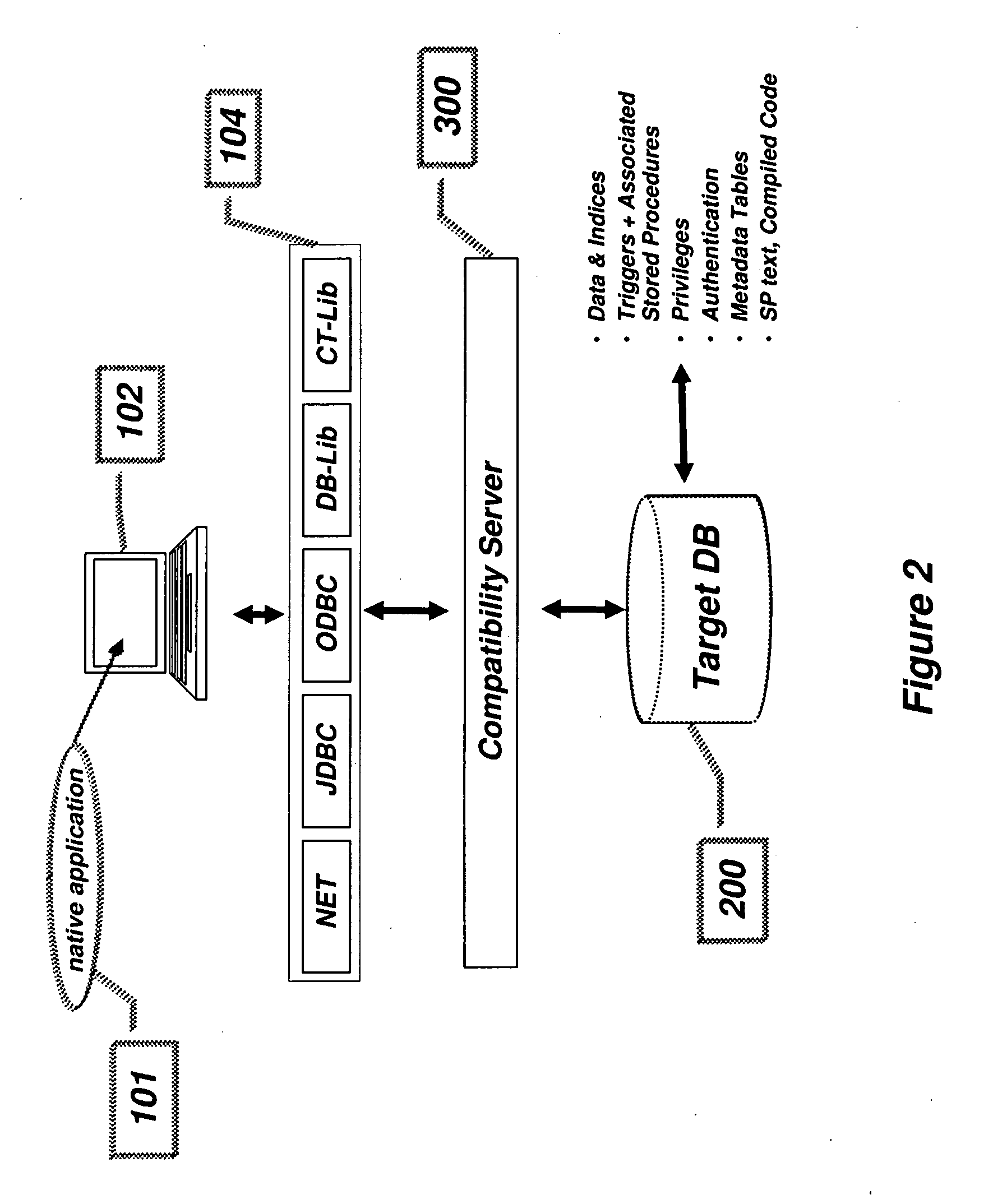
Compatibility Server for Database Rehosting
InactiveUS20100094838A1Digital data information retrievalDigital data processing detailsApplication programming interfaceDatabase application
A system and method describing a compatibility server for rehosting database applications written for a specific vendor's database on the database of a second vendor, without the need of rewriting the application to take into account differences in the application programming interfaces between the first vendor's database and the second vendor's database. Requests for access to the database are translated from one format to another at execution time. The server is also capable of translating error messages, data types and data formatting from the format used by the second database to that expected when making requests to the first database. Stored procedures defined in the first database are migrated to the second database as text blocks, and are translated at execution time into a high level programming language, compiled and executed against the second database. All information necessary for the mapping of schema, data, data types, error and status messages and data formatting, as well as information necessary to execute stored procedures, is stored in a plurality of metadata tables in the second database, which are created during a migration phase prior to executing the application.
Owner:ANTS SOFTWARE
System, method and software for creating or maintaining local or distributed mapping and transparent persistence of complex data objects and their data relationships
InactiveUS20080189240A1Database management systemsSpecial data processing applicationsSemi automaticProject management
The invention provides computer systems, computer data stores and methods and software for accessing and utilizing data stores. More particularly, the present invention provides systems, methods and software for creating or maintaining local or distributed mapping and optional transparent persistence of data objects, objects for stored procedures, complex data objects, data object graphs and associated data stores. The present invention further provides a computer system and software implemented method for a development mapping workspace for improved project management of mapping and persistence development activities along with a system implemented organization of mapping projects. In another aspect, the invention provides a computer system and software implemented methods for automatically mapping objects to one or more data source with an interface for setting variable stringency for such automatic mapping with an optional interface for editing the resulting system generated mapping, which system and software implemented methods may be collectively referred to as a “magic mapper” system. Further, such systems and software implemented methods are optionally integrated with IDEs, case tools and other third party platform or development environments to provide an extension of functionality or alternative functionality to such IDEs, third party platforms and other development environments, and to optionally provide for improved automatic or semi-automatic logic code generation.
Owner:MULLINS WARD R +1
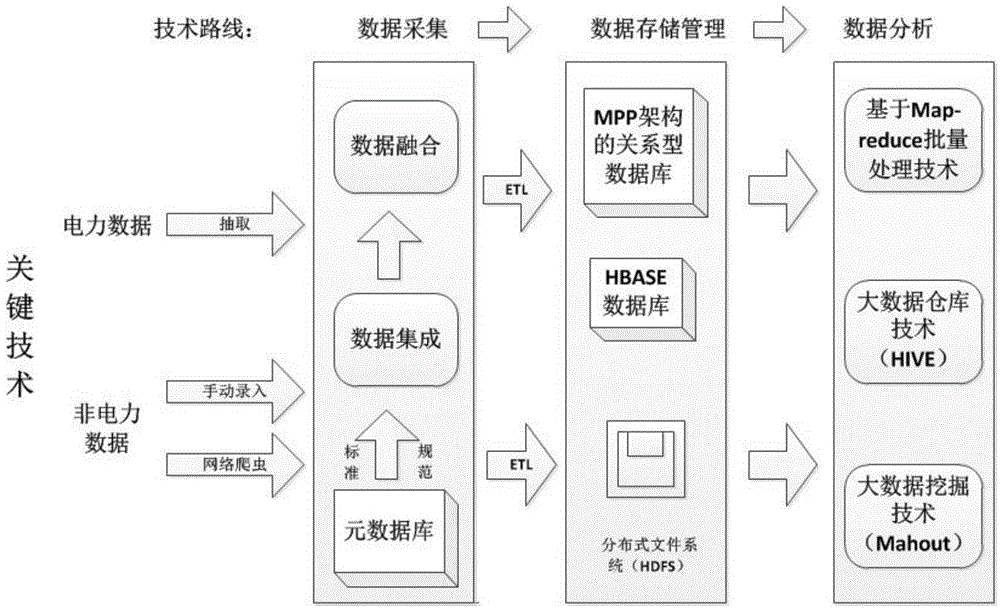
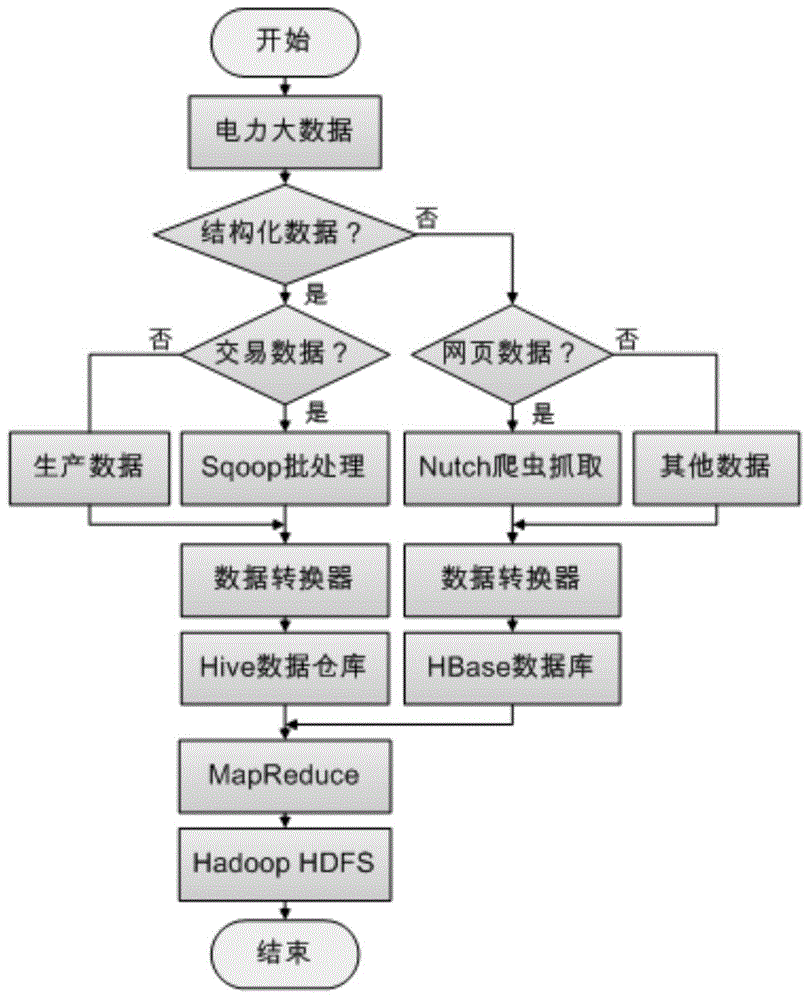
Method for acquiring and storing big data of power information
ActiveCN104820670AFunction is easy to expandGood analysis functionData processing applicationsSpecial data processing applicationsData acquisitionNetwork media
The present invention, belonging to the field of acquisition and storage of big data of power information, relates to a method for acquiring and storing the big data of power information, and solves the problems in the acquisition and storage process of the big data of power information. The method comprises three steps: data acquisition, data storage and management, and data analysis. The method achieves the beneficial effects that the present invention provides the method for acquiring and storing the power information big data; and the problems of low response speed of a service system and long consumed time for waiting of a user, which are generated due to a large cardinal number of power users and a large quantity of information, can be well solved. Meanwhile, for massive information generated by a trading system on the basis of power data, the method can better complete data extension and analysis functions than a traditional database. Moreover, according to the method, massive Internet media data can be acquired, stored and processed so as to better learn about the trade trend; and during the operation process, the storage method has an efficient inquiring function so that retrieval can be rapidly completed when the data volume is increased sharply.
Owner:CENT CHINA GRID +2
Low-downtime and zero-downtime upgrades of database-centric applications
ActiveUS20080098046A1Digital data information retrievalDigital data processing detailsDowntimeDatabase application
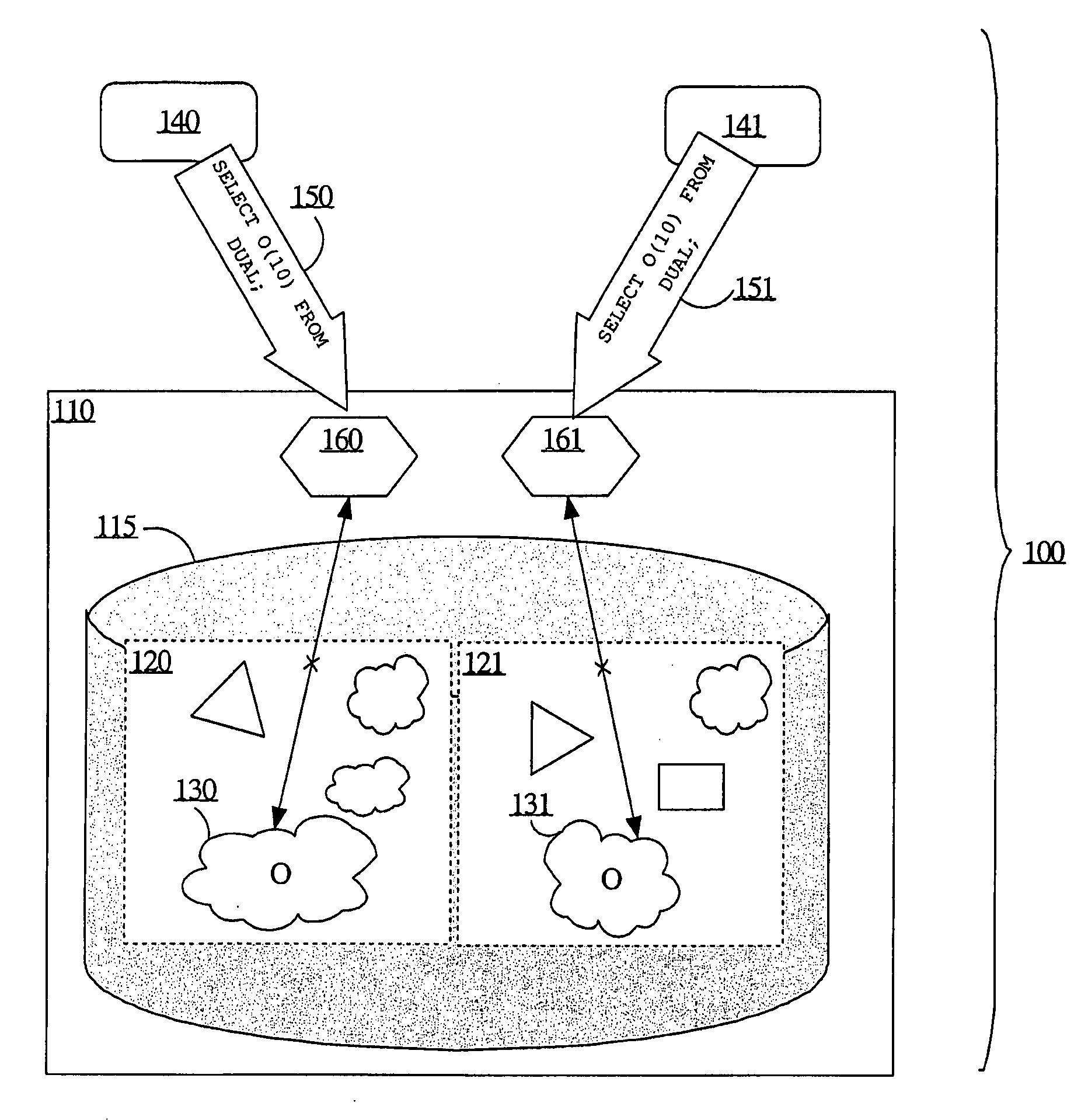
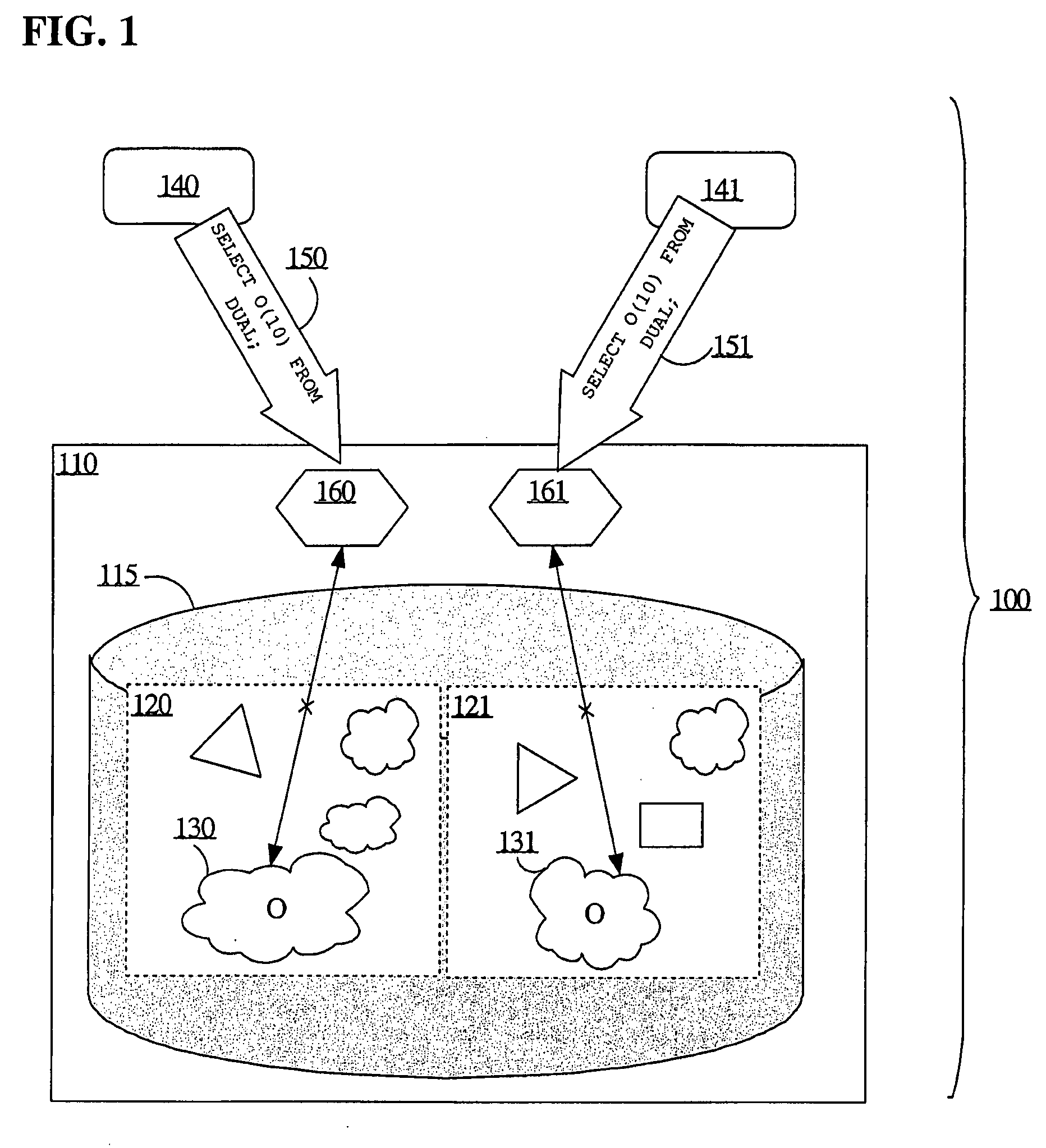
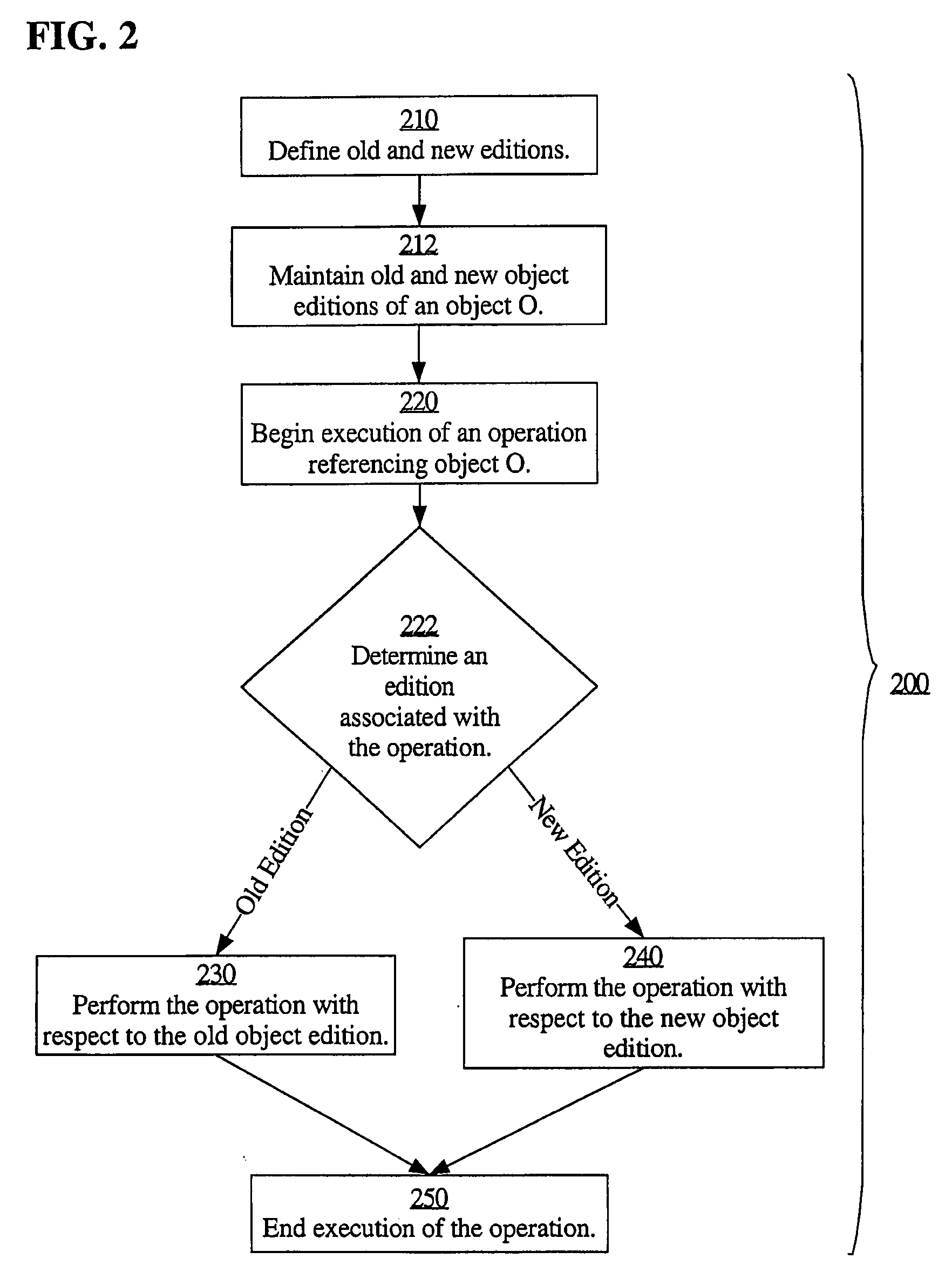
A database may facilitate zero-downtime upgrades by concurrently maintaining multiple editions of database objects for use by both pre-upgrade and post-upgrade clients of a database application. Operations performed within the database are associated with an edition based on, for example, an initiating client or transaction. When an operation references an object or data, the database automatically performs the operation using the object or data associated with the edition with which the operation is itself associated. The database may determine the associated edition without explicit identification of the associated edition in a query or in code. Thus, no client or stored procedure code changes are necessary to reflect a new edition added during an update. Data changes in one edition may be automatically and immediately propagated to the other edition through the use of cross-edition triggers, thereby allowing both pre-upgrade and post-upgrade clients to remain fully functional throughout an upgrade.
Owner:ORACLE INT CORP
Application independent write monitoring method for fast backup and synchronization of open files
InactiveUS6847983B2Reduce data transferReduce unit loadData processing applicationsInput/output to record carriersFile synchronizationFile system
An application independent method for monitoring file system requests made by any application program, storing changes made to a first copy of a selected file by the application program into a first file and synchronizing the selected file, whether the file is open or closed, with a second copy of the selected file. The monitoring and storing process is repeated each time a file system request to write into the selected file is made by the application program to track changes made to the selected file. At the time of synchronization, if the selected file is closed, all the changes that are stored in the first file are applied to a second copy of the selected file. If, however, the selected file is open, a portion of the changes are selected pursuant to a predetermined time period and applied to a second copy of the selected file. As a result, both copies of the selected files are identical, thereby synchronizing them. For open files, both copies of the selected file are identical up to the predetermined time period.
Owner:CA TECH INC
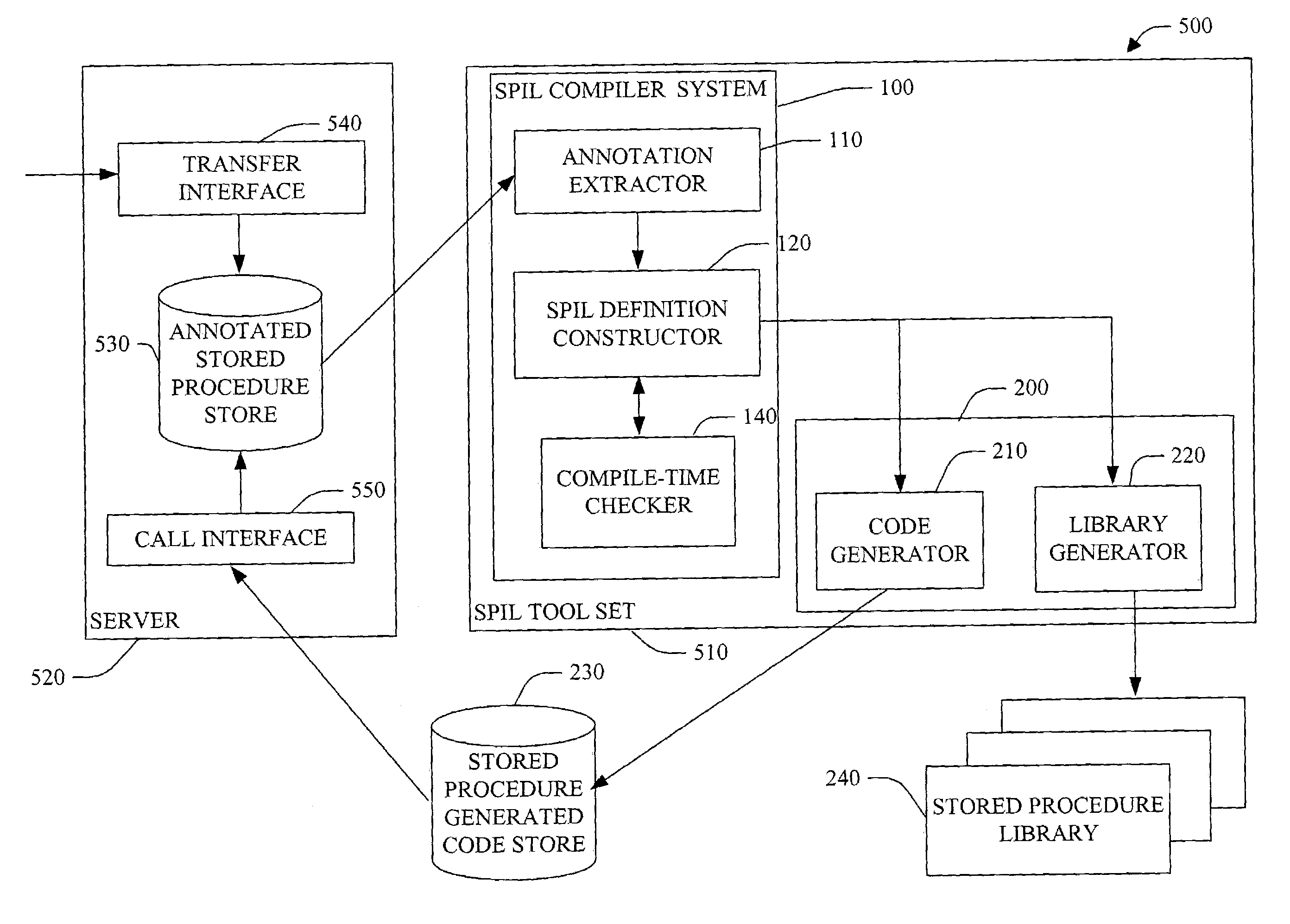
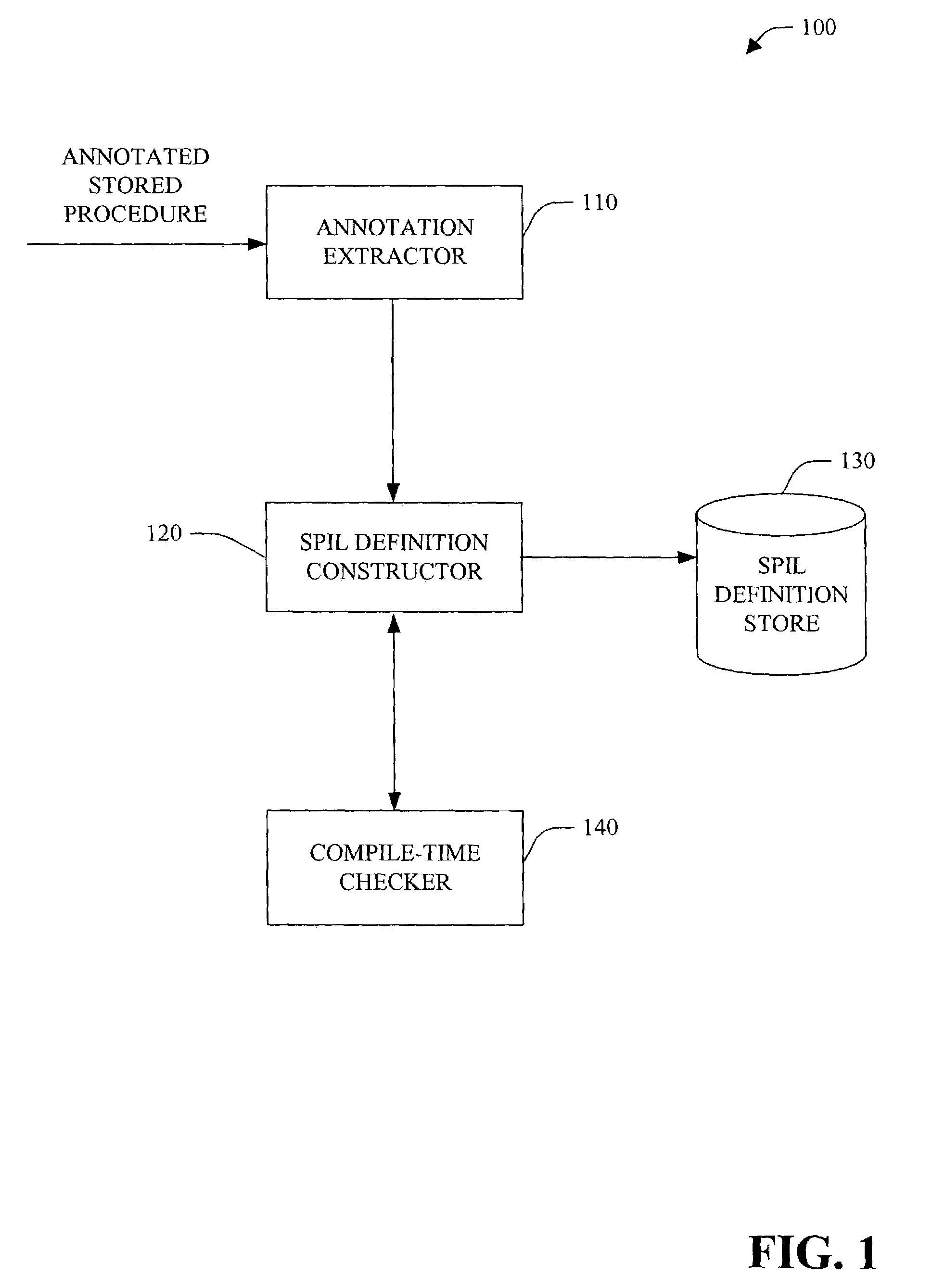
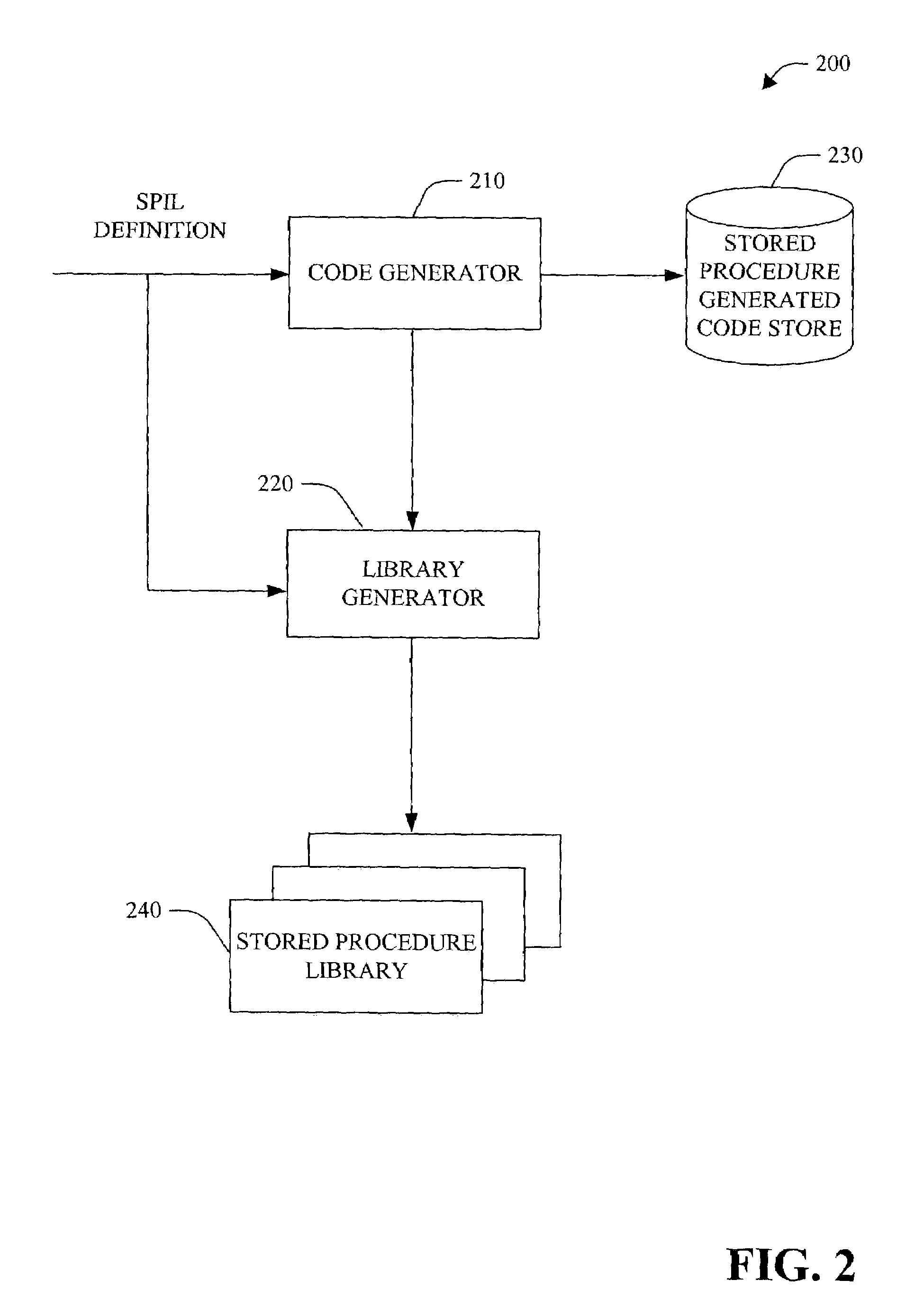
Stored procedure interface language and tools
InactiveUS7318215B1Reduce developmentReduce debuggingData processing applicationsDigital data processing detailsProcedure callsApplication software
The present invention relates to systems and methods to generate stored procedure calling code. The invention includes system and methods that utilize annotation(s) included in a stored procedure. The annotations comprise attributes that indicate the intent to have stored procedure calling code generated. After the annotated stored procedure becomes available, the code is compiled and, optionally, checked for errors, and an intermediate definition with metadata is created. The definition is a stored procedure interface language (SPIL) file. The SPIL definition is then utilized to generate high-level, stored procedure calling code, or class libraries. The high level code can then be employed within an application to invoke the stored procedure.
Owner:MICROSOFT TECH LICENSING LLC
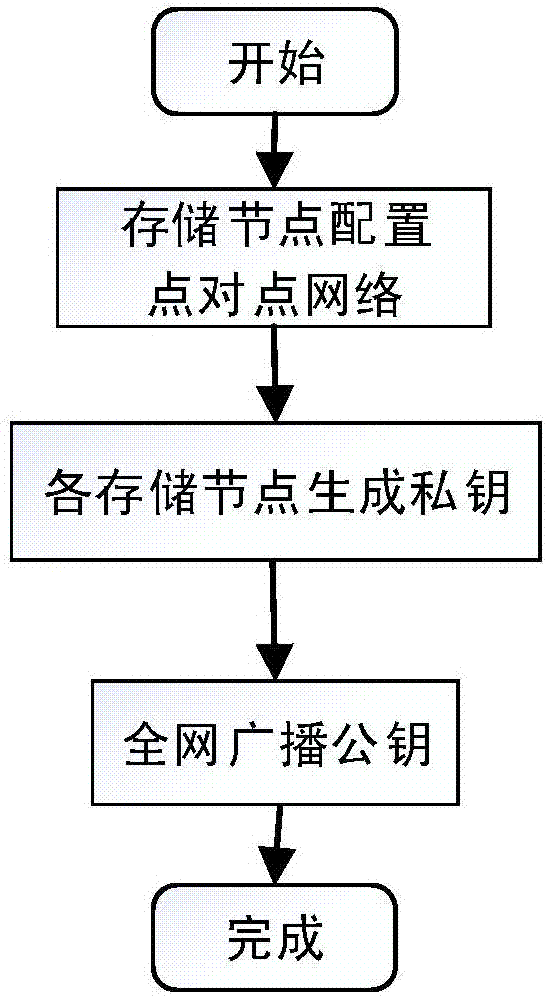
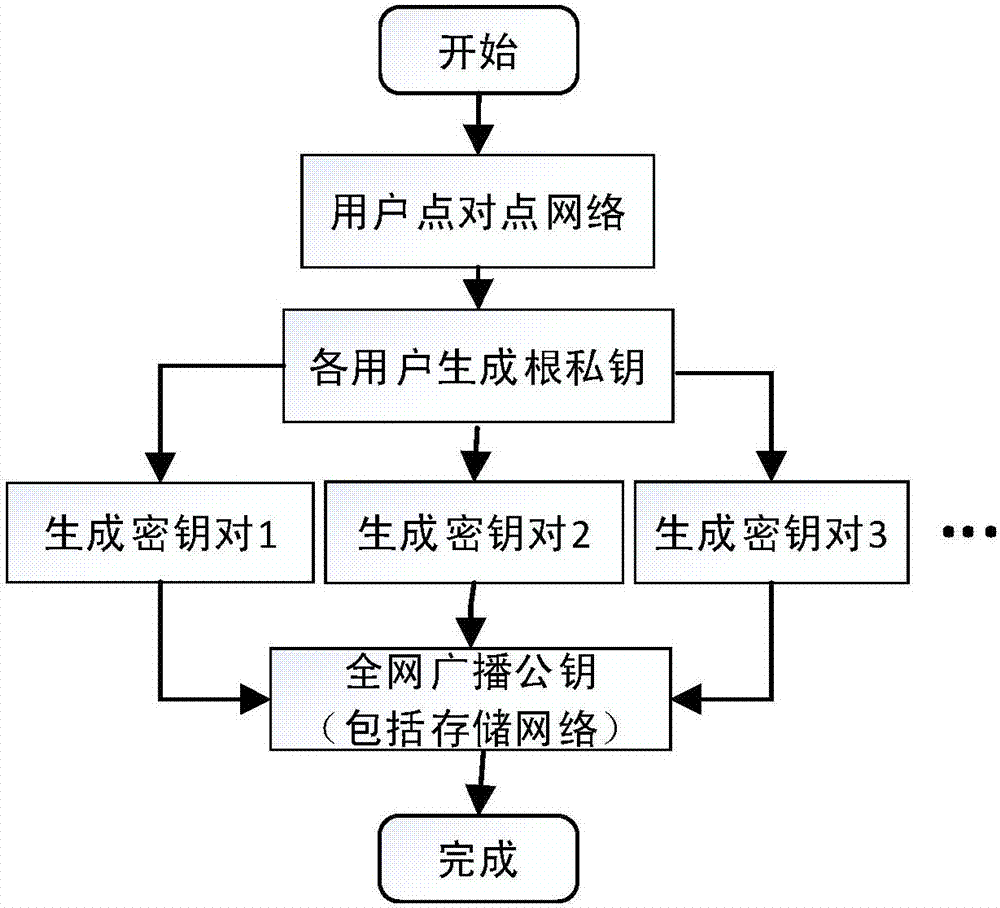
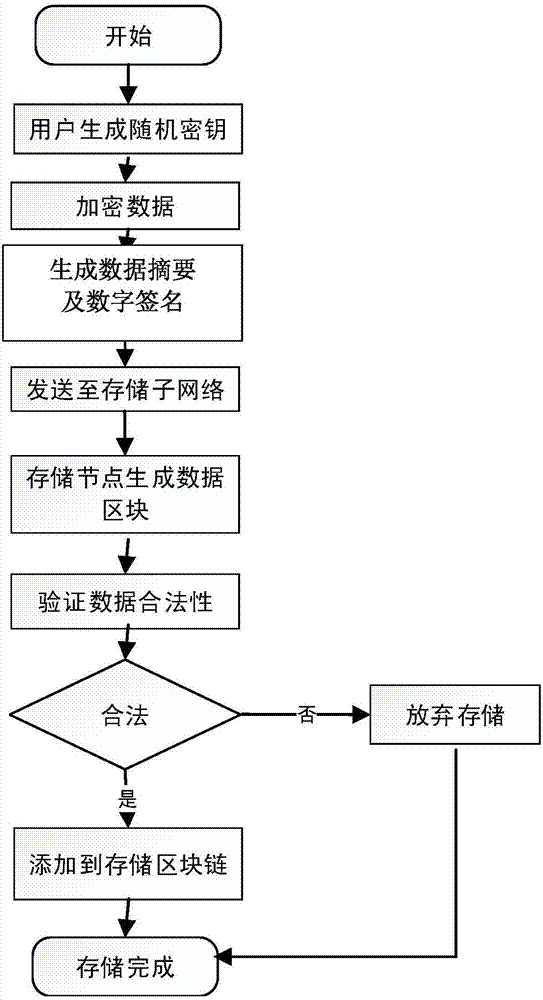
Routing position data secrecy storing and sharing method based on block chain
ActiveCN107181599AGood data protectionSolve workload bottlenecksKey distribution for secure communicationUser identity/authority verificationByzantine fault toleranceOriginal data
Provided is a routing position data secrecy storing and sharing method based on block chains. The routing position data secrecy storing and sharing method includes a data storing method and a data sharing method. The data storing method includes the steps of node configuration, data encryption sending, storage subnetwork verification storing, etc. The data sharing method includes the steps of demand generation, demand response, sharing achievement and the like. The effects of the invention are as follows: through a block chain technology, data sharing is realized through data encryption storage and a decentralized network to solve the problems that data storage parties have no right to use data and users do not have channels to selectively enable personal data to be accessed; local encryption sending is adopted during data storage, service parties store encrypted data, the users themselves save decryption secret keys, and the service parties have no access to original data, so a better data protection effect is achieved; and the block chain technology is adopted during storage, commonly recognized storage is realized through a practical Byzantine fault-tolerant algorithm, workload bottleneck problems of centralized storage are solved, and data is prevented from being tampered.
Owner:TIANJIN UNIVERSITY OF TECHNOLOGY
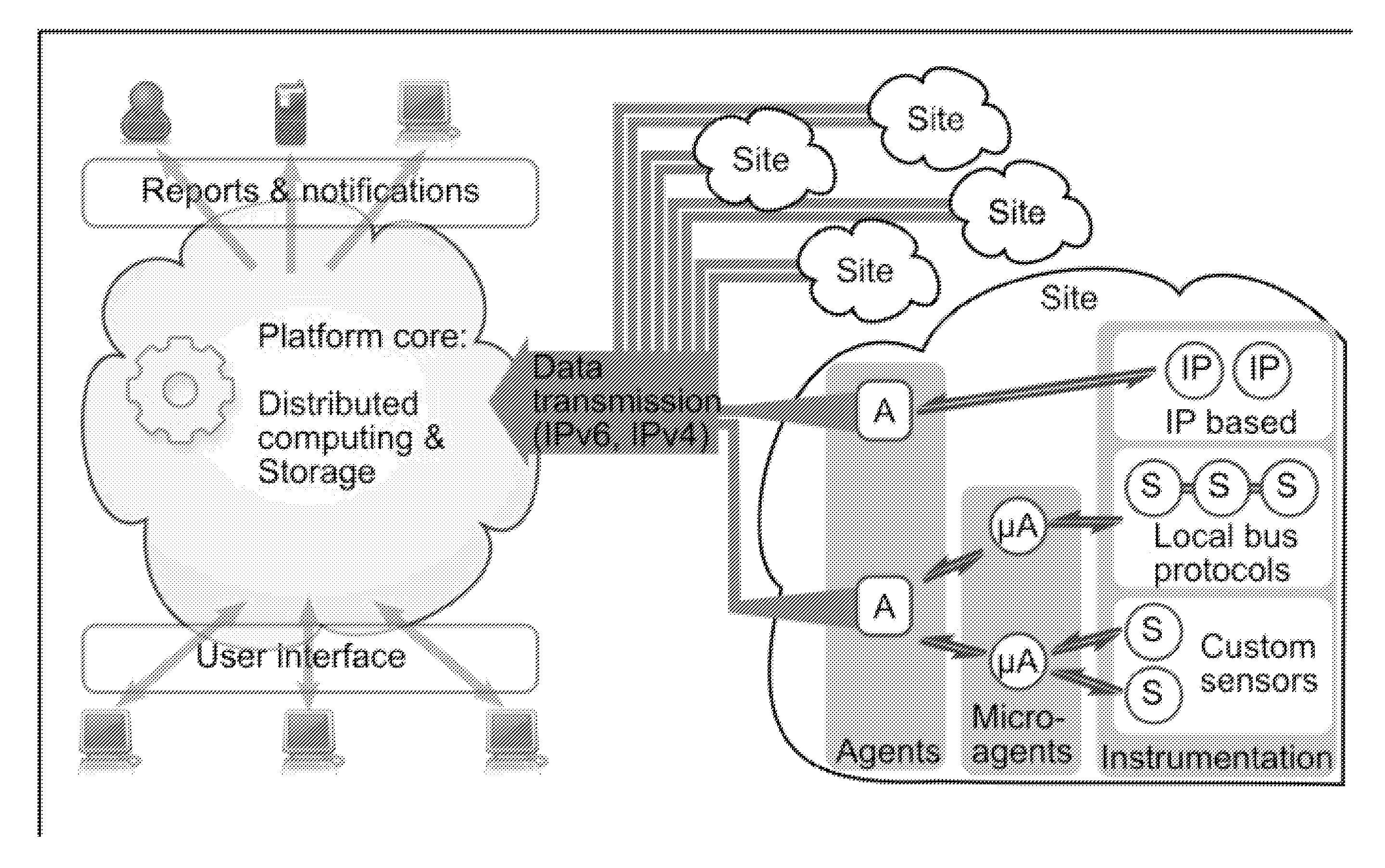
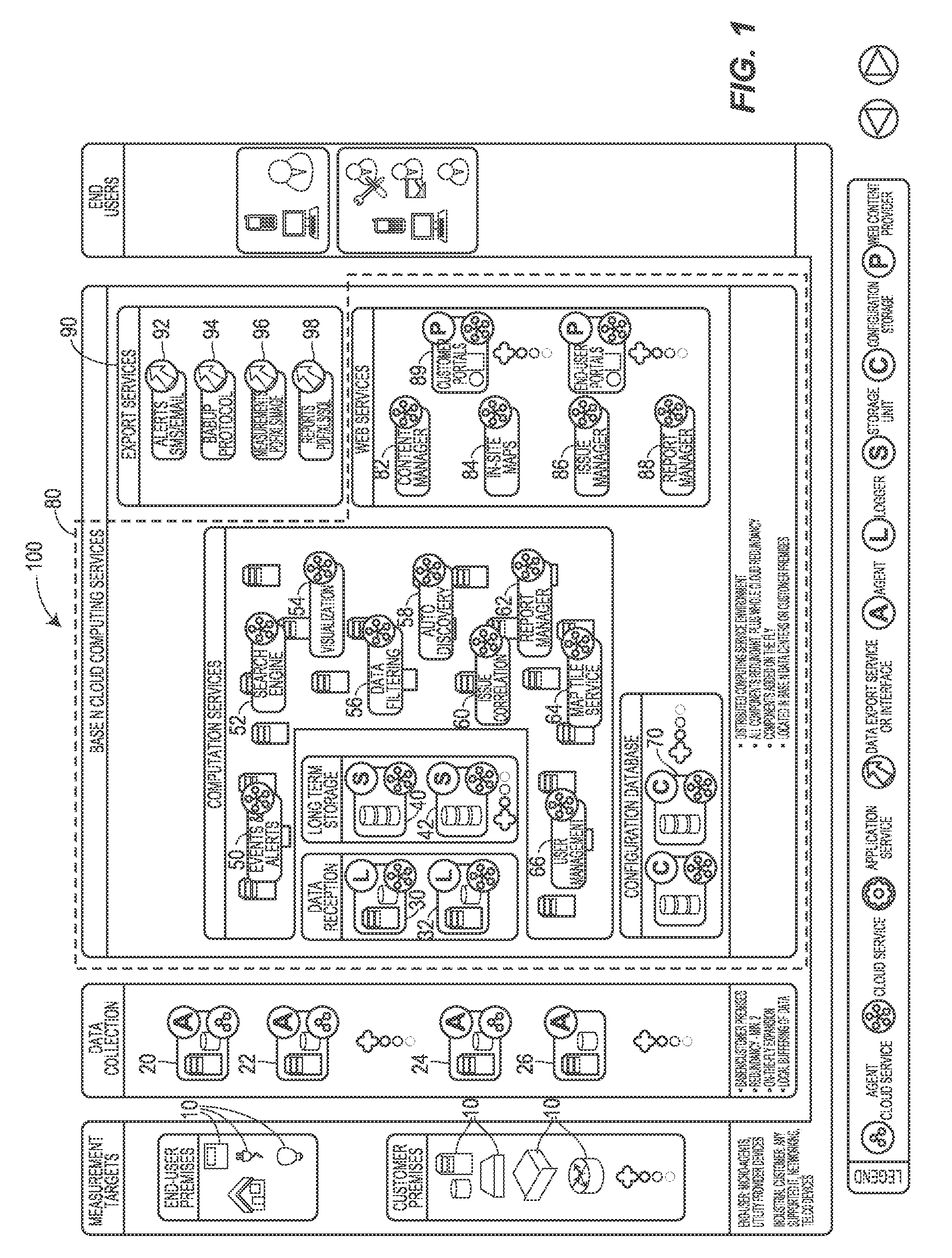
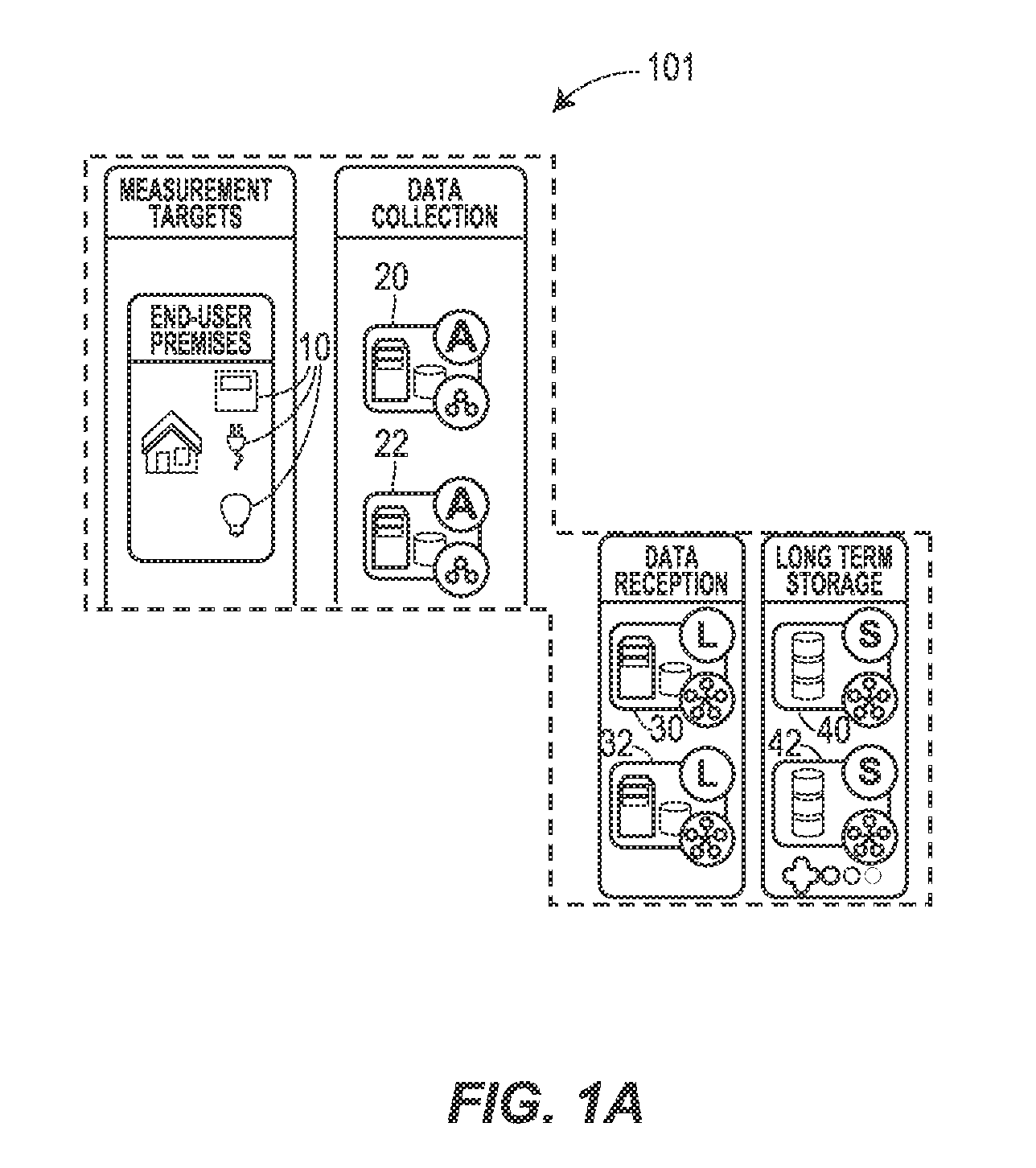
Smartgrid Energy-Usage-Data Storage and Presentation Systems, Devices, Protocol, and Processes Including a Visualization, and Load Fingerprinting Process
This disclosure relates to systems, devices, protocols, and processes for retrieving, accessing, and presenting information of energy usage using a distributed storage process and distributed logical services to provide a user with real-time energy usage information and visualization.
Owner:BASEN CORP
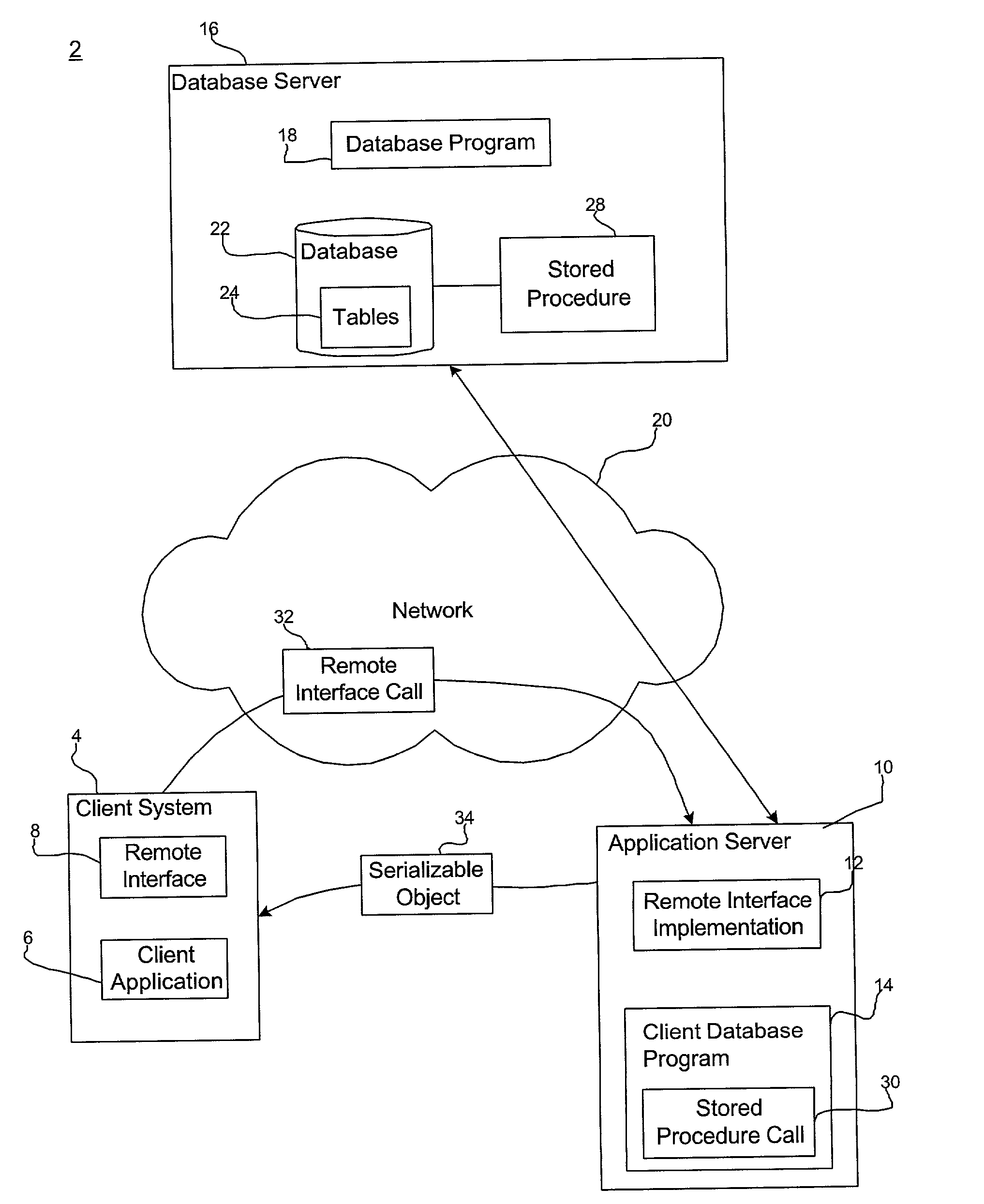
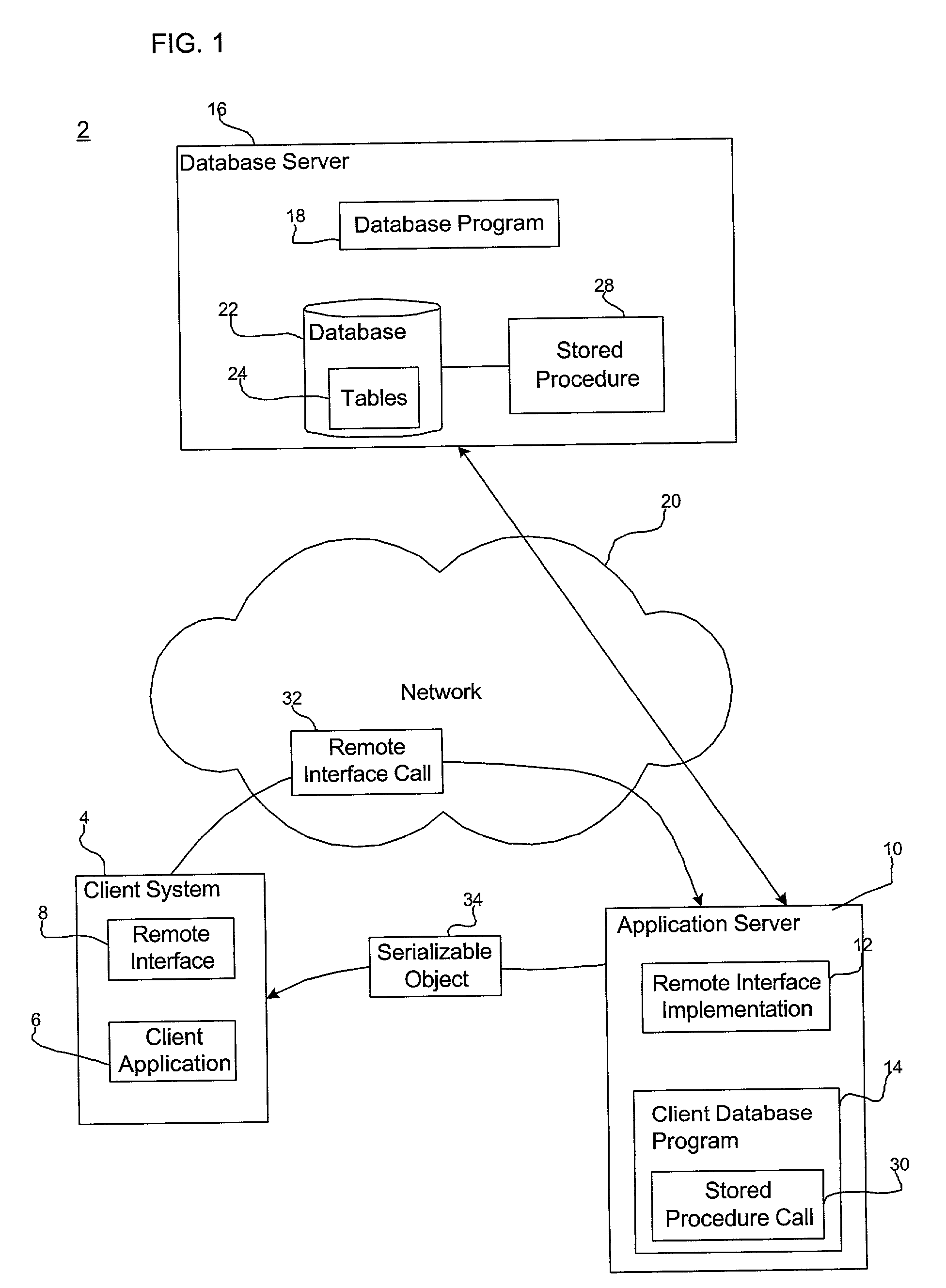
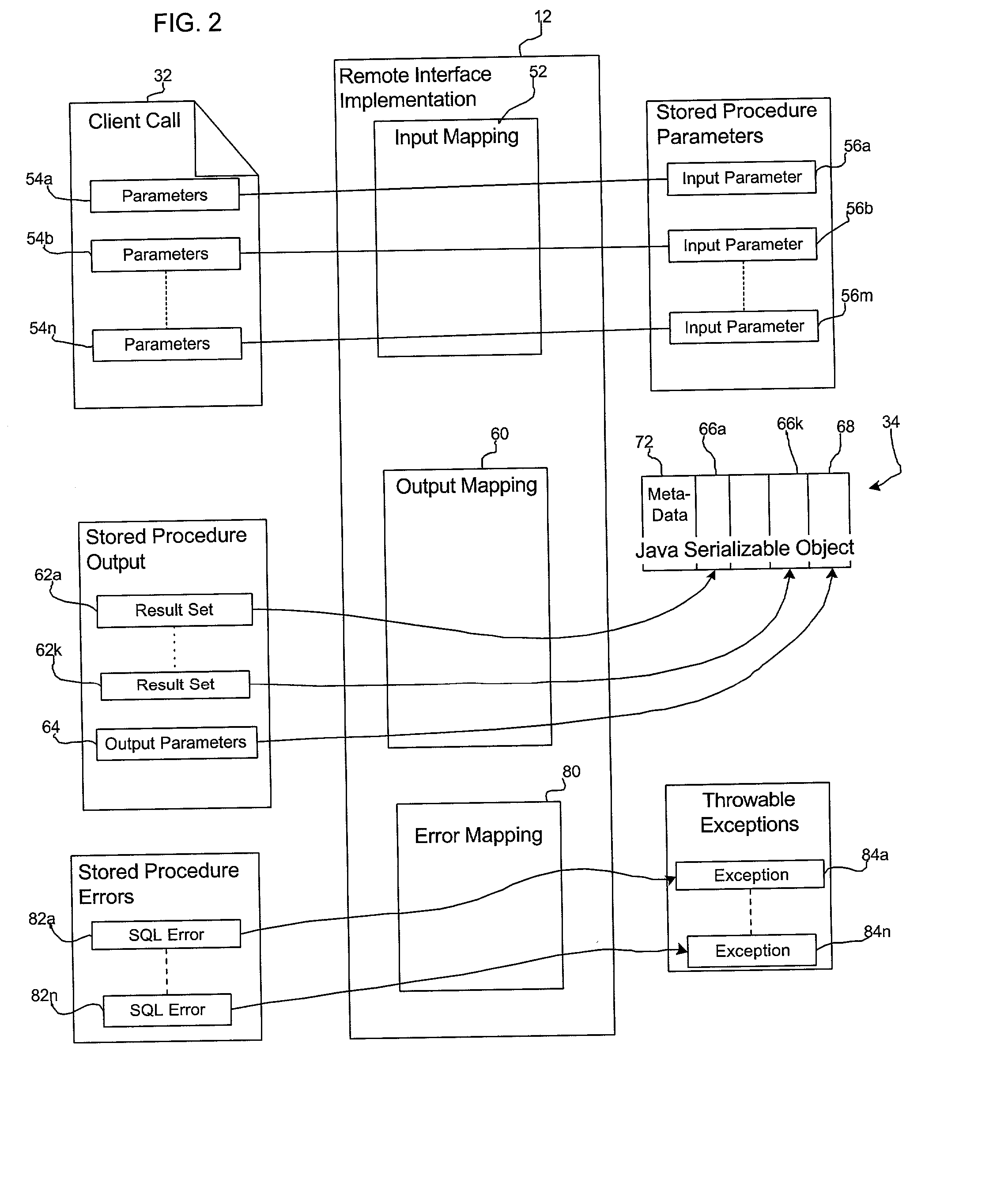
Method, system, and program for invoking stored procedures and accessing stored procedure data
InactiveUS20020016814A1Avoid the needMultiple digital computer combinationsDistributed object oriented systemsClient-sideStored procedure
Provided is a method, system, and program for enabling access to data. A call is received from a client to invoke a remote interface method. A remote interface implementation accesses parameters from the received call in response to the invocation of the remote interface method. A stored procedure call is generated with the accessed parameters as input parameters of the stored procedure. The stored procedure call is transferred to a stored procedure named by the call to execute. Output from the stored procedure is received and inserted into a data object that is returned to the client.
Owner:IBM CORP
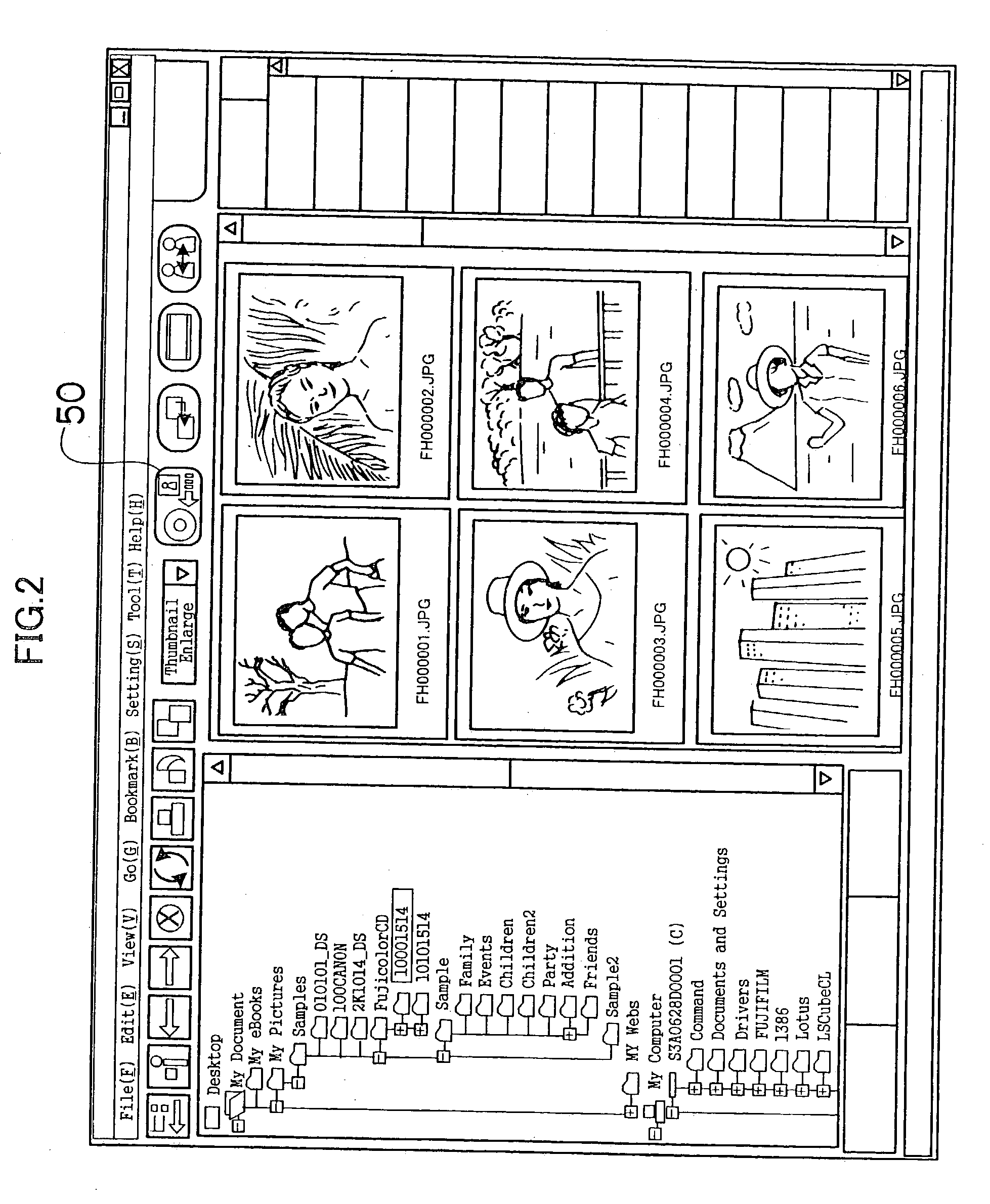
Album generation program and apparatus and file display apparatus
InactiveUS20030142953A1Optimized storage medium to be browsedTelevision system detailsElectronic editing digitised analogue information signalsRecordable CDStored procedure
A computer is directed to select one or more folders containing an image file on at least one of the lower hierarchical levels, and record an image file contained in and below the selected folders on a CD-R when a storing process is specified, and generates a CD album. The album generation program sequentially searches folders having an image file immediately below the folders when the image file is recorded on the CD-R, generates a new folder for the folder having an image file immediately below the folder, and copies a target image file as a new image file in the new folder, thereby giving a folder name and a file name automatically generated according to DCF rule to the stored new folder and new image file.
Owner:FUJIFILM CORP
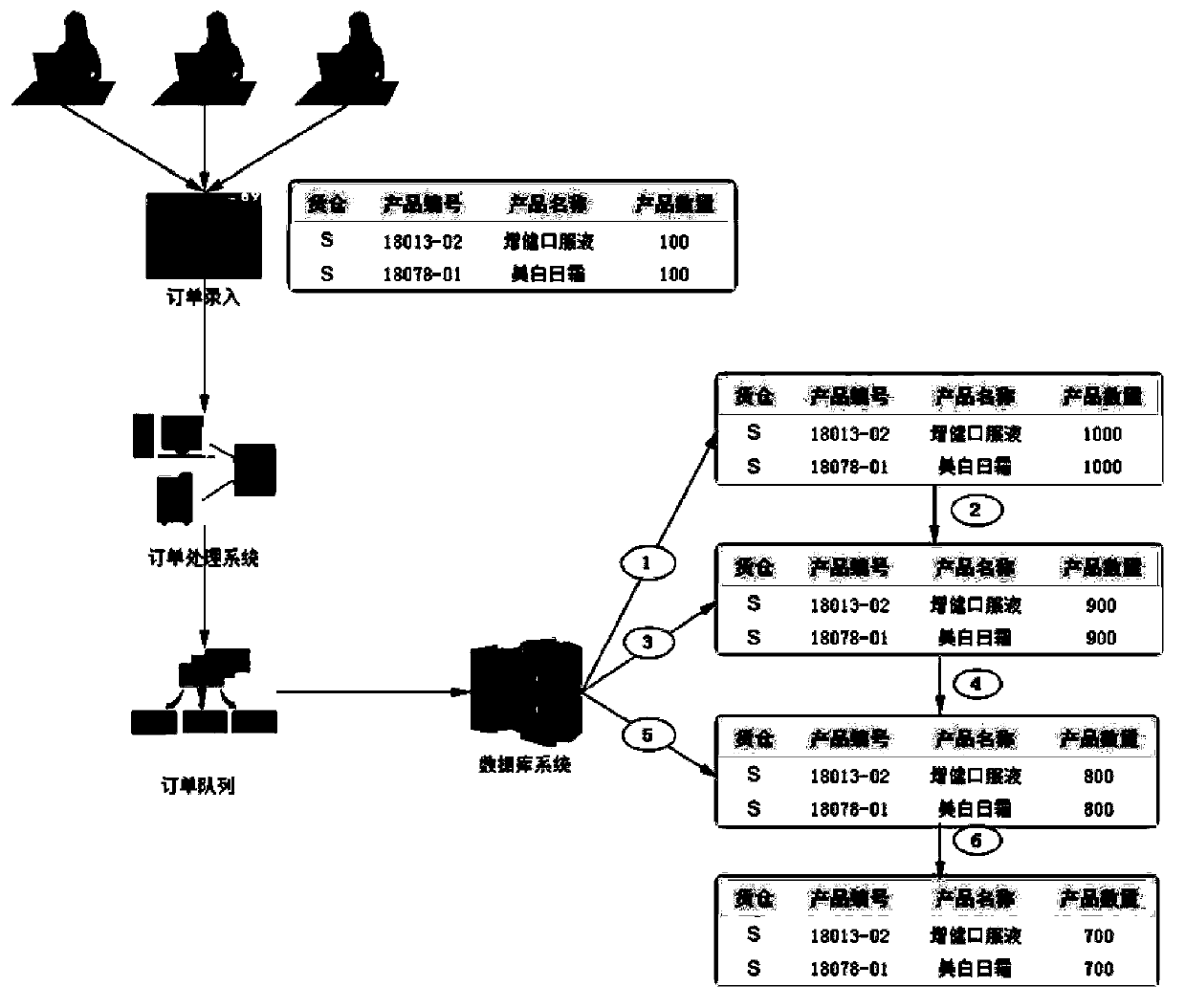
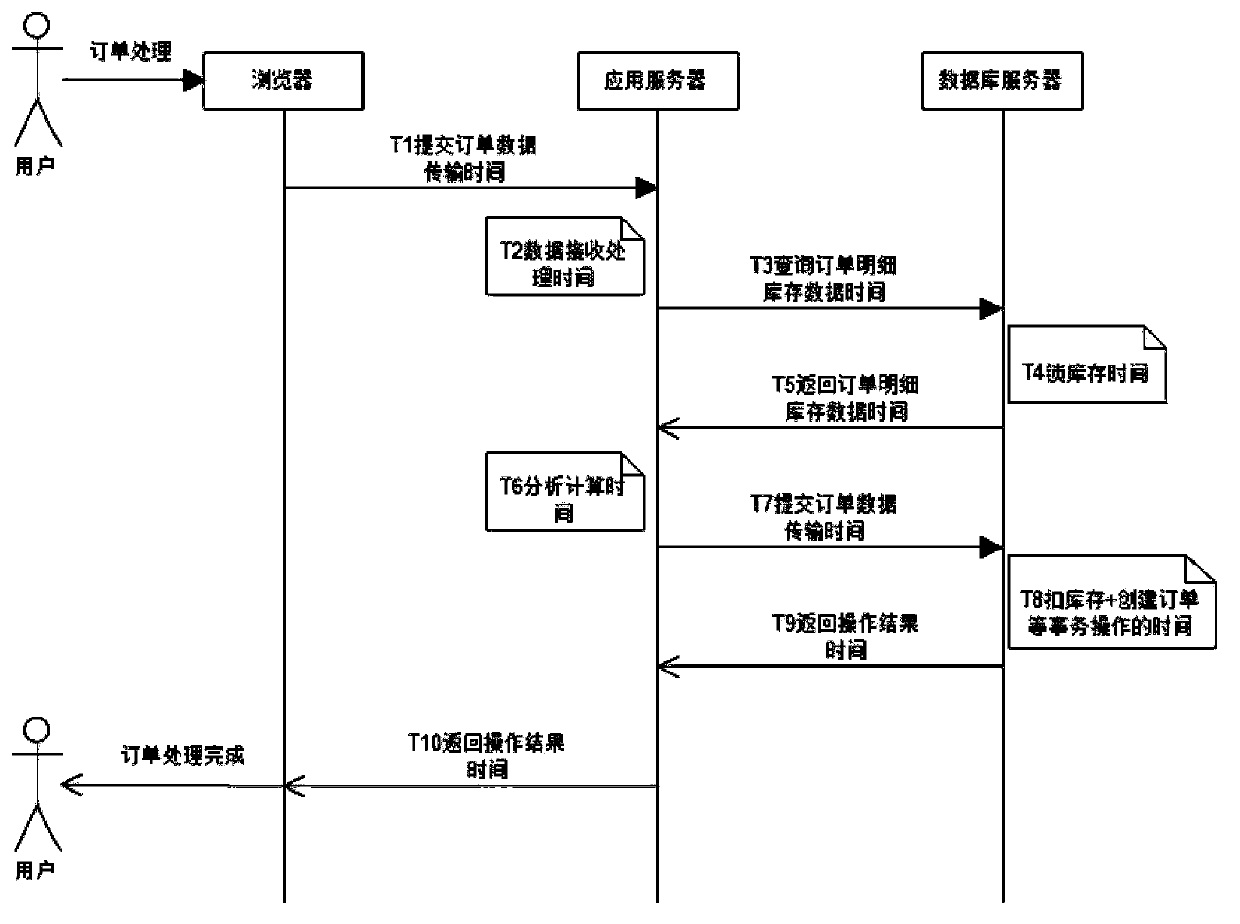
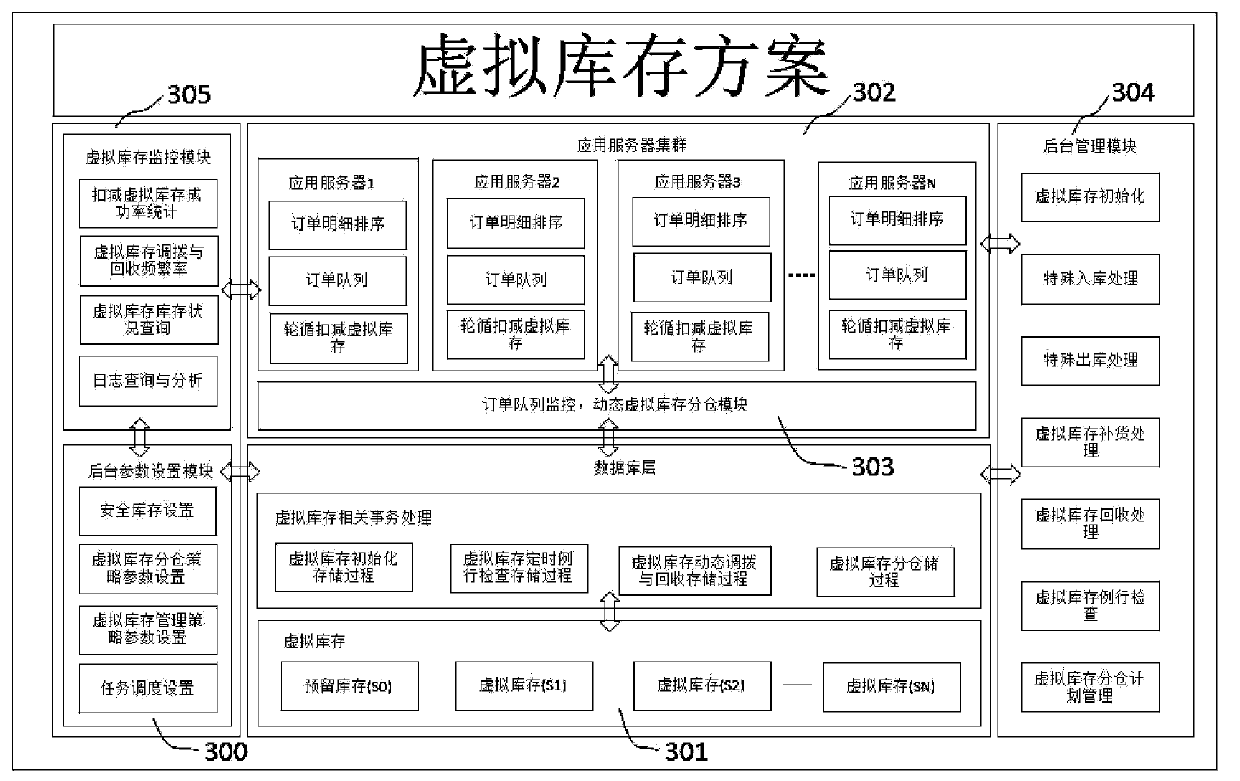
Order processing system of high concurrency competitive inventory and processing method thereof
ActiveCN103426072ASolve processing performance bottlenecksImprove concurrent order processing capabilitiesLogisticsInformation technology support systemProcess systemsApplication server
The invention discloses an order processing system of high concurrency competitive inventory and a processing method thereof. The order processing system of the high concurrency competitive inventory comprises a virtual inventory background parameter setting module, a database layer stored procedure function module, an application server cluster, an order queue monitoring and dynamic virtual inventory storehouse classifying module, a virtual inventory background management module and a virtual inventory monitoring module. Whether to deduct the inventory of a reserved warehouse or to deduct the inventory of a virtual warehouse in an order in the order processing transactional queue is determined, if the inventory of the virtual warehouse is enough, the deduction of the inventory of the virtual warehouse is selected, a counter is selected through the virtual warehouse and the virtual warehouse is distributed to every order in a round-robin mode, inventory deduction operation is performed according to the distributed virtual warehouse through the order, after the inventory deduction succeeds, meanwhile, relative data of the order in the order processing transactional queue is deleted, and information about the success creation of the order is returned to a user. According to the order processing system of the high concurrency competitive inventory and the processing method thereof, the number of virtual warehouses and the inventory of every virtual warehouse can be adjusted dynamically, the concurrent order processing capacity is greatly improved under the condition of existing software and hardware resources, and the order processing efficiency of high concurrency competitive inventory is improved.
Owner:INFINITUS (CHINA) CO LTD
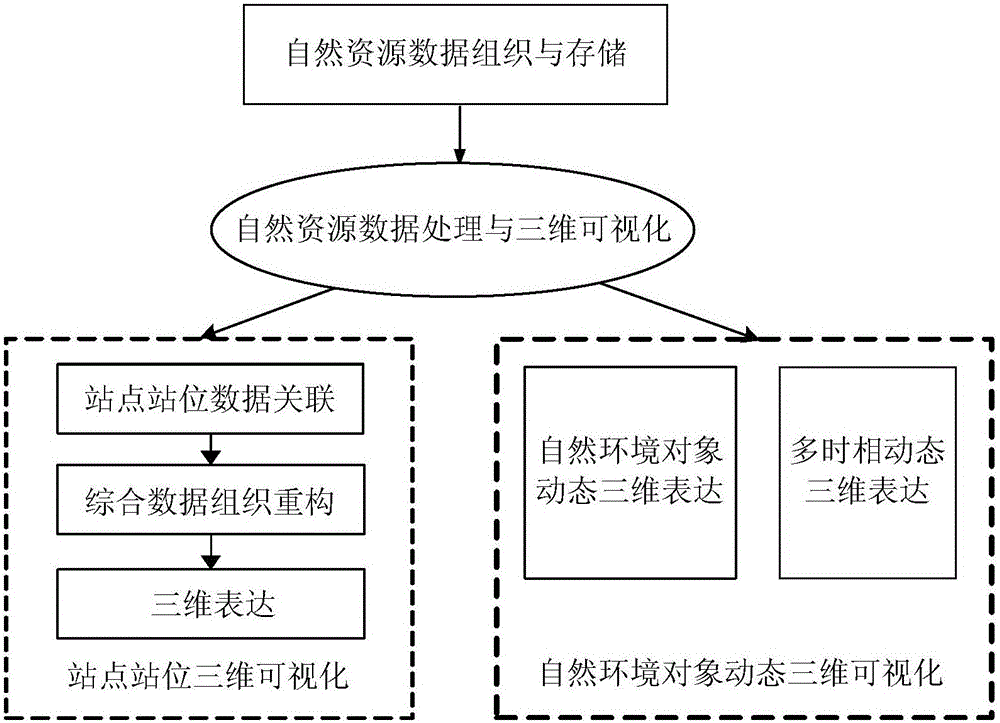
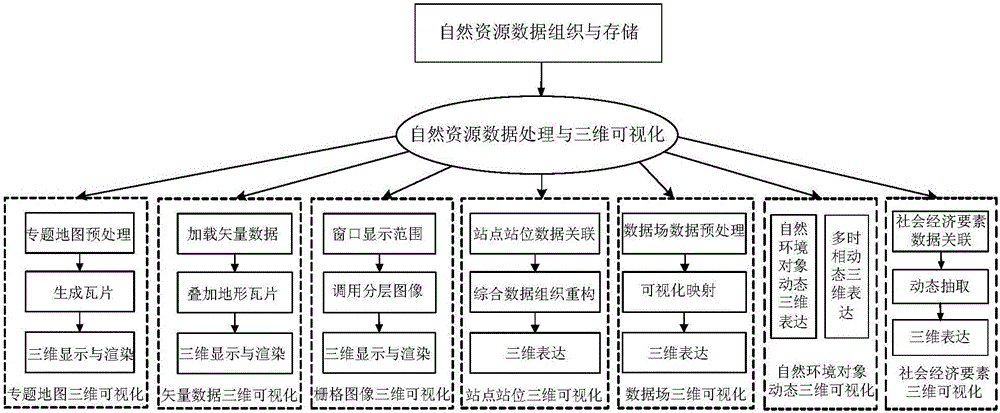
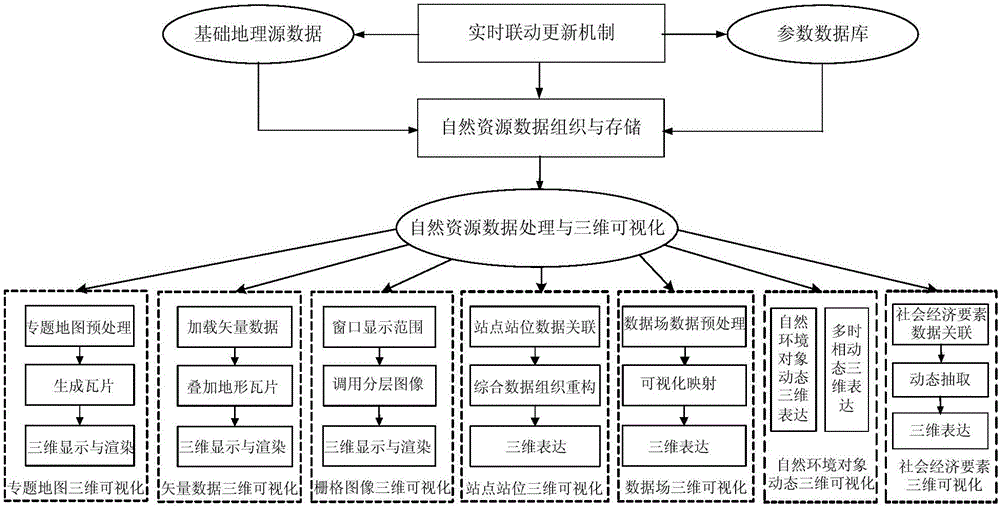
3D visualization method and system of natural resource data
InactiveCN105069020AReal-time online 3D rendering displayRealize high-performance 3D visualization expressionGeographical information databasesOther databases browsing/visualisationData setEmbedded database
The present invention relates to an on line 3D visualization method and system of natural resource data. The method mainly includes a step of natural resource data organization and storage and a step of natural resource data processing and 3D visualization. The step of natural resource data organization and storage includes: according to natural resource data characteristics and service characteristics, dividing data types, and making the natural resource data as tile image data formed by a plurality of tiles by adopting a pyramid model, then encoding each tile, and establishing a tile data set based on an embedded database technology, storing the tile data set in database, and establishing a quadtree index of space for each tile. The step of natural resource data processing and 3D visualization includes site and position 3D visualization and natural environment object dynamic 3D visualization. The method achieves real time on line 3D rendering display for all kinds of natural resources and geographic space information data in a high-performance 3D visualization environment.
Owner:国家信息中心
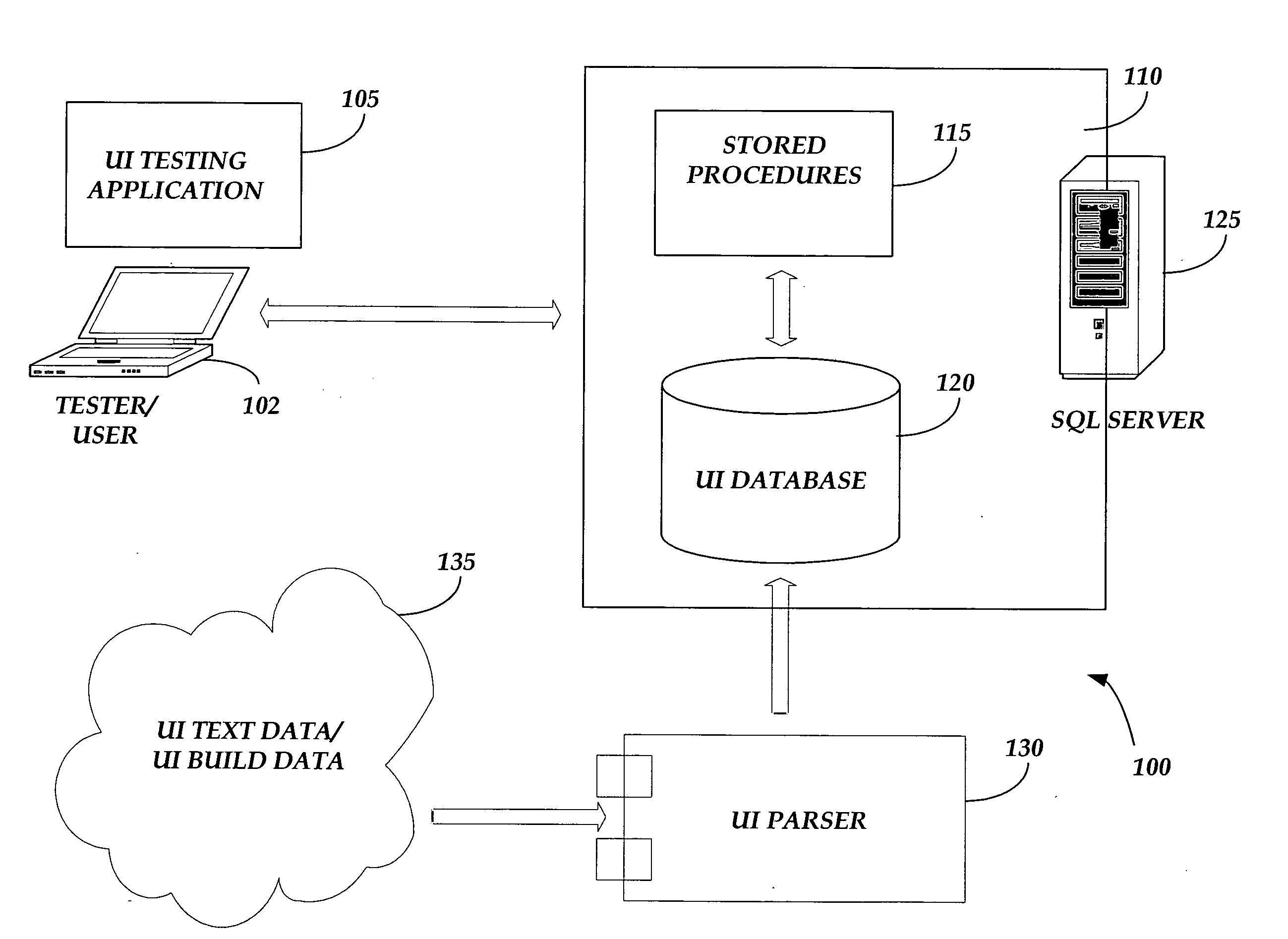
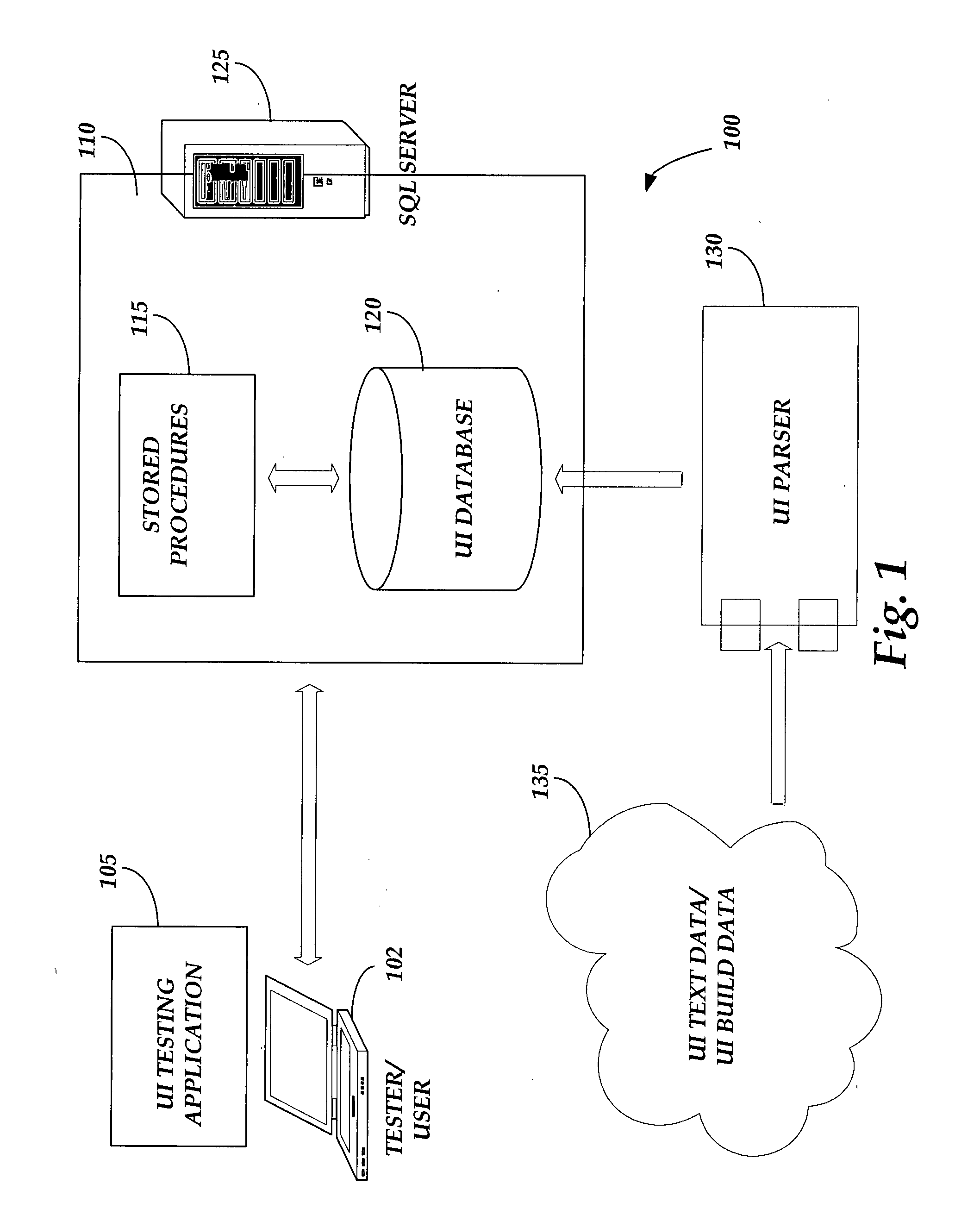
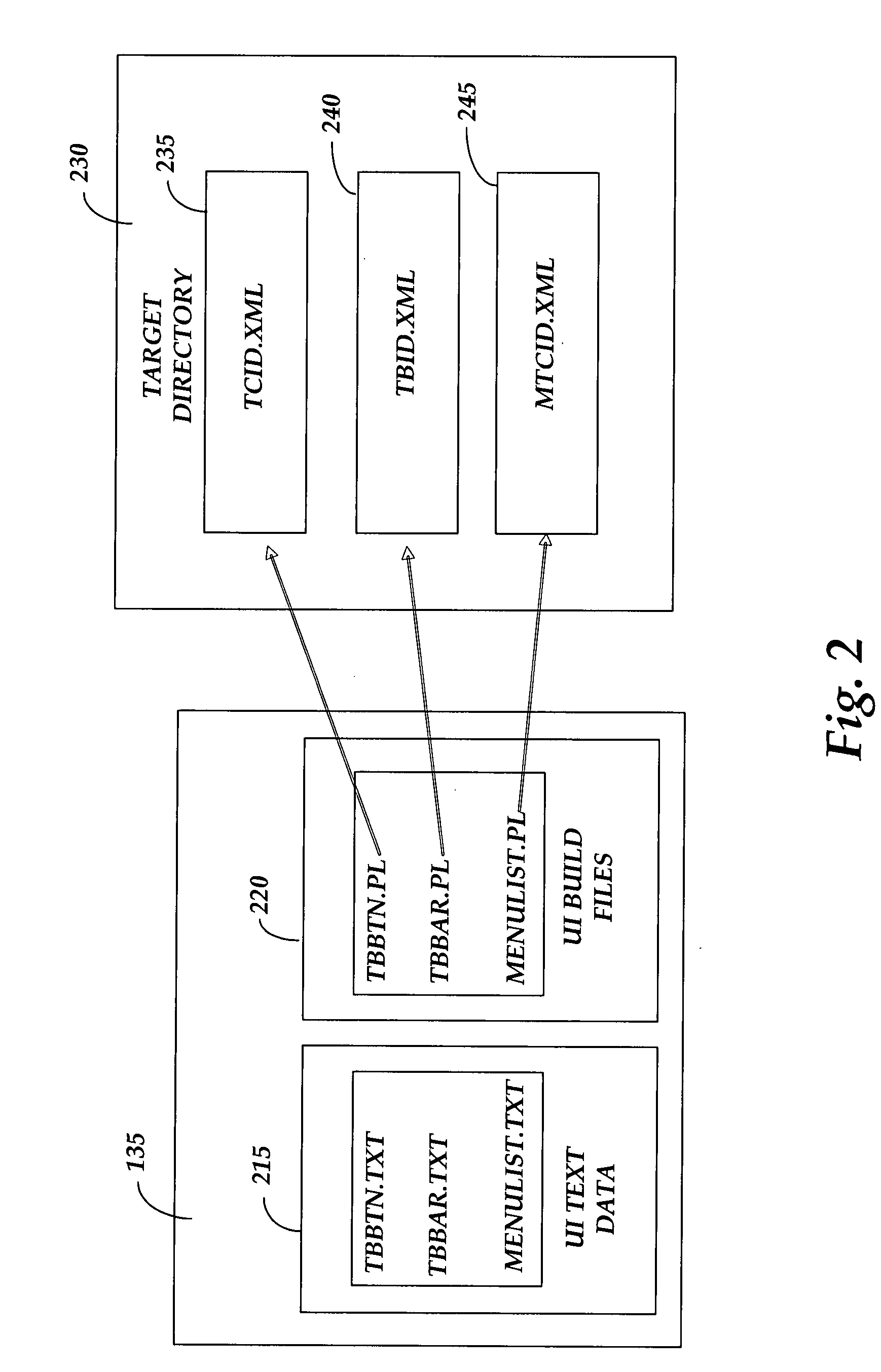
Graphical user interface testing
InactiveUS20080295076A1Efficient testingSoftware testing/debuggingExecution for user interfacesGraphicsGraphical user interface
Graphical user interface testing is provided. User interface (UI) build data and text data are transformed into a testable data format, such as XML, by a UI parser. The transformed UI data may be stored to a backend server where stored procedures and functions may be utilized to analyze the UI data against build differencing procedures, command mapping procedures, comparison to previous or subsequent user interface builds, etc. Additional stored procedures may allow UI testers to query data, create test suites and record testing information for a given UI. A front end testing module may provide a testing user an interface to query the backend database for information on various UI components and to review results for tests conducted on UI data. The front end testing module may also provide an interface for allowing testers to generate and execute new tests for a given user interface.
Owner:MICROSOFT TECH LICENSING LLC
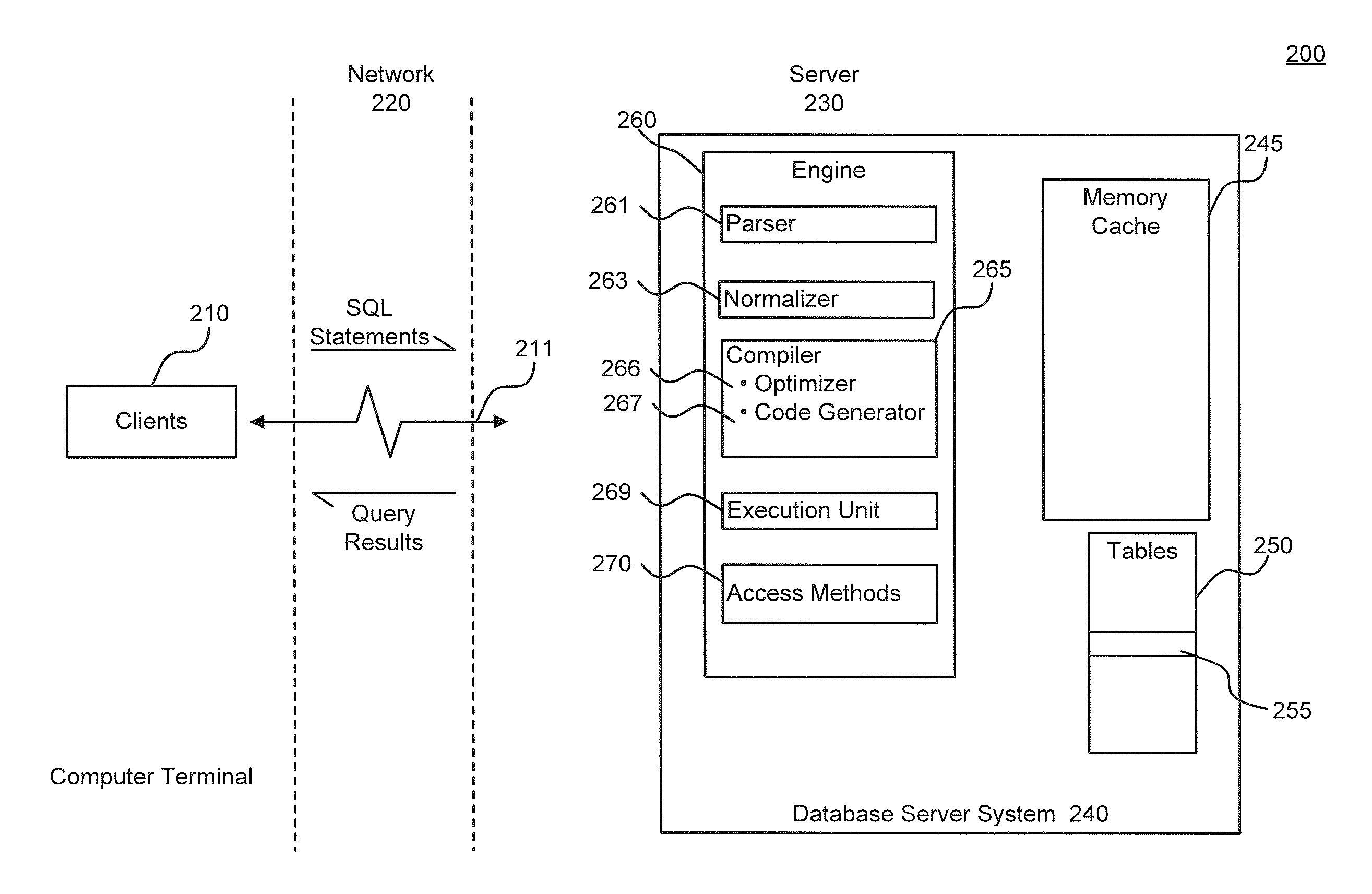
Query Plan Optimization for Prepared SQL Statements
ActiveUS20120084315A1Avoid accessDigital data information retrievalDigital data processing detailsQuery planDatabase server
System, methods and articles of manufacture for optimizing a query plan reuse in a database server system accessible by a plurality of client connections. An embodiment comprises providing at least one global cache storage and a private cache storage to a plurality of client connections, and coordinating utilization of the at least one global cache storage and the private cache storage to share light weight stored procedures and query plans for prepared SQL statements across the plurality of client connections via the at least one global cache storage while avoiding a spinlock access for executing the prepared SQL statements.
Method, system, and program for performing workflow related operations using an application programming interface
InactiveUS7047535B2Data processing applicationsProgram controlApplication programming interfaceDatabase server
Owner:INT BUSINESS MASCH CORP
Systems and methods for management of contact information
Owner:BERGIN JAMES P
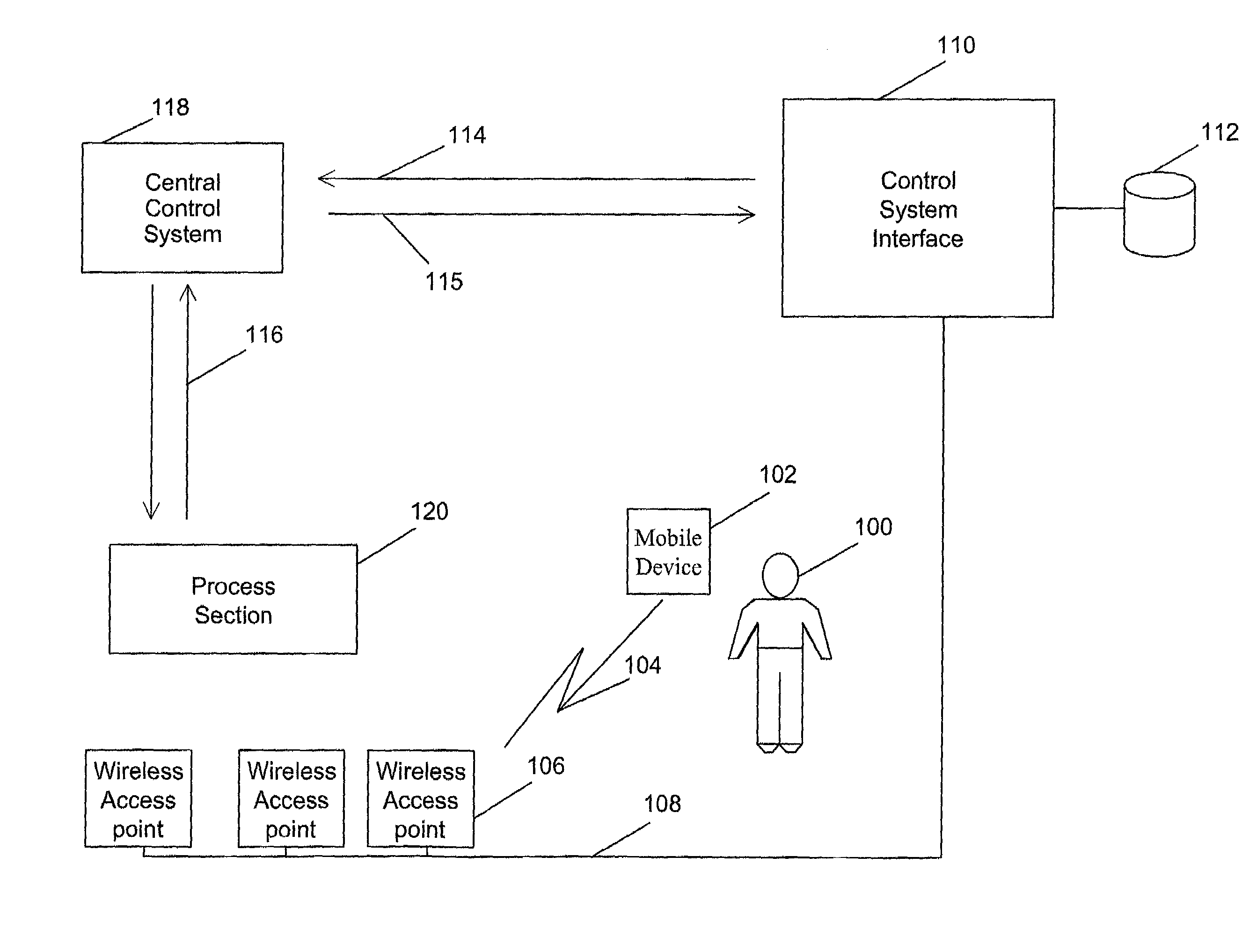
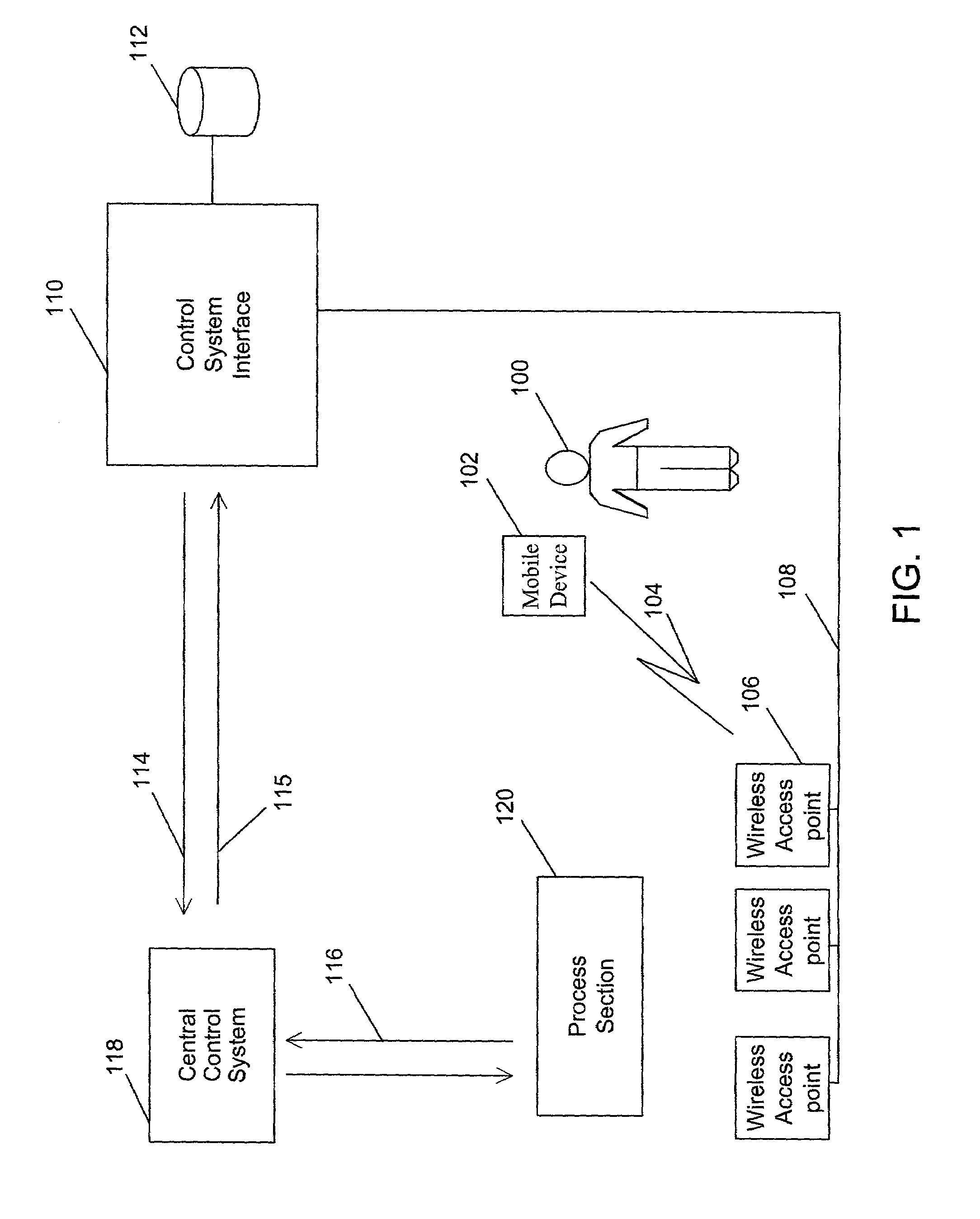
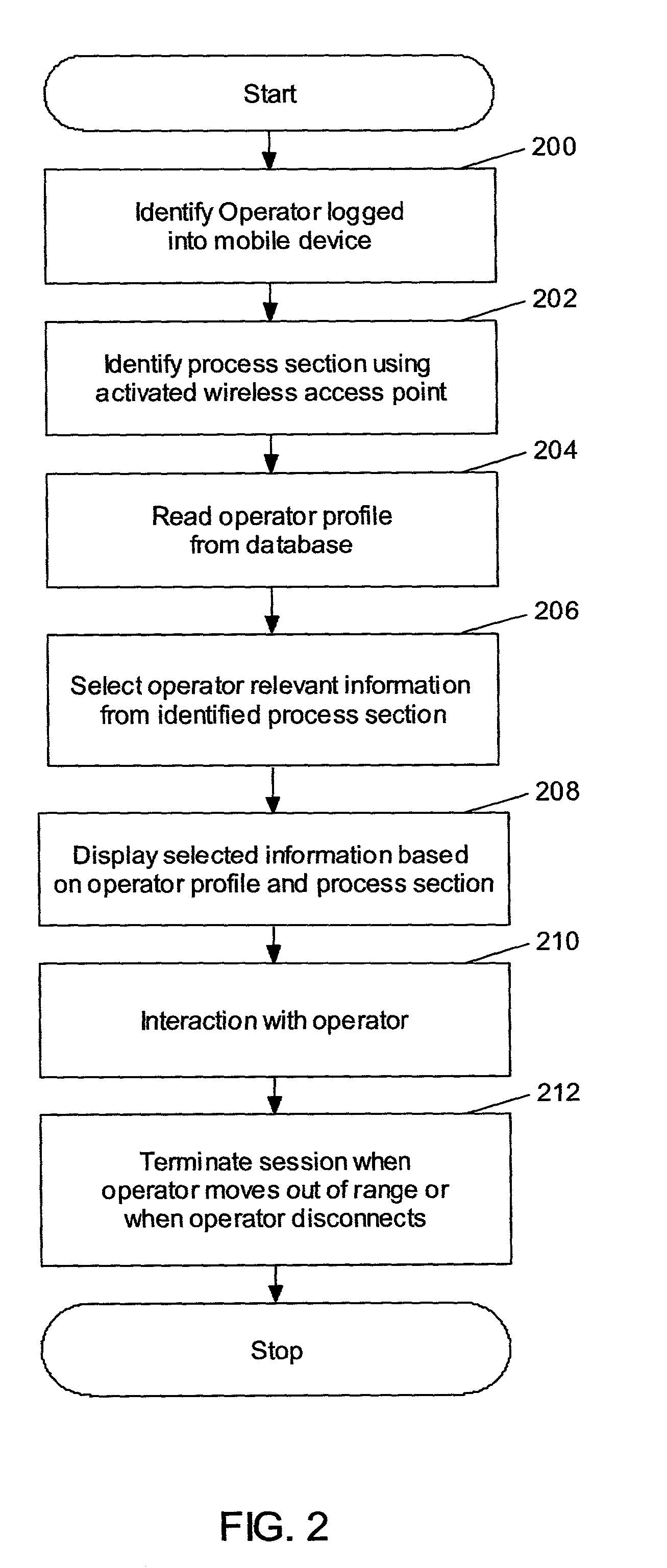
Dynamic operator functions based on operator position
InactiveUS7143149B2Enhanced interactionShorten the timeProgramme controlNetwork topologiesCommunications systemStored procedure
A communication system that enables an operator to remotely query and control the process sections in an industrial plant by exchanging data with a central computer that controls the process sections. The operator communicates with the process sections through a mobile wireless device remotely connected with one of the multiple wireless access points on a data network. This data network is, in turn, connected to the central computer that controls these process sections. The central computer stores the location of the process sections and the operator profiles. When requested, it collates and processes this data and presents it to the operator. Further, if the need arises, the central computer tracks and interacts with the operator.
Owner:ABB (SCHWEIZ) AG
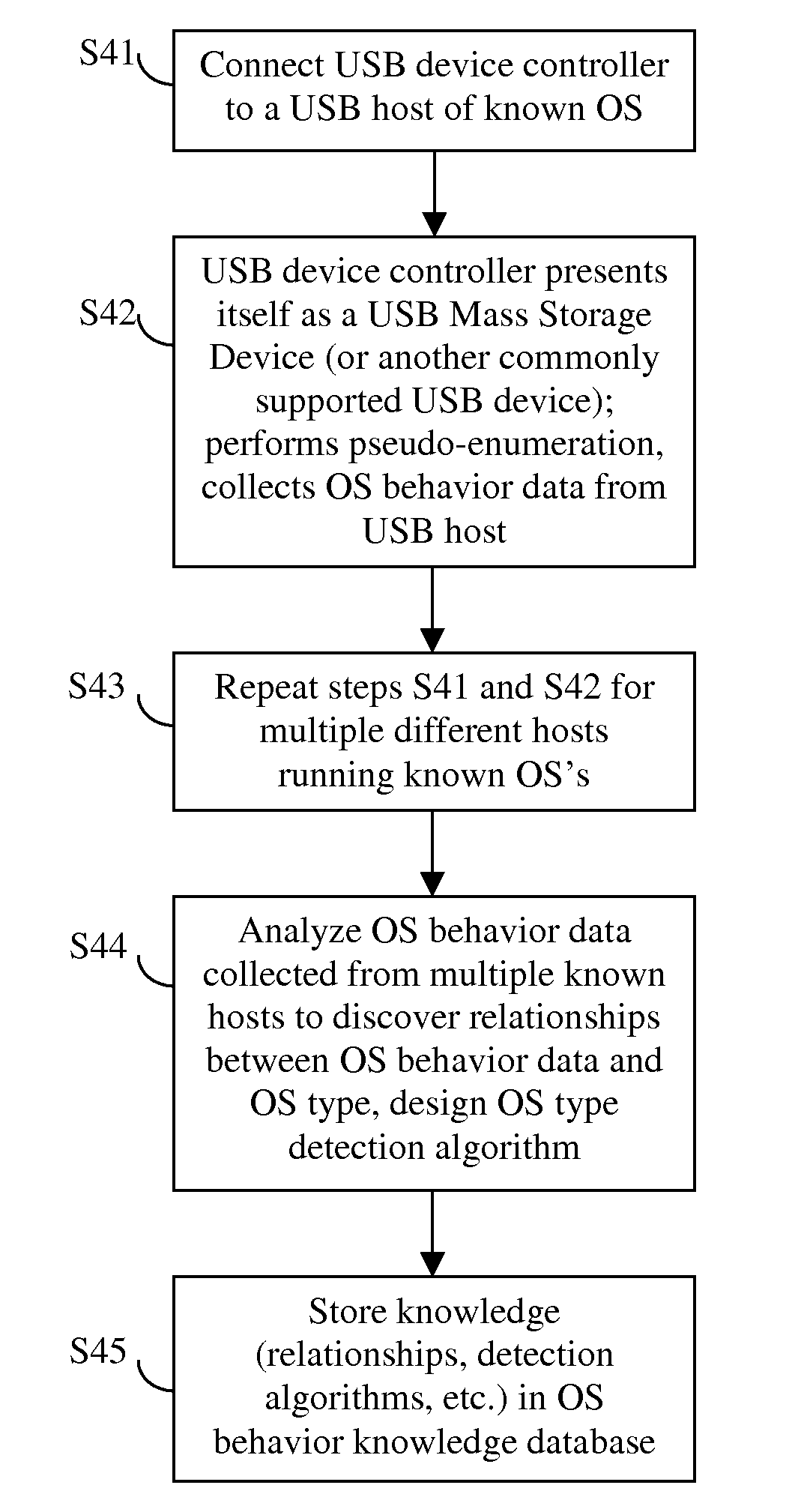
Method of USB device enumeration including detecting the operating system type of the USB host
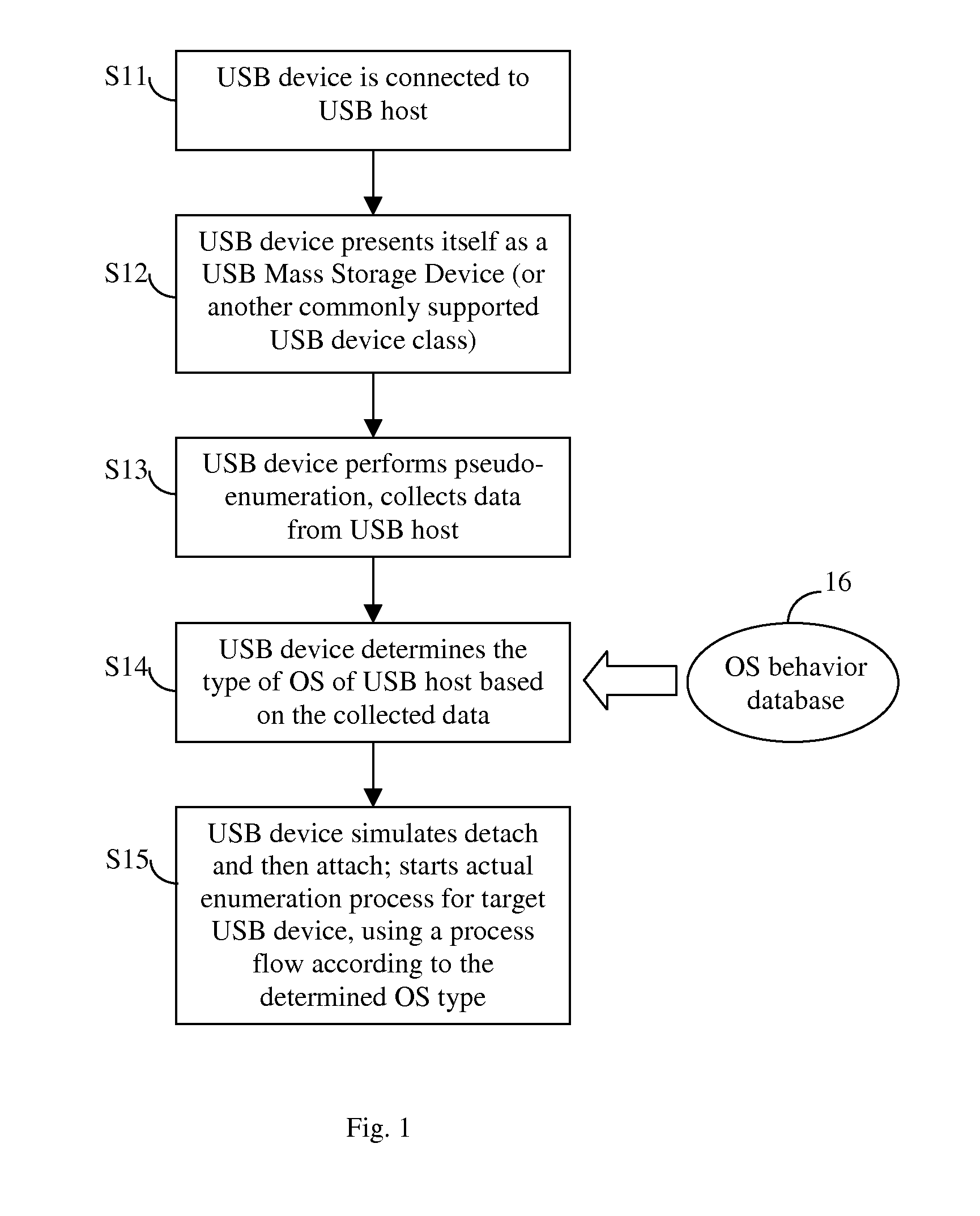
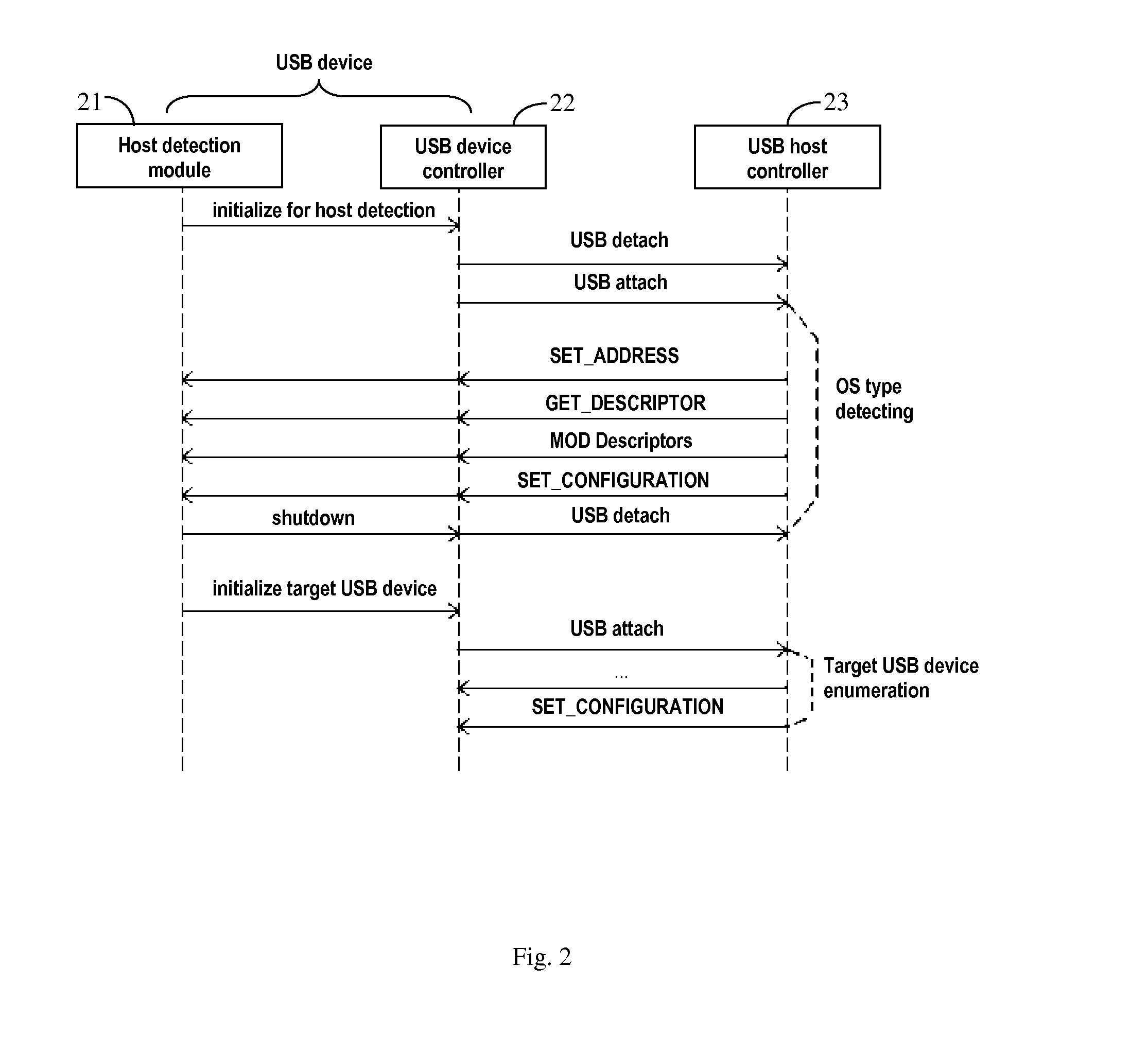
ActiveUS20120054372A1Reliably perform device enumerationEliminate bad effectsProgram controlInput/output processes for data processingUSBStored procedure
A USB device enumeration process implemented in a USB device is described. The USB device first detects a type of the operating system (OS) of the USB host connected to the device, and performs device enumeration using a process selected from multiple stored processes based on the detected host OS type. To detect the host OS type, the USB device first presents itself to the host as a USB MSD or HID, performs device enumeration to collect OS behavior factors from the host, and determines the OS type from the OS behavior factors. Thereafter, the USB device performs actual device enumeration by presenting itself as the USB device it actually is, using an enumeration process specific to the detected host OS type. The multiple stored enumeration processes are customer configurable. Further, a method is provided to stop an enumeration process when the host is in a BIOS stage.
Owner:MEDIATEK INC
Flash memory and method and system for automatically separating cold and hot data based on same
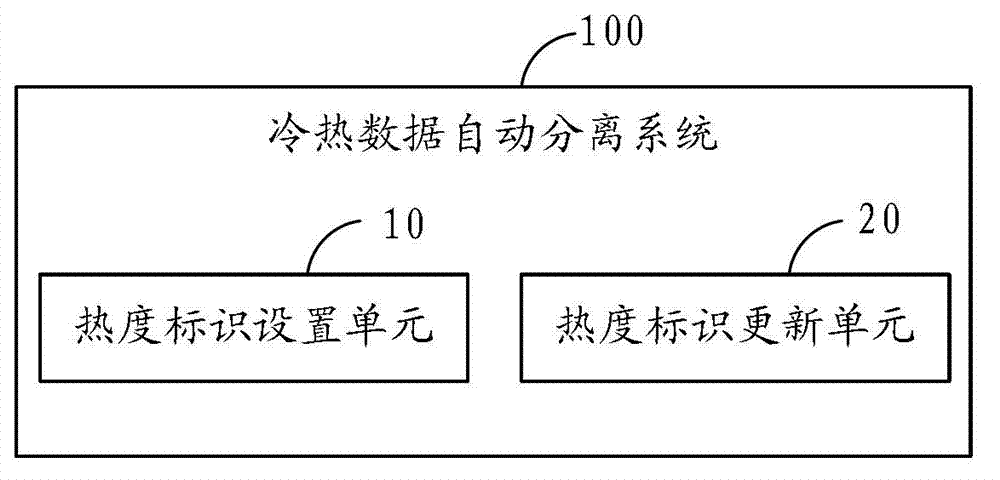
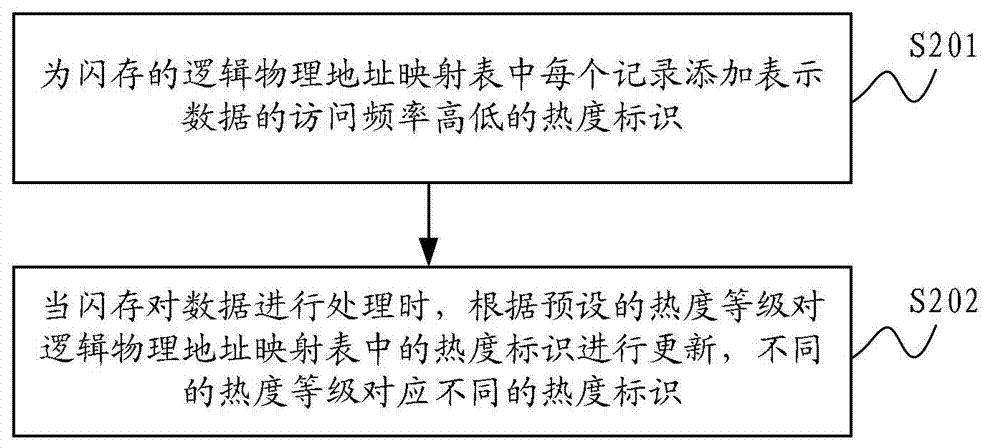
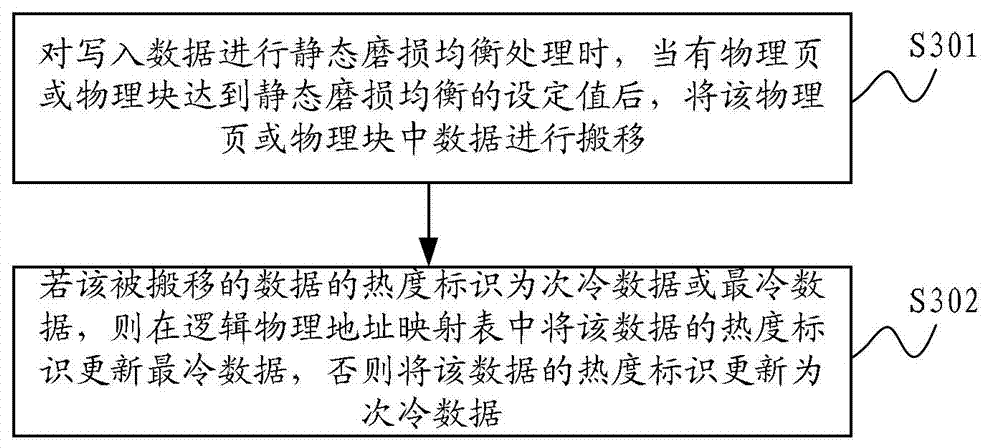
ActiveCN102902628AThe frequency of visitsRealize hot and cold separationMemory adressing/allocation/relocationPhysical addressAccess frequency
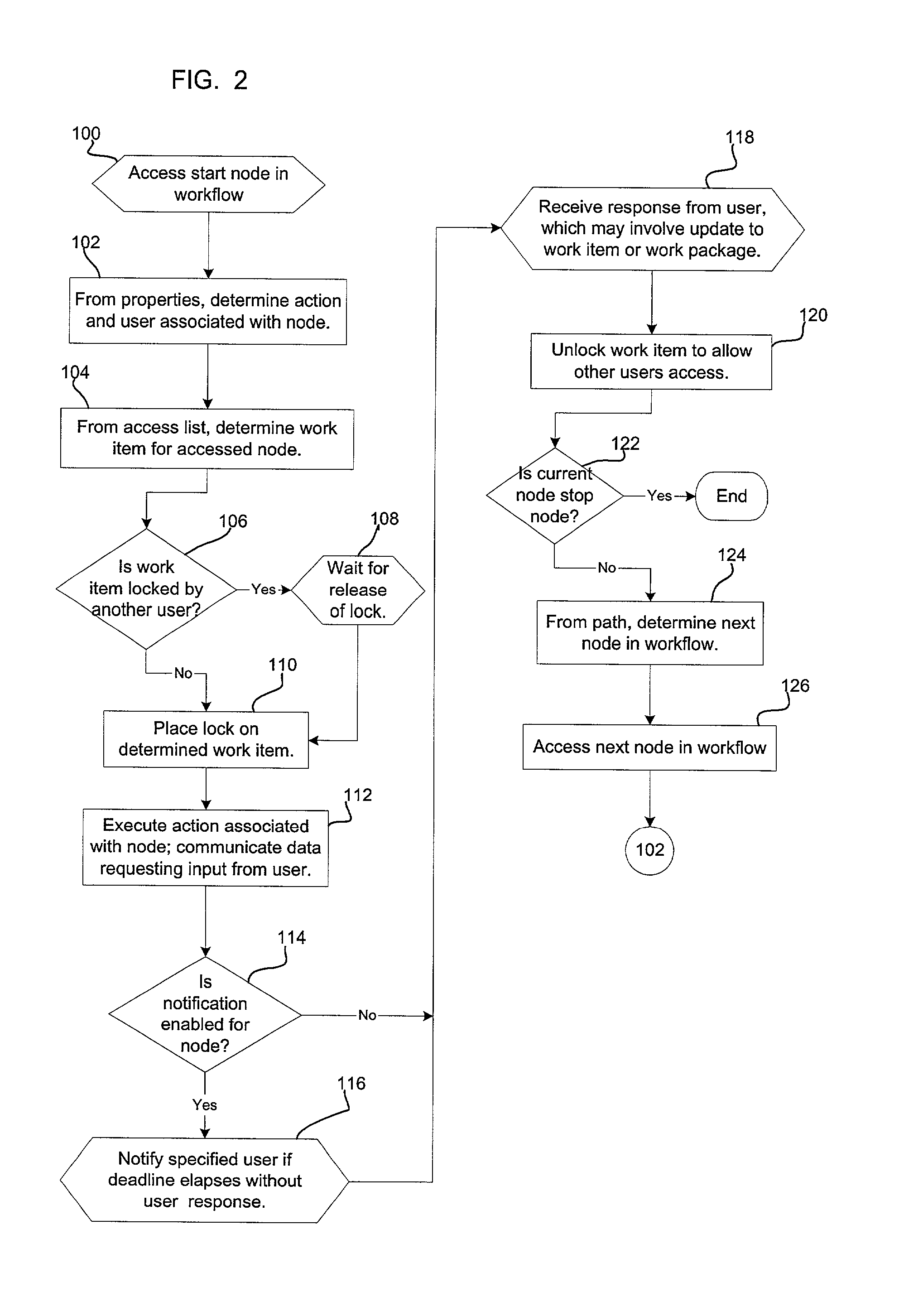
The invention is applied to the technical field of flash memory storage, and provides a flash memory and a method and a system for automatically separating cold and hot data based on the same. The method comprises the steps that a hot degree identifier for showing the access frequency of data is added for each record in a logic physical address mapping table of the flash memory; and when the flash memory processes data, the hot degree identifiers in the logic physical address mapping table are updated according to the preset hot levels, and different hot levels correspond to different hot degree identifiers. According to the flash memory and the method and the system for automatically separating cold and hot data based on the same, the cold and hot degrees of data are processed directly in the logic physical address mapping table of the flash memory, and just modifying an FTL (Flash Translation Layer) algorithm can separate cold and hot data without using additional software and cache. Therefore, the flash memory and the method and the system for automatically separating cold and hot data can automatically realize the separation and storage according to the access frequency during the storage of data in the flash memory instead of using additional cold and hot data judgment algorithm and cache.
Owner:RAMAXEL TECH SHENZHEN
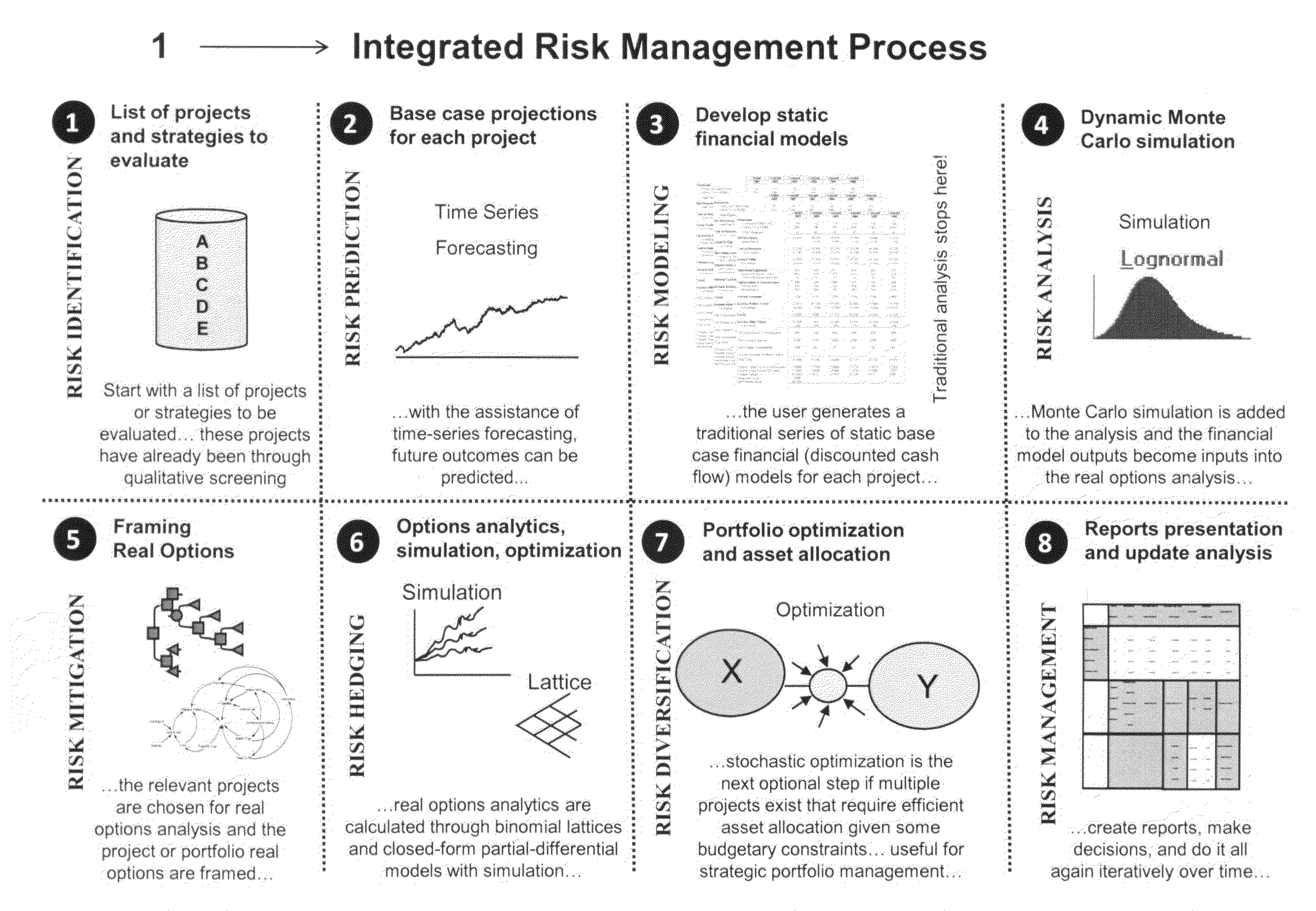
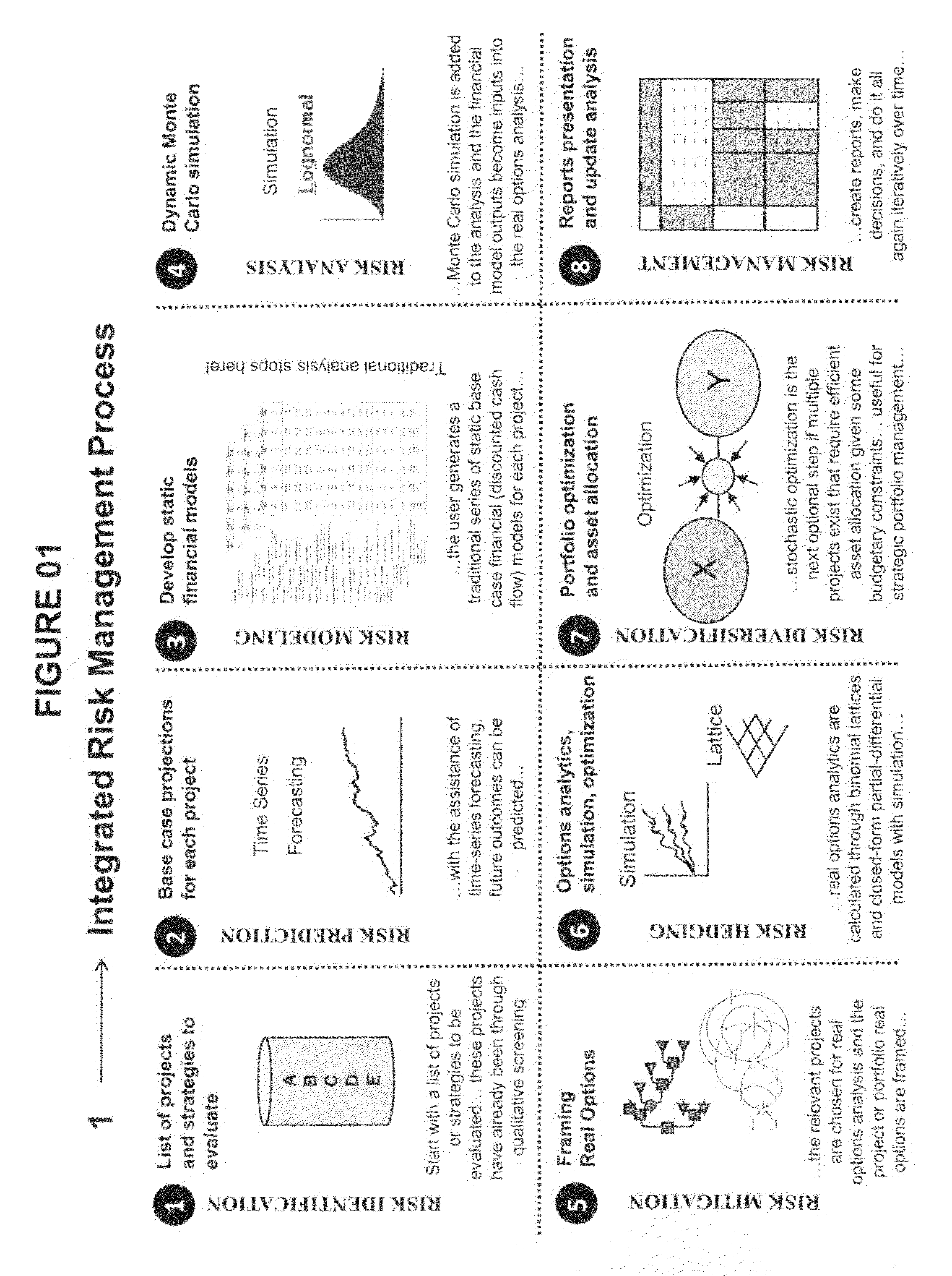
Integrated risk management process
ActiveUS20100205042A1Facilitate business risk analysisEasy to explainDigital data processing detailsAnalogue secracy/subscription systemsManagement processBusiness forecasting
A method and system allowing the analysis of risk through the use of Monte Carlo simulation, statistical and data analysis, stochastic forecasting, and optimization. The present invention includes novel methods such as the detailed reporting capabilities coupled with advanced analytical techniques, an integrated risk management process and procedures, adaptive licensing technology, and model profiling and storage procedures.
Owner:MUN JOHNATHAN C
System and method for adding context to the creation and revision of artifacts
ActiveUS20100095298A1Efficiently understoodGreat and efficient understandingDigital data processing detailsText processingData managementApplication software
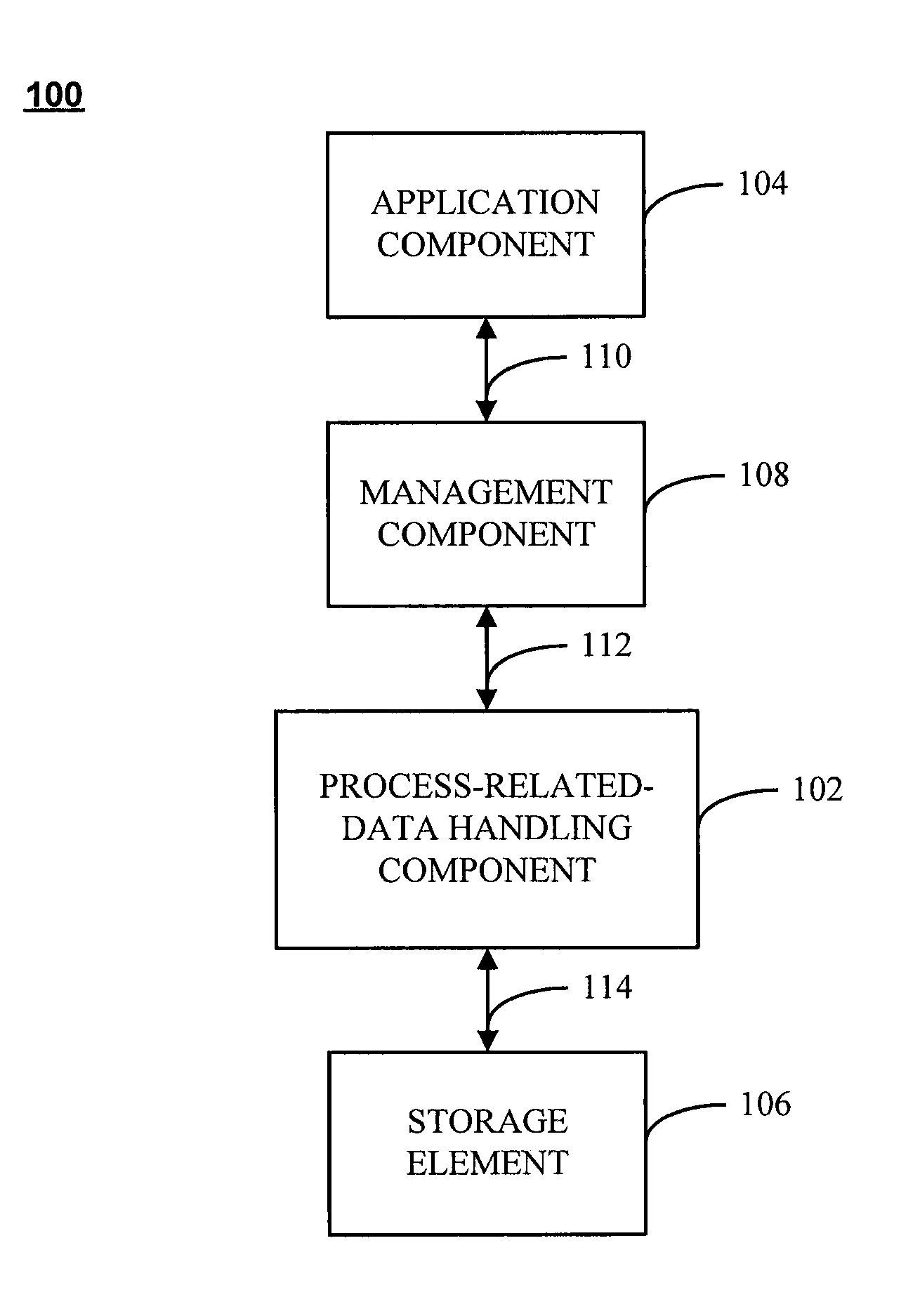
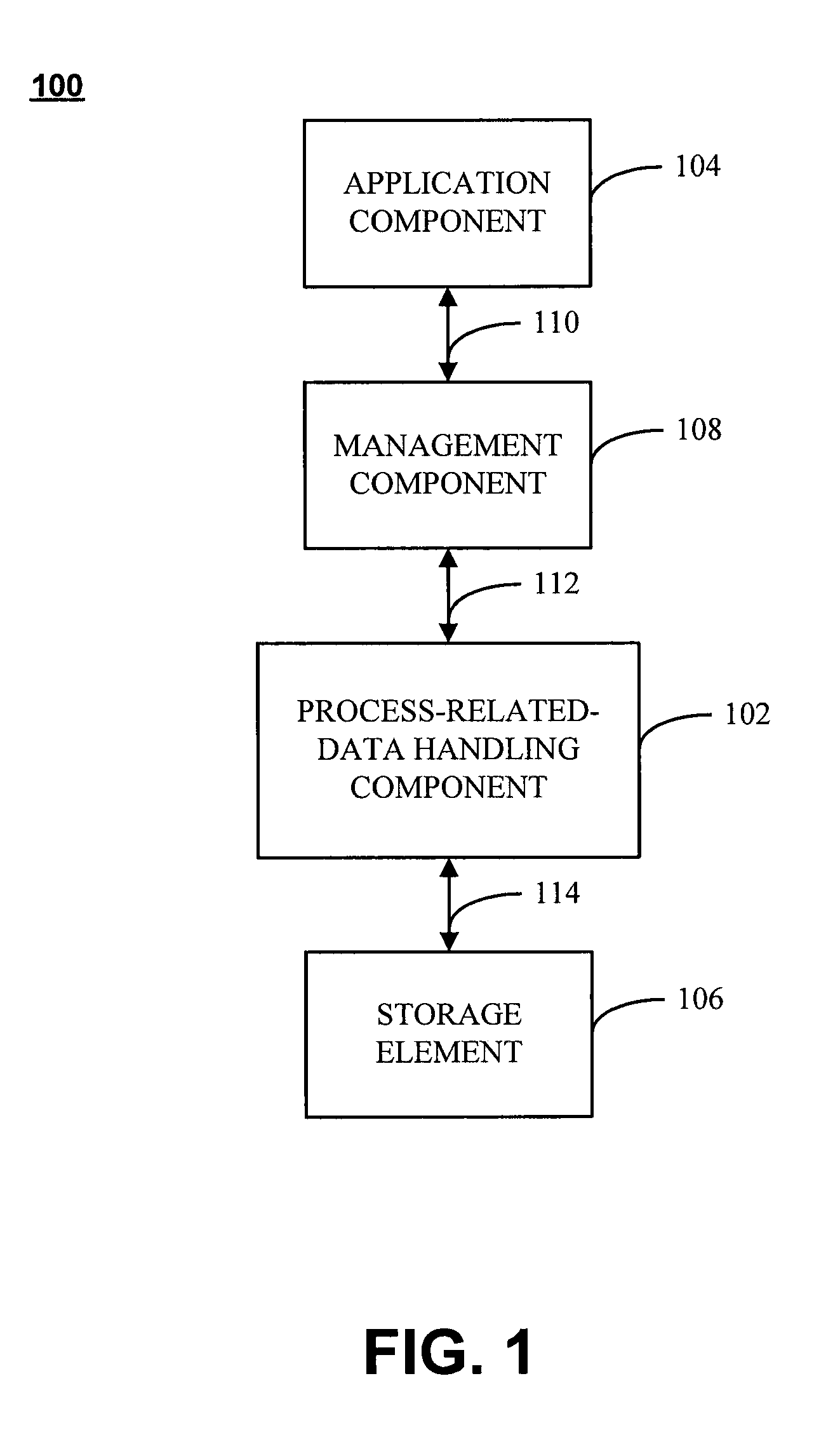
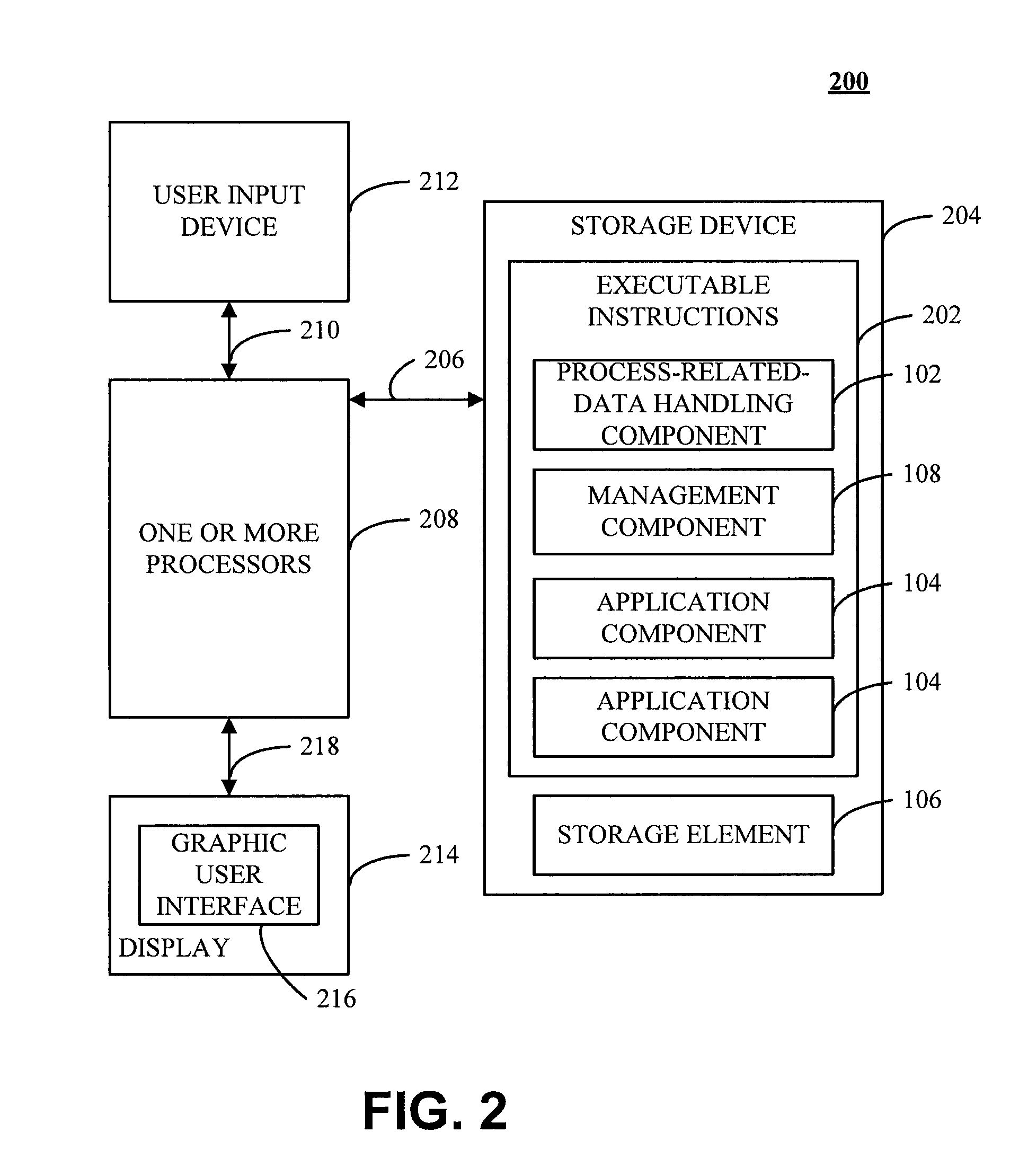
A system includes a process-related-data handling component operative to handle process-related data corresponding to an operation associated with an artifact, such as the creation or revision of the artifact. An application component is operatively coupled to the process-related-data handling module and is operative to interact with the artifact. A storage element is also operatively coupled to the process-related-data handling module and is operative to store the process-related data. The process-related data may be displayed, created, or otherwise manipulated through a data management tool, which may include, a calendar interface, a task interface, and / or a media capture module. A method is also directed towards establishing process-related context concerning at least one artifact.
Owner:ACCENTURE GLOBAL SERVICES LTD
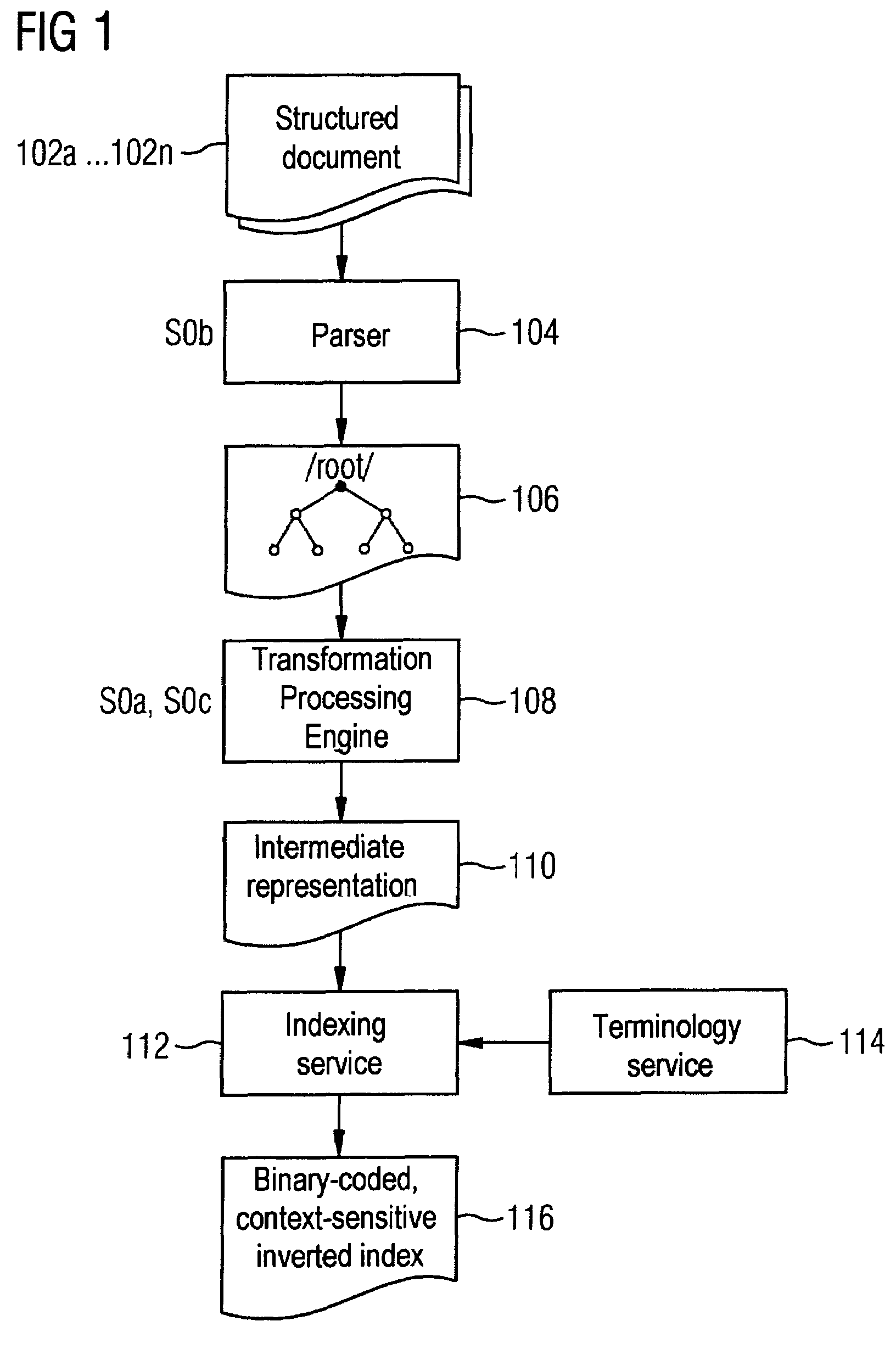
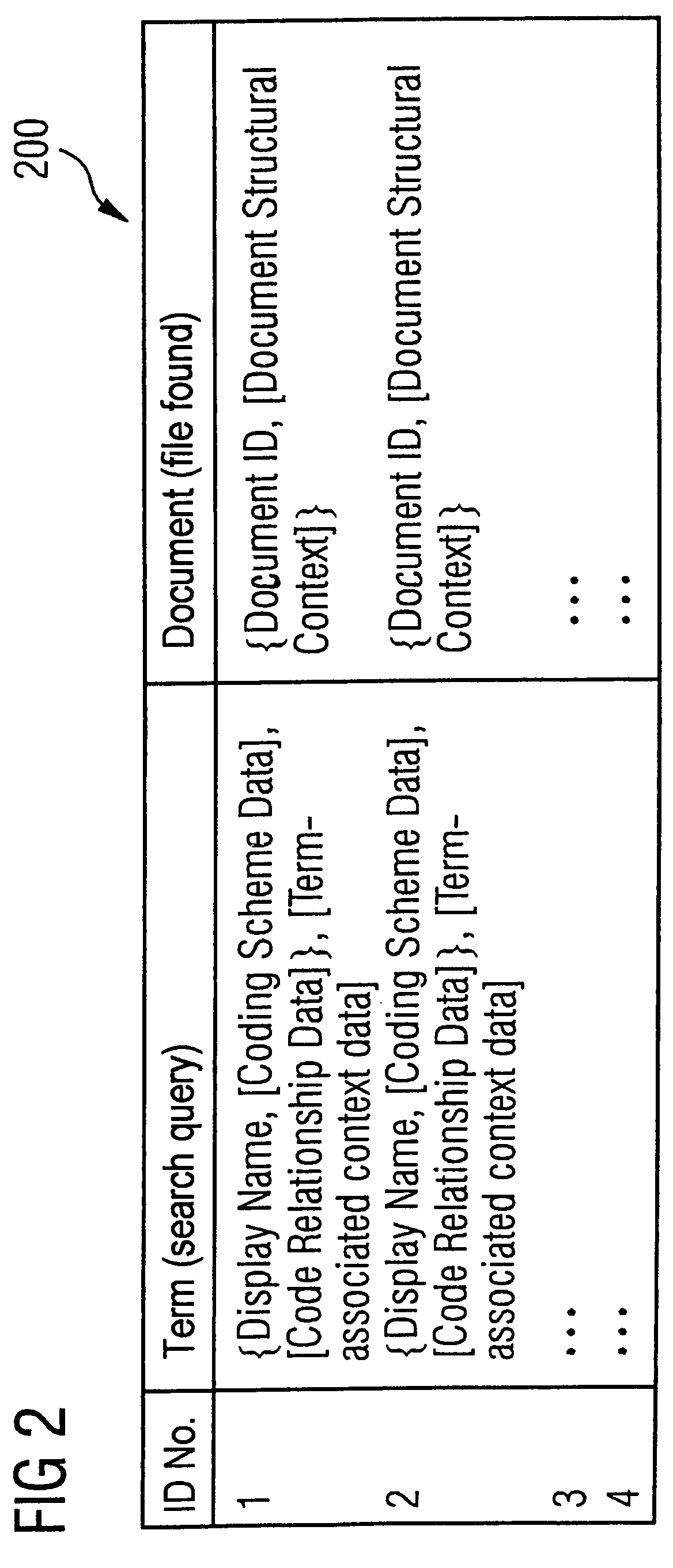
Automatic indexing of digital image archives for content-based, context-sensitive searching
InactiveUS7689544B2Decision supportHigh precisionPicture changing apparatusData processing applicationsAcquired characteristicFeature extraction algorithm
Owner:SIEMENS HEALTHCARE GMBH
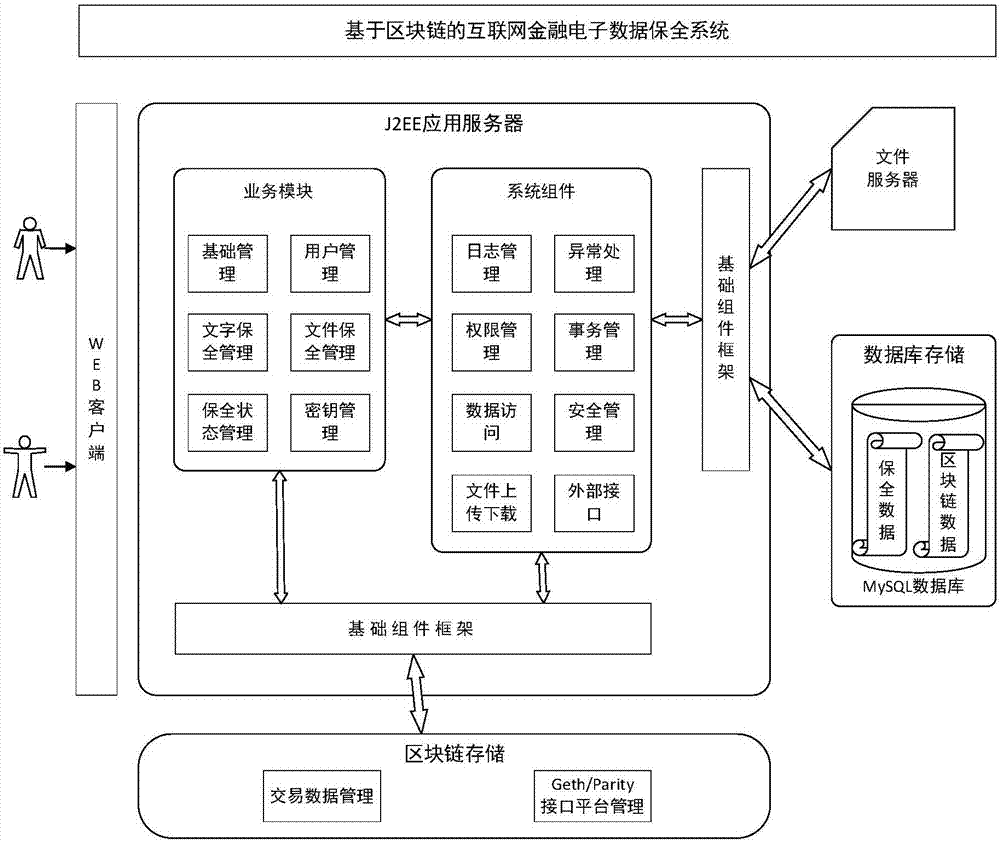
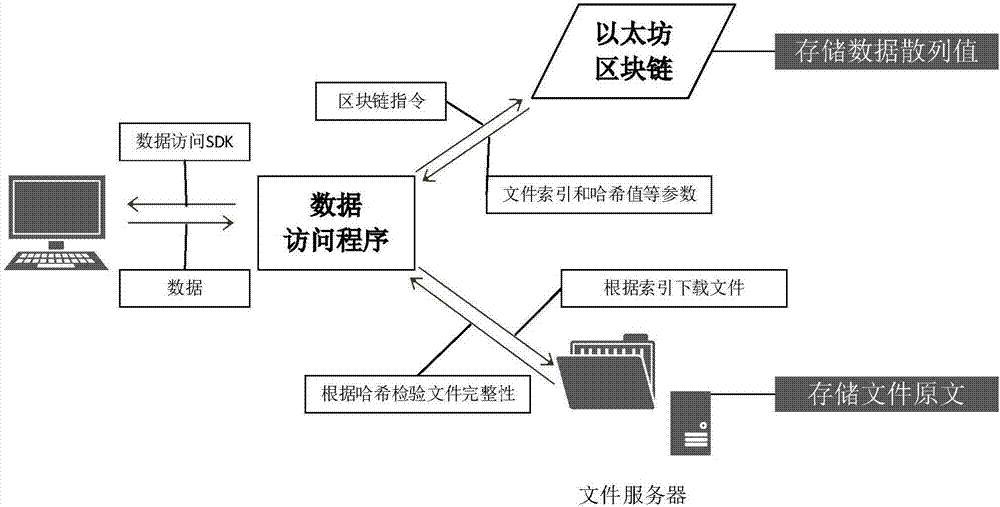
Blockchain-based Internet financial electronic data security system and method
InactiveCN107508806AAddress the risk of tamperingMeet security needsMultiple keys/algorithms usageUser identity/authority verificationPlaintextOriginal data
The invention provides a blockchain-based Internet financial electronic data security system and method, and belongs to the fields of computer application technologies and blockchain network application technologies. A user submits Internet financial electronic data, an original data file is stored in a file server, the storage location and data content of the data file are encrypted through a modern cryptography technology, and a Harsh value of the data file and the encrypted data are stored in an Ethereum blockchain transaction; and when originality verification is conducted, the Harsh value is read from the blockchain transaction, and a Harsh value of a to-be-verified file is calculated and compared with the Harsh value. By using the Ethereum blockchain network, the security requirements of most data types can be met, the storage process can be transparentized, and the conditions that the data is lost, and the stored data is tampered can be avoided; and the security data is encrypted through the modern cryptography technology, and therefore the condition that the privacy data is embezzled by plaintext is avoided.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
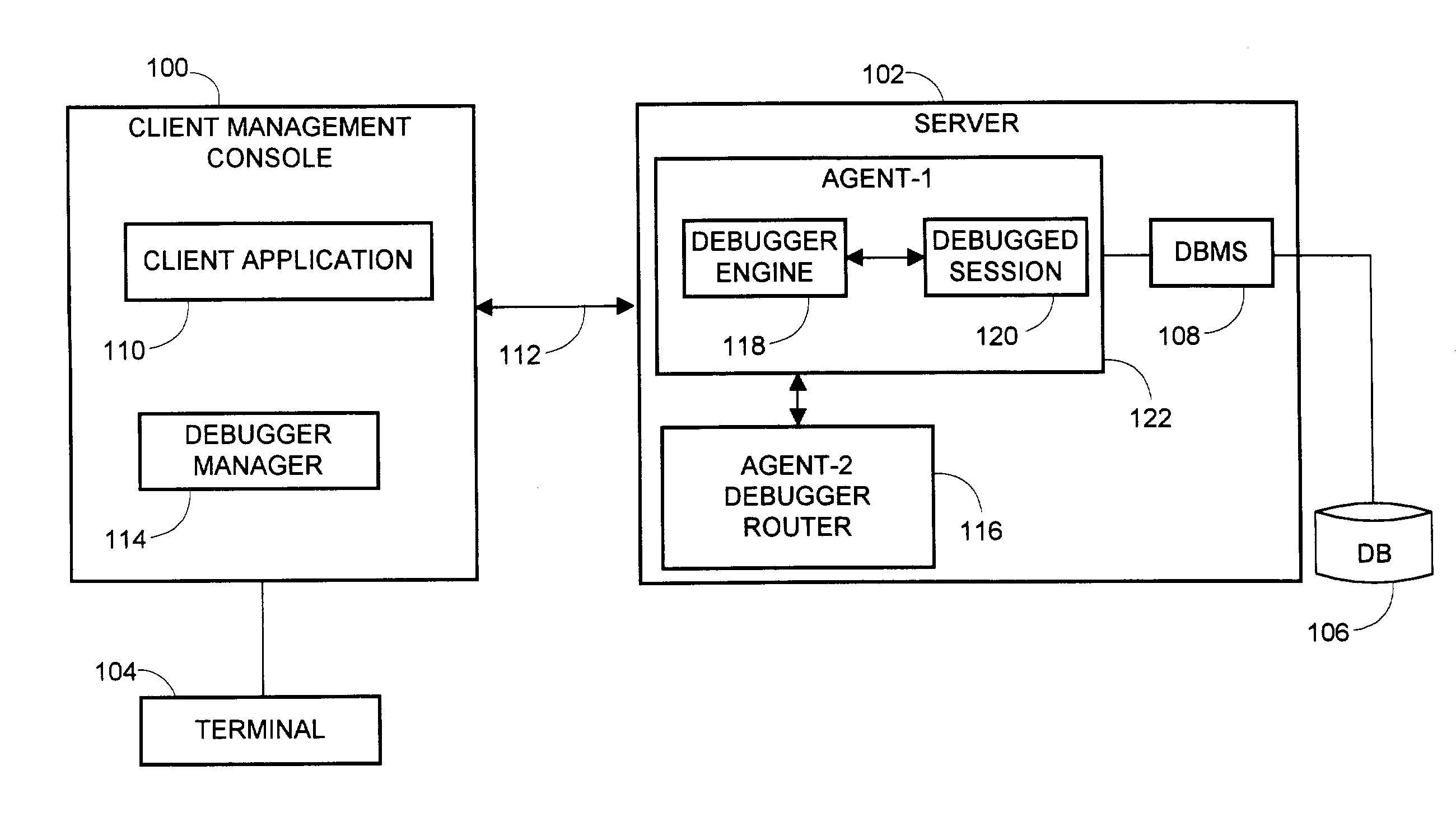
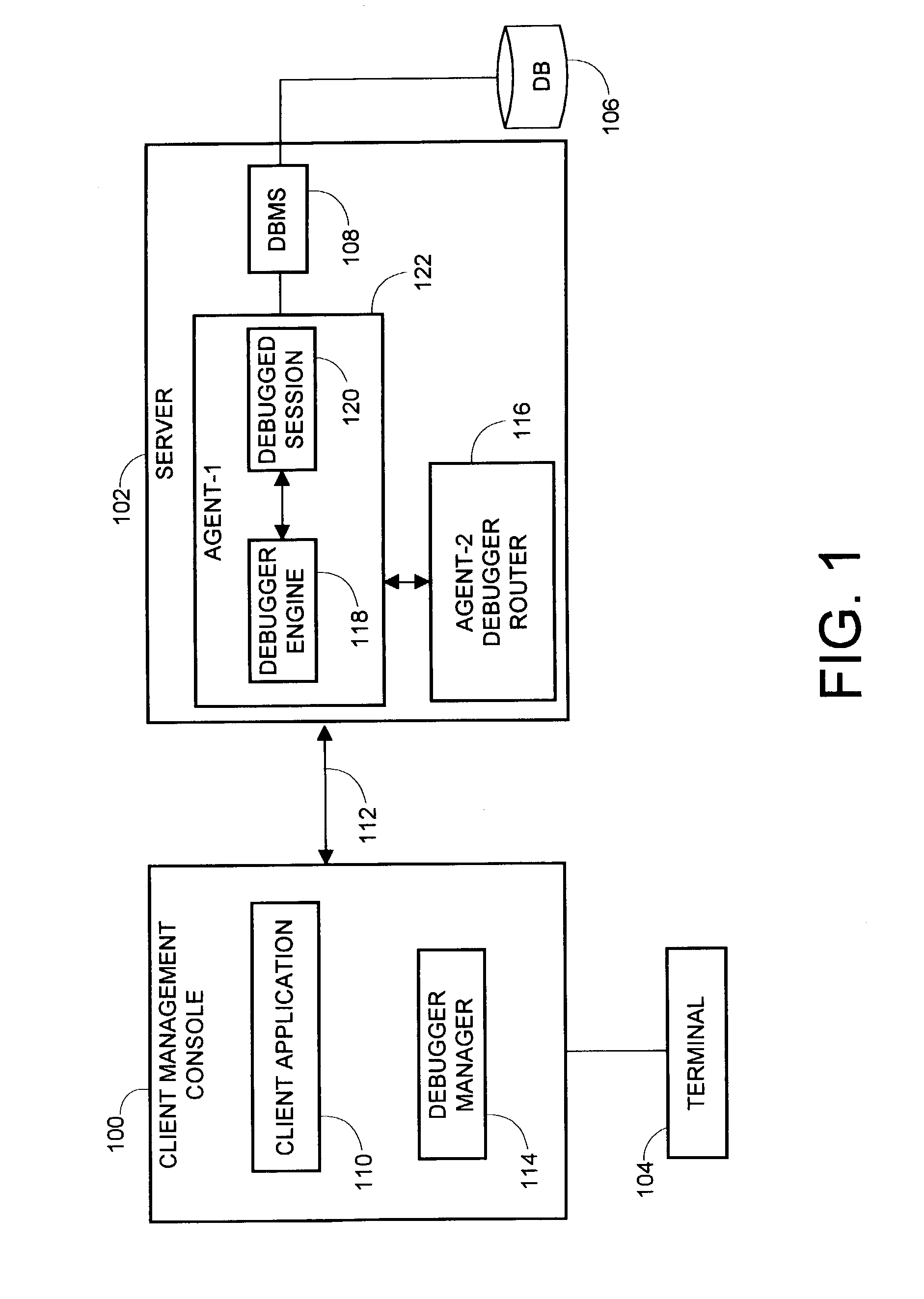
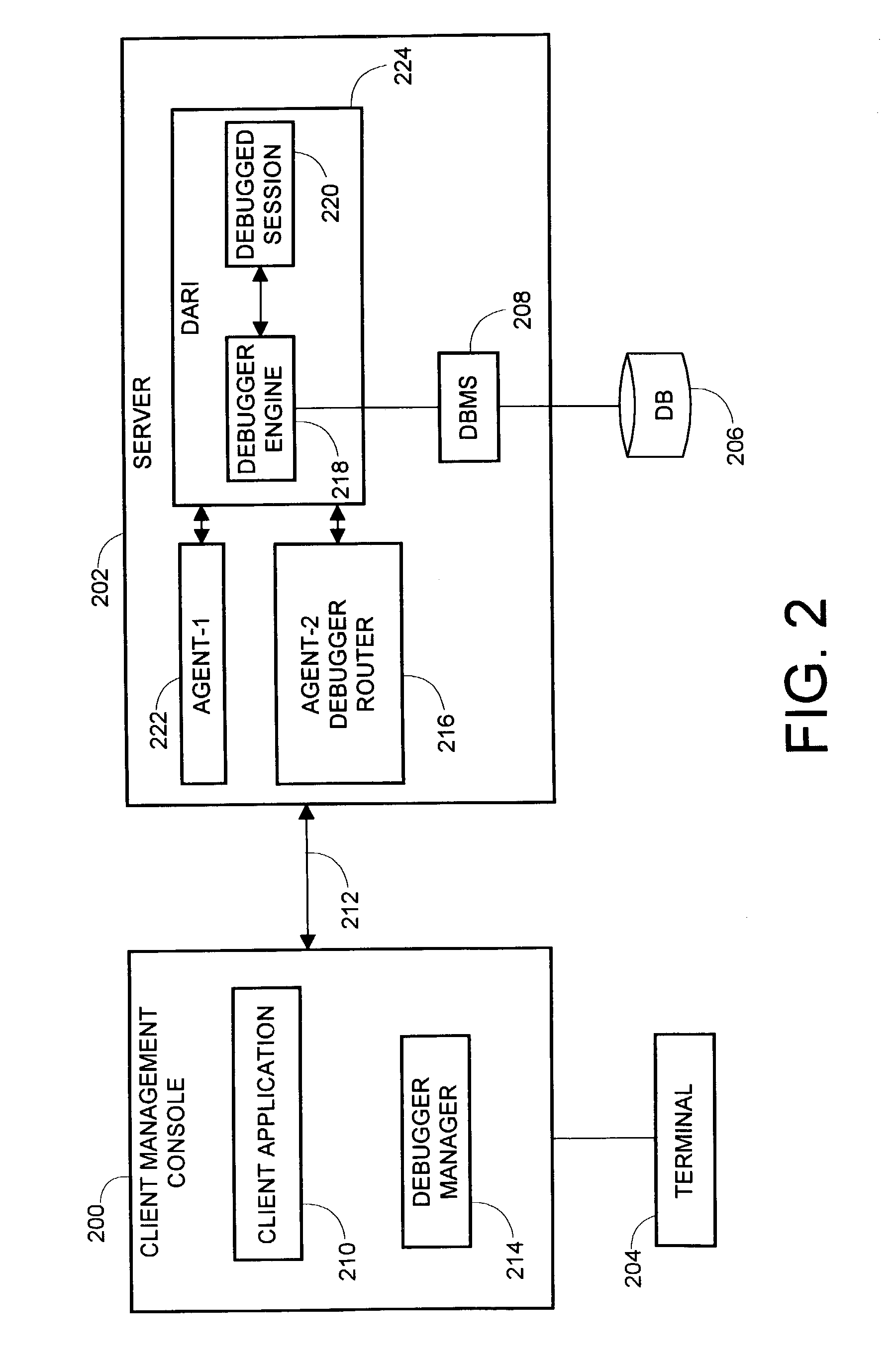
SQL debugging using stored procedures
ActiveUS7155426B2Data processing applicationsDigital data processing detailsCommunication interfaceComputerized system
A method, apparatus and article of manufacture is provided for SQL debugging within a computer system network. The method uses stored procedures via a console for debugging of SQL instructions located in a server, wherein preferably only one database communication line exists between the server and the console. The server has a database management system for retrieving data from a database stored in an electronic storage device coupled to the server. The method uses a debugger manager at the console for commanding and monitoring debugging operations of the server-side SQL instructions performed by a debugger engine, and uses stored procedures of a debugger router as a database communication interface for receiving commands and sending status reports between the debugger manager and the debugger engine.
Owner:IBM CORP
Method of, system for, and computer program product for providing automatic identification of a computer program code candidate for web deployment or a stored procedure
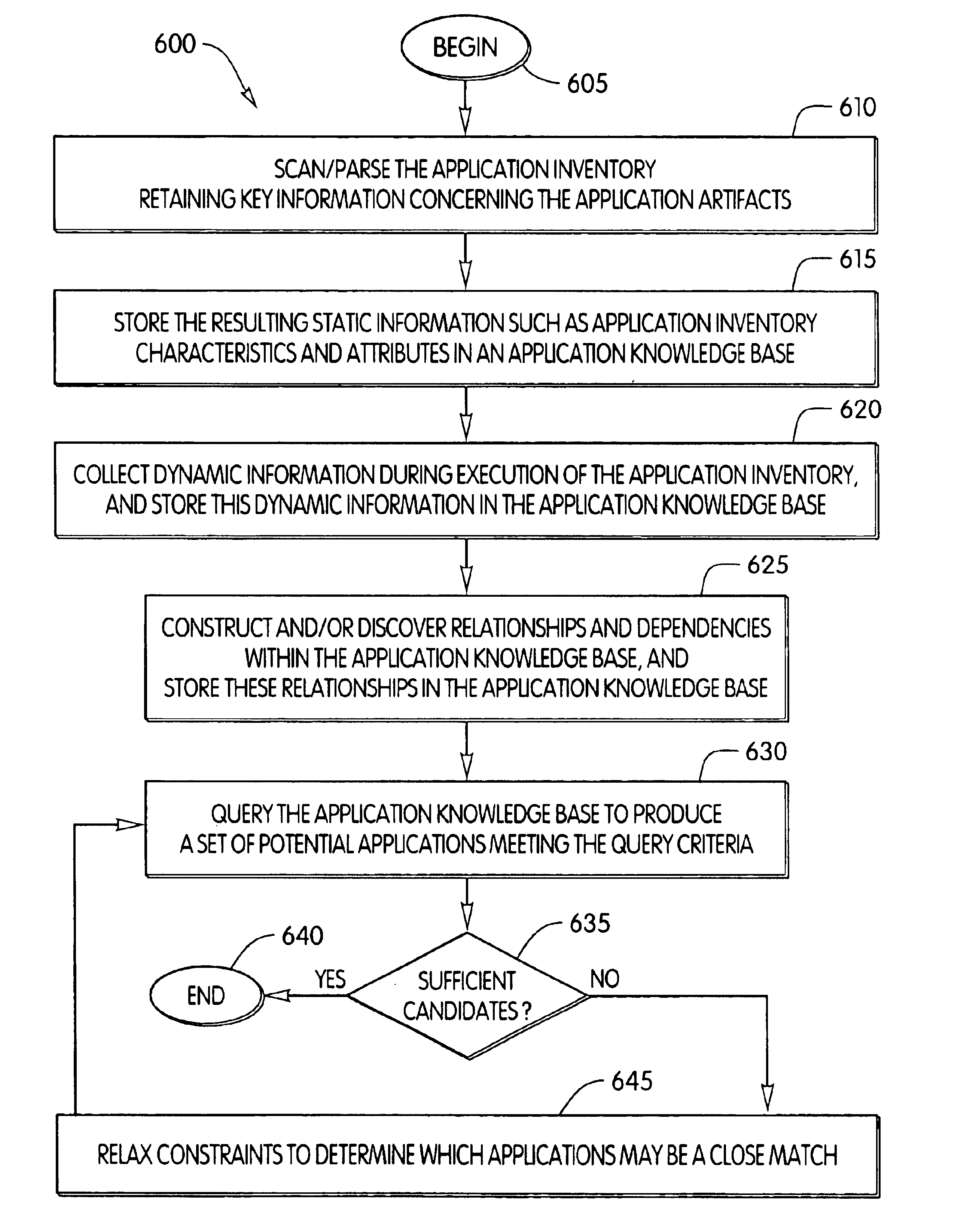
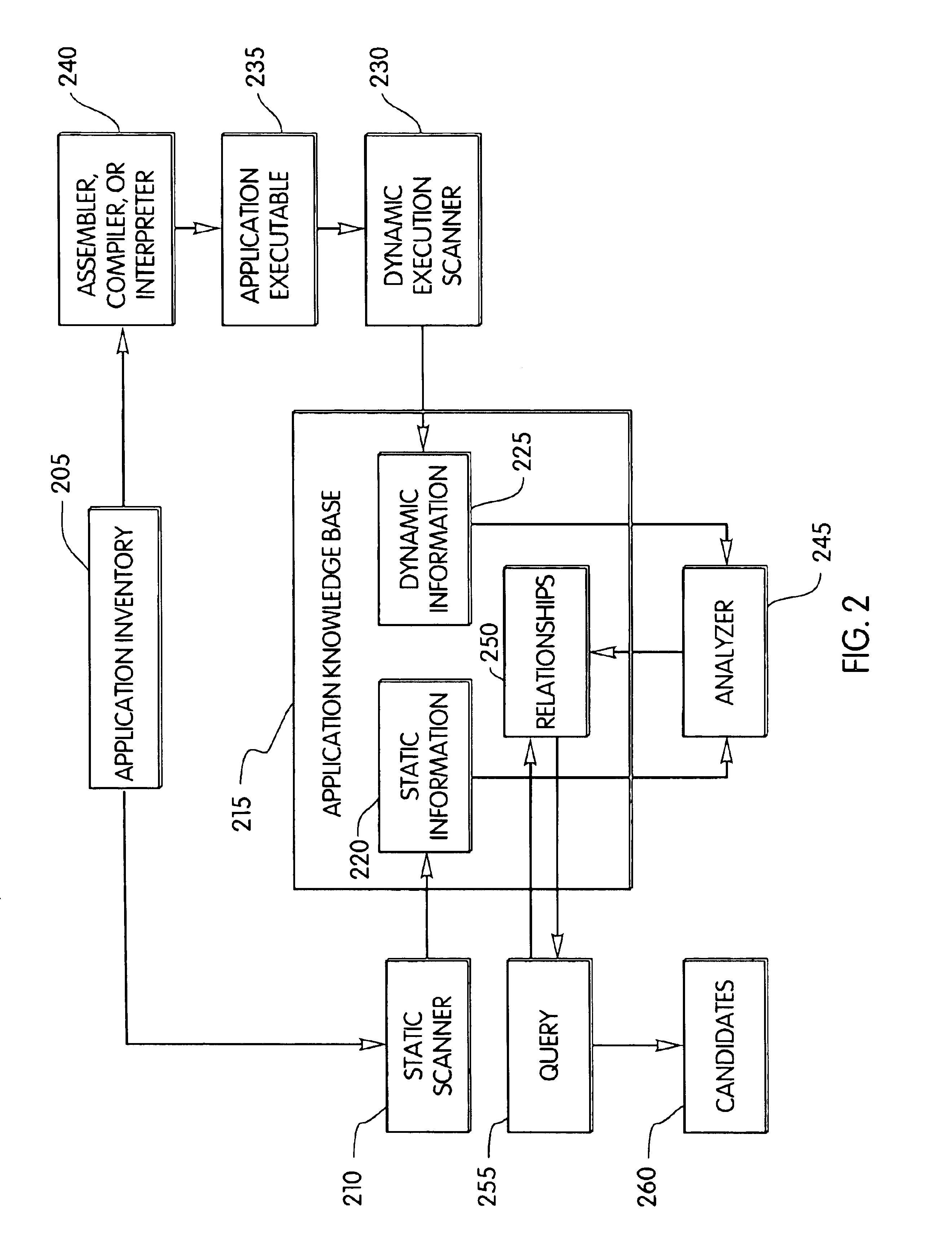
InactiveUS6931630B1Good user interfaceImprove usabilitySoftware maintainance/managementSpecific program execution arrangementsTheoretical computer scienceSource code
Computer program code which is a candidate for Web enablement or stored procedures is identified. Source code corresponding to computer program code is scanned and parsed to determine static information concerning the computer program code. The static information is stored in a database. Dynamic information concerning the computer program code during an execution of the computer program code is also collected and stored in the database. Responsive to the static information and dynamic information stored in the database, relationships and dependencies are then developed and stored in the database. The database may then be queried to produce a set of potential candidates of computer program code meeting a constraint of the query. If insufficient candidates are returned by the query, then the query constraint may be relaxed, and the query repeated.
Owner:IBM CORP
A method for implementing foreground data configuration in network management system
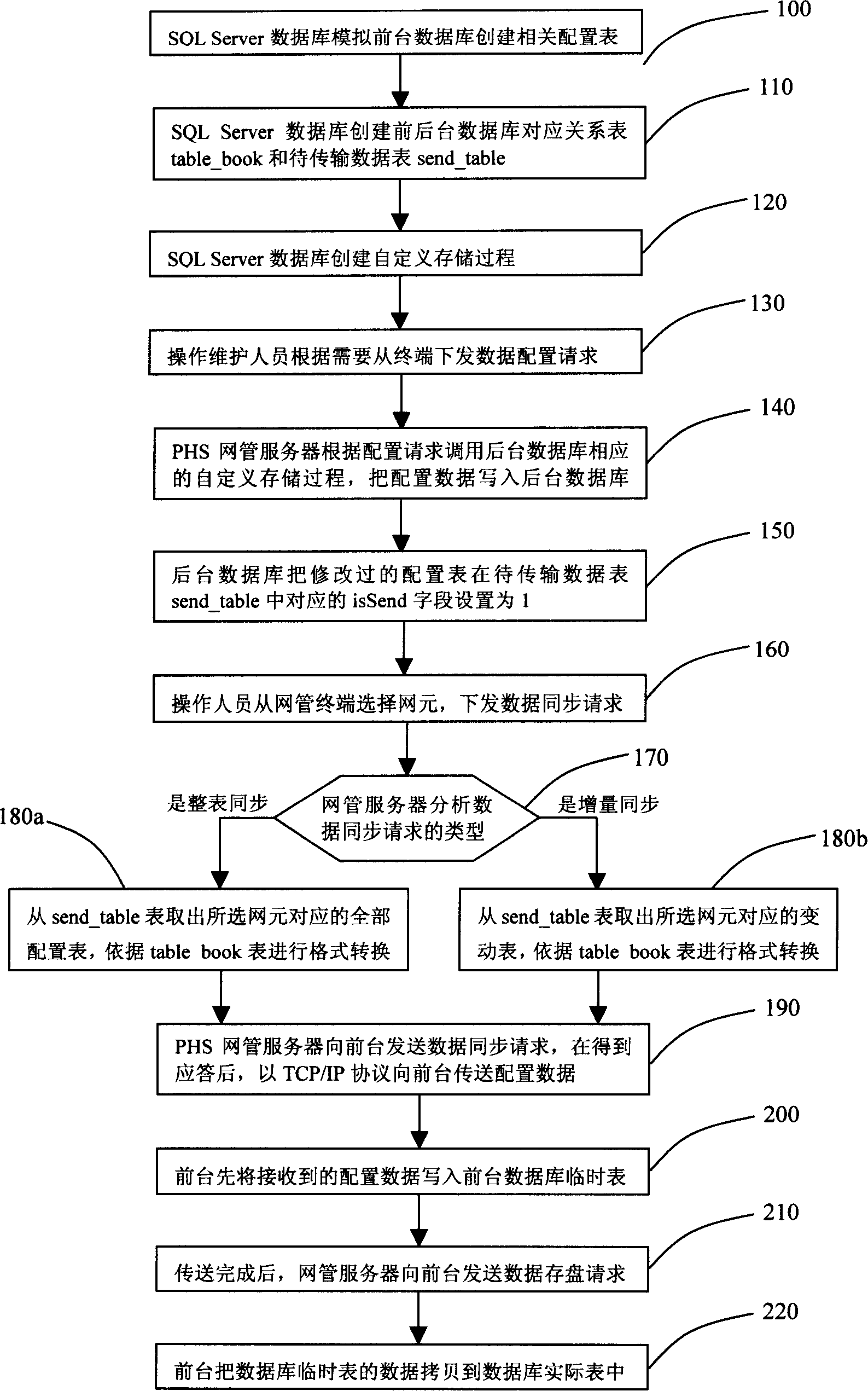
InactiveCN1545252AReduce the burden onImprove work efficiencyData switching networksData synchronizationLimited resources
The invention discloses a foreground data configuring method in network management system, firstly simulating the coursed of establishing relative configuration tables, data tables to be transmitted, foreground-background database relation tables and custom memory; the operating personnel sends a request for data synchronization, and the network management program reads the data in the configuration tables to be transmitted according to the data tables to be transmitted, making data conversion according to the above relation tables, and then transmitting the data to the foreground. It can save limited resources of CPU, memory, etc, enhance working efficiency of the foreground, and at the same time make full use of strong functions of the background relation database system, to make the configuration data more reliable.
Owner:ZTE CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com