Firmware unknown vulnerability detection method based on vulnerability analysis
A technology for unknown vulnerabilities and detection methods, which is applied in the field of firmware unknown vulnerability detection based on vulnerability analysis, and can solve problems such as incomplete confirmation of vulnerabilities, false positives of static firmware vulnerability detection methods, and failure to consider firmware program path constraints in IoT devices.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 2
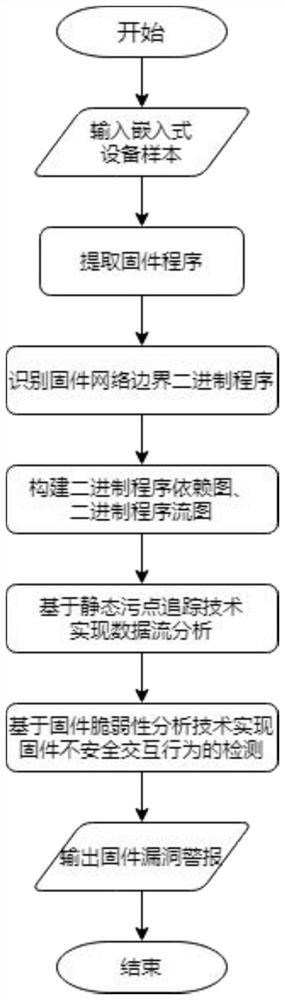
[0077] The present invention needs to provide input firmware sample source paths, firmware parameters, binary file base addresses, import user output functions, and firmware architecture information. In addition, it also provides a list of binary files that firmware needs to analyze, a list of network interactive binary programs, and a list of binary programs. Shared data keys for communication, global variable addresses entered by users, etc.
[0078] After accepting the above input, the system can complete the vulnerability detection of the input firmware sample. When the embedded device system has the vulnerability that can be exploited by the attacker, it will give an alarm, and the relevant information will be written. Firmware vulnerability analysis log.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com