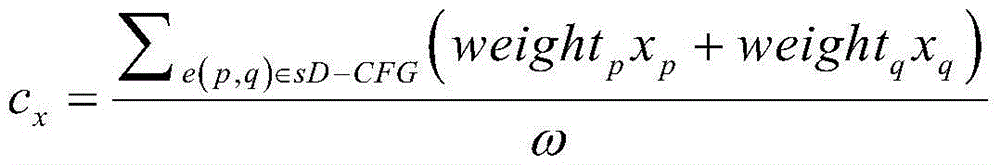Android platform counterfeit application detection method based on program dependency graph
A technology of program dependency graph and detection method, applied in the field of mobile terminal application security, can solve the problems of accuracy and scalability discount, plagiarism of labor results, loss of advertising revenue and user reputation, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0026] The present invention will be described in further detail below through specific embodiments and accompanying drawings.
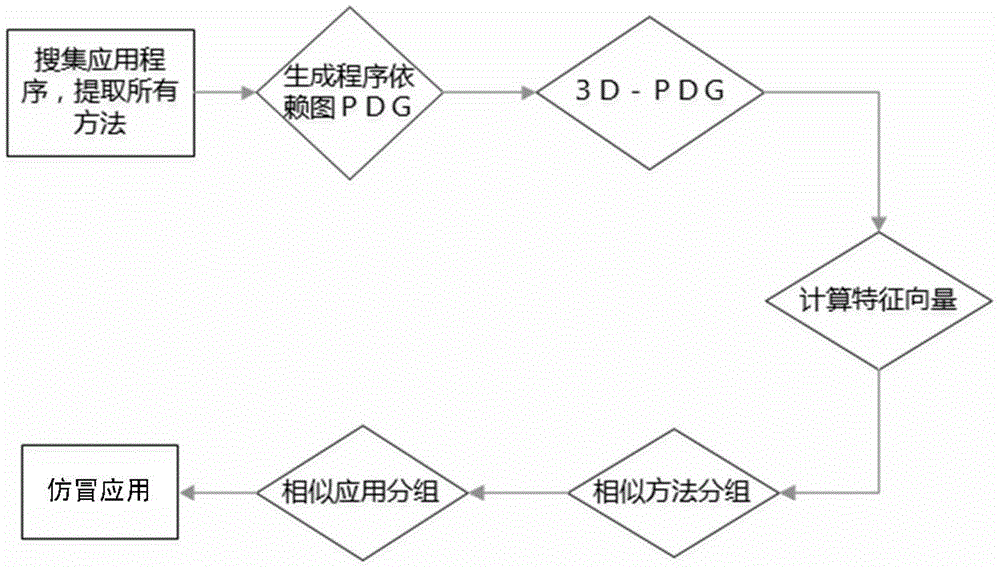
[0027] figure 1 It is an overall flow chart of Android software counterfeit detection of the present invention, specifically comprising the following steps:
[0028] 1. First, collect the application programs on the market and extract all the methods in the installation package to generate a corresponding program dependency graph. For each graph, use the method proposed by the present invention to calculate its eigenvector.
[0029] The collection of applications on the Android market, the extraction of methods, and the generation of program dependency graphs can all be completed using existing tools and technologies, and will not be repeated here. The present invention mainly proposes a method that abstracts the geometric characteristics of program dependency graphs into a A method for representable vectors.
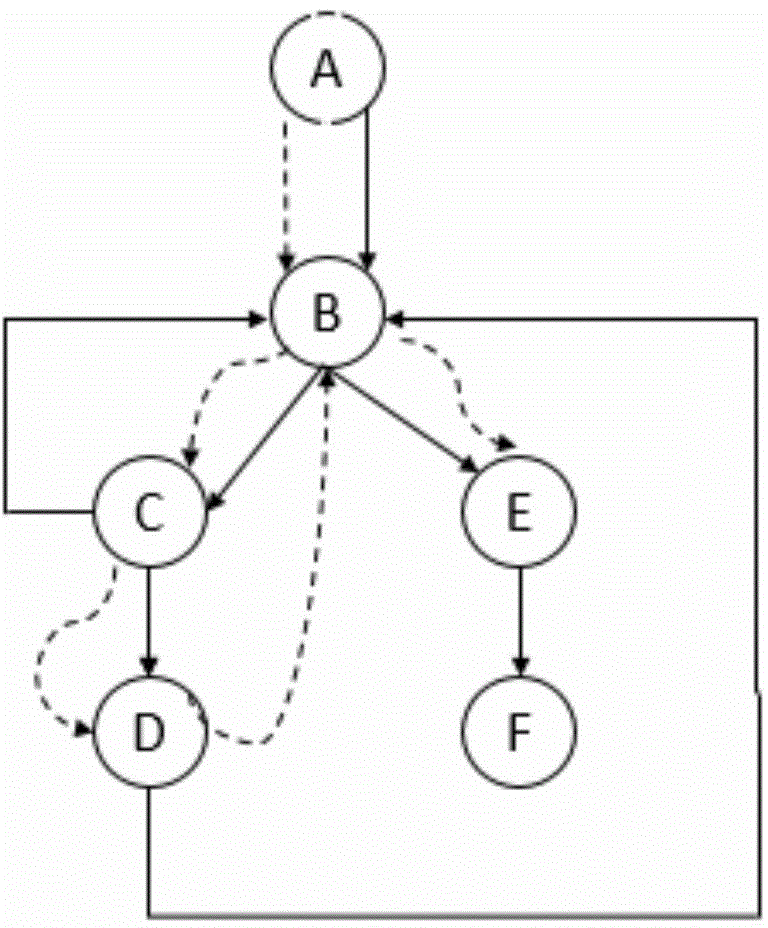
[0030] Program Dependence Graph (Prog...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com