Secure session keys context
a session key and context technology, applied in the field of secure wireless communications, to achieve the effect of faster and more efficient handoffs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
IV. Session Keys Context
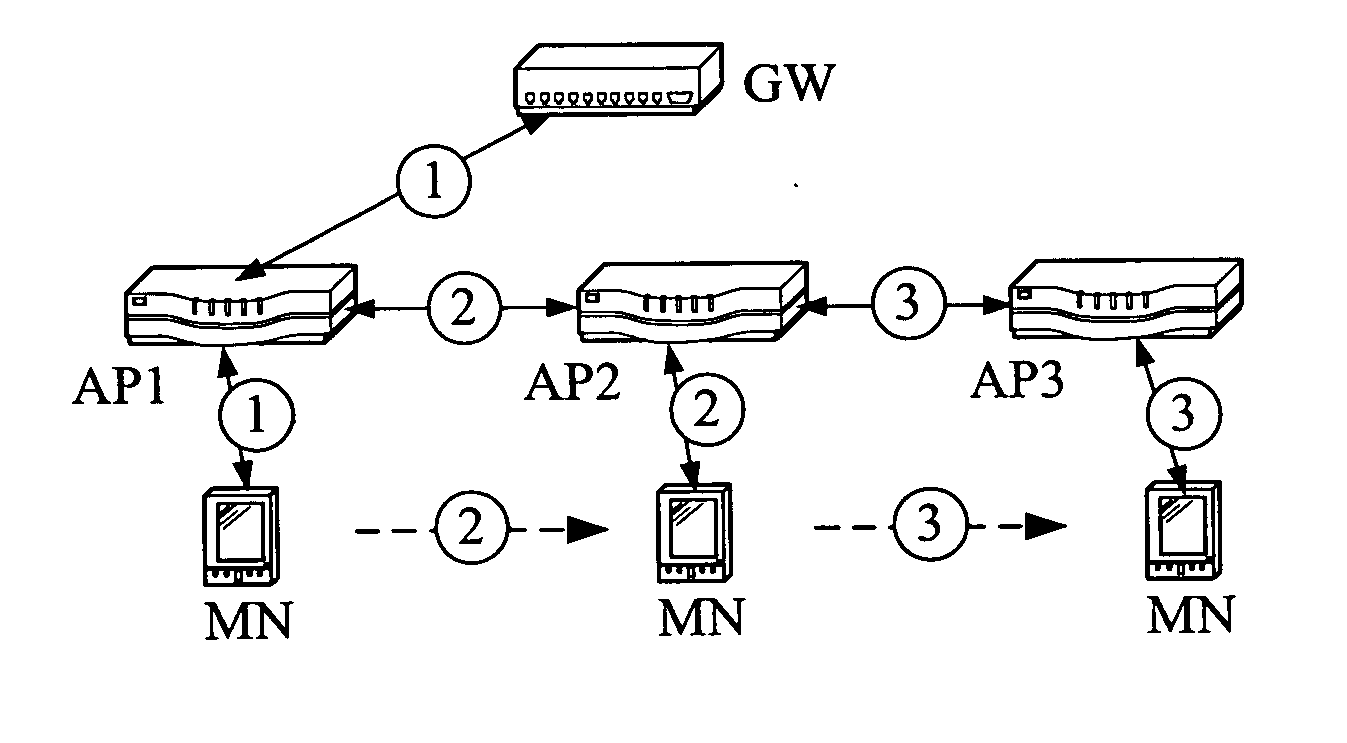
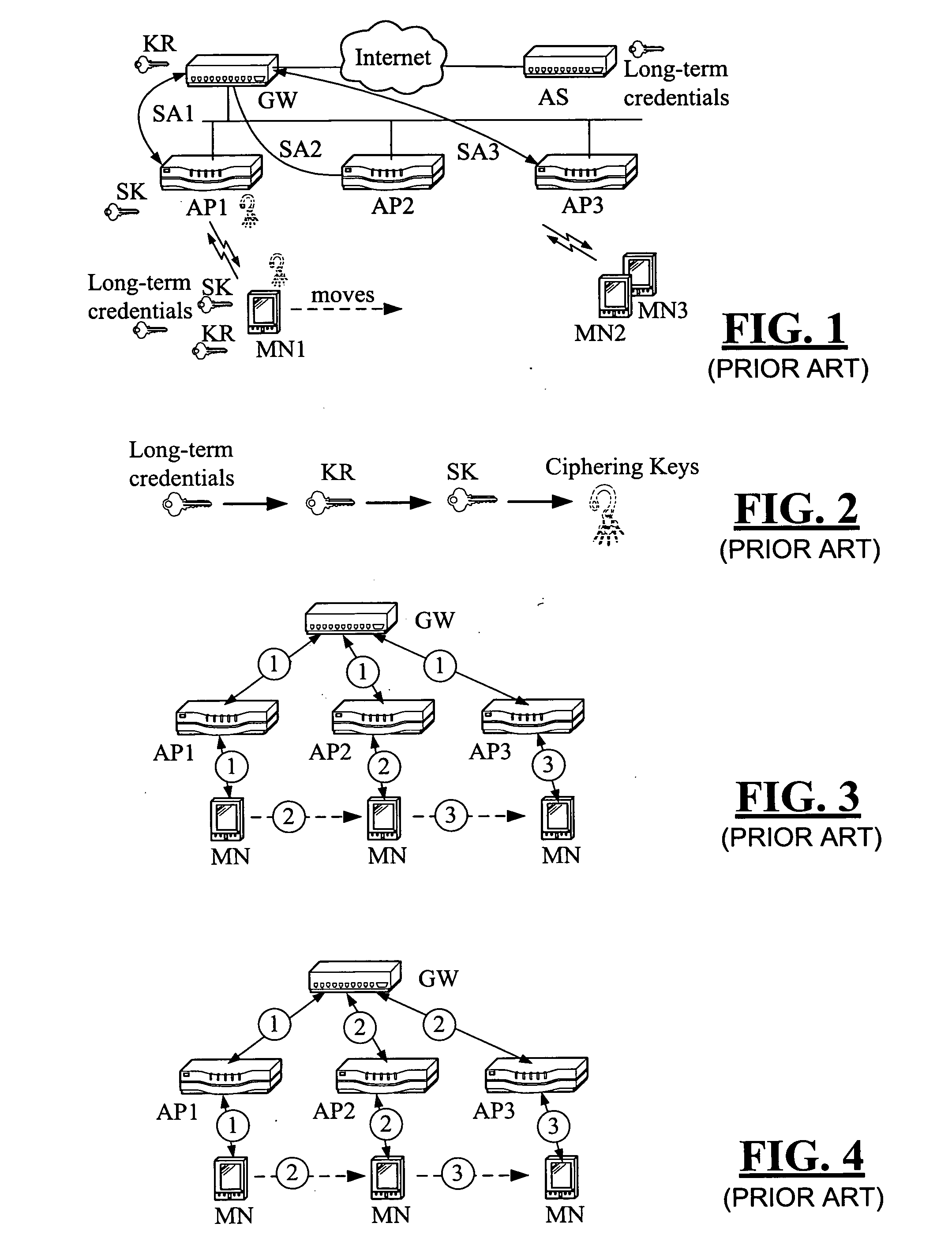
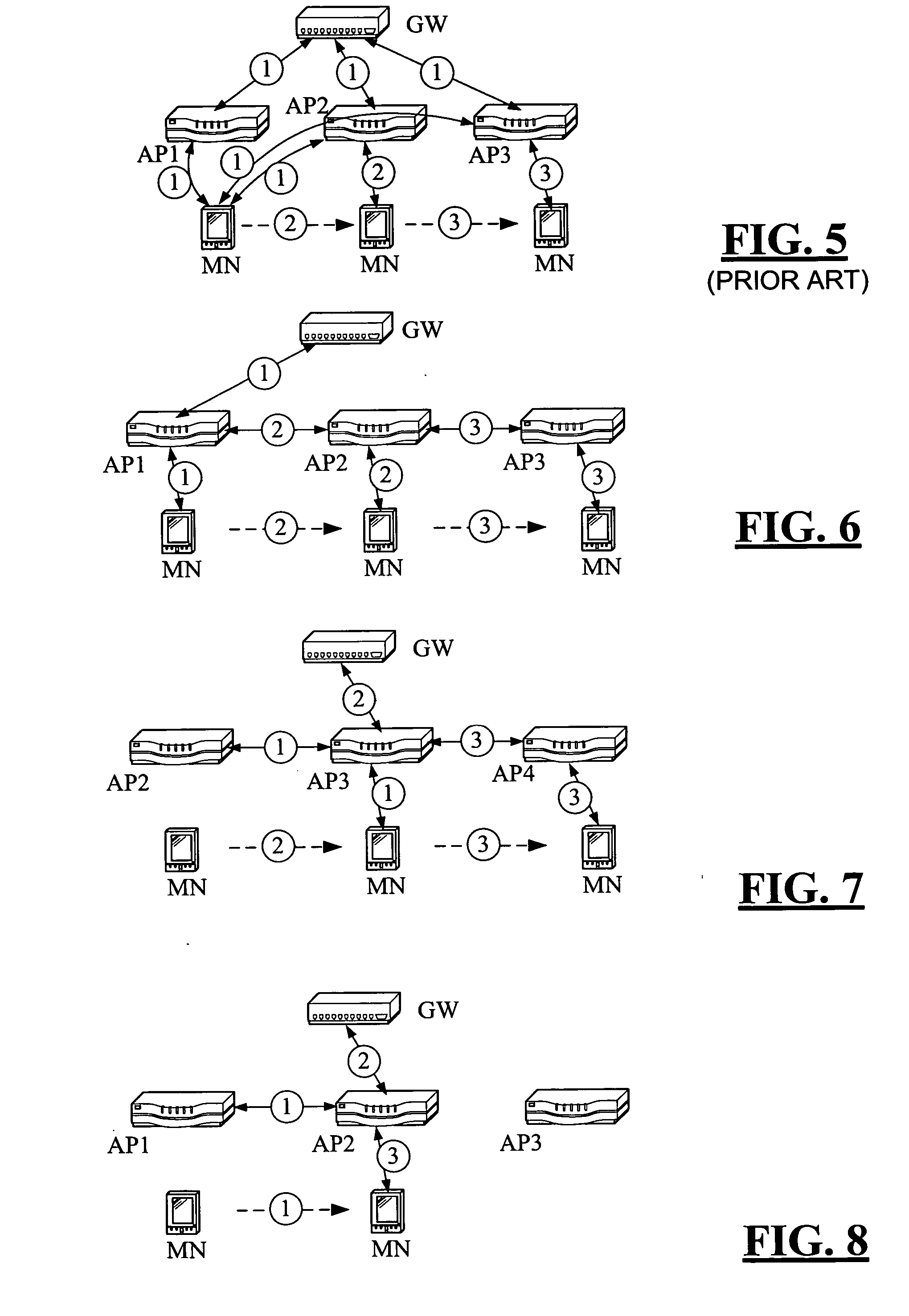
[0067] Context transfer is a mechanism to transfer MN specific session data from one node to another. The context transfer requires a protocol, for example the Context Transfer Protocol (CTP) [14], currently being defined in the IETF. It is designed to be used between Access Routers during handoffs [3]. Session context could contain for example header compression state, QoS settings, filtering rules, and an accounting counter, etc. IEEE has also defined a signaling protocol between Access Points [9]. WiMAX Forum is also specifying a protocol between Base Stations (=APs). An assumption in this specification is that context transfers are possible between Access Points either by using IETF CTP, IEEE 802.11F or something else. The assumption is that a context gets transferred from an old AP to a new AP in one or more packets. This can happen either proactively (old AP pushes the context to the new AP) or reactively (new AP pulls the context from the old AP) depen...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com