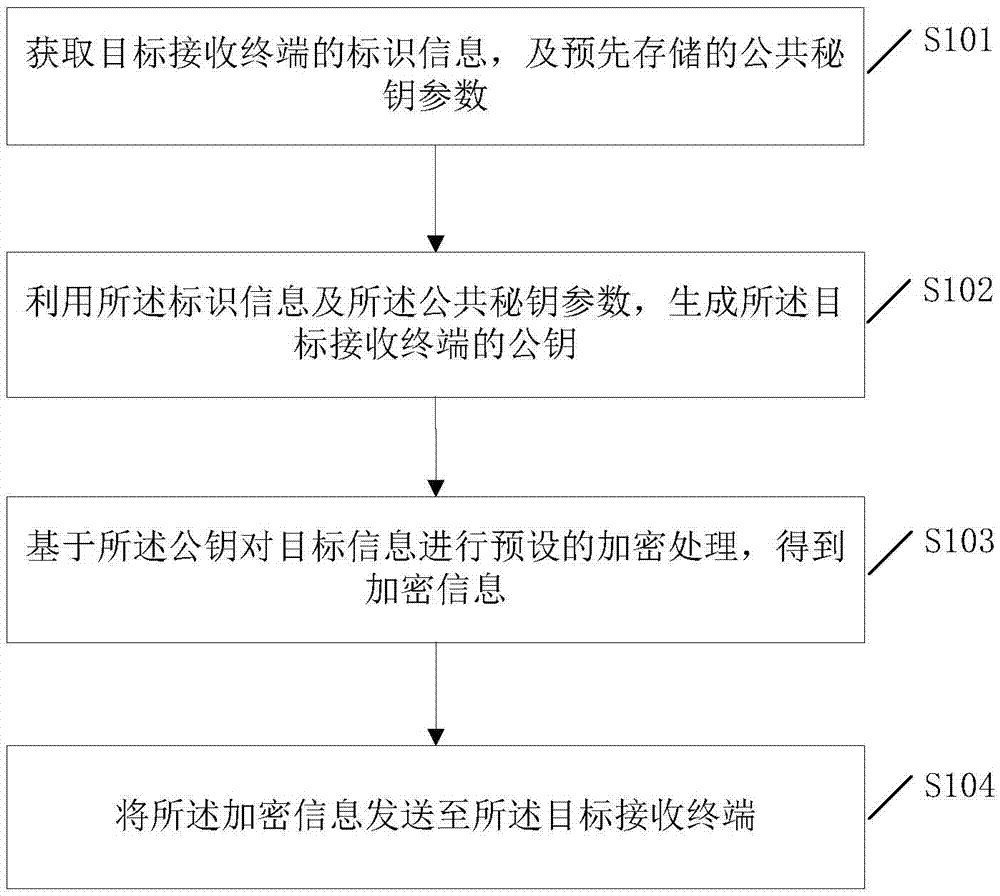
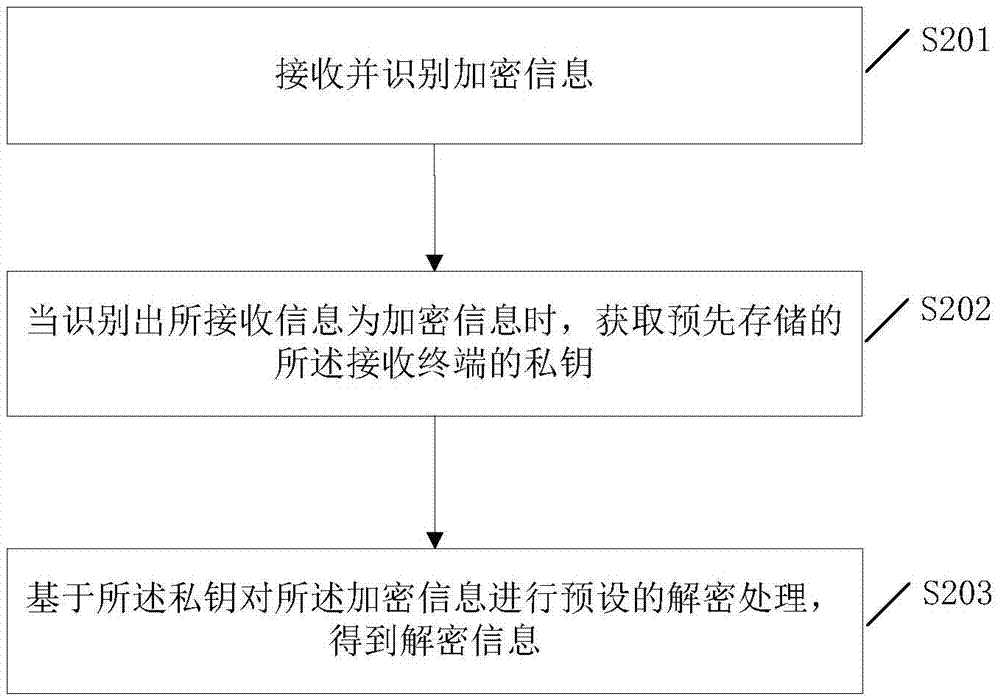
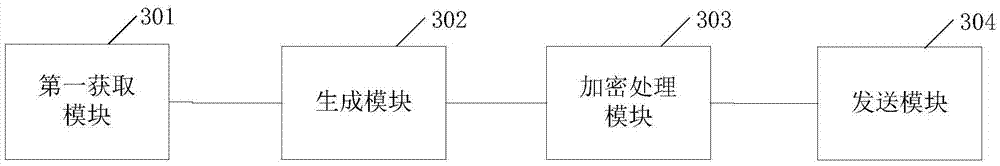
Patents
Literature
150 results about "End-to-end encryption" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
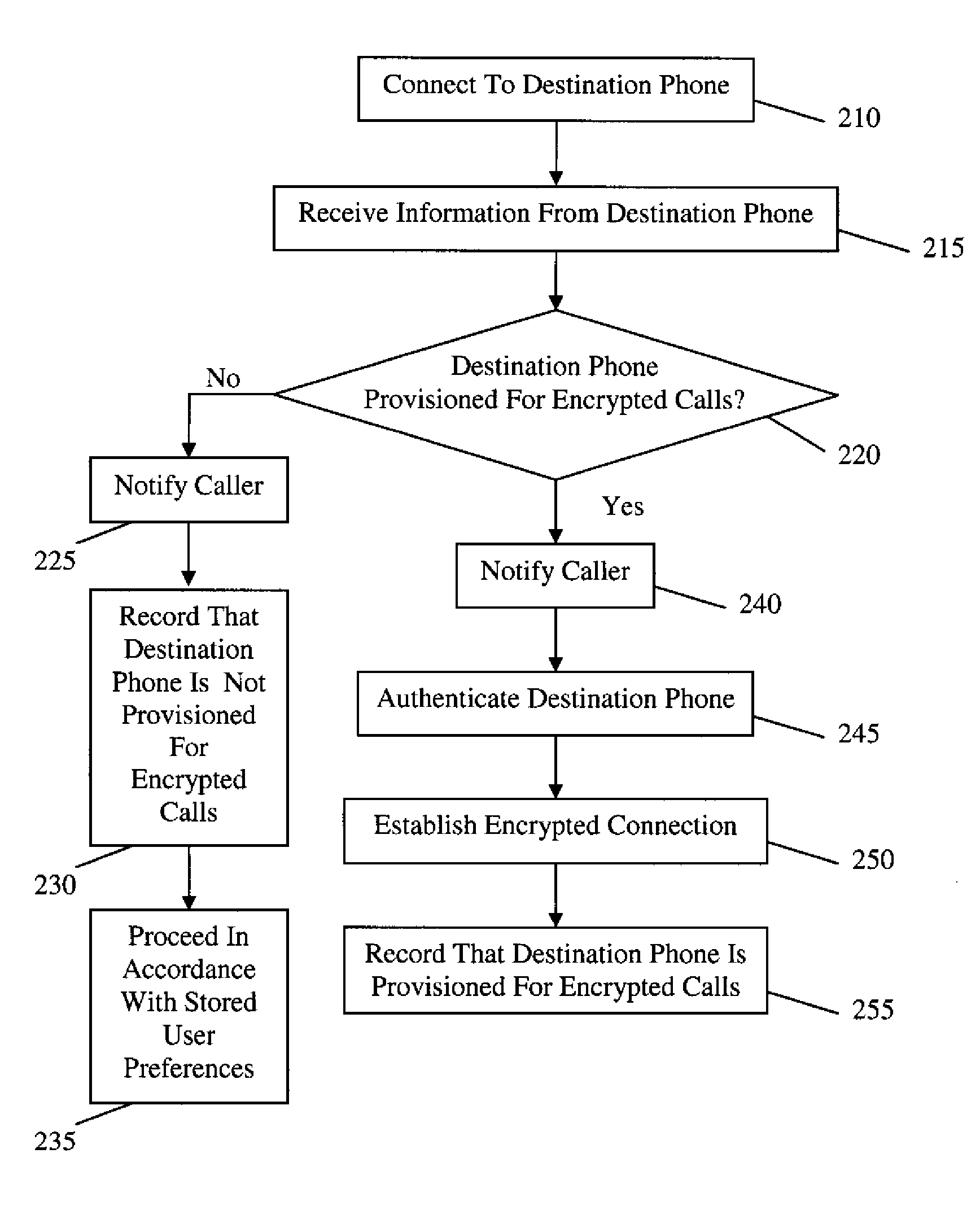
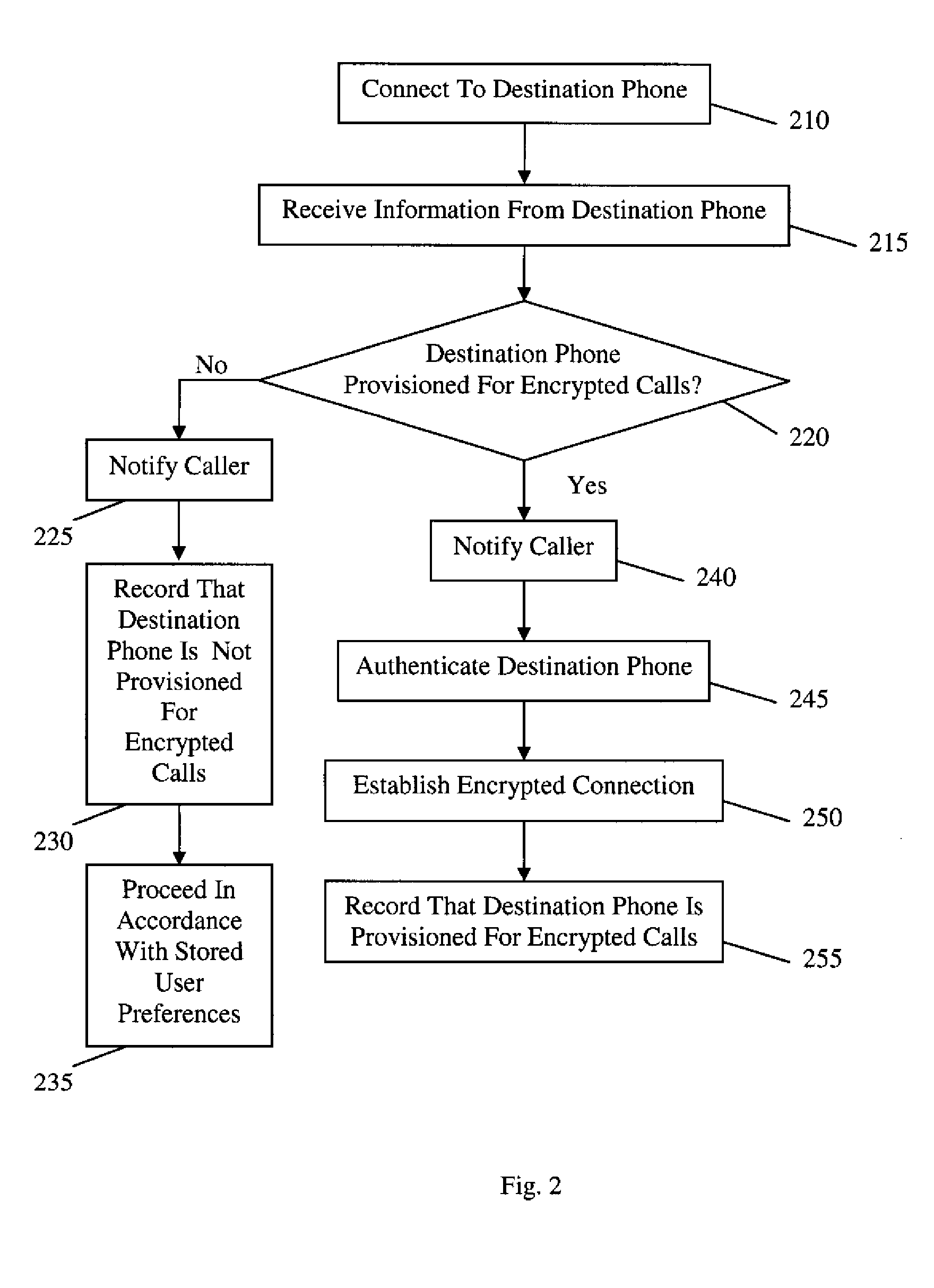
End-to-end encryption (E2EE) is a system of communication where only the communicating users can read the messages. In principle, it prevents potential eavesdroppers – including telecom providers, Internet providers, and even the provider of the communication service – from being able to access the cryptographic keys needed to decrypt the conversation.
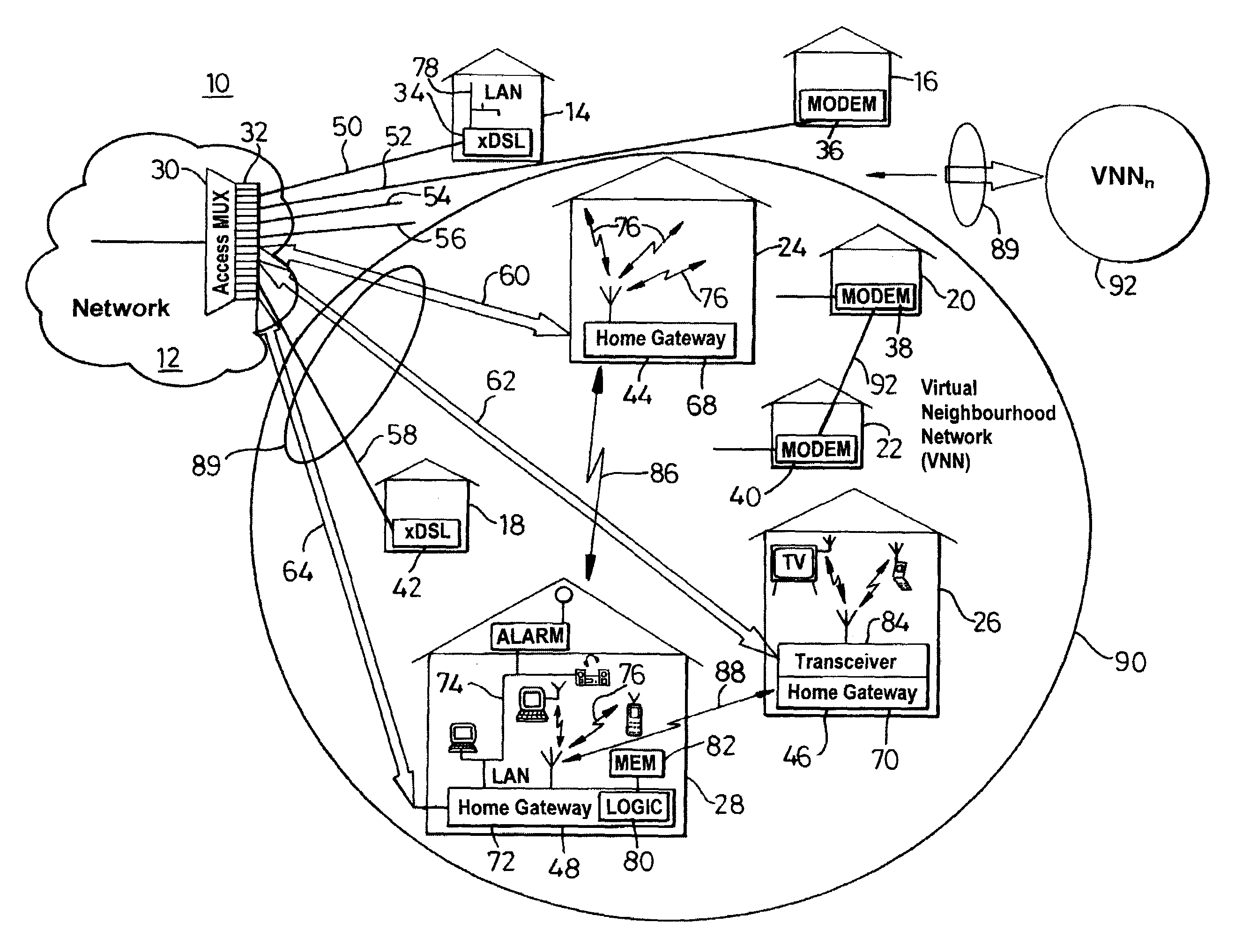
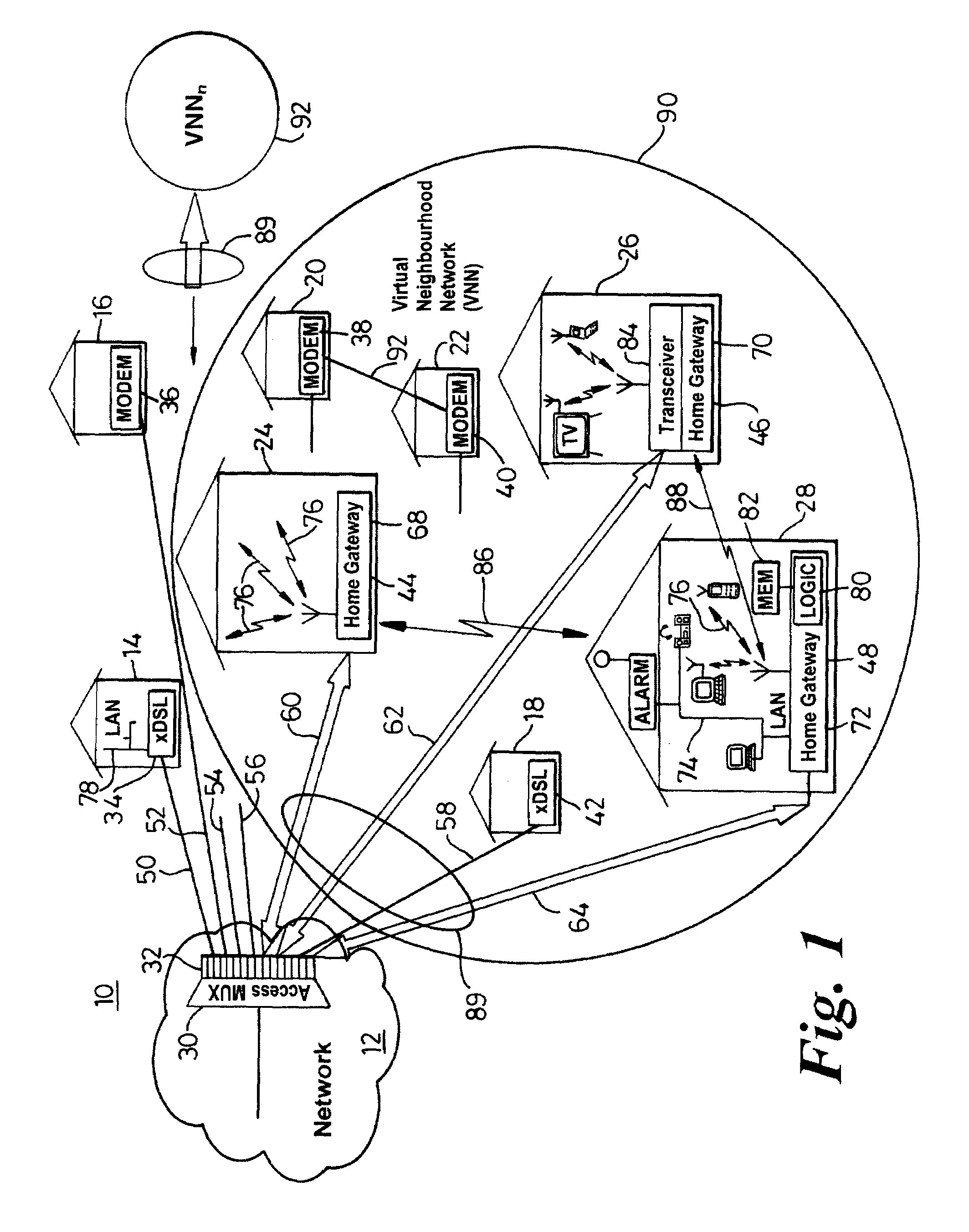
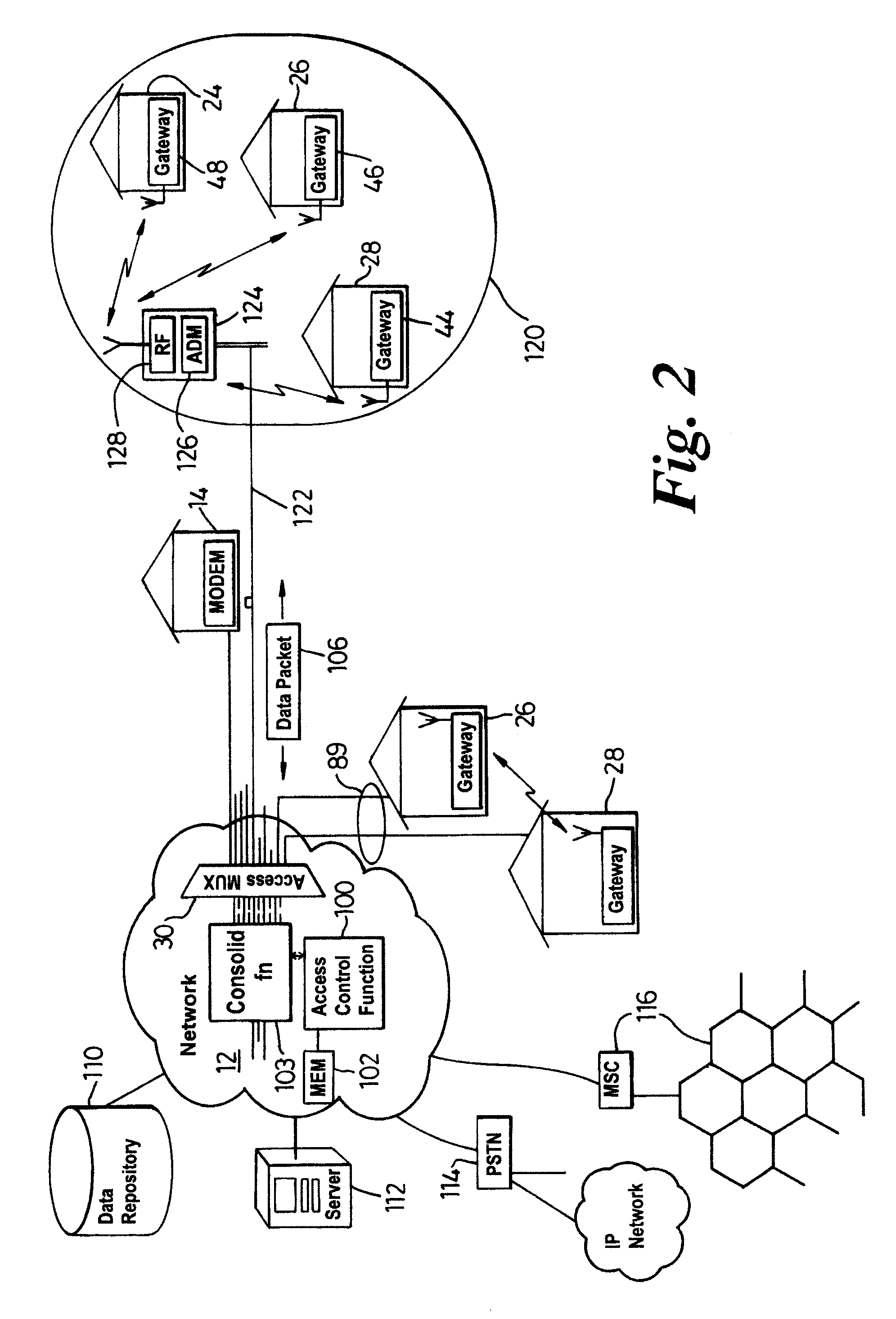
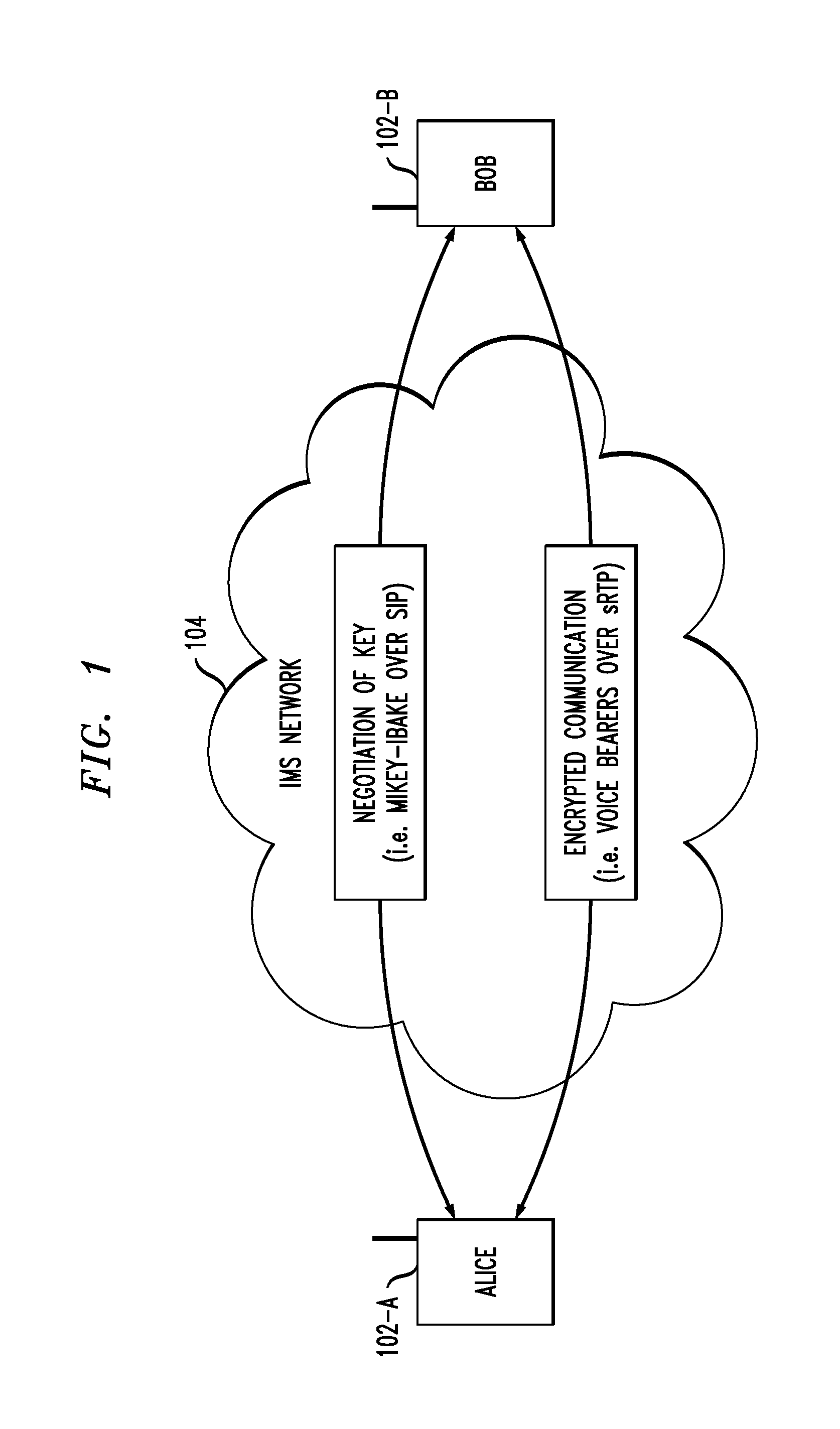
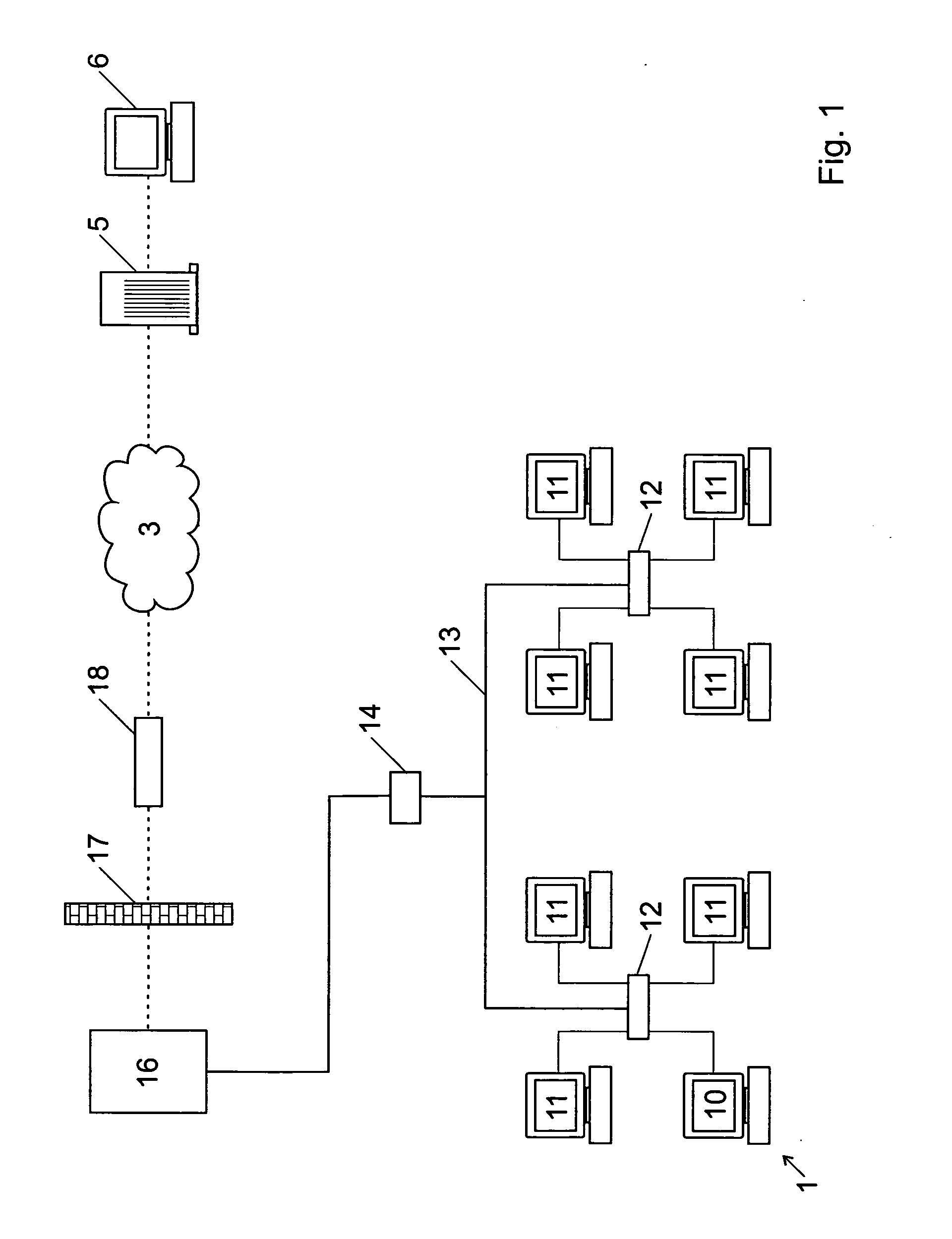
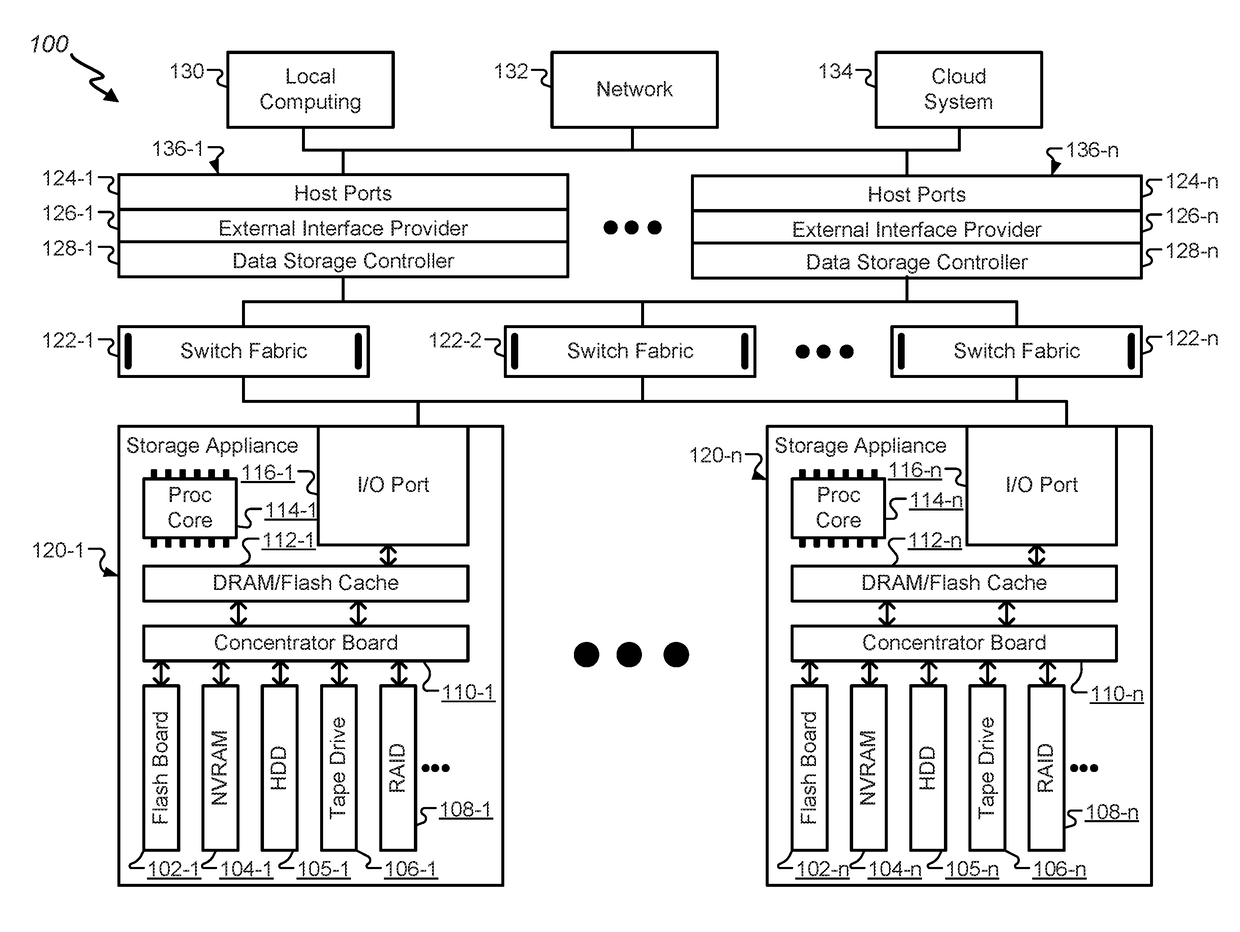
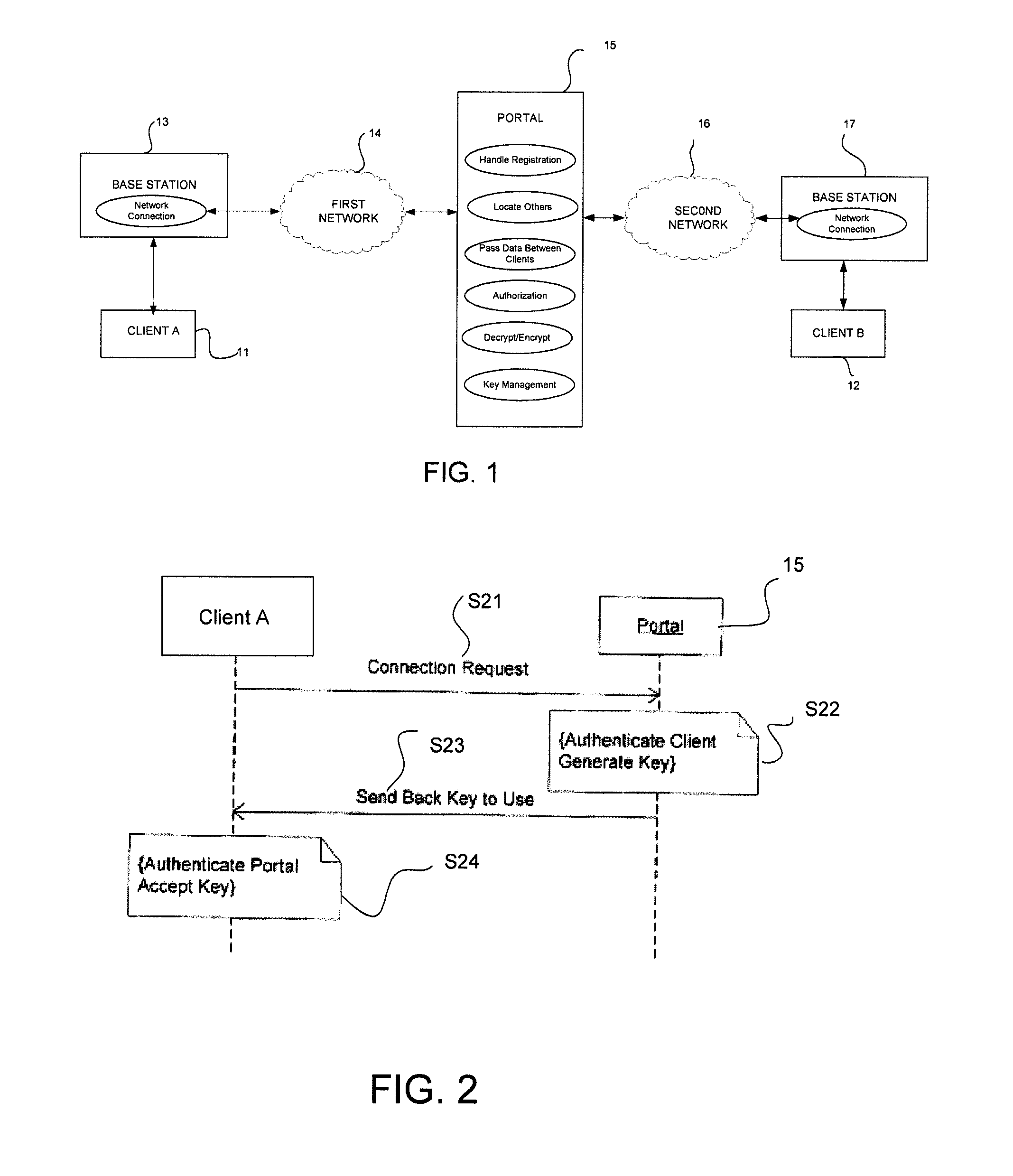
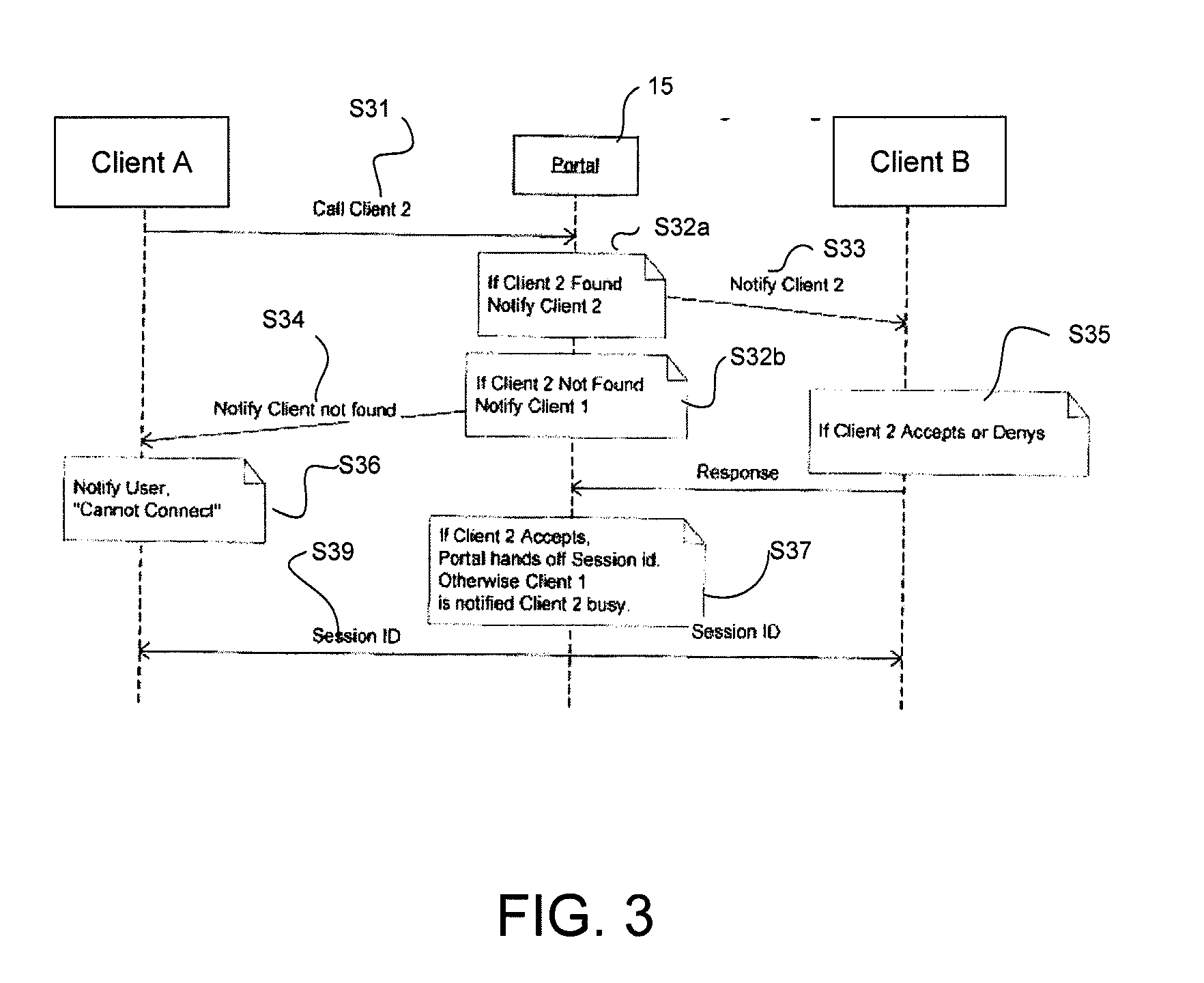
Communication system architecture and operating methodology providing a virtual neighborhood network
InactiveUS7142503B1Overcome bandwidth limitationIncreased peak bandwidth capacityError preventionFrequency-division multiplex detailsEnd-to-end encryptionTransceiver
A communication system (10) supports the provision of a plurality of dedicated communication resources (50–64), such as copper drops, RF links and optical fibers, to dedicated home-gateway devices (44–48) or distribution points (124). The communication resources (50–64) support broadband interconnection (104) between the dedicated home-gateway devices (44–48) or distribution points (124) and an access multiplexor (30) in a network (12). Each gateway device (44–48) or distribution point (124) generally includes a local RF transceiver (84) and associated control logic (80–82) that allows local communication (86) between gateway devices (44–48) and hence statistically multiplexed access (60–64, 89) to multiple communication resources, thereby providing increased bandwidth in uplink and / or downlink directions. With the control logic (80) operable to provide a routing and prioritisation / arbitration function, each gateway (44–48) is able to selectively engage use of supplemental, non-reserved communication resources usually associated with a dedicated ono-to-one connection between the access network (12) and at least one secondary gateway. Physical layer access to information routed via a secondary gateway within a virtual neighborhood network (90–92) comprising several gateways is restricted through an end-to-end encryption algorithm between an originating gateway and, at least, the access multilpexor (30).
Owner:RPX CLEARINGHOUSE
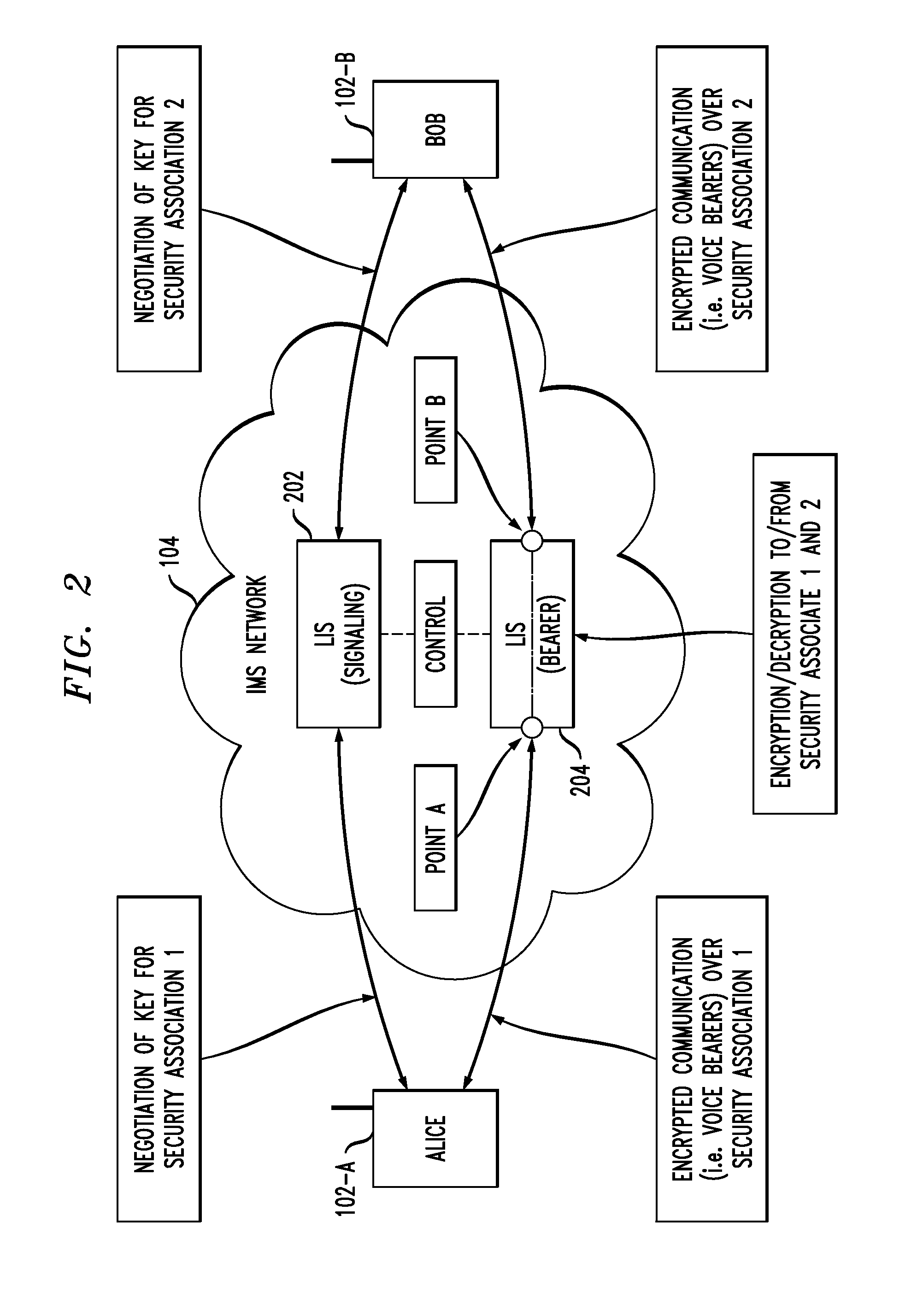
Policy routing-based lawful interception in communication system with end-to-end encryption
Techniques are disclosed for lawfully intercepting information in communication environments with end-to-end encryption. For example, a method for intercepting encrypted communications exchanged between a first computing device and a second computing device in a communication network, wherein the interception is performed by a third computing device in the communication network, comprises the following steps. The third computing device obtains one or more packets having a packet address associated with one of the first computing device and the second computing device. The one or more packets are obtained by the third computing device, in response to at least one interception routing policy being implemented in at least one element in the communication network, such that the one or more obtained packets may be decrypted so as to obtain data contained therein. The third computing device preserves the packet address of the one or more obtained packets. The third computing device forwards the one or more packets toward a packet-destination one of the first computing device and the second computing device such that the packet-destination one of the first computing device and the second computing device is unable to detect from the one or more packets that the one or more packets were intercepted by the third computing device.
Owner:ALCATEL LUCENT SAS
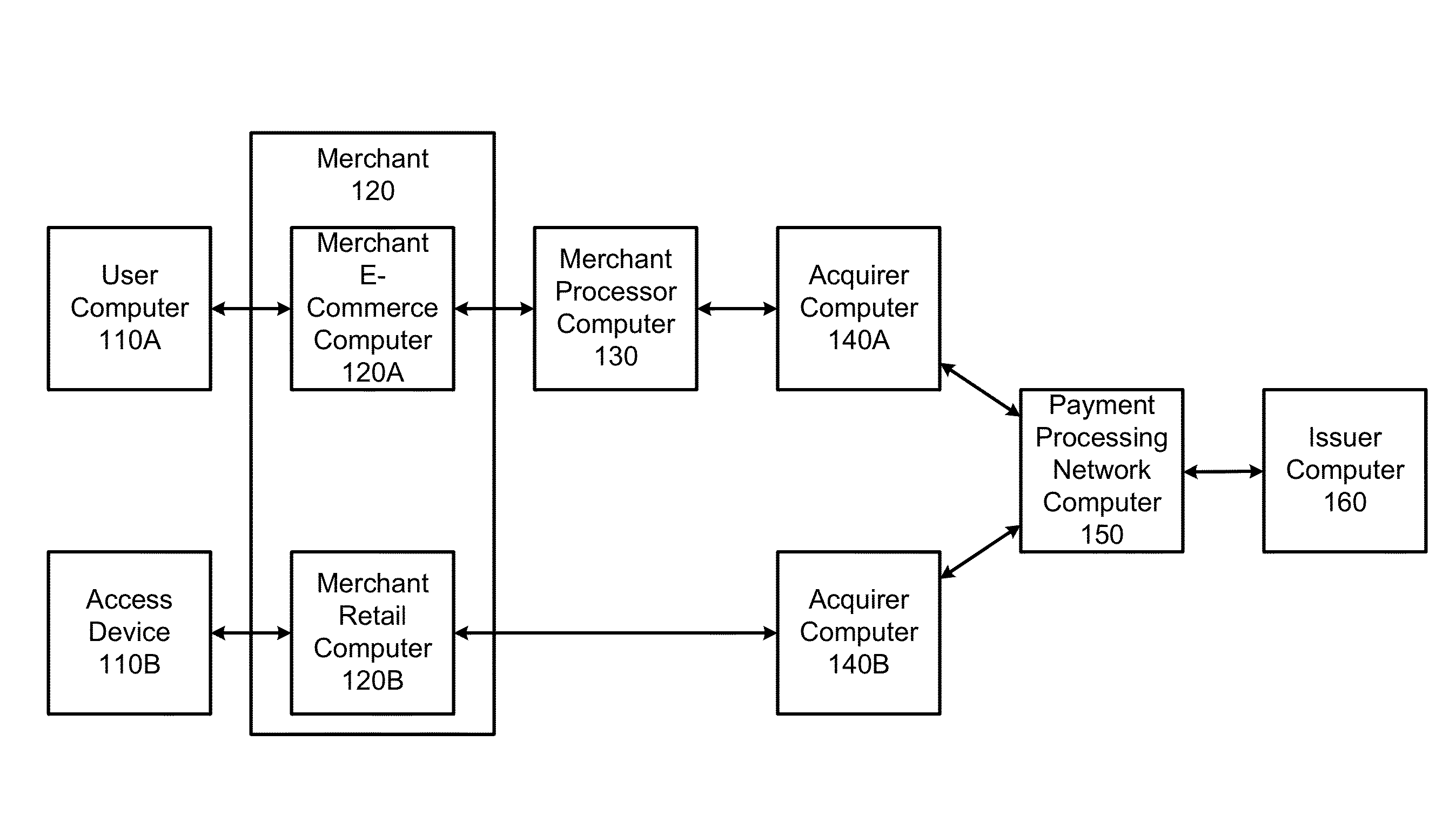
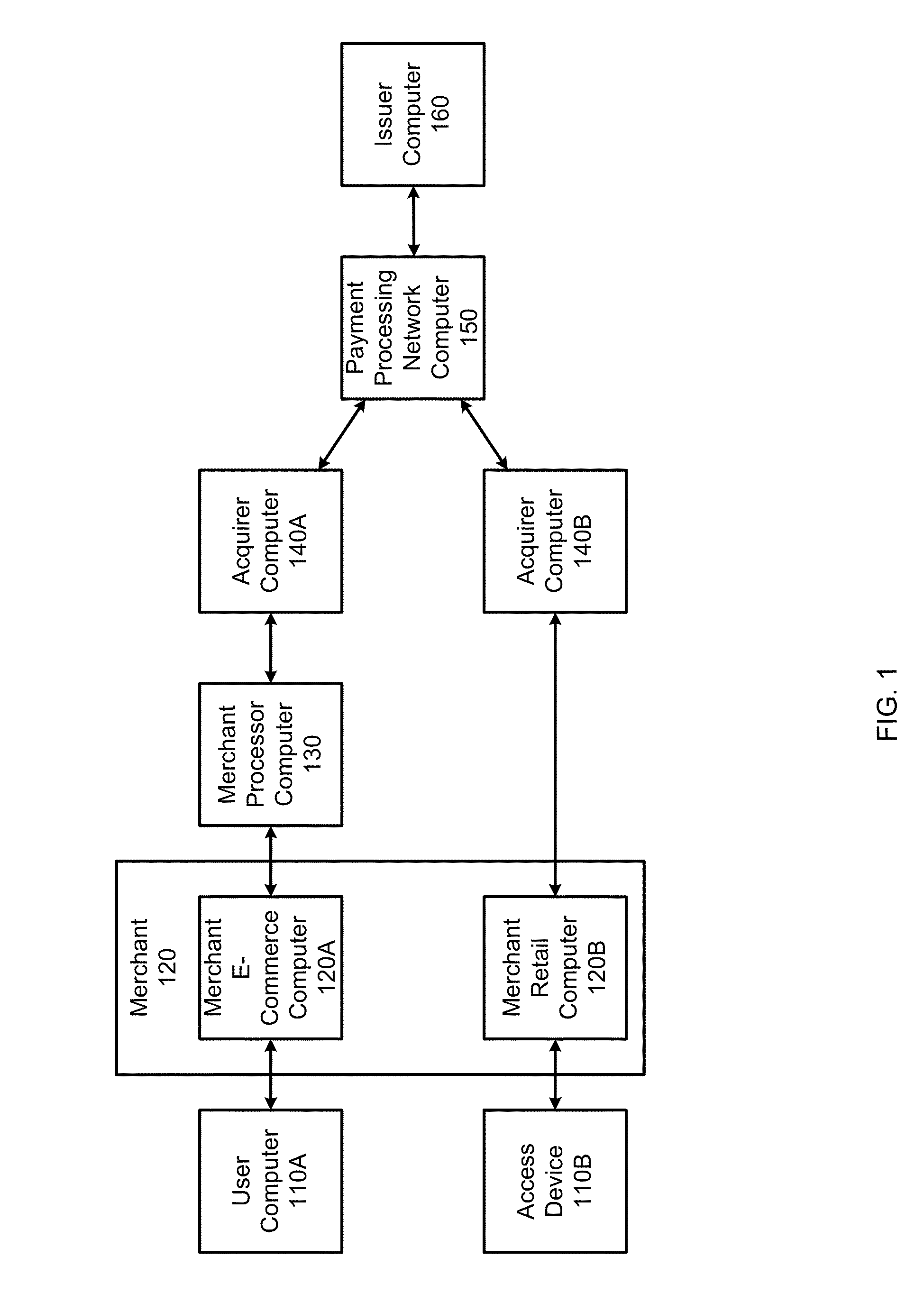
Embedded acceptance system
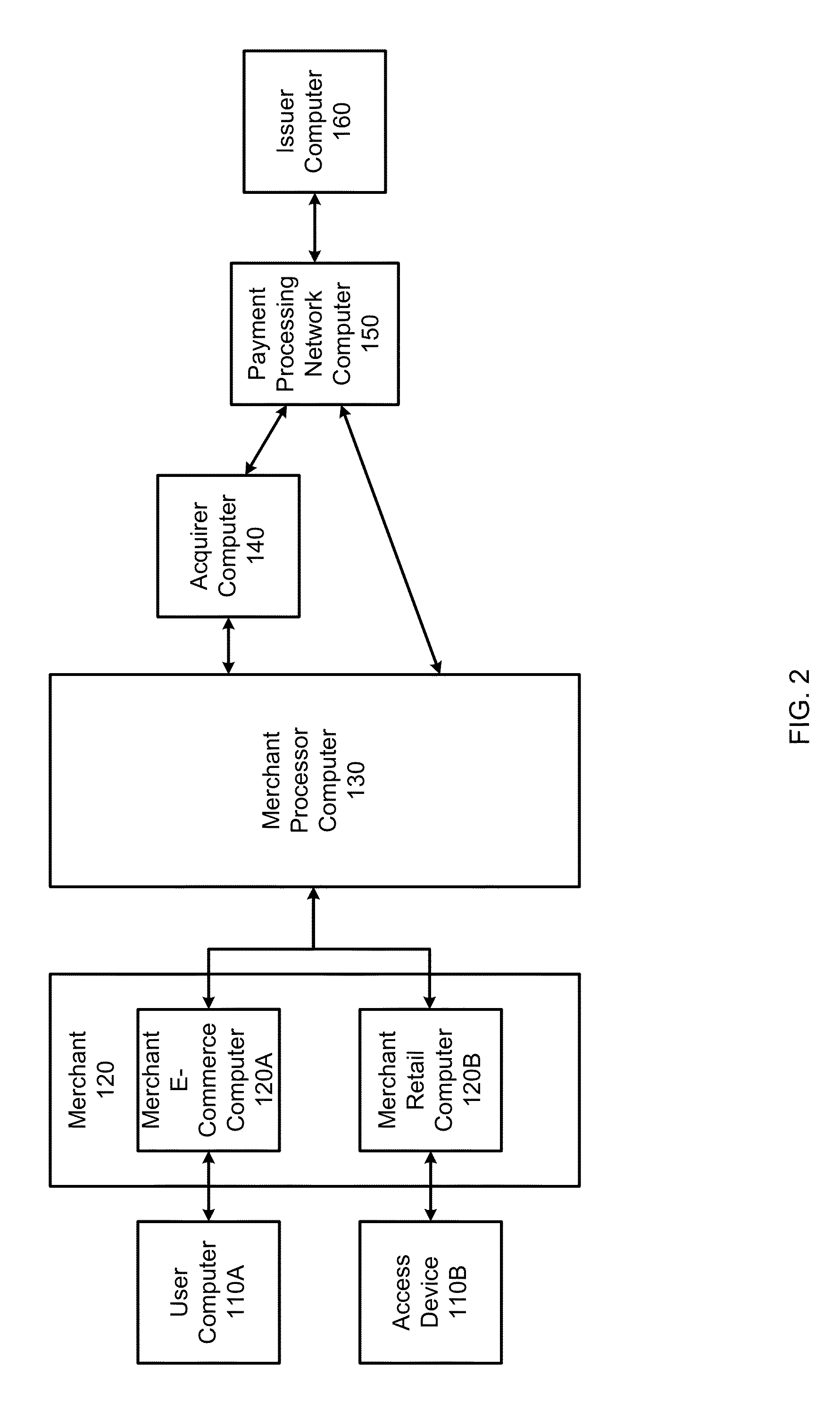
InactiveUS20140310183A1Reduce management costsImprove securityFinancePayment protocolsEnd-to-end encryptionPayment
Methods and systems can provide for unified processing of merchant transactions over various payment channels over which the transactions originate, such as in-person retail transactions and e-commerce transactions. For example, transactions can be received from payment channels through different payment channel-specific interfaces. The transactions from the various payment channels can then be sent to an entry point module that centrally manages the transactions. An orchestrator can then identify payment channel-agnostic transaction services to be applied to the transactions. This can allow for a unified end-to-end encryption implementation across a merchant's enterprise, reducing management costs and improving overall security. Similarly, universal tokenization services, payment and fraud management can be provided across a merchant's entire enterprise.
Owner:VISA INT SERVICE ASSOC
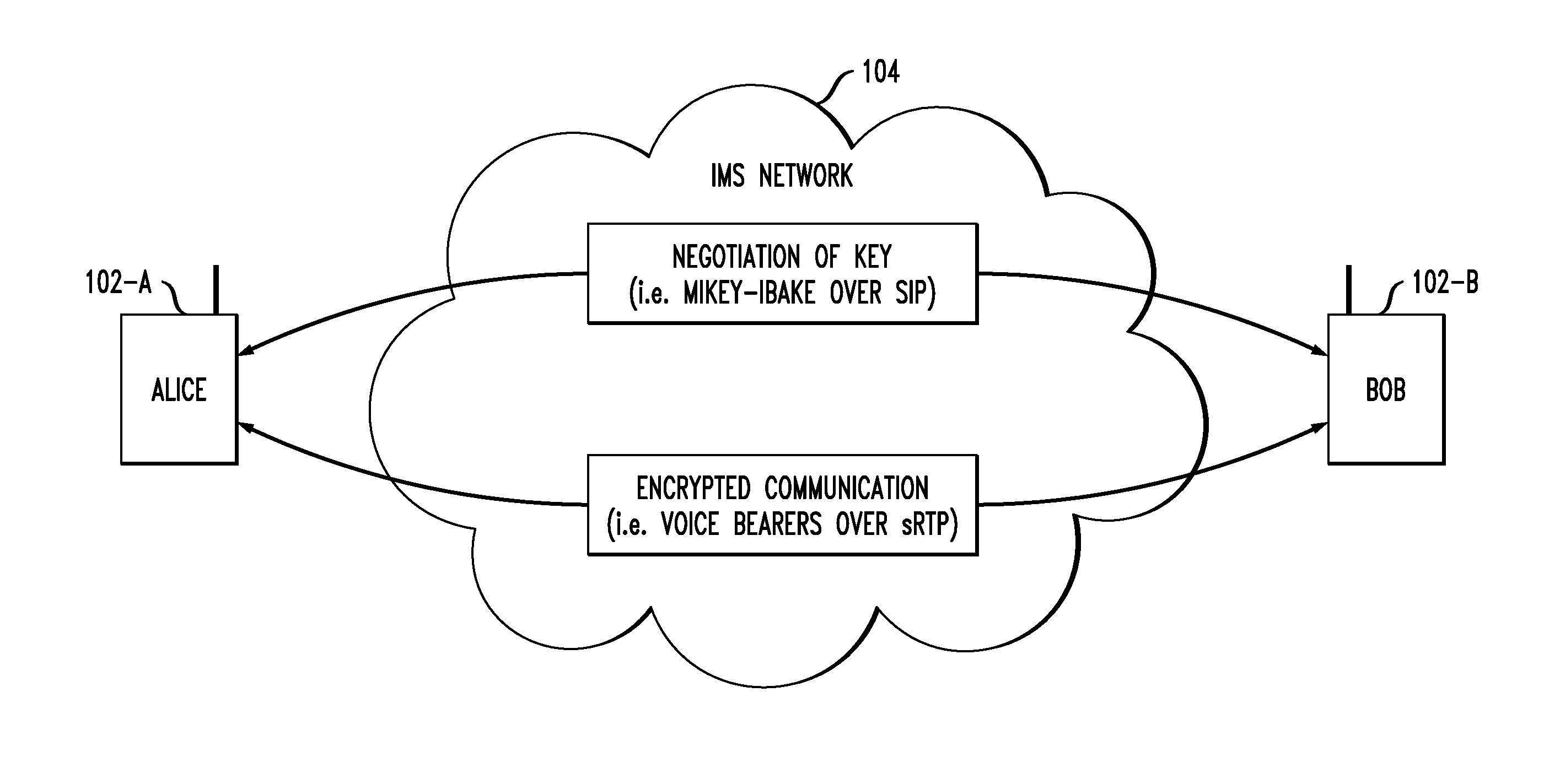
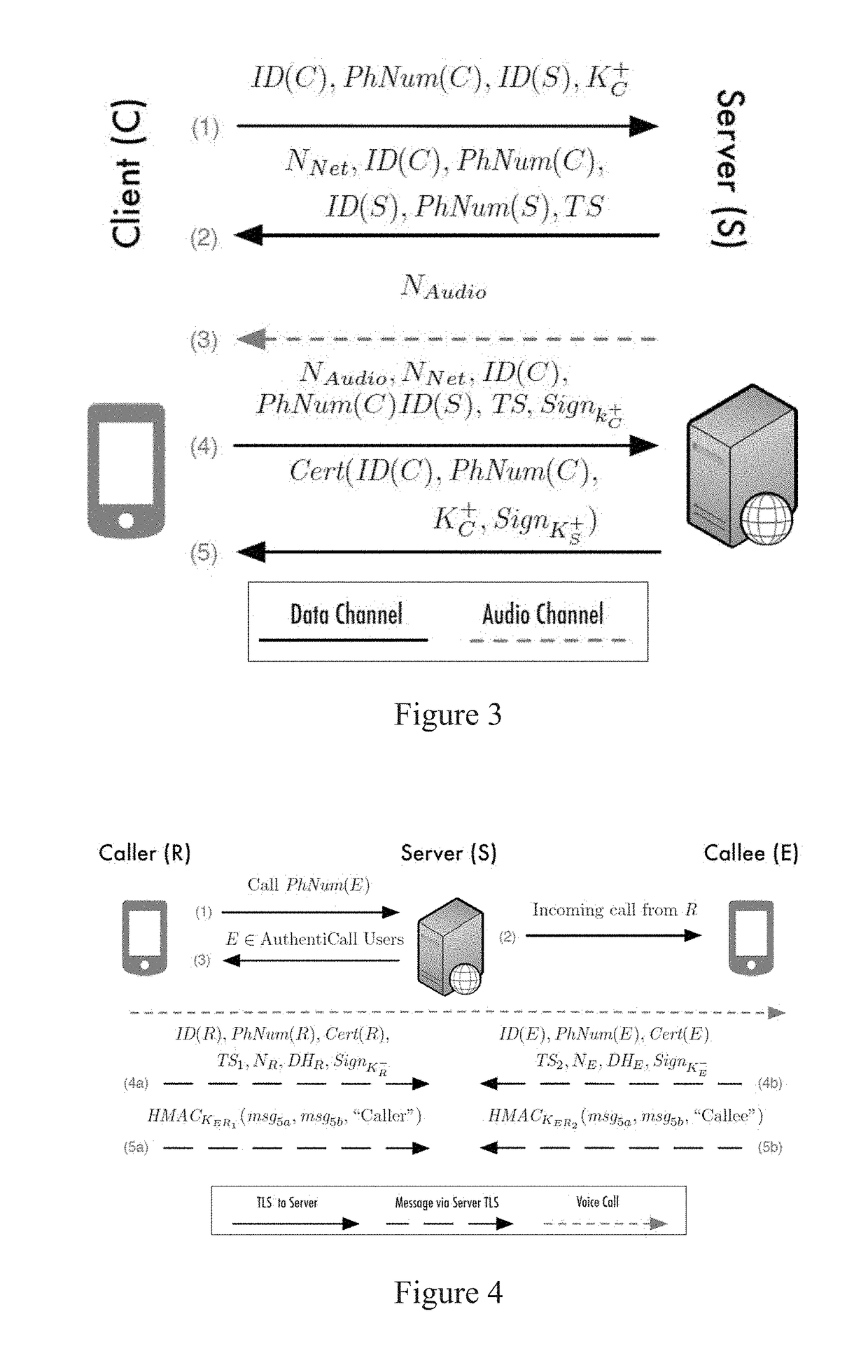
Identity and content authentication for phone calls
ActiveUS20180294959A1Negligible latencyNegligible overheadKey distribution for secure communicationUser identity/authority verificationEnd-to-end encryptionClient-side
Systems and methods for call authentication are provided. A method can include an enrollment protocol that ensures users control the number they claim to own, a handshake protocol that mutually authenticates the calling parties, and a call integrity protocol that ensures the security of the voice channel and the content it carries. A server can act as either an endpoint or intermediary between user clients and client-server architecture can be employed. All protocols can include end-to-end cryptography and the enrollment protocol can issue a certificate that binds the identity of the client to a phone number.
Owner:UNIV OF FLORIDA RES FOUNDATION INC
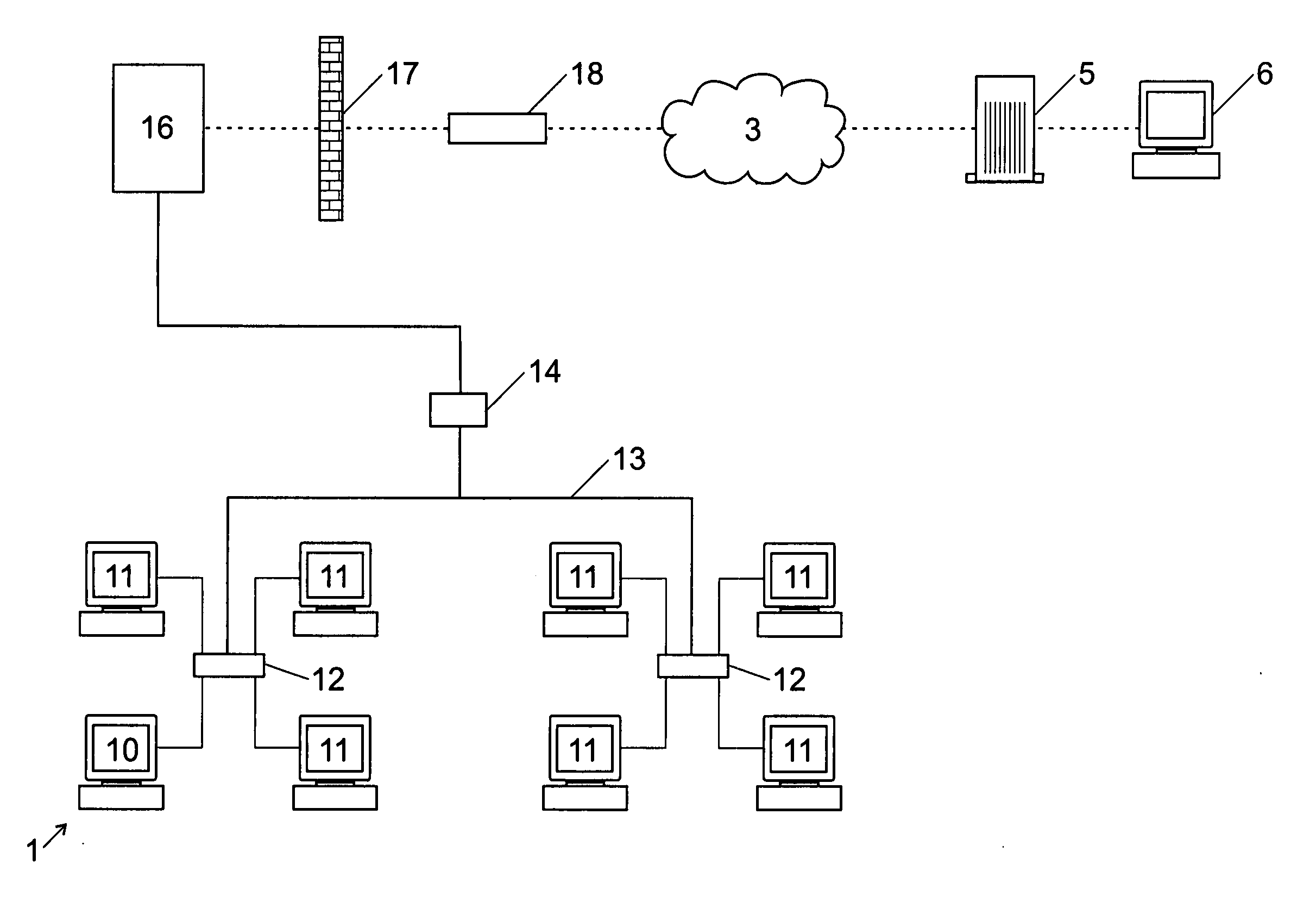
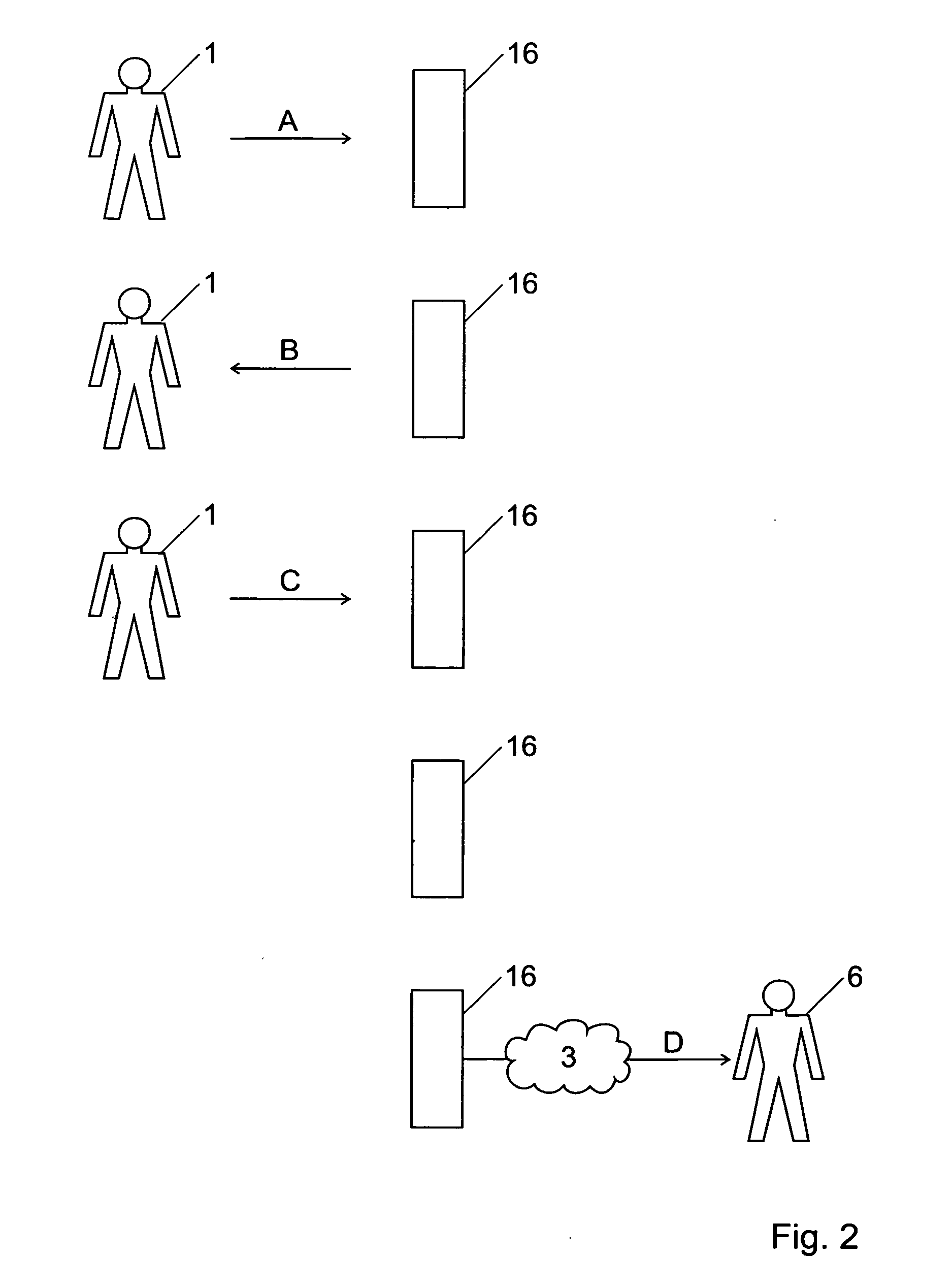
End-to-end encryption method and system for emails
ActiveUS20050114652A1Easy to installControl lossData switching networksSecuring communicationEnd-to-end encryptionInternet privacy
End-to-end encryption method for emails sent from a sender (1) to a recipient (6), comprising the following steps: [0001]the sender requests from an encryption system (16) a certificate corresponding to said recipient (6), [0002]the encryption system (16) returns to said sender (11) a first, proforma certificate corresponding to said recipient (6), [0003]the sender (1) sends with his email client (11) an outgoing email to said recipient encrypted with said proforma certificate, [0004]said email is forwarded through said encryption system (16), [0005]said encryption system (16) decrypts said email using a private key corresponding to said certificate, [0006]said encryption system makes the content of said email available to said recipient (6).
Owner:TOTEMO
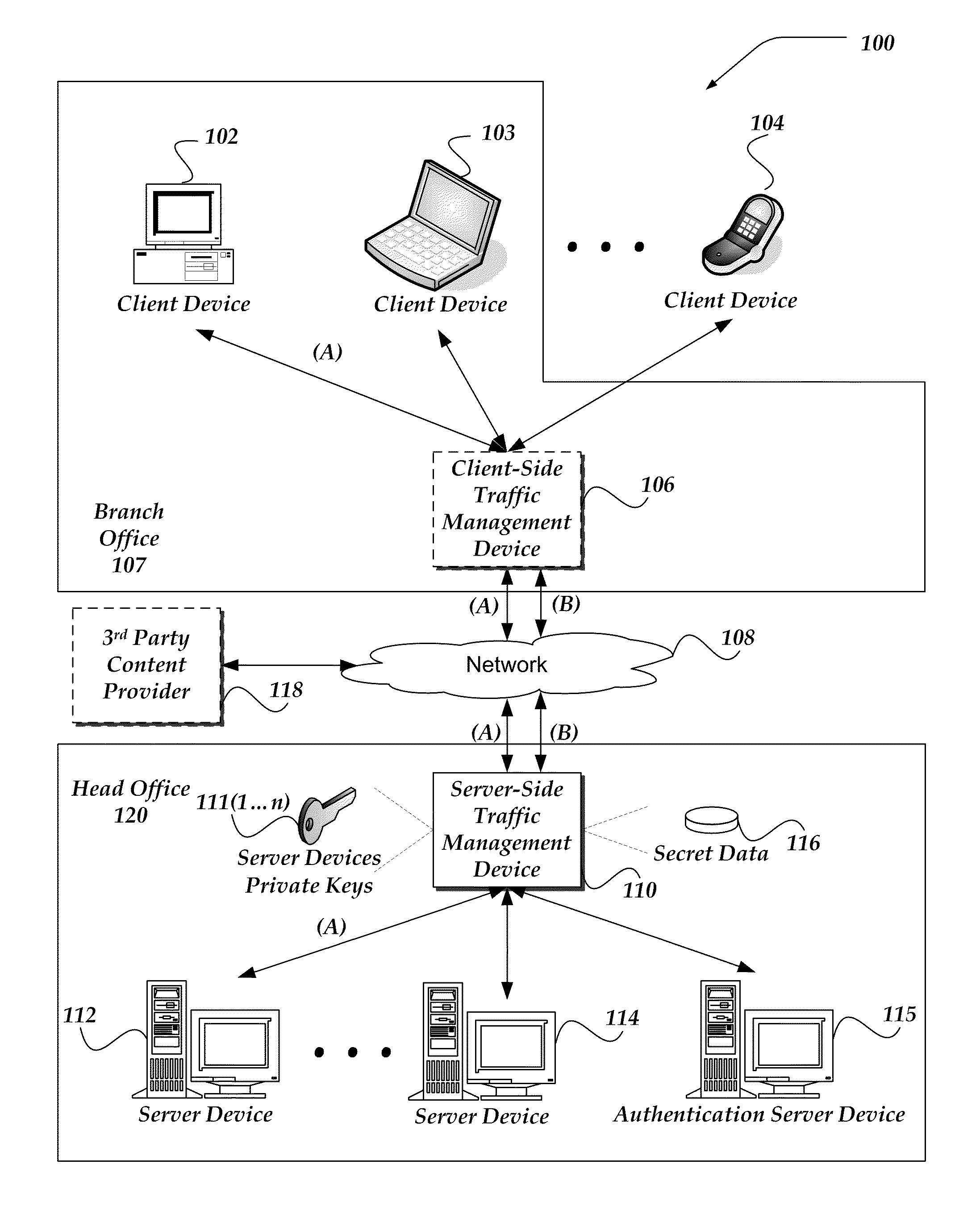
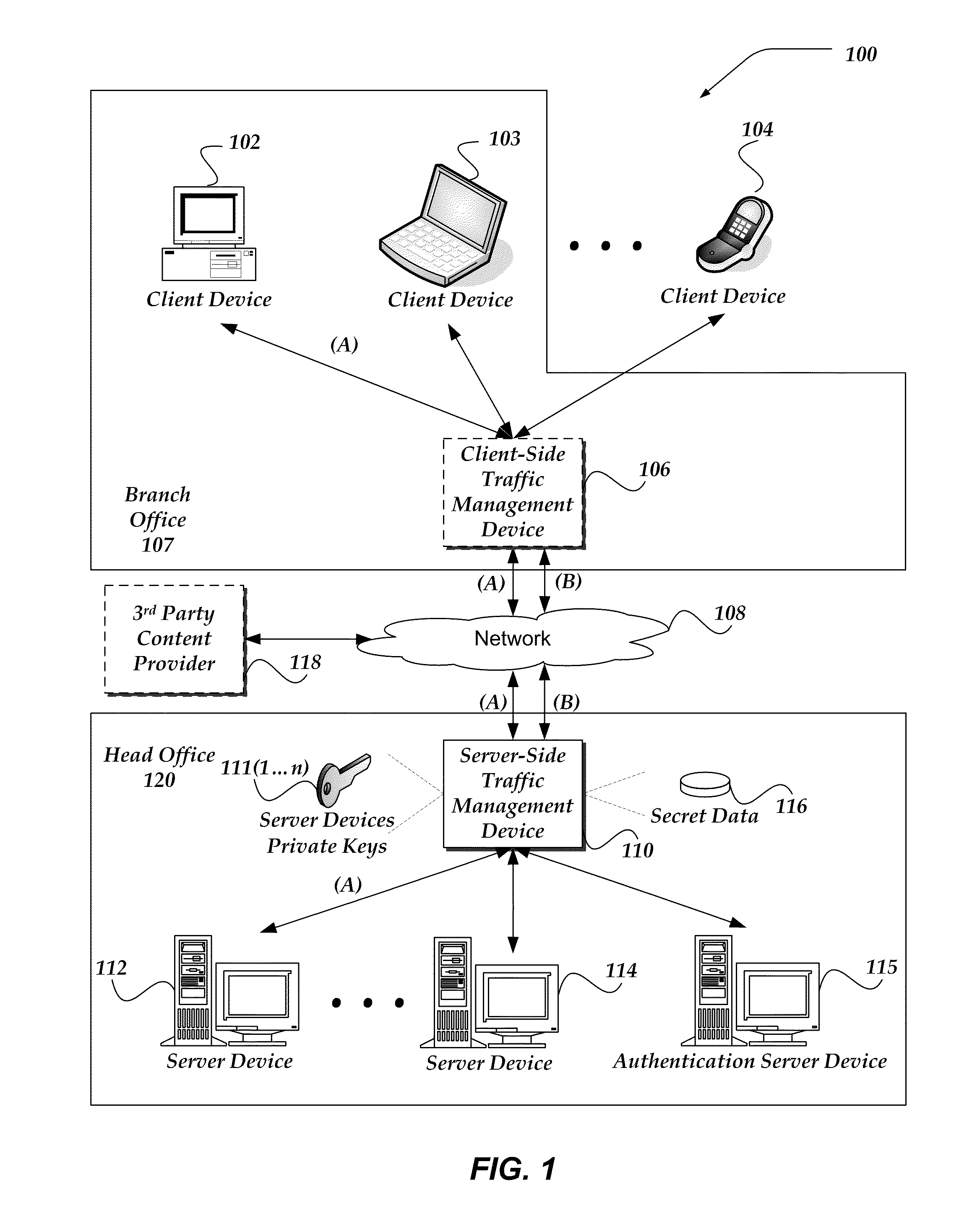
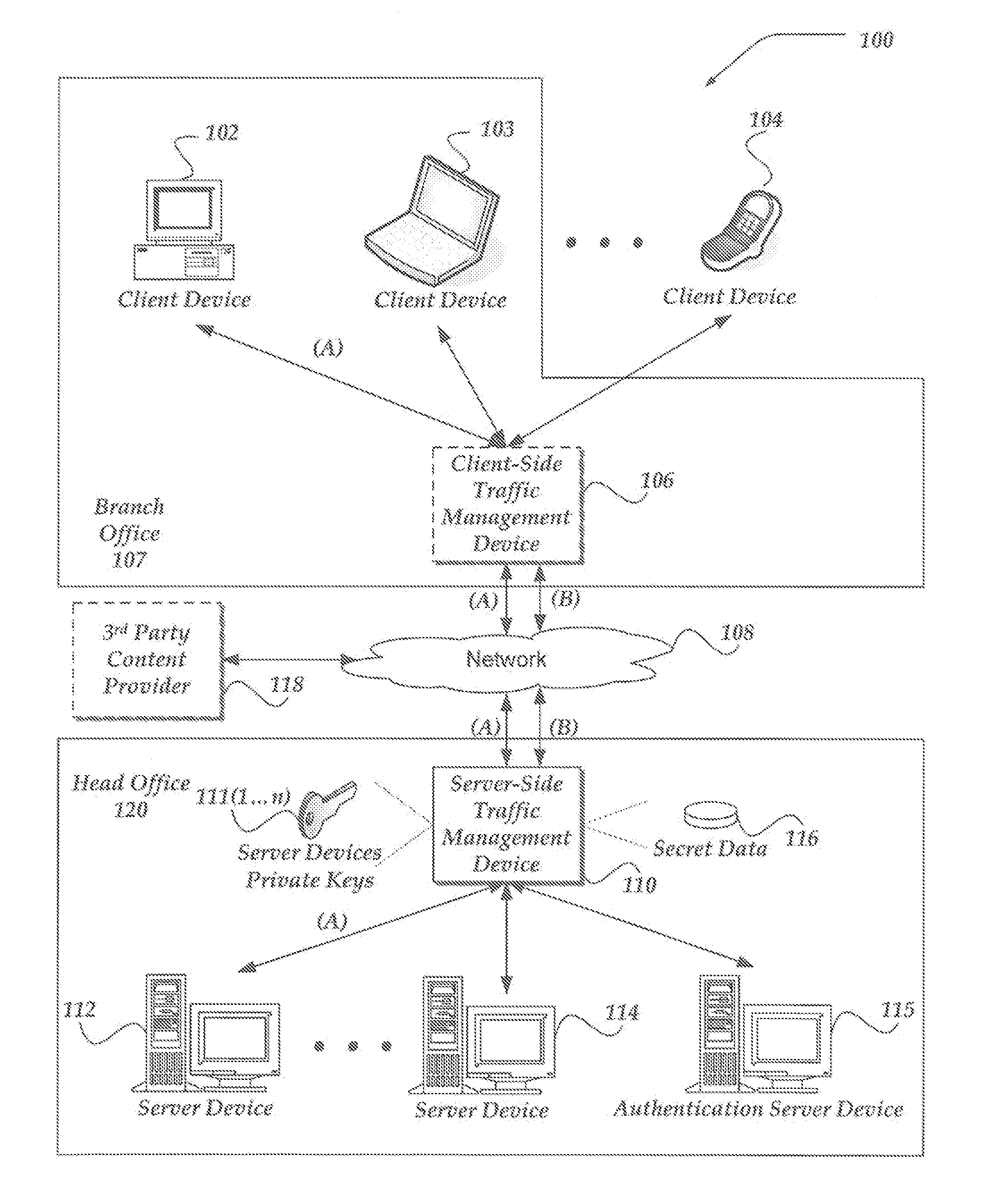
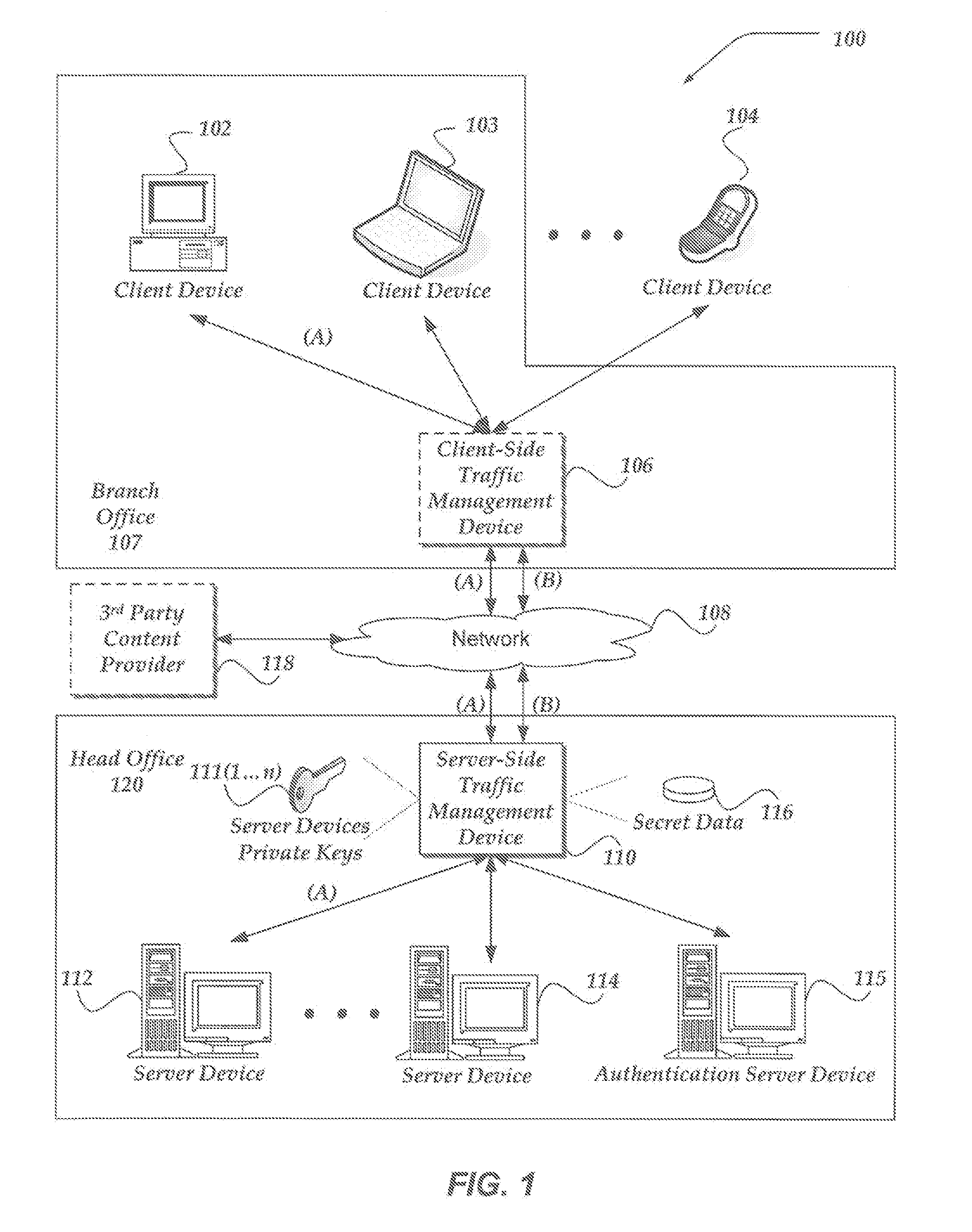
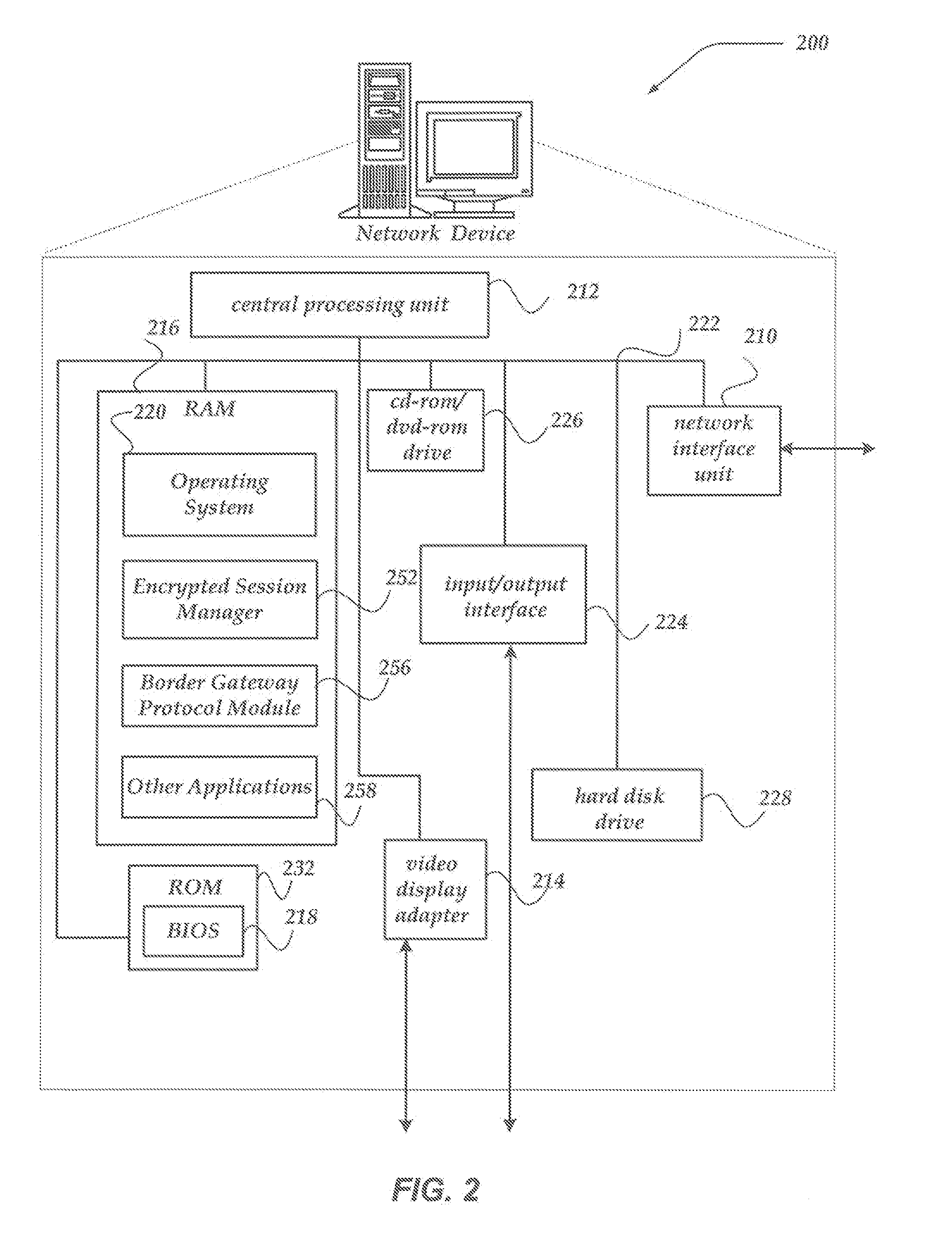
Proxy SSL authentication in split SSL for client-side proxy agent resources with content insertion
A traffic management device (TMD), system, and processor-readable storage medium are directed to determining that an end-to-end encrypted session has been established between a client and an authentication server, intercepting and decrypting subsequent task traffic from the client, and forwarding the intercepted traffic toward a server. In some embodiments, a second connection between the TMD and server may be employed to forward the intercepted traffic, and the second connection may be unencrypted or encrypted with a different mechanism than the encrypted connection to the authentication server. The encrypted connection to the authentication server may be maintained following authentication to enable termination of the second connection if the client becomes untrusted, and / or to enable logging of client requests, connection information, and the like. In some embodiments, the TMD may act as a proxy to provide client access to a number of servers and / or resources.
Owner:F5 NETWORKS INC
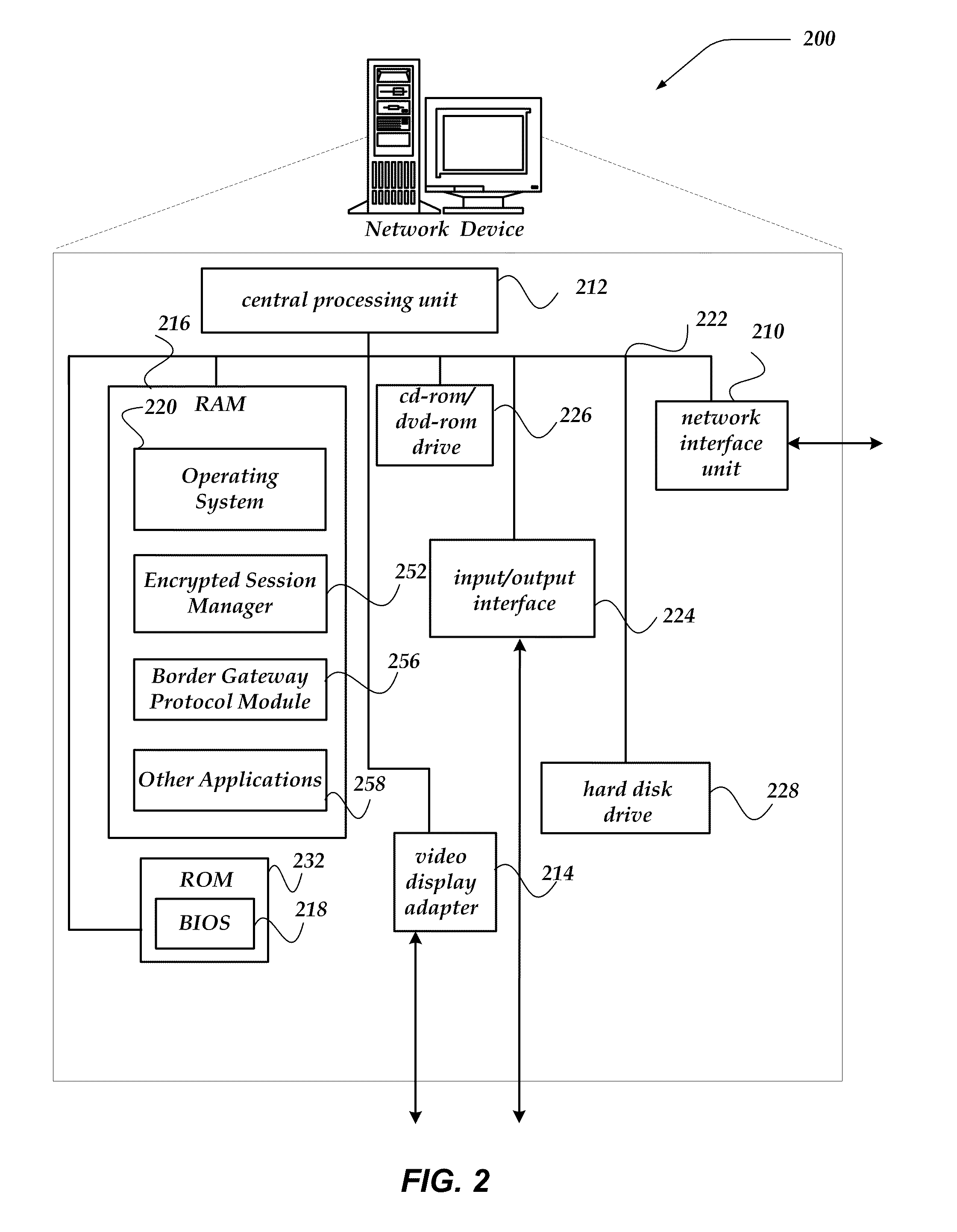
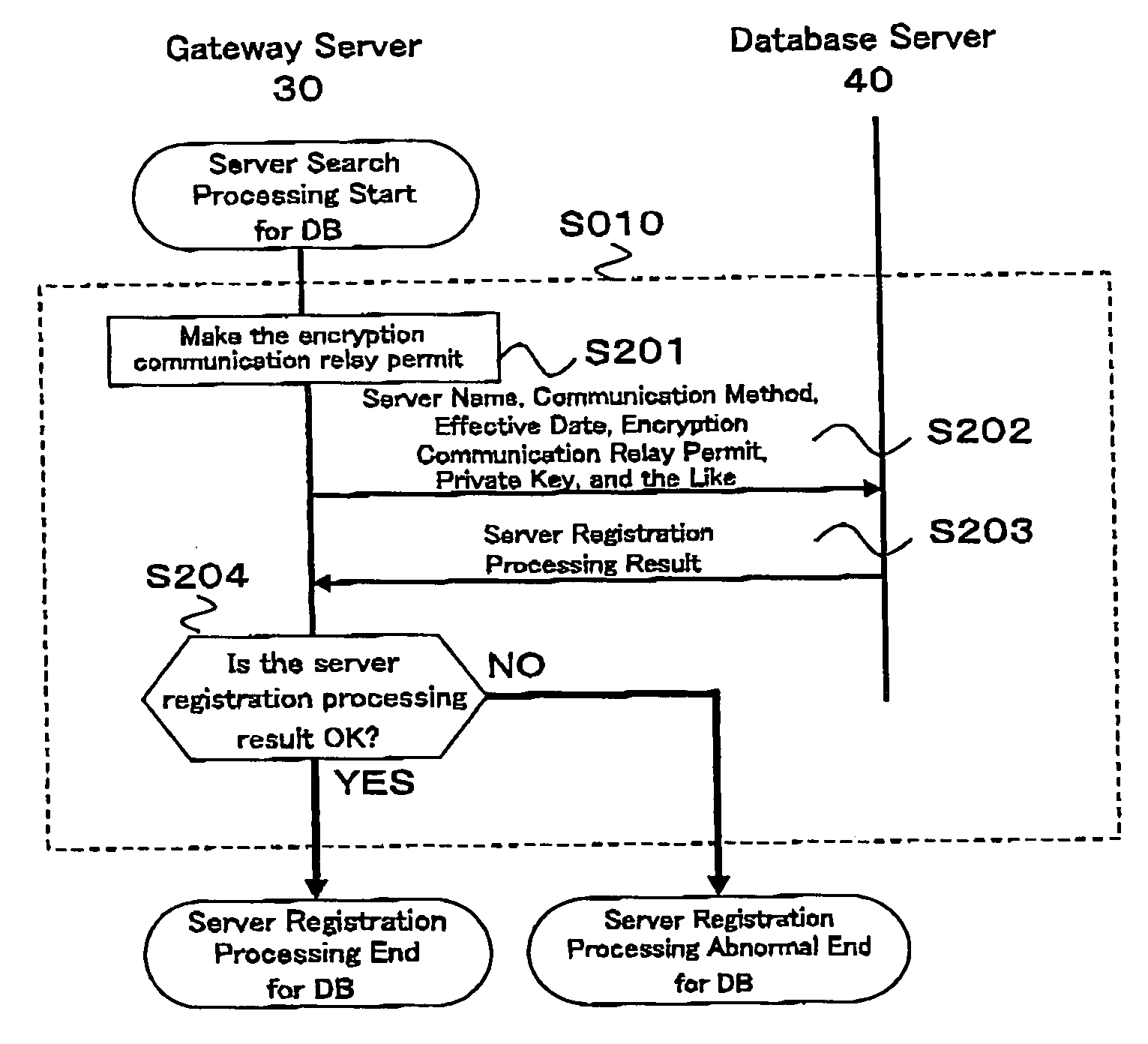
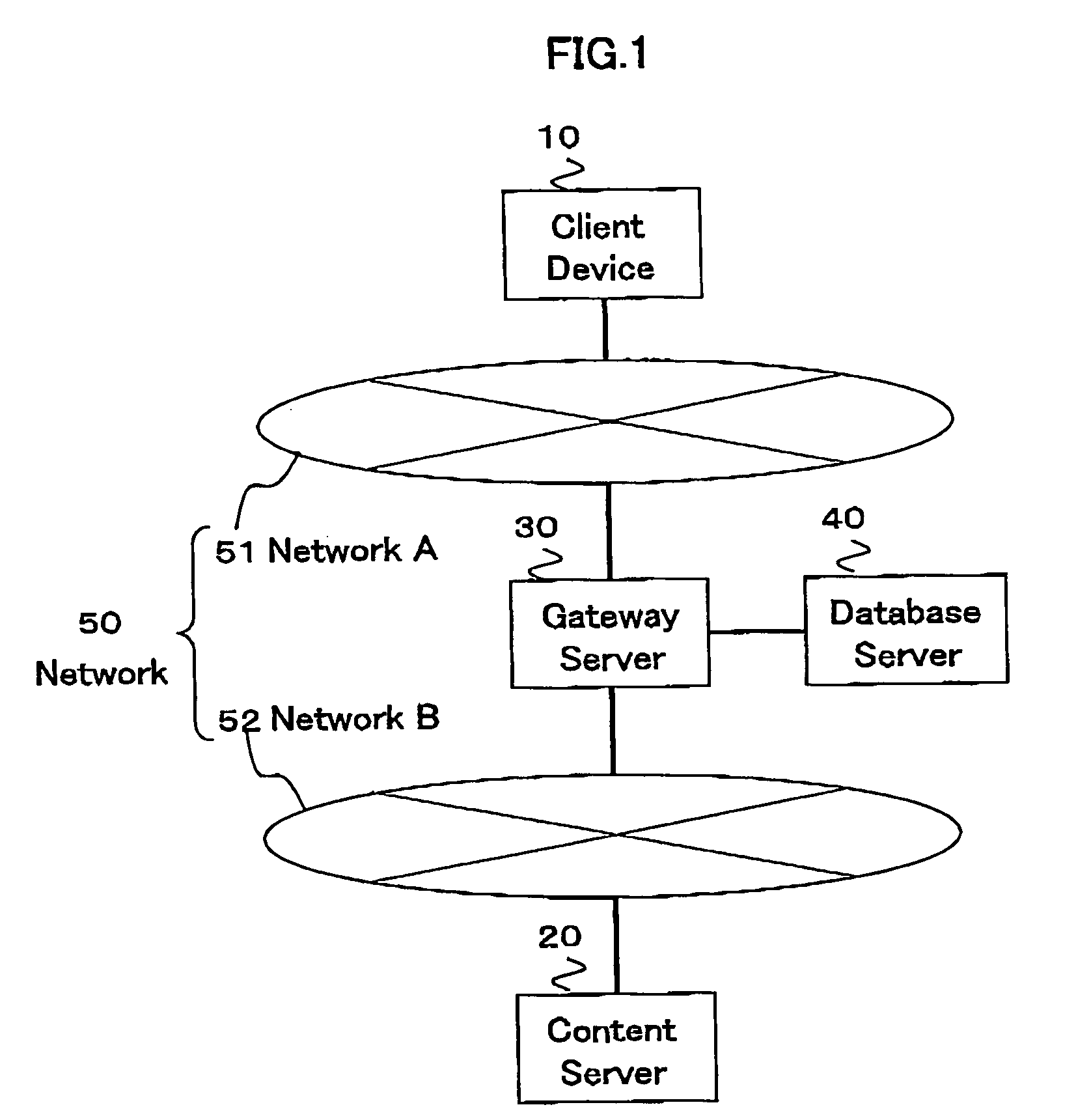
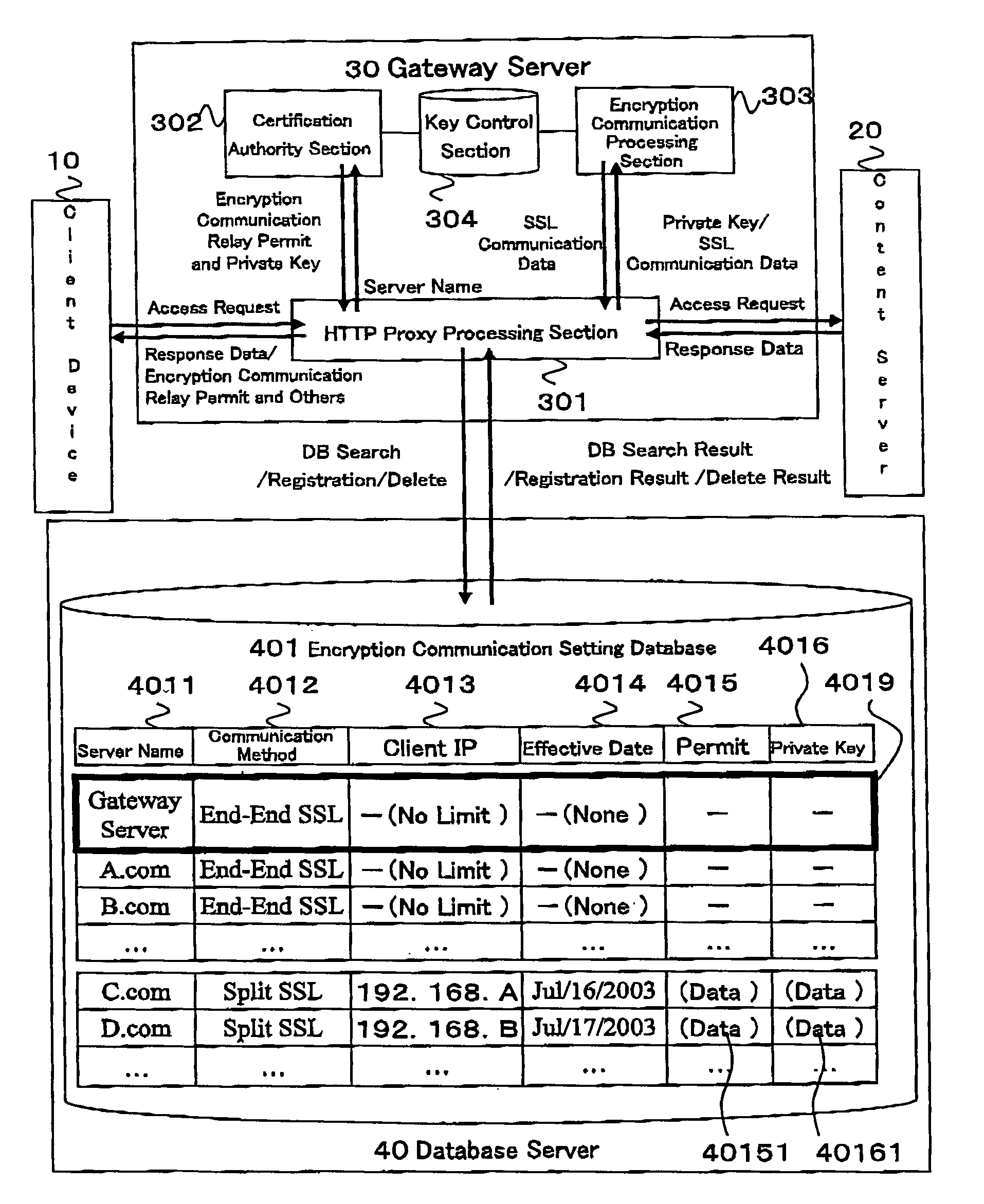
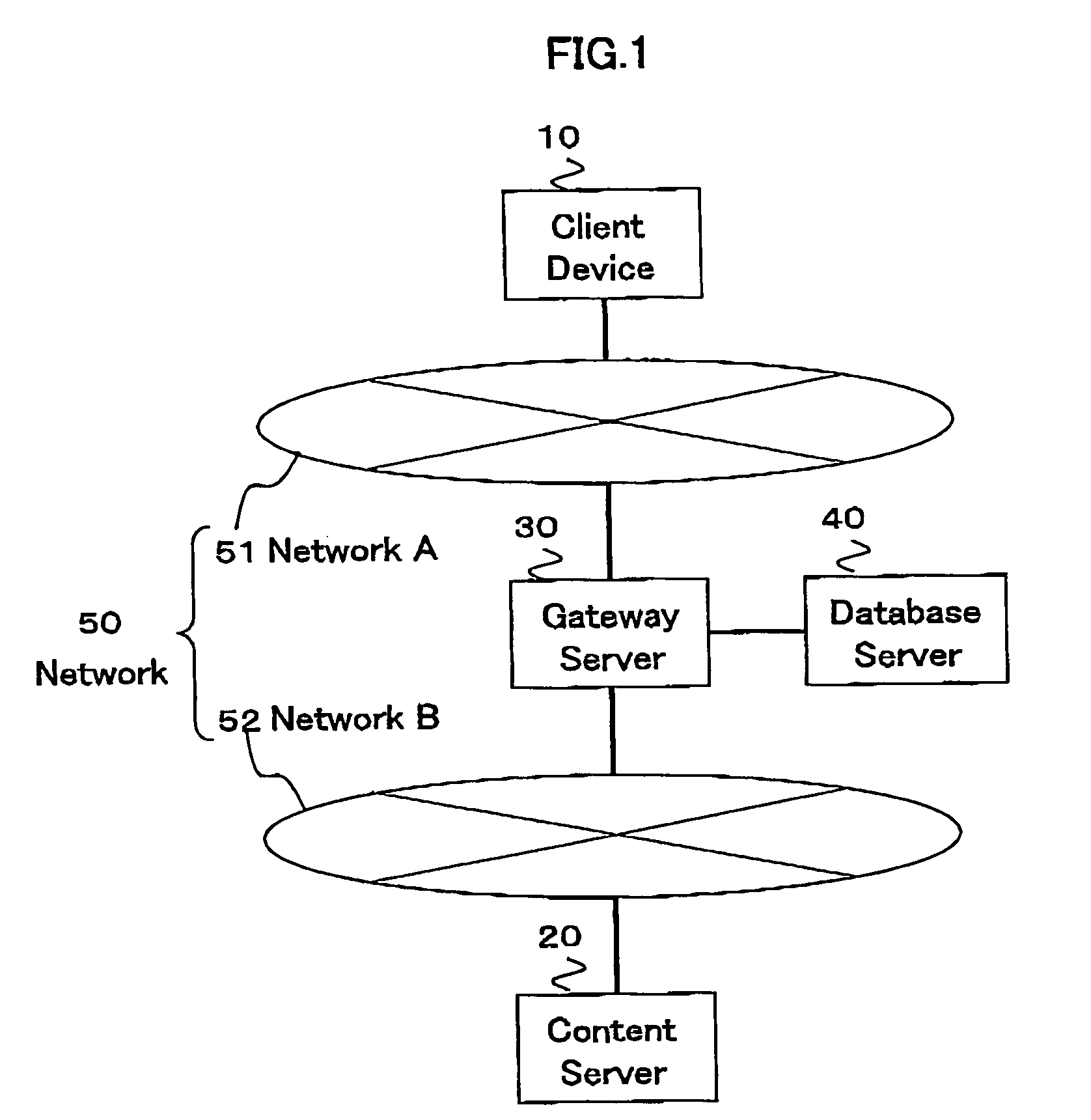
Relay method of encryption communication, gateway server, and program and program memory medium of encryption communication
InactiveUS20060136724A1User identity/authority verificationMultiple digital computer combinationsPlaintextEnd-to-end encryption
The relay method for relaying an encryption communication in a gateway server between a client device and a content server includes the steps of receiving an encryption communication connection message to the content server from the device; producing a temporary encryption communication permit and a private key of its counterpart for the content server of a destination server name included in the connection message; sending the permit to the device; performing an End-End encryption communication with the device, receiving an encrypted access request message sent by the device, and decrypting and converting the request message to an access request message of a plain text; performing an End-End encryption communication with the content server, and acquiring content information instructed by the access request message; and performing value added processing for the acquired content information and its communication header, encrypting the information and the header, and sending them to the device.
Owner:HITACHI LTD
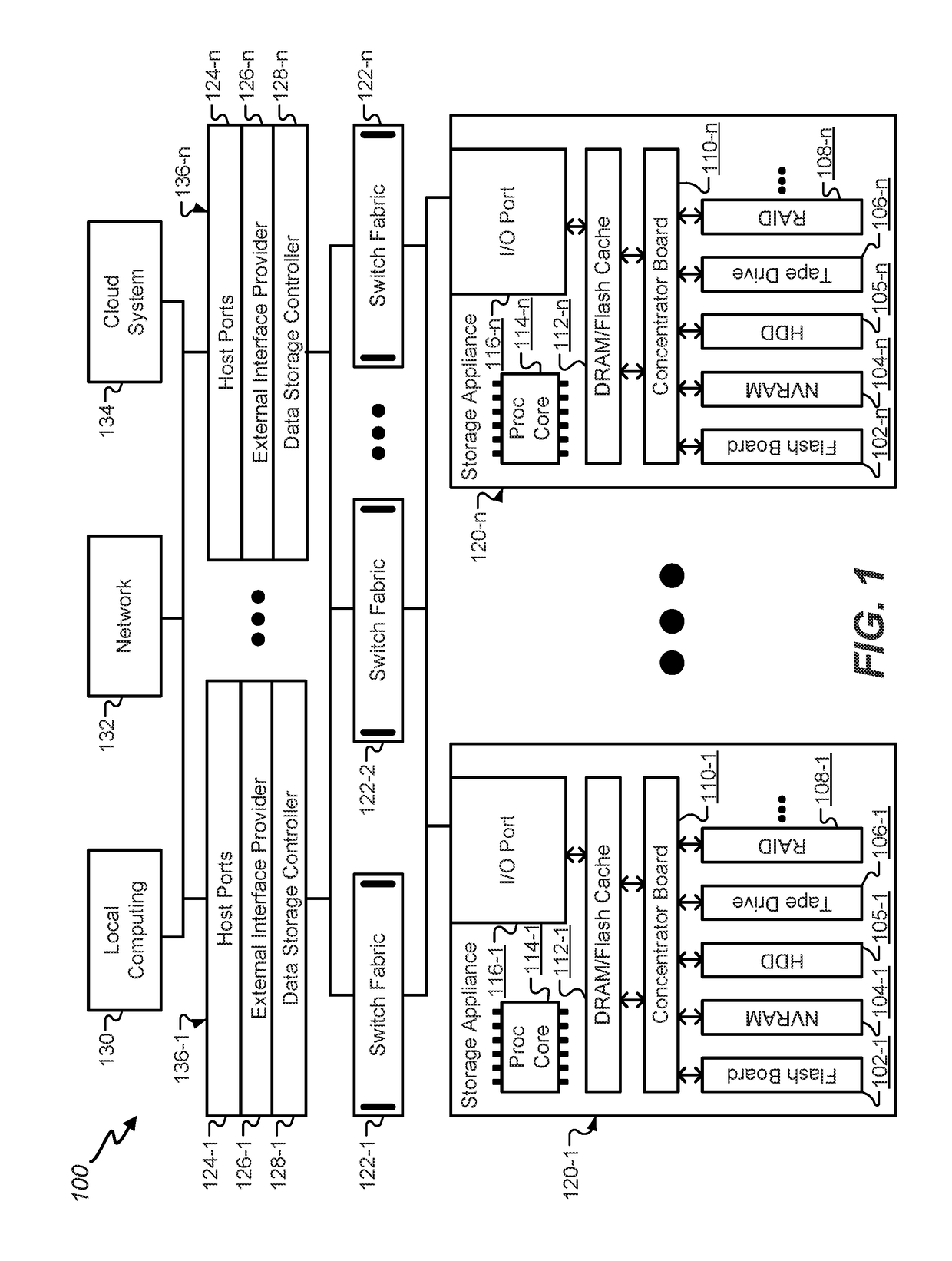
Compression and secure, end-to-end encrypted, zfs cloud storage
ActiveUS20180198765A1Improve natureEnsure consistencyMemory architecture accessing/allocationKey distribution for secure communicationEnd-to-end encryptionFile system
Techniques described herein relate to systems and methods of data storage, and more particularly to providing layering of file system functionality on an object interface. In certain embodiments, file system functionality may be layered on cloud object interfaces to provide cloud-based storage while allowing for functionality expected from a legacy applications. For instance, POSIX interfaces and semantics may be layered on cloud-based storage, while providing access to data in a manner consistent with file-based access with data organization in name hierarchies. Various embodiments also may provide for memory mapping of data so that memory map changes are reflected in persistent storage while ensuring consistency between memory map changes and writes. For example, by transforming a ZFS file system disk-based storage into ZFS cloud-based storage, the ZFS file system gains the elastic nature of cloud storage.
Owner:ORACLE INT CORP
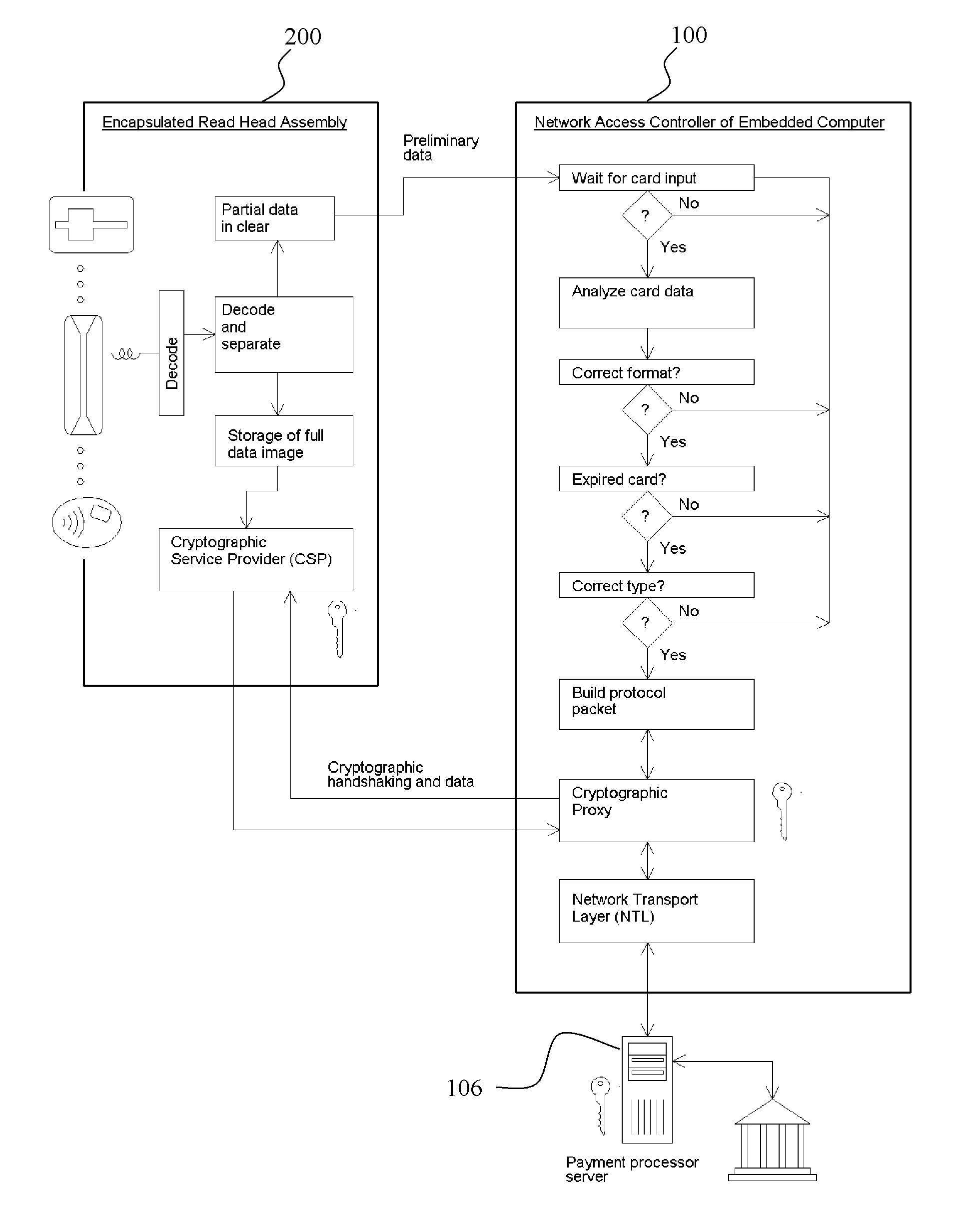
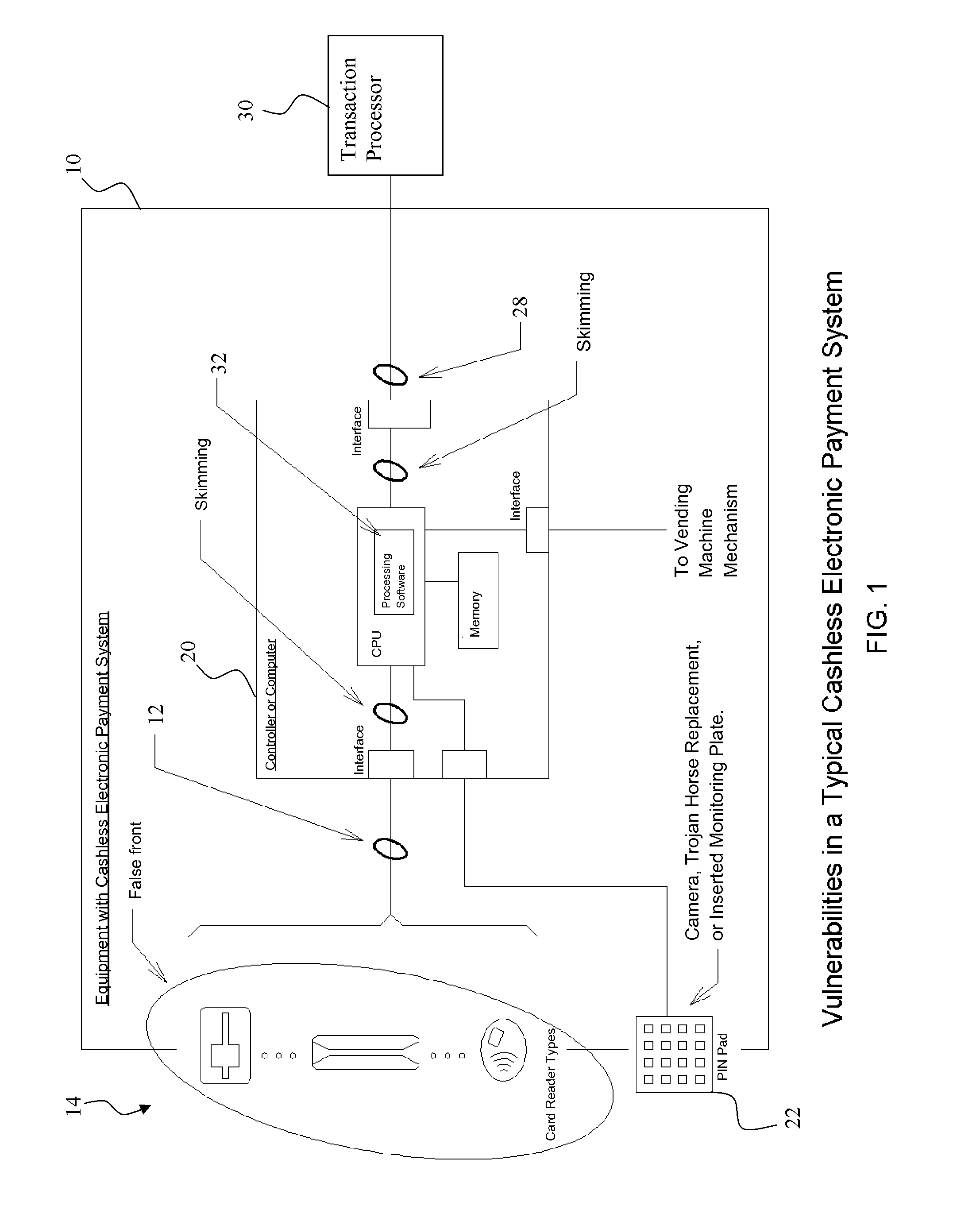
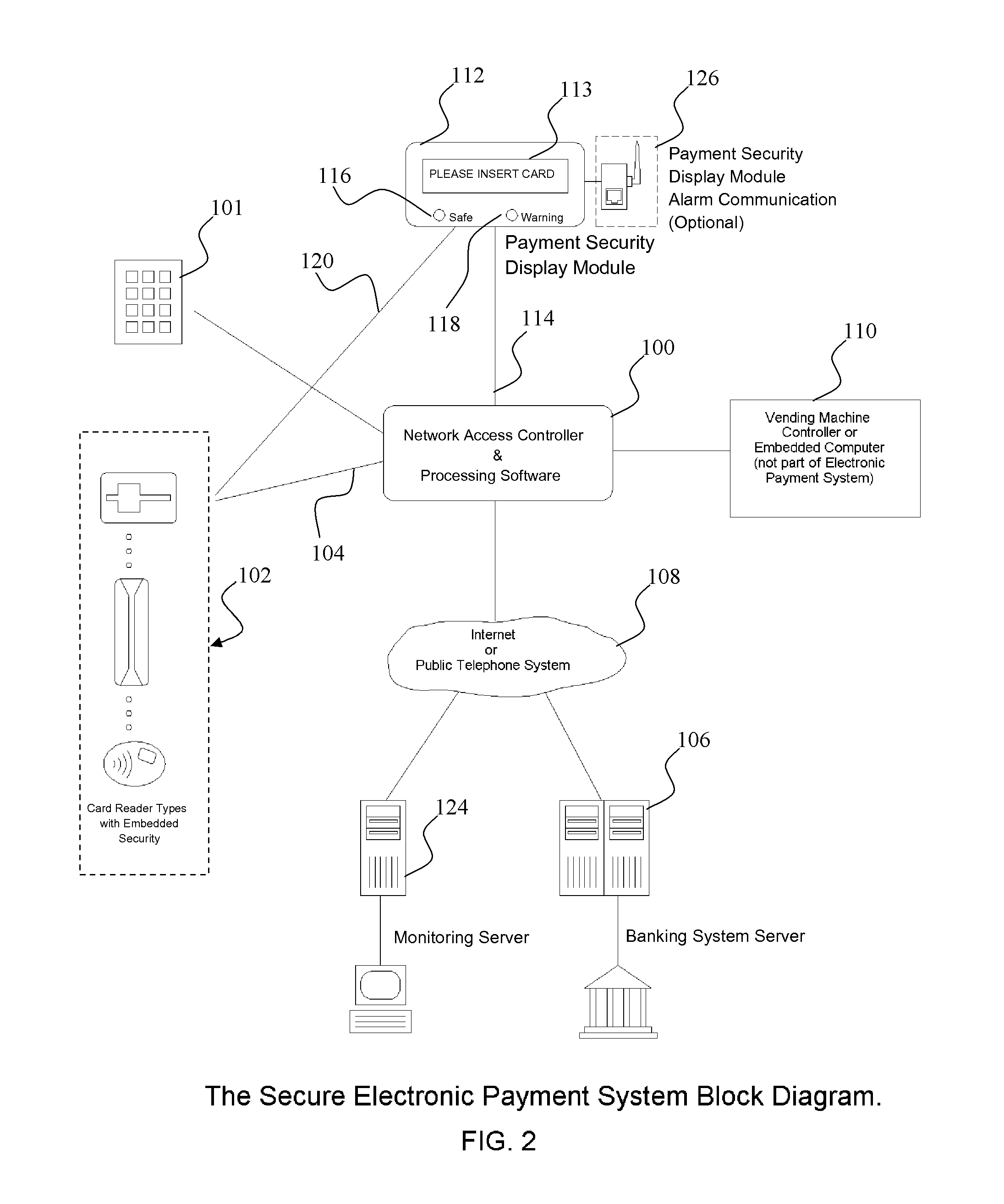
Secure electronic cash-less payment systems and methods
InactiveUS20110238581A1Improved fail-safe detectionImproved reporting mechanismAcutation objectsPayment circuitsEnd-to-end encryptionCredit card
Systems and methods to provide and maintain secure financial transaction conducted with a credit card or other cashless payment mechanism at a vending machine or other potentially unattended vending or point of sale device. Encapsulated card readers providing end-to-end encryption capabilities encrypt transaction data for secure transmission to a transaction host or server. Pre-authorization transaction data checking maintains account numbers in a secure encrypted format further enhancing security. Protection mechanisms that guard against, and provide warnings of equipment tampering, while also providing a visual indication to customers regarding the security of the system.
Owner:FORWARD PAY SYST
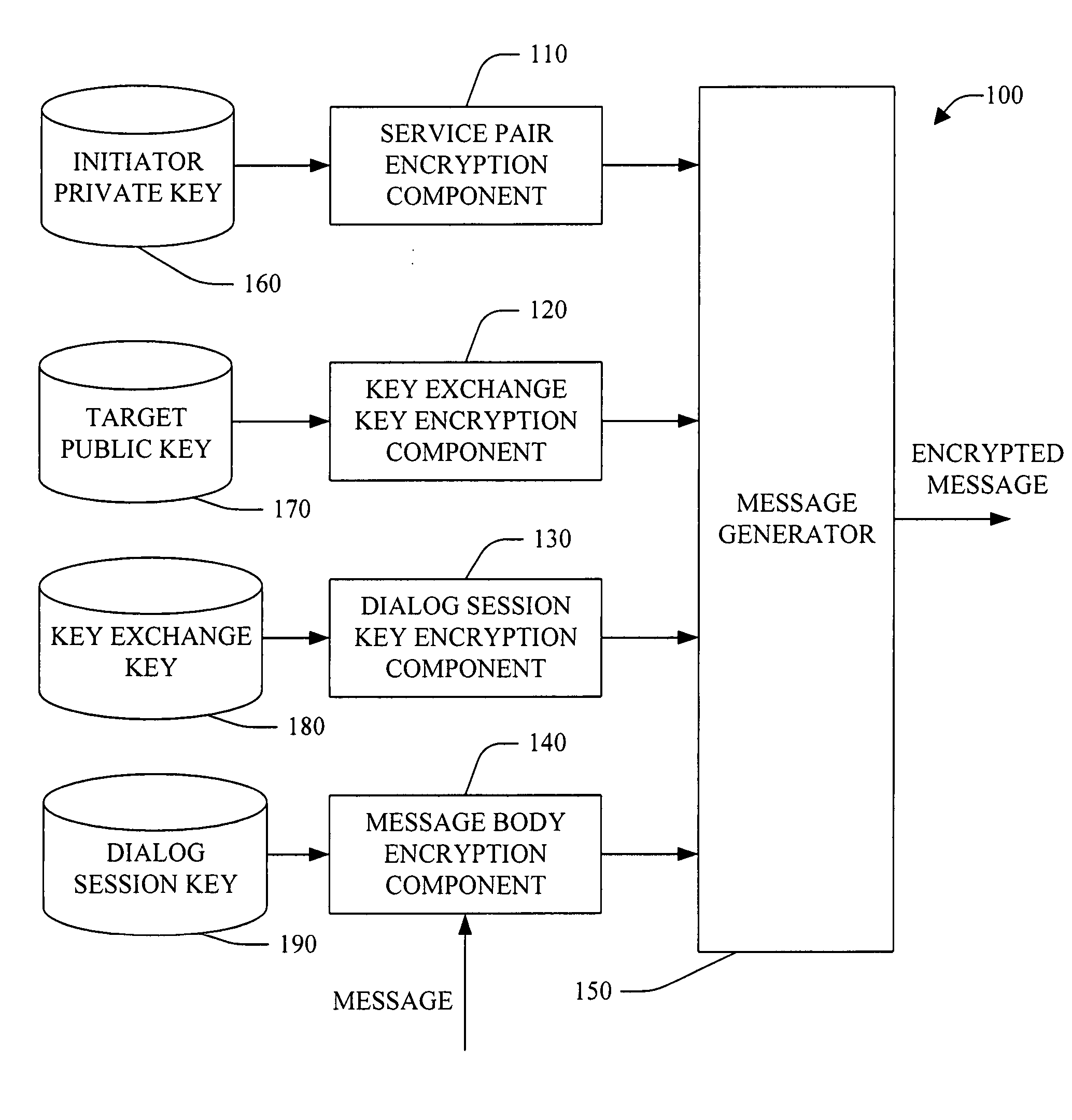
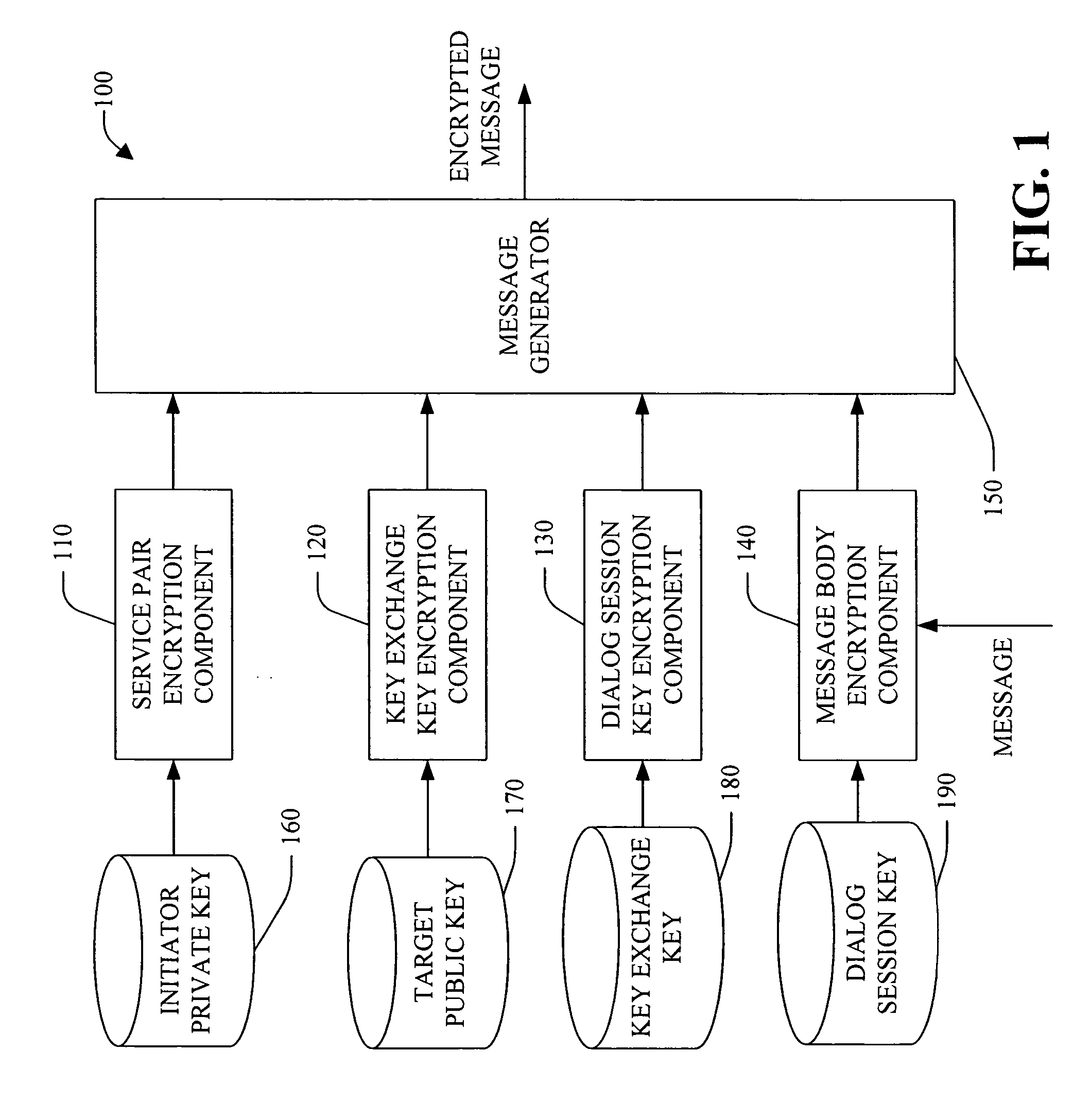
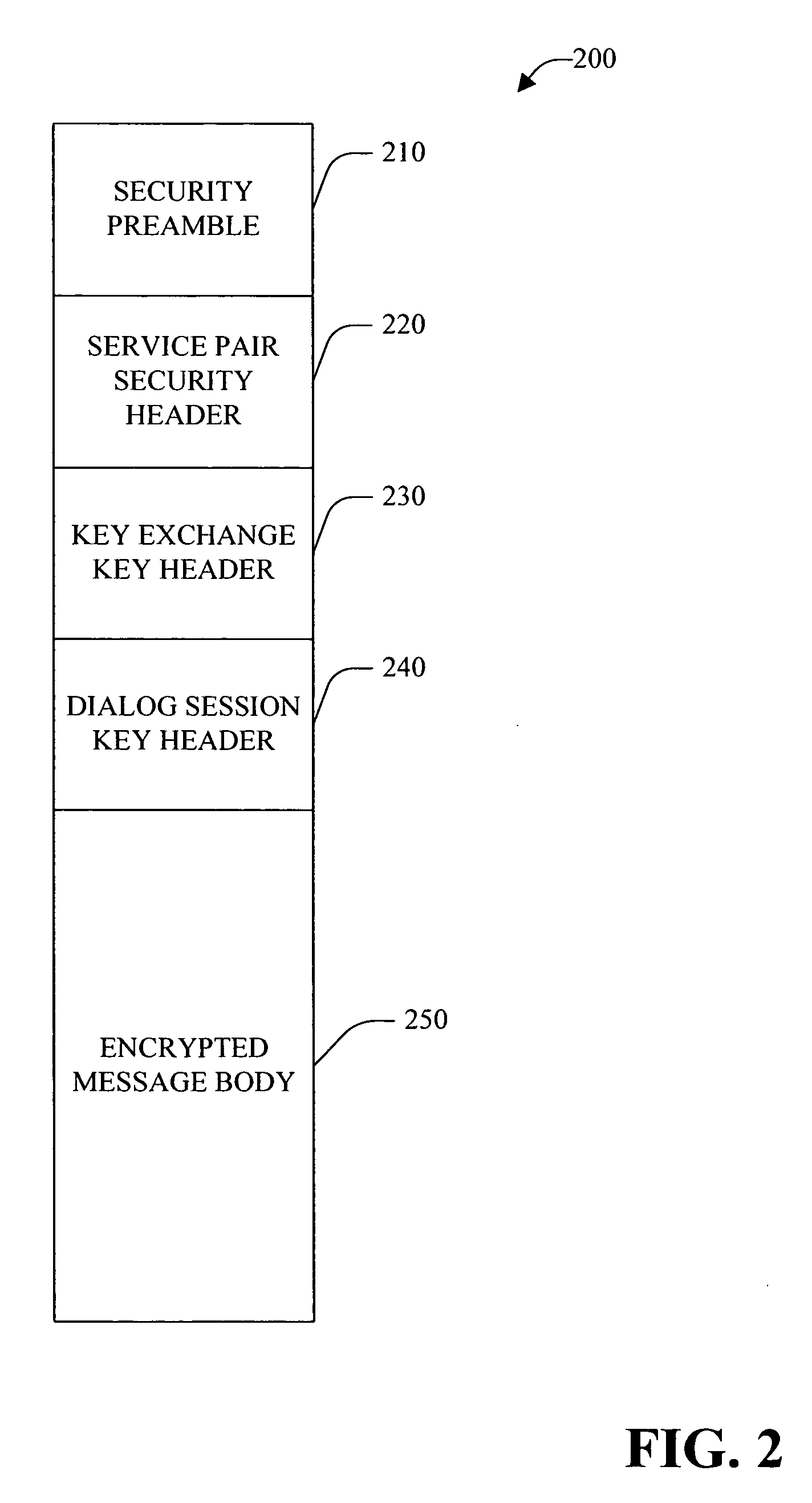
Session key exchange key
InactiveUS20050232426A1Reduce processing timeIncrease flexibilityKey distribution for secure communicationMultiple keys/algorithms usageKey exchangeSecure communication
A system and method for employing a key exchange key to facilitate secure communication is provided. The key exchange key can be employed, for example, to encrypt and / or decrypt dialog session key(s) that are used to encrypt and / or decrypt message(s) that form a dialog between an initiator system and target system. In one example, a key exchange key is unique to a service pair, while a dialog session key is unique to a particular dialog between the service pair. The system can facilitate end-to-end encryption of message data in a dialog—the message data is encrypted at one dialog endpoint and not decrypted until it reaches the other dialog endpoint. The system can be employed to facilitate secure dialog with minimal performance overhead when compared with conventional system(s). Optionally, the system can facilitate load balancing (e.g., among deployed instances of a service). In this example, secured dialogs to a service can be location transparent so that a dialog targeted to a service can be able to talk to any instance of the same service transparently without any additional security setup. The system employs both public key / private key asymmetric encryption technique(s) and symmetric encryption technique(s) to authenticate and secure information exchanged between an initiator system and a target system.
Owner:MICROSOFT TECH LICENSING LLC
Proxy ssl handoff via mid-stream renegotiation
InactiveUS20110231655A1Computer security arrangementsSecuring communicationEnd-to-end encryptionTraffic capacity
A traffic management device (TMD), system, and processor-readable storage medium directed towards re-establishing an encrypted connection of an encrypted session, the encrypted connection having initially been established between a client device and a first server device, causing the encrypted connection to terminate at a second server device. As described, a traffic management device (TMD) is interposed between the client device and the first server device. In some embodiments, the TMD may request that the client device renegotiate the encrypted connection. The TMD may redirect the response to the renegotiation request towards a second server device, such that the renegotiated encrypted connection is established between the client device and the second server device. In this way, a single existing end-to-end encrypted connection can be used to serve content from more than one server device.
Owner:F5 NETWORKS INC
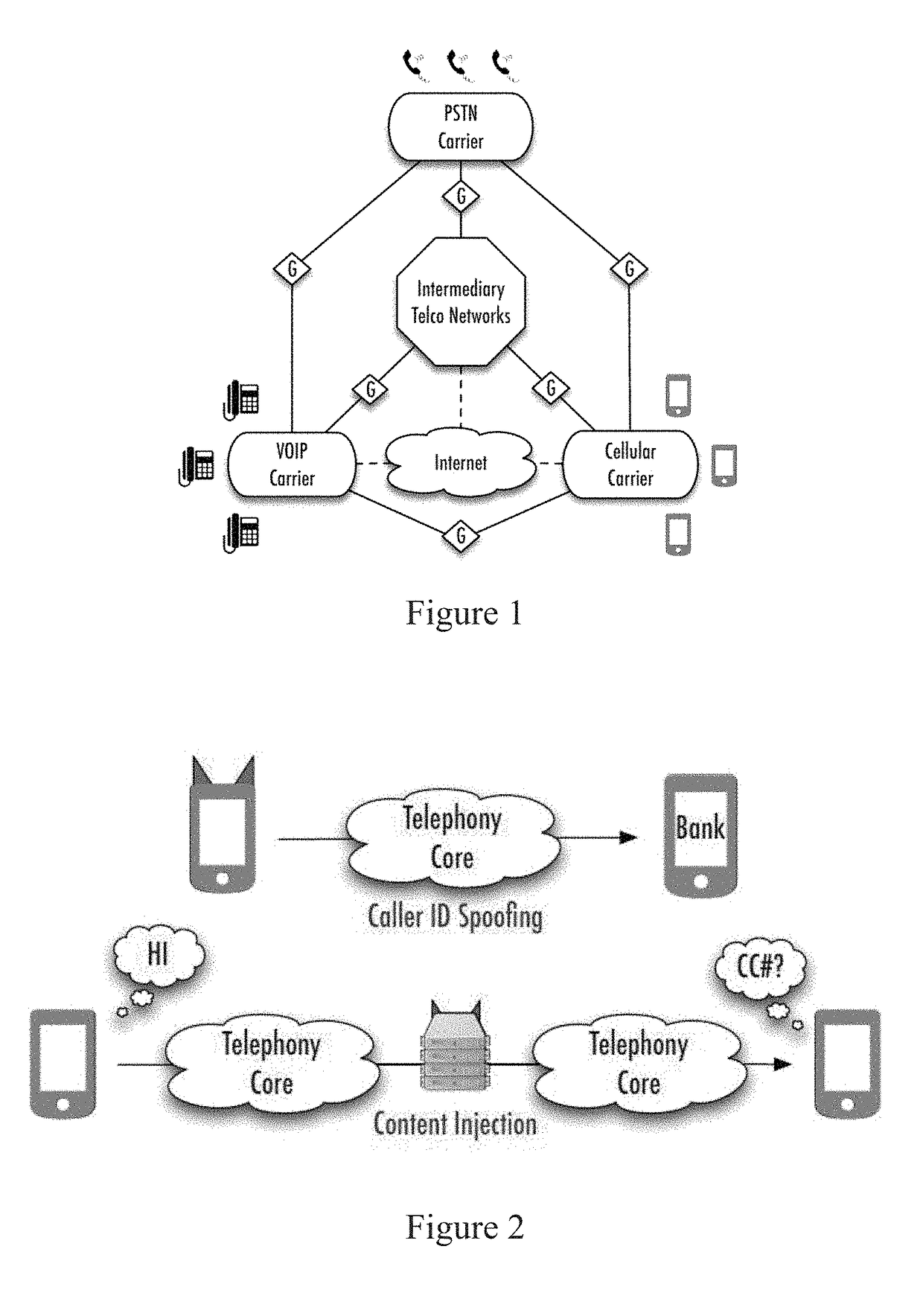
Secure mobile telephony
ActiveUS20090122984A1User identity/authority verificationUnauthorized memory use protectionEnd-to-end encryptionMobile telephony
An system for and method of providing end-to-end encrypted real-time phone calls using a commodity mobile phone and without requiring service provider cooperation is presented. The system and method improve upon prior art techniques by omitting any requirement for mobile phones that are specially manufactured to include end-to-end encryption functionality.
Owner:KOOLSPAN
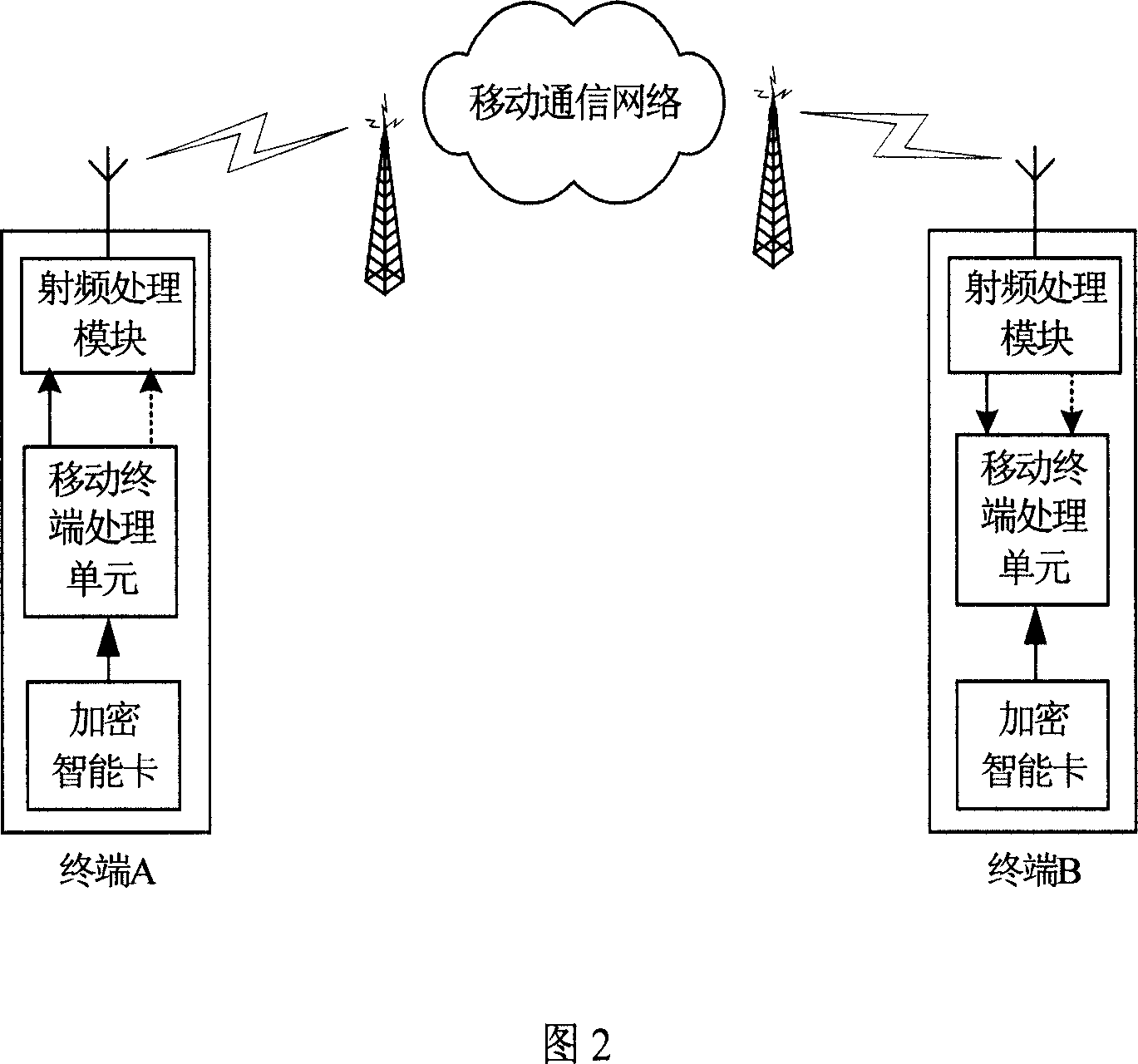
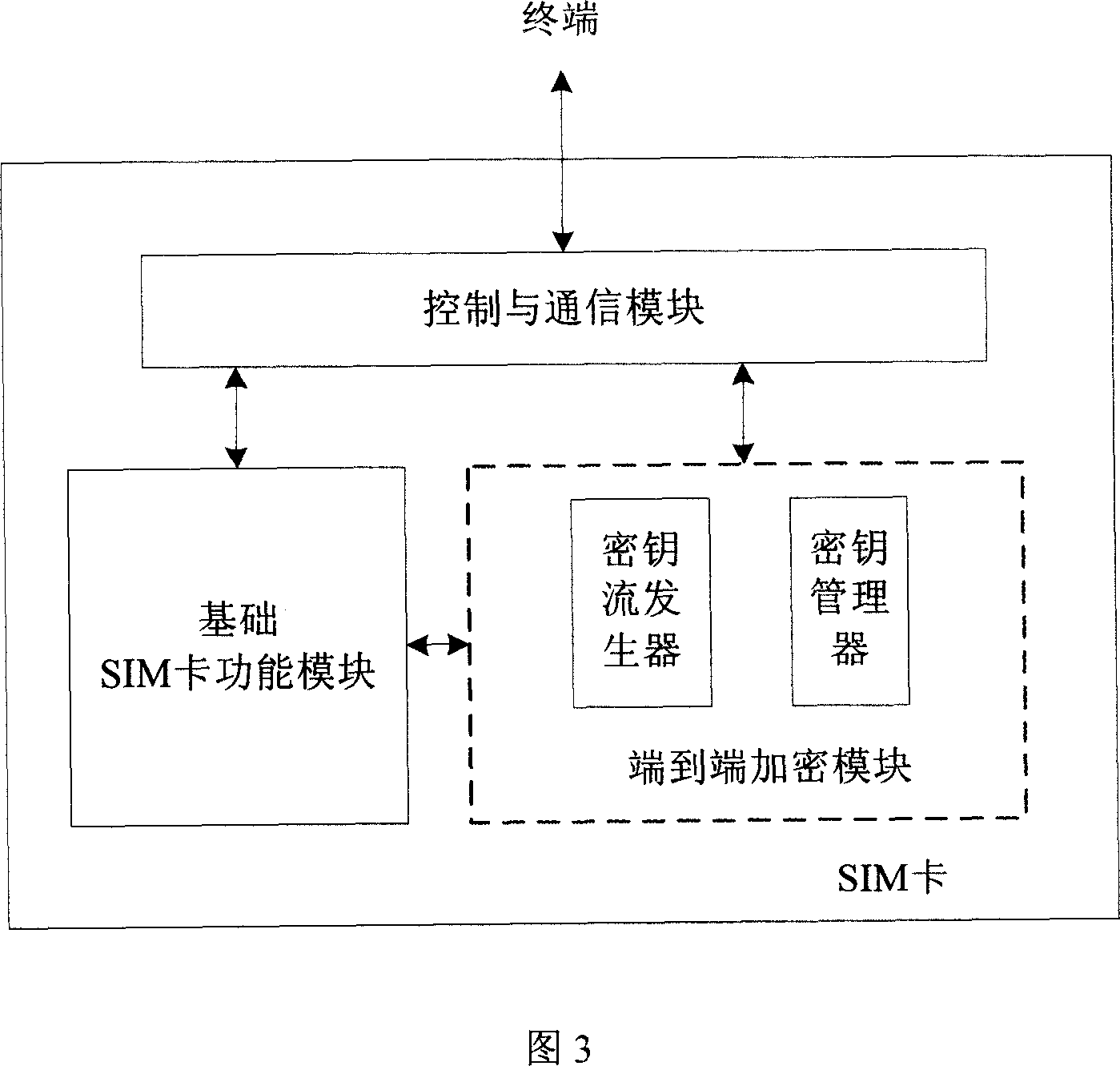
End-to-end encrypting method and system based on mobile communication network
InactiveCN1925681AAvoid controlAvoid the defects of plaintext transmissionUser identity/authority verificationRadio/inductive link selection arrangementsEnd-to-end encryptionSecret code
This invention relates to end to end coding method and system based on mobile communication network, which comprises the following steps: adopting codes end to end coding and adopting key management center for whole codes system and adopting keys intelligent cards as terminal end to coded safety module; according to center generating codes flow and decodes flow through or formula on messages and codes to realize end to end coding communication; the said system comprises key management center and terminal interact through center to terminal end with intelligent card.
Owner:BEIJING TAIJI UNITED LAB TECH
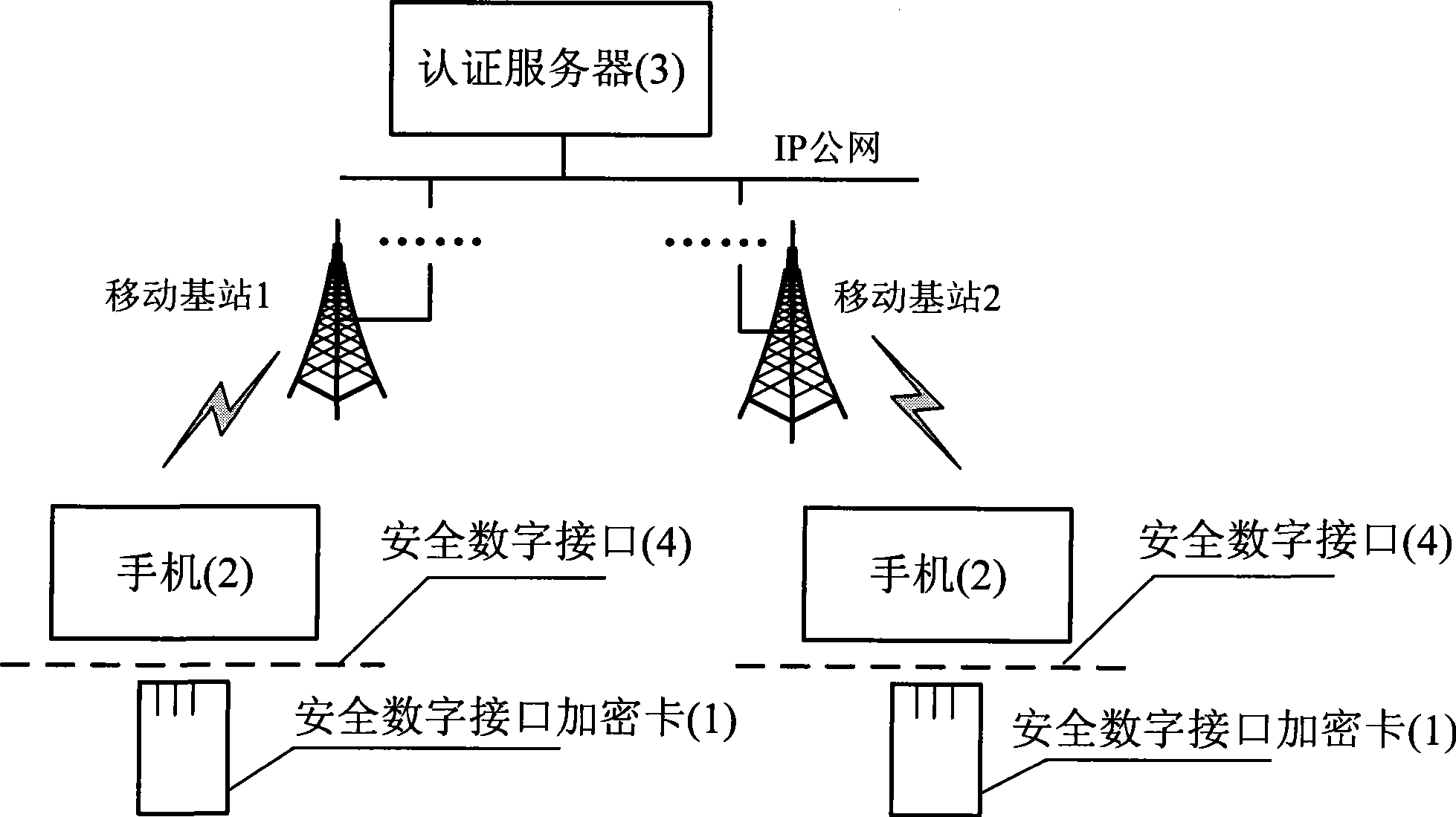
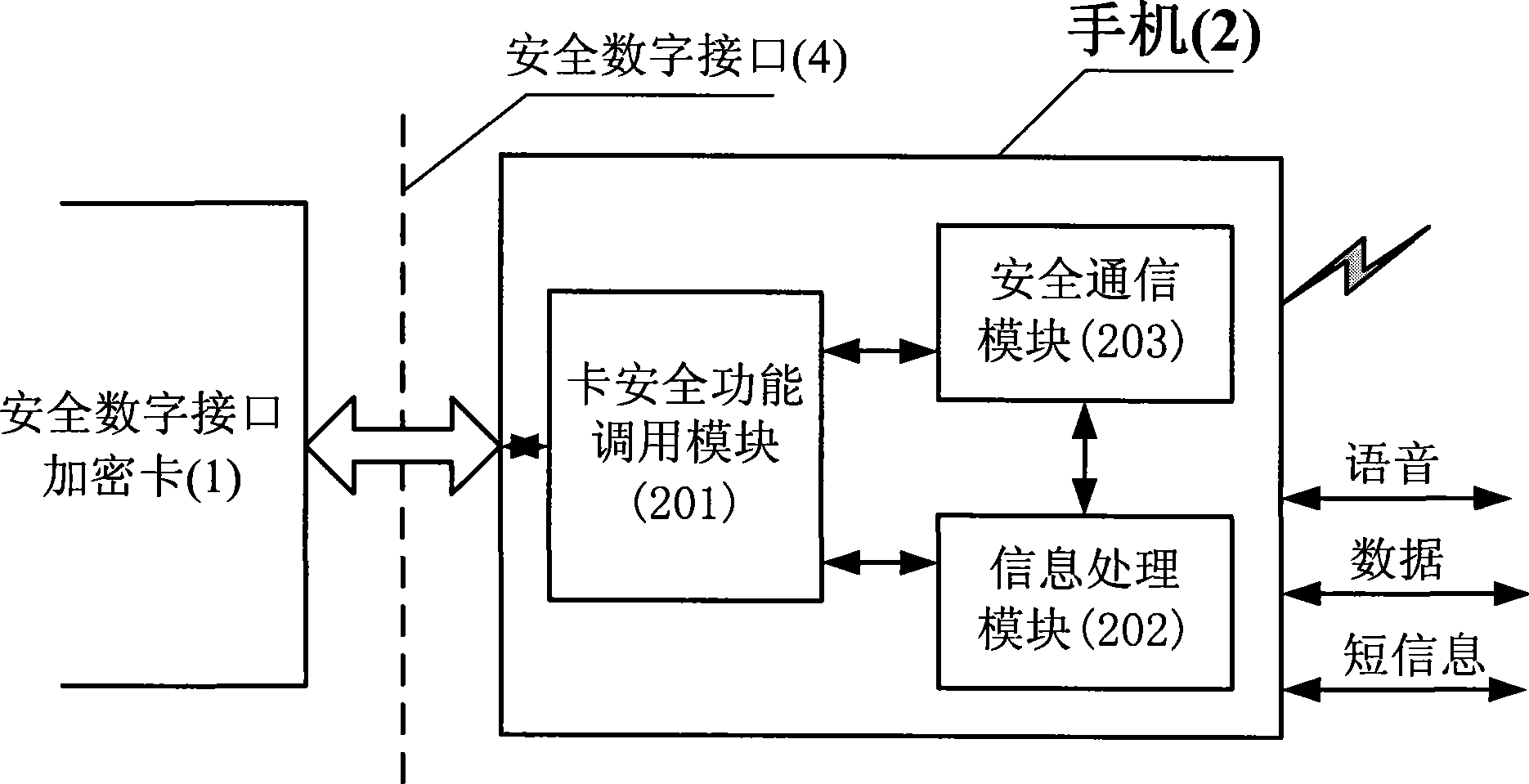
Mobile phone ciphering method based on safe digital interface ciphering card
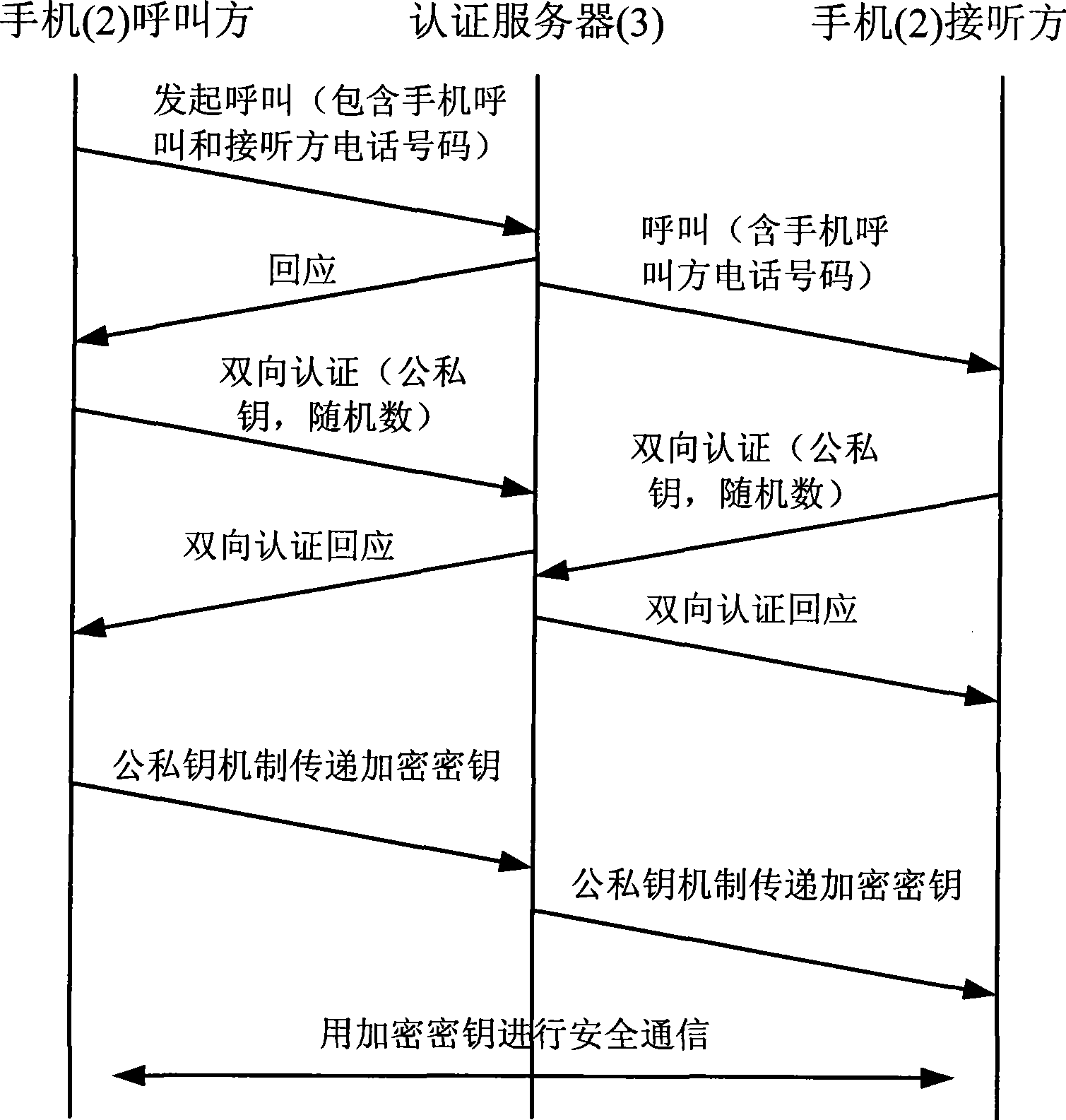
InactiveCN101384042AAchieve safe distributionHigh encryption strengthRadio/inductive link selection arrangementsTransmissionEnd-to-end encryptionDigital interface
The invention discloses a handset encryption method based on a safety digital interface encryption card, which can realize end-to-end encryption data transmission on the basis of unchanging the prior handset hardware facilities through inserting the safety digital interface encryption card in a handset with a safety digital interface slot. The invention is mainly based on three safety main bodies including the safety digital interface encryption card, the handset (2) and a certificate server (3). The connection and communication of the safety digital interface encryption card and the handset are finished in accordance with the mechanical feature, the electrical character and the communication protocol of a safety digital interface (4). After the encryption process of the safety digital interface encryption card, voice, data and the data of messages on one handset are transmitted to the other handset through a mobile communication network, and the encryption of the data is finished by another safety digital interface encryption card. Before the encryption data is transmitted, the certificate server, a handset calling party and a handset called party which are set up need to finish the mutual certificate and secret negotiation together.
Owner:SOUTHEAST UNIV
Method performed by at least one server for processing a data packet from a first computing device to a second computing device to permit end-to-end encryption communication
ActiveUS20160134594A1Multiple keys/algorithms usageUser identity/authority verificationEnd-to-end encryptionNetwork packet
A method (500) performed by at least one server for processing a data packet from a first computing device to be transmitted to a second computing device is disclosed, in which the data packet includes a message encrypted using a first encryption key to form an encrypted message, identification data of the second computing device encrypted using a second encryption key to form encrypted identification data, and encrypted first and second encryption keys. The method comprises decrypting (504) the encrypted second encryption key; encryption key; decrypting (506) the encrypted identification data using the decrypted second encryption key; and transmitting (508) the data packet based on the decrypted identification data, wherein the encrypted message and first encryption key are arranged to be undecryptable by the server to permit end-to-end encryption communication between the first and recipient info encryption key end-to-end encryption communication between the first and second computing devices. A related system is also disclosed.
Owner:TREEBOX SOLUTIONS
Realization method of end-to-end voice encryption system based on 3G/B3G
InactiveCN102202299ACommunication securityEasy to deployKey distribution for secure communicationUser identity/authority verificationEnd-to-end encryptionVoice communication
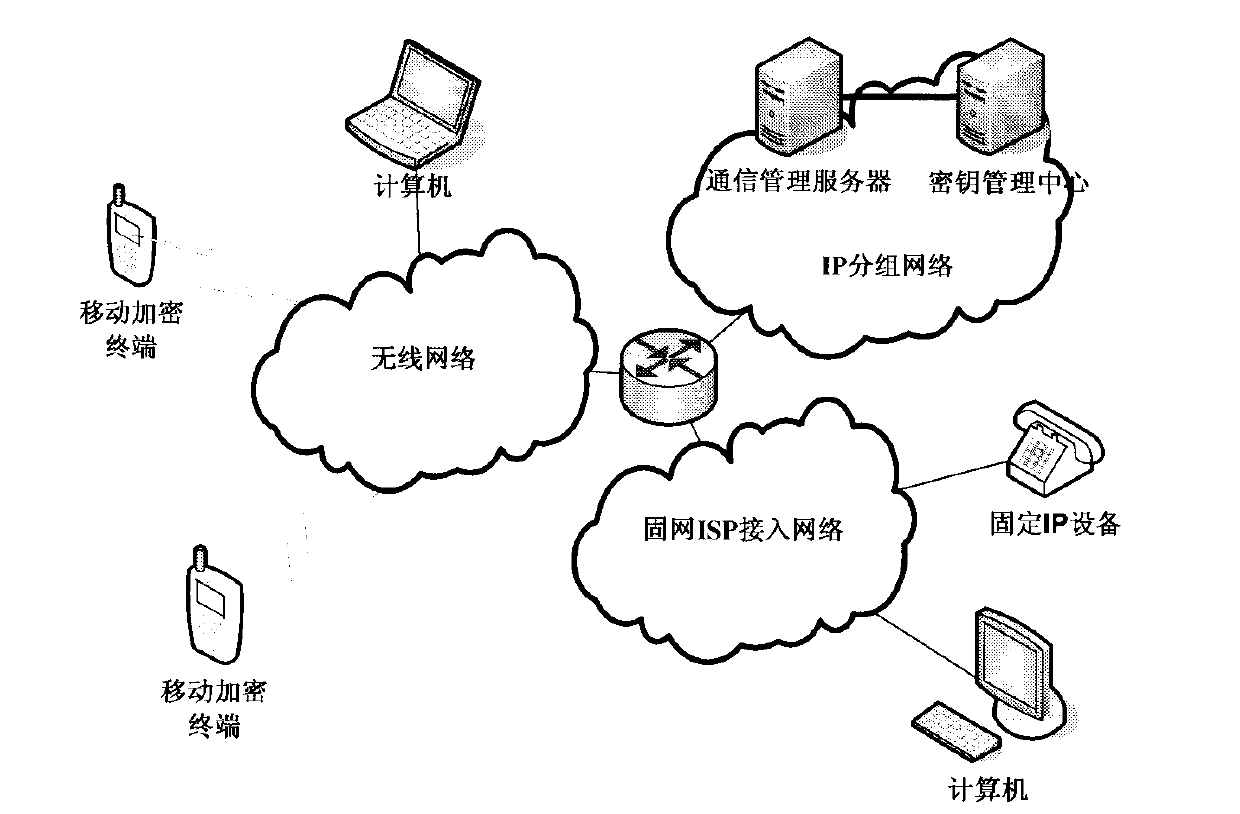
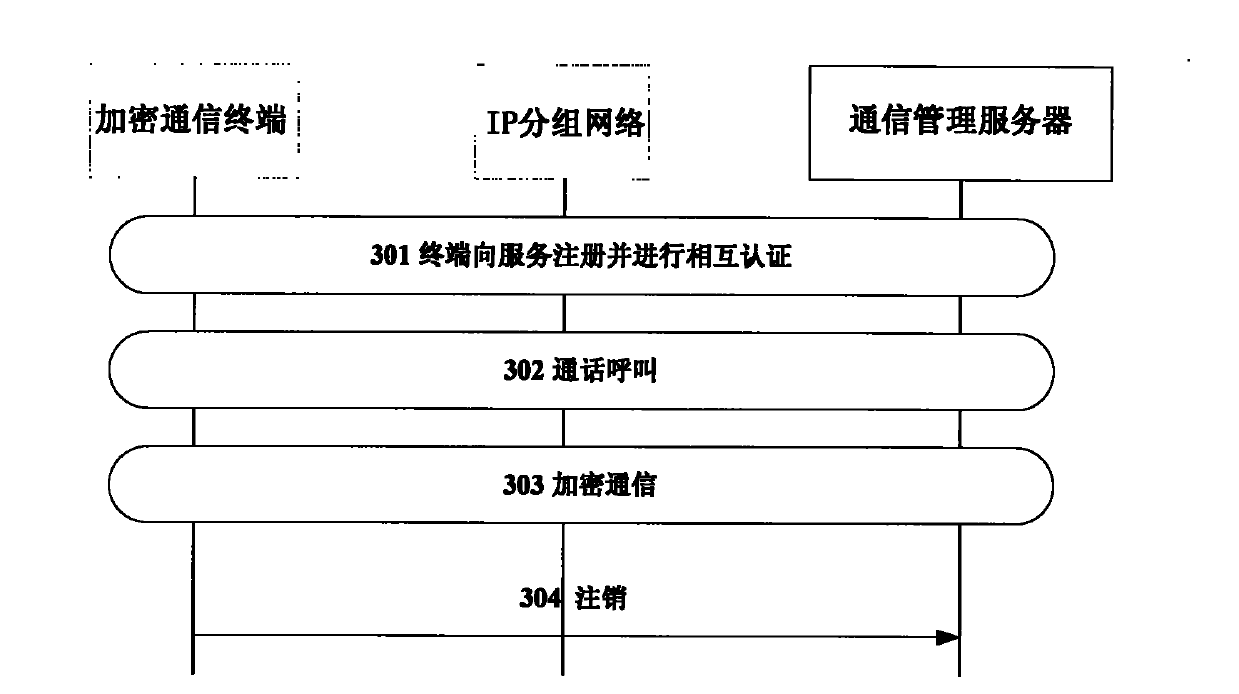
The invention provides a realization method of end-to-end voice encryption system based on 3G / B3G. A mobile encryption terminal is accessed into a grouping network through 3G / B3G, and launches registration to a communication management server (CMS); after the registration is finished, a terminal user can launch a calling request to the registered legal user; a calling party sends a calling request to the CMS; the CMS sends a communication working key request to a key management center (KMC); the KMC encrypts and packages the working key and sends to the CMS; the CMS can perform direct communication according to the communication capacity of two parties of the communication, or performs transit communication; no matter in which manner, the calling party and the called party perform mutual authentication, and receive the working key distributed by the KMC, thus the two-party encryption realizes end-to-end voice communication. The corresponding system for providing the encryption service comprises a mobile encryption terminal, a content management system (CMS) and the KMC. By utilizing the whole set of system, the end-to-end encryption voice communication can be realized.
Owner:谢德育
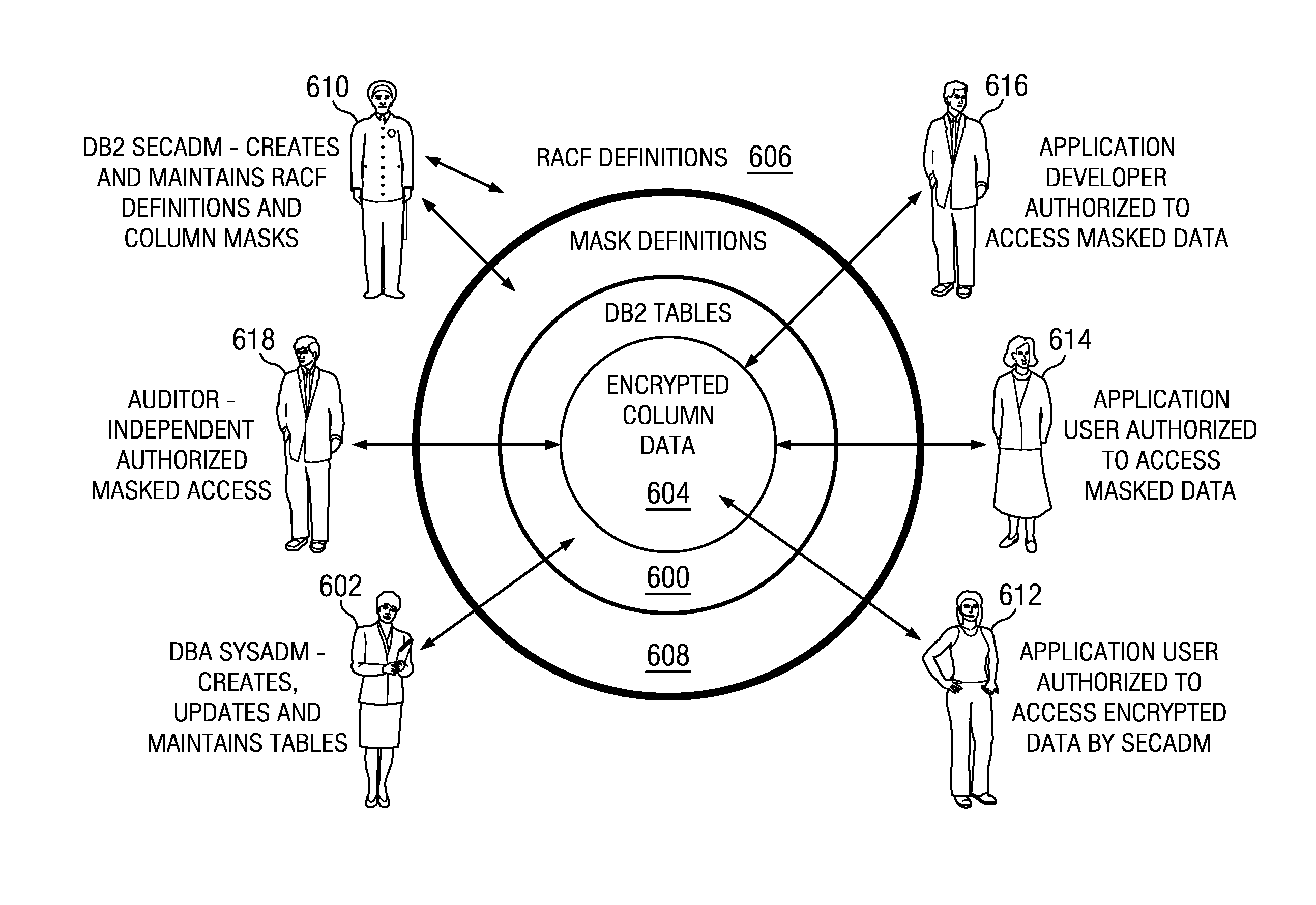
Role-oriented database record field security model
ActiveUS20140075571A1Supports accessDigital data processing detailsAnalogue secracy/subscription systemsEnd-to-end encryptionField data
A database management system implements a role-oriented authorization scheme that facilitates operating system (OS) supported encrypted field access for a table in the database. A security model provides for various roles that have varying responsibilities and rights with respect to the database tables and the data supported therein. In this approach, data that is considered sensitive is encrypted. A system administrator role is authorized to create, update, and maintain a table but is not authorized to view sensitive field data, i.e., data stored in encrypted columns of the table. A security administrator role is authorized to define column masks with OS-enforced security access control to the sensitive field data. By separating (fencing) these responsibilities, the security model enforces end-to-end encryption across the entire database management system.
Owner:IBM CORP
Method for encrypted communication with a computer system and system therefor
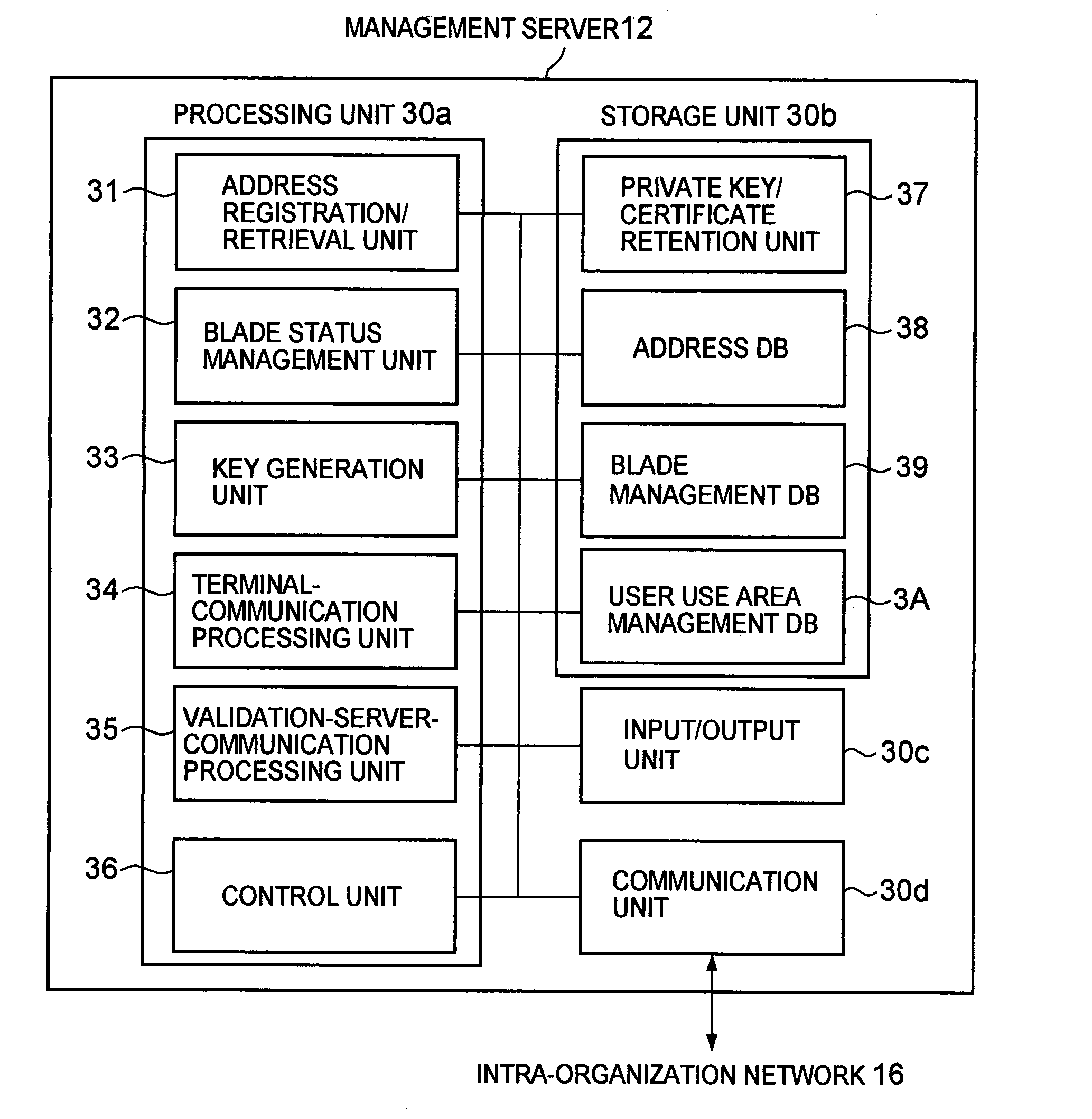
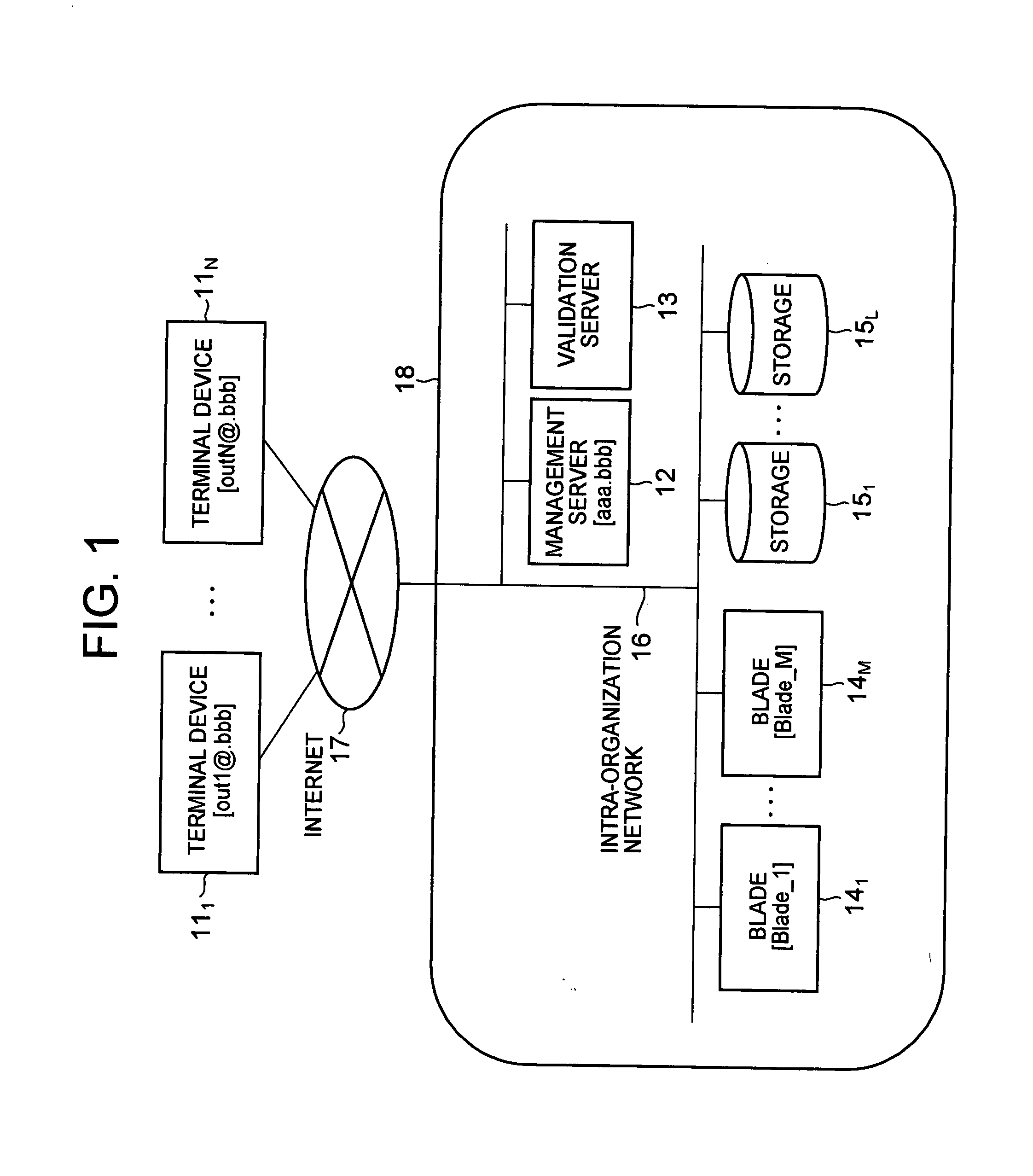
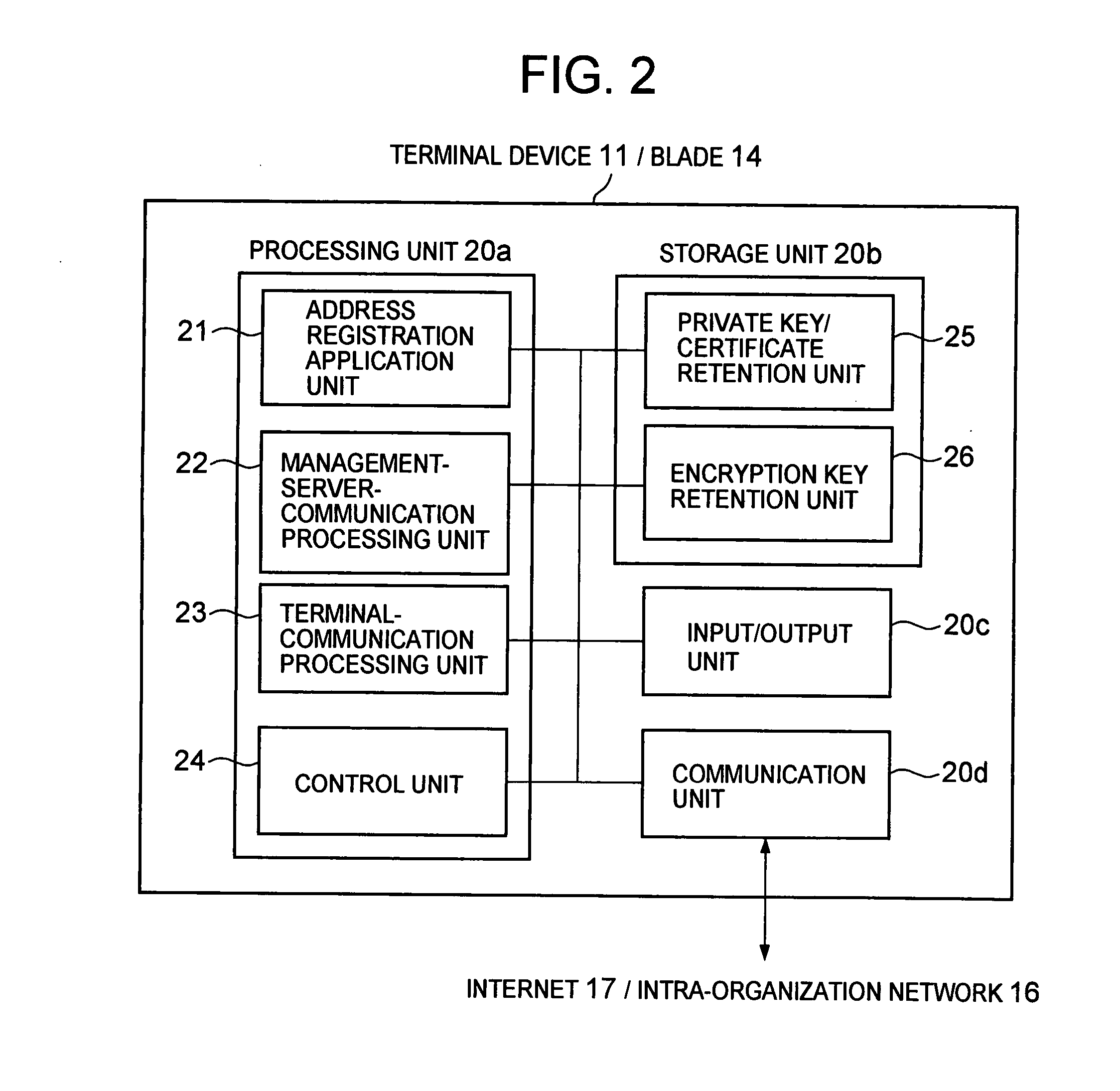
InactiveUS20080098221A1Accurate authenticationReduce loadUser identity/authority verificationMultiple digital computer combinationsEnd-to-end encryptionComputer hardware
To solve problems in that a load on a VPN device is large in a case where the number of terminal devices increases in encrypted communication using a VPN technique, and that only communication between the terminal device and the VPN device is encrypted, thus disabling end-to-end encrypted communication, a communication system is provided, including: a terminal device; a plurality of blades; and a management server that manages the blades, in which: the management server selects a blade, authenticates the terminal device and the selected blade, and mediates encrypted communication path establishment between the terminal device and the selected blade; the terminal device and the blade perform encrypted communication without the mediation of the management server; and the management server requests a validation server to authenticate each terminal.
Owner:HITACHI LTD
In-group message communication method and system
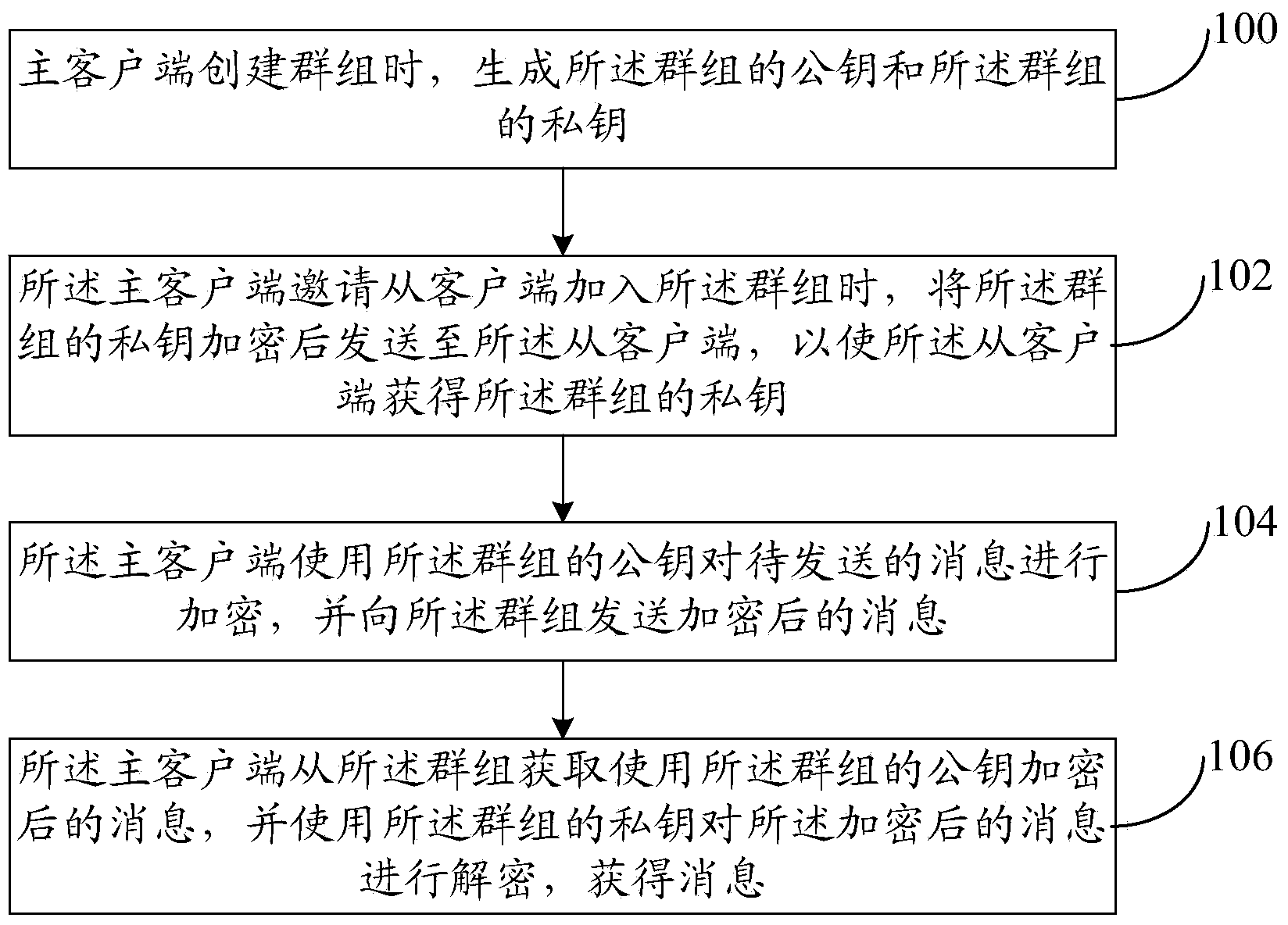
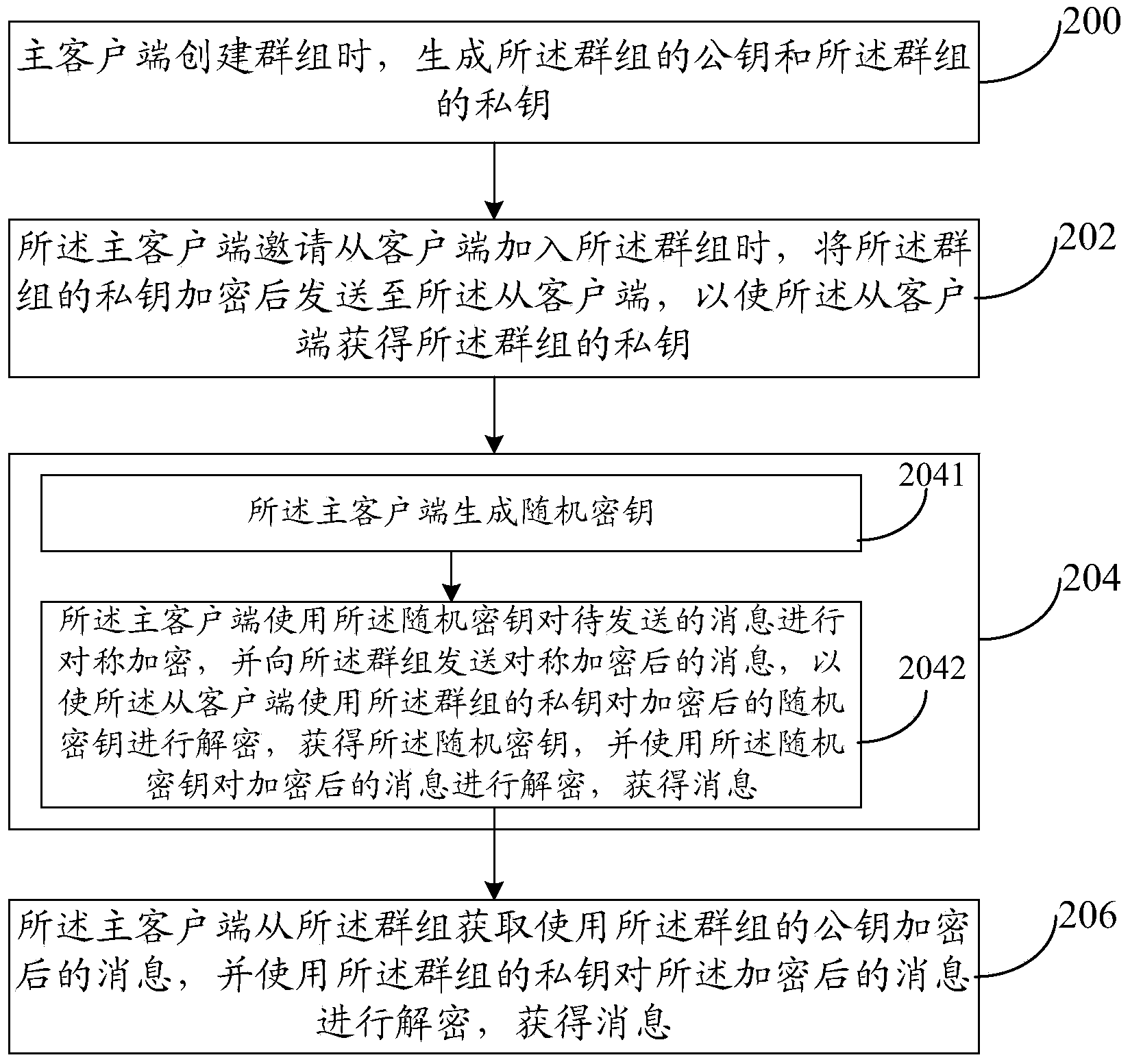
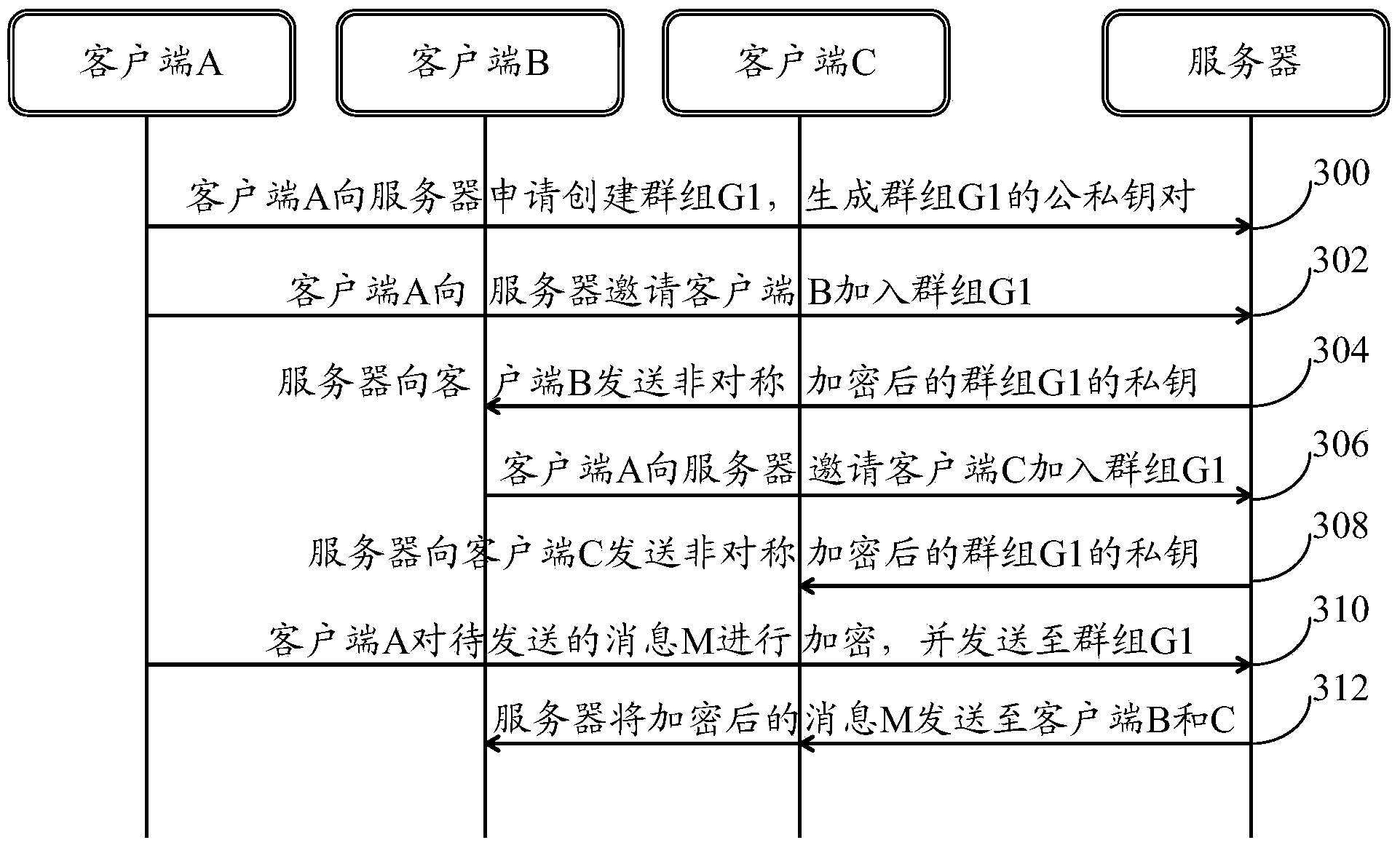
ActiveCN104219051AIncrease flexibilityImprove securityKey distribution for secure communicationUser identity/authority verificationEnd-to-end encryptionClient-side
The invention provides an in-group message communication method and system. The in-group message communication method includes: generating a public key of a group and a private key of the group when the group is established in a master client side; when the master client side is invited to join the group, transmitting the encrypted private key of the group to a slave client side so as to acquire the private key of the group from the slave client side; sharing the public key of the group between the master client side and the slave client side; the master client side using the public key of the group to have to-be-transmitted information encrypted and transmitting the encrypted information to the group; and / or the master client side acquiring information of the encrypted public key of the group from the group and using the private key of the group to decrypt the encrypted information to acquire messages. By the in-group message communication method and system, end-to-end encryption in the group is realized, and flexibility and safety in communication are improved.
Owner:BEIJING QIYI CENTURY SCI & TECH CO LTD
End-to-end encryption method and control device for the mobile phone SMS
InactiveCN101056176AEasy to operateCutting costsKey distribution for secure communicationUser identity/authority verificationEnd-to-end encryptionComputer hardware
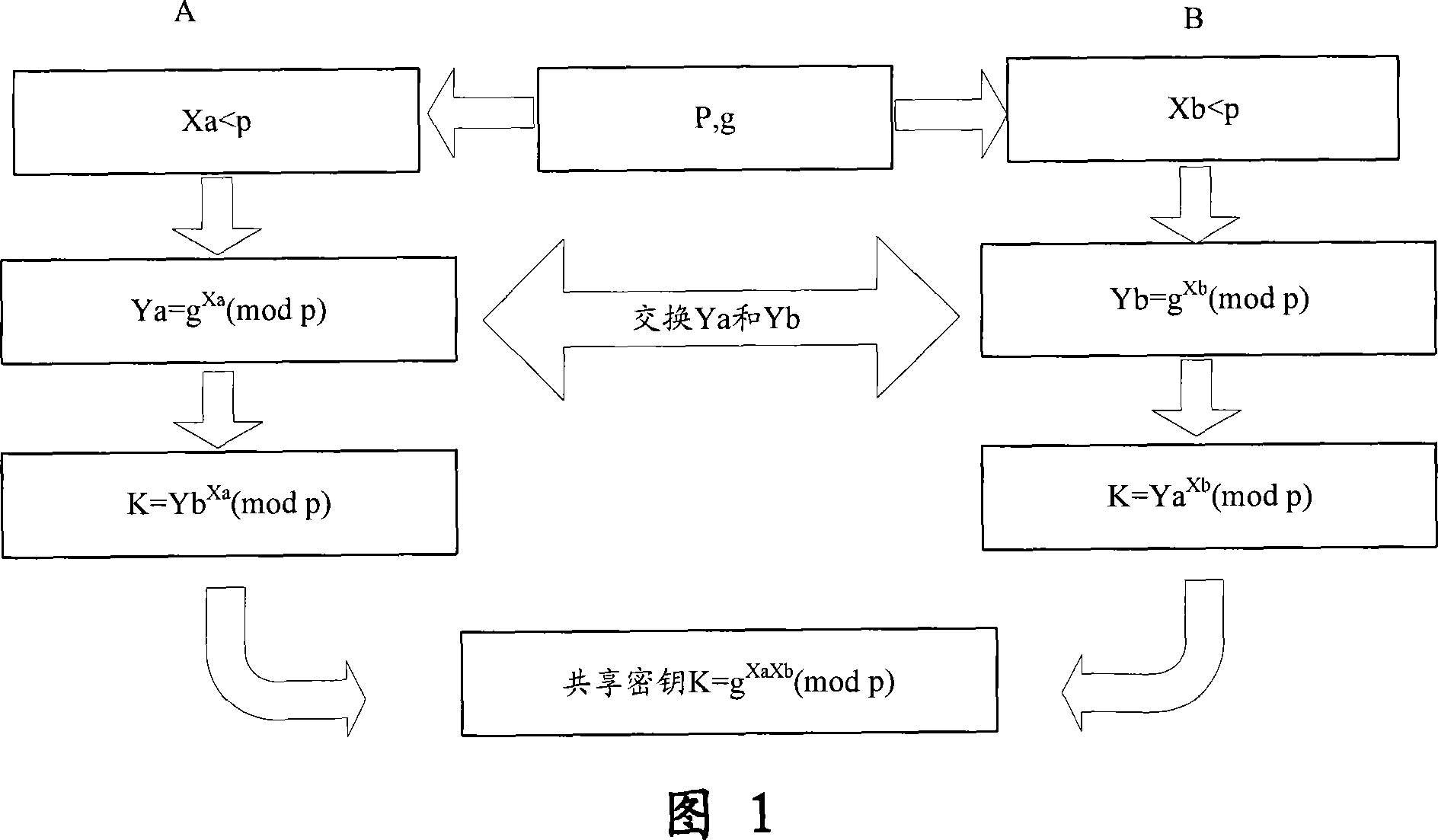
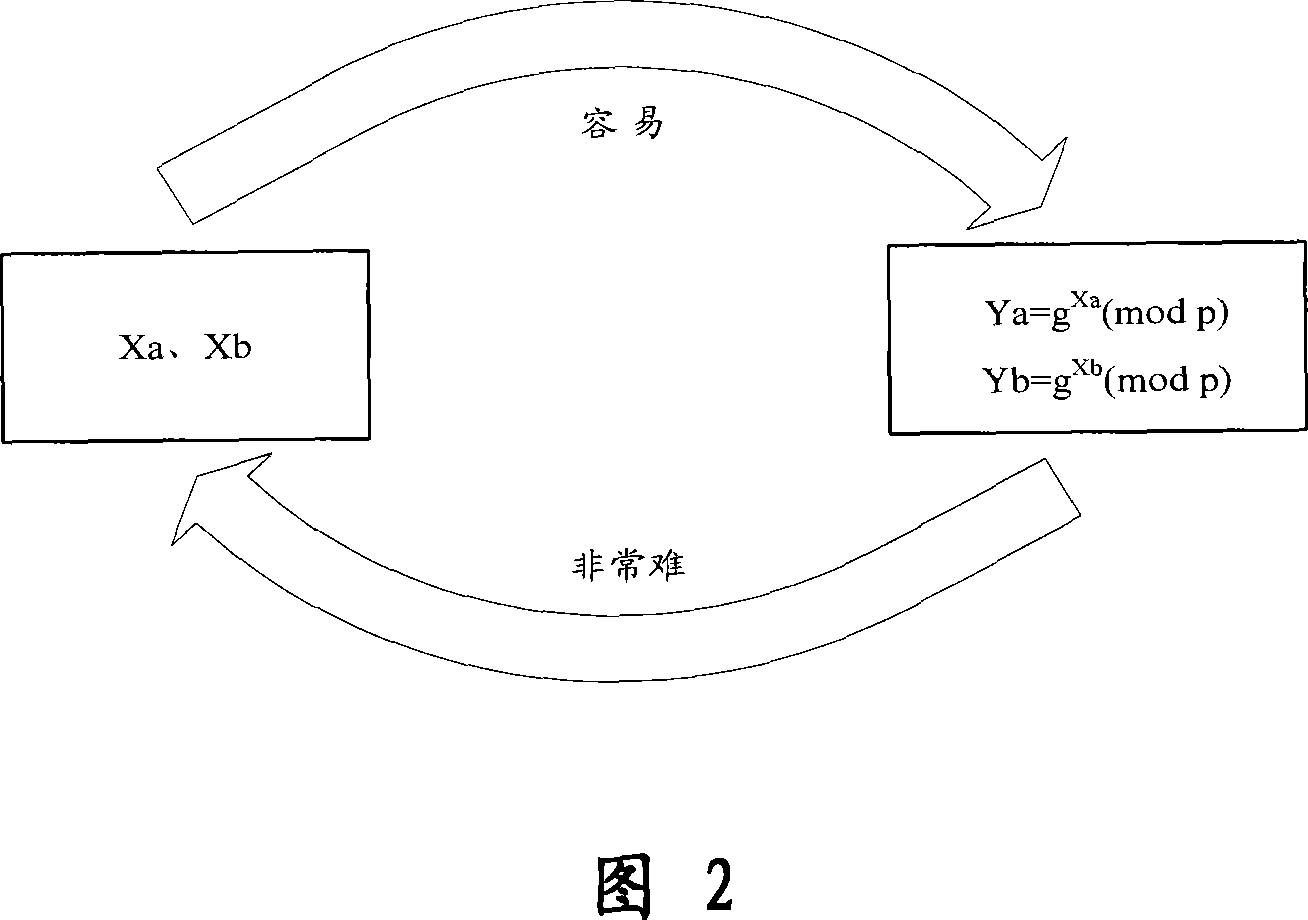
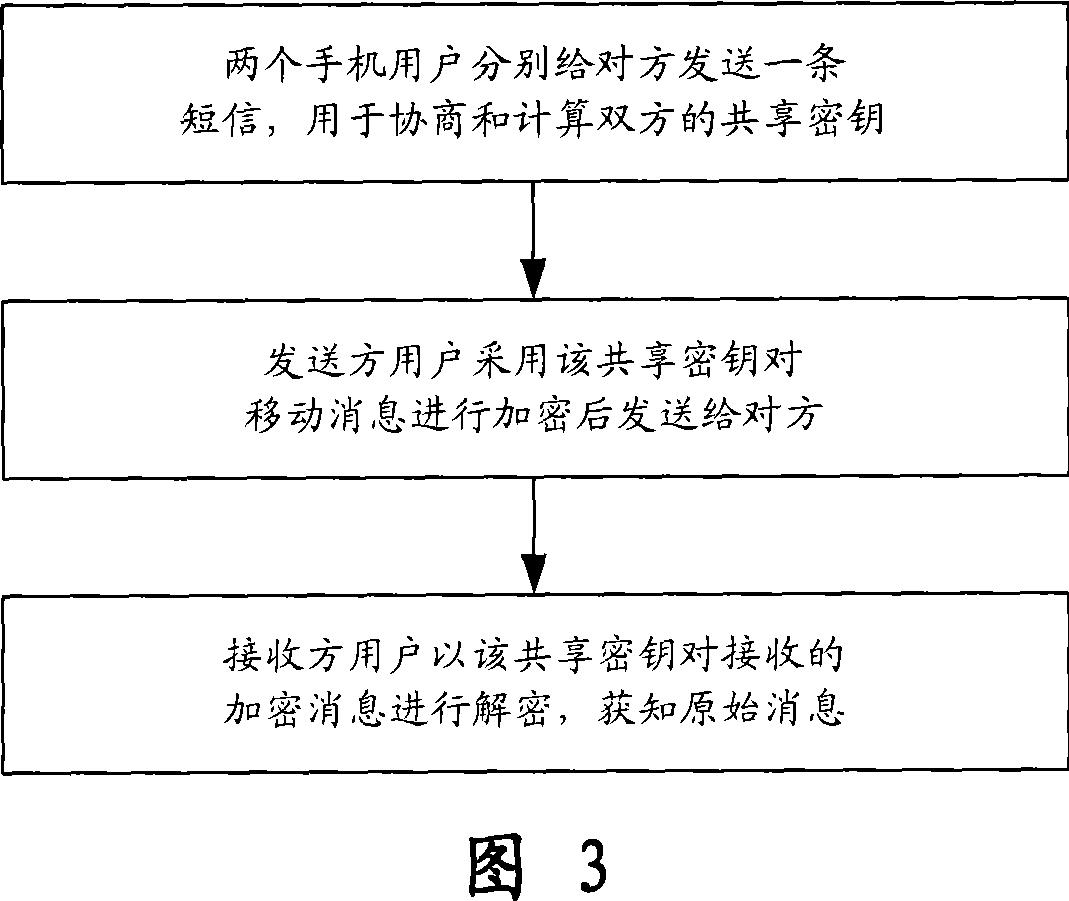
A method for the end-end encryption of message sent by mobile, before communication, two mobile users may mutually negotiate through the Diffie-Hellman key switching algorithm and calculate respectively to establish a shared key for both parties; then after encrypted the mobile message with the shared key, sent to the other party; after another user received this encrypted message, decrypts the encrypted message with the shared key, presents the original information to the receiver. The control device for the invention is a control component equipped in the mobile for mutual communicating with the message transmitting and receiving module, consists of decryption module, interface presenting module, encryption message storage module, key management module and key negotiation module. The invention method is easier to realize, high feasibility, the structure of control device is simple, the operating of user is almost identical with the receiving and transmitting of ordinary mobile messages, but the method has higher safety, meets with the high safety demand for mobile messages.
Owner:BEIJING NETQIN TECH
Method for payload encryption of digital voice or data communications
ActiveUS20090327703A1Key distribution for secure communicationUser identity/authority verificationEnd-to-end encryptionAuthorization
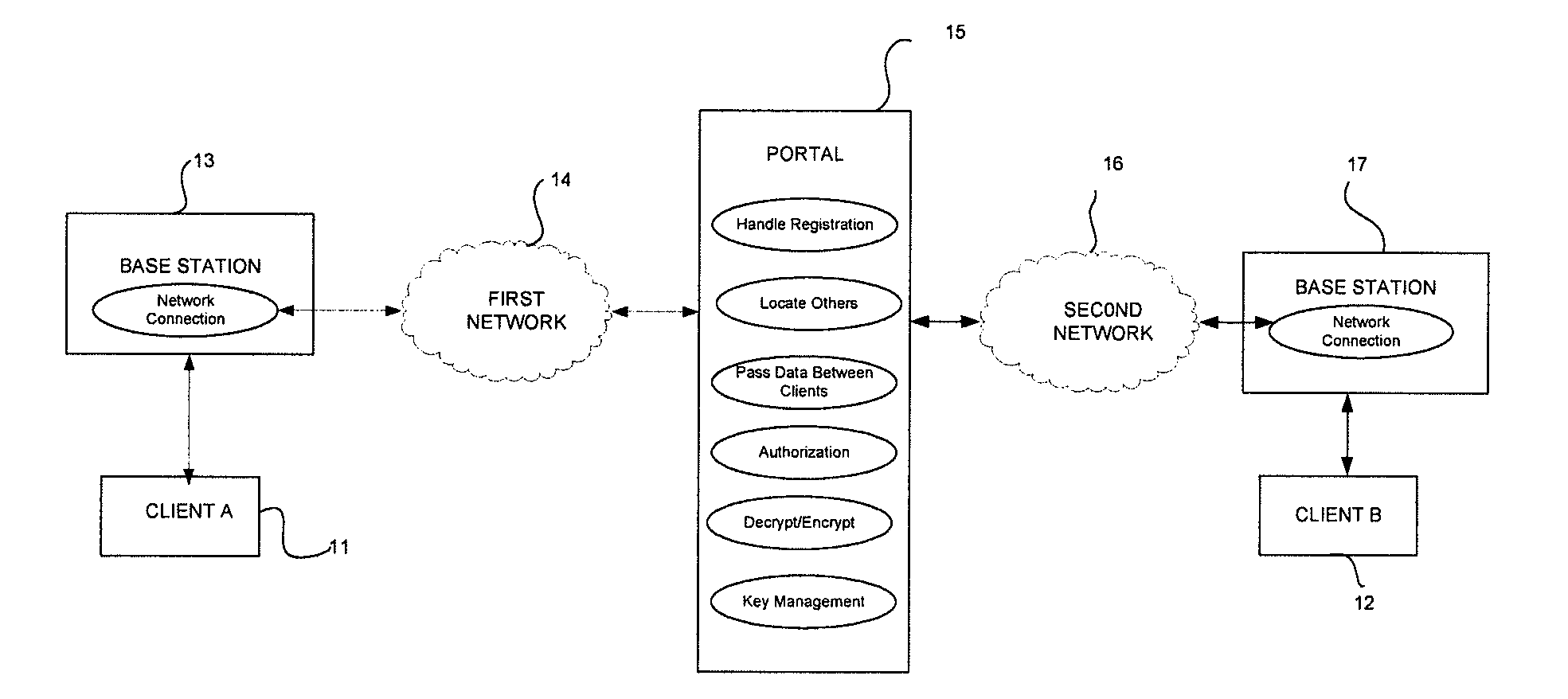
A security platform or network for transmitting end-to-end encrypted voice or data communications between at least a first digital device and a second device is disclosed. The network includes a network portal for registering the first digital device and the second device. The portal provides the first digital device and second device with at least first and second keys and receives requests from each device to communicate with each other. The portal searches for and receives authorization from the called device to set up a secure session with the calling device. The portal receives encrypted messages from the devices, decrypts the encrypted messages with the keys provided to the devices, and re-encrypts the received messages. The portal sends the re-encrypted messages to the other device. Accordingly, the devices are capable of securely communicating with each other by encrypting and decrypting the messages sent to and received from the portal. The intent is to provide a commercially feasible approach to protect sensitive information that is not government classified, with potential users including (a) Individuals—for protecting private information and conversations; (b) Companies—for protecting proprietary / sensitive information; and (c) Government—for protecting SBU conversations and information.
Owner:SECUREANT
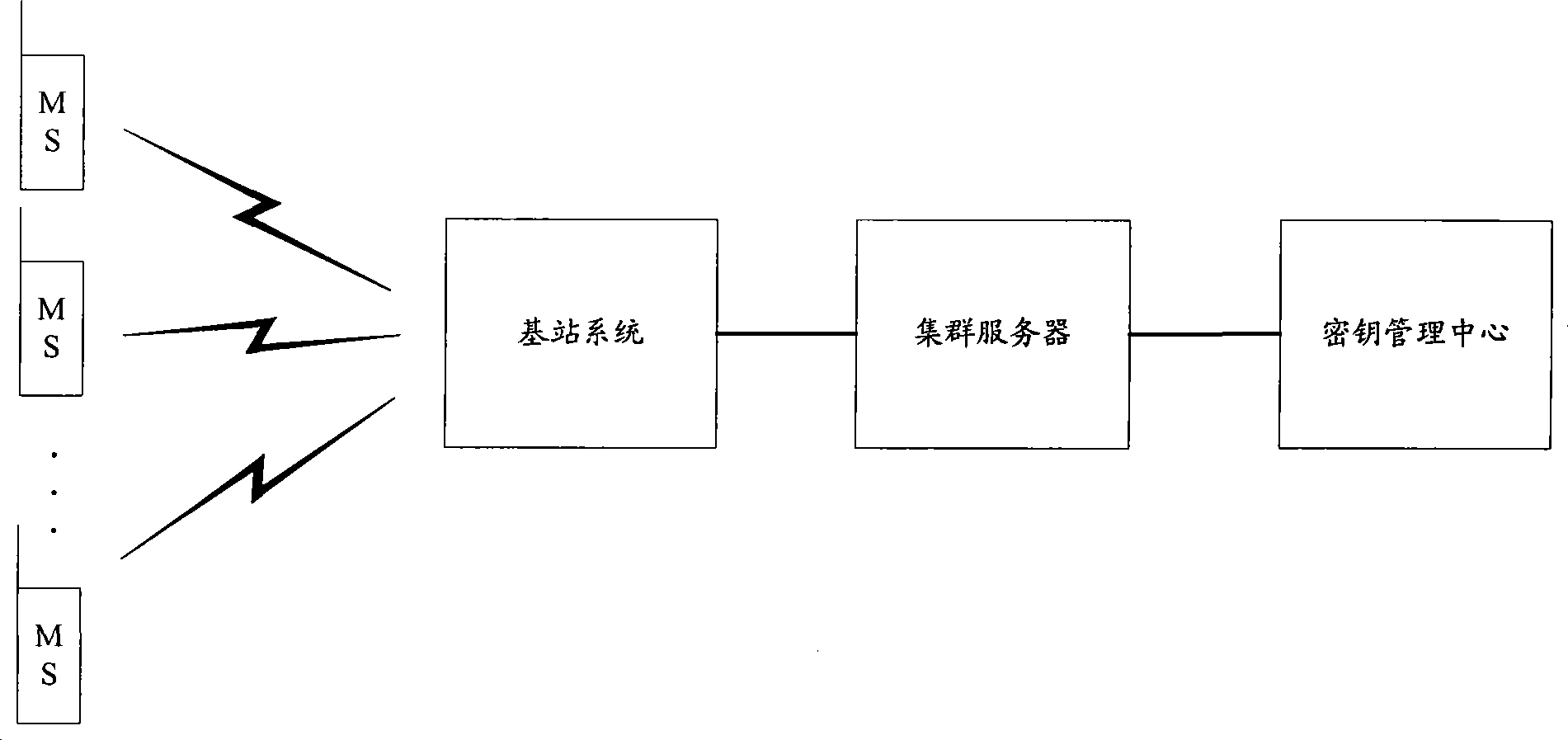
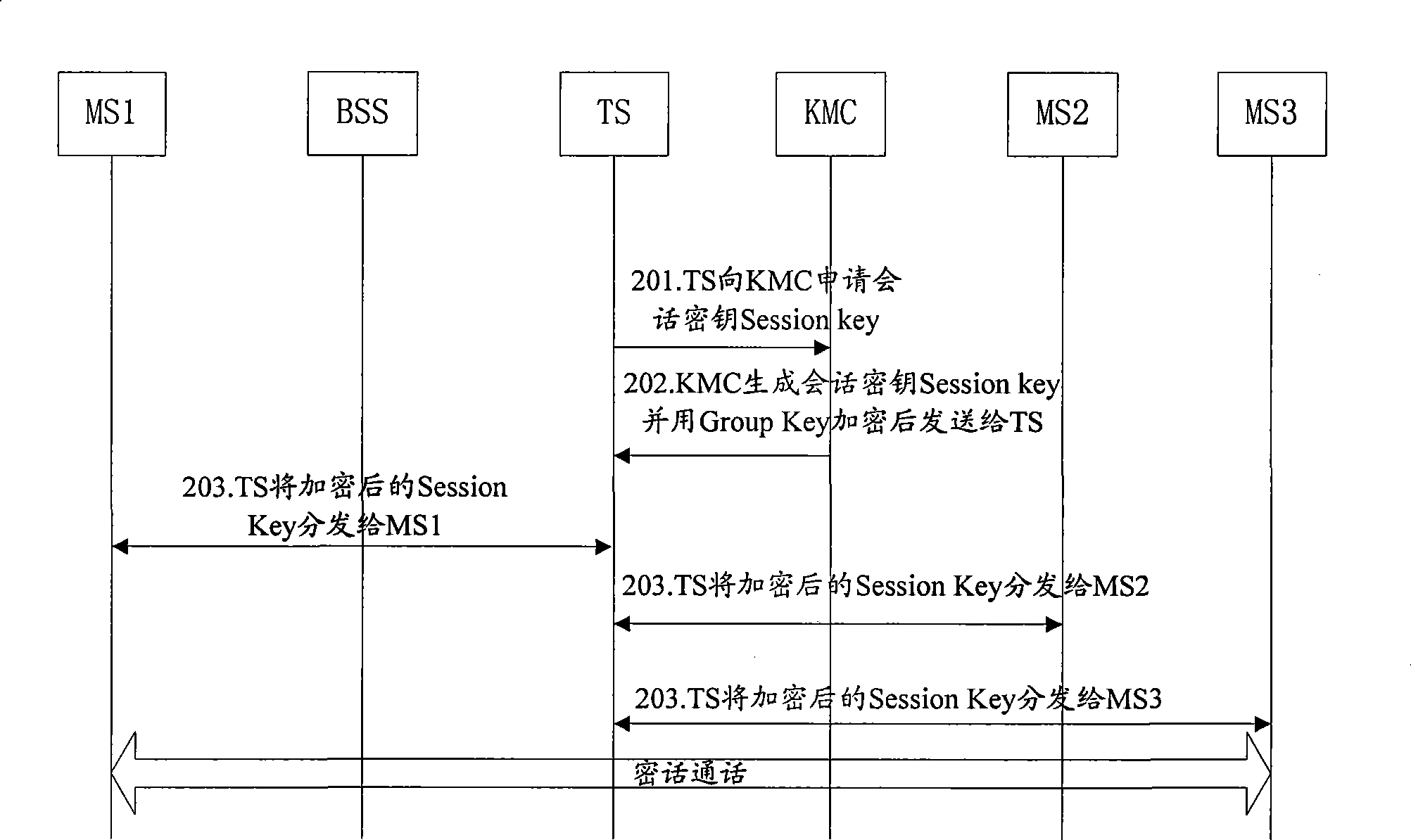
Method, system and equipment for implementing end-to-end encipher of mobile cluster set call
InactiveCN101442742AReduce loadShorten call setup delayNetwork topologiesBroadcast service distributionEnd-to-end encryptionCluster group
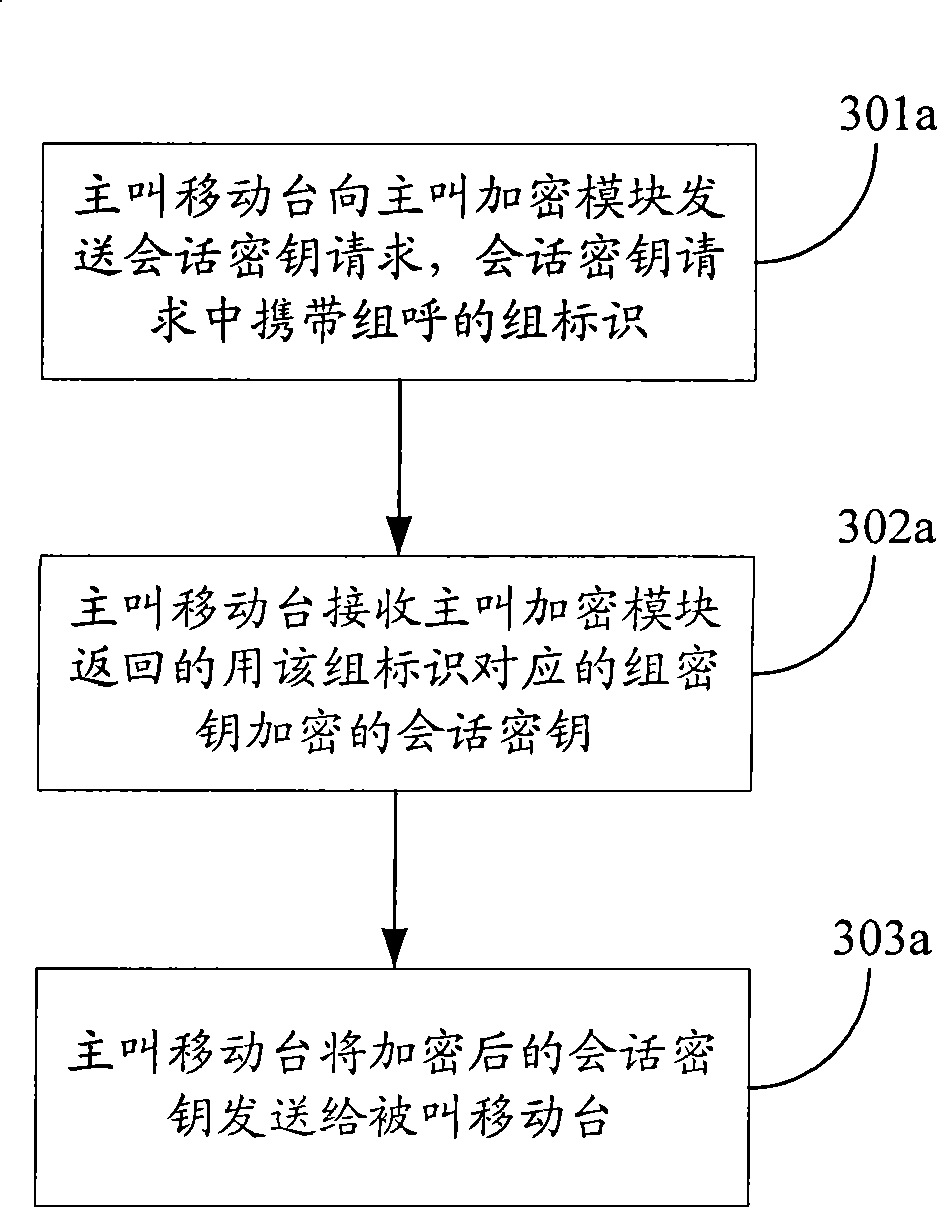
The embodiment of the invention discloses a method for implementing group calling end-to-end encryption for mobile cluster comprising: transmitting session key request to calling encryption module, the session key request carrying group ID of group calling; receiving the session key of group key encryption corresponding to the group ID returned by the encryption module; transmitting the encrypted session key to called mobile station. In the embodiment, end-to-end encryption cluster group calling can be still performed under single station cluster mode or KMC failure or end-to-end encryption application context of through mode; KMC is not needed to participate in session key generation and distribution in end-to-end encryption group calling, which largely reduces load of KMC and calling establishment time delay of end-to-end encryption of cluster group calling.
Owner:HUAWEI TECH CO LTD
Method for end-to-end enciphoring voice telecommunication
InactiveCN1816213AImprove scalabilityRealize safe and reliableSynchronising transmission/receiving encryption devicesRadio/inductive link selection arrangementsEnd-to-end encryptionExtensibility
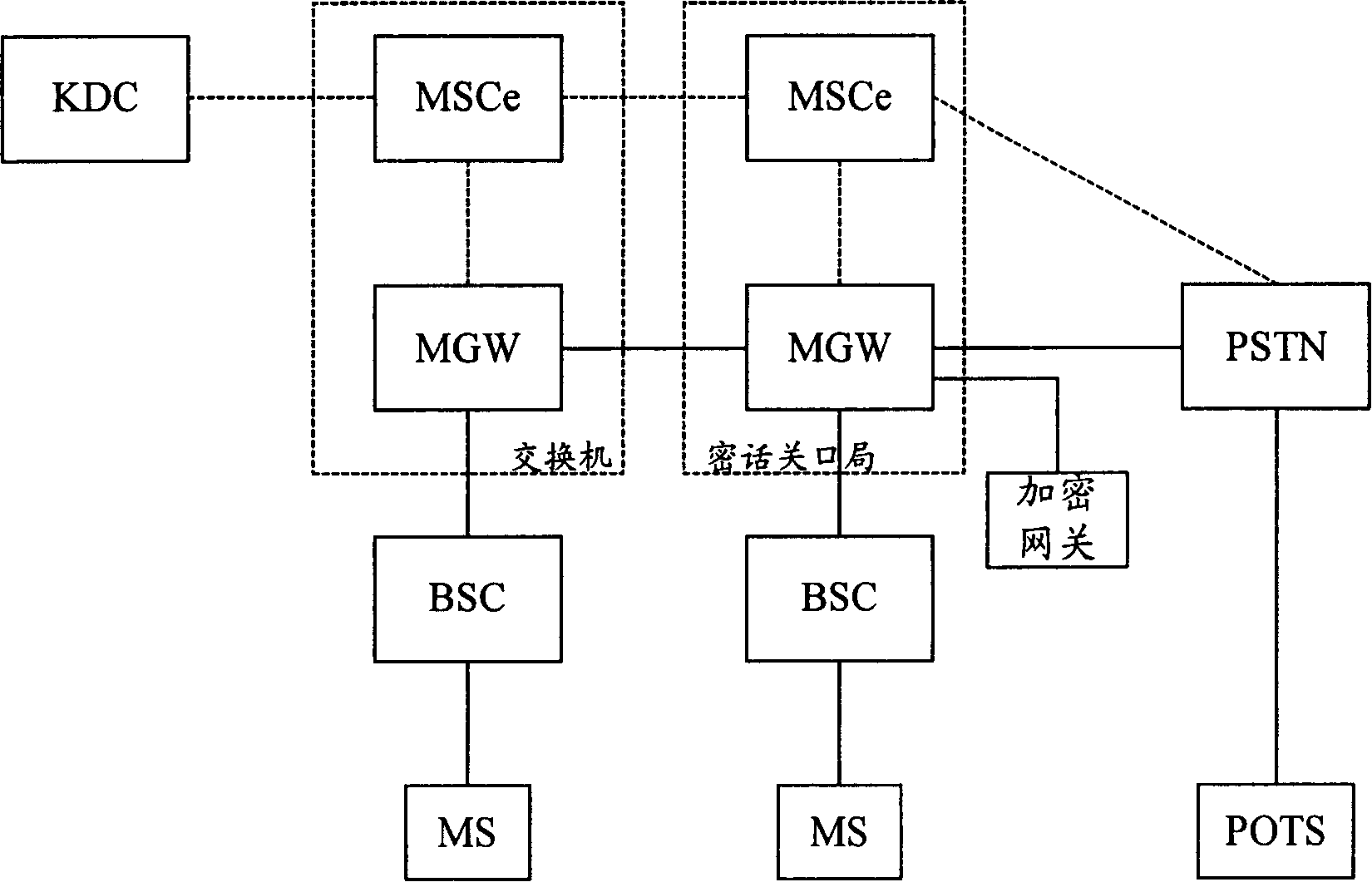
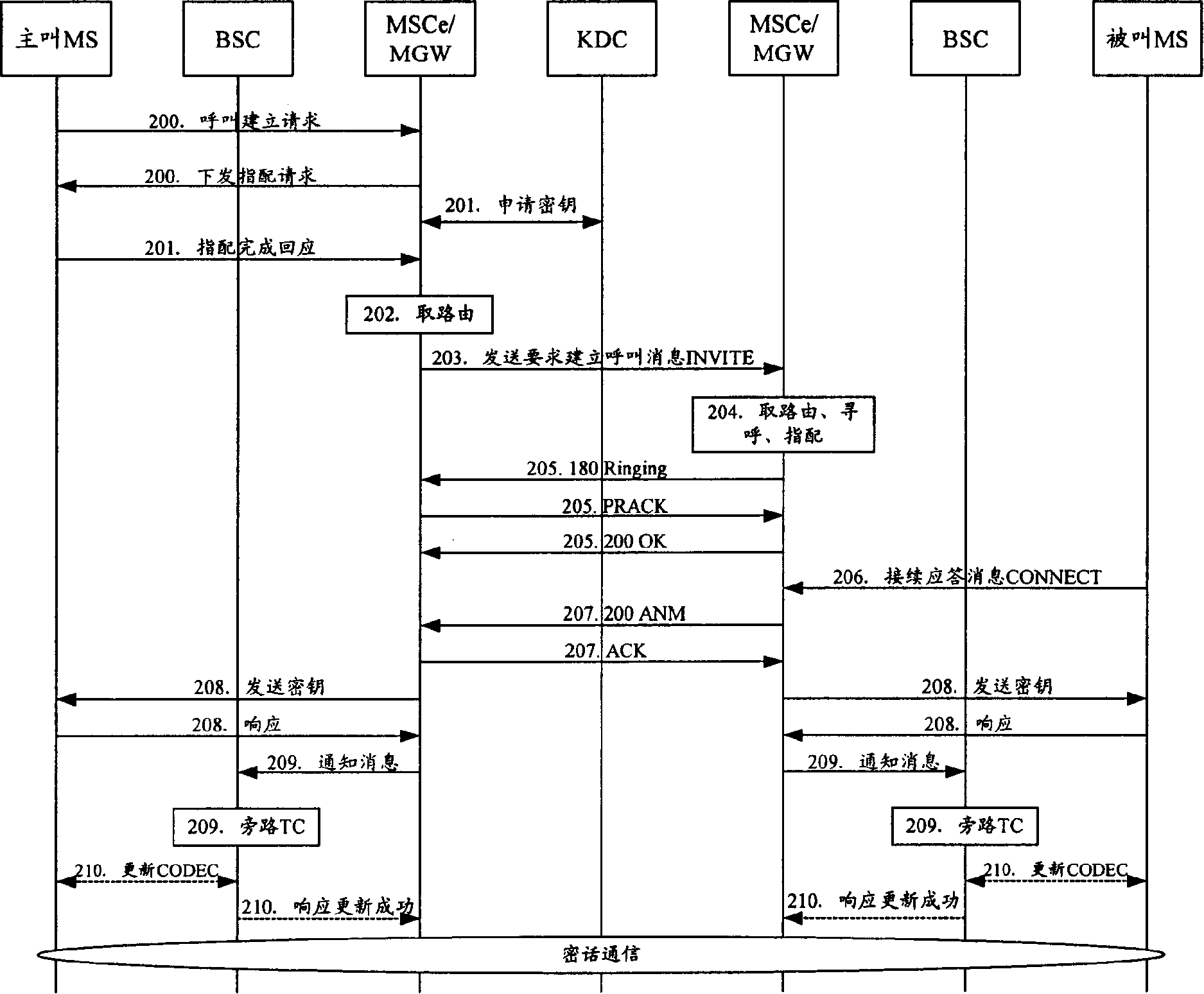
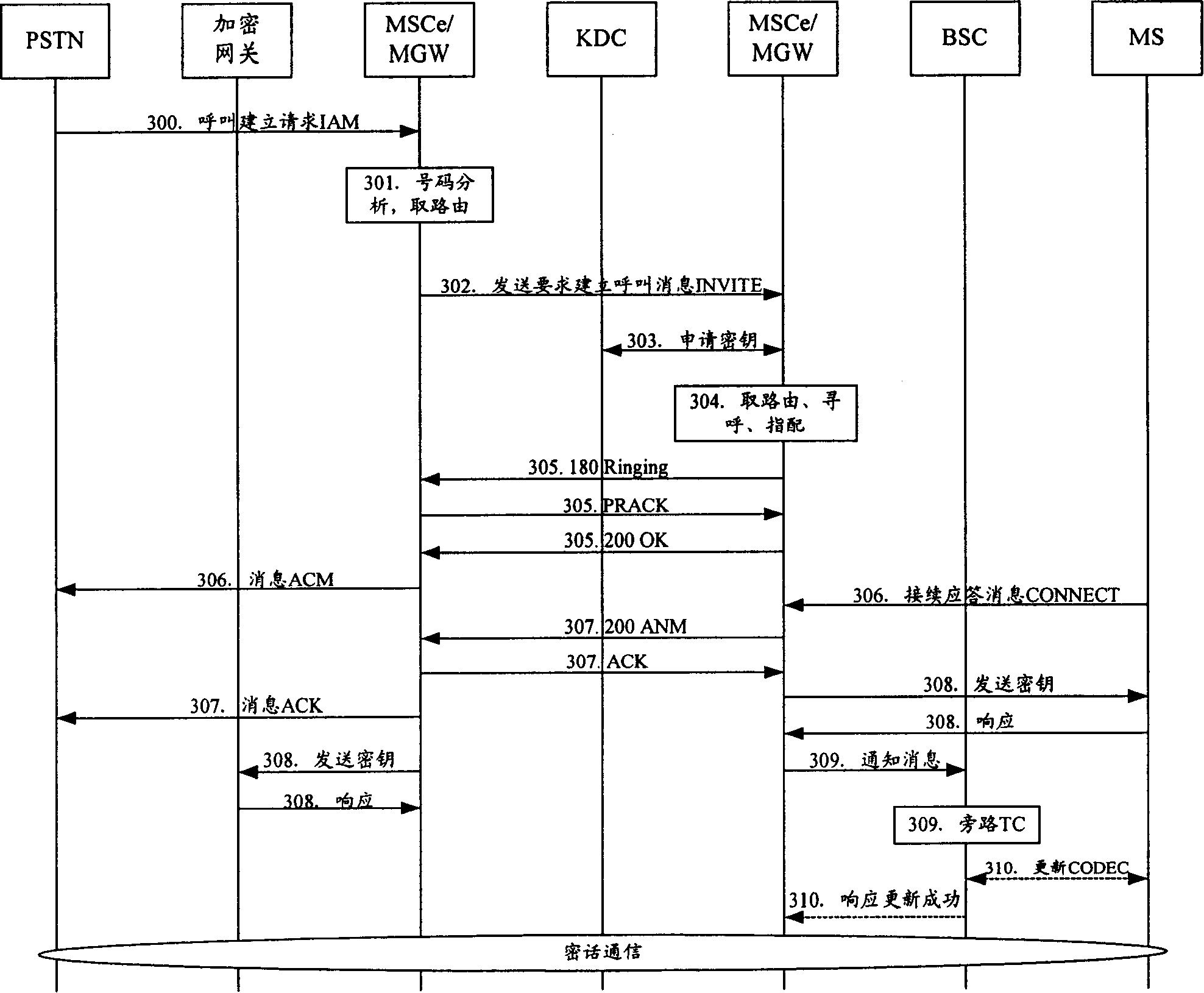
The method includes steps: after receiving request for building encrypted call from calling terminal, switchboard sends request for applying encryption key to key distribution center (KDC); receiving the request, and passing through authentication of encrypting qualification, KDC generates calling and called encryption keys, which are returned back to switchboard; switchboard sends the calling and called encryption keys to calling party and called party respectively, and switchboard the mobile terminal locates on informs converter TC in bypass speech encoding format of base station controller; using the received encryption keys, the calling terminal and called terminal carry out encrypted speech communication. Based on network control being as center, the invention realizes point-to-point encrypted speech communication. Powerful function on network side provides advantages are: safety, reliable, flexible and enhanced extensibility.
Owner:HUAWEI TECH CO LTD
Information encryption and decryption processing method and system
InactiveCN105450395AImprove securityDecryption implementationKey distribution for secure communicationEnd-to-end encryptionThird party
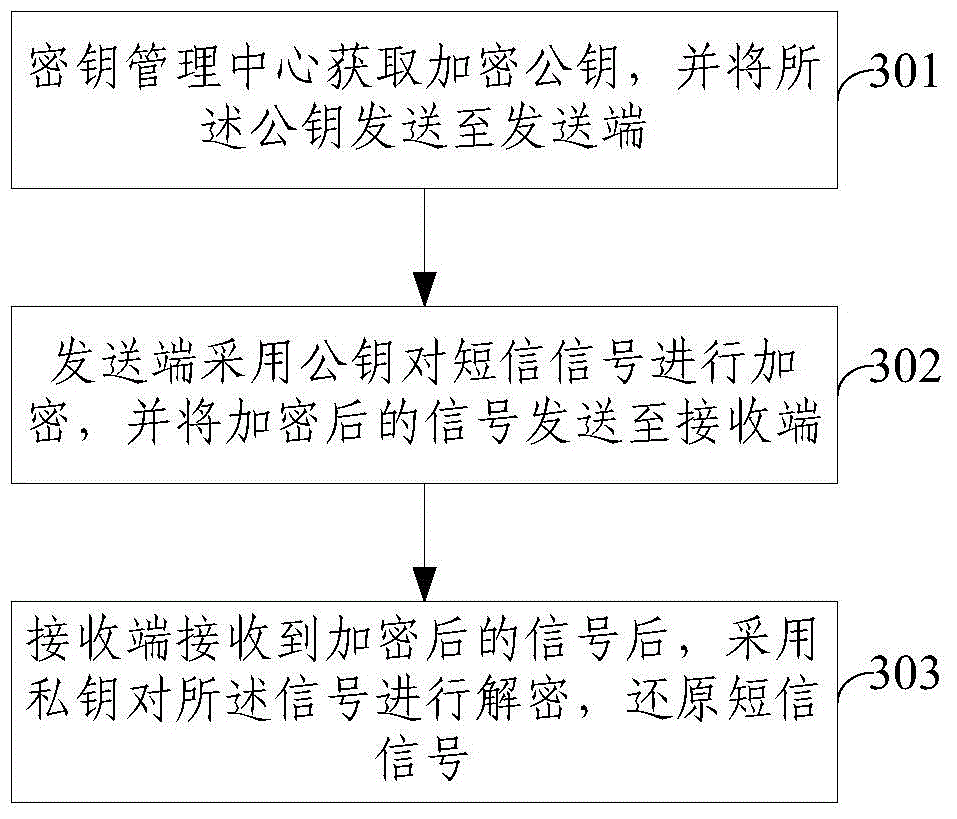
The invention discloses an information encryption and decryption processing method, a sending terminal, a receiving terminal and an information encryption and decryption processing system. According to the method, a public key of a target receiving terminal is generated at the sending terminal based on identification information of the target receiving terminal, information to be sent is encrypted by the generated public key to improve the security of the information, the received encrypted information is decrypted by a particular private key of the terminal at the receiving terminal. Therefore, end-to-end encryption of the user information is realized by a "public key-private key" key based on the asymmetric encryption technology, any third party cannot obtain the information contents of a user, so information leakage of terminal information resulting from illegal interception and other reasons in a transmission process is avoided, and the security of the terminal information is further improved.
Owner:THUNDERSOFT
Terminal to terminal encryption method of cell phone voice and data
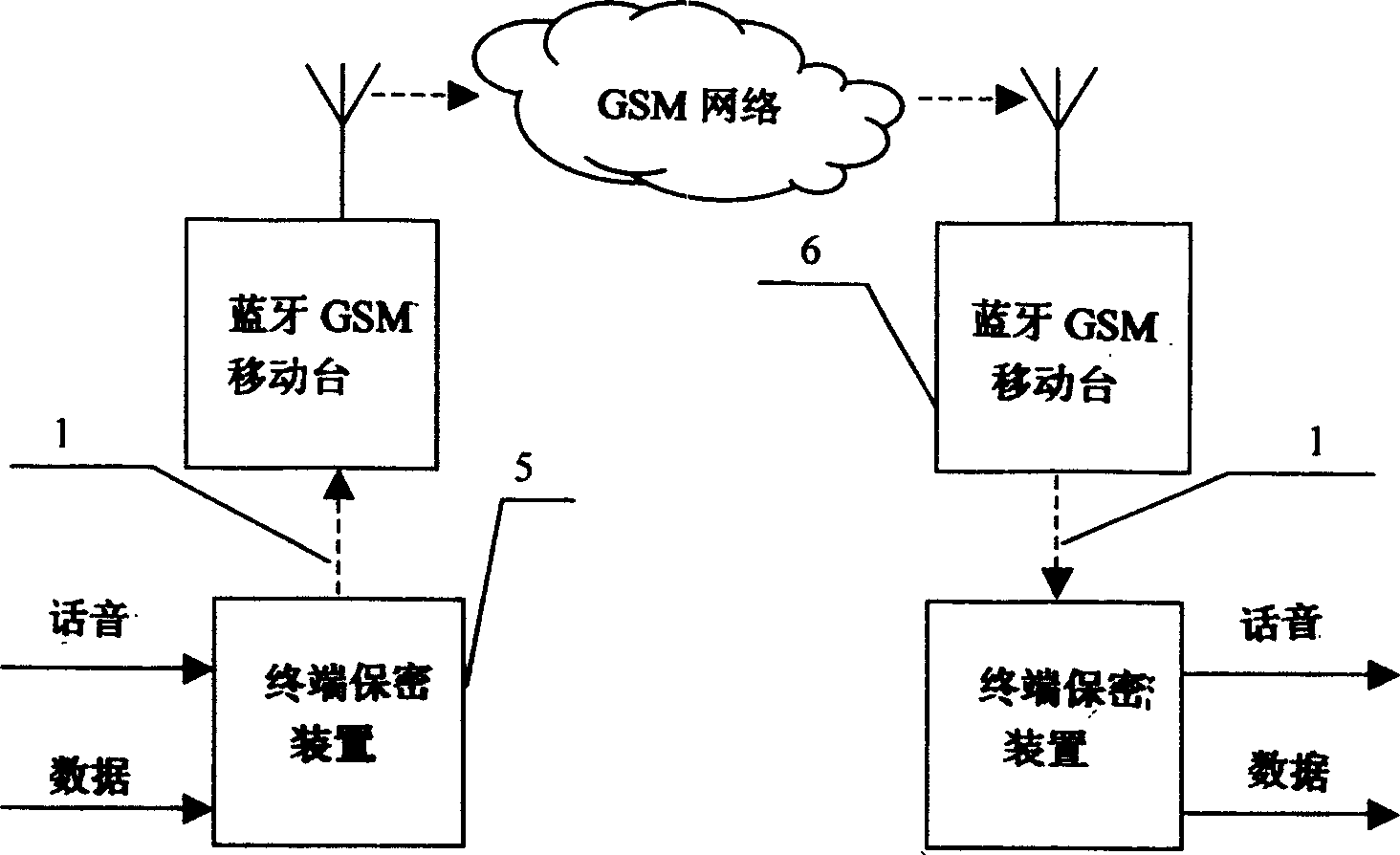
InactiveCN1592141AAchieve wireless connectionProperly encryptedSynchronising transmission/receiving encryption devicesNear-field systems using receiversEnd-to-end encryptionData information
This invention discloses an end-to-end ciphering method for GSM network voice and data when mobile stations carry out voice / data communication between them, voice / data information sent by the delivery end are coded and ciphered by an outboard terminal security device to be delivered to the blue tooth mobile station of the delivery end by its channel, the out board device is connected with GSM mobile station supporting the blue tooth data communication function to realize the end-to-end ciphering of GSM network voice and data service.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
Andriod system-oriented implement method of mobile secure terminal
InactiveCN105025475AEnsure safetyDo not interfere with normal callsSecurity arrangementEnd-to-end encryptionVoice communication
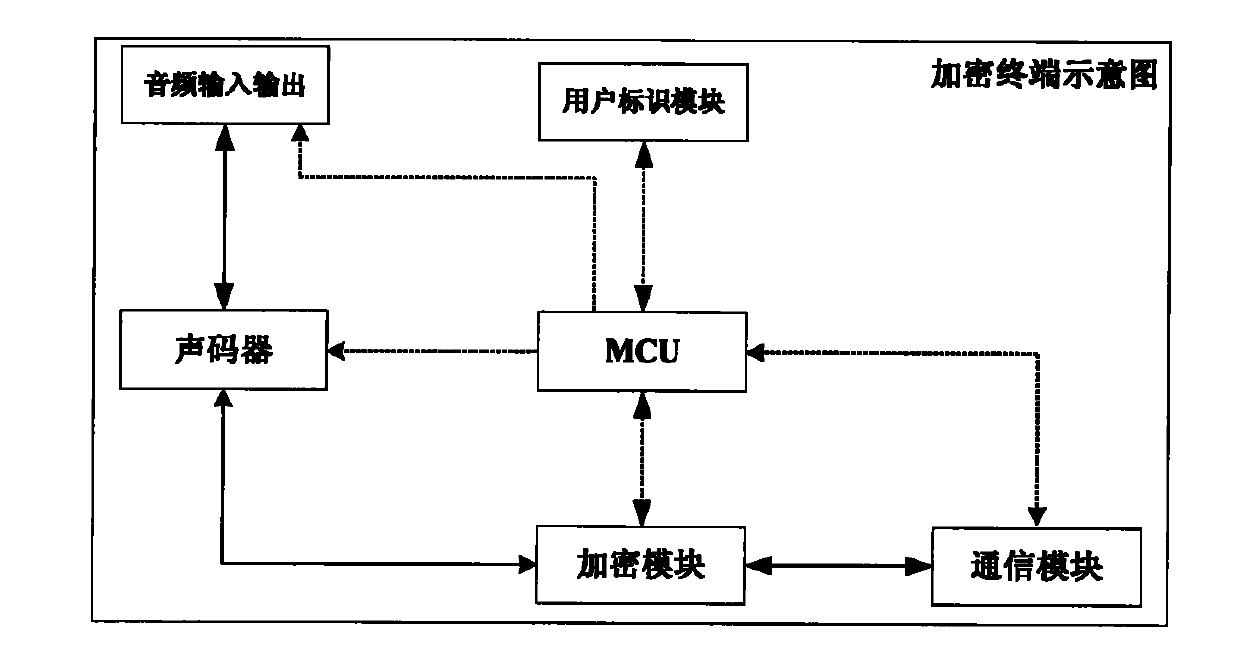
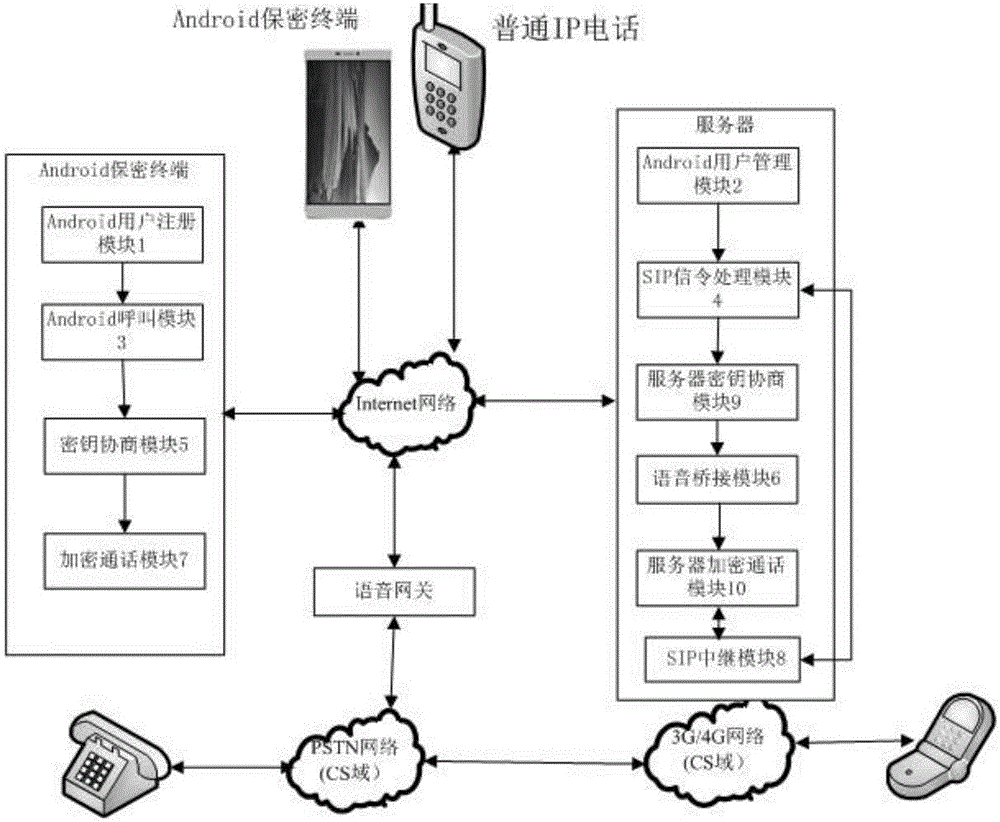
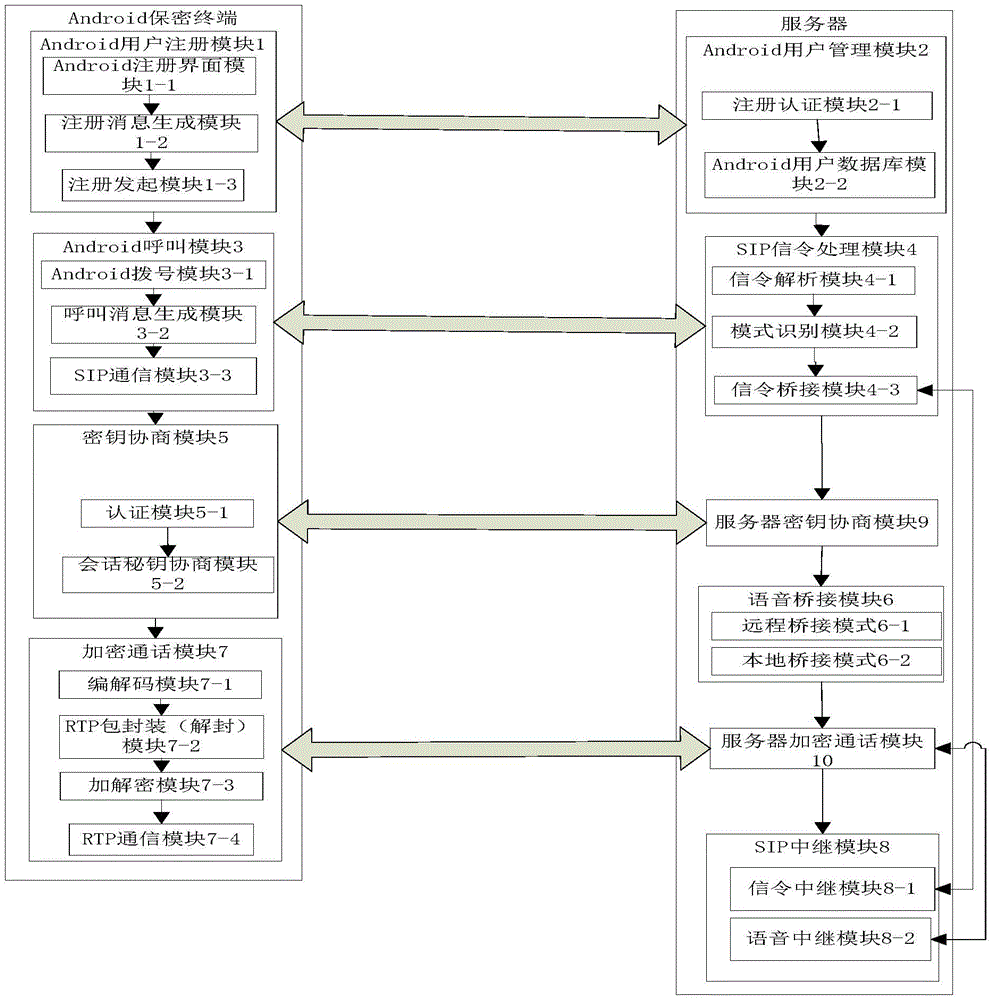
The invention discloses an Andriod system-oriented implement method of a mobile secure terminal. The mobile secure terminal comprises an Andriod user registration module, an Andriod user management module, an Andriod calling module, an SIP signaling processing module, a key negotiation module, a server key negotiation module, a voice bridging module, an encrypted conversation module, a server encrypted conversation module and an SIP relay module. The implement method supports two encrypted communication modes: the first one is that one-time pad end-to-end encrypted voice communication for mobile terminals with Andriod operating systems is achieved while the two parties who communicate with each other are both secure terminals, namely the first mode is an end-to-end encrypted communication mode; the second one is that one-time pad encrypted voice communication from the mobile terminal with the Andriod operating system to a server is achieved while only one of the two parties who communicate with each other is the secure terminal, namely the second mode is a halfway encryption communication mode from the secure terminal to the server. The implement method of the invention does not need extra hardware to support, and is friendly in user interface and easy to operate.
Owner:东南大学常州研究院
Security module for encrypting a telephone conversation
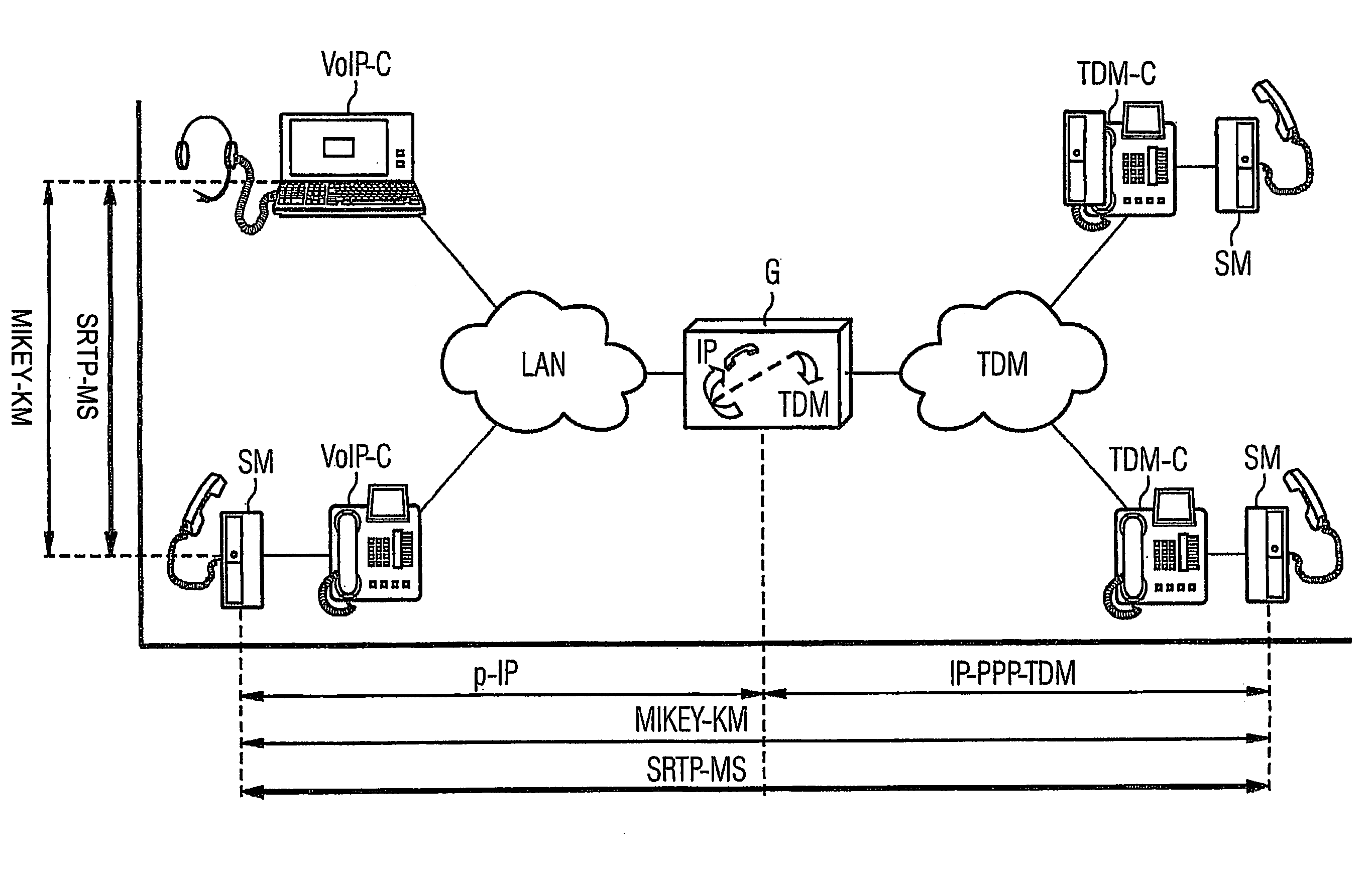
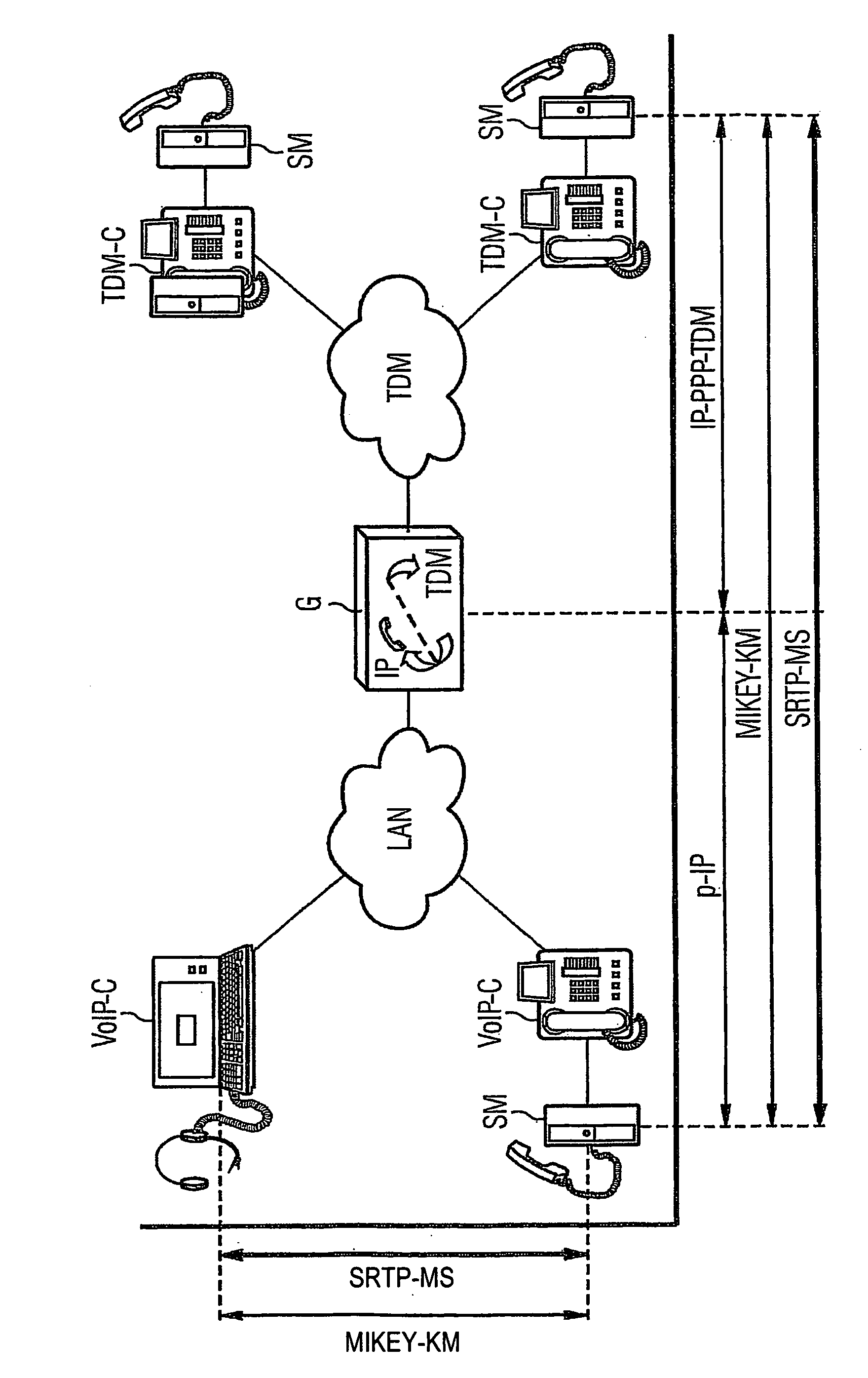
InactiveUS20070121582A1Solve insufficient bandwidthSufficient rateKey distribution for secure communicationInterconnection arrangementsEnd-to-end encryptionCrypto phone
A telephone conversation between one or several first telecommunication terminals in a packet oriented data network and telecommunication terminals in an analog and / or digital network is encrypted by a module which enables the use of protocols from a LAN network to a TDM network to carry out end-to-end encryption.
Owner:SIEMENS AG
Relay method of encryption communication, gateway server, and program and program memory medium of encryption communication
The relay method for relaying an encryption communication in a gateway server between a client device and a content server includes the steps of receiving an encryption communication connection message to the content server from the device; producing a temporary encryption communication permit and a private key of its counterpart for the content server of a destination server name included in the connection message; sending the permit to the device; performing an End-End encryption communication with the device, receiving an encrypted access request message sent by the device, and decrypting and converting the request message to an access request message of a plain text; performing an End-End encryption communication with the content server, and acquiring content information instructed by the access request message; and performing value added processing for the acquired content information and its communication header, encrypting the information and the header, and sending them to the device.
Owner:HITACHI LTD
Fuel dispensing payment system for secure evaluation of cardholder data
A system used in a retail environment for providing end-to-end encryption of payment cardholder data. An input device configured to receive cardholder data is operative to encrypt the cardholder data according to a first encryption method to produce first encrypted cardholder data. A cardholder data handling device is in electronic communication with the input device. A secure evaluation assembly (SEA) is operatively connected to the cardholder data handling device and comprises antitampering control electronics adapted to decrypt the first encrypted cardholder data to produce unencrypted cardholder data. The antitampering control electronics evaluate the unencrypted cardholder data to determine whether the unencrypted cardholder data is payment cardholder data or nonsensitive cardholder data. Finally, if the unencrypted cardholder data is payment cardholder data, the antitampering control electronics of the SEA are adapted to encrypt the unencrypted cardholder data according to a second encryption method to produce second encrypted cardholder data.
Owner:GILBARCO ITAL SRL
Encryption communication method and system of mobile terminal
InactiveCN104581712ARealize and guarantee end-to-end encrypted transmissionImprove securitySecurity arrangementEnd-to-end encryptionComputer hardware
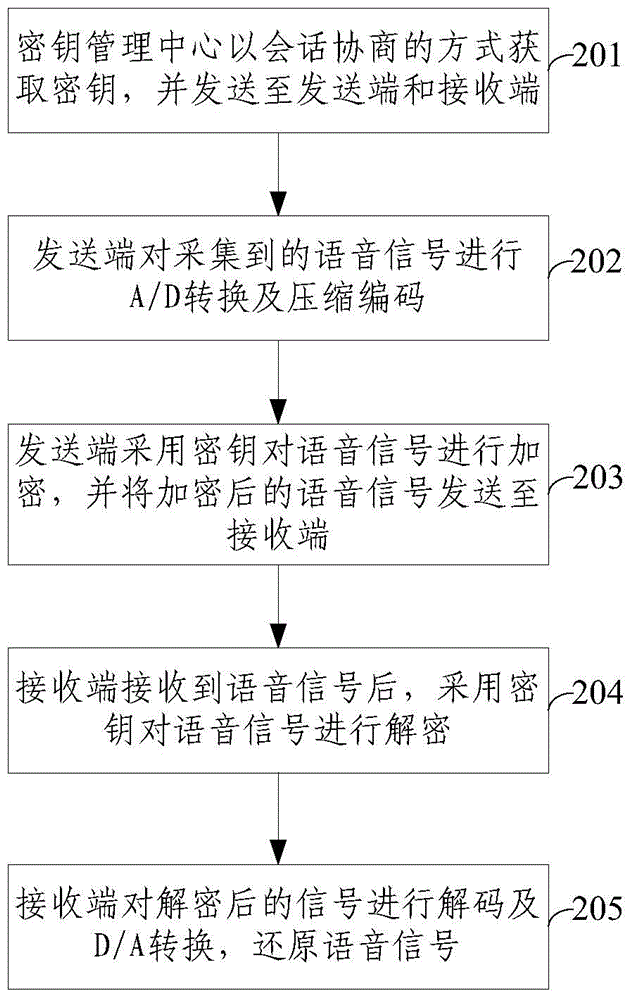
The invention provides an encryption communication method of a mobile terminal. The method comprises steps as follows: a key management center distributes a key for a sending end and a receiving end; the sending end encrypts a signal sent by the key and sending the encrypted signal to the receiving end; after receiving the signal, the receiving end decrypts the signal through the key to restore the signal. The invention further provides an encryption communication system of the mobile terminal. The system comprises the mobile terminal, an encryption communication device and the key management center. The encryption communication method and system of the mobile terminal can guarantee end-to-end encryption transmission of data in a mobile communication system and the safety is high.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com