End-to-end encryption method and control device for the mobile phone SMS
A technology for mobile phones and messages, applied in the fields of control devices, mobile communications and information security, can solve problems such as damage, severe damage to user interests, and no security guarantee, and achieve the effects of low cost, simple method and process safety.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0054] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be further described in detail below in conjunction with the accompanying drawings.
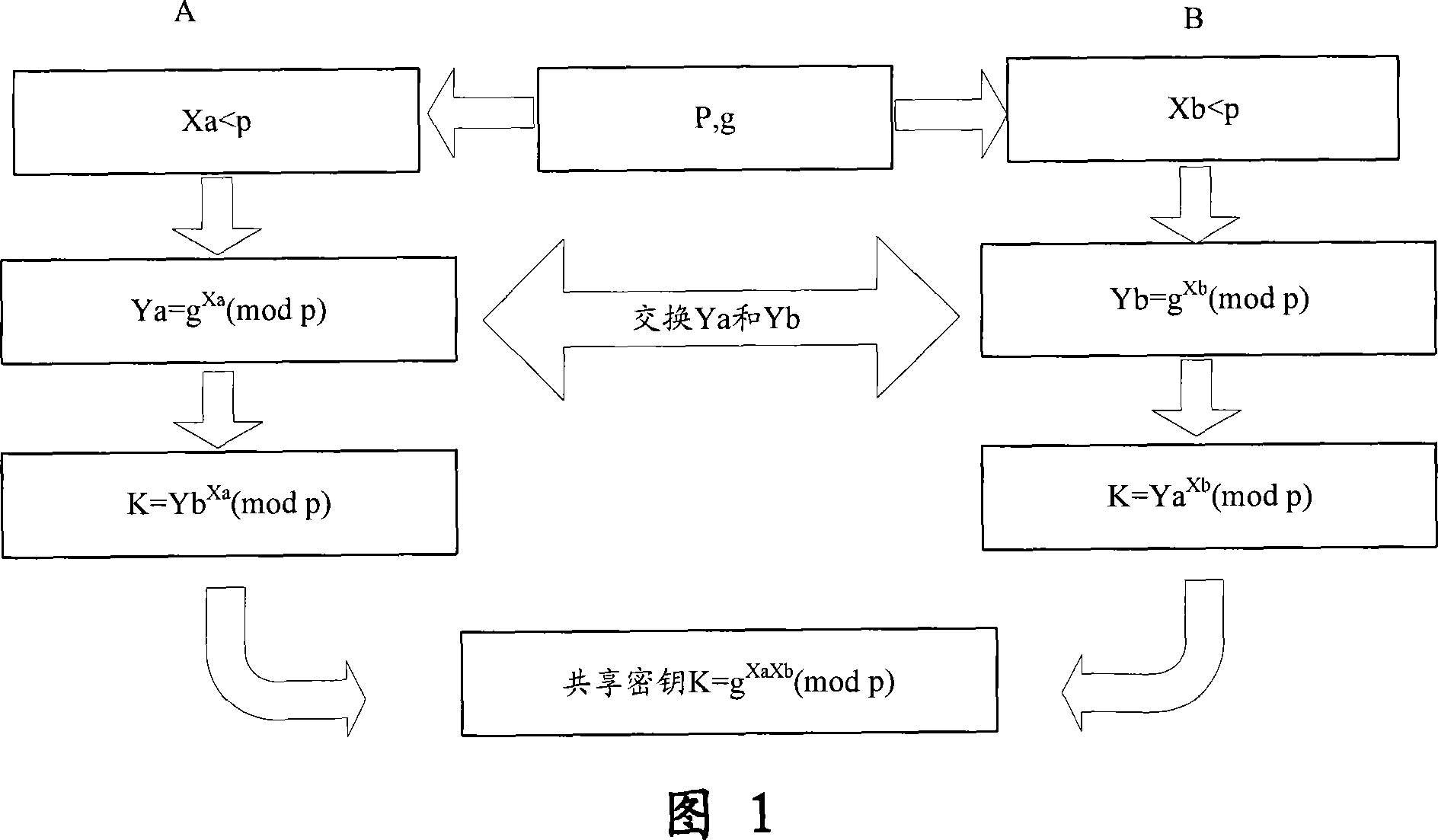
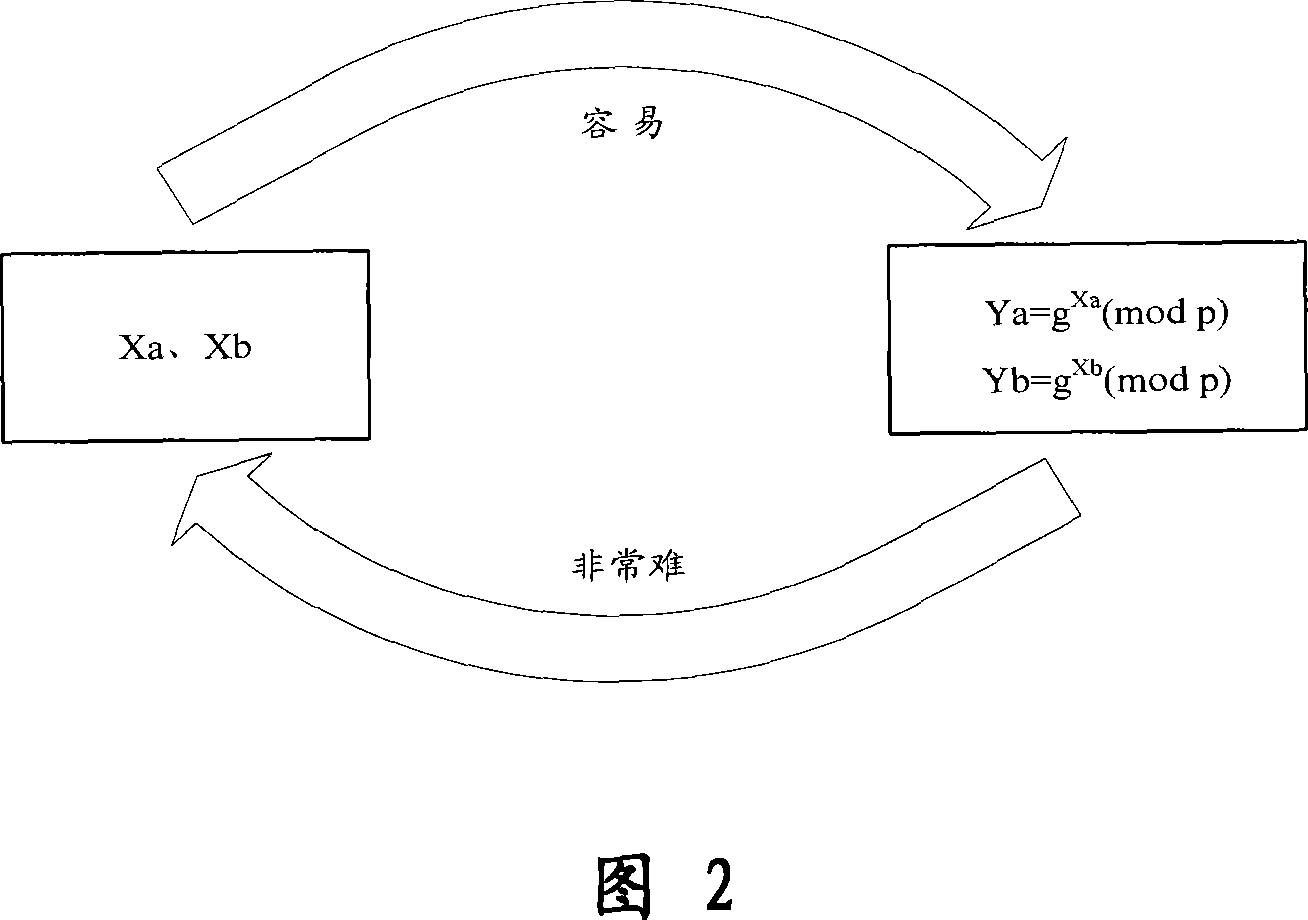
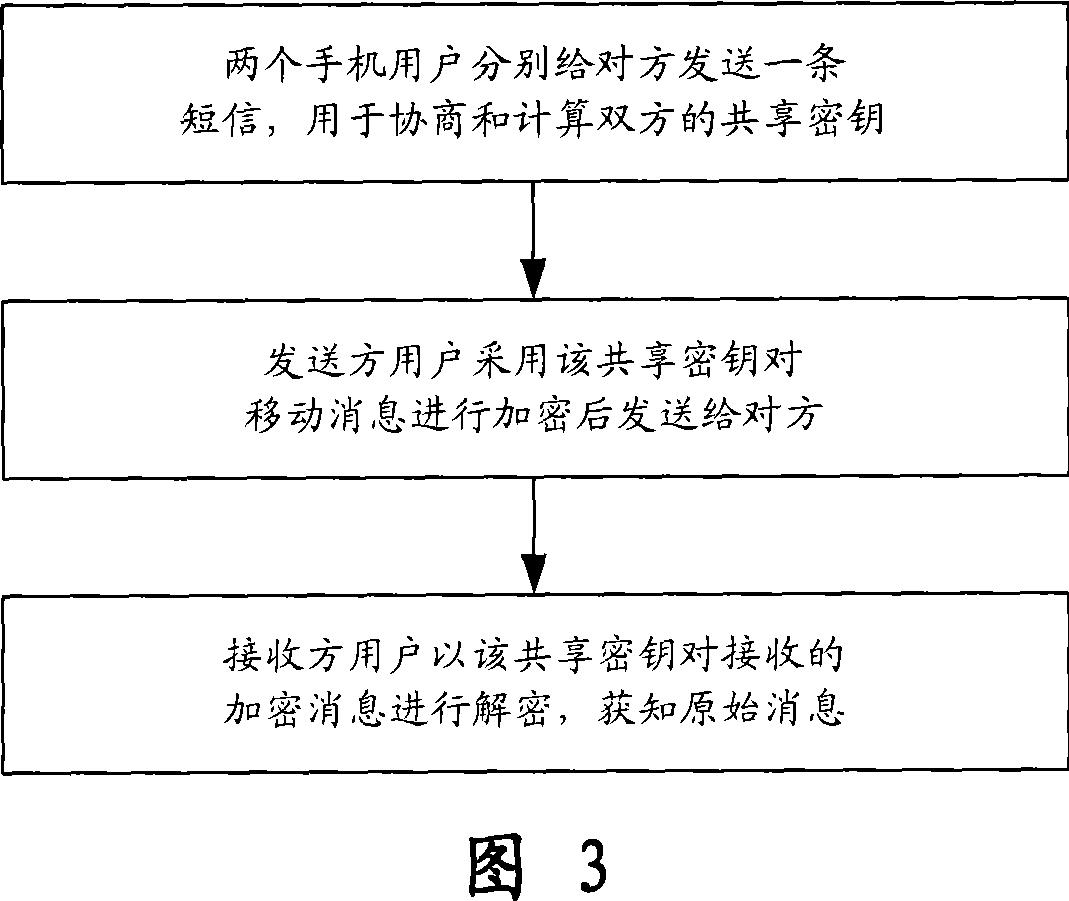
[0055] The present invention is an end-to-end encryption method for messages transmitted by mobile phones. Before communication, two mobile phone users use the Diffie-Hellman key exchange algorithm to negotiate with each other and calculate separately to establish a key shared by both parties. ; Then use the negotiated shared key to encrypt the mobile message and send it to the other party; after receiving the encrypted message, another user decrypts the encrypted message according to the shared key, and presents the original information to Receiver; in this way, end-to-end encrypted communication can be realized on the insecure wireless communication channel. In addition, when viewing a received common message, the user can press a specific key or select a specif...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com