Information encryption and decryption processing method and system
A processing method and encryption and decryption technology, applied in the field of information encryption and decryption processing methods and systems, can solve problems such as information content leakage, hidden dangers of end user information security, and inability to control information content security, so as to improve security and avoid information leakage. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
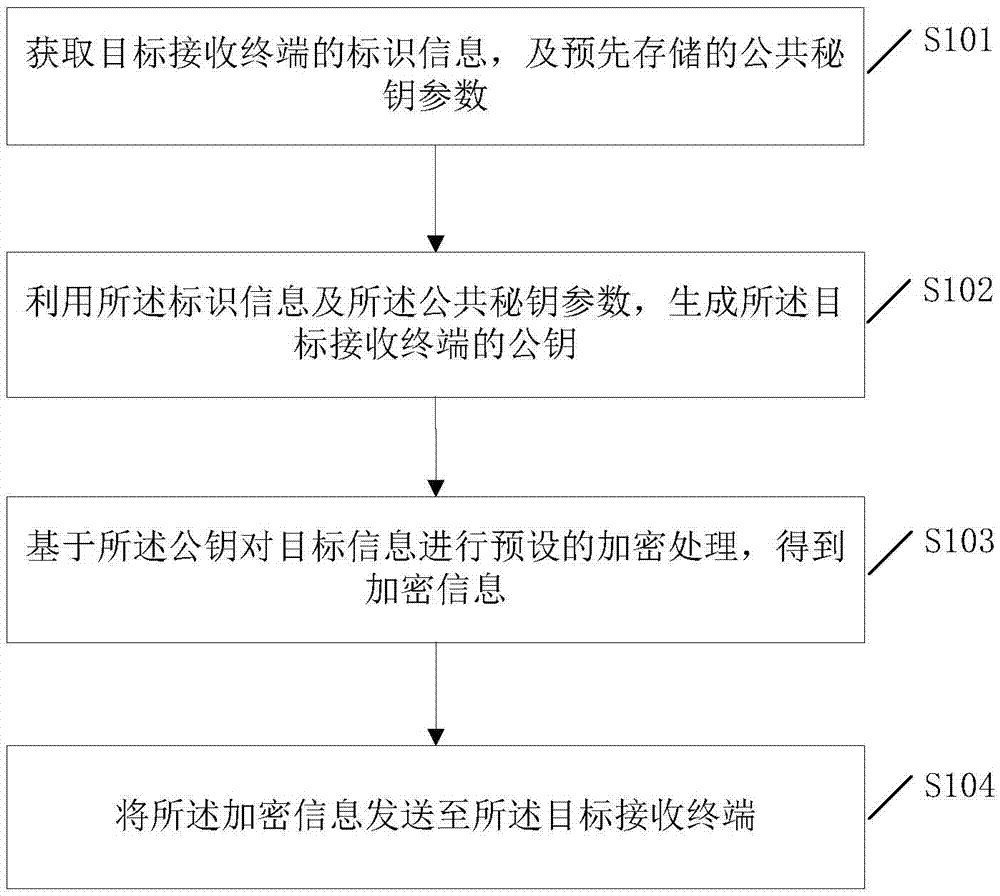
[0072] Embodiment 1 of the present invention discloses an information encryption and decryption processing method applicable to a sending terminal. The sending terminal may specifically be a mobile terminal such as a smart phone, a wearable device, or a tablet computer. Refer to figure 1 , the information encryption and decryption processing method may include the following steps:
[0073] S101: Obtain identification information of a target receiving terminal and pre-stored public key parameters.
[0074] This application aims to implement end-to-end encryption of user information such as user short messages based on asymmetric encryption technology, so as to prevent any third party from obtaining the information content of the end user. This embodiment specifically uses a mobile phone device as an example to encrypt and decrypt the information The processing method is described, wherein the identification information may be information such as a mobile phone number that can i...
Embodiment 2
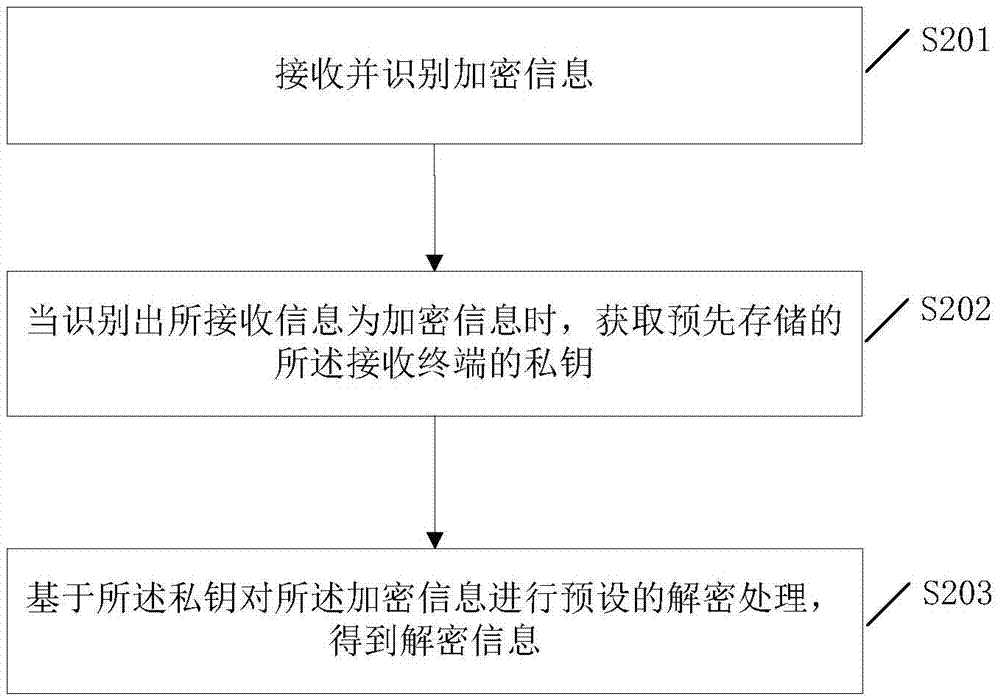
[0086] Embodiment 2 of the present invention discloses an information encryption and decryption processing method applicable to a receiving terminal. Refer to figure 2 , the information encryption and decryption processing method may include the following steps:
[0087] S201: Receive and identify encrypted information;
[0088] S202: When it is recognized that the received information is encrypted information, acquire a pre-stored private key of the receiving terminal;
[0089] S203: Perform preset decryption processing on the encrypted information based on the private key to obtain decrypted information.
[0090] When the receiving terminal receives the encrypted information sent by the sending terminal, it first recognizes that the received information is encrypted information through the encrypted identification of the information header, such as "#", "*" or "$", and then filters out the information header Part of the encrypted identification to obtain ciphertext inform...
Embodiment 3
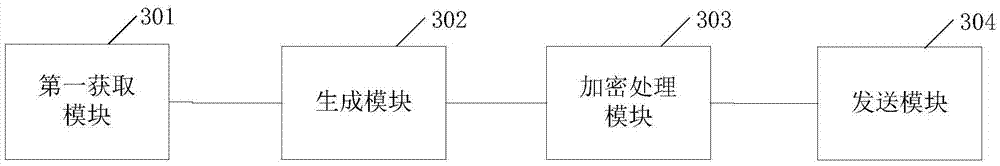
[0094] Embodiment 3 of the present invention discloses a sending terminal, refer to image 3 , the sending terminal includes a first acquiring module 301 , a generating module 302 , an encryption processing module 303 and a sending module 304 .
[0095] The first obtaining module 301 is configured to obtain identification information of a target receiving terminal and pre-stored public key parameters.
[0096] The generation module 302 is configured to use the identification information and the public key parameters to generate the public key of the target receiving terminal.
[0097] The encryption processing module 303 is configured to perform preset encryption processing on the target information based on the public key to obtain encrypted information.
[0098] Wherein, the encryption processing module 303 includes an encryption unit and an encryption identification adding unit.
[0099] An encryption unit, configured to use the public key to encrypt the target informatio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com