End-to-end encrypting method and system based on mobile communication network
A technology of mobile communication network and encryption method, which is applied in the field of end-to-end encryption and encryption system, which can solve the problems of inconvenient use, insecurity, and low security level, and achieve the goals of improving security and safety level, reducing costs, and being convenient to use Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
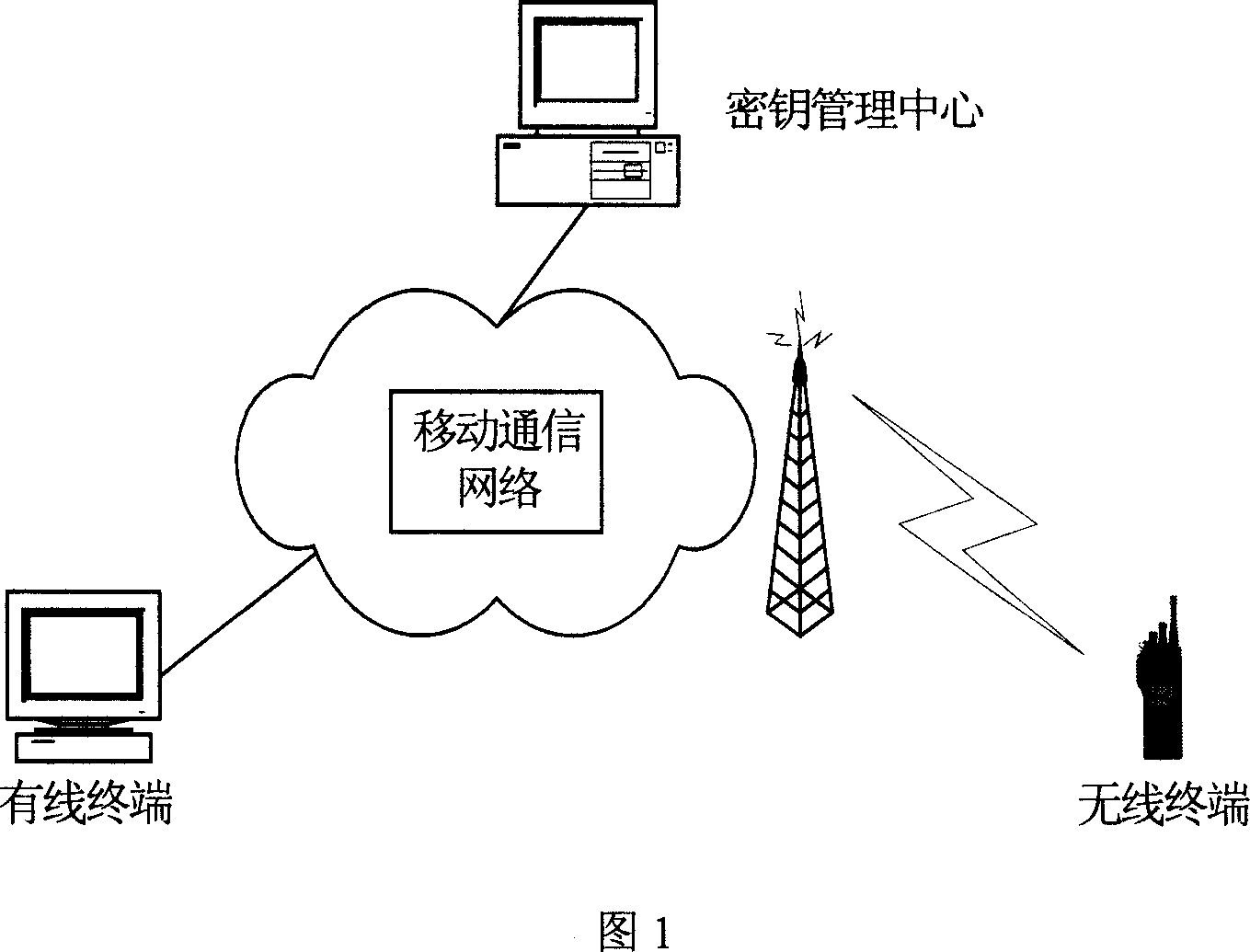
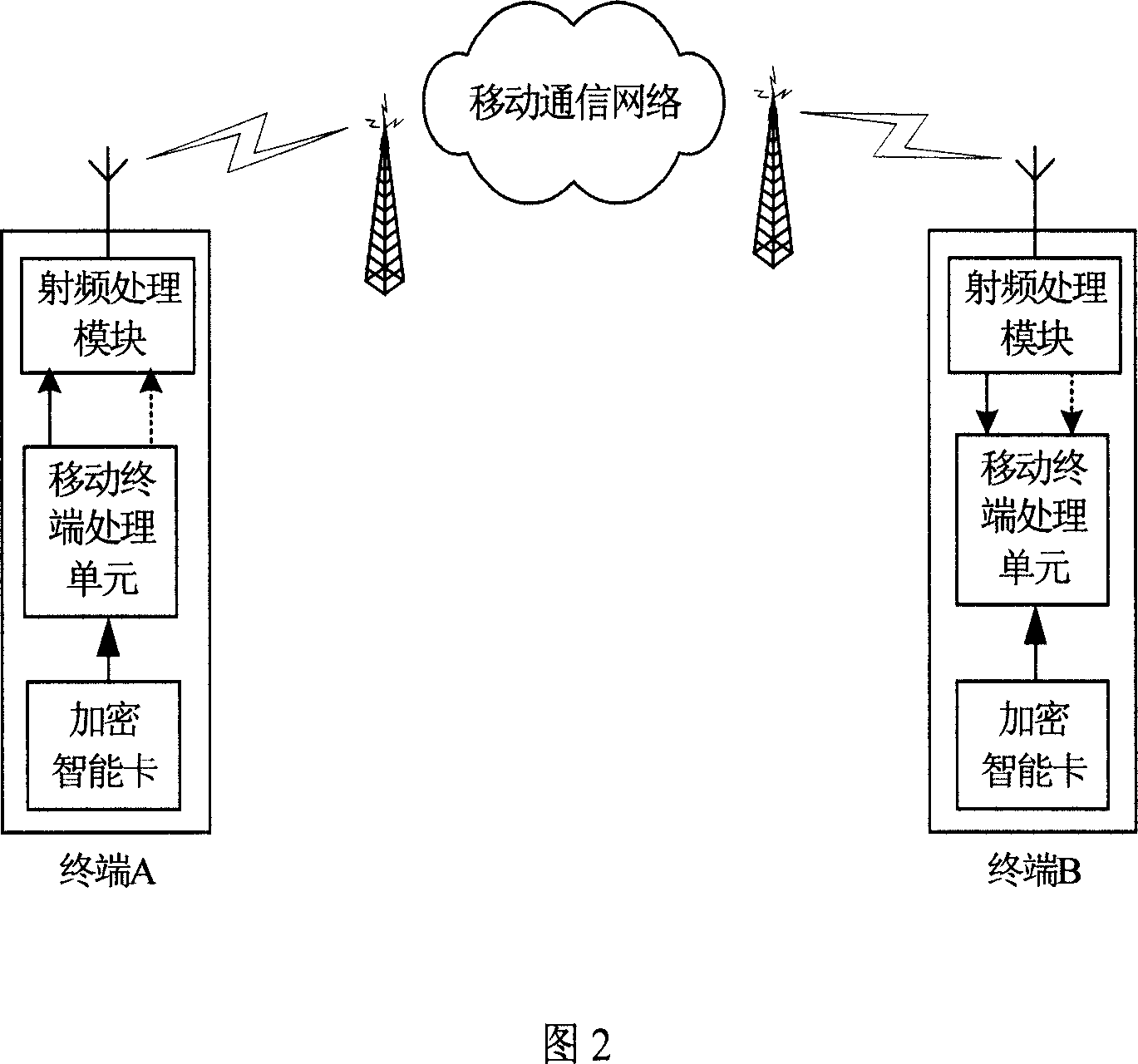
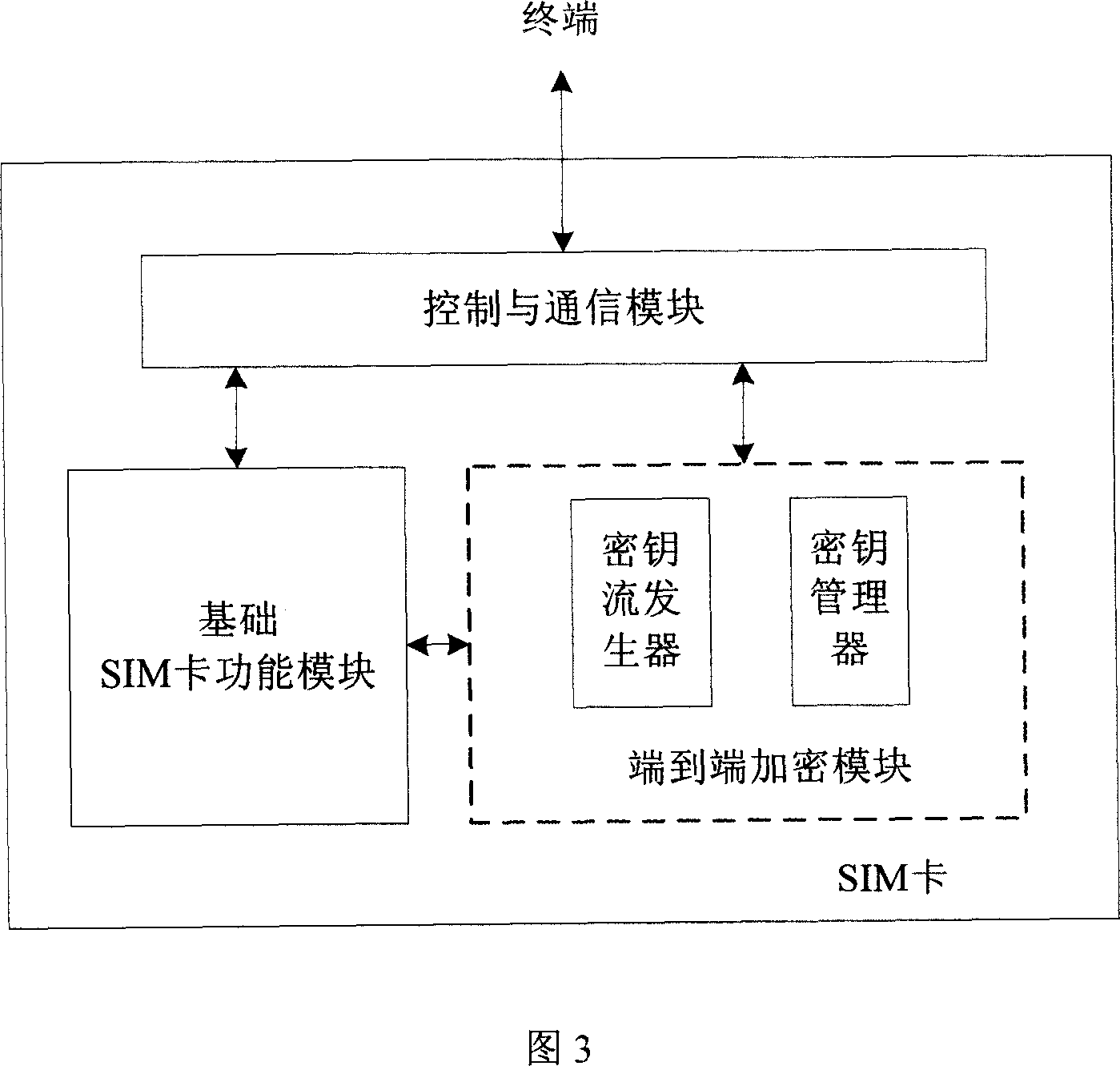
[0012] Referring to Fig. 1-Fig. 3, the present invention provides a kind of end-to-end encryption method based on mobile communication network, and it adopts stream cipher system to carry out end-to-end encryption; Adopt key management center to carry out key management to the whole security system, wherein Including the authentication of encrypted users (terminals), key generation, distribution, update, and key deletion; an encrypted smart card is used as a security module for terminal end-to-end encryption, and the encrypted smart card stores the key held by the terminal and management, generate encryption key stream and / or decryption key stream according to the key distributed by the key management center, and synchronize the encryption and decryption key stream, and obtain the corresponding key from the encrypted smart card by the processing unit of the terminal stream, and perform encryption / decryption operations of plaintext / ciphertext voice or data information.
[0013]...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com