Mobile phone ciphering method based on safe digital interface ciphering card
A secure digital and mobile phone encryption technology, applied in the direction of radio/inductive link selection and arrangement, electrical components, transmission systems, etc., can solve problems such as insufficient encryption strength, single function, and unreliable guarantee of data security, etc., to achieve control The effects of malicious security attacks, simple and convenient system, high encryption strength and reliability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
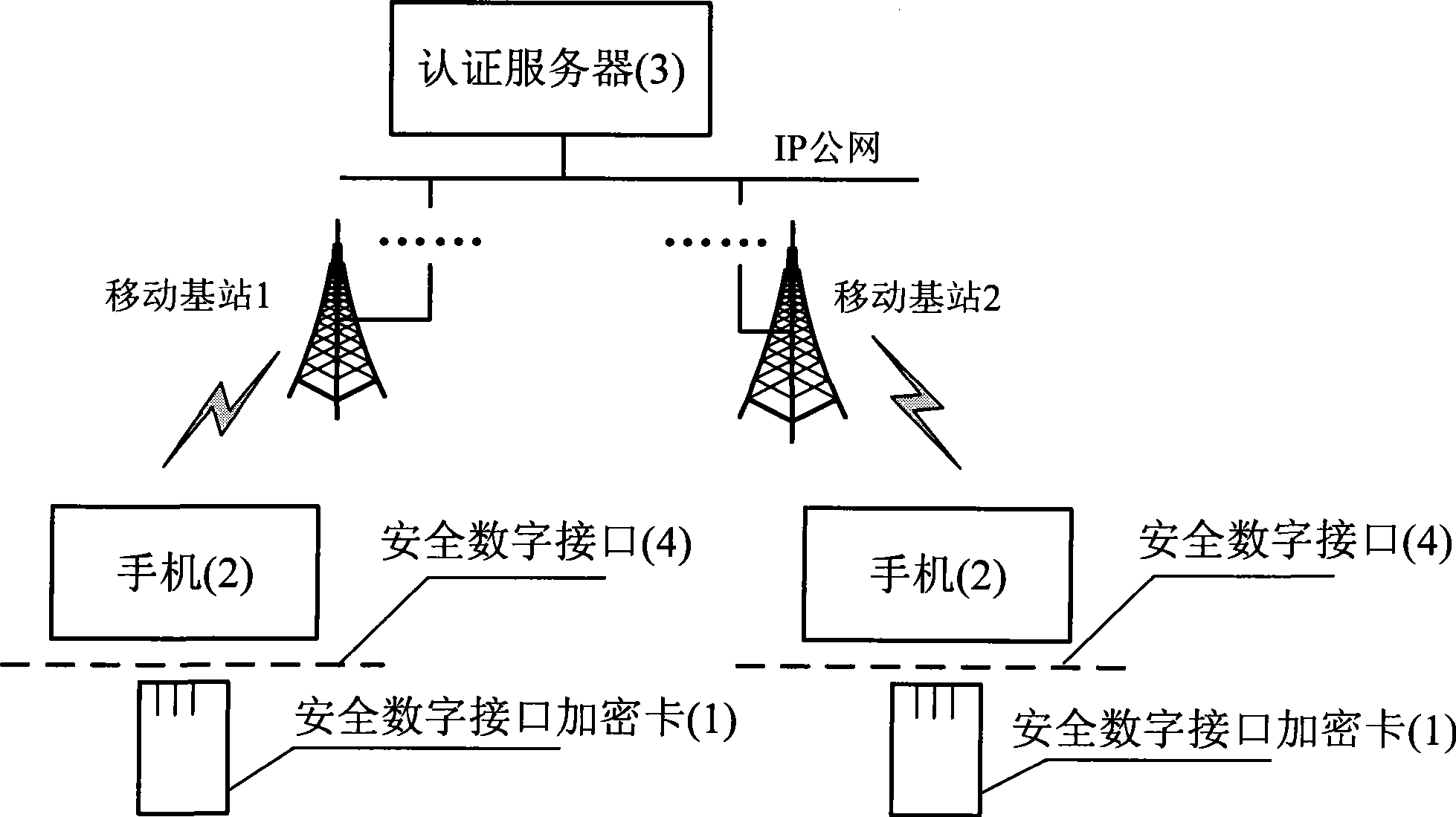
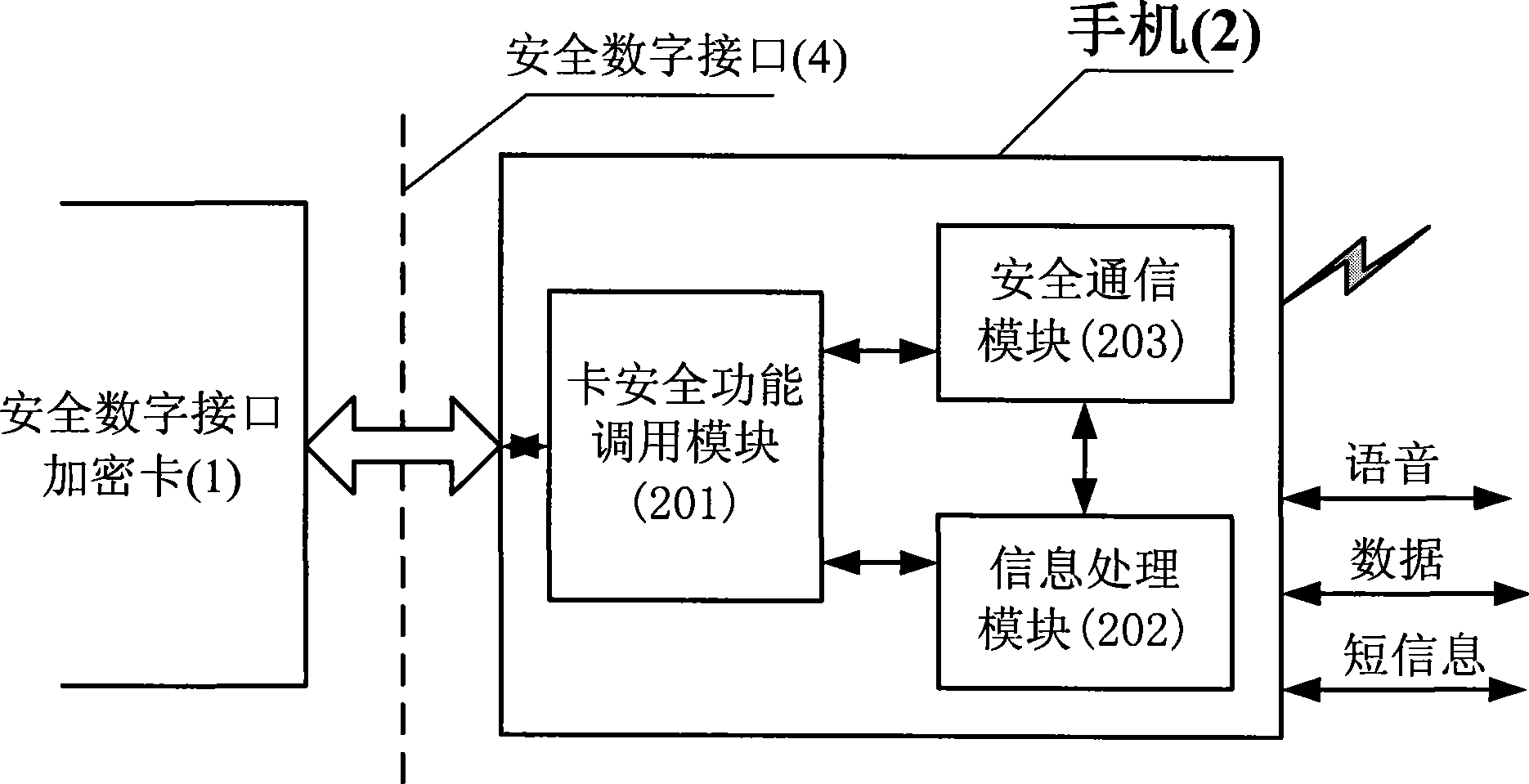
[0029] figure 1 Described is the overall block diagram of the mobile phone encryption method based on the secure digital interface encryption card, which is mainly implemented based on the three security subjects of the secure digital interface encryption card 1, the mobile phone 2 and the authentication server 3. Voice, data and short message data on a mobile phone 2 are encrypted by the secure digital interface encryption card 1, and then transmitted to another mobile phone 2 through the mobile communication network, and the data decryption is also completed by the secure digital interface encryption card 1. The communication between the secure digital interface encryption card 1 and the mobile phone 2 complies with the mechanical characteristics, electrical characteristics and communication protocols of the secure digital interface 4 .
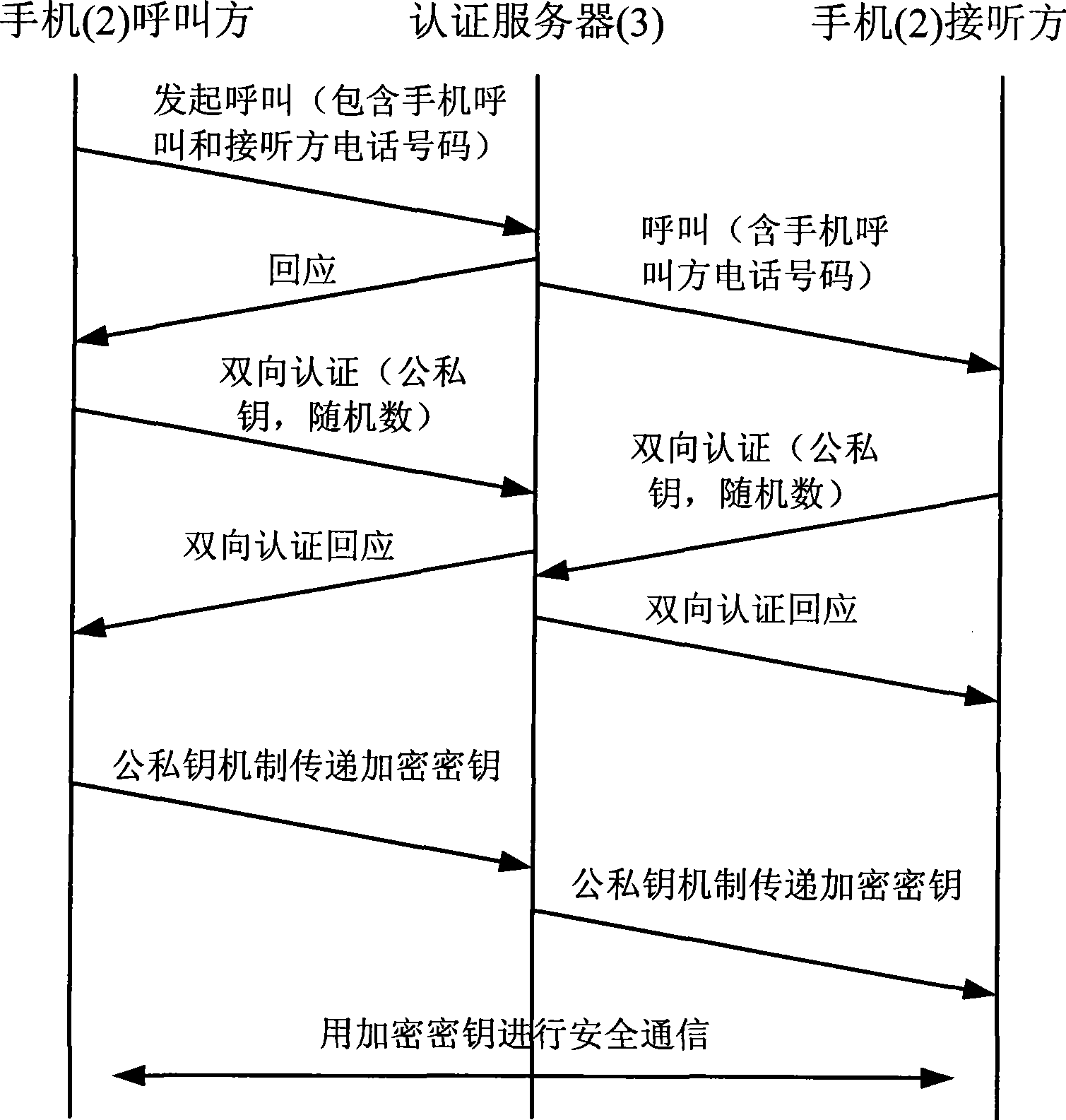
[0030] Before encrypted data transmission, the calling party of mobile phone 2 and the receiving party of mobile phone 2 must complete mut...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com