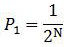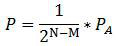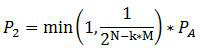A Symmetric Key Distribution Method for Resisting Quantum Attacks
An anti-quantum attack, symmetric key technology, applied in the field of anti-quantum attack symmetric key distribution, can solve the problems of human error, lack of convenience, high price, etc. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
[0029] The symmetric key distribution mechanism proposed in this embodiment involves two kinds of keys. One is the key distributed in the system, which is used to encrypt the application data. One is the key used to encrypt the application key to ensure its transmission security, hereinafter referred to as the root key, its length is denoted as N, and N=256, M=128.
[0030] Before the key distribution process is started, the key service terminal must have shared at least one root key with the key management server, denoted as KR1, and then start the key distribution process:
[0031] (1) The key management server generates a random number of length N through the random number generator to update KR1, which is recorded as KR2; at the same time, the key management server generates k random numbers of length M through the random number generator, Used as an application key, denoted as KA, and k is greater than or equal to 1, the random number generator can be in the form of hardw...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com