Andriod system-oriented implement method of mobile secure terminal
An implementation method and terminal technology, applied in the field of information security, can solve problems such as no key negotiation and no patent formation, and achieve the effects of friendly user interface, low cost, and easy implementation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
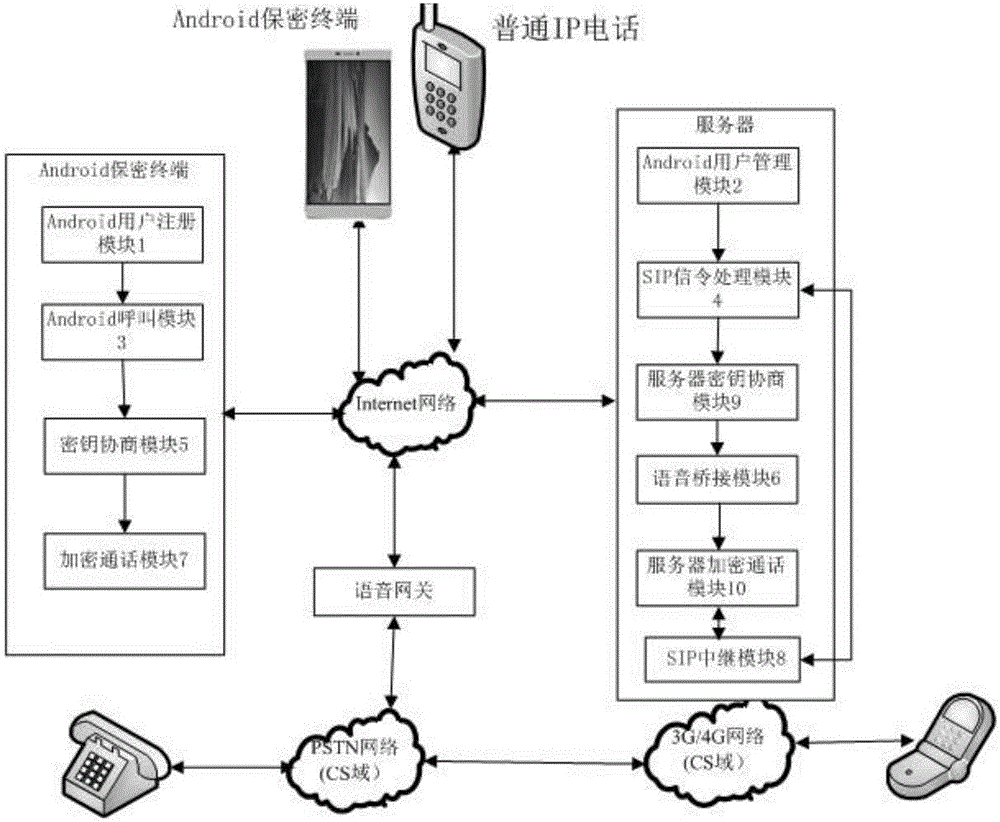
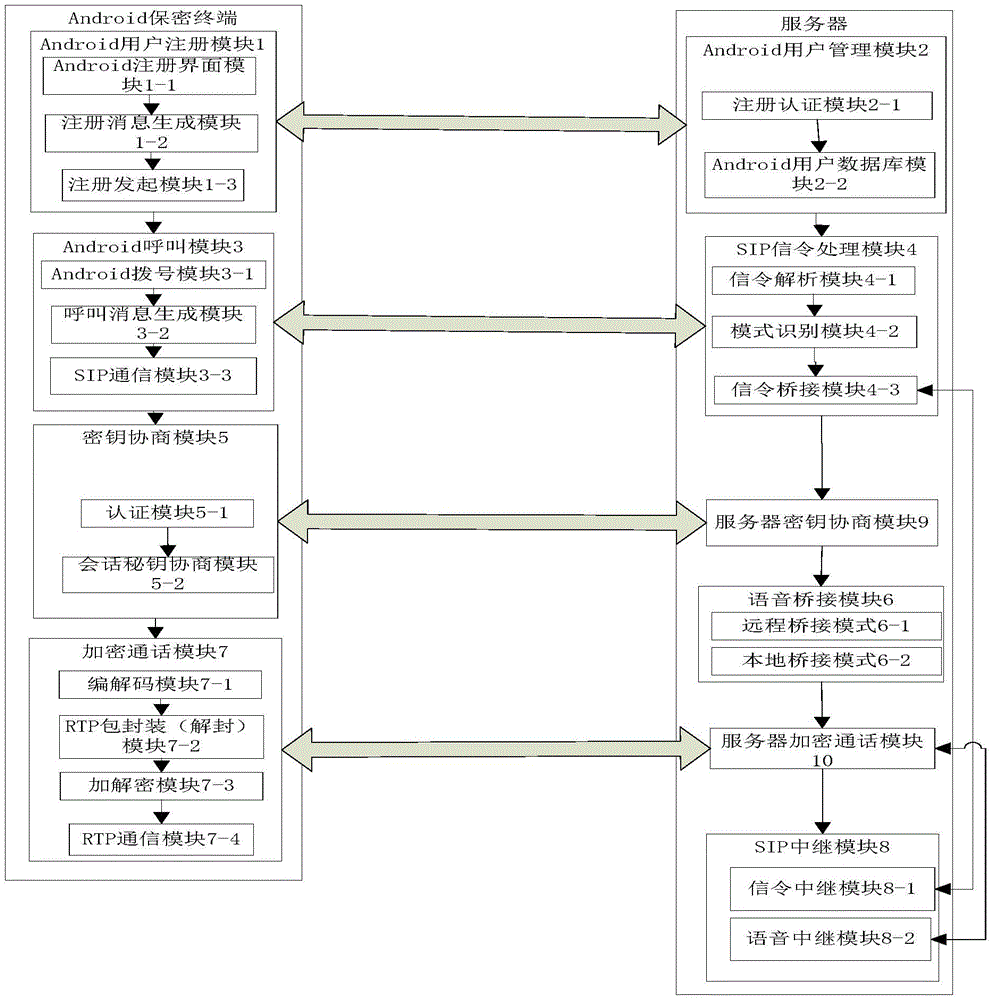
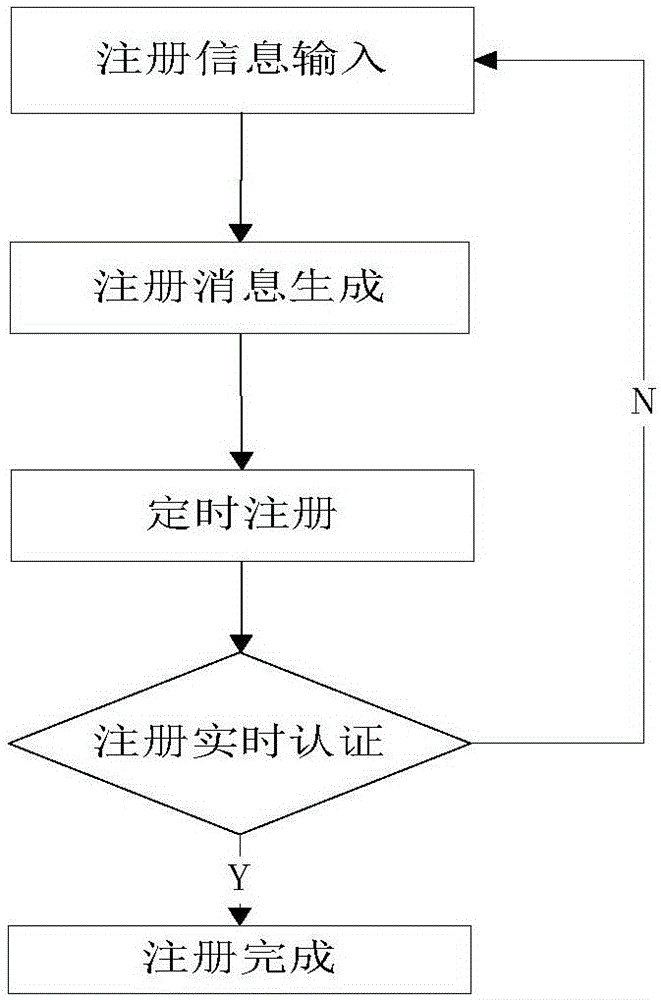
[0036] Such as figure 1 Shown, the structural diagram of the present invention, a kind of implementation method of mobile security terminal facing Android system mainly includes Android user registration module 1, Android user management module 2, Android calling module 3, SIP signaling processing module 4, key Negotiation module 5 , voice bridging module 6 , encrypted call module 7 , SIP relay module 8 , server key negotiation module 9 and server encrypted call module 10 . The security terminal can support two encrypted communication modes: first, when both parties in the call are Android security terminals, it can realize end-to-end encrypted voice communication for Android operating system mobile terminals, that is, end-to-end encrypted communication mode ; Second, when only one of the two parties in the call is a confidential terminal, it can realize the encrypted voice communication between the Android operating system mobile terminal and the server, that is, the half-way...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com