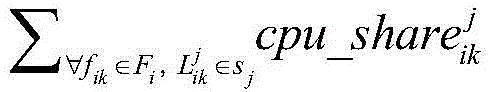Patents
Literature
430 results about "Inter-server" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computer network protocol design, inter-server communication is an extension of the client–server model in which data are exchanged directly between servers. In some fields server-to-server (S2S) is used as an alternative, and the term inter-domain can in some cases be used interchangeably.
Inter-server communication using request with encrypted parameter
InactiveUS6970849B1Preventing unchecked proliferationDigital data processing detailsUser identity/authority verificationUniform resource locatorBiological activation
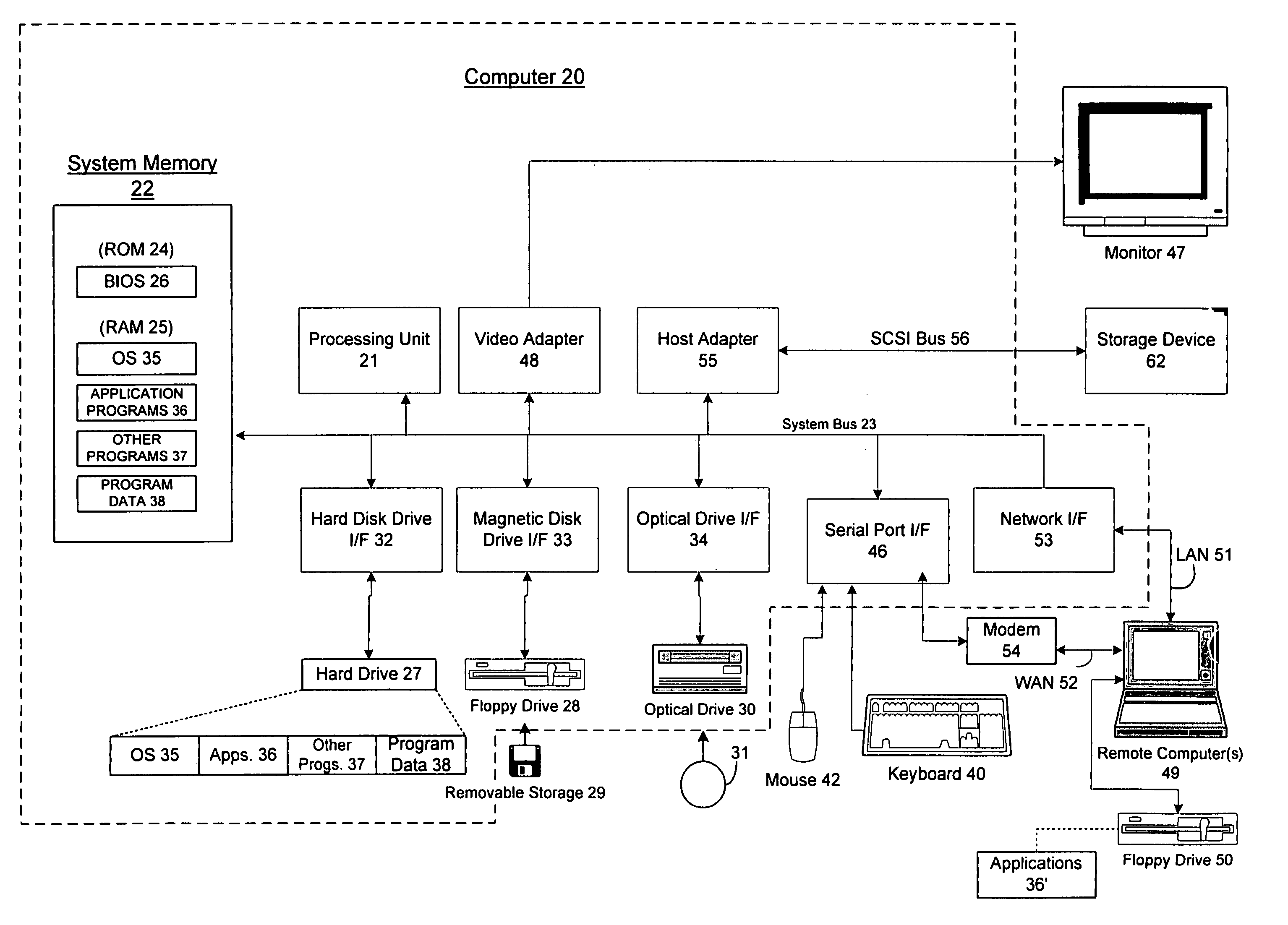
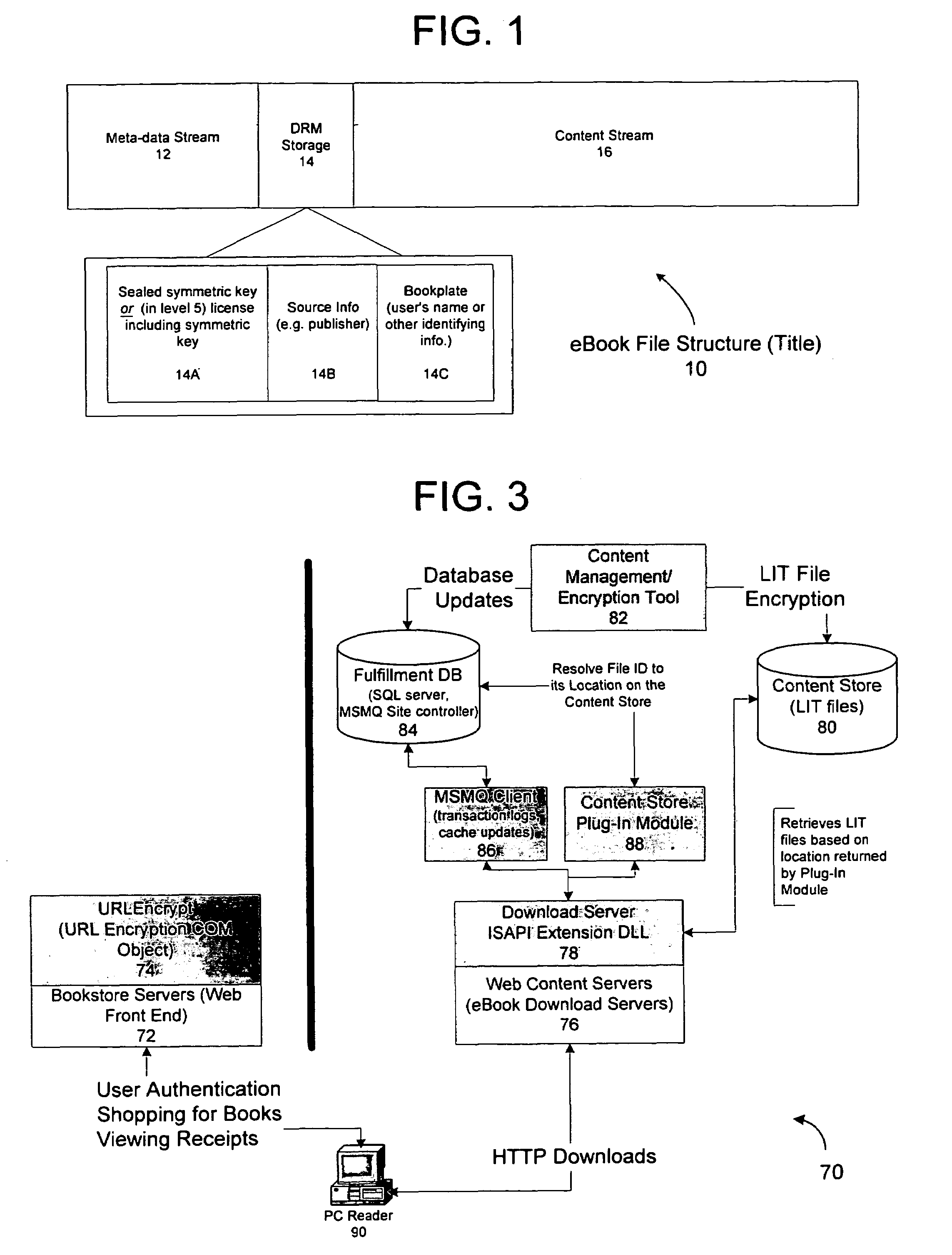
A server architecture for a digital rights management system that distributes and protects rights in content. The server architecture includes a retail site which sells content items to consumers, a fulfillment site which provides to consumers the content items sold by the retail site, and an activation site which enables consumer reading devices to use content items having an enhanced level of copy protection. Each retail site is equipped with a URL encryption object, which encrypts, according to a secret symmetric key shared between the retail site and the fulfillment site, information that is needed by the fulfillment site to process an order for content sold by the retail site. Upon selling a content item, the retail site transmits to the purchaser a web page having a link to a URL comprising the address of the fulfillment site and a parameter having the encrypted information. Upon following the link, the fulfillment site downloads the ordered content to the consumer, preparing the content if necessary in accordance with the type of security to be carried with the content. The fulfillment site includes an asynchronous fulfillment pipeline which logs information about processed transactions using a store-and-forward messaging service. The fulfillment site may be implemented as several server devices, each having a cache which stores frequently downloaded content items, in which case the asynchronous fulfillment pipeline may also be used to invalidate the cache if a change is made at one server that affects the cached content items. An activation site provides an activation certificate and a secure repository executable to consumer content-rendering devices which enables those content rendering devices to render content having an enhanced level of copy-resistance. The activation site “activates” client-reading devices in a way that binds them to a persona, and limits the number of devices that may be activated for a particular persona, or the rate at which such devices may be activated for a particular persona.
Owner:MICROSOFT TECH LICENSING LLC
Internet of Vehicles safety communication method, vehicle-mounted terminal, server and system
ActiveCN106453269AImprove securityKey distribution for secure communicationEncryption apparatus with shift registers/memoriesTransmission protocolThe Internet
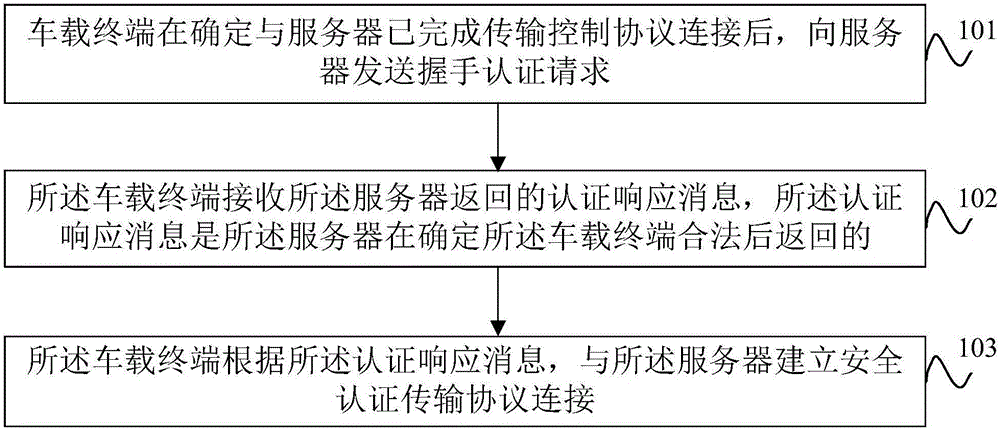
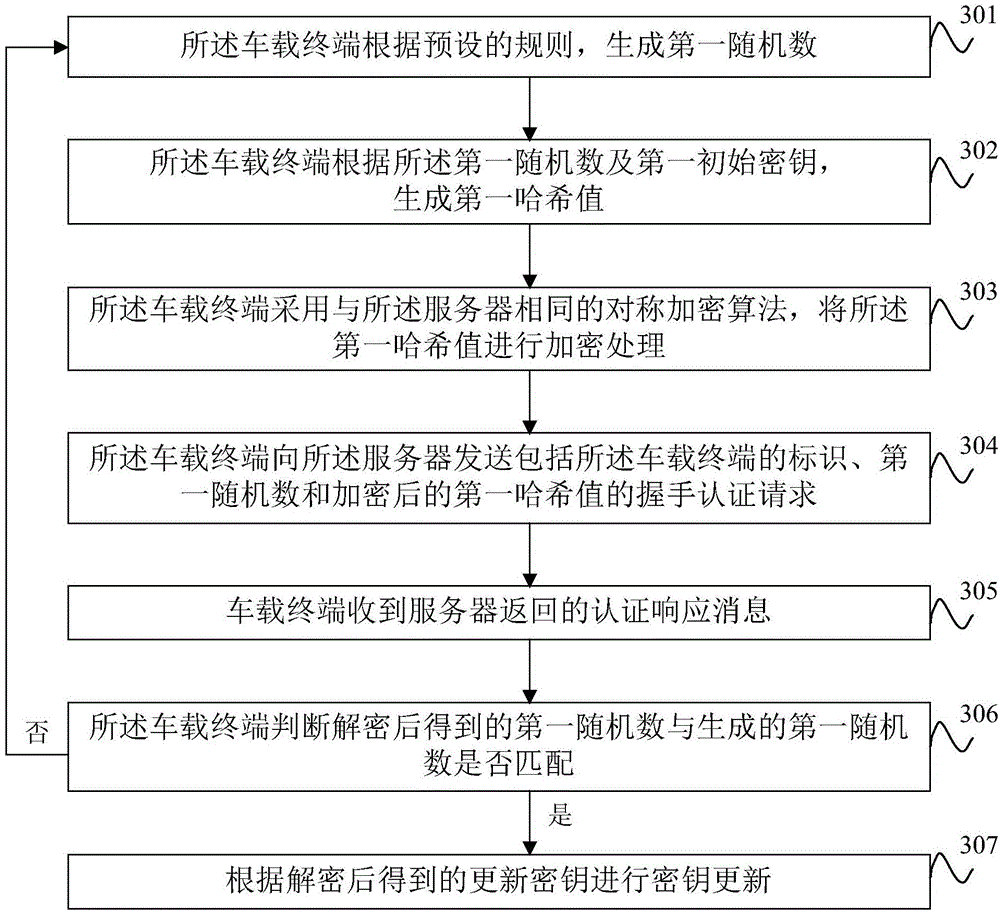
The application provides an Internet of Vehicles safety communication method, a vehicle-mounted terminal, a server and a system. The Internet of Vehicles safety communication method is characterized by comprising the following steps: the vehicle-mounted terminal sends a handshake authentication request to a server after determining that the transmission control protocol connection with the server has been finished, wherein the handshake authentication request comprises an identifier of the vehicle-mounted terminal and a first Hash value encrypted by use of a symmetrical encryption algorithm same as that adopted by the server; the vehicle-mounted terminal receives an authentication response message returned by the server, wherein the authentication response message is returned by the server after determining that the vehicle-mounted terminal is legal; and the vehicle-mounted terminal establishes a safety authentication transmission protocol connection with the server according to the authentication response message. A lightweight safety authentication transmission protocol is established between the vehicle-mounted terminal and the server by use of less resource, and the security of the data transmission between the vehicle-mounted terminal and the server is improved.
Owner:NEUSOFT CORP
Method, device and system of test application program interface
InactiveCN103136095AReduce workloadImprove accuracySoftware testing/debuggingTransmissionHuman–machine interfaceWorkload
The invention discloses a method, a device and a system of a test application program interface, wherein the method of the test application program interface is used in an application program interface arranged on a server by a client test and comprises the following steps: S1, receiving parameter information and assertion of the application program interface through a human-computer interface of a client, S2, according to a communication protocol between the client and the server, packaging the parameter information to be interface test data which confirm to the communication protocol and sending the interface test data to the server, S3, receiving return data processed by the server, and S4, analyzing the return data through the assertion and displaying a test result through the human-computer interface. According to the method, the device and the system of the test application program interface, a tester needs not to write a test code, the test data are input through a page table and the test result can be displayed through the page table directly, and workload of the tester is lightened and accuracy is improved.
Owner:ALIBABA GRP HLDG LTD
Method for integrated load balancing among peer servers
ActiveUS7284067B2Digital computer detailsMultiprogramming arrangementsBalancing networkInternet traffic
A system for balancing network loads among a group of computer servers. A load balancing module is provided for each server and includes multiple network ports for receiving network traffic and coupling messages to its server or to another module. The interconnect map for the modules is automatically determined by a topology discovery system and maintained by a topology update system. Each module monitors the loading and health of its server and provides this information to the other modules. One or more master modules are directly connected to an external network and route received traffic to their own servers and other servers through other modules or a networking switch based on a priority system. The priority system may be based on dynamic conditions of server capacities and current loading.
Owner:VALTRUS INNOVATIONS LTD +1
Data resource security control method in thin client mode
ActiveCN103441986AEfficient identificationEnsure authenticityDigital data protectionTransmissionThin clientServer-side
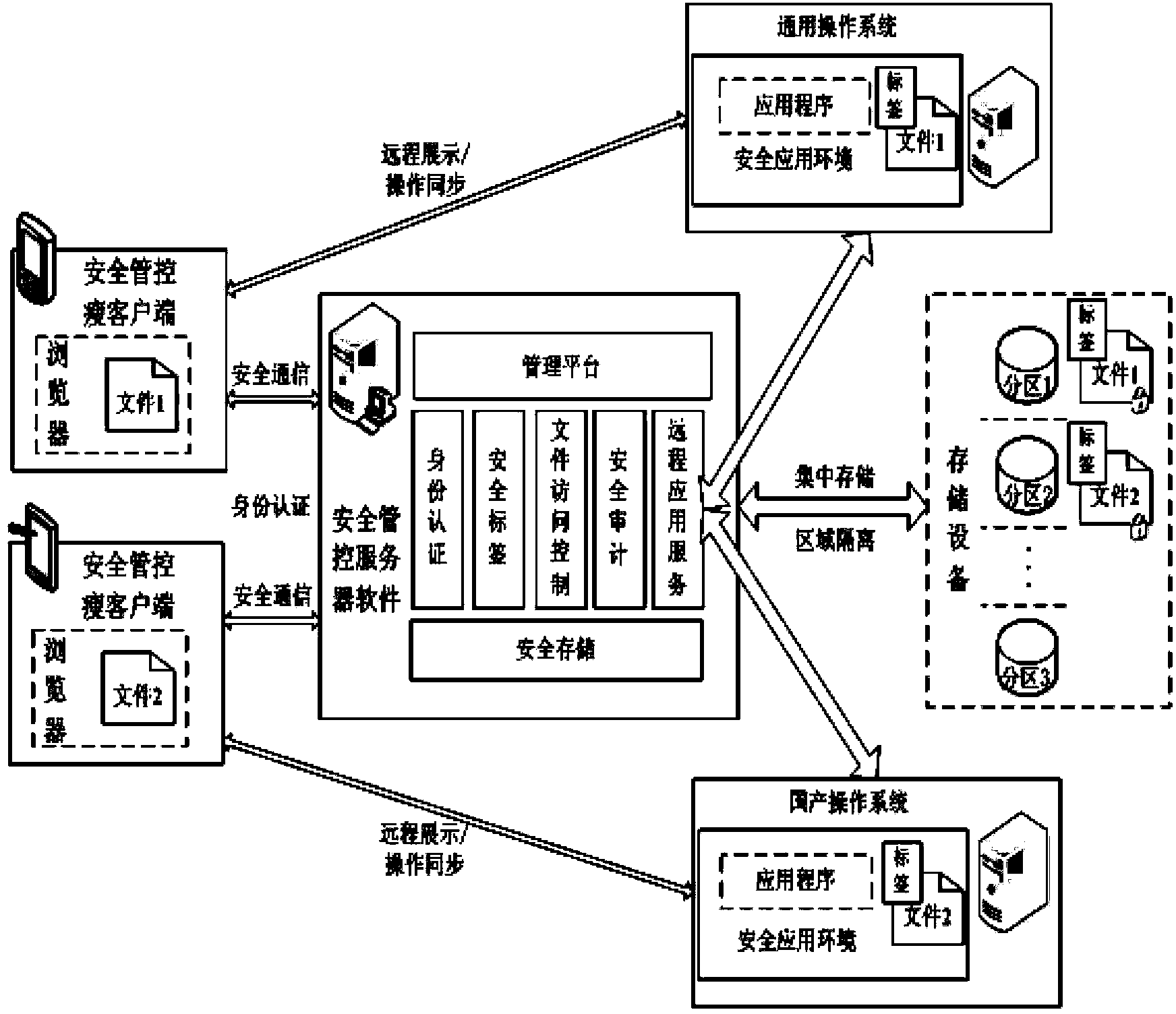
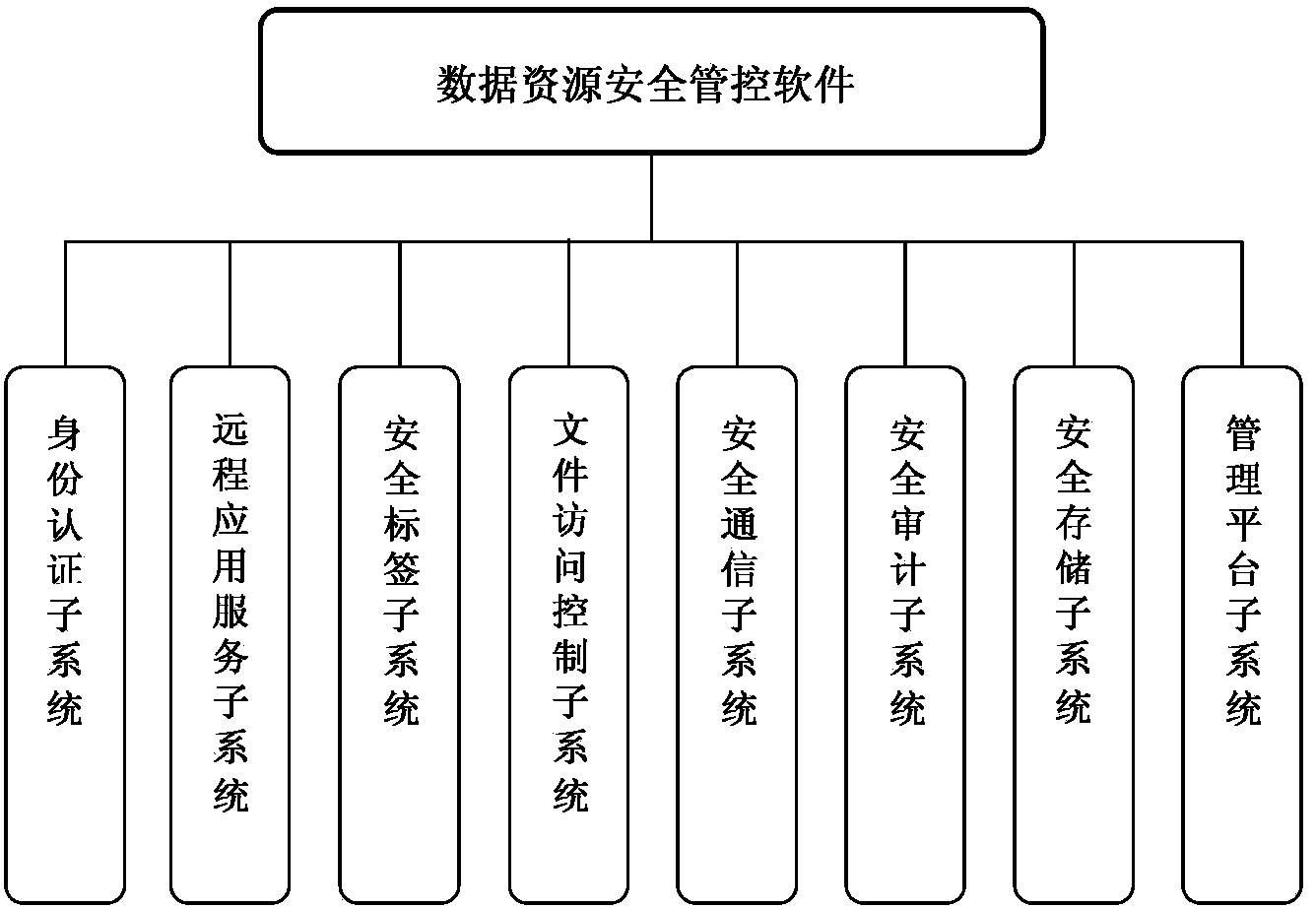
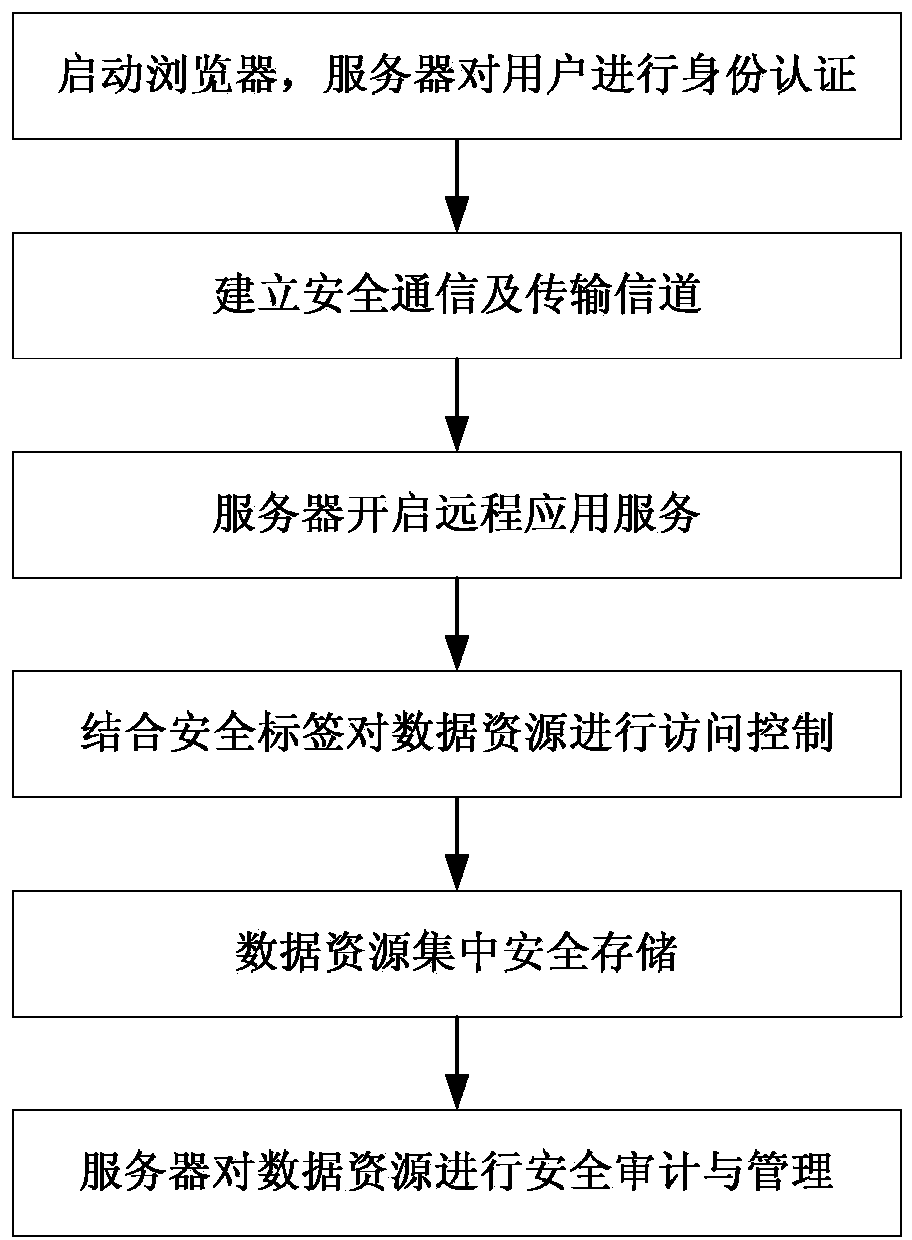
The invention belongs to the field of network security, and particularly relates to a data resource security control method in a thin client mode. The data resource security control method in the thin client mode comprises eight subsystems, namely the identity authentication subsystem, the remote application service subsystem, the security label subsystem, the file access control subsystem, the security communication subsystem, the security audit subsystem, the security storage subsystem and the management platform subsystem. Storage and control of files are mainly performed on a background server, the files are stored in different partitions according to user types or security levels of the files, the files are stored and protected, and a server side can not recognize the content of the files. When a user needs to have access to and process the files, the user logs in on a browser, identity authentication is conducted between the user and a server, and then file access connection is established. The files of a thin client are processed on the server side (provided by a physical application server or a virtual application server), no application or agent needs to be installed on the thin client, and interface interoperability is supported by related services released by remote application services.
Owner:706 INST SECOND RES INST OF CHINAAEROSPACE SCI & IND
Dynamic optimization of simulation resources
ActiveUS20180048532A1Easy to changeOptimize timingError detection/correctionProgram controlDynamical optimizationResource utilization
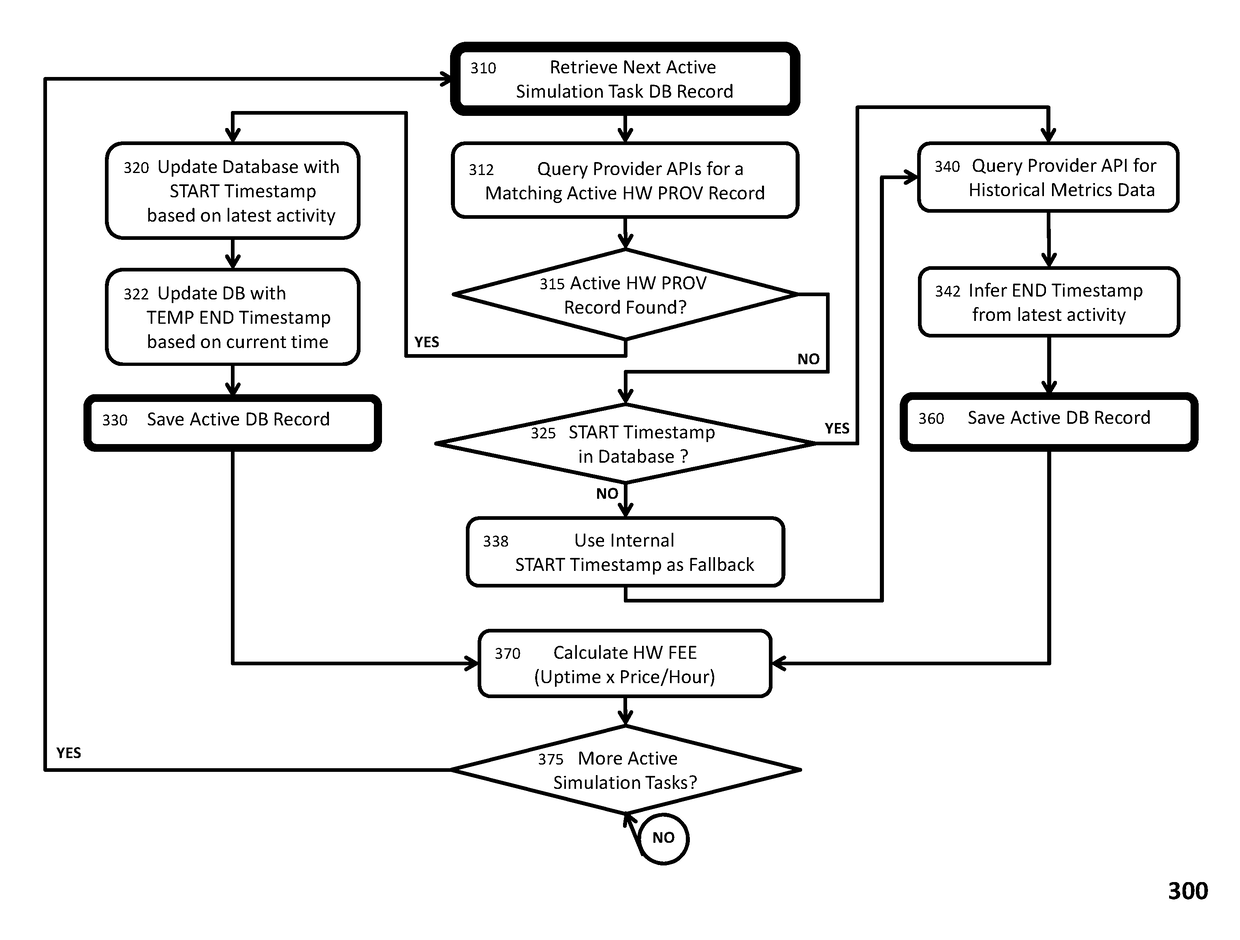
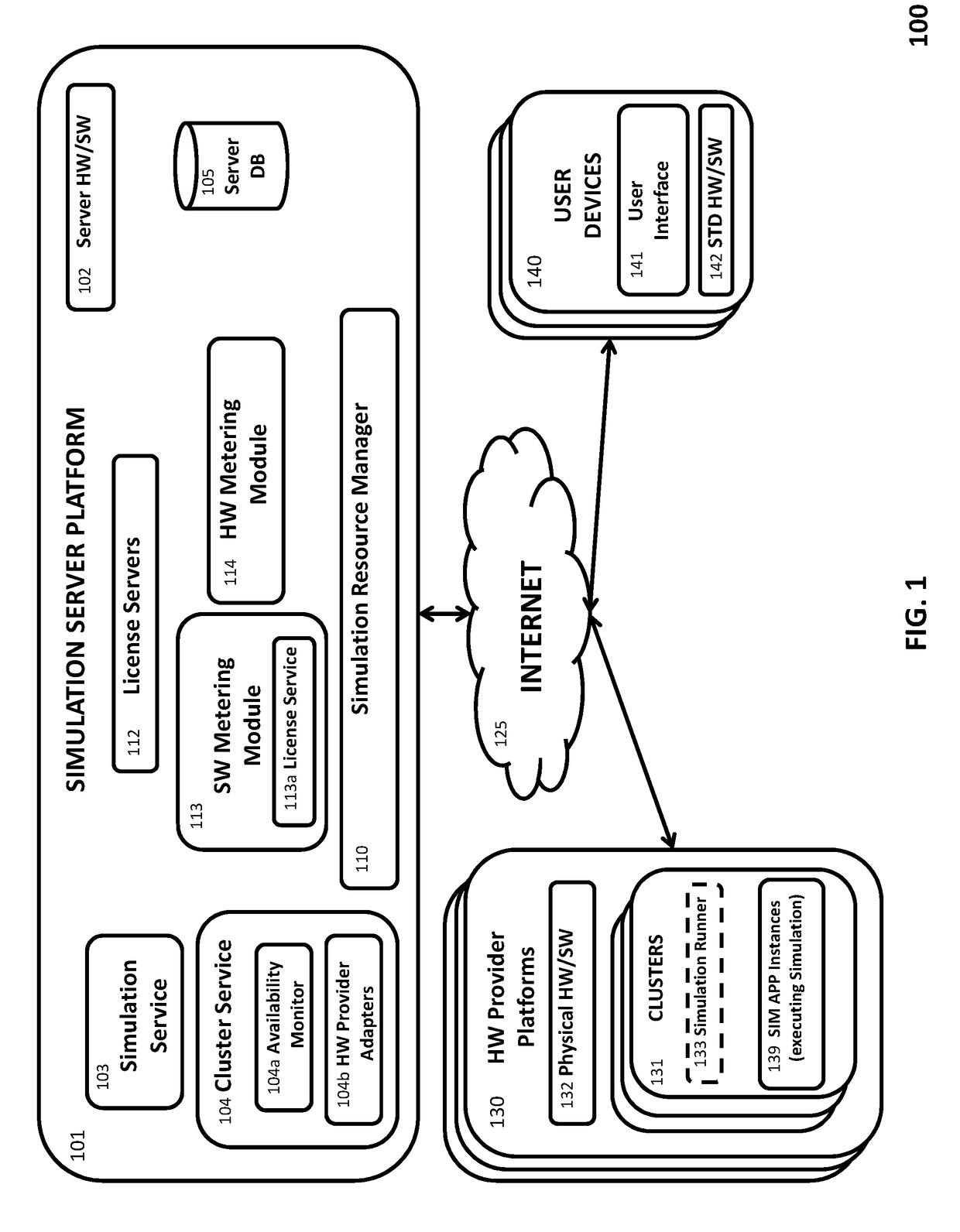
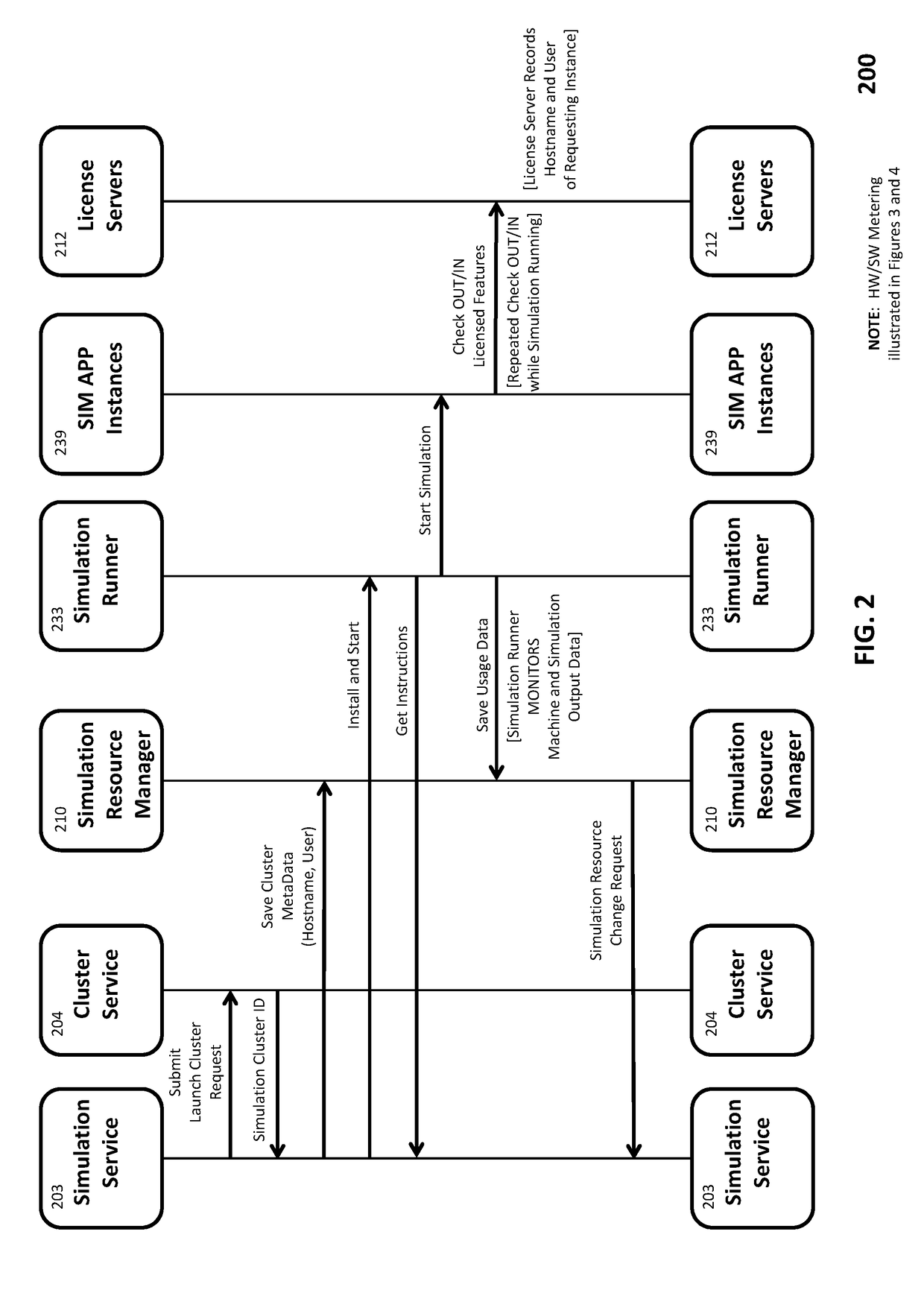
The present invention dynamically optimizes computing resources allocated to a simulation task while it is running. It satisfies application-imposed constraints and enables the simulation application performing the simulation task to resolve inter-instance (including inter-server) dependencies inherent in executing the simulation task in a parallel processing or other HPC environment. An intermediary server platform, between the user of the simulation task and the hardware providers on which the simulation task is executed, includes a cluster service that provisions computing resources on hardware provider platforms, an application service that configures the simulation application in accordance with application-imposed constraints, an application monitoring service that monitors execution of the simulation task for computing resource change indicators (including computing resource utilization and application-specific information extracted from output files generated by the simulation application) as well as restart files, and a computing resource evaluation engine that determines when a change in computing resources is warranted.
Owner:RESCALE INC
A method to realize cluster server inner load sharing agent
InactiveCN101217483AEnhance external stabilityEnsure consistencyData switching by path configurationMultiple digital computer combinationsClient-sideProxy server
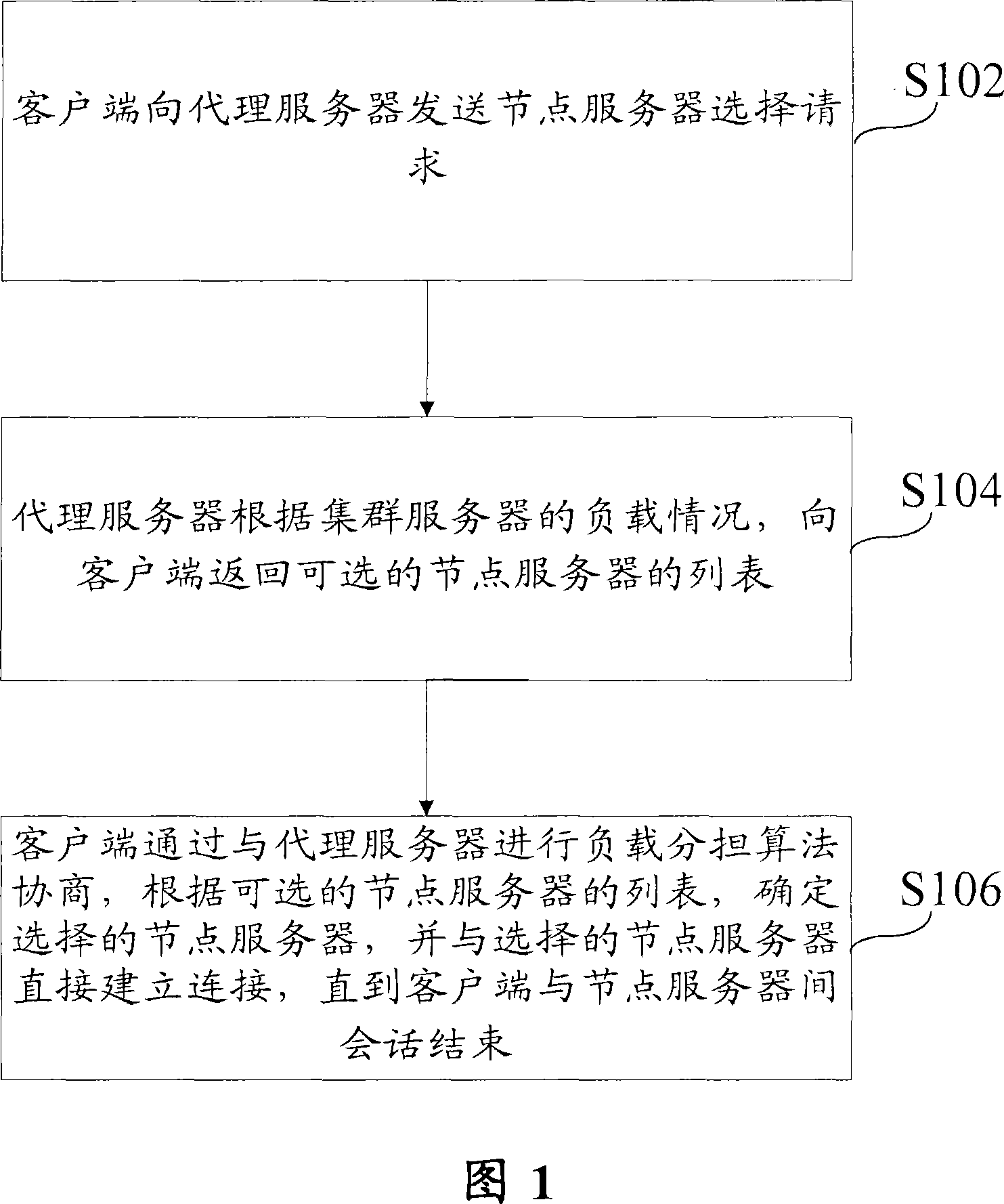
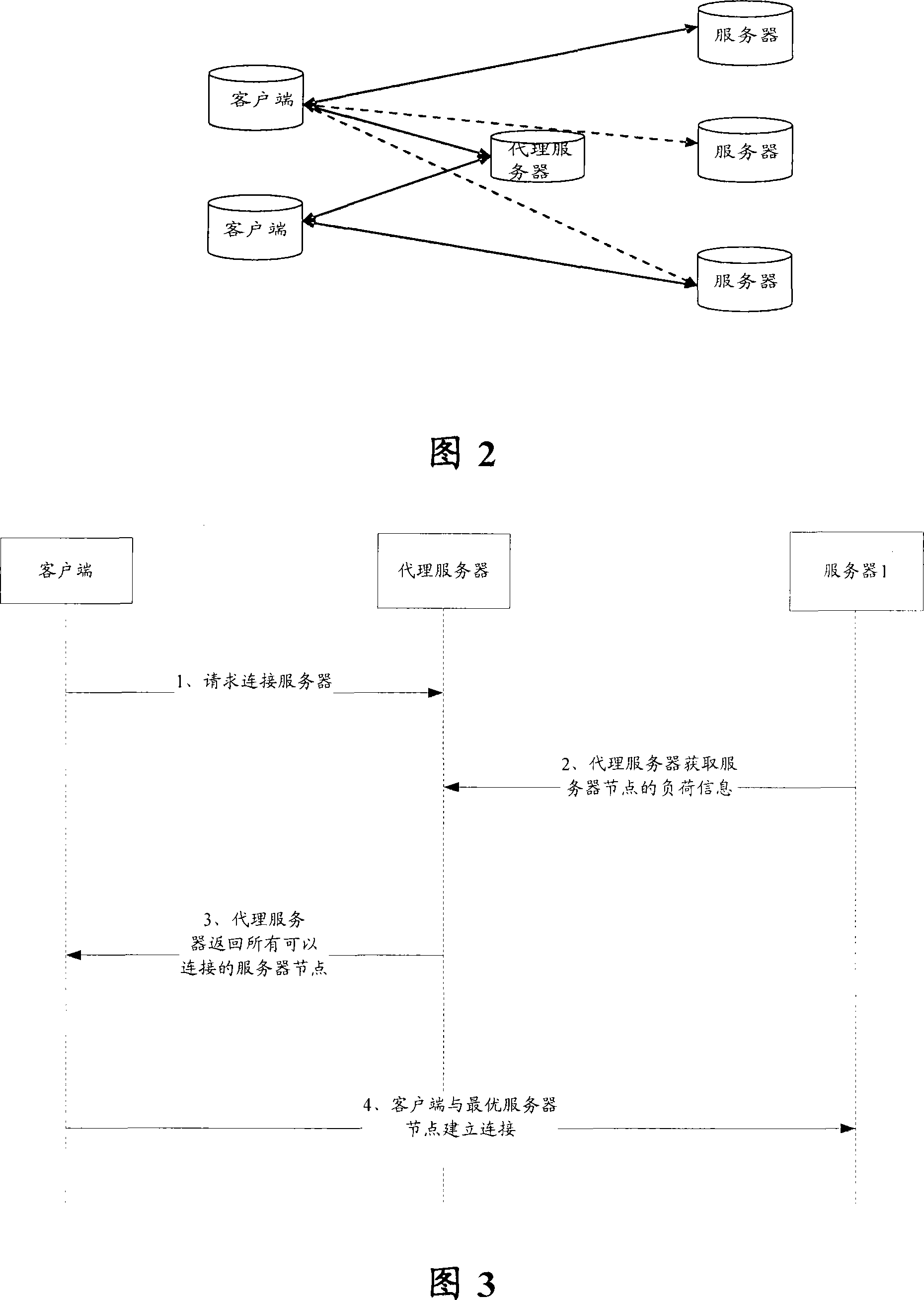
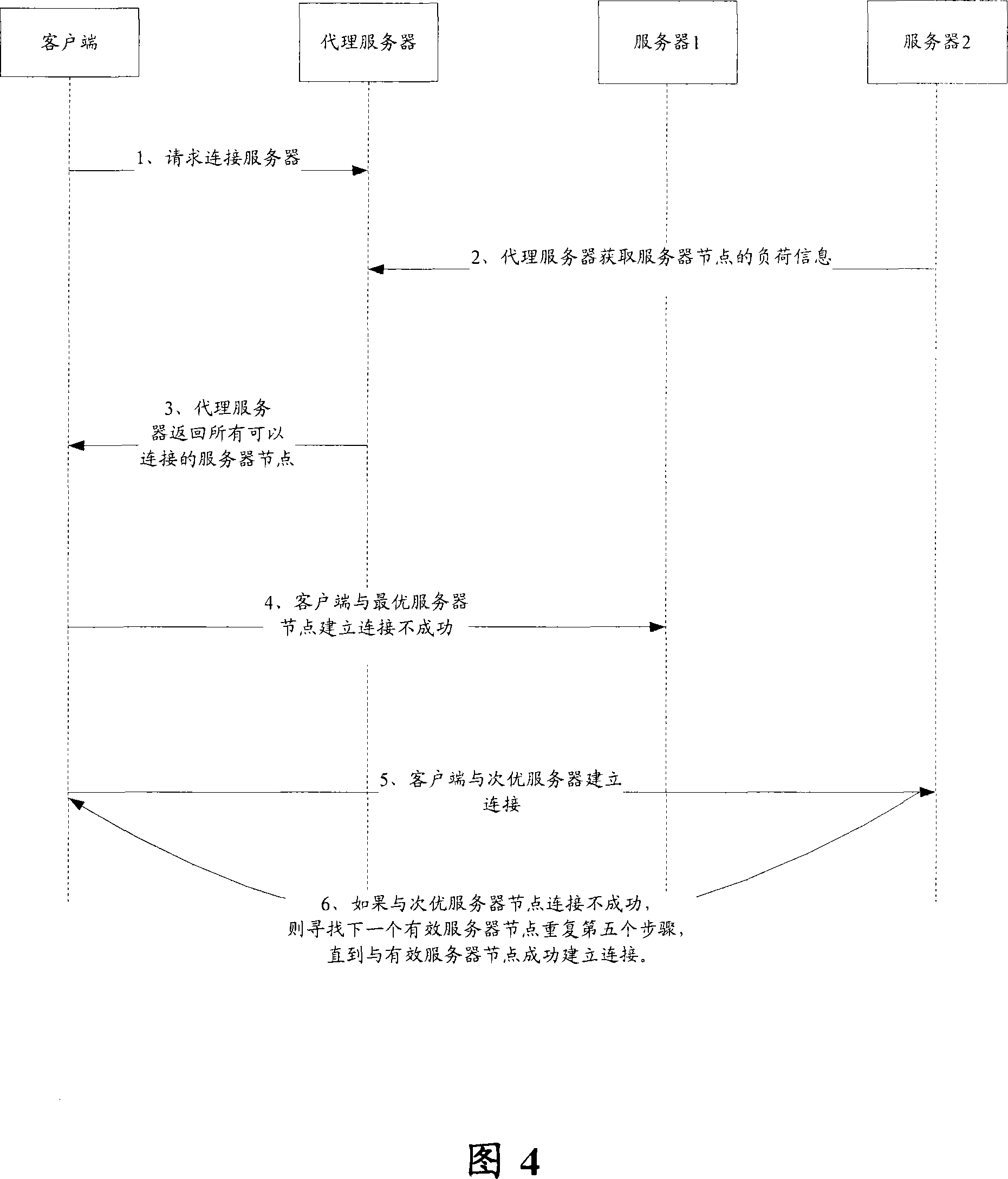
The invention discloses a method for realizing the loading sharing agent in a cluster server, comprising the following steps: a client sends a node server selecting request to a agent server; the agent server returns a list of selectable node servers to the client according to the loading situation of the cluster server; according to the list of selectable node servers, the client determines the selected node server and establishes connection directly with the selected node server by negotiating the loading sharing algorithm with the agent server until the conversation between the client and the node server is ended. As adopting the loading sharing agent method that the client is provided with the optimal server node and the suboptimal server node, the invention strengthens the external stability of the cluster server. Furthermore, the agent server does not retransmit the application data between the client and the server; therefore, the agent server is not easy to cause the network bottleneck.
Owner:ZTE CORP
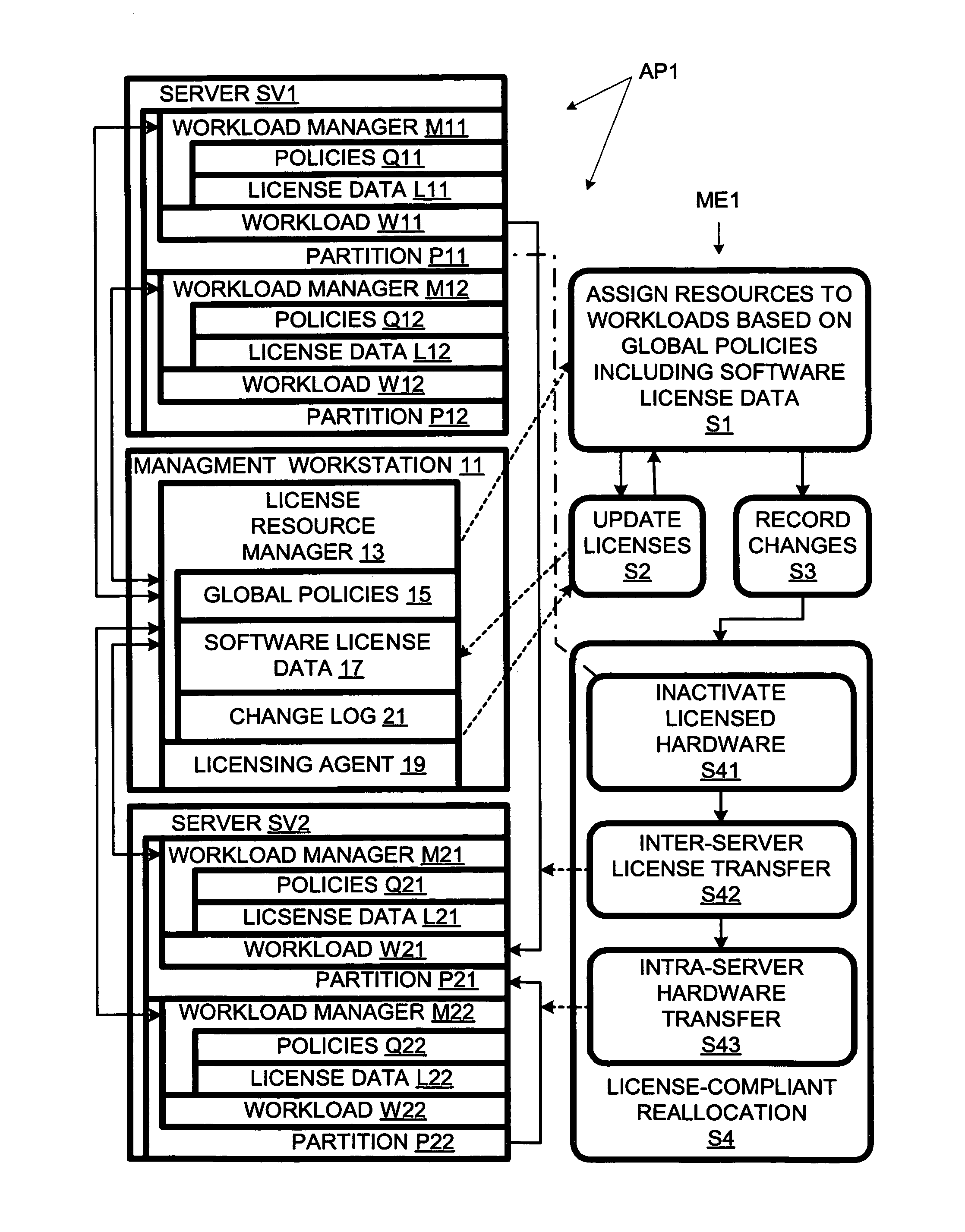
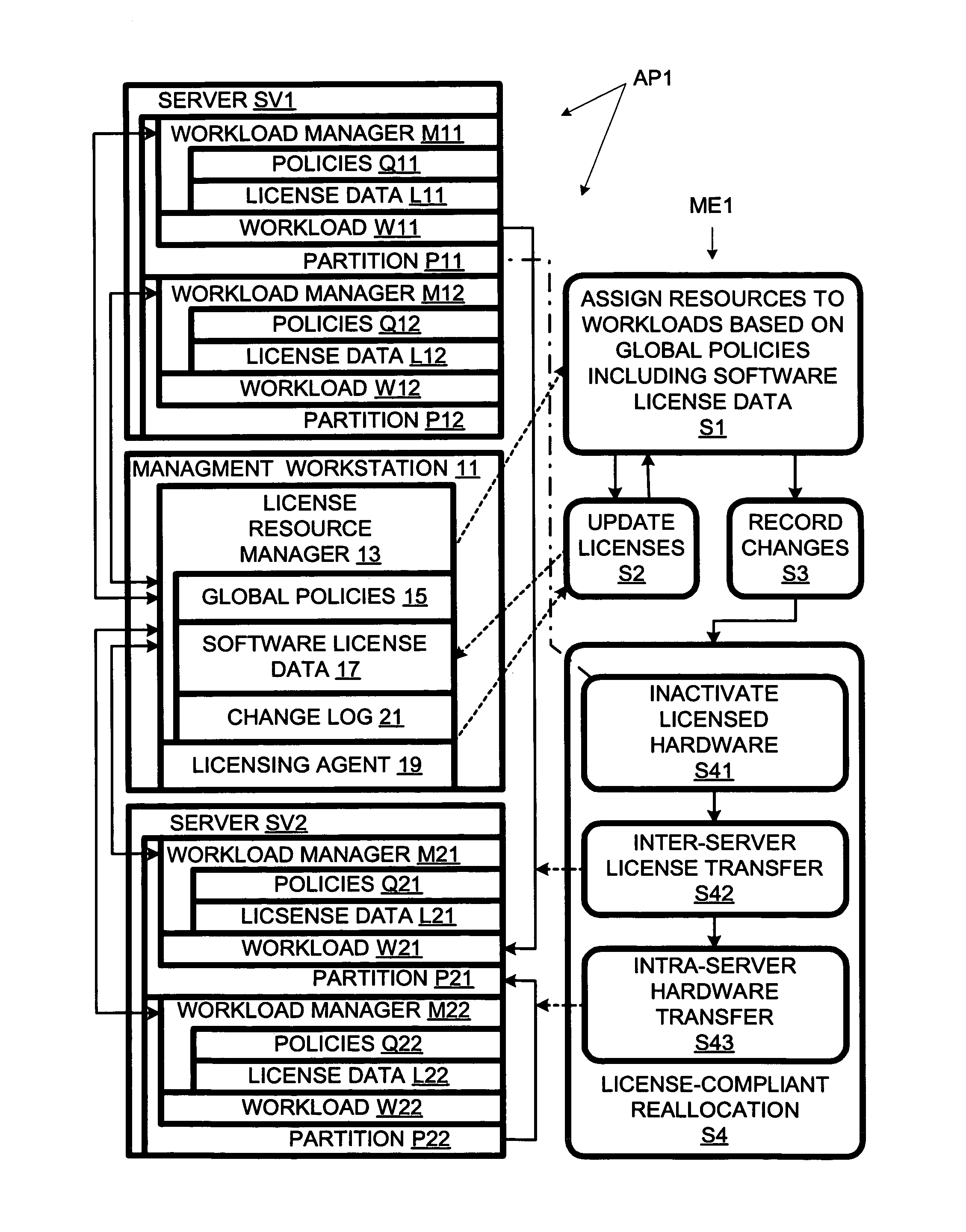
Workload reallocation involving inter-server transfer of software license rights and intra-server transfer of hardware resources
ActiveUS8650296B1Minimizing expenseLower requirementDigital computer detailsComputer security arrangementsSoftware licenseWorkload
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP +1
Application virtualization security communication method in autonomous and controllable environment
ActiveCN109347809AKey distribution for secure communicationUser identity/authority verificationVirtualizationNetwork connection
The invention relates to an application virtualization security communication method in an autonomous and controllable environment, and relates to the technical field of network security. The invention expands a security socket layer based on the domestic commercial cipher suite based on the RDP protocol by reconstructing the original RDP protocol stack, and adds the security socket layer to the network connection layer of the protocol stack, which can provide a secure transmission service for the client to the server, thereby realizing the dual identity authentication between the client and the server, and completing the identity verification of the client to the server.
Owner:BEIJING INST OF COMP TECH & APPL
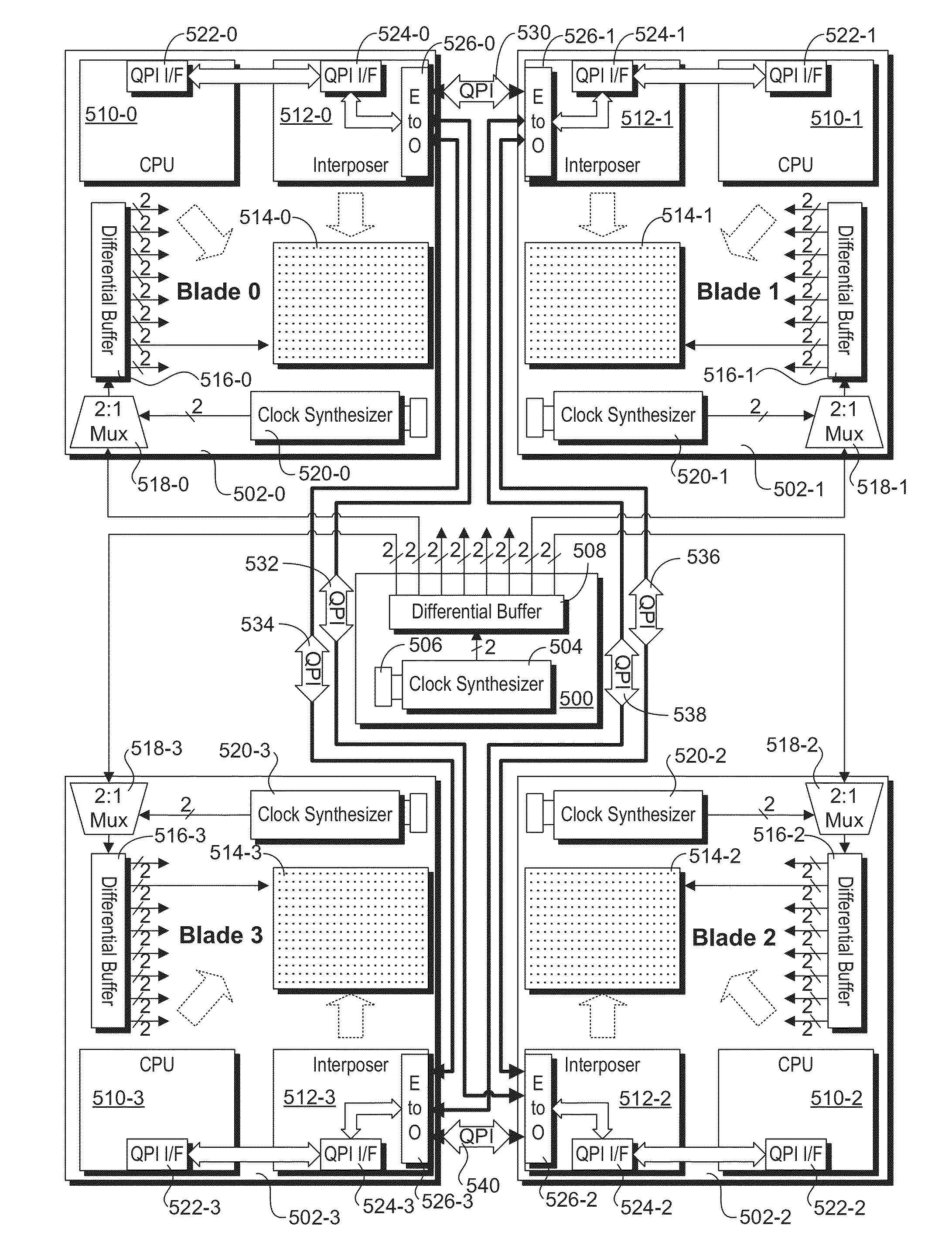
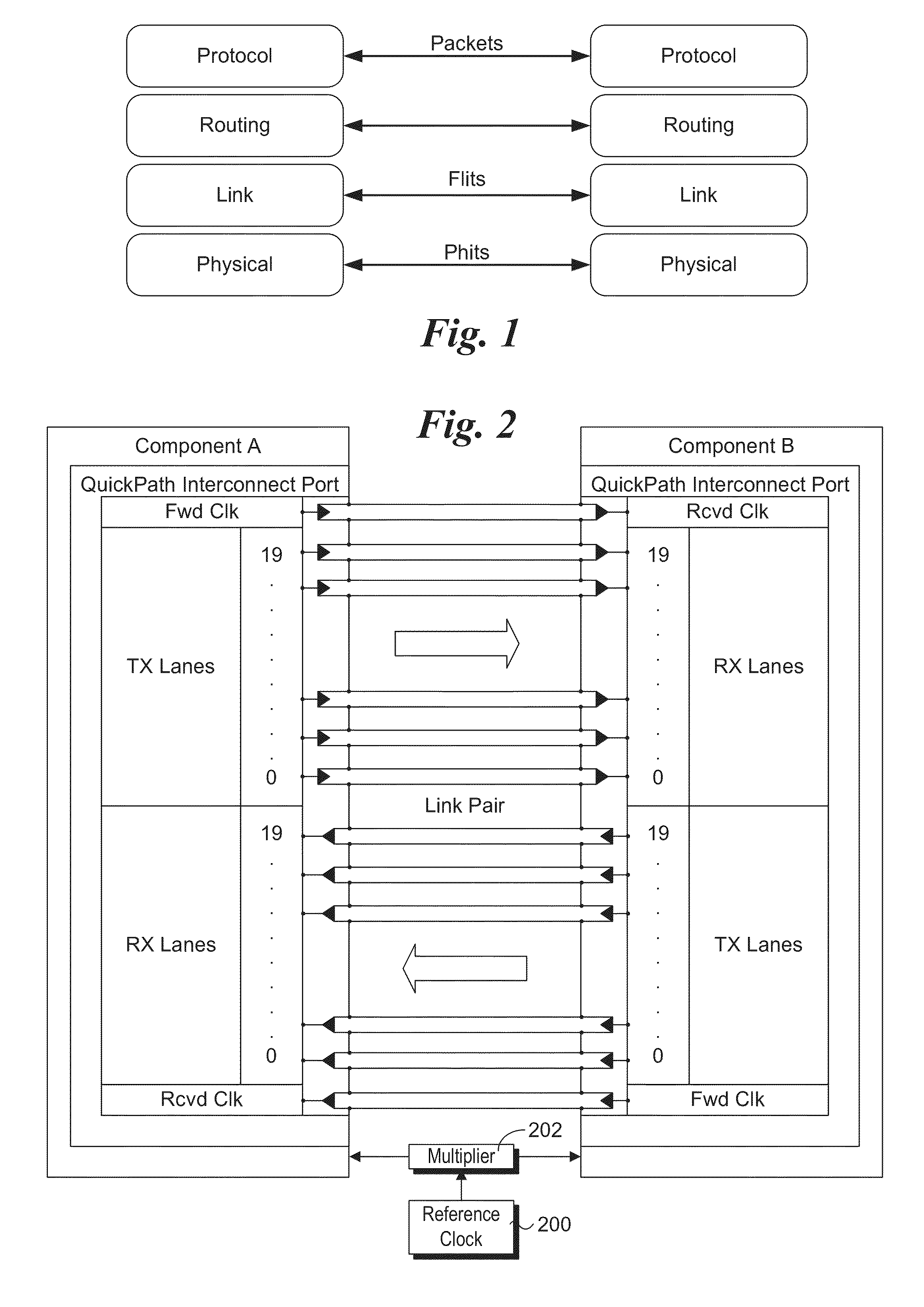
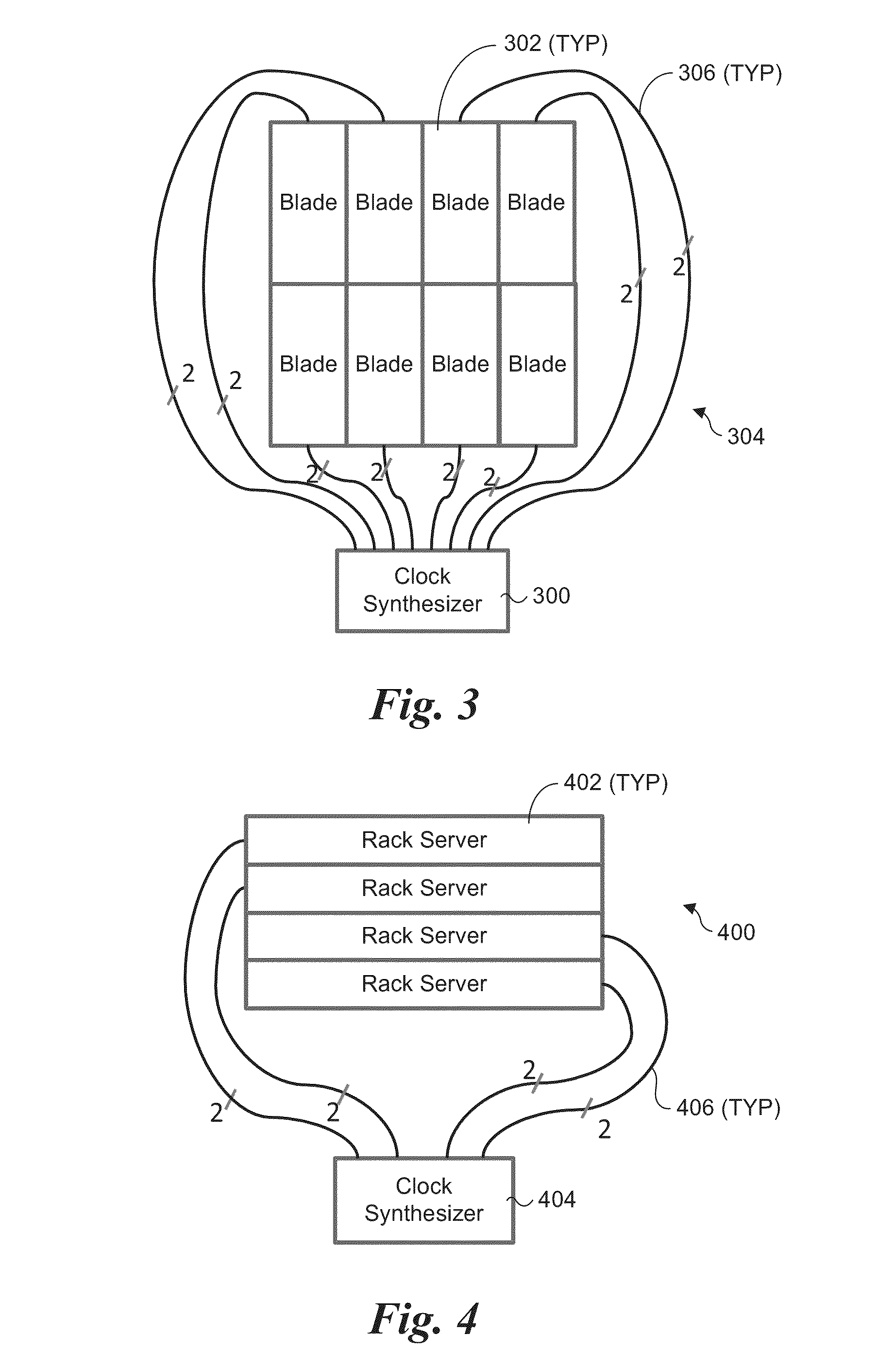
Scalable, common reference-clocking architecture using a separate, single clock source for blade and rack servers
Scalable, common reference-clocking architecture and method for blade and rack servers. A common reference clock source is configured to provide synchronized clock input signals to a plurality of blades in a blade server or servers in a rack server. The reference clock signals are then used for clock operations related to serial interconnect links between blades and / or servers, such as QuickPath Interconnect (QPI) links or PCIe links. The serial interconnect links may be routed via electrical or optical cables between blades or servers. The common reference clock input and inter-blade or inter-server interconnect scheme is scalable, such that the plurality of blades or servers can be linked together in communication. Moreover, when QPI links are used, coherent memory transactions across blades or servers are provided, enabling fine grained parallelism to be used for parallel processing applications.
Owner:INTEL CORP
System and method to join and cut two-way rest overlay trees for distributed knowledge bases
ActiveUS20130085993A1Digital data processing detailsDatabase distribution/replicationDistributed knowledgeDistributed computing
System and method of event-driven synchronization of a database distributed among servers connected in a tree topology, including: transmitting, from a root server, a composition request to a first level of child servers of the root server; recursively transmitting, from each child server of a first level, a composition request to child servers at a second level, wherein the second level is lower than the first level; recursively transmitting, from each child server of the second level, a notification message to child servers at the first level, wherein the notification message comprises an identification of database fragments accessible to the child server; transmitting, from child servers at the first level, respective notification messages to the root server, wherein the root server synchronizes an availability of database fragments from the respective notification messages transmitted to the root server. Subtrees may be cut from or joined to the tree topology.
Owner:AVAYA INC
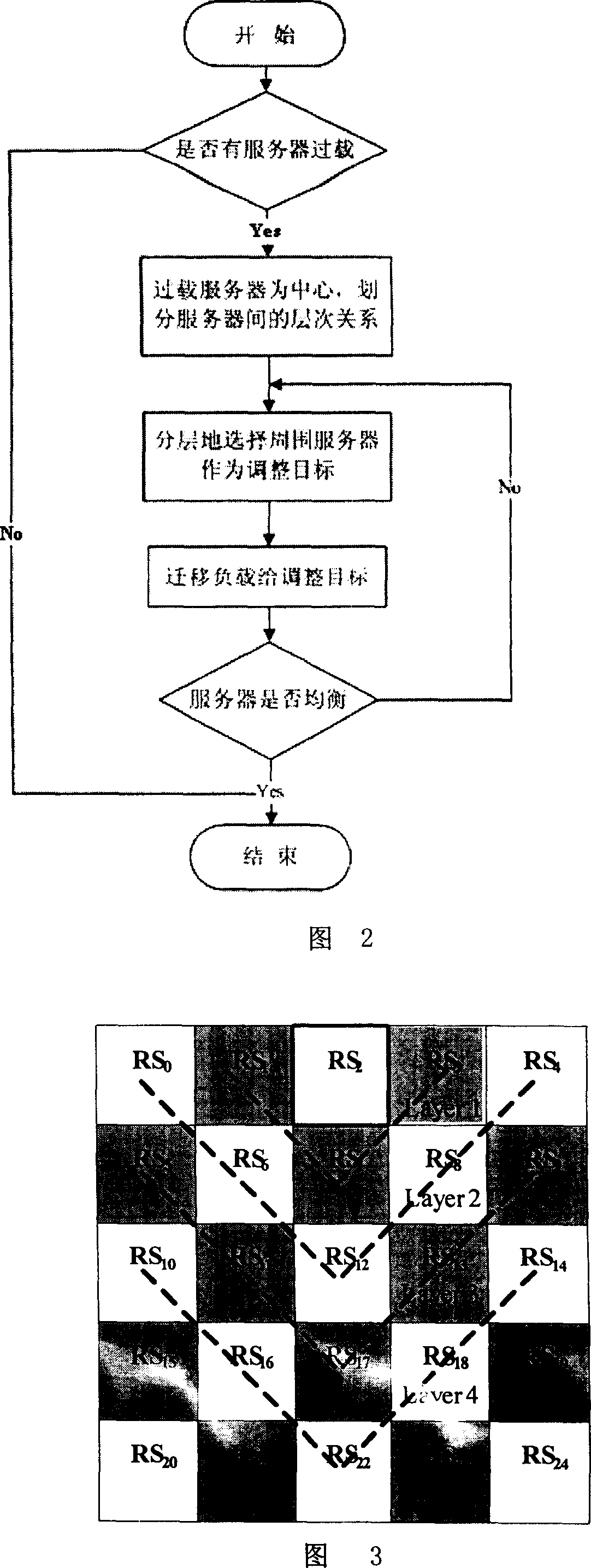
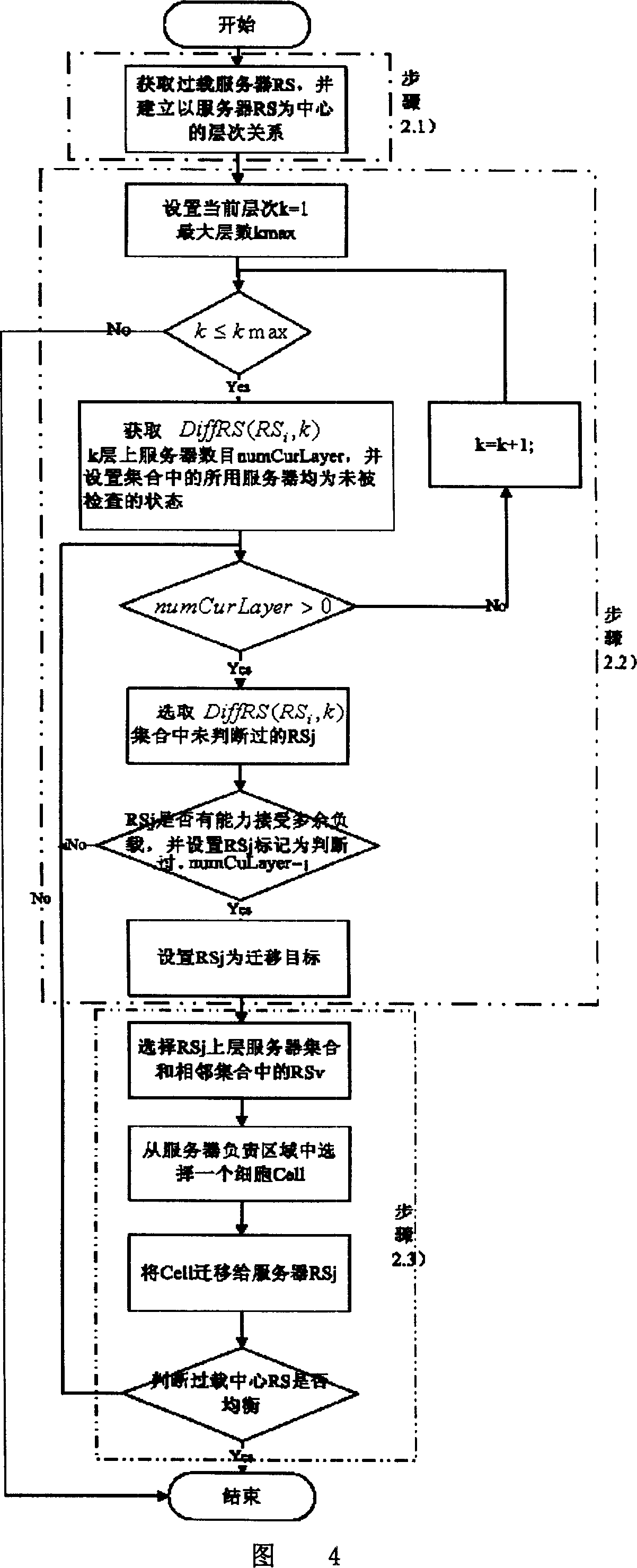
Multi-server hierarchical alterative load balance method
InactiveCN101009648AReduce operational complexityEliminate the bottleneck effectDigital computer detailsData switching networksComputation complexityDynamic balance
The related hierarchical iterative loading balance method for multiple servers comprises: 1 deciding whether the server over loading; 2 if over loading, then 2.1 taking the over-loading server as center to divide the hierarchy fir servers; 2.2 selecting hierarchically servers around as adjust targets; 2.3 selecting transmit loading from the superior server of adjust server to transmit to target, and deciding whether balancing the over-loading server; yes to end process, or else going to step 2.3 till complete balance. This invention has high efficiency, and can realize dynamic balance fast.
Owner:BEIHANG UNIV
A Method of Ensuring the Security of Client Software
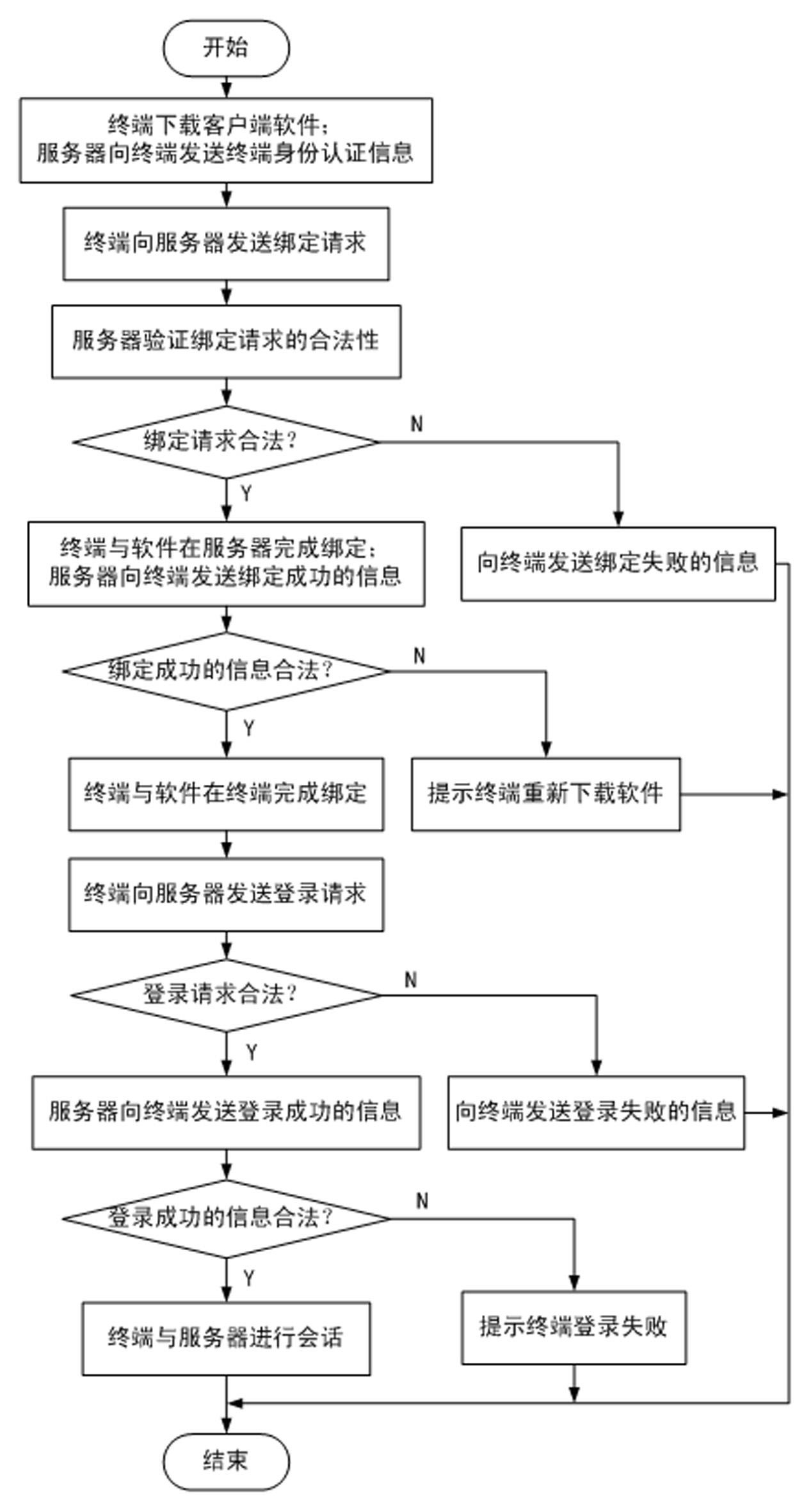
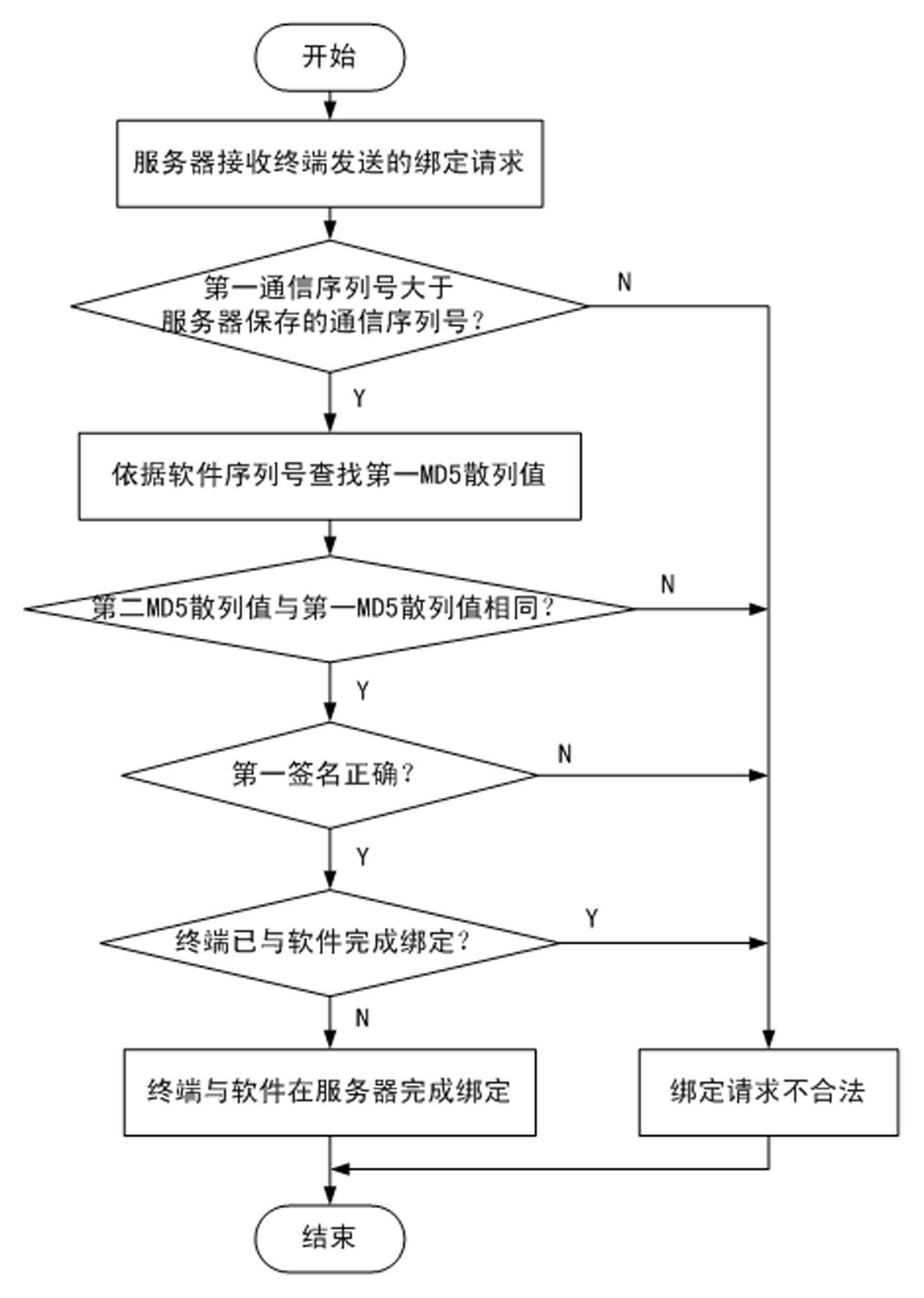
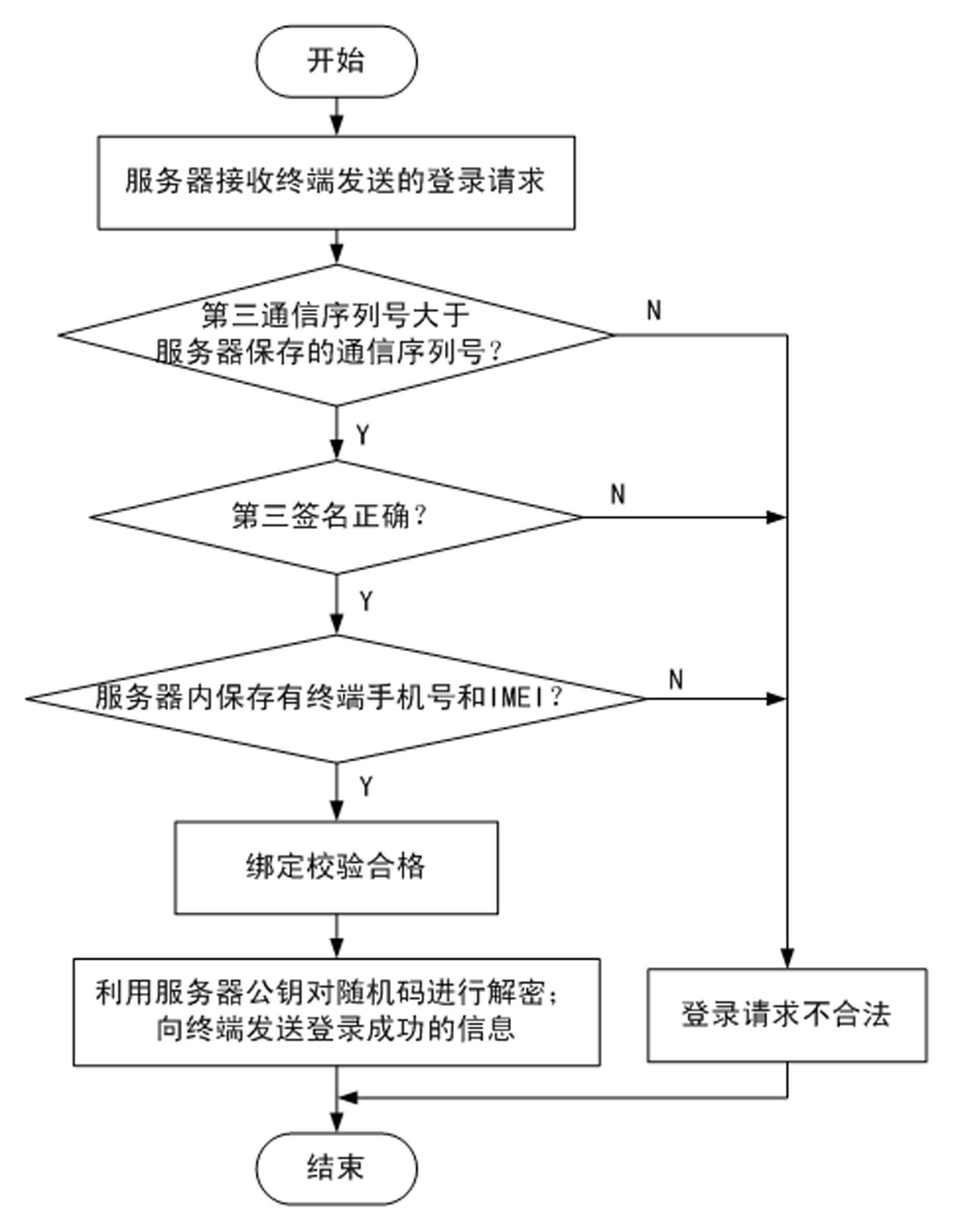
InactiveCN102299930AEnsure communication securityNormal use will not be harmfulUser identity/authority verificationCommunications securityClient-side
The invention discloses a method for ensuring the security of client software. The method comprises the following steps of: 1, downloading the software by using a terminal, and adding terminal identity authentication information into a software packet by using a server; 2, transmitting a binding request to the server by using the terminal; 3, verifying the legality of the binding request, and if the binding request is legal, transmitting a binding success information to the terminal; 4, verifying the legality of the binding success information; 5, transmitting a login request to the server by using the terminal; 6, verifying the legality of the login request, and if the login request is legal, transmitting a login success information to the terminal; and 7, verifying the legality of the login success information, and if the login success information is legal, keeping a session. By the method, the software can be better prevented from being falsified; the security of communication between the terminal and the server can be ensured; replay attacks can be effectively prevented; the software can be detected whether to be falsified or not; and even though a hacker downloads the software and attacks the server by falsifying the software, only the terminal cannot be used normally and the normal use of other users may not be influenced.
Owner:北京无限新锐网络科技有限公司
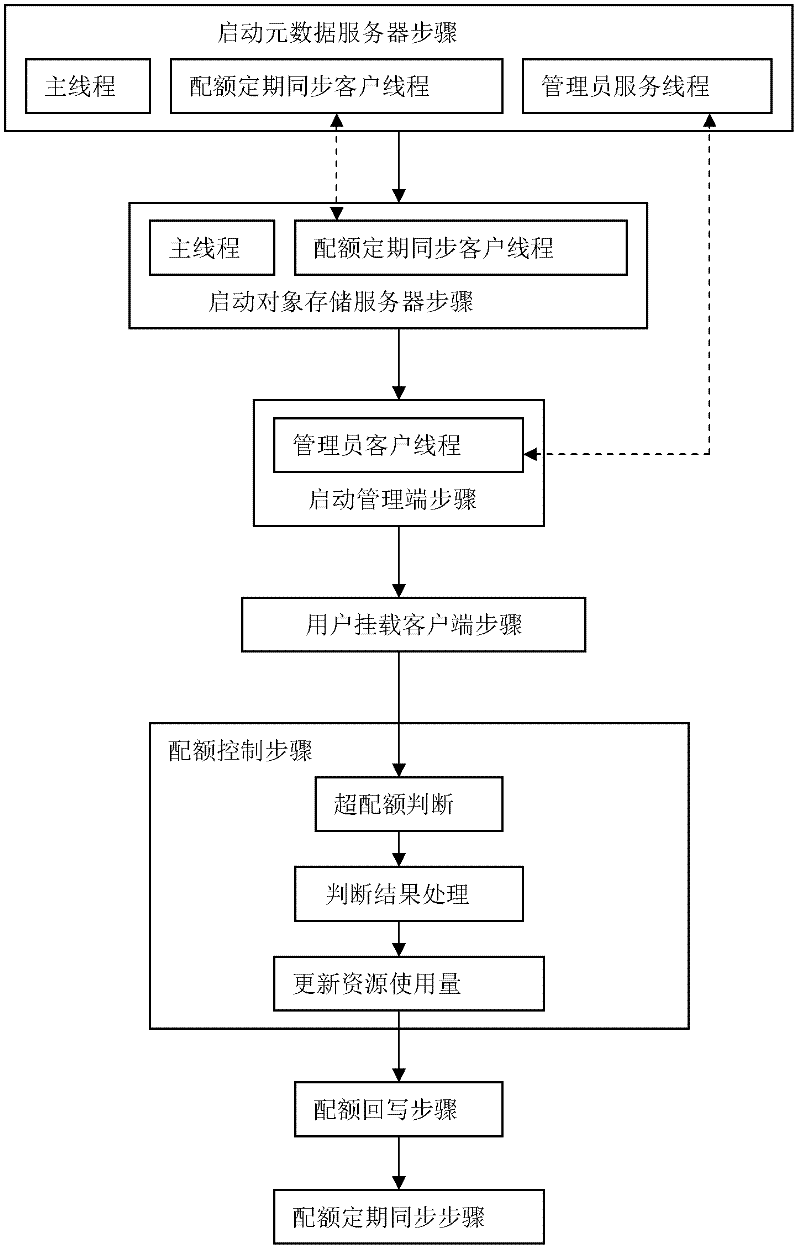
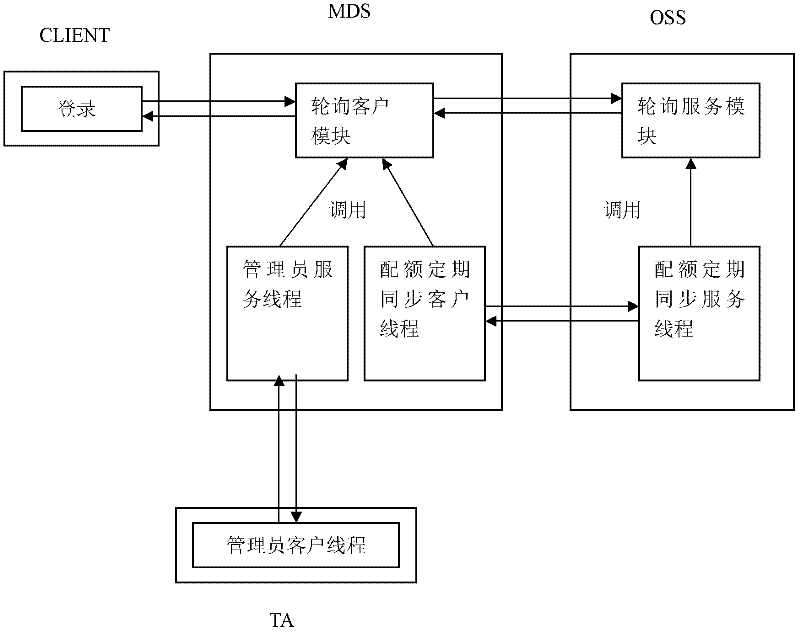
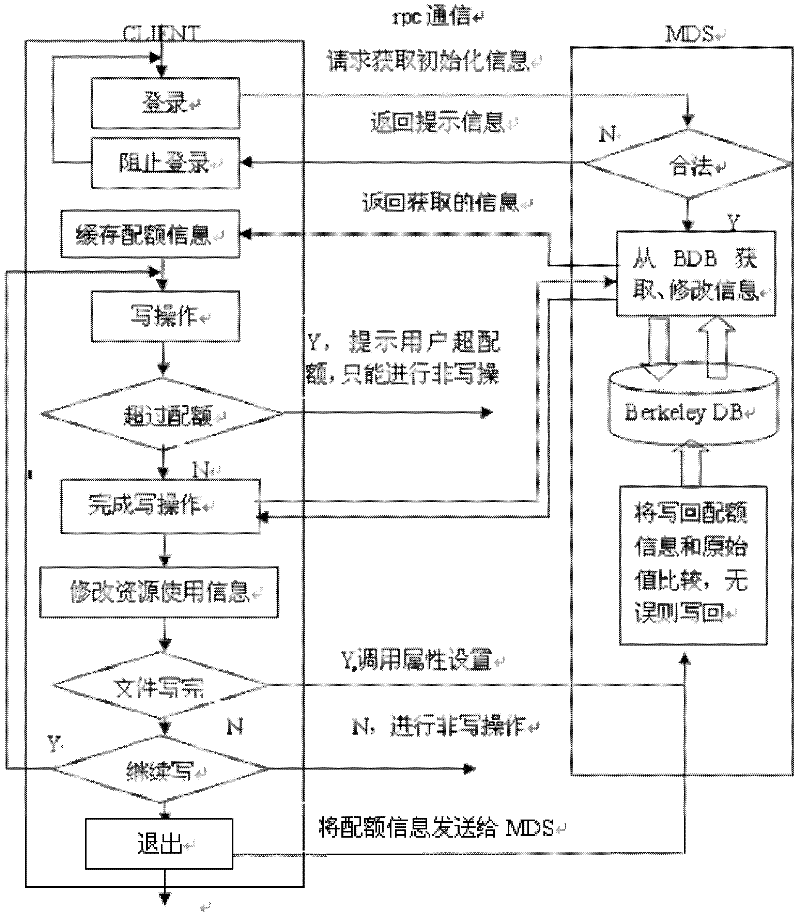
Management and control method for user quota in multi-network storage system
The invention discloses a management and control method for user quota in a multi-network storage system. The method comprises the following steps of starting a metadata server, starting an object storage server, starting a management end, carrying a client end, controlling quotas and back writing quotas. The invention further discloses a management and control system for user quotas. The system comprises a management end, a client end, a metadata server and an object storage server; the management end has an administrator client thread; the client end comprises a quota control module; the metadata server comprises a metadata service thread, a quota regularly synchronized client thread and an administrator service thread; and the object storage server has a document service thread and a quota regularly synchronized service thread. With the adoption of the method and system provided by the invention, waste of network bandwidth caused by unnecessary communication and excessive quota data among servers due to change of resource usage can be avoided, the influence of the quota control function to the system performance is reduced, and meanwhile, a quota consistency synchronizing mechanism is further provided to ensure correctness and consistency of the usage amount of user resources in the system.
Owner:HUAZHONG UNIV OF SCI & TECH
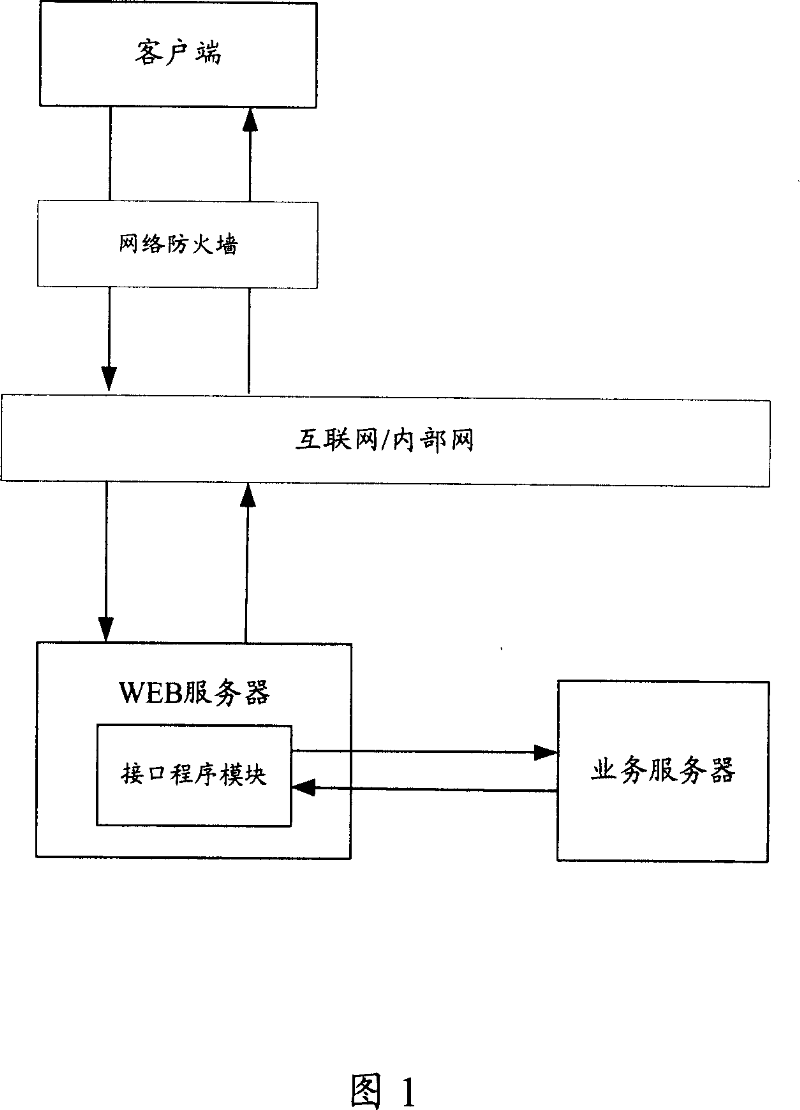
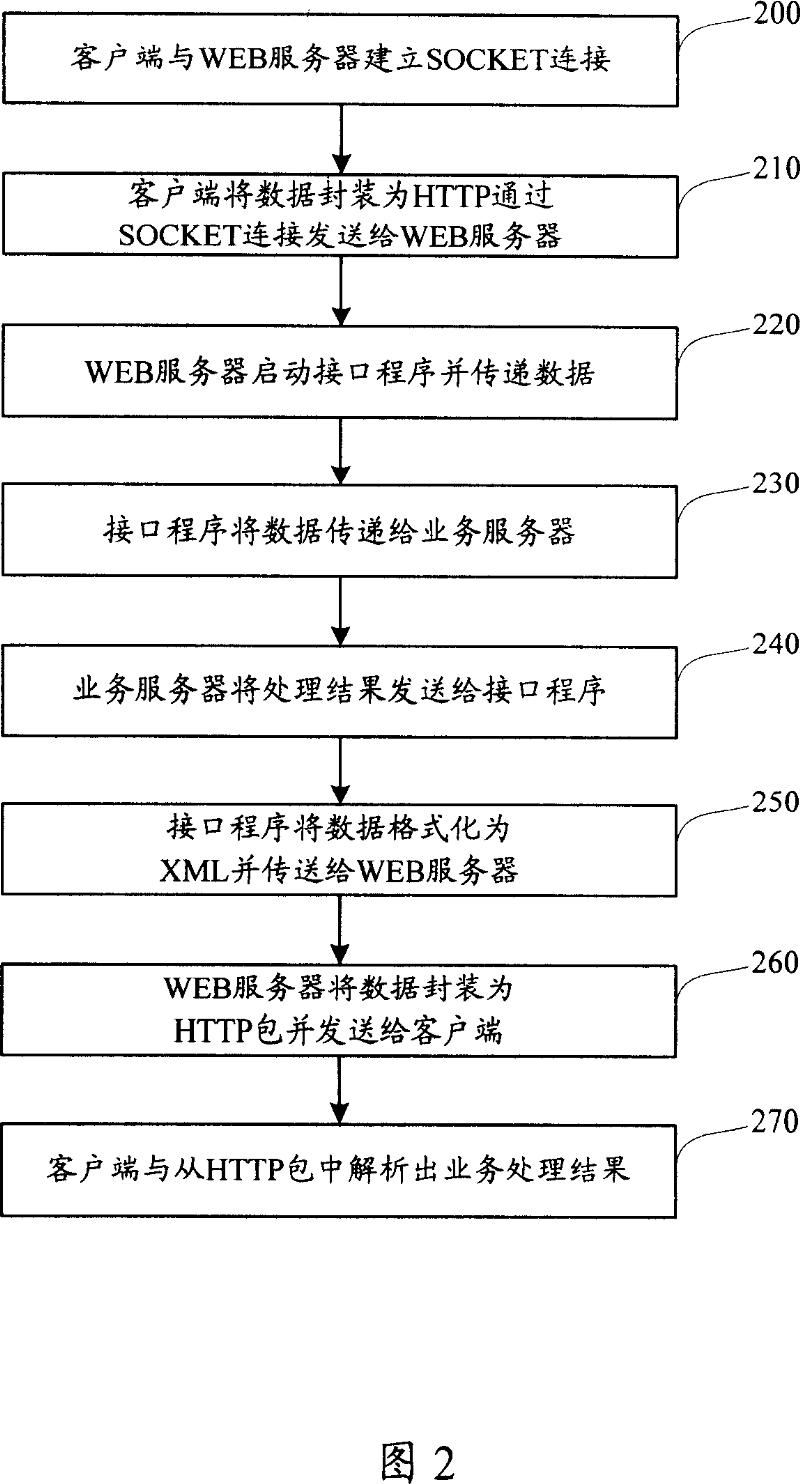
Web server based communication method and system
ActiveCN101043522AAvoid no communicationEasy to implementTransmissionCommunications systemWeb service
The invention discloses a communication method based on Web server, so as to solve the problem in present technology that the communication port is limited when the SLCKET communicating between the client-side and server, the method comprises: the client packs data into HTTP package to send to the Web server through the SOCKET, the latter analyzes the HTTP data package and calls appointed interface program, and the interface program connects with the business server for communication. The invention also discloses a communication system at the same time.
Owner:TENCENT TECH (SHENZHEN) CO LTD
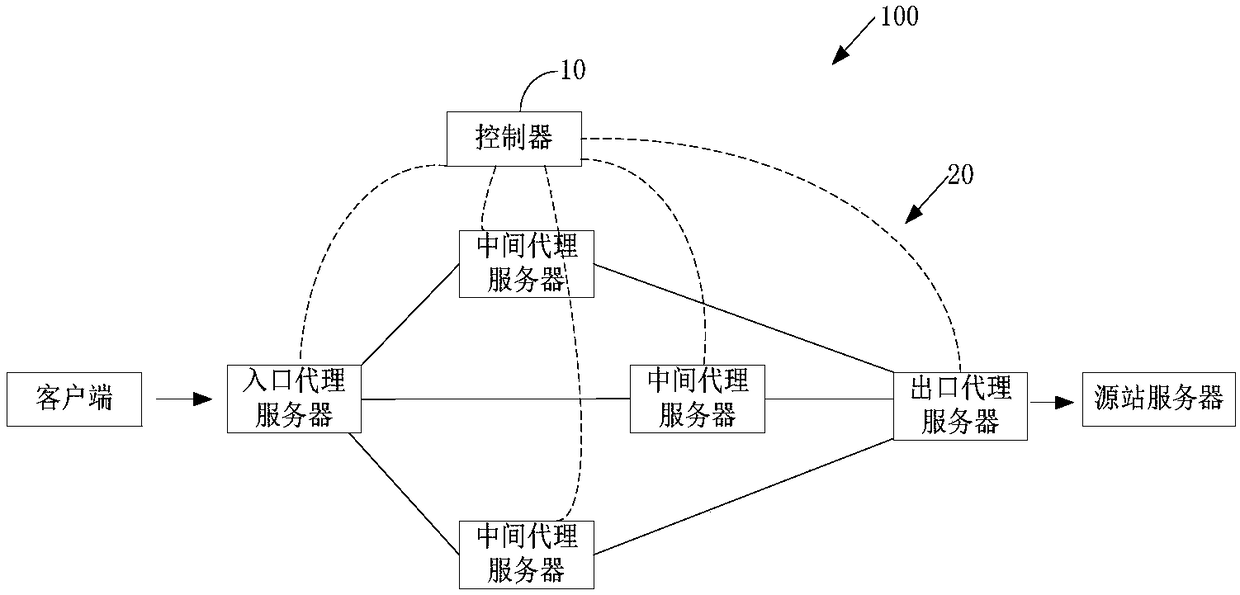
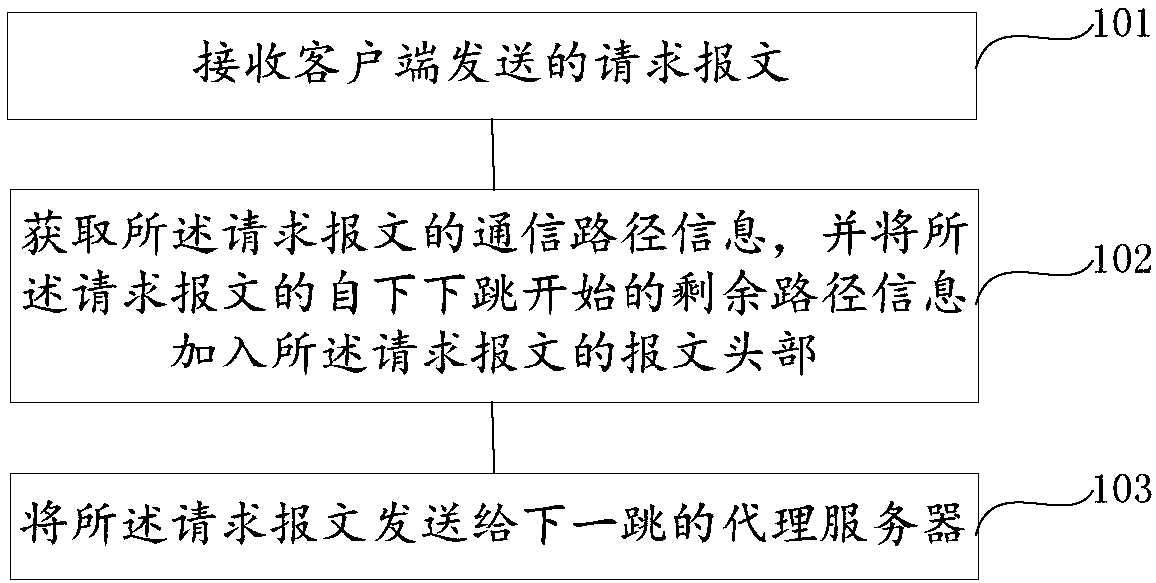
Proxy forwarding method and apparatus, proxy server and multi-level proxy network
ActiveCN108064443AImprove data transfer efficiencyData switching networksNetwork communicationClient-side
Embodiments of the present invention relate to the technical field of network communication, for example, to a proxy forwarding method and apparatus, a proxy server, and a multi-level proxy network, the proxy forwarding method being applied to a proxy server, the proxy server communicating with at least two other proxy servers, the proxy server serving as an entry proxy server, the method including: receiving a request message sent by a client; acquiring communication path information of the request message, and adding residual path information of the request message starting from the next-next-hop to the header of the request message; and sending the request message to the next-hop proxy server. In the embodiments of the present invention, the preferred communication path information is added to the header of the data message, so that each proxy server performs data forwarding according to the preferred communication path. Through the interaction between the client and the source server through the multi-level proxy server, the preferred path can be selected for data packet transmission, and the data transmission efficiency is high.
Owner:CLOUDMINDS SHANGHAI ROBOTICS CO LTD
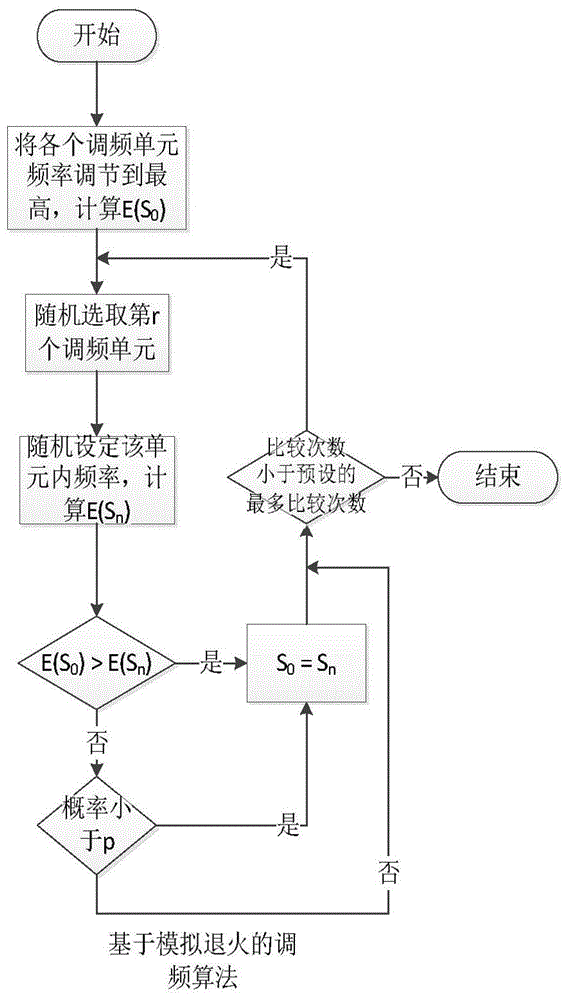
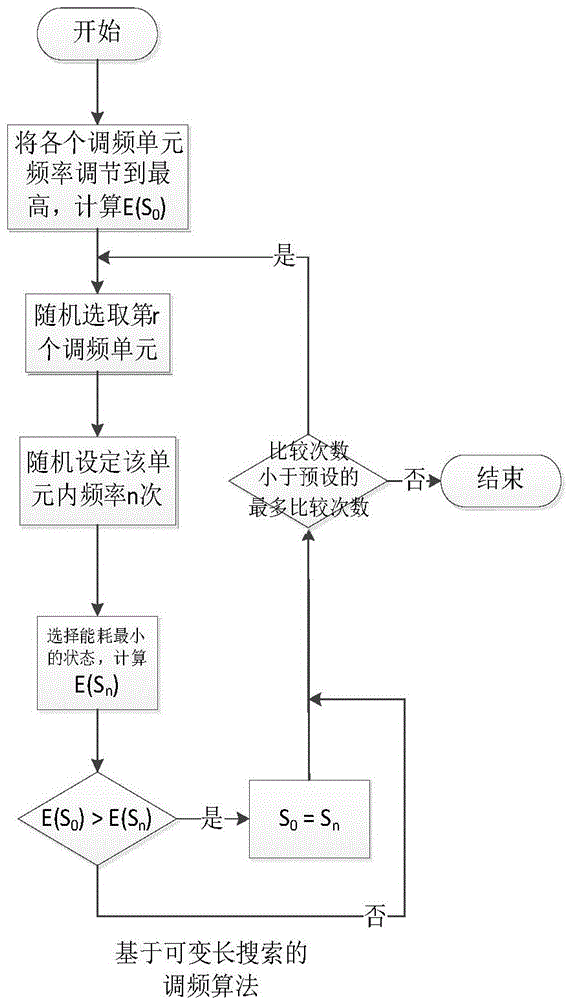
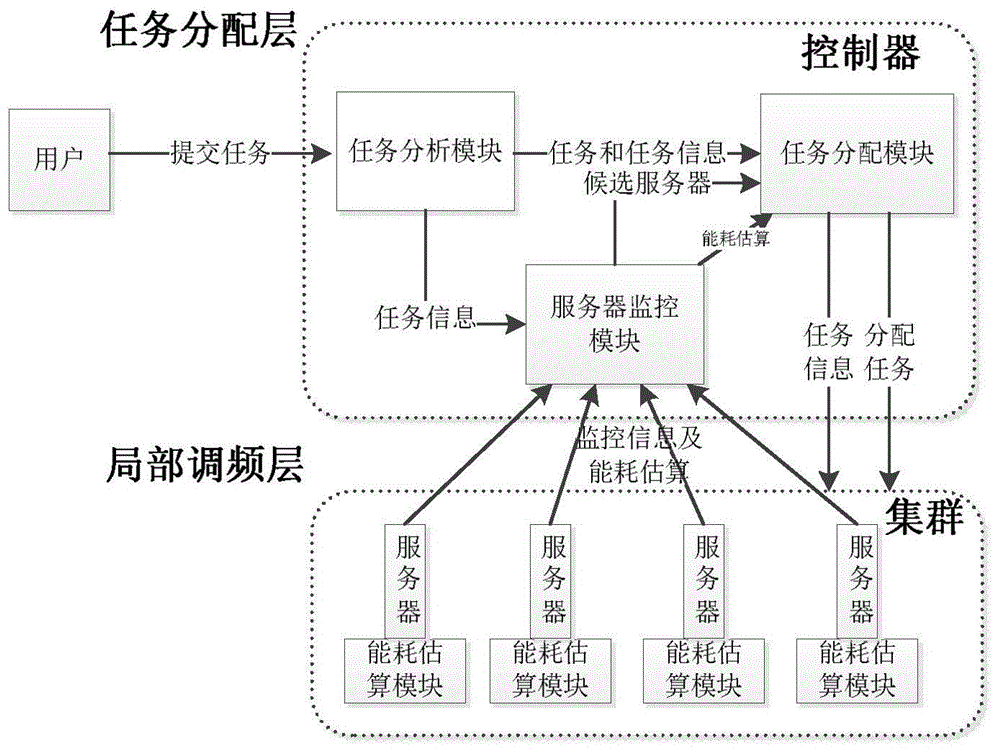
Data center energy consumption management method and system based on dynamic frequency modulation
ActiveCN104808770AReduce energy consumptionSave money on electricityResource allocationPower supply for data processingData centerServer allocation
The invention discloses a data center energy consumption management method and system based on dynamic frequency modulation. The method comprises frequency modulation energy conservation of a single server and task scheduling of energy awareness among servers, wherein the frequency modulation energy conservation of the single server comprises the steps of taking a time quantum of a constant task number as a frequency modulation unit, estimating dissipative energy of each unit according to an energy consumption model and task information, and utilizing a heuristic algorithm to select a frequency modulation mode which enables the sum of energy consumption of all units to be minimum so as to adjust the frequency of a processor; the task scheduling of energy awareness among the servers comprises the steps of selecting a candidate server according to the state of each server and the task information when a task reaches, utilizing a frequency modulation energy conservation method on the single server by each server according the task information to estimate the energy consumption change, selecting the server with the minimum energy consumption change by a controller to distribute a new task, and utilizing the frequency modulation energy conservation method on the single server by the selected server to modulate the frequency and operate the new task. According to the invention, the energy consumption of the servers in a data center is reduced by frequency modulation and task distribution, and energy saving and emission reduction effects are achieved.
Owner:NANJING UNIV
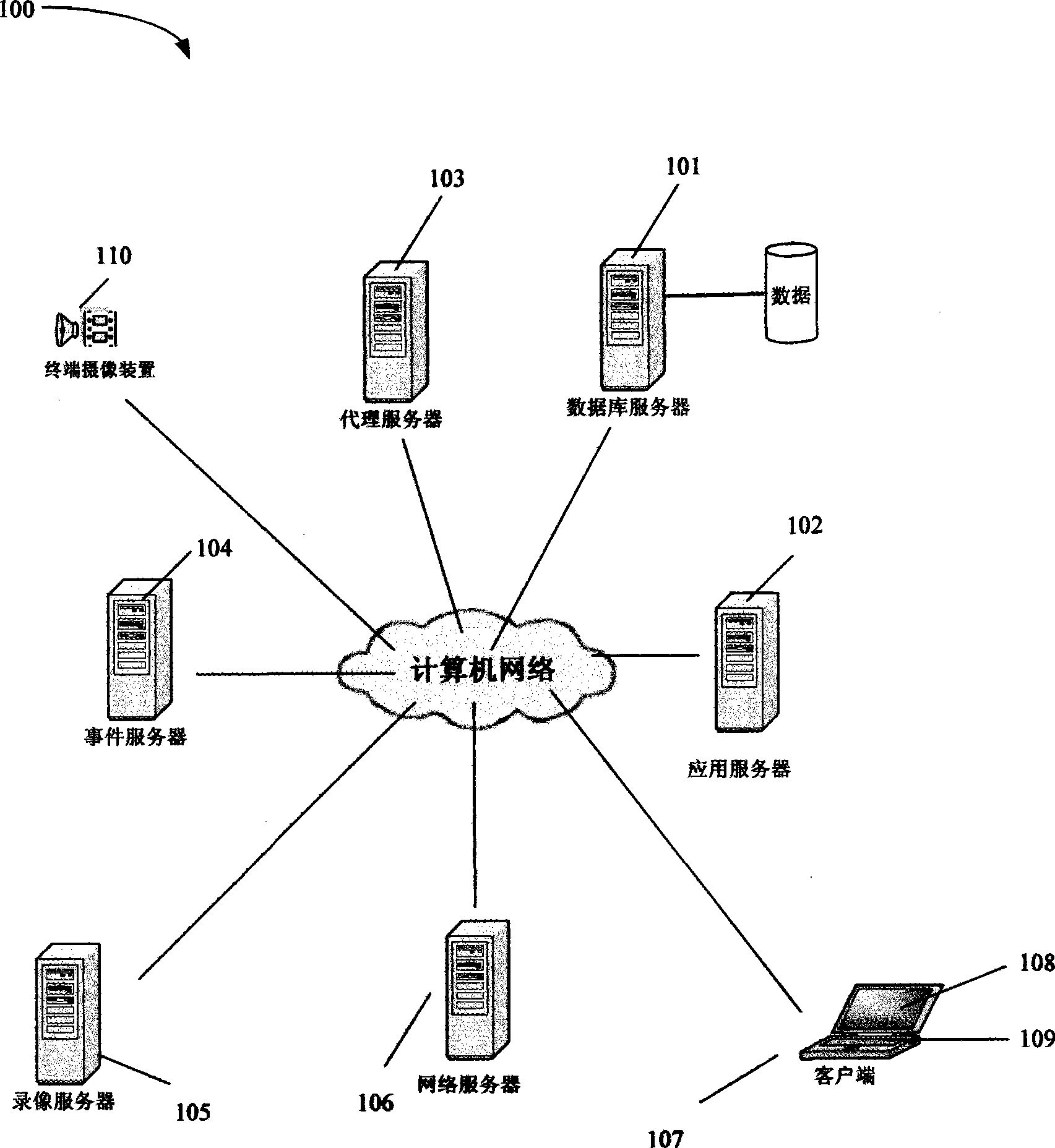
Video monitoring system based on computer network
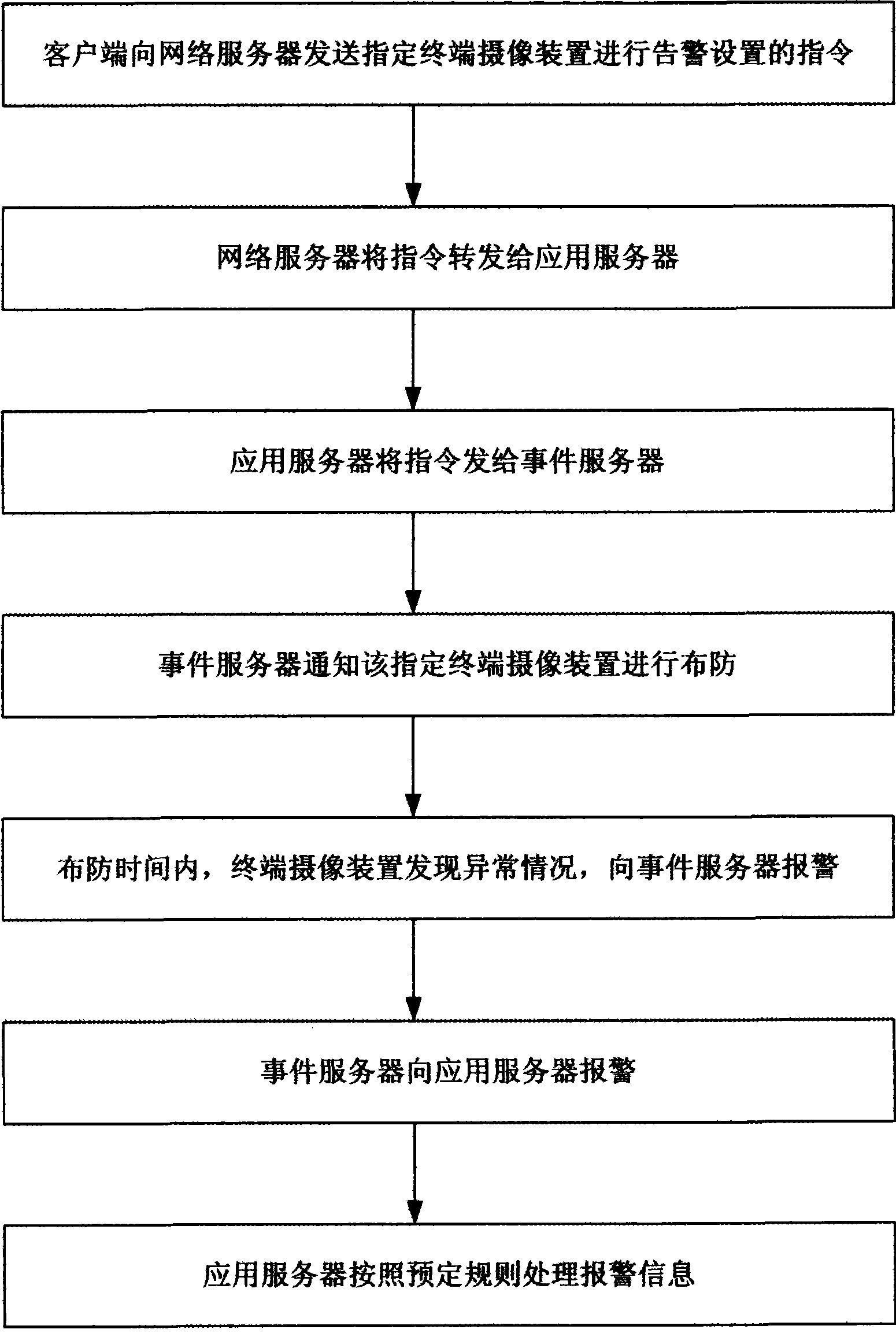
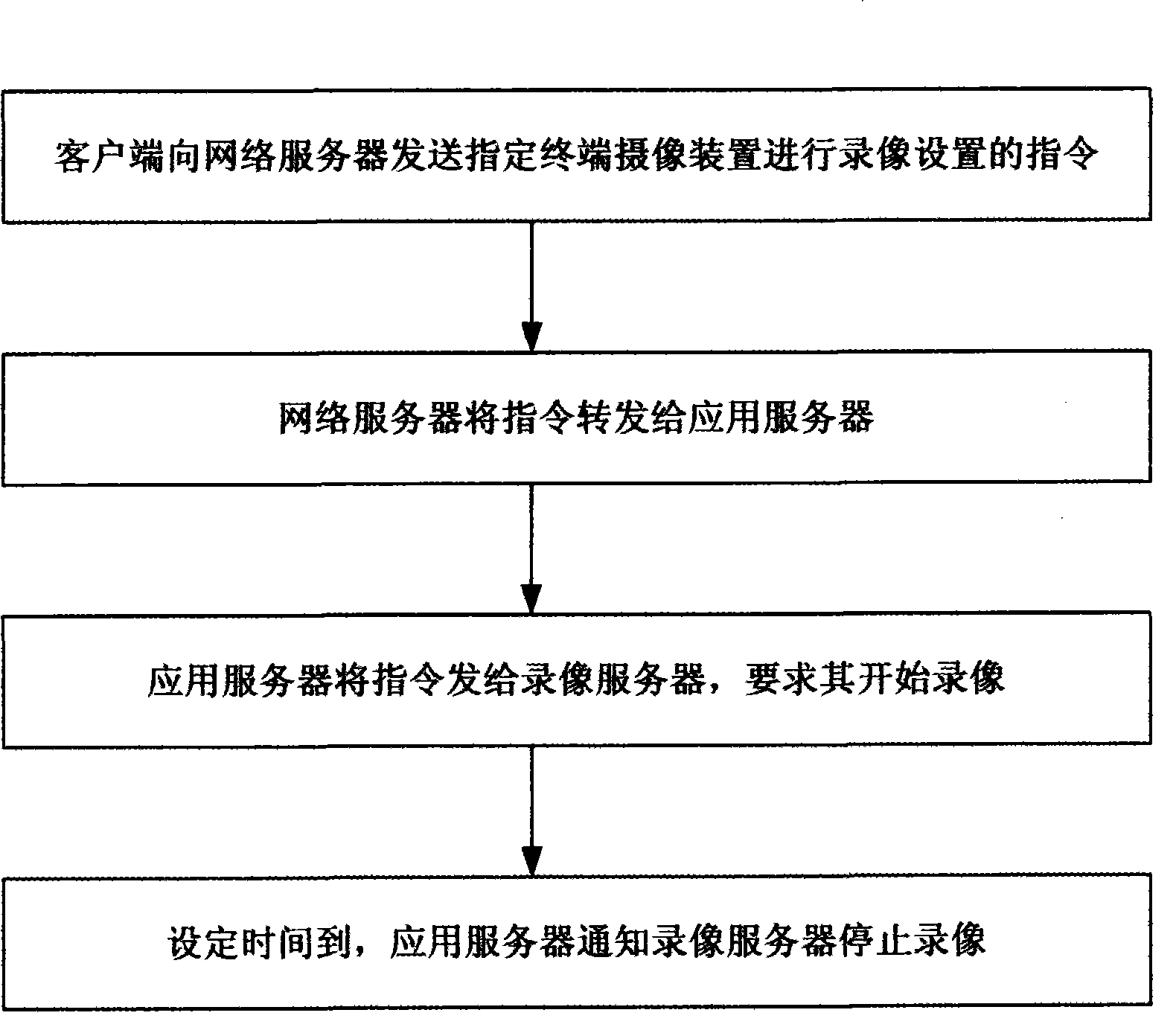
ActiveCN101365118AGuaranteed ease of operationNew experienceClosed circuit television systemsTransmissionVideo monitoringApplication server
The invention discloses a video monitoring system based on a computer network, which comprises a client, a terminal camera device, an event server, a video recording server, a network server, an application server, a database server, etc., wherein the application server is respectively connected with the event server, the video recording server, the network server and the database server through the computer network, and exchanges data with the servers. By using the application server to conduct the data relay among the servers, the entire video monitoring system becomes convenient, fast, safe and reliable.
Owner:GUANGDONG VIMICRO
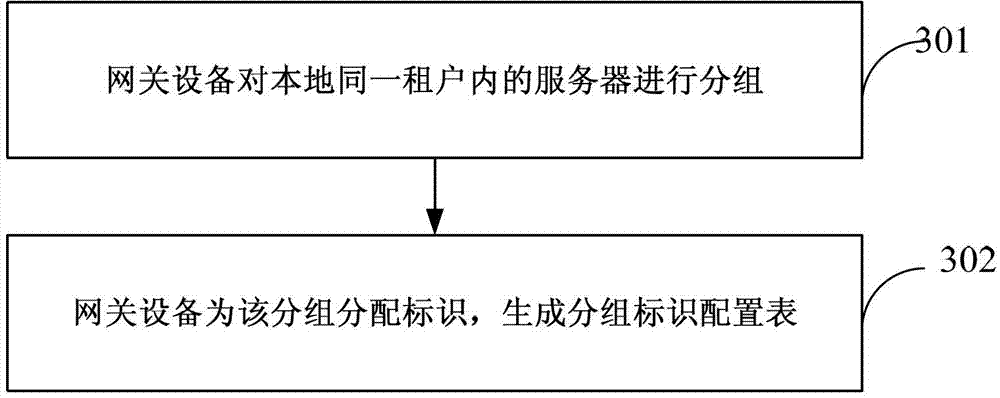
Communication control method for servers of same lessee and network device
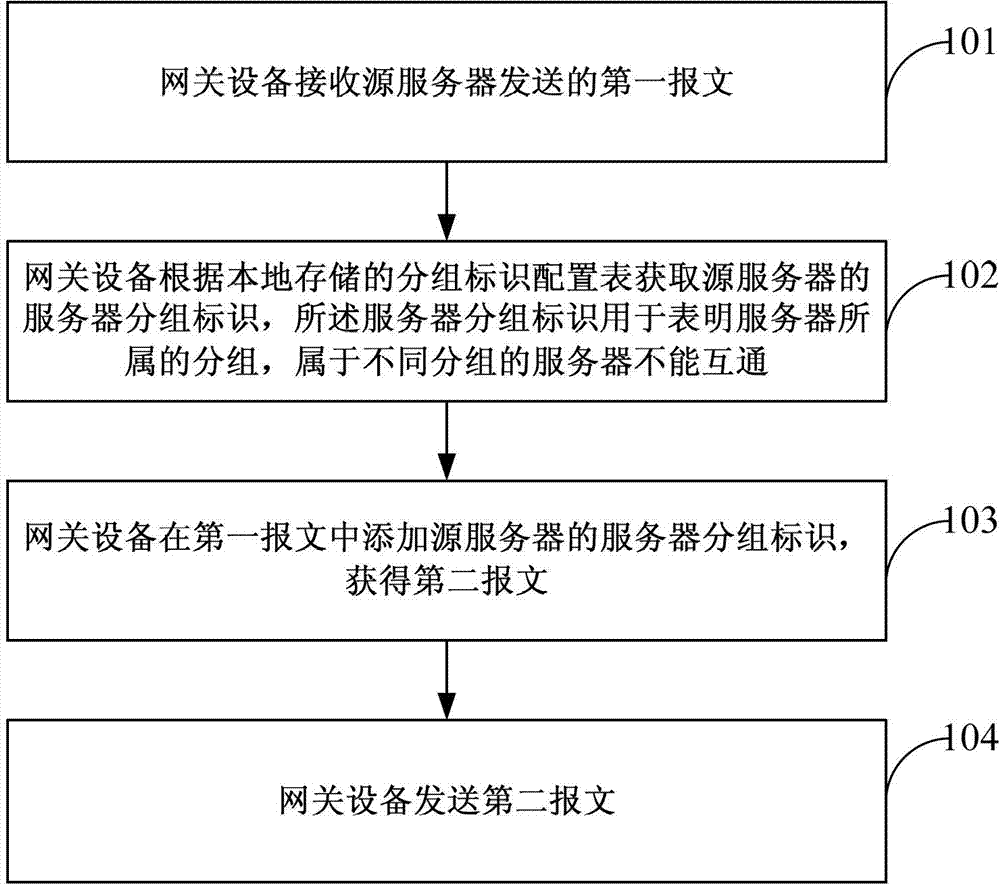
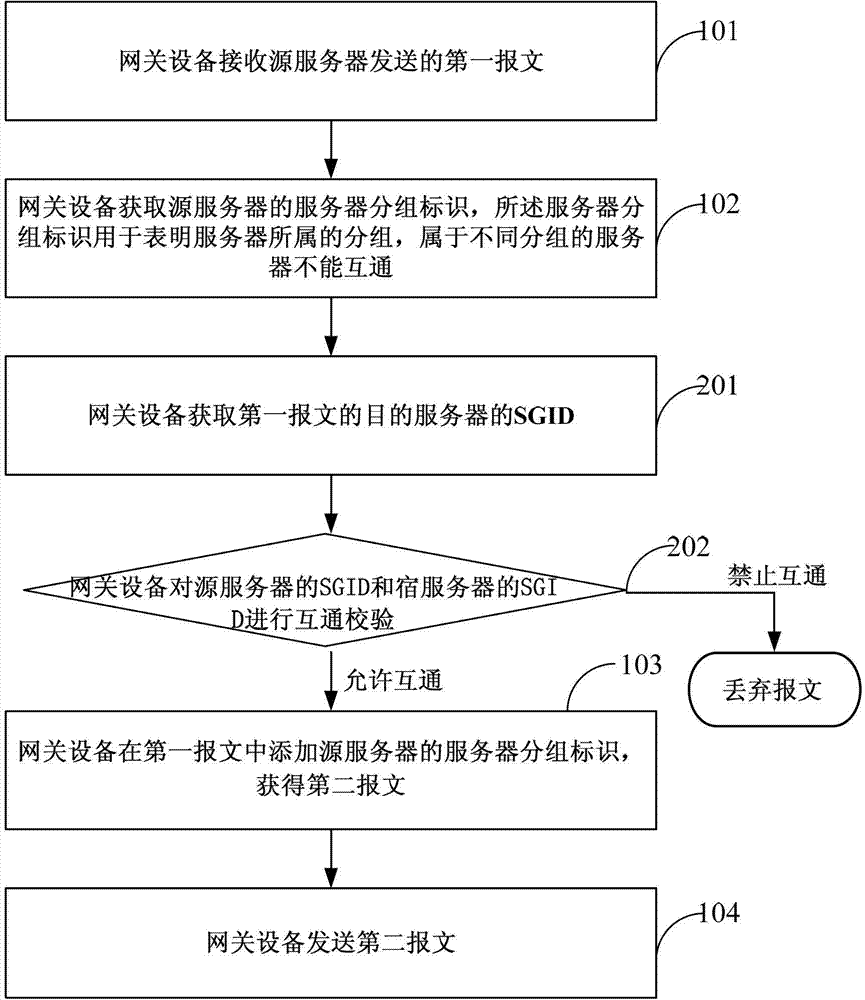
ActiveCN103118149AImprove interoperabilityHybrid transportNetworks interconnectionCommunication controlInter-server
An embodiment of the invention discloses a communication control method for servers of the same lessee and a network device. The network device receives a first message sent by a source server. The network device obtains server grouping identifications of the source server according to a grouping identification configuring table stored locally, the server grouping identifications are used for indicating groups which the servers belong to, and the servers belonging to different groups cannot be intercommunicated. The network device adds the server grouping identifications of the source server in the first message to obtain a second message. The network device sends the second message. By means of the method, intercommunication or isolation control among the servers in the same visual networking index (VNI) or virtual subnet ID (VSID).
Owner:HUAWEI TECH CO LTD
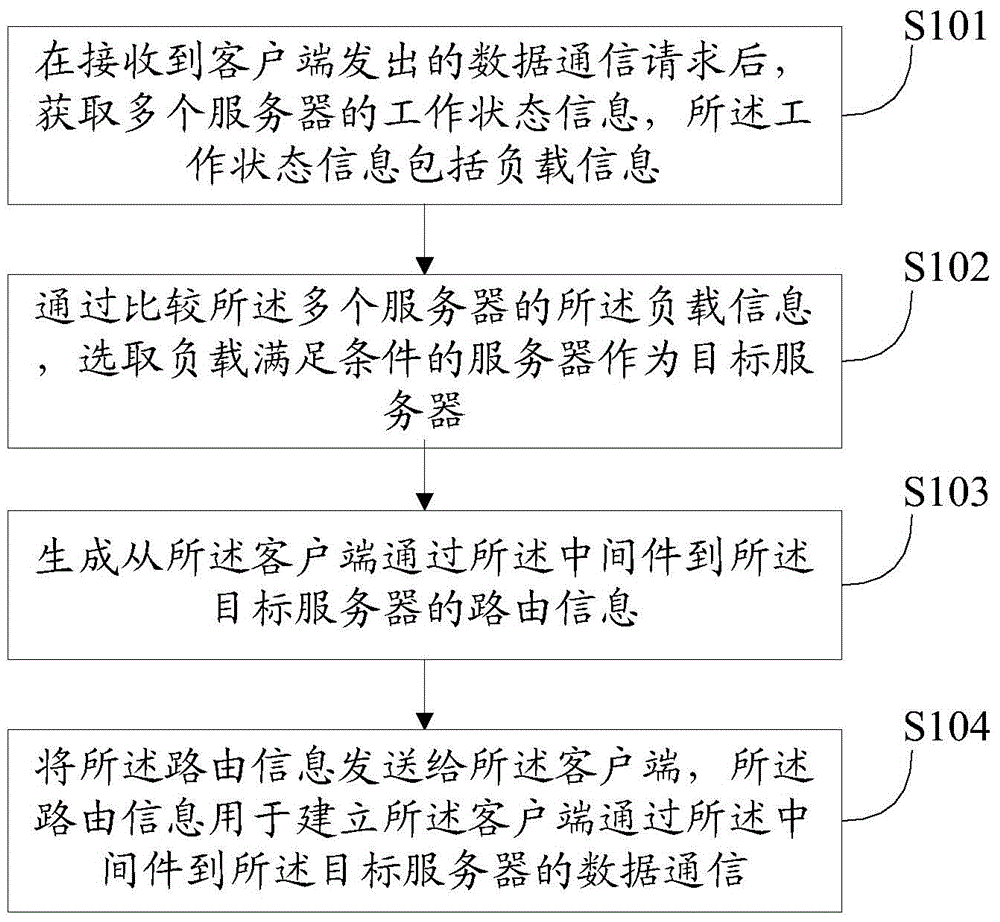
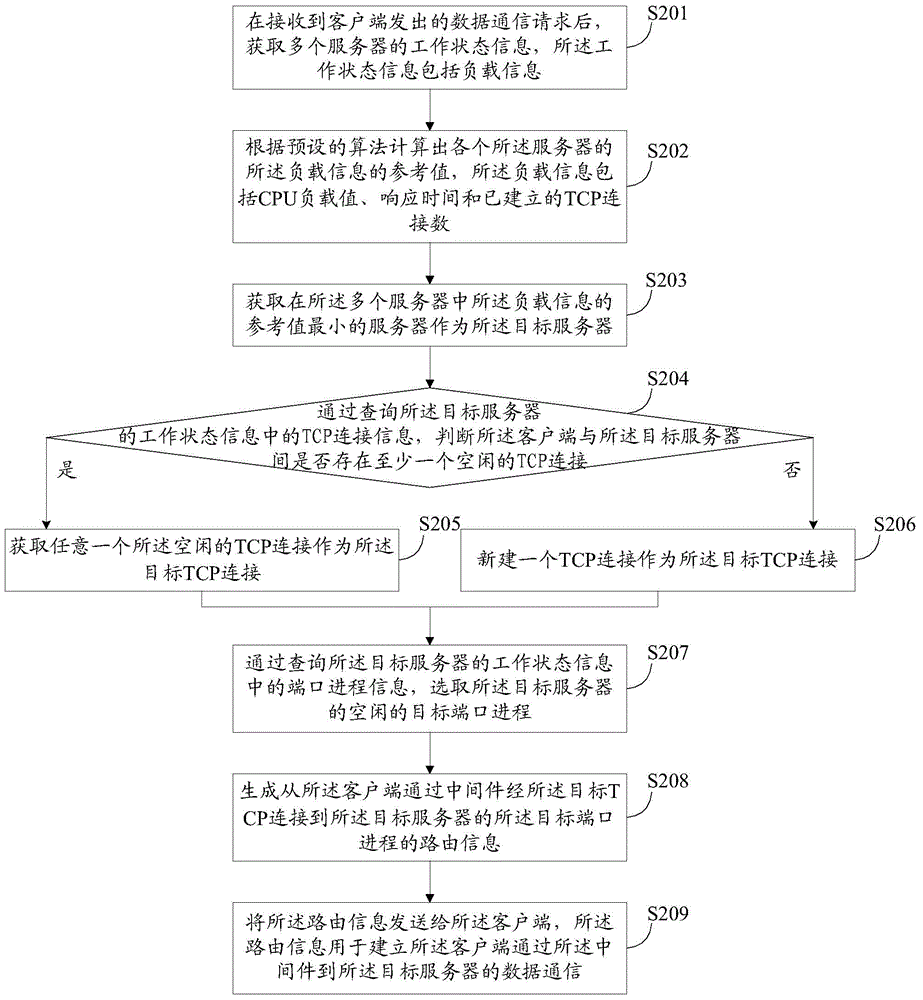
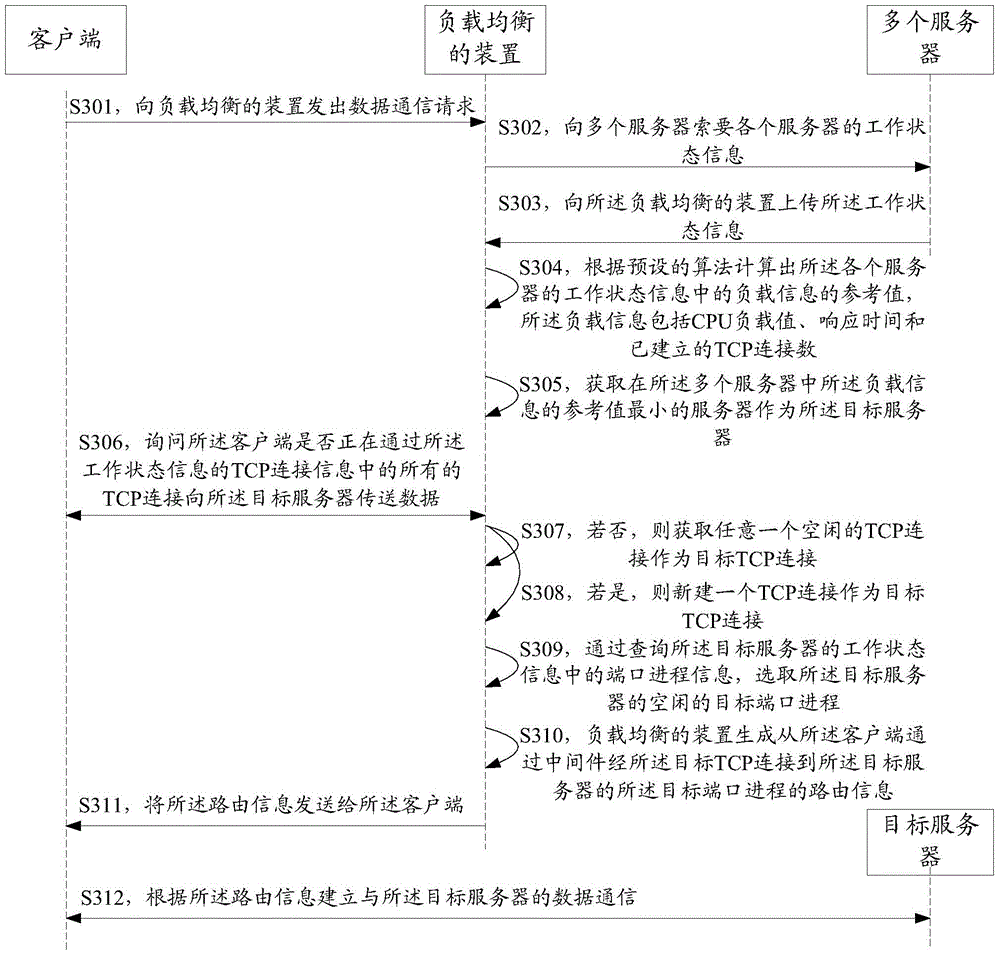
Routing method, load balancing device and data communication system
ActiveCN105471760ALoad balancingFlexible requestData switching networksCommunications systemMiddleware
The embodiment of the invention discloses a routing method which comprises a step of obtaining the working state information of multiple servers after receiving the data communication request emitted by a client, wherein the working state information comprises load information, a step of selecting a server whose load satisfies a condition as a target server through comparing the load information of the multiple servers, a step of generating the routing information of a client to the target server through an intermediate piece, a step of sending the routing information to the client, wherein the routing information is used for establishing the data communication of the client to the target server through the intermediate piece. Correspondingly, the embodiment of the present invention also discloses a load balancing device and a data communication system. By using the routing method, the load balancing device and the data communication system, the load of the data communication between the client and multiple servers can be balanced, the request is flexible, the reliability is high, and the cost is low.
Owner:HUAWEI TECH CO LTD
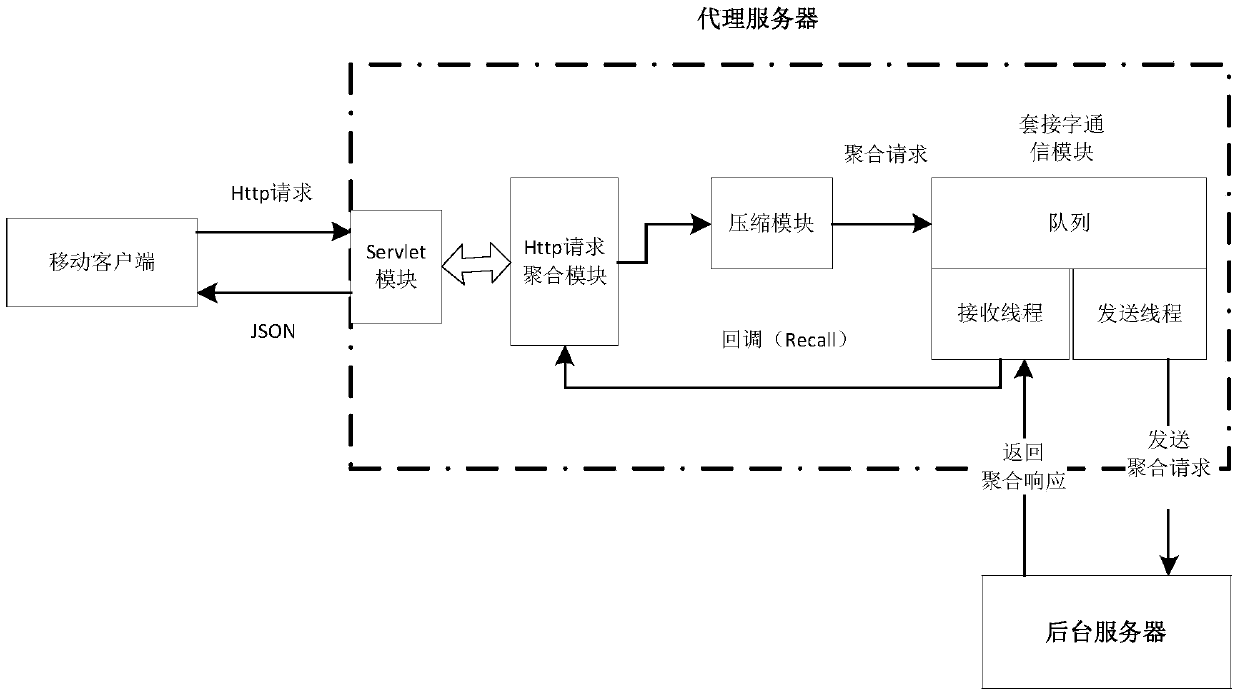
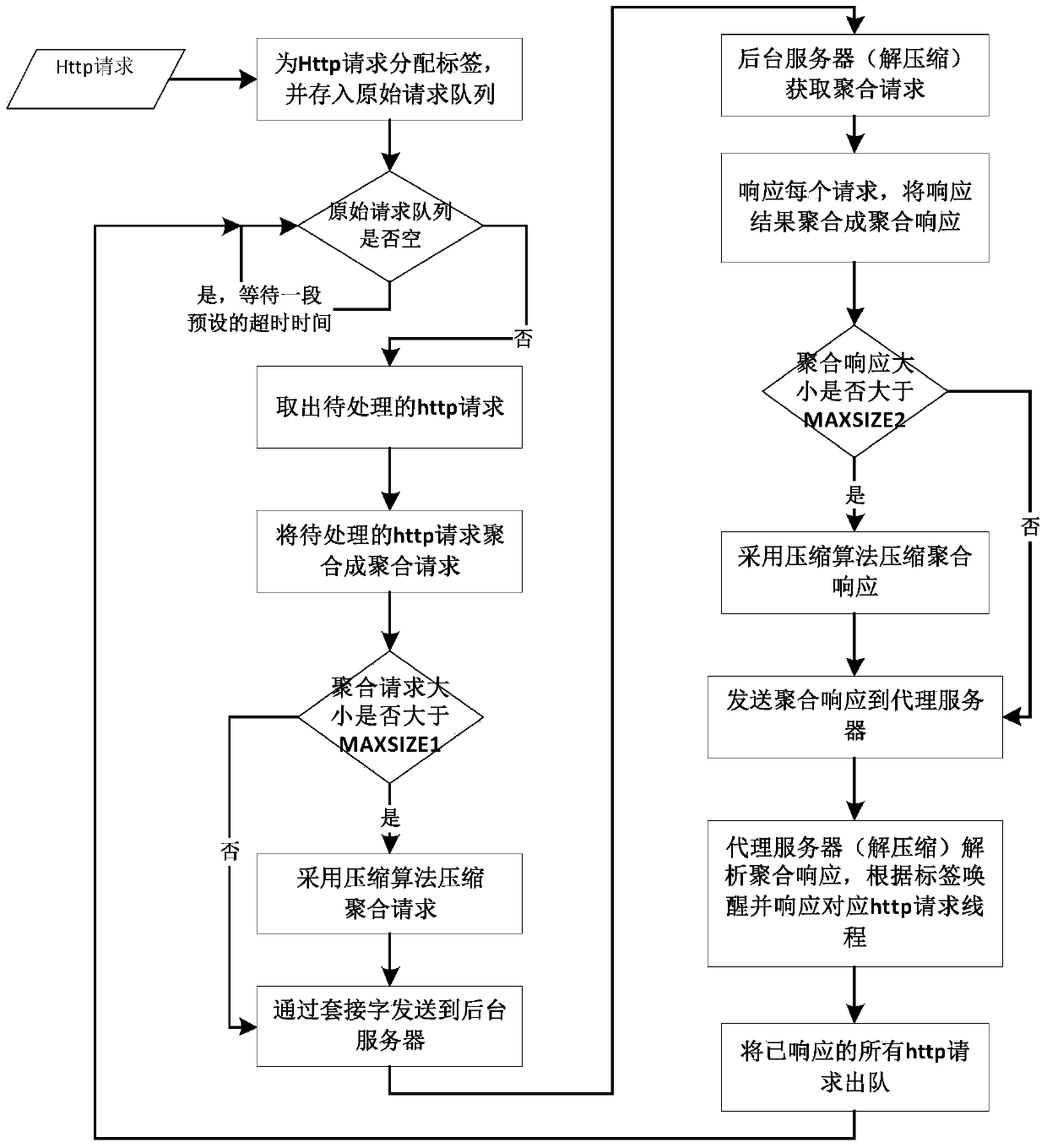
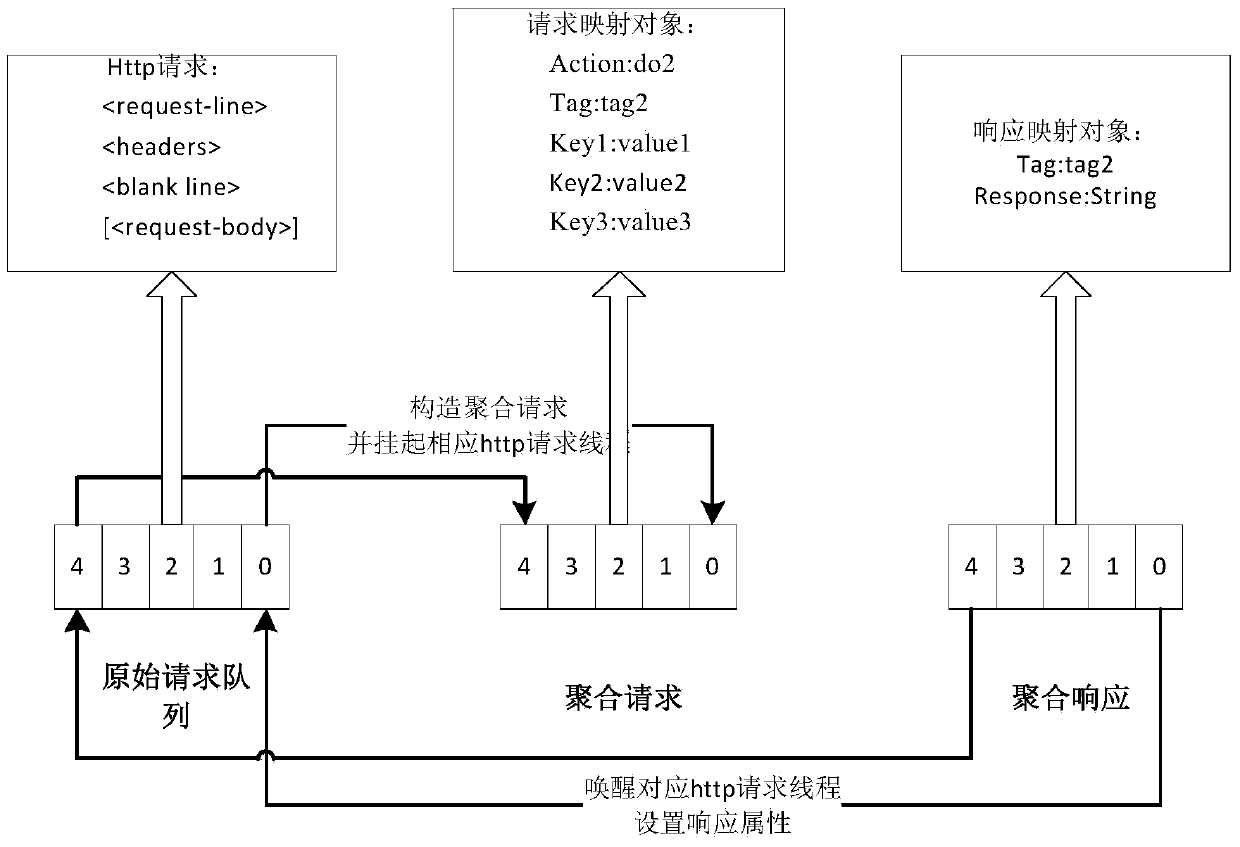
Mobile terminal HTTP (Hyper Text Transport Protocol) request aggregation compression system and method
InactiveCN103747097AReduce communication data volumeReduce response delayTransmissionData compressionResponse delay
The invention discloses a mobile terminal HTTP (Hyper Text Transport Protocol) request aggregation compression system and method, and belongs to the technical field of computer network communication; the system comprises a Servlet module, an HTTP request aggregation module, a data compression module and a socket communication module. The system and the method disclosed by the invention have the beneficial effects that the aggregation compression of an HTTP request is realized at a proxy server, and HTTP requests of a plurality of mobile terminals can be processed by performing one-time socket communication between the proxy server and a background server. For the occasions that the number of communication sockets between proxy servers and background servers is limited, and a plurality of terminal requests concur, less sockets are utilized by the system and the method disclosed by the invention for processing the HTTP requests of a great deal of mobile terminals, the communication data volume between the proxy servers and the background servers can be reduced remarkably, and response delay of the servers for the terminal requests is reduced.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
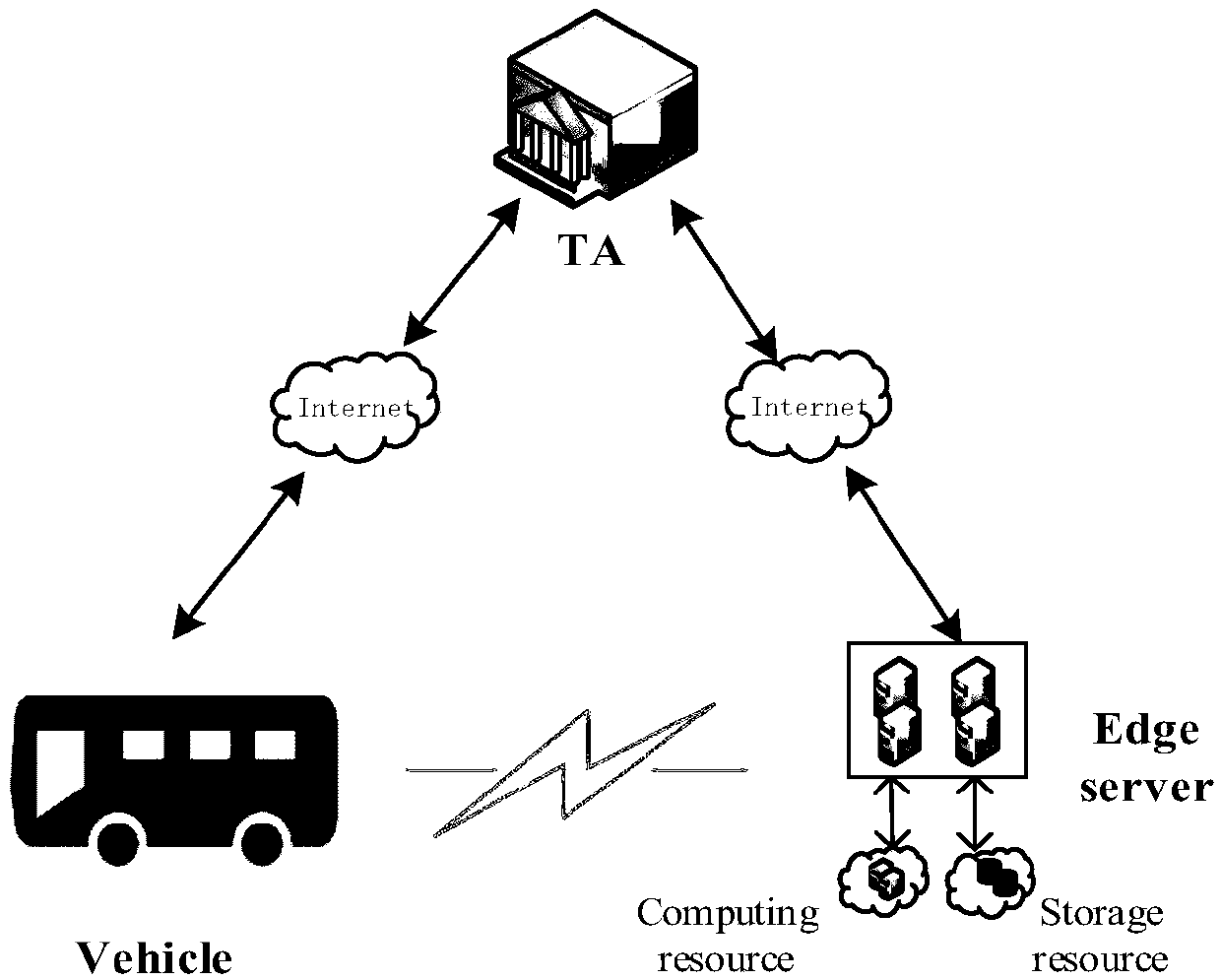
A message authentication method between an unmanned vehicle and a multi-mobile edge computing server
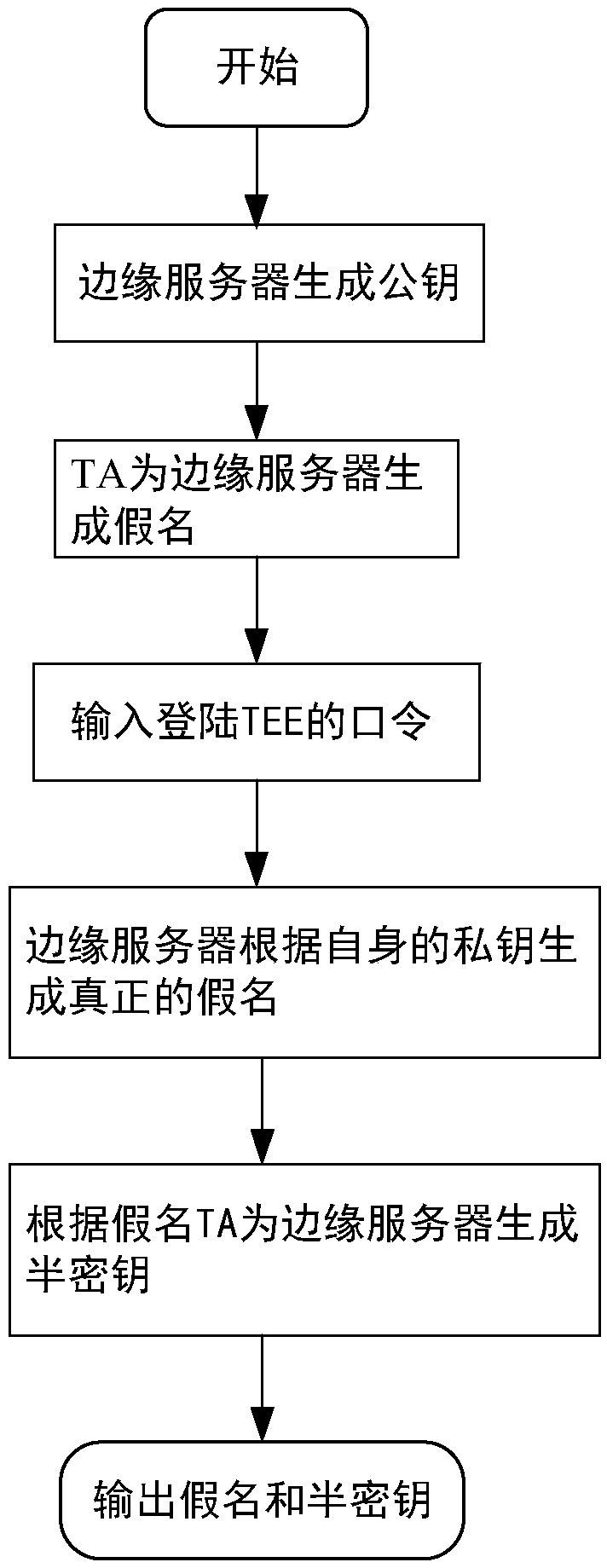
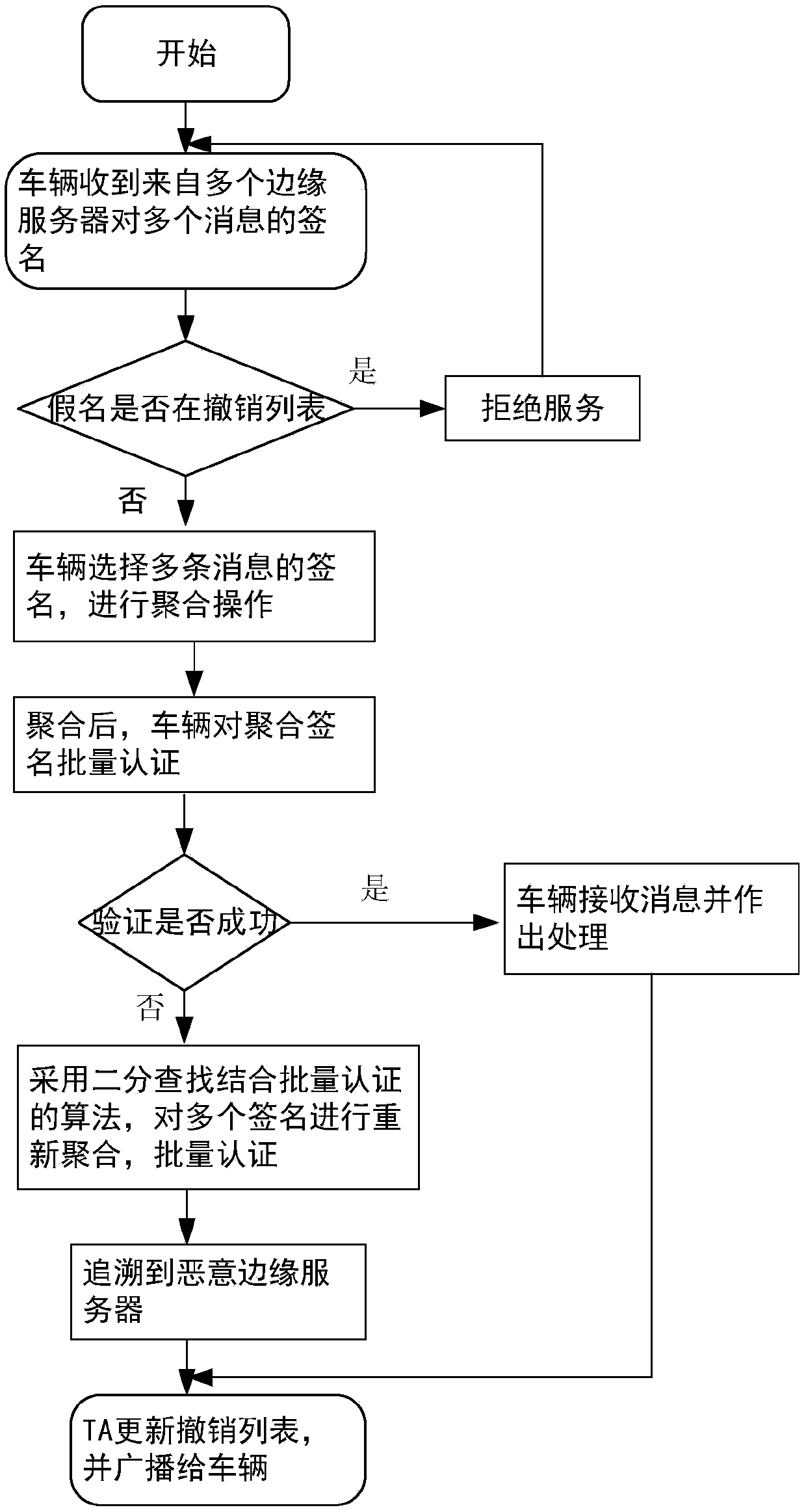
ActiveCN109005538ARealize privacy protectionReduce resource consumptionKey distribution for secure communicationUser identity/authority verificationEdge serverEdge computing
A message authentication method between an unmanned vehicle and a multi-mobile edge computing server is disclosed. The steps are system parameter generation, pseudonym generation for a mobile edge computing server and semi-key extraction, and authentication of a message between the mobile edge computing server and the vehicle. The step comprises: the vehicle migrates a large number of calculationor stored tasks to the mobile edge computing server, the mobile edge computing server performs ring signature on the message, and the vehicle authenticates the message in batch. The invention introduces the edge computing into the traditional vehicle-mounted ad hoc network, and the vehicle can migrate the computing or storage tasks to the edge server to execute instead of sending them to the cloudend for centralized processing. In the signature part of the invention, ring signature is combined with pseudonym, and the application of ring signature effectively protects the privacy of mobile edge computing server and traces the malicious mobile edge computing server through pseudonym.
Owner:ANHUI UNIVERSITY
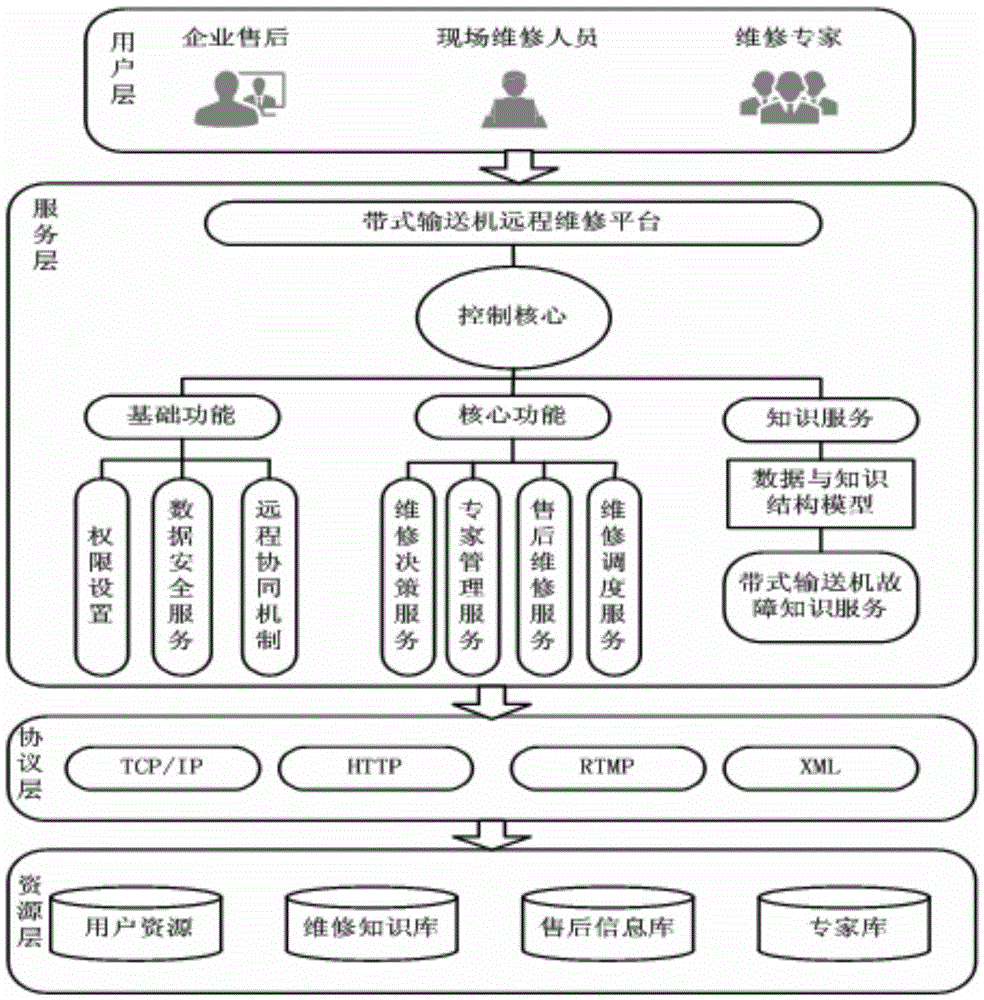
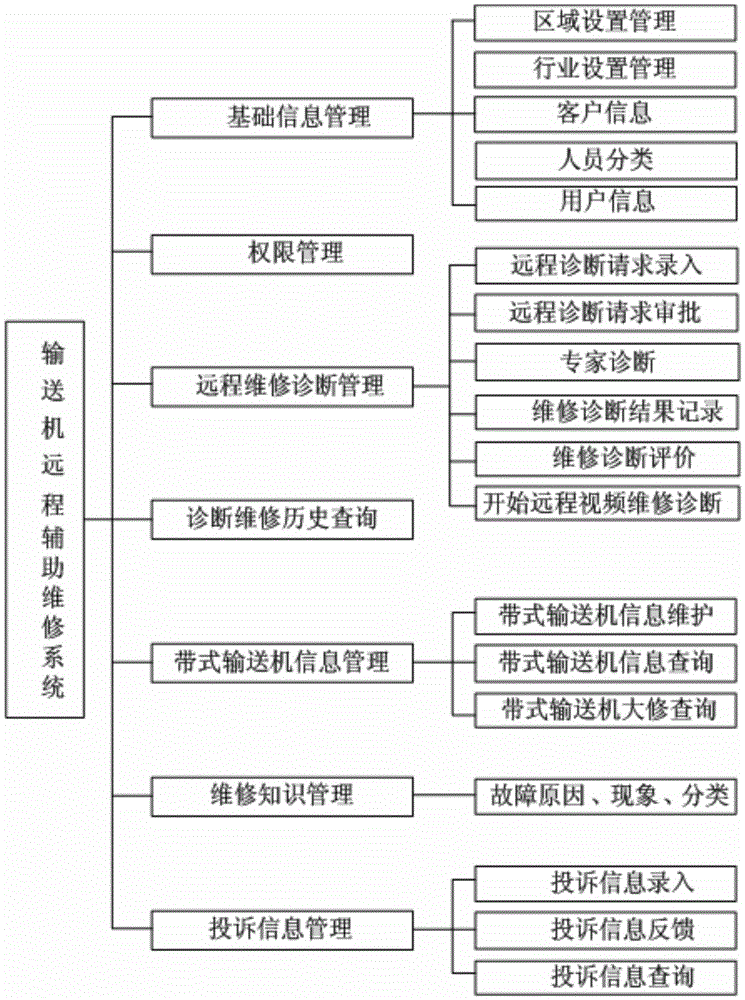
Belt conveyer remote video maintenance auxiliary diagnosis system
InactiveCN105578132AReduce economic lossSolve the problem of not being able to reach the scene immediatelyClosed circuit television systemsSelective content distributionTablet computerWeb service
The invention discloses a belt conveyer remote video maintenance auxiliary diagnosis system comprising a server, a client side and an equipment management database. The server comprises a web server and a streaming media server. The client side comprises an industrial tablet computer, a macro-focus camera, a 3G network and a standby battery. The whole system is based on a B-S mode. The client side logs in the system through a browser and enters a conference room to request for remote assistance according to set permissions. Onsite equipment situations are acquired by the macro-focus camera and transmitted to the server through the 3G network, and videos are analyzed and equipment is diagnosed by the experts of the server side. The equipment management database provides data support for onsite detection and diagnosis. The web server is the medium of a user side for accessing to the database and the streaming media server. The streaming media server realizes a streaming media service between the Flash client side and the server. The belt conveyer remote video maintenance auxiliary diagnosis system is easy to operate and convenient to use, and interaction of the site and the diagnosis experts can be realized and resource sharing can also be realized.
Owner:XIAN UNIV OF SCI & TECH
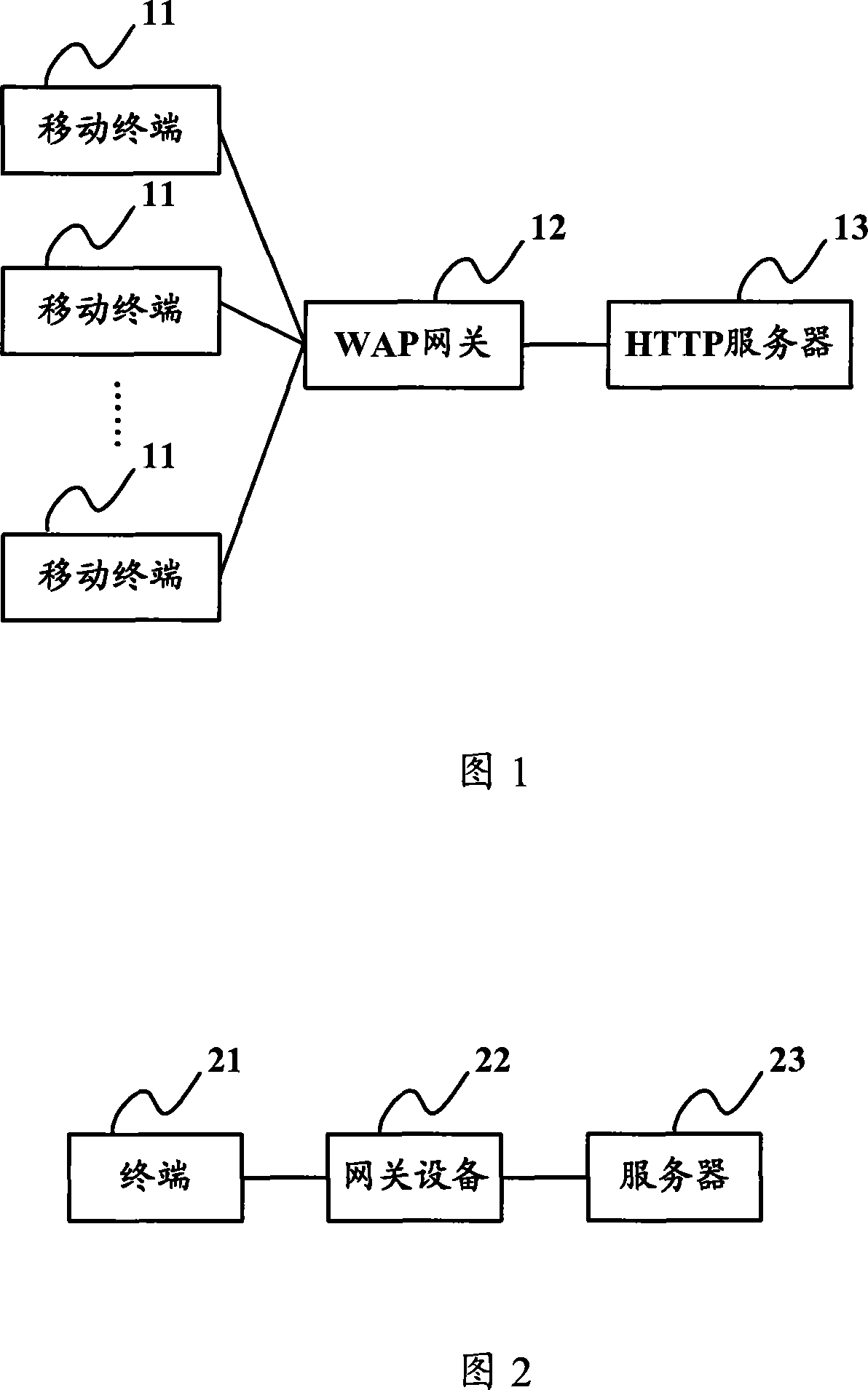
Communication method, system and gateway equipment
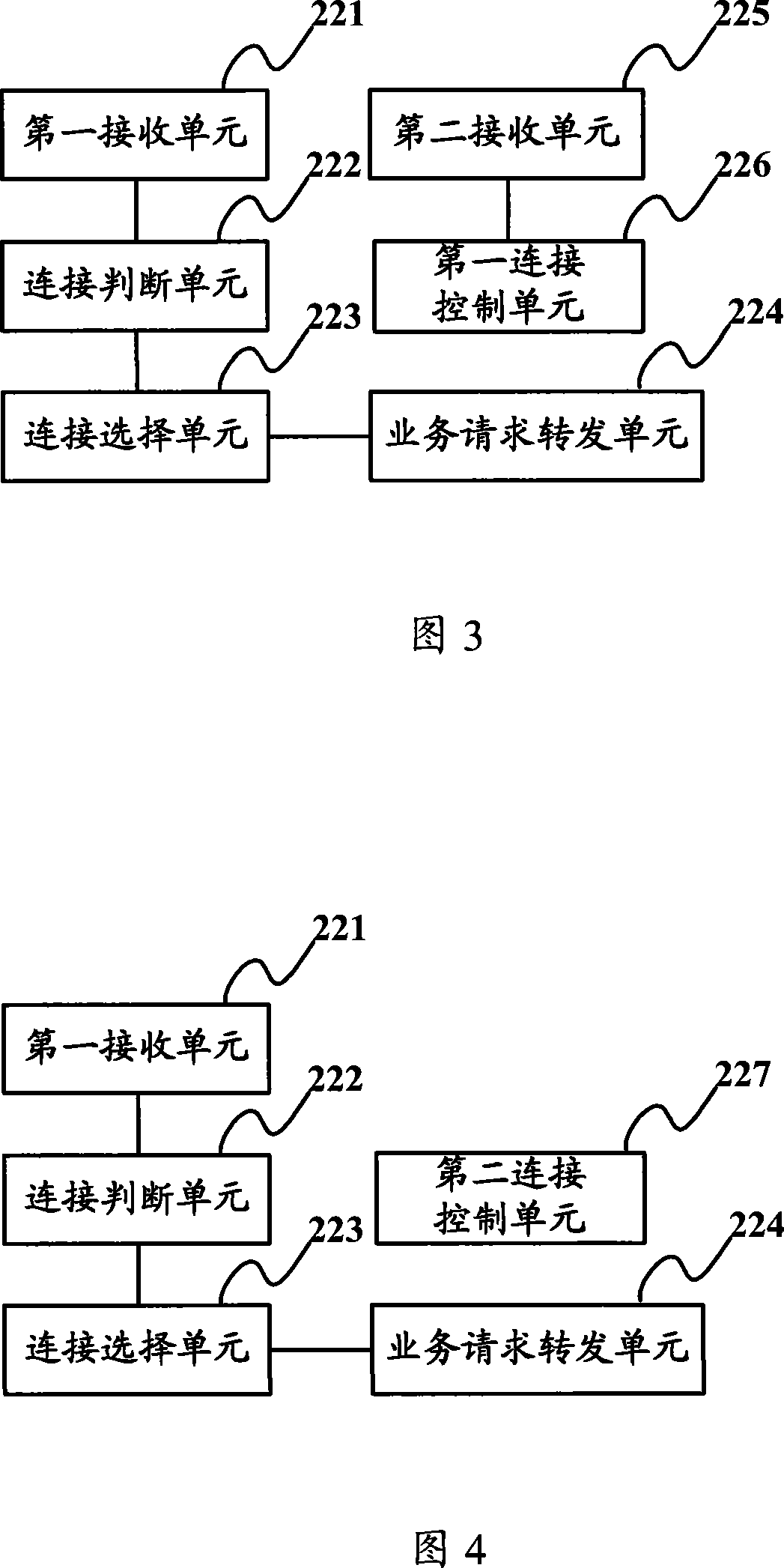
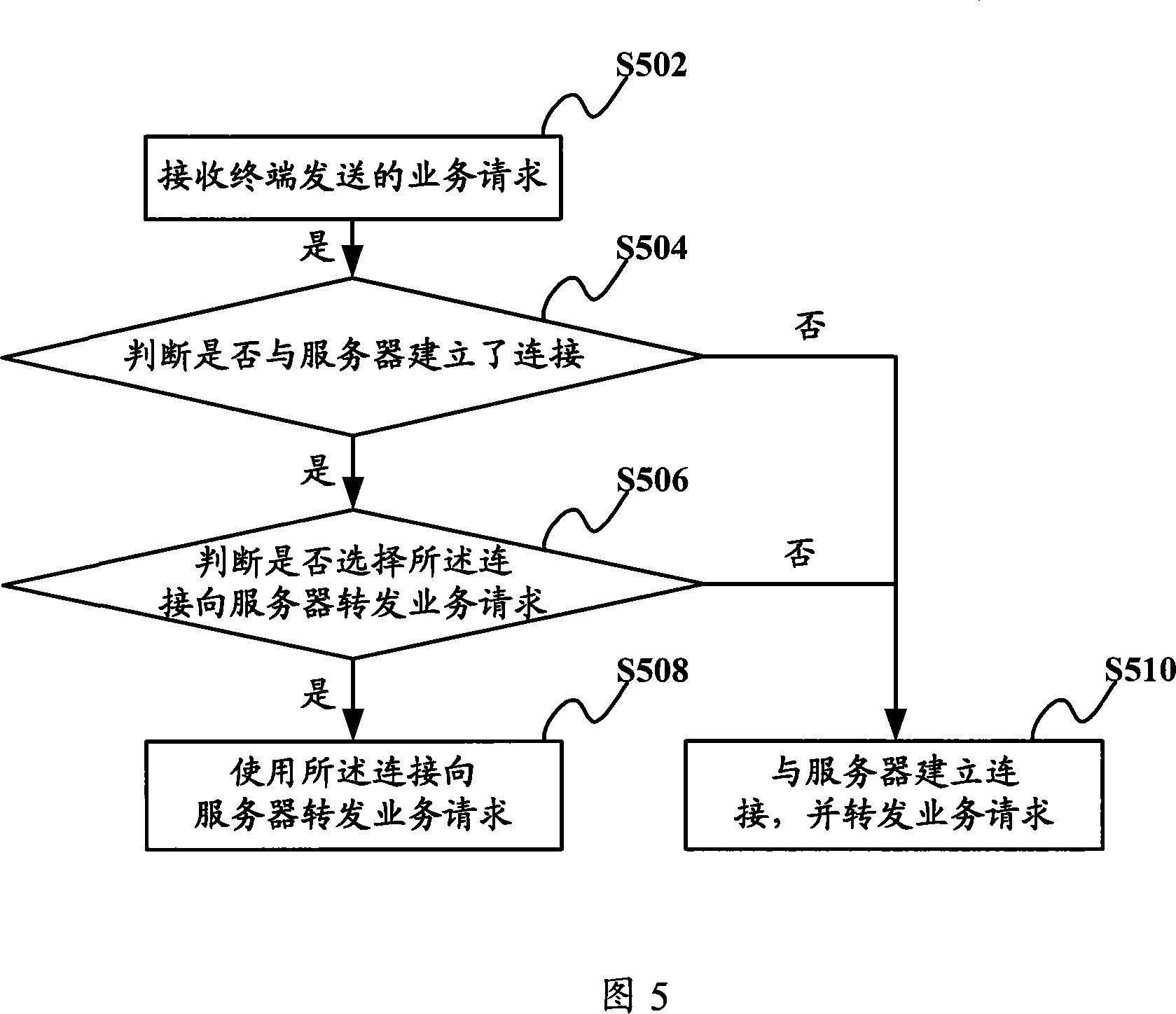
Especially, being related to a communication method, system and gateway device, the invention implements communication between gateway device and server through mode of connection multiplexing, as well as reduces number for building connection between gateway device and server, and reduces number of connection between gateway device and server so as to raise handling property of gateway device, lighten load of server, and increase use ratio of connected resources. The invention also discloses a communication method, which includes steps: receiving service request including ID of server sent from terminals; based on ID of server, and determining connection having been built with the server; if connection is available in multiplexing, then service request is forwarded to the server through the available connection. The invention also discloses a communication system and a gateway device.
Owner:HUAWEI SOFTWARE TECH
Andriod system-oriented implement method of mobile secure terminal
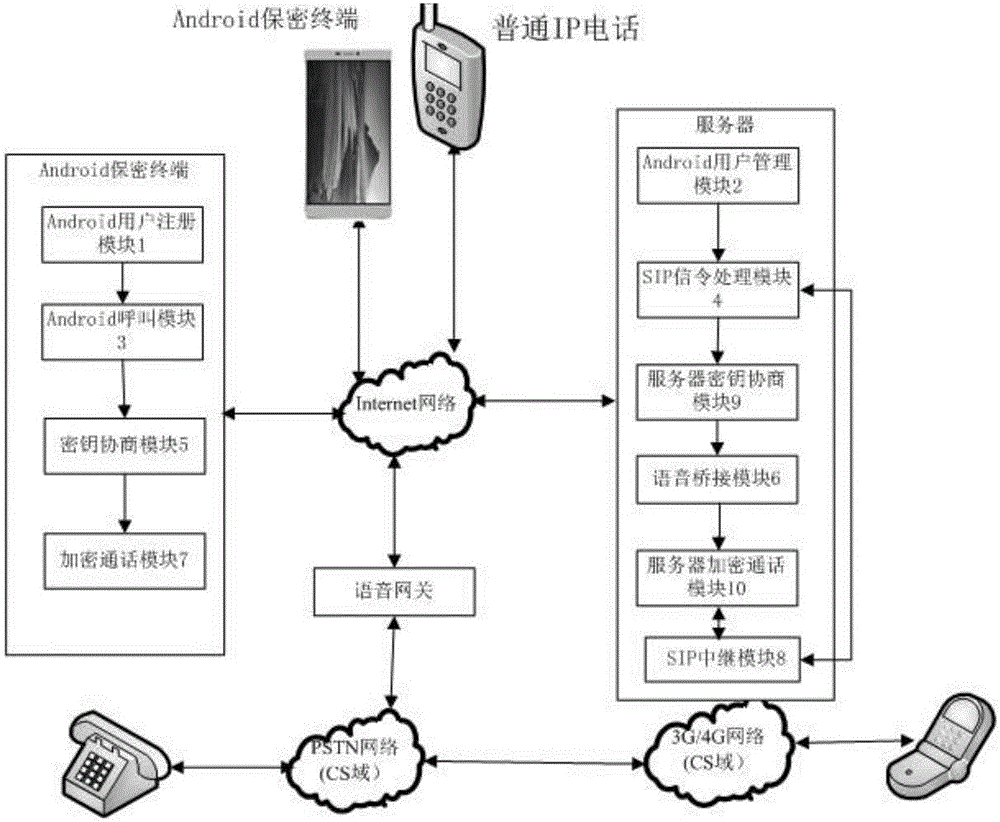
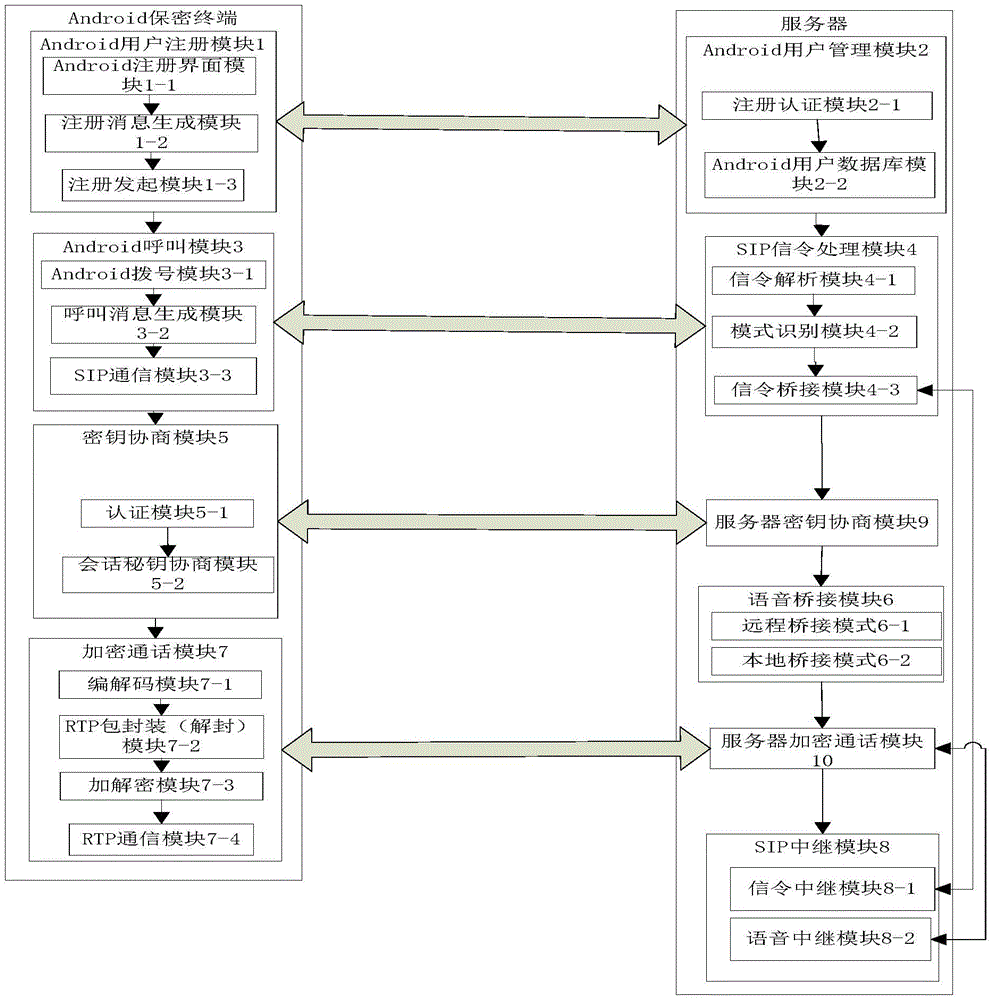
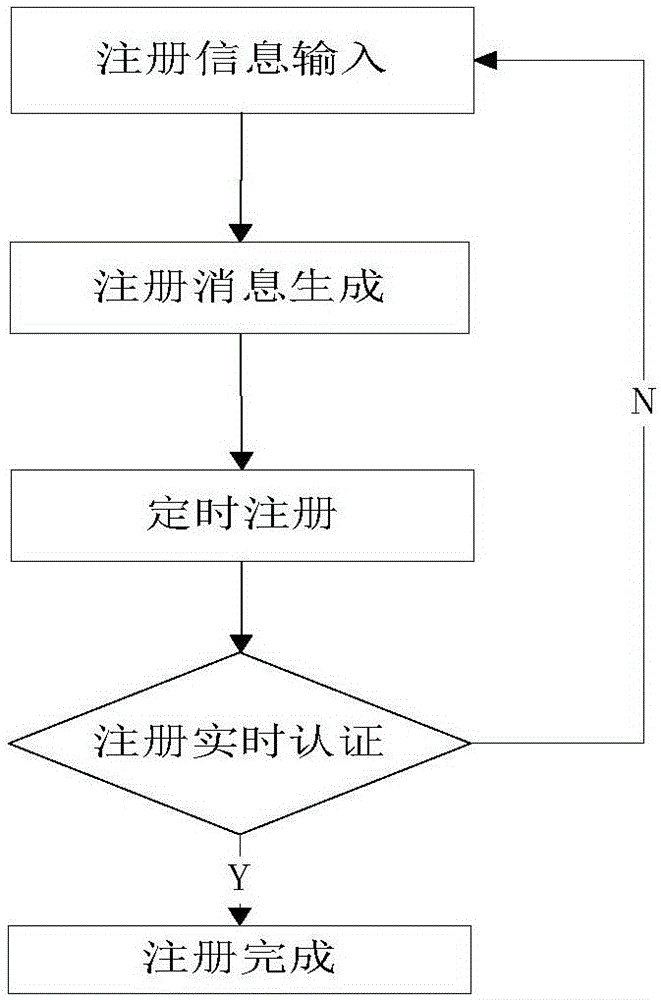
InactiveCN105025475AEnsure safetyDo not interfere with normal callsSecurity arrangementEnd-to-end encryptionVoice communication
The invention discloses an Andriod system-oriented implement method of a mobile secure terminal. The mobile secure terminal comprises an Andriod user registration module, an Andriod user management module, an Andriod calling module, an SIP signaling processing module, a key negotiation module, a server key negotiation module, a voice bridging module, an encrypted conversation module, a server encrypted conversation module and an SIP relay module. The implement method supports two encrypted communication modes: the first one is that one-time pad end-to-end encrypted voice communication for mobile terminals with Andriod operating systems is achieved while the two parties who communicate with each other are both secure terminals, namely the first mode is an end-to-end encrypted communication mode; the second one is that one-time pad encrypted voice communication from the mobile terminal with the Andriod operating system to a server is achieved while only one of the two parties who communicate with each other is the secure terminal, namely the second mode is a halfway encryption communication mode from the secure terminal to the server. The implement method of the invention does not need extra hardware to support, and is friendly in user interface and easy to operate.
Owner:东南大学常州研究院
Implementation method for network sound-searching unit and specific device thereof
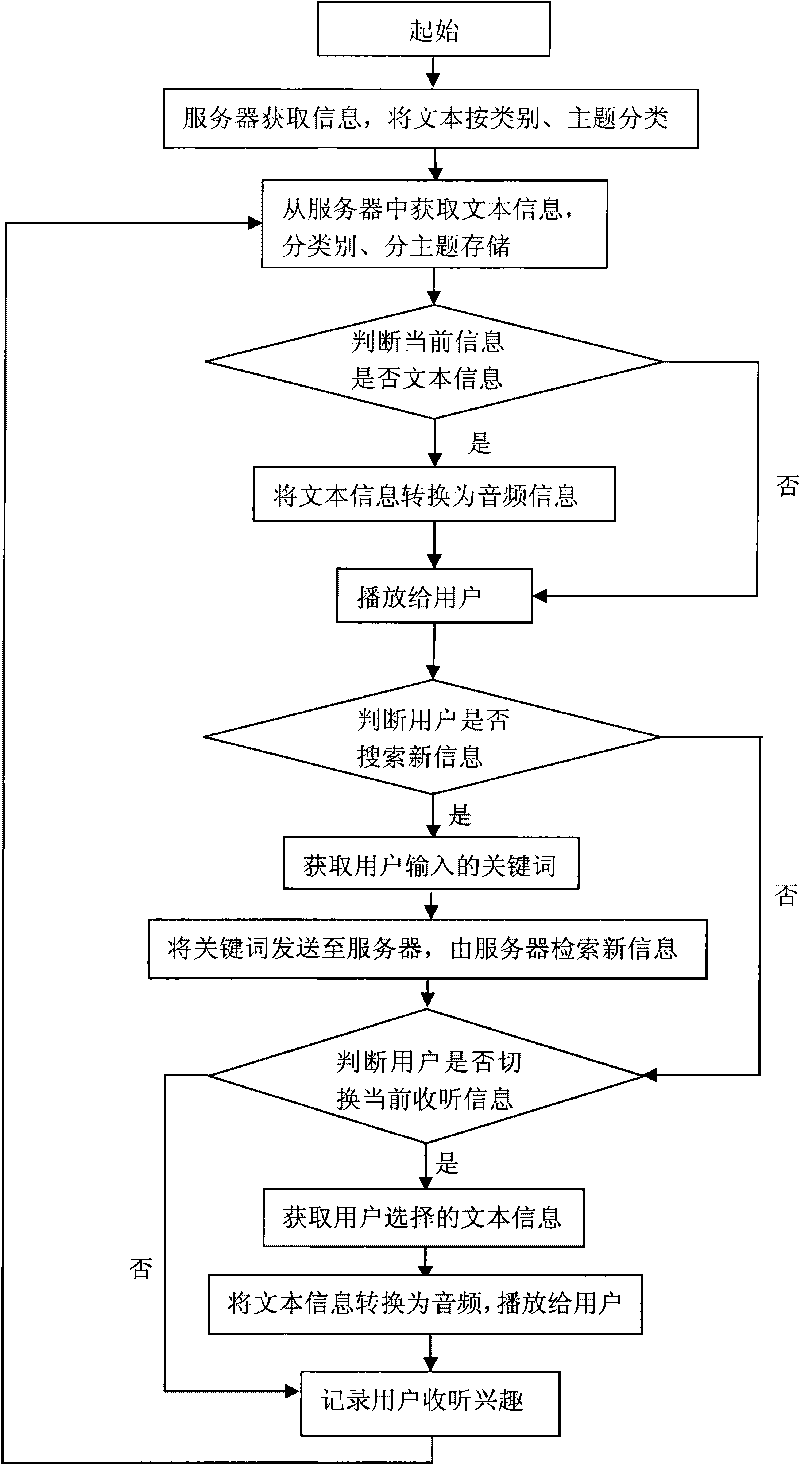
InactiveCN101739437AFast exchangeSpeech recognitionSpecial data processing applicationsUser needsUser input
The invention discloses an implementation method for a network sound-searching unit, which comprises the steps: acquiring information from outside by a server, acquiring the information from the server, judging whether the currently acquired information is text information, converting the text information to audio information, directly playing the audio information to a user; judging whether the user needs to search for new information, acquiring a keyword input by the user, sending the keyword to the server and searching by the server according to the keyword. The network sound-searching unit comprises a network communication module for data exchange with the server, the network communication module is connected with a storage module which is connected with a speech synthesis module, and the speech synthesis module is connected with a playing module; and the network sound-searching unit further comprises an interaction module which transmits the keyword to the server via the network communication module. The implementation method has the advantages of wide information scope involved, fast information exchange speed with the server and great freeness for user to select intrigued information.
Owner:HANGZHOU XINFANG SOFTWARE
Method for load balancing of Web requests based on operating system virtualization
InactiveCN104902001ALoad balancingAvoid overloaded situationsTransmissionVirtualizationOperational system
The invention discloses a method for load balancing of Web requests based on operating system virtualization. The method comprises the following steps of firstly, carrying out collection and normalization of server resource information; secondly, collecting dynamic information of a server and service instances; thirdly, computing final weights of service instance copies of all services according to the server resource information and the periodically-collected dynamic information; and lastly, distributing the requests through weighted round robin. According to the method, the phenomenon that the different service instance copies on one server simultaneously receive a large amount of Web requests due to the lower server load to cause the server overload can be effectively avoided, the load balancing between the service instance copies and the server is implemented, the concurrence capacity of a Web cluster system is improved, and the average response time of the requests is reduced.
Owner:HANGZHOU DIANZI UNIV
Method for safe cross-domain access to SIP video monitoring system
ActiveCN101729871AGuaranteed confidentialityEnsure safetyClosed circuit television systemsTransmissionVideo monitoringAccess method
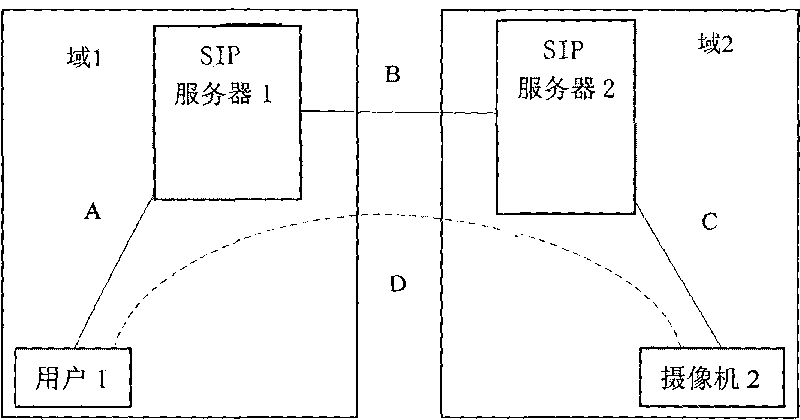
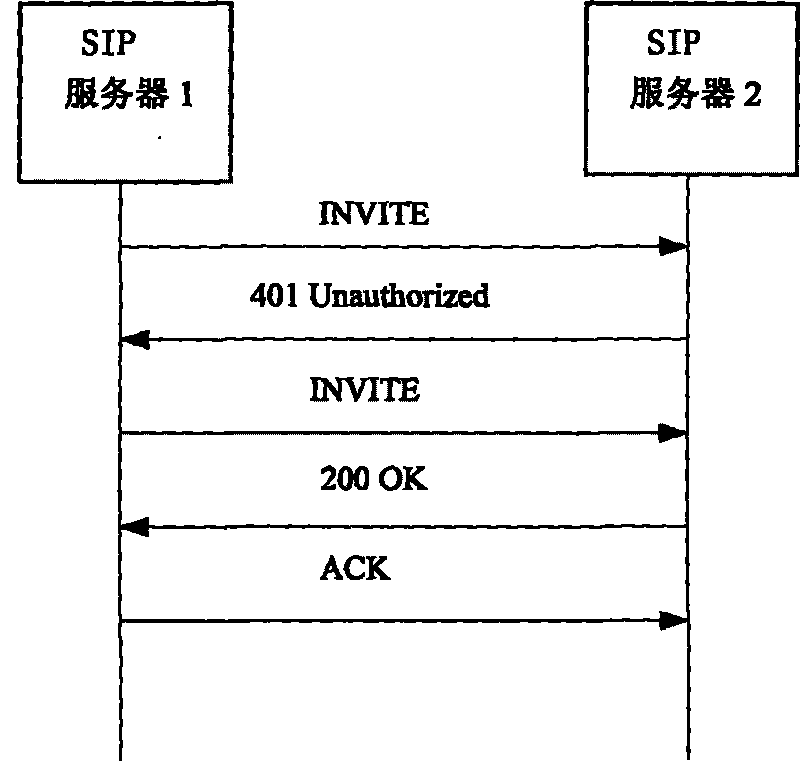
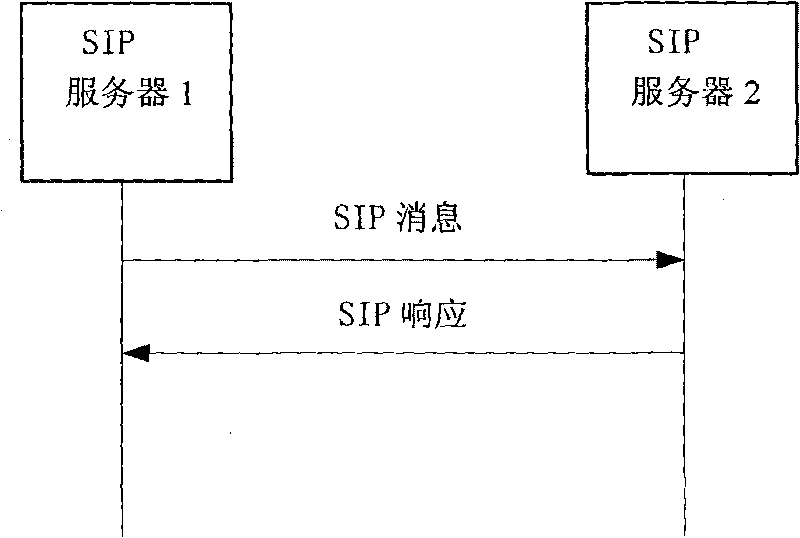
The invention discloses a method for the safe cross-domain access to an SIP video monitoring system. In the method, an INVITE method defined in RFC 3261 is expanded to complete cross-domain route exploration, server safety capacity negotiation and inter-server bidirectional identity authentication and safely transmit two shared keys between servers, and after the route exploration is completed, the digest computing of information on the two shared keys, user identity and the like guarantees the legality of a follow-up cross-domain signaling source so as to guarantee the safety of the cross-domain access of a user. The method solves the safety problem of cross-domain access, prevents phishing server attack and replay attack, solves single sing-on problem of the cross-domain access user and ensures simple safety capacity negotiation and digest authentication-based signaling safety. And due to the high efficiency of the digest computing, the high efficiency of the system is achieved, and the real-time and high application value of the system are guaranteed.
Owner:THE FIRST RES INST OF MIN OF PUBLIC SECURITY +1
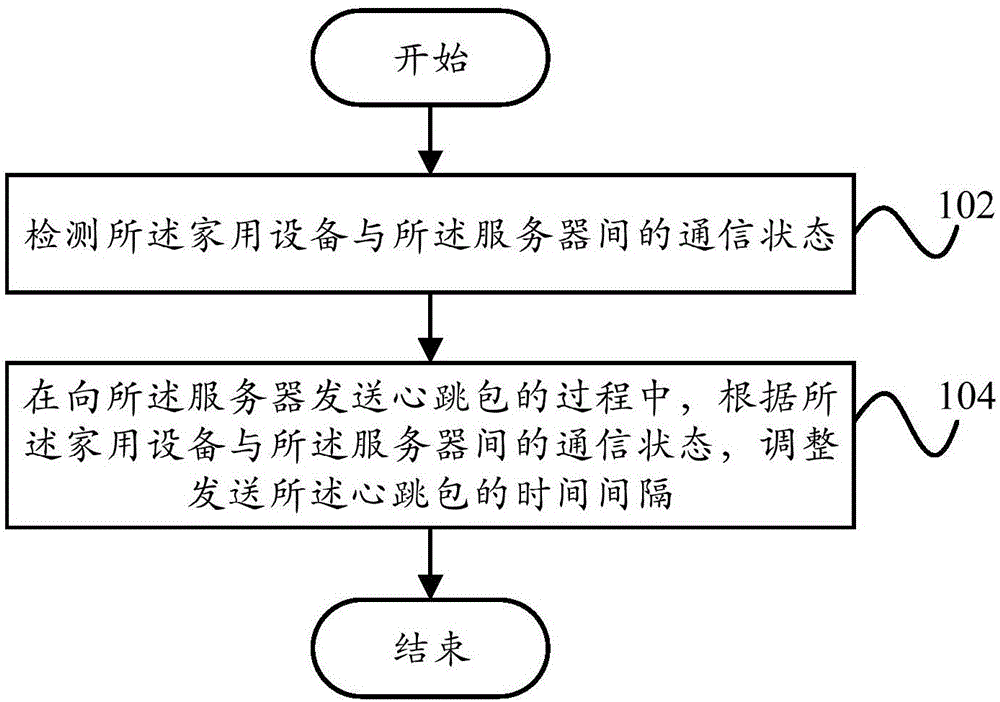
Communication method, communication device and household appliance
InactiveCN106506277AMaintain linkSmooth transmissionData switching networksCommunication deviceTelecommunications equipment
The invention provides a communication method, a communication device and a household appliance. The household appliance can build communication connection with a server. The communication method comprises steps: the communication state between the household appliance and the server is detected; and during a process of sending a heartbeat packet to the server, the time interval for heartbeat packet sending is adjusted according to the communication state between the household appliance and the server. Through the technical scheme of the invention, the time interval for heartbeat packet sending can be adaptively adjusted, and the link between the household appliance and the server is maintenance to a larger degree.
Owner:GD MIDEA HEATING & VENTILATING EQUIP CO LTD +1
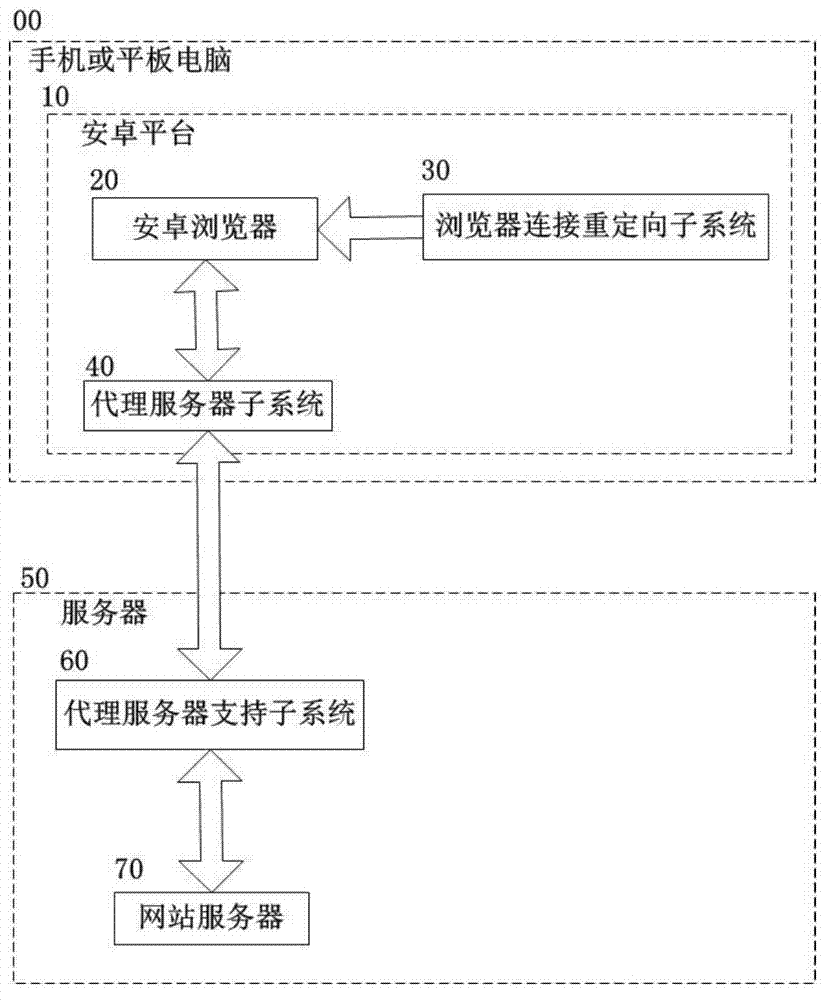
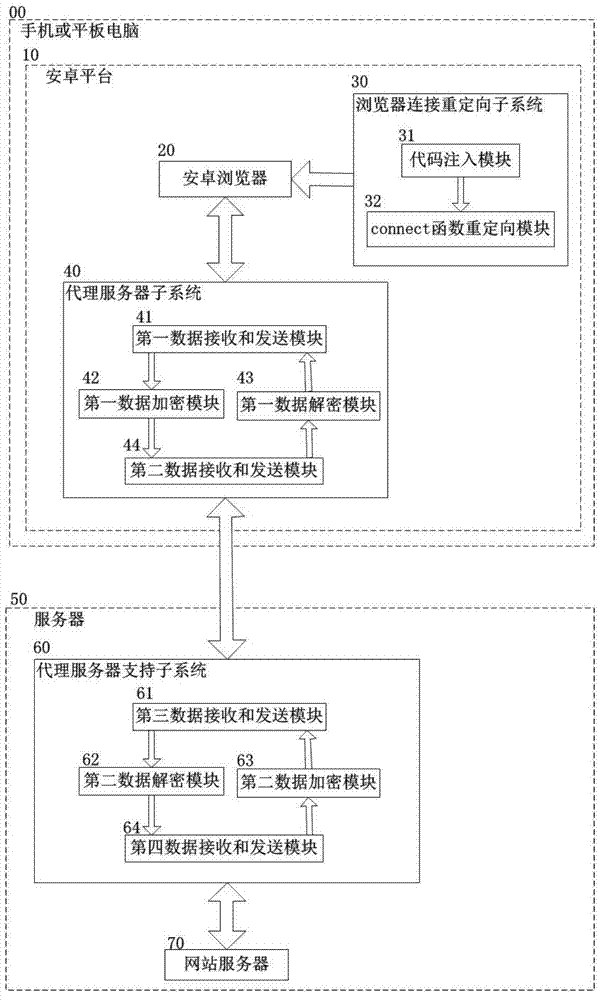
Communication security enhancement agent system between Android platform browser and website server
InactiveCN103179128AImprove securityImprove general performanceTransmissionCommunications securityTablet computer
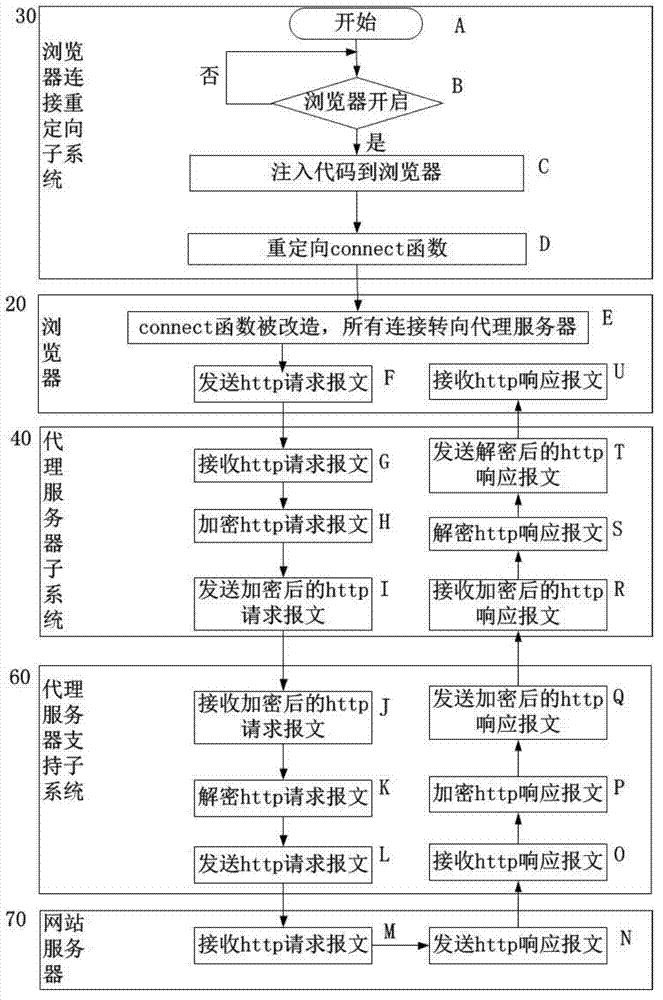
The invention discloses a communication security enhancement agent system between an Android platform browser and a website server, and belongs to the technical field of computer and information security. The communication security enhancement agent comprises a handset or a flat computer and a server which are mutually communicated, wherein an Android platform arranged on the handset or the flat computer comprises the Android browser and is provided with a browser connecting redirection subsystem and an agent server subsystem; the server comprises the website server and is provided with an agent service support subsystem; and the browser connecting redirection subsystem, the Android browser, the agent server subsystem, the agent server support subsystem and the website server are sequentially communicated. The communication security enhancement agent system disclosed by the invention enhances the security under the condition without influencing user experience by executing a layer of encryption transmission between the browser and the website server, has the advantages of low cost, high generality and flexibility in configuration, can provide the security service with different intensities by regulating an encryption and decryption algorithm and is suitable for the secure communication process between a browser and a server of an Android operation system.
Owner:STATE GRID CORP OF CHINA +3
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com