Application virtualization security communication method in autonomous and controllable environment
A technology that applies virtualization and secure communication. It is applied to secure communication devices and key distribution. It can solve the problems of unable to verify the identity of the server and the integrity of the data package, and the protocol is easy to be attacked and stolen by the middleman.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] In order to make the purpose, content, and advantages of the present invention clearer, the specific implementation manners of the present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments.
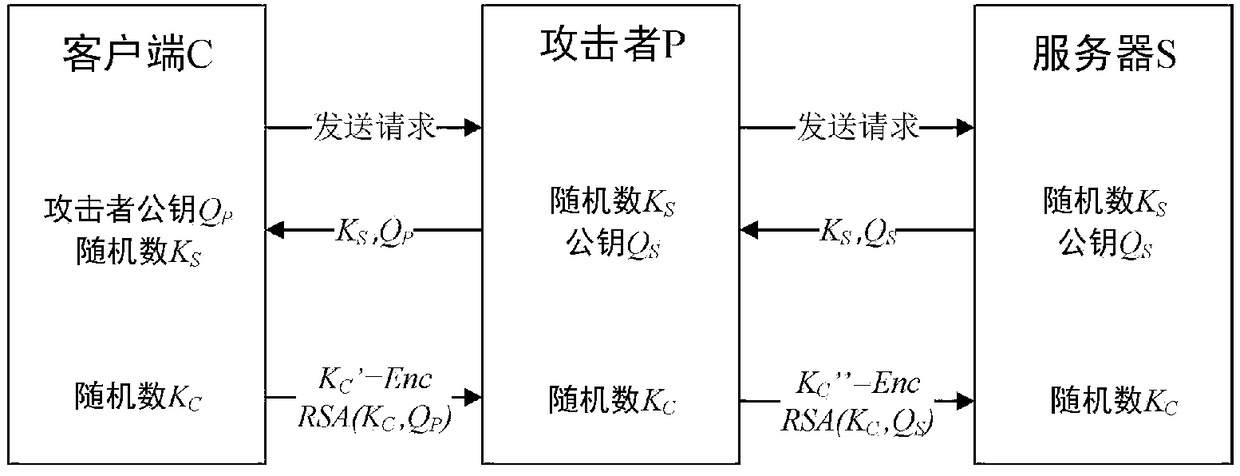
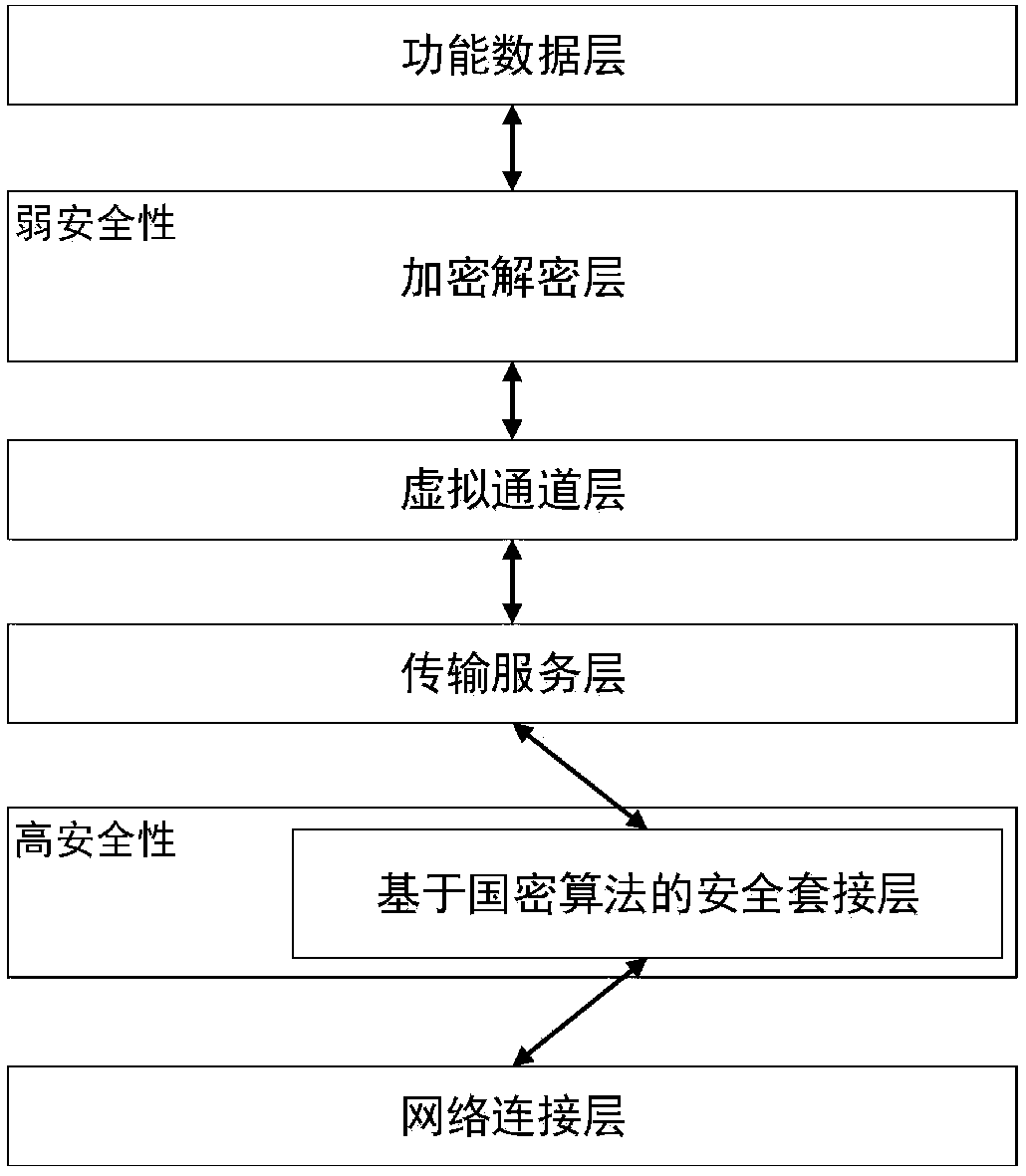
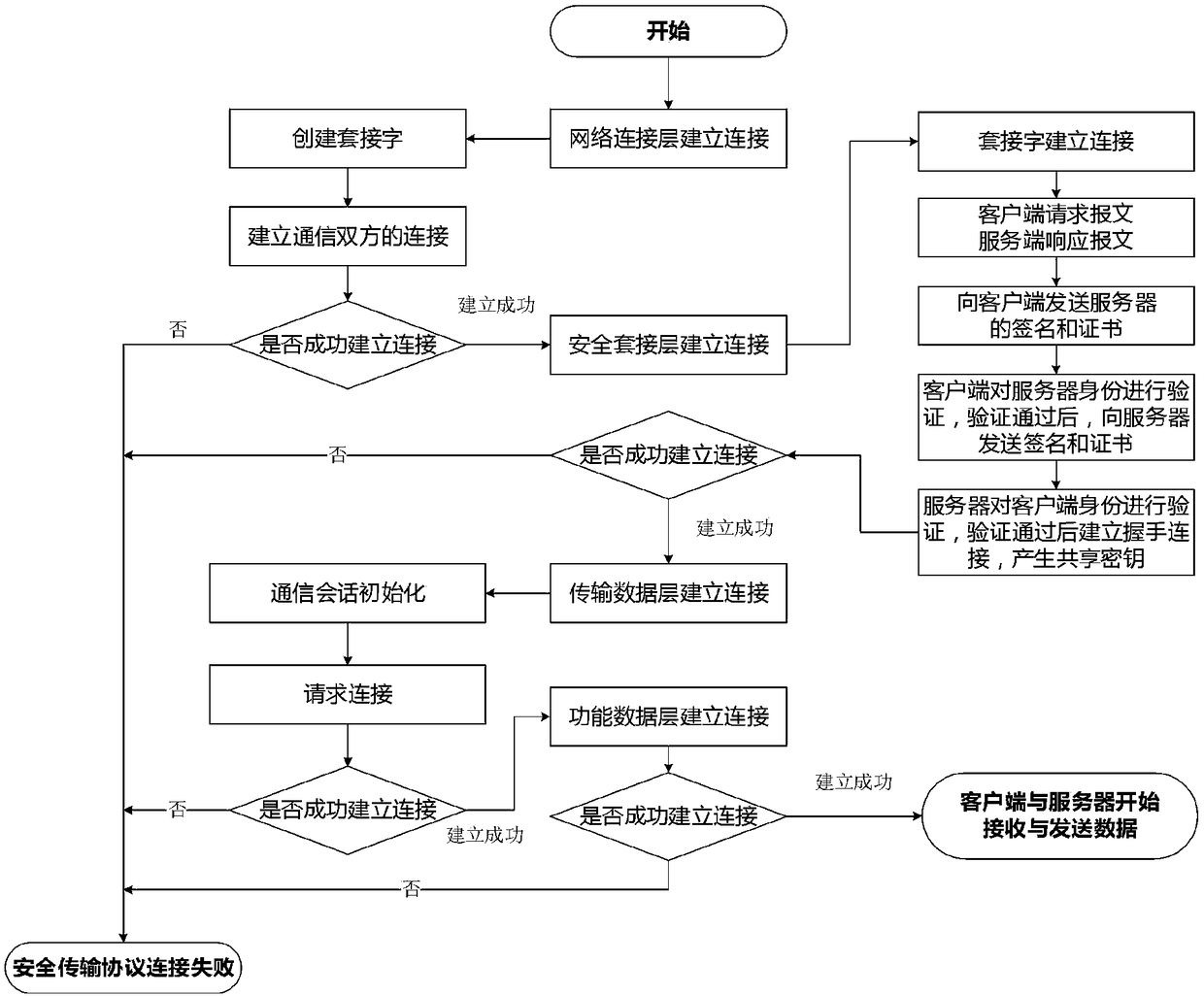
[0036] After analyzing the security mechanism of the existing RDP protocol, it can be seen that the one-way identity authentication mechanism of the RDP protocol cannot resist various types of address spoofing, especially in the process of key exchange. This makes the encryption and decryption layer of the original protocol unable to resist the risks existing in the current network environment and the endless attack software. For its deficiencies, the present invention rebuilds the structure of the original RDP protocol stack, expands a kind of secure socket layer based on domestic commercial cipher suites on the basis of the RDP protocol, and adds the secure socket layer to the network connection layer of the protocol ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com