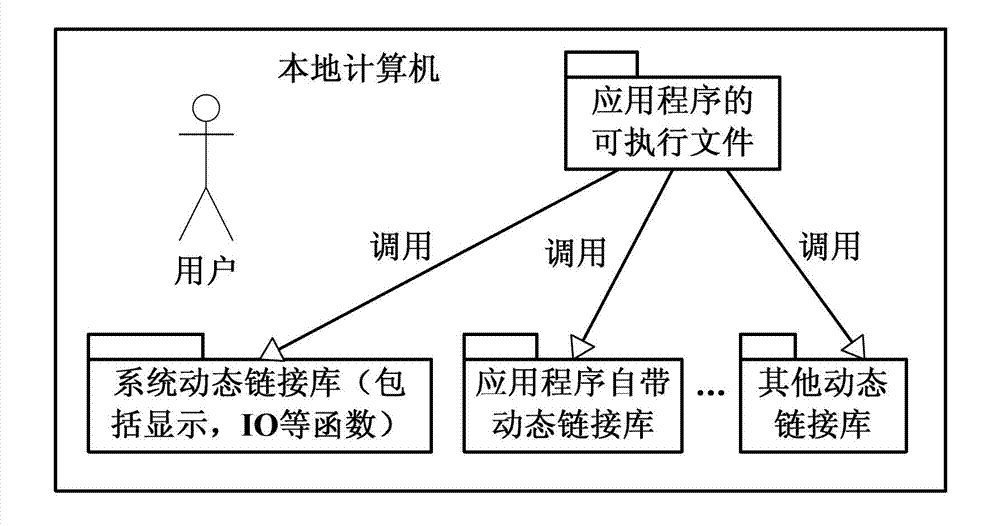
Patents
Literature
98 results about "Application virtualization" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
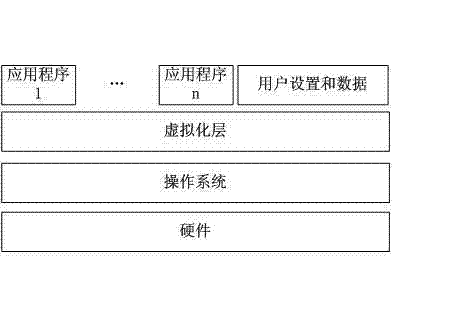
Application virtualization (also known as process virtualization) is a software technology that encapsulates computer programs from the underlying operating system on which it is executed. A fully virtualized application is not installed in the traditional sense, although it is still executed as if it were. The application behaves at runtime like it is directly interfacing with the original operating system and all the resources managed by it, but can be isolated or sandboxed to varying degrees.
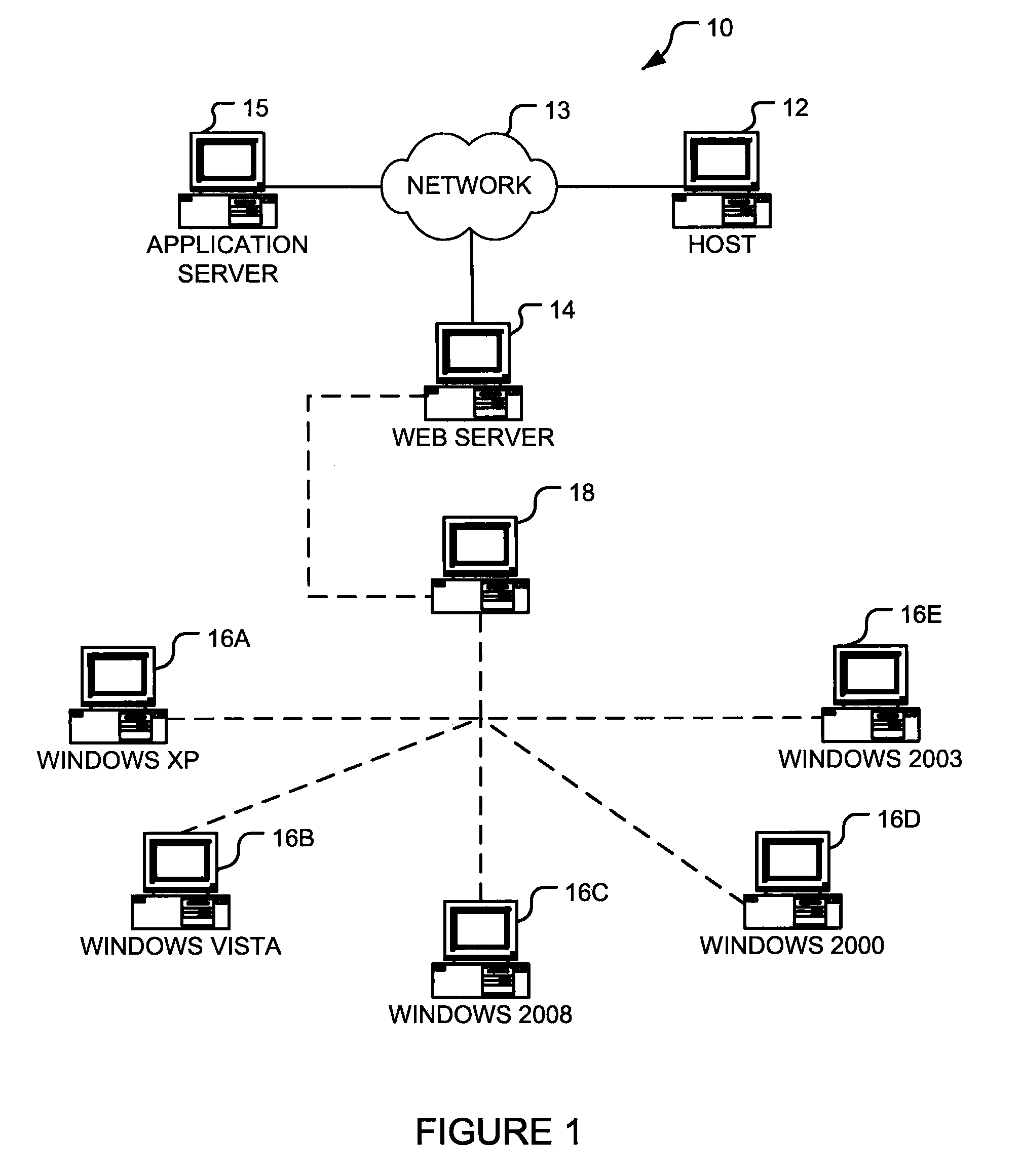
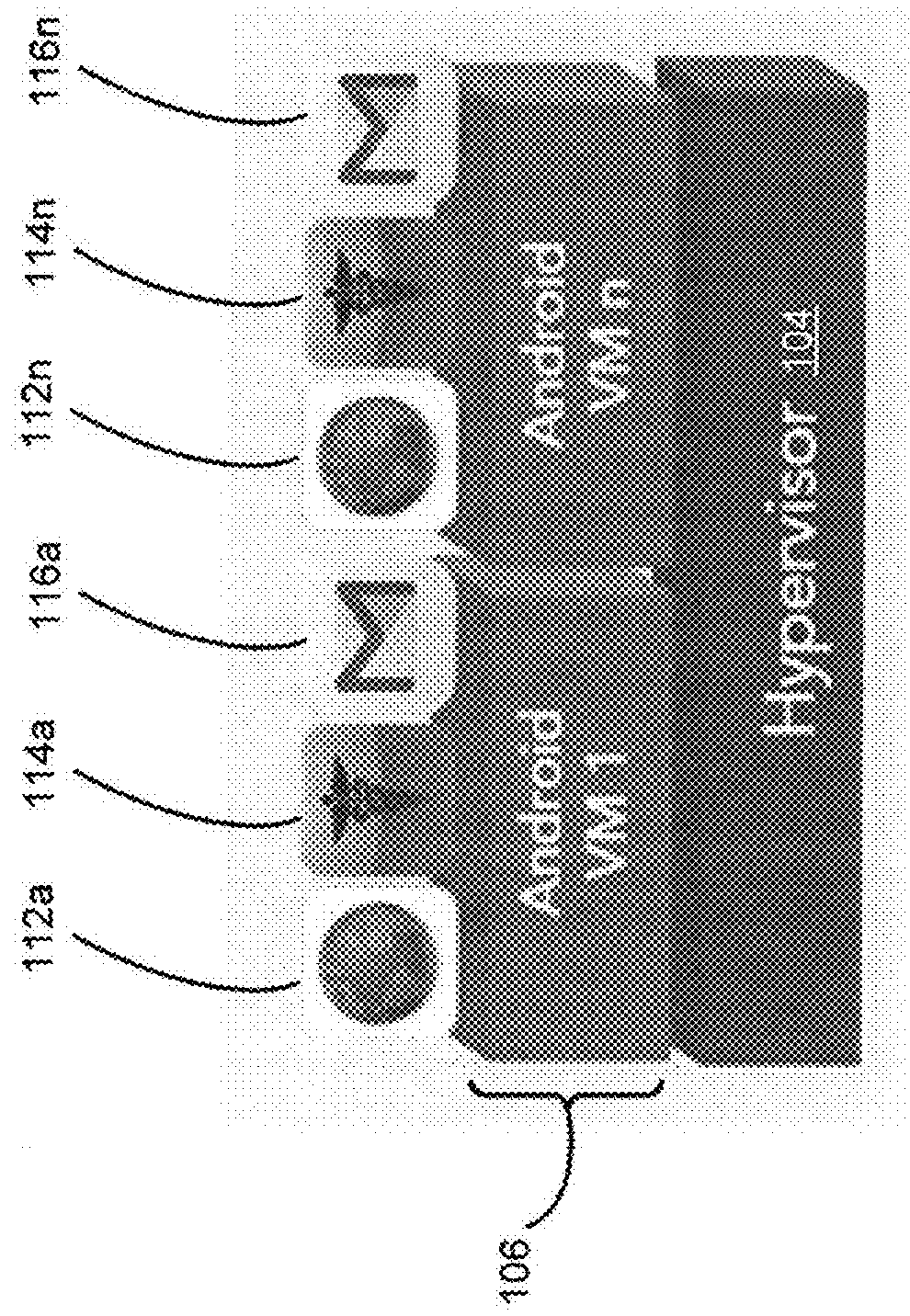
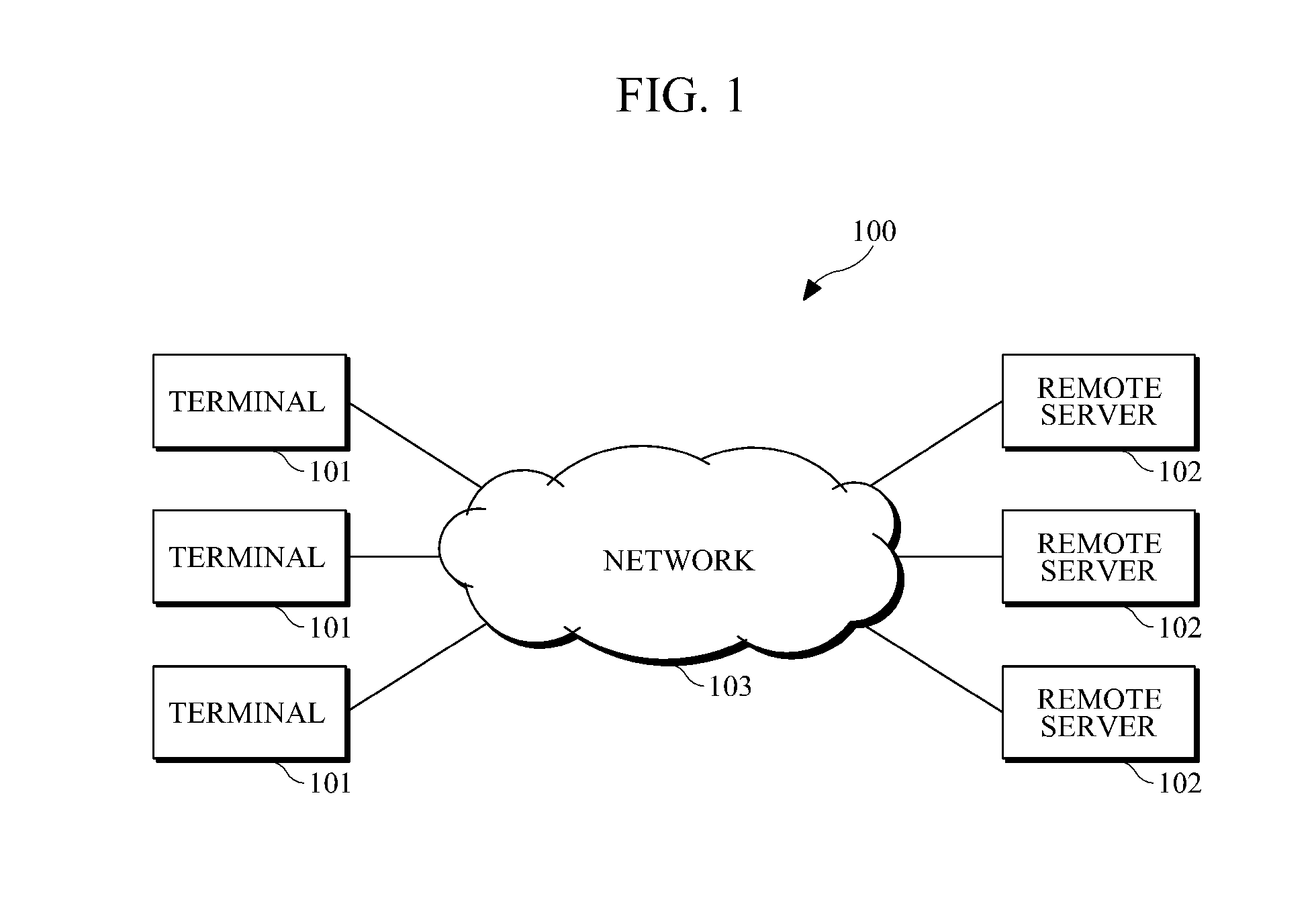
Terminal services application virtualization for compatability
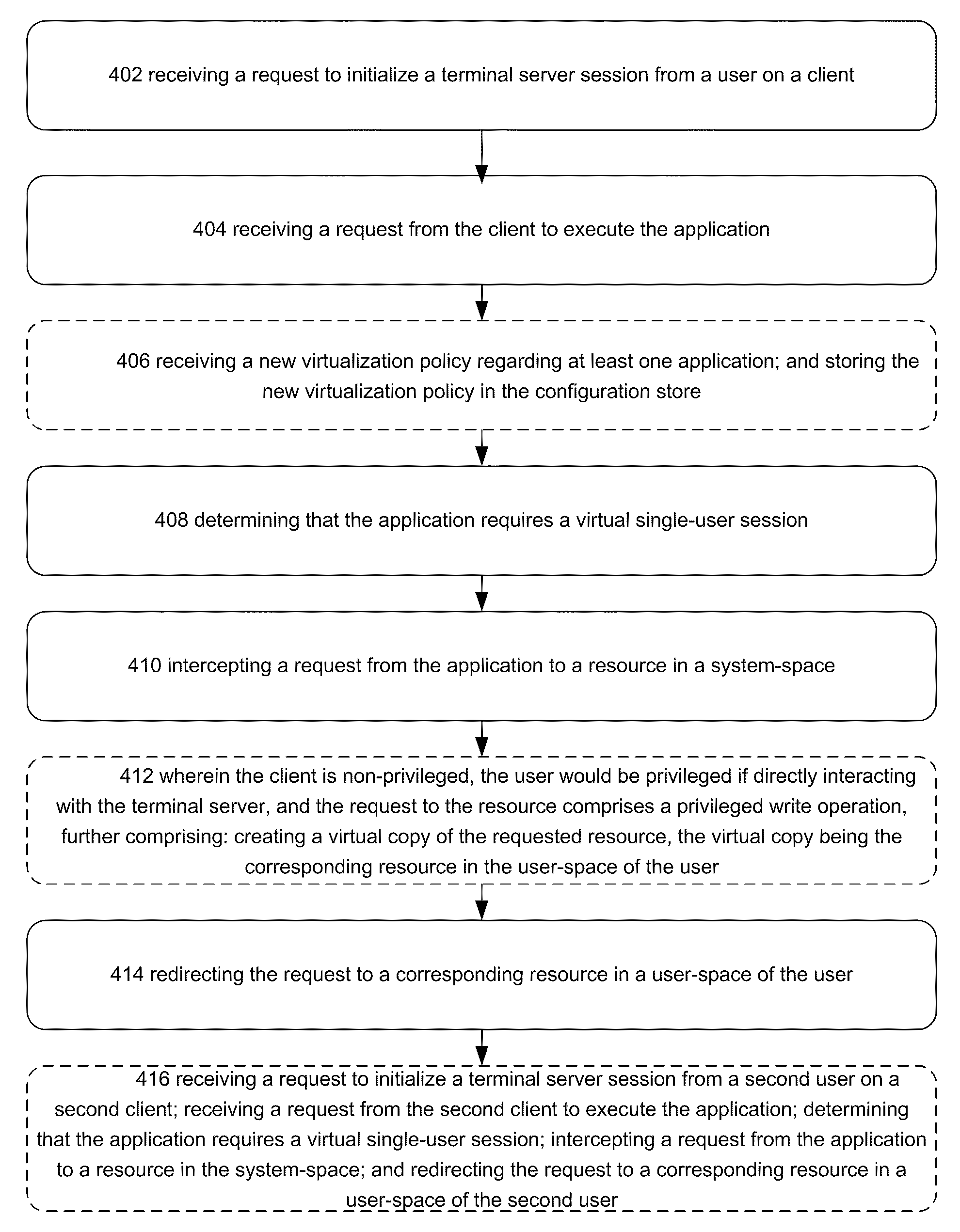
ActiveUS20100318992A1Improve baseline compatibilityLow costMultiple digital computer combinationsSoftware simulation/interpretation/emulationVirtualizationTerminal server
Systems, methods and computer-readable storage media are disclosed for providing a virtual single-user session to a client in a terminal server session. In an embodiment, requests to a resource in the system-space of a system made by an application are intercepted. A determination is made as to whether to virtualize the resource for the application. Where the resource is to be virtualized, a user-specific virtualized resource is created or maintained in user-space and provided to the application.
Owner:MICROSOFT TECH LICENSING LLC
Method and system for virtualization of software applications
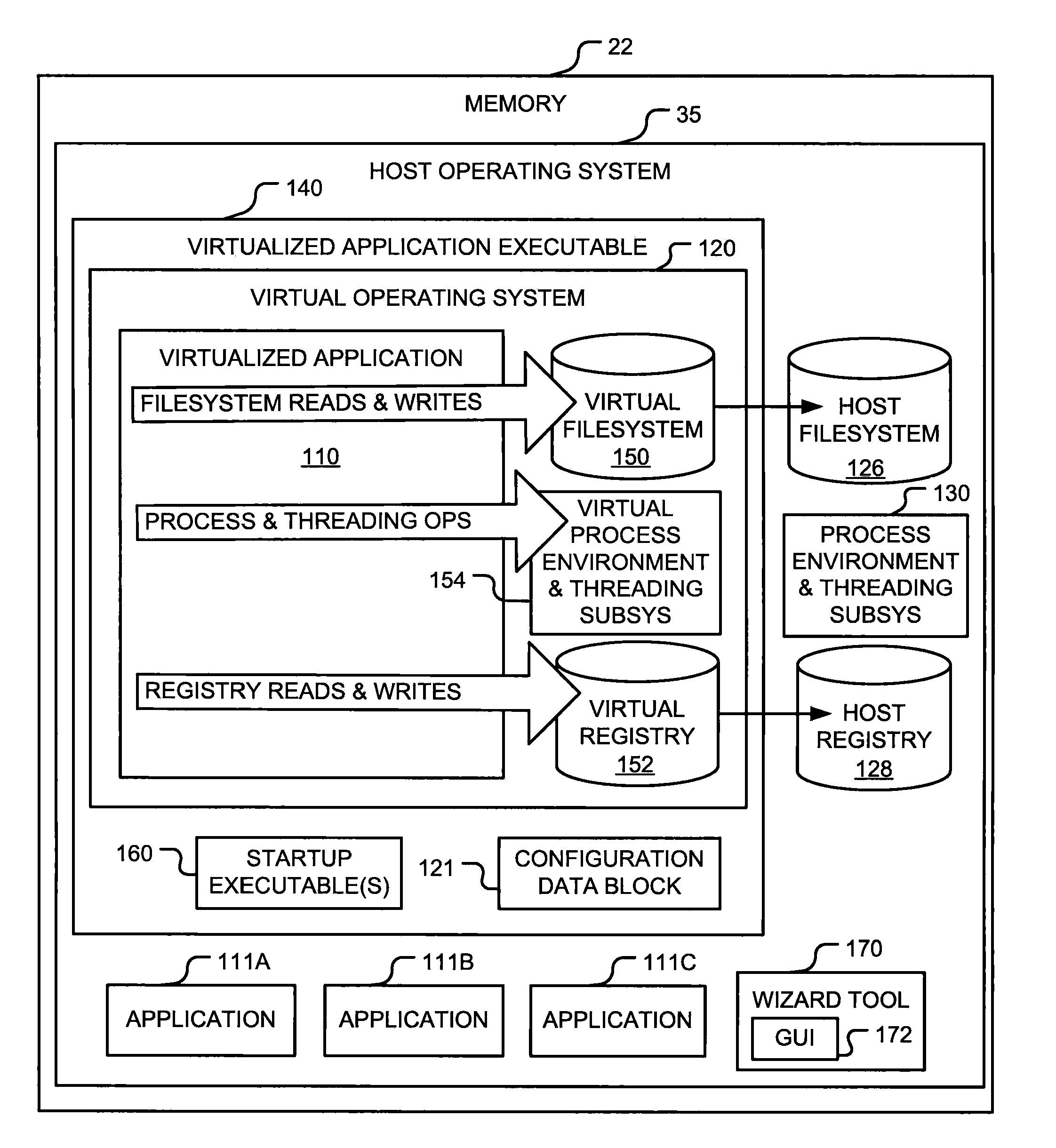
A method of virtualizing an application to execute on a plurality of operating systems without installation. The method includes creating an input configuration file for each operating system. The templates each include a collection of configurations that were made by the application during installation on a computing device executing the operating system. The templates are combined into a single application template having a layer including the collection of configurations for each operating system. The collection of configurations includes files and registry entries. The collections also identifies and configures environmental variables, systems, and the like. Files in the collection of configurations and references to those files may be replaced with references to files stored on installation media. The application template is used to build an executable of the virtualized application. The application template may be incorporated into a manifest listing other application templates and made available to users from a website.
Owner:CODE SYST CORPOATION
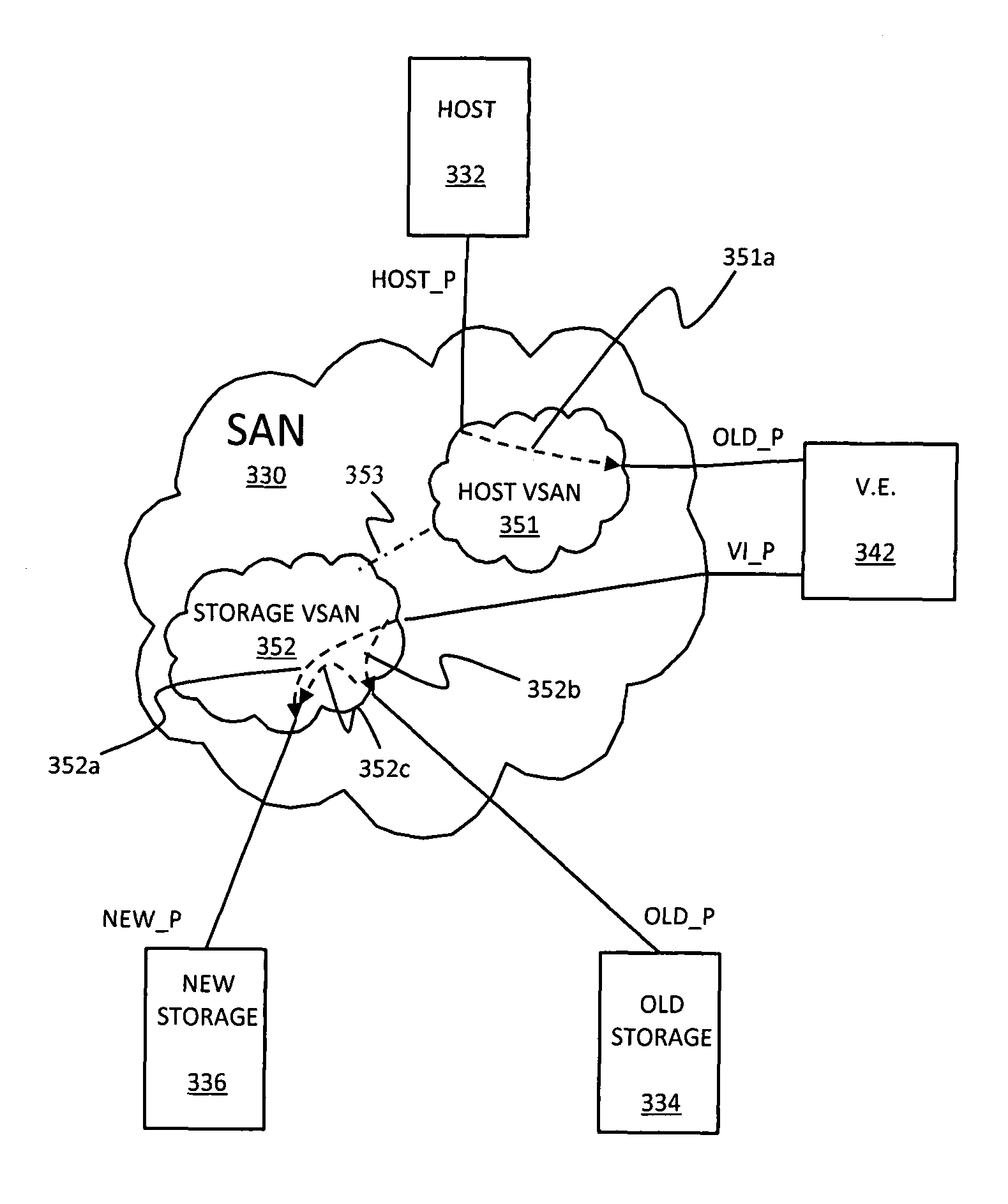
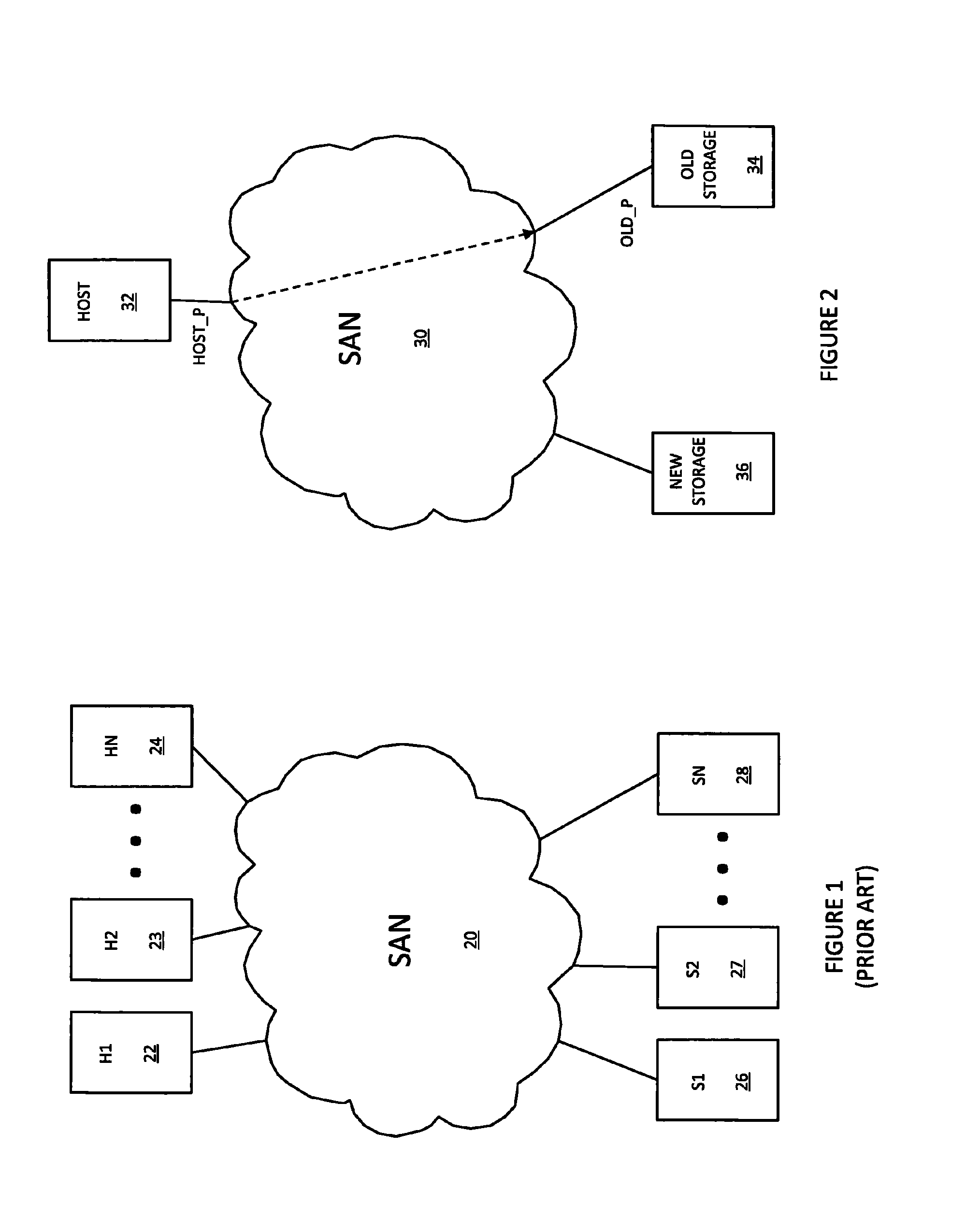
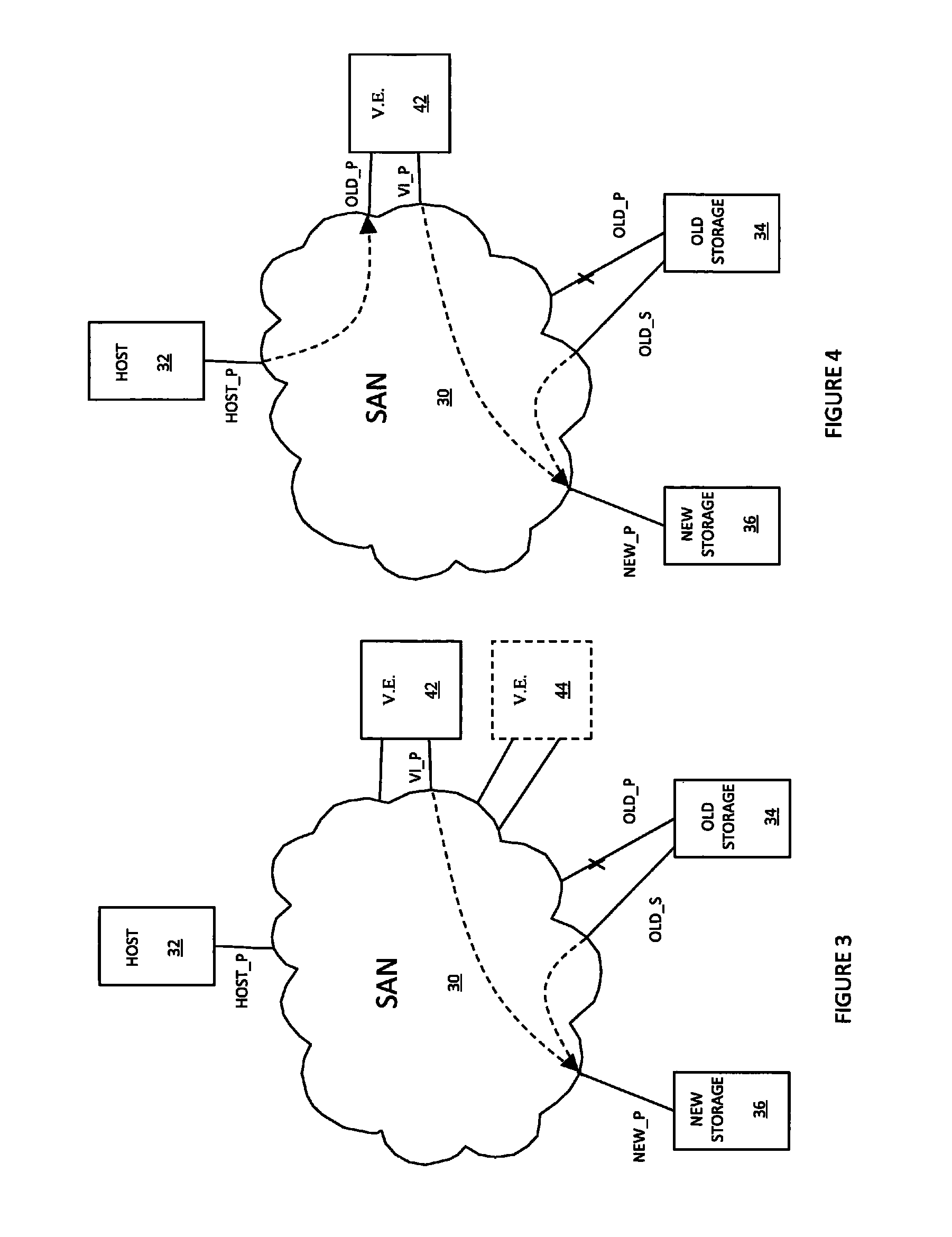
Non-disruptive data mobility using virtual storage area networks with split-path virtualization
ActiveUS8028062B1Computer security arrangementsMultiple digital computer combinationsArea networkName server
A system creates a storage area network (SAN) centric storage virtualization layer in front of storage devices. The system allows data mobility and migration without disruption to the one or more host servers attached to the SAN. Specifically, the host servers are not disrupted when switching I / Os between physical and virtual storage, for example, by taking advantage of WWPN spoofing and Fibre Channel VSAN technology. The use of VSANs effectively allow multiple virtual directors and / or switches to be created within a physical director and / or switches, each with their own separate name server, thereby providing complete isolation from one another. The host-storage pathing information is unchanged as the original physical storage port's WWPNs are spoofed by the virtual storage port. The result is two identical WWPNs within the SAN which is normally disallowed; however, by separating the physical port WWPN into one VSAN and the virtual port WWPN into another, the restriction may be circumvented.
Owner:EMC IP HLDG CO LLC
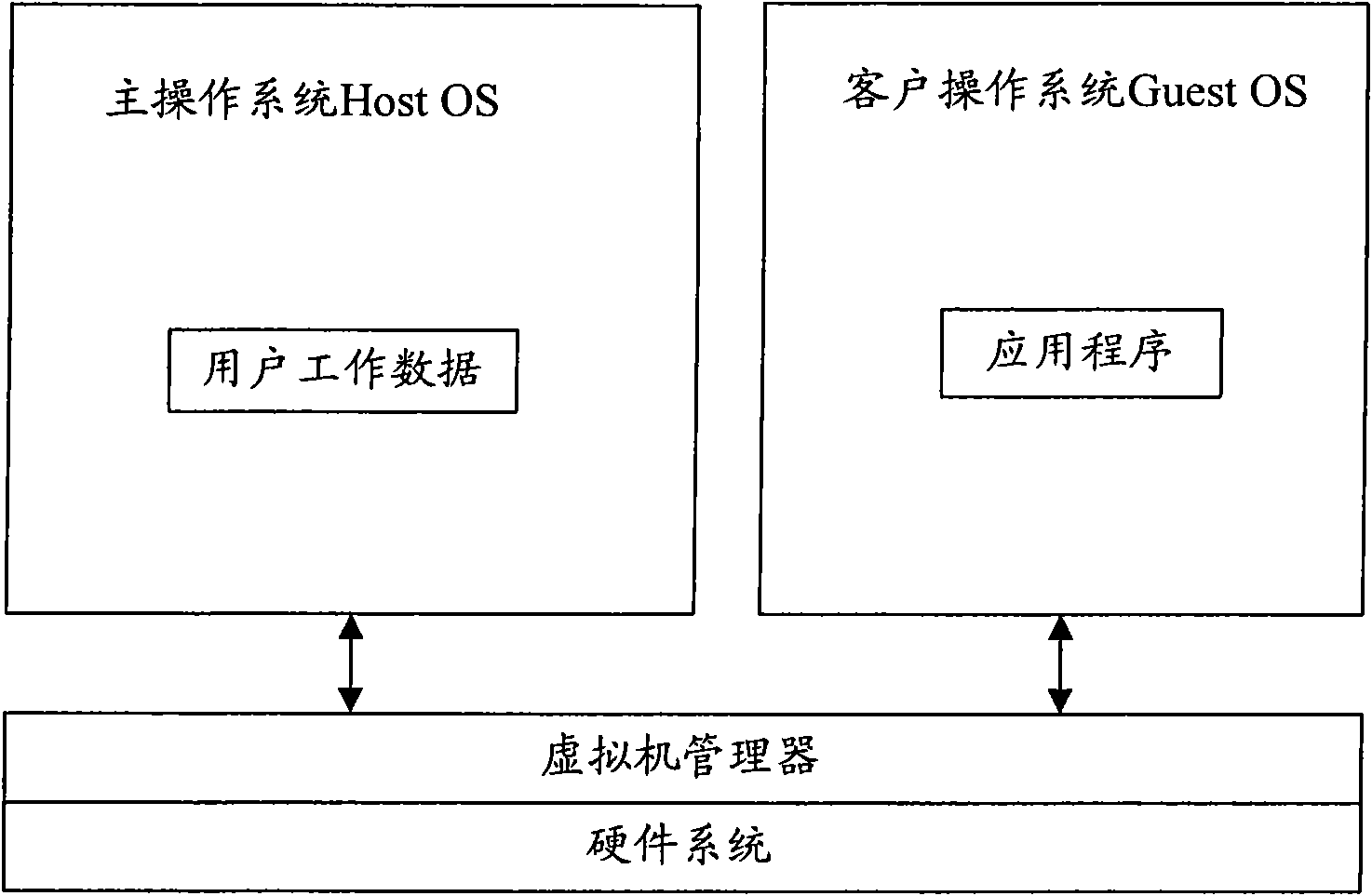
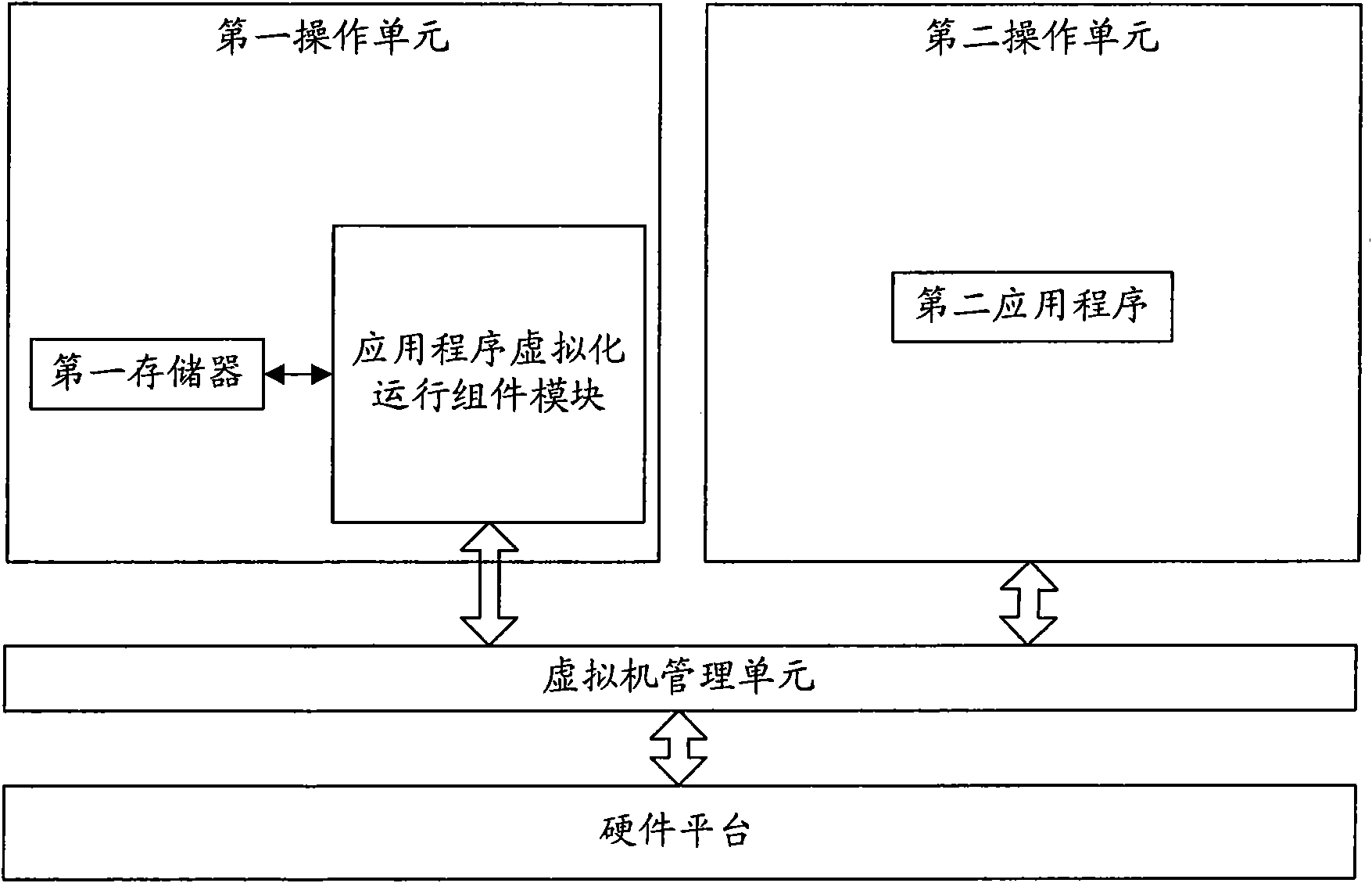
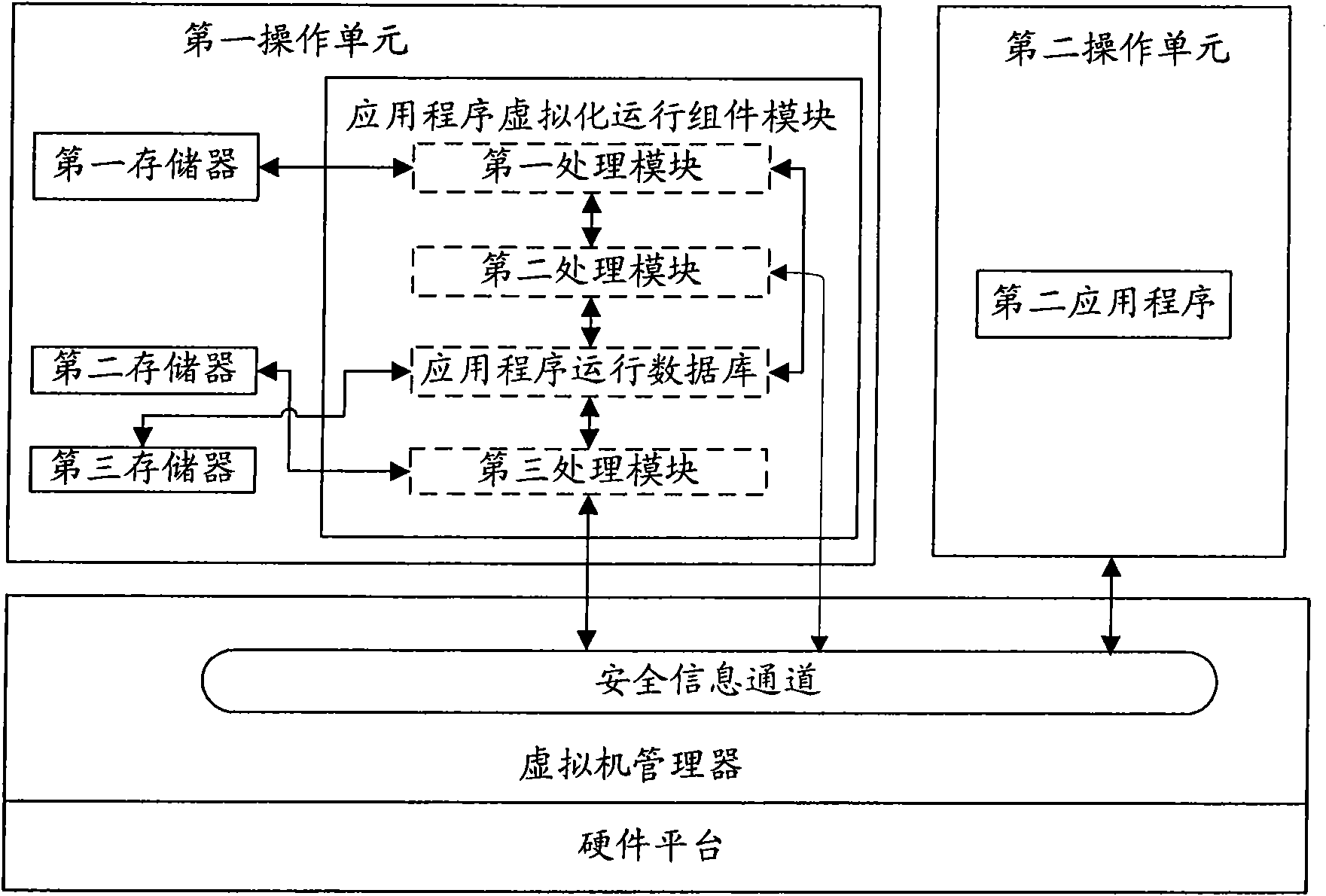
Method for deployment and operation of application in computer and virtual machine environments
ActiveCN101655798ASimplify workMultiprogramming arrangementsProgram loading/initiatingVirtualizationOperational system
The invention provides a device and a method for the deployment and operation of application in computer and virtual machine environments. The device comprises a virtual machine manager, a first operation system, a system operation system and an application virtual operation component module, wherein the second operation system is connected with a first operation system through the virtual machine manager; the first operation system comprises a first storage module for storing an installation file of a first application; the application virtual operation component module is connected with the first storage module and the virtual machine manager respectively and is used for processing installation information during the operation of the first application, the installation information is input into the second operation system through the virtual machine manager, and a second application and an operation environment of the second application are established in the second operation system according to the installation information; and the virtual machine manager acquires a second application reading and writing operation request and feeds a corresponding reading and writing operation result back to the second operation system. The method prevents the transfer of user working data between the operation systems and simplifies the work of the user.
Owner:LENOVO (BEIJING) LTD
Method and apparatus for performing application virtualization
InactiveUS20050005018A1Resource allocationMultiple digital computer combinationsVirtualizationResource utilization
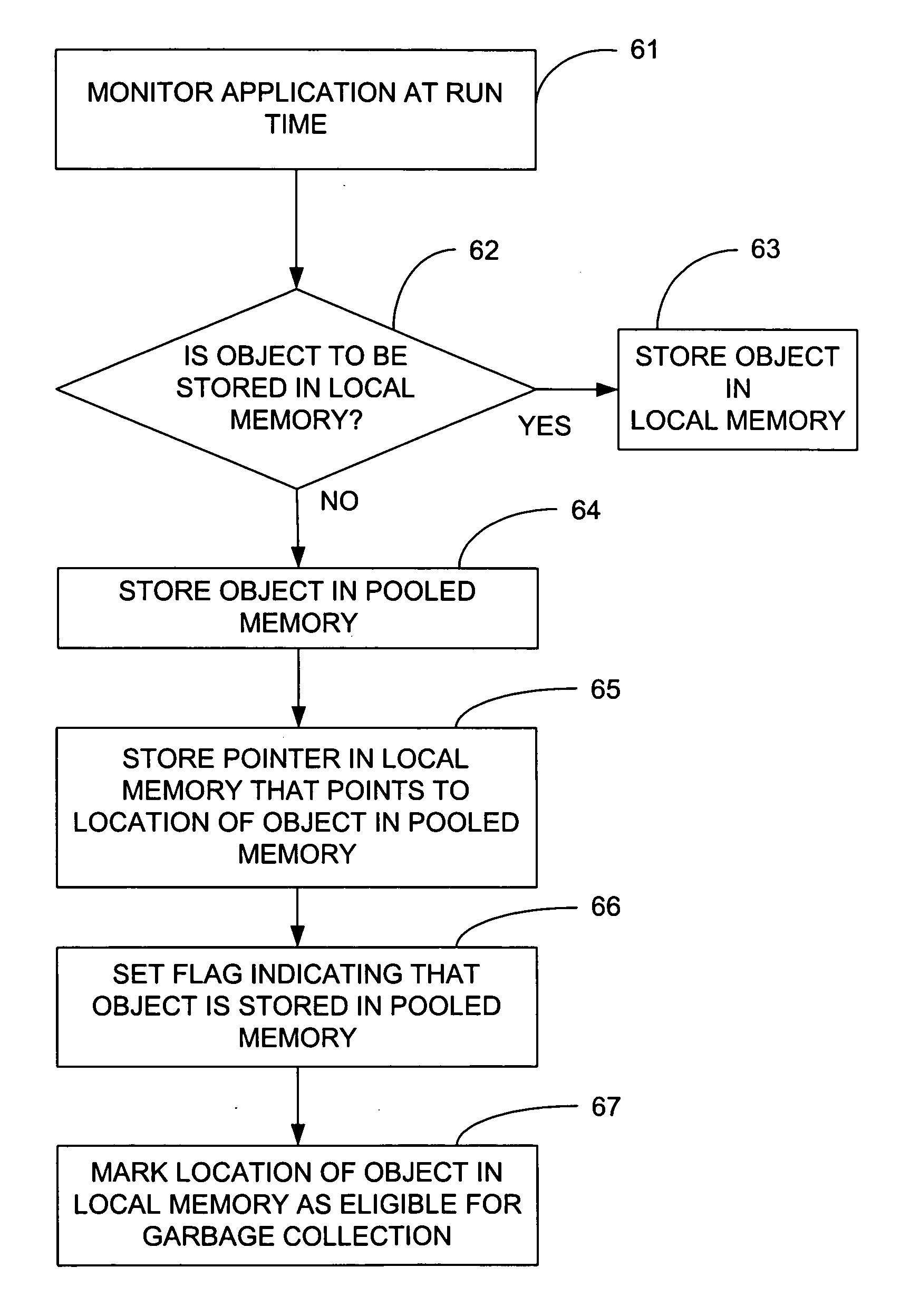
The present invention provides an application virtualization framework that allows dynamic allocation and de-allocation of compute resources, such as memory. Runtime applications are pooled across multiple application servers and compute resources are allocated and de-allocated in such a way that resource utilization is optimized. In addition, objects are either stored in local memory or in a non-local memory pool depending on certain criteria observed at runtime. Decision logic uses decision rules to determine whether an object is to be stored locally or in a memory pool. Resource management logic monitors the memory pool to determine which locations are available for storing objects and how much memory is available overall in the memory pool for storing objects.
Owner:CHUTNEY TECH
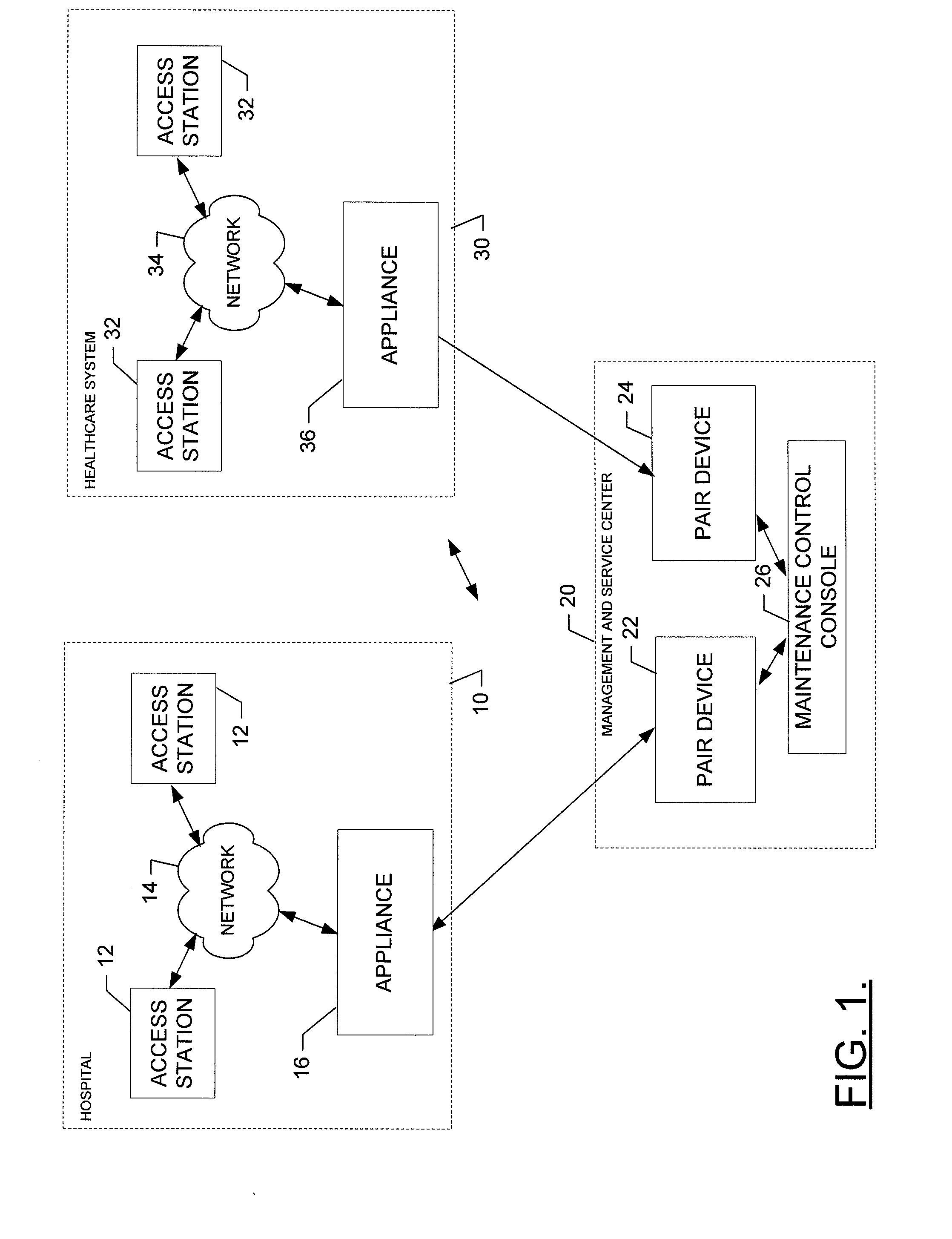
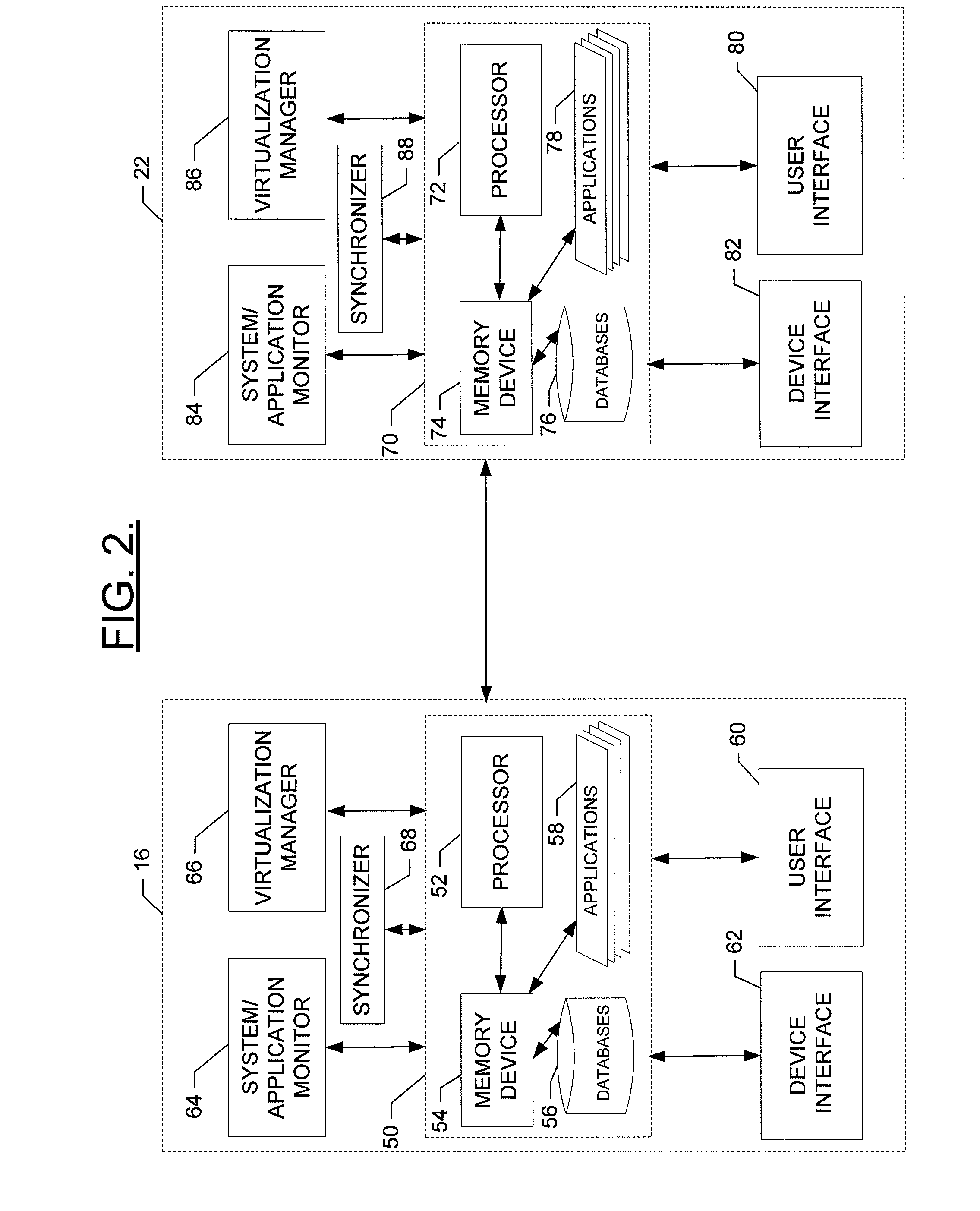
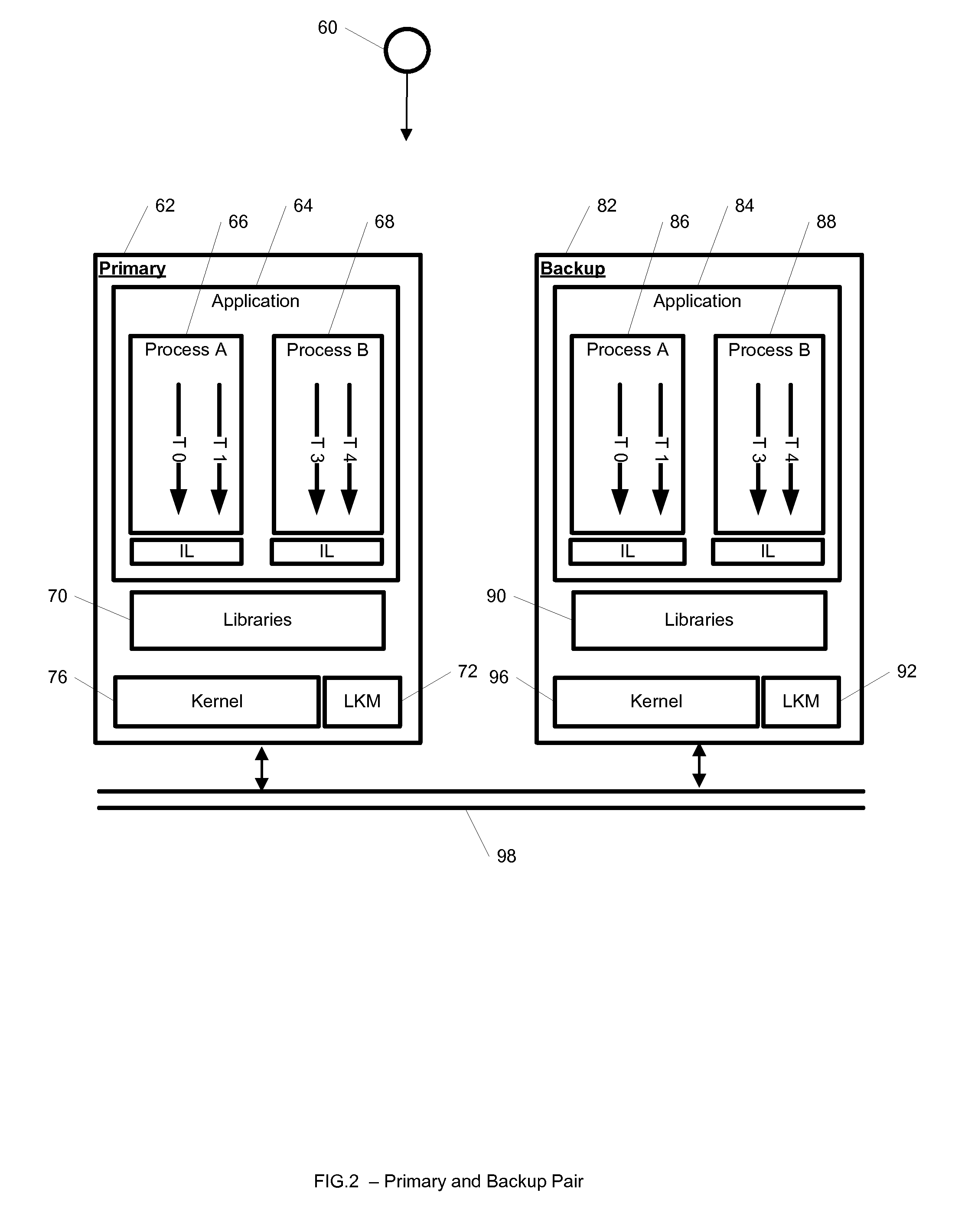
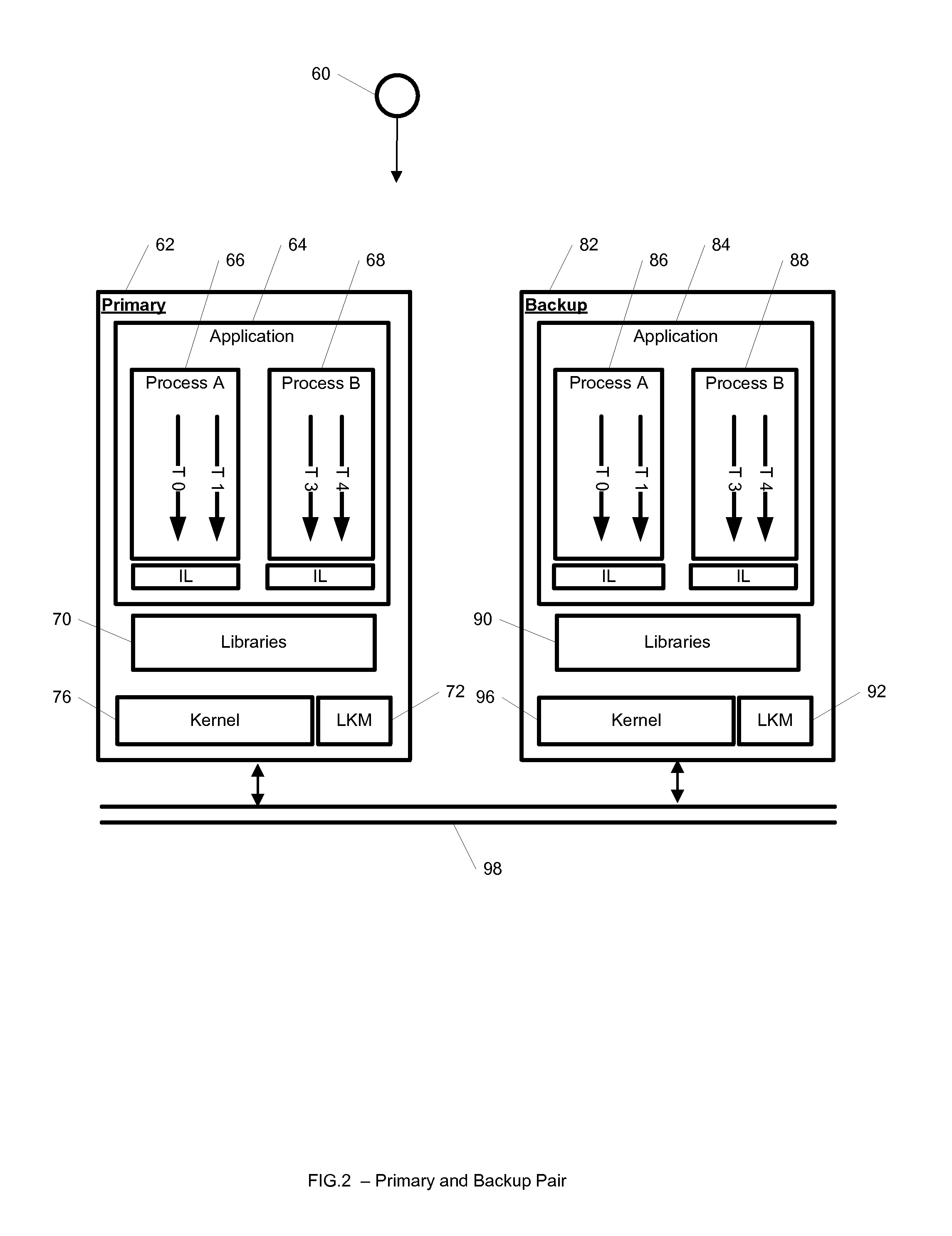
Appliance and pair device for providing a reliable and redundant enterprise management solution
ActiveUS20110040575A1Provides redundancyFault responseMultiprogramming arrangementsVirtualizationMultiple applications
A system for providing a reliable and redundant enterprise management solution includes an appliance disposed at a healthcare facility and a pair device disposed at a remote facility. The appliance includes first processing circuitry, a first virtualization manager and a first synchronizer. The first processing circuitry is configured to enable execution of a plurality of applications. The first virtualization manager is configured to virtualize at least storage components and an execution environment for at least some of the applications. The pair device includes second processing circuitry, a second virtualization manager and a second synchronizer. The second processing circuitry provides redundancy for the first processing circuitry. The second virtualization manager is configured to provide redundancy with respect to the virtualized storage components and execution environment. The second synchronizer is configured to communicate with the first synchronizer to enable shifting of operations with respect to one of the applications being executed between the appliance and the pair device. A corresponding method and apparatus are also provided.
Owner:HARRIS DAWN HLDG INC
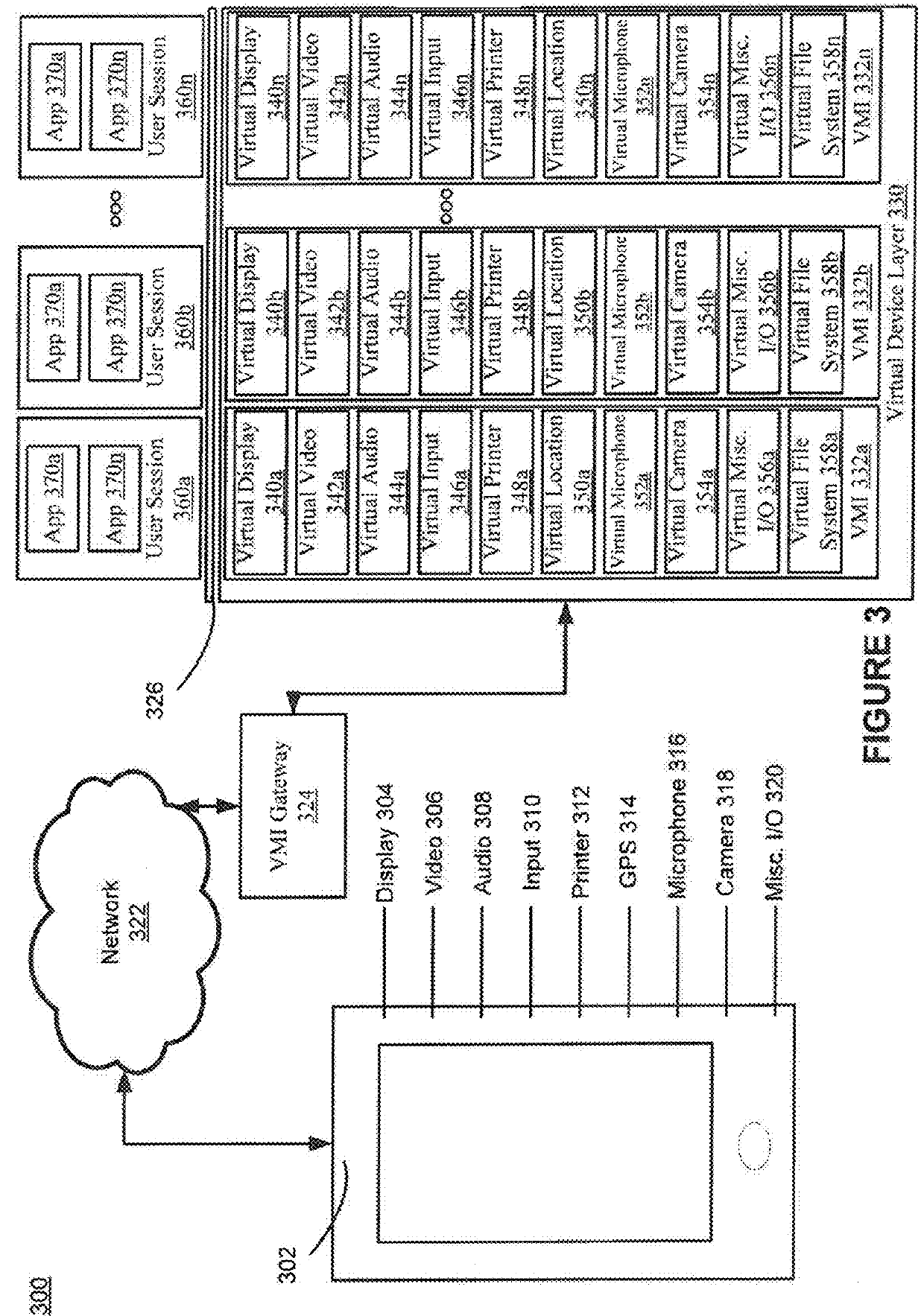
Method for cloud based mobile application virtualization
ActiveUS20180109625A1Reduce in quantityImprove performanceTransmissionExecution for user interfacesVirtualizationCloud base
A system and method for mobile application virtualization. The method includes creating a plurality of user sessions each comprising a unique session ID and allocating server resources to each user session. The method further includes creating a plurality of sets of virtual devices. Each set of the plurality of sets of virtual devices is associated with a respective session ID. The method further includes executing an application of a plurality of applications within a user session of the plurality of user sessions and receiving a request from the application. The method further includes sending the request to a first virtual device of a set of virtual devices based on a session ID. The sending is performed by a single operating system and the single operating system is configured to route requests between applications and the plurality of sets of virtual devices based on the session IDs.
Owner:SIERRAWARE LLC
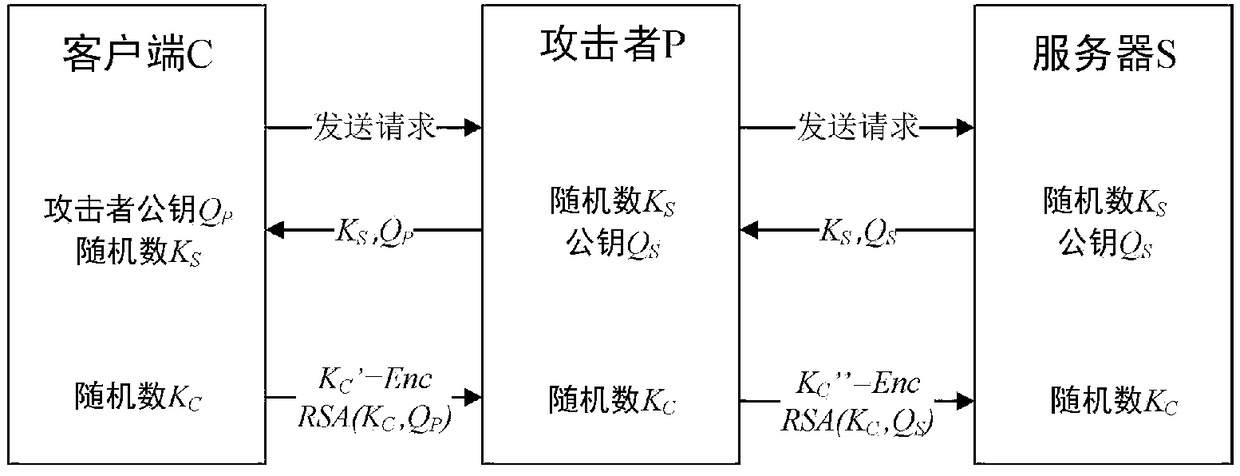
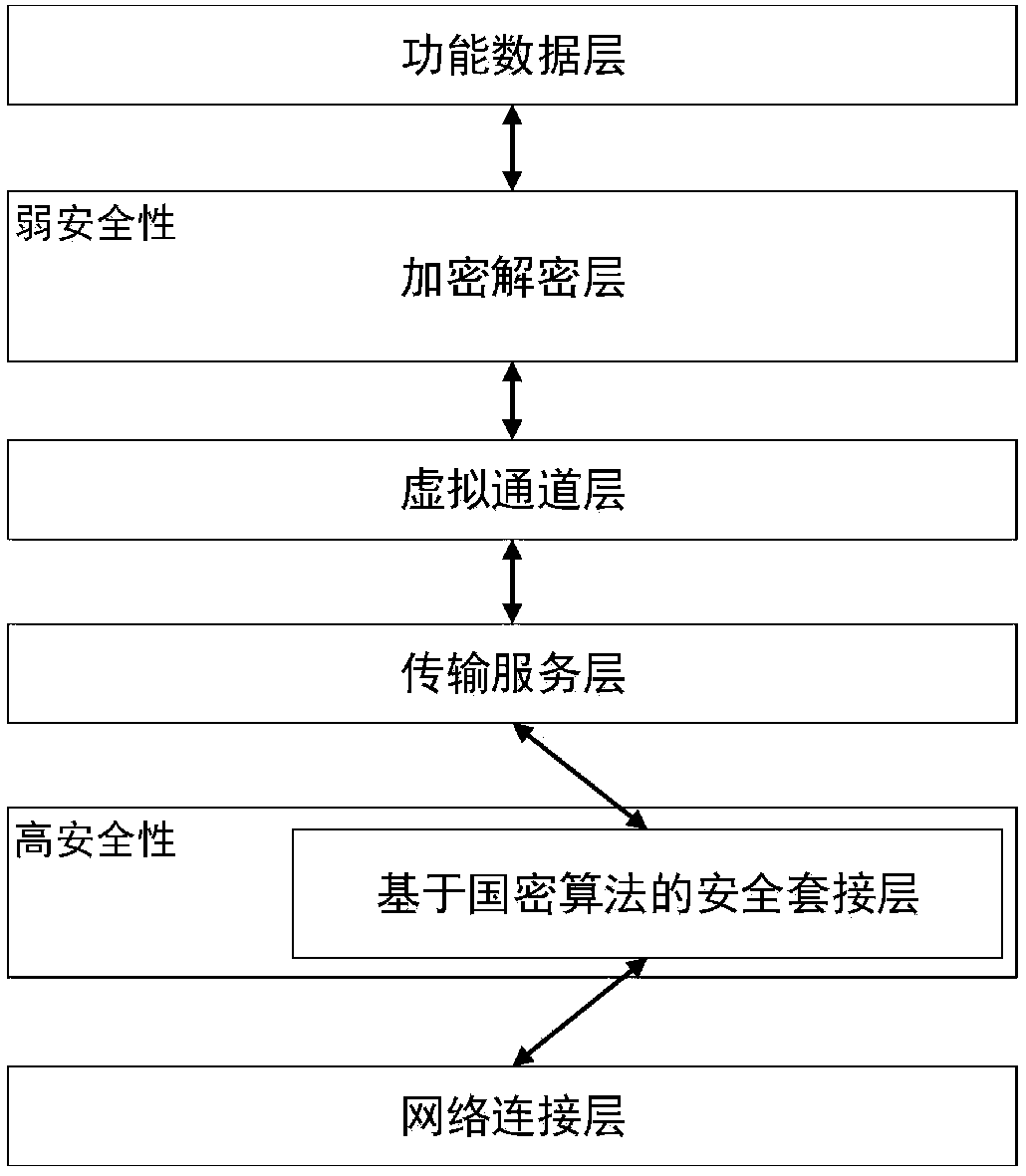
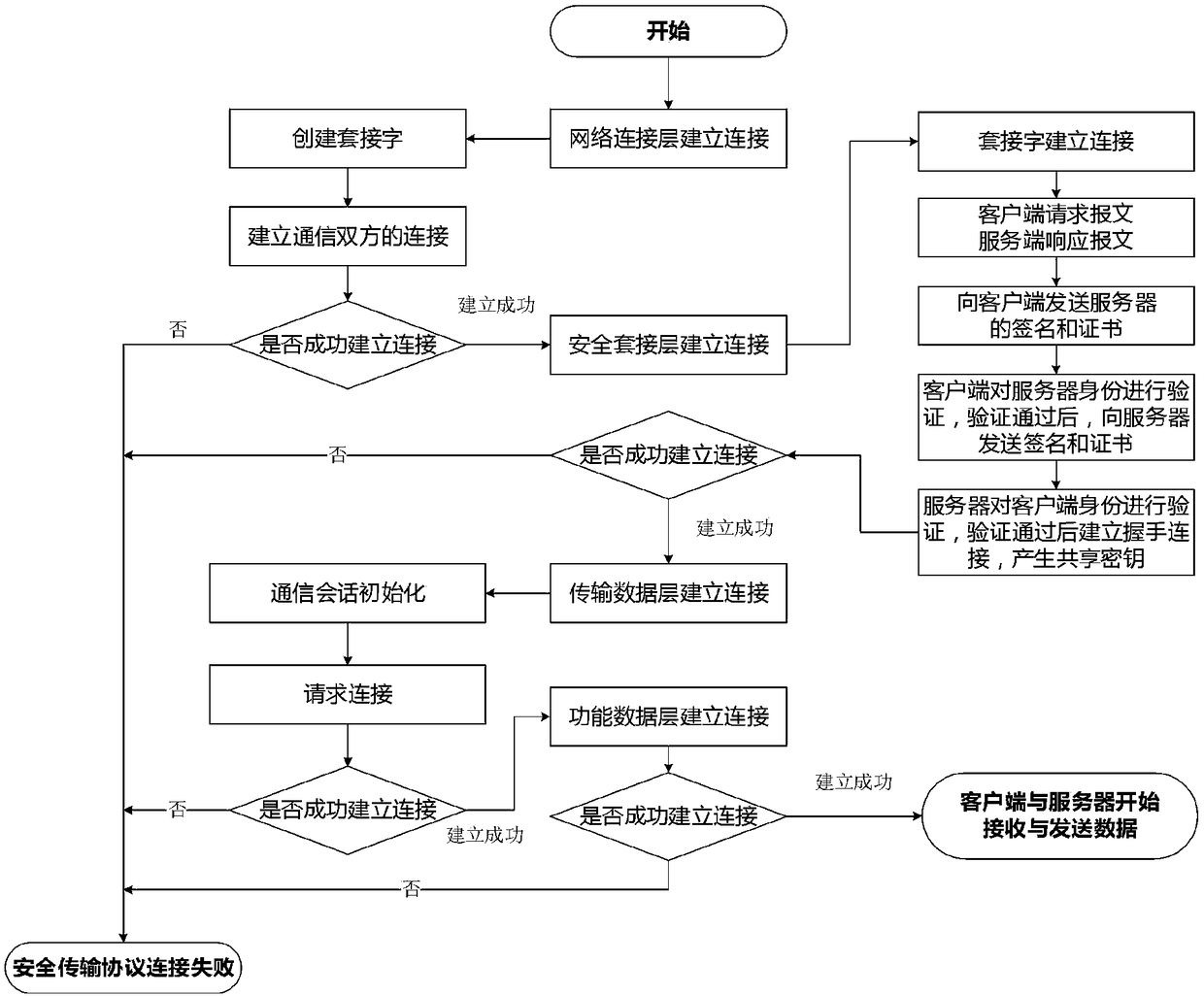
Application virtualization security communication method in autonomous and controllable environment
ActiveCN109347809AKey distribution for secure communicationUser identity/authority verificationVirtualizationNetwork connection
The invention relates to an application virtualization security communication method in an autonomous and controllable environment, and relates to the technical field of network security. The invention expands a security socket layer based on the domestic commercial cipher suite based on the RDP protocol by reconstructing the original RDP protocol stack, and adds the security socket layer to the network connection layer of the protocol stack, which can provide a secure transmission service for the client to the server, thereby realizing the dual identity authentication between the client and the server, and completing the identity verification of the client to the server.
Owner:BEIJING INST OF COMP TECH & APPL
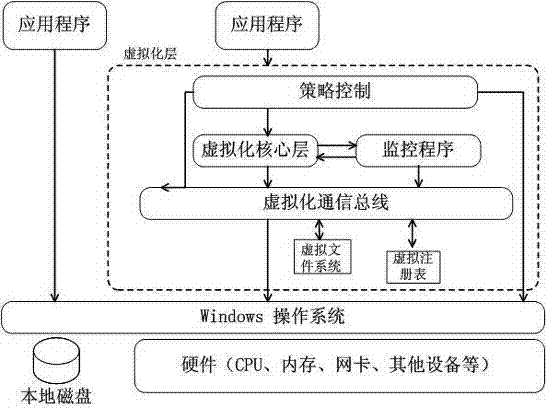
Method for realizing safe working environment based on virtualization technology
InactiveCN102314373AEasy to deployPlatform integrity maintainanceSoftware simulation/interpretation/emulationVirtualizationVirtual file system
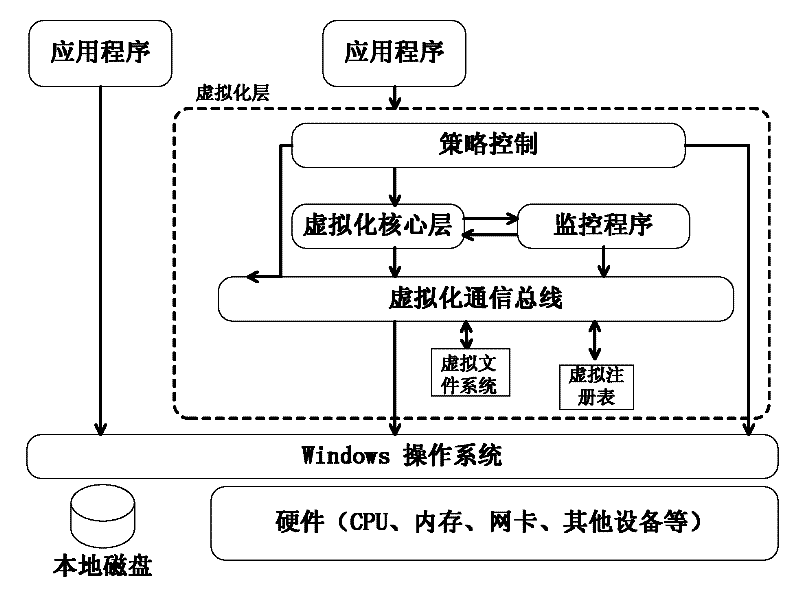
The invention provides a method for realizing a safe working environment based on a virtualization technology. In the method, a virtual layer is constructed on an operating system, and an application program virtualization technology is utilized to establish a virtual safe working environment to accommodate a plurality of virtual application programs, wherein the virtual safe working environment is a virtual file system, and the virtual layer is formed by a strategy control module, a virtual core layer module, a monitoring module, a virtual communication bus, a virtual file system and a virtual registry. The method has the advantages that the application program virtualization technology is utilized to establish a virtual working area to accommodate a plurality of virtual application programs, and the operating system is separated from the application programs, the settings and the data while the mutual interaction of multiple applications is realized through the virtual communication bus, thereby greatly facilitating the deployment of the application programs.
Owner:胡建斌 +1
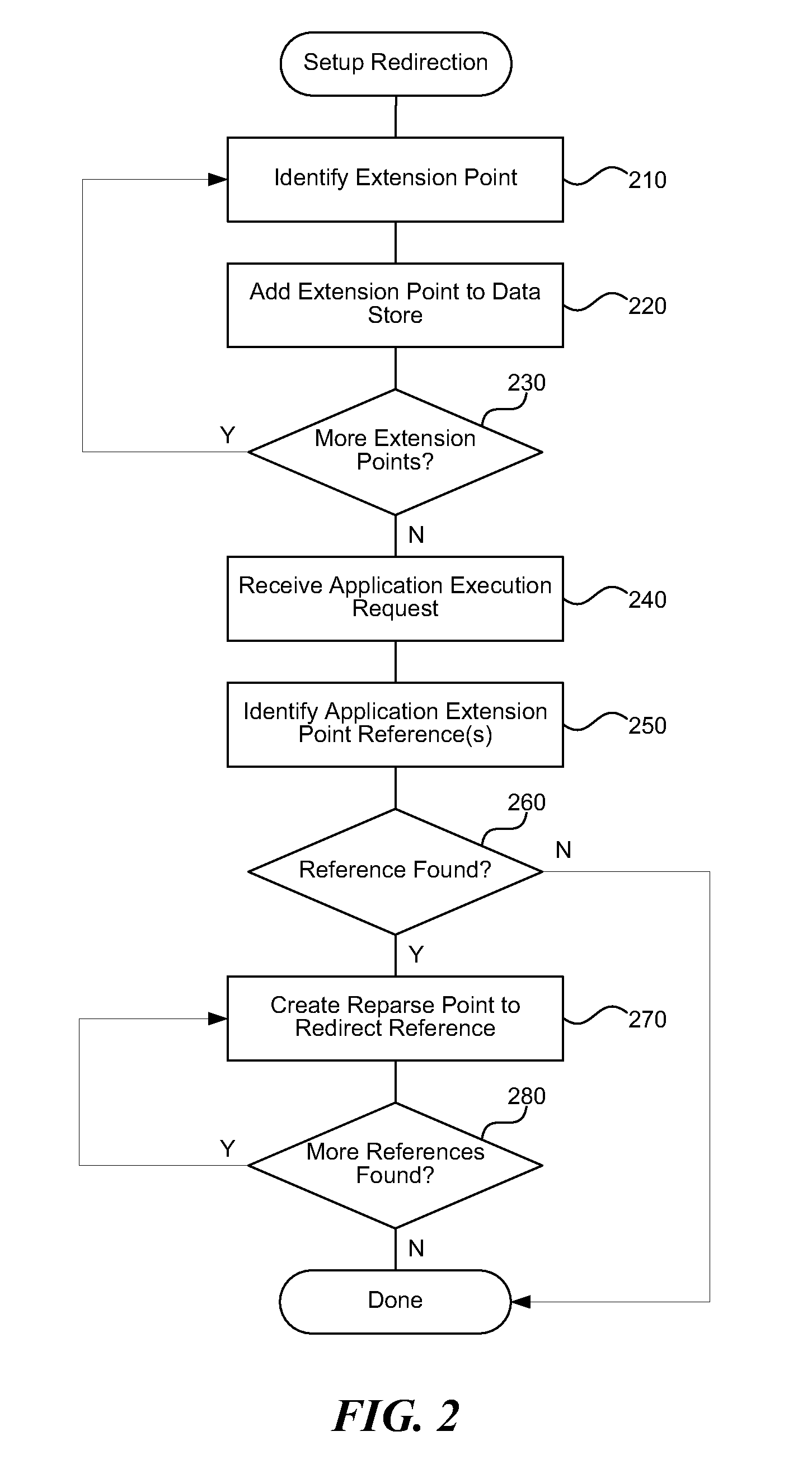
Extension point declarative registration for virtualization
ActiveUS20110197184A1Preserve application isolationSimple processSoftware simulation/interpretation/emulationMemory systemsPoint registrationOperational system
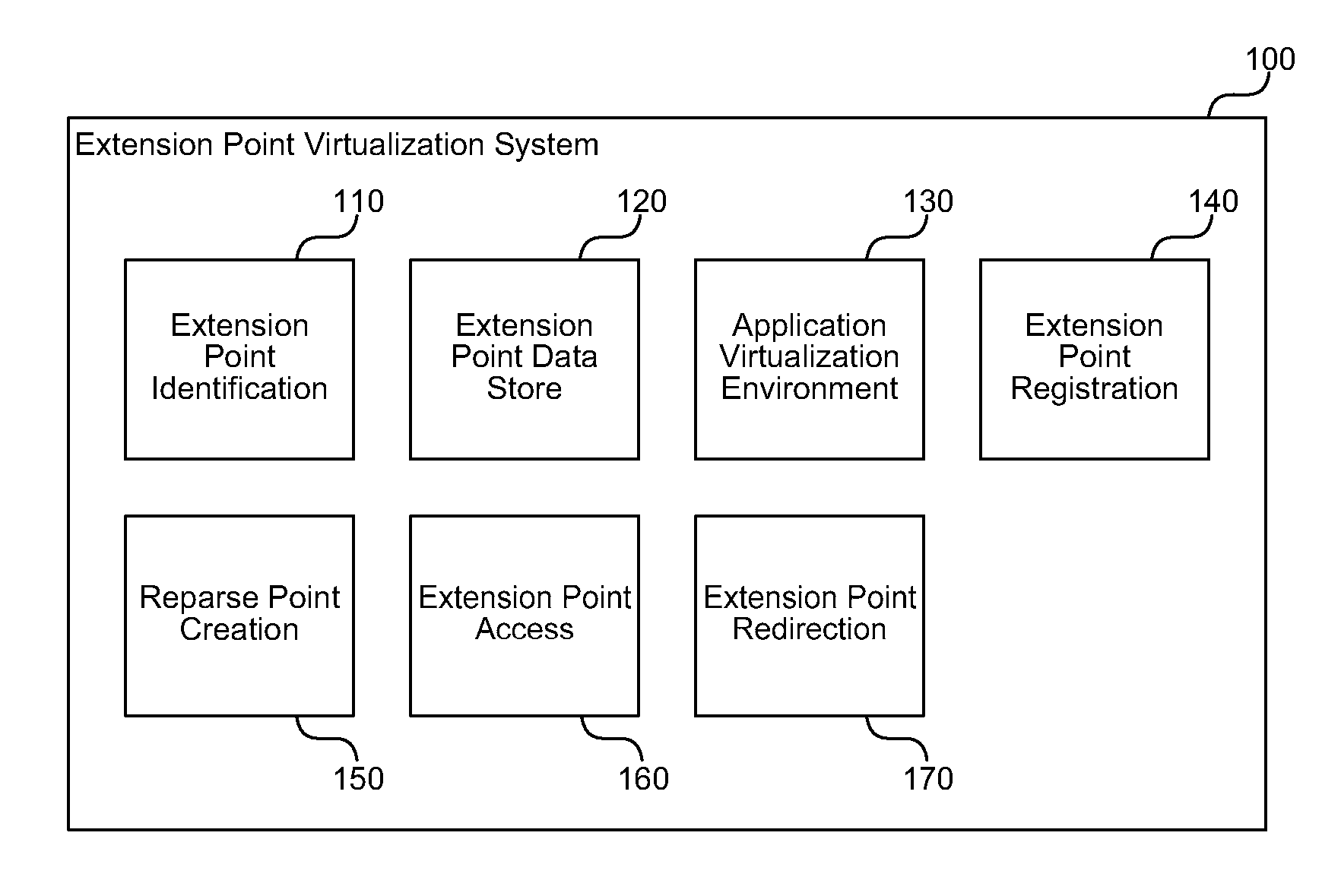
An extension point virtualization system uses operating system-provided reparse points to provide minimal extension point registration. Reparse points preserve application isolation while removing the scale problem of writing custom extension point proxies for each extension point. Instead, the system can use a single file system filter that generically handles application virtualization reparse points, and store reparse point data for extension points that need redirection. Many extension points can be handled by redirecting the operating system from a typical location for an application resource to a virtualized safe location for the application resource. Thus, the system simplifies the process of handling new extension points by allowing an application virtualization system to simply register new locations that should be handled with reparse points and to then handle registered locations generically.
Owner:MICROSOFT TECH LICENSING LLC
Method and system for building desktop cloud
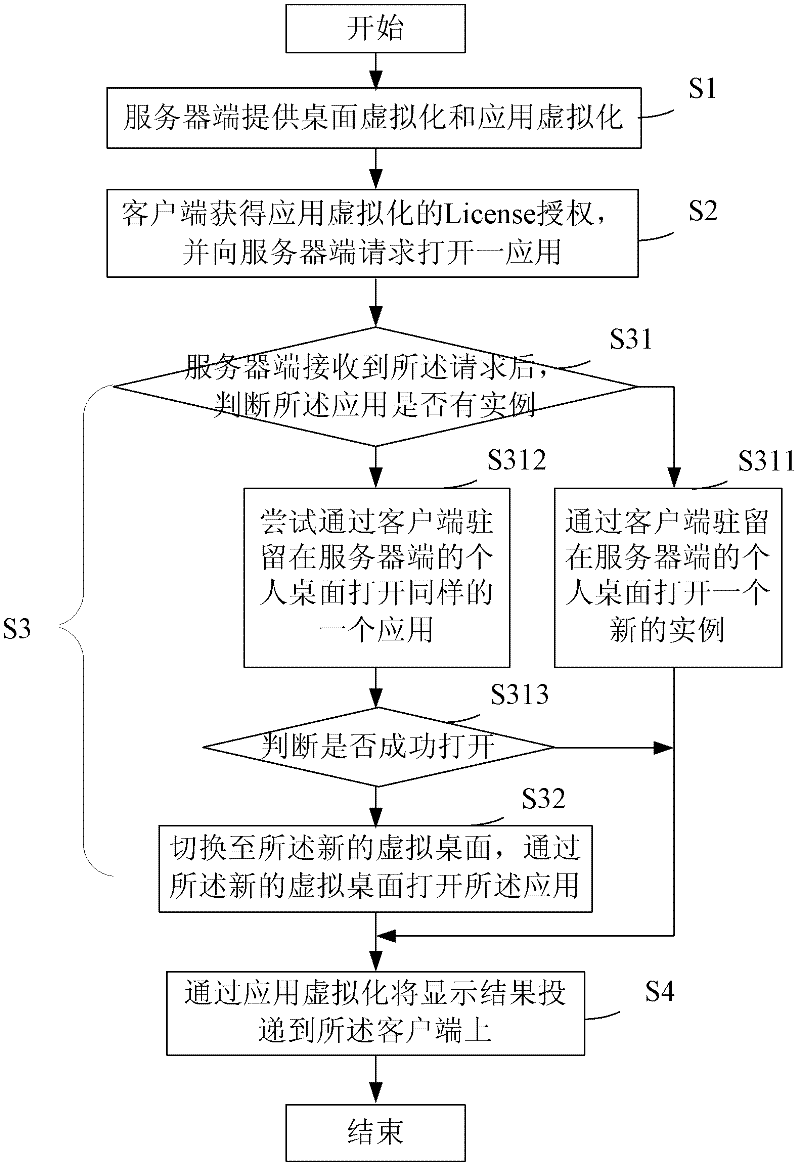
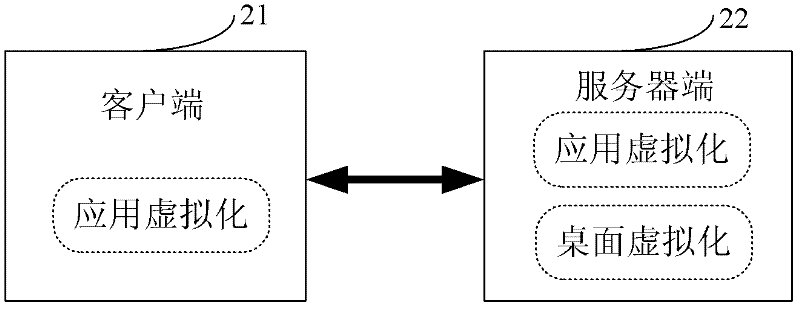
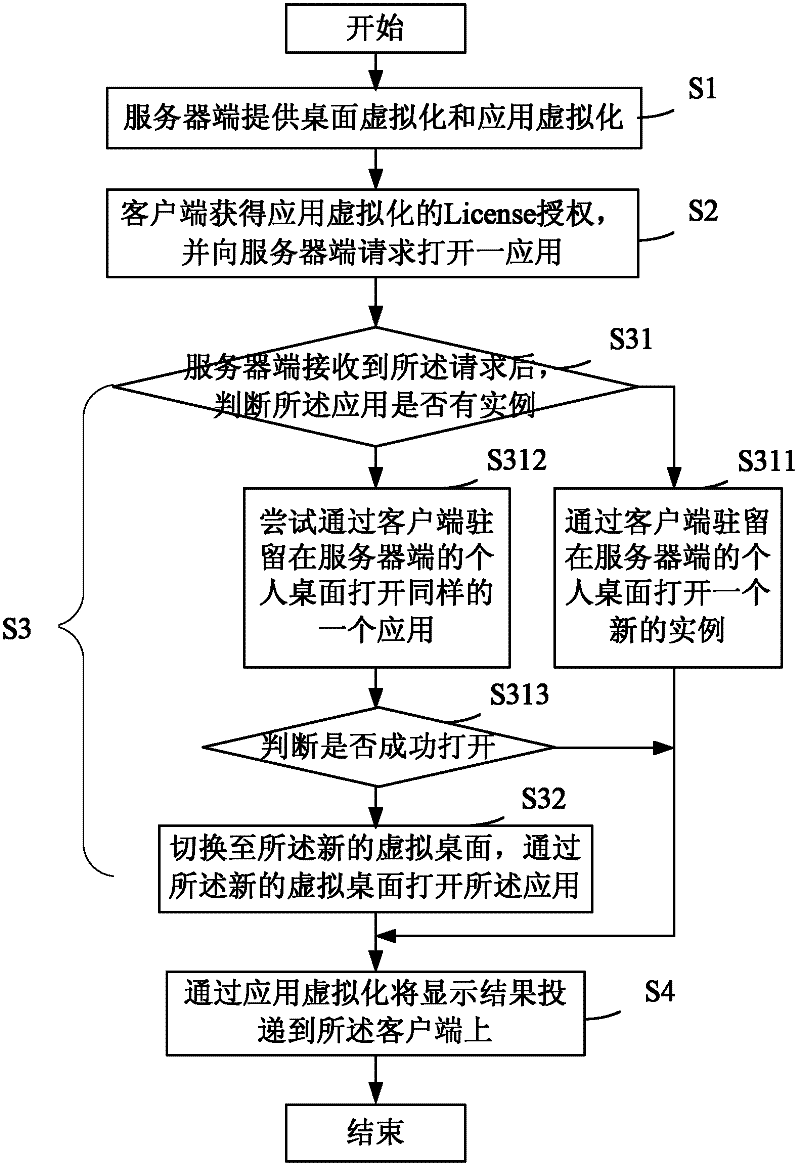
InactiveCN102647456AReduce the process of running automated scripts to measure application compatibilityReduce Compatibility IssuesTransmissionSoftware simulation/interpretation/emulationOperational systemApplication software
The invention provides a method and a system for building desktop cloud, which can automatically integrate application virtualization and desktop virtualization products by utilizing a desktop cloud technology at a server side, thus reducing the processes of evaluating compatibility of application programs by applying a virtualized evaluation tool operation automation script and solving the application program compatibility problem and the inaccurate application program judgment problem. In the invention, an operating system can be arranged for application for single instance, the operating system is directly switched to a desktop virtualization mode when being opened and applied, and the operating system is transparent for the user, and a user does not worry about whether the desktop virtualization and application virtualization technologies are adopted; and simultaneously, only application virtualization License authorization is used at a client side, license expenses can be taken according to the quantity of logging users, thus avoiding troubles of two License authorizations.
Owner:ISOFT INFRASTRUCTURE SOFTWARE
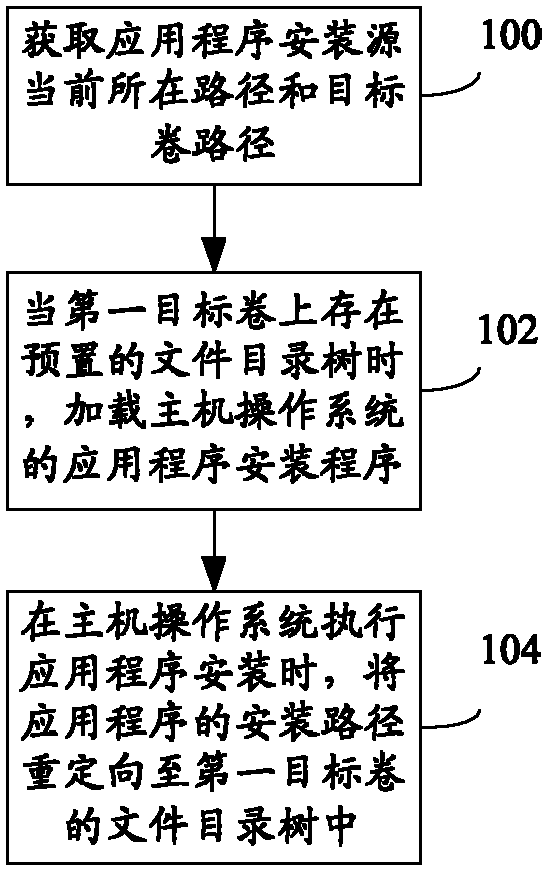
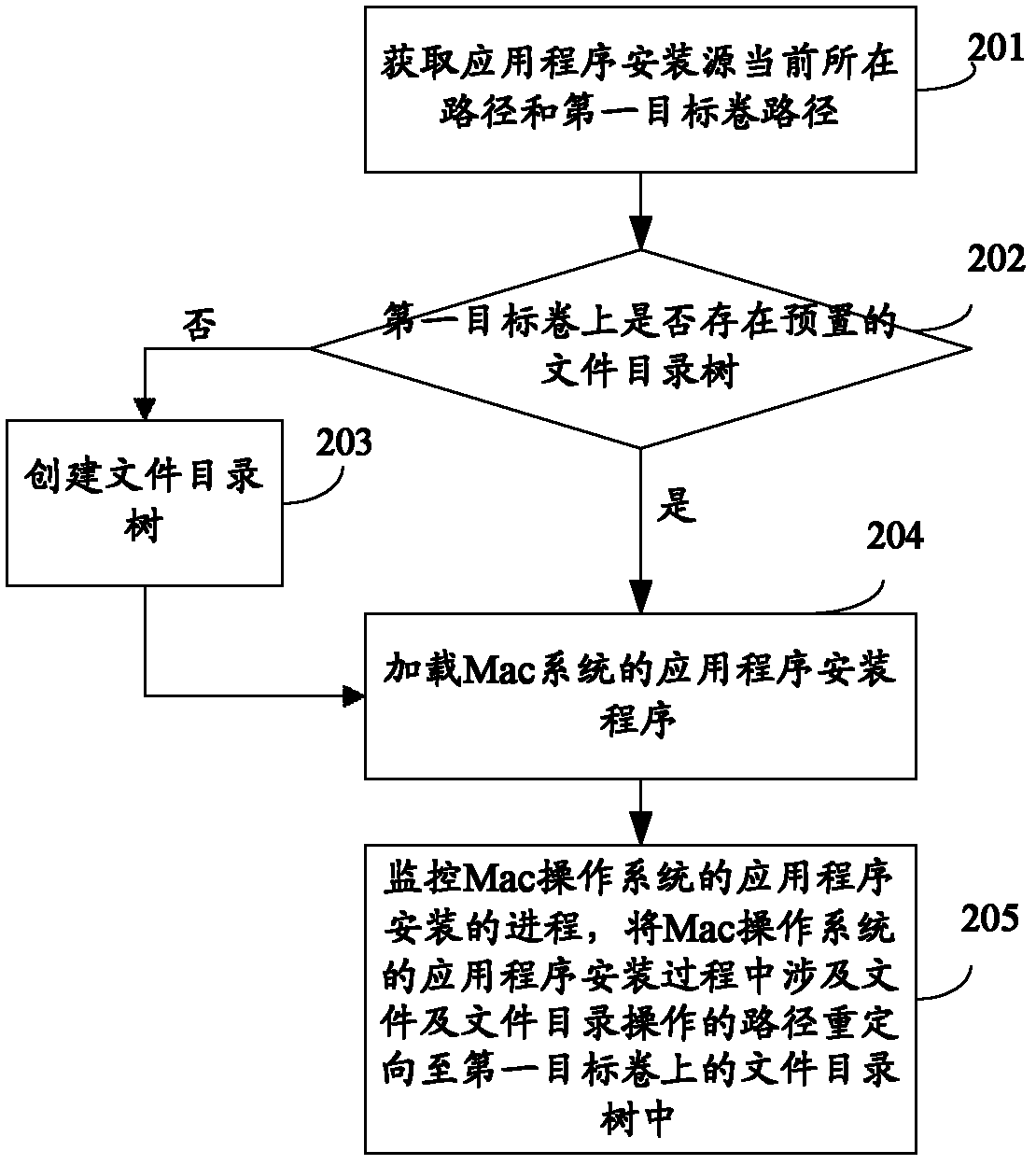
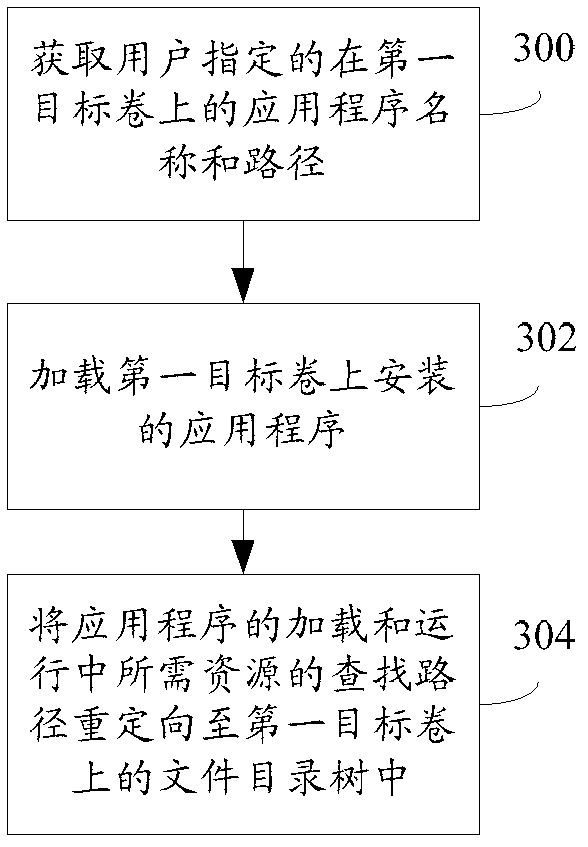
Application program virtualization installing and loading method and device
InactiveCN102231116AMobileDigital data information retrievalProgram loading/initiatingVirtualizationOperational system
The embodiment of the invention provides an application program virtualization installing and loading method and an application program virtualization installing and loading device. A large and complex application program which cannot change the original installing position on a host operating system platform can be installed on a target volume selected by a user, such as a mobile hard disk drive and the like, a plurality of application programs can be installed on the same target volume by the user, and a file directory tree is shared; and when the user selects a removable medium to serve as a target volume of application program virtualization installation, the application program and data move simultaneously along the movement of the medium, and a software installation and deployment method with mobility is provided for the user.
Owner:HUAWEI DIGITAL TECH (CHENGDU) CO LTD
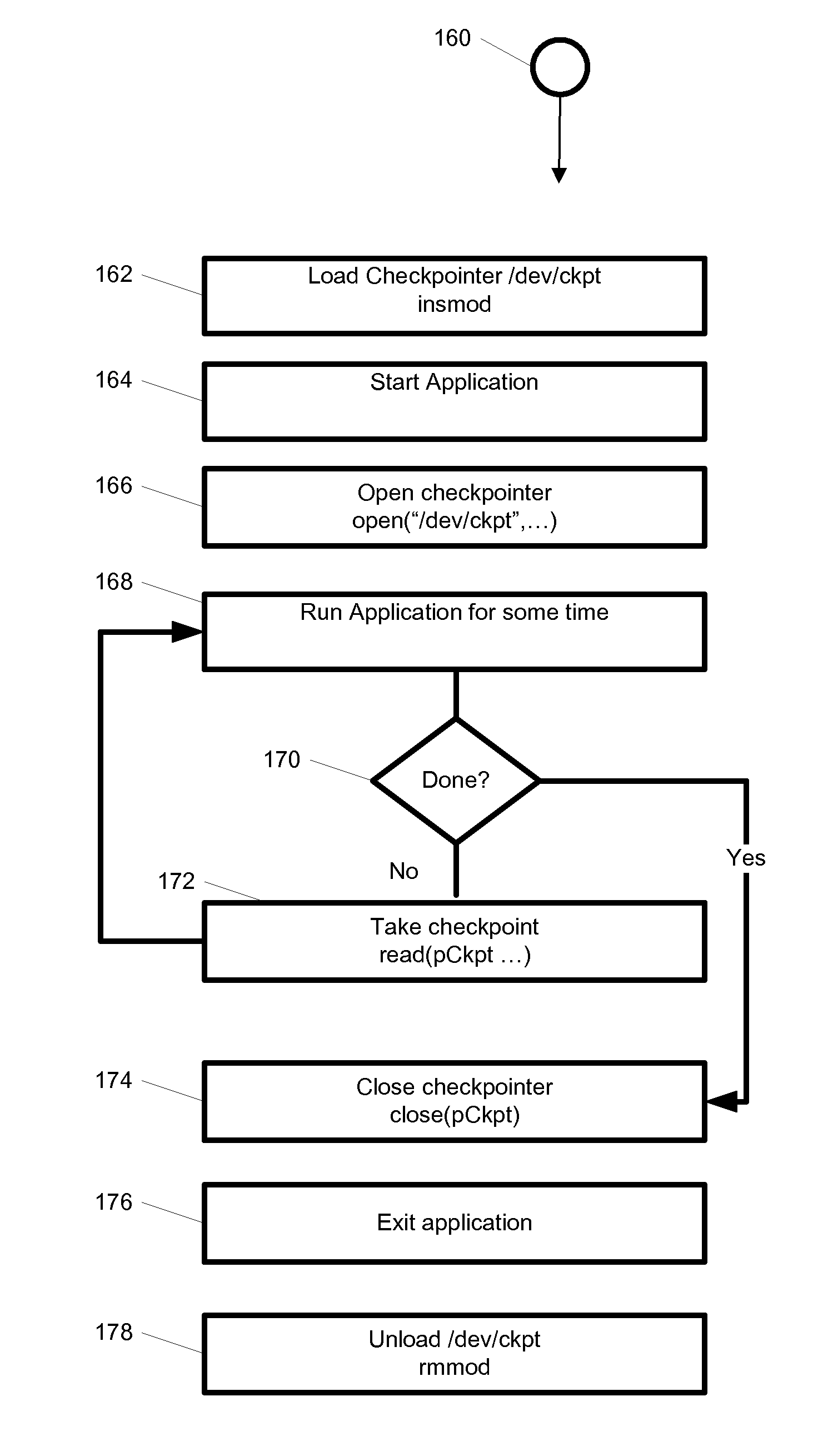
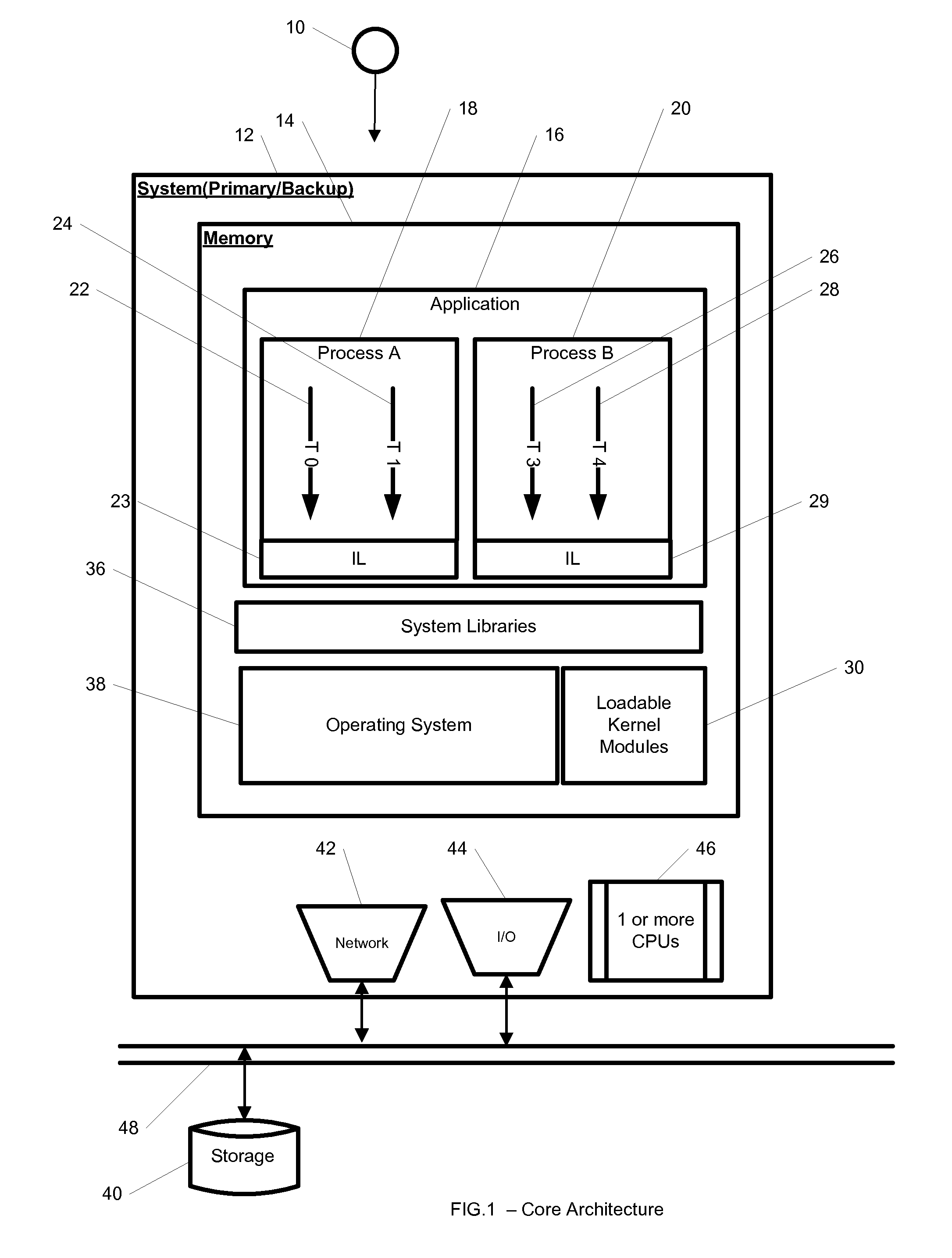
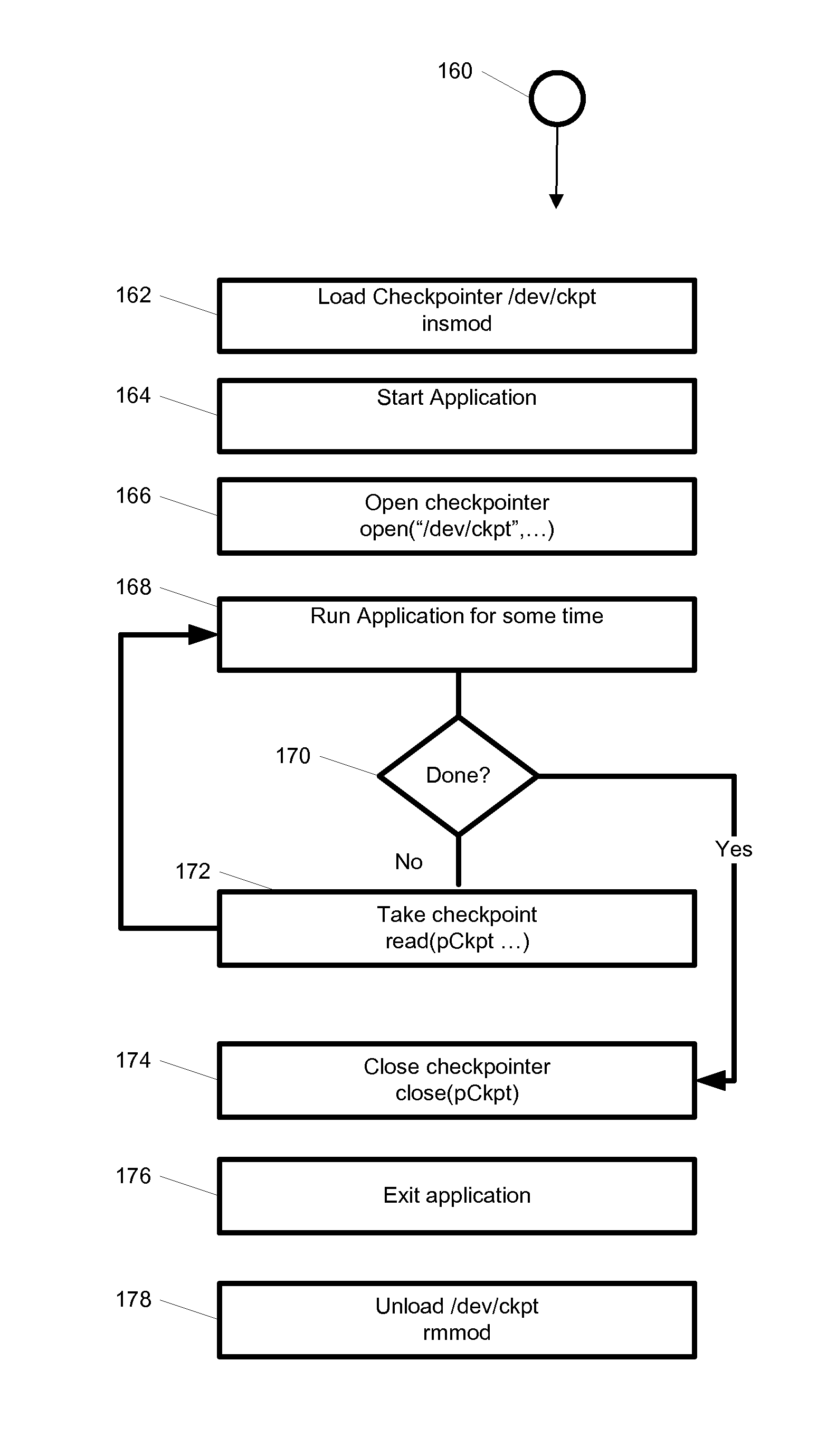
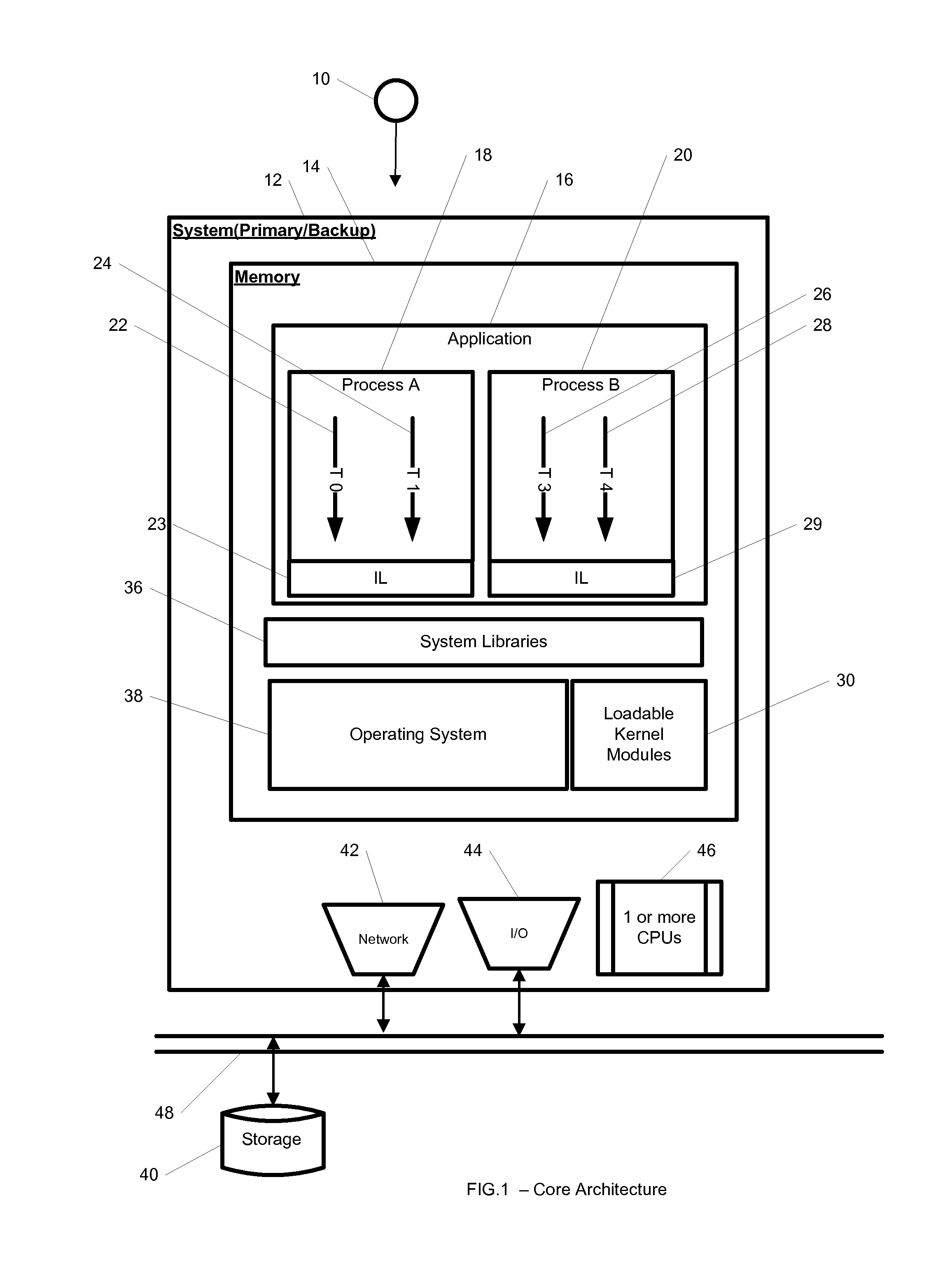
System and method for hybrid kernel- and user-space incremental and full checkpointing
A system includes a multi-process application that runs. A multi-process application runs on primary hosts and is checkpointed by a checkpointer comprised of at least one of a kernel-mode checkpointer module and one or more user-space interceptors providing at least one of barrier synchronization, checkpointing thread, resource flushing, and an application virtualization space. Checkpoints may be written to storage and the application restored from said stored checkpoint at a later time. Checkpointing may be incremental using Page Table Entry (PTE) pages and Virtual Memory Areas (VMA) information. Checkpointing is transparent to the application and requires no modification to the application, operating system, networking stack or libraries. In an alternate embodiment the kernel-mode checkpointer is built into the kernel.
Owner:IBM CORP
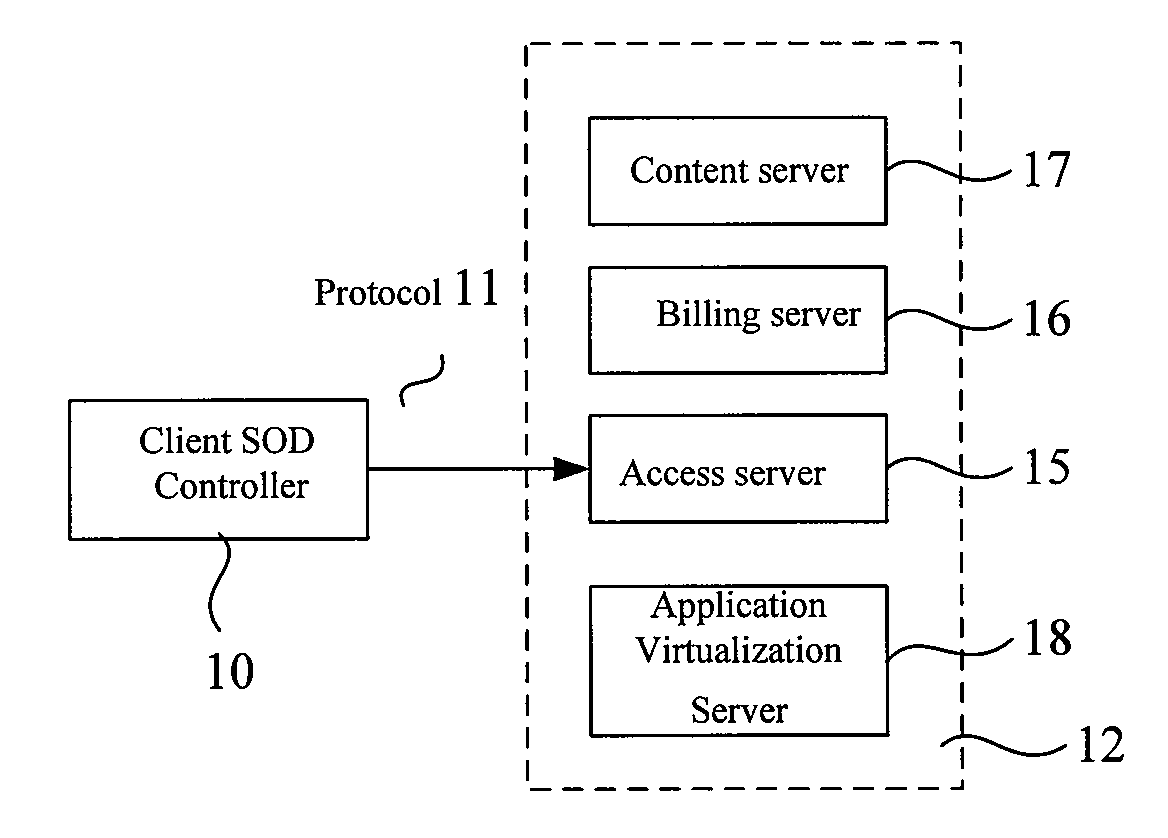
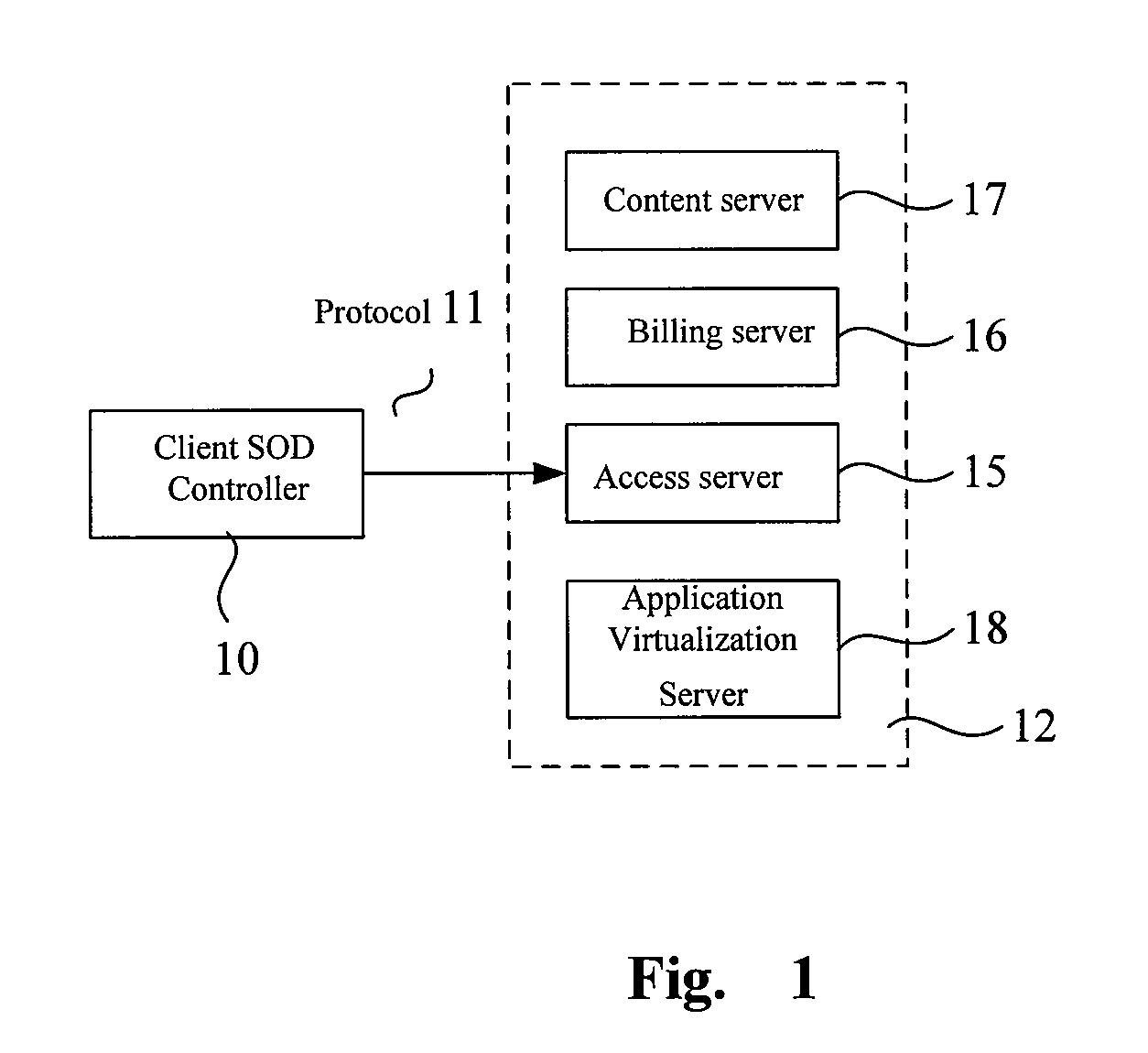
Generalized application virtualization method for business use on the web and the mini server using this method
ActiveUS20080183641A1Increase transfer speedReduce delaysTicket-issuing apparatusBuying/selling/leasing transactionsVirtualizationData center
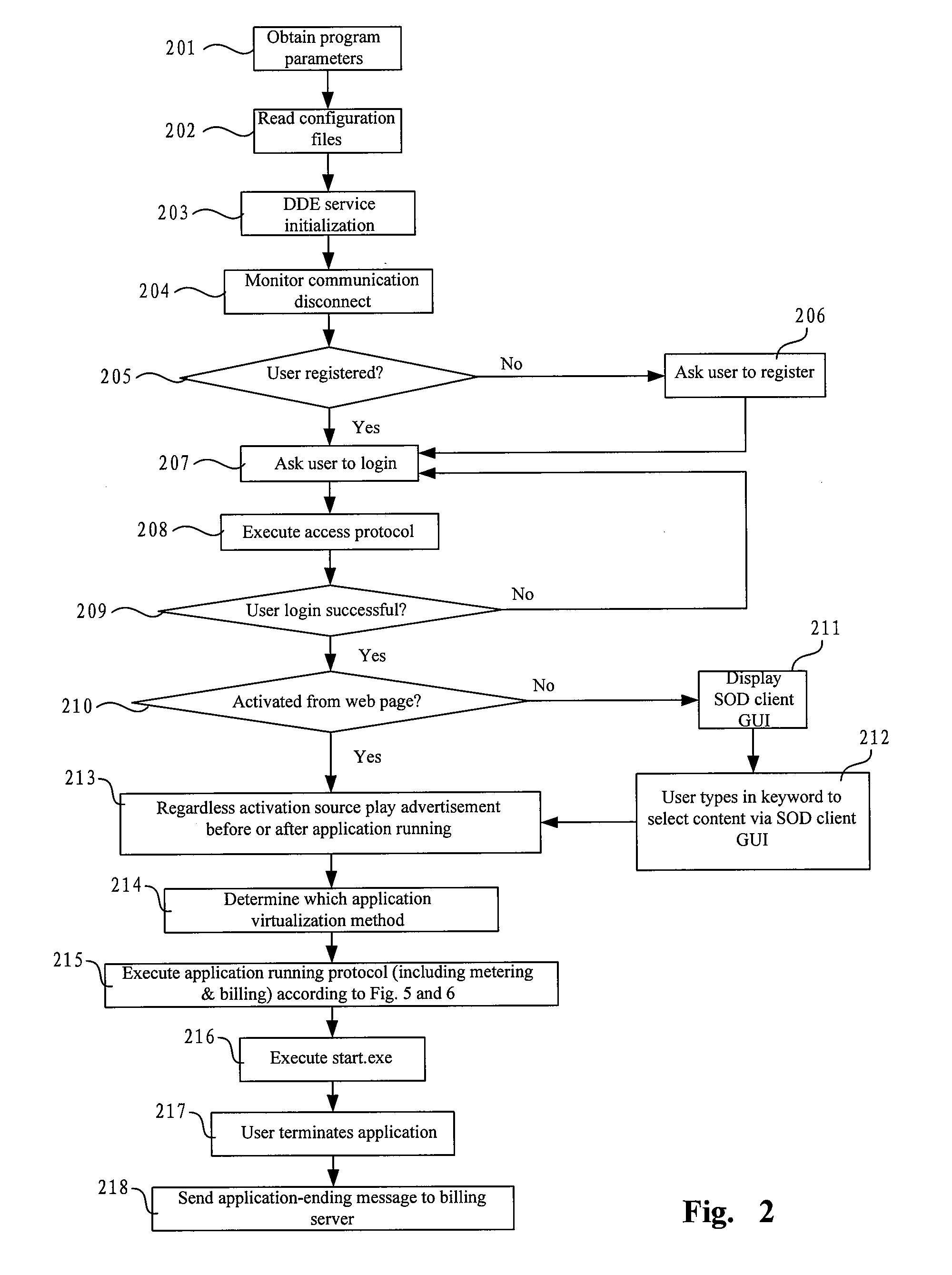
The invention issued is a generalized application virtualization method for business use on the web and the mini server, including: (1) Initializing (which includes obtaining parameters, reading configuration file, and initializing a DDE service), application monitoring, registration and login. (2) Accessing to a server via Access Protocol from a client-side SOD controller (aka SOD client controller, or SOD controller). (3) Content selecting via keyword search, with the selected contents provided by the Content Management Protocol. (4) Choosing one of the available application virtualization methods according to bandwidth needed by the user and the resources consumed in the data center. (5) Binding of the executable software for the application virtualization method and the contents selected, and running of that executable software. (6) Metering and billing: Meter the start and end time of the execution of application virtualization method and calculate the billing. The aforementioned method, not only invents a client controller on the basis of application virtualization, but also allows a user to do secure access, choose contents, run application, meter the content usage and calculate the billing; furthermore, this reaches a goal to complete content leasing and billing without being monopolized by Microsoft products.
Owner:TRANSOFT SHANGHAI
Systems and methods for server cluster application virtualization
Application instances can be virtualized and operate in a fault tolerant and load-balanced means across a cluster of servers while still maintaining access to a common pool of data. Each application instance is instantiated so to operate on top on top of a virtual host that possesses a distinct virtual Internet protocol address. Each node within a server cluster environment can possess one or more virtual hosts wherein upon server failover the virtual host and its associated virtual Internet protocol address can be relocated to another server without disturbing the instantiation of the application on the virtual host.
Owner:DH2I
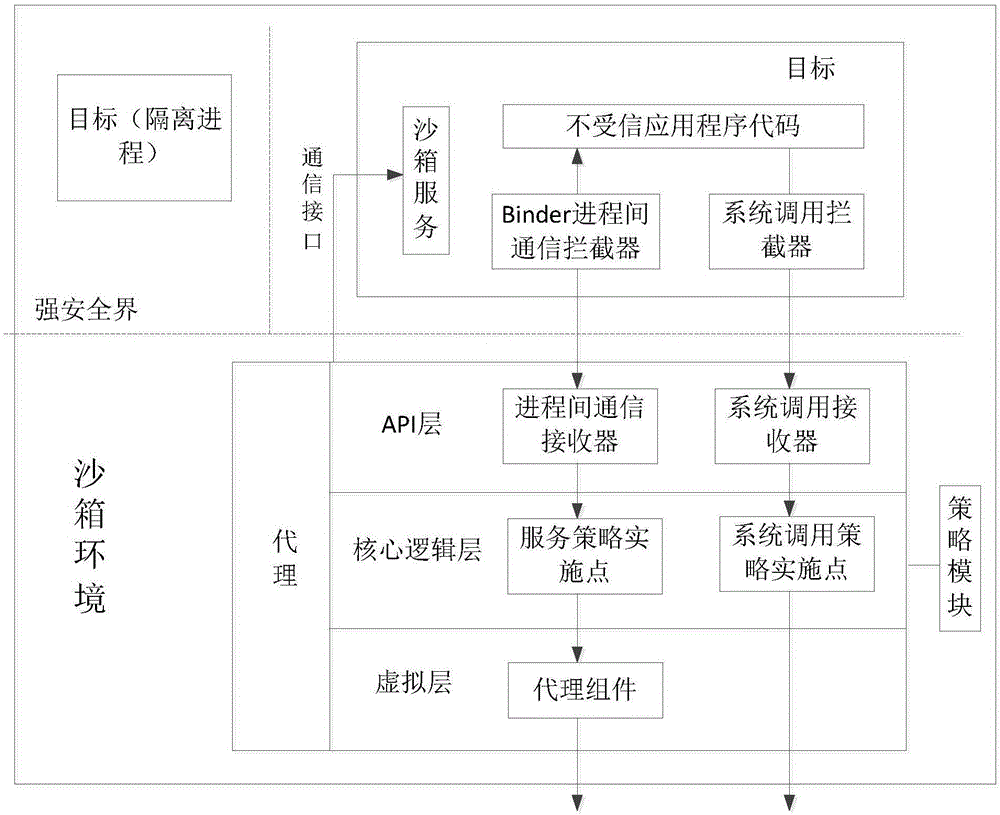
Android storage application sandbox based on application program virtualization, and communication method thereof
ActiveCN106384045AOvercomes the disadvantage of restricting the permissions of untrusted applicationsImprove communication securityPlatform integrity maintainanceVirtualizationOperational system
The invention discloses an Android storage application sandbox based on application program virtualization. The Android storage application sandbox comprises an agent and a target, wherein a strong secure boundary used for securely isolating untrusted application programs exists between the target and the agent; the agent is an application program process, owns all platform permissions distributed by a system, can normally interact with Android middleware and is used as all interactive compulsory agents between the target and an Android system; the agent comprises an API (Application Program Interface) layer, a core logic layer and a virtual layer; and the target does not have a platform permission, can not access Android firmware, can not change a file system and comprises sandbox service, a Binder interprocess communication interceptor and a system calling interceptor. Safety provided by an isolation process is used, and the untrusted application programs are dynamically loaded and executed in the process to avoid revising an operating system and the untrusted application programs. Meanwhile, a controllable method is used for permitting the untrusted application programs to execute an input / output operation and access system resources, and the untrusted application programs are packaged in the sandbox environment.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
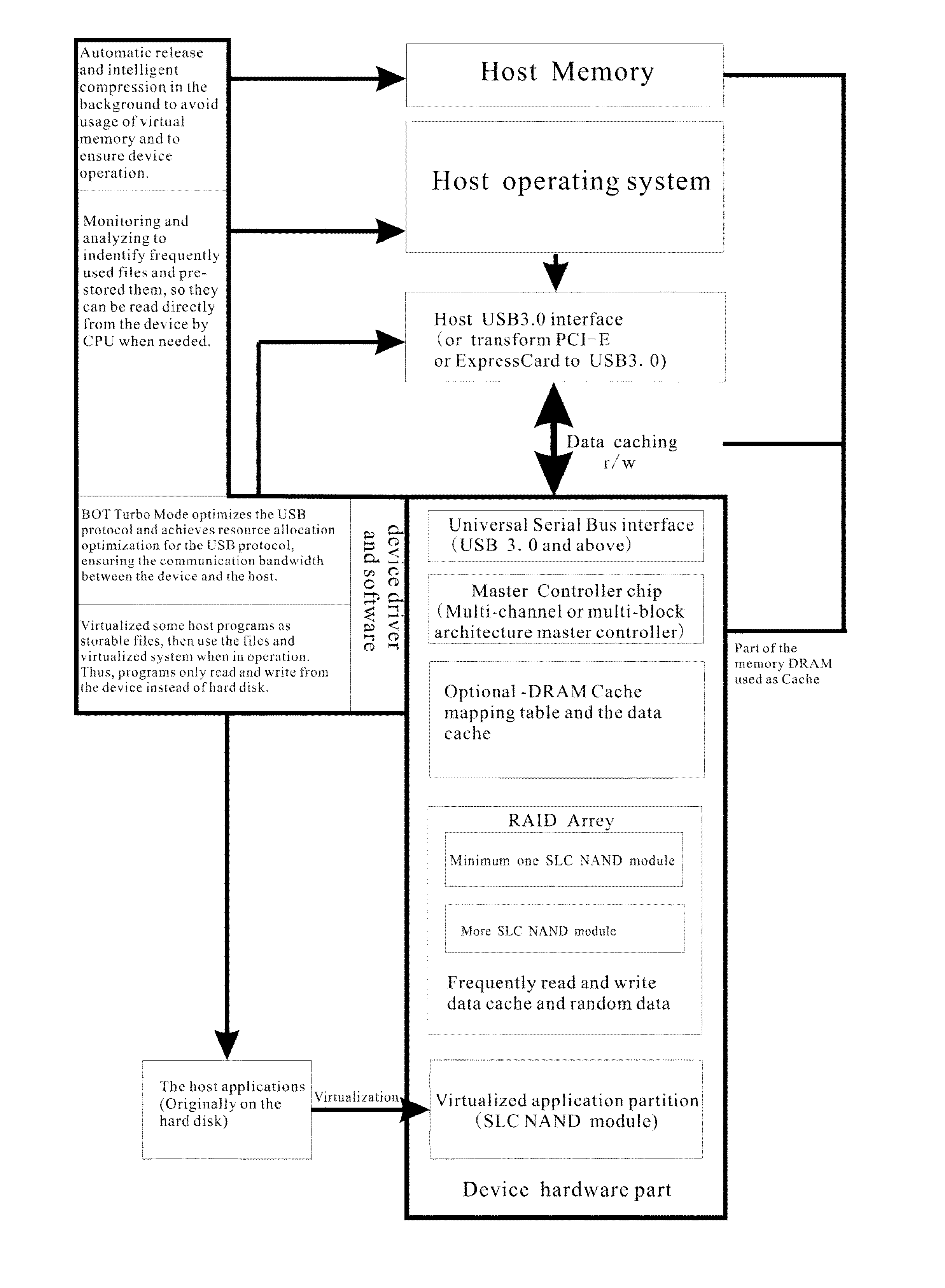
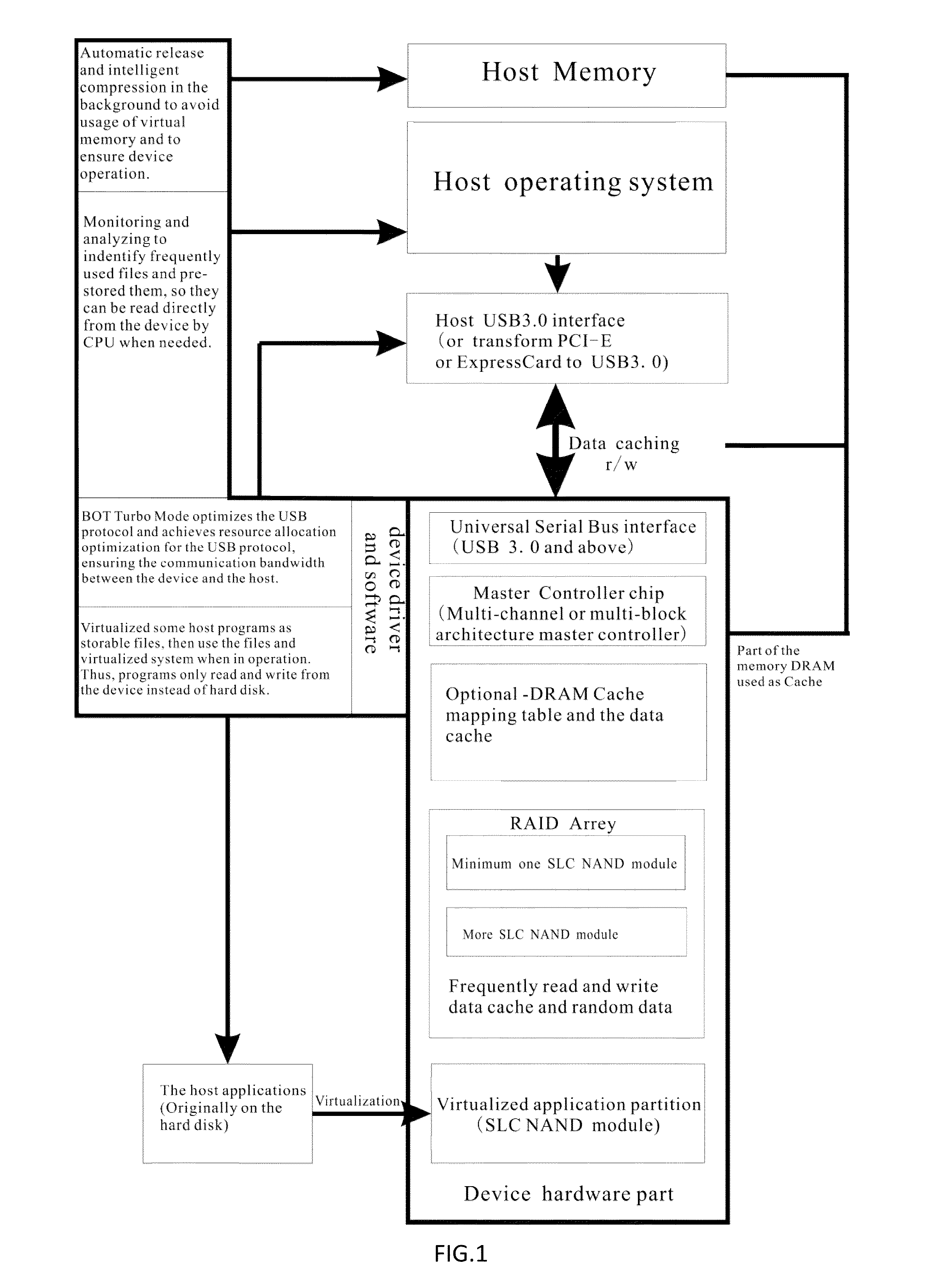
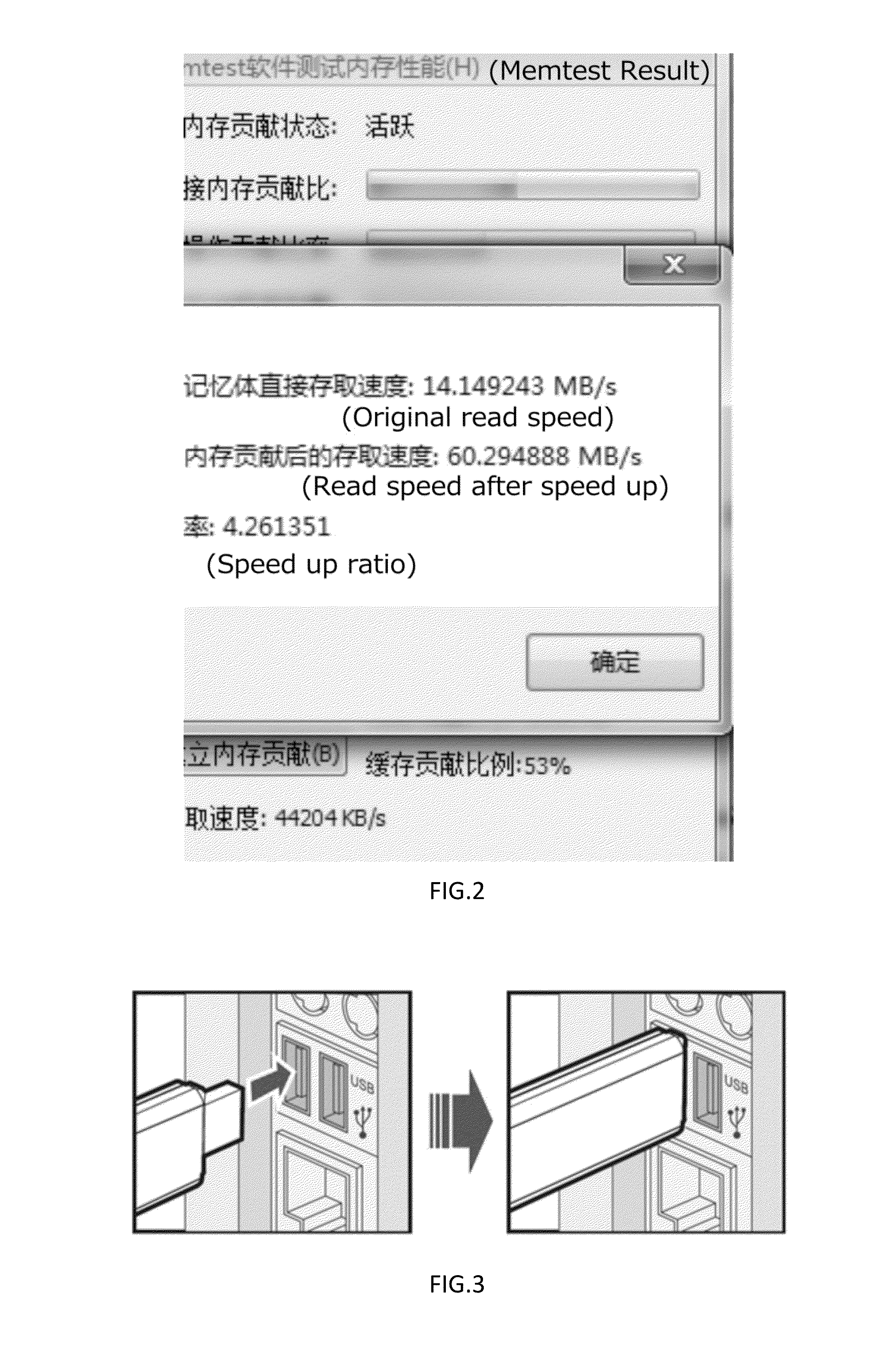
A new USB protocol based computer acceleration device using multi I/O channel SLC NAND and DRAM cache
InactiveUS20160253093A1Increase speedEasy to operateMemory architecture accessing/allocationInput/output to record carriersHabitApplication software
This study presents a new USB protocol based computer acceleration device that uses multi-channel single-level cell NAND type flash memory (SLC NAND) and Dynamic random-access memory (DRAM) cache. This device includes a main controller chip, at least one SLC NAND module, and a USB interface to connect the device to a computer. It then creates and assigns a cache file in SLC NAND and DRAM for the computer cache system, caches the common used applications, and read and pre-reads frequently used files. The device drive improves the USB protocol, optimizes the BOT protocol in the traditional USB interface protocol, and optimizes resource allocation for the USB transport protocol.The algorithm and framework of the device employ the following design:1. The device virtualizes the application programs for pre-storing all program files and the system environment files required by programs into the device.2. The device works in multi I / O channel mode, an array module integrates an array of SLC NAND chips and uses main controller chip that can deal with multi I / O channel.3. By monitoring long-term user habits, data that will be used by system can be estimated, and the data can be pre-stored in the device.4. The device allows intelligent compression and automatic release of system memory in background.
Owner:WEIJIA ZHANG
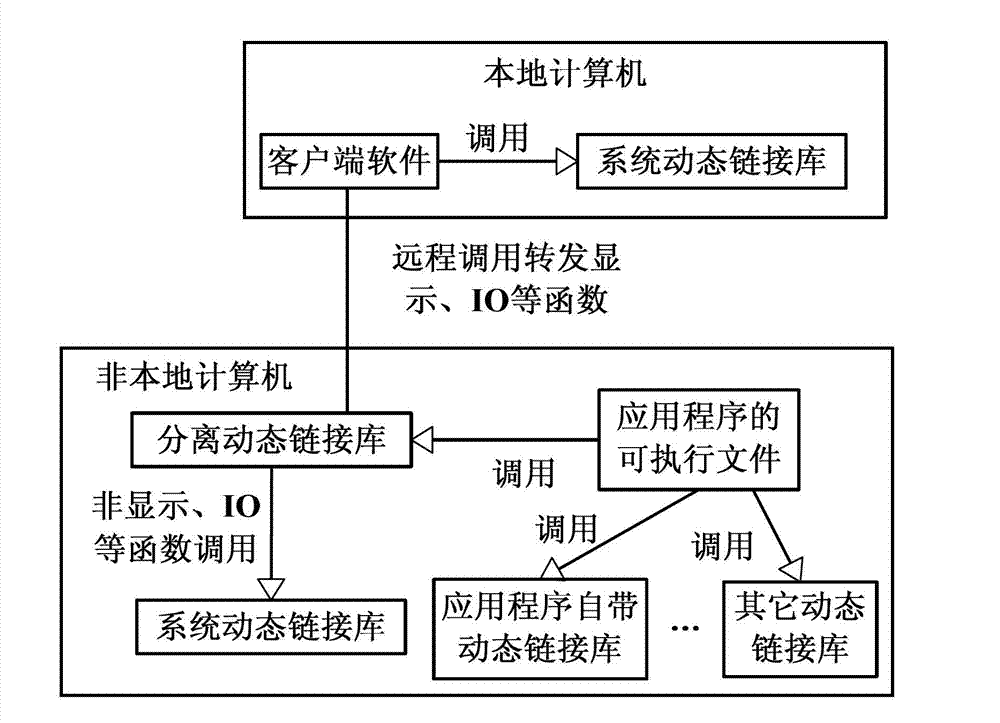
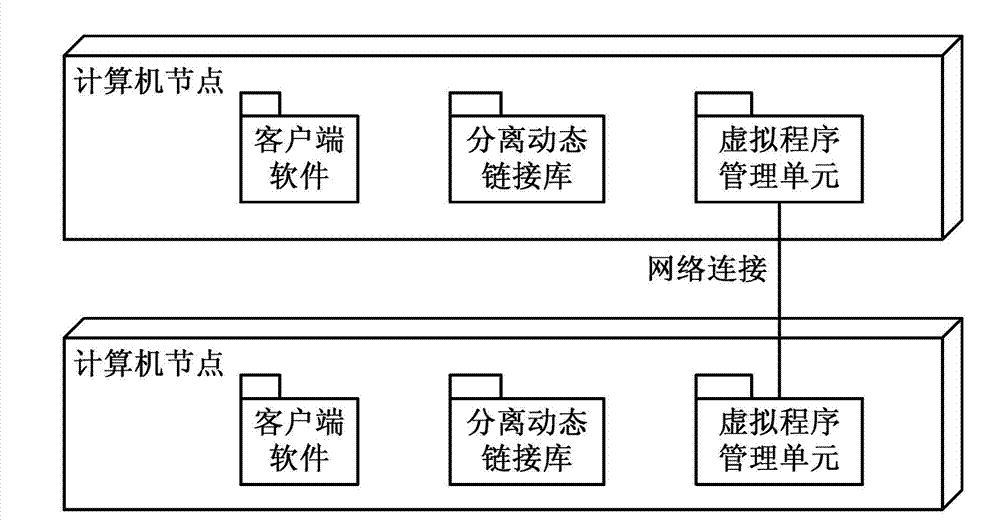
Realization method and realization system of distributed deployment application program based on input/output (IO) decoupling
ActiveCN103036959AGuaranteed uptimeGuaranteed execution resultsTransmissionSoftware simulation/interpretation/emulationProgram managementOperational system
The invention discloses a realization method and a realization system of a distributed deployment application program based on input / output (IO) decoupling, and relates to a virtual machine. The realization system comprises client software, a separation dynamic link library and a virtual program management unit, wherein the separation dynamic link library is located between executable program of a server end and a system dynamic link library, the separation dynamic link library invokes and transfers the functions about displaying and an IO part to a local end to execute by means of remote procedure call (RPC), and the functions about the displaying and the IO part comprise all the functions related to man-machine interface interaction, graphical display, file IO and network IO. The realization method and the realization system of the distributed deployment application program the IO decoupling based on the IO decoupling separate the logic part of an application program from the display and the IO part, do not change the application program and other parts, and enable the application program to be virtualized, the virtualized granularity is relatively low, the excitation effect of a virtualization program is the same as that of the local program, the interactively between the virtualization program and the other local programs is good, and the consumption of resources of a operation system of the virtual machine is reduced.
Owner:WUHAN POST & TELECOMM RES INST CO LTD
A virtualization system and method based on xen secure computer trusted device
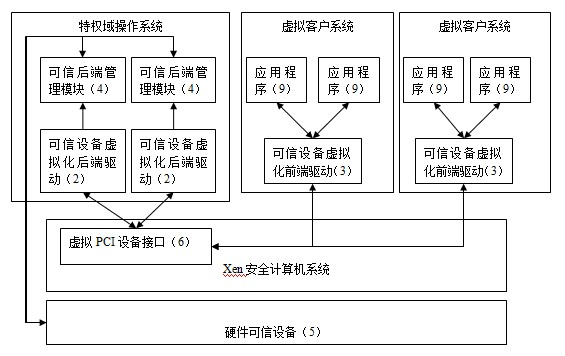
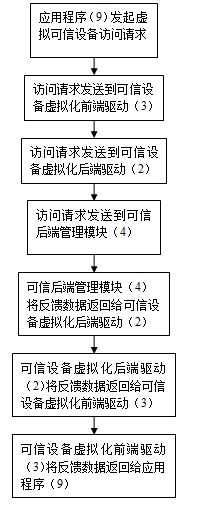
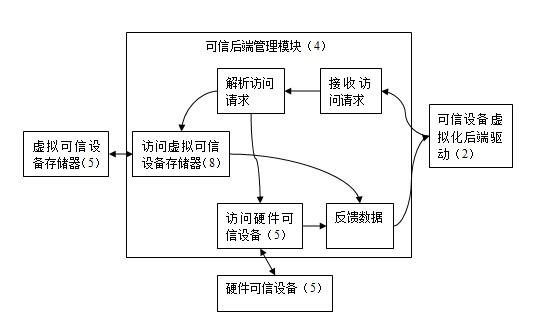
InactiveCN102289620AEasy accessEnsure crediblePlatform integrity maintainanceVirtualizationTrusted hardware
The invention belongs to the application field of virtualization technology, and in particular relates to a virtualization system and method based on a Xen secure computer trusted device. The system includes a virtual trusted device, and the virtual trusted device includes a trusted device virtualization back-end driver, a trusted device virtualization front-end driver and a trusted back-end management module; the trusted device virtualization front-end driver is set in the virtual client system In the virtual client system, there is also an application program, and the application program is connected to the trusted device virtualization back-end driver set in the privileged domain operating system through the trusted device virtualization front-end driver; the trusted back-end management module is set in the privileged domain In the domain operating system, it is connected with the trusted device virtualization back-end driver and the hardware trusted device. The invention provides trusted device services for the virtual client system under the condition of ensuring the credibility of the virtual client operating system, relieves the dependence of the original trusted device virtualization technology on the trusted device simulation tool, and realizes the domestic trusted device virtualization.
Owner:SOUTH CHINA UNIV OF TECH
Method and system for providing a deterministic virtual clock
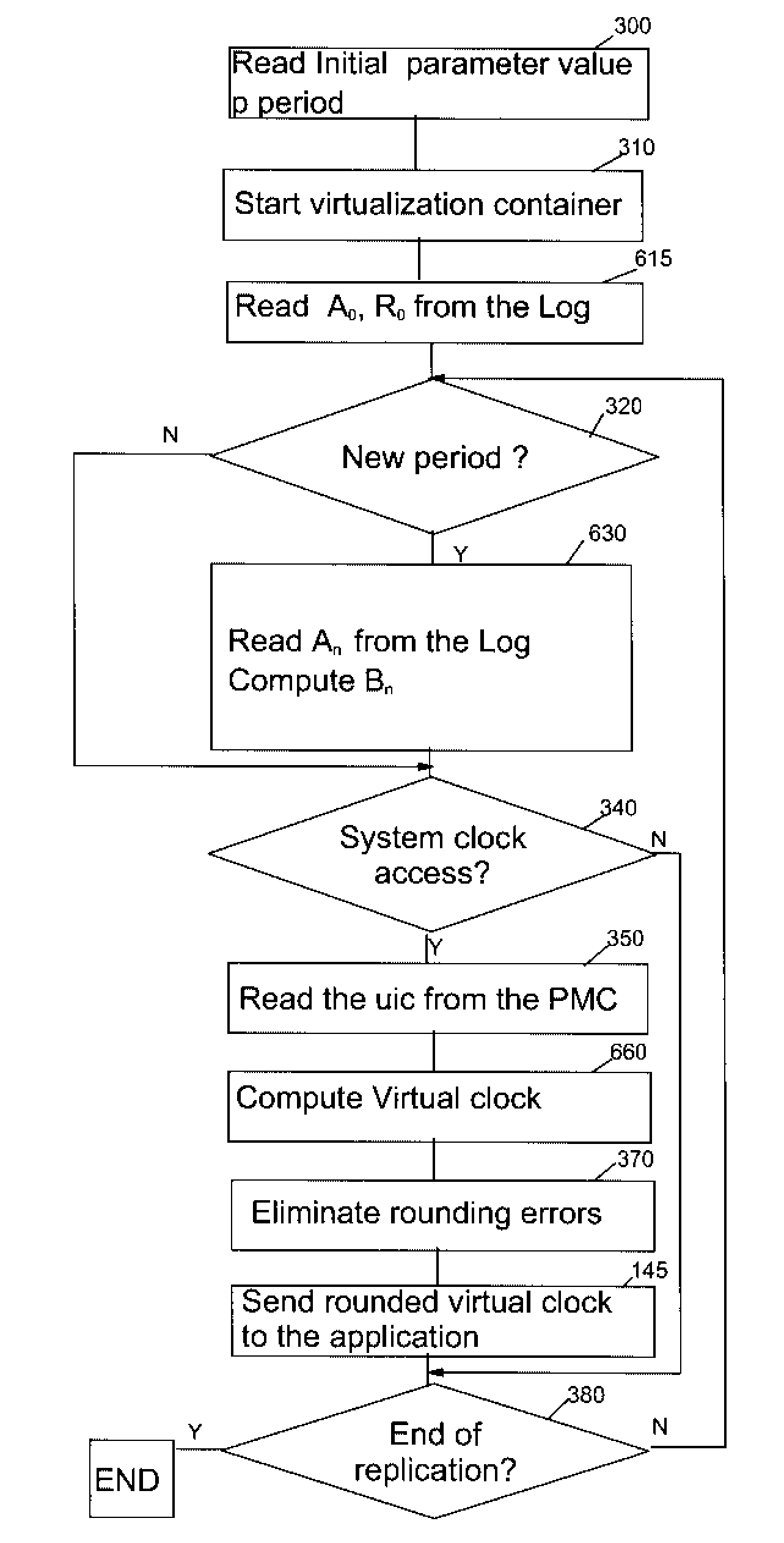
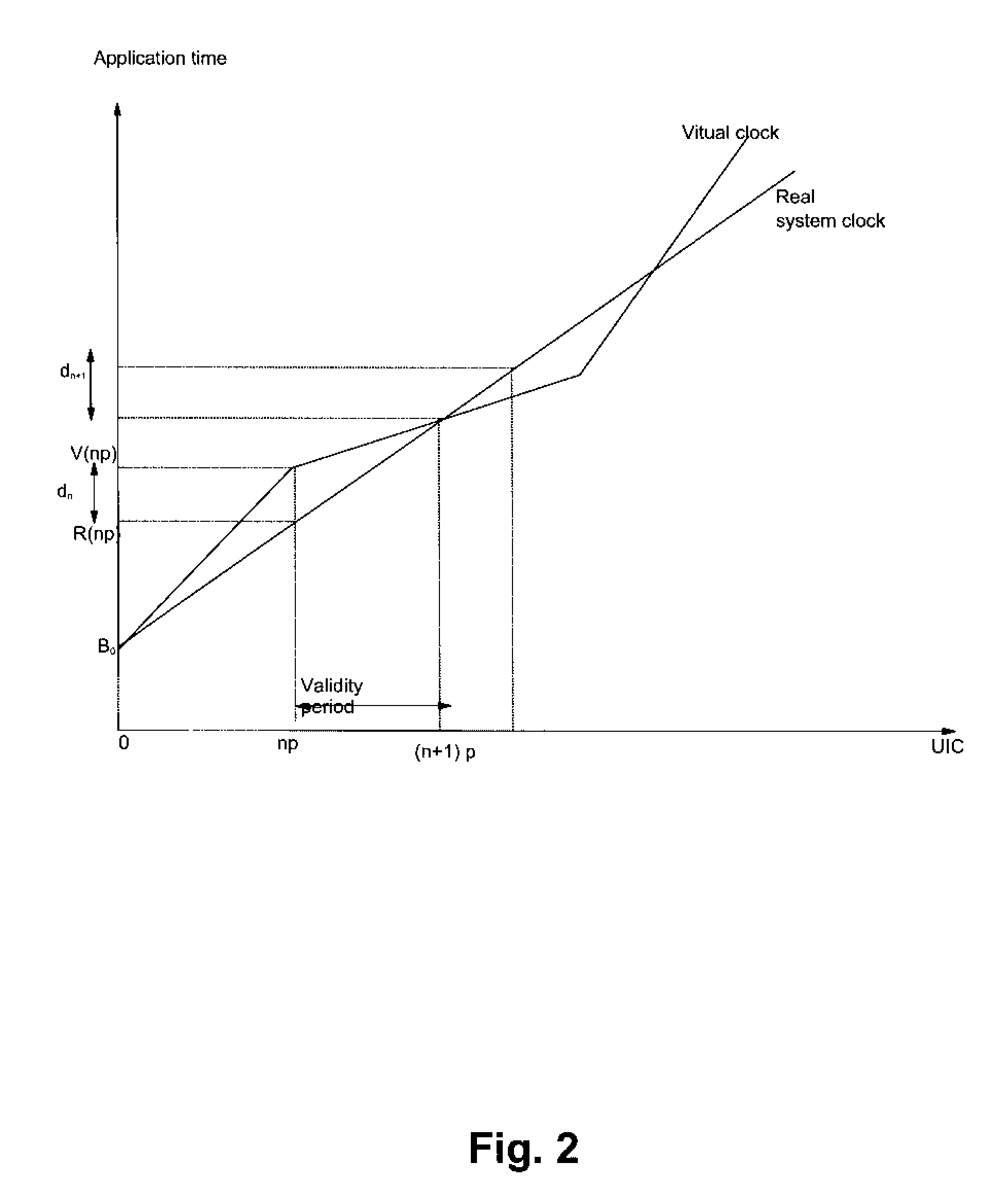
InactiveUS20080155299A1Efficient and reliableAllow useError detection/correctionGenerating/distributing signalsVirtualizationComputer hardware
A method and system for providing a virtual clock on a computer by multiplying the number of instructions executed by the average instruction execution time. It is however not reliable to use this generic computation for virtualization of application in a fault tolerant system because the virtual clock computed like this quickly deviates from the system clock. A virtual clock computation is provided which includes periodic readjustment of the virtual to the system clock. Also, the errors coming from rounding of the number of executing instruction are suppressed.Taking the assumption that the user instruction counters are maintained synchronized in the operational and the replication computers, replacing the system clock access by a virtual clock when virtualizing applications thus turning the system clock acquisition into a deterministic event. Replicating the system clock access can be thus done by reexecuting the application code in the replication machine avoiding transfer of information at each system clock access of the virtualized application programs.
Owner:IBM CORP
System and method for hybrid kernel—and user-space incremental and full checkpointing
A system includes a multi-process application that runs on primary hosts and is checkpointed by a checkpointer comprised of a kernel-mode checkpointer module and one or more user-space interceptors providing at least one of barrier synchronization, checkpointing thread, resource flushing, and an application virtualization space. Checkpoints may be written to storage and the application restored from said stored checkpoint at a later time. Checkpointing may be incremental using Page Table Entry (PTE) pages and Virtual Memory Areas (VMA) information. Checkpointing is transparent to the application and requires no modification to the application, operating system, networking stack or libraries. In an alternate embodiment the kernel-mode checkpointer is built into the kernel.
Owner:IBM CORP
Device and system for cloud based mobile application virtualization
ActiveUS20180109624A1Increased app densityHigh densityTransmissionSecurity arrangementVirtualizationSession management
Owner:SIERRAWARE LLC
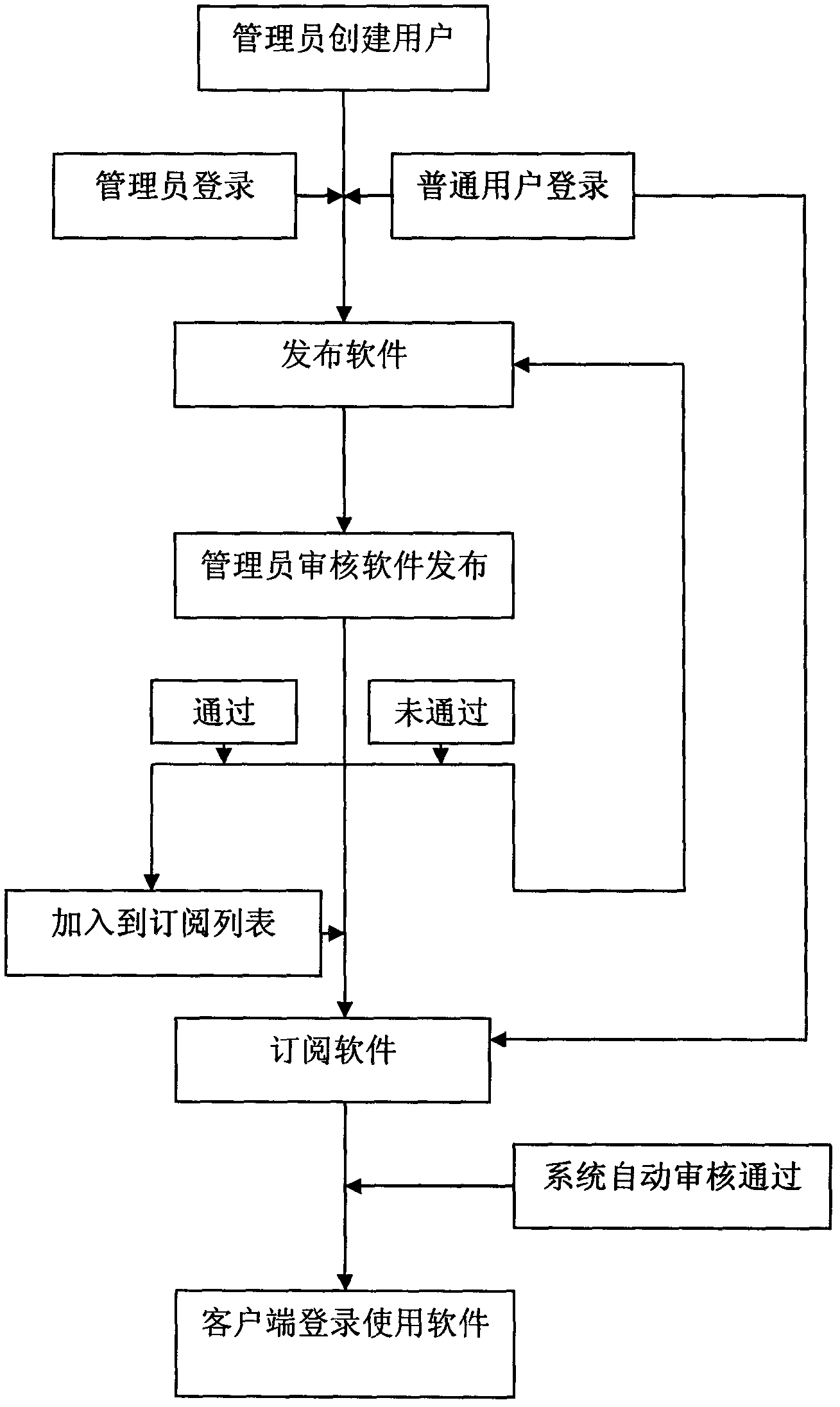
Application virtualization technology based on cloud platform
The invention provides an application virtualization technology based on a cloud platform. The application virtualization technology based on the cloud platform provides release and personalized customization service of various operation system application programs, customizes various application programs after conducting identity authentication of a user through a customer terminal based on web. The user can use the application programs through various cloud platforms after the customization is finished. According to the core of the technology, the application virtualization technology based on the cloud platform allows the user to obtain a virtual operation environment of software through internet without installation of software, can directly operate the software in a virtual environment, provide an effective method of resource share and resource saving for a company and not only improve using efficiency of resources but also facilitate customers.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Method for implementing portable mobile desktop terminal
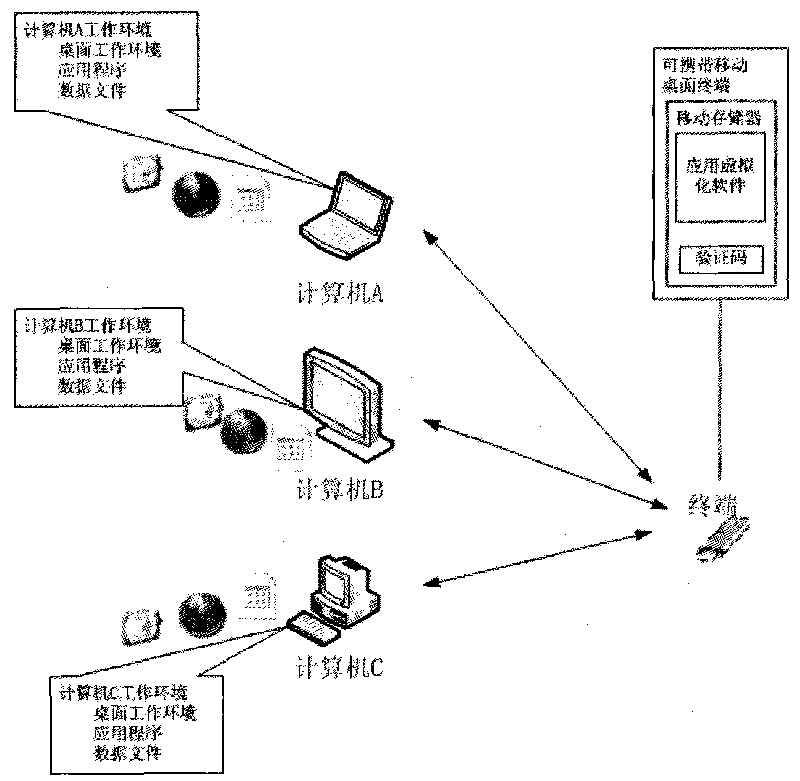
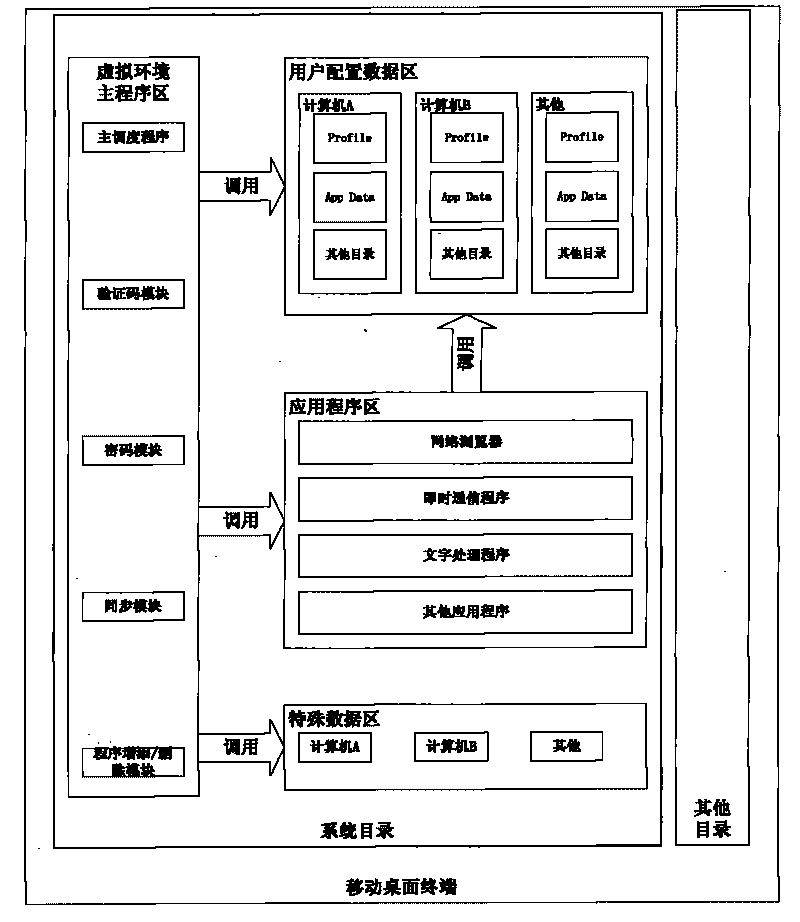
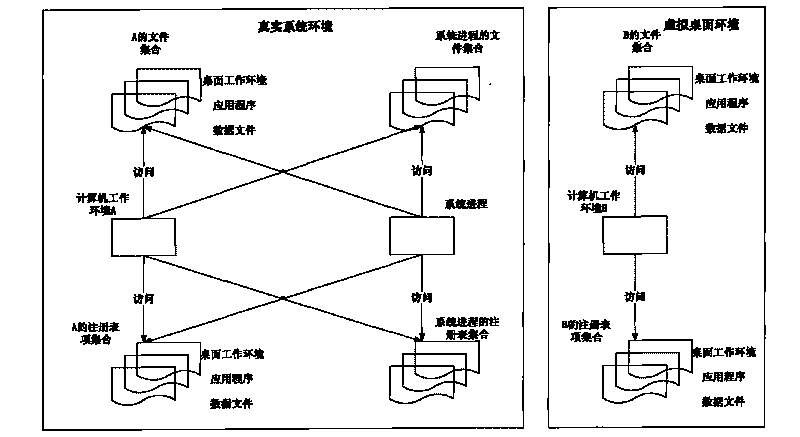
InactiveCN101710290AAvoid security issuesSolve the problem of not easy to carryProgram loading/initiatingData synchronizationVirtualization
The invention provides a method for implementing a portable mobile desktop terminal, which is applied to a Windows XP operating system platform. The portable mobile desktop terminal comprises a mobile memory with a USB interface, a set of application virtualization software loaded in the memory and an identification code corresponding to the memory. When the terminal is connected to a computer through a USB port for use, the software loaded in the memory is automatically loaded to run in the computer. A virtual computer working environment integrated in the portable mobile desktop terminal comprises a desktop working environment, an application program, a data file and the like; in addition, the virtual computer working environment can be isolated from the real computer working environment, and the data synchronization and switch can be performed between the two working environments if necessary so as to realize an application virtualization technology-based solution for the portable mobile desktop terminal.
Owner:SOUTHEAST UNIV
Dynamic local function binding apparatus and method
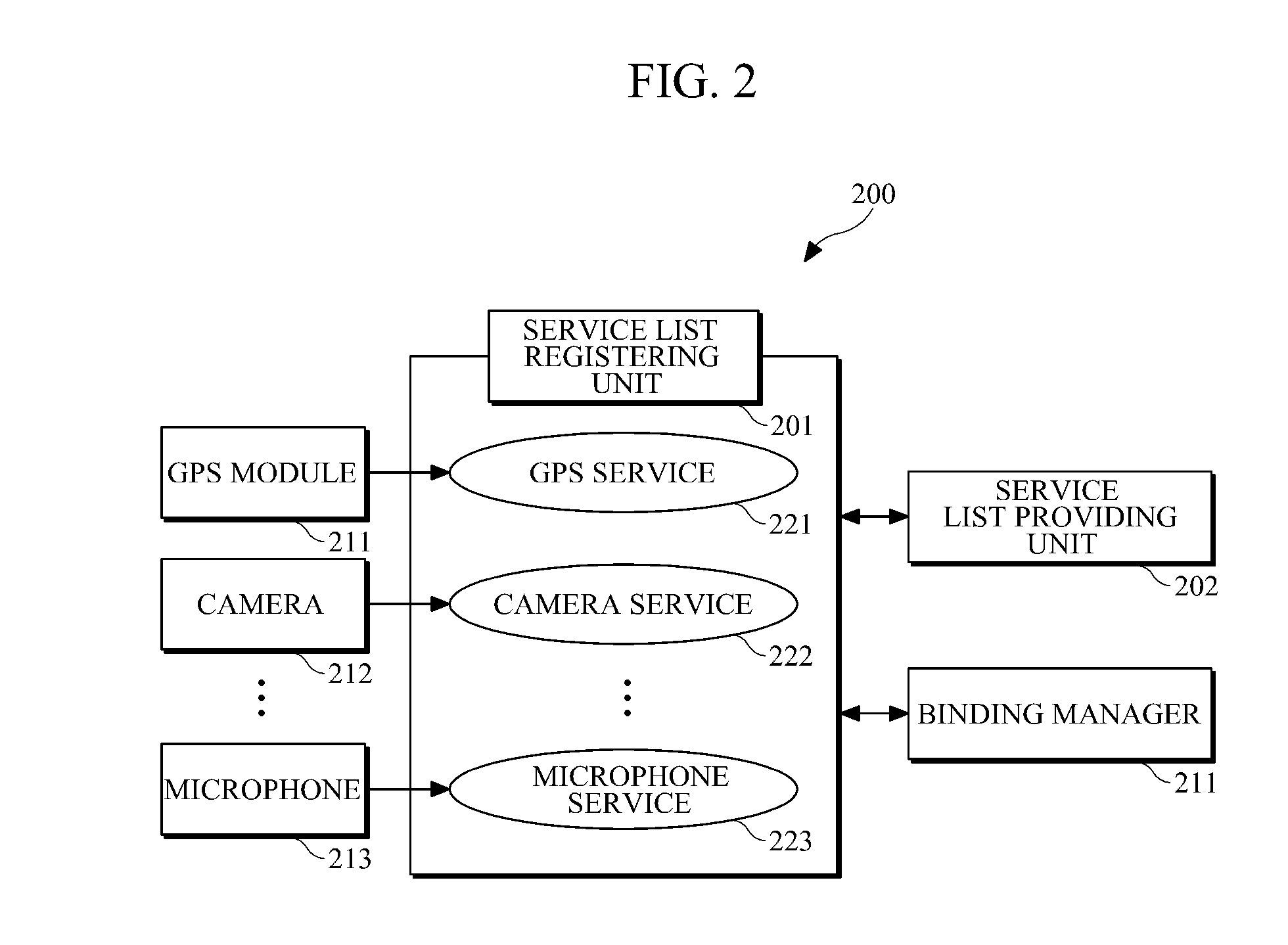
ActiveUS20110138016A1Substation remote connection/disconnectionMultiple digital computer combinationsVirtualizationComputer network
A dynamic local function binding apparatus and method are provided. In an application virtualization environment, a terminal may register local services associated with local functions of the terminal, and a remote server may call the serviced local functions to be used while the server is executing an application for the terminal. The local functions may be unique functions of various local devices installed in the terminal. The servicing of the local functions may include creating service descriptions of the functions that are provided by the individual local devices and publishing the service descriptions.
Owner:SAMSUNG ELECTRONICS CO LTD
System and method for hybrid kernel and user-space checkpointing using a character device
ActiveUS9164843B1Redundant operation error correctionElectrical componentsVirtualizationOperational system
A system, method, and computer readable medium for hybrid kernel-mode and user-mode checkpointing of multi-process applications. The computer readable medium includes computer-executable instructions for execution by a processing system. A multi-process application runs on primary hosts and is checkpointed by a checkpointer comprised of a kernel-mode checkpointer module and one or more user-space interceptors providing barrier synchronization, checkpointing thread, resource flushing, and an application virtualization space. Checkpoints may be written to storage and the application restored from said stored checkpoint at a later time. Checkpointing is transparent to the application and requires no modification to the application, operating system, networking stack or libraries. In an alternate embodiment the kernel-mode checkpointer is built into the kernel.
Owner:PHILIPS NORTH AMERICA LLC
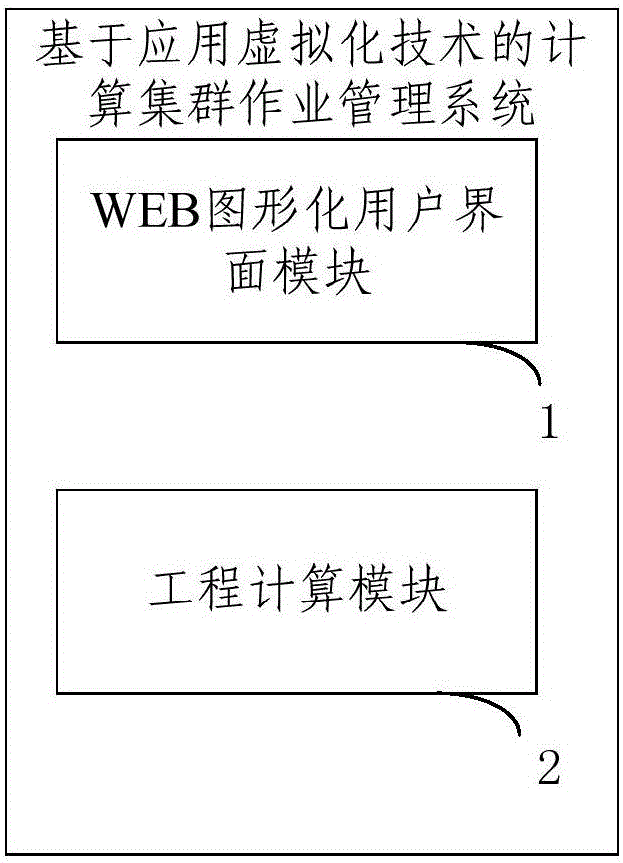
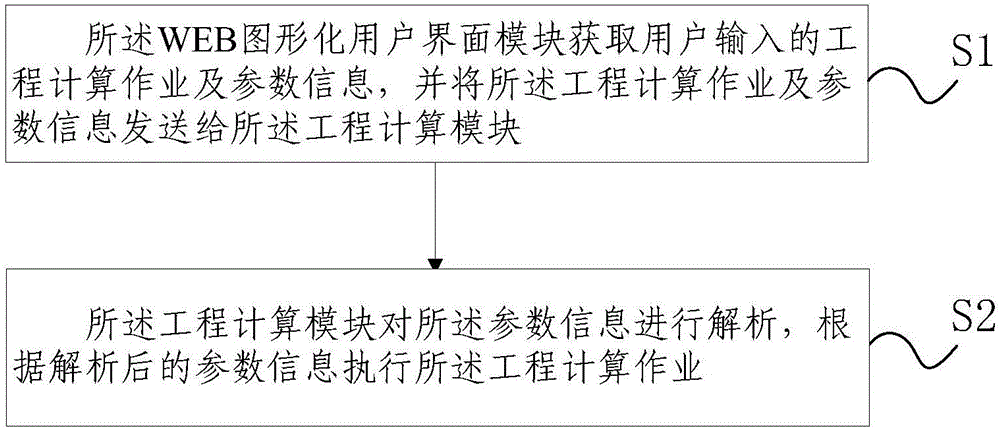
Application virtualization technique based computing cluster job management system and method
InactiveCN106227397AImprove management efficiencyReduce complexityHardware monitoringMultiple digital computer combinationsVirtualizationUser input
The invention discloses an application virtualization technique based computing cluster job management system and method through which engineering computing job can be managed effectively, and complexity in high-performance computing cluster operation and maintenance is lowered. The system comprises a WEB graphic user interface module and an engineering computing module; wherein, the WEB graphic user interface module is used for acquiring engineering computing job and parameter information inputted by a user, and transmitting the engineering computing job and parameter information to the engineering computing module; the engineering computing module is deployed on a high-performance computing cluster, and is used for analyzing the parameter information and executing the engineering computing job according to the analyzed parameter information; the WEB graphic user interface module is further used for monitoring the running status of the cluster.
Owner:BEIJING COMPUTING CENT
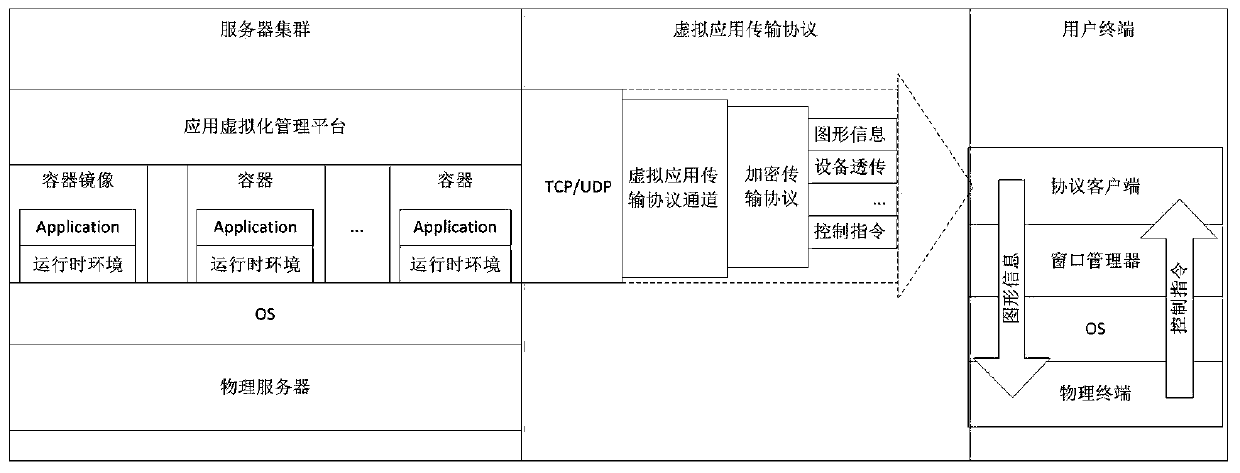
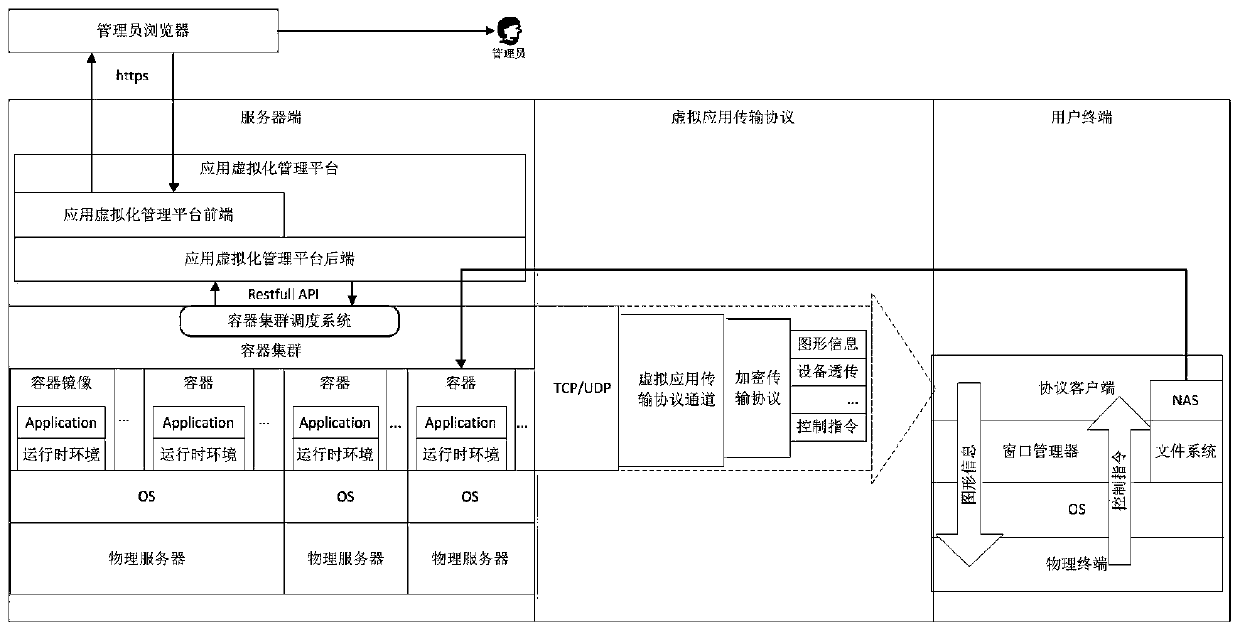
Application virtualization method and system based on container technology
ActiveCN111061540AImprove the isolation effectReduce overheadTransmissionEnergy efficient computingVirtualizationTransmission protocol
The invention relates to an application virtualization method and system based on a container technology, and belongs to the technical field of computer science. According to the invention, the methodincludes removing a virtual OS layer virtualized by a traditional application; packaging a runtime environment of the application program by using a container technology; finishing computing logic ofan application program at a server side by customizing a remote application transmission protocol, pushing graphical interface rendering of the application program and user interaction to a client side to be carried out, so isolation between users can be enhanced, system safety can be improved, resource expenditure can be reduced, and the resource utilization rate can be increased.
Owner:BEIJING INST OF COMP TECH & APPL
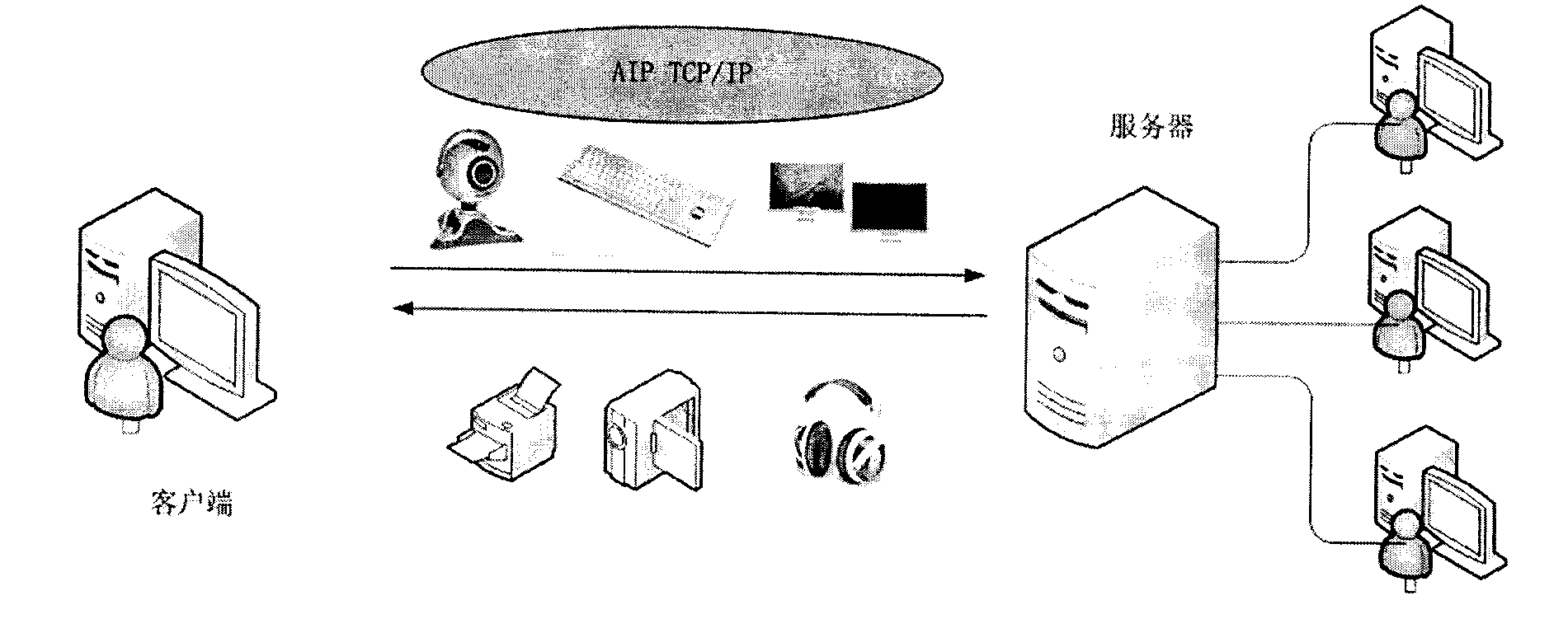
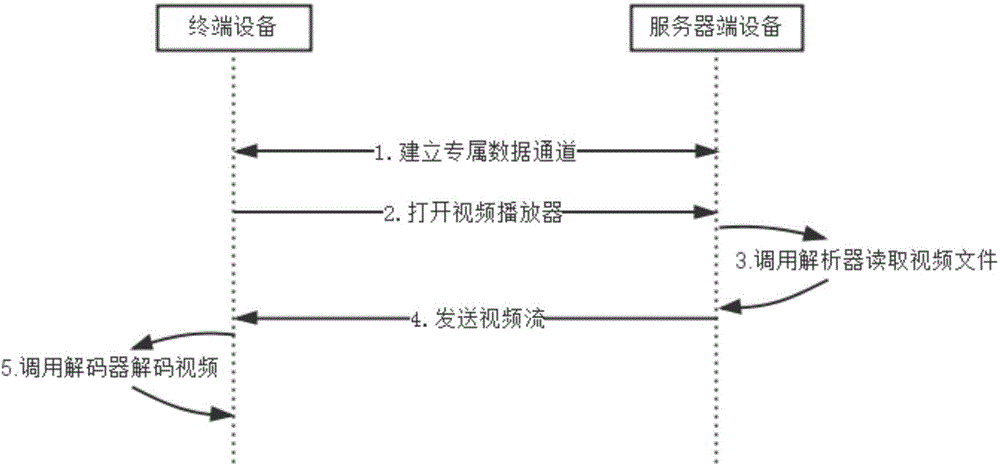
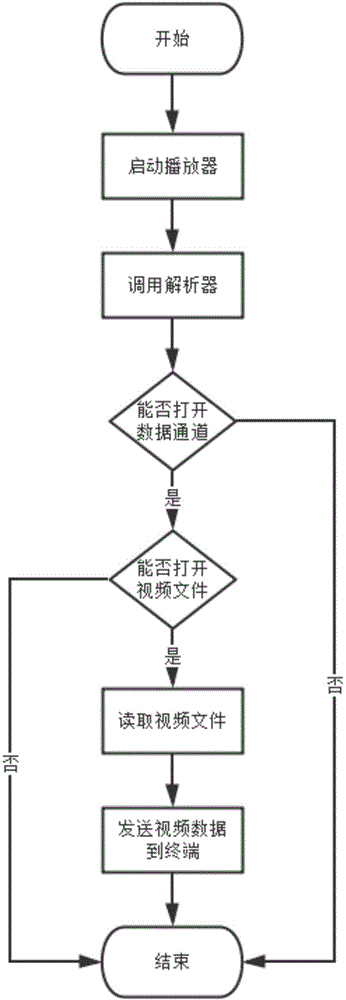
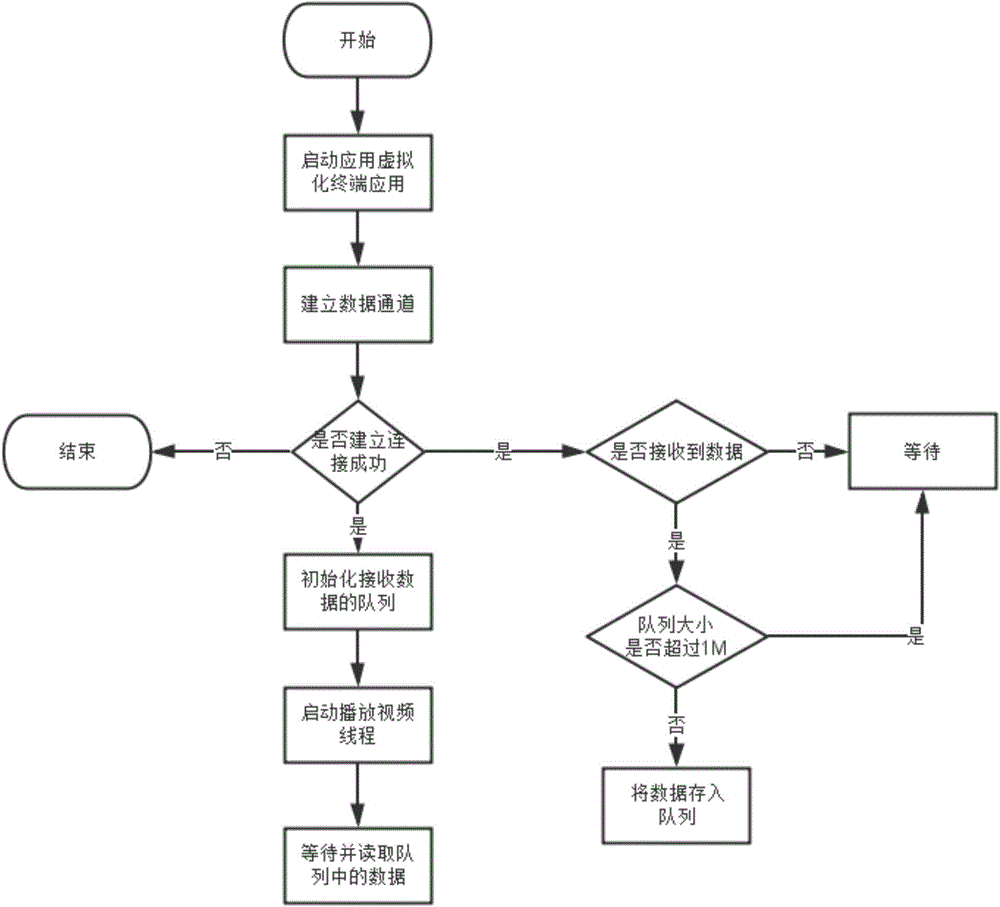
Video redirecting system and method based on application virtualization technology
InactiveCN103957445AInnovative ideasEasy to implementSelective content distributionVirtualizationComputer hardware
The invention discloses a video redirecting system and method based on the application virtualization technology. The system comprises a terminal device and a server, wherein the application virtualization technology is applied to the terminal device and the server. A decoder module is integrated into the terminal device, a parser module is integrated into the server, and the decoder module and the parser module achieve data interaction through an exclusive data channel for the application virtualization technology. The parser module is firstly called by a player, video files are read by the parser module, video streams are sent to the terminal device through the exclusive data channel, and the video streams are separated and decoded by the decoder module. According to the video redirecting system and method based on the application virtualization technology, video playing is accomplished by a decoder integrated into a terminal, so that the formats of played videos are not restrained by video playing formats of the player of the server. Through the mode, a user processes the videos directly through the terminal device rather than the player of the server, and therefore user interaction speed can be increased effectively, and user experience can be effectively enhanced.
Owner:MASSCLOUDS
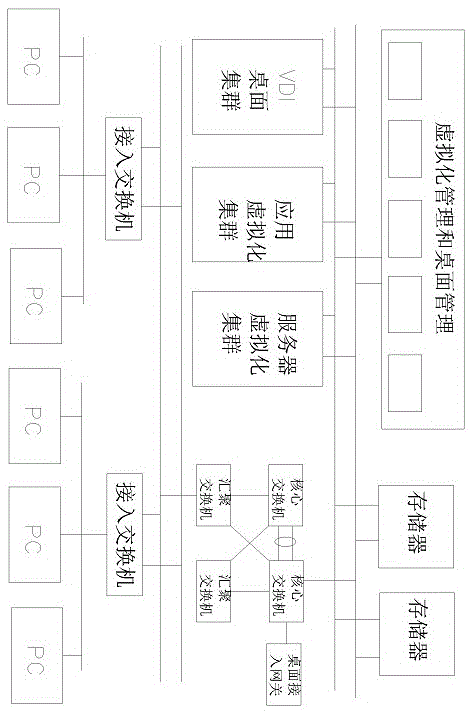
Desktop cloud system
InactiveCN105681424AImprove convenienceRealize centralized managementTransmissionExecution for user interfacesVirtualizationManagement unit
The invention relates to the technical field of the internet, specifically relates to a desktop cloud system. The system comprises an access layer and a desktop cloud layer; the access layer is equipped with multiple access switches; the multiple access switches are connected with multiple PC terminals; the desktop cloud system is equipped with a convergent switch, a core switch, a memory, a VDI desktop cluster, an application virtualization cluster, a server virtualization cluster, a virtualization management unit and a desktop management unit; the convergent switch is connected with the access switches; the core switch is connected with the convergent switch; the memory, the VDI desktop cluster, the application virtualization cluster, the server virtualization cluster, the virtualization management unit and the desktop management unit are all connected with the core switch. According to the desktop cloud system provided by the invention, the desktop, application issuing and server are virtualized through a virtualization technique; concentrated management is realized; and the reliability and availability are greatly improved.
Owner:巫立斌
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com