Android storage application sandbox based on application program virtualization, and communication method thereof
An application program and virtualization technology, applied in the field of communication, can solve problems such as violation of the homology model and poor security, and achieve the effect of improving communication security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0030] The technical solution of the present invention will be further described below in conjunction with the accompanying drawings.
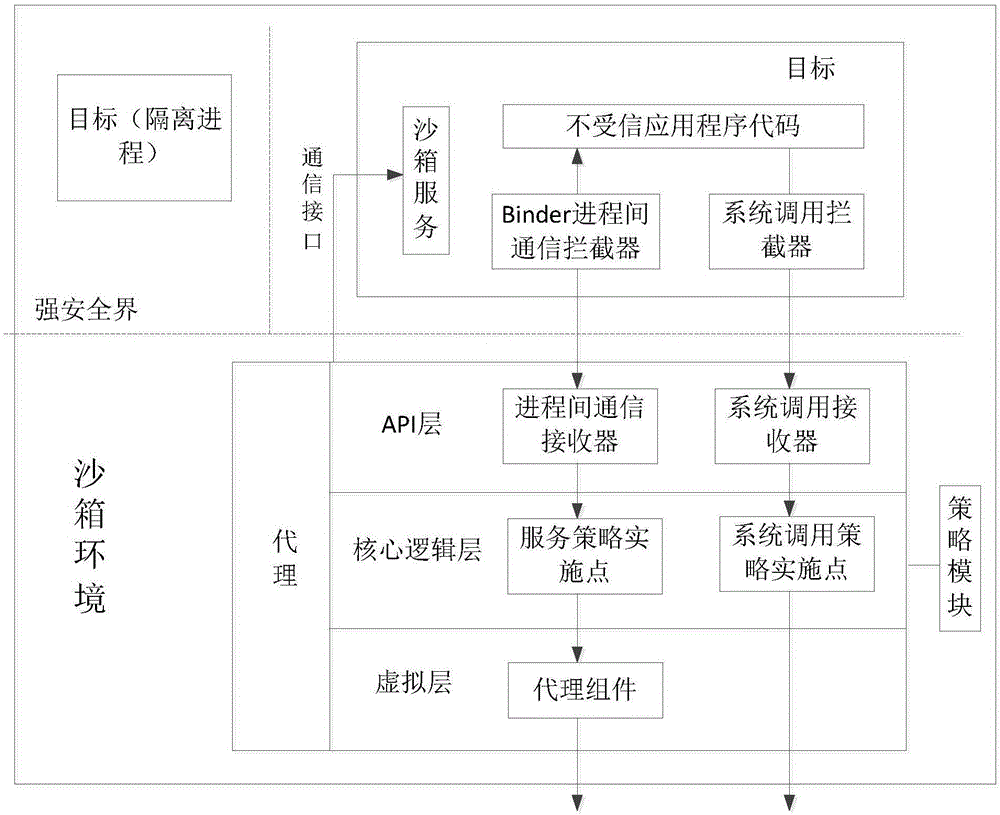
[0031] like figure 1 As shown, the Android storage application sandbox based on application virtualization includes an agent running in a permission control process and one or more targets running in an isolated process. strong security circle;
[0032] The agent is an application program process, has all platform permissions assigned by the system, and can interact normally with the Android middleware as a mandatory agent for all interactions between the target and the Android system; the agent includes an API layer, a core logic layer and a virtual layer:
[0033] API layer: including inter-process communication receivers and system call receivers;
[0034] Core logic layer: Implement policy enforcement points for Binder inter-process communication and system calls, and provide basic functions for applications by replicating the functions ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com