Method for realizing safe working environment based on virtualization technology
A virtualization technology and security work technology, applied in the field of virtualization technology application and Windows driver development, it can solve the problems of inability to call each other, prevent interaction, and lengthy, and achieve the effect of convenient deployment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
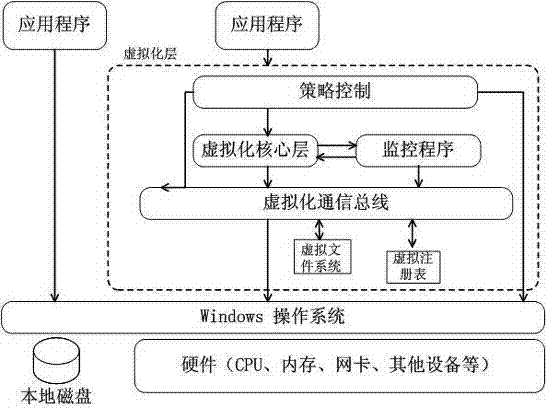
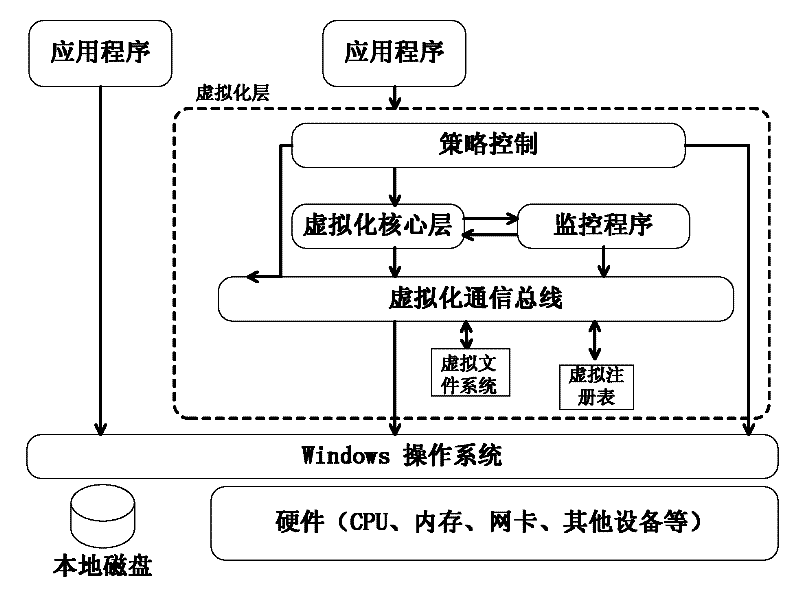
[0022] Such as figure 1 and figure 2 As shown, a method of realizing a safe working environment based on virtualization technology is to build a virtualization layer on the operating system, and use application virtualization technology to create a virtualized safe working environment to accommodate multiple virtualized applications. The virtualized safe working environment is a virtualized file system, and the virtualized layer is composed of a policy control module, a virtualized core layer module, a monitoring module, a virtualized communication bus, a virtualized file system and a virtual registry.
[0023] The virtualized communication bus mainly completes the communication between the virtualized application programs and the communication and interaction between the virtualized application programs and the application programs installed on the PC; meanwhile, during the installation process of the application programs, the virtualized communication bus manages all standa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com