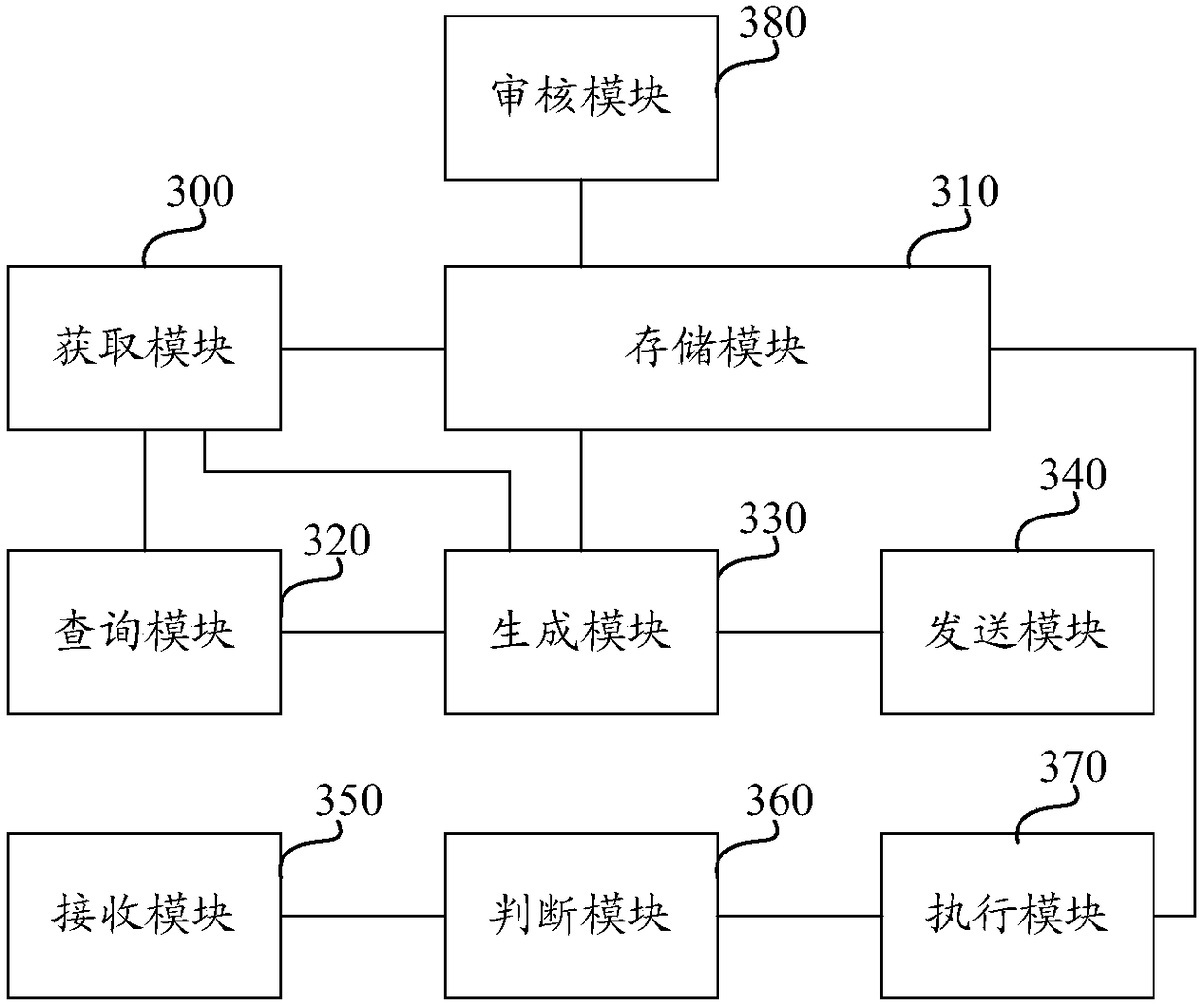
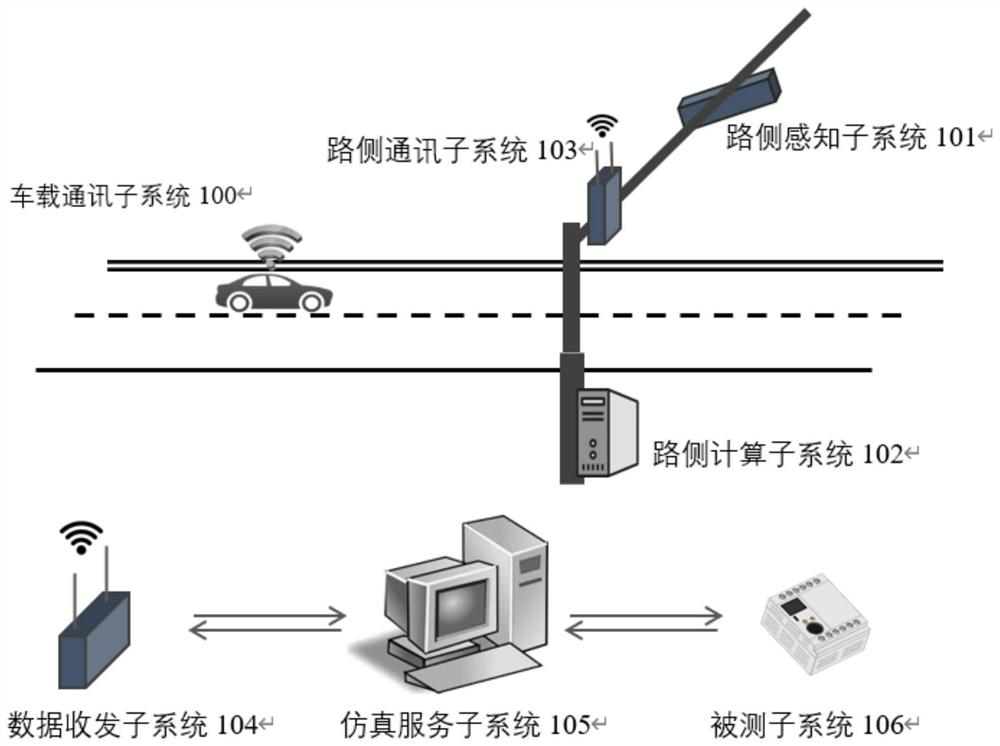
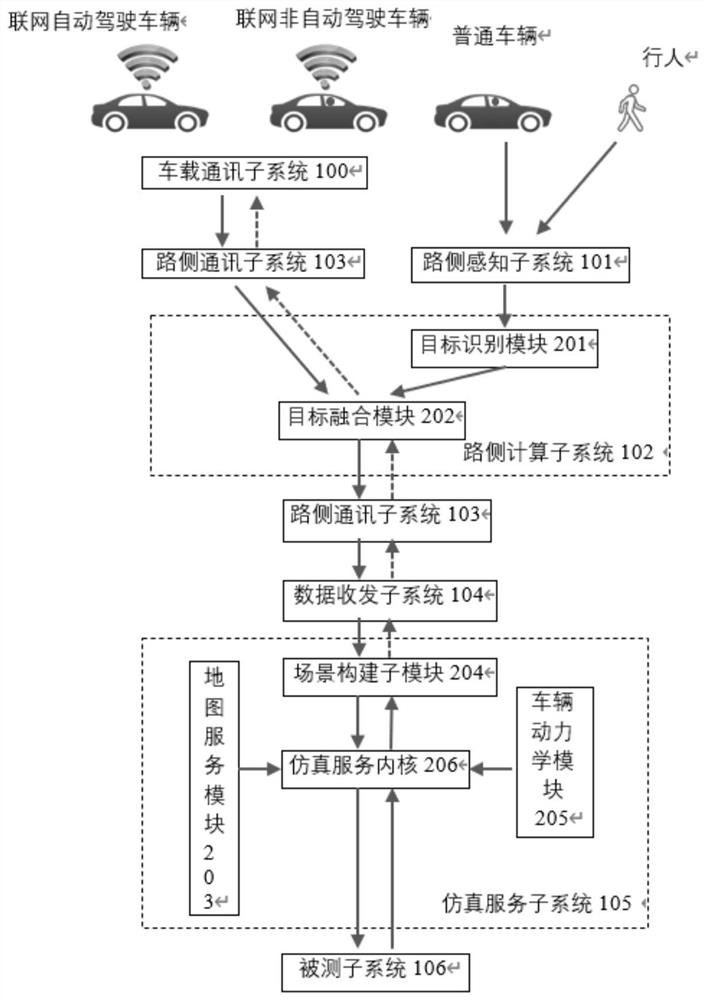
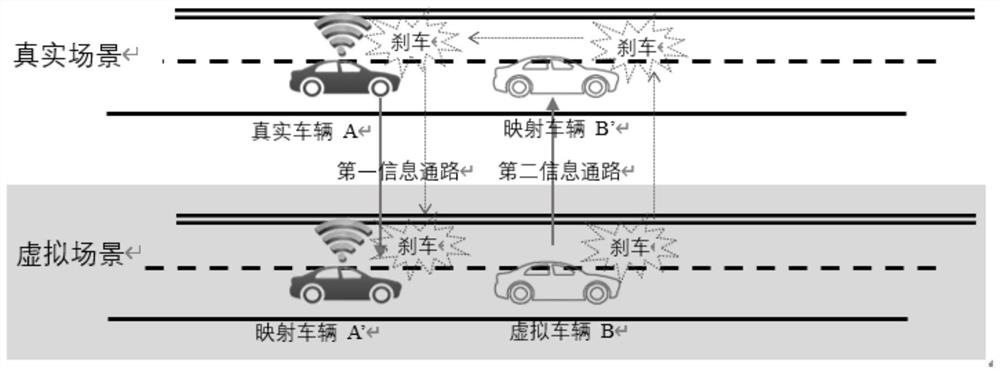
Patents
Literature
297results about How to "Ensure authenticity" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
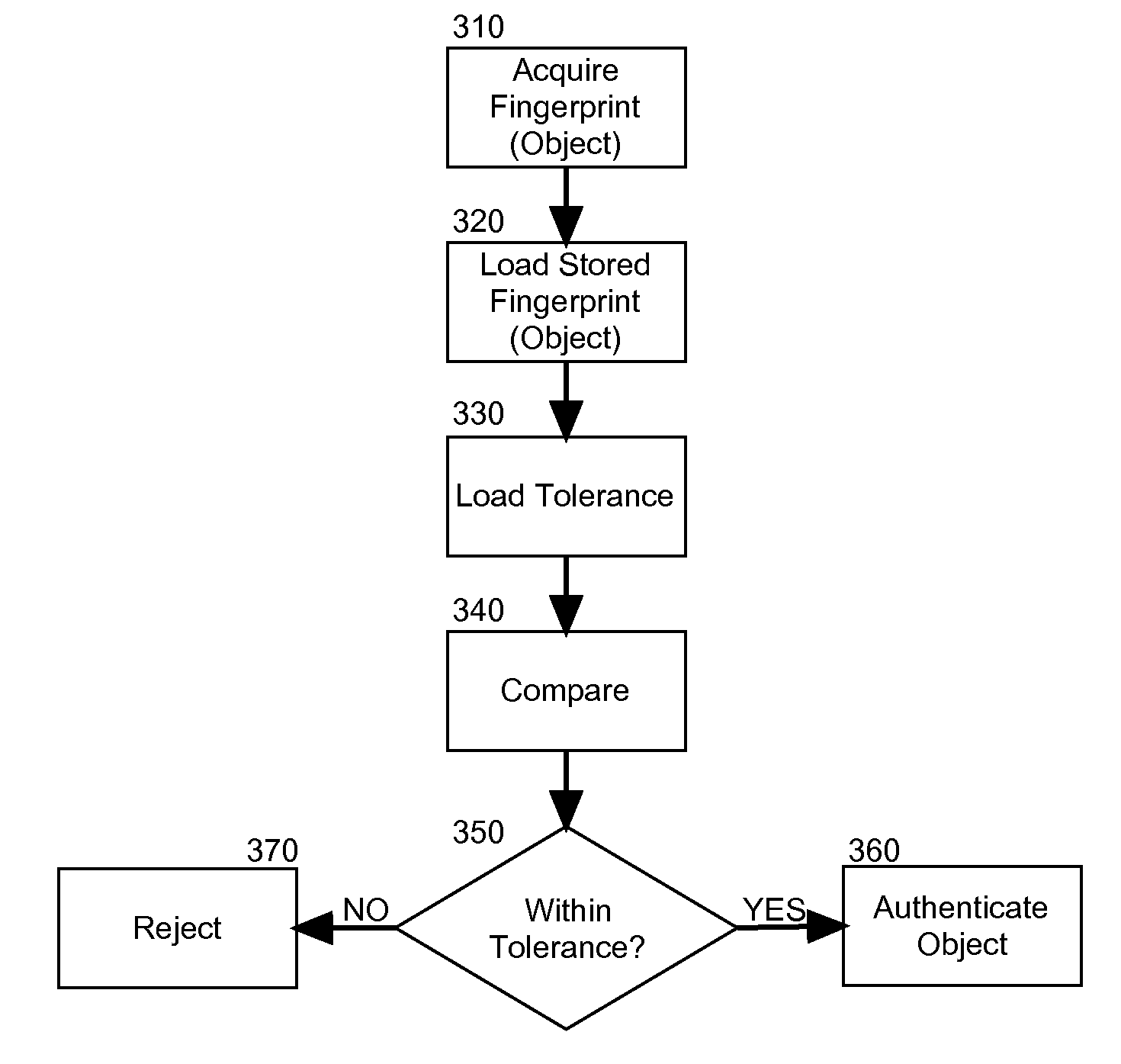
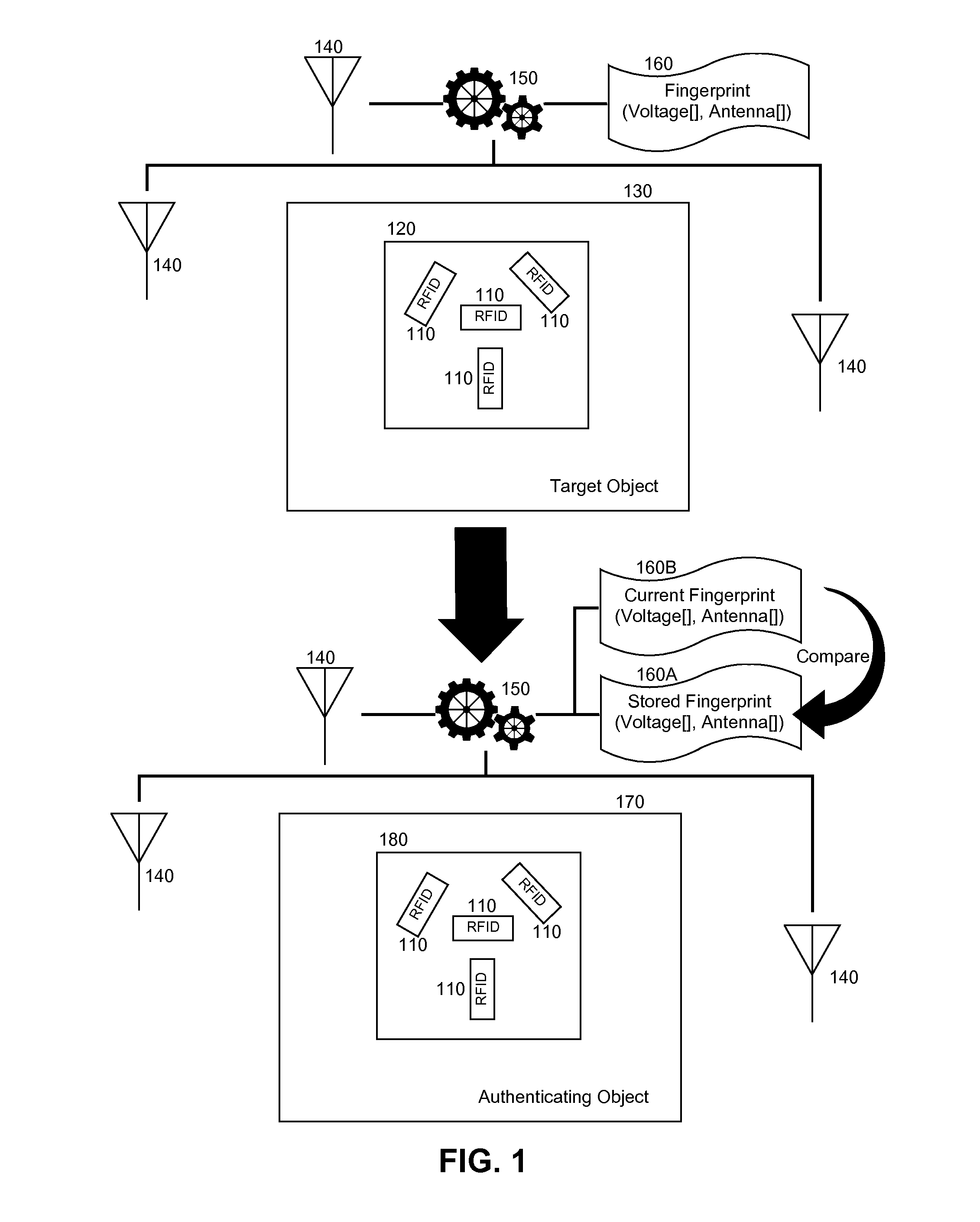
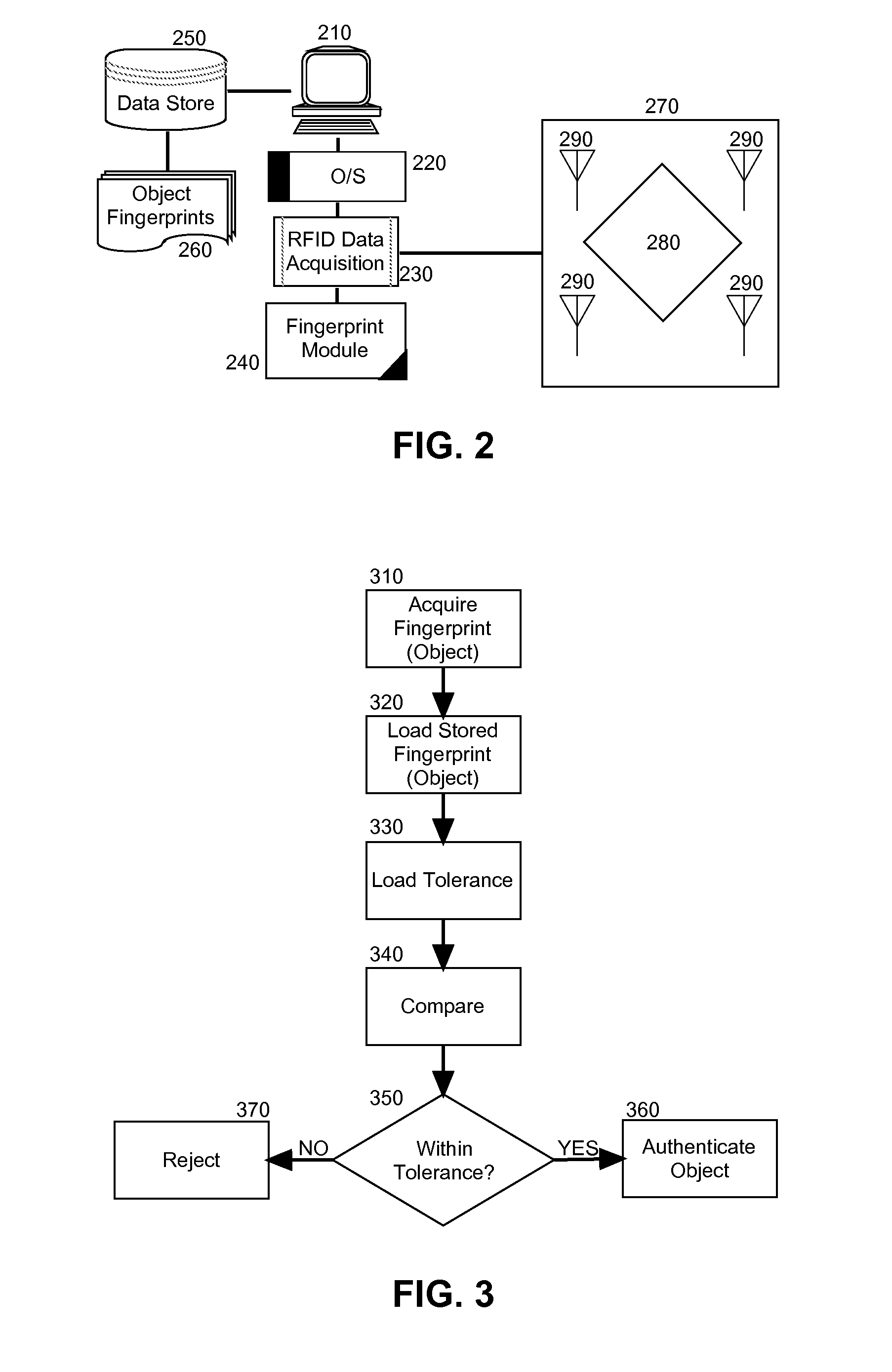
RFID fingerprint creation and utilization
InactiveUS20110068893A1Ensure authenticityProgramme controlElectric signal transmission systemsComputer hardwareRadio frequency
Embodiments of the present invention provide a method, system and computer program product for creating and managing radio frequency identification (RFID) fingerprints to ensure item authenticity. In an embodiment of the invention, an object fingerprint creation method can be provided. The method can include receiving a sensed signal from at least one RFID reader resulting from at least one RFID tag affixed to a target object. The method further can include extracting a voltage produced by the RFID tag from the sensed signal. Finally, the method can include storing the voltage as a fingerprint for the target object for later comparison with another fingerprint for an authenticating object to determine whether or not the authenticating object is the target object.
Owner:IBM CORP
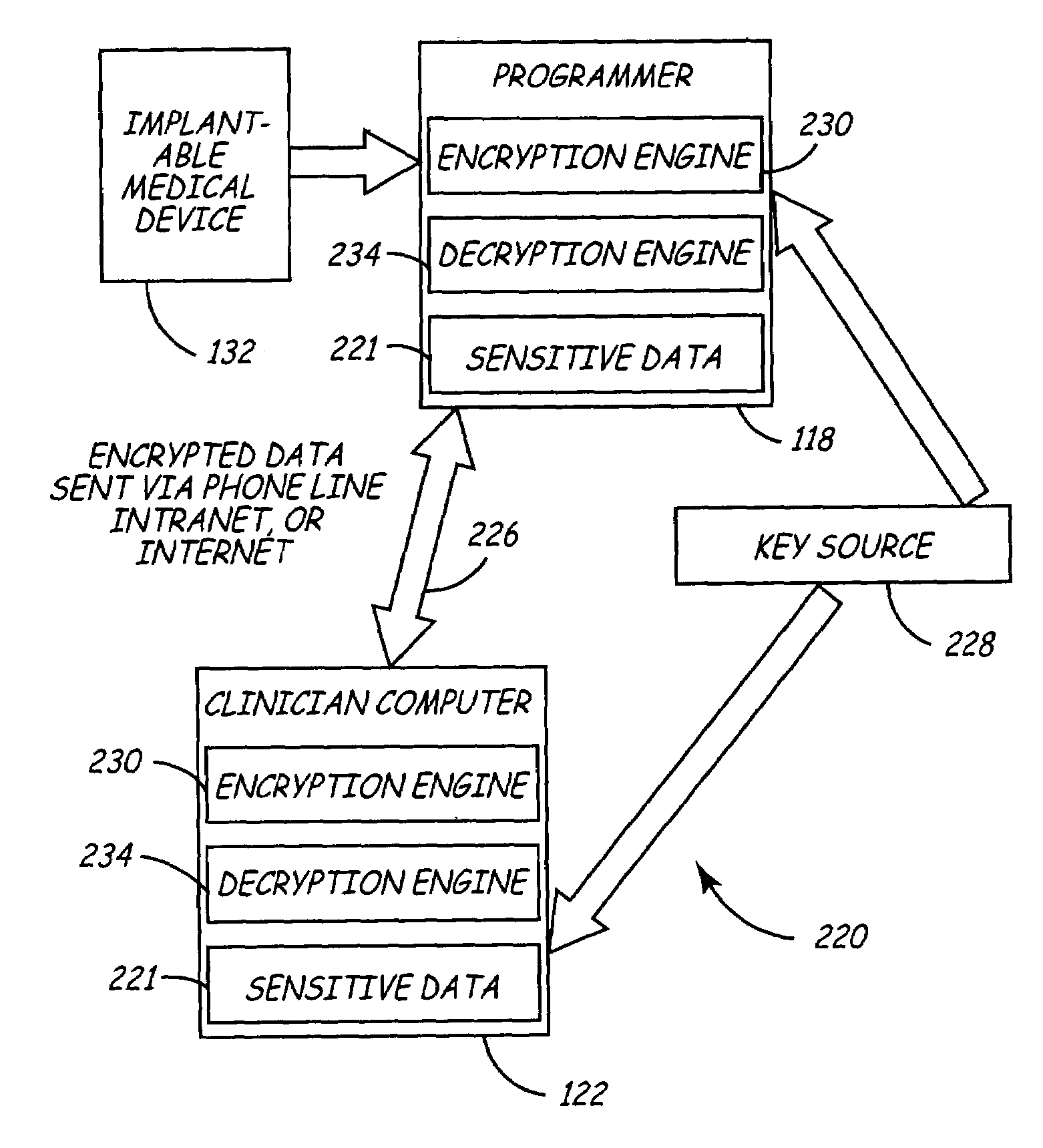
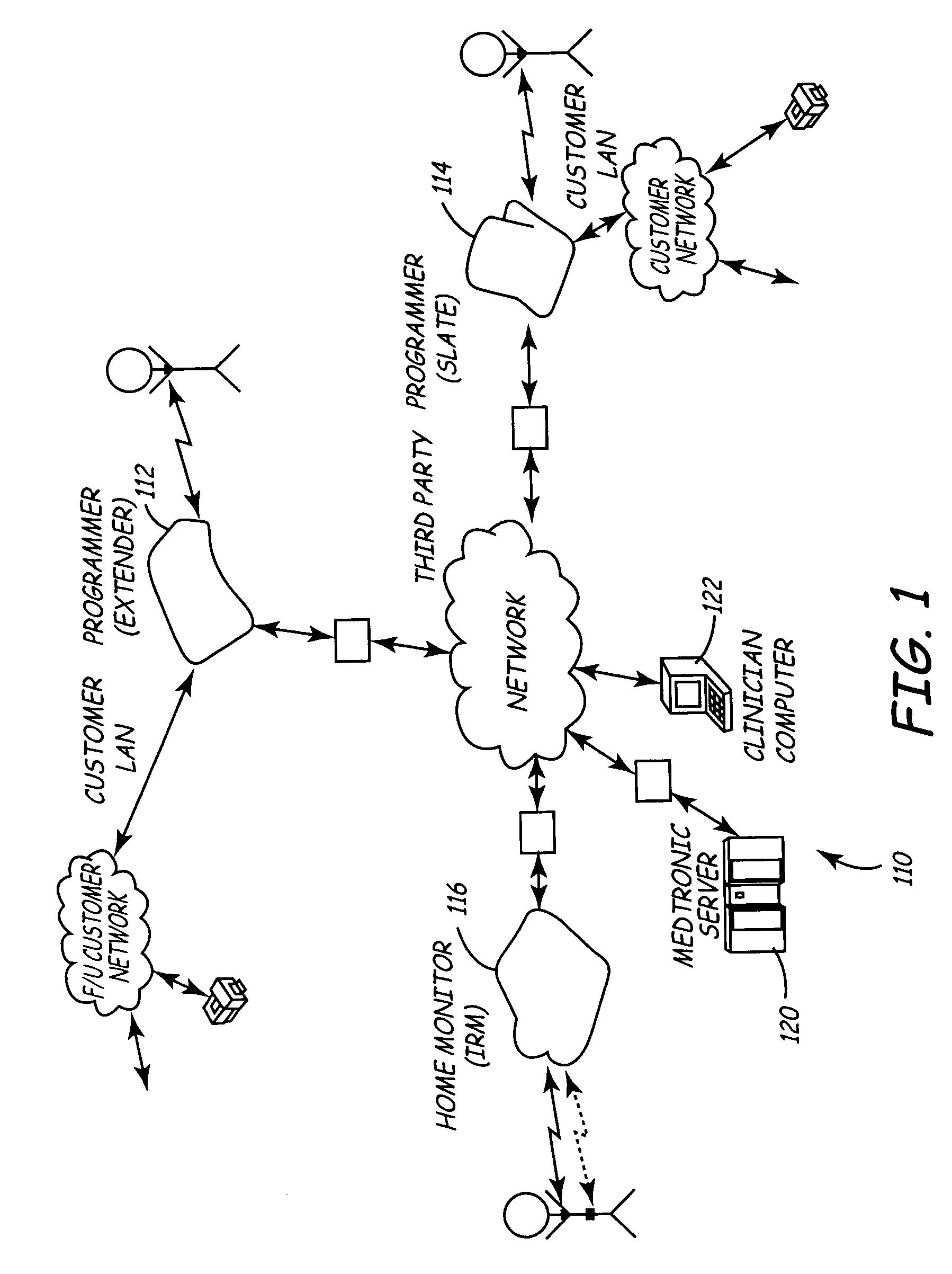
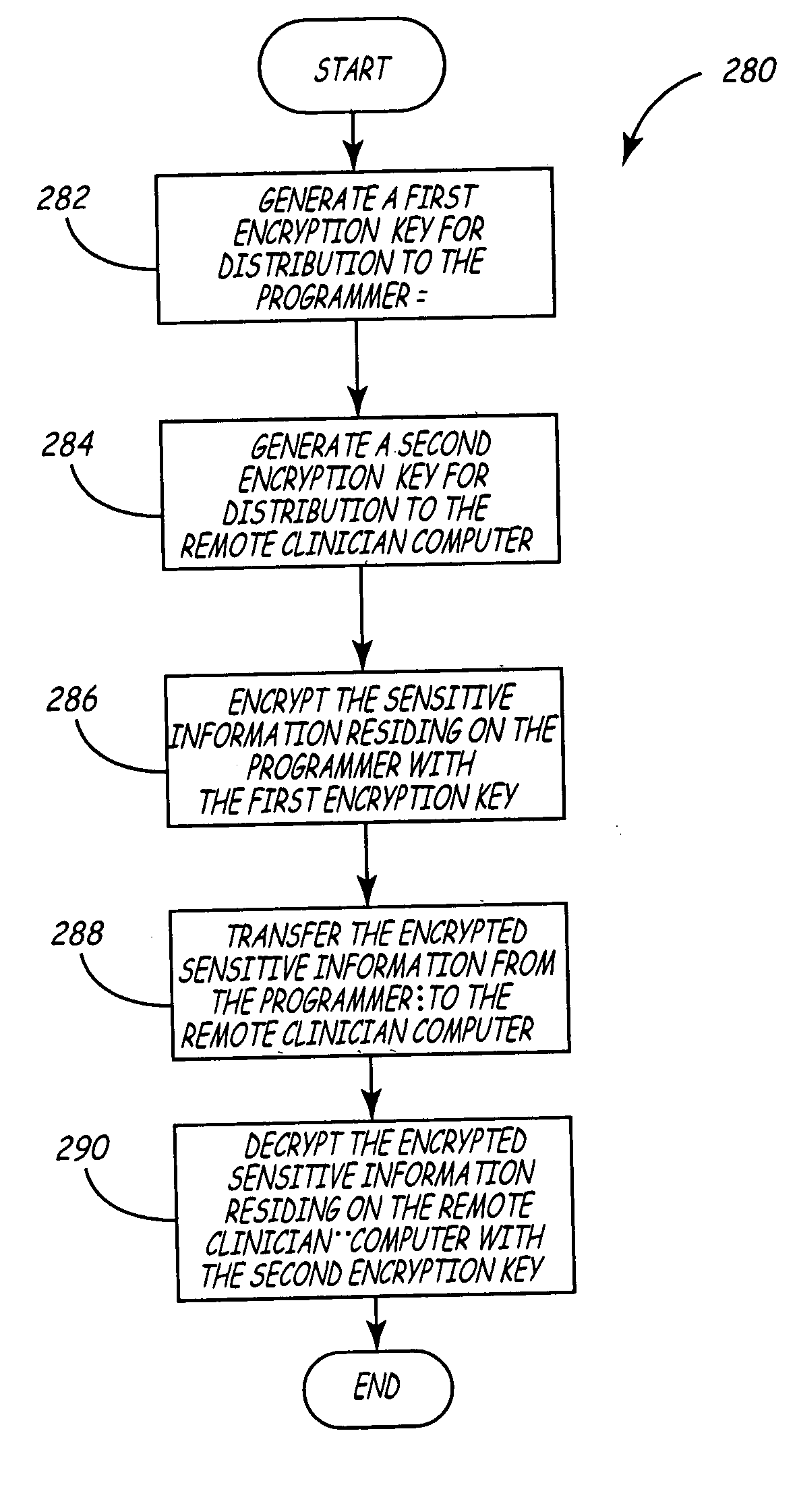
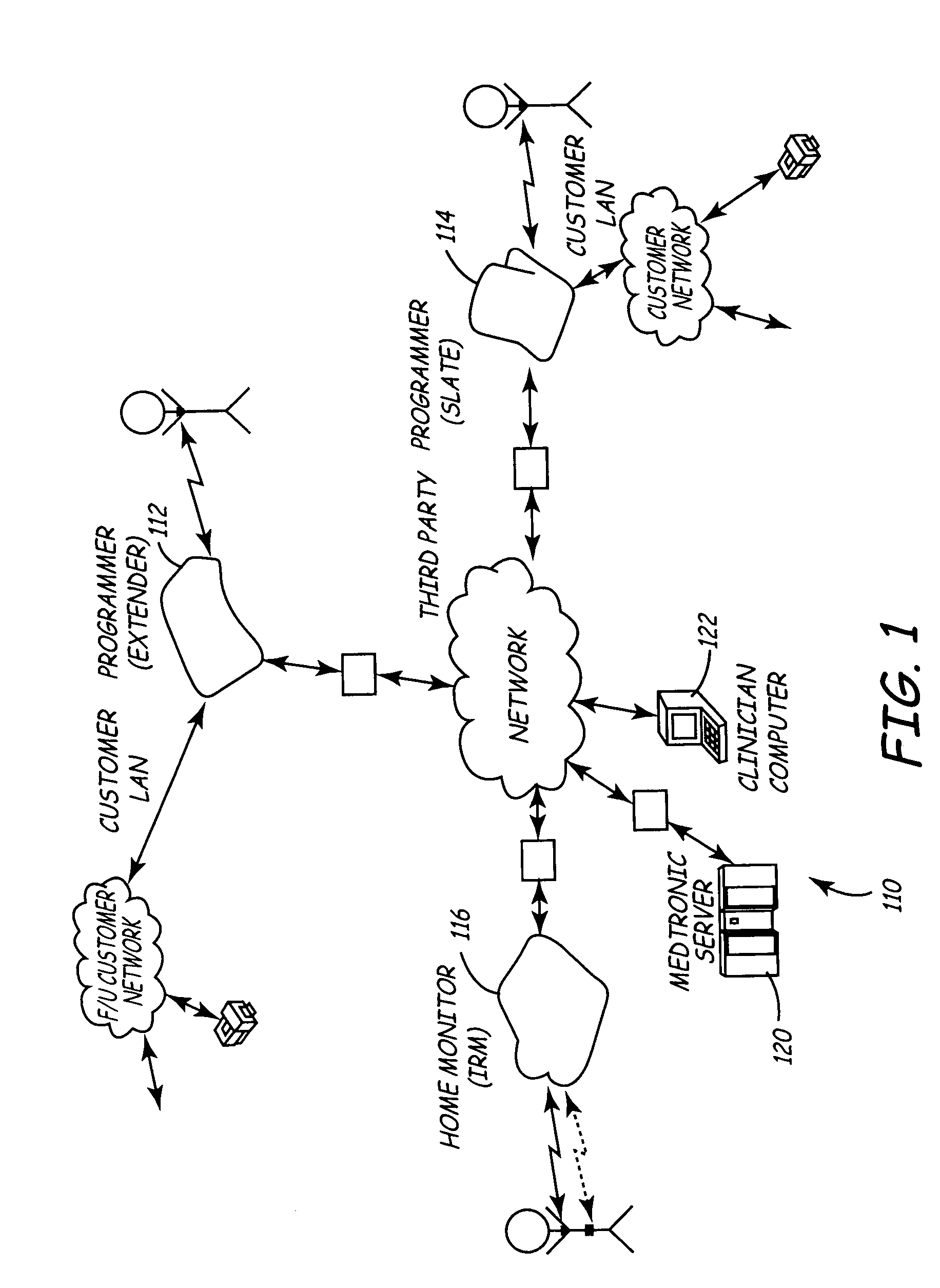
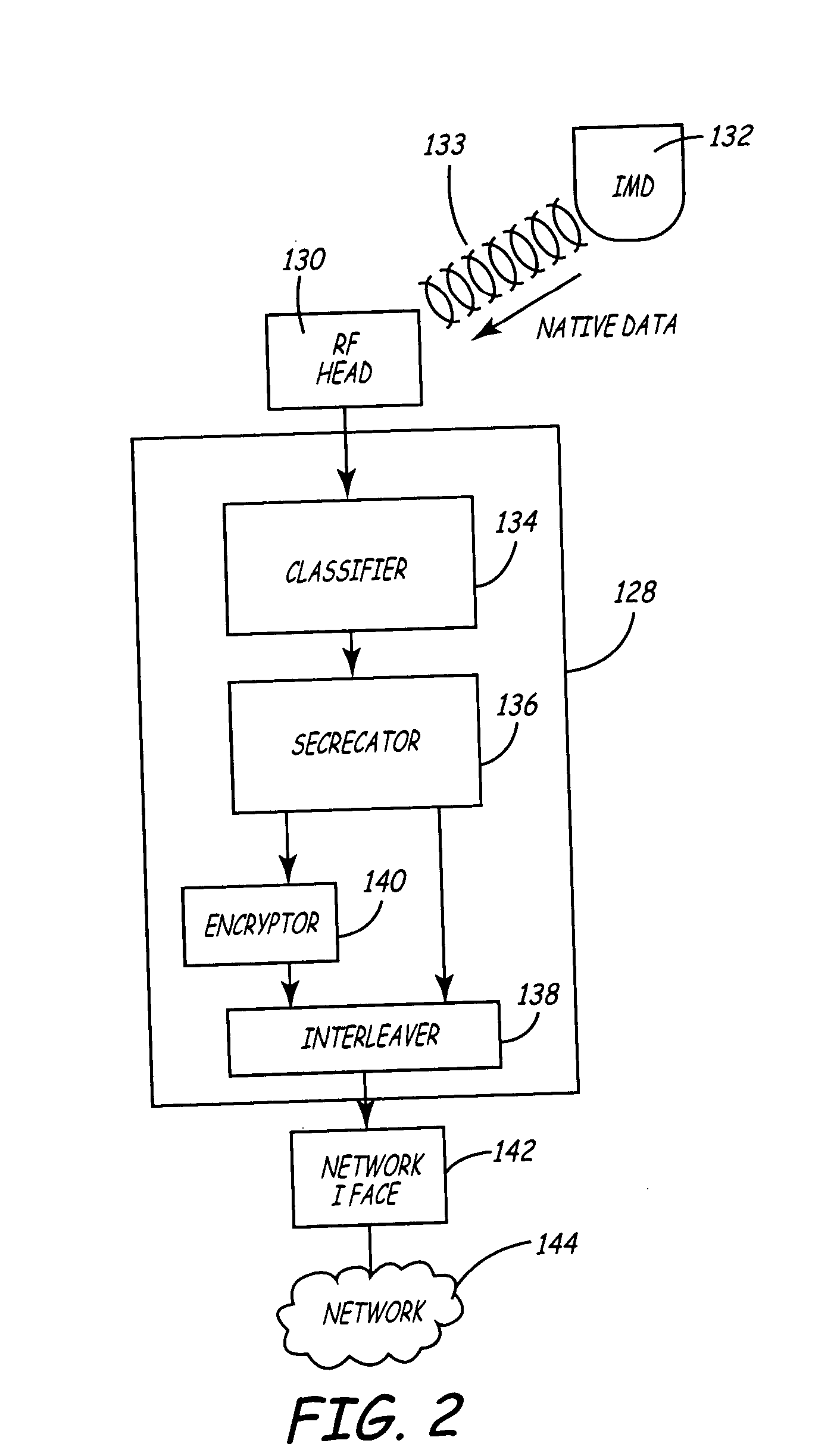
Variable encryption scheme for data transfer between medical devices and related data management systems
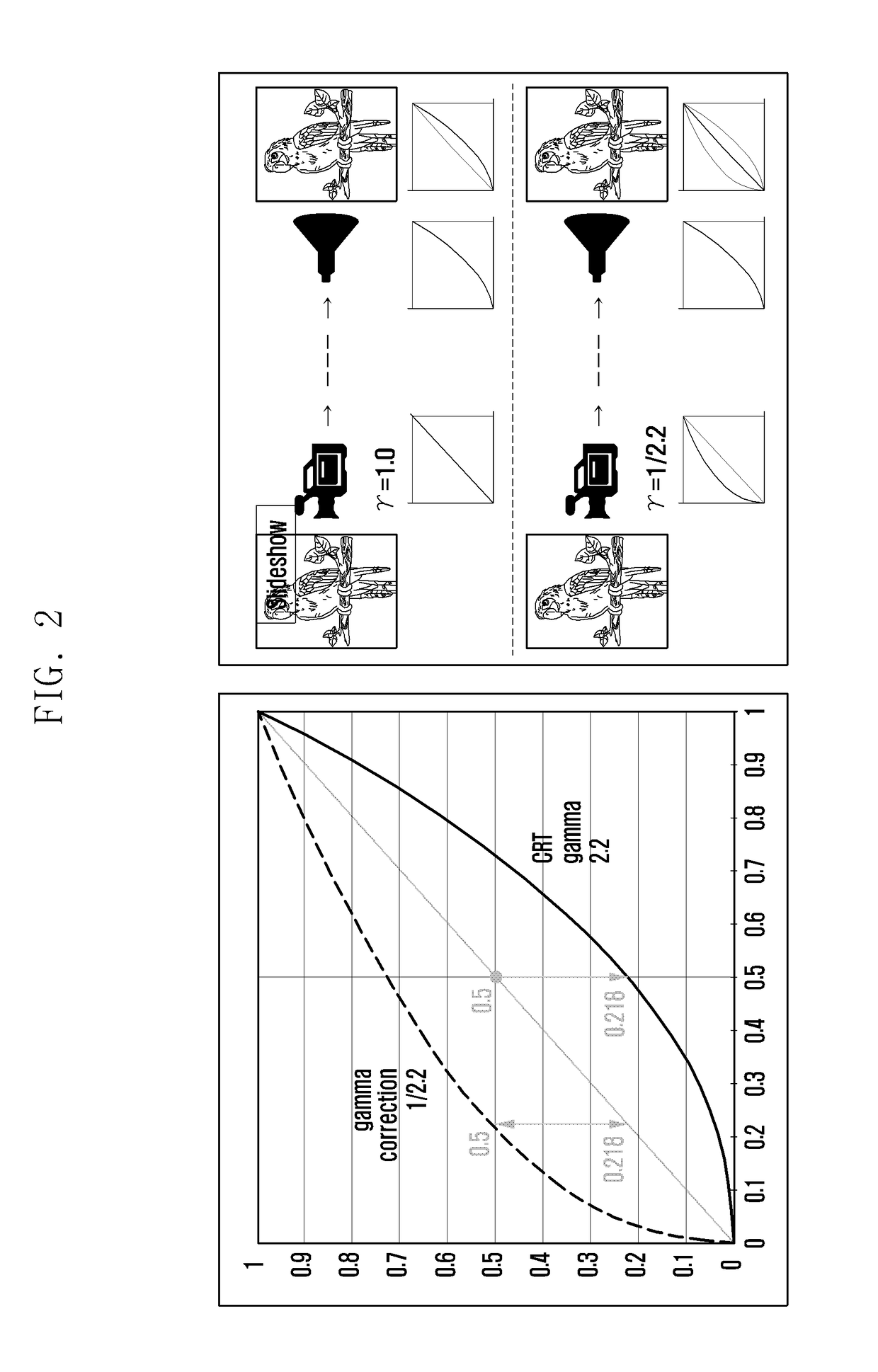
InactiveUS7027872B2Ensure authenticityEnsure integrityElectrotherapyData processing applicationsData centerData management
Owner:MEDTRONIC INC
Information storage
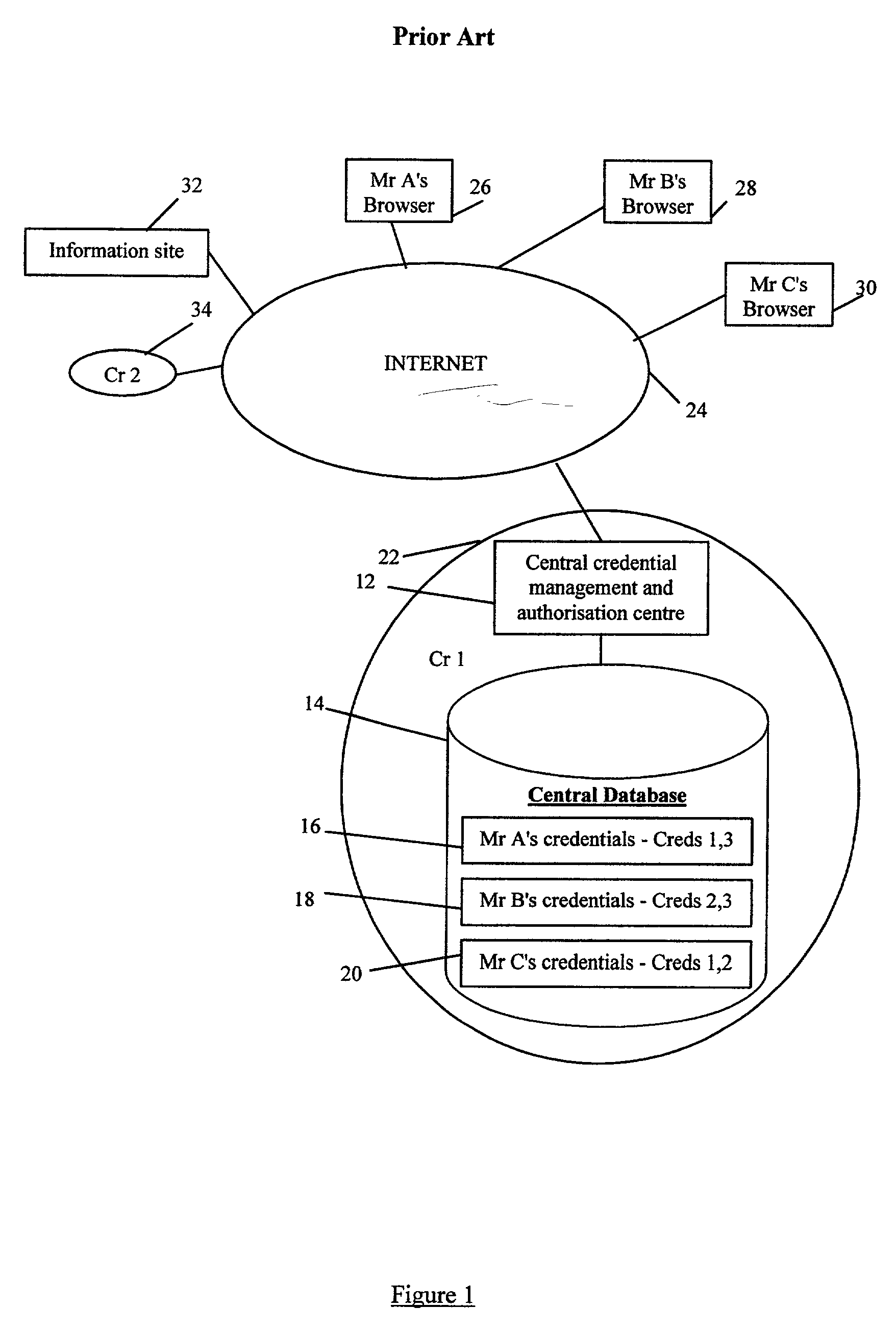
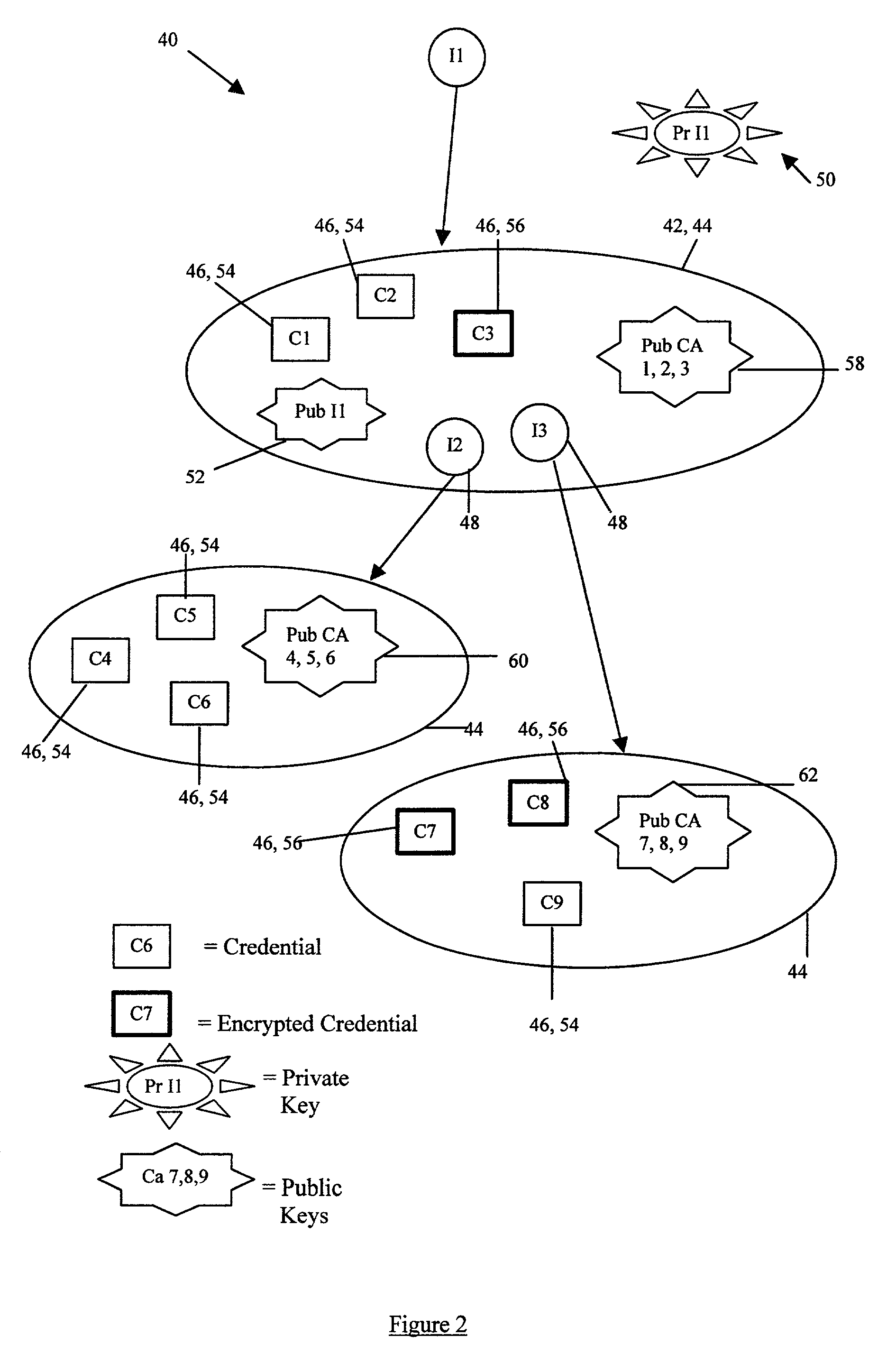
ActiveUS20010049786A1Improve security levelEnsure authenticityDigital data processing detailsUser identity/authority verificationMobile telephonyComputer security
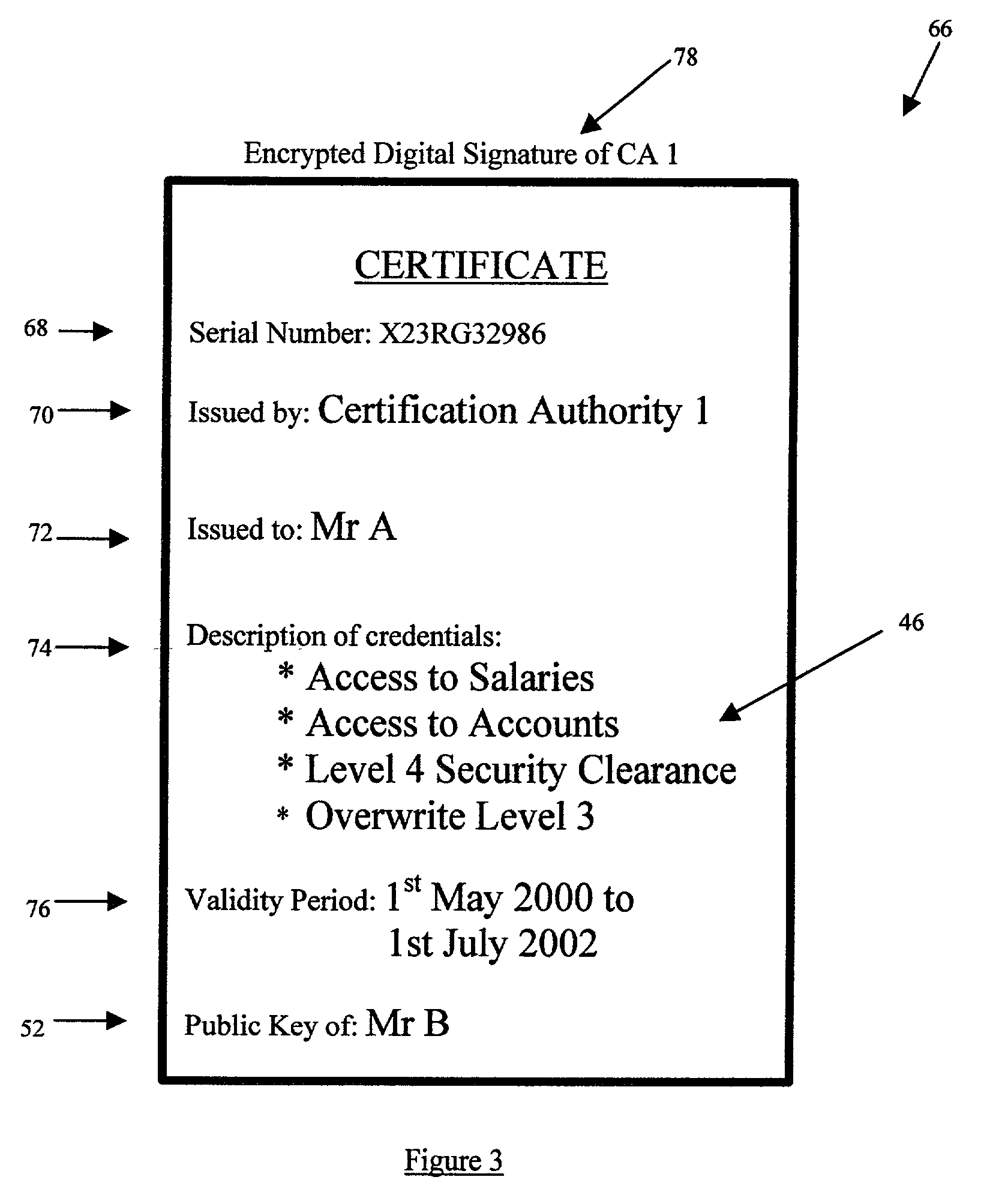
A distributed storage system for storing at least one credential (46), provided by an issuing authority and relating to an identity (42, 44), is described. The system comprises: a plurality of unique identities (42, 44) each having a local store (40). Each local store (40) securely stores credentials (46) relating to the owner of the identity (42, 44). The system also comprises one or more security certificates (66) provided at each identity (42, 44) for ensuring the authenticity of the credentials (46). The security certificates (66) provide secure references to the issuers of the credentials (46) and this can be used in verifying the origin of each credential (46). The identity can be provided a website or a mobile phone for example.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP +1
Location prediction system and method based on historical track data mining
InactiveCN102509170AUnaffected by environmental infrastructureAvoid the disadvantages of short prediction lengthsForecastingTrajectory data miningMotion Mode
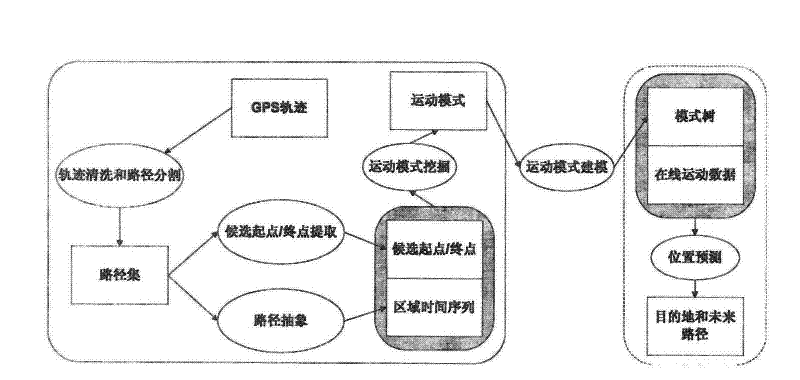
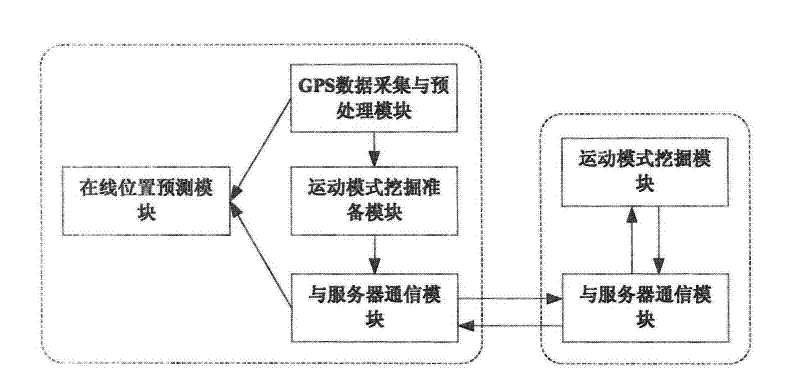
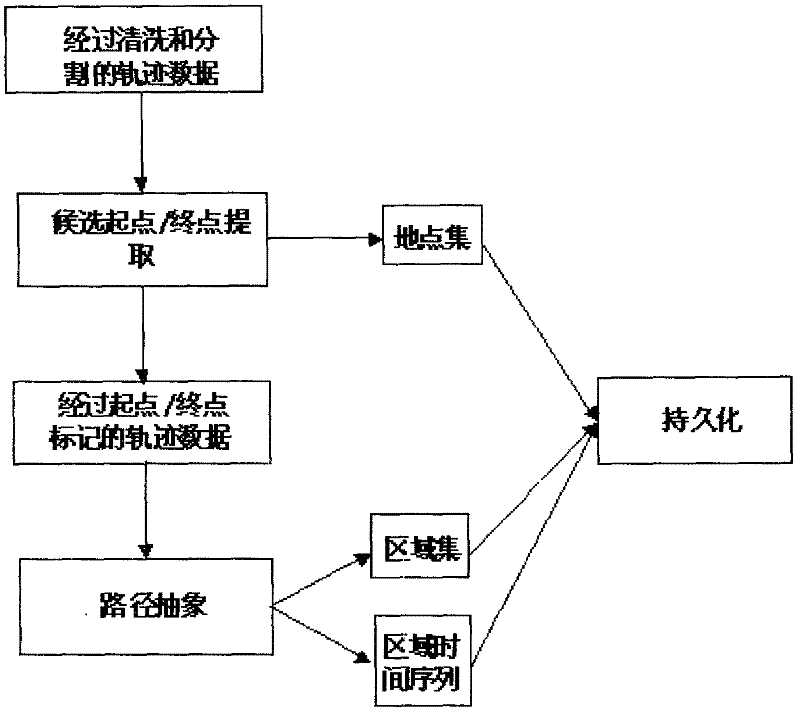
The invention relates to the technical field of data mining, in particular to a location prediction system and a method based on historical track data mining. In the method, the location prediction problem is decomposed into two sub-problems of offline track mining and online mode matching, wherein the offline track mining mainly adopts the data mining technology to process and analyze the historical track data of a user; and the online mode matching is mainly based on the online motion conditions of the user and the mined motion mode to perform matching and searching. According to the invention, various needs based on the location-based services (such as location-based advertisement, recommendation, reminding and other services) are effectively met, and the problems of the prior art are solved.
Owner:ZHEJIANG HONGCHENG COMP SYST
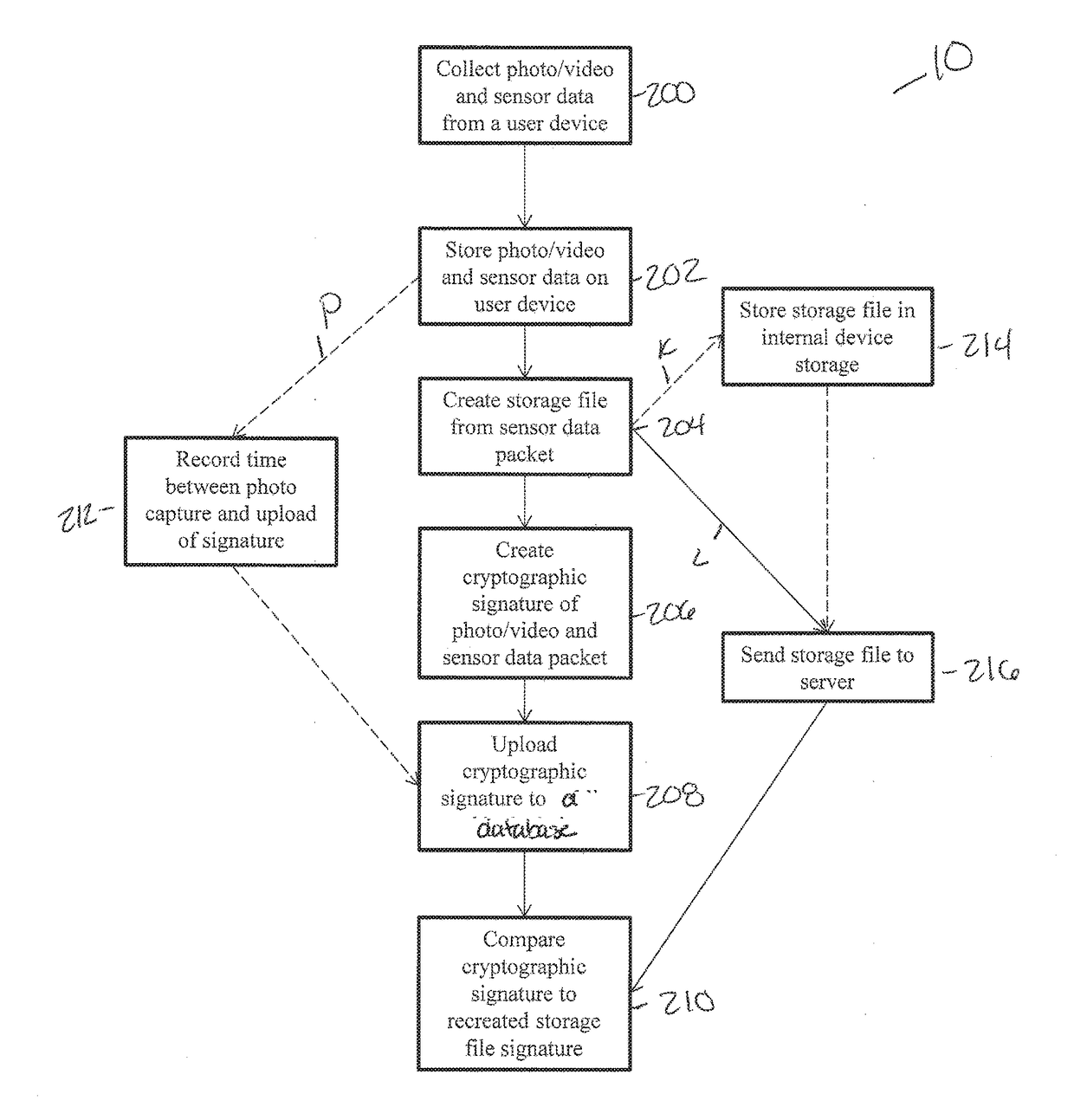
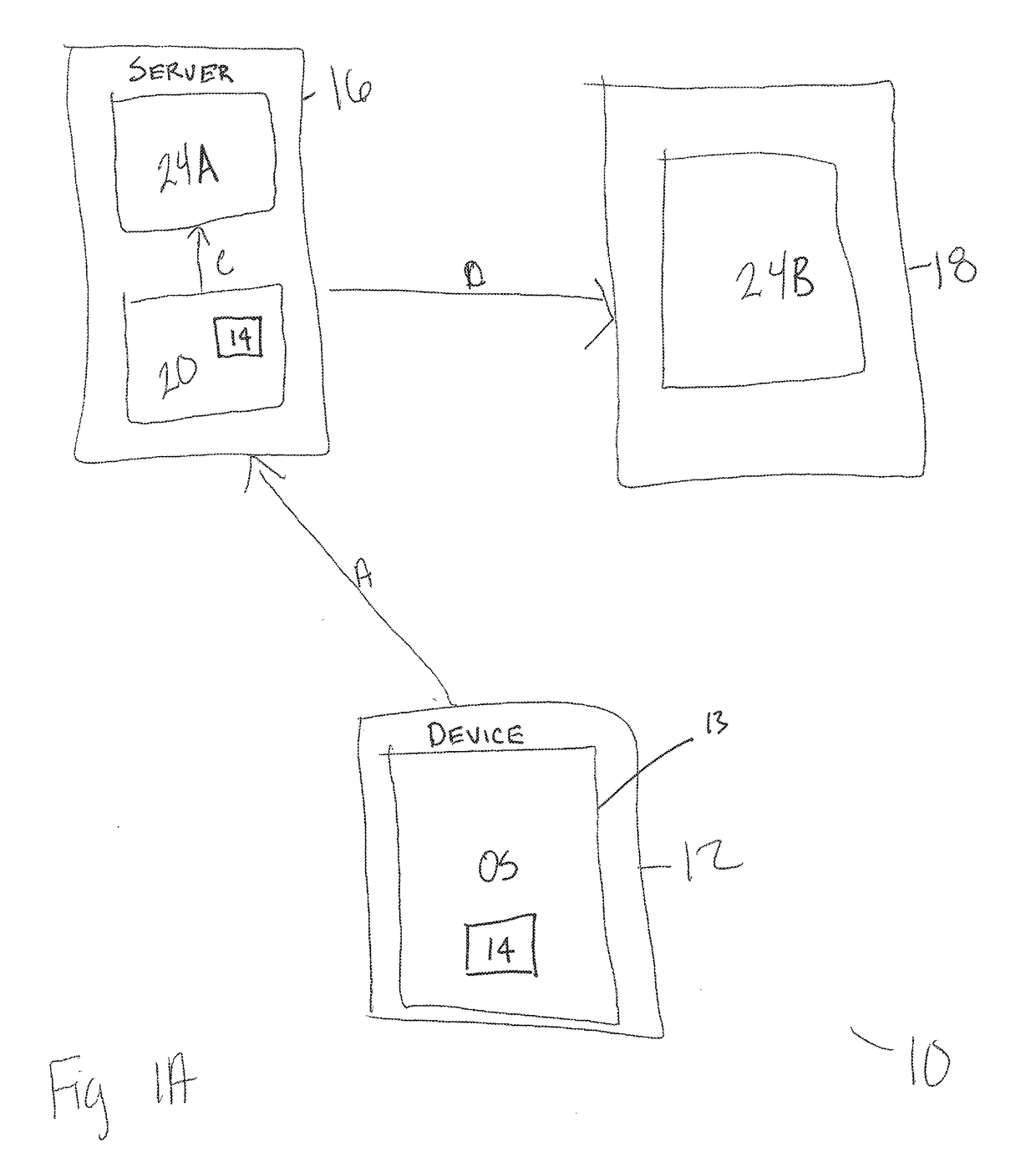
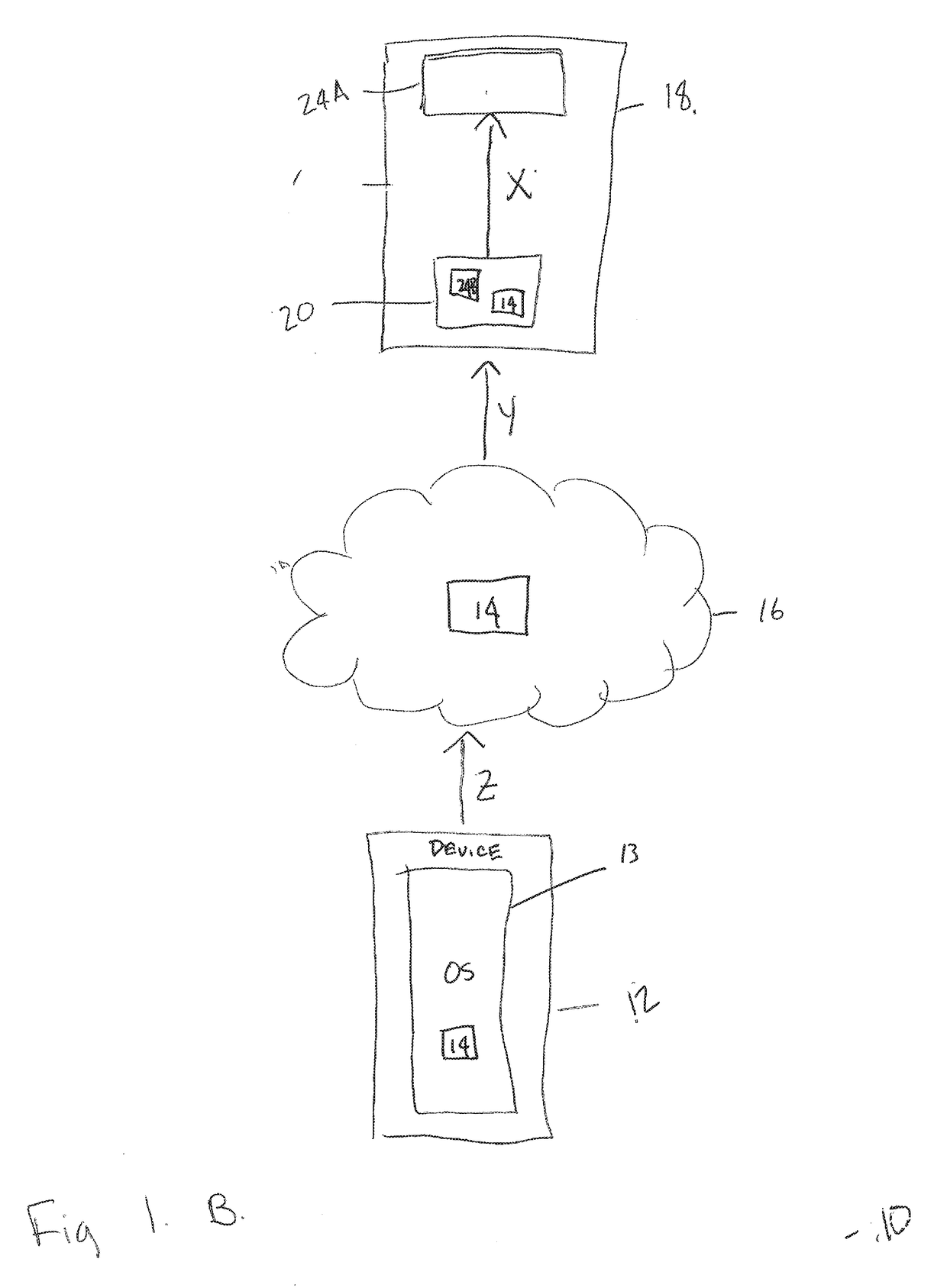
Cryptographic Signature System and Related Systems and Methods
InactiveUS20170373859A1Increase redundancyImprove protectionUser identity/authority verificationCoding/ciphering apparatusVideo sensorsHandling system
The disclosed devices, systems, and methods relate to a validation system which can be used to authenticate photos and videos. The system can have various steps including; a user taking a photo or video, sensor data being collected by a processing system, the sensor data being hashed to create a cryptographic signature, and the cryptographic signature being stored. The cryptographic signature can be later compared with the correspond photo or video for purposes of authentication.
Owner:PRAXIK LLC
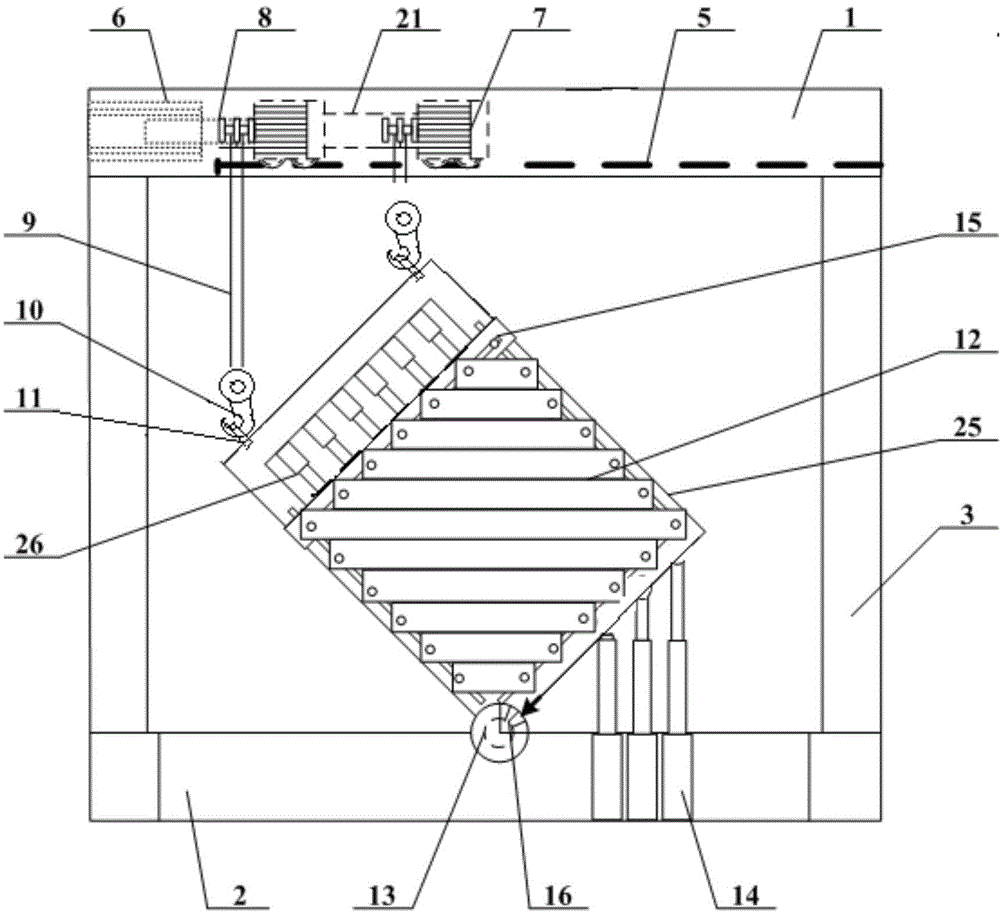
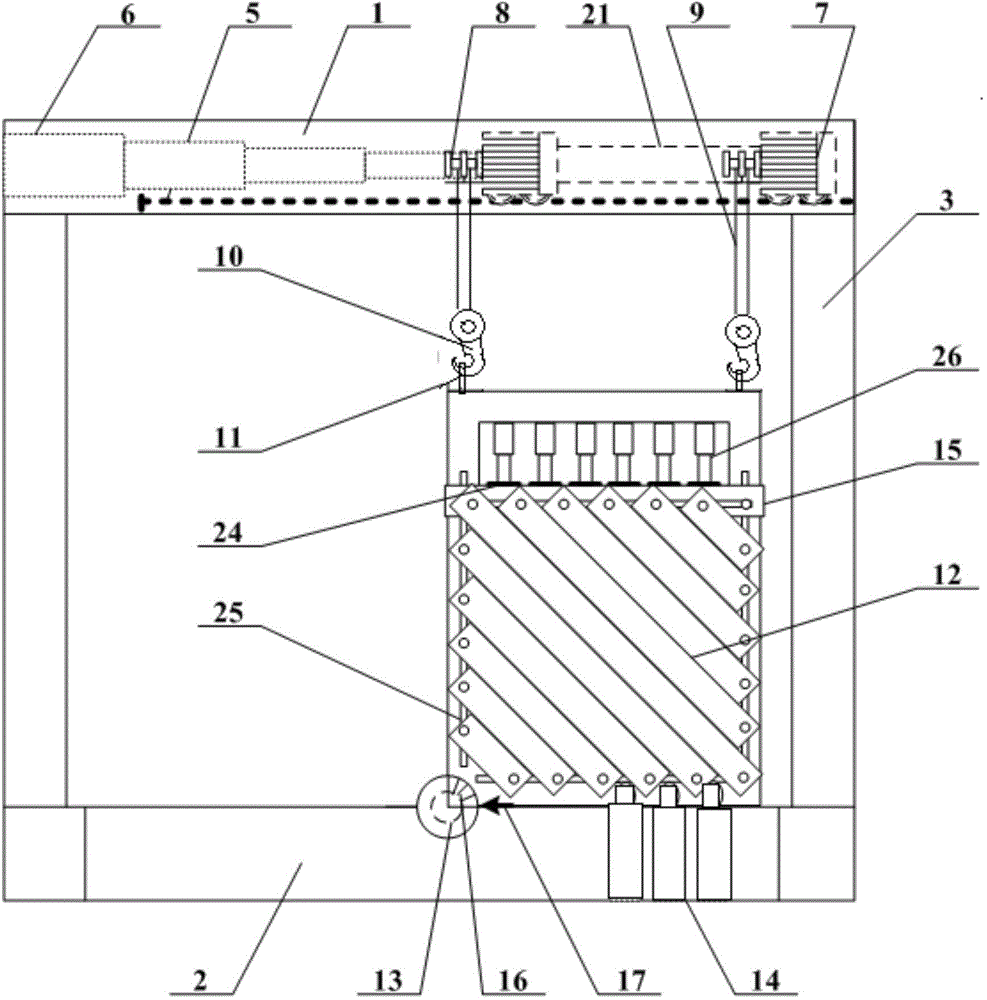
Physical similar simulation test device and physical similar simulation test method for tilted stratums
ActiveCN104596855AGuaranteed balance and stabilityEliminate potential safety hazardsMaterial strength using tensile/compressive forcesUsing optical meansStress distributionComputer science
The invention discloses a physical similar simulation test device and a physical similar simulation test method for tilted stratums. The physical similar simulation test device comprises an external framework, a tiltable rack, a front baffle, a rear baffle, a hydraulic supporting device and a hanging hoisting device, a similar simulation test is performed on stratums with different tilt angles by adopting the device and the method, physical mechanical performances of stress distribution, displacement change and the like inside the stratums under the action of external disturbance, ground stress, external force application and the like can be measured to obtain related technical indexes and parameters so as to research the rule of the true stratums in the process, and the effective struts can be facilitated during the construction of the stratums, thus providing a guarantee for the safety construction of the stratums.
Owner:SHANDONG UNIV OF SCI & TECH
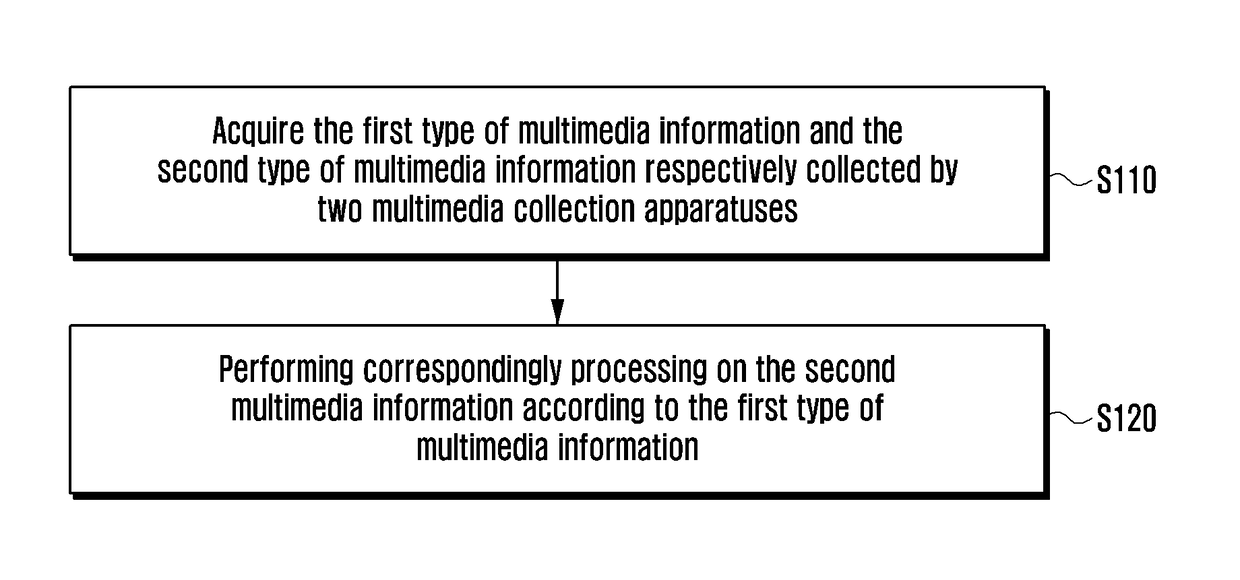
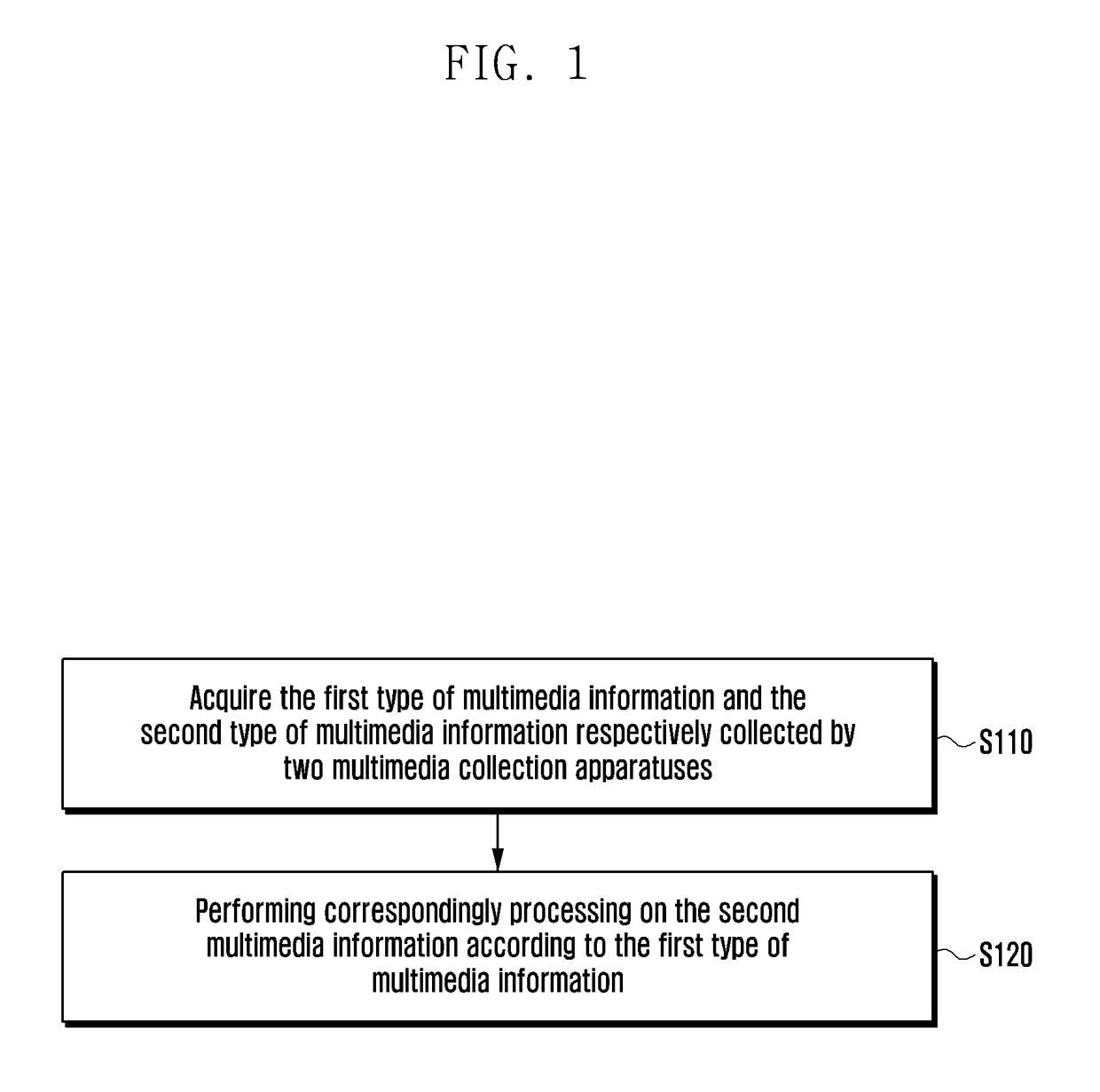
Method and device for processing multimedia information
ActiveUS20170278546A1Quality improvementEnsure authenticityImage enhancementTelevision system detailsComputer networkMultimedia information
A method and an apparatus for processing multimedia information is provided. The method includes receiving a first type of multimedia information collected by a first multimedia collection apparatus and a second type of multimedia information collected by a second multimedia collection apparatus and processing the second type of multimedia information based the first type of multimedia information.
Owner:SAMSUNG ELECTRONICS CO LTD
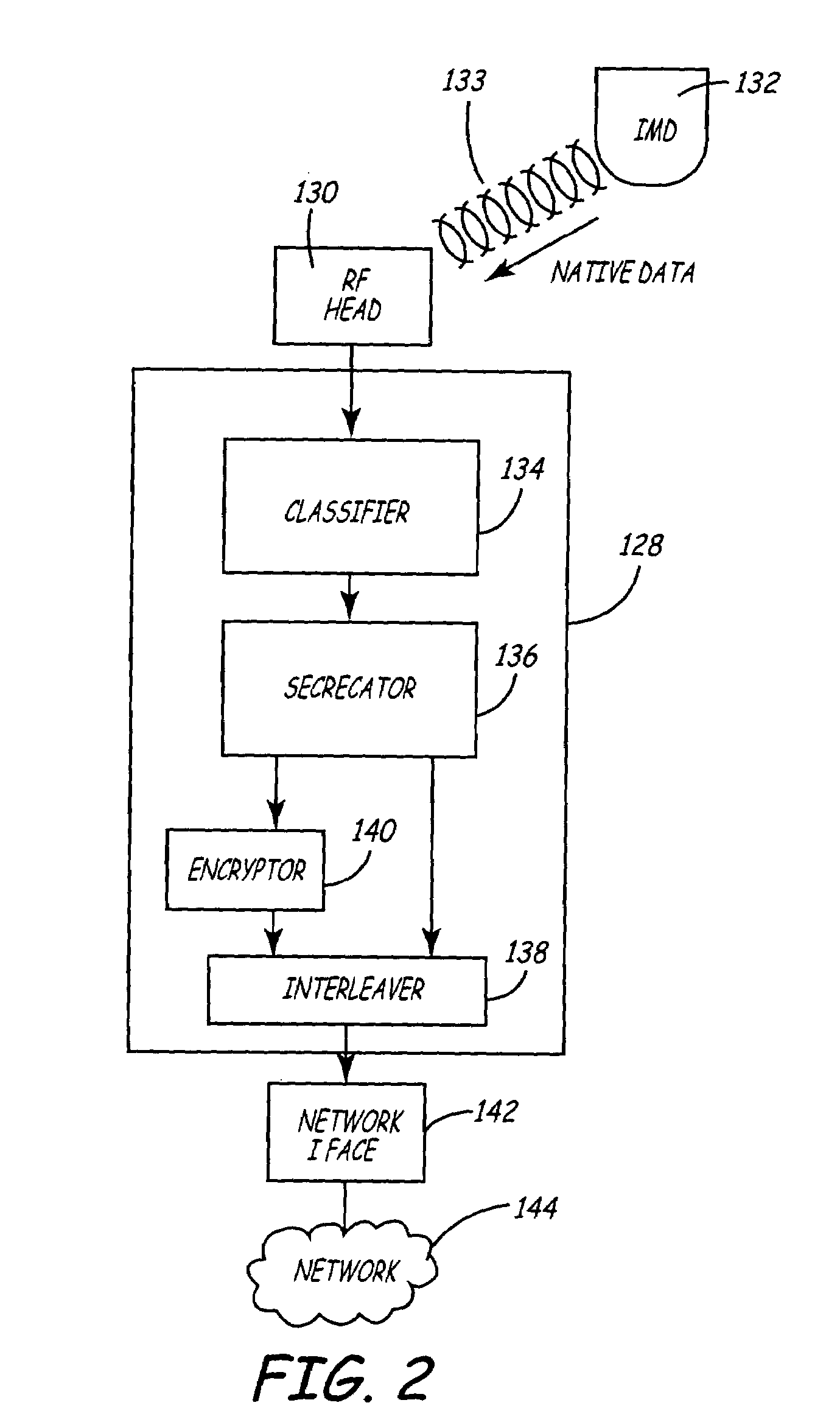
Variable encryption scheme for data transfer between medical devices and related data management systems
InactiveUS20050261934A1Minimal and no protectionLow accuracyElectrotherapyData processing applicationsData centerData management
The present invention provides for an encryption apparatus, system, and method in which data from an Implantable Medical Device (IMD) and a data center could be transferred based on a differentiated encryption system. The encryption scheme allows for the differentiation, segregation, and classification of data at required or needed levels of security. Before transfer of the data, either from an IMD or any other part of a support network for the IMDs, the encryption device begins to distinguish the data. The variable data is then classified based on various levels of security having distinct encryption protocols. After classification the data is encrypted based on the data's level of security. The data is then transmitted. Upon being received the data is then segregated based on whether the data is encrypted. The encrypted data is then de-encrypted and interpreted.
Owner:MEDTRONIC INC
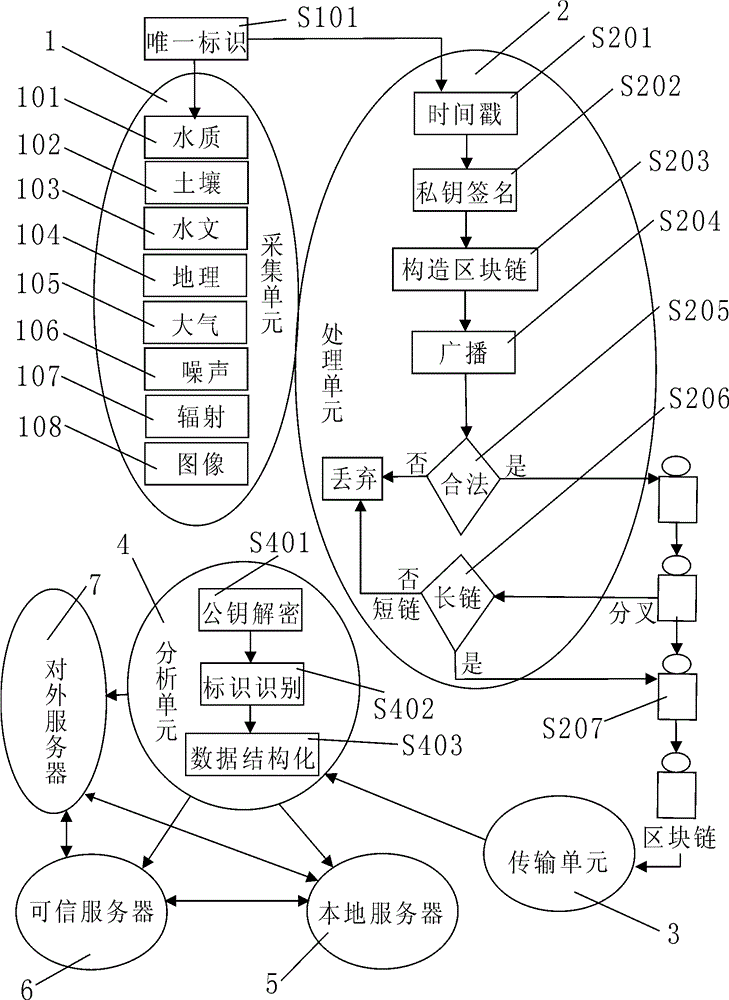
Block chain architecture-based ecological environment monitoring system and implementation method thereof
ActiveCN106407481AEnsure integrityEnsure authenticityData processing applicationsGeneral water supply conservationEcological environmentTimestamp
The invention relates to a block chain architecture-based ecological environment monitoring system, which comprises collection units, a processing unit, a transmission unit, an analysis unit, a local server, a trusted server and an external server, wherein each collection device has an inalterable device series number and is combined with geographic information to reform a unique identifier of a whole network; and meanwhile, a timestamp and a private key DSA signature are added to real-time monitoring data of each collection unit, and a new block which cannot be tampered and cannot be anonymous is constructed and added to a block chain. All participants in the network have copies of the block chain, the credibility of the data can be confirmed without check of any centralized mechanism, and meanwhile, ecological environment monitoring information and data are opened to the society, so that illegal acts of excess emission, data tampering or data falsification and the like can be effectively blocked; the integrity and the authenticity of the data are ensured; and the ecological environment monitoring uniformity and effectiveness are strengthened.
Owner:福州微启迪物联科技有限公司
Method of producing sensors for monitoring corrosion of heat-exchanger tubes
InactiveUS7310877B2Sensitively and reliably monitoredAccurate monitoringCellsWeather/light/corrosion resistanceEngineeringCost of treatment
The present invention relates to a method of producing the sensors for monitoring corrosion of heat exchanger tubes in a thermal power plant. The sensor is made of the tubes taken out from actual heat-exchanger. As a result, the sensor not only has the same material as the actual heat-exchanger tubes, but also has the same surface state where it contacts the working medium. Therefore, a serious technical difficulties have been solved that the sensor made by the prior art can't measure different corrosion states of actual heat-exchanger tubes, that the corrosion rate measured is different from the corrosion rate of actual heat-exchanger tubes, and that the cost of anti-corrosive treatments is high . By use of the sensor made by the present invention, the different corrosion states of actual heat-exchanger tubes can be measured, not only the rate of uniform corrosion of actual heat-exchanger tubes can be measured but also the rate of localized corrosion of the heat-exchanger tubes can be measured. Moreover, the cost of treatment of anti-corrosion can be decreased.
Owner:THERMAL POWER RES INST
Multi-vision-based bridge three-dimensional deformation monitoring method
InactiveCN102645173ADo not interfere with the natural stateNot easy to deform monitoringBiological neural network modelsCharacter and pattern recognitionContinuous measurementVision based
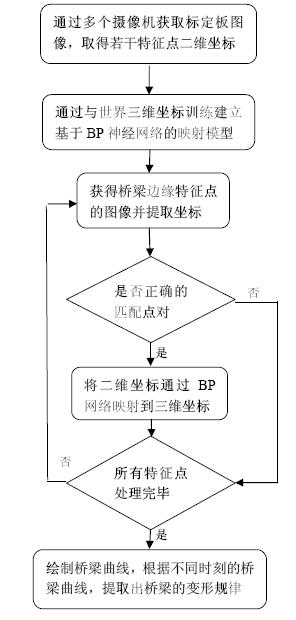
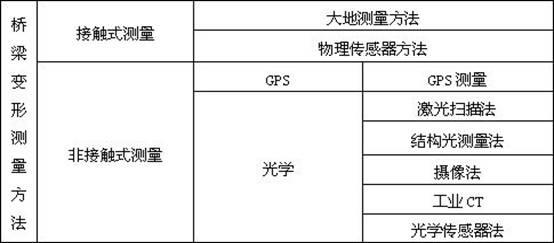
The invention provides a multi-vision-based bridge three-dimensional deformation monitoring method which comprises the following steps of: (1) obtaining the images of calibration plates and extracting the feature points on the multiple calibration plates by multiple video cameras respectively; (2) establishing a mapping model based on a BP neural network; (3) obtaining each video camera image at the bridge edge feature points; (4) eliminating the error point pairs by use of RANSAC to obtain the correct matching point pairs; (5) extracting the two-dimensional coordinates of each video camera image at the bridge edge feature points, obtaining the three-dimensional world coordinates of the feature points according to the mapping model based on BP neutral network, and drawing a three-dimensional curve of the bridge surface; and (6) extracting the bridge deformation rule according to the bridge curves of the bridge at different moments, and judging the bridge deformation trend. The method provided by the invention can perform non-contact three-dimensional measurement on the bridge deformation, and has the advantages of continuous measurement, instant measurement, synchronous measurement of multiple points, high precision, repeatability, low cost and the like.
Owner:张文杰
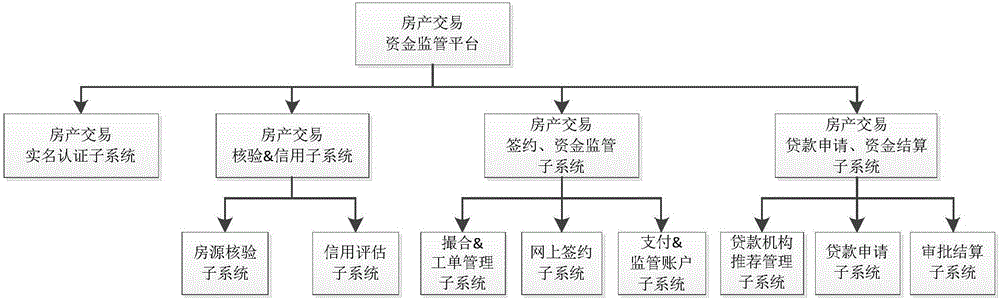
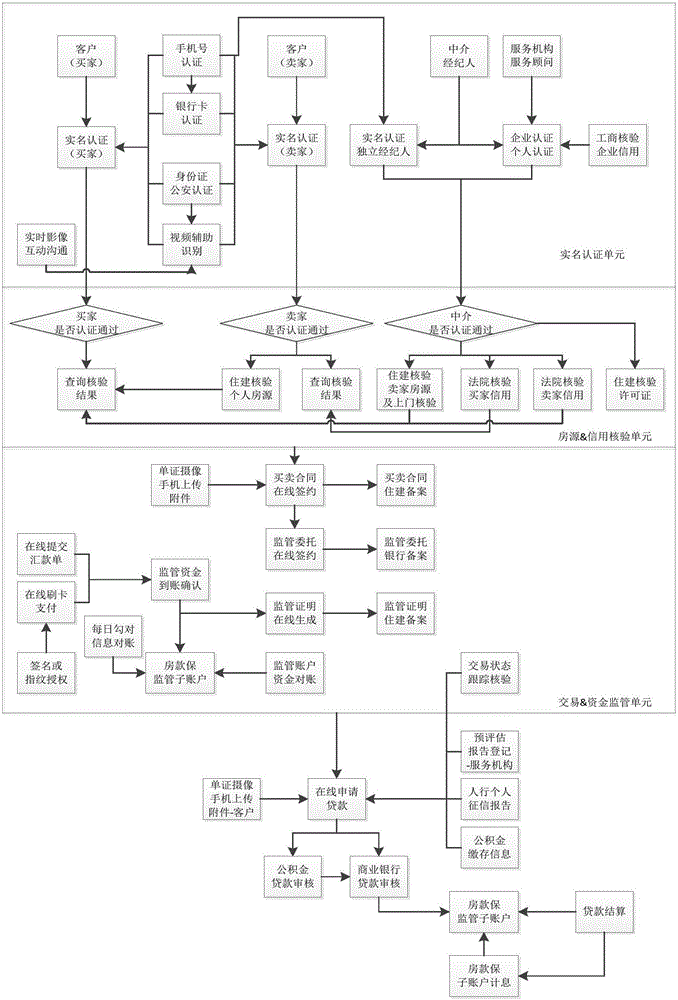
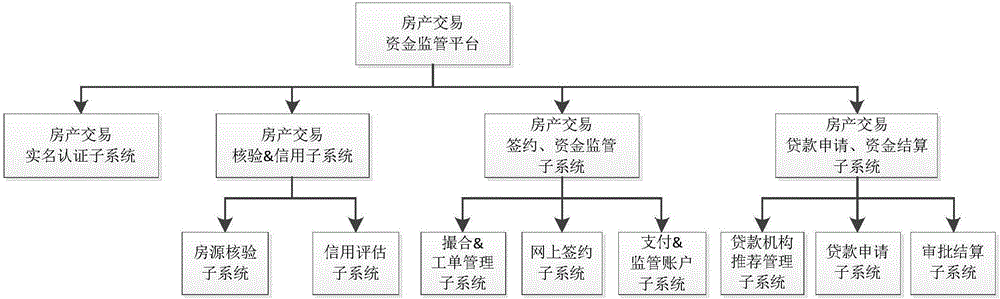
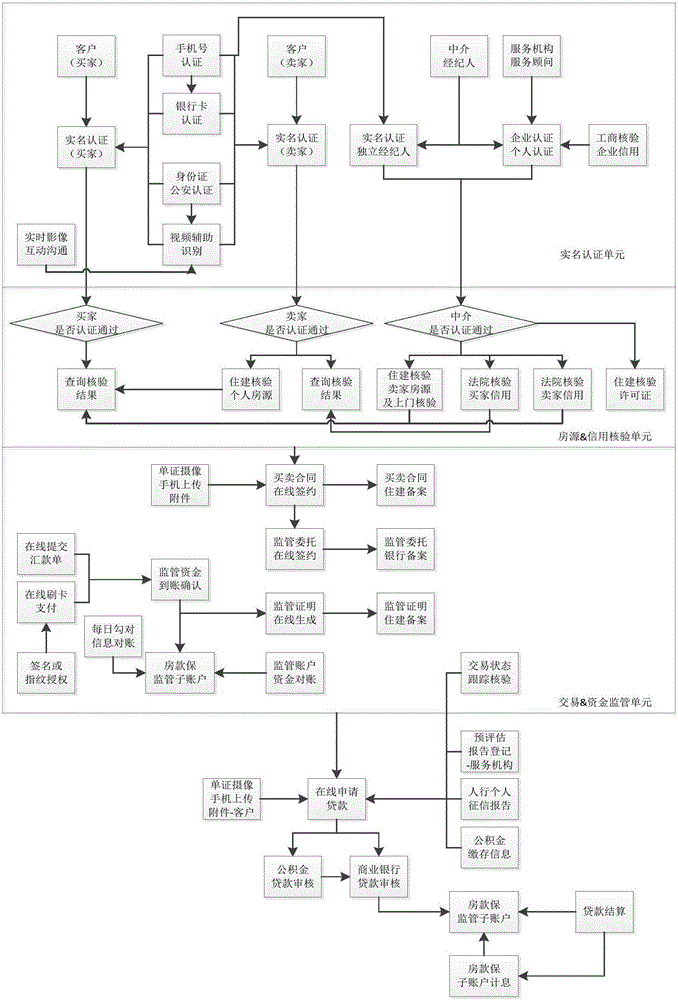
Method and system for completing house property transaction fund supervision based on intermediate platform
InactiveCN106157194AImprove transaction efficiencyImprove efficiencyFinanceProduct appraisalPaymentData information
The invention discloses a method and system for completing house property transaction fund supervision based on an intermediate platform. The method for completing house property transaction fund supervision based on the intermediate platform includes the steps of real name authentication, house resource & credit checking, house property transaction & fund supervision, and loan application. According to the method and system for completing house property transaction fund supervision based on the intermediate platform, by establishing communication between the intermediate platform and various terminals and systems involved in the house property transaction process, high-value house payment is completed online, so that the house property transaction efficiency is greatly improved, and meanwhile the data transmission security is guaranteed; besides, a strict authentication process is adopted for important data information, so that the authenticity and validity of information are guaranteed, the transaction authenticity is effectively guaranteed, the credibility of transaction parties is improved, operation is convenient and fast, and it is easier to conclude the transaction.
Owner:FUJIAN PROVINCE CHINA E COMMERCE INVESTMENT
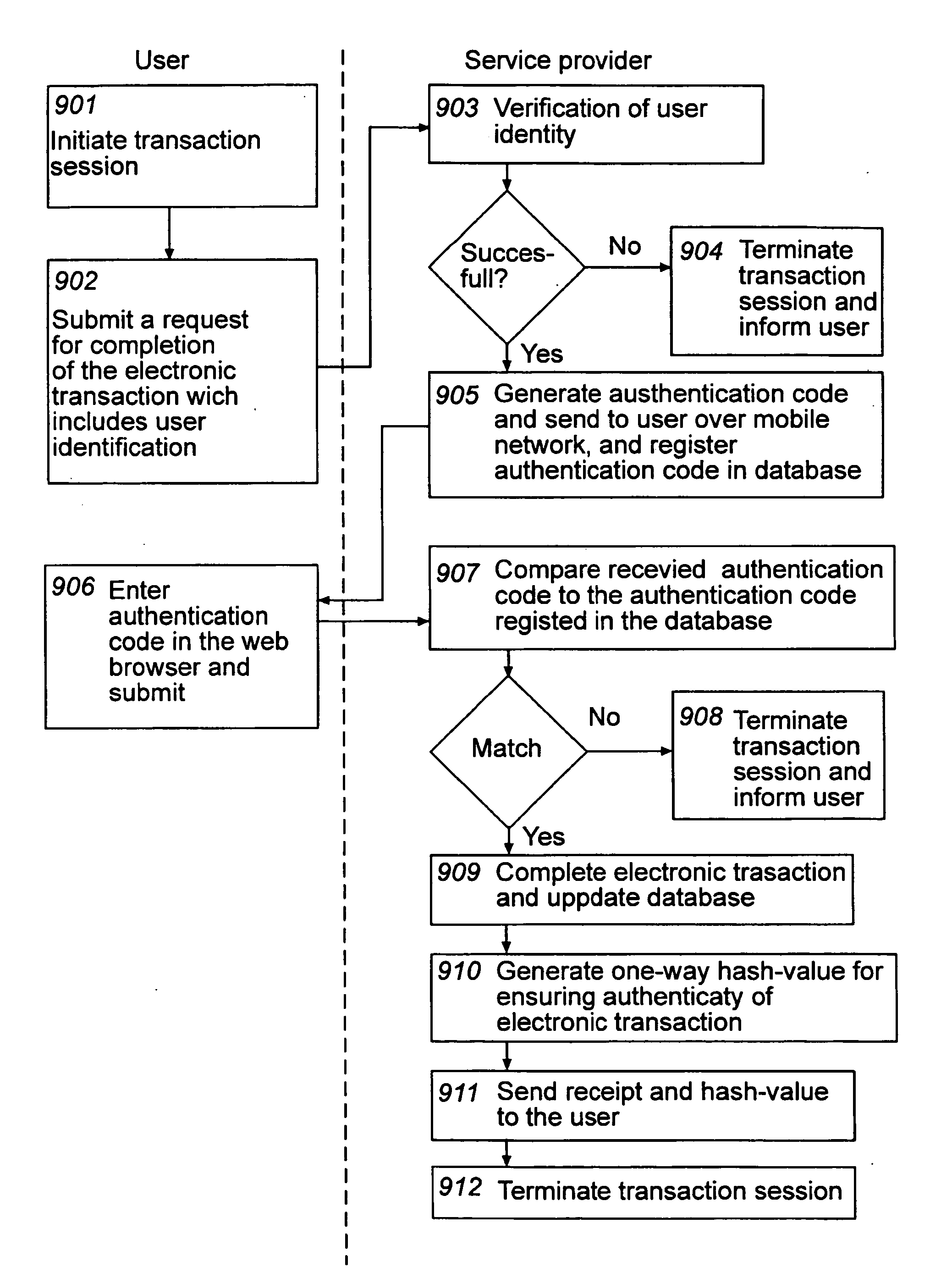
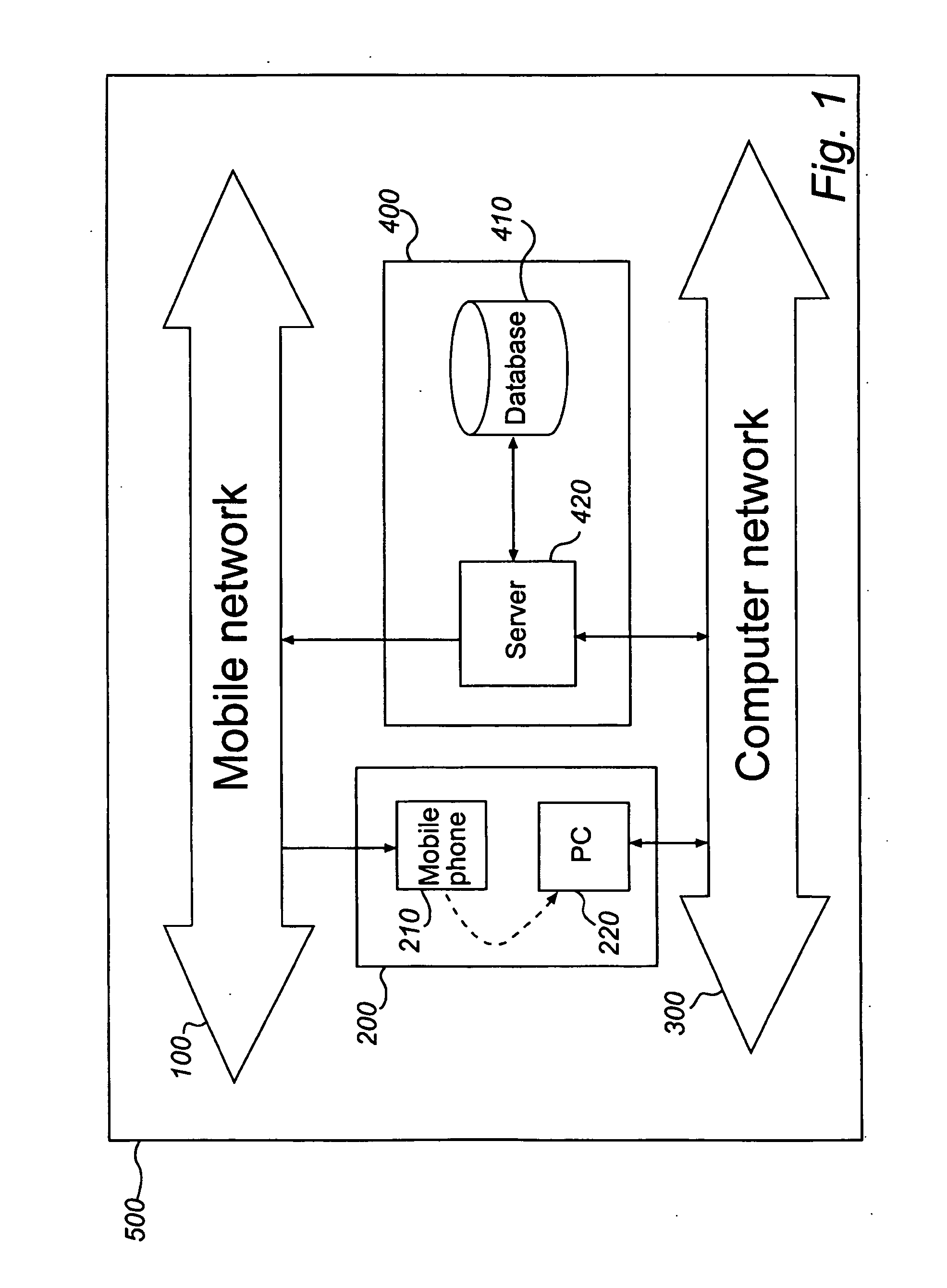
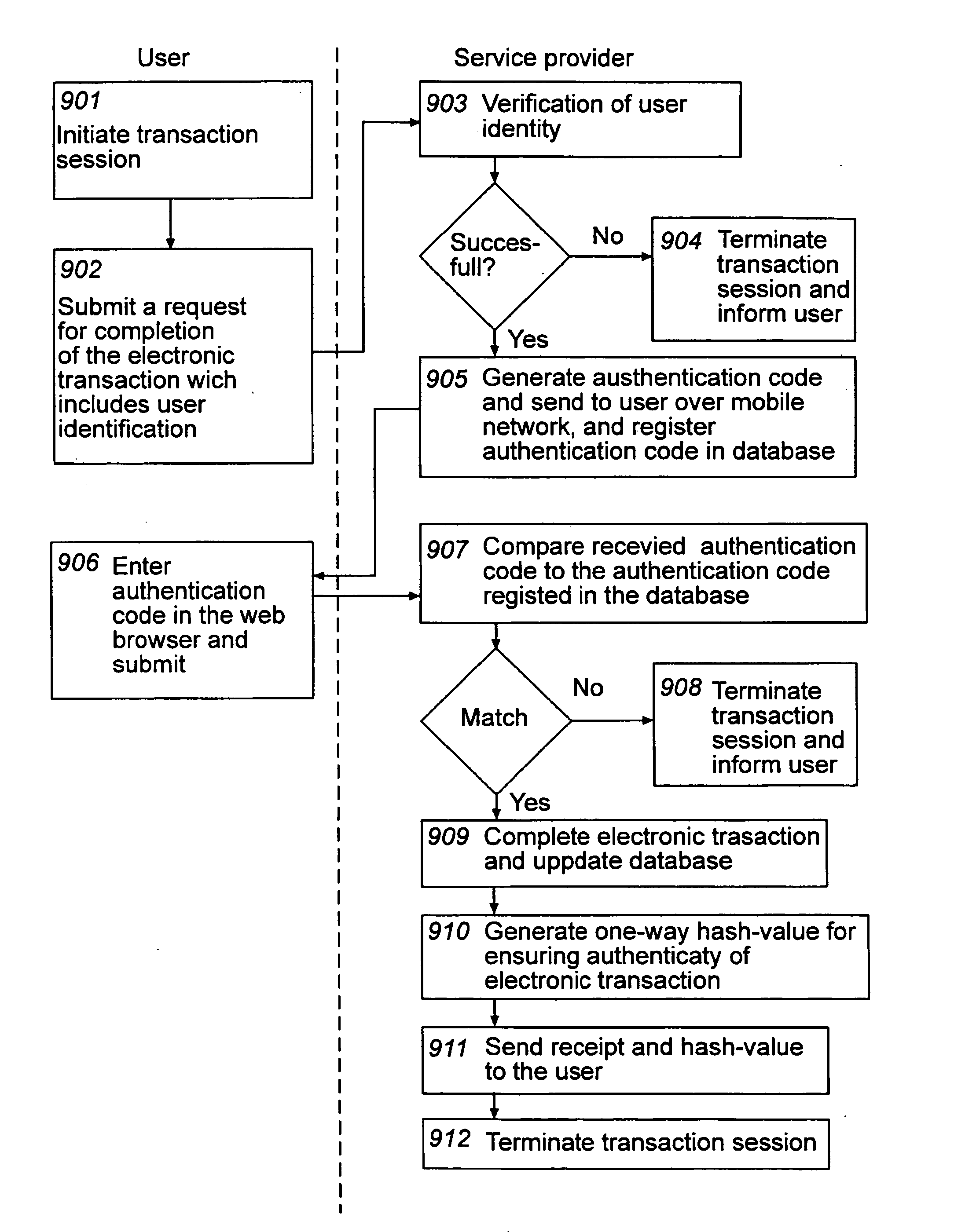
Method and computer system for ensuring authenticity of an electronic transaction
InactiveUS20090319797A1Easy to useReduce the risk of fraudKey distribution for secure communicationDigital data processing detailsComputerized systemSecurity level
At least one embodiment of the present invention relates to a method for ensuring authenticity of an electronic transaction performed during a transaction session. The method includes receiving, over a first network, a request from a user for the completion of an electronic transaction; receiving, over the first network, an authentication code from the user which has been provided to the user over a second network separated from the first network, thereby authenticating the user, completing the electronic transaction; and storing information associated with the electronic transaction and the transaction session. The method further includes generating a one-way hash value based on information comprised in the electronic transaction and information associated with the transaction session, and providing the one-way hash value to the user, wherein the one-way hash value is usable for ensuring the authenticity of the electronic transaction. The procedure enables authentication, integrity, non-repudiation, and time stamping in a cost efficient way. An enhanced security level can be achieved as the network used for providing the authentication code to the user is separate from the network where the user returns the authentication code. At least one embodiment of the present invention also relates to a corresponding computer system adapted for ensuring the authenticity of an electronic transaction.
Owner:COMFACT AB
Embedded optical signatures in documents
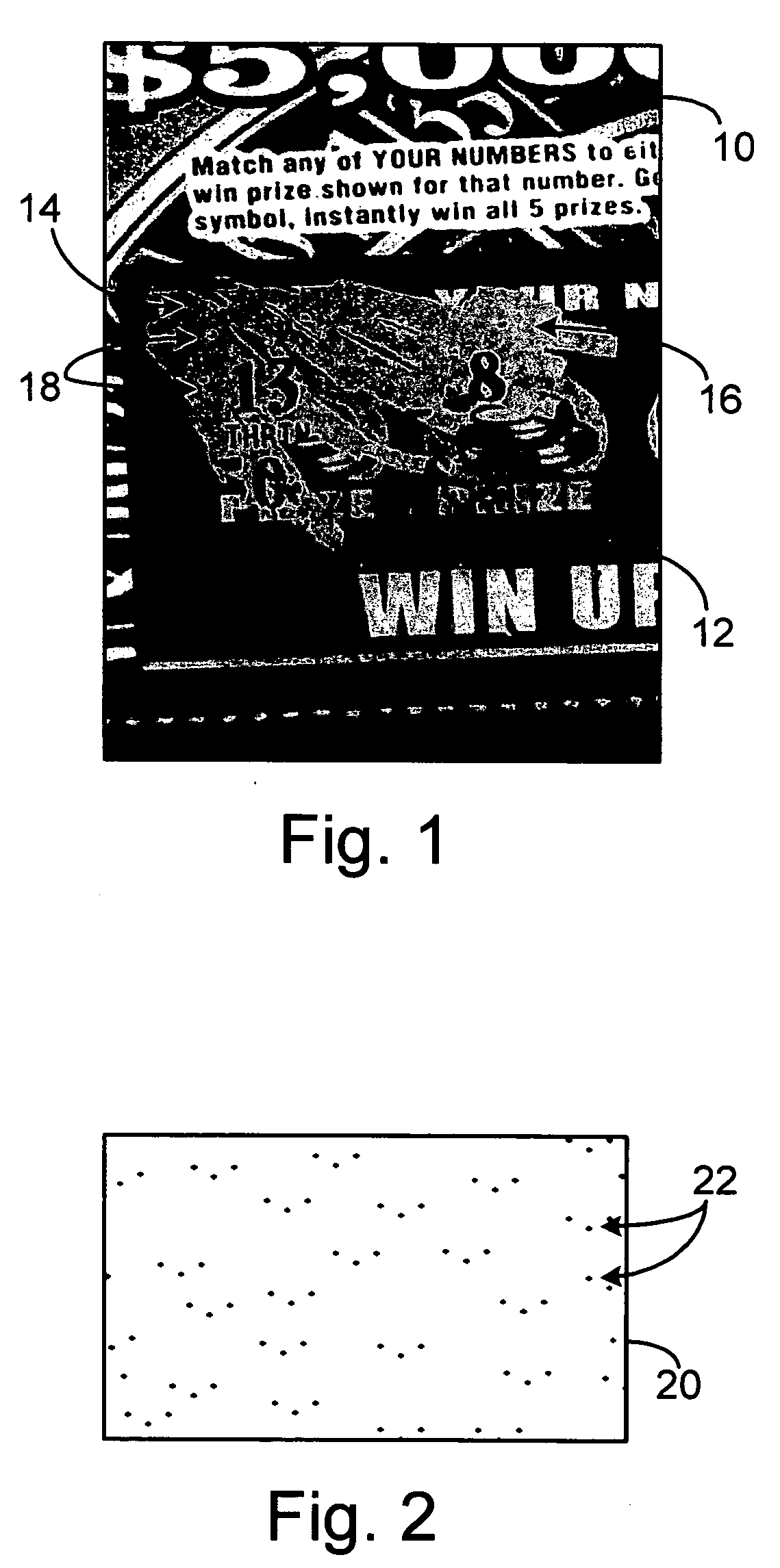
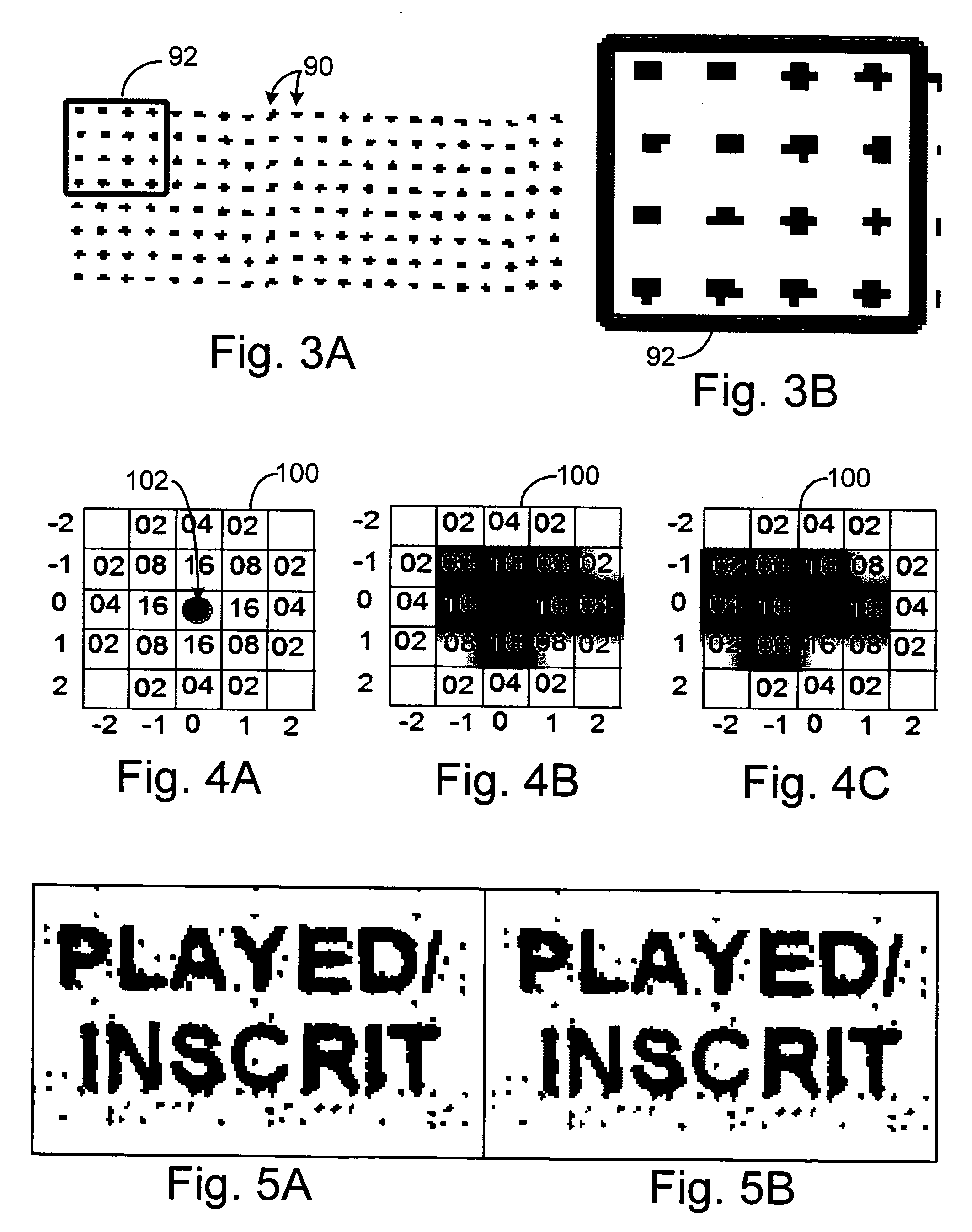
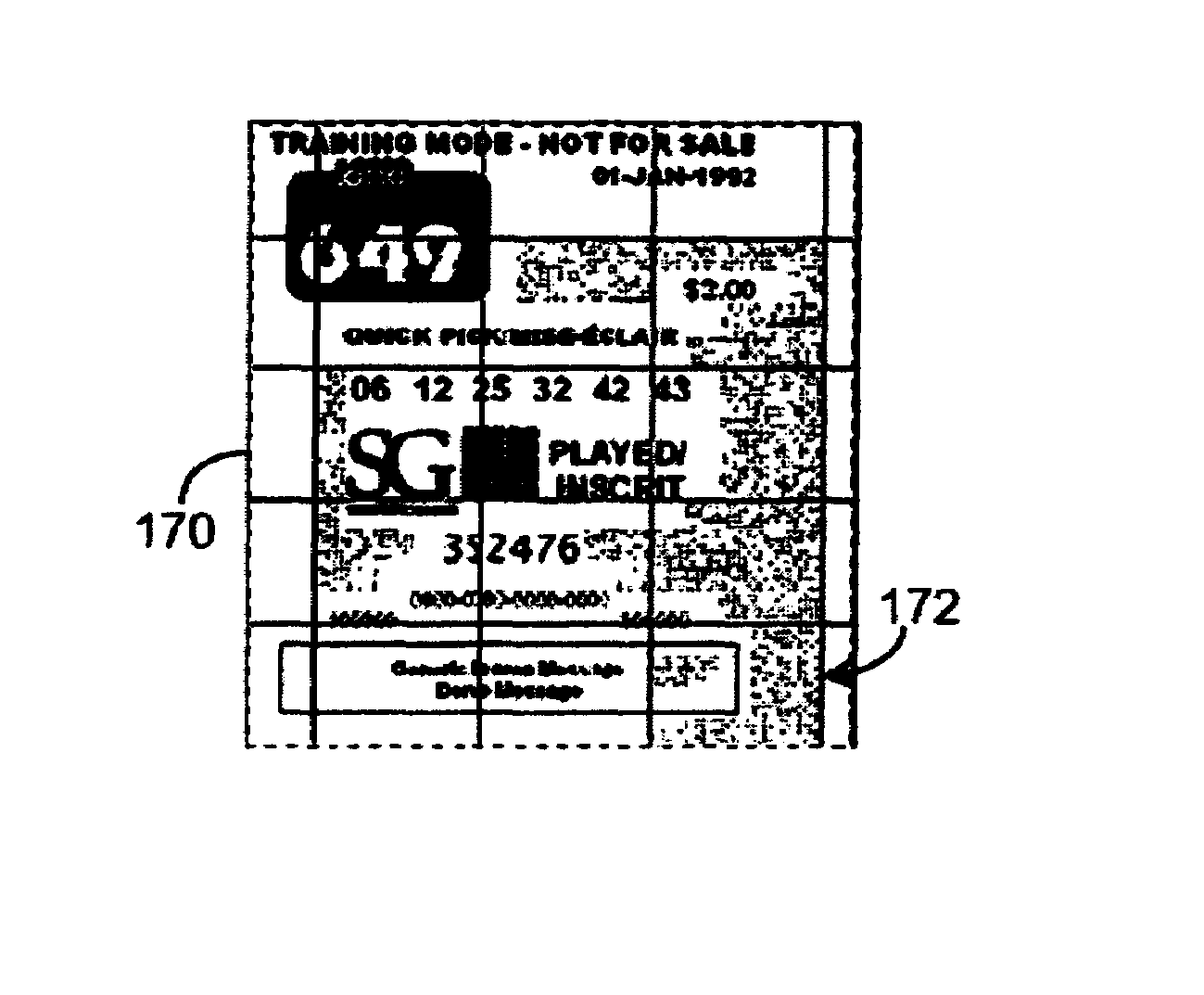
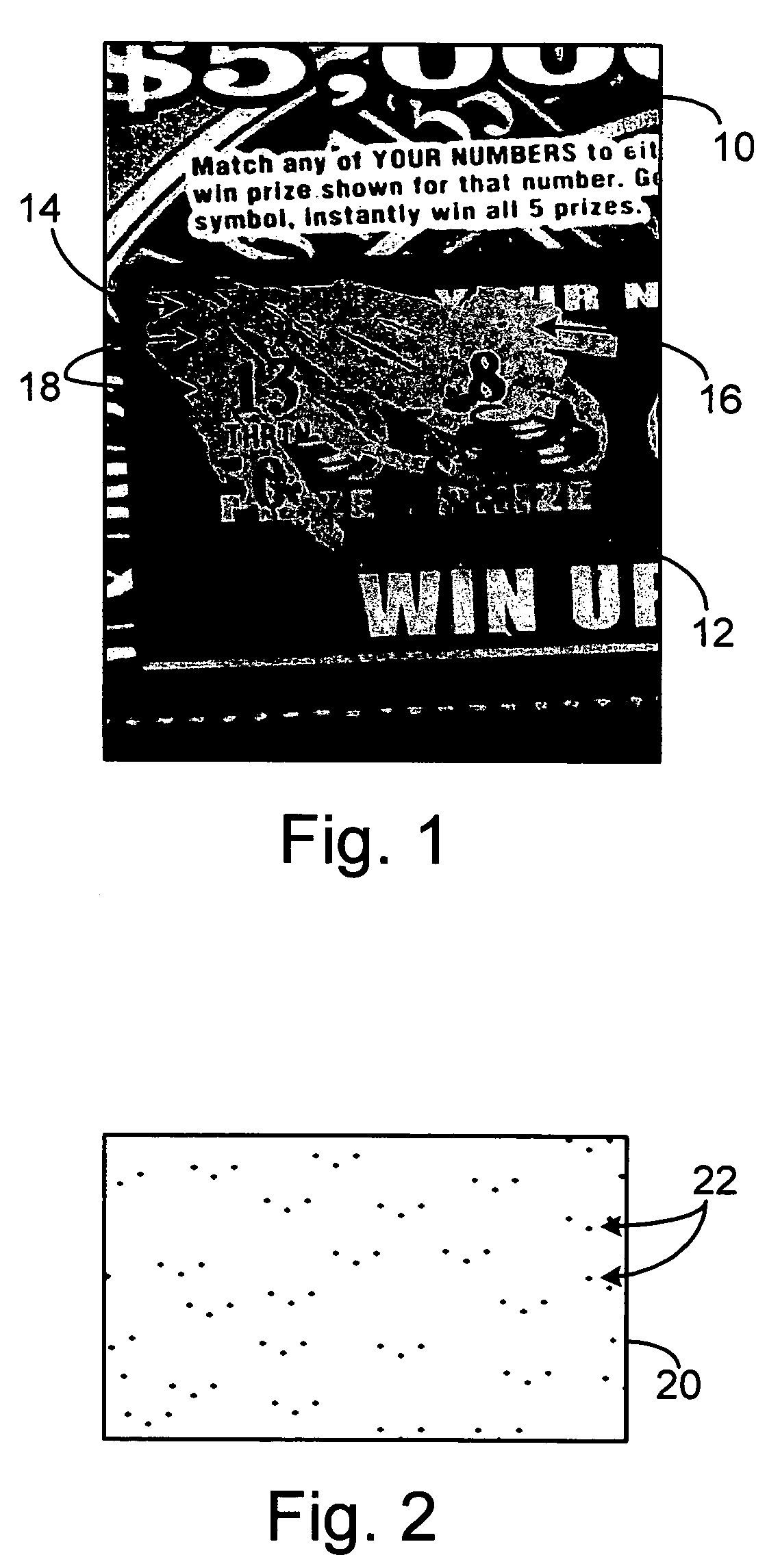
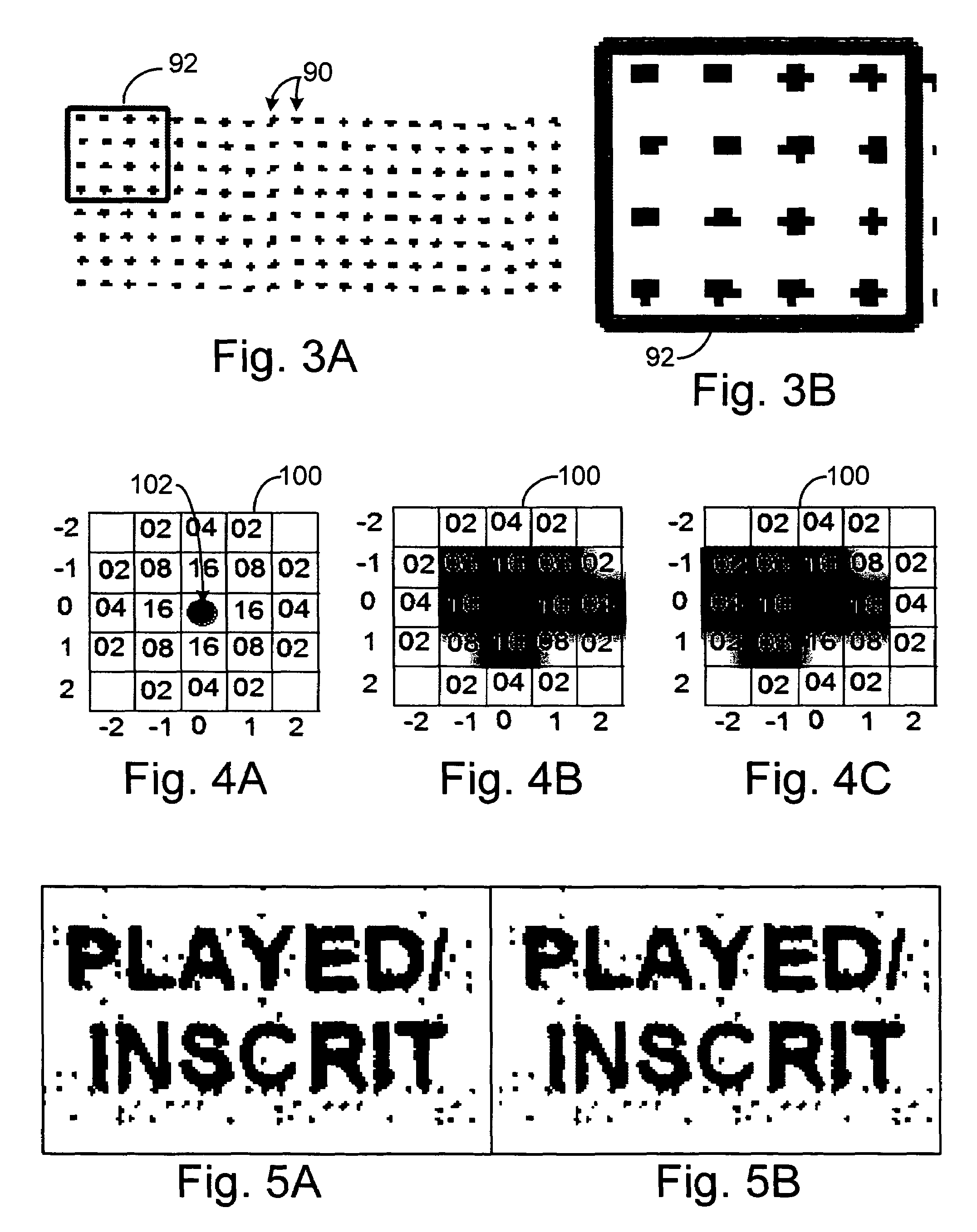
ActiveUS20060081710A1Provide informationEnsure authenticityPaper-money testing devicesBoard gamesComputer scienceMesh grid
A method of embedding an optical signature in a document and document produced therefrom. The optical signature is an optical pattern preferably being a series of discrete marks that can be aligned in a grid that generates a known value, and the same value can be generated from examination of a document by aligning at least an X-Y coordinate grid over the embedded optical pattern. The document can be validated, authenticated, or the determination of a valid copy of an original document with the embedded optical signature made through comparison of the known value and the value generated from the optical pattern on the document. The optical pattern can also be generated from other identification codes on the document.
Owner:SCI GAMES LLC
System and method for logo identification and verification
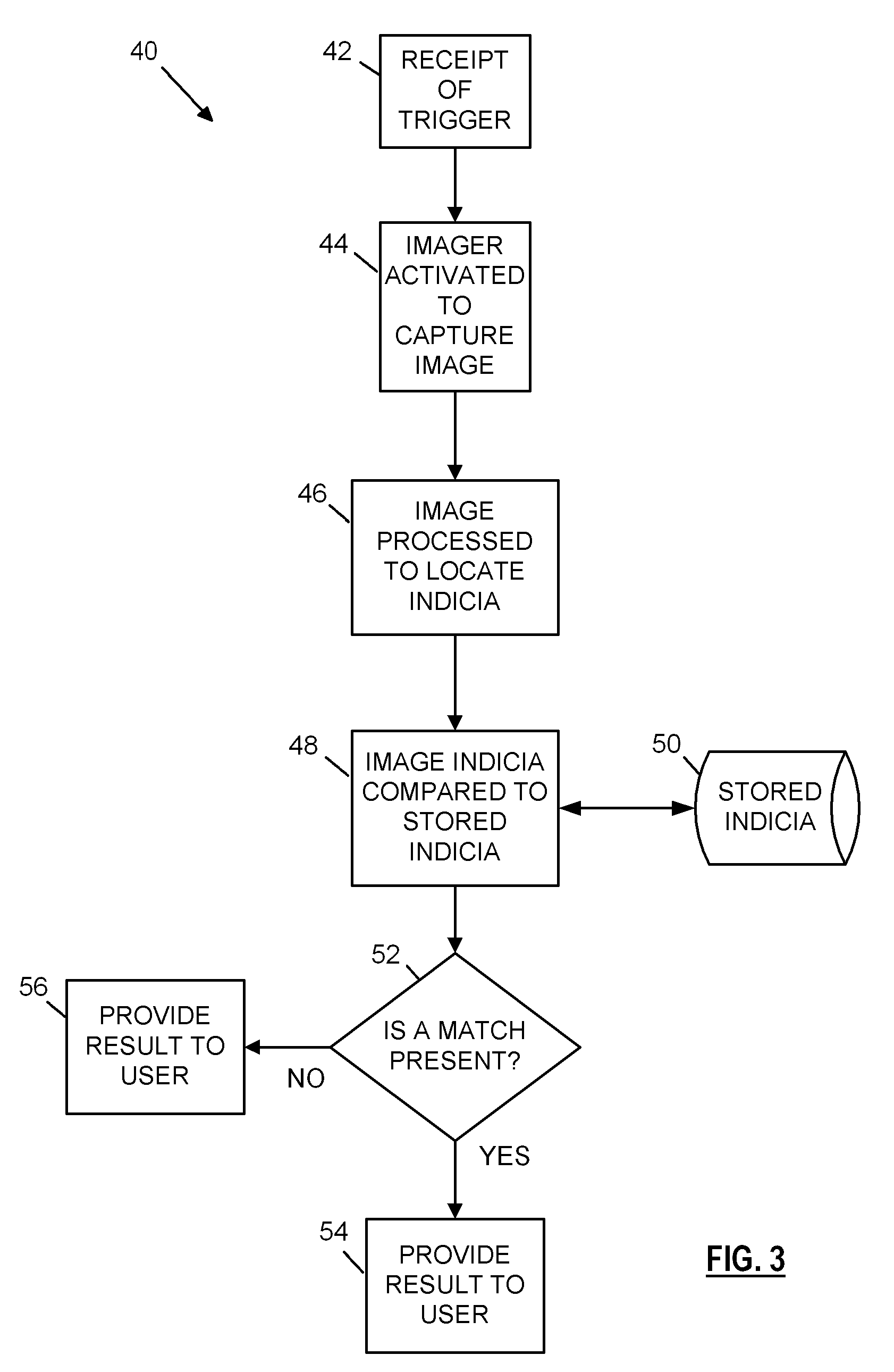
A system for automatically identifying a logo or trademark applied to a device and verifying that the logo or trademark is acceptably identifies a compatible device. The system uses an optical imager to capture optical images of the target device and a microcontroller interconnected to the imager for processing the optical image to extract image information and verify that the contents of the image reflect the appropriate manufacturer or supplied indicia required by a host device. The decision reached by the microcontroller may be provided externally to a host device, thereby precluding or allowing use of the device, or provided directly to a user via know means, such as a visual display or audible output.
Owner:NOVANTA CORP
Diagnositic and treatmetnt tool and method for electronic recording and indexing patient encounters for allowing instant search of patient history
InactiveUS20200043579A1Effective treatmentAccurate currentNatural language data processingSpecial data processing applicationsPatient diagnosisDatabase
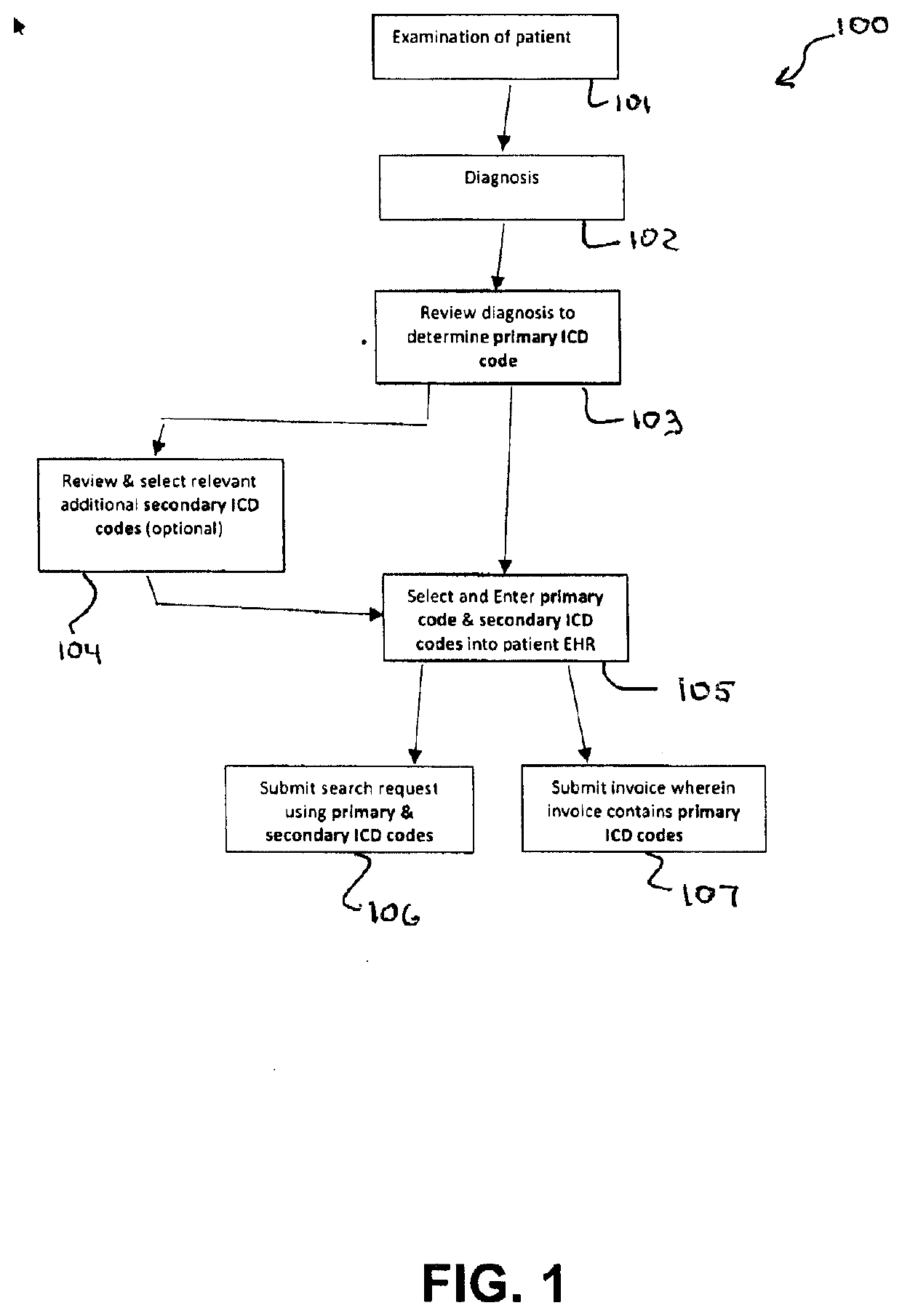
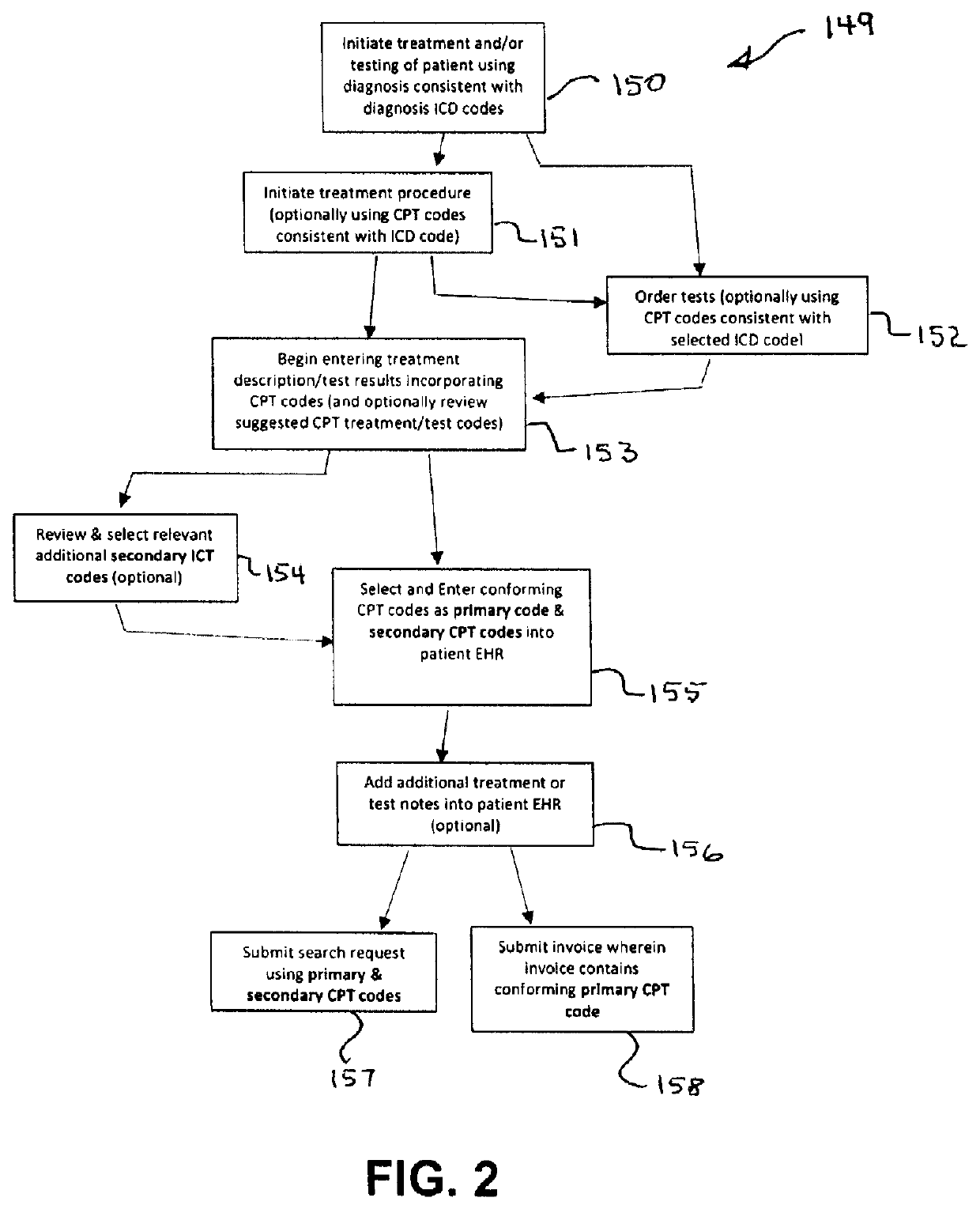
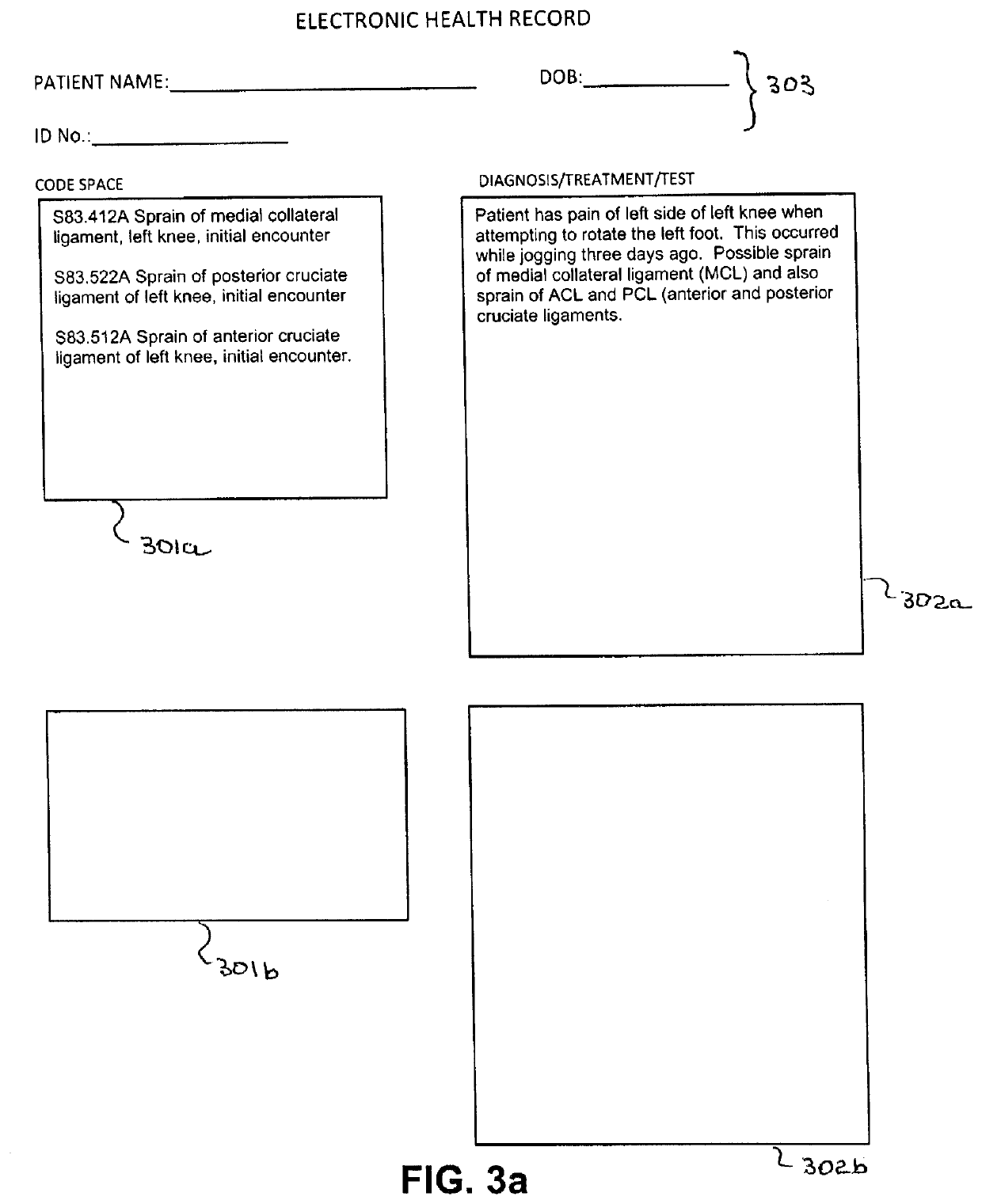
Device and method for improved diagnostic and treatment of patients. Clinician's notes of diagnosis, treatment or testing are electronically recorded thereby becoming an entry in a patient specific EHR. Coding appropriate to diagnosis etc., may be adapted by the clinician and the coding integrated into the EHR entry. The EHR may be searched using adapted codes as an index of diagnosis, treatment and testing. The tool and method includes program for facilitating entry of clinician notes (auto complete and autocorrection) and suggestion of appropriate code entries correlated to the content of the clinician notes. The program may include authentication protocols for protecting privacy and accesses to patient EHR. Code and code descriptors may be the product of established protocols such as CBD-10 or CPT. The tool and method may allow immediate search of patient's EHR for prior relevant conditions or treatment thereby facilitating prompt treatment of underlying cause of malady.
Owner:MIRR LLC
Method for online restoring abnormal data of wind power plant
ActiveCN103631681AQuick checkAccurate detectionRedundant operation error correctionPeaking power plantData set
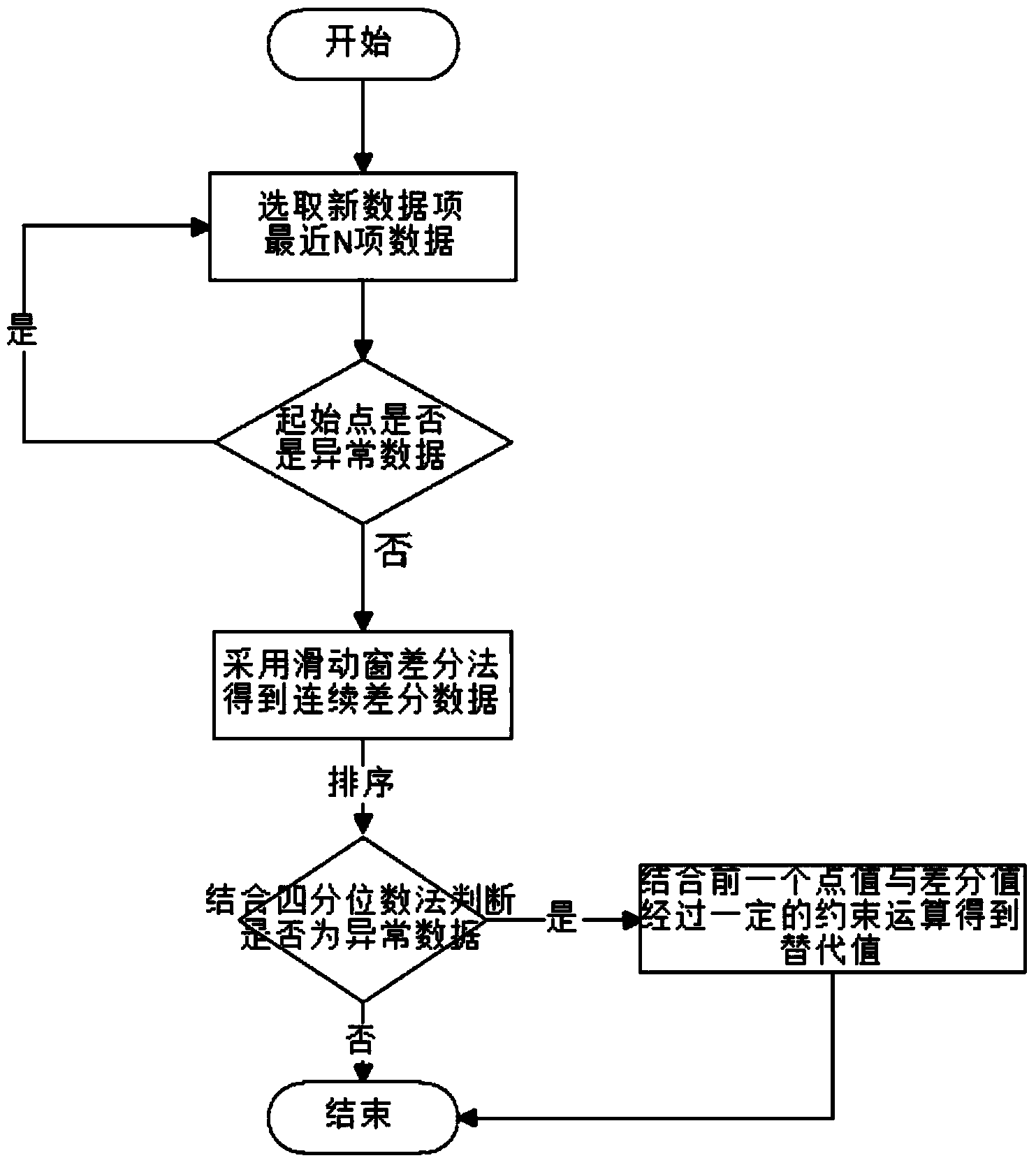
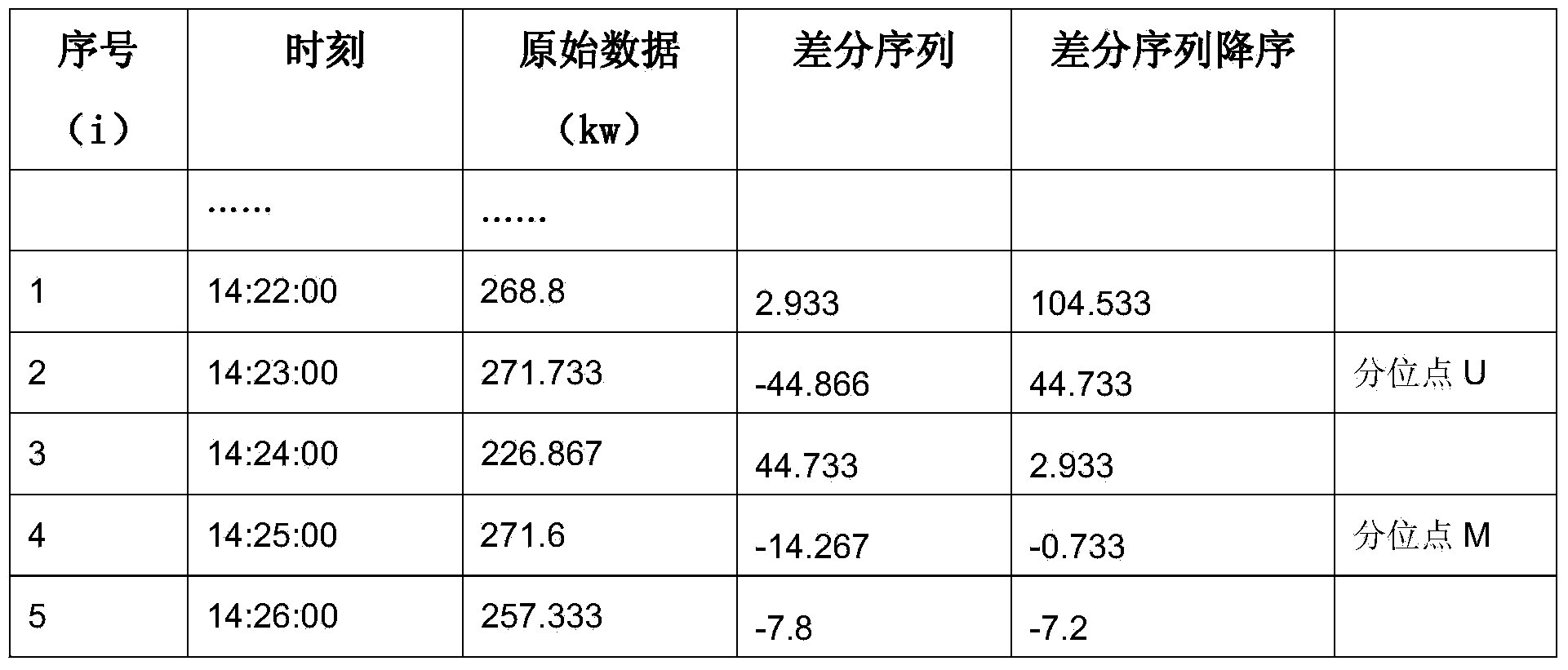
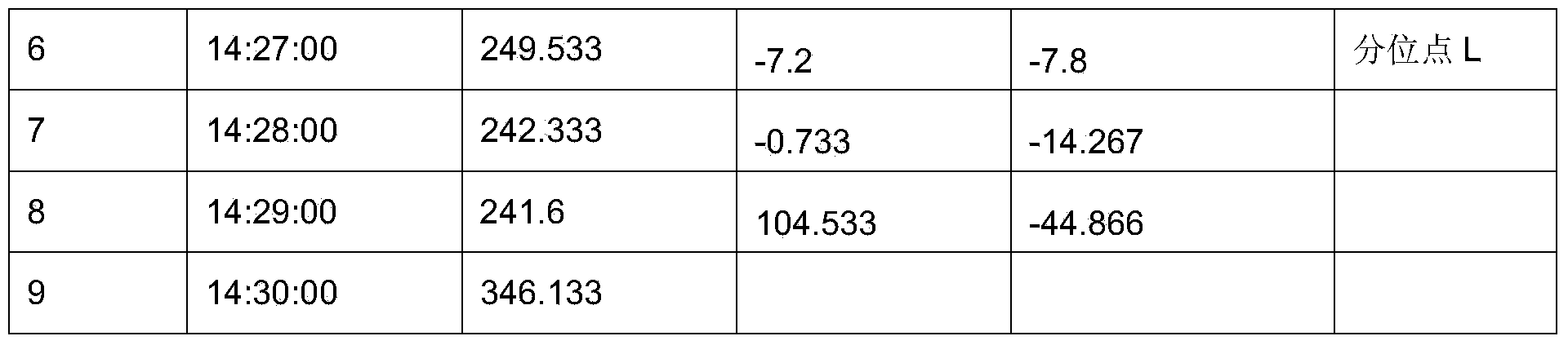
The invention provides a method for online restoring abnormal data of a wind power plant. The method comprises the following steps of I, determining a processed data item according to the data of the wind power plant; II, selecting a starting point of the processed data item; III, acquiring a continuous differential data sequence by adopting a slide window differential method; IV, judging whether the data is the abnormal data or not by utilizing a quartile method; and V, determining a restored data set. By adopting the method, the requirement on online detecting and restoring the abnormal data can be met, the data quality can be effectively improved, the quality of the collected data can be guaranteed, and the influence of the abnormal source on the data analysis can be reduced.
Owner:STATE GRID CORP OF CHINA +3
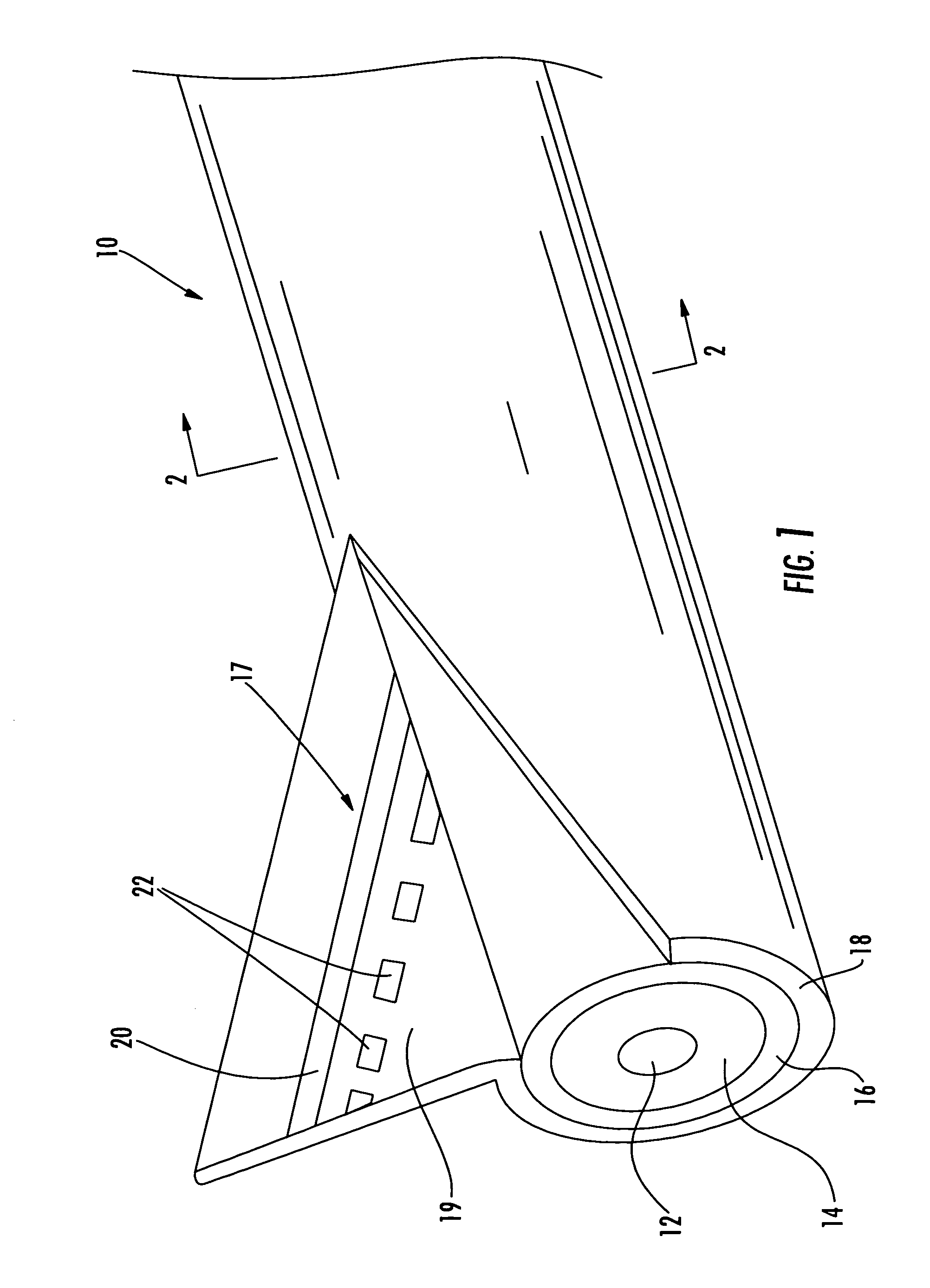
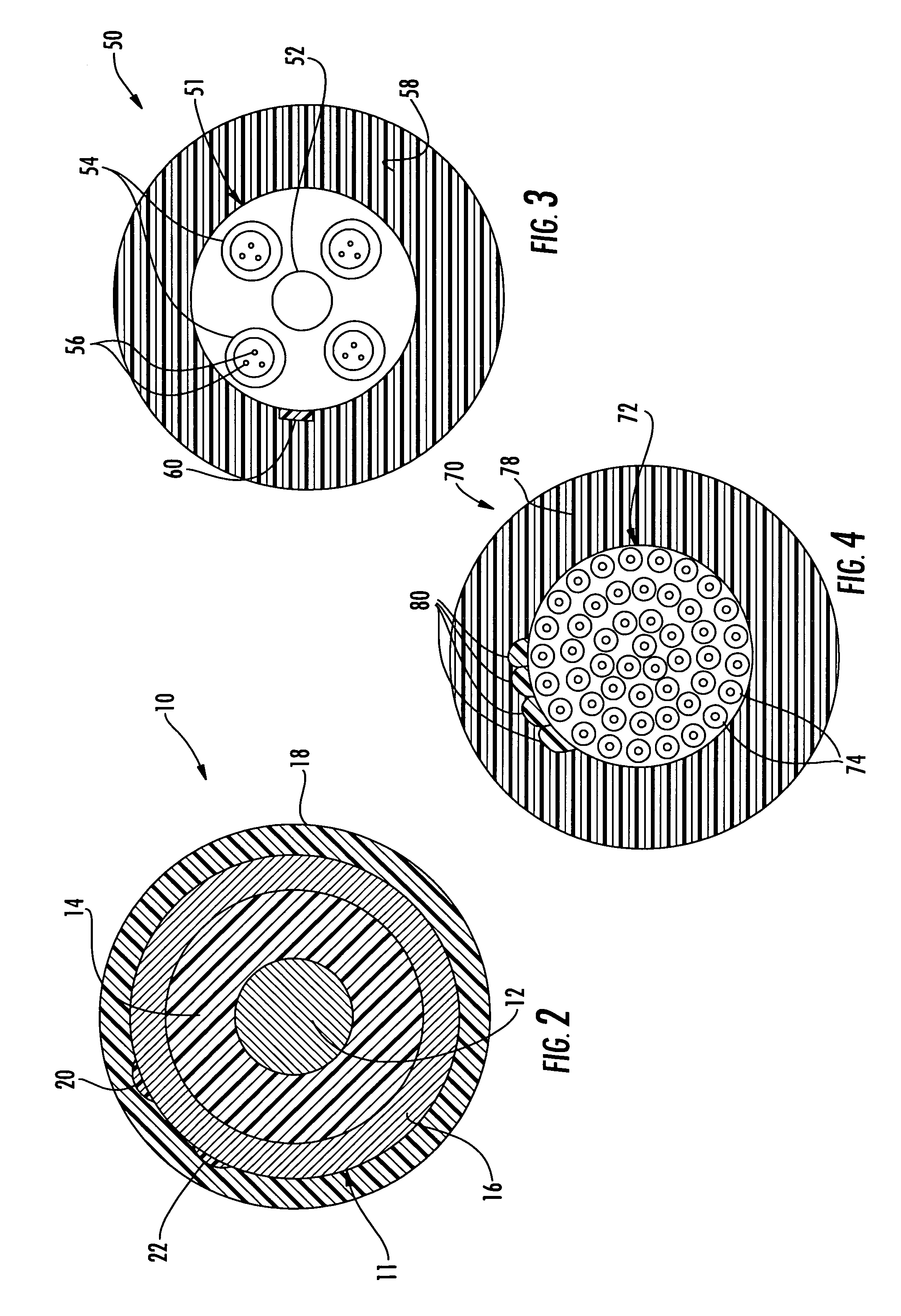
Cable having internal identifying indicia and associated methods
InactiveUS7468489B2Discouraging unauthorized counterfeitingEnsure authenticityInsulated cablesFibre mechanical structuresEngineeringElectrical and Electronics engineering
Owner:COMMSCOPE INC
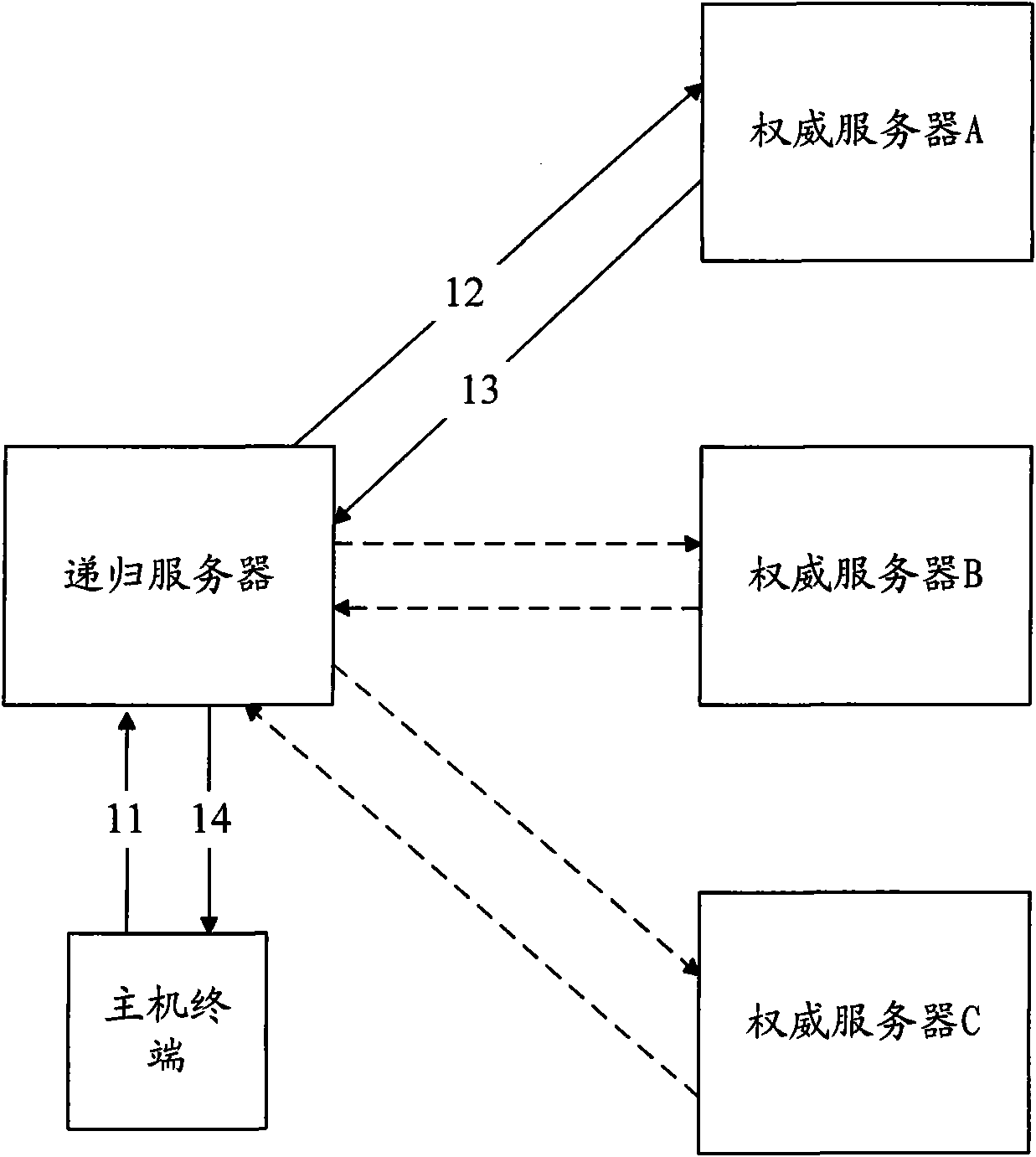
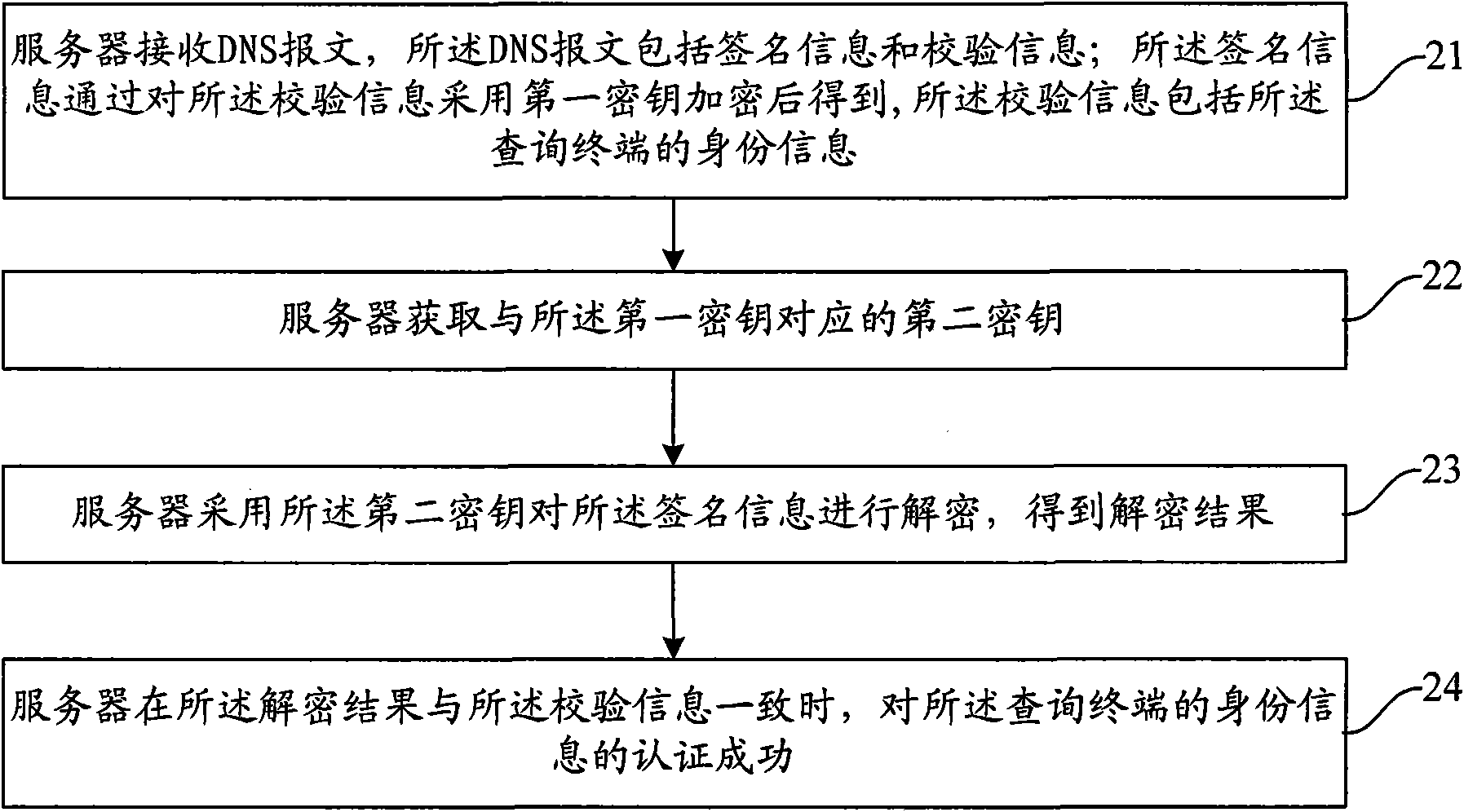
Method, server and system for authenticating identify information in DNS message
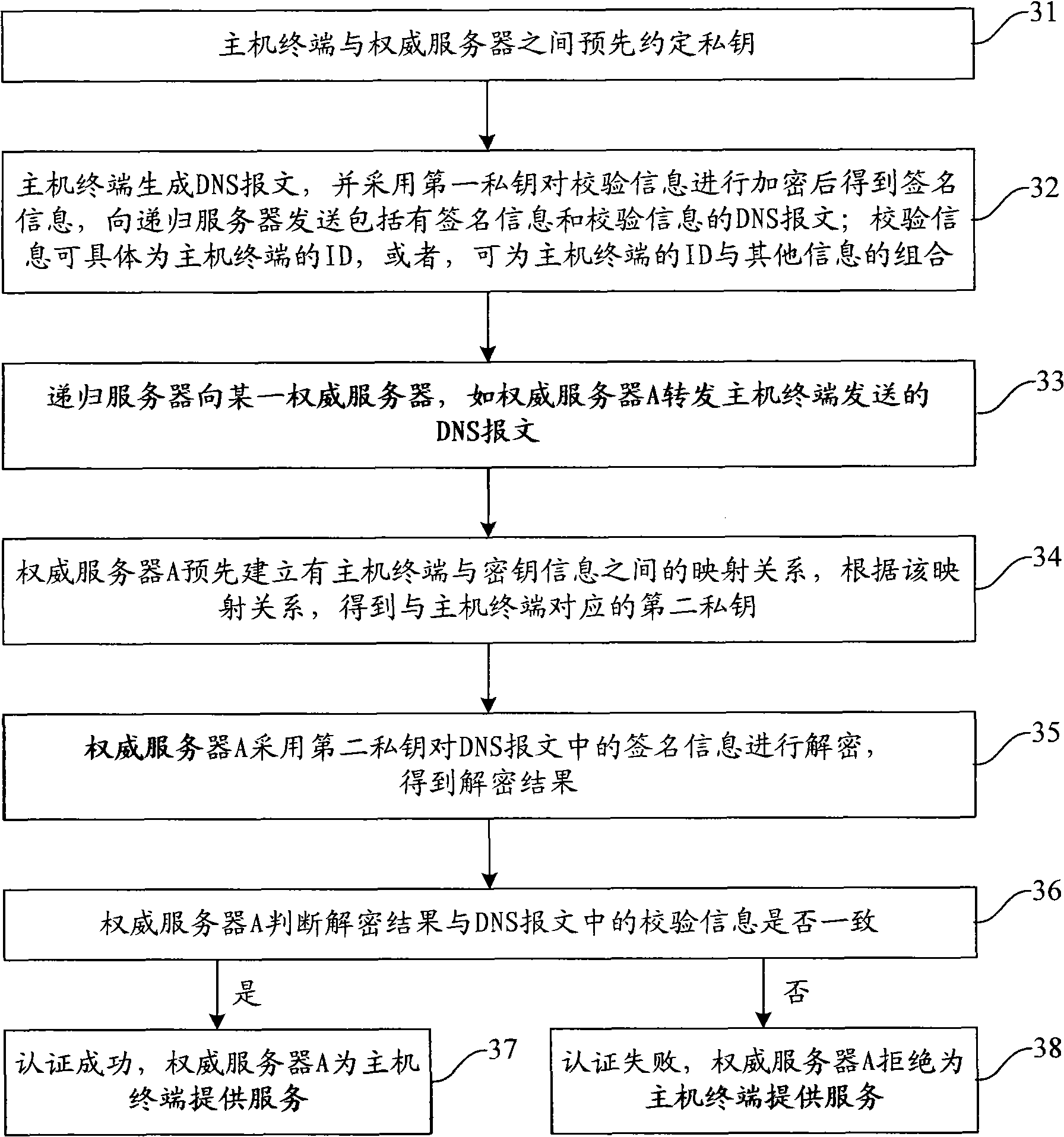
InactiveCN101841521AImprove securityEnsure authenticityUser identity/authority verificationDomain nameDomain Name System
The invention provides a method, a server and a system for authenticating identify information in a DNS (Domain Name Server) message, belonging to the technical field of internet. The method comprises the following steps of: receiving a DNS message, wherein the DNS message comprises signature information and check information, the signature information is obtained by encrypting the check information with a first key, and the check information comprises the identify information of the inquiry terminal; acquiring a second key corresponding to the first key; decrypting the signature information with the second key to obtain a decryption result; and succeeding in authenticating the identify information of the inquiry terminal when the decryption result is in accordance with the check information. By introducing the mechanism of authenticating the identify information in the DNS message to a domain name system, the invention effectively prevents other terminals from defrauding service by counterfeiting the identify information of the inquiry terminal having access authority when the server carries out access control based on the identify information of the inquiry terminal, thereby improving the safety of the domain name system.
Owner:COMP NETWORK INFORMATION CENT CHINESE ACADEMY OF SCI
Method and Device for Identifying an Electric Vehicle to a Billing Centre
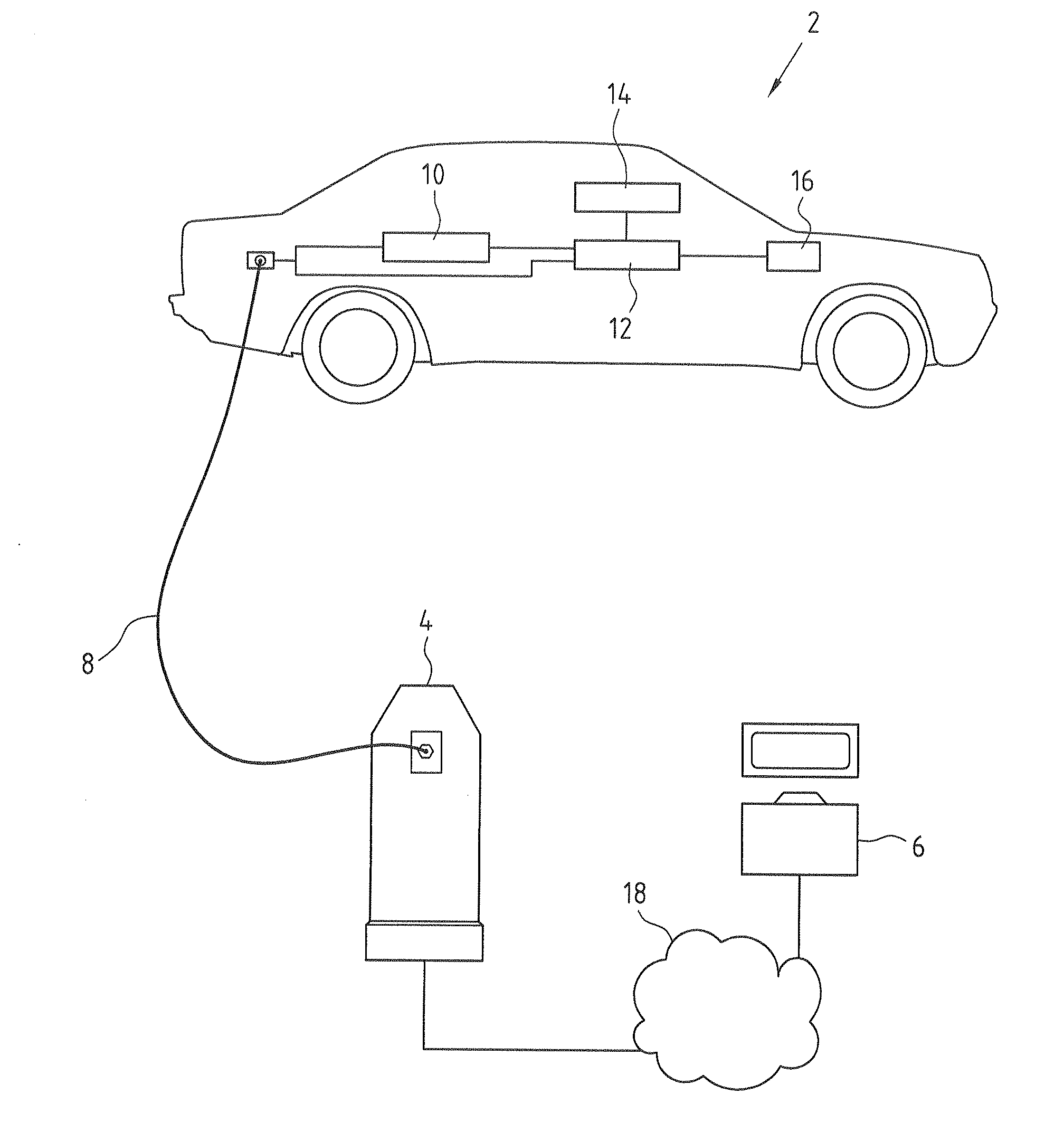
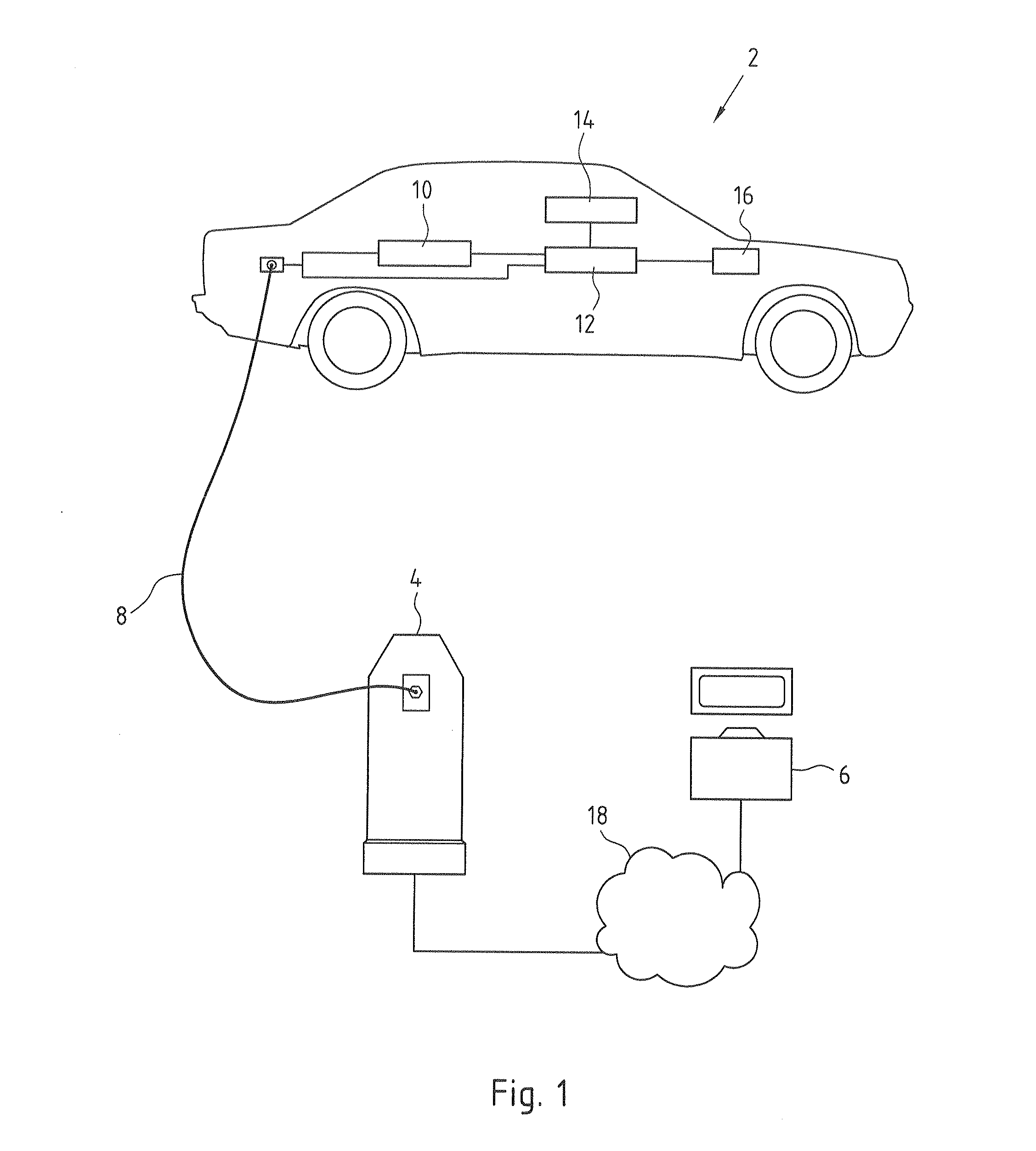
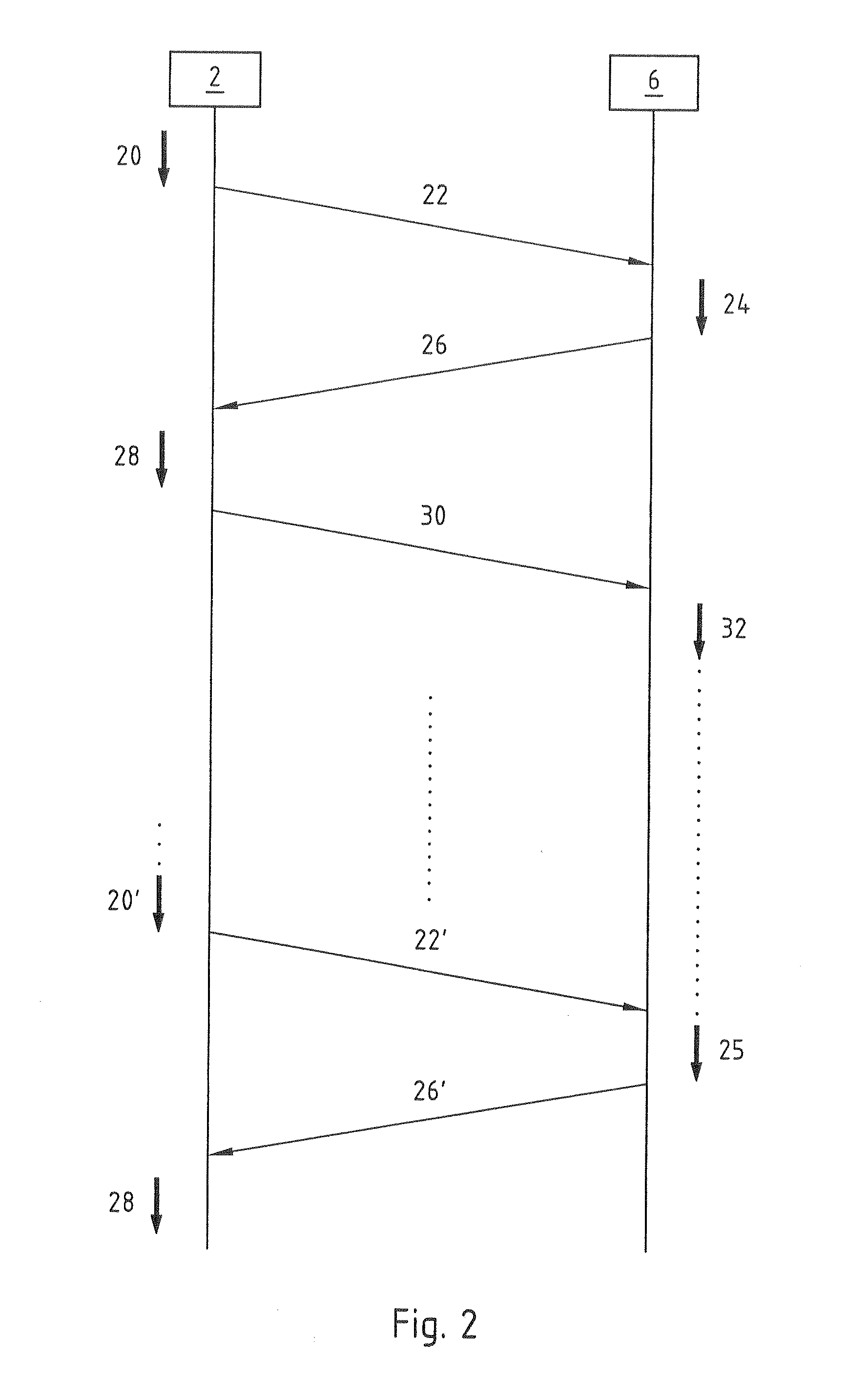
InactiveUS20120169282A1Ensure authenticityCost-intensiveCircuit authenticationCharging stationsCharging stationAutomotive engineering
Method, device and system for charging electric vehicles. Carrying out 28 on the vehicle side a charging process at a charging station, emitting 30 on the vehicle side an item of information about the charging process and receiving 24 on the vehicle side a current contract key after the emission on the vehicle side of the information about the charging process are proposed for identifying an electric vehicle to a billing centre.
Owner:INNOGY SE
Embedded optical signatures in documents
ActiveUS7252222B2Provide informationEnsure authenticityPaper-money testing devicesCharacter and pattern recognitionDocument preparationDocumentation
Owner:SCI GAMES LLC
System and method for signing and authenticating secure transactions through a communications network
ActiveUS20150170144A1Ensure authenticityPrevent cheatingFinanceElectronic credentialsPasswordHardware security module
A system to sign and authenticate secure transactions with an institution through a communications network, comprising a terminal connected to a communications network; a remote server with a database that stores for each user the user data userID, a private password encrypted K′priv, userID, a first security password K′mac, userID to generate an authentication password Kmac, userID and an identifier of the mobile device, Id′cel,userID; a mobile communication device of a user comprising a security code pin; an application, a transport password Ktransporte; a public password encrypted K″pub, userID and a second security password K″mac, userID for generating said authentication password Kmac, userID, and a remote hardware security module. A method to sign and authenticate secure transactions with an institution through a communications network with said system.
Owner:PALMA LIZANA MAURICIO EDUARDO +1
Method and system for finishing house property transaction and fund supervision based on intermediate platform
InactiveCN106204359AImprove transaction efficiencyImprove efficiencyFinanceProduct appraisalPaymentData information
The invention discloses a method and a system for finishing house property transaction and fund supervision based on an intermediate platform. The method for finishing the house property transaction fund supervision based on the intermediate platform comprises a real name authentication process, a house source and credit check process, a house property transaction and fund supervision process and a loan application process. According to the method and the system, the intermediate platform is in communication connection with terminals and systems involved in the house property transaction process to finish large house payment online, so that the house property transaction efficiency is greatly improved and the data transmission security is ensured; and the strict authentication process is adopted for important data information, so that the authenticity and validity of the information are ensured, the authenticity of transaction is effectively guaranteed, the credibility of a transaction party is enhanced, the operation is convenient, and the transaction is facilitated more easily.
Owner:上海三富信息科技有限公司
Distributed public key infrastructure construction method based on editable blockchain
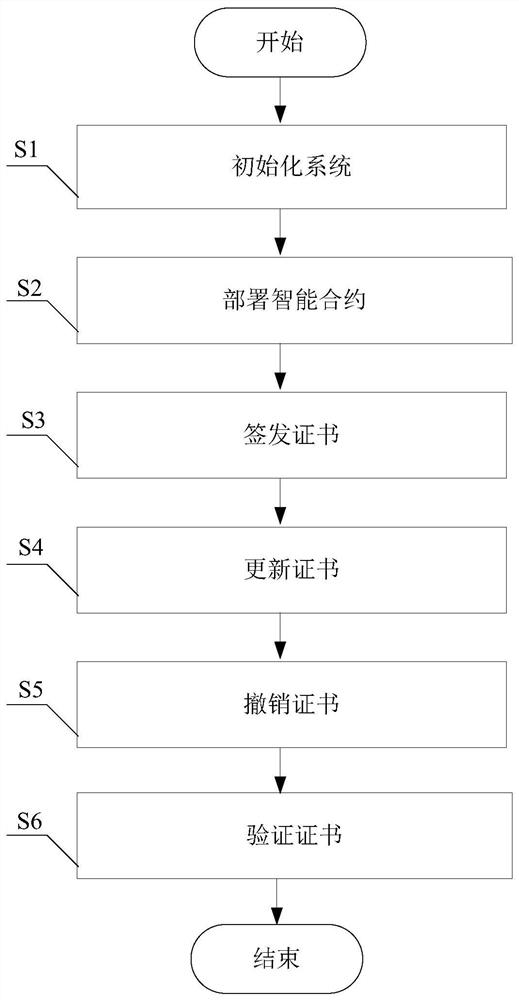
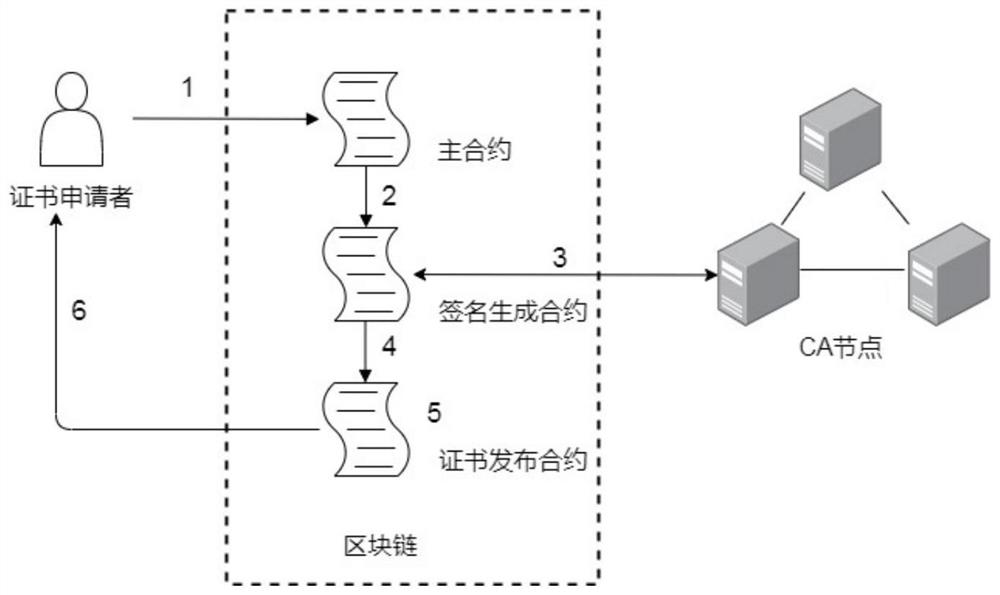
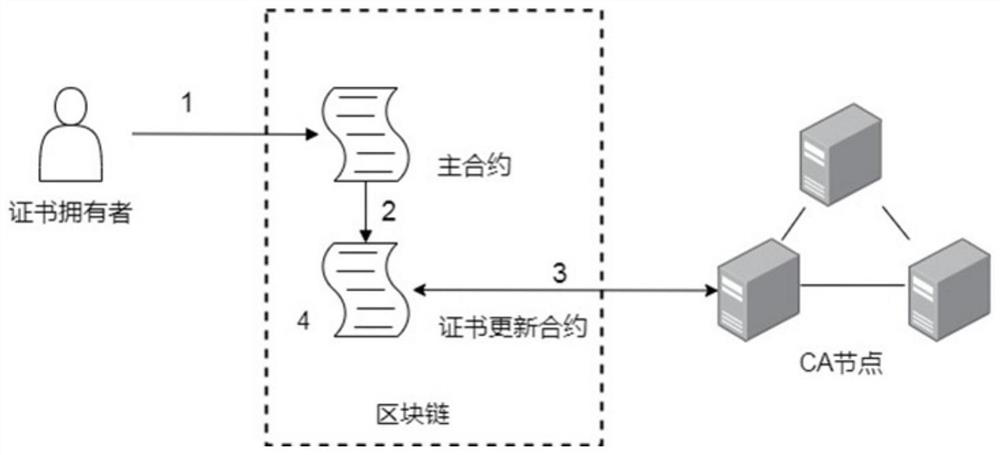
ActiveCN112187455AReduce storage pressureReduce verification timeKey distribution for secure communicationUser identity/authority verificationEngineeringSmart contract
The invention provides a distributed public key infrastructure construction method based on an editable blockchain, and belongs to the technical field of public key infrastructure, and the method comprises the following steps: S1, initializing a system; S2, deploying an smart contract; S3, signing and issuing a certificate; S4, updating the certificate; S5, revoking the certificate; and S6, verifying the certificate. Compared with an existing PKI system based on a blockchain, an editable blockchain framework is creatively adopted, a new block does not need to be uploaded during certificate updating and revocation, the storage pressure of a blockchain network can be reduced, the certificate verification time can be shortened, a threshold ring is used for signing and issuing a certificate, and an authentication mechanism is composed of multiple CA nodes; the CA independently audits the operation request for the certificate, and the certificate can be operated only after the CA exceedingthe threshold number passes the auditing, so that the tolerance of the system to a Byzantine node is improved, and the security is relatively high.
Owner:SOUTHWEST JIAOTONG UNIV +1
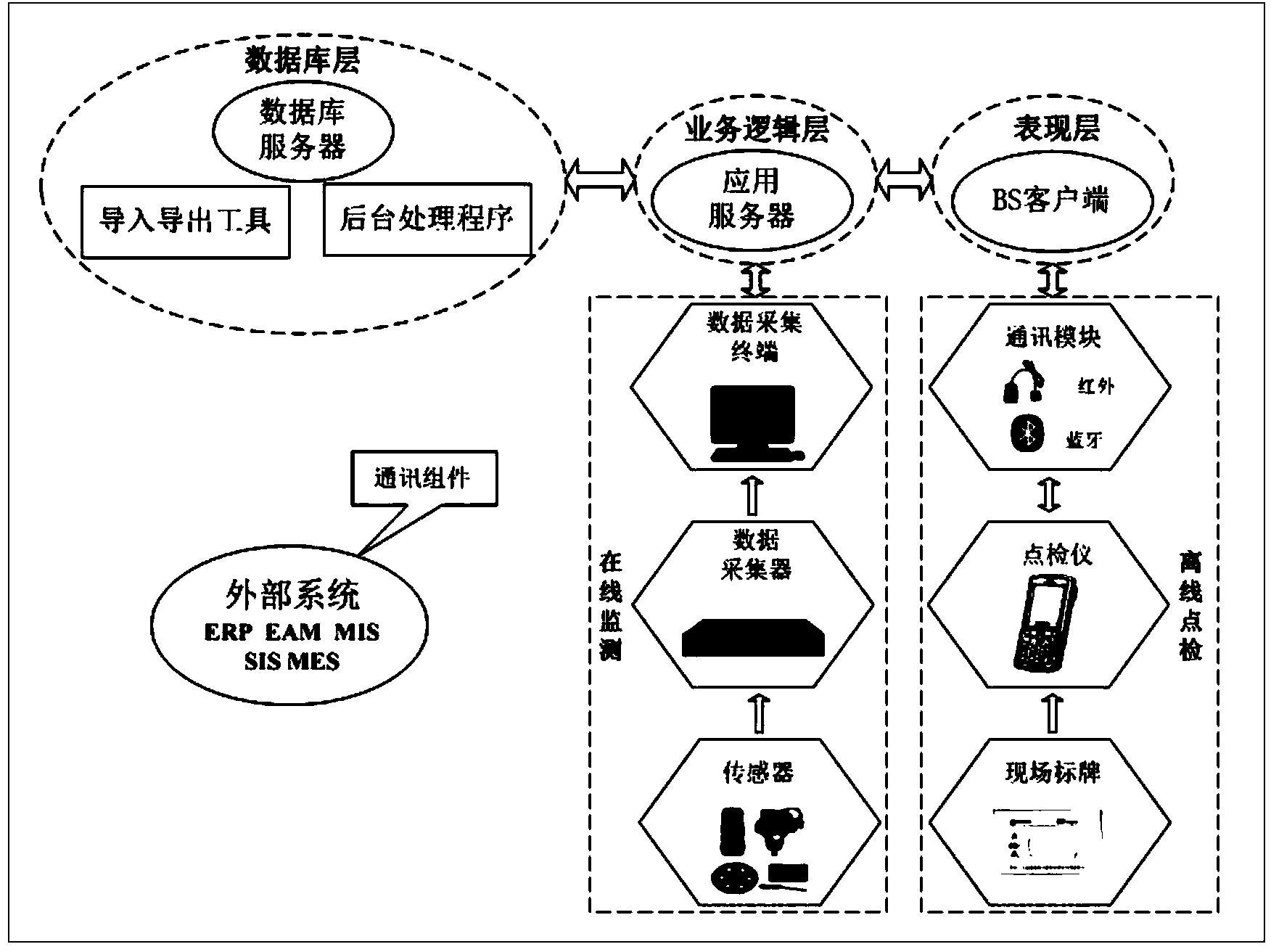
Chemical industry production site patrol system based on internet of things technology
InactiveCN103714434AChange uncontrollableImprove production management levelChecking time patrolsTechnology managementChemical industryThe Internet
The invention discloses a mechanical industry production site patrol system based on the internet of things technology. An MVC mode is adopted for the system. The system comprises a presentation layer, a service logic layer and a database layer, wherein the presentation layer is used for presenting functions of the system and interacting with a user, and the presentation layer of the system includes two forms, namely, a user browser end and a handheld patrol instrument. The service logic layer is used for data exchange between the database layer and the presentation layer, dispatching requests of the user, selecting an appropriate presentation method for display, explaining input of the user, and mapping the input of the user to the executable operation of the database layer. The database layer is composed of all levels of database resources.
Owner:SHANGHAI HUAYI INFORMATION TECH
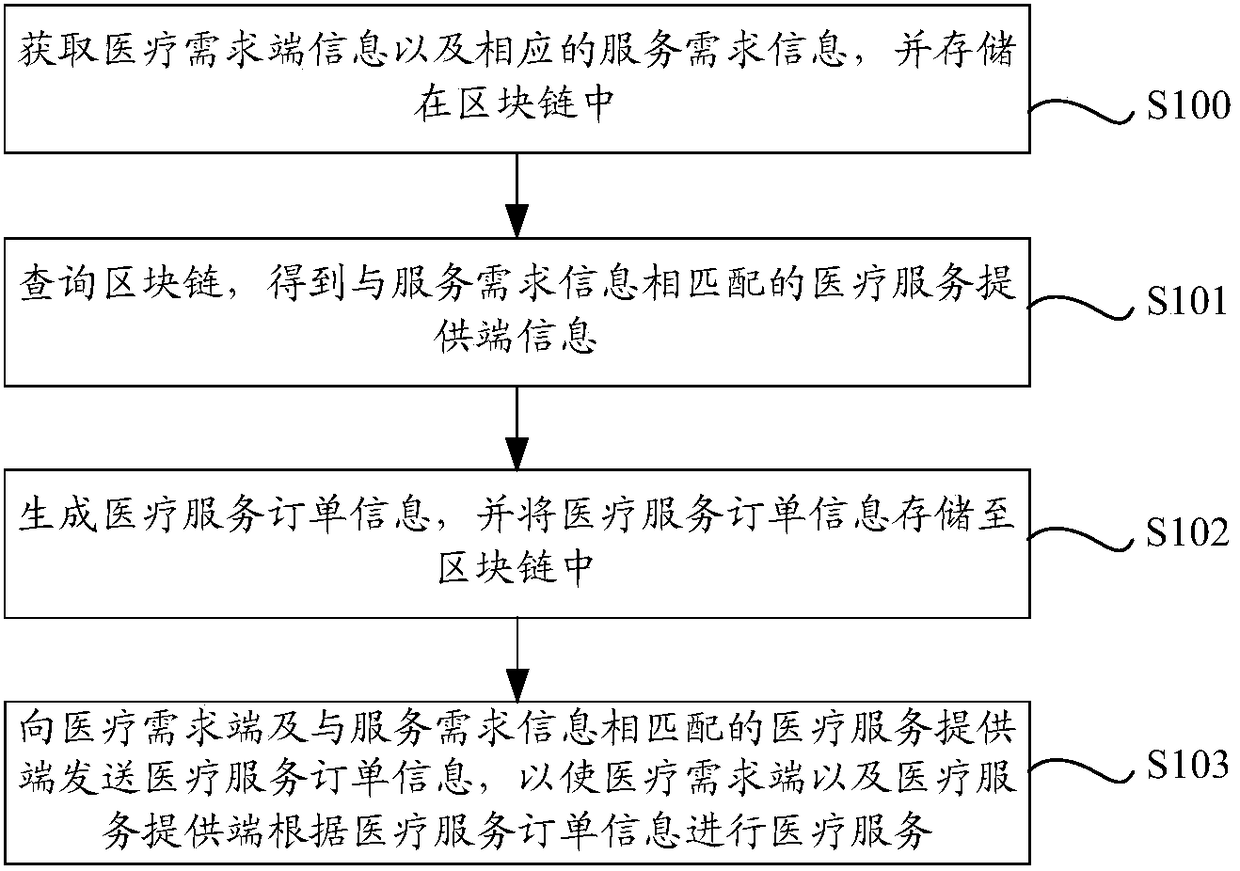
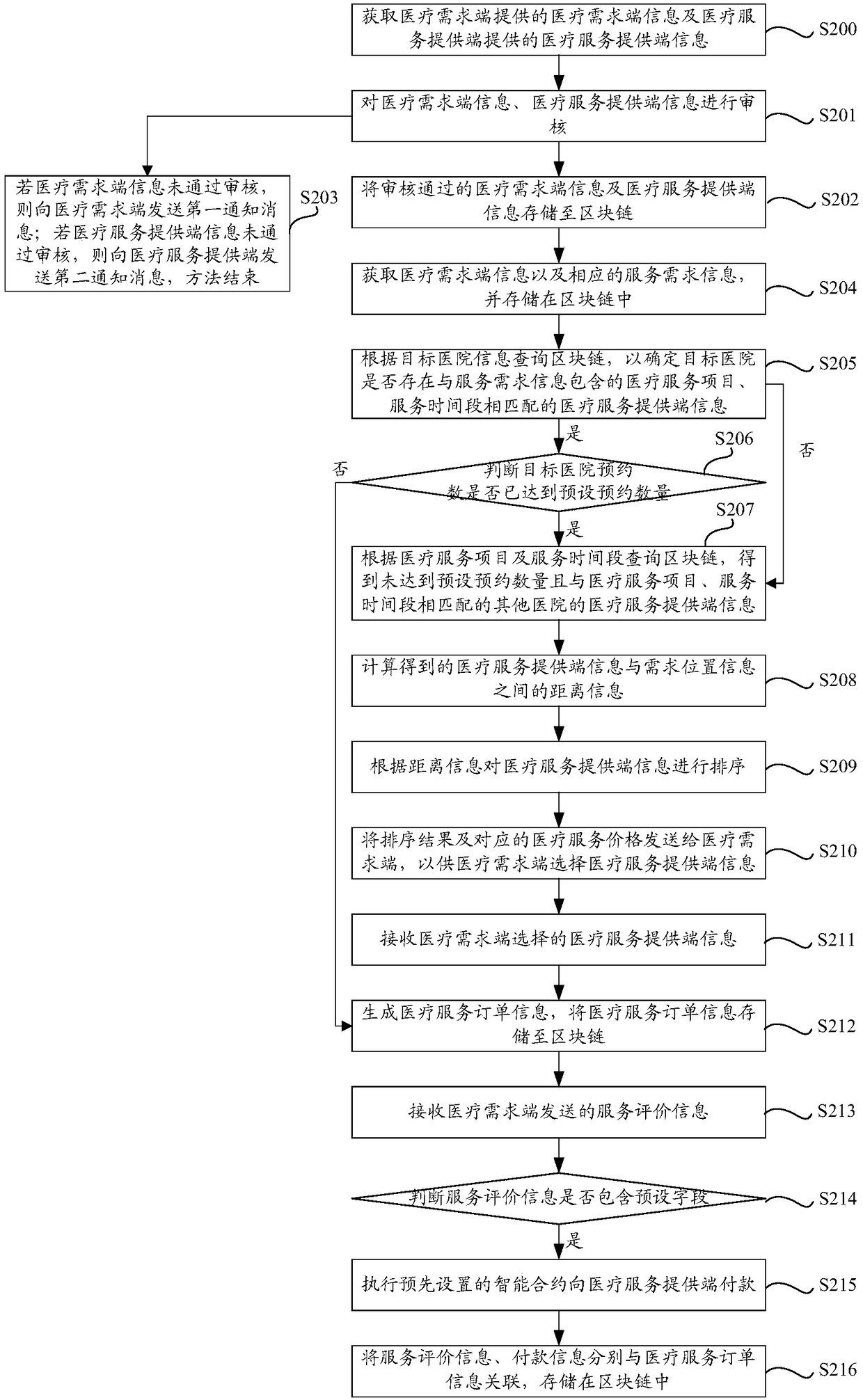
Blockchain-based medical resource data processing method and device
InactiveCN109256195AAvoid wasting timeImprove medical experienceMedical communicationHealthcare managementService provisionMedical treatment
The invention discloses a blockchain-based medical resource data processing method and device. The method includes the following steps that: medical demand end information and corresponding service demand information are obtained, and are stored in a blockchain; the blockchain is queried, so that medical service provision end information matched with the service demand information is obtained; medical service order information is generated, and the medical service order information is stored in the blockchain, wherein the medical service order information contains the service demand information, the medical demand end information, and the medical service provision end information; and the medical service order information is sent to a medical demand end and a medical service provision endmatched with the service demand information, so that the medical demand end and the medical service provision end can perform medical service according to the medical service order information. With the blockchain-based medical resource data processing method and device provided by the technical schemes of the invention adopted, data fidelity can be realized through the blockchain; the authenticity of the data can be improved; and the medical demand end can enjoy on-site medical services without going to a hospital, and therefore, convenient medical consultation and treatment is realized, andthe experience of the medical demand end in medical consultation and treatment can be improved.
Owner:苏州朗润创新知识产权运营有限公司
Traffic in-loop automatic driving simulation system
PendingCN111781855AGuarantee authenticityGuaranteed accuracySimulator controlTraffic sceneVirtual test
The invention discloses a traffic in-loop automatic driving simulation system, which can acquire transmitted real roads and traffic data according to an Internet of Vehicles technology, and constructa first simulation traffic scene according to the real roads and the traffic data so as to ensure the authenticity of the first simulation traffic scene. And on the basis, the system constructs the virtual tested vehicle and the state data thereof, the virtual tested vehicle and the state data thereof are fused into the first simulation traffic scene to obtain a virtual traffic scene, and the virtual tested vehicle is controlled to automatically drive and timely update the virtual traffic scene according to the virtual traffic scene so as to complete interactive simulation of the virtual traffic scene and the virtual tested vehicle. The authenticity and the accuracy of a simulation result in a simulation test can be ensured.
Owner:北京领骏科技有限公司
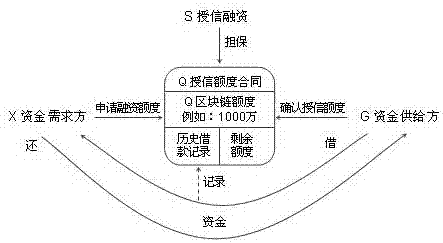
Guarantee credit financing program based on blockchain
The invention discloses a guarantee credit financing scheme based on block chain technology, which adds block chain technology to the existing guarantee credit financing plan, and records all credit line contracts, historical loan records, remaining credit line, etc. in the On the blockchain, with the help of distributed encrypted records and non-tamperable modification of blockchain technology, the guarantee credit line of all parties involved can be verified in real time, improving efficiency and reducing costs.
Owner:HANGZHOU FUZAMEI TECH CO LTD
Robot intelligent grabbing method based on digital twinning and deep neural network
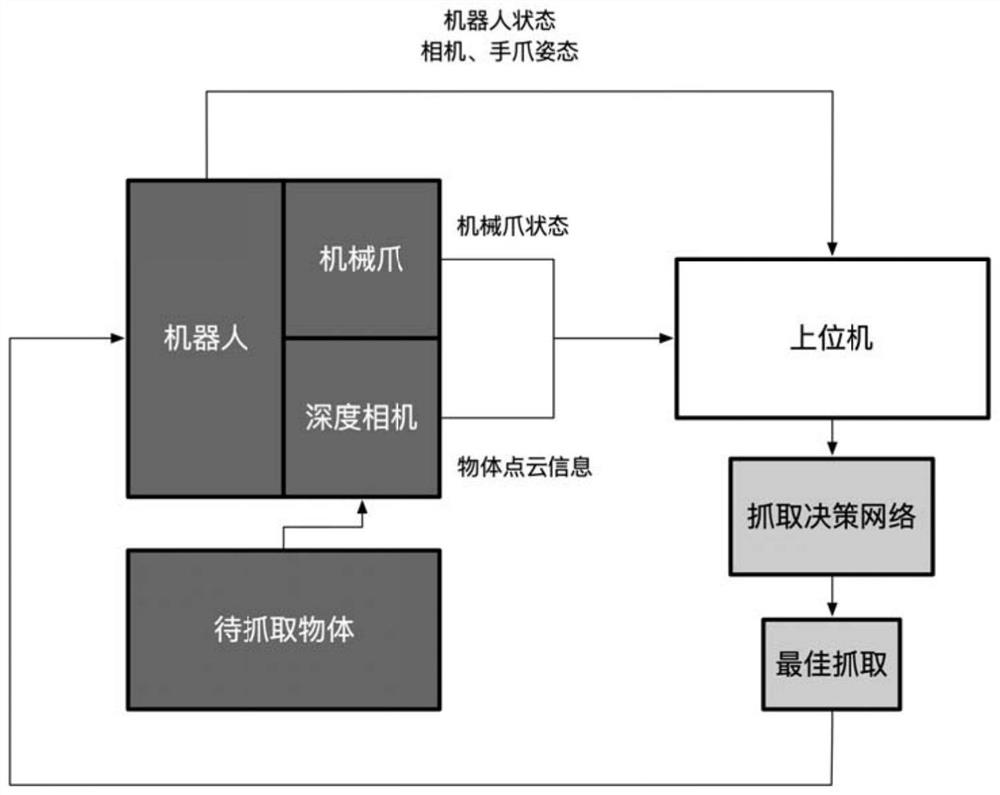
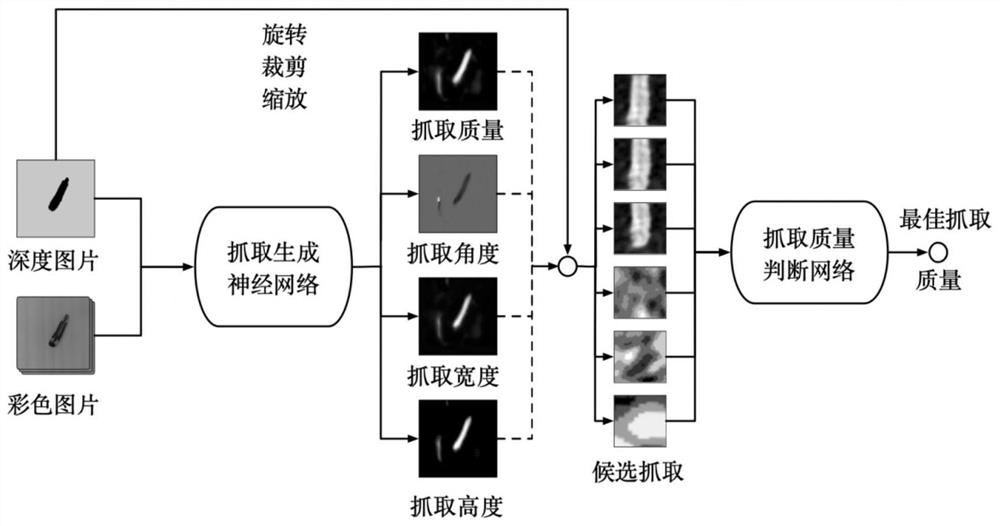
ActiveCN112297013AEnsure authenticityEnsure reliabilityProgramme-controlled manipulatorNeural architecturesPattern recognitionPoint cloud
The invention discloses a robot intelligent grabbing method based on digital twinning and a deep neural network. The robot intelligent grabbing method comprises a physical grabbing environment, a virtual recognition environment and a core neural network part. The physical environment is composed of a depth camera, a robot, a mechanical claw and a grabbed object and is a main executing mechanism for grabbing. The virtual recognition environment is composed of a point cloud file constructed by the depth camera and related postures of a robot and a claw, and is a virtual environment set of a robot state, a mechanical claw position, a camera posture and an object placement position. The core neural network comprises a grabbing generation network and a grabbing recognition network, and the grabbing mode is sampled and judged to generate an optimal grabbing posture. According to the robot intelligent grabbing method, the optimal grabbing position and posture can be rapidly and efficiently judged based on the color-depth image collected by the camera.
Owner:ZHEJIANG UNIV
Embedded optical signatures in documents
ActiveUS7364091B2Provide informationEnsure authenticityPaper-money testing devicesBoard gamesDocumentationComputer science
A method of embedding an optical signature in a document and document produced therefrom. The optical signature is an optical pattern preferably being a series of discrete marks that can be aligned in a grid that generates a known value, and the same value can be generated from examination of a document by aligning at least an X-Y coordinate grid over the embedded optical pattern. The document can be validated, authenticated, or the determination of a valid copy of an original document with the embedded optical signature made through comparison of the known value and the value generated from the optical pattern on the document. The optical pattern can also be generated from other identification codes on the document.
Owner:SCI GAMES LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com