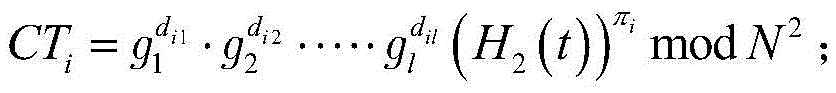Patents
Literature
254results about How to "Reduce verification time" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
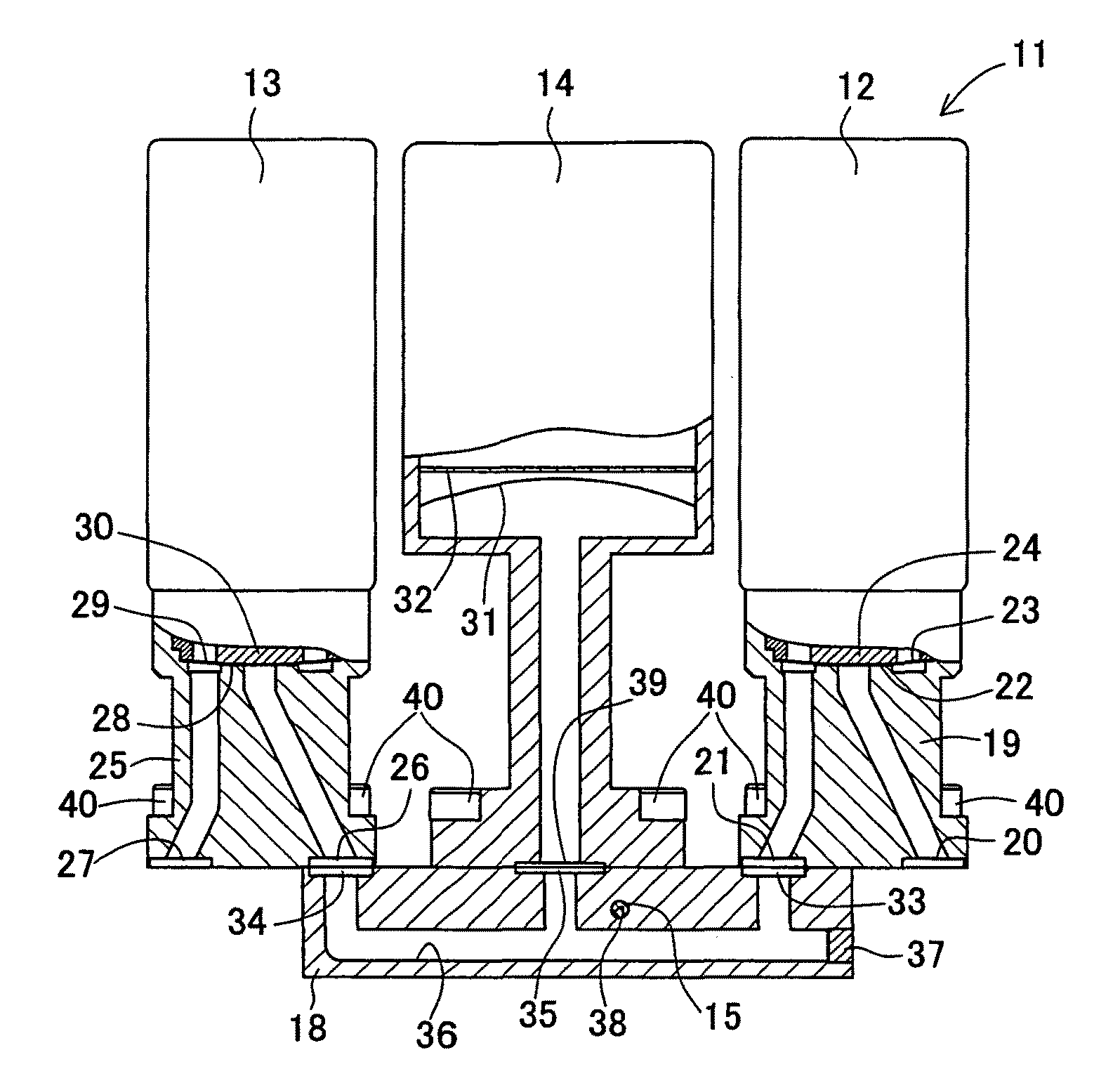
Gas flow rate verification unit
ActiveUS7716993B2Increase flow rateUniform pressureMultiple way valvesPipeline systemsEngineeringGas supply
A gas flow rate verification unit capable of enhancing reliability of gas flow rate verification. The gas flow rate verification unit has a first cutoff valve that is connected to a flow rate control device and to which gas is inputted, a second cutoff valve for discharging the gas, a communication member for allowing the first cutoff valve and the second cutoff valve to communicate with each other, a pressure sensor for detecting the pressure of the gas supplied between the first cutoff valve and the second cutoff valve, a temperature detector for detecting the temperature of the gas supplied between the first cutoff valve and the second cutoff valve, and a control means for verifying the flow of the gas flowing in the flow control device, the verification being performed by using both the result of the pressure detected by the pressure sensor and the result of the temperatures detected by the temperature detector. The volume (Vk) between the valve seat of the first cutoff valve and the valve seat of the second cutoff valve is equal to or less than the volume (Ve) between the outlet of the flow control device and the valve seat of the first cutoff valve.
Owner:CKD
Dynamic-based verification apparatus for verification from electronic system level to gate level, and verification method using the same
InactiveUS20110184713A1Reduce verification timeImprove verification efficiencyAnalogue computers for electric apparatusCAD circuit designElectronic systemsComputer architecture
The simulation consists of a front-end simulation and a back-end simulation. The front-end simulation can use an equivalent model at different abstraction level, or a simulation model for the back-end simulation. The back-end simulation uses the simulation result of front-end simulation so that it can run one or more simulation runs sequentially or in parallel. Alternatively, models at lower level of abstraction are simulated together with a model at higher level of abstraction in parallel using two or more simulators.
Owner:YANG SEI YANG
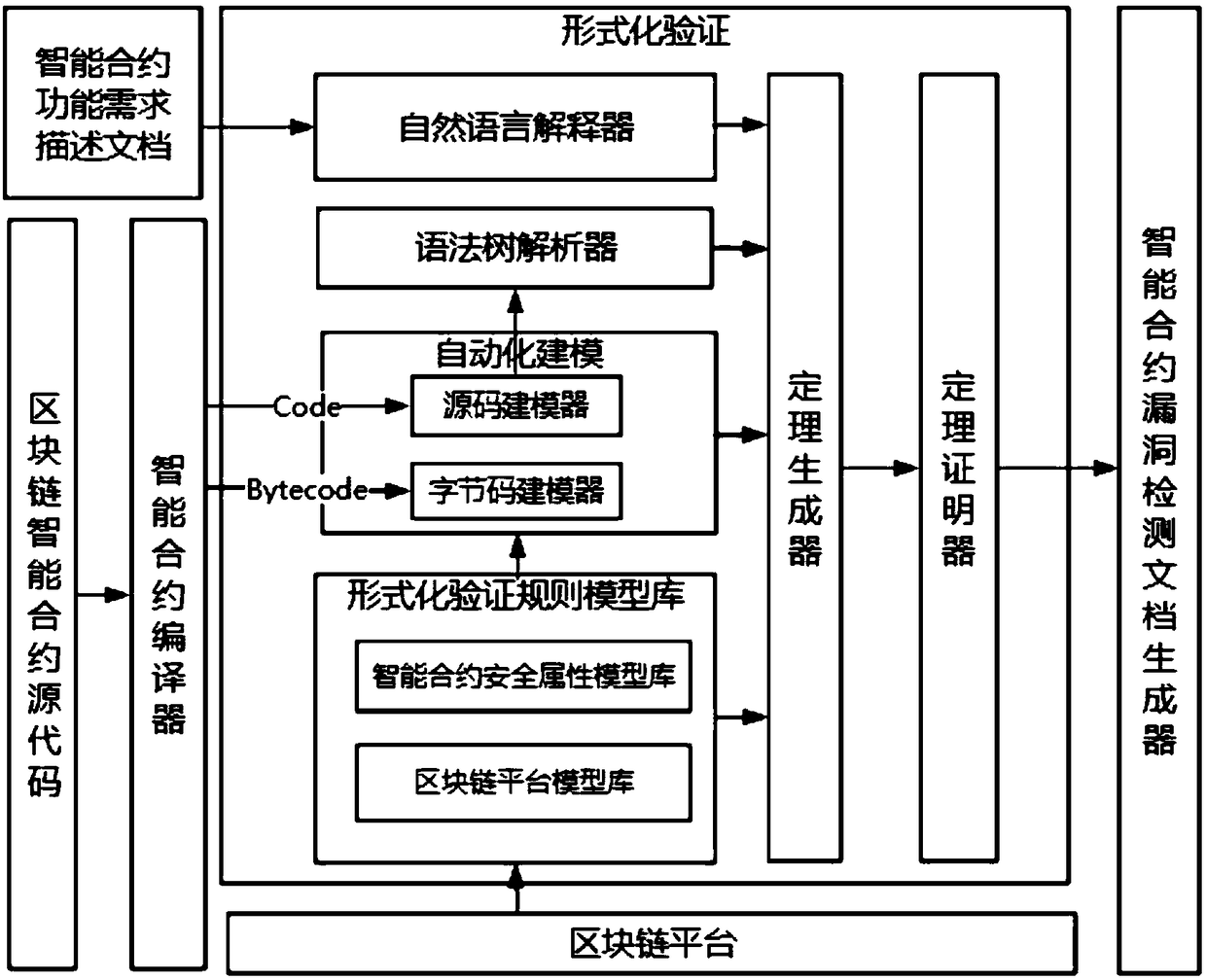
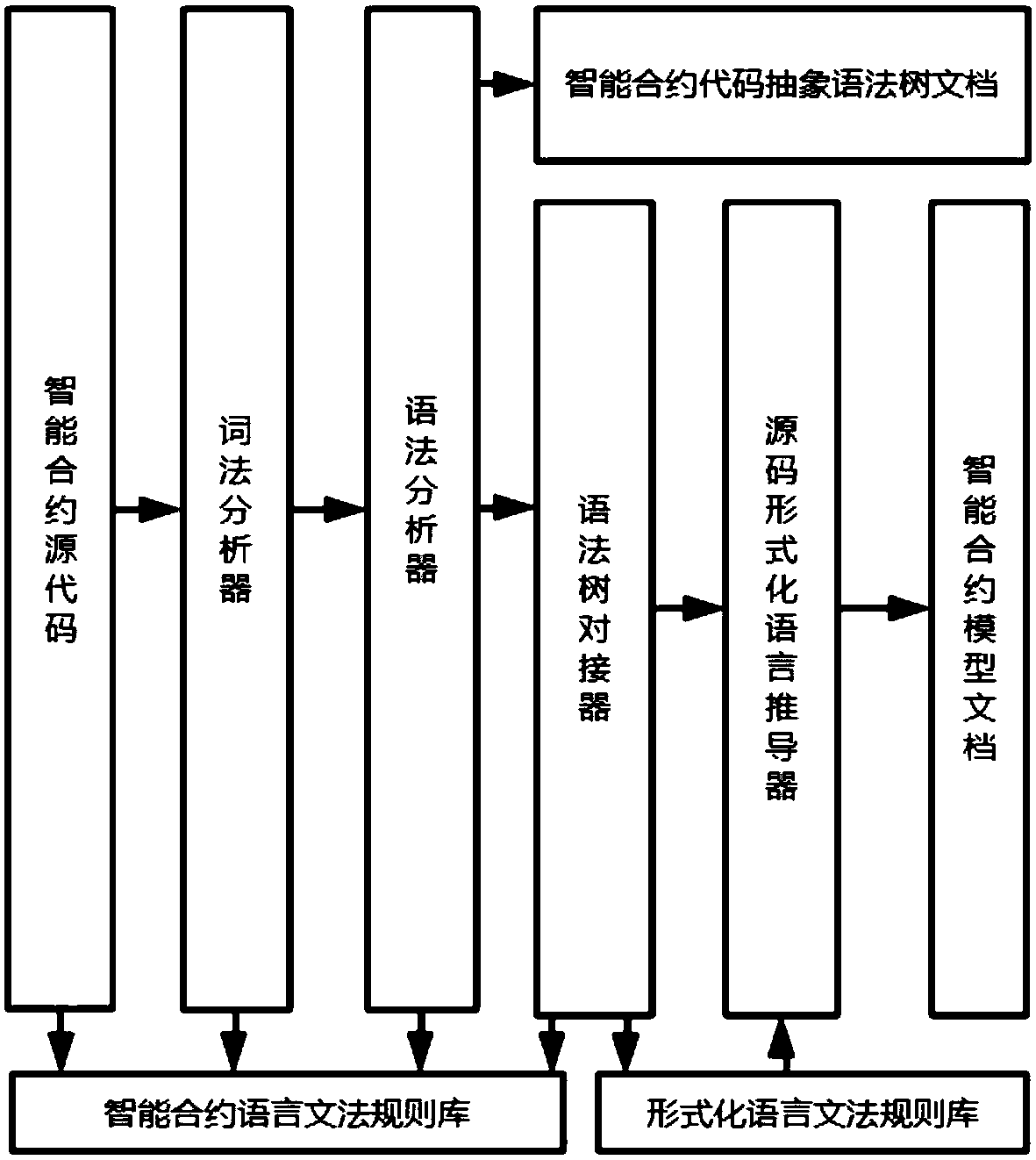
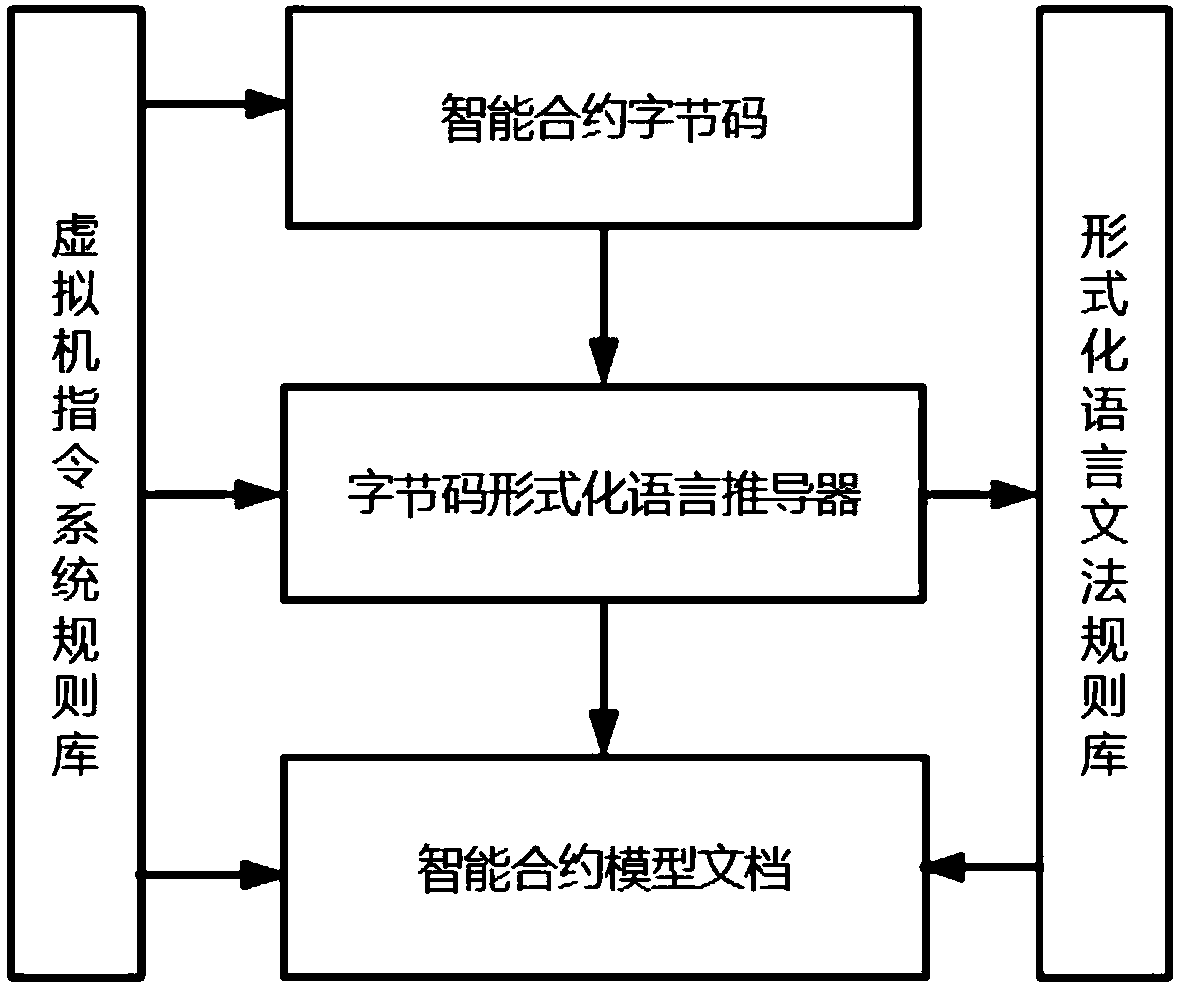
A highly automated intelligent contract formal verification system and method
ActiveCN108985073ASave time and costShorten the verification cycleFinancePlatform integrity maintainanceSpecification documentAutomaticity
The invention discloses a highly automated intelligent contract formal verification system and method. The method includes the following steps: step 001, converting an intelligent contract function requirement description document into an intelligent contract function requirement specification document described in a non-natural language, wherein the content of intelligent contract function requirement specification document includes target contract function specification description and security attribute description; step 002, creating a formal validation rule model library; step 003, automatically modeling the contract source code and / or bytecode by an automated modeling tool; step 004, parsing the abstract syntax tree generated in step 003, and allocating memory addresses for constantsand variables in the code; step 005, performing formal proof. The invention is adapted to program codes written in a plurality of high-level programming languages and also adapted to a plurality of formal languages, and simultaneously provides two automatic modeling modes of source code modeling and bytecode modeling, so that modeling can be carried out according to different modeling requirements of users, and the verification efficiency is further improved.
Owner:成都链安科技有限公司
Piggyback magneto-resistive read/write tape head with optimized process for same gap read/write
InactiveUS6038106AReduce spacingReduce verification timeConstruction of head windingsHeads using thin filmsResistElement space
A magneto-resistive read / write tape head is provided for reading and writing to tape media along a tape head face. The tape head comprises a plurality of modules, each module comprising a read element and a write element spaced apart and terminating at the tape head face and formed over a substrate. The read element comprises a soft film bias layer and a hard film bias layer butted against the SFB layer. The write element comprises two pole tips spaced apart by a gap. The tape head further includes a plurality of activating conducting coil turns operatively associated with the write element and covered by a cross-linked photoresist and positioned between the gap and one of the pole tips and set back from the tape head face. The tape head has at least one of the following elements: (a) a wear shield between the read element and the write element for limiting wear of the gap between the two pole tips, the wear shield being grounded for decoupling read and write functions of the tape head, for allowing same module read / servo / write functions simultaneously, and for grounding static charge from the tape media; (b) a layer of electrically conductive and corrosion-resis tant material, such as rhodium, under the hard film bias layer to reduce its resistance; and (c) a non-activating dummy coil turn closer to the pole tips than the activating coil turns for defining a forward termination of the cross-linked photoresist between the activating coil turns and the tape head face to thereby provide improved ease of processability.
Owner:IBM CORP
Biometric authentication method and biometric authentication apparatus
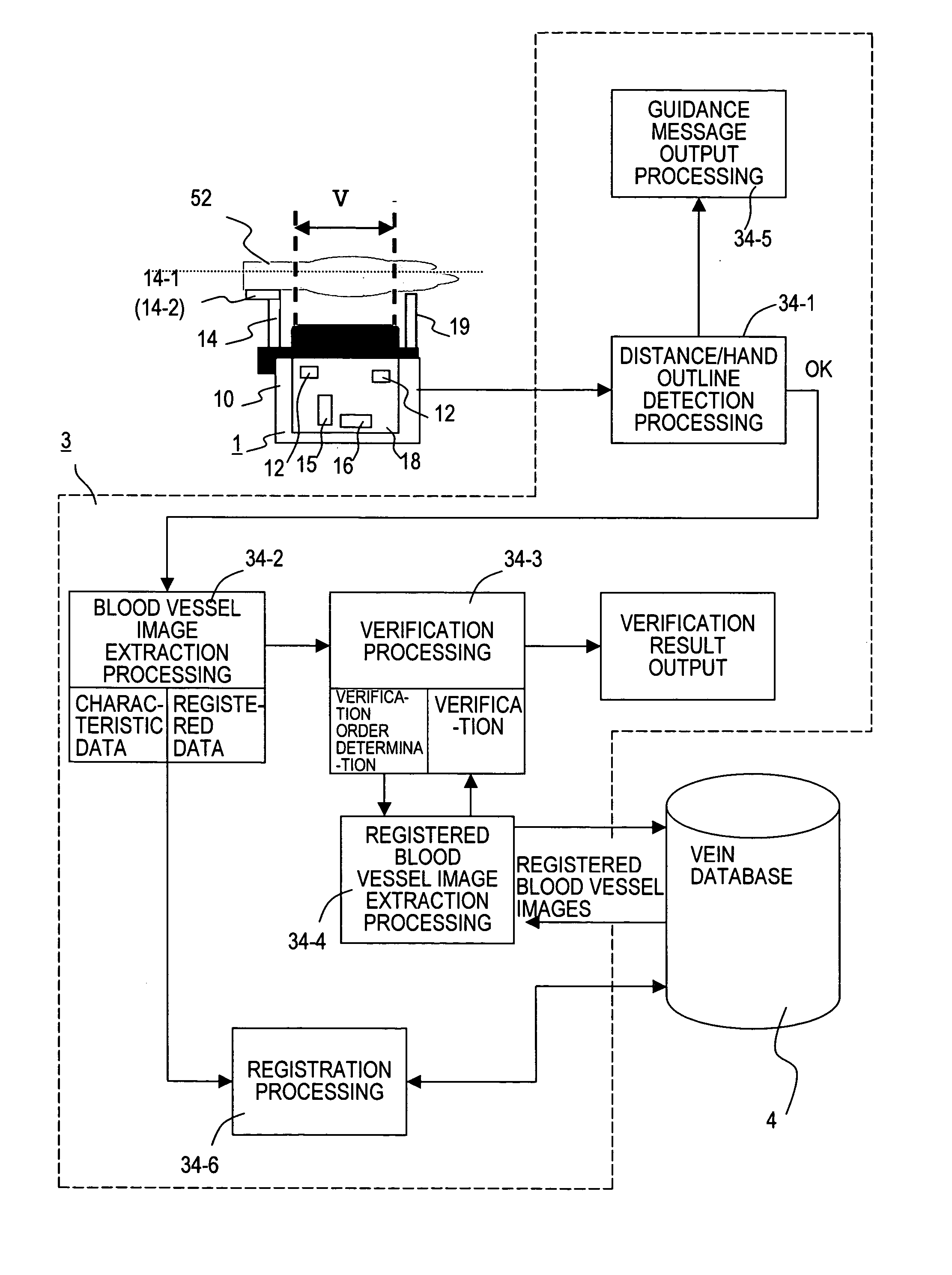
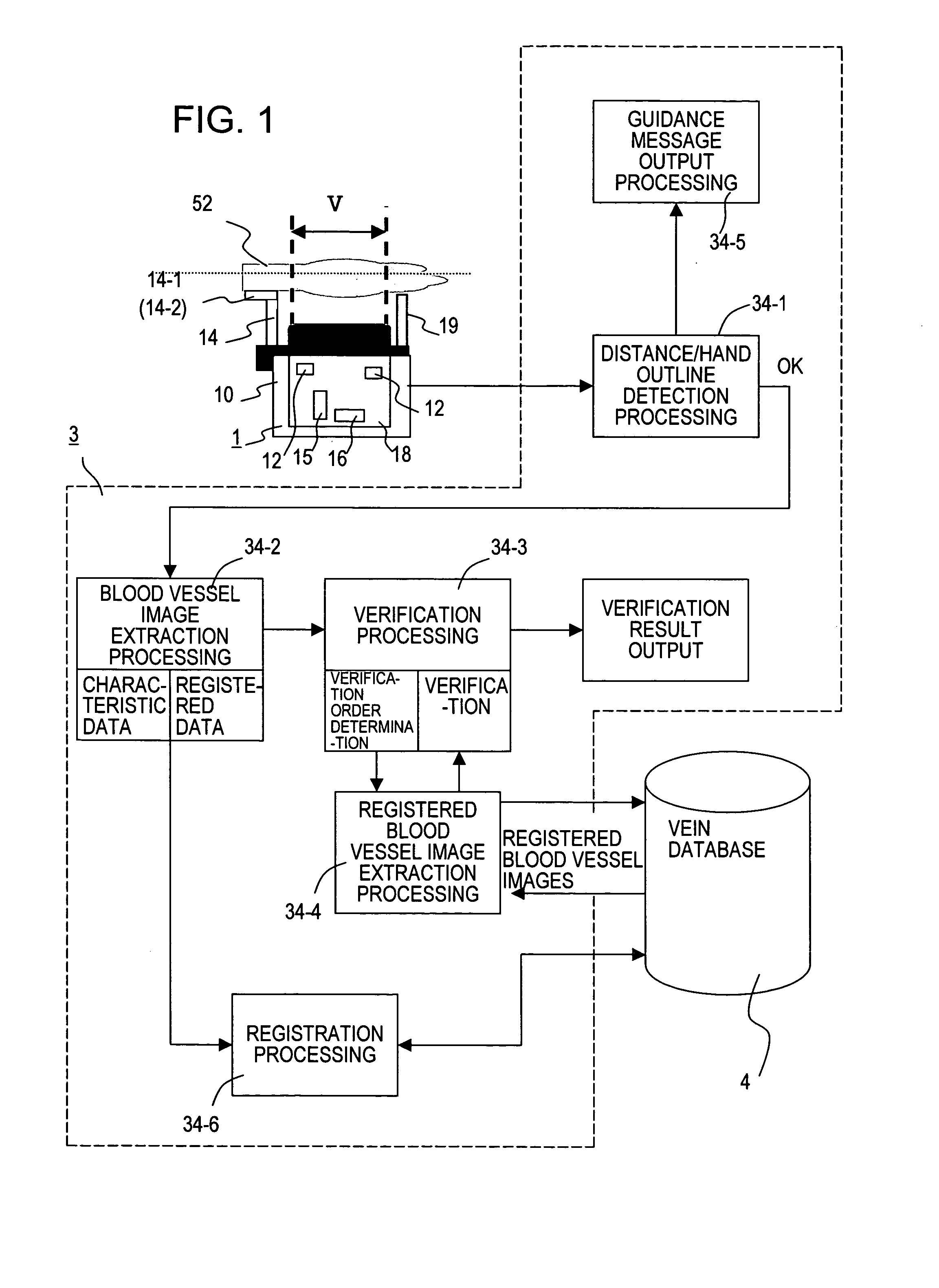
ActiveUS20070217660A1Reduce verification timeIncrease speedImage analysisPerson identificationPattern recognitionData set
A biometric authentication device, which uses biometrics characteristic information to perform individual authentication, prevents declines in verification speed even when numerous biometrics information sets have been registered. A control unit registers broad characteristic quantities for blood vessel image data from an image capture device, together with characteristic data for verification. And at the time of authentication the control unit uses degrees of similarity of characteristic quantities to determine an order of verification, and performs verification of blood vessel image characteristic data in the verification order thus determined. The order of verification is determined based on captured blood vessel images, so that even when numerous characteristic data sets have been registered, verification can be performed in an order of verification based on a blood vessel image of the user, and the speed of verification can be improved.
Owner:FUJITSU FRONTECH LTD
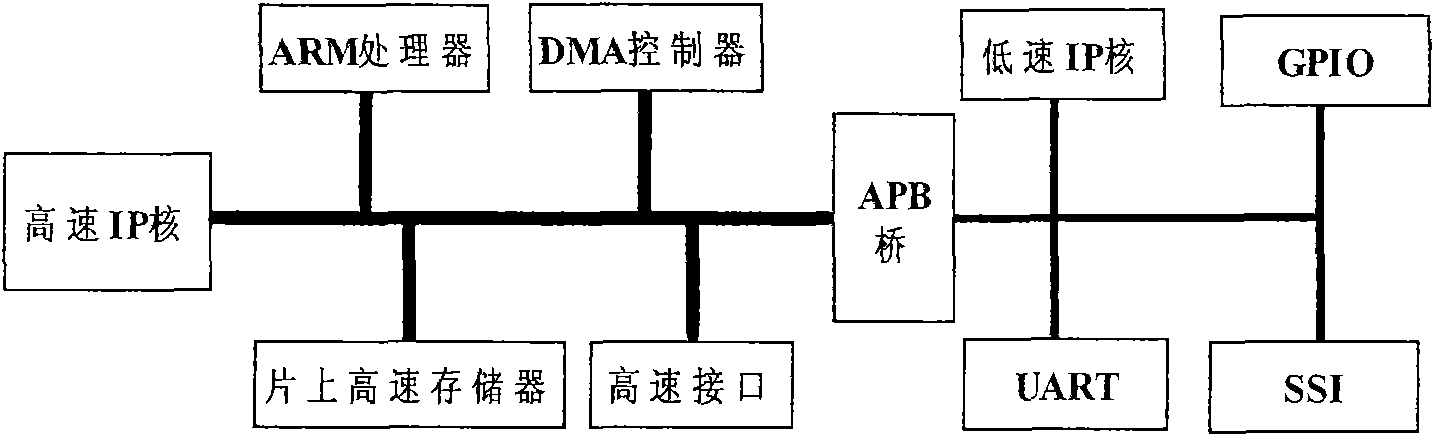
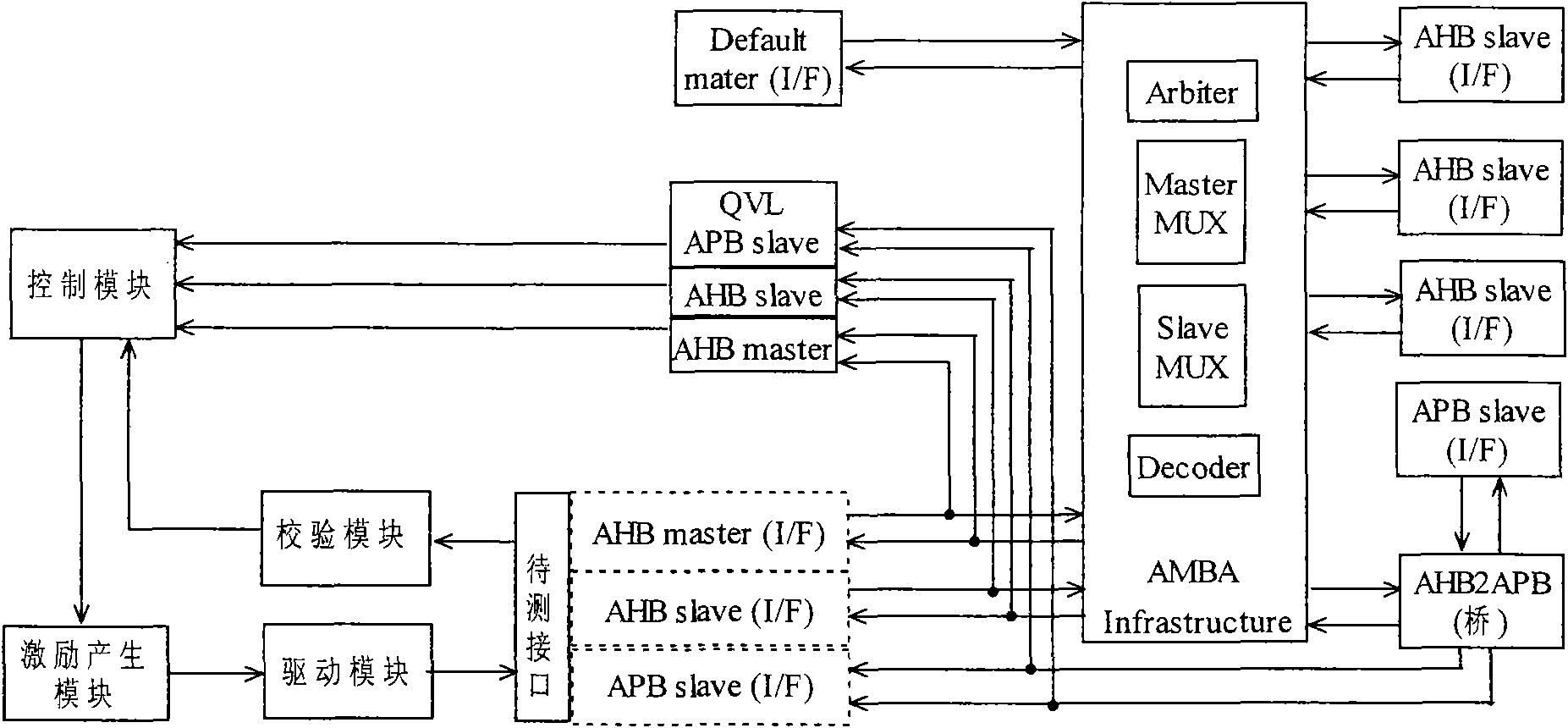
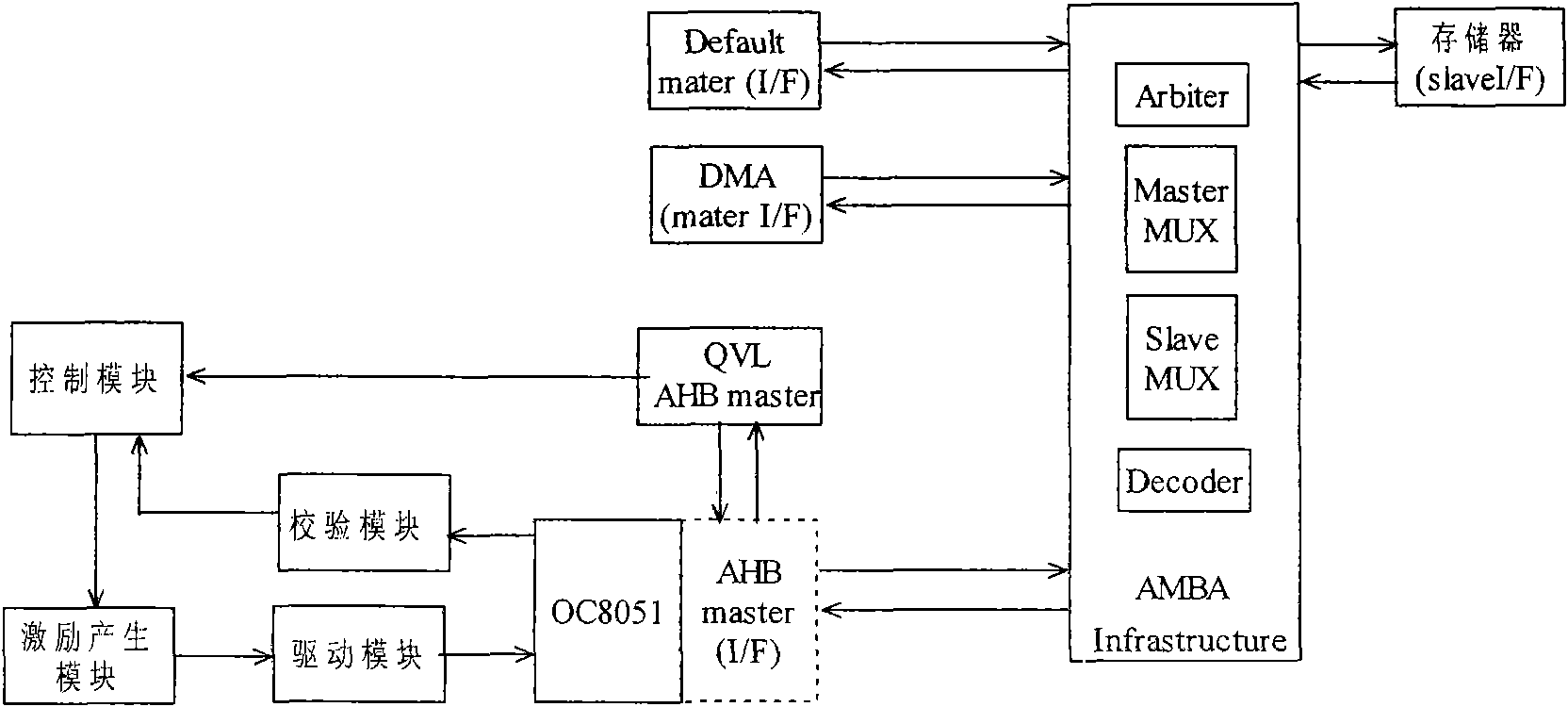
Universal method and platform for verifying compatibility between intellectual property (IP) core and advanced microcontroller bus architecture (AMBA) bus interface
InactiveCN102117238AImprove verification efficiencyImprove accuracyFunctional testingValidation methodsIntellectual property
The invention provides a universal platform of verifying compatibility between an intellectual property (IP) core and an advanced microcontroller bus architecture (AMBA) bus interface, which comprises a functional simulation tool, an AMBA bus infrastructure, a third-party verification IP core, a controller, a driver, a stimulus, a checker, an advanced peripheral bus (APB) bridge, an advanced high-performance bus (AHB) master interface, an AHB slave interface and an APB slave interface, wherein all the modules are connected to form an integrated coordinating verification environment by adopting a verification component and hierarchical packaging and interconnections ways provided by a SystemVerilog language and advanced verification methodology (AVM). The platform can verify the compatibility of different types of IP core interfaces, and the development time and cost of the verification platform and a verification method are reduced. The invention also provides the universal method for verifying the compatibility between the IP core and the AMBA bus interface. In the method, excitation is produced more normatively, scientifically and accurately, unnecessary iteration is reduced and the verification time is shortened.
Owner:SHANGHAI SILICON INTPROP EXCHANGE
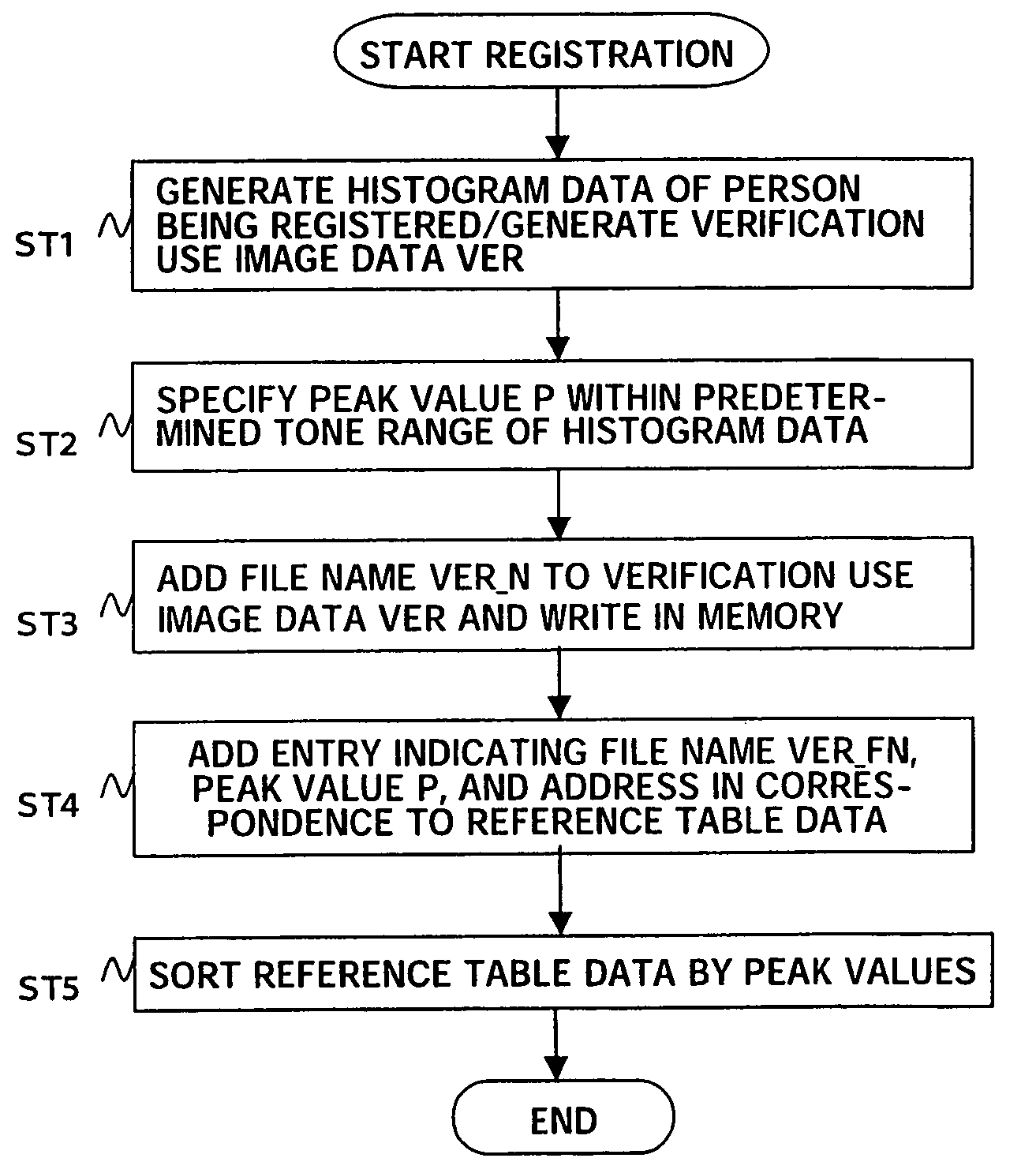
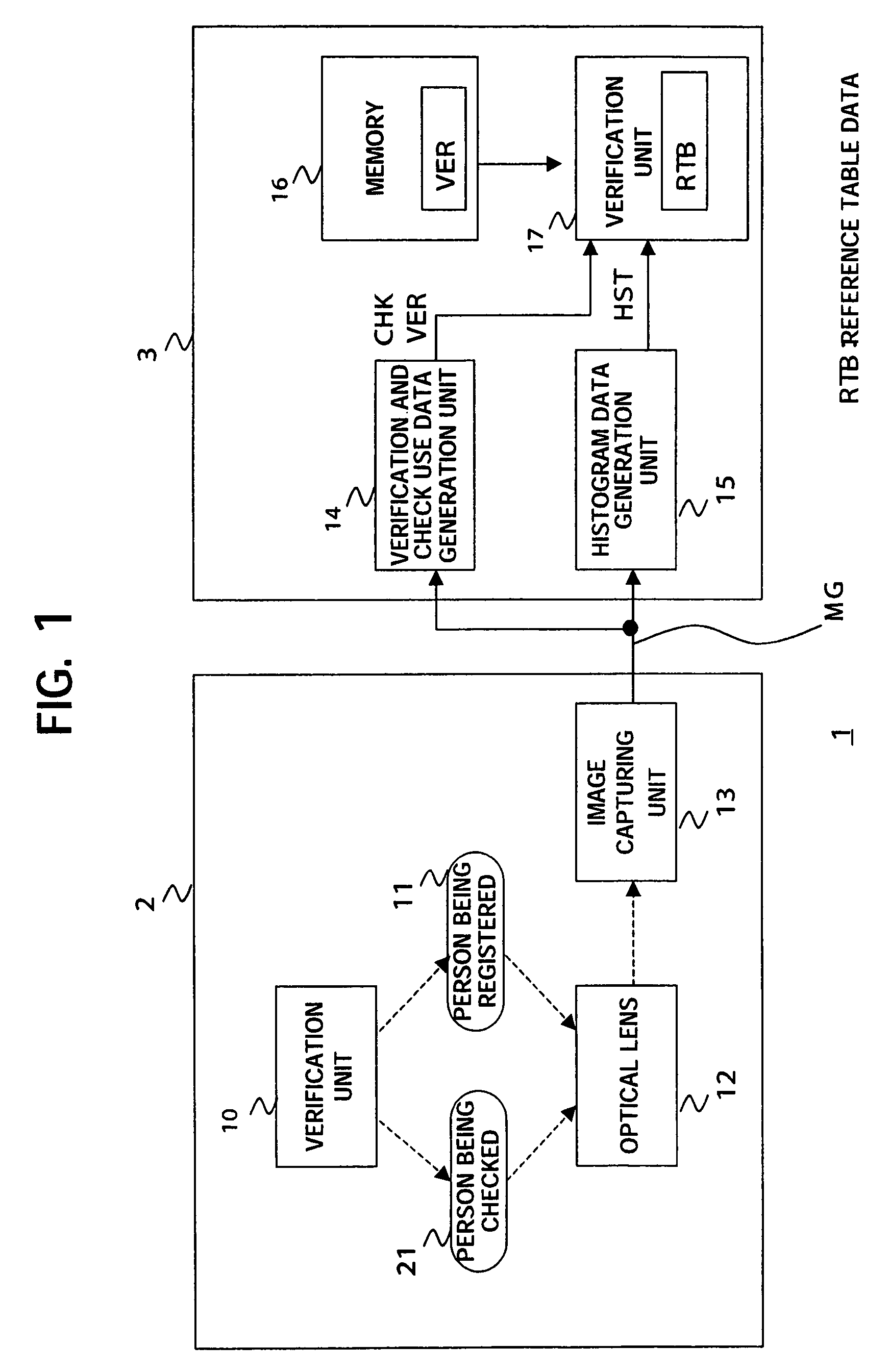
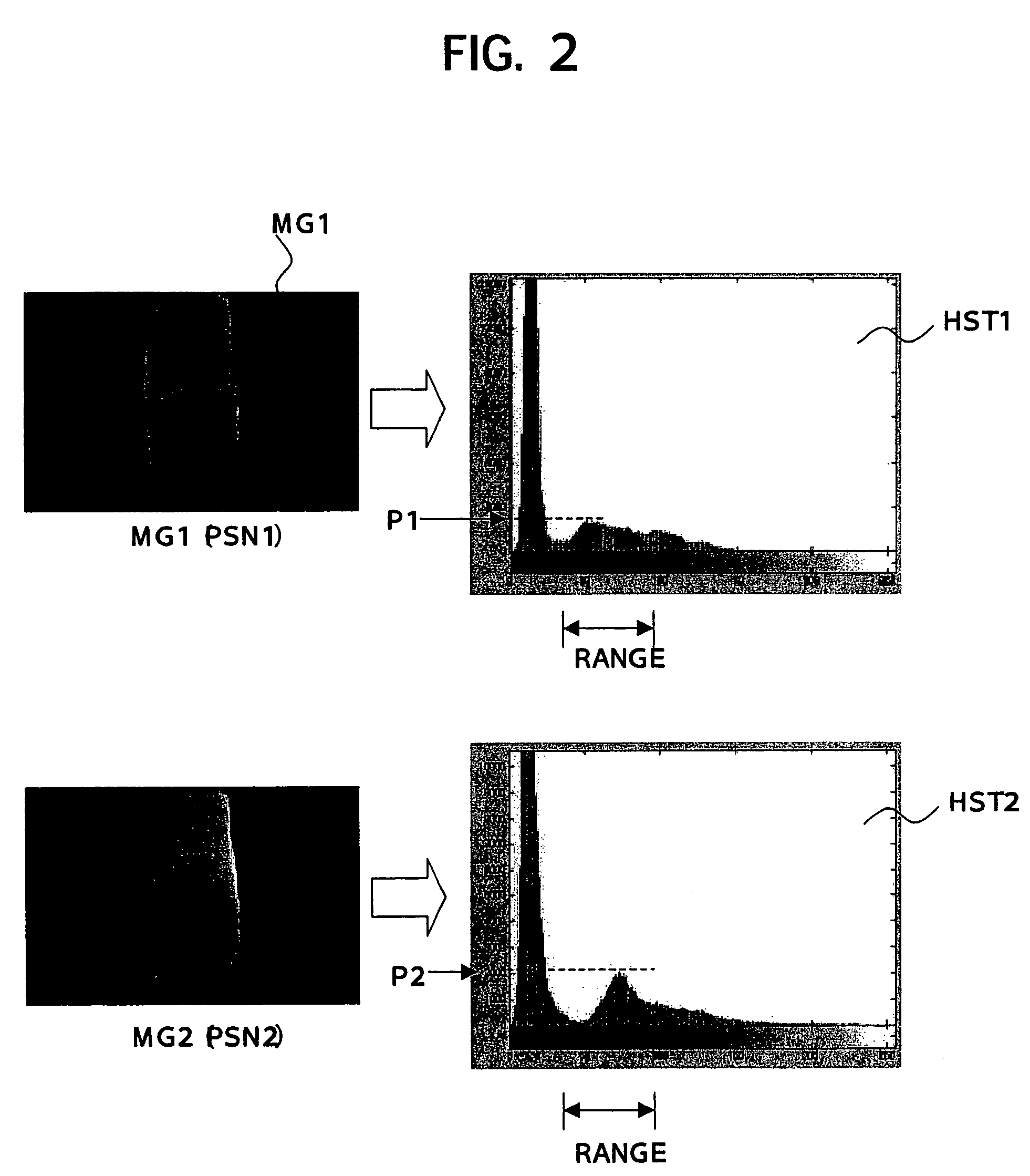
Image processing apparatus and image processing method
An image processing apparatus and an image processing method are provided. The image processing apparatus can shorten the verification time when using a plurality of verification use image data stored in a memory for verification, identifically a verification apparatus which generates histogram data by a histogram data generation unit based on image captured data of a person being checked, specifies a peak value of the number of the pixel data in the histogram data by a verification unit, and reads out verification use image data stored in the memory linked with the peak value closest to the specified peak value for the verification, and a method of the same. Verification use image data stored in the memory is stored based on the peak values.
Owner:SONY CORP
Semi-physical simulation testing table of network control system of high-speed motor train unit train
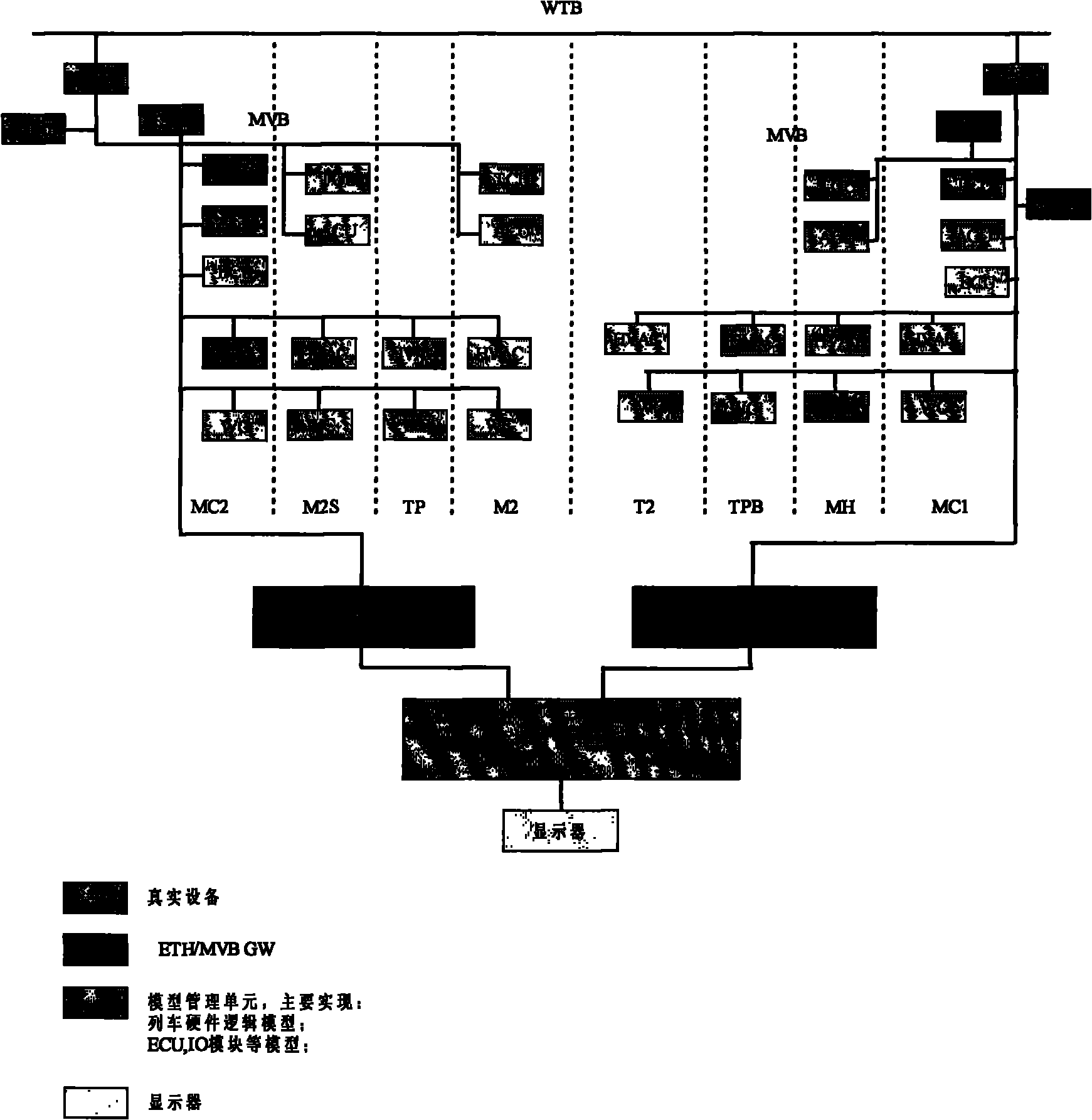
InactiveCN102156052AShorten the development cycleReduce R&D costsRailway vehicle testingManagement systemSimulation testing
The invention relates to a semi-physical simulation testing table of a network control system of a high-speed motor train unit train. The semi-physical simulation testing table comprises a model management unit, a real device and a model unit, wherein the real device and the model unit communicate with the model management unit. The semi-physical simulation testing table has the following obvious advantages in train control algorithm and control logic verification and optimization: lowering the research and development cost: by the establishment of the semi-physical simulation testing table of a high-speed trainset control and management system (TCMS), the research and development period is shortened, the research and development cost is lowered; shortening the development and manufacturing period: the establishment of the semi-physical simulation testing table of the high-speed TCMS contributes to the shortening of the debugging time on the train.
Owner:CRRC QINGDAO SIFANG ROLLING STOCK RES INST
Biometric information authentication device, biometric information authentication method, and computer-readable recording medium with biometric information authentication program recorded thereon
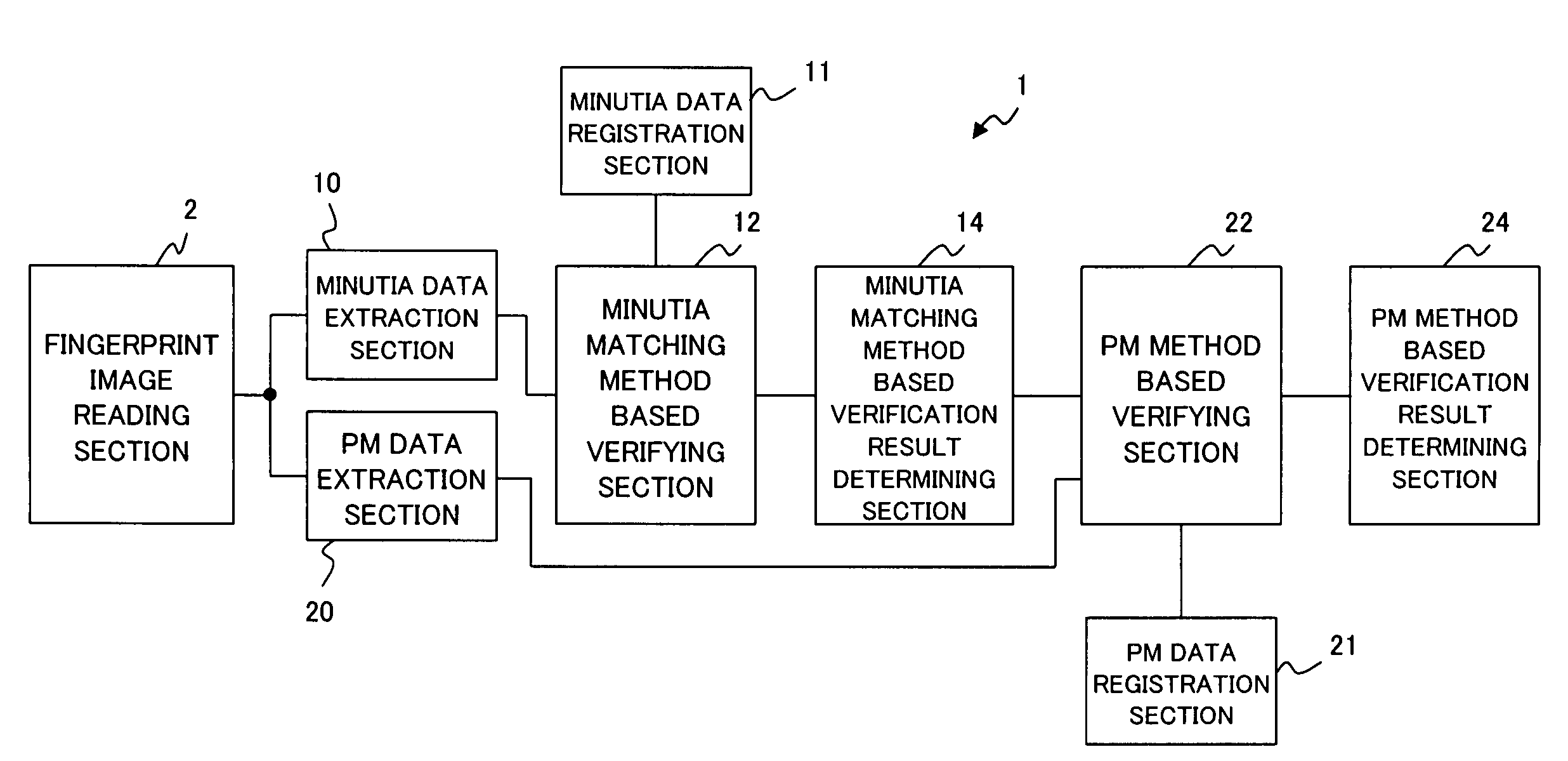
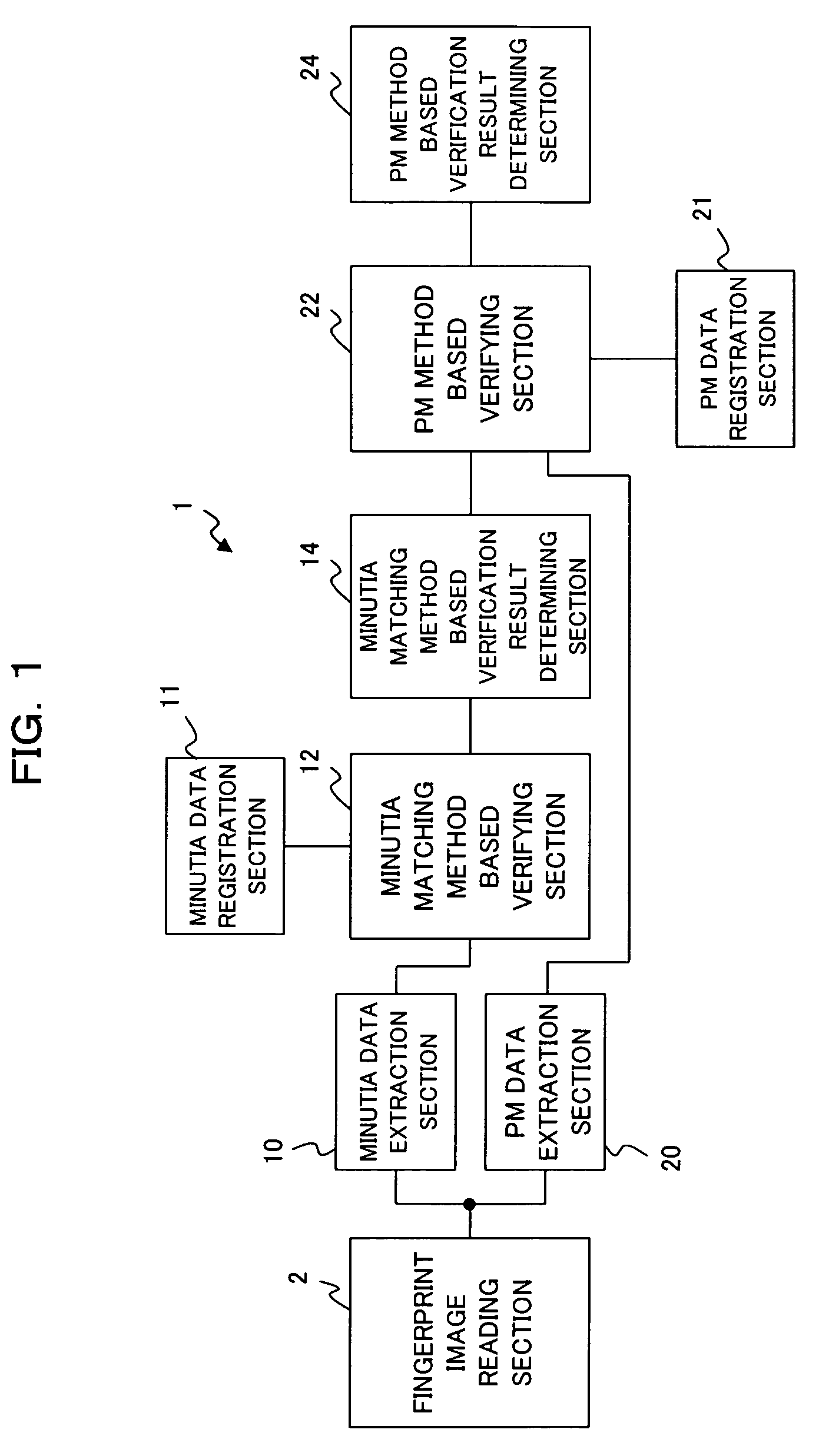
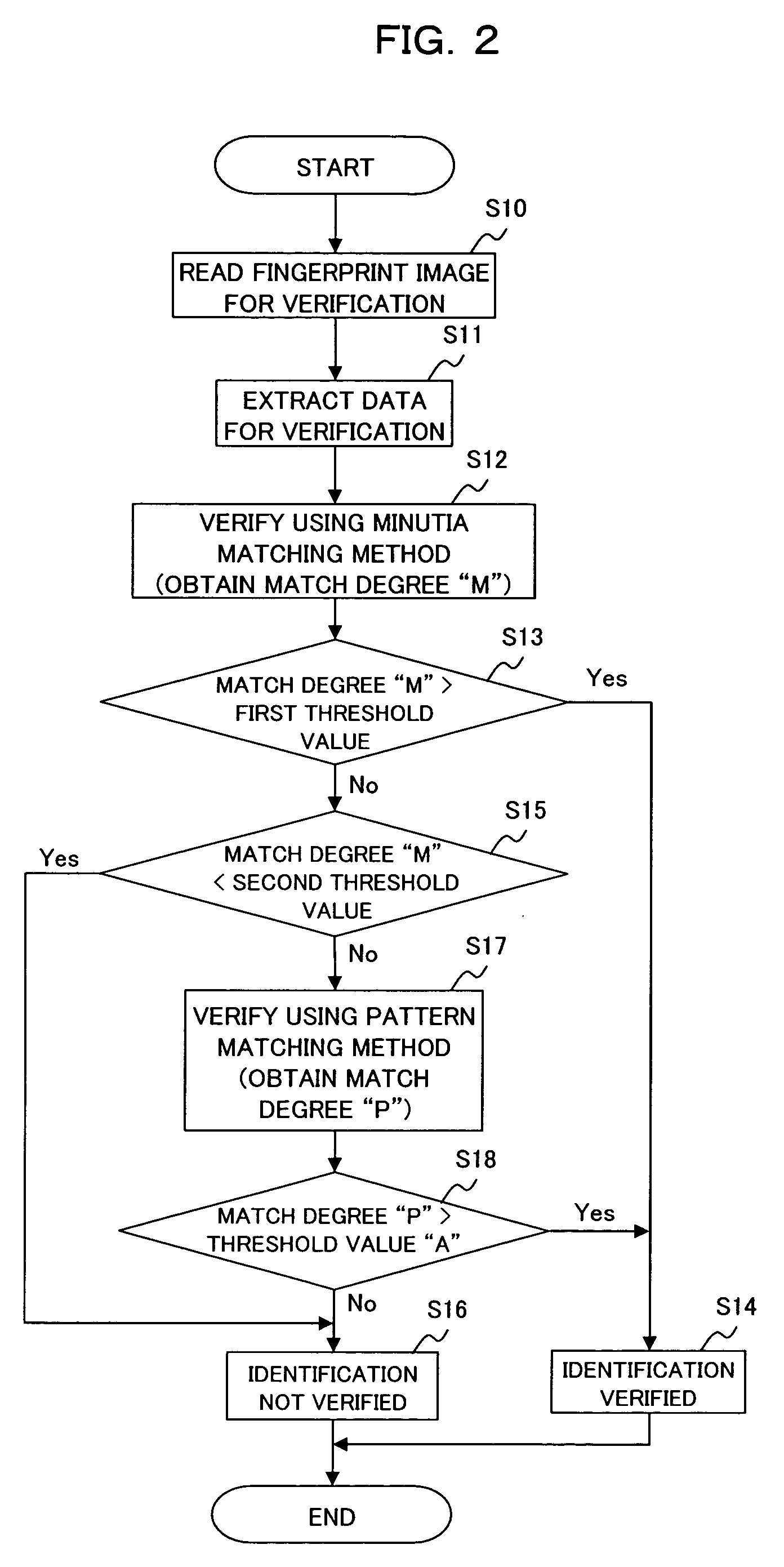
ActiveUS7526110B2Extension of timeReduce verification timeElectric signal transmission systemsImage analysisData validationPattern matching
For personal authentication using biometric information, to allow for unfailing authentication without increasing verification time even for an authentication object that is not supported only by a minutia matching method, the present invention provides a biometric information authentication device comprising: a first verifying section for verifying first to-be-verified data against first registration data registered preliminarily using a minutia matching method; a second verifying section for verifying second to-be-verified data against second registration data registered preliminarily using a pattern matching method; and a determining section for comparing match degree, which is obtained as a result of verification by the first verifying section, with a first threshold value and a second threshold value to allow the second verifying section to perform verification in the case where the match degree is equal to or smaller than the first threshold value and equal to or larger than the second threshold value.
Owner:FUJITSU LTD
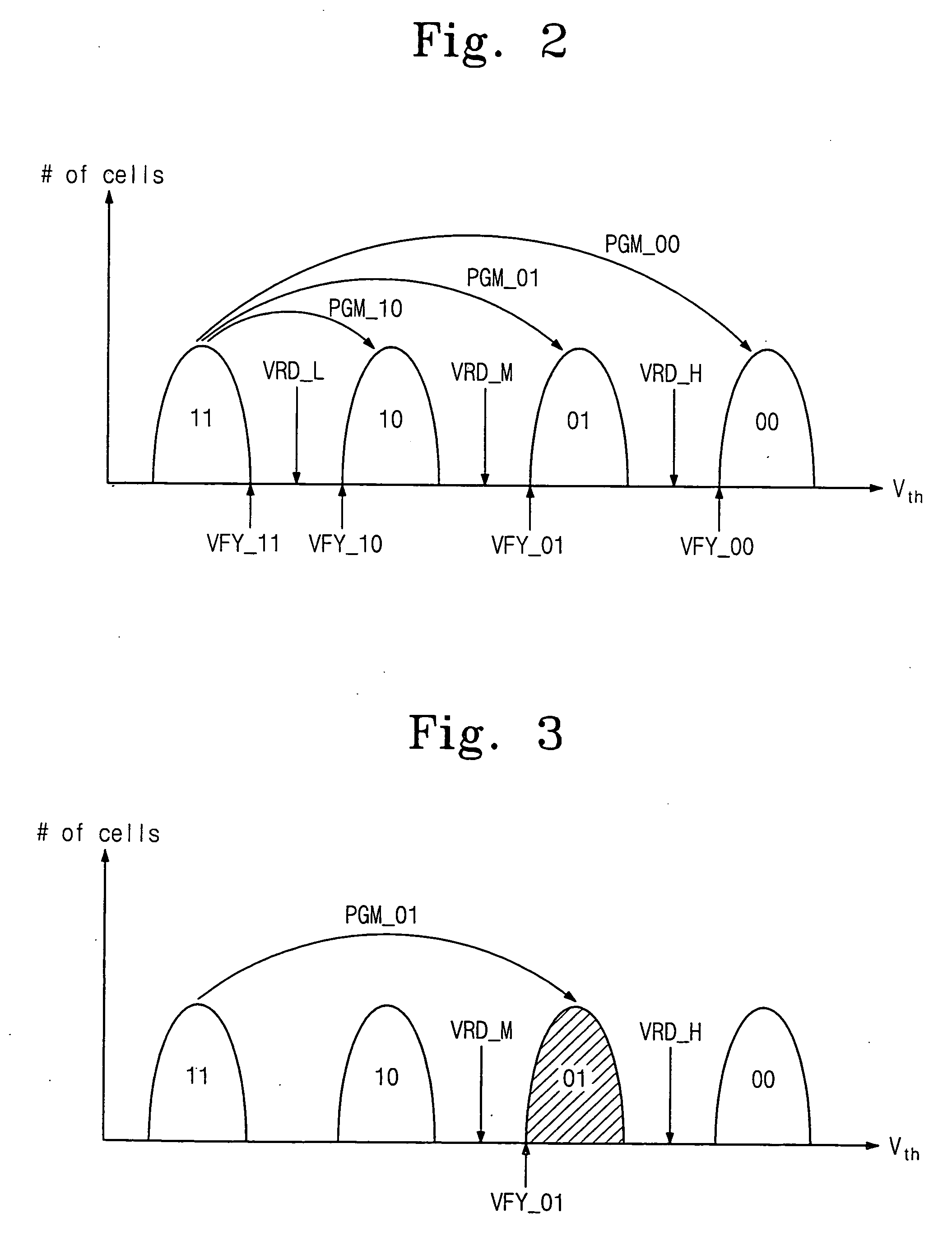
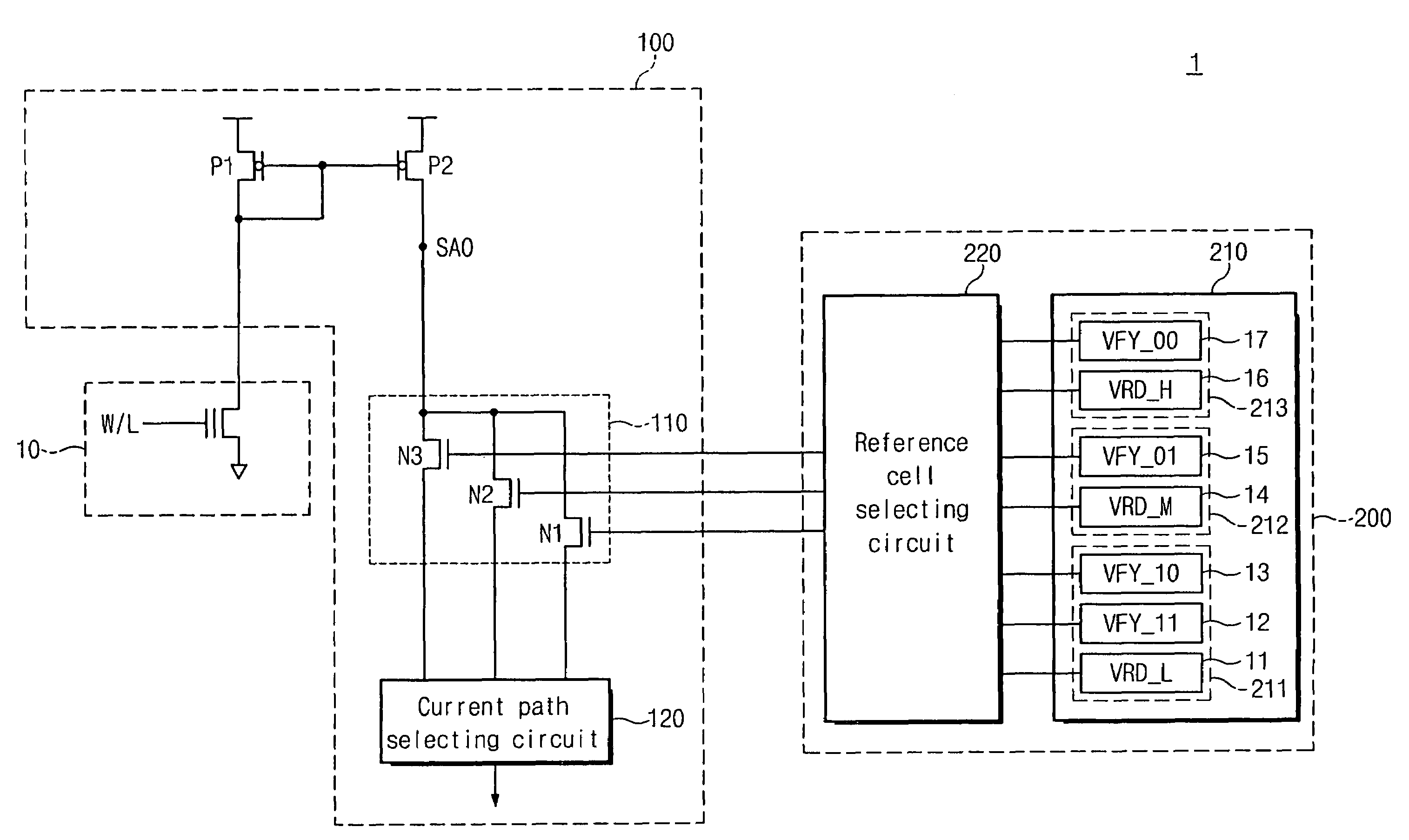
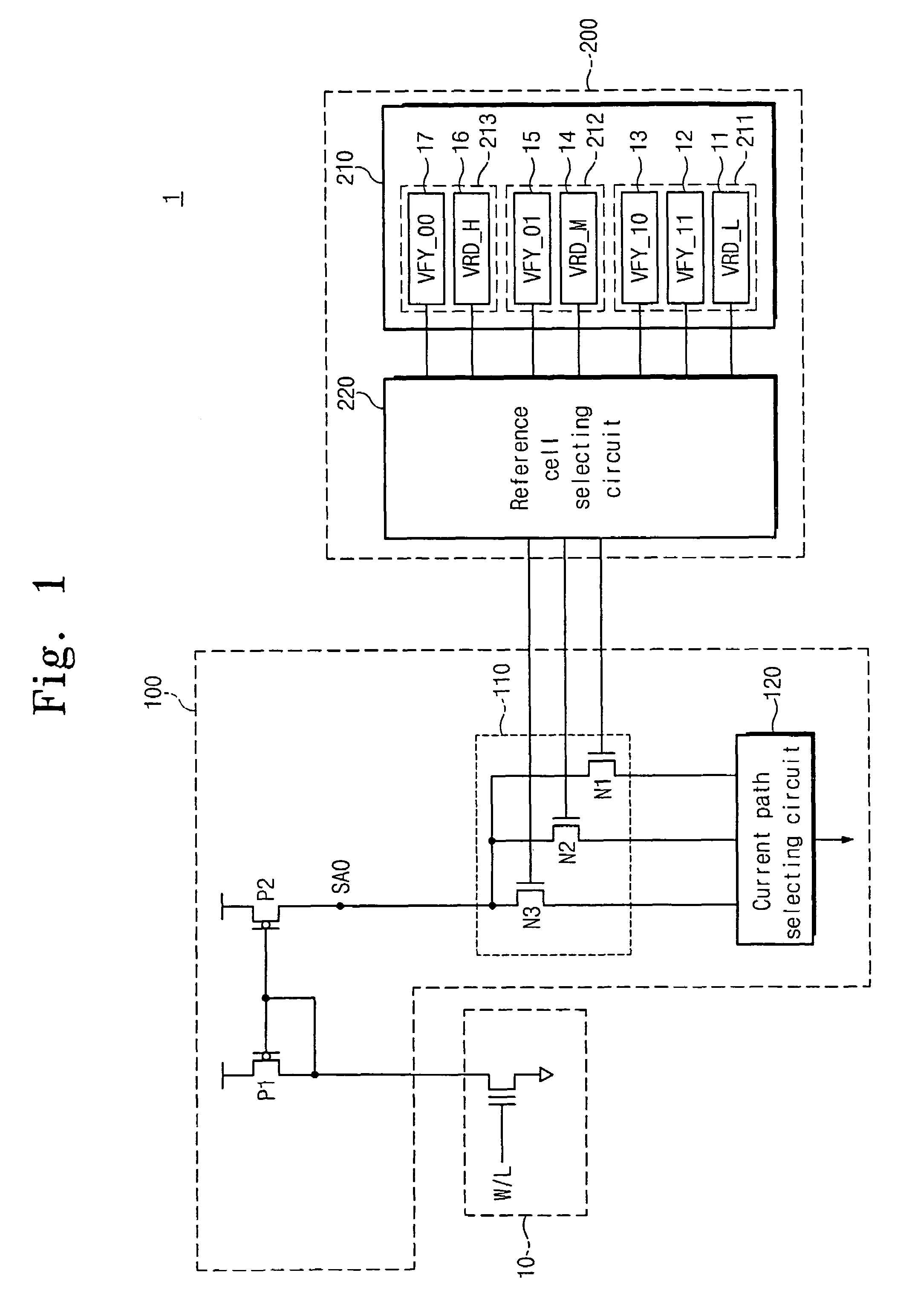
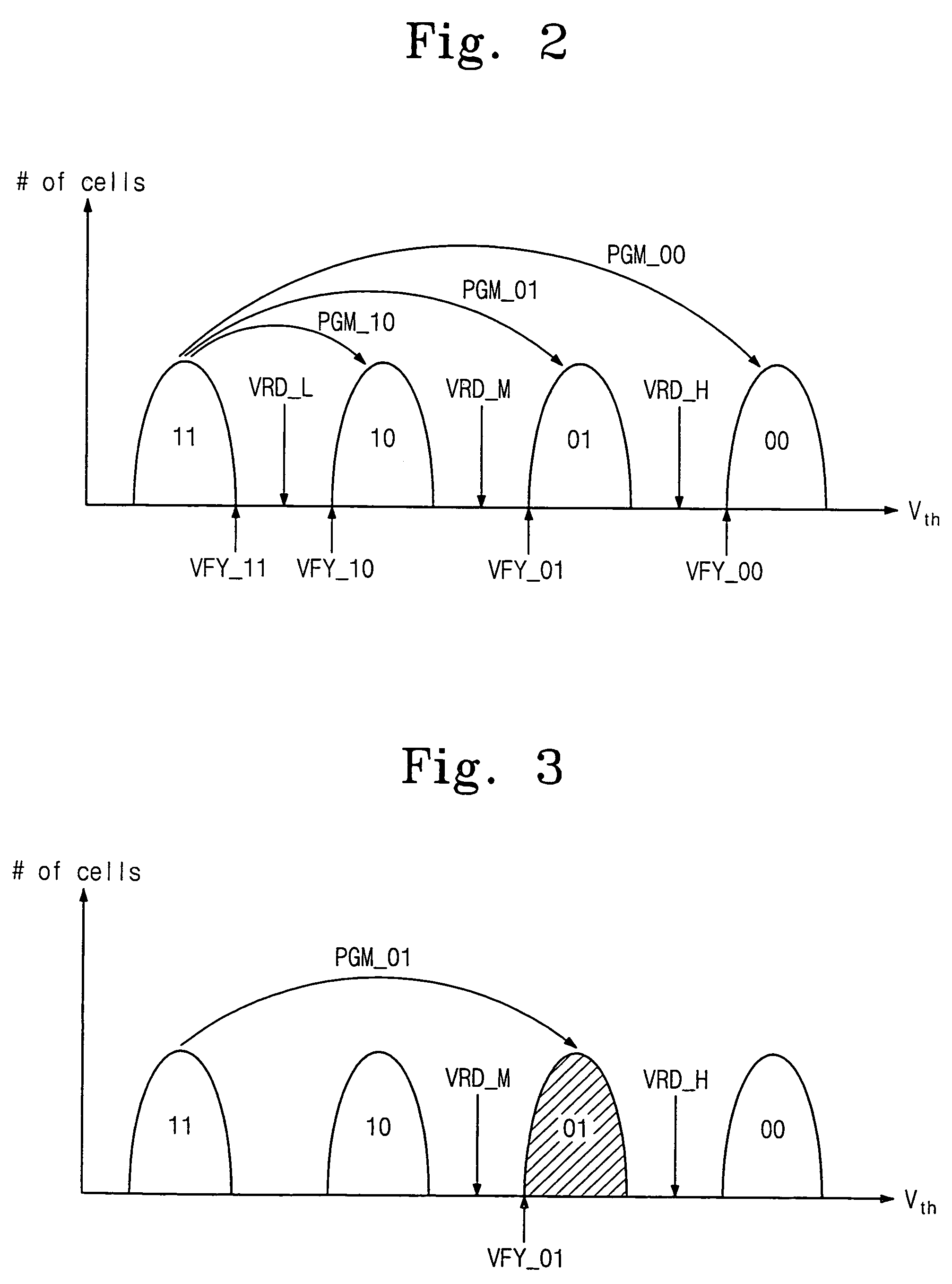
Methods of program verifying non-volatile memory devices
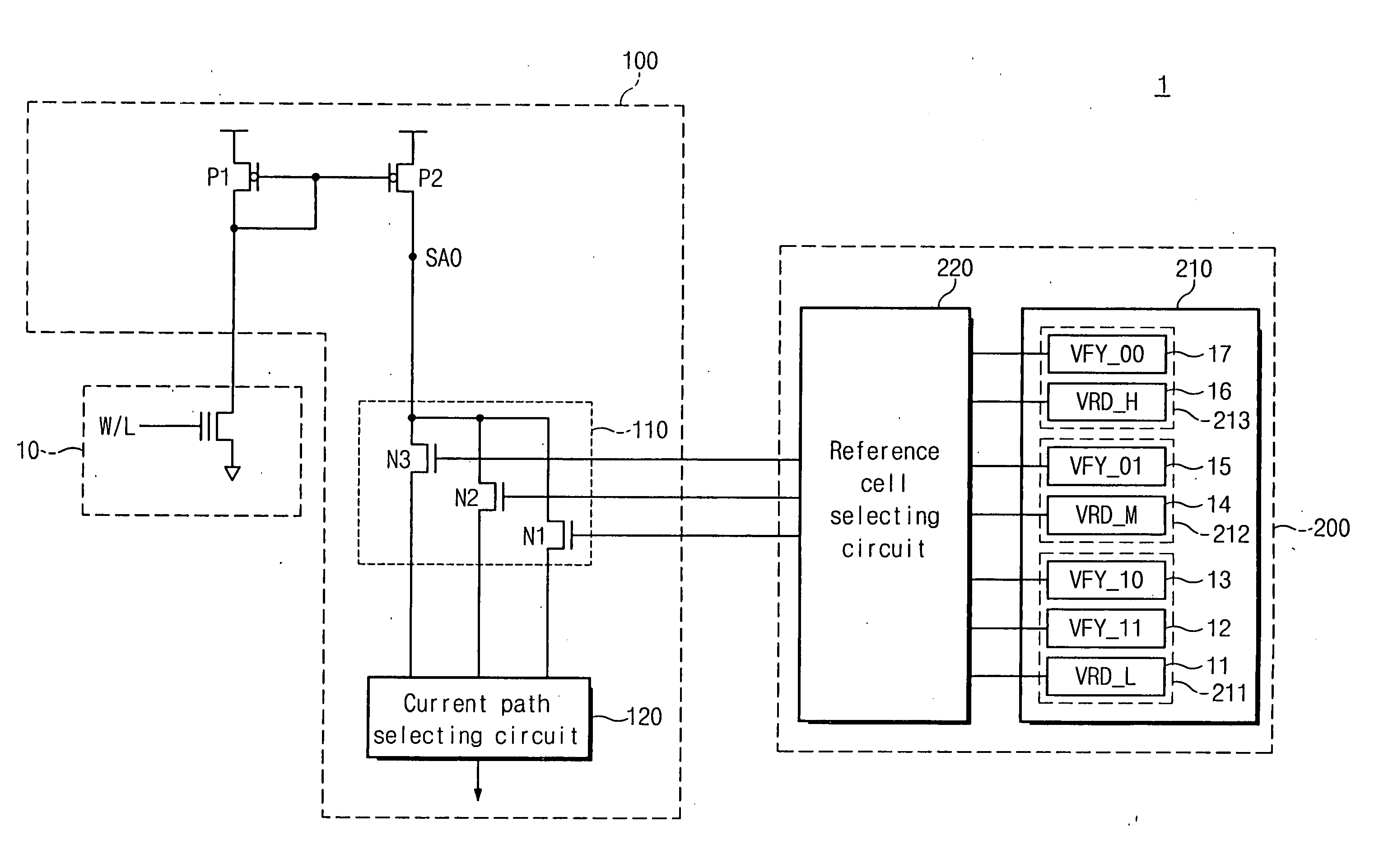
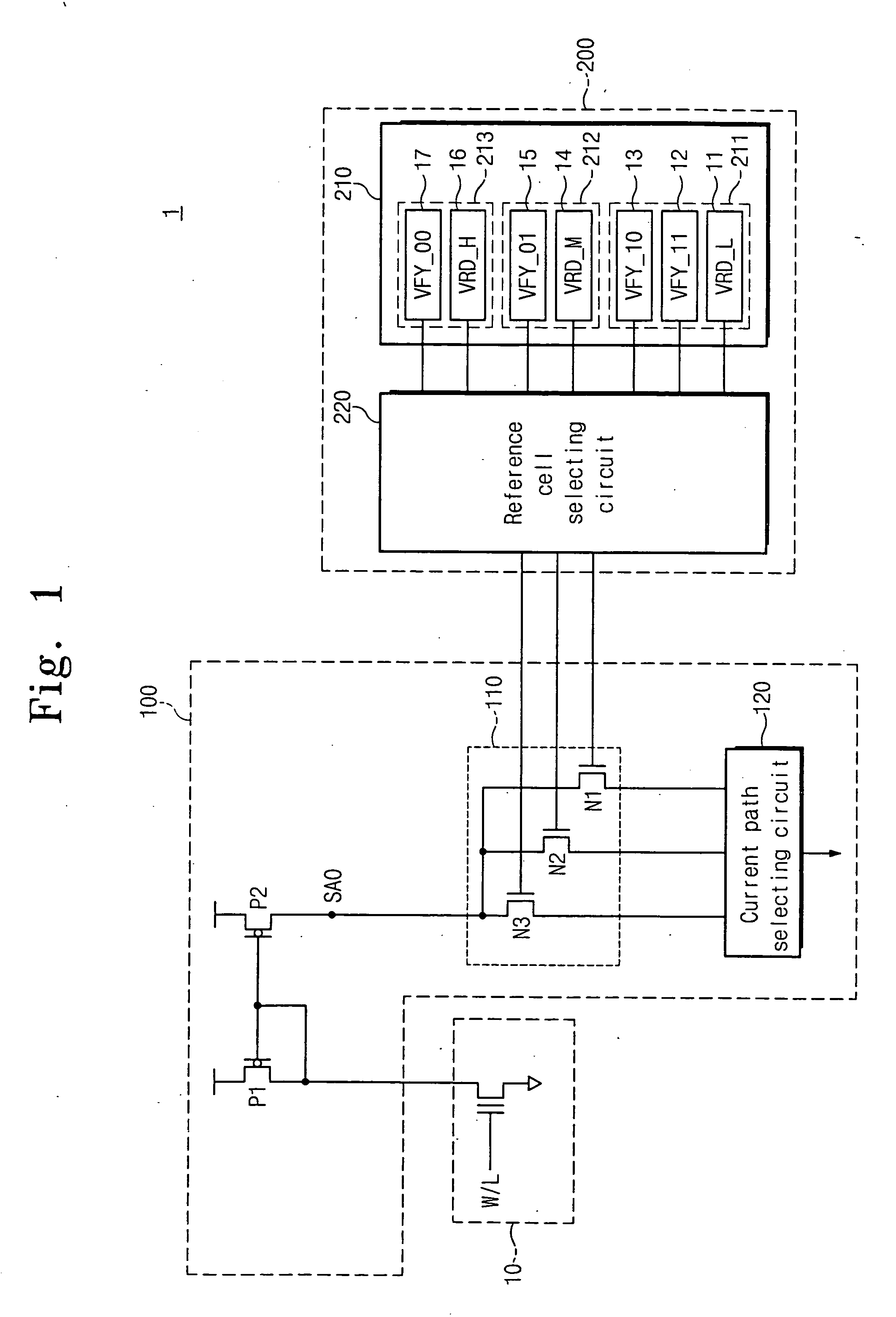
InactiveUS20060126391A1Reduce timeEasy to readRead-only memoriesDigital storageNon-volatile memoryReference memory
Methods of verifying a program state may be provided for a non-volatile memory device including a multi-bit memory cell transistor providing more than two different program states. More particularly, the multi-bit memory cell transistor may be programmed from a first program state to a second program state, and a reference memory cell corresponding to the second program state may be selected. After programming the multi-bit memory cell transistor to the second program state and after selecting the reference memory cell corresponding to the second program state, a current flowing through the multi-bit memory cell transistor programmed to the second memory state and a current flowing through the reference memory cell may be compared. Programming the multi-bit memory cell transistor to the second program state may then be verified responsive to comparing the currents flowing through the multi-bit memory cell and the reference memory cell.
Owner:SAMSUNG ELECTRONICS CO LTD
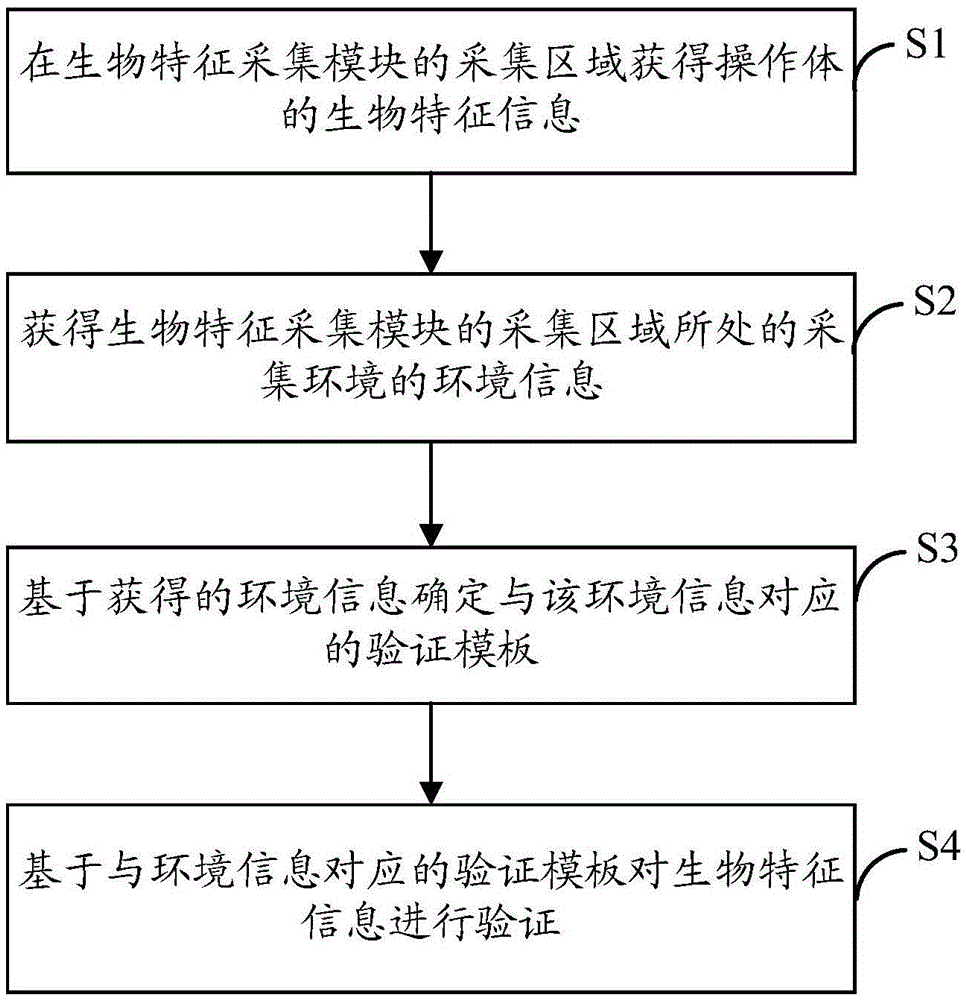
Bio-feature verification method and electronic device
ActiveCN105653922AImprove user experienceImprove effectivenessDigital data authenticationInformation acquisitionComputer engineering
The invention provides a bio-feature verification method and an electronic device. By utilizing environment information of an acquisition environment during bio-feature information acquisition, a proper verification template is selected for verifying the acquired bio-feature information so as to improve the effectiveness of verification processing. The bio-feature verification method comprises the steps of obtaining the bio-feature information of an operation body in an acquisition region of a bio-feature acquisition module; obtaining the environment information of the acquisition environment in which the acquisition region of the bio-feature acquisition module is located; based on the environment information, determining a verification template corresponding to the environment information; and based on the verification template corresponding to the environment information, verifying the bio-feature information.
Owner:LENOVO (BEIJING) CO LTD
Methods of program-verifying a multi-bit nonvolatile memory device and circuit thereof
InactiveUS7327609B2Easy to readReduce verification timeRead-only memoriesDigital storageComputer architectureHemt circuits
Methods of verifying a program state may be provided for a non-volatile memory device including a multi-bit memory cell transistor providing more than two different program states. More particularly, the multi-bit memory cell transistor may be programmed from a first program state to a second program state, and a reference memory cell corresponding to the second program state may be selected. After programming the multi-bit memory cell transistor to the second program state and after selecting the reference memory cell corresponding to the second program state, a current flowing through the multi-bit memory cell transistor programmed to the second memory state and a current flowing through the reference memory cell may be compared. Programming the multi-bit memory cell transistor to the second program state may then be verified responsive to comparing the currents flowing through the multi-bit memory cell and the reference memory cell.
Owner:SAMSUNG ELECTRONICS CO LTD
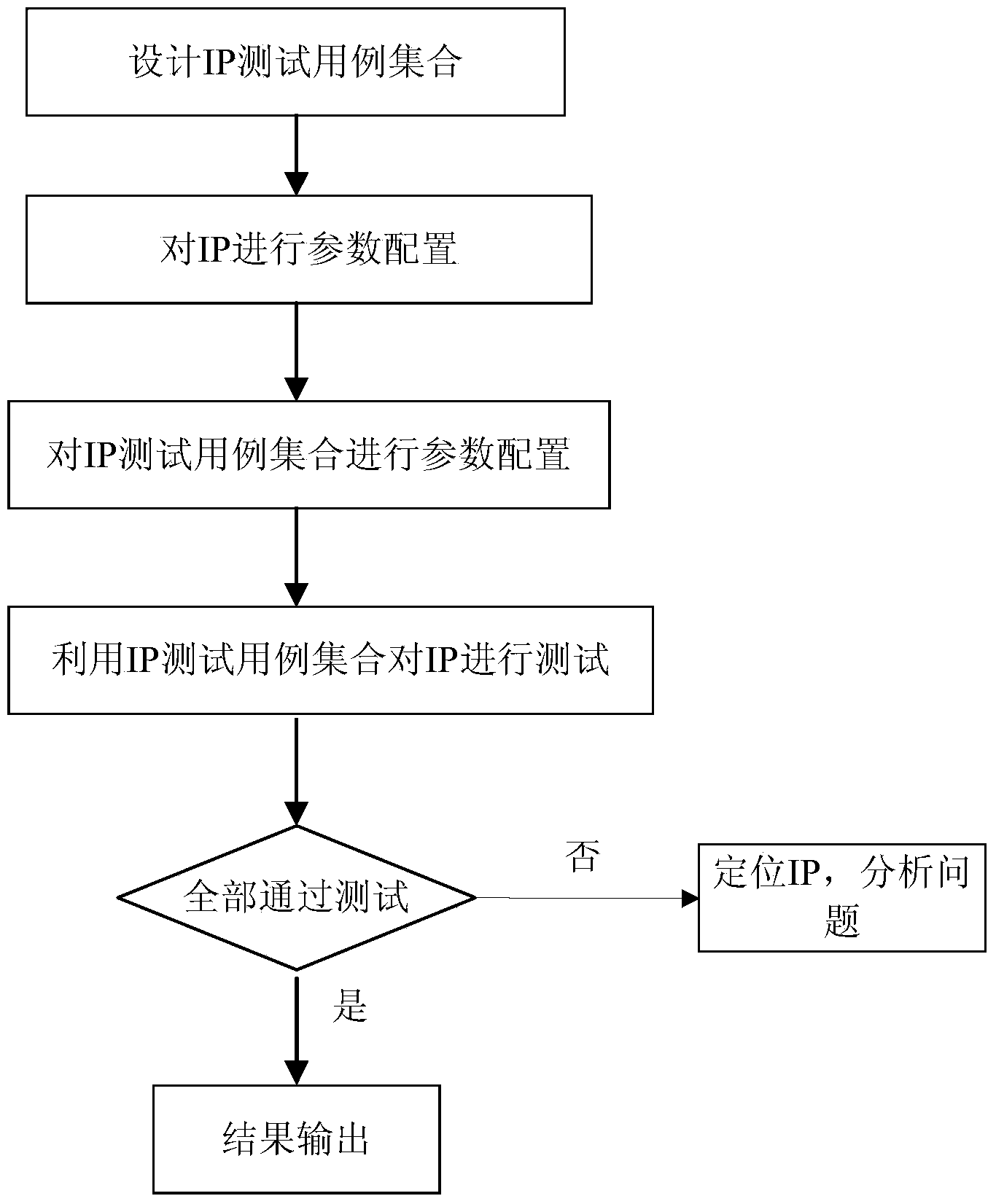
Automatic chip validation method based on parameterized IP test case set
ActiveCN104268078AFully automatedImprove verification efficiencySoftware testing/debuggingProgramming languageTest stimulus
The invention discloses an automatic chip validation method based on a parameterized IP test case set. The automatic chip validation method is achieved by adding test stimulus of IP test cases to the traditional validation method. The automatic chip validation method includes the following steps: designing the test case set of each IP constituting a chip; setting the parameter of each IP constituting the chip; setting the corresponding test case set according to the parameter definition of each IP during design; testing each IP in the chip on the basis of the set test case set to verify the correctness of the design. The automatic chip validation method can be achieved simply, greatly reduces expenses for re-writing of the test cases for the same IP, and improves the IP-based chip validation efficiency.
Owner:BEIJING INST OF CONTROL ENG
Apparatus, system and method for person verification
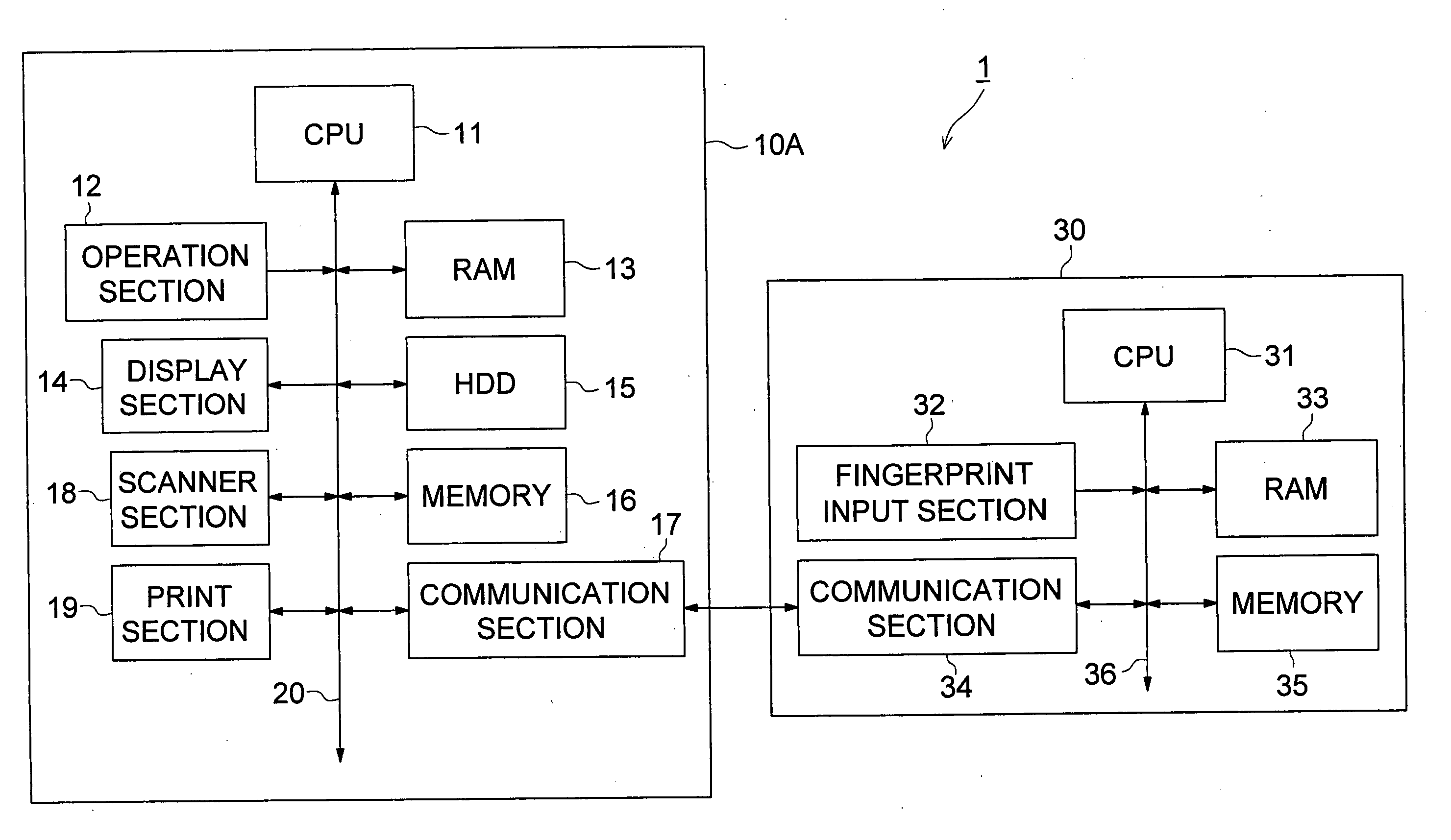
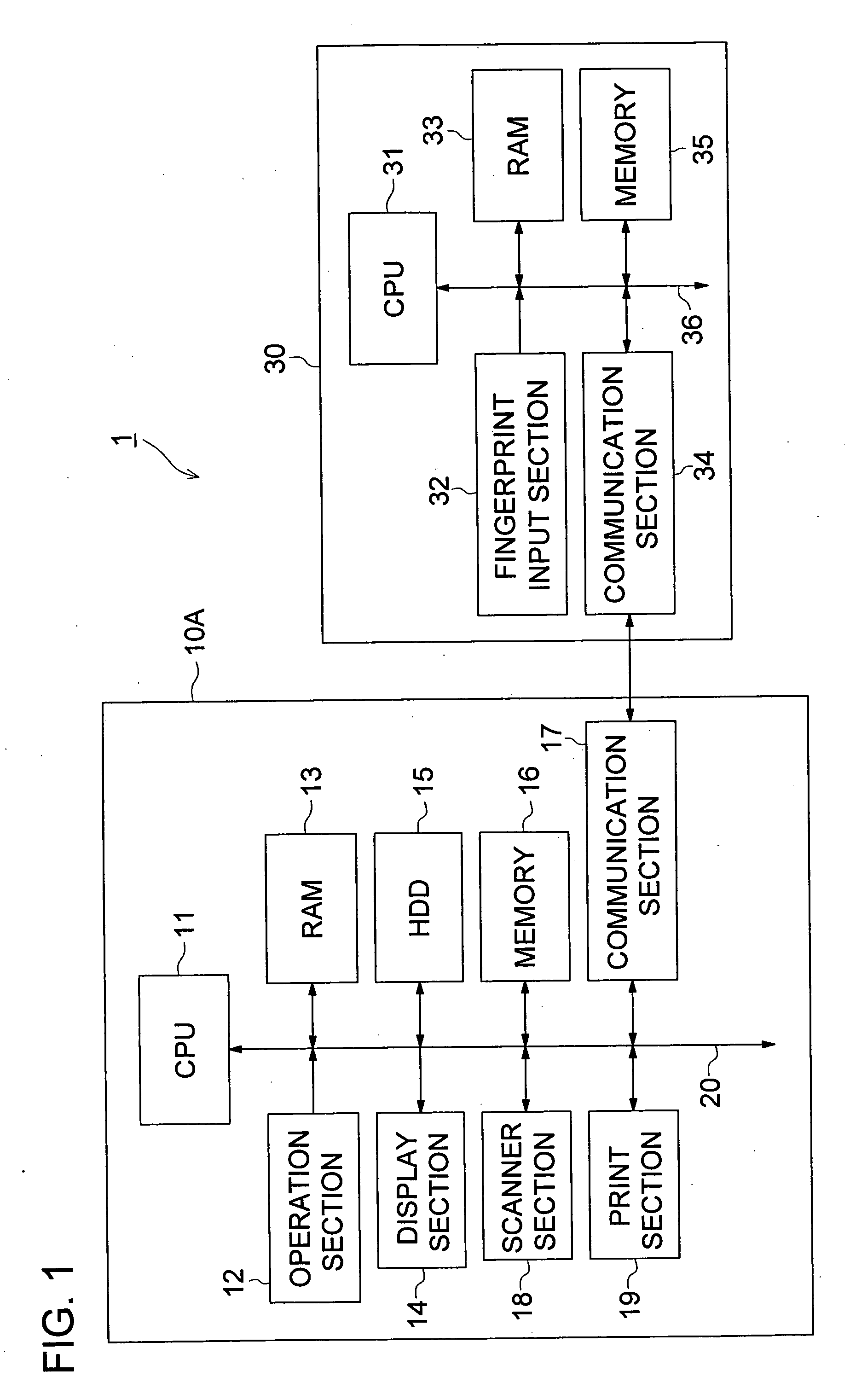
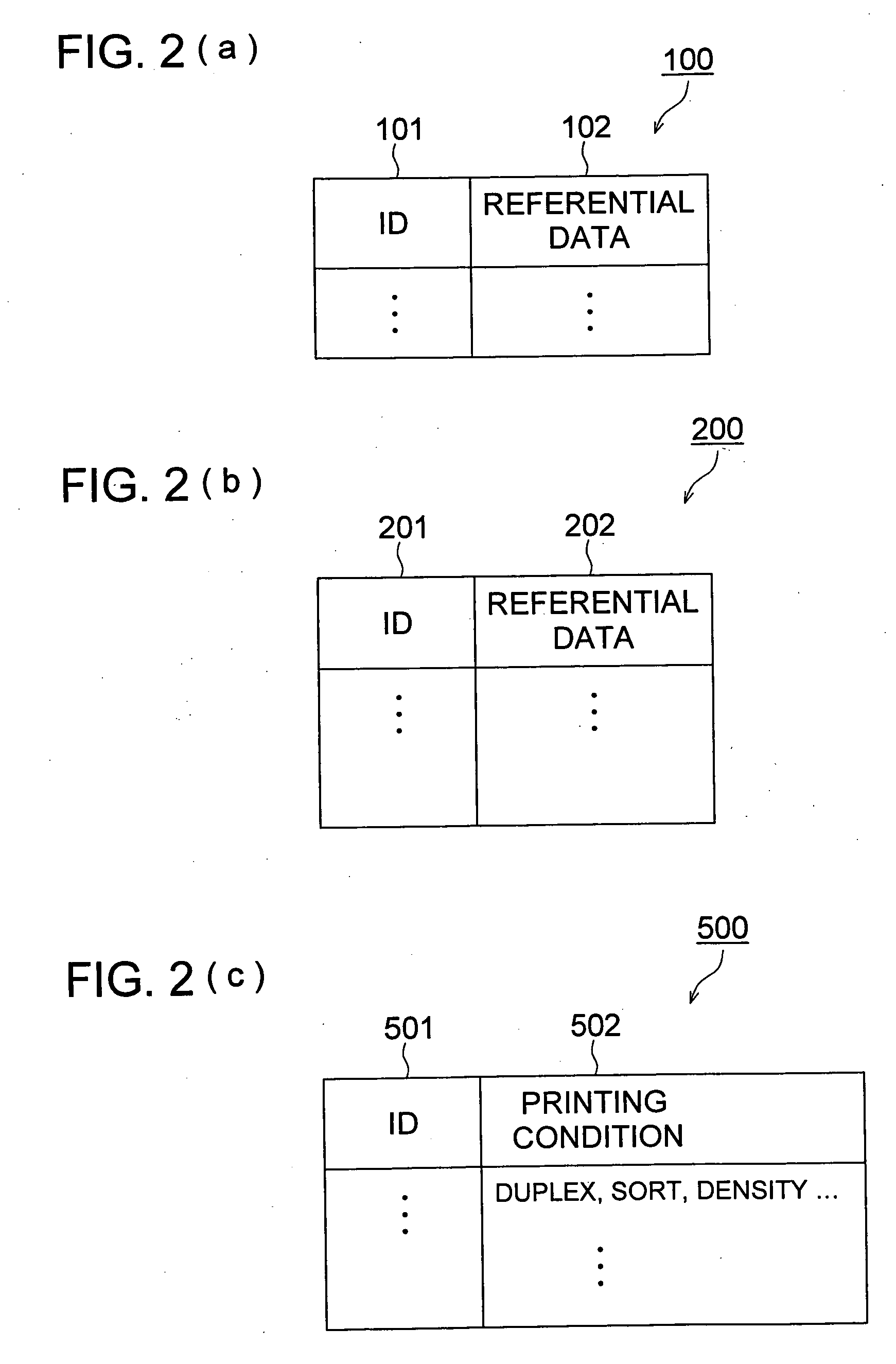
InactiveUS20060165262A1High precisionImprove user convenienceProgramme controlElectric signal transmission systemsData mining
A person verification apparatus having: a biological information input section to receive an input of biological information of a person and to obtain a data of the biological information as a data to be verified; an ID input section to receive an input of ID of a person; and a control section to compare the data to be verified with plural pieces of referential data registered in advance, and to obtain referential data corresponding to the ID received by the ID input section and compare whether the referential data corresponding to the ID matches with the data to be verified when the data to be verified does not match with the plural referential data.
Owner:KONICA MINOLTA BUSINESS TECH INC
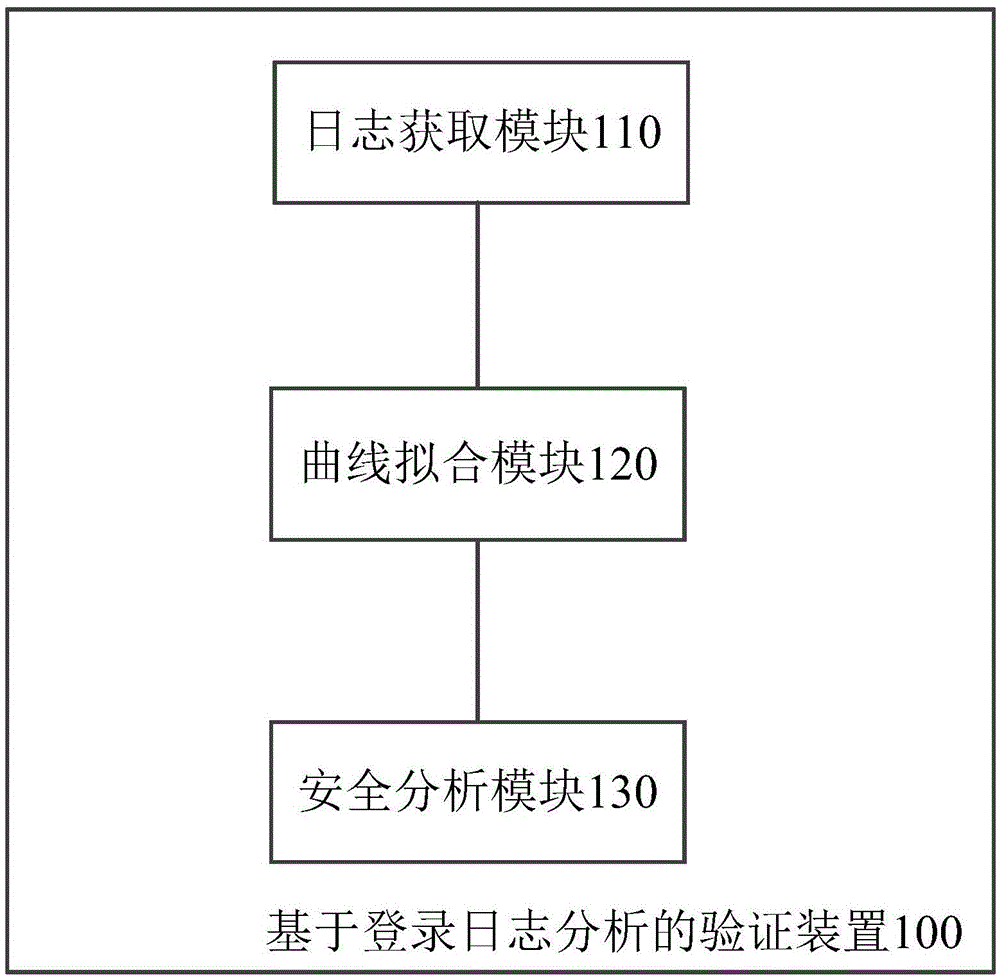
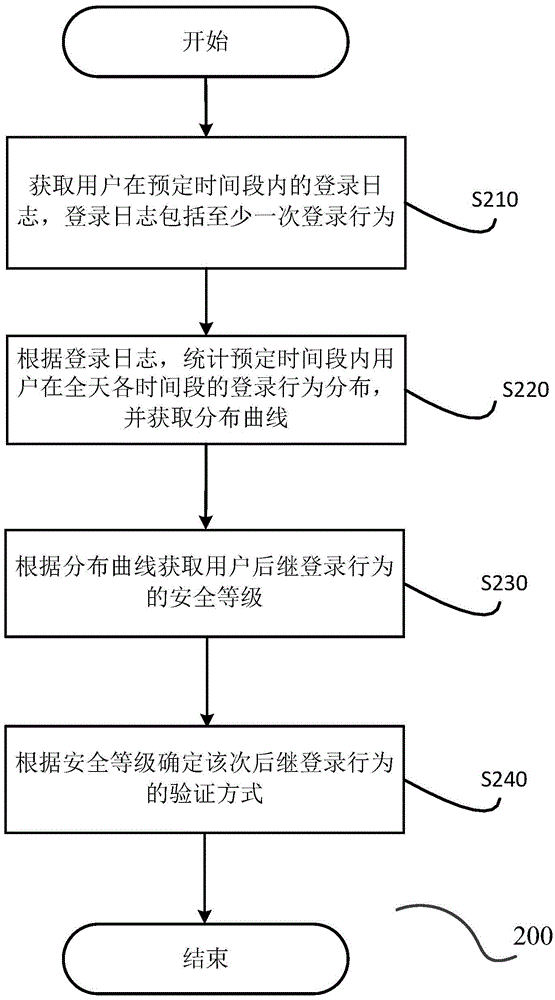
Verification method and device based on login log analysis
ActiveCN105516138AImprove experienceReduce verification timeTransmissionValidation methodsComputer science
The invention discloses a verification method based on login log analysis. The method comprises: obtaining a login log of a user in a preset time period, wherein the login log comprises at least once login behavior; counting the login behavior distribution of the user in the preset time period of every time period all day according to the login log and obtaining a distribution curve; obtaining the safety levels of the subsequent login behaviors of the user according to the distribution curve; and determining the verification mode of the subsequent login behavior of this time according to the safety levels. The invention also discloses a verification device based on login log analysis.
Owner:广州密码科技有限公司
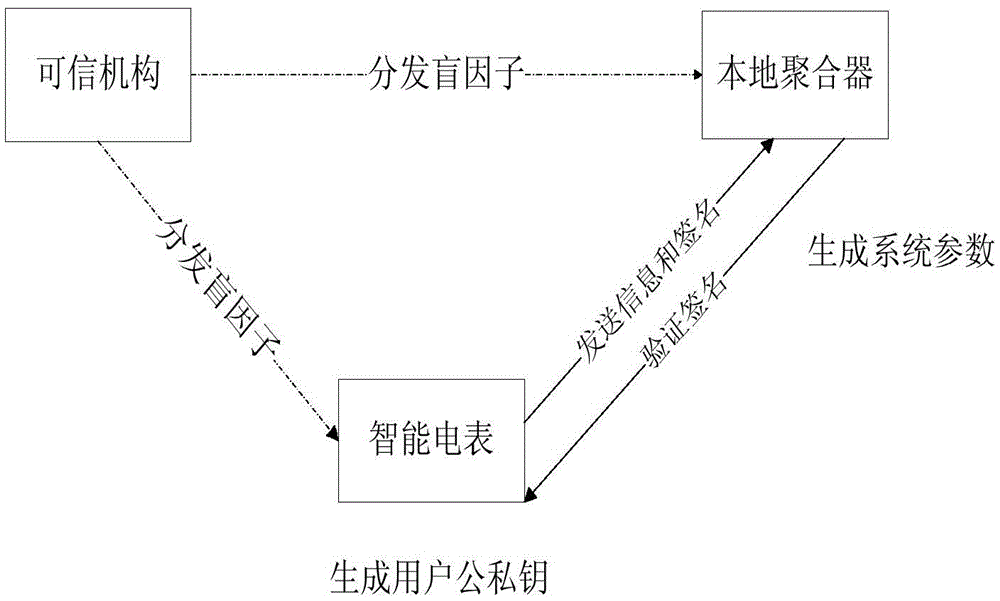
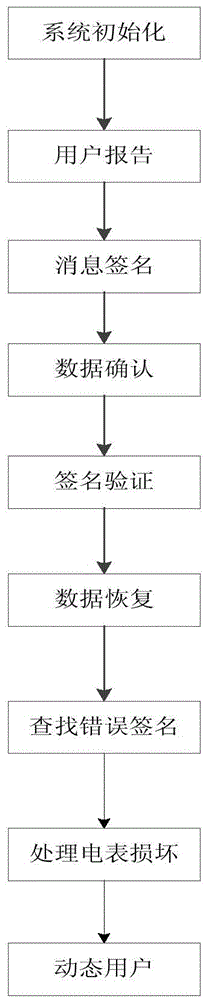
Data collection method in smart power grid based on user privacy protection
ActiveCN105577356AImprove practicalityAchieve unforgeabilityUser identity/authority verificationCommunication with homomorphic encryptionGrid basedUser privacy
The invention discloses a data collection method in a smart power grid based on user privacy protection. The method comprises the following steps that: firstly, a system is initialized; secondly, a smart electric meter sends a plurality of kinds of electricity consumption information of users to a local aggregator; thirdly, the smart electric meter signs the user information and sends the user information to the local aggregator; fourthly, the local aggregator determines the user information and signatures; fifthly, the local aggregator verifies the signatures in batch; sixthly, the local aggregator aggregates total electricity consumption information of all users; seventhly, the local aggregator searches for invalid signatures; eighthly, electric meter fault conditions are processed; and ninthly, user joining and exiting conditions are processed. According to the invention, the collection of plurality of kinds of electricity consumption information is realized, external attackers are resisted, internal attackers can also be resisted, and unforgeability of information is realized, so that the electricity consumption privacy of the users is protected.
Owner:XIDIAN UNIV
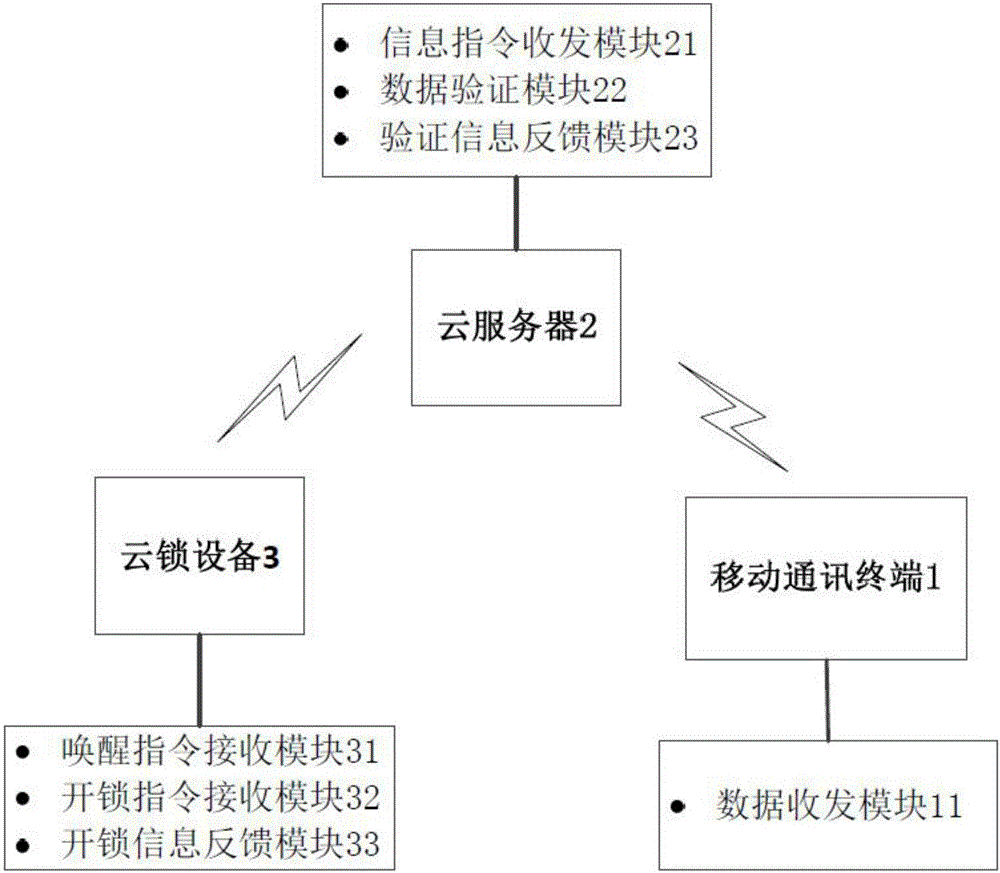
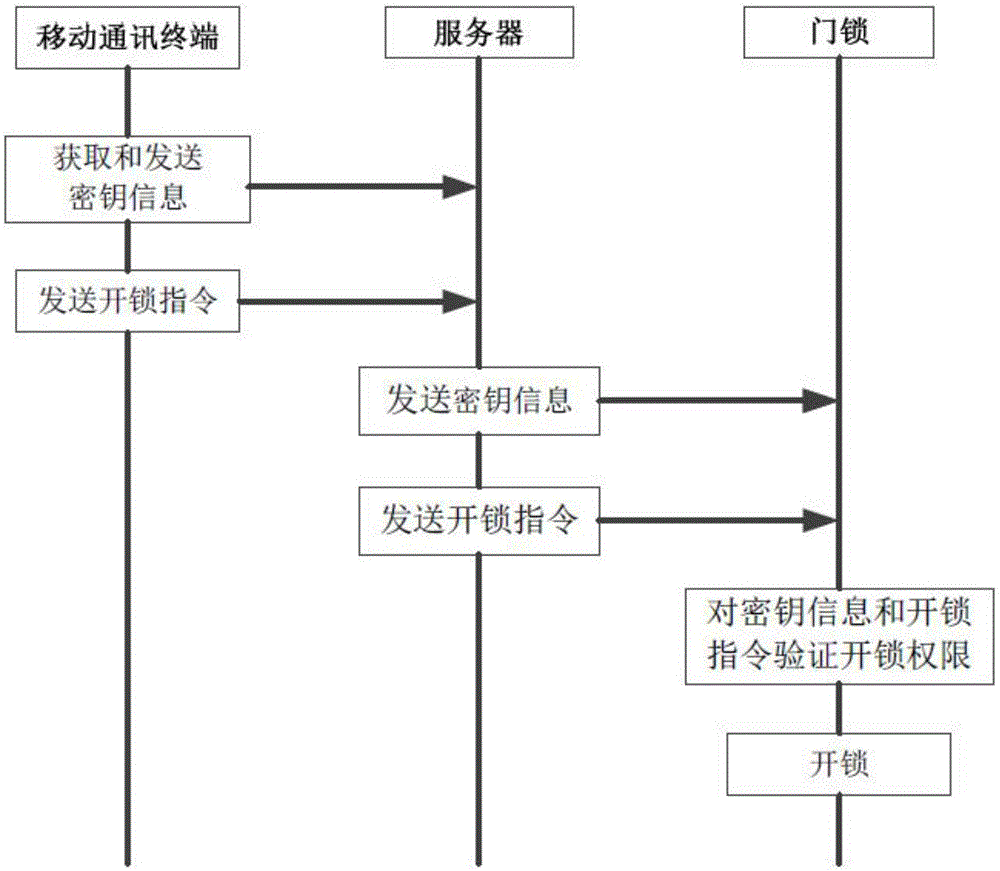
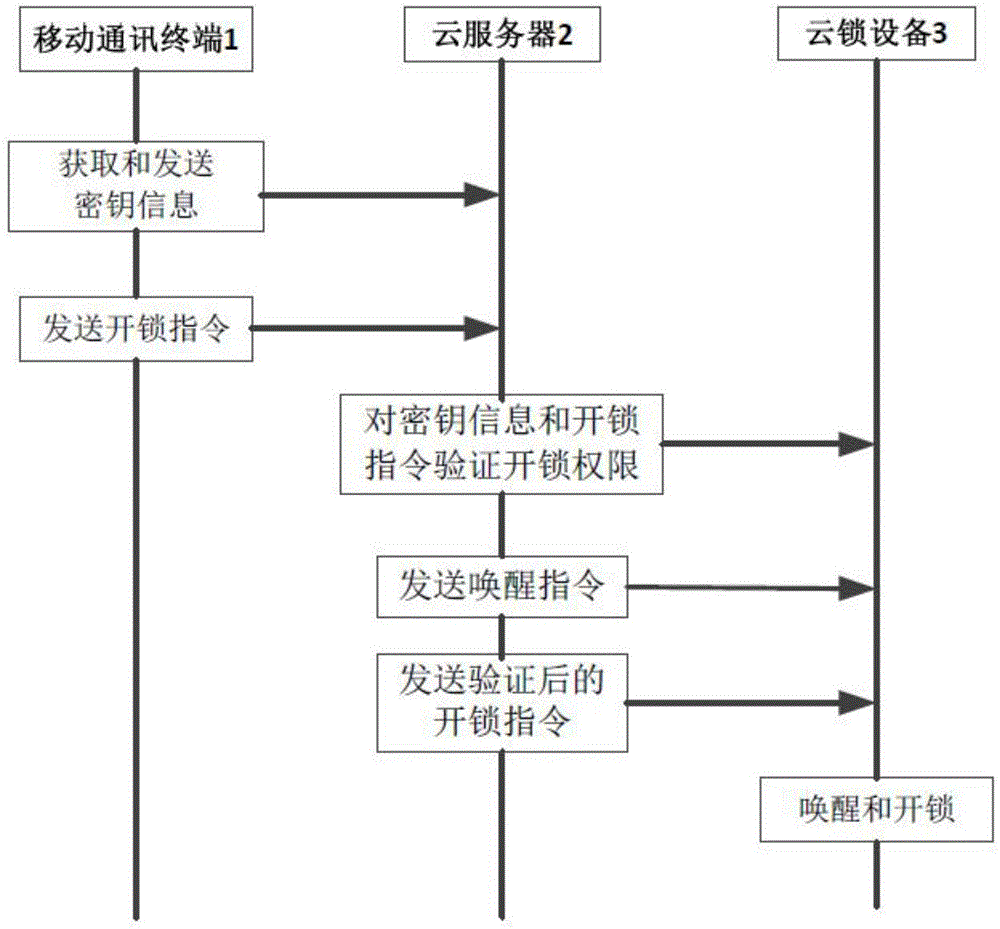
Cloud lock management method and system based on network
InactiveCN107180467AReduce verification timeFix security issuesPower managementIndividual entry/exit registersComputer terminalCloud server
The invention discloses a cloud lock management method and system based on a network. The system comprises a mobile communication terminal, a cloud server and cloud lock equipment, wherein the mobile terminal and the cloud lock equipment are connected with the cloud server by wireless communication; the mobile communication terminal acquires secret key information, and transmits the secret key information and an unlocking instruction to the cloud server; the cloud server receives the secret key information and the unlocking instruction, and verifies the secret key information and the unlocking instruction, and whether unlocking authority exists or not is judged according to a verification result; if the verification result shows that the unlocking authority exists, an awakening instruction and an unlocking instruction after verification is successful are transmitted to the cloud lock equipment; the cloud lock equipment receives the awakening instruction and the unlocking instruction after verification is successful; the awakening instruction awakens the cloud lock equipment from an intermittent dormancy state; and the unlocking instruction after verification is successful drives the cloud lock equipment to carry out unlocking operation. By the cloud lock management method based on the network, the unlocking speed is increased, the unlocking operation is speedy, power is saved, and the safety is good.
Owner:HUITAILONG DECORATION MATERIAL YUEXIU DIST GUANGZHOU
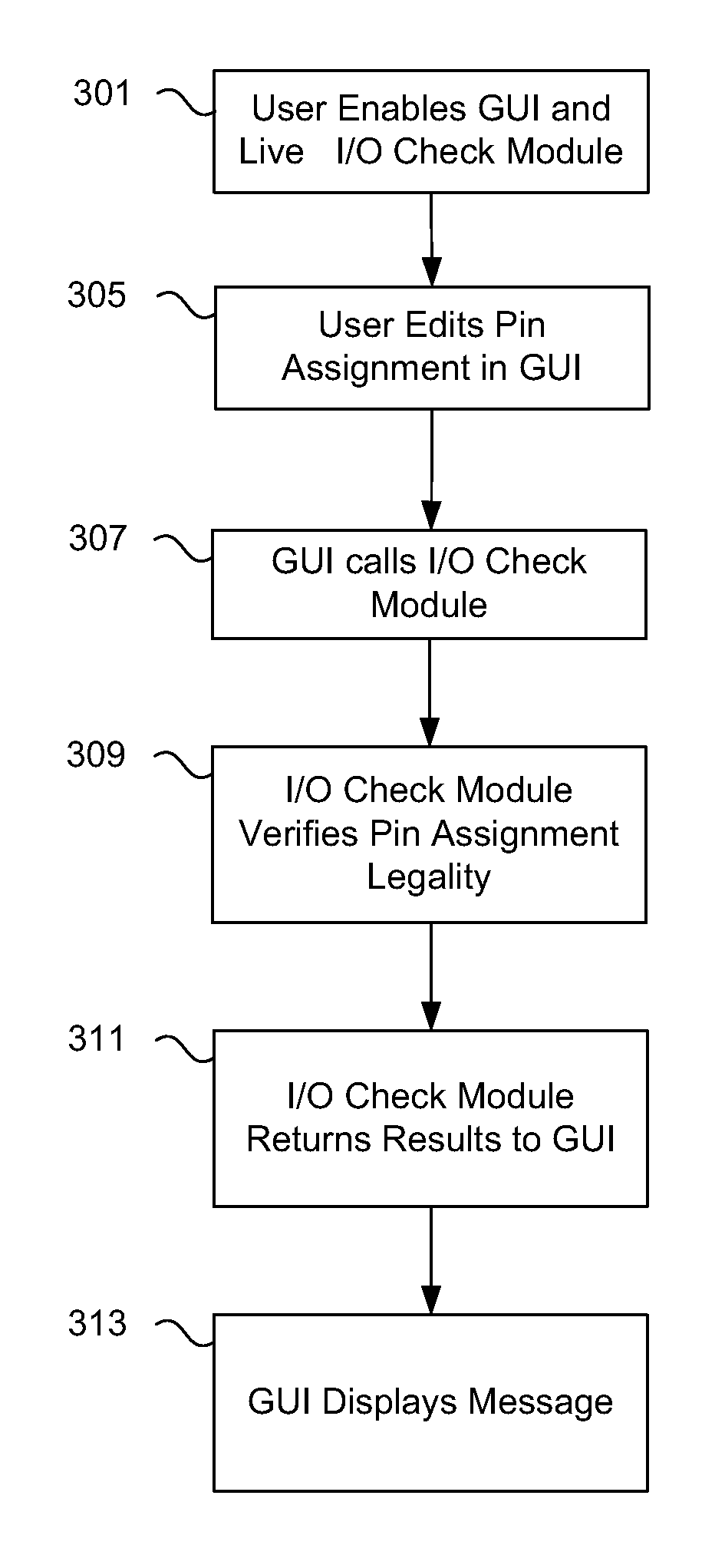
Real-time background legality verification of pin placement
ActiveUS7992119B1Improves pin assignment and placement processReduce numberCAD circuit designSoftware simulation/interpretation/emulationProgrammable logic deviceInput/output
Pin placement legality is verified in real-time in a background to reduce a number of input / output assignment analysis runs during a physical design of a programmable logic device. Edited pin properties are checked quickly in the background against certain rules, and results displayed to a user usually before a new pin is edited. Available and legal positions are found and displayed for a selected pin to reduce errors.
Owner:ALTERA CORP
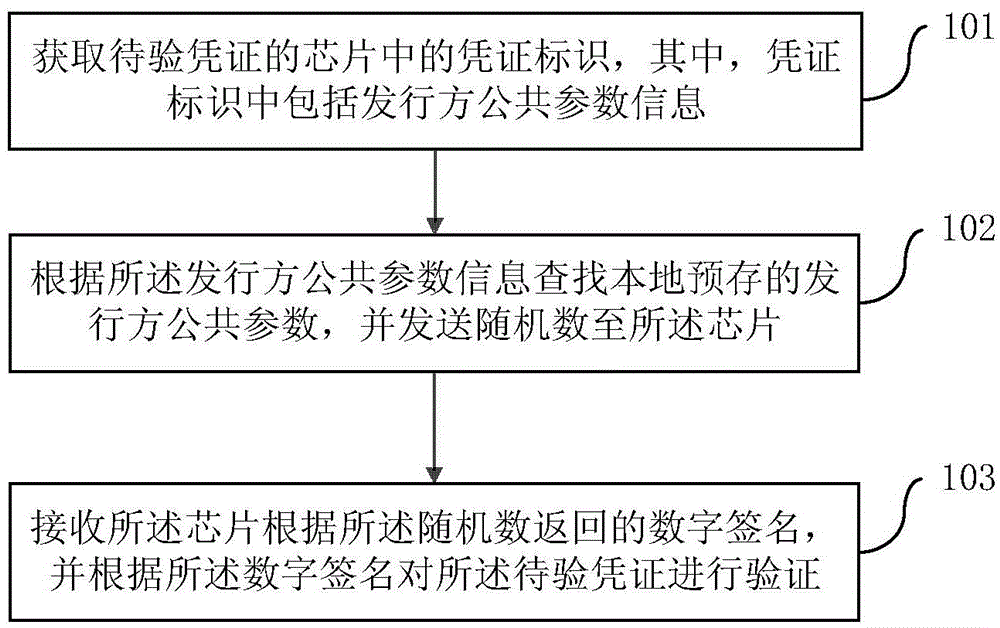
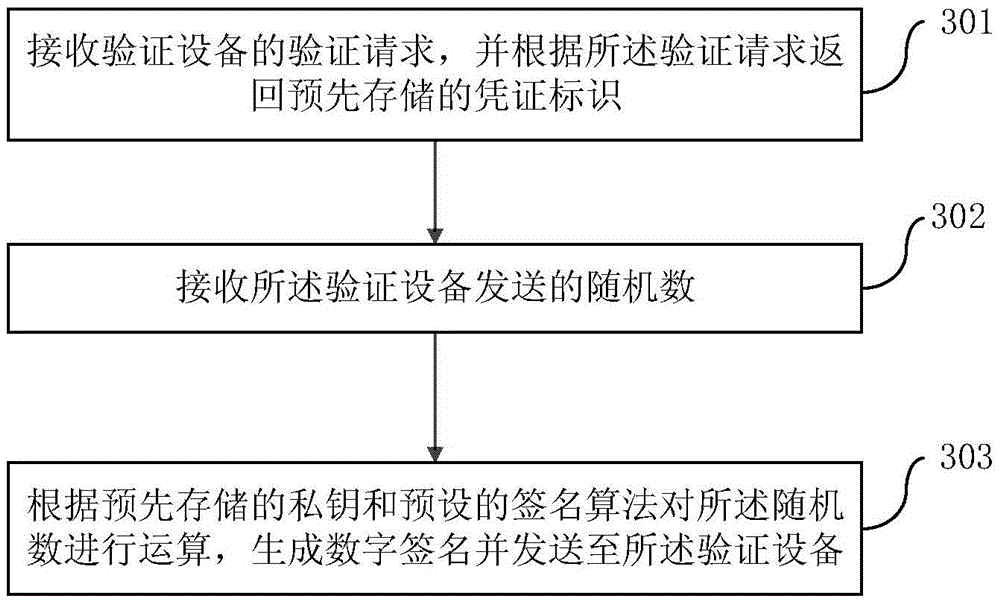
Anti-fake verification method, device and system and anti-fake certificate based on IBC (Identity-Base Cryptography)
InactiveCN105530099ARealize offline anti-counterfeiting verificationEasy to operateUser identity/authority verificationValidation methodsDigital signature
The invention discloses an anti-fake verification method, device and system and an anti-fake certificate based on IBC (Identity-Base Cryptography). The method comprises: obtaining the certificate identifier in the chip of a certificate to be verified; sending random numbers to the chip; receiving a digital sign returned by the chip according to the random numbers, verifying the digital sign according to the random numbers, locally stored issuer public parameters, the certificate identifier and a pre-stored IBC verification algorithm. According to the invention, offline anti-fake verification is carried out to the certificate without installing and verifying a digital certificate for many times; the operation flow is simplified; the verification time is shortened; and the cost is reduced.
Owner:GIESECKE & DEVRIENT (CHINA) INFORMATION TECH CO LTD
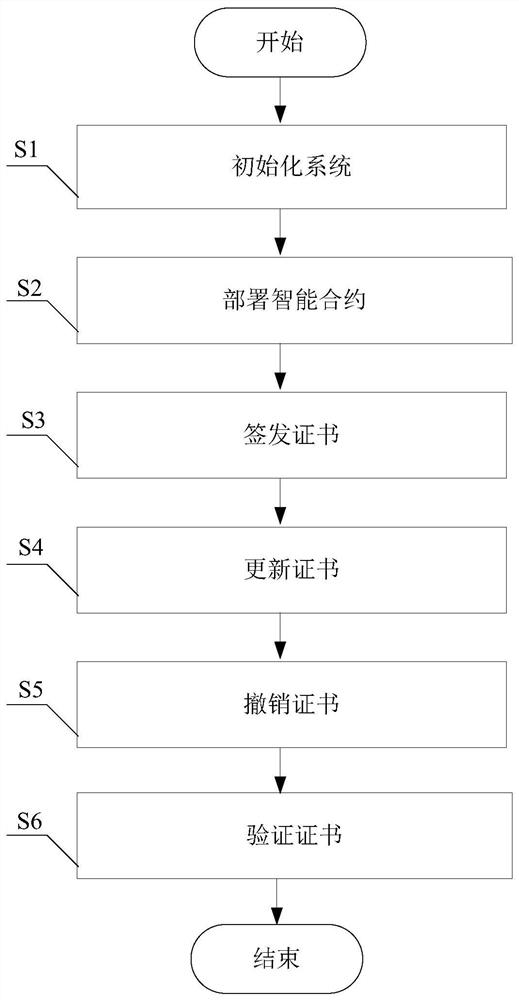
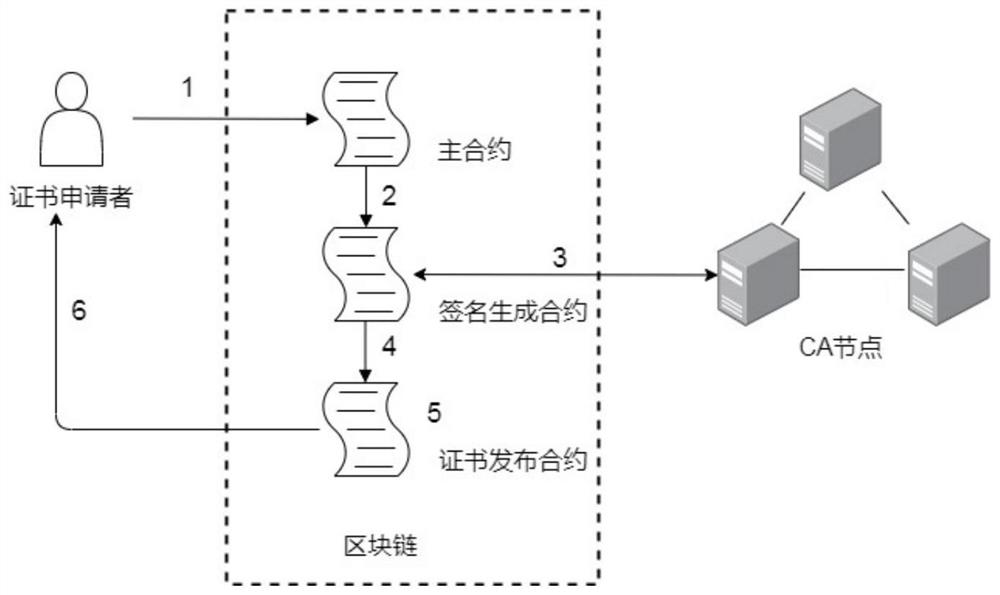
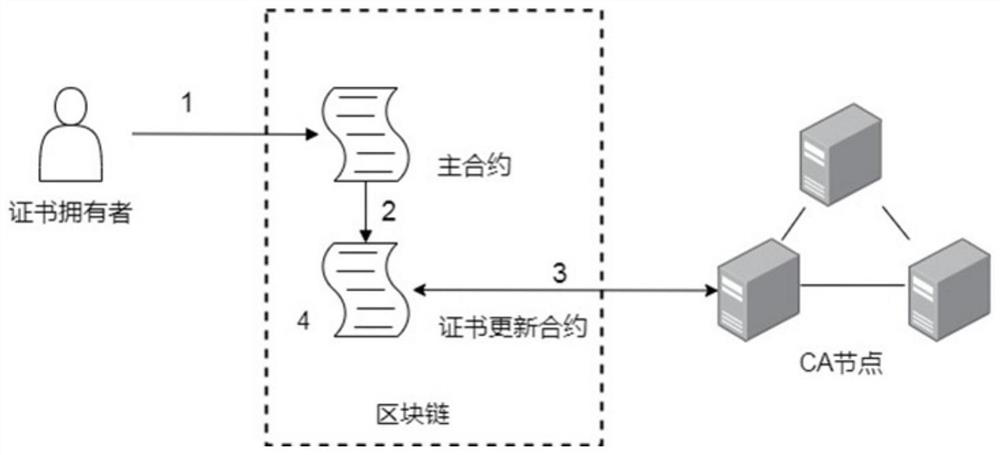
Distributed public key infrastructure construction method based on editable blockchain
ActiveCN112187455AReduce storage pressureReduce verification timeKey distribution for secure communicationUser identity/authority verificationEngineeringSmart contract
The invention provides a distributed public key infrastructure construction method based on an editable blockchain, and belongs to the technical field of public key infrastructure, and the method comprises the following steps: S1, initializing a system; S2, deploying an smart contract; S3, signing and issuing a certificate; S4, updating the certificate; S5, revoking the certificate; and S6, verifying the certificate. Compared with an existing PKI system based on a blockchain, an editable blockchain framework is creatively adopted, a new block does not need to be uploaded during certificate updating and revocation, the storage pressure of a blockchain network can be reduced, the certificate verification time can be shortened, a threshold ring is used for signing and issuing a certificate, and an authentication mechanism is composed of multiple CA nodes; the CA independently audits the operation request for the certificate, and the certificate can be operated only after the CA exceedingthe threshold number passes the auditing, so that the tolerance of the system to a Byzantine node is improved, and the security is relatively high.
Owner:SOUTHWEST JIAOTONG UNIV +1
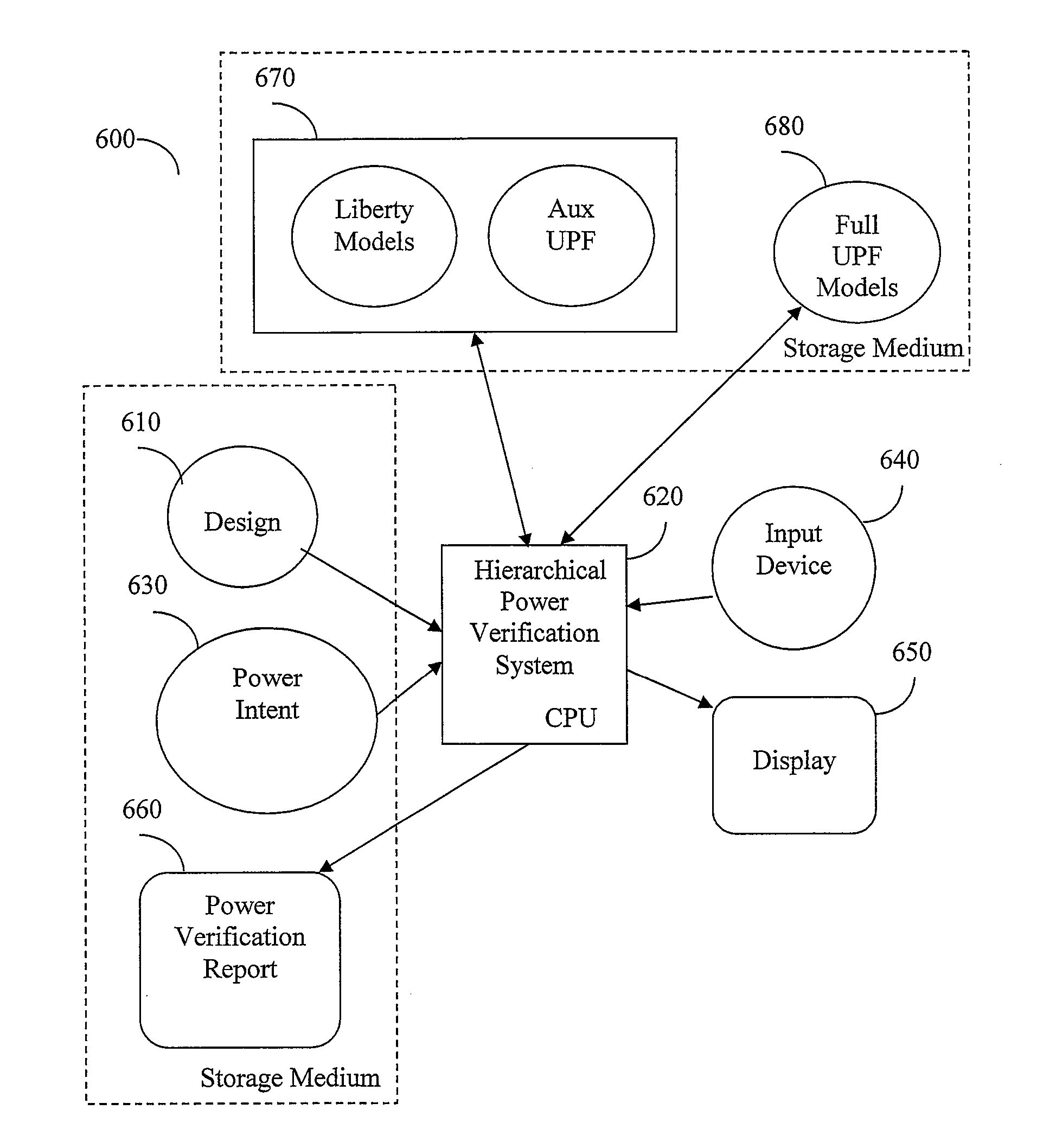
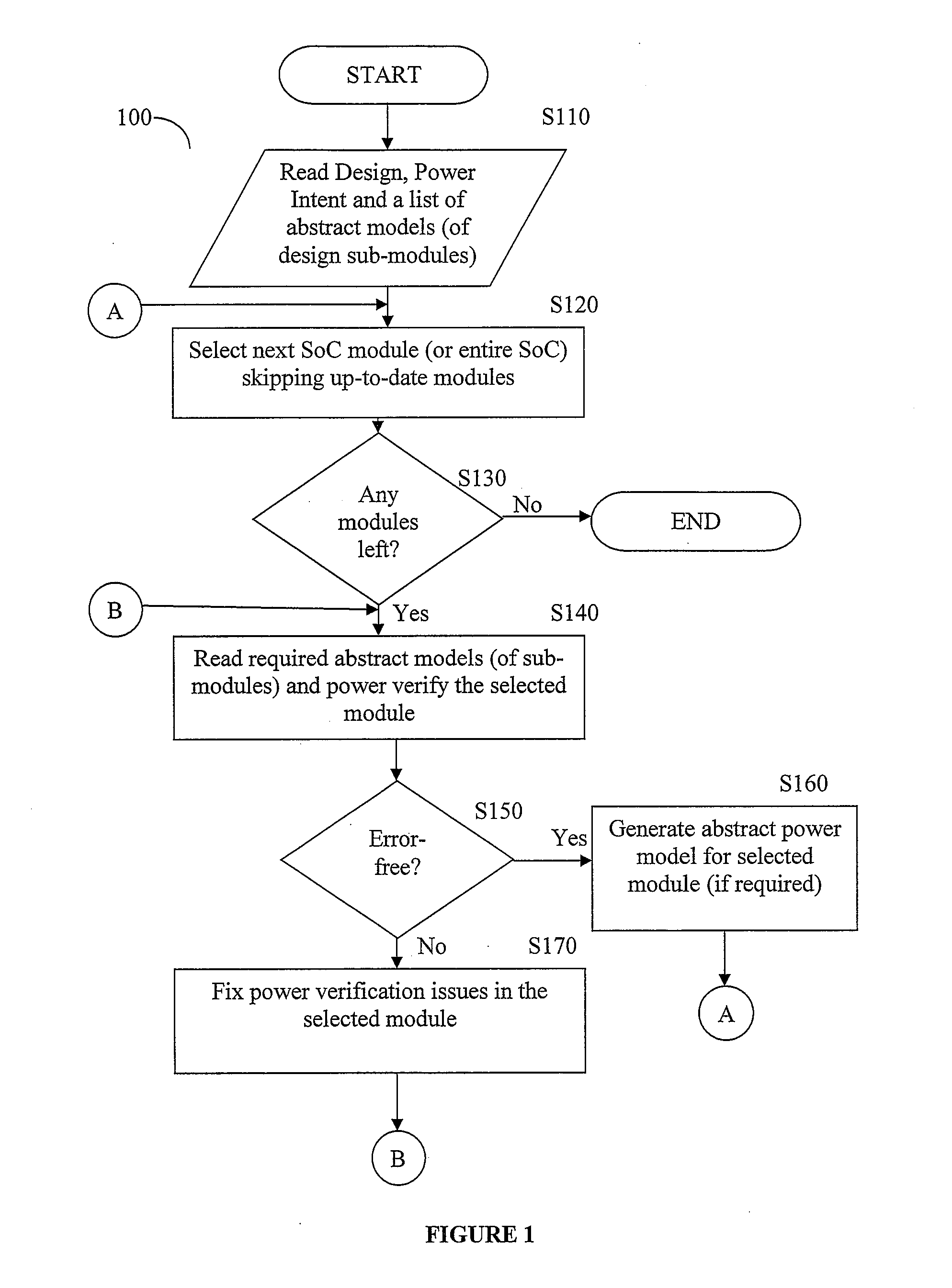
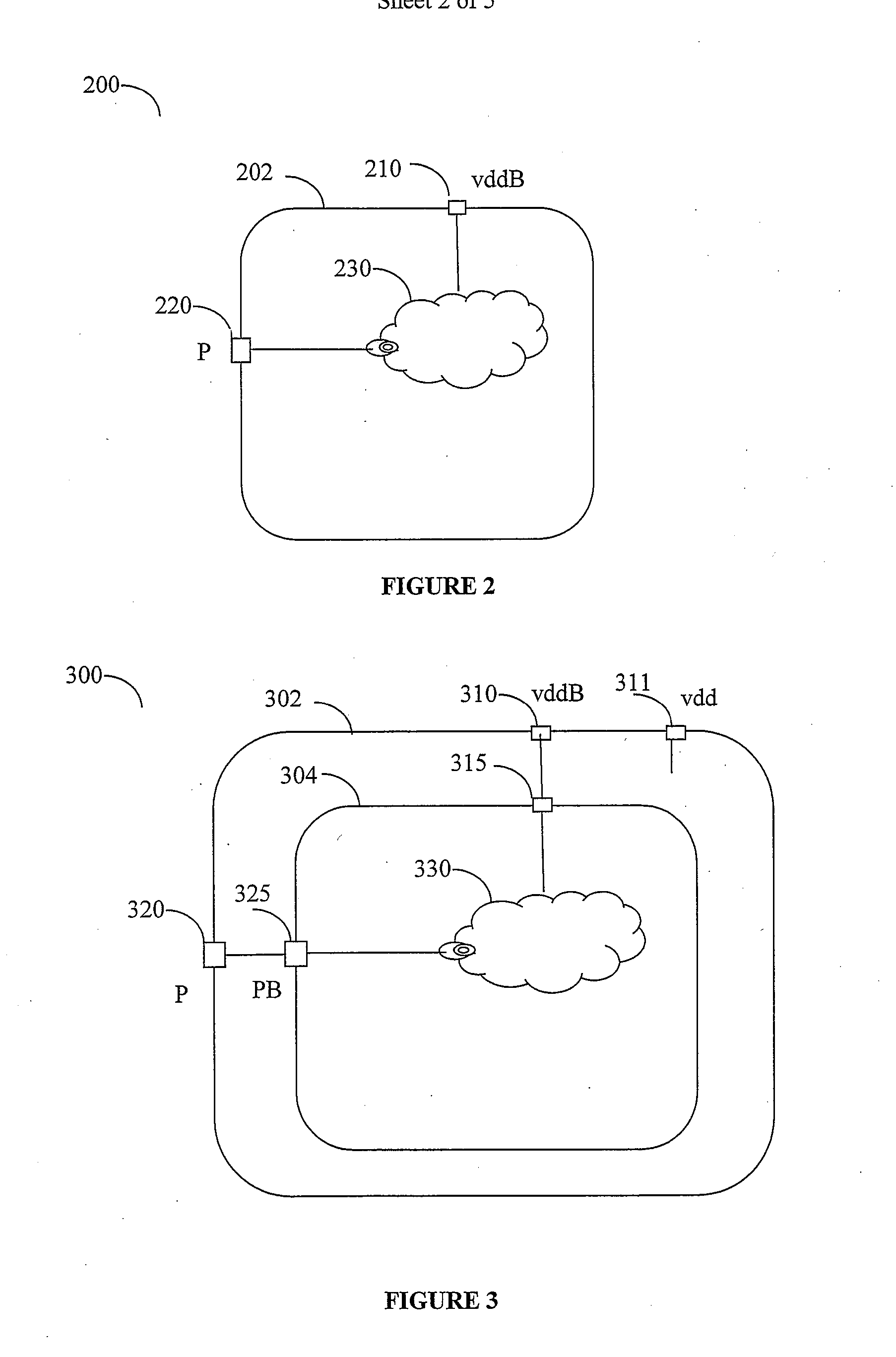
System and method for hierarchical power verification
InactiveUS20170011138A1Reduce runtimeReduce memory requirementsComputer aided designSpecial data processing applicationsVerification systemPower management
A hierarchical power verification system and method creates abstract models of power behavior of modules that it successfully verifies. The abstract models simplify the module definition by omitting internal module details but provide sufficient information for power verification of higher level modules that incorporate this abstracted module. Design blocks are replaced with these abstract power models, resulting in reduced run-time and memory requirements. The power models can include power switches inside the block, related supplies of logic ports, supply power states, system power states, power management devices such as isolation logic and level shifters, feed-through and floating ports. The power model may be expressed either in UPF or as a combination of liberty model and UPF. After replacing modules with abstracted models the HPVS can quickly verify an entire SoC with a small memory footprint. When a user modifies a module, the HPVS need only verify the changed module and related modules at higher levels of module hierarchy.
Owner:SYNOPSYS INC
SOC verification system and method based on UVM
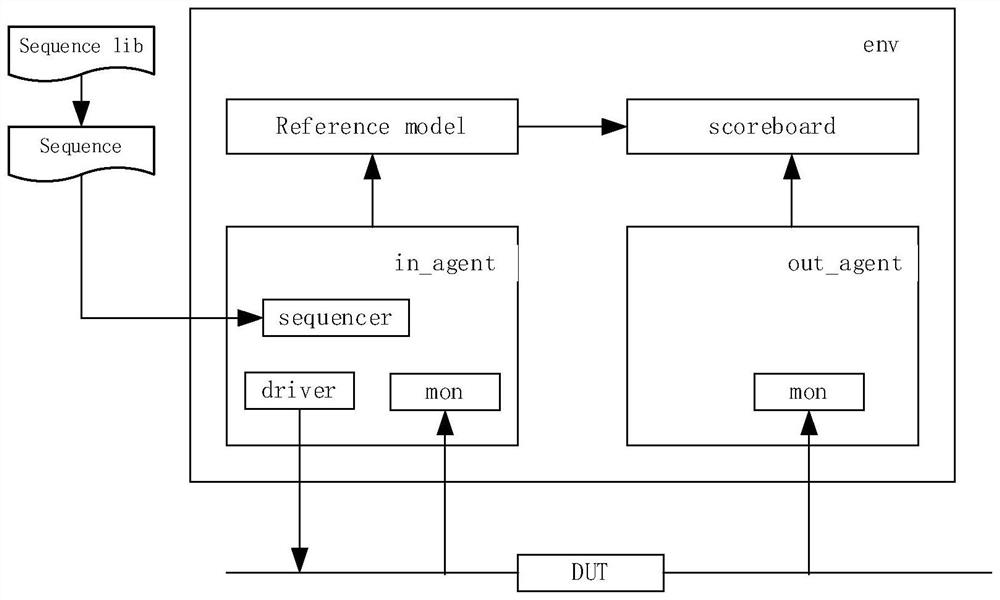
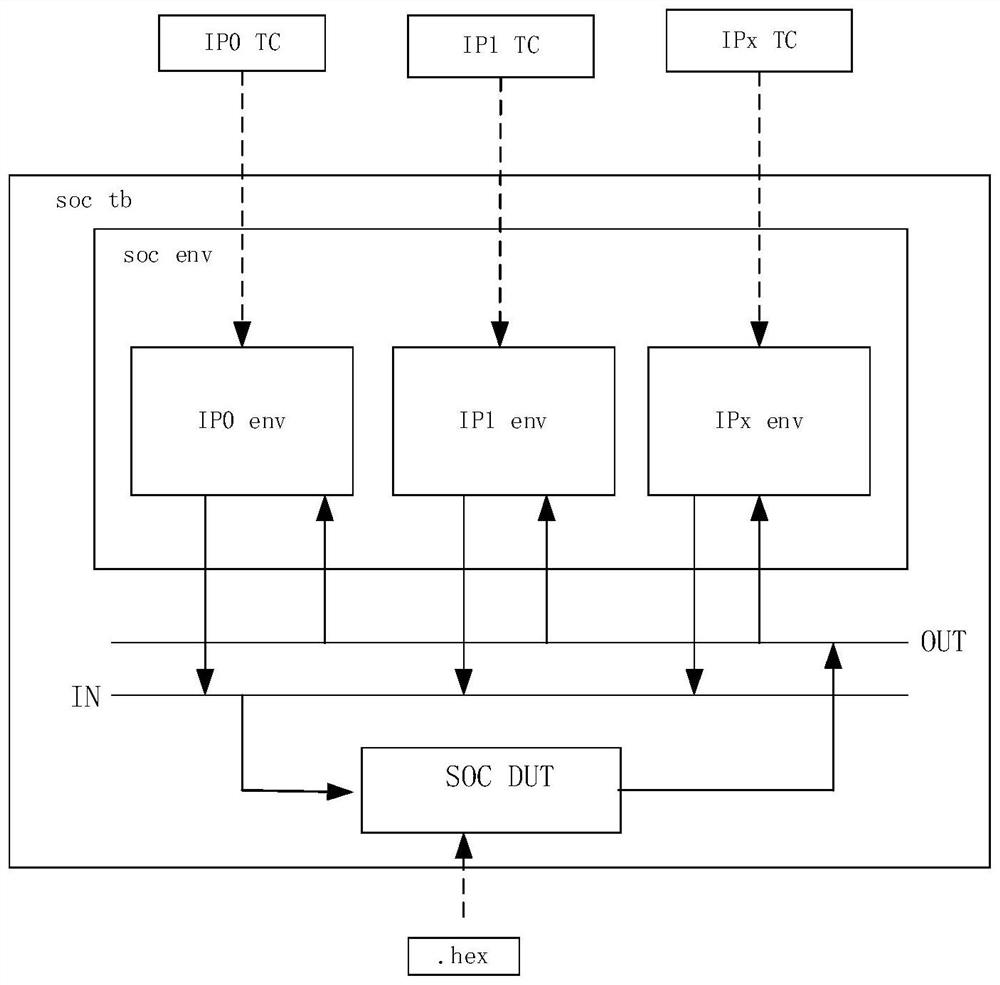
ActiveCN113297017AGuaranteed testing flexibilityReduce verification timeDetecting faulty computer hardwareComputer aided designReference modelVerification system
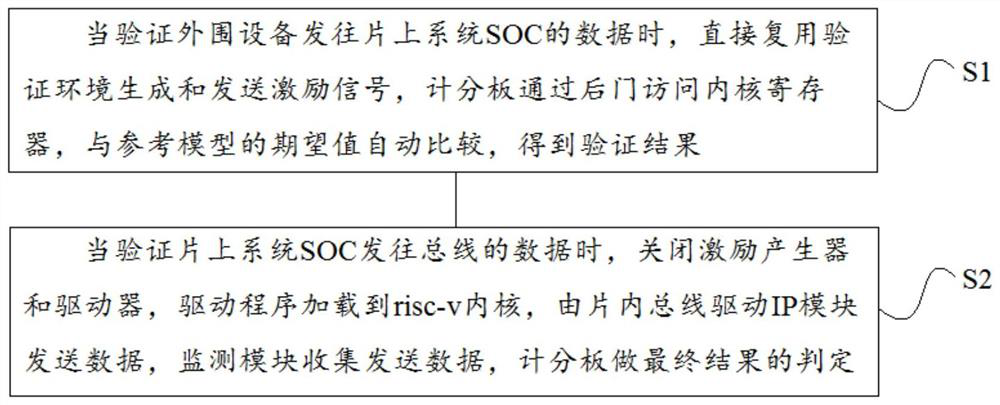
The invention relates to the technical field of chip verification, in particular to an SOC verification system and method based on UVM, and the system comprises a test excitation which covers design specifications and is randomly generated, a verification environment layer which is formed by combining a plurality of IP_ENVs, and a system-on-chip SOC based on a risc-v kernel. Each IP_ENV comprises a scoreboard, a kernel register, a reference model, an excitation generator, a driver and a monitoring module. When data sent by peripheral equipment to the SOC is verified, a verification environment is directly multiplexed to generate and send an excitation signal, and the scoreboard accesses the kernel register through a back door and automatically compares the kernel register with an expected value of the reference model to obtain a verification result; when the data sent to a bus by the SOC is verified, the excitation generator and the driver are closed, a driving program is loaded to the risc-v kernel, an IP module is driven by the on-chip bus to send the data, the monitoring module collects the sent data, and the scoreboard judges a final result. The system has the following beneficial effects that the verification time is greatly shortened while the test flexibility is ensured.
Owner:杭州德旺信息技术有限公司
Formation method for assistance graph
InactiveCN106950795AReduce widthReduce verification timeOriginals for photomechanical treatmentGraphicsPhotoresist
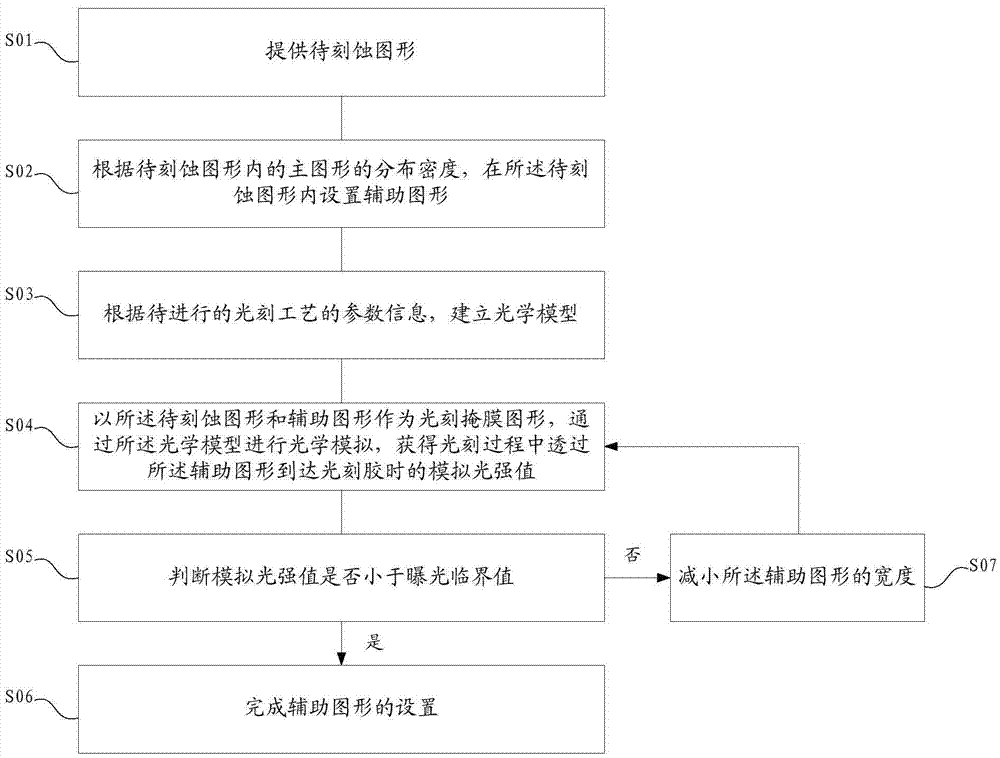
Disclosed is a formation method for an assistance graph. The formation method comprises the steps of providing a to-be-etched graph which comprises a plurality of main graphs; setting an initial assistance graph in the to-be-etched graph according to the distribution density of the main graphs in the to-be-etched graph; establishing an optical model according to parameter information of a to-be-implemented photoetching process; performing optical simulation through the optical model to obtain a simulation light intensity value when light penetrates through the initial assistance graph to arrival at photoresist in the photoetching process; if the maximum of the simulation light intensity value is less than an exposure critical value, completing the setting of the assistance graph; and if the maximum of the simulation light intensity value is greater than or equal to the exposure critical value, reducing the width of the initial assistance graph until the obtained simulation light intensity value is less than the exposure critical value, and completing the setting of the assistance graph. By virtue of the formation method, chip verification on the set assistance graph is not needed, so that chip verification time can be saved, and it is ensured that the assistance graph does not appear on the photoresist in the actual photoetching process.
Owner:SEMICON MFG INT (SHANGHAI) CORP +1
Station entrance identity authentication method based on two-dimensional code
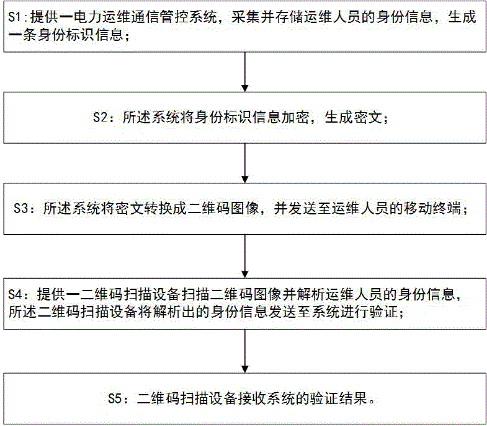
InactiveCN105844747AResolve authenticationAvoid safety hazardsData processing applicationsIndividual entry/exit registersControl systemCiphertext
The invention relates to a station entrance identity authentication method based on a two-dimensional code. The method particularly includes the following steps: S1) providing an electric operation and maintenance communication management and control system for collecting and storing identity information of operation and maintenance workers to generate identity identification information; S2) encrypting the identity identification information to generate a cipher text by a system; S3) converting the cipher text into a two-dimensional code image by the system and sending the two-dimensional code image to a mobile terminal of the operation and maintenance workers; S4) providing a two-dimensional code scanning device, so that when the operation and maintenance workers enter the station for maintenance and show the two-dimensional code image on the mobile terminal, the two-dimensional code scanning device scans the two-dimensional code and analyses the identity information of the workers, and sends the analyzed identity information to the system for identification; and S5) receiving the verification result from the system by the two-dimensional code scanning device. The method solves the problem of identity identification of the operation and maintenance workers through the two-dimensional code and data encryption technologies.
Owner:STATE GRID FUJIAN ELECTRIC POWER CO LTD +1
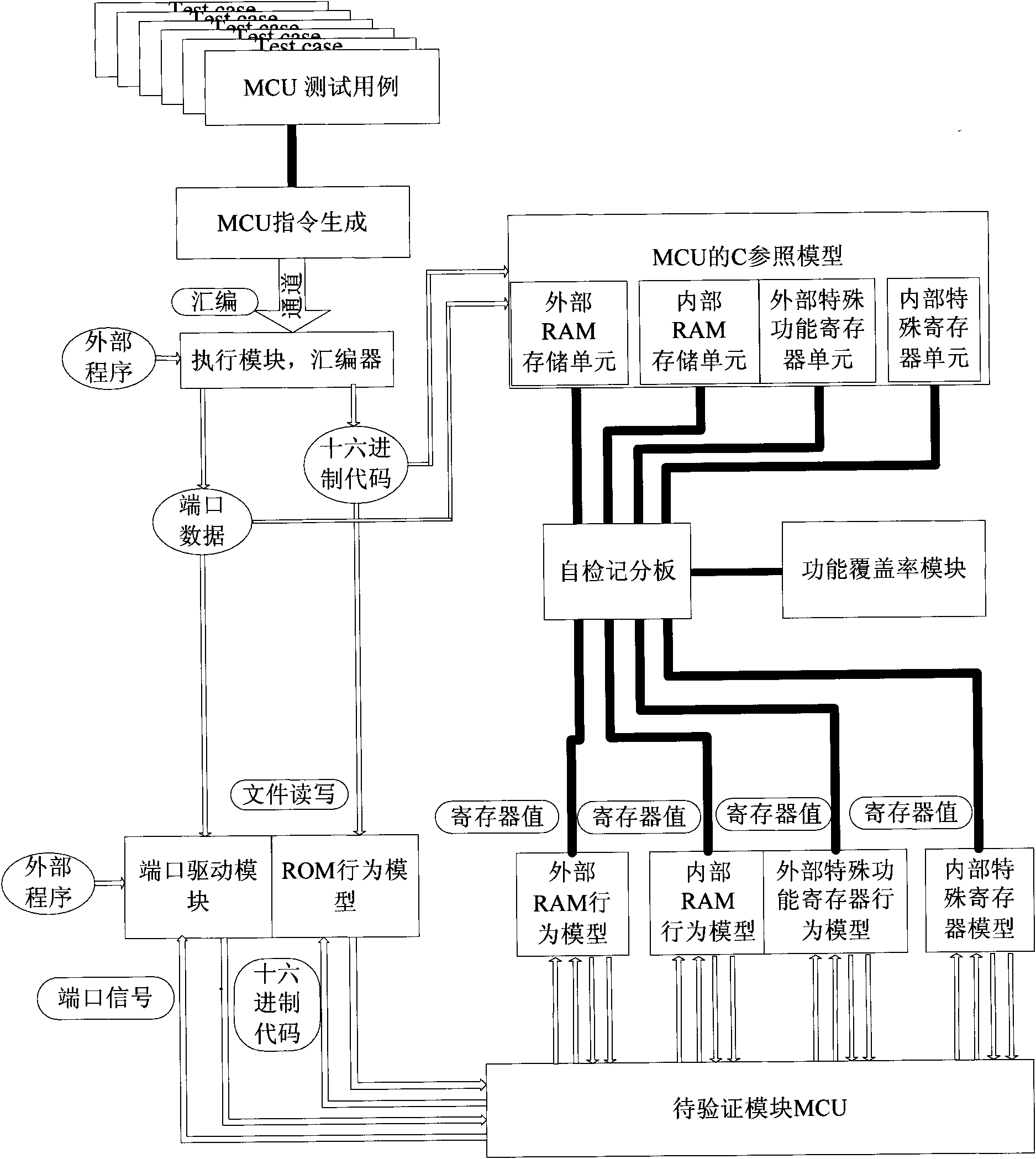
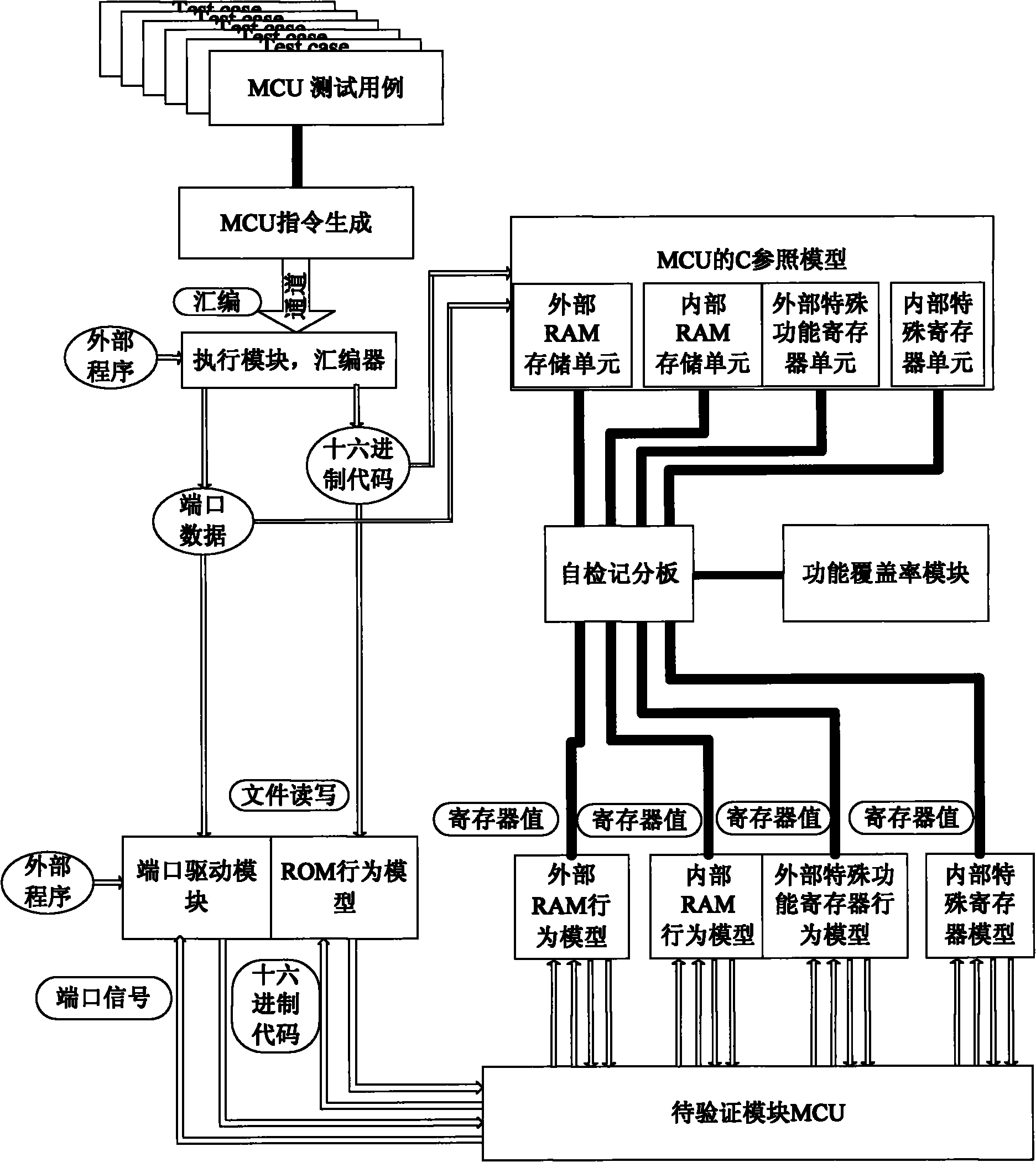
Method for realizing microprogrammed control unit (MCU) verification platform based on verification methodology of verification methodology manual (VMM)
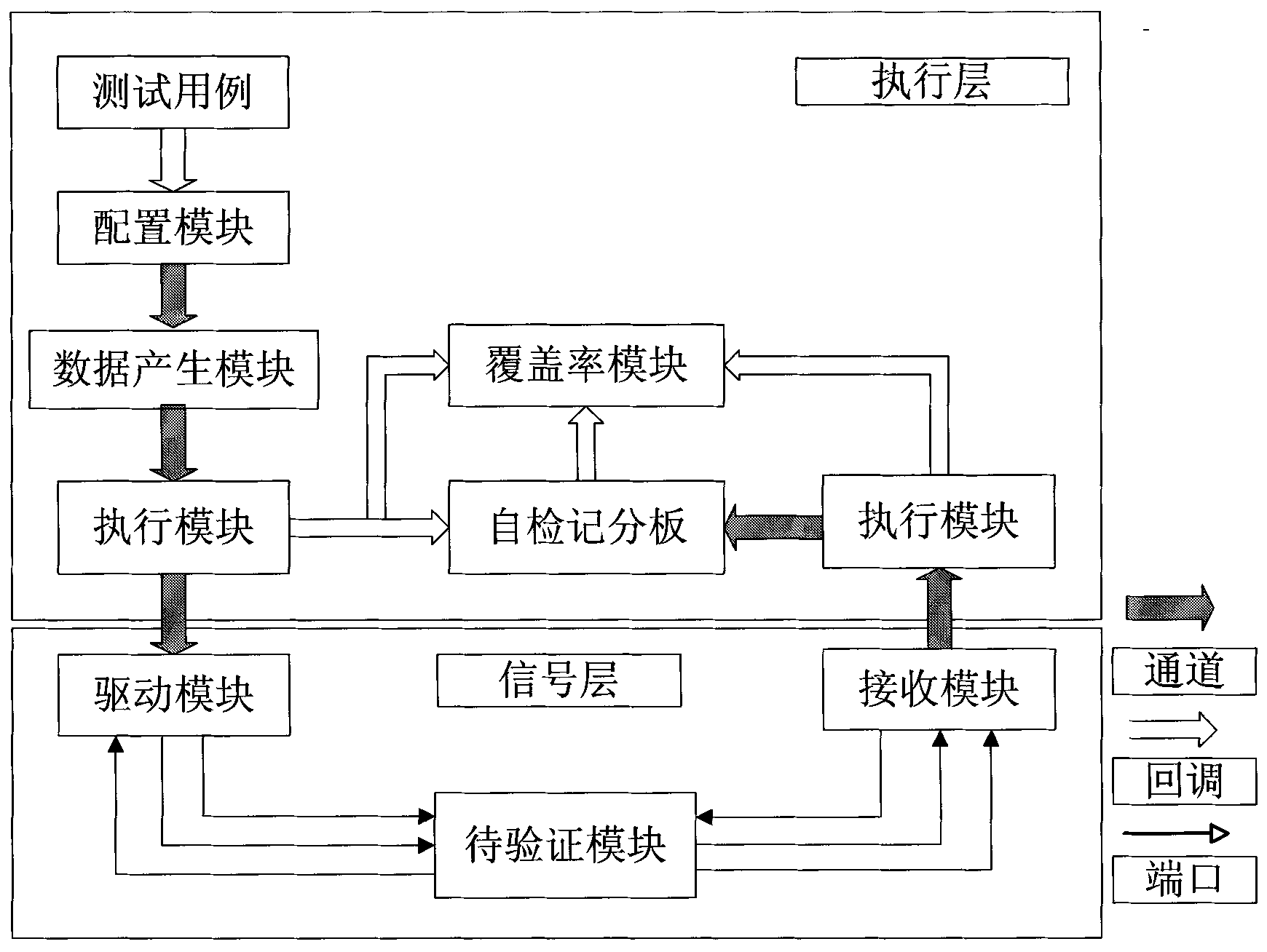
InactiveCN102096628ASimple migration and verificationExtended fully automated checksSoftware testing/debuggingComputer architectureSpecial function register
The invention discloses a method for realizing a microprogrammed control unit (MCU) verification platform based on the verification methodology of a verification methodology manual (VMM). The method comprises the following steps of: inputting all usable application program codes or generating a constraint random instruction by using the platform; realizing a model C of an MCU and providing values of all memory units and special function registers, and calling through a direct program interface (DPI); automatically performing self-checking according to a memory unit model serving as a reference; and describing various functional coverage models and providing a functional coverage result. By the method, a portable, reusable, extensible and fully automatic check MCU verification platform with a hierarchical structure can be established.
Owner:SHANGHAI HUAHONG INTEGRATED CIRCUIT
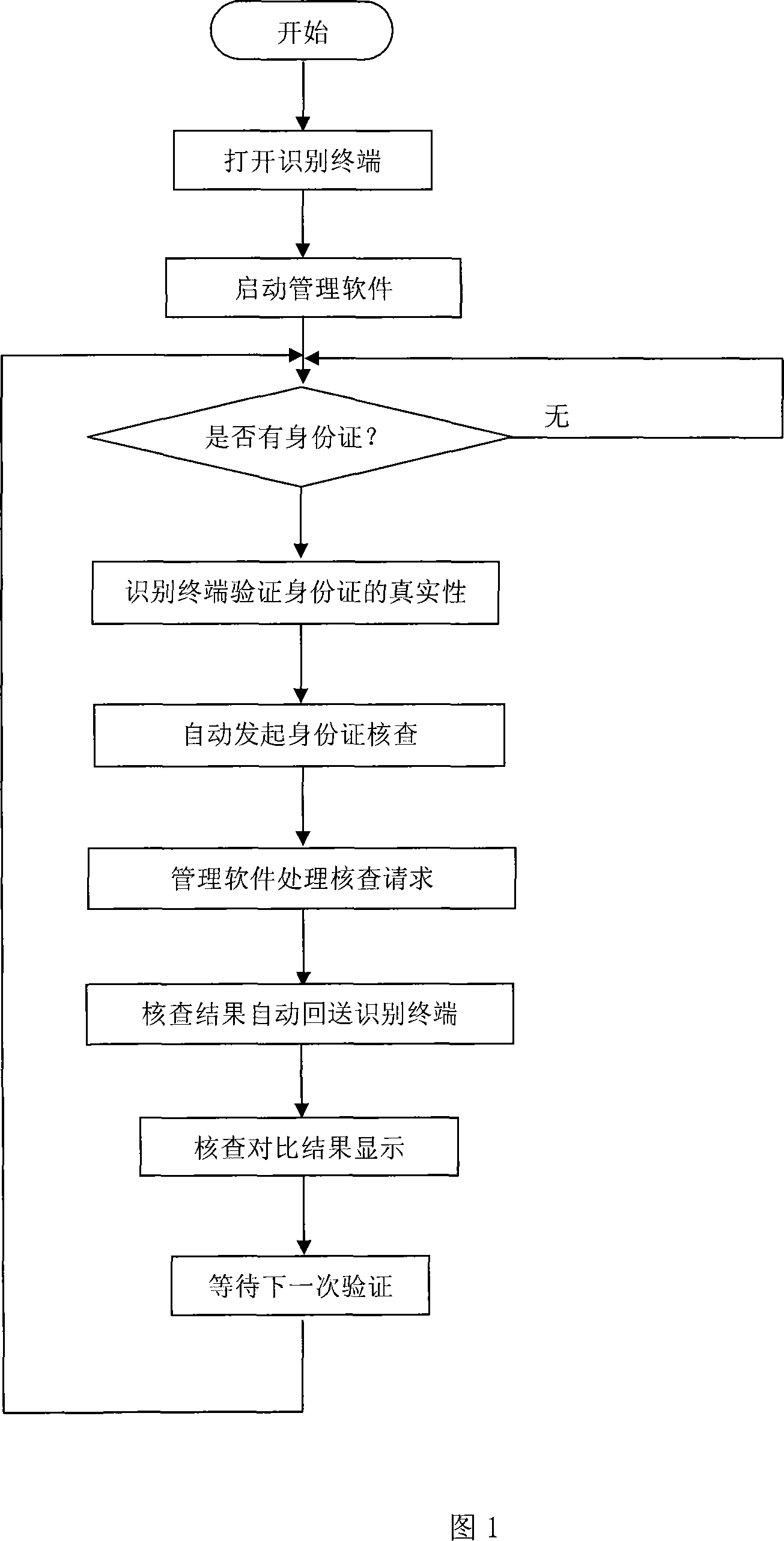
Network checking method for identity card validation
InactiveCN101123010AGuarantee the safety of fundsPrevent money launderingChecking apparatusPrivate networkThe Internet
The invention discloses a method of checking identity certificate verification, which is used to realize check via the internet for verification of authenticity of identity certificate of individual customers through an identity certificate recognizing terminal provided with a networking check managing software and a special network. The steps of verifying check via network are: starting; opening the recognizing terminal and starting the managing software; recognizing whether the terminal has detected an identity certificate, and if a certificate has been detected, the recognizing terminal reads the identity certificate information and display the photo and related information on the recognizing terminal screen; the recognizing terminal transfers the request to the population information database of the Ministry of Public Security; the database checks the verification and feeding back the check results to the recognizing terminal; the recognizing terminal screen simultaneously displays photo and related information of the identity certificate requested for verification, and the check result, photo and related information are fed back from the population information database of the Ministry of Public Security to the recognizing terminal; and finishing the check and waiting for next verification check. The invention can be used for quickly and accurately checking authenticity of the identity certificate of an individual customer, i. e. the second generation of individual identity certificate.
Owner:SHANDONG SYNTHESIS ELECTRONICS TECH
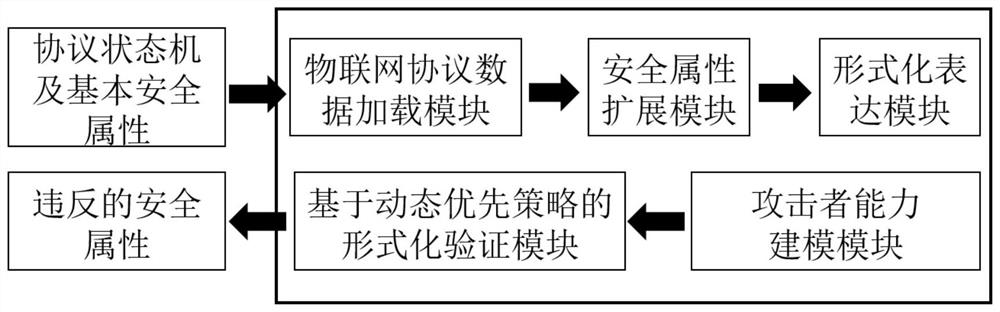
Internet of Things protocol security automatic analysis method and system based on formal verification
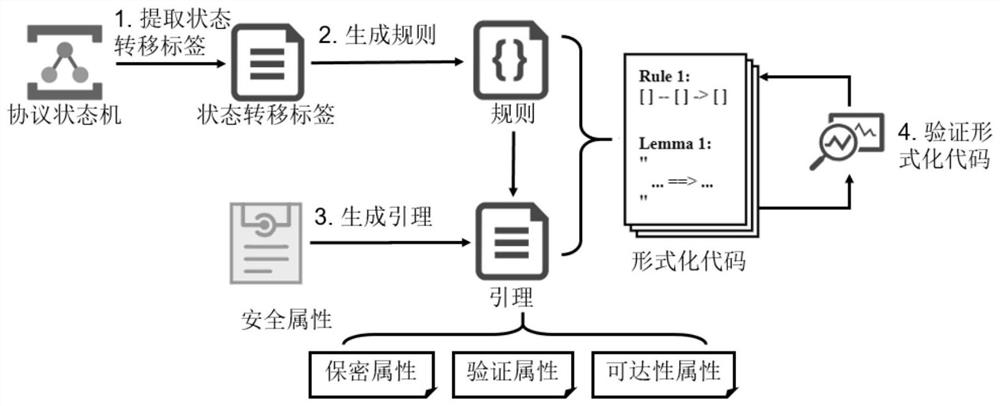
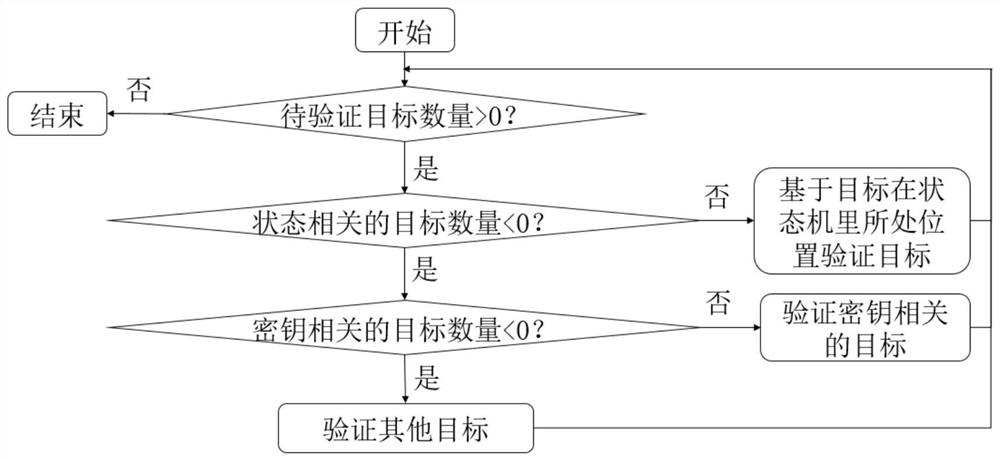
ActiveCN112153030AReduce manual burdenImprove securityData switching networksAttackSoftware engineering
The invention discloses an Internet of Things protocol security automatic analysis method and system based on formal verification, and the method comprises the steps: building a security attribute needing to be satisfied by a protocol based on an Internet of Things protocol state machine, and automatically achieving the formal description of an Internet of Things protocol and the security attribute needing to be satisfied by the Internet of Things protocol; modeling attacker ability by applying two attack scenes, and formal verification being realized based on a dynamic priority strategy. According to the Internet of Things protocol security automatic analysis method based on formal verification, protocol state machines, deployed on a plurality of Internet of Things platforms, of MQTT, CoAP and AMQP protocols can be efficiently converted into formal languages, and automatic and systematic security analysis is carried out.
Owner:杭州智达融信科技有限公司
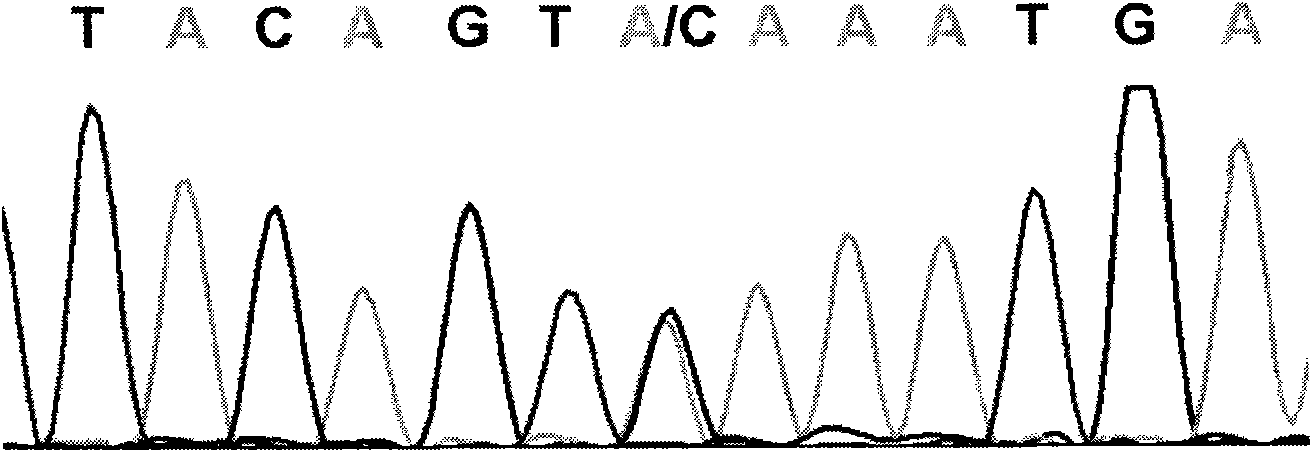
Cucumber SNP marker and detection methods thereof
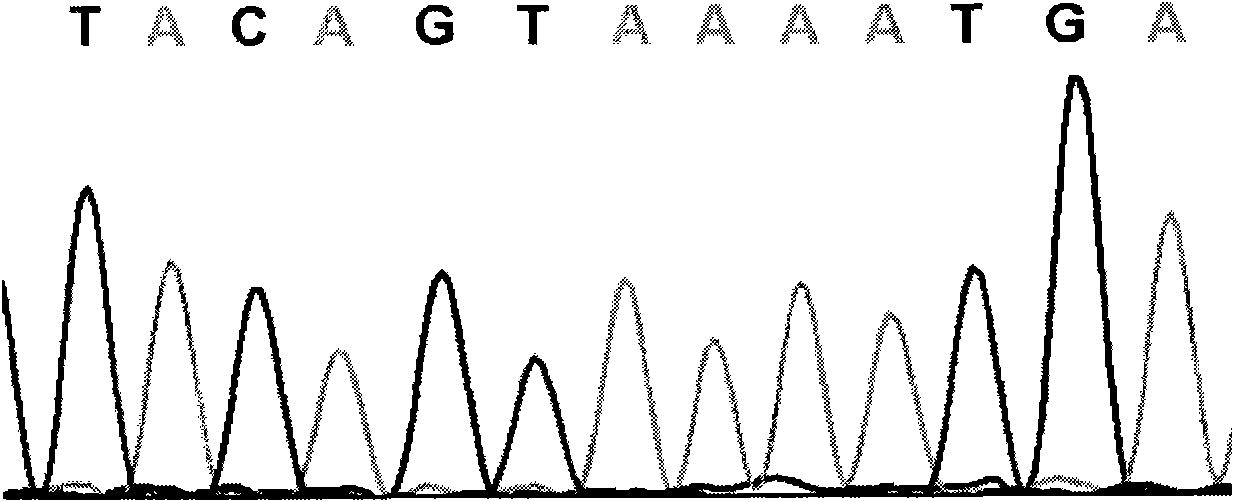
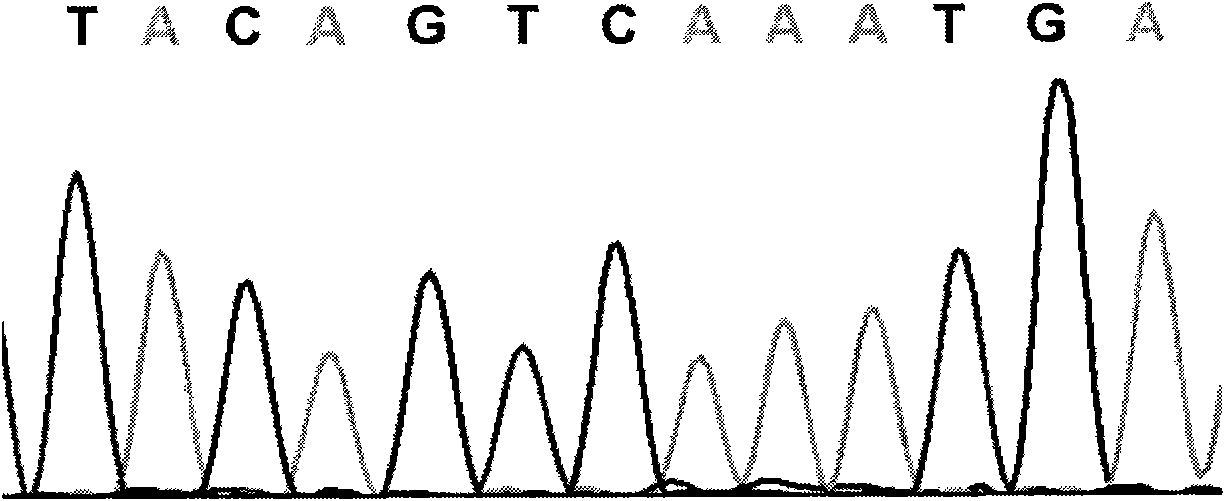
InactiveCN101591708AShorten development timeReduce verification timeMicrobiological testing/measurementDNA/RNA fragmentationF1 generationCucumber family
The invention relates to a cucumber SNP marker and detection methods thereof in the technical field of plant gene engineering. A method for identifying cucumber SNP locus comprises the following steps: selecting homozygous cucumber parents, and performing sequencing to determine candidate SNP locus; hybridizing to obtain F1 generation single plants, and performing sequencing; and detecting a peak shape chart of a F1 generation sequencing result to determine candidate locus with heterozygous peaks. A method for determining SNP marked polymorphic single plants in F2 generation separation group of cucumber comprises the following steps: selecting homozygous cucumber parents, and obtaining the F2 generation separation group; selecting recessive phenotype single plants in the F2 generation, mixing DNAs of the single plants in equal quantity, and construct a recessive gene pool; performing amplification and sequencing by an SNP primer, and detecting a peak shape chart of a sequencing result; and respectively performing amplification and sequencing on single plants in the recessive gene pool by the SNP primer, and detecting a peak shape chart of a sequencing result. The cucumber SNP marker has a sequence shown as SEQ ID NO:1. The invention shortens the development and testing time of the SNP marker, and reduces the detection cost of the marker.
Owner:SHANGHAI JIAO TONG UNIV
Prediction-based distributed parallel simulation method
InactiveUS8781808B2Reduce verification timeImprove verification efficiencyDigital data processing detailsAnalogue computers for electric apparatusParallel simulationEquivalent model
The simulation consists of a front-end simulation and a back-end simulation. The front-end simulation can use an equivalent model at different abstraction level, or a simulation model for the back-end simulation. The back-end simulation uses the simulation result of front-end simulation so that it can run one or more simulation runs sequentially or in parallel. Alternatively, models at lower level of abstraction are simulated together with a model at higher level of abstraction in parallel using two or more simulators.
Owner:YANG SEI YANG
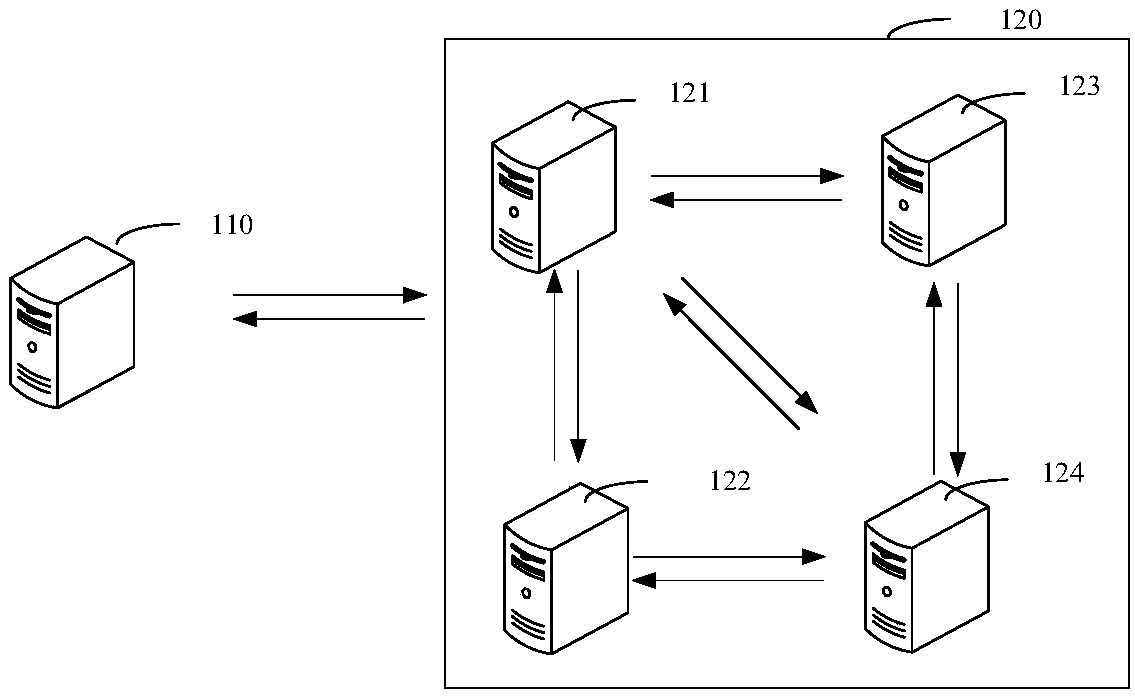
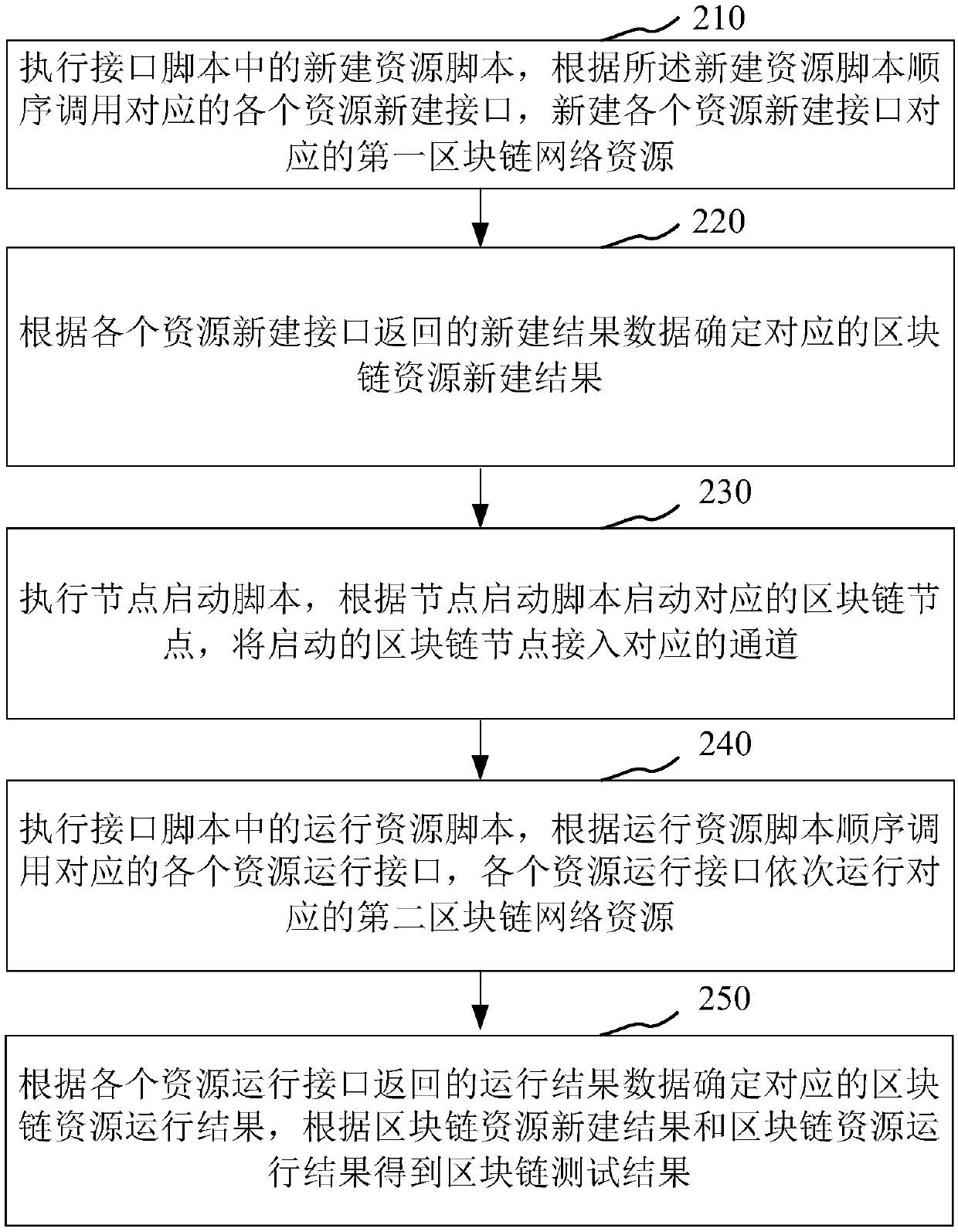
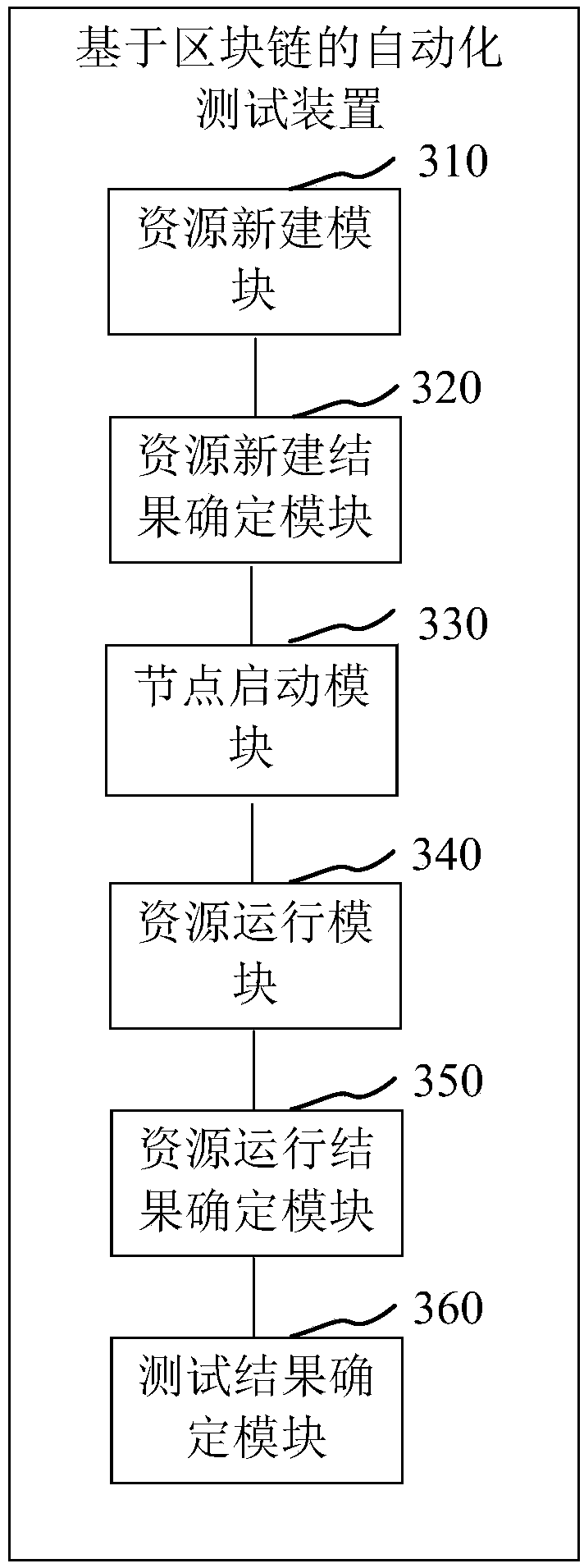
Block-chain-based automated test method and apparatus, computer device and storage medium
PendingCN109542767AQuickly verify feature availabilityReduce verification timeSoftware testing/debuggingEnergy efficient computingChain systemChain network
The invention relates to a block chain, which provides a block-chain-based automatic test method and apparatus, , a computer device and a storage medium. The method comprises the following steps: executing a new resource script in an interface script, sequentially calling corresponding resources to create new interfaces, and creating first block chain network resources corresponding to each resource to create new interfaces; determining a corresponding block chain resource creation result according to the returned creation result data; executing a node start script, starting a corresponding block chain node according to the node start script, and accessing the started block chain node into a corresponding channel; executing a running resource script in the interface script, sequentially calling corresponding resource running interfaces, and sequentially running corresponding second block chain network resources; according to the running result data returned by each resource running interface, determining the block chain resource running result is determined, and obtaining the block chain test result according to the block chain resource building result and the block chain resourcerunning result, which can quickly verify the functional usability of the block chain system.
Owner:PING AN TECH (SHENZHEN) CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com