Realization method of end-to-end voice encryption system based on 3G/B3G
A voice encryption and implementation method technology, applied in user identity/authority verification, key distribution, can solve problems such as not supporting encrypted voice communication, achieve the effect of reducing deployment cost and complexity, and ensuring communication process security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0044] Basic embodiments of the invention will be described in detail below with reference to the accompanying drawings, examples of which are shown. Wherever possible, the same reference numbers will be used throughout the drawings to refer to the same or like parts.
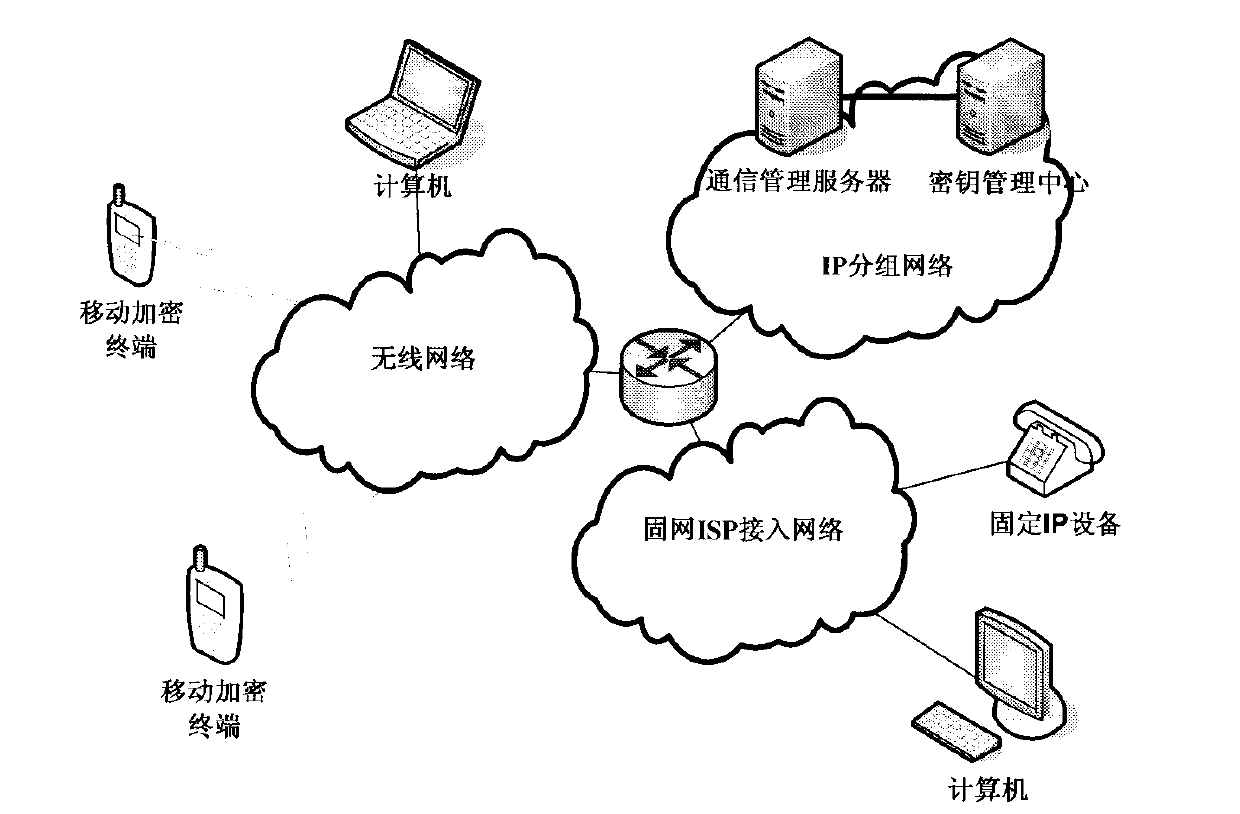
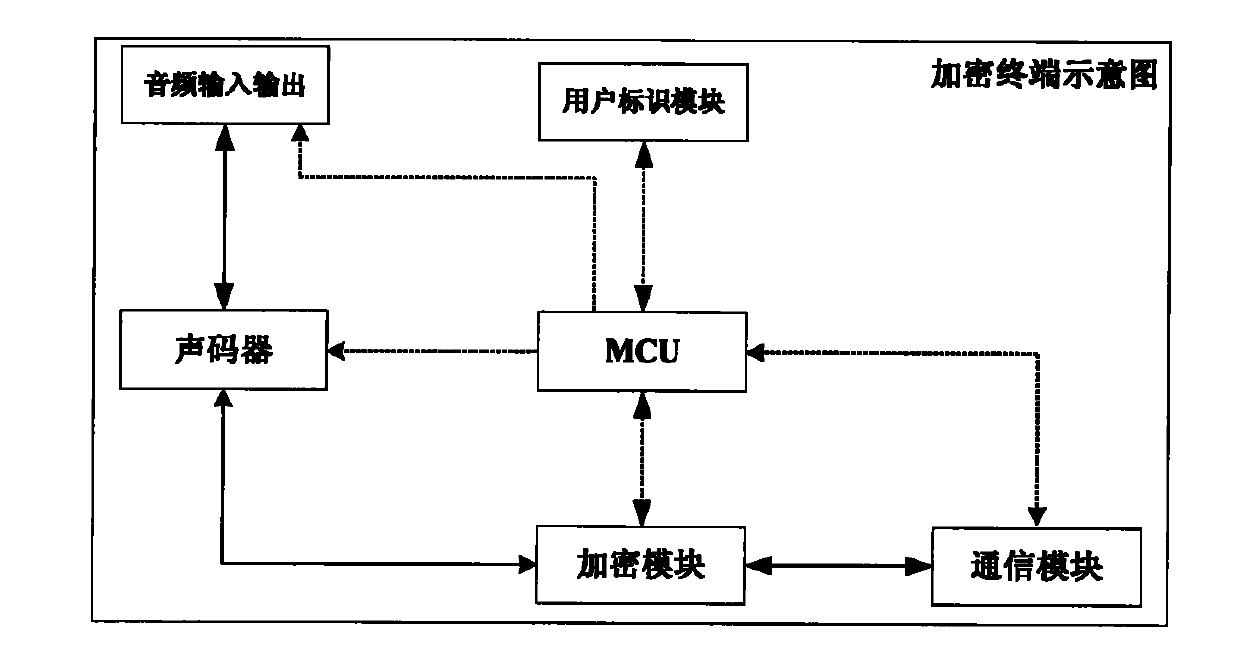
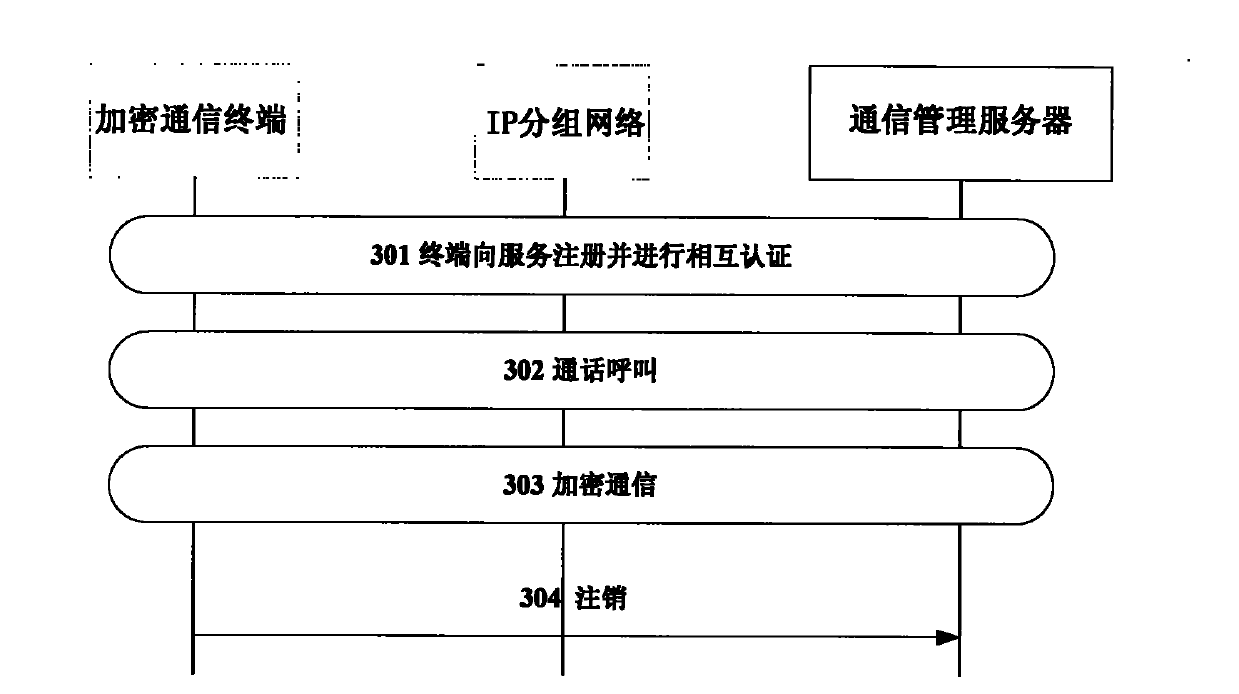
[0045] The invention is a realization method of an end-to-end voice encryption system based on 3G / B3G, which mainly includes processes such as user registration, call and communication, and communication cancellation, including key management functions.
[0046] After obtaining the ability to access the packet network, various terminals initiate registration with the CMS, and the CMS records the current user's IP address and port number, and registers its status. After registration, encrypted communication requests to registered users can be initiated at any time. At the same time, the registered terminal regularly sends a status message to the CMS, including the user ID, etc., so that the CMS considers the us...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com