Method for end-to-end enciphoring voice telecommunication
A technology for encrypting voice and encryption keys, applied in wireless communication, synchronous sending/receiving encryption equipment, security devices, etc., can solve problems such as technical decryption, and achieve flexible, safe and reliable voice communication, and powerful effects.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0063] Embodiment 1: Implement encrypted voice communication between mobile terminals.
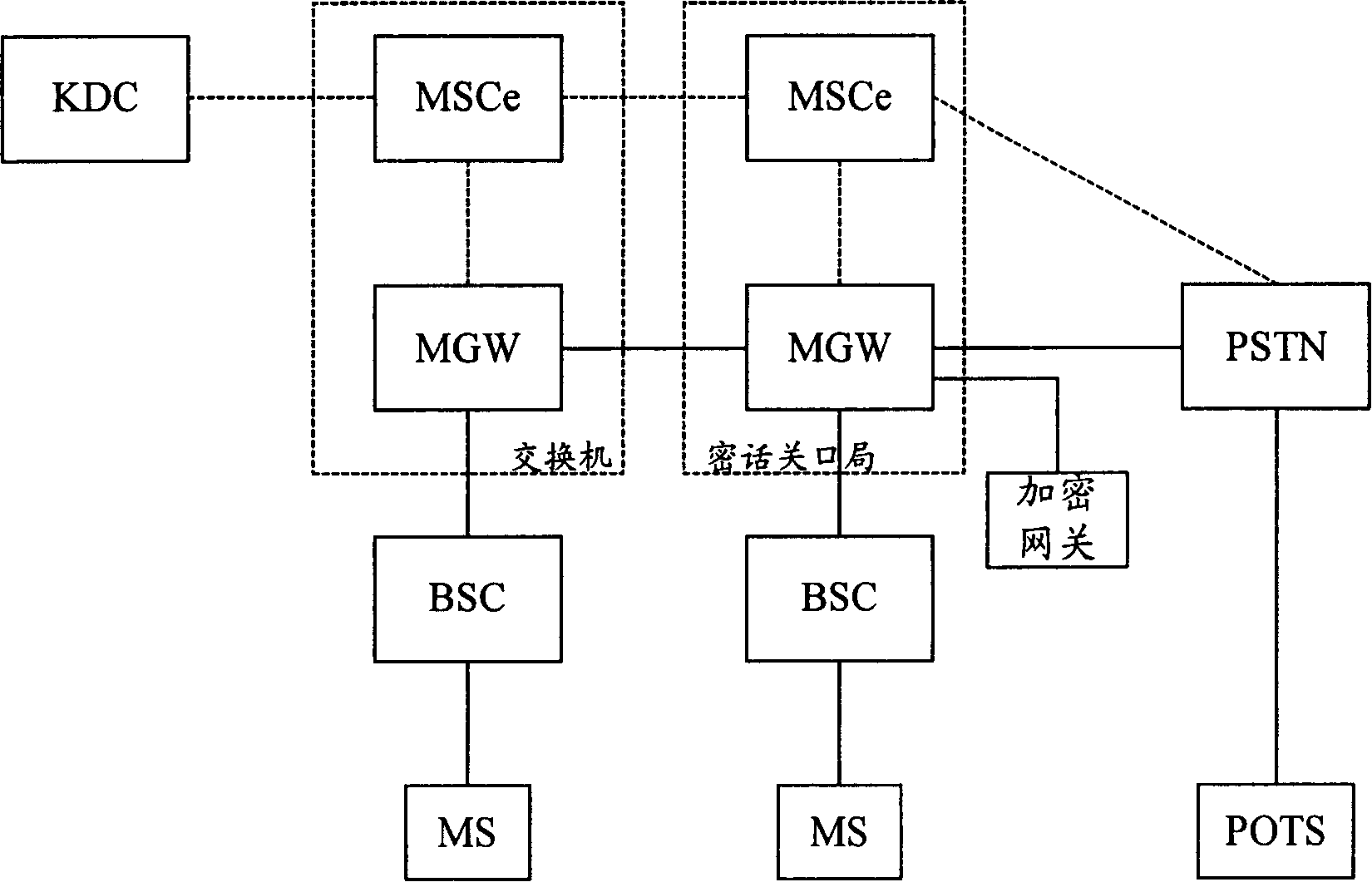
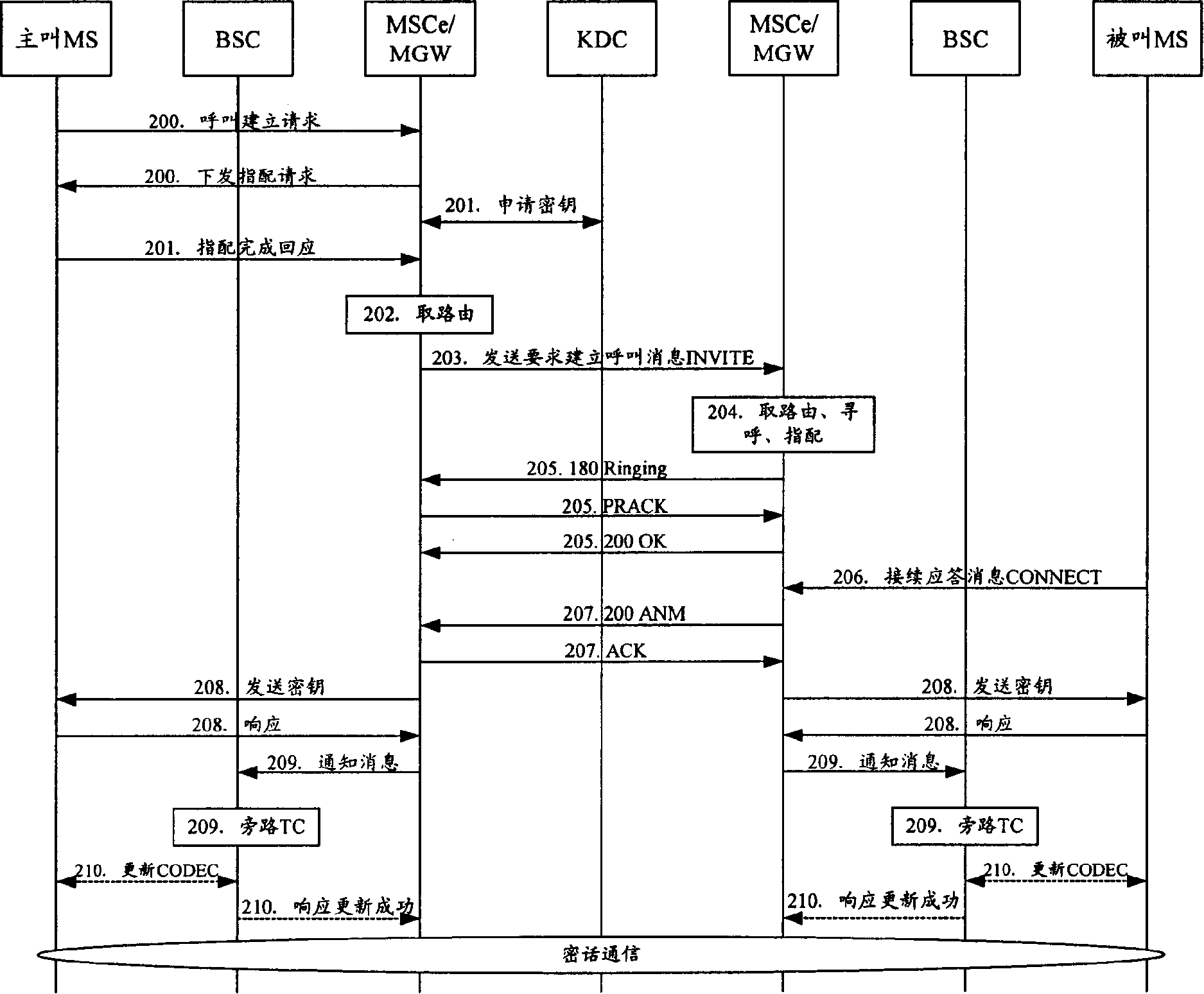
[0064] figure 2 It is a flowchart of encrypted voice communication between mobile terminals in the present invention. It is assumed that both the calling MS and the called MS have passed the encryption qualification authentication at KDC, that is, KDC authentication, and each transmission branch in the voice transmission path from the calling MS to the called MS The segments are transmitted using different CODECs; the encrypted session trigger prefix is preset on the softswitch server of the network switching center, for example, the encrypted session trigger prefix is set to 19000, and the softswitch server of the network switching center starts using the encrypted session trigger prefix Secret communication. Encrypted voice communication between mobile terminals of the present invention comprises the following steps:
[0065] Step 200: The calling MS initiates an encrypted call re...
Embodiment 2
[0096] Embodiment 2: Encrypted voice communication is realized between the analog fixed telephone terminal and the mobile terminal, and the encrypted call request is initiated by the analog fixed telephone terminal.
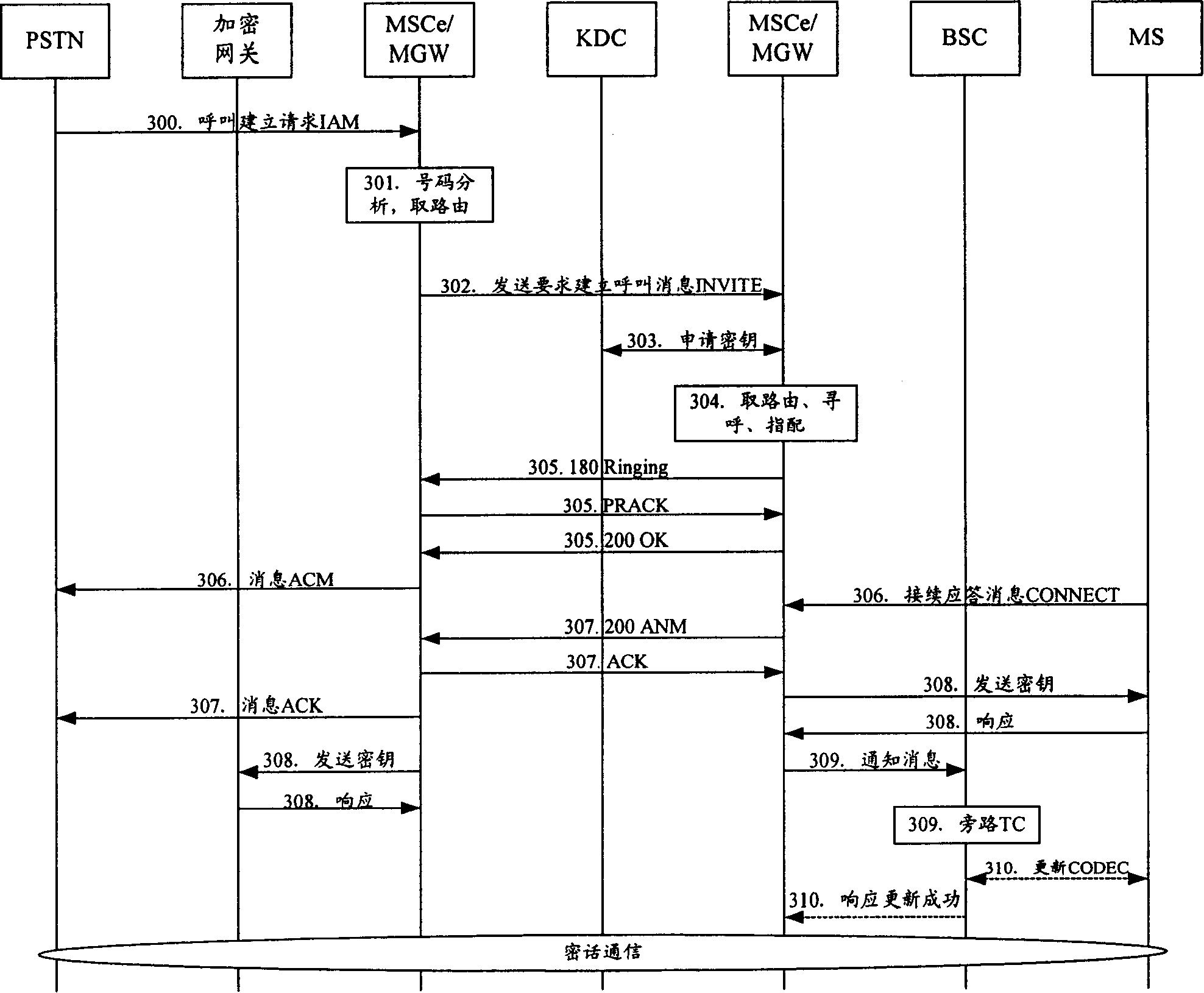
[0097] image 3 It is a flow chart of encrypted voice communication between an analog fixed phone terminal and a mobile terminal in which an encrypted call request is initiated by an analog fixed phone terminal in the present invention. It is assumed that the called MS passes the encrypted call qualification authentication in KDC and is connected with the encrypted call gateway office Each transmission segment in the voice transmission path to the called MS uses a different CODEC for transmission; the encrypted voice trigger prefix is preset on the softswitch server of the encrypted voice gateway office, for example, the encrypted voice trigger prefix is set to 19000. In the present invention, the encrypted voice communication between the simulated fixed tele...
Embodiment 3
[0130] Embodiment 3: Encrypted voice communication is realized between the mobile terminal and the analog fixed telephone terminal, and the mobile terminal initiates an encrypted call request.
[0131] Figure 4 It is a flow chart of encrypted voice communication between the mobile terminal and the analog fixed telephone terminal in the present invention where the mobile terminal initiates an encrypted call request. It is assumed that the calling MS passes the encrypted call qualification authentication at the KDC, and the encryption gateway from the calling MS to the called POTS terminal is located. Each transmission segment in the voice transmission path uses a different CODEC for transmission; the encrypted conversation trigger prefix is preset on the softswitch server, for example, the encrypted conversation trigger prefix is set to 19000.
[0132] Figure 4 The process in the embodiment is composed of the mobile terminal triggering the encrypted call process in the f...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com