Patents
Literature
38 results about "Dynamic program analysis" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
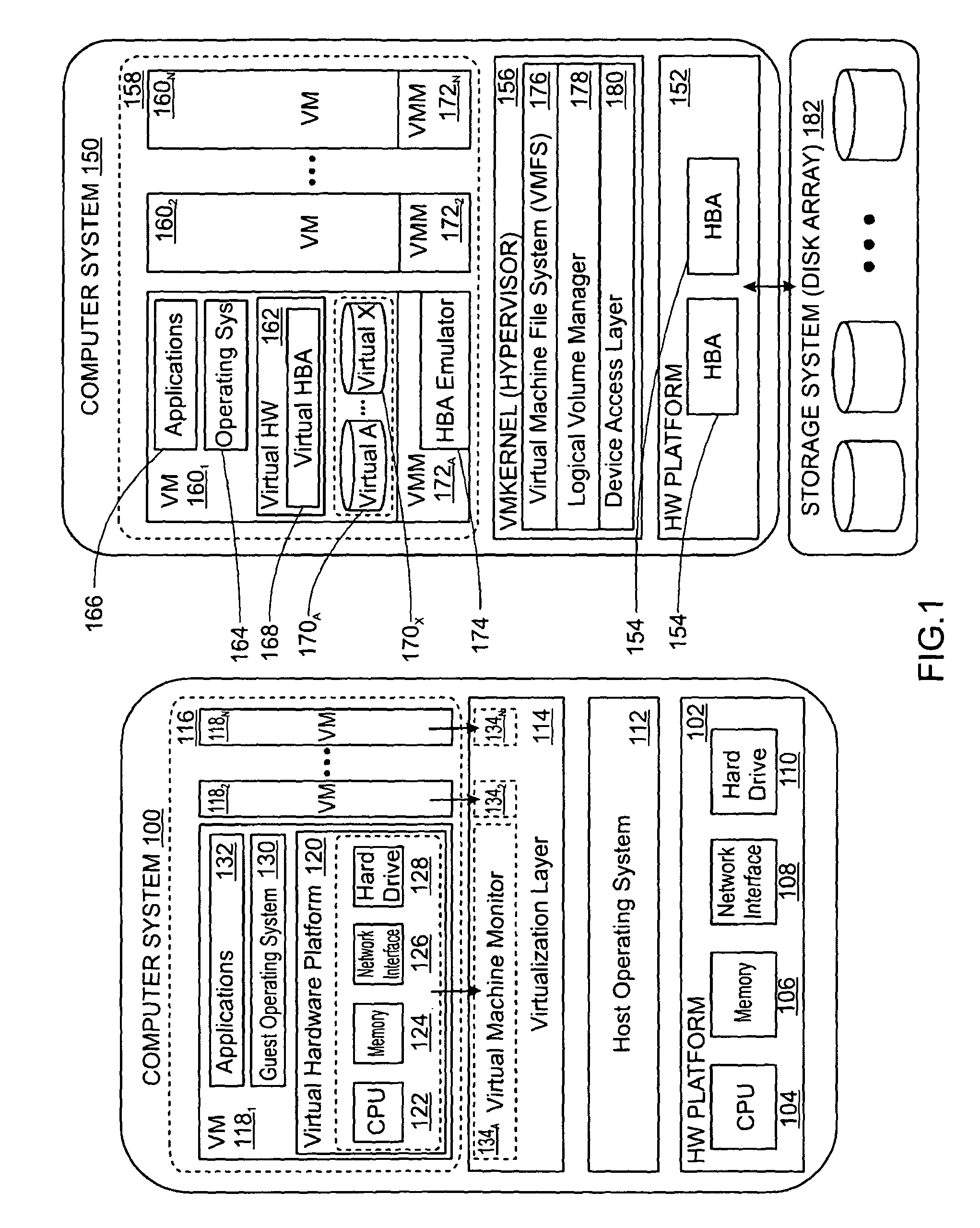
Dynamic program analysis is the analysis of computer software that is performed by executing programs on a real or virtual processor. For dynamic program analysis to be effective, the target program must be executed with sufficient test inputs to cover almost all possible outputs. Use of software testing measures such as code coverage helps ensure that an adequate slice of the program's set of possible behaviors has been observed. Also, care must be taken to minimize the effect that instrumentation has on the execution (including temporal properties) of the target program. Dynamic analysis is in contrast to static program analysis. Unit tests, integration tests, system tests and acceptance tests use dynamic testing.
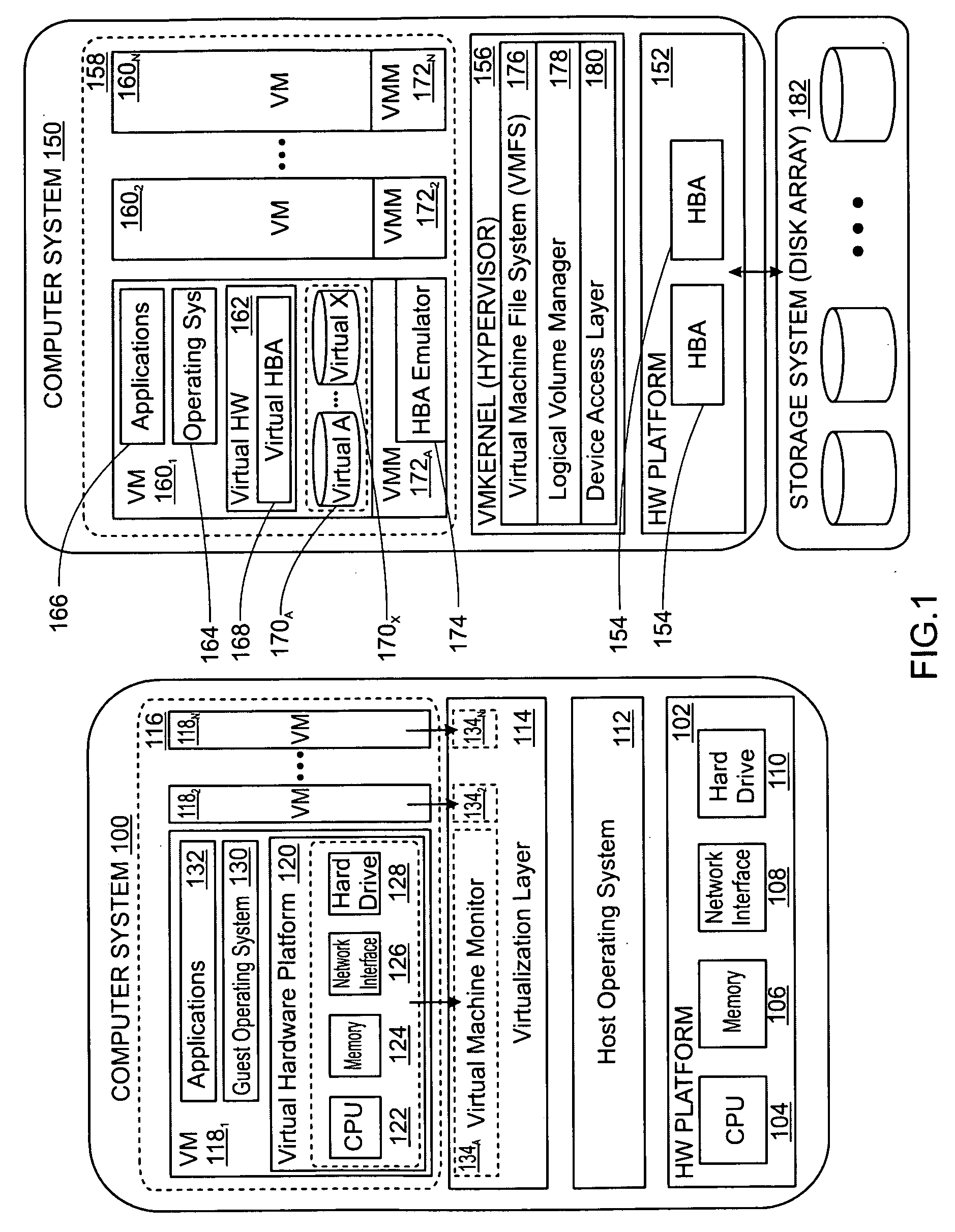
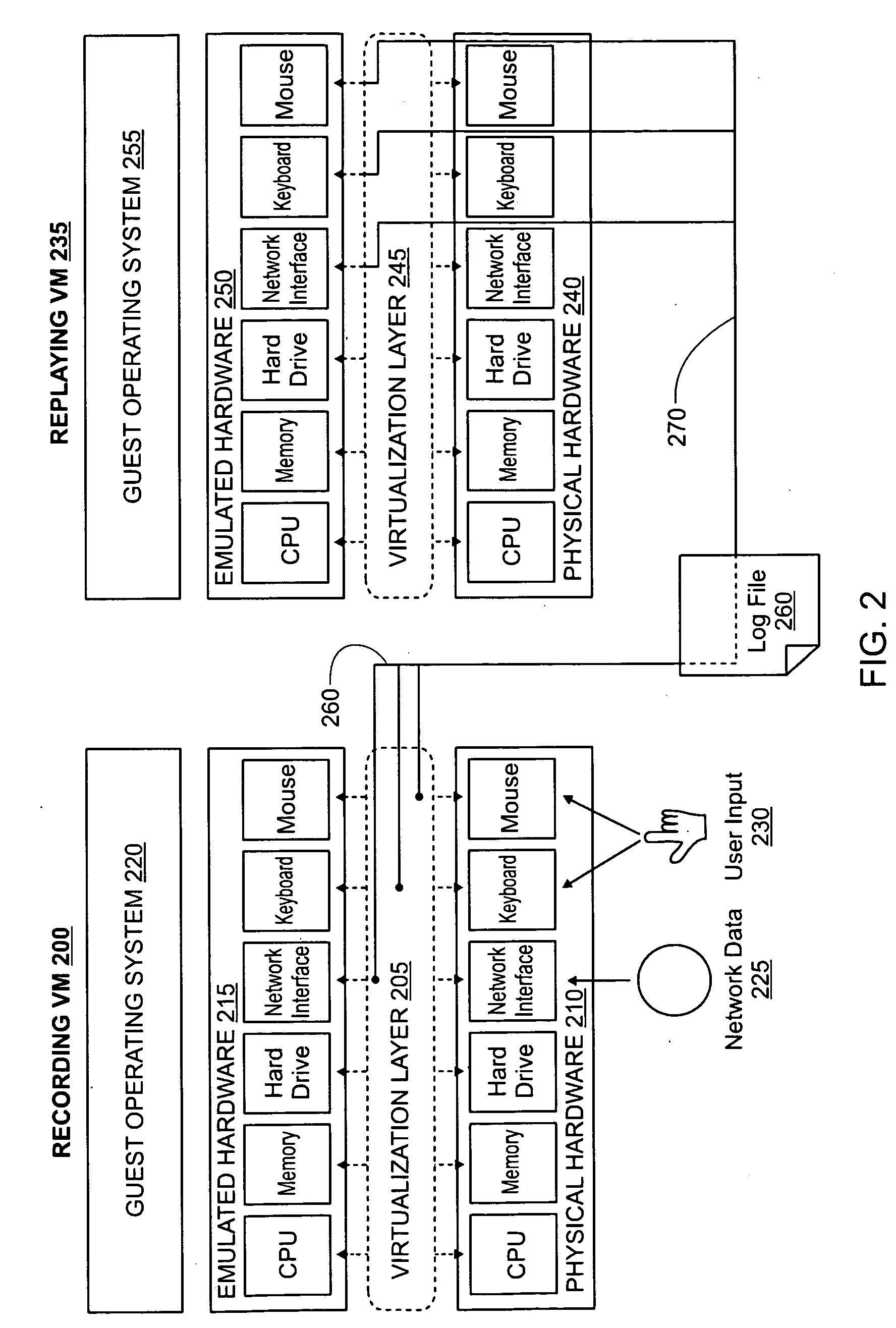
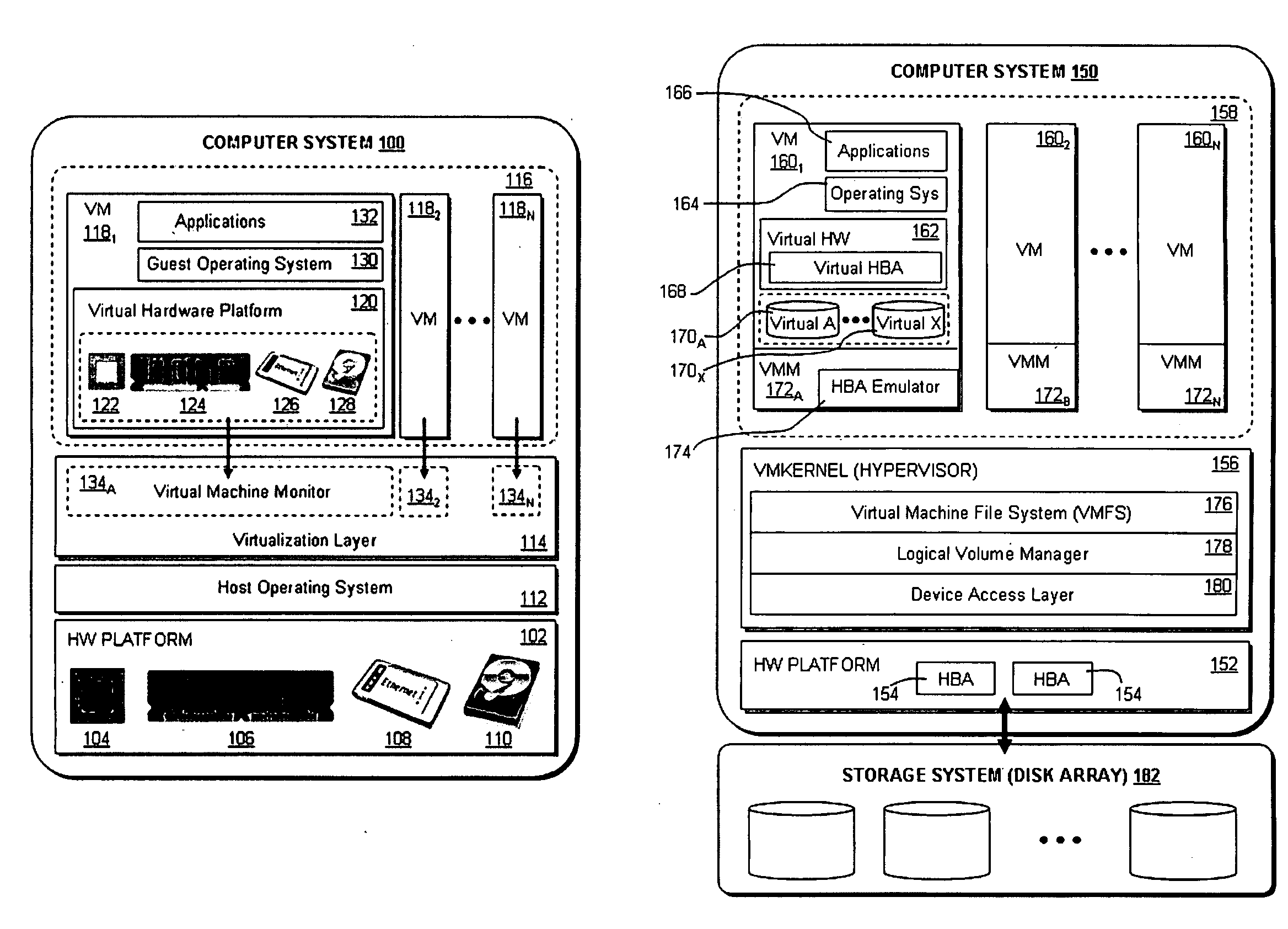
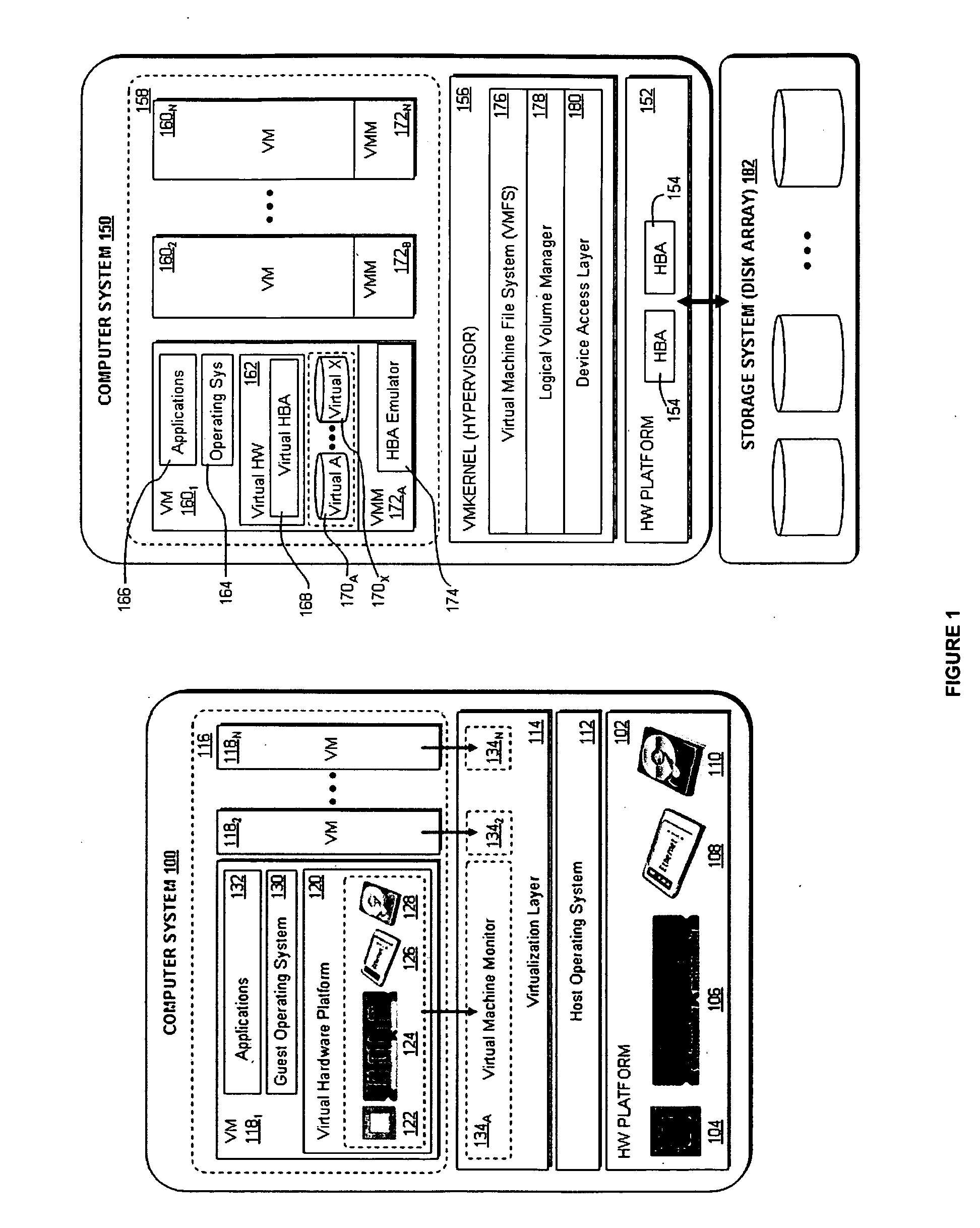
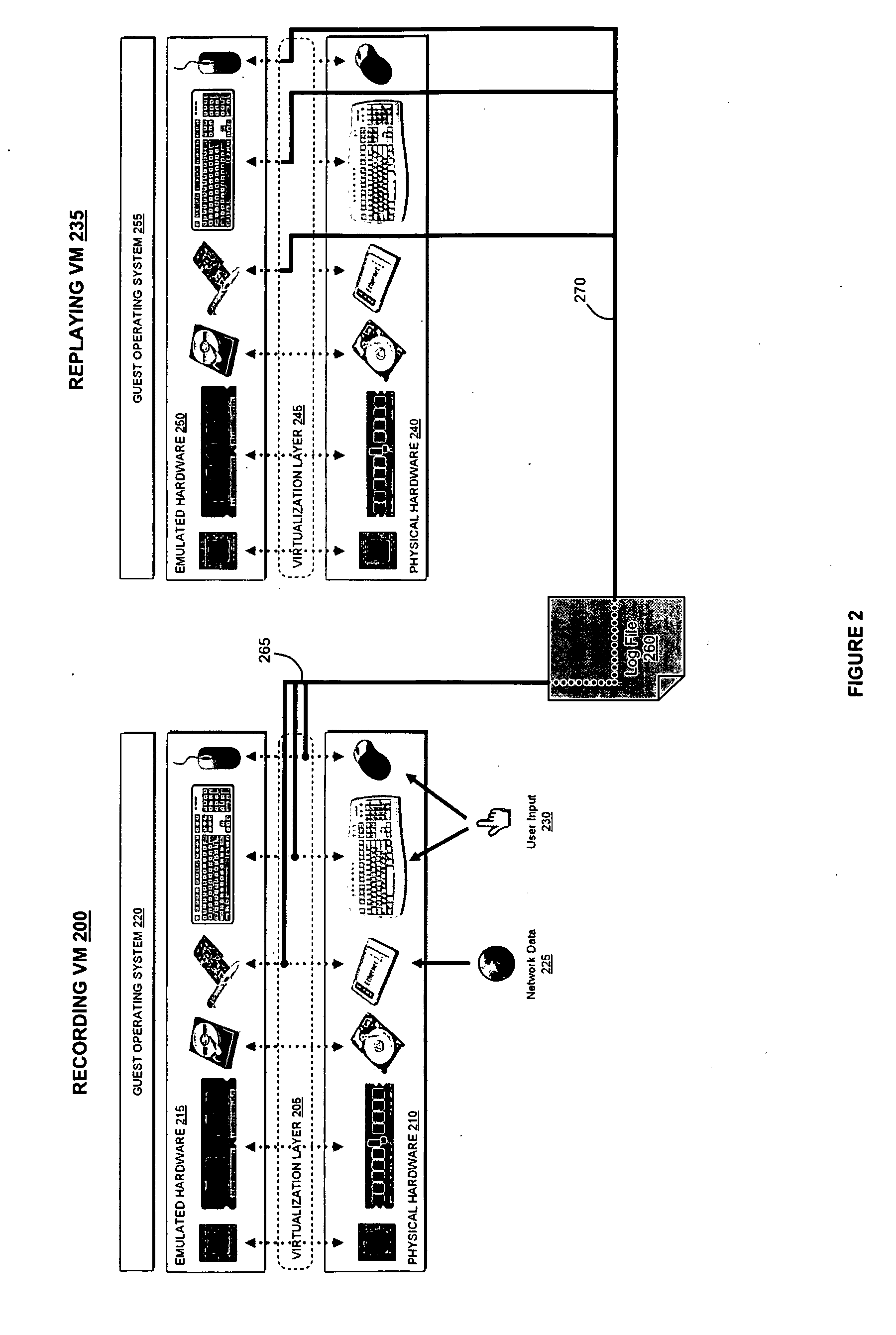
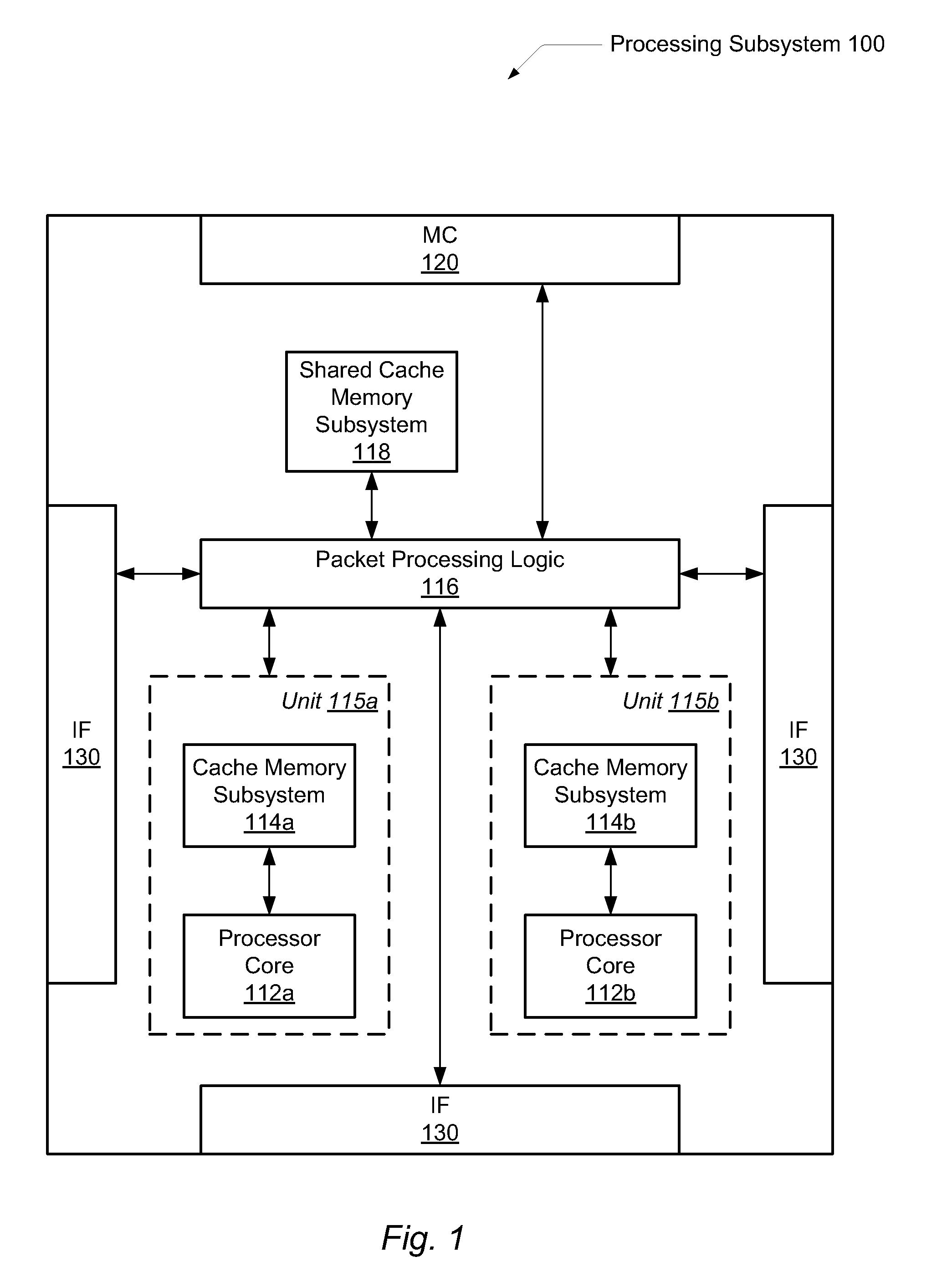
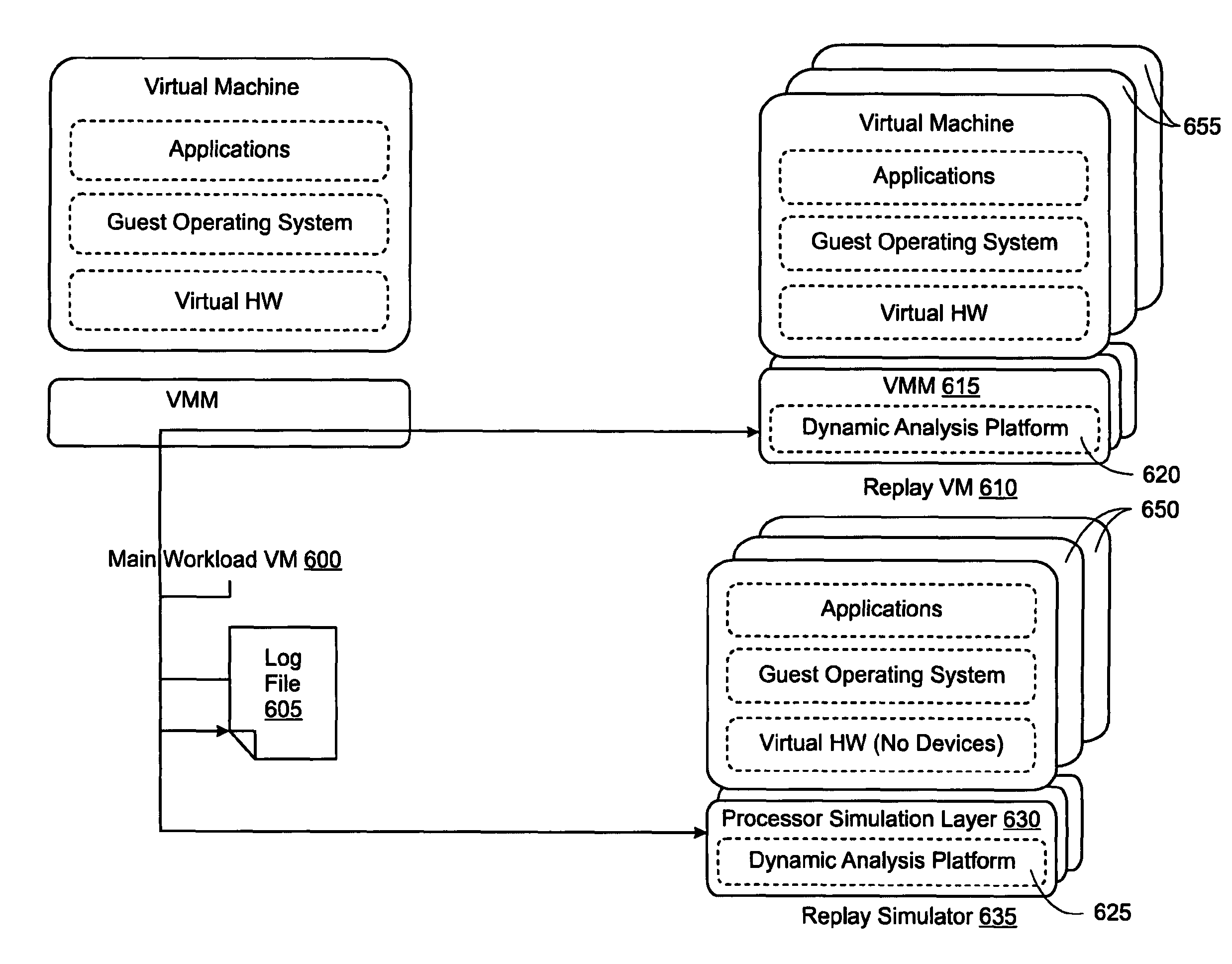
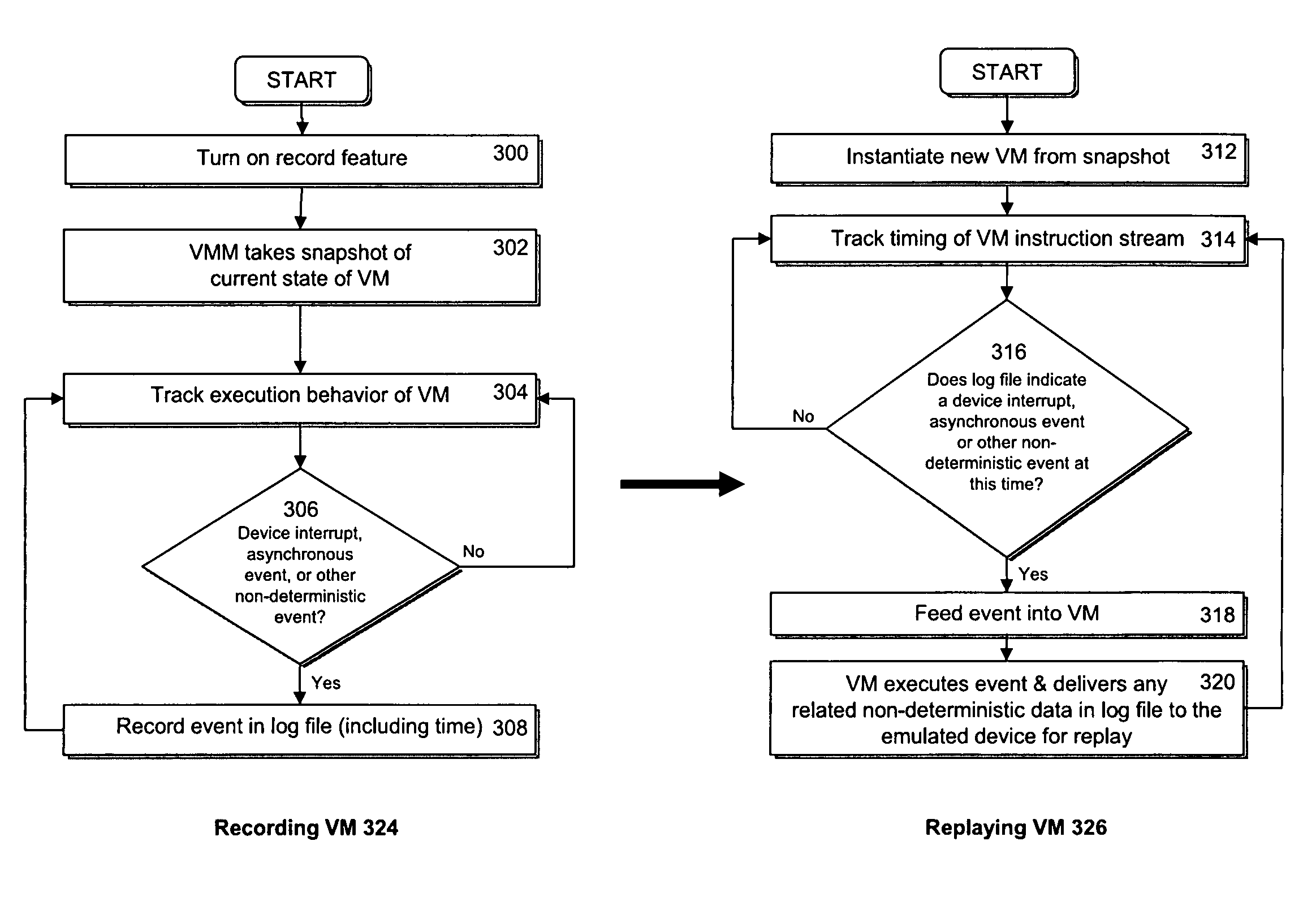
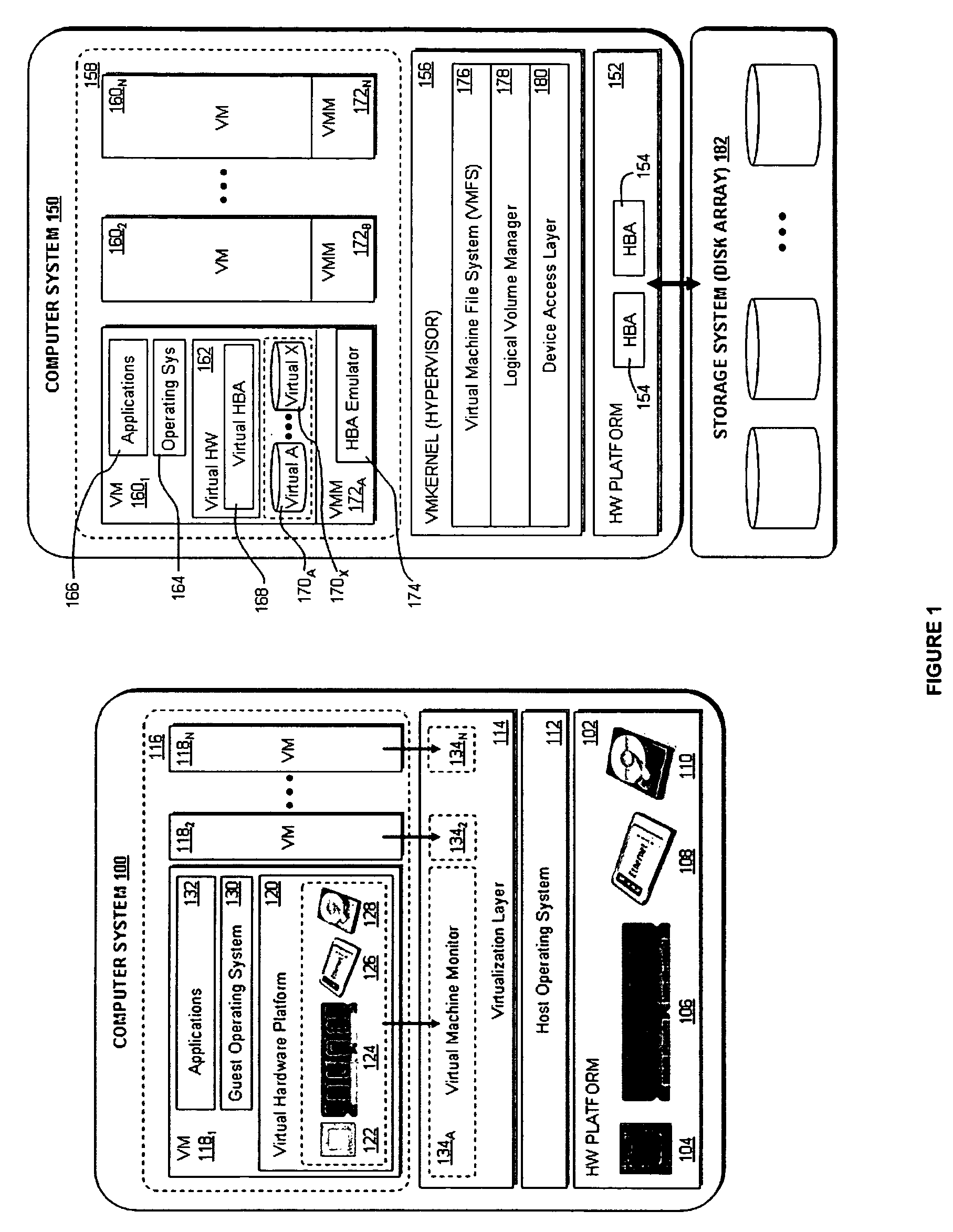
Accelerating replayed program execution to support decoupled program analysis
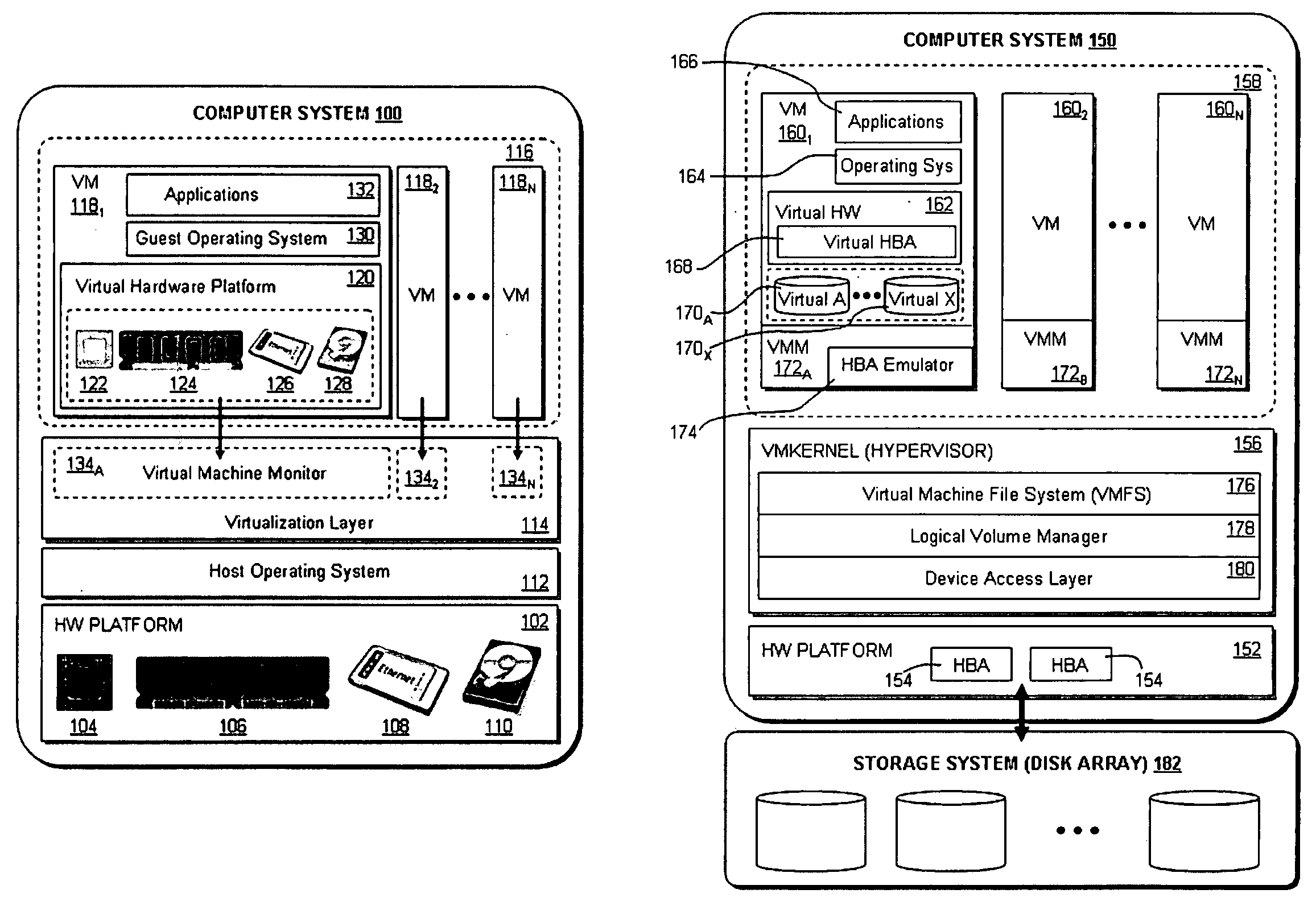
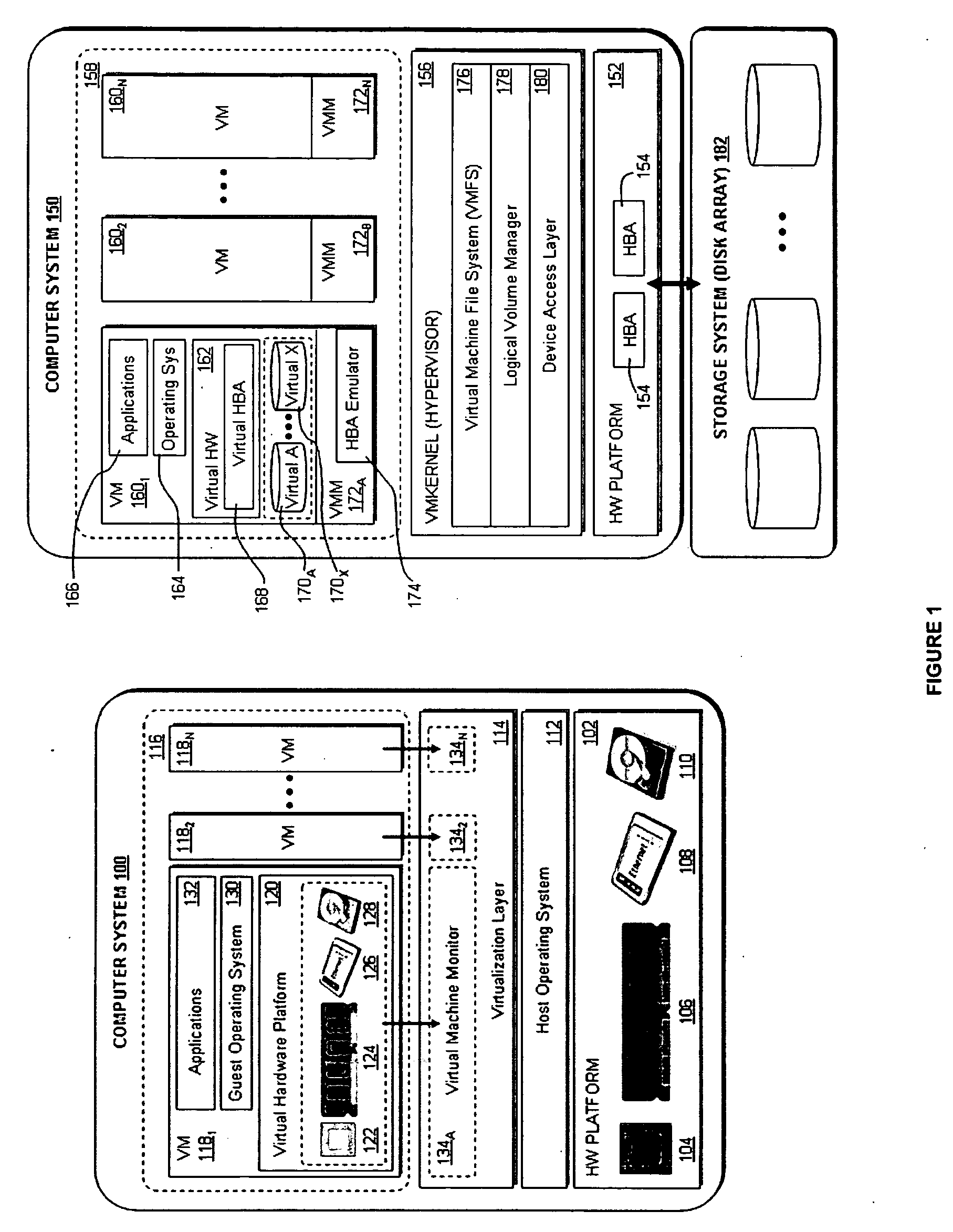
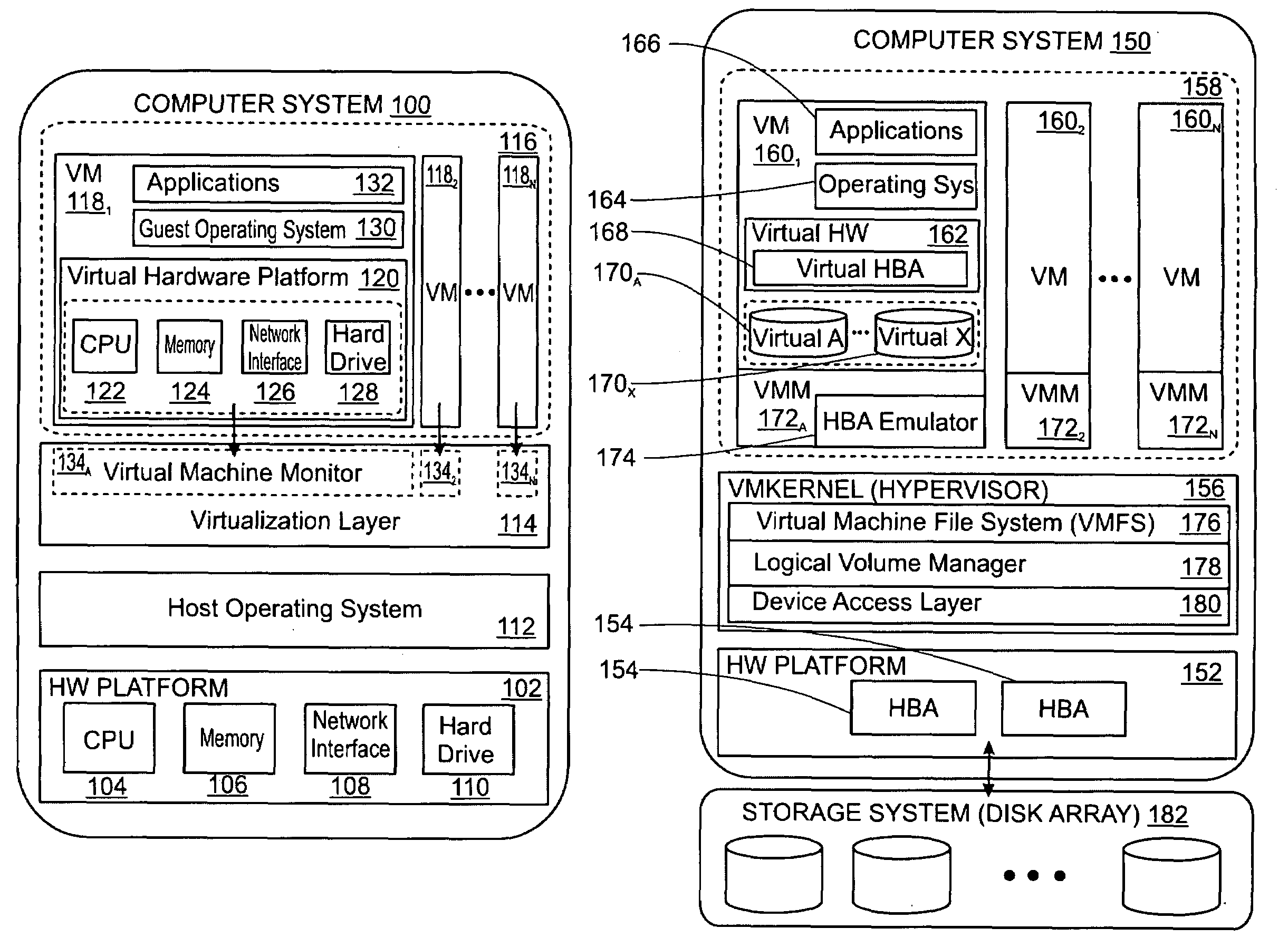
ActiveUS20090320011A1Error detection/correctionProgram controlDynamic program analysisVirtual machine
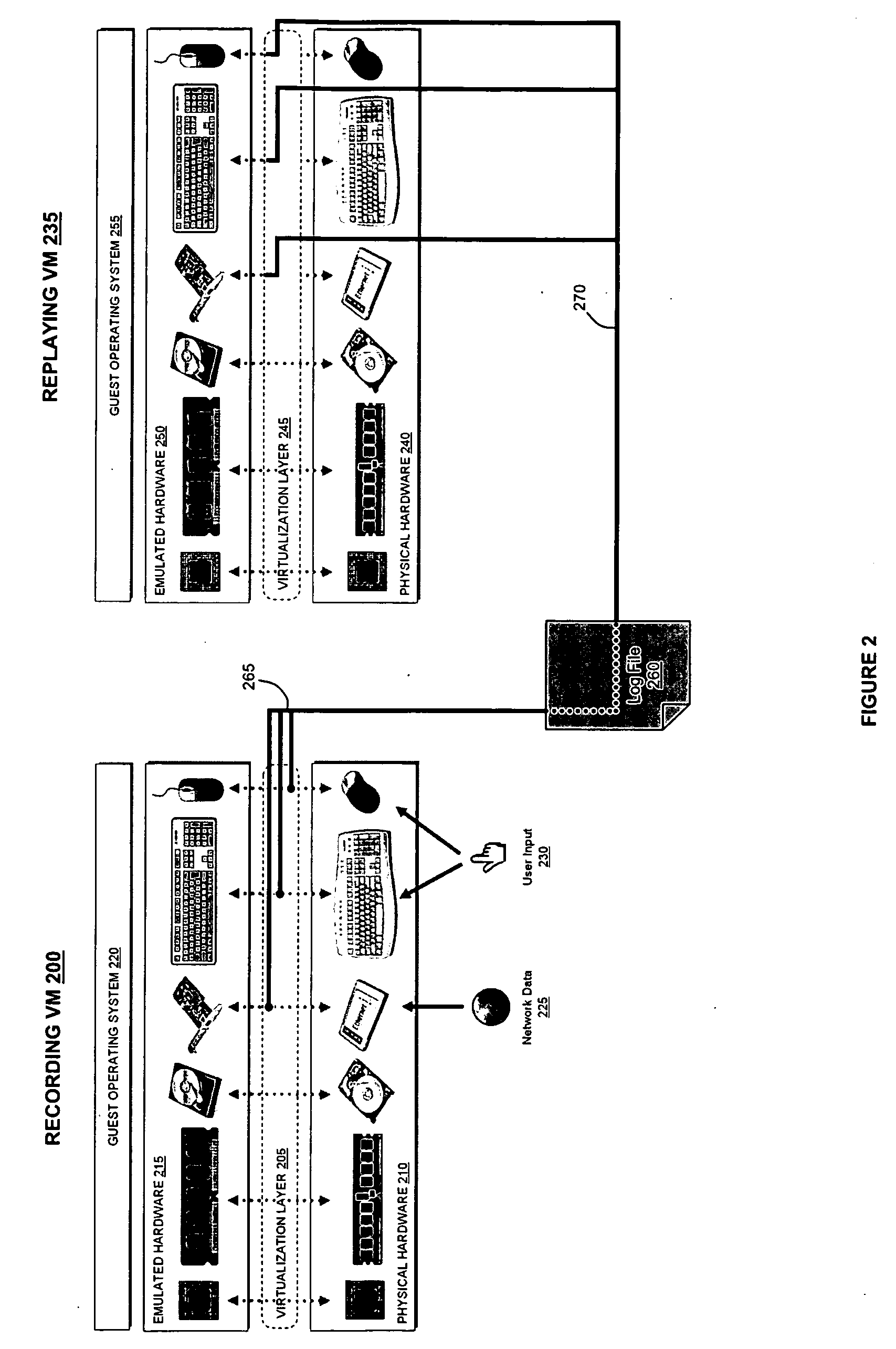
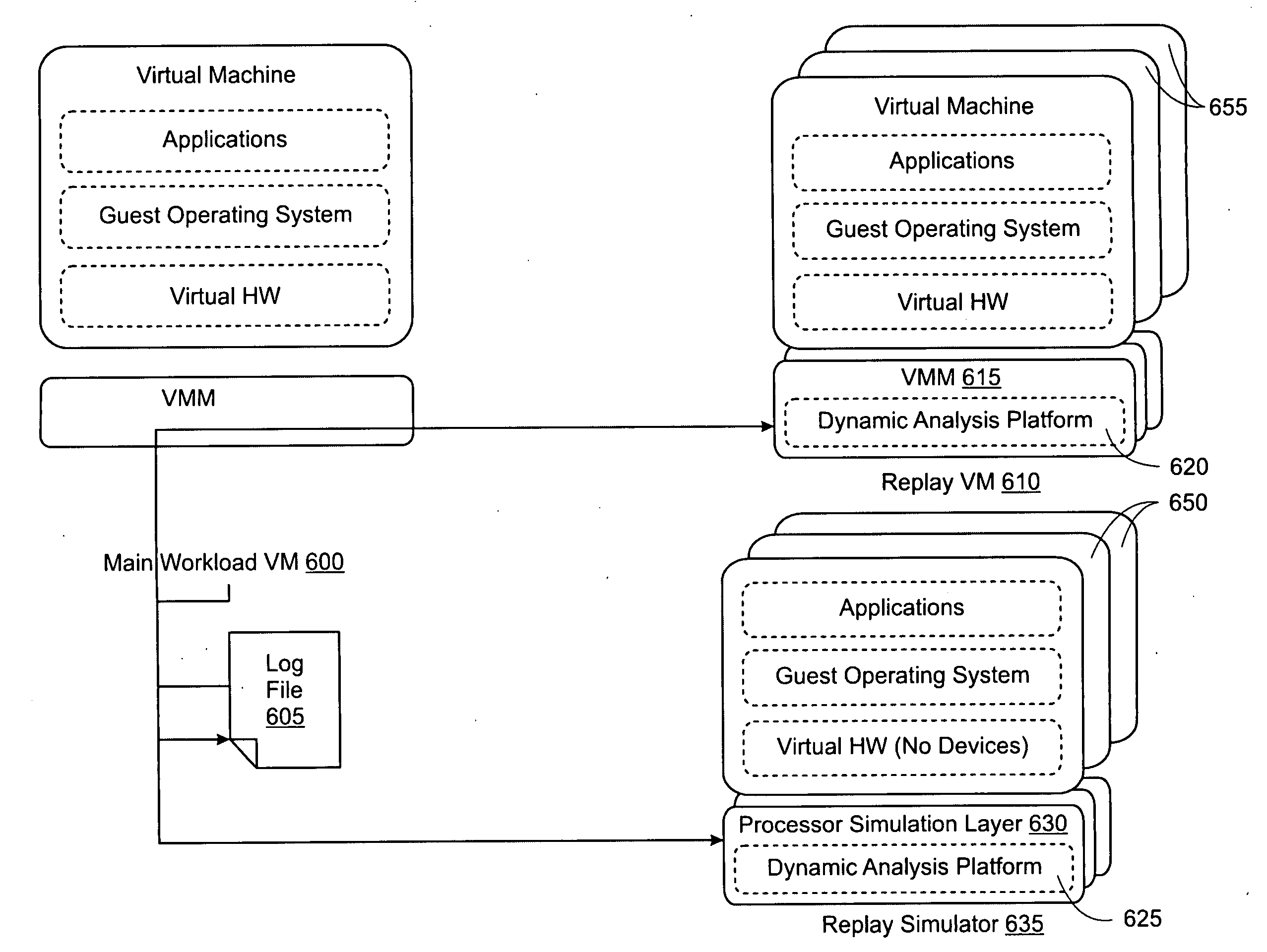
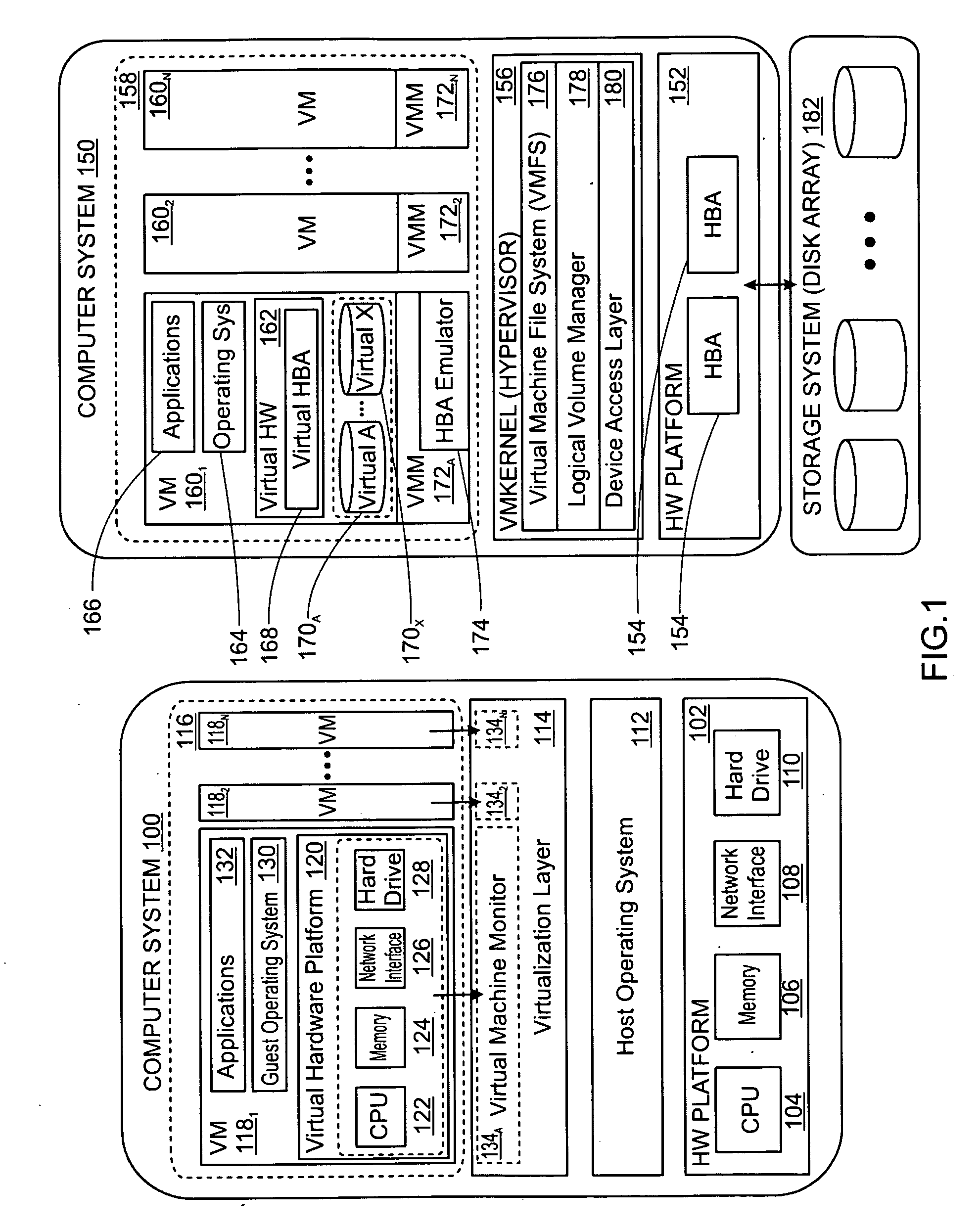
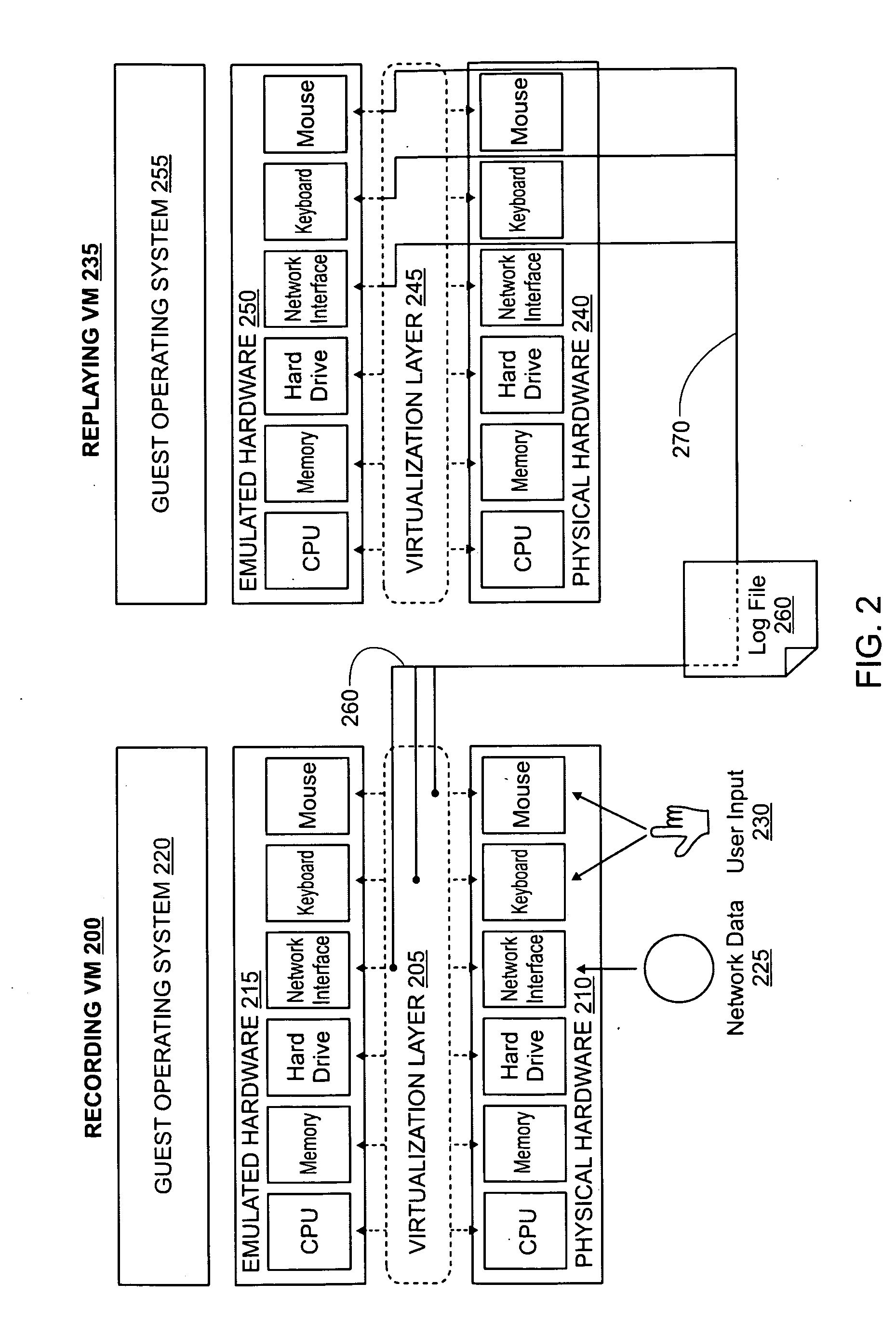
A virtual machine system decouples dynamic program analysis from program execution. Program analysis is decoupled from program execution through the use of a virtual machine to record program execution and an analysis platform to replay and analyze the program execution. Optimization techniques are applied to prevent the analysis platform from falling too far behind the program execution platform during replay.
Owner:VMWARE INC
Synchronous decoupled program analysis in virtual environments
ActiveUS20090320010A1Error detection/correctionProgram controlSoftware engineeringDynamic program analysis
Dynamic program analysis is decoupled from execution in virtual computer environments and is carried out synchronously with program execution. Decoupled dynamic program analysis is enabled by separating execution and analysis into two tasks: (1) recording, where system execution is recorded with minimal interference, and (2) analysis, where the execution is replayed and analyzed. Synchronous decoupled program analysis is enabled by suspending execution or data outputs of the program until a confirmation is received that the analysis is in sync with the program execution.
Owner:VMWARE INC
Detecting malicious software
ActiveUS8863288B1Memory loss protectionUnauthorized memory use protectionStatic timing analysisDynamic program analysis
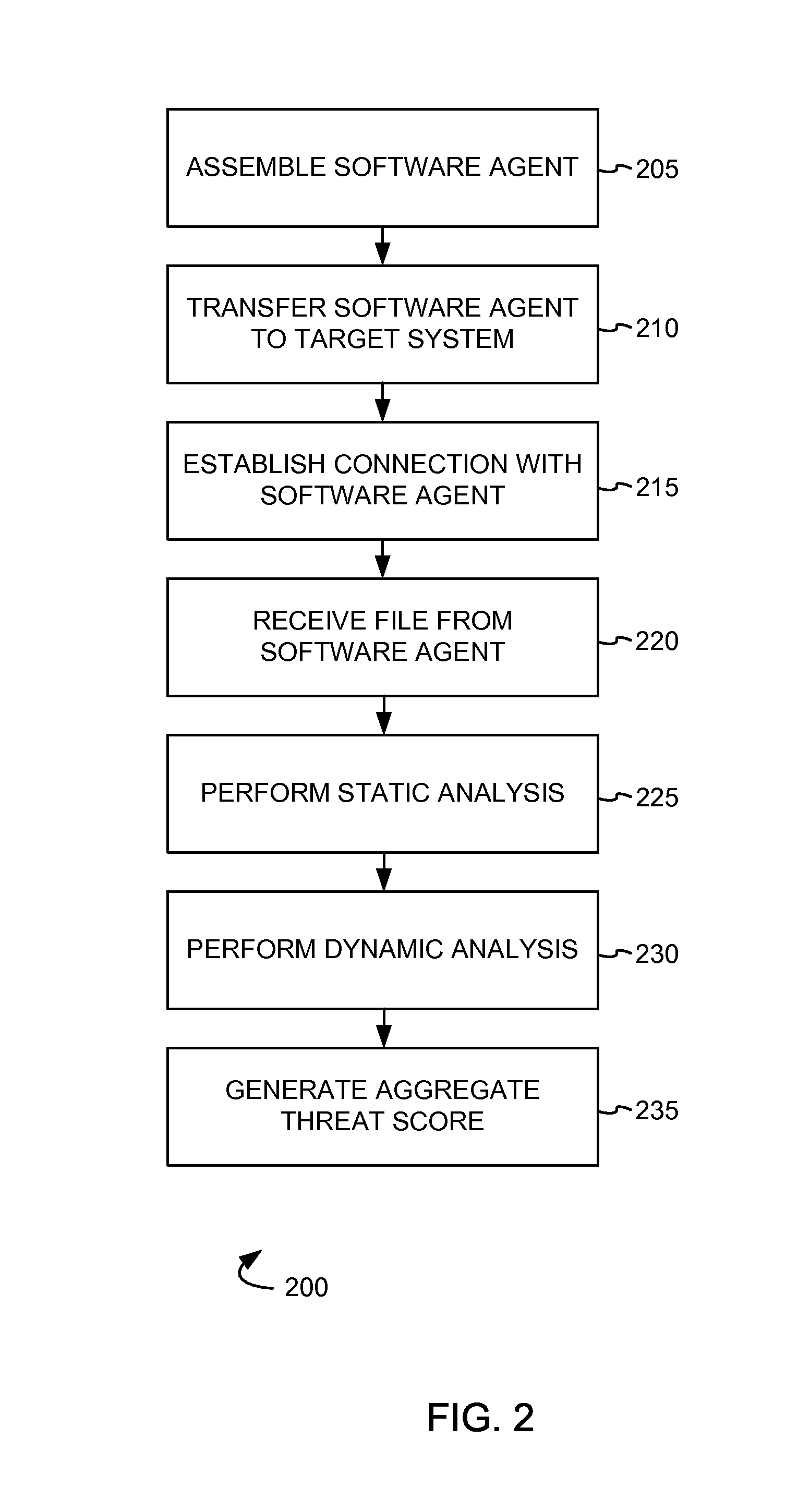
In systems and methods of detecting malicious software, a software agent comprising at least one scan module is assembled by a source system and is transferred by the source system to a target system. In response to a connection request from the software agent a connection is established to the software agent and a file is received from the target system. At the source system, a static analysis is performed on the transferred file to generate a static threat score, and a dynamic analysis is performed to generate a dynamic threat score. Based on the static threat score and the dynamic threat score an aggregate threat score is generated for the transferred file.
Owner:MANTECH ADVANCED SYST INT
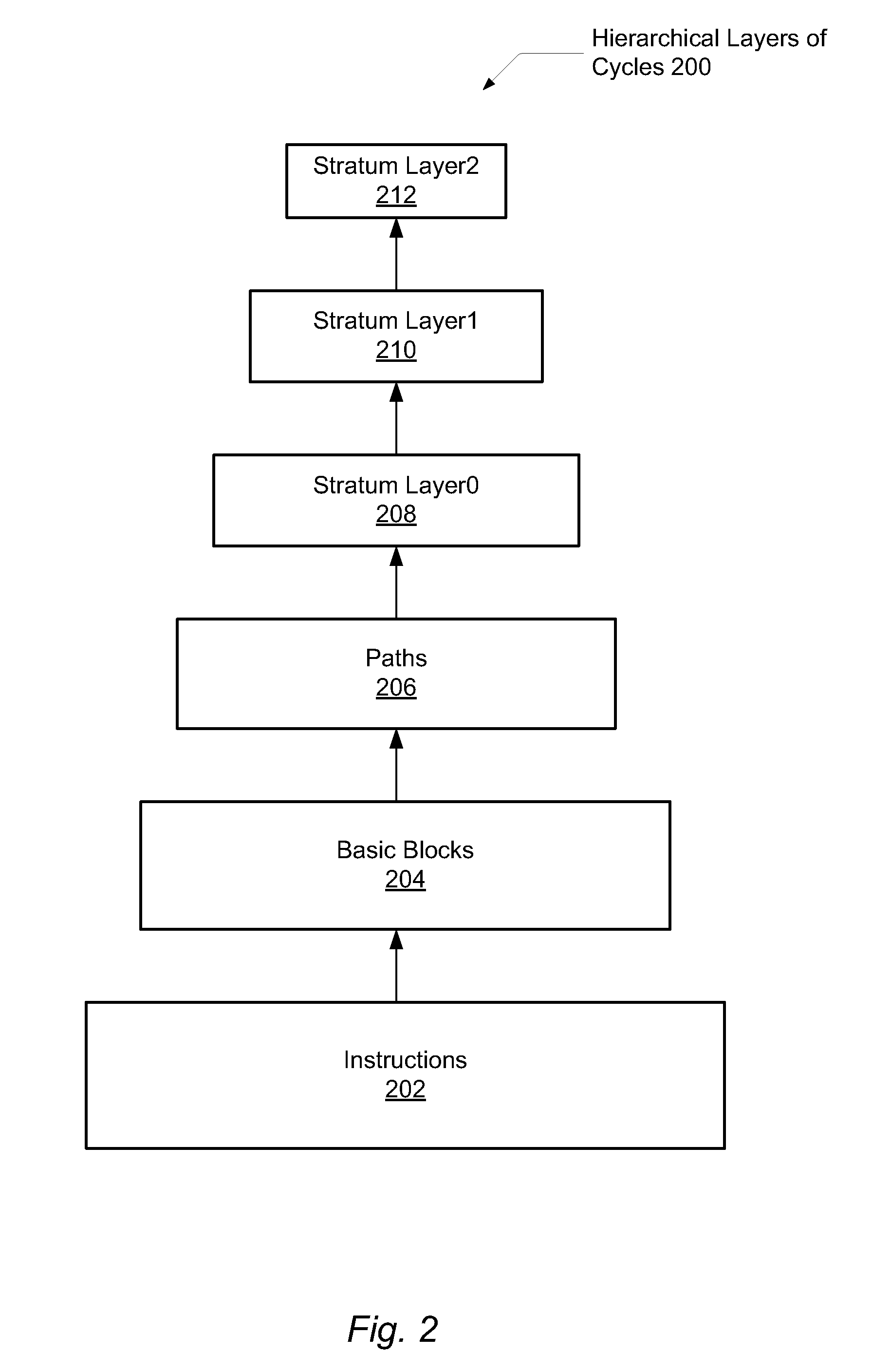
System for dynamic program profiling
InactiveUS20100115494A1Error detection/correctionSpecific program execution arrangementsProgram profileDynamic program analysis
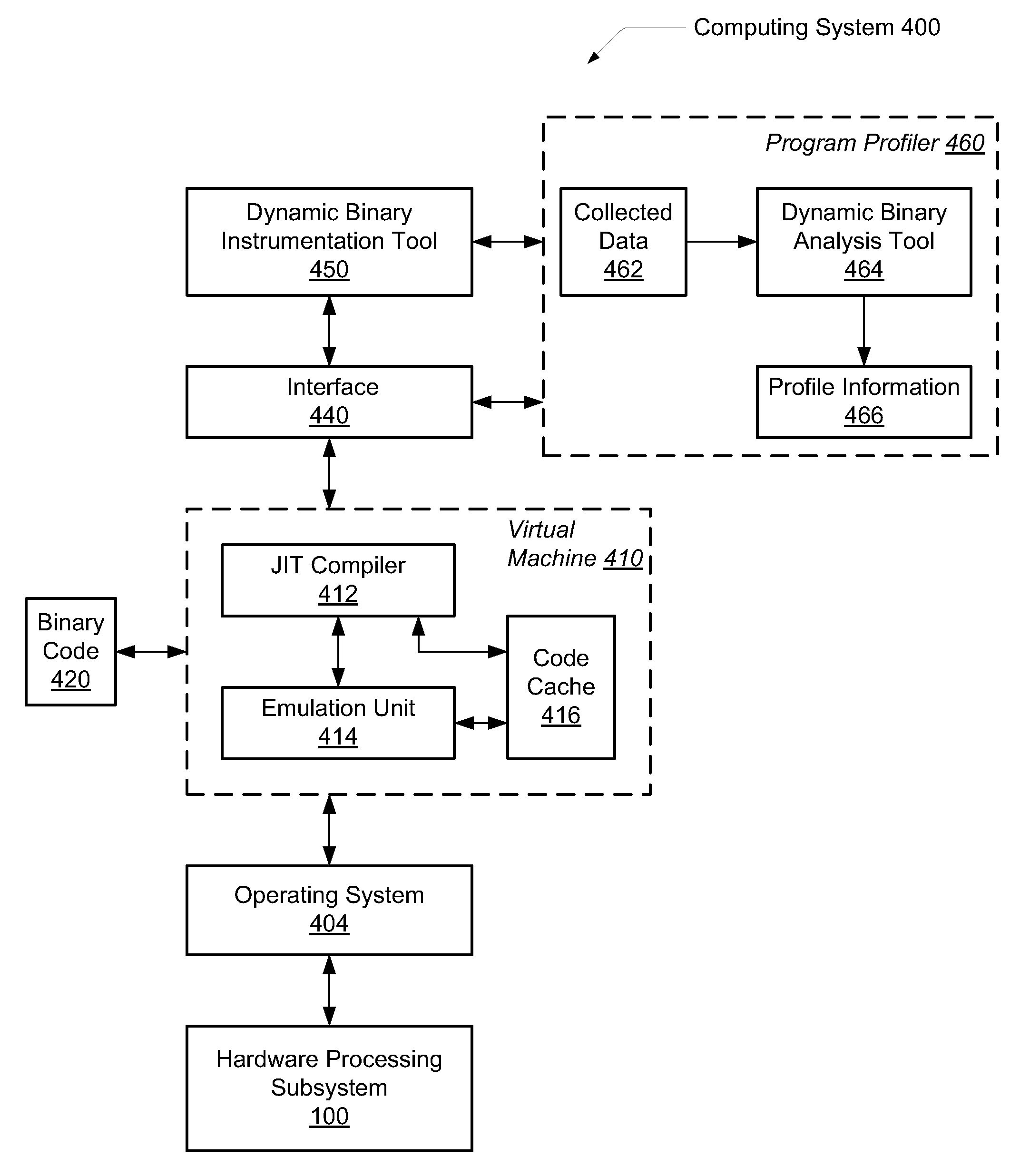
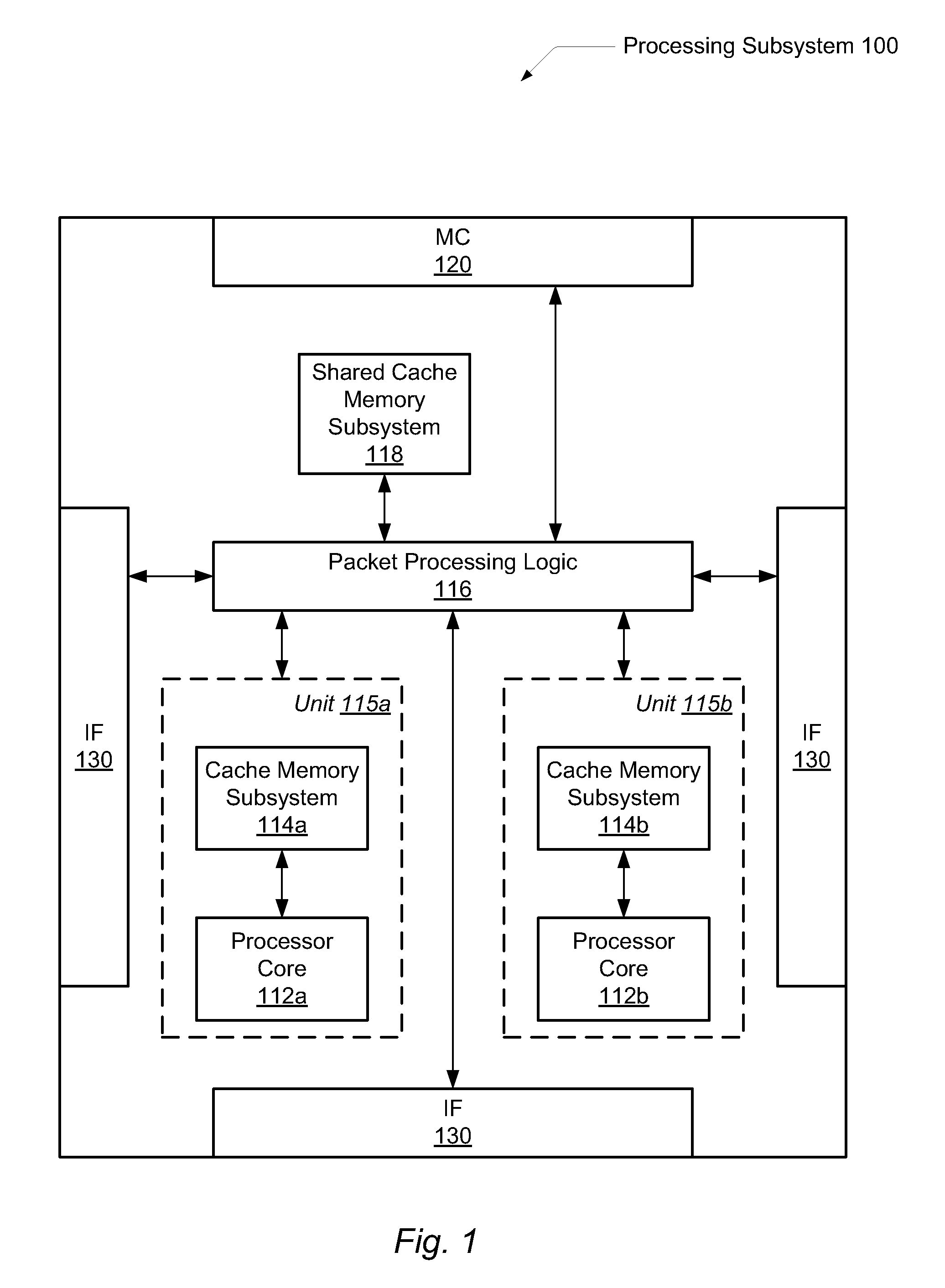
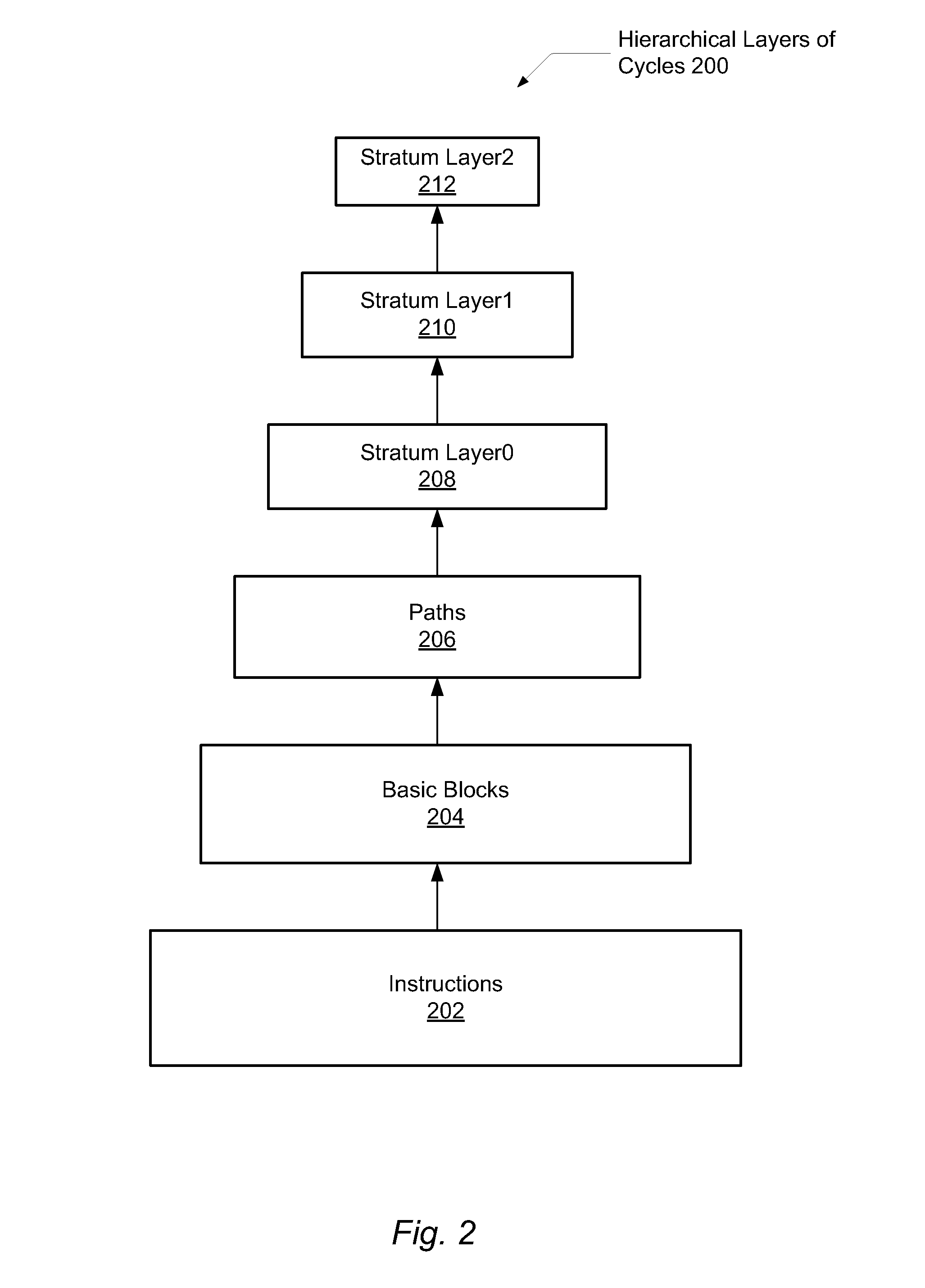
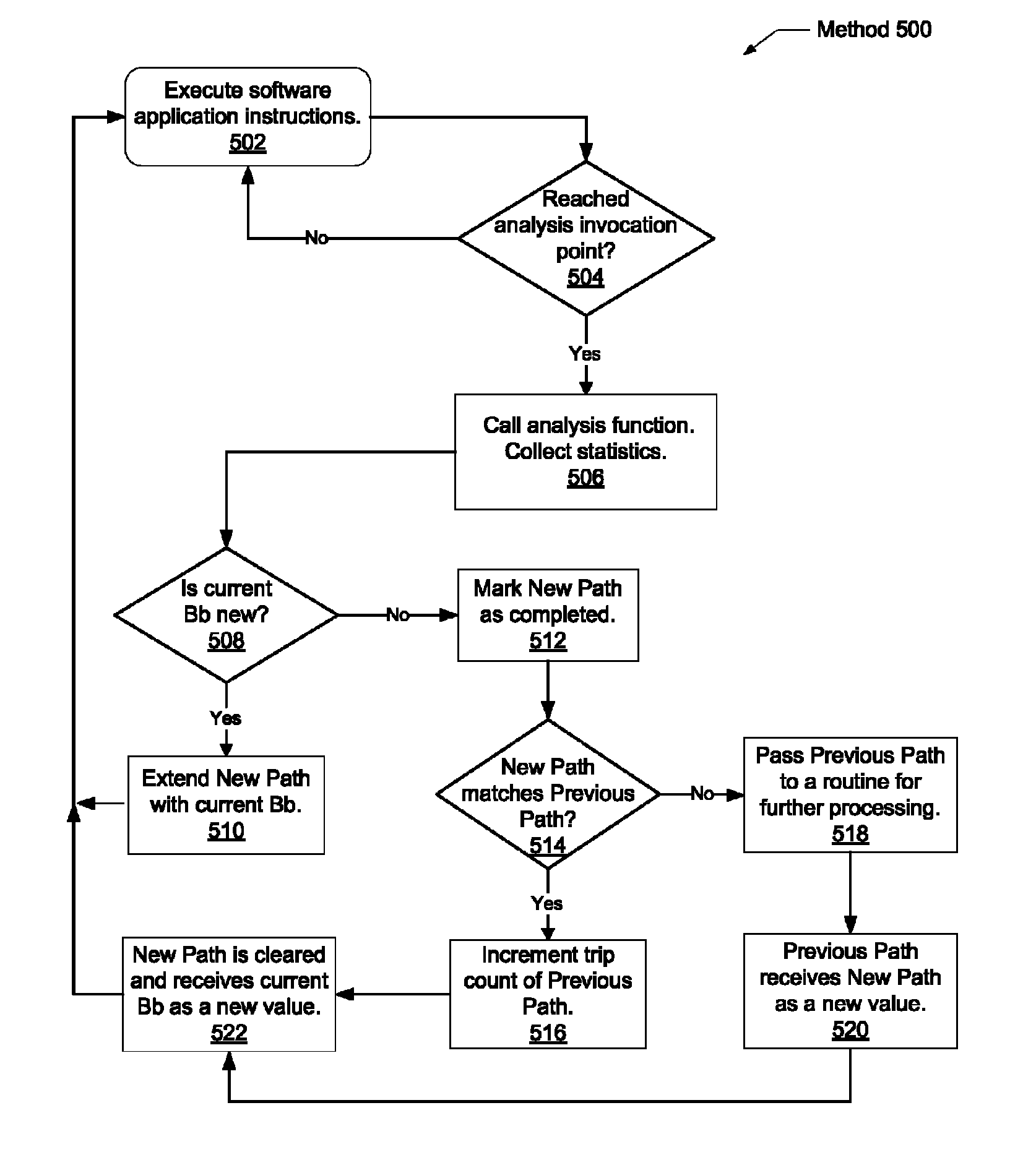
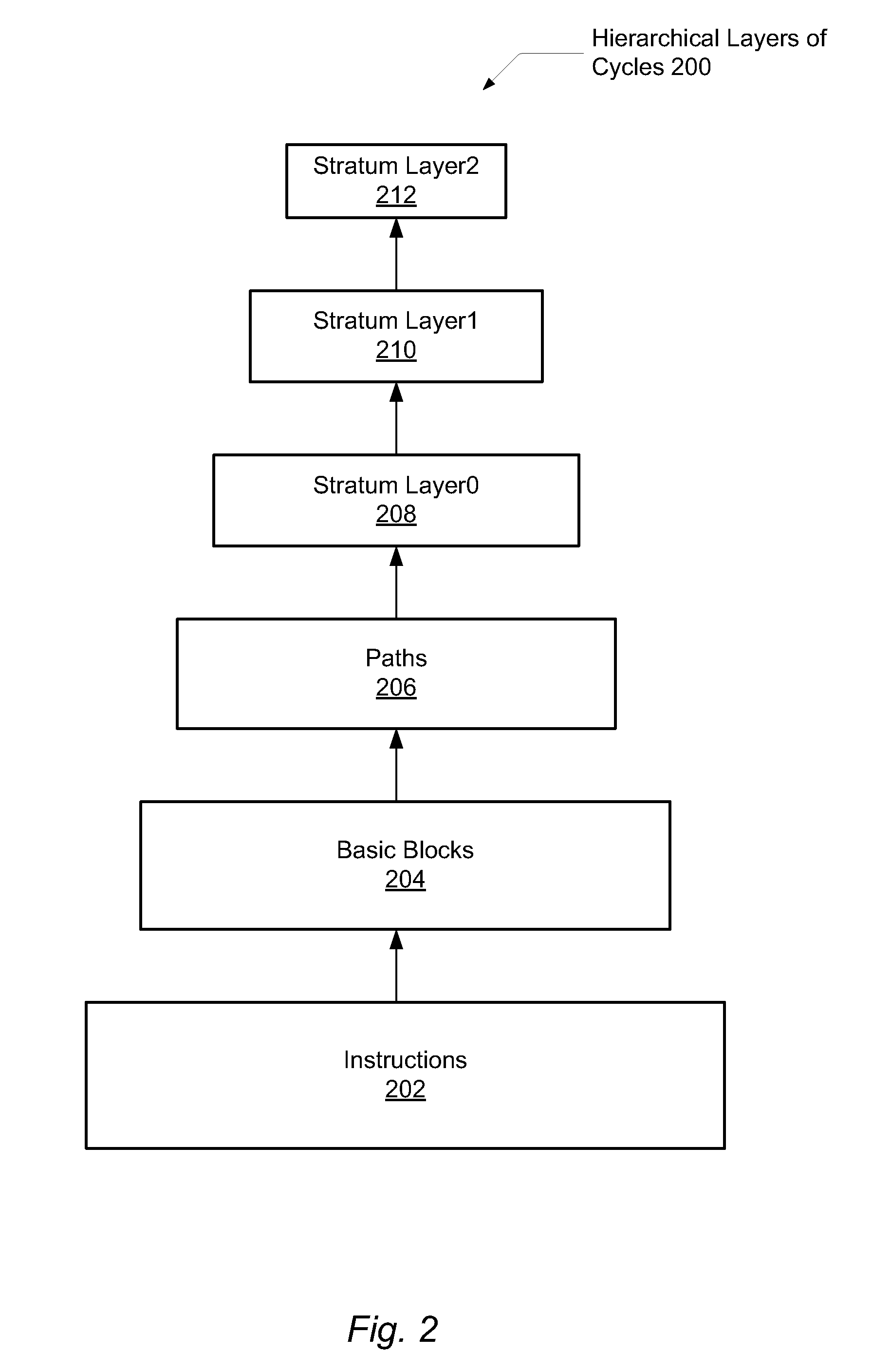
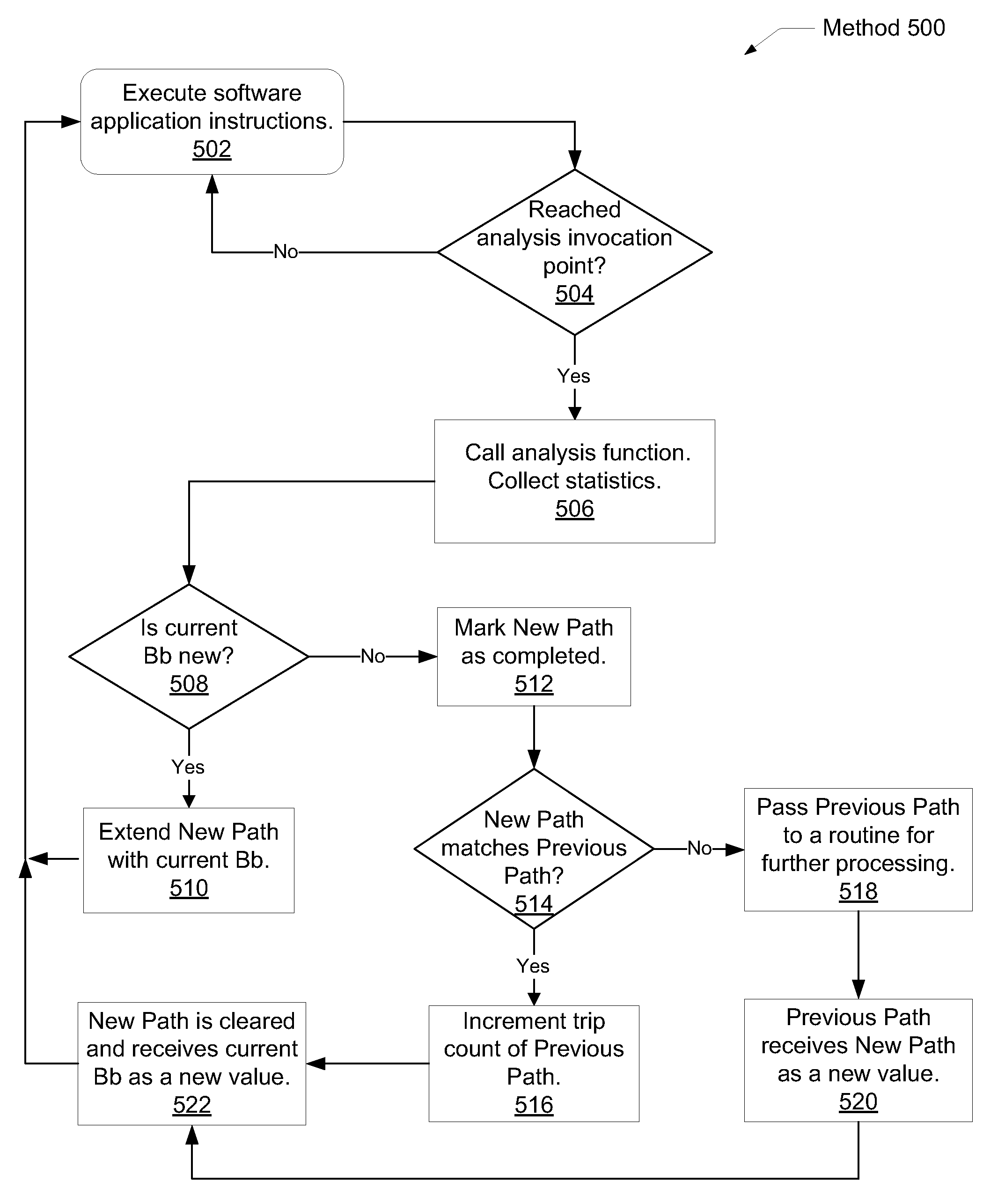
A system and method for efficient whole program profiling of software applications. A computing system comprises a dynamic binary instrumentation (DBI) tool coupled to a virtual machine configured to translate and execute binary code of a software application. The binary code is augmented with instrumentation and analysis code during translation and execution. Characterization information of each basic block is stored as each basic block is executed. A dynamic binary analysis (DBA) tool inspects this information to identify hierarchical layers of cycles within the application that describe the dynamic behavior of the application. A sequence of basic blocks may describe paths, a sequence of paths may describe a stratum, and a sequence of strata may describe a stratum layer. Statistics of these layers and hot paths may be determined and stored. This data storage yields a whole program profile comprising program phase changes that accurately describes the dynamic behavior of the application.
Owner:GLOBALFOUNDRIES INC
System for detecting software bug triggered during practical running of computer program
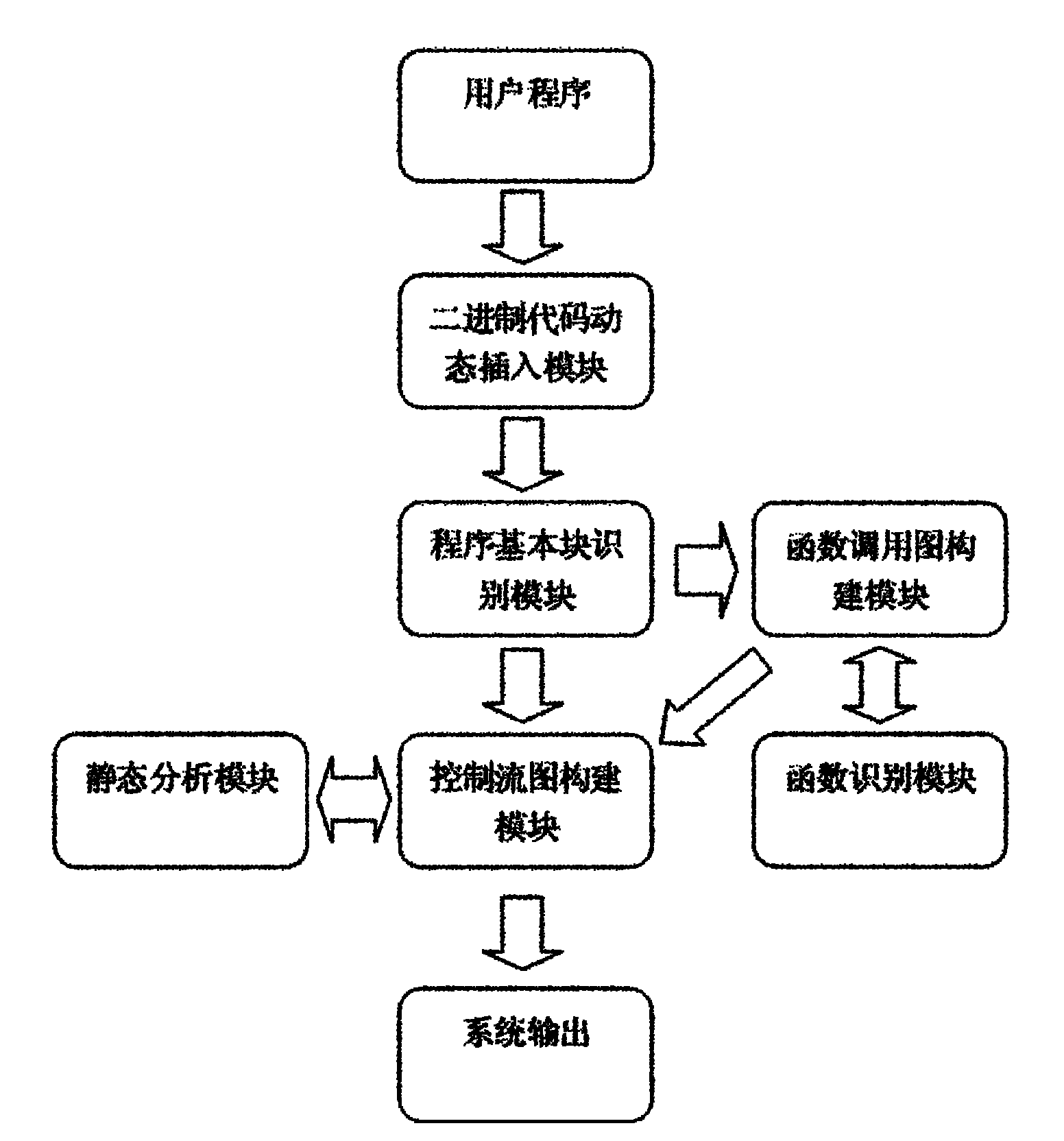
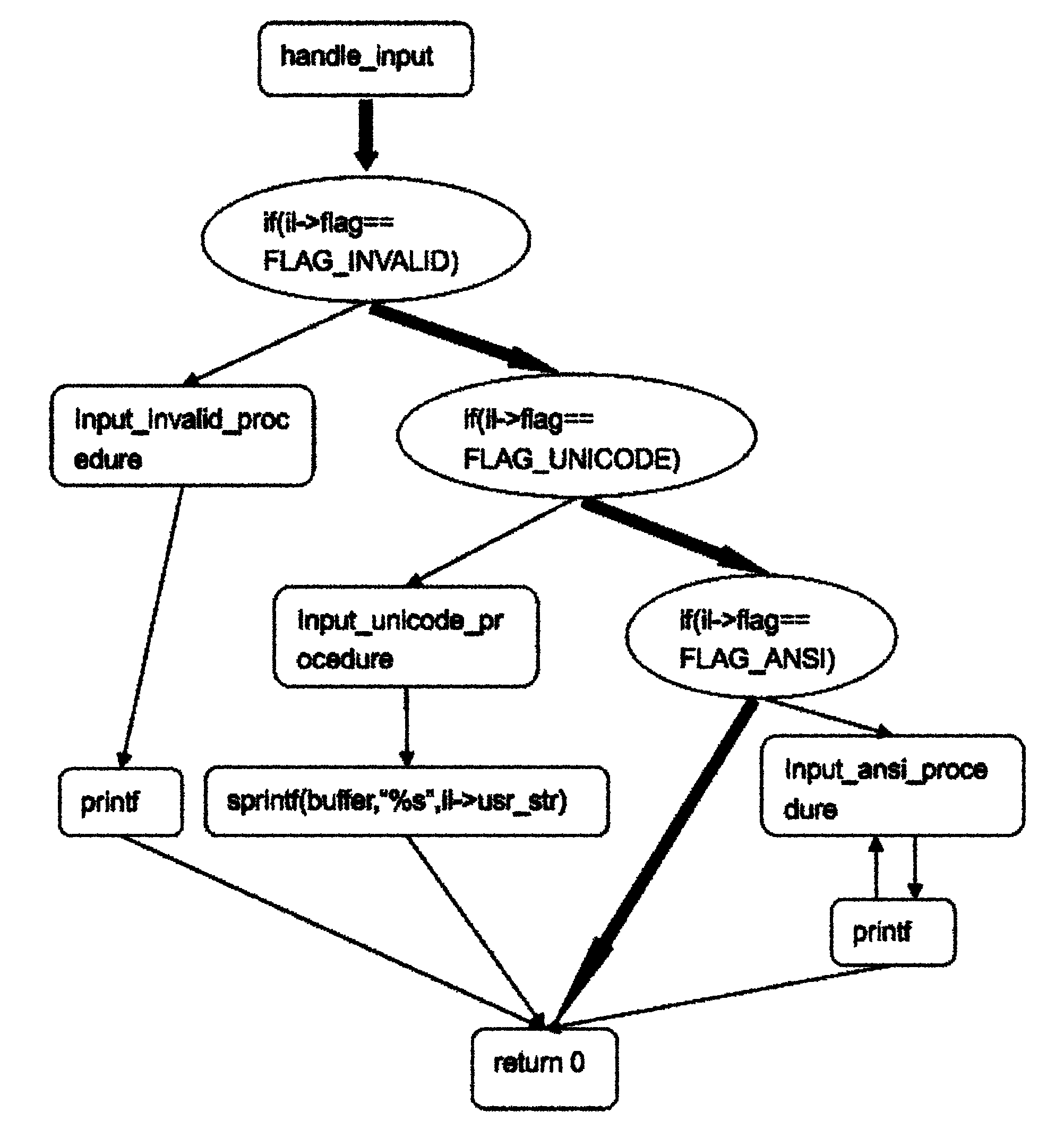
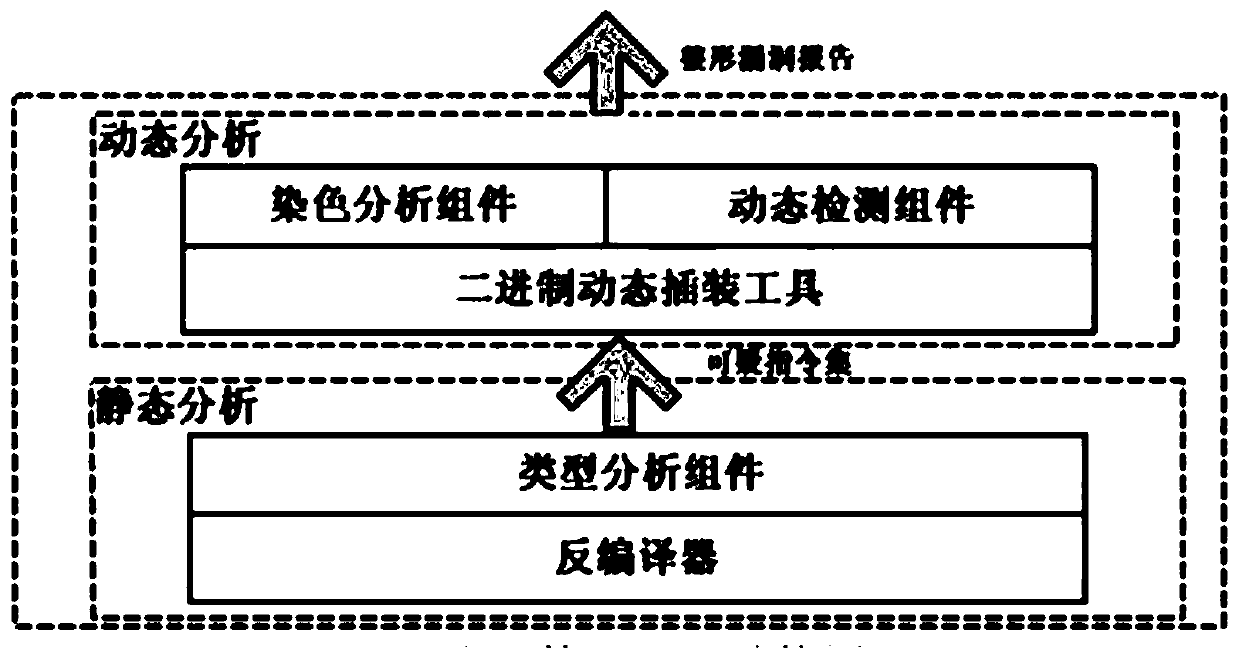
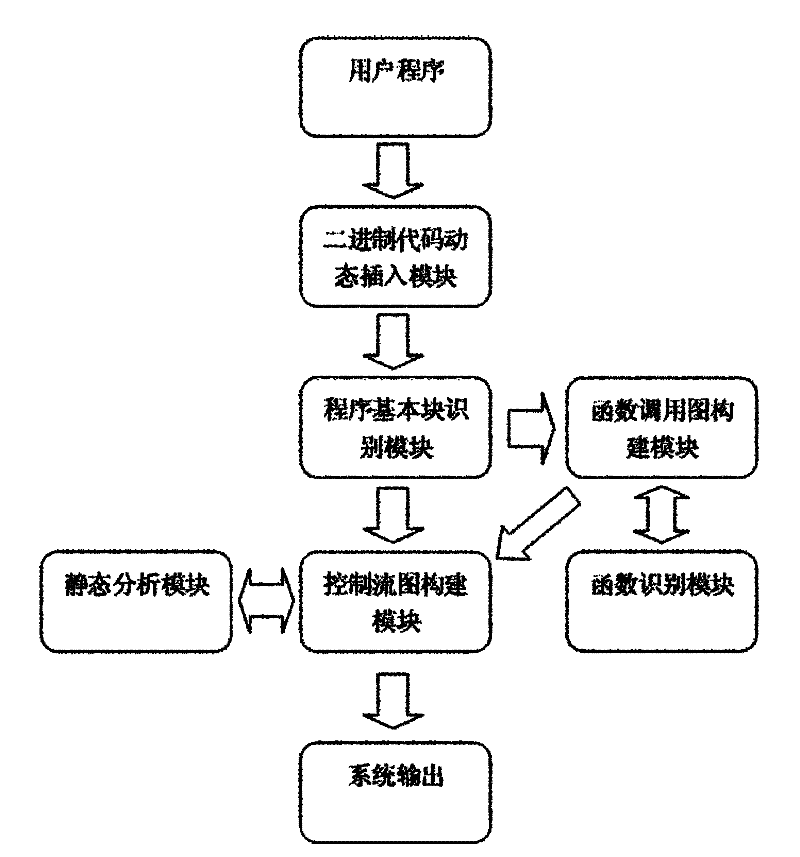
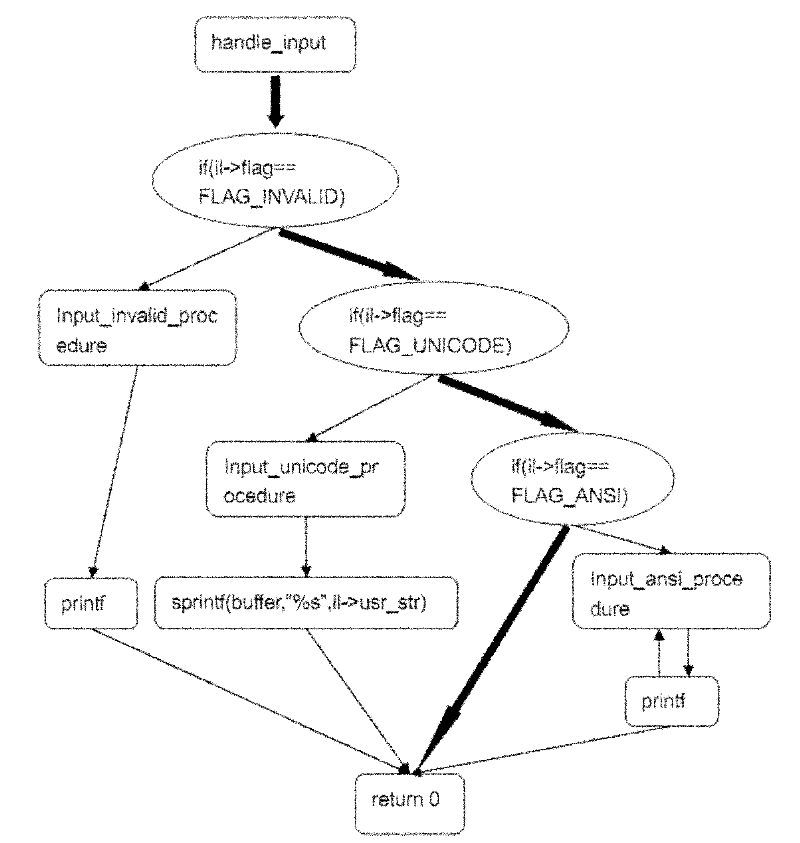
InactiveCN101968766AOvercoming the disadvantage of low analysis coverageIncrease vulnerabilitySoftware testing/debuggingSoftware bugDynamic program analysis
The invention relates to a system for detecting a software bug triggered during practical running of a computer program in the technical field of computers. The system comprises a binary code dynamic inserting module, a program basic block recognizing module, a function call graph constructing module, a control flow graph constructing module, a function recognizing module and a static analysis module. By combining two technologies of dynamic program analysis and static analysis path complementation, the invention not only can detect the bugs which can be triggered during the practical running of the program but also can reach higher program path coverage rate, carry out bug detects on the path which is not covered in the dynamic analysis process, improve the success rate of bug detection and reduce the false rate of the bugs. Meanwhile, the static analysis path complementation technology only analyzes a path which is not executed in dynamic analysis instead of all program paths, thereby greatly reducing the cost on time and system resources.
Owner:SHANGHAI JIAO TONG UNIV
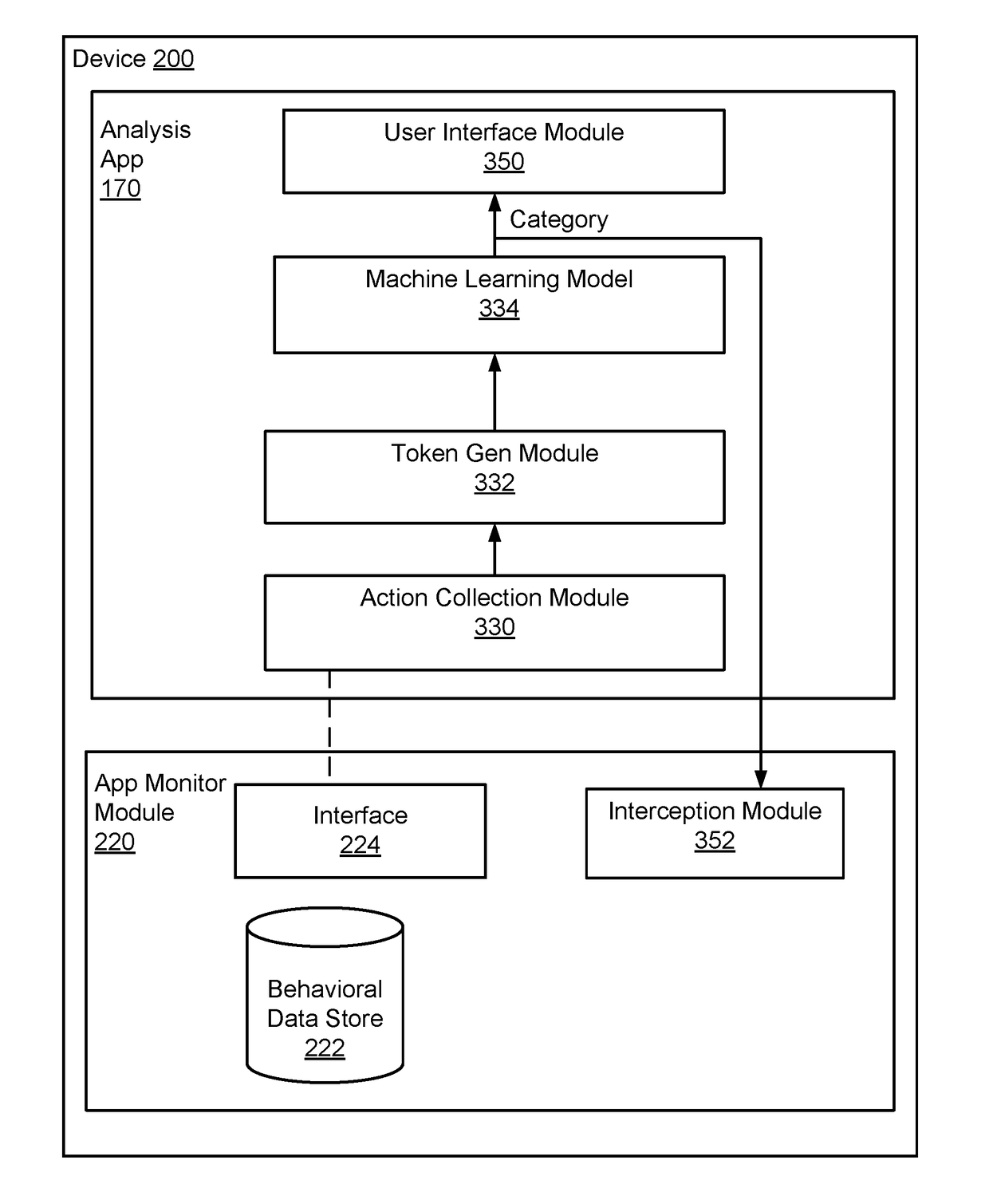
On-Device Maliciousness Categorization of Application Programs for Mobile Devices
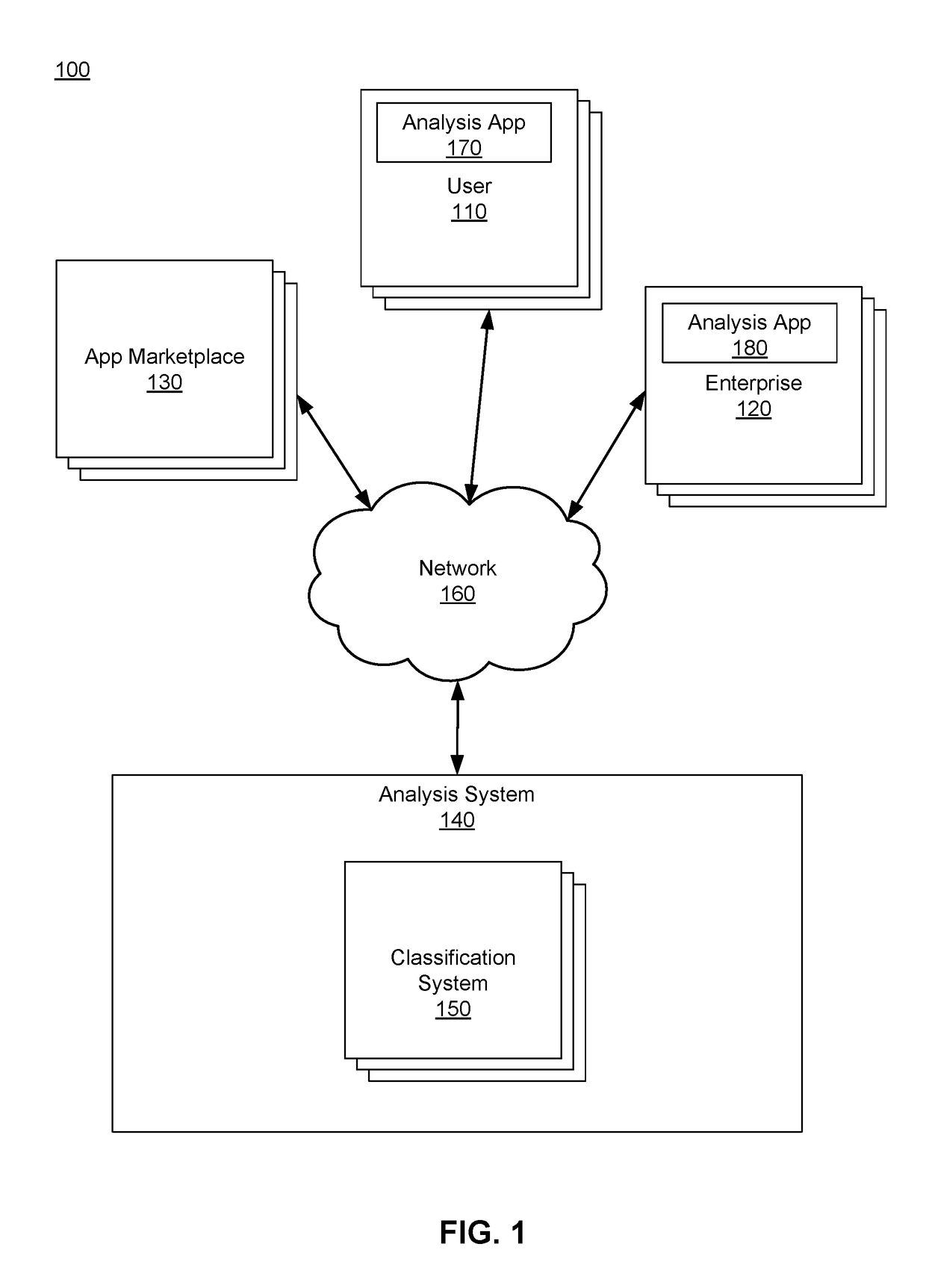
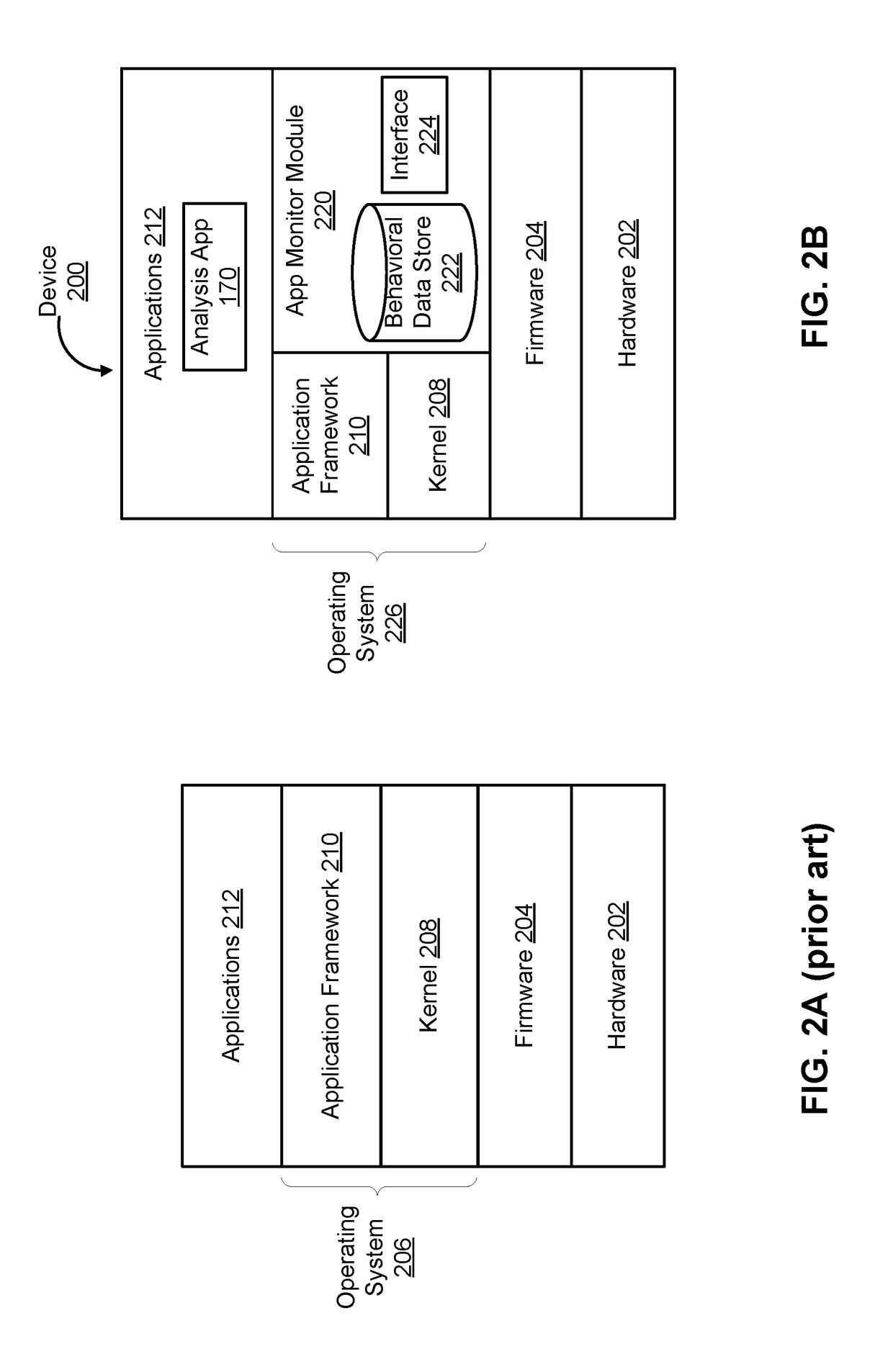
An on-device security vulnerability detection method performs dynamic analysis of application programs on a mobile device. In one aspect, an operating system of a mobile device is configured to include instrumentations and an analysis application program package is configured for installation on the mobile device to interact with the instrumentations. When an application program executes on the mobile device, the instrumentations enables recording of information related to execution of the application program. The analysis application interfaces with the instrumented operating system to analyze the behaviors of the application program using the recorded information. The application program is categorized (e.g., as benign or malicious) based on its behaviors, for example by using machine learning models.
Owner:TRUSTLOOK INC
Decoupling dynamic program analysis from execution across heterogeneous systems
ActiveUS20090319256A1Reduce the burden onError detection/correctionSoftware simulation/interpretation/emulationParallel computingDynamic program analysis
Dynamic program analysis is decoupled from execution in virtual computer environments so that program analysis can be performed on a running computer program without affecting or perturbing the workload of the system on which the program is executing. Decoupled dynamic program analysis is enabled by separating execution and analysis into two tasks: (1) recording, where system execution is recorded with minimal interference, and (2) analysis, where the execution is replayed and analyzed. Recording and analysis are carried out on heterogeneous systems so that they can be separately optimized.
Owner:VMWARE INC
Bounded hash table sorting in a dynamic program profiling system
ActiveUS8024719B2Digital data processing detailsSoftware engineeringTheoretical computer scienceDynamic program analysis
A system and method for efficient bounded hash table sorting during dynamic whole program profiling of software applications. A computing system comprises a dynamic binary instrumentation (DBI) tool coupled to a virtual machine configured to translate and execute binary code of a software application. The binary code is augmented with instrumentation and analysis code during translation and execution. A dynamic binary analysis (DBA) tool identifies hierarchical layers of cycles within the application that describe the dynamic behavior of the application. Corresponding characterization information is stored in a hash table. Periodic sorting of entries of the hash table occur for highly accessed entries in deep buckets within the hash table. Repositioning the entries within the hash table may reduce pointer chasing problems and identify program phase changes within the dynamic behavior of the application.
Owner:ADVANCED MICRO DEVICES INC
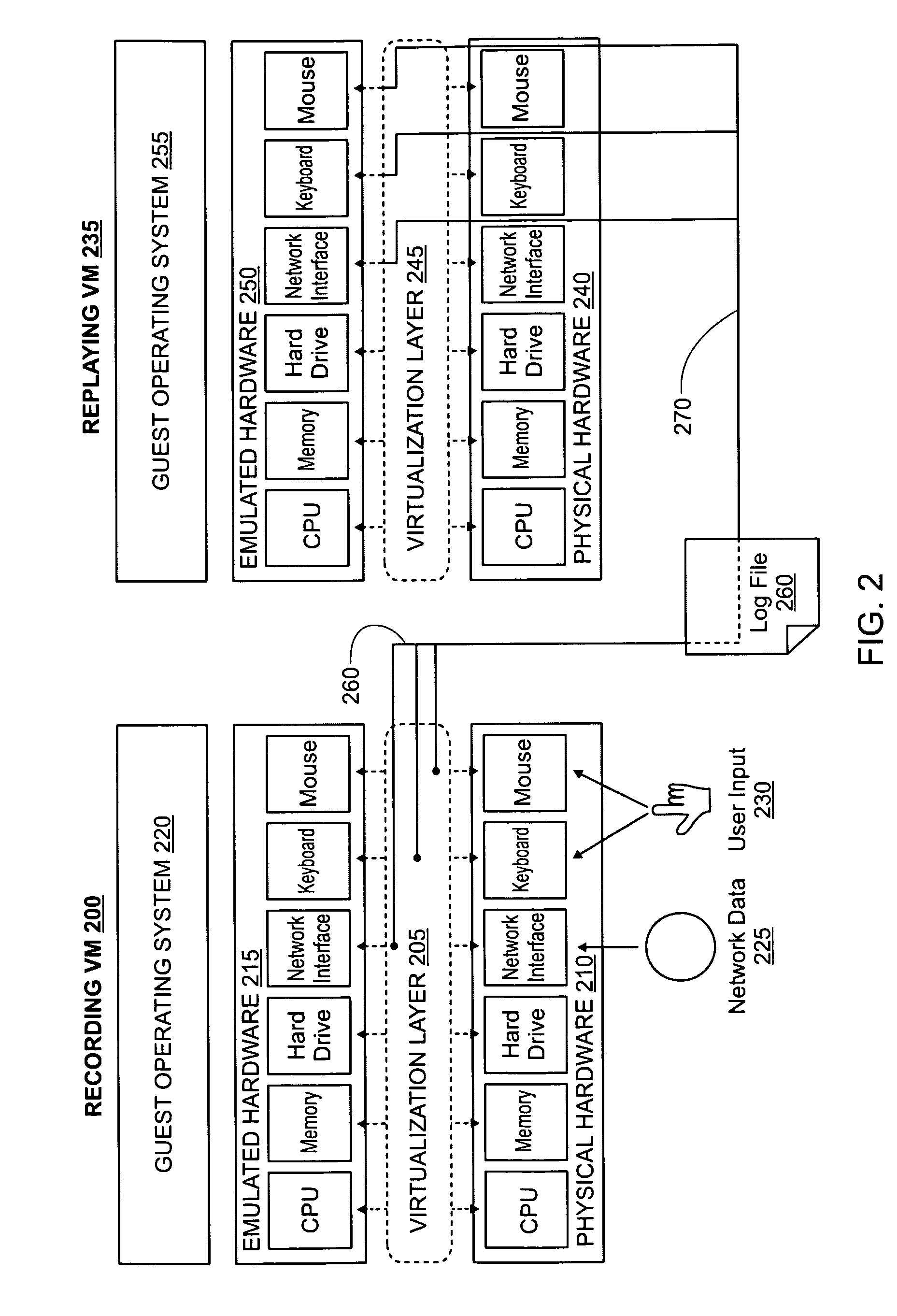
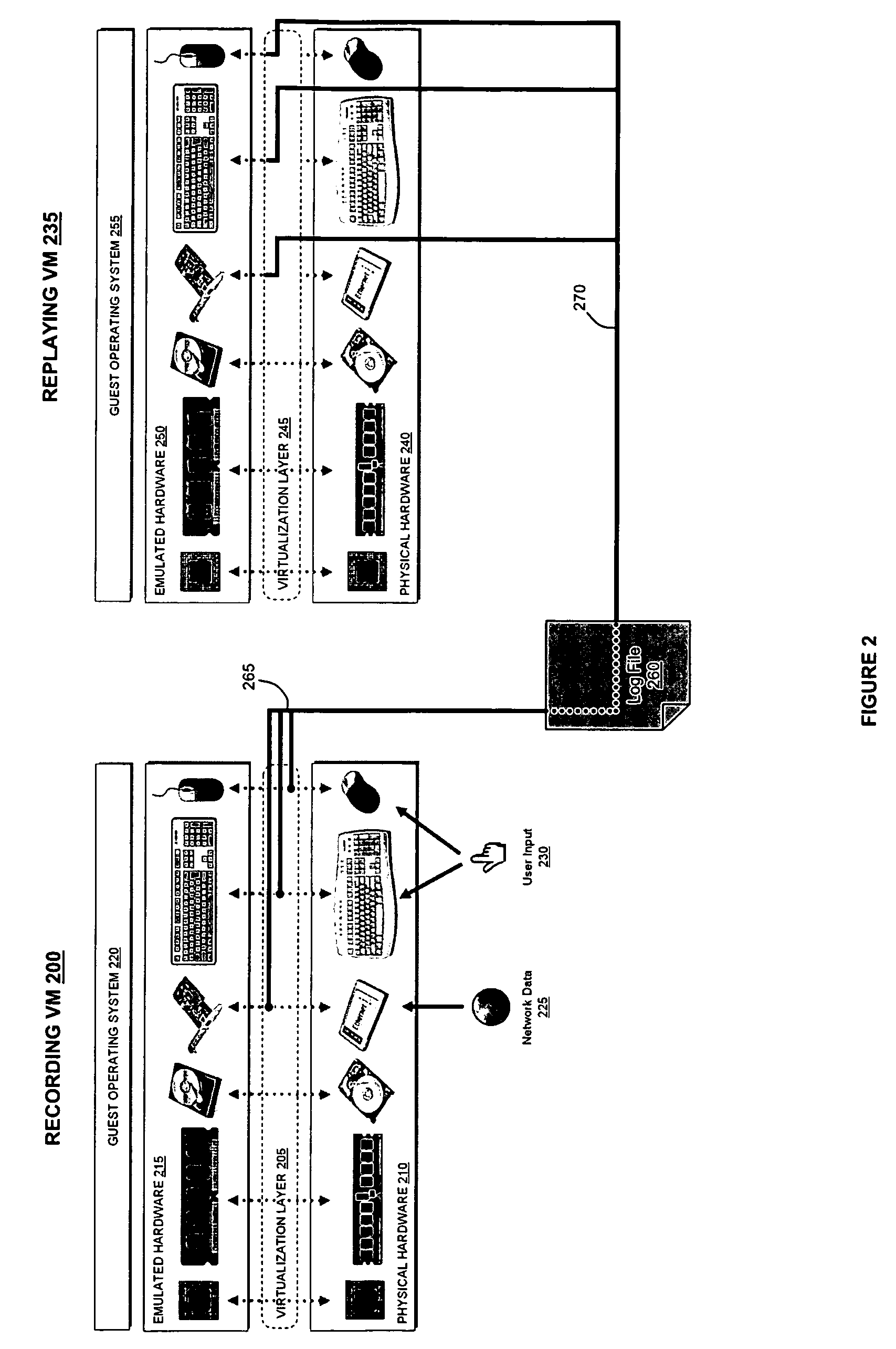
Decoupling dynamic program analysis from execution in virtual environments
Dynamic program analysis is decoupled from execution in virtual computer environments so that program analysis can be performed on a running computer program without affecting or perturbing the workload of the system on which the program is executing. Decoupled dynamic program analysis is enabled by separating execution and analysis into two tasks: (1) recording, where system execution is recorded with minimal interference, and (2) analysis, where the execution is replayed and analyzed.
Owner:VMWARE INC
Bounded hash table sorting in a dynamic program profiling system
ActiveUS20100114915A1Digital data processing detailsSoftware engineeringTheoretical computer scienceDynamic program analysis
A system and method for efficient bounded hash table sorting during dynamic whole program profiling of software applications. A computing system comprises a dynamic binary instrumentation (DBI) tool coupled to a virtual machine configured to translate and execute binary code of a software application. The binary code is augmented with instrumentation and analysis code during translation and execution. A dynamic binary analysis (DBA) tool identifies hierarchical layers of cycles within the application that describe the dynamic behavior of the application. Correpsonding characterization information is stored in a hash table. Periodic sorting of entries of the hash table occur for highly accessed entries in deep buckets within the hash table. Repositioning the entries within the hash table may reduce pointer chasing problems and identify program phase changes within the dynamic behavior of the application.
Owner:ADVANCED MICRO DEVICES INC
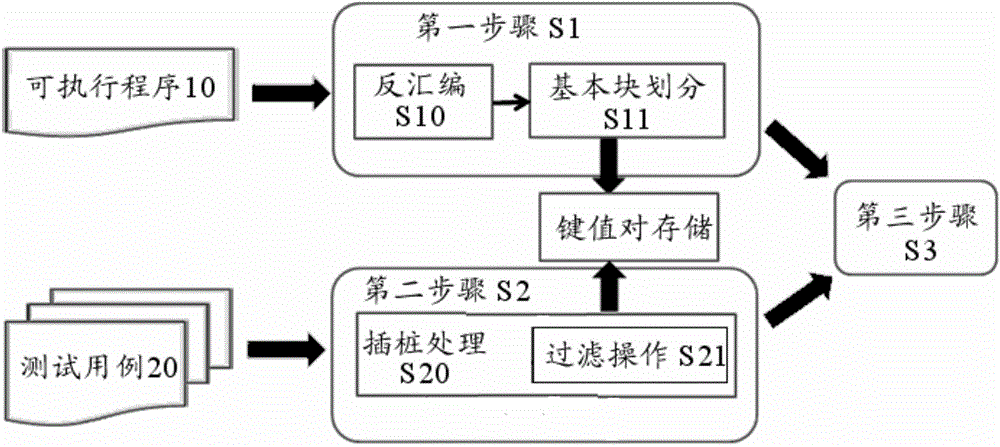
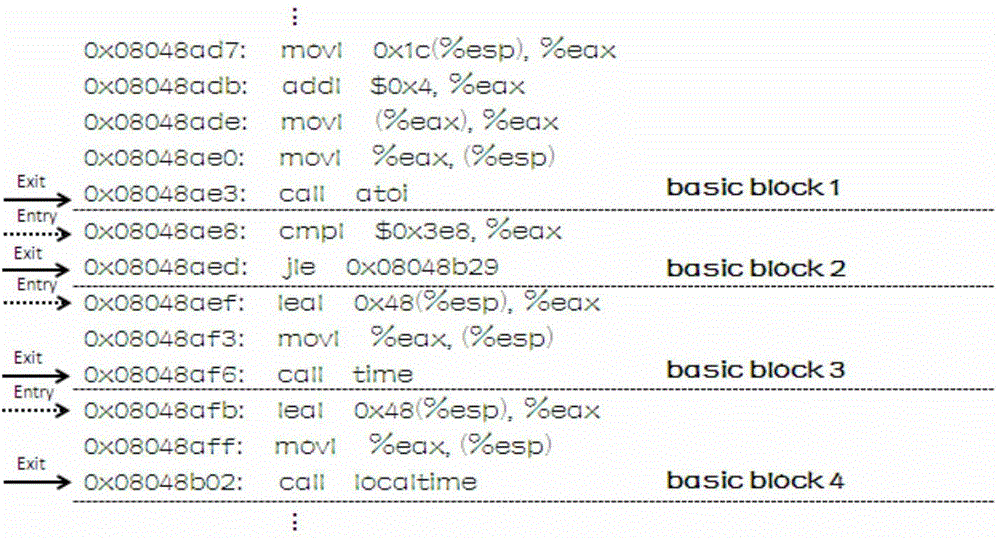
Automated evaluation method for binary code coverage of testing case set for executable program
ActiveCN104375941AQuality improvementImprove accuracySoftware testing/debuggingVirtual memoryStatic timing analysis
The invention provides an automated evaluation method for binary code coverage of a testing case set for an executable program. The automated evaluation method includes step 1, executing static analysis on the executable program with a binary code expression form, converting the binary code expression form into an assembly instruction expression form through disassembly during static analysis, and performing basic block division on the executable program with the assembly instruction expression form; step 2, utilizing a testing case to execute dynamic analysis on program process, executing instrumentation processing during dynamic analysis to capture executing track, executing filtering operation during instrumentation processing for basic block filtering to remove an external instruction of the executable program; step 3, utilizing a virtual memory address of the executable program to evaluate binary code coverage of the testing case set by matching static analysis result of the step 1 and dynamic analysis result of the step 2.
Owner:JIANGNAN INST OF COMPUTING TECH
Decoupling dynamic program analysis from execution across heterogeneous systems
ActiveUS8352240B2Reduce the burden onError detection/correctionSoftware simulation/interpretation/emulationDynamic program analysisWorkload
Owner:VMWARE INC
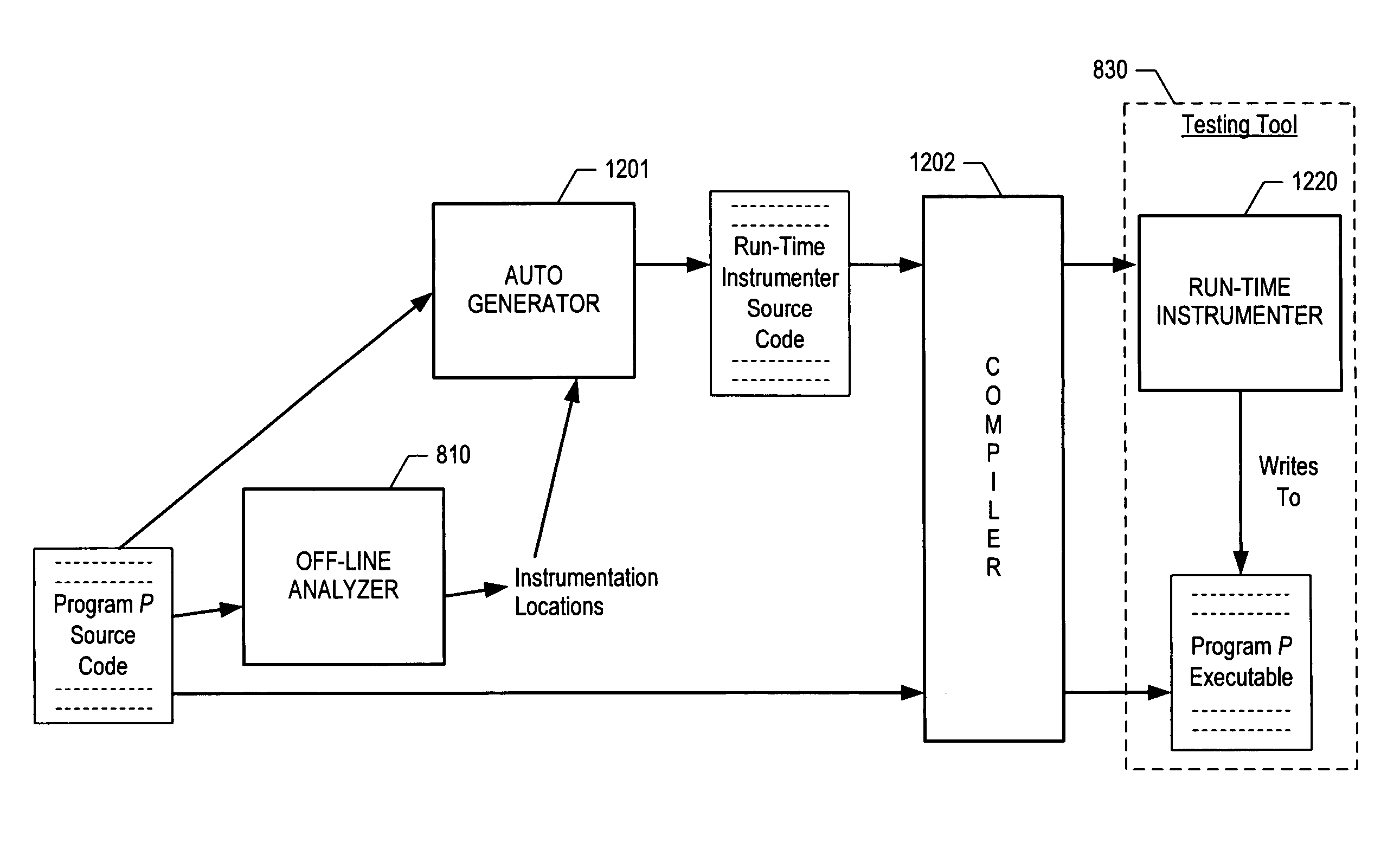
Off-line program analysis and run-time instrumentation
ActiveUS8291399B2Error detection/correctionSpecific program execution arrangementsCode coverageDynamic program analysis
A technique is disclosed for determining off-line the number and location of instrumentation probes to be inserted into a program under testing, and subsequently instrumenting the program at run-time based on the off-line analysis. In accordance with the illustrative embodiment, an off-line analyzer first determines instrumentation locations for a program under test in accordance with a method called the Super Nested Block Method. After the instrumentation locations have been determined, a testing / monitoring tool executes the program and a run-time instrumenter in parallel. The run-time instrumenter accordingly inserts probes into the program, removes probes after they have been executed once, and generates and reports information about code coverage based on the probes.
Owner:AVAYA INC
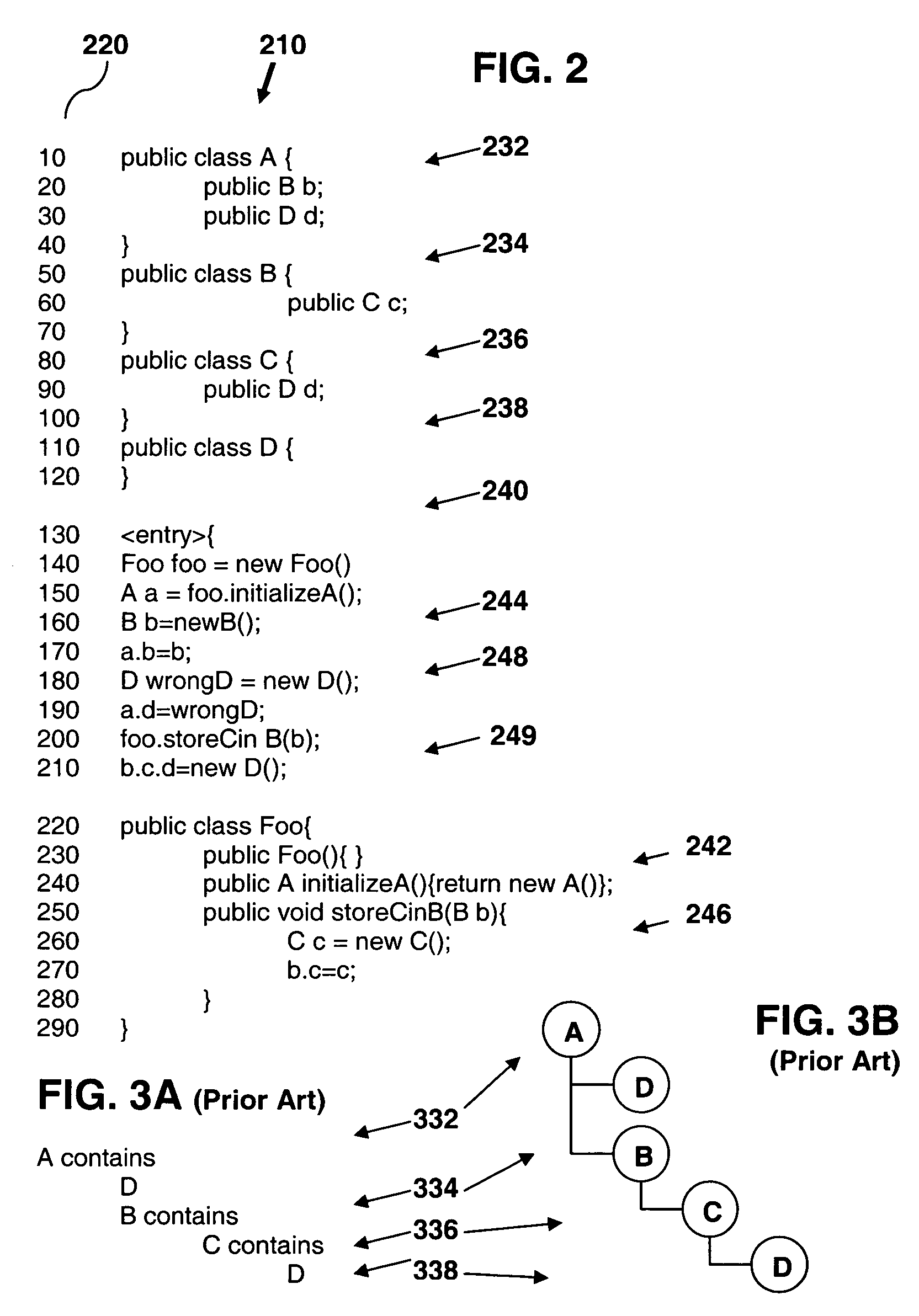
Program analysis tool presenting object containment and temporal flow information
InactiveUS7530054B2Error detection/correctionSpecific program execution arrangementsTemporal informationData processing system
The present invention provides a method, apparatus, and computer instructions for program analysis. In an exemplary embodiment, a target program is loaded onto a data processing system including a program analysis software component. Hierarchies in the form of control flow and containment information about the target program are determined, using either static or dynamic, and direct (e.g., instrumented profilers) or indirect (e.g., monitored runtime), processing techniques, depending on the application and program analysis tool being used. The control flow and object containment information are then presented in a related and selected format for consideration by a user. One embodiment includes a program and GUI (graphical user interface) operably providing control flow-annotated object containment hierarchies to a user, the hierarchies including control flow, allocation and storage information added to object containment information.
Owner:INT BUSINESS MASCH CORP
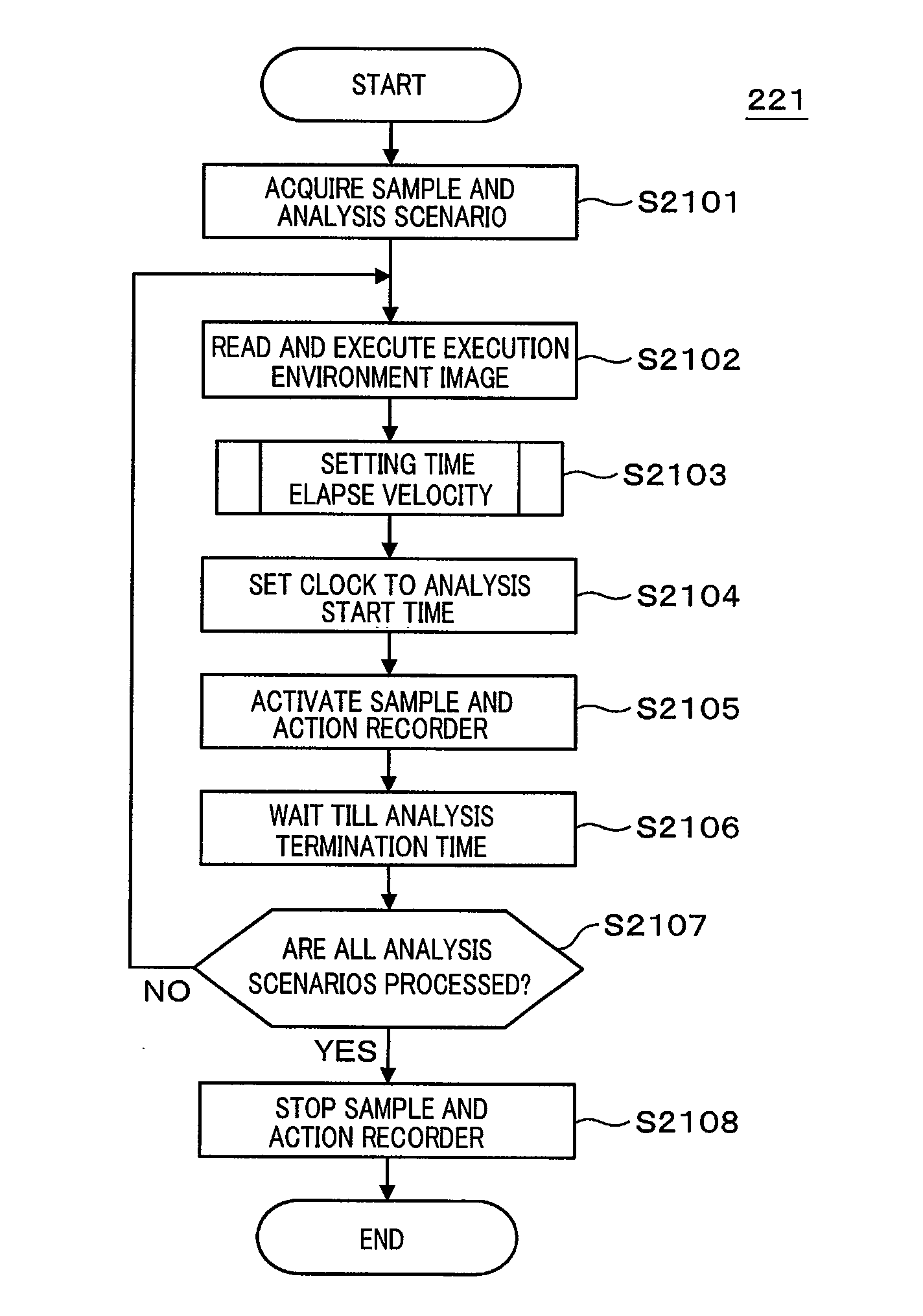
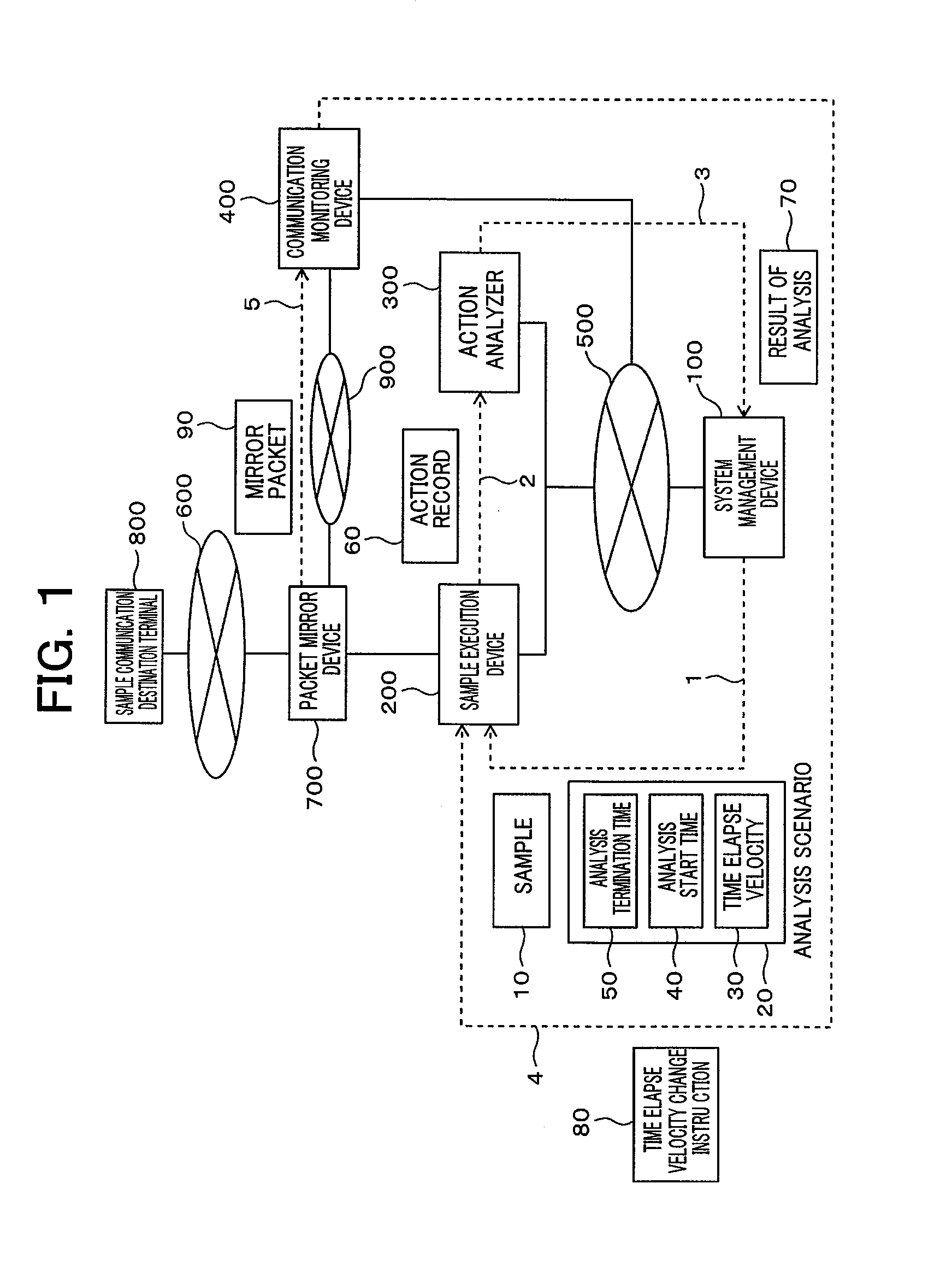
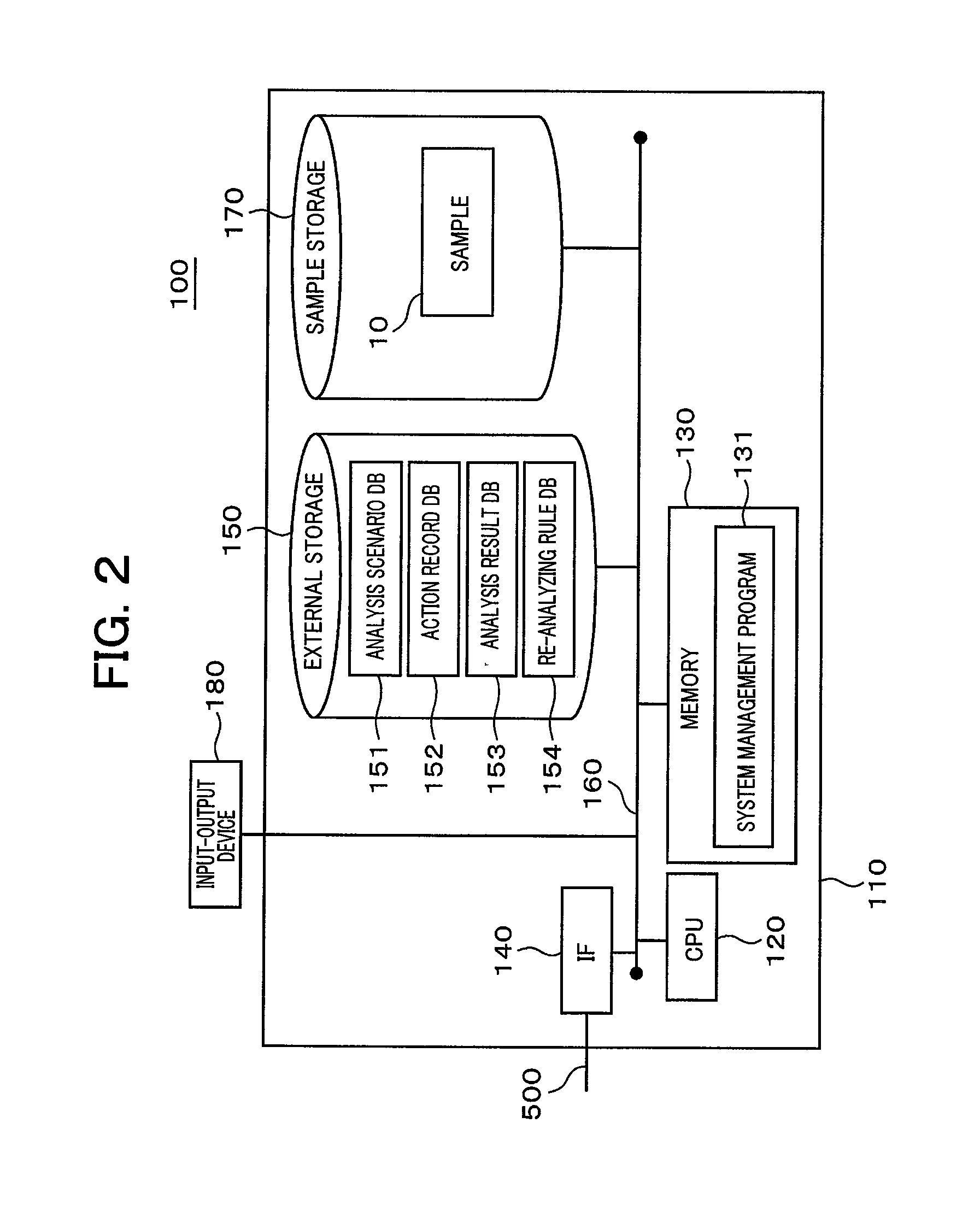
Program analysis system and method thereof
InactiveUS20130227690A1Efficient analysisMemory loss protectionError detection/correctionStart timeDynamic program analysis
A program analysis system that analyzes a program while adjusting time elapse velocity in program execution environment sets analysis conditions such as time elapse velocity in the execution environment, program execution start time and execution termination time, adjusts the time elapse velocity and the program execution start time according to the determination of an analysis manager, executes the program till the execution termination time, monitors the execution environment, acquires an action record of the program, analyzes the action record, and clarifies the behavior of the program. Further, the program analysis system resets the analysis conditions based upon a result of analysis, re-analyzes, monitors communication between a sample and an external terminal, and varies the time elapse velocity set by the analysis manager to prevent time-out from occurring in communication.
Owner:HITACHI LTD
Visualization method and system for program analysis processes
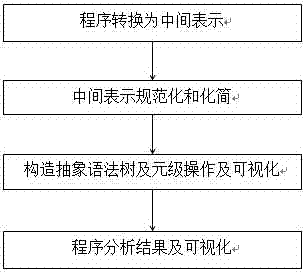
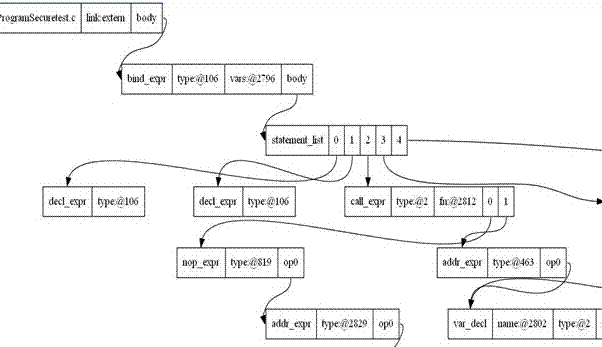
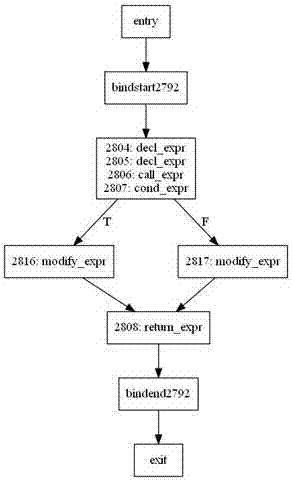
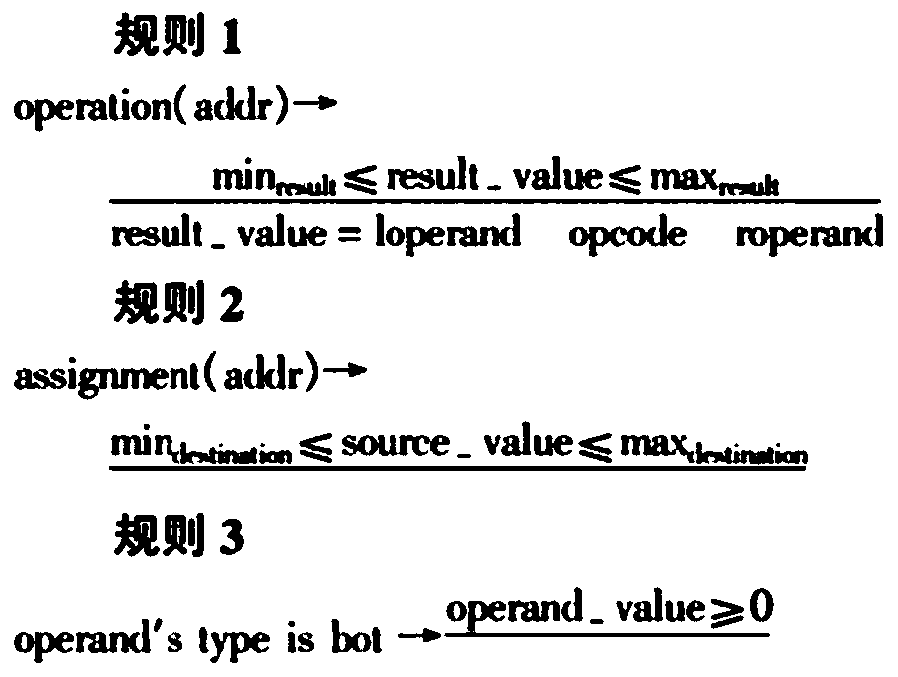
The invention discloses a visualization method and system for program analysis processes. The method includes a program switch module, a standardized processing module, a meta-level operation module and a graphical display module, wherein the program switch module generates intermediate representation of a computer program; the standardized processing module normalizes and simplifies the intermediate representation of the program; the meta-level operation module provides the intermediate representation with a primary program modification mode; the graphical display module extracts information of data flows and control flows of the program, and displays an abstract syntax tree, a control flow diagram and a program dependence graph in a graphical mode. The visualization method and system for program analysis processes have the advantages of visually showing the whole processes of a program analysis, using a graph to demonstrate the result of the program analysis, and helping students better understand analysis processes and analysis methods of programs.
Owner:郭德贵
Shaping vulnerability detection method based on dynamic and static analysis
InactiveCN110909358AEfficient detectionEfficient analysisPlatform integrity maintainanceAlgorithmDynamic program analysis
The invention provides a shaping vulnerability detection method based on dynamic and static analysis. Static and dynamic program analysis technologies are combined. Points to be protected include thefollowing contents that in a static analysis stage, the tool decompiles the binary program and creates a suspicious instruction set; in a dynamic analysis stage, the tool dynamically scans instructions in the suspicious instruction set, and whether the instructions are vulnerabilities or not is judged in combination with input capable of triggering the vulnerabilities. At present, vulnerability mining is either static analysis or dynamic analysis. The vulnerability detection technology can well overcome the defects of existing vulnerability mining, accurate and sufficient type information is provided, and through static analysis based on the decompiler, the number of instructions needing to be detected during dynamic operation is reduced.
Owner:上海安智信息科技有限公司
Parallel acceleration method for dynamic analysis of program behavior
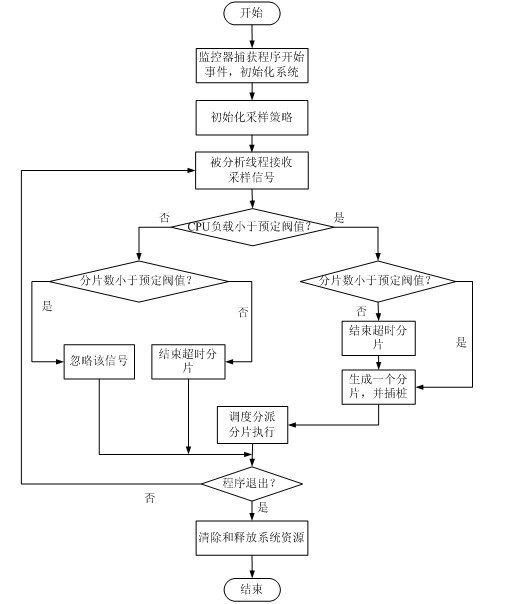
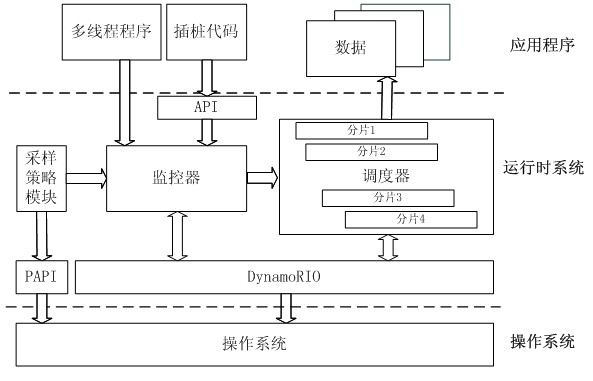
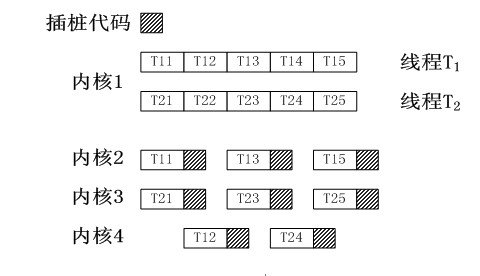
InactiveCN102110052ASpeed up dynamic analysisAchieve decouplingMultiprogramming arrangementsSoftware testing/debuggingComputer resourcesParallel computing
The invention discloses a parallel acceleration method for dynamic analysis of a program behavior. The method comprises the following steps of: acquiring an analyzed program, and generating fragments of all threads of the analyzed program on the basis of resource and load states; performing analysis code pile pitching on all the fragments; allocating the fragments subjected to the pile pitching to a specific processor core and performing concurrent execution on the fragments and the analyzed threads; performing reduction processing on execution results of the fragments after the concurrent execution is finished; and acquiring program behavior information on the basis of reduction processing results. Due to the adoption of behavior information of an idle computer resource collection program, the dynamic analysis process of the program is accelerated.
Owner:HUAZHONG UNIV OF SCI & TECH
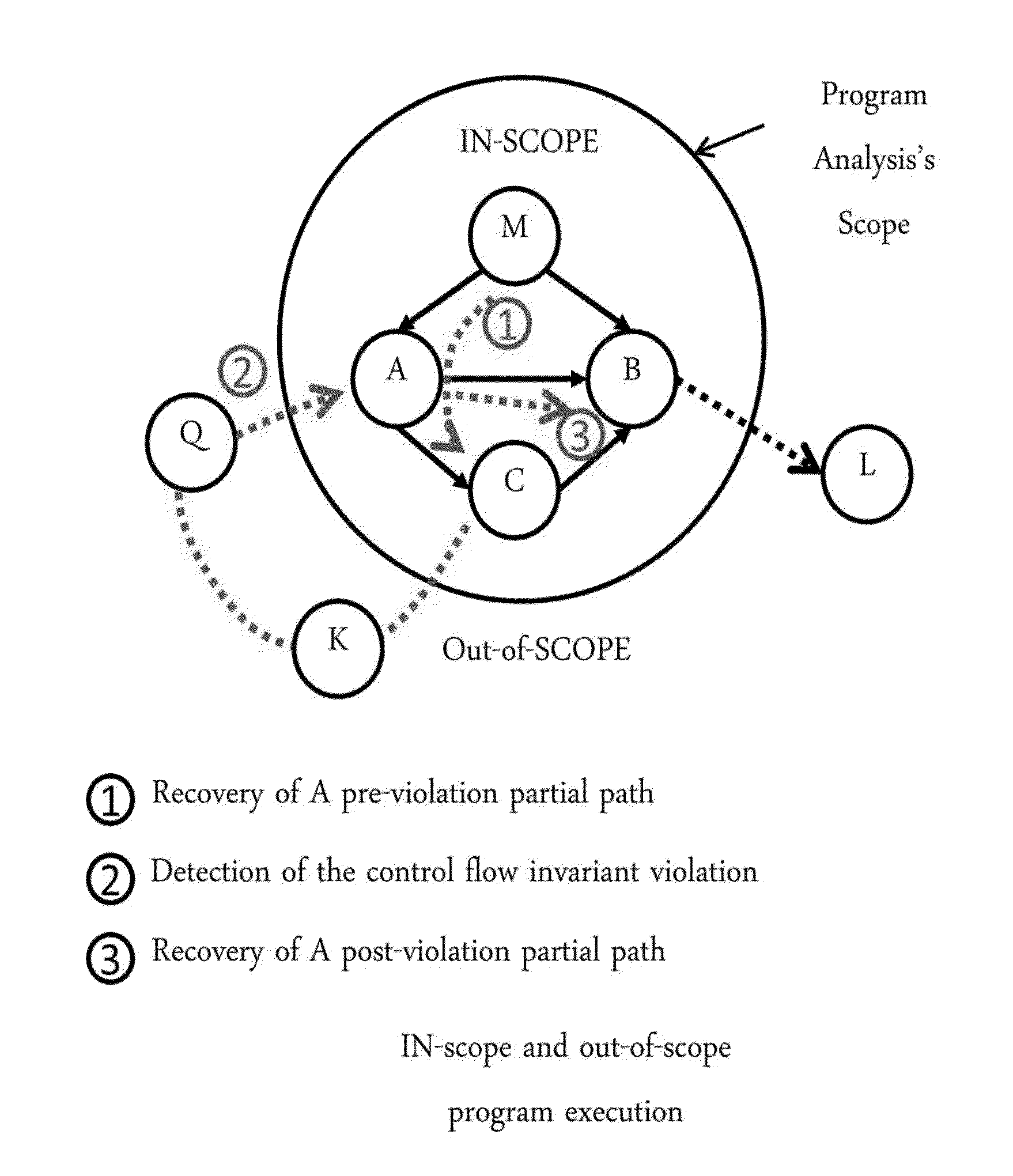
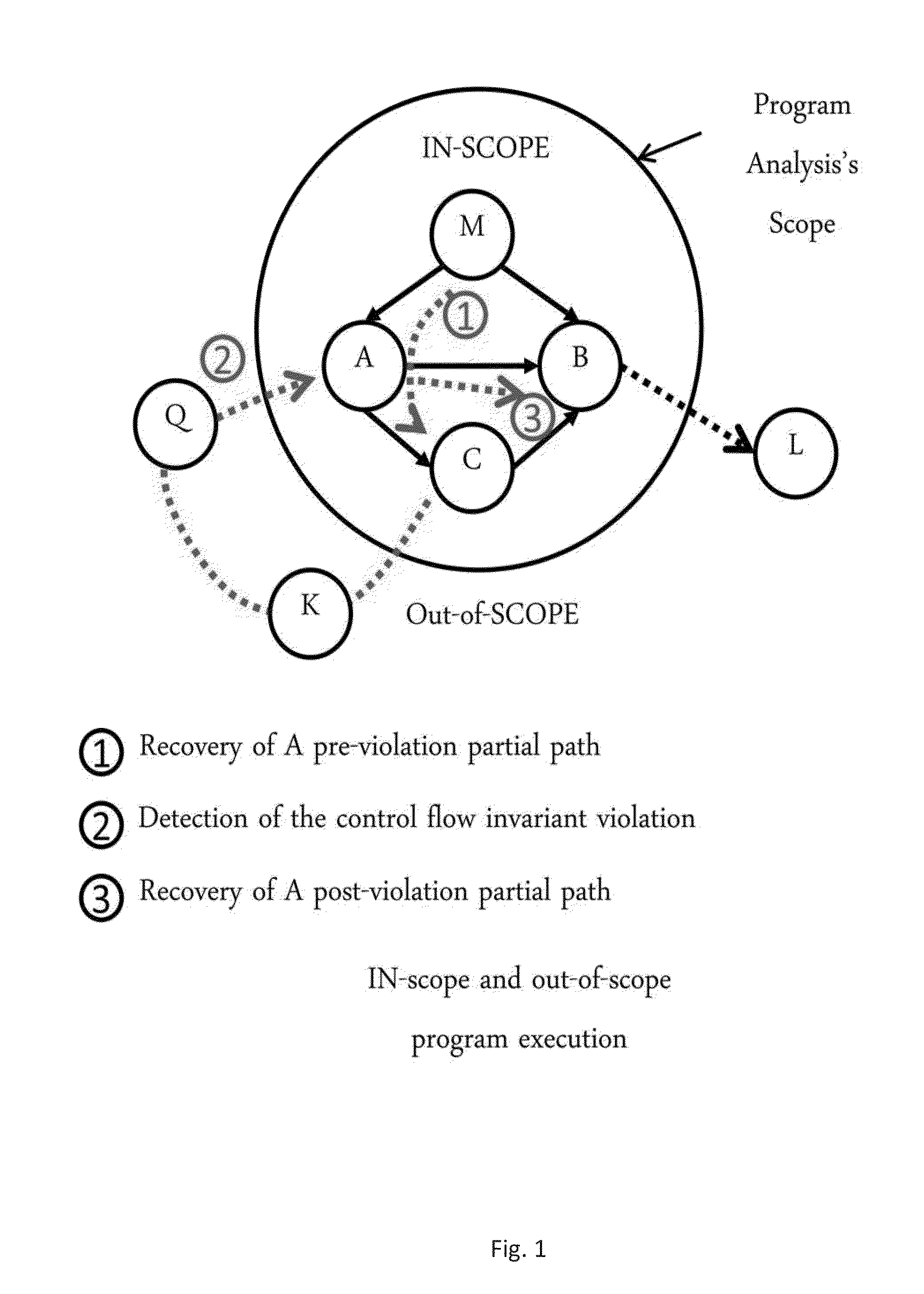
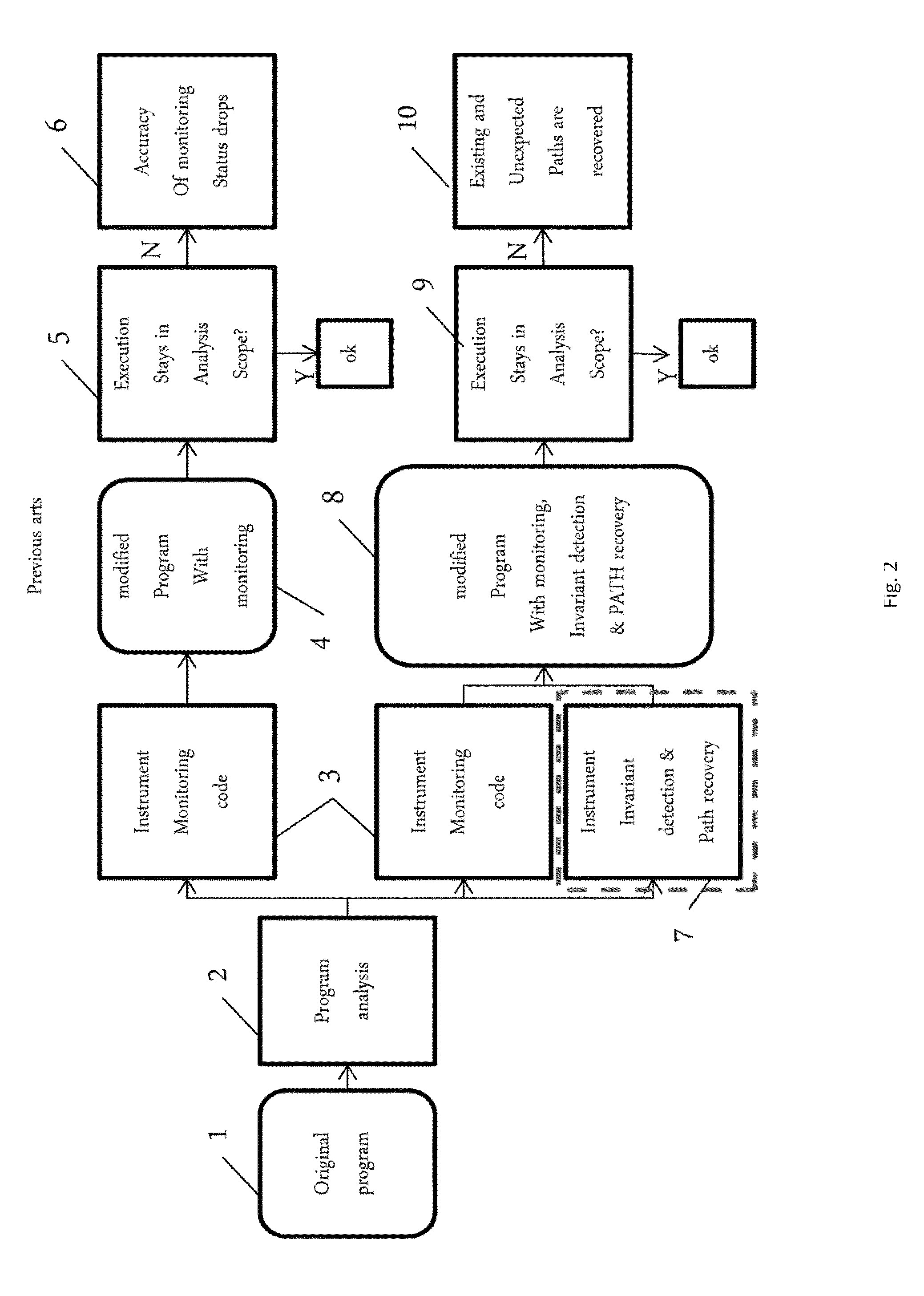
Guarding a Monitoring Scope and Interpreting Partial Control Flow Context
ActiveUS20140298300A1Hardware monitoringSpecific program execution arrangementsControl flowSoftware system
A computer implemented method for maintaining a program's calling context correct even when a monitoring of the program goes out of a scope of a program analysis by validating function call transitions and recovering partial paths before and after the violation of the program's control flow. The method includes detecting a violation of control flow invariants in the software system including validating a source and destination of a function call in the software system, interpreting a pre-violation partial path responsive to a failure of the validating, and interpreting a post violation path after a violation of program flow.
Owner:NEC CORP
Accelerating replayed program execution to support decoupled program analysis
ActiveUS8719800B2Error detection/correctionSpecific program execution arrangementsDynamic program analysisStatic program analysis
A virtual machine system decouples dynamic program analysis from program execution. Program analysis is decoupled from program execution through the use of a virtual machine to record program execution and an analysis platform to replay and analyze the program execution. Optimization techniques are applied to prevent the analysis platform from falling too far behind the program execution platform during replay.
Owner:VMWARE LLC
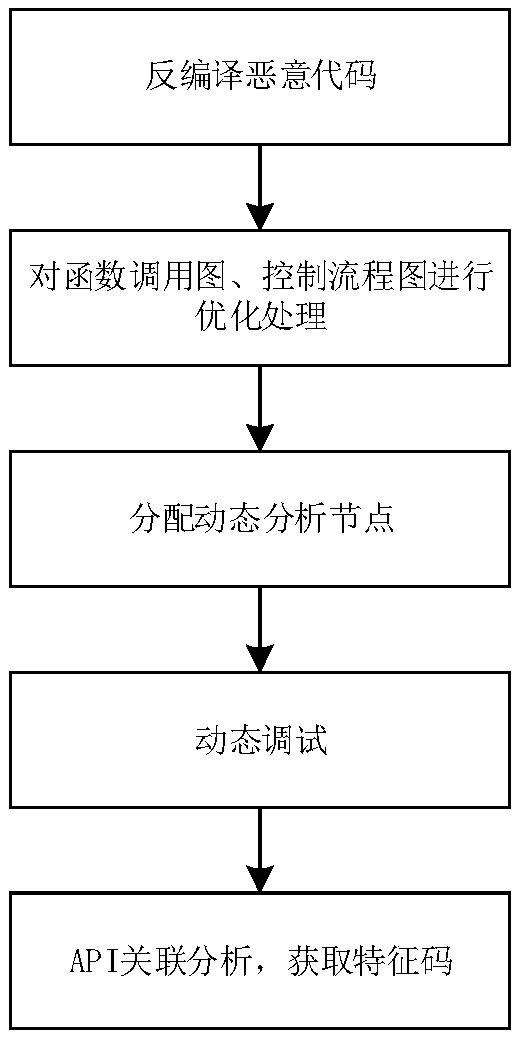
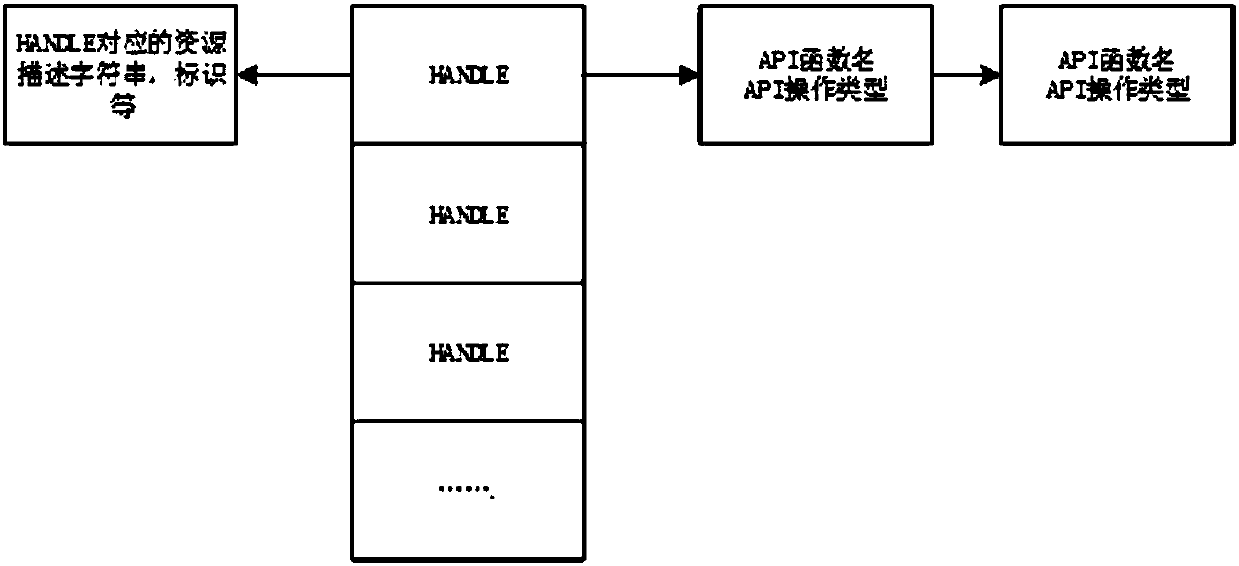
Malicious code behavior feature extraction method
InactiveCN107679402AAccurate extractionEfficient expression of featuresSoftware testing/debuggingPlatform integrity maintainanceStatic timing analysisControl flow
The invention discloses a malicious code behavior feature extraction method. The method comprises the following steps of 1, performing disassembling analysis on a malicious code sample by using a disassembling tool through adopting a static analysis method to obtain a function call graph and a control flow graph; 2, performing optimization processing on the function call graph and the control flowgraph, generating an executable path set, and allocating a dynamic analysis node to each path; 3, through a dynamic analysis tool, performing dynamic analysis by using an automatic single-step debugging method, enabling a program to be executed according to a control flow sequence of executable paths obtained by static analysis, and obtaining an API call correlation of a malicious code; and 4, according to API call correlation analysis, obtaining a behavior feature value of the malicious code. A behavior feature of the code can be represented more accurately, so that the analysis and detection of the malicious code are more accurate.
Owner:SICHUAN CHANGHONG ELECTRIC CO LTD
Hybrid Program Analysis
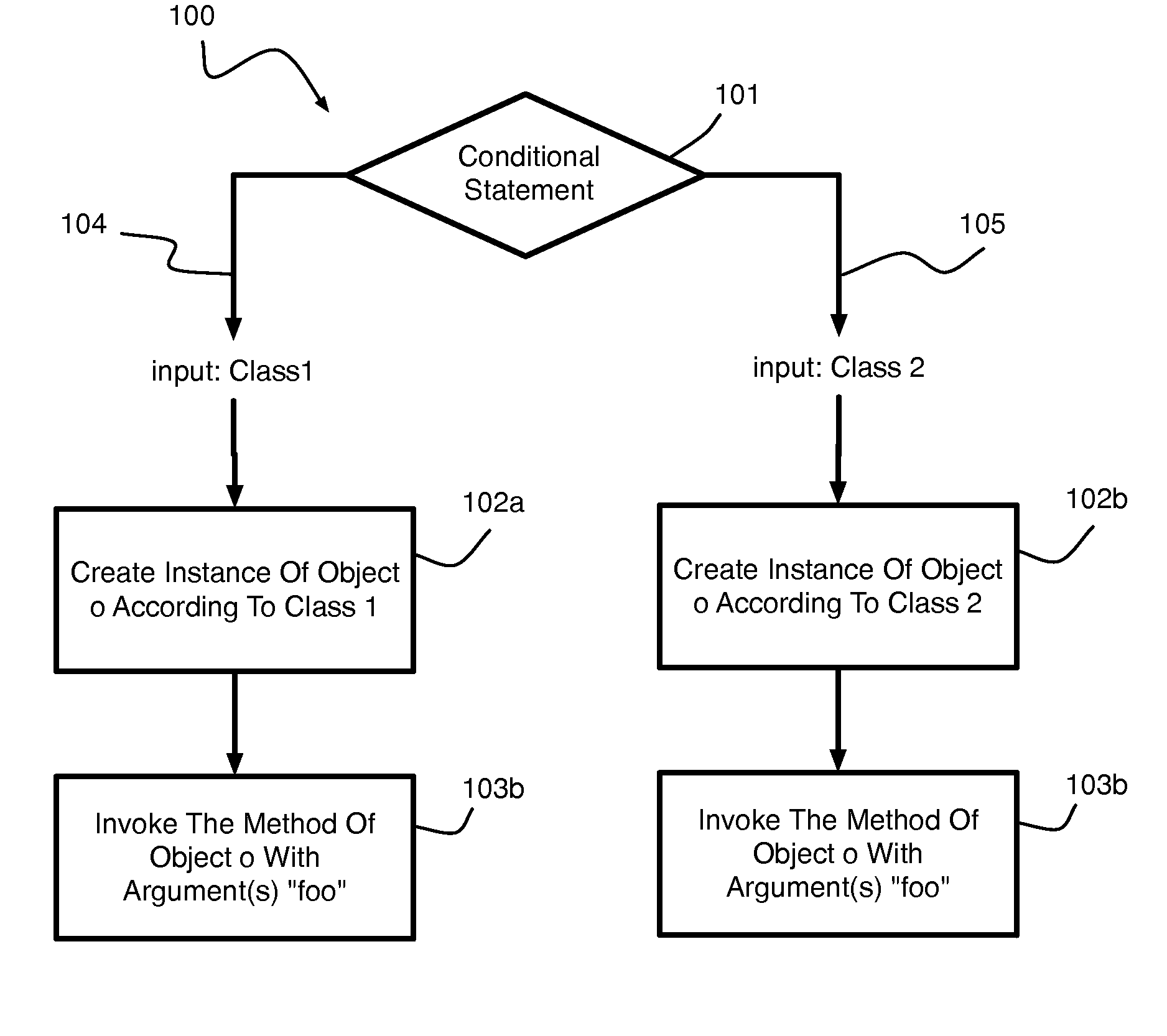
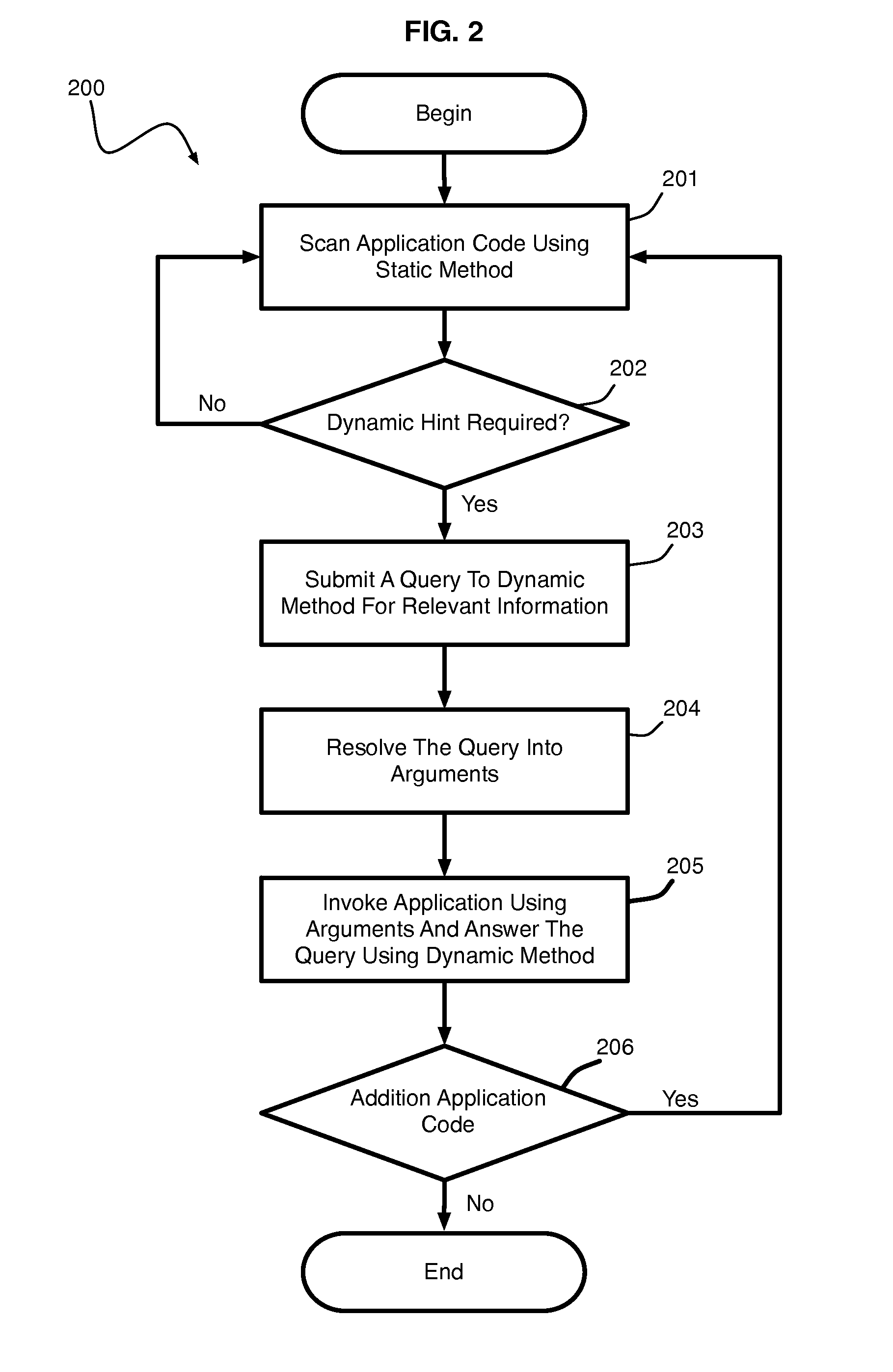
ActiveUS20140130019A1Error detection/correctionReverse engineeringDynamic program analysisApplication software
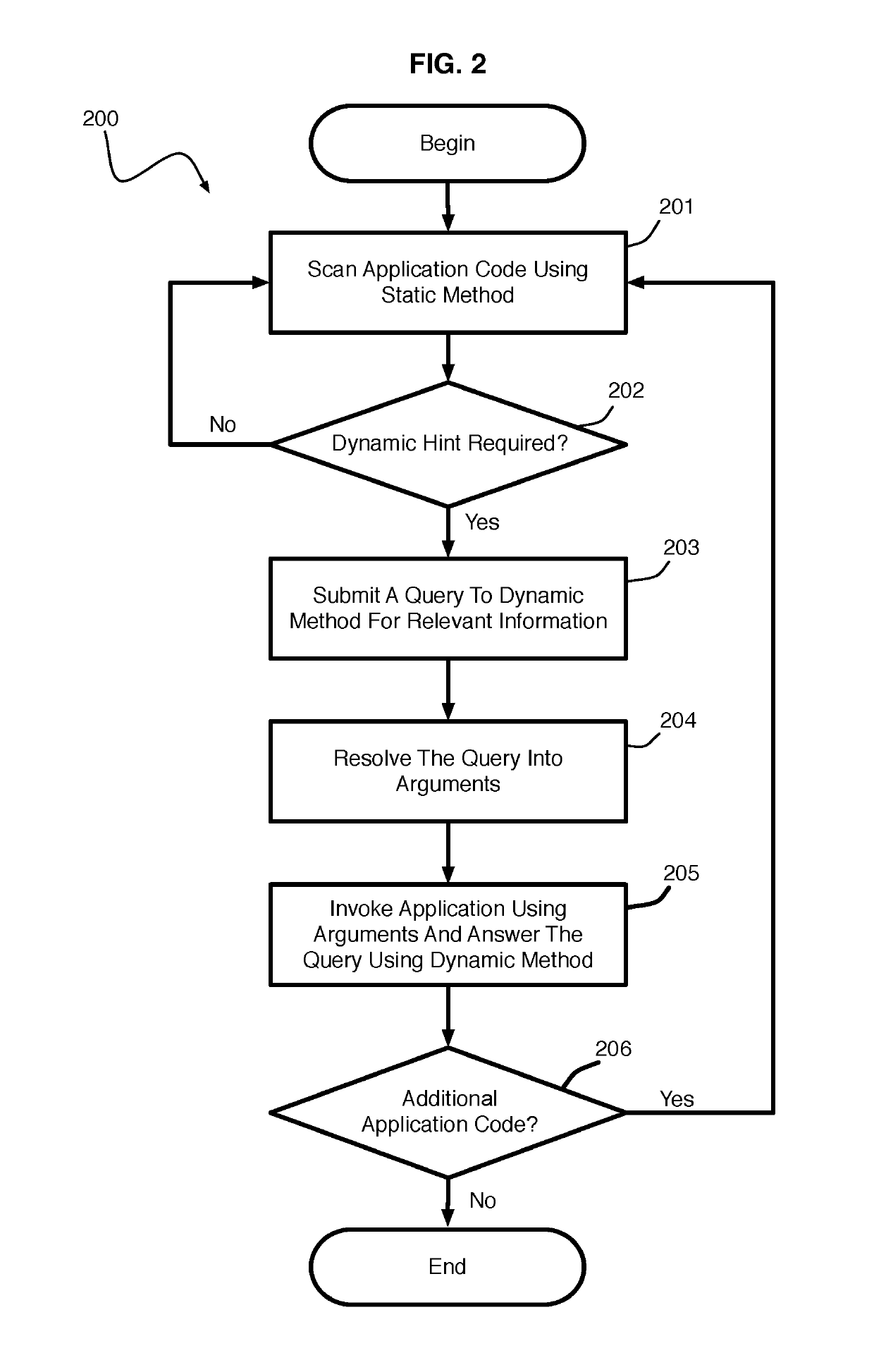
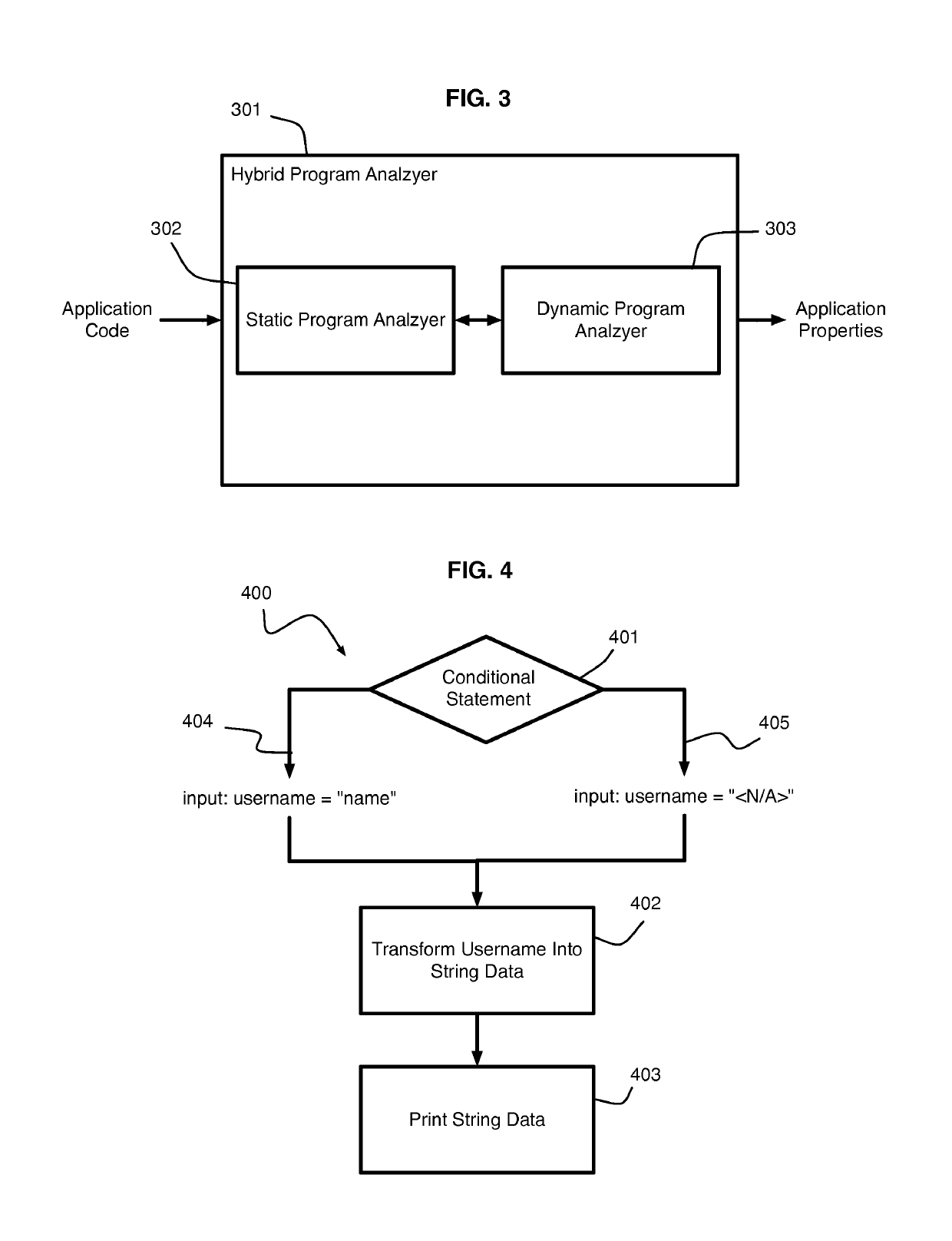
A hybrid program analysis method includes initiating a static program analysis of an application, generating, by a static program analyzer, a query to a dynamic program analyzer upon determining a code construct of the application requiring dynamic analysis, resolving, by the dynamic program analyzer, the query into a set of arguments with which to invoke the code construct of the application, generating, by the dynamic program analyzer, the set of arguments, invoking, by the dynamic program analyzer, the code construct of the application using set of arguments, answering, by the dynamic program analyzer, the query, and continuing the static program analysis of the application.
Owner:IBM CORP
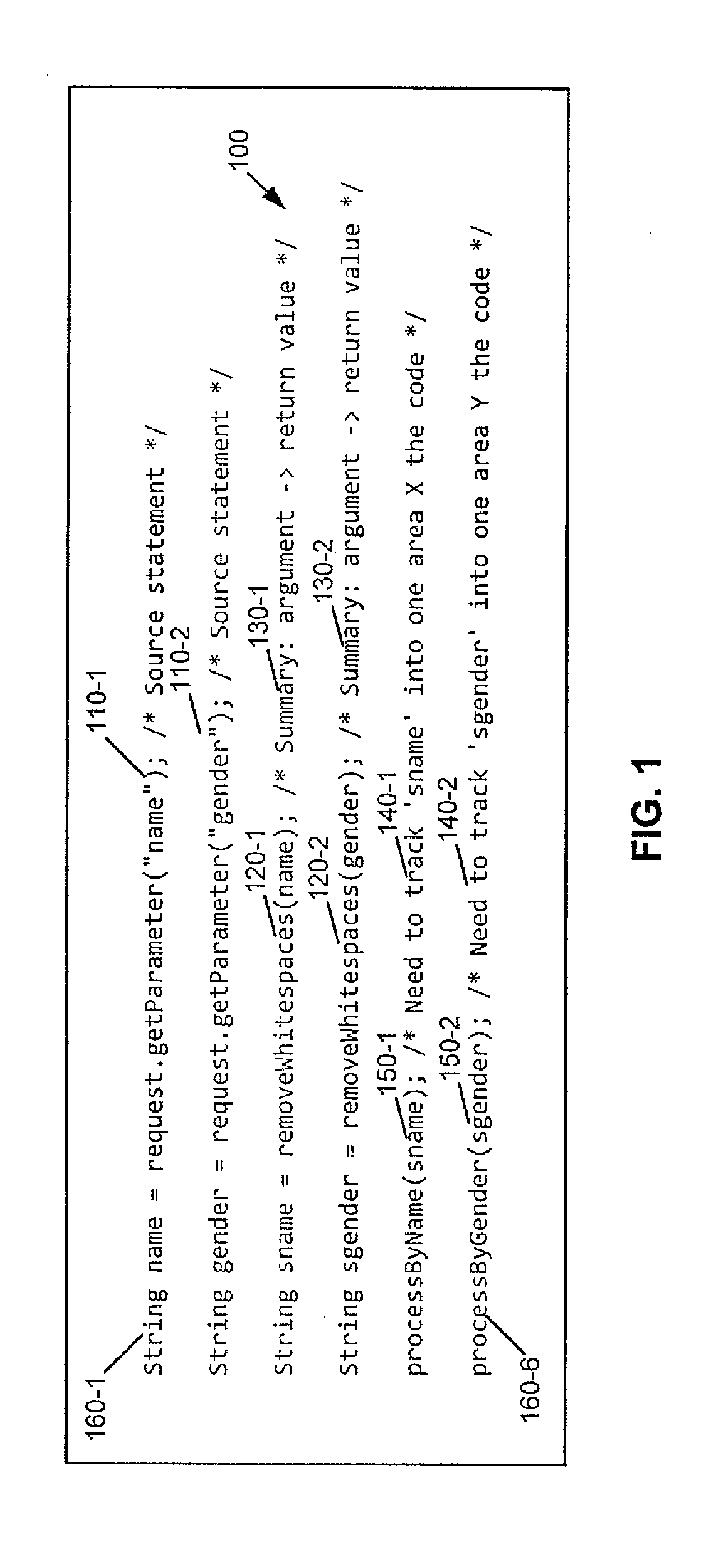
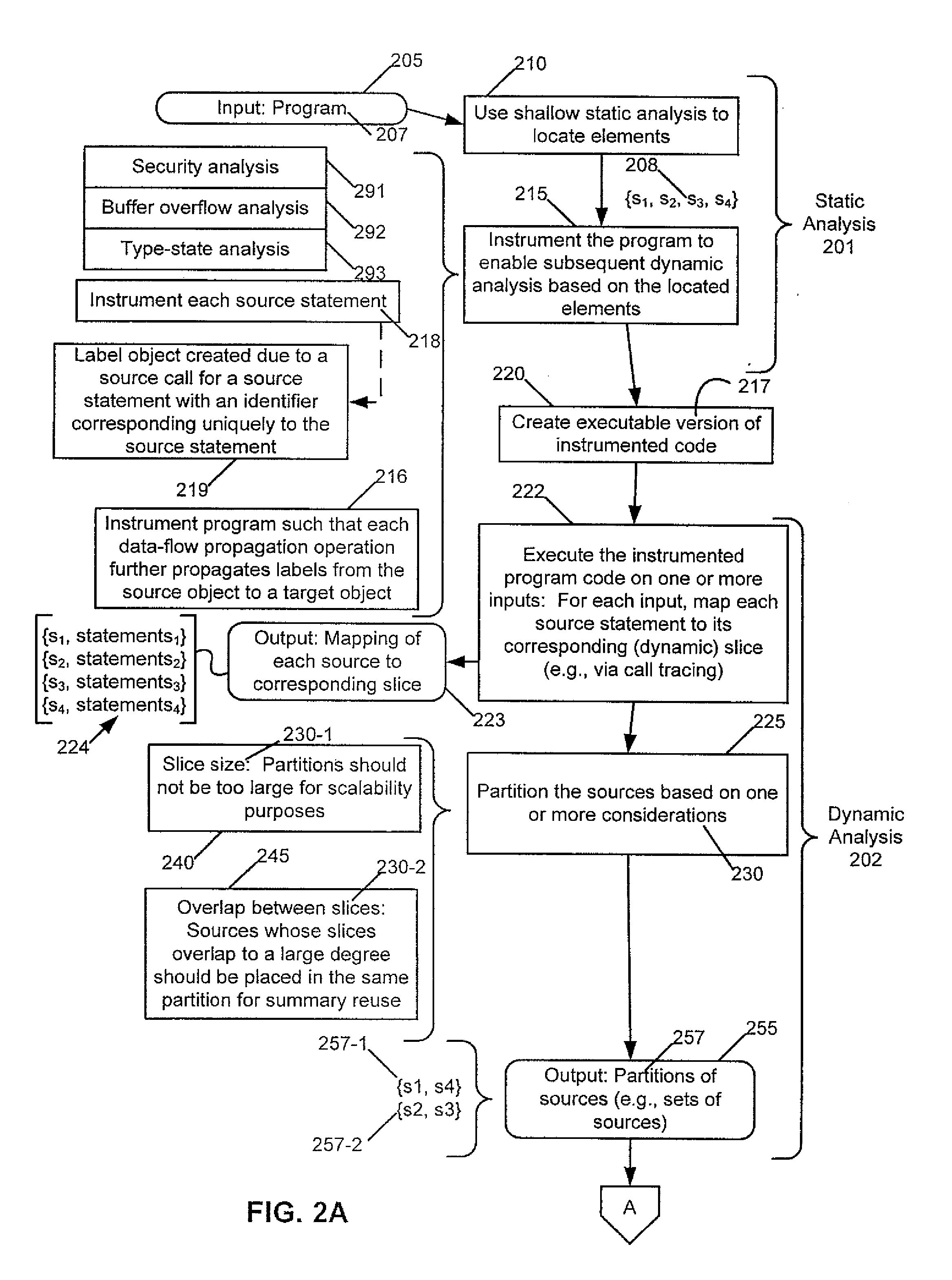
Partitioning of Program Analyses into Sub-Analyses Using Dynamic Hints
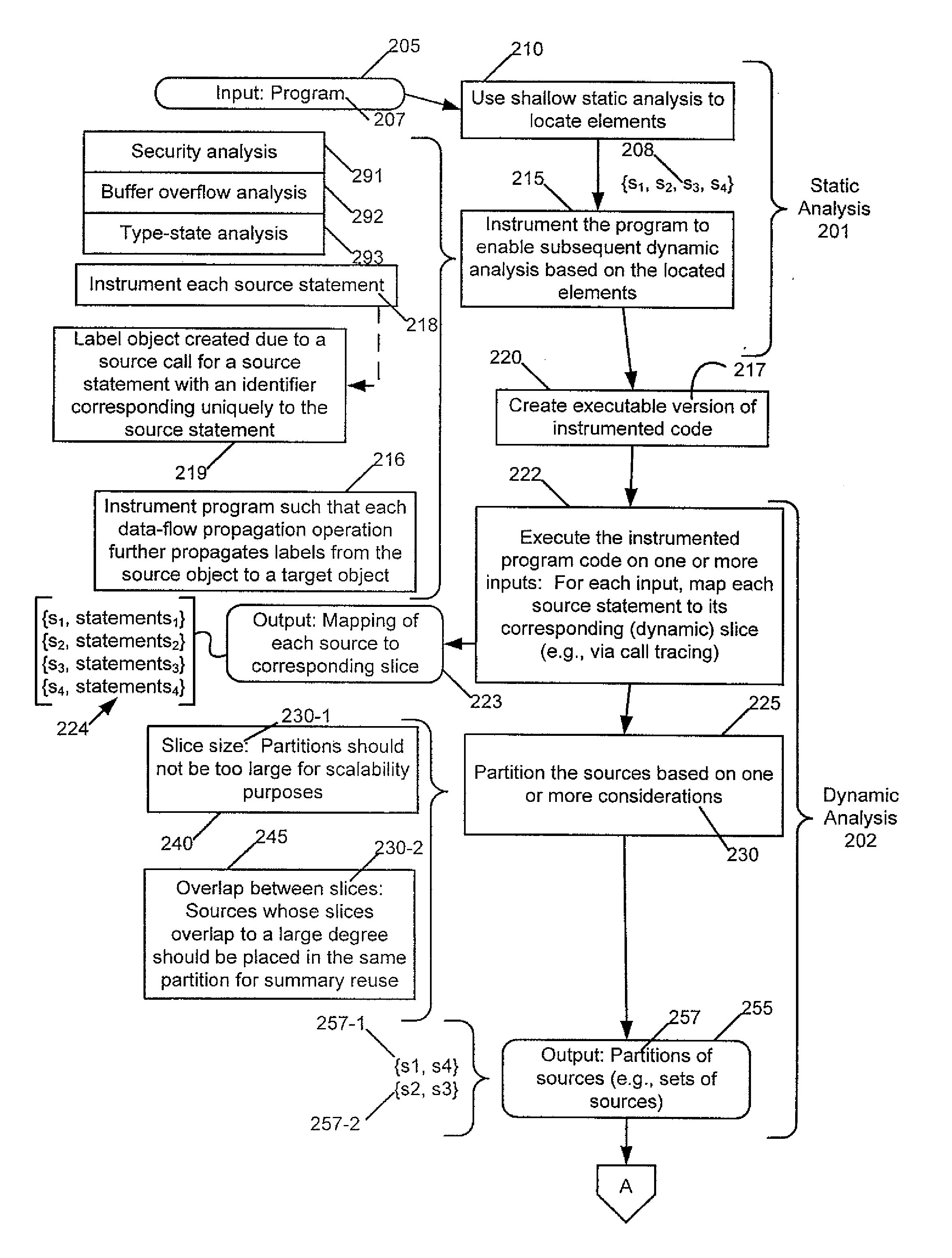
InactiveUS20140317748A1Increase in sizeMemory loss protectionUnauthorized memory use protectionTypestate analysisBuffer overflow
An exemplary apparatus and computer program product are disclosed which employ a method that includes performing a first static analysis to locate elements within a program and instrumenting the program to enable a subsequent dynamic analysis based on the located elements. The method includes executing the instrumented program and performing during execution analysis to determine individual sets of statements in the program affected by a corresponding element. The method includes partitioning the sets of statements into partitions based on one or more considerations, each partition including one or more of the elements. The method includes performing a second static analysis on the partitions of the program to produce results and outputting the results. The method may be performed for, e.g., security (e.g., taint) analysis, buffer overflow analysis, and typestate analysis.
Owner:GLOBALFOUNDRIES INC
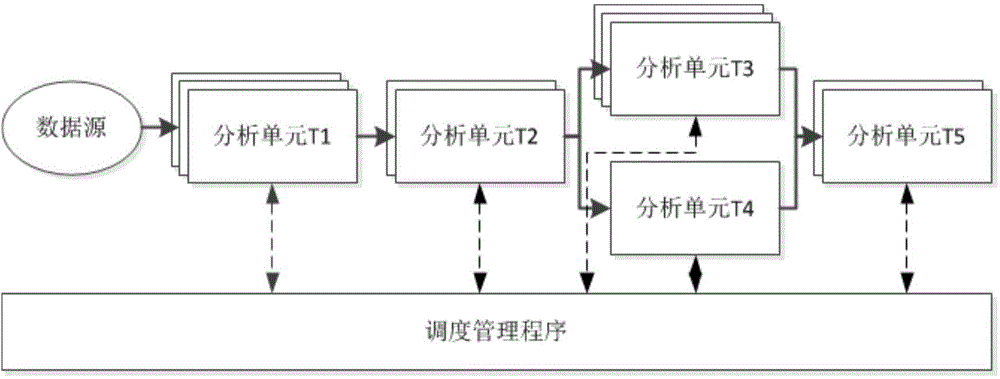
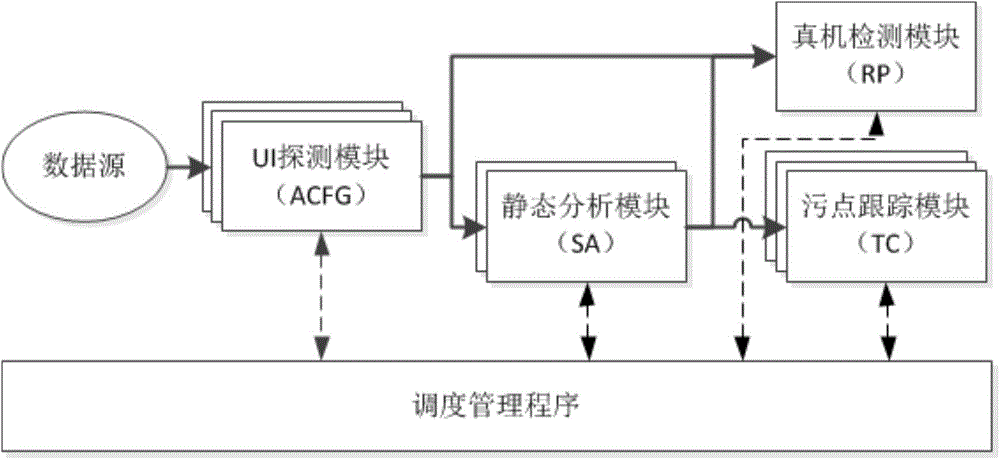
System and method for automatic program analysis based on strategy
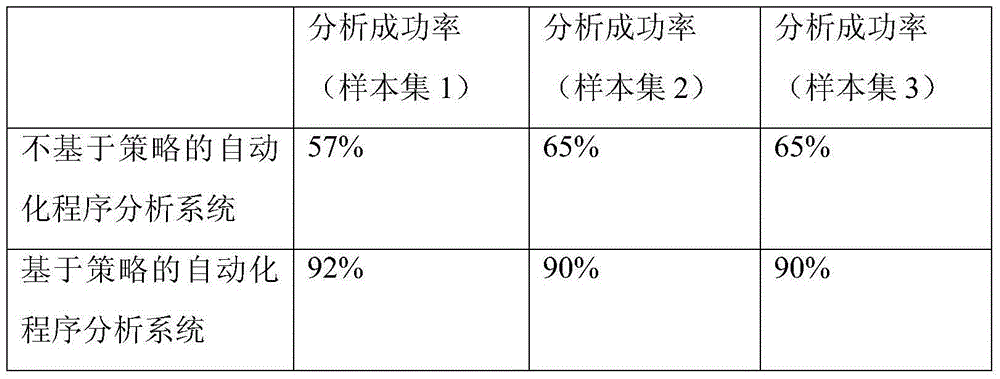
ActiveCN106155880AImprove accuracyImplement parallel processingSoftware testing/debuggingData sourceSoftware analytics
The invention relates to a system and a method for automatic program analysis based on a strategy. The system comprises a data source, analysis units, and a dispatching management program. The data source is a set of to-be-analyzed software. The analysis unit is a packaged software analysis module, and is used to communicate with a scheduler, to complete program security analysis of a certain method or a certain stage of assigned software. The dispatching management program is used to configure an analysis strategy, and realizes dispatching and management of an analysis task through analyzing the configured analysis strategy and monitoring states of the plurality of analysis units, to form effective joining and combination of each analysis unit. Through the pre-configured strategy and global task dispatching, a plurality of analysis modules or a plurality of analysis stages are automatically joined, so as to realize a complete, efficient, and automatic analysis process of a program.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
Static program analysis system for target code
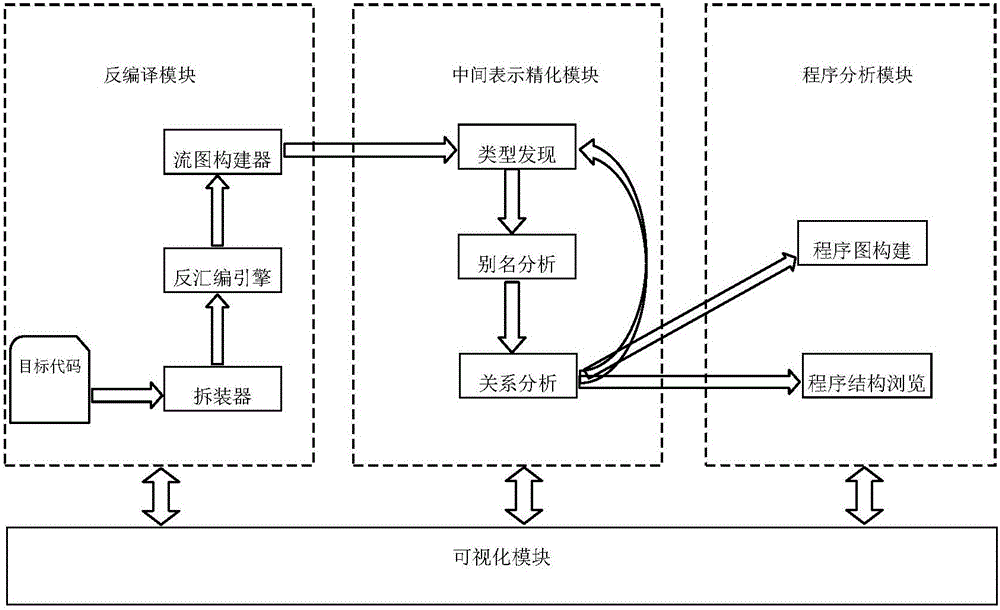
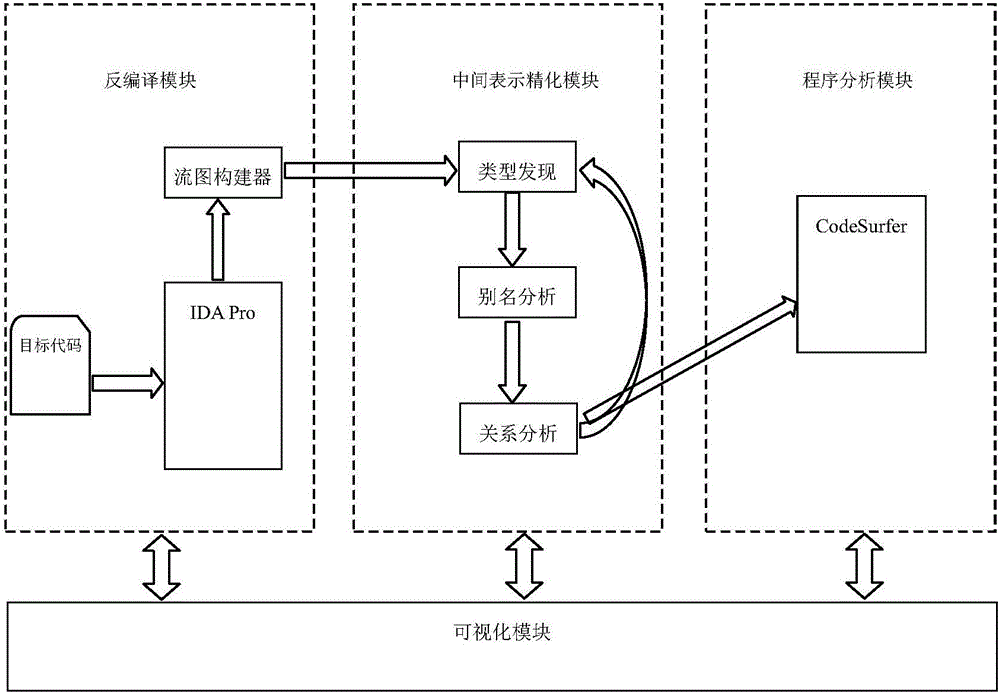
InactiveCN106649095AGuaranteed correctnessThe result is accurateSoftware testing/debuggingGraphicsObject code
The invention discloses a static program analysis system for a target code. The system comprises a decompilation module, an intermediate expression refinement module, a program analysis module and a visual module. The decompilation module adopts a to-be-analyzed target code file as input, performs packaging format removal and decompilation operations on an input file, generates an assembly code, a control flowchart and process boundary and other information and adopts the same as the output of the model; the intermediate expression refinement module generates a corresponding data structure and performs a refinement operation according to the information generated by the decompilation module; the program analysis module generates several expression forms of the to-be-analyzed program according to the information output by the decompilation module and the intermediate expression refinement module; and the visual module is applied to visible display of various patterns and other information in an analysis process. The system analyzes the program behaviors according to actually executed binary codes and has higher fidelity compared with an analysis tool for source codes.
Owner:EAST CHINA NORMAL UNIV
Program analysis and variation input-based cross-site script attack detection method
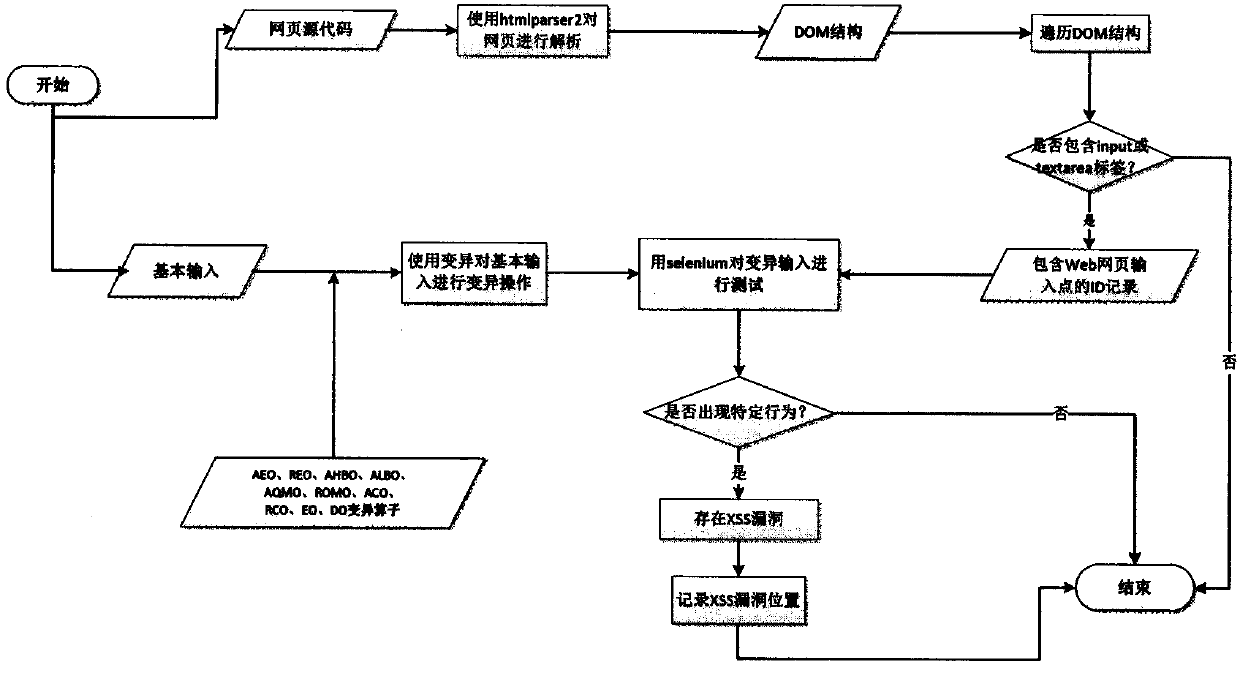
InactiveCN107844701AImprove scalabilityHigh-precision detectionPlatform integrity maintainanceDynamic program analysisWeb page
The invention discloses a program analysis and variation input-based cross-site script attack detection method. The method comprises the steps of firstly, analyzing a crawled webpage by using htmlparser2 to obtain a DOM structure of the webpage; secondly, finding all possible input points in a website by traversing the DOM structure, and recording IDs of the input points; thirdly, generating possible user inputs in combination with a variation operator; and finally, automatically running a test script by using a tool Selenium, and mining possibly existent XSS vulnerabilities in the website.
Owner:NANJING UNIV
Preference setting-oriented Android application testing method
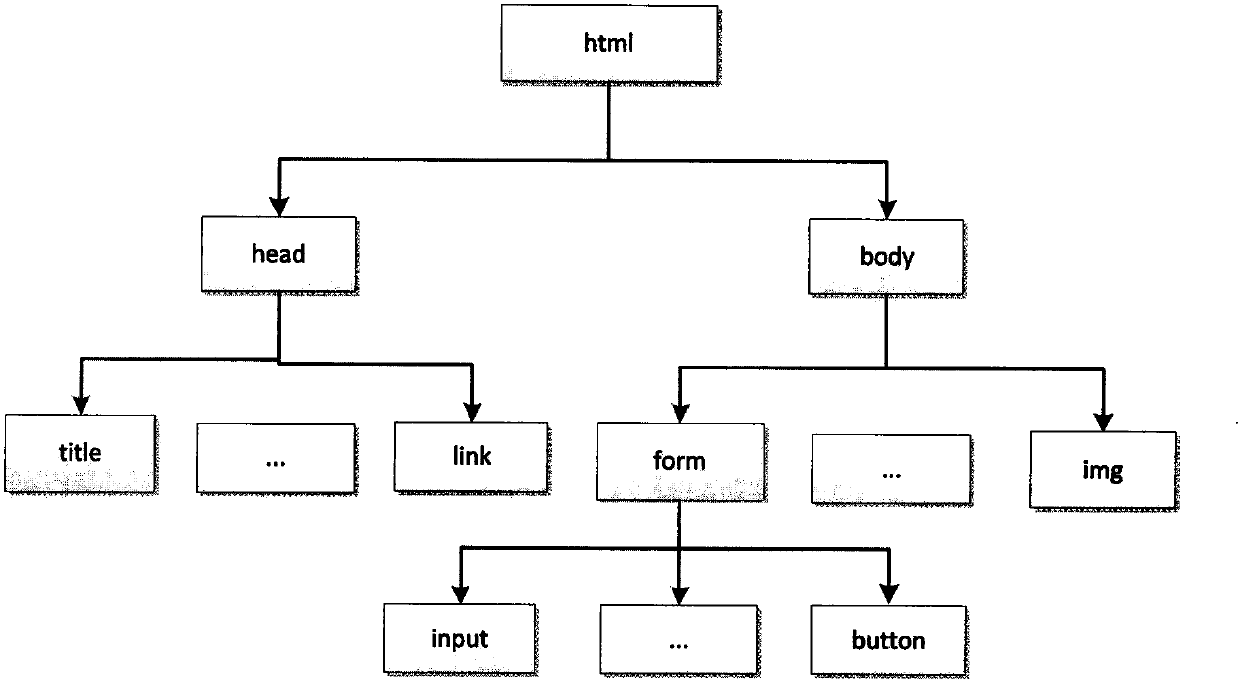
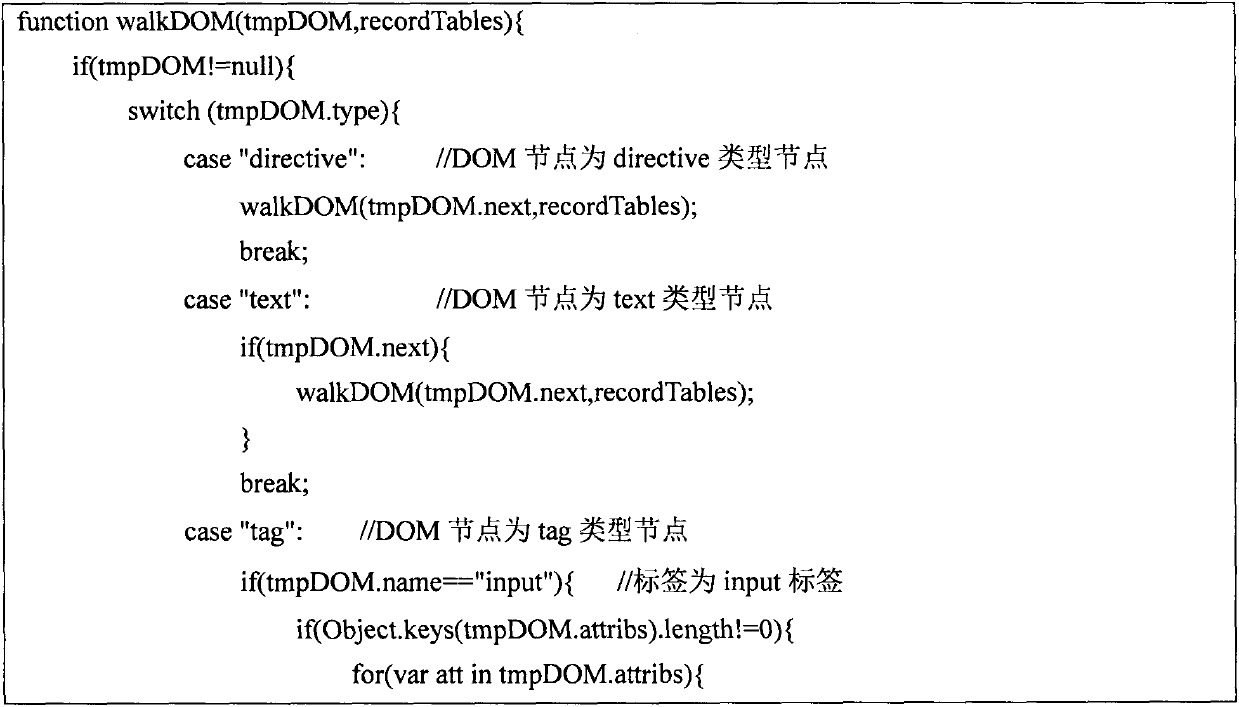
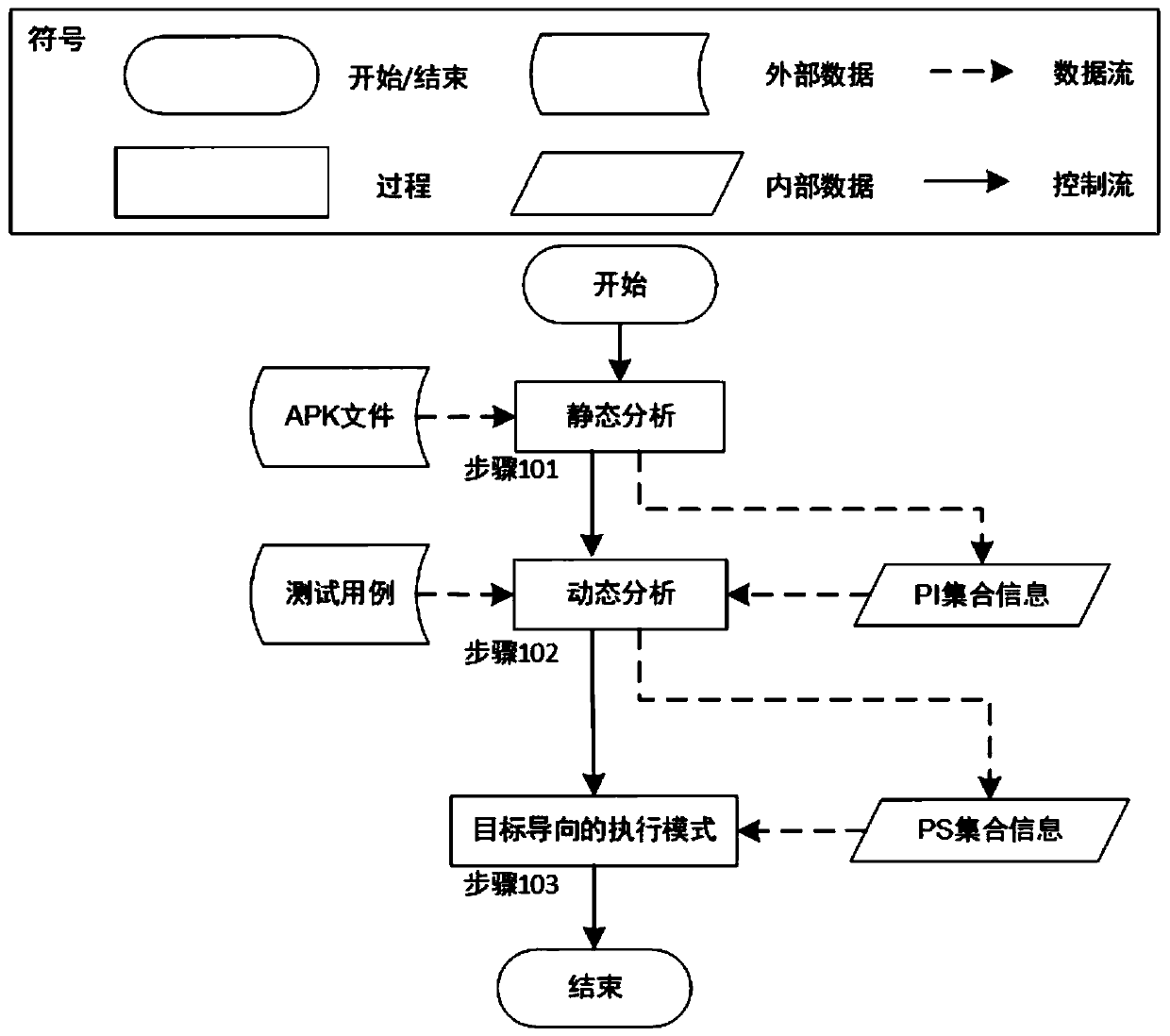
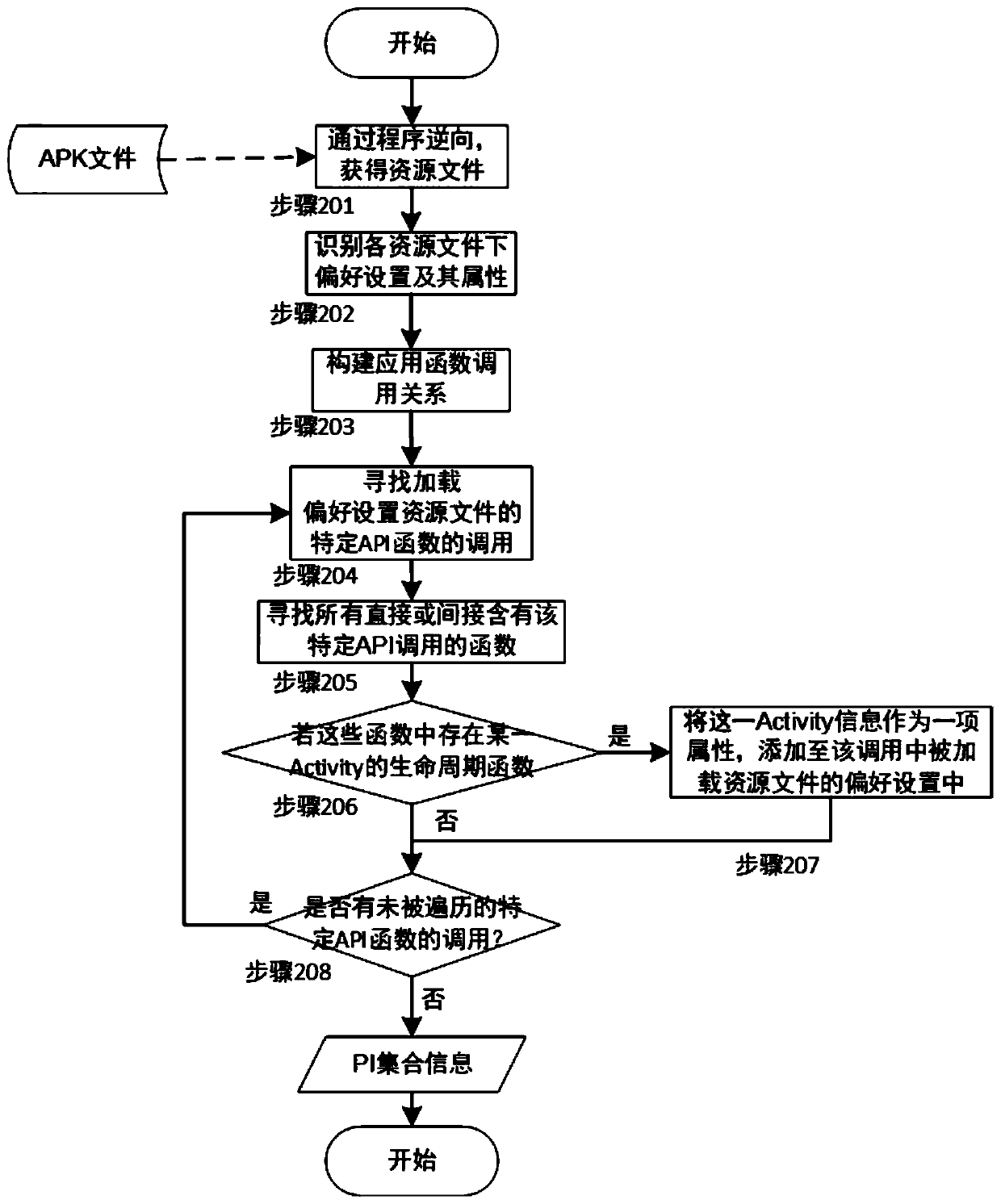
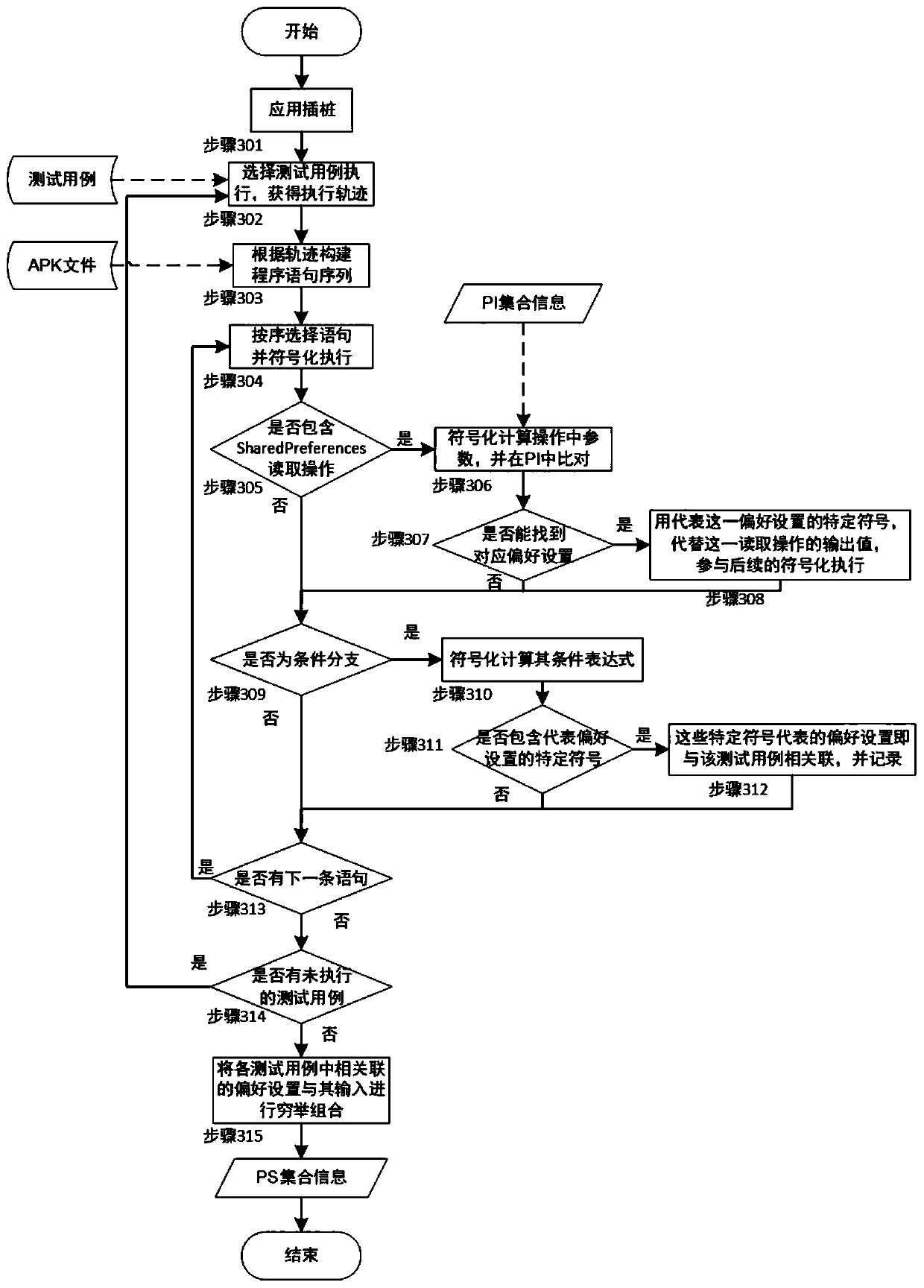
ActiveCN110209593AReduce testingReduce testing costsSoftware testing/debuggingGreedy algorithmDynamic program analysis
The invention provides a preference setting-oriented Android application testing method. The method comprises the following steps: firstly, performing static program analysis on an executable file ofan application to be tested to obtain all preference settings defined in the application and attributes thereof; and then, on the existing test cases, obtaining relevant preference settings in the test cases in a dynamic program analysis manner. For each test case, a combination of all related preference settings and its possible inputs can be tested to implement a preference setting-oriented test. Finally, in order to reduce the cost of the test, the invention provides a target-oriented execution mode, which divides the code of the test case into basic blocks, and combines the basic blocks with the input of the preference settings related thereto as the test target. According to the greedy algorithm, the combination of the test case covering the most test target and the preference settingis selected for testing, so that the repeated test of the preference setting input combination under each test case is reduced, and the test cost is greatly reduced.
Owner:NANJING UNIV
Identifying factorable code
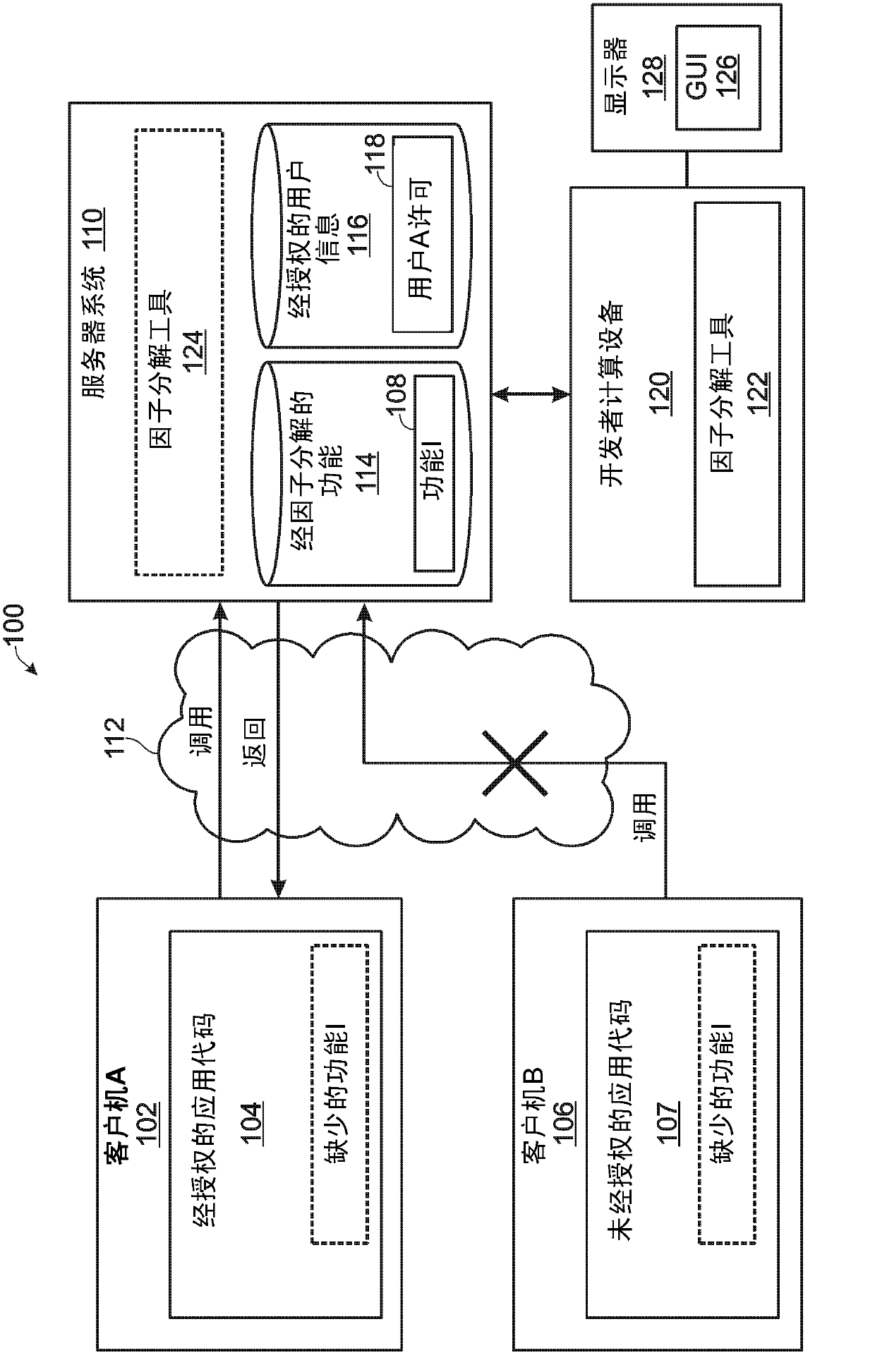
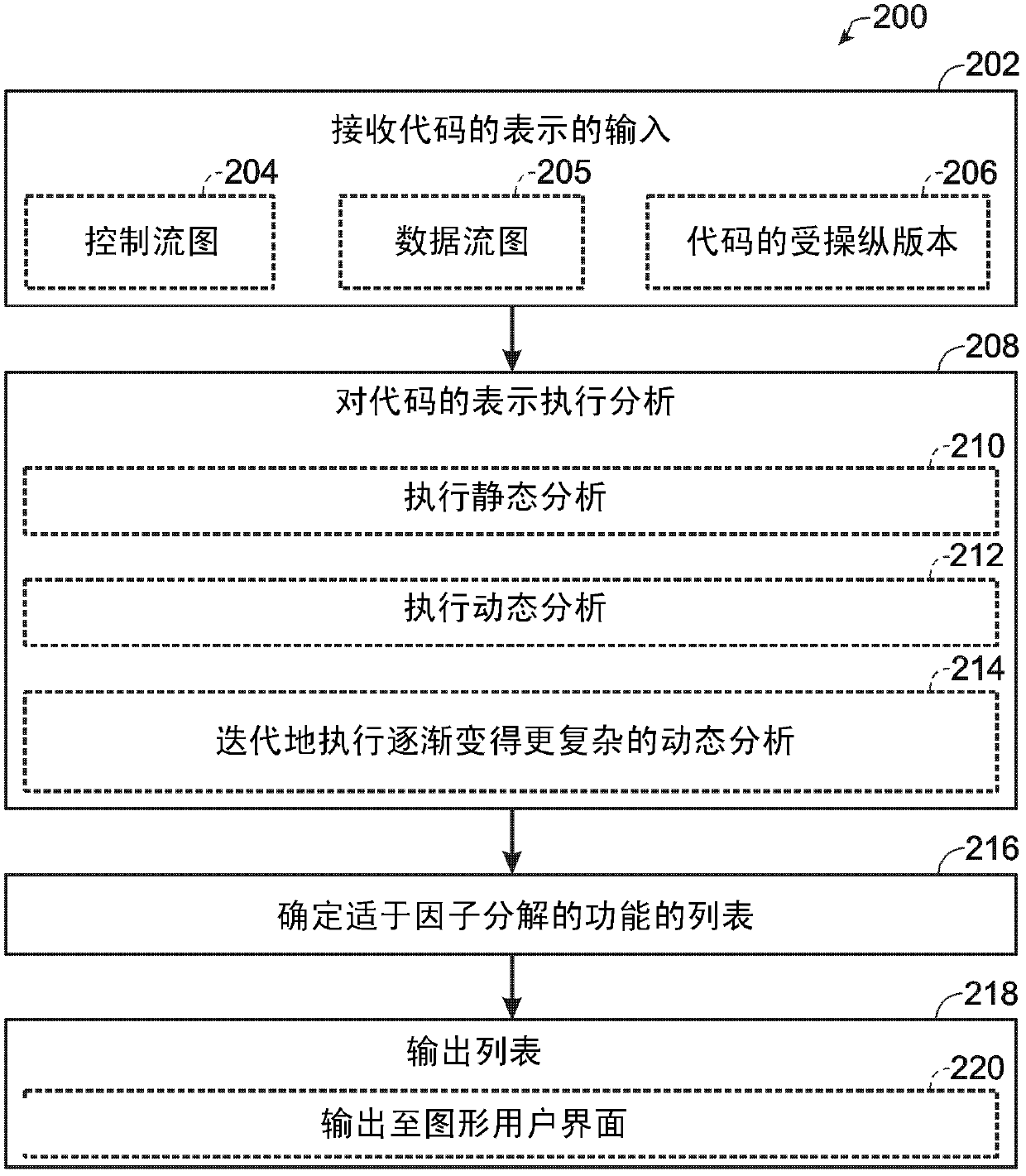
The invention relates to identifying factorable code. Various embodiments are disclosed that relate to the automated identification of one or more computer program functions for potentially placing on a remote computing device in a split-computational computing environment. For example, one disclosed embodiment provides, on a computing device, a method of determining a factorable portion of code to locate remotely from other portions of the code of a program to hinder unauthorized use and / or distribution of the program. The method includes, on a computing device, receiving an input of a representation of the code of the program, performing analysis on the representation of the code, the analysis comprising one or more of static analysis and dynamic analysis, and based upon the analysis of the code, outputting a list of one or more functions determined from the analysis to be candidates for locating remotely.
Owner:MICROSOFT TECH LICENSING LLC
System for detecting software bug triggered during practical running of computer program
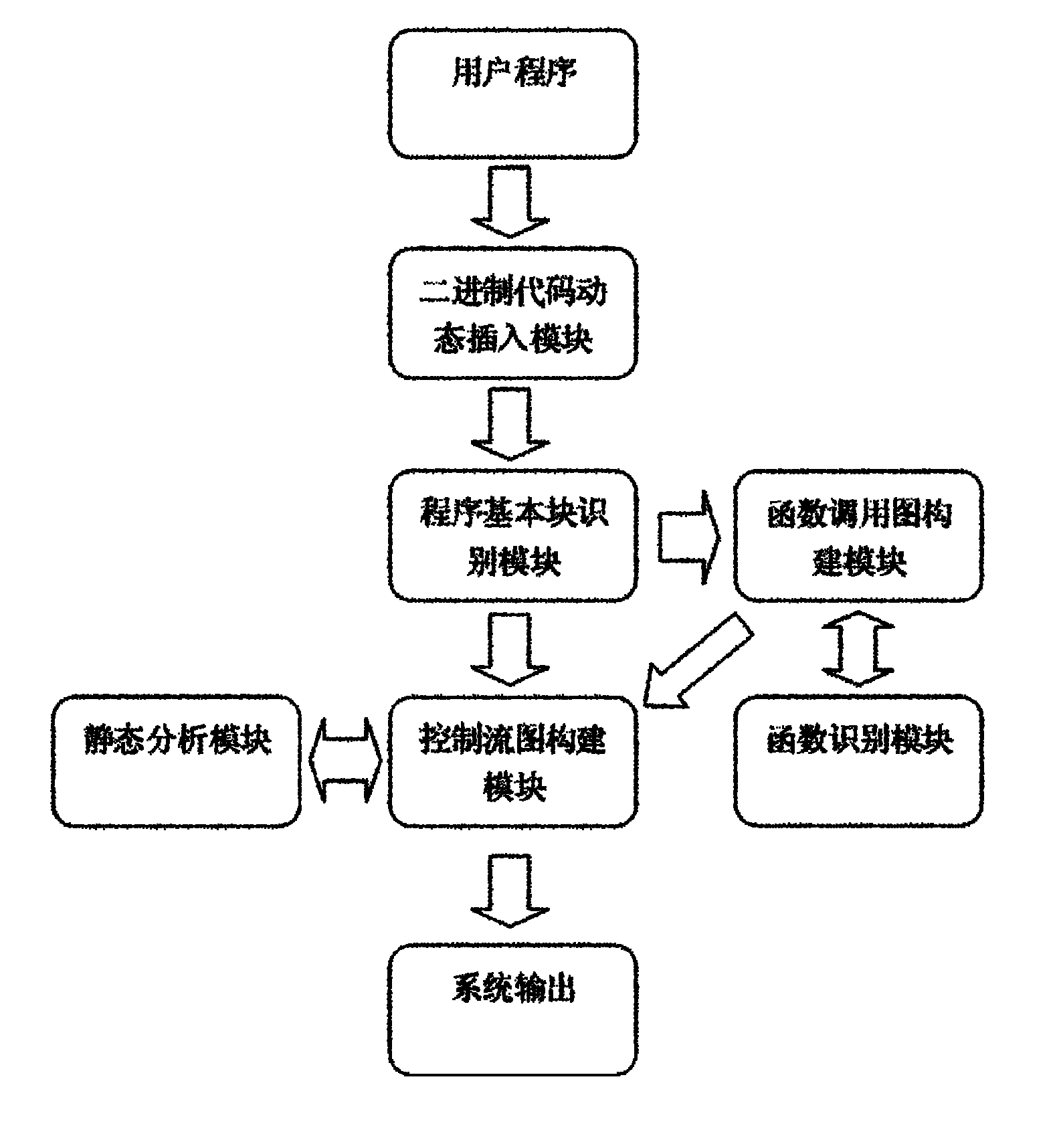
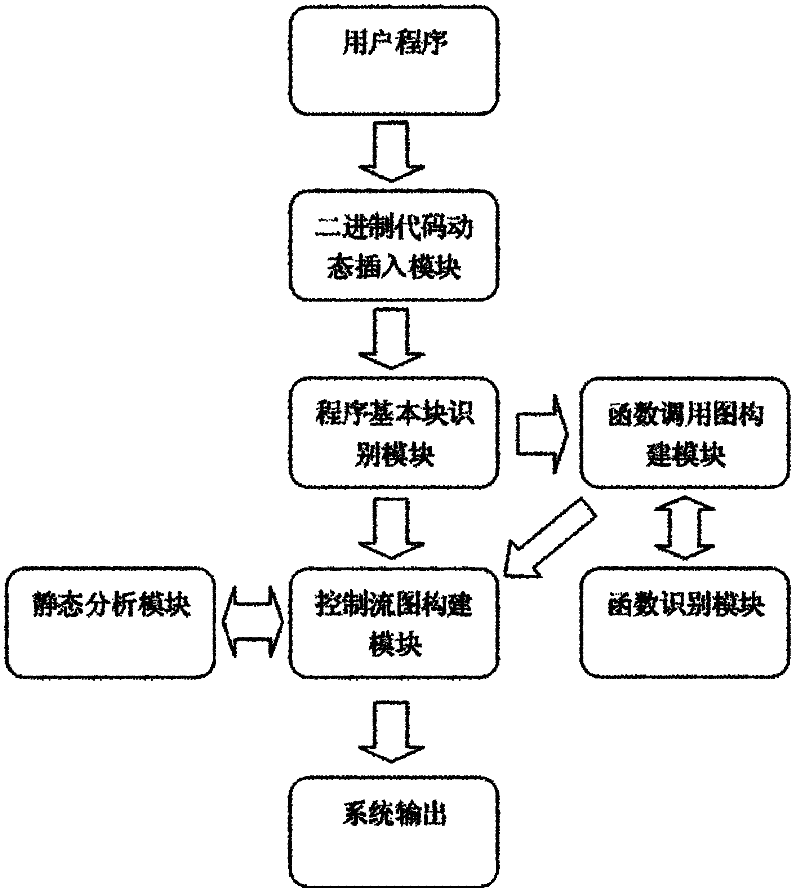
InactiveCN101968766BOvercoming the disadvantage of low analysis coverageHigh program executable path coverageSoftware testing/debuggingSoftware bugDynamic program analysis
The invention relates to a system for detecting a software bug triggered during practical running of a computer program in the technical field of computers. The system comprises a binary code dynamic inserting module, a program basic block recognizing module, a function call graph constructing module, a control flow graph constructing module, a function recognizing module and a static analysis module. By combining two technologies of dynamic program analysis and static analysis path complementation, the invention not only can detect the bugs which can be triggered during the practical runningof the program but also can reach higher program path coverage rate, carry out bug detects on the path which is not covered in the dynamic analysis process, improve the success rate of bug detection and reduce the false rate of the bugs. Meanwhile, the static analysis path complementation technology only analyzes a path which is not executed in dynamic analysis instead of all program paths, thereby greatly reducing the cost on time and system resources.
Owner:SHANGHAI JIAOTONG UNIV
Hybrid program analysis
ActiveUS10275238B2Reverse engineeringSoftware testing/debuggingDynamic program analysisApplication software
A hybrid program analysis method includes initiating a static program analysis of an application, generating, by a static program analyzer, a query to a dynamic program analyzer upon determining a code construct of the application requiring dynamic analysis, resolving, by the dynamic program analyzer, the query into a set of arguments with which to invoke the code construct of the application, generating, by the dynamic program analyzer, the set of arguments, invoking, by the dynamic program analyzer, the code construct of the application using set of arguments, answering, by the dynamic program analyzer, the query, and continuing the static program analysis of the application.
Owner:INT BUSINESS MASCH CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com