Patents
Literature
62 results about "Program profile" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
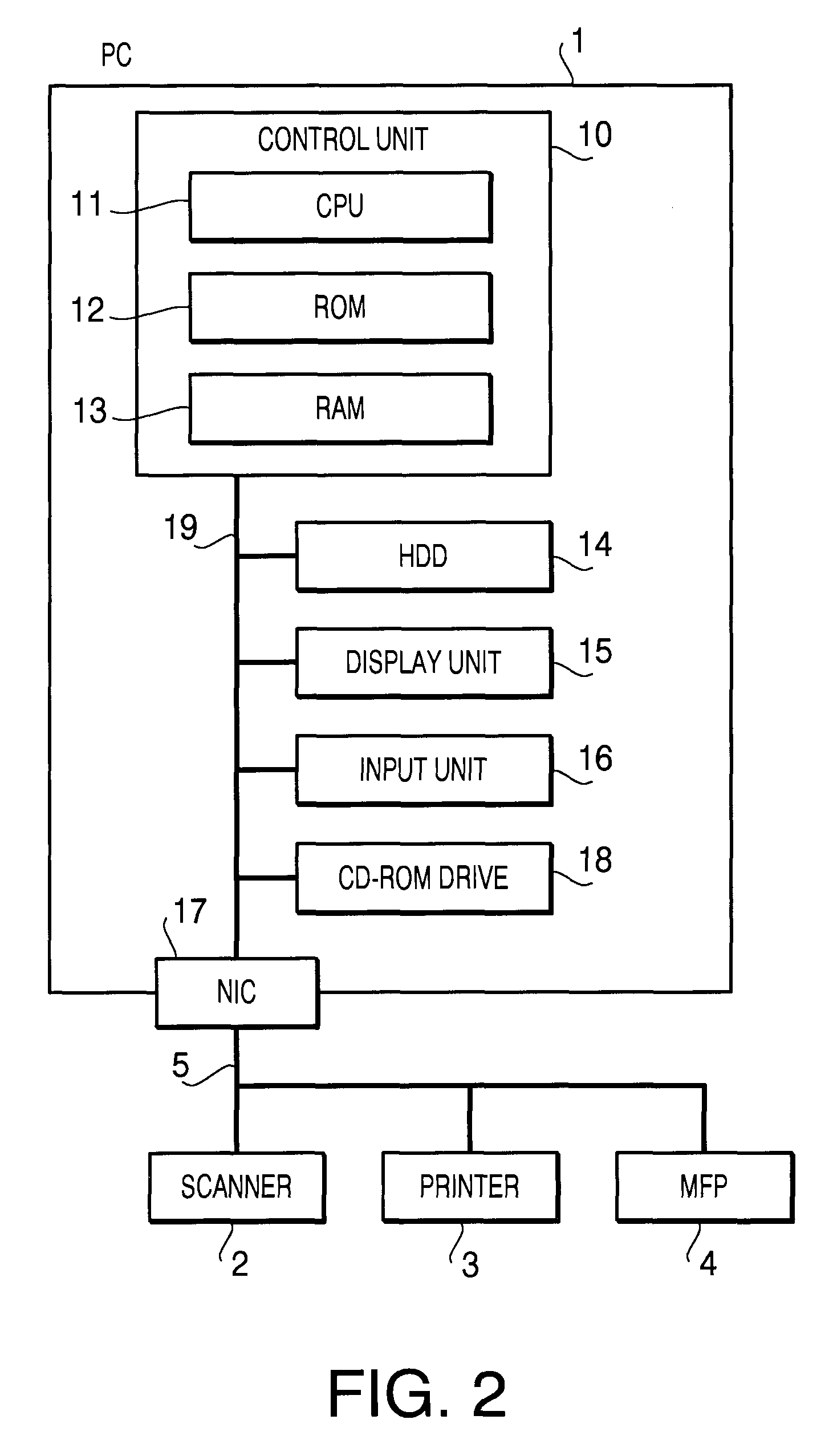
Personalized content processing and delivery system and media
ActiveUS20060123053A1Improve economyImprove utilizationDigital data information retrievalDigital data processing detailsPersonalizationUser input
Owner:INSIGNIO TECH
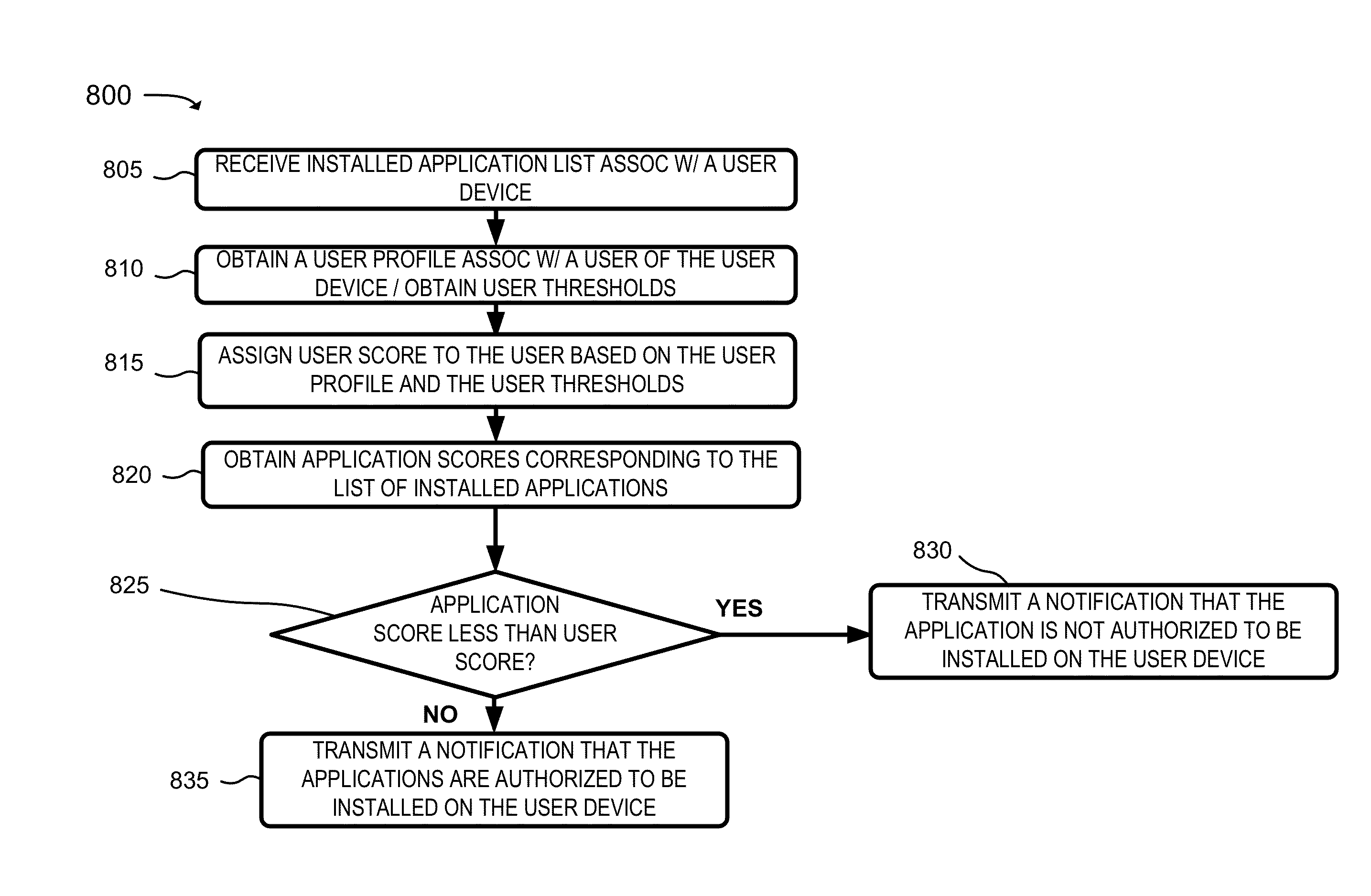
Mobile application security and management service
A system is configured to receive a list of applications installed on a user device; obtain application profiles that identify risk levels associated with the applications; obtain a user profile that identifies a job level, security risk level, or an access level to confidential information associated with the user of the user device; identify a highest risk level authorized for the user device based on whether the job level is greater than a first threshold, the security risk level is greater than a second threshold, or the access level is greater than a third threshold; determine whether any of the risk levels are greater than the highest risk level; and transmit a notification that one of the applications is to be removed from the user device when one of the risk levels, associated with the one of the applications, is greater than the highest risk level.
Owner:VERIZON PATENT & LICENSING INC
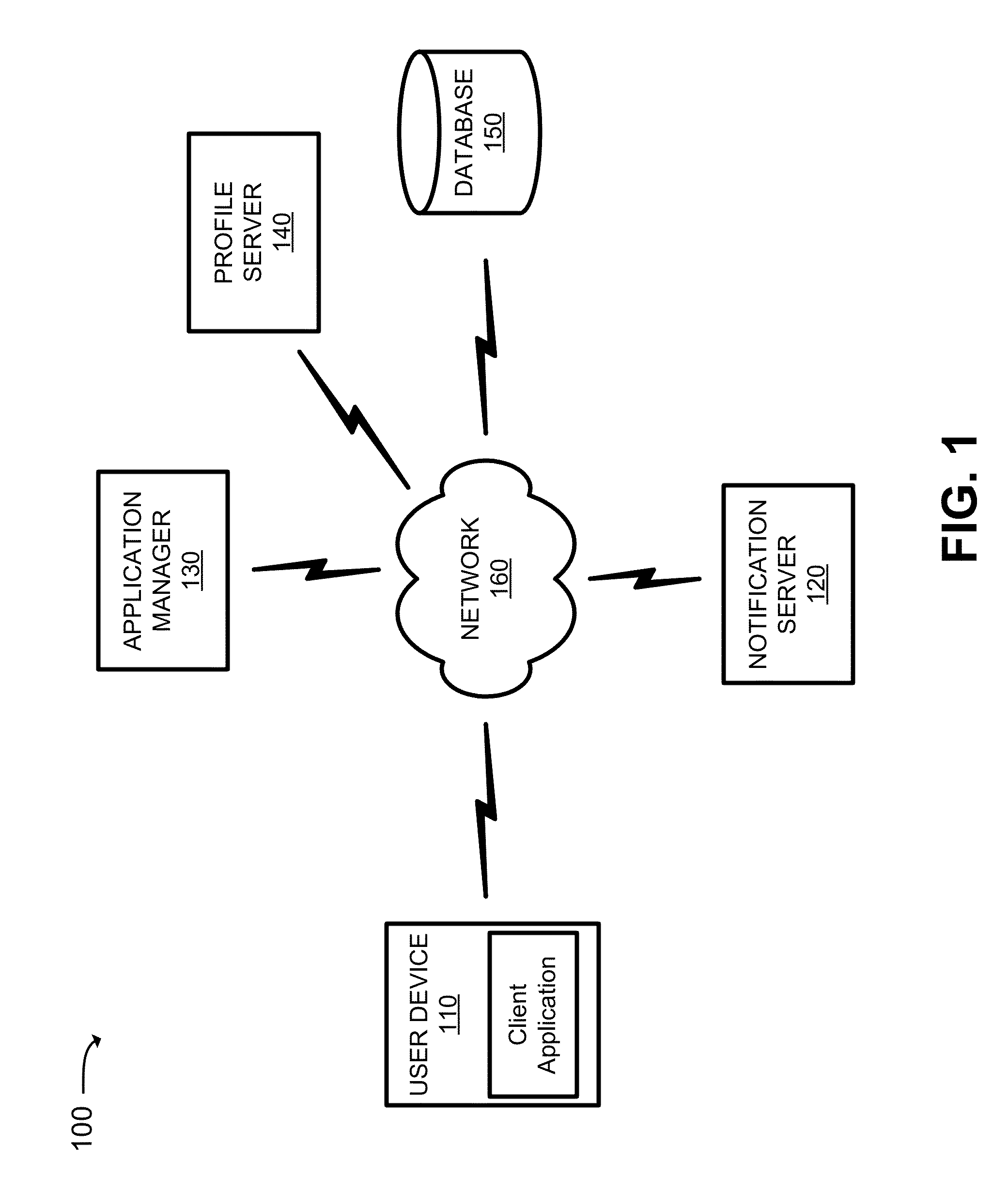
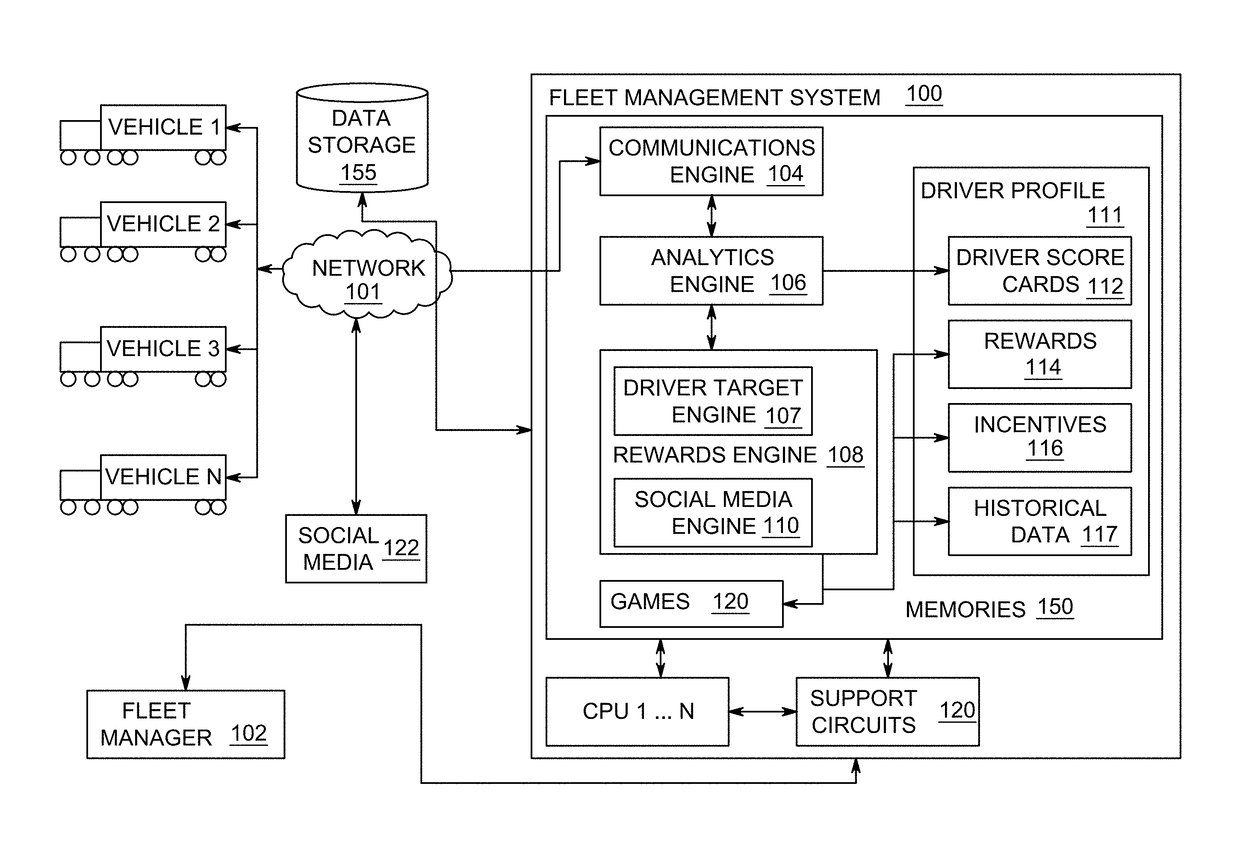
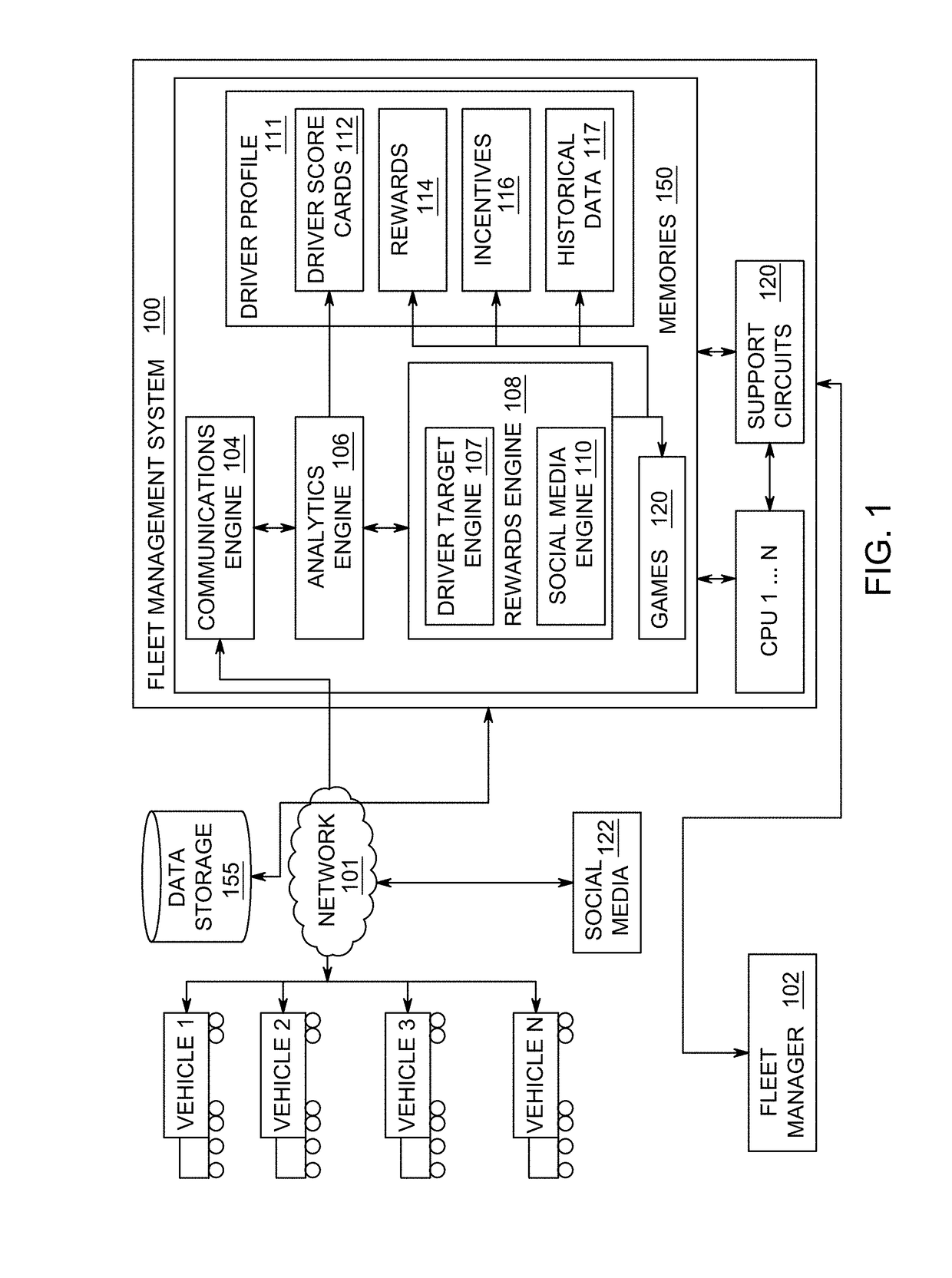
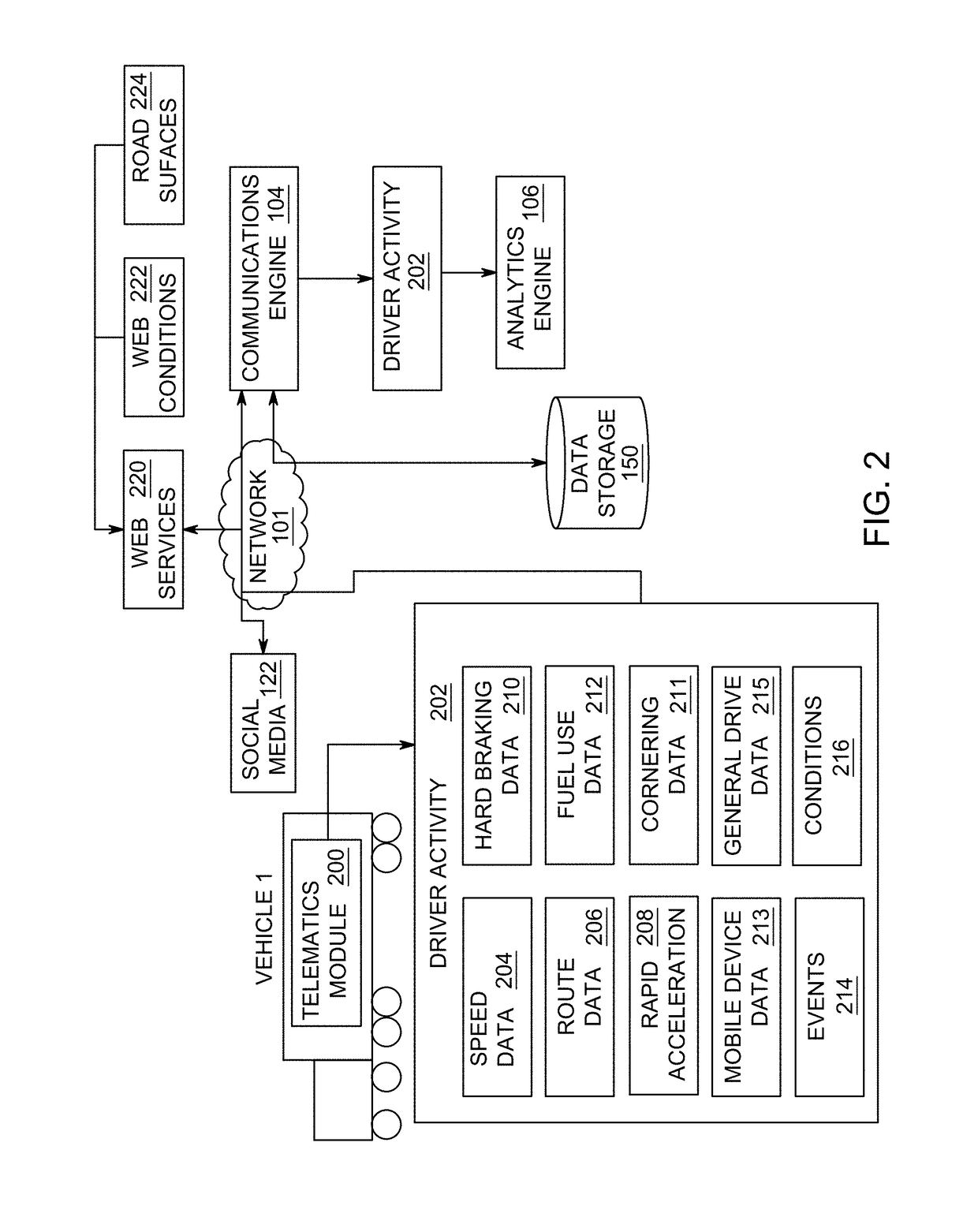
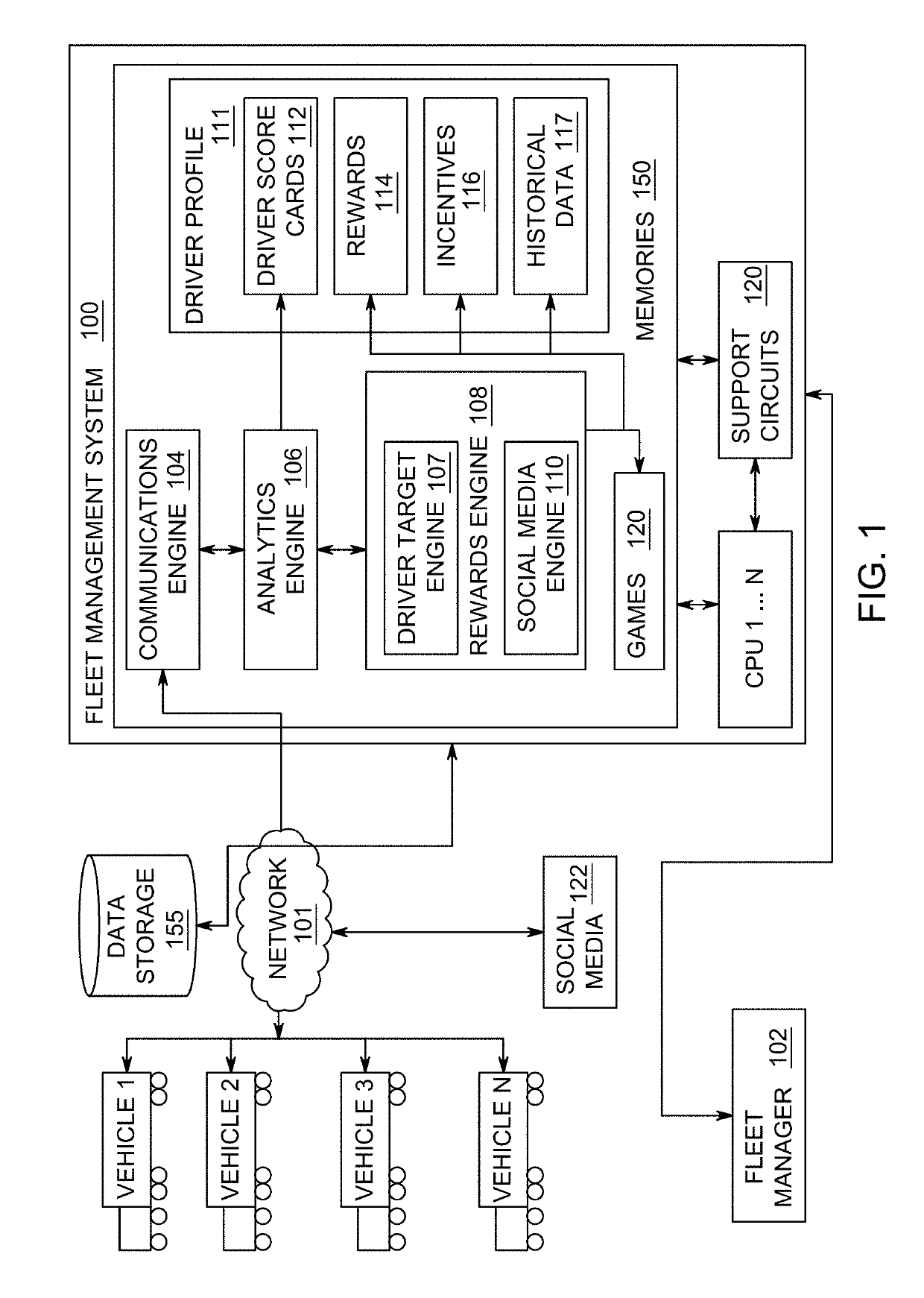
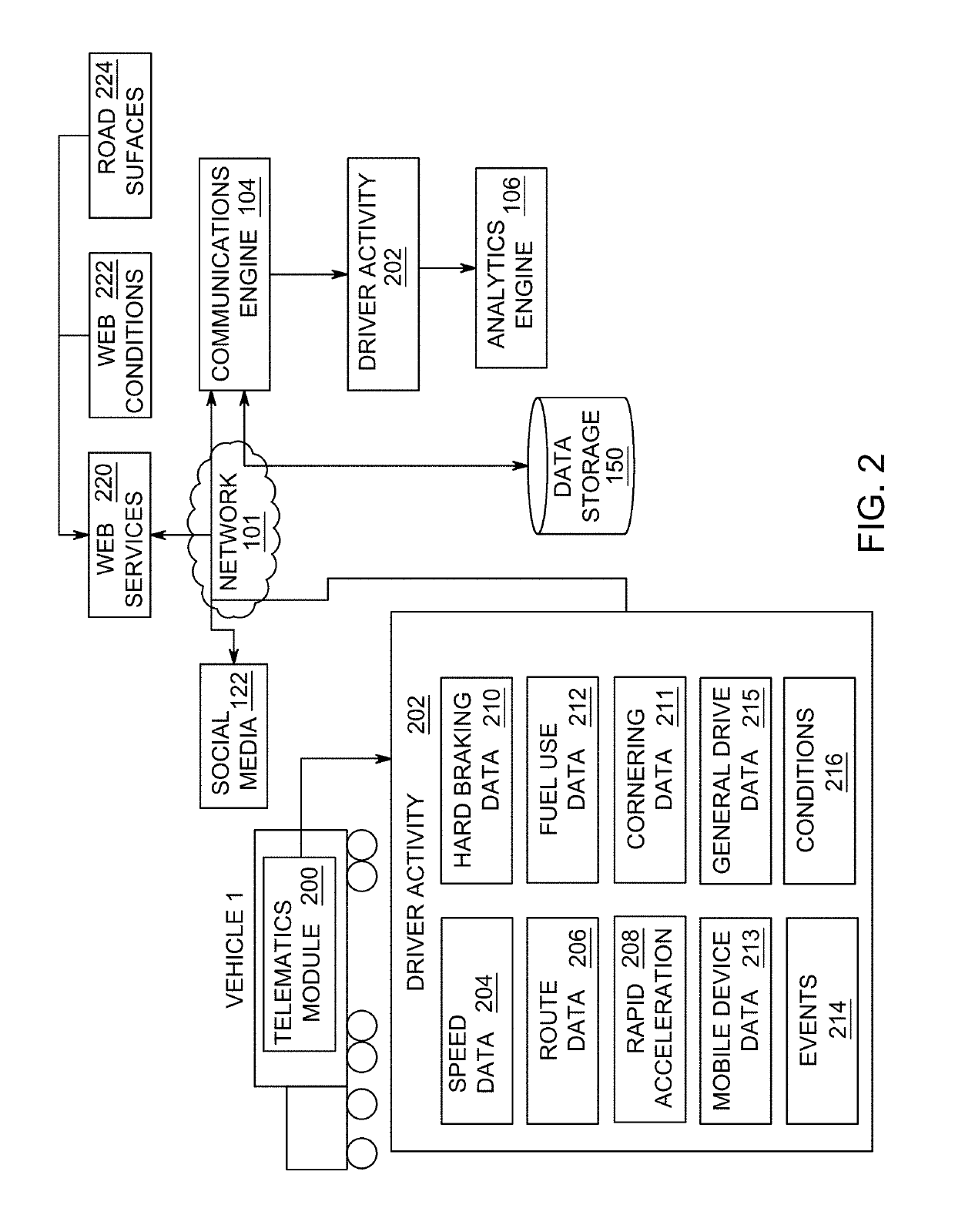
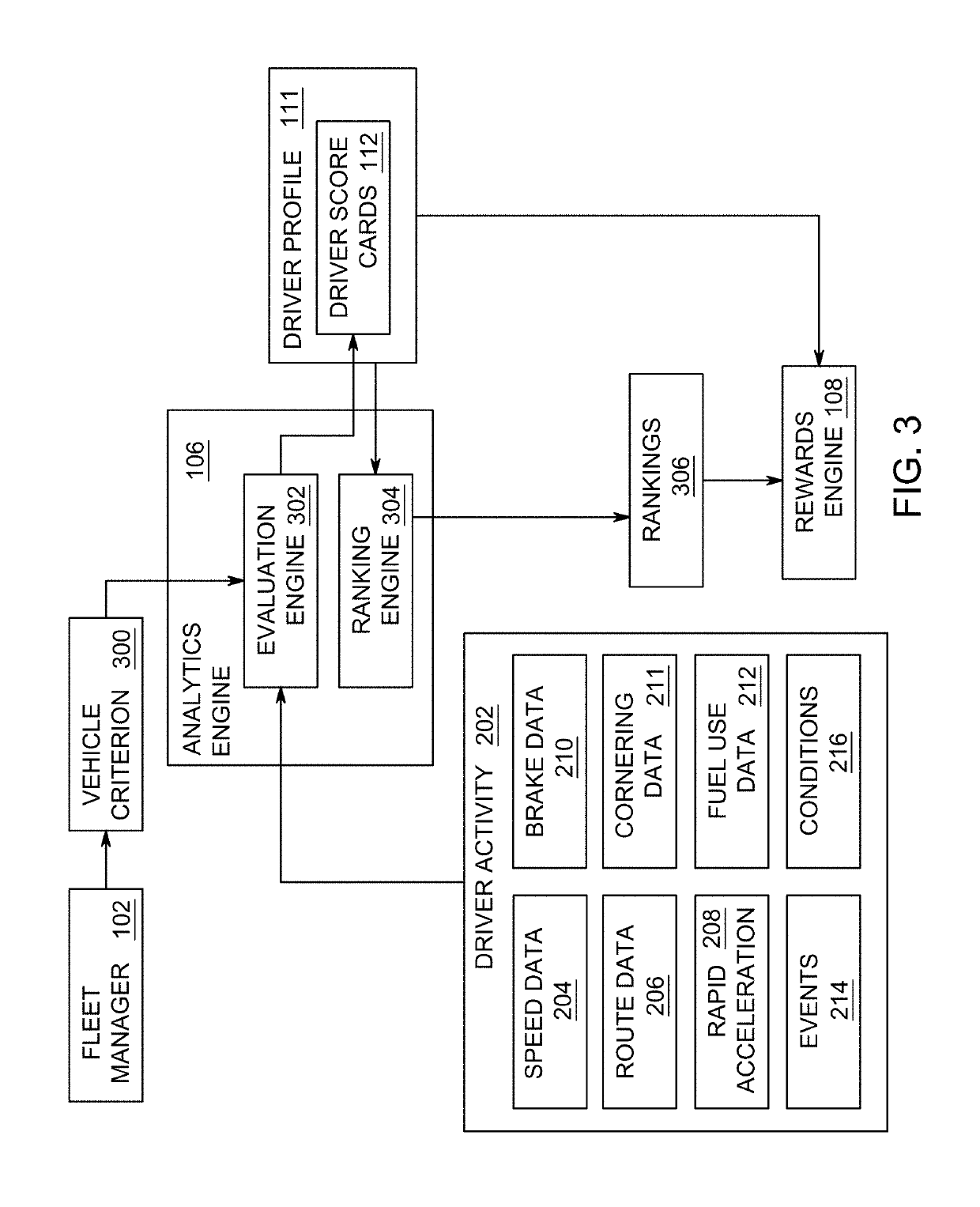
Method and apparatus for evaluating driver performance and determining driver rewards
ActiveUS20170323244A1Improving driver performanceRegistering/indicating working of vehiclesResourcesProgram profileEngineering
The present invention is directed towards a method for evaluating driver performance. In exemplary embodiments, the method comprises receiving driver activity associated with a driver of a vehicle in a fleet, determining a driver score based on predetermined criteria and generating and updating a driver profile based on the driver activity and evaluating the driver score to generate rewards for the driver and updating the driver profile accordingly.
Owner:AZUGA INC
System for dynamic program profiling
InactiveUS20100115494A1Error detection/correctionSpecific program execution arrangementsProgram profileDynamic program analysis
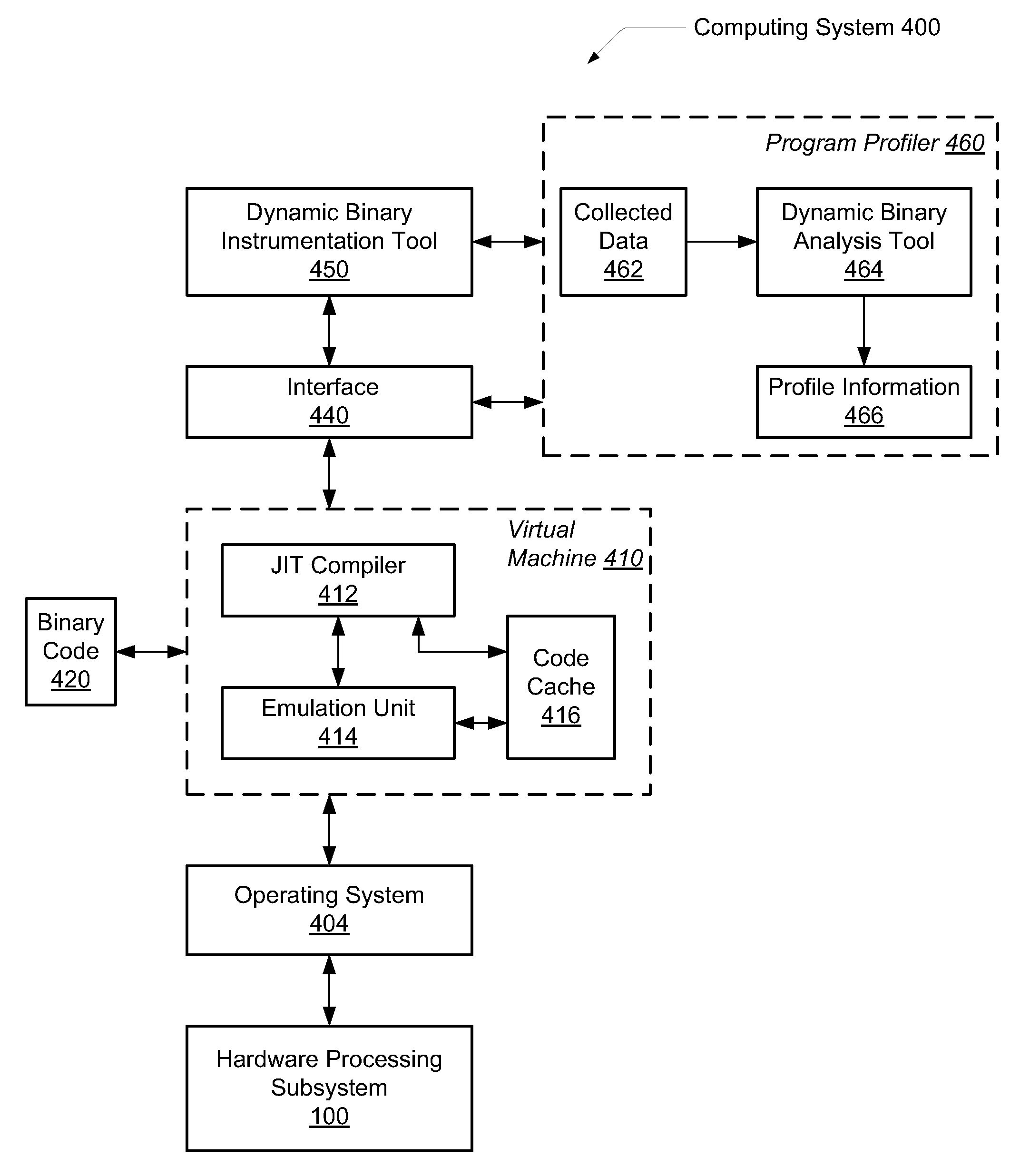
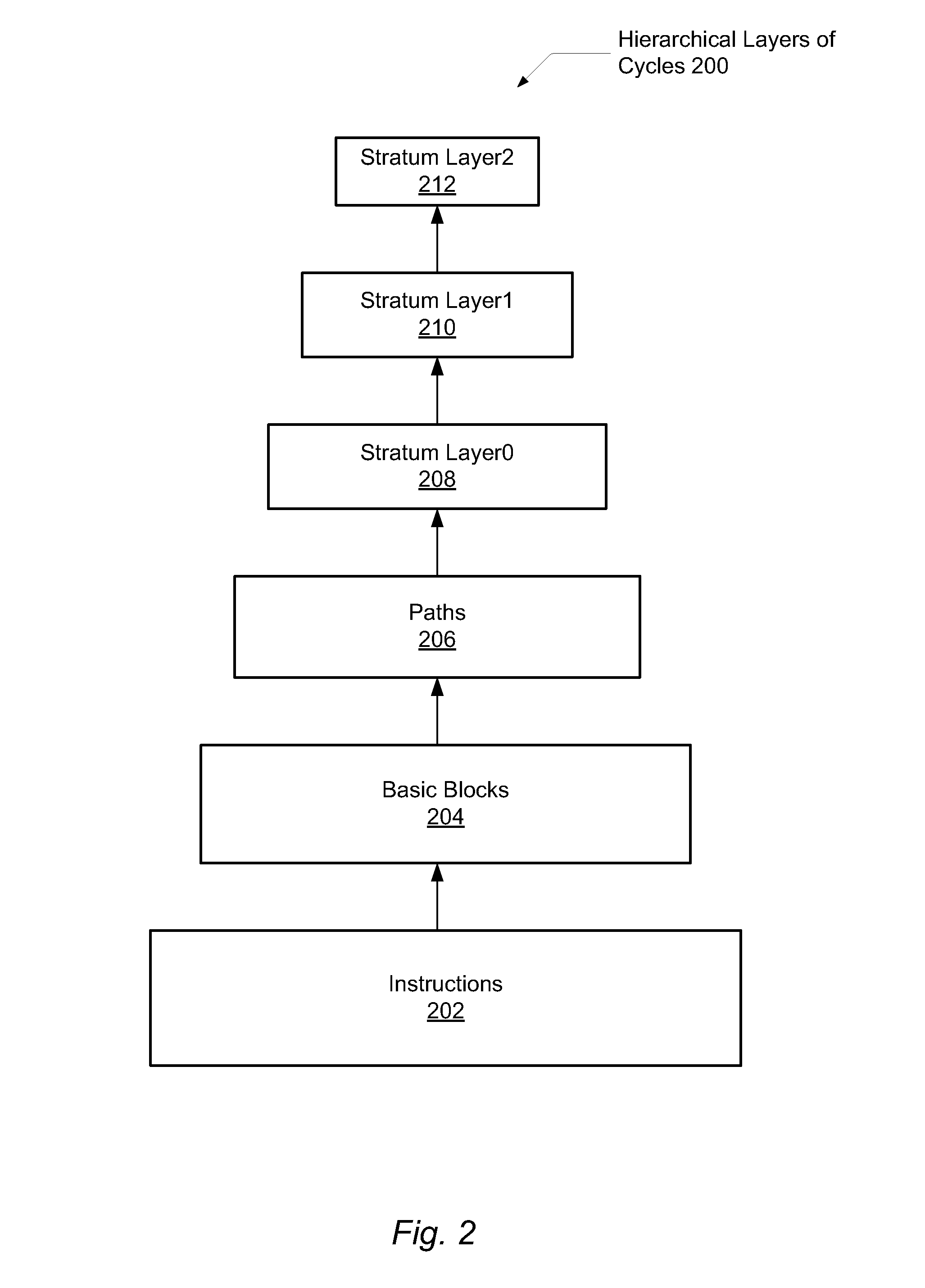
A system and method for efficient whole program profiling of software applications. A computing system comprises a dynamic binary instrumentation (DBI) tool coupled to a virtual machine configured to translate and execute binary code of a software application. The binary code is augmented with instrumentation and analysis code during translation and execution. Characterization information of each basic block is stored as each basic block is executed. A dynamic binary analysis (DBA) tool inspects this information to identify hierarchical layers of cycles within the application that describe the dynamic behavior of the application. A sequence of basic blocks may describe paths, a sequence of paths may describe a stratum, and a sequence of strata may describe a stratum layer. Statistics of these layers and hot paths may be determined and stored. This data storage yields a whole program profile comprising program phase changes that accurately describes the dynamic behavior of the application.
Owner:GLOBALFOUNDRIES INC
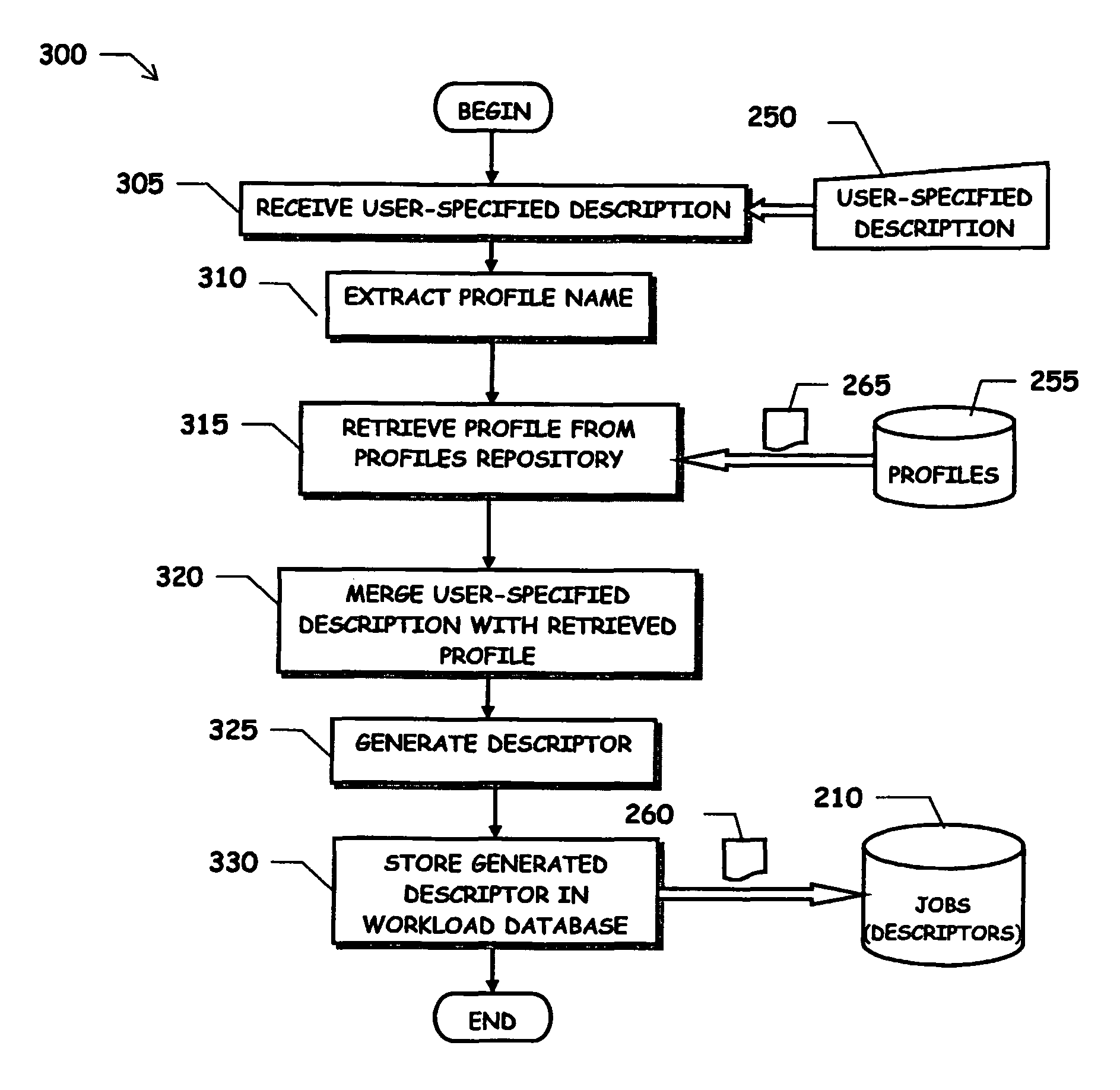
Method and system for scheduling jobs based on predefined, re-usable profiles
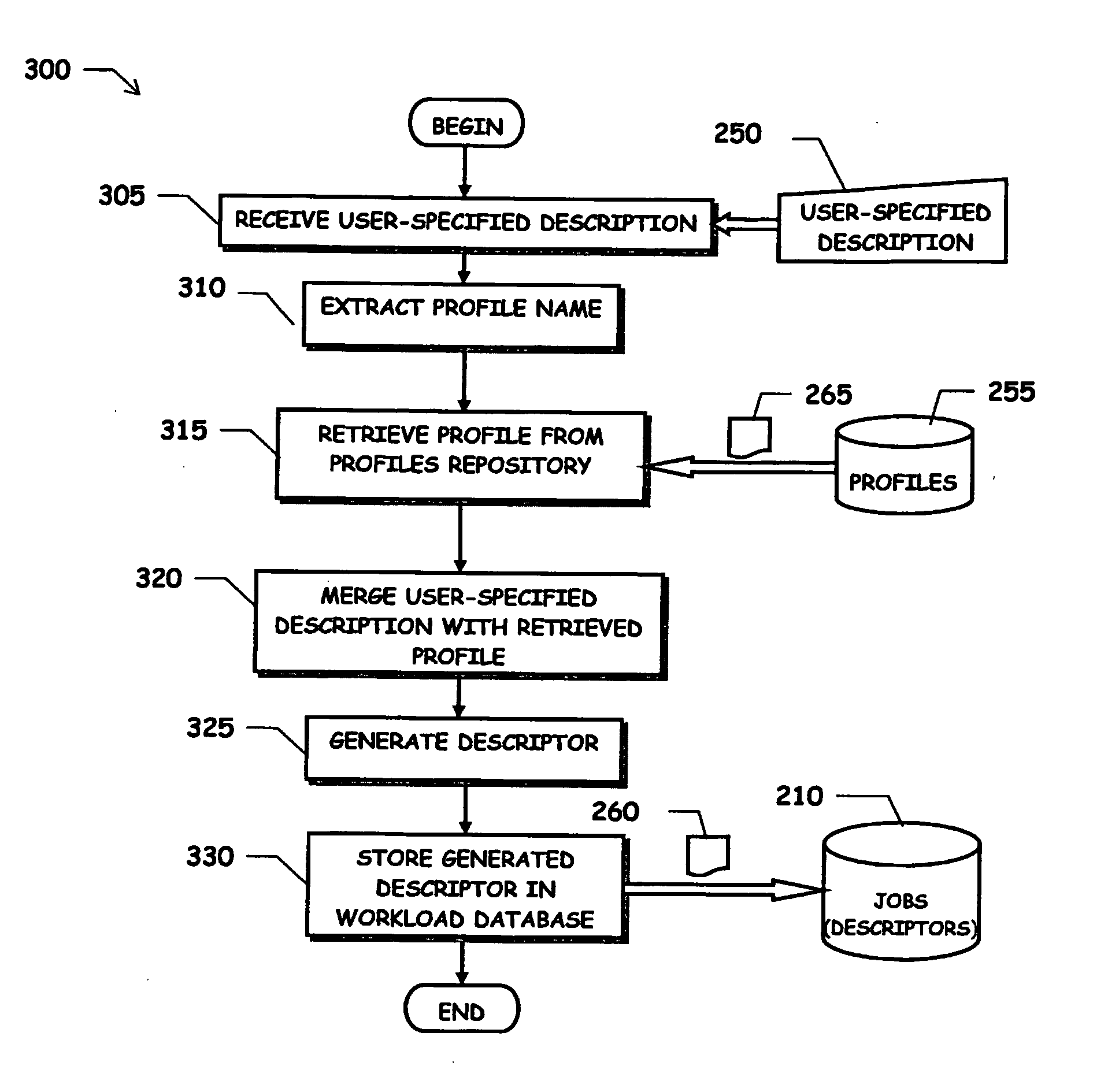
A method for scheduling execution of a work unit in a data processing system, wherein the execution of the work unit involves the execution of at least one program, the method comprising: providing a first collection (265) of pieces of information necessary to execute the work unit, said first collection of pieces of information being arranged in at least one pre-defined, re-usable program profile corresponding to the at least one program to be executed; receiving (305), in a request for scheduling execution of the work unit, a second collection (250) of pieces of information necessary to execute the work unit; determining execution information (260) for the execution of the work unit based on the first and second collections of pieces of information, and scheduling the execution of the work unit based on the determined execution information. In particular, the first collection of information pieces includes data needed for executing the work unit that do not vary from invocation to invocation of the at least one program, and the second collection of information pieces includes data needed for executing the work unit that are specific of the invocation of the at least one program for the execution of the work unit.
Owner:IBM CORP
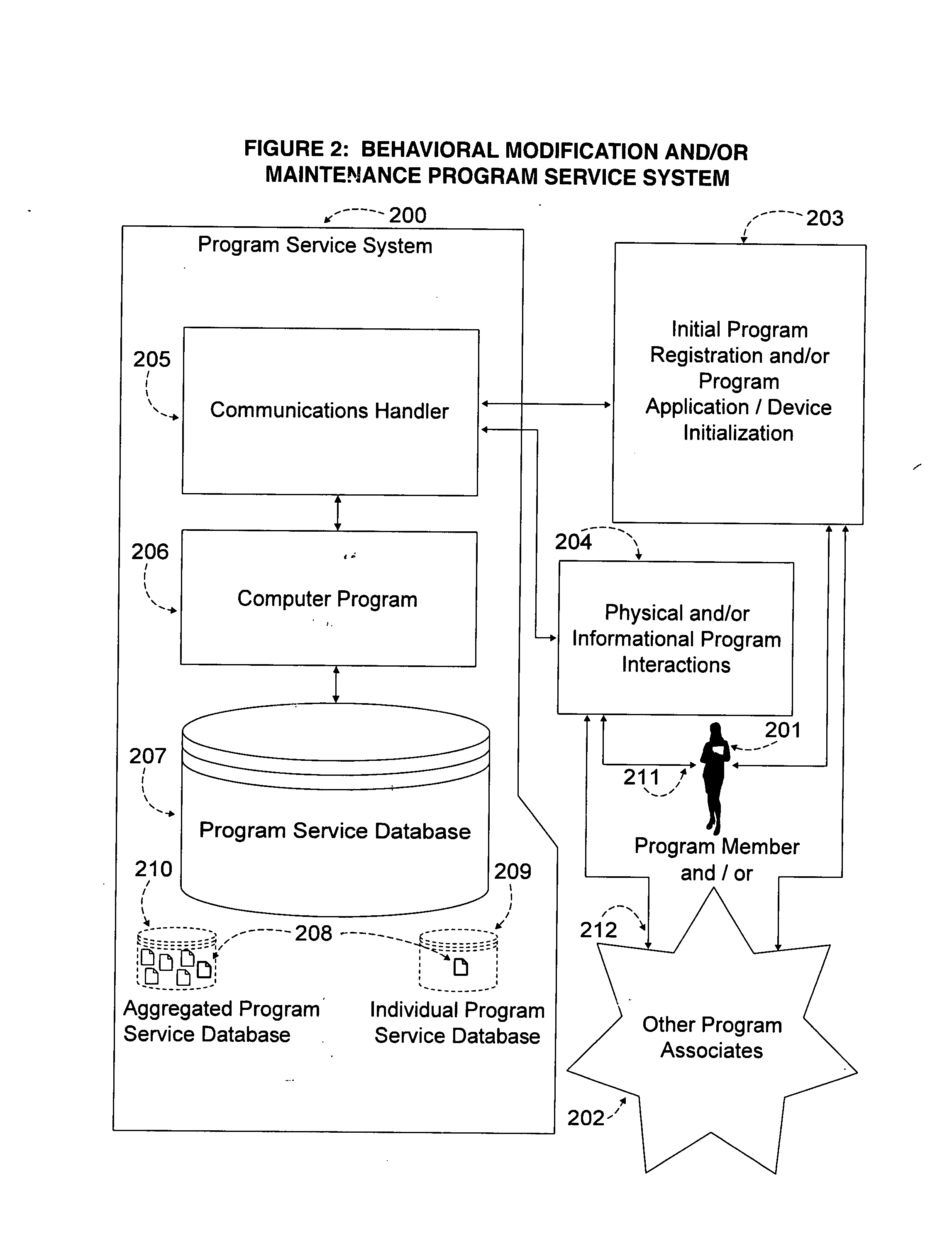
System and methodology for management and modification of human behavior within a goal-oriented program
InactiveUS20070282930A1Increased and decreasedChange maintenanceInput/output for user-computer interactionPhysical therapies and activitiesHuman behaviorTime segment
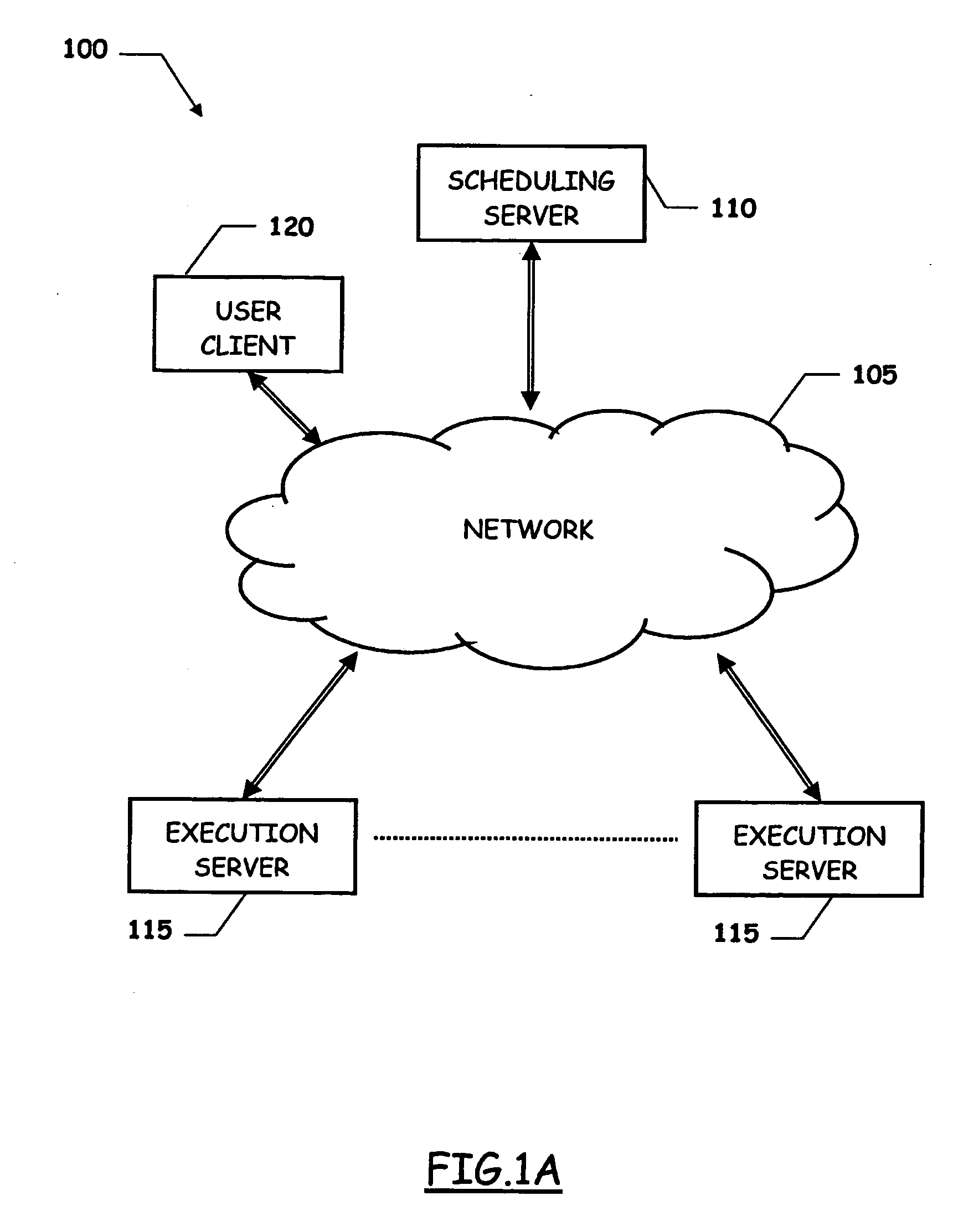
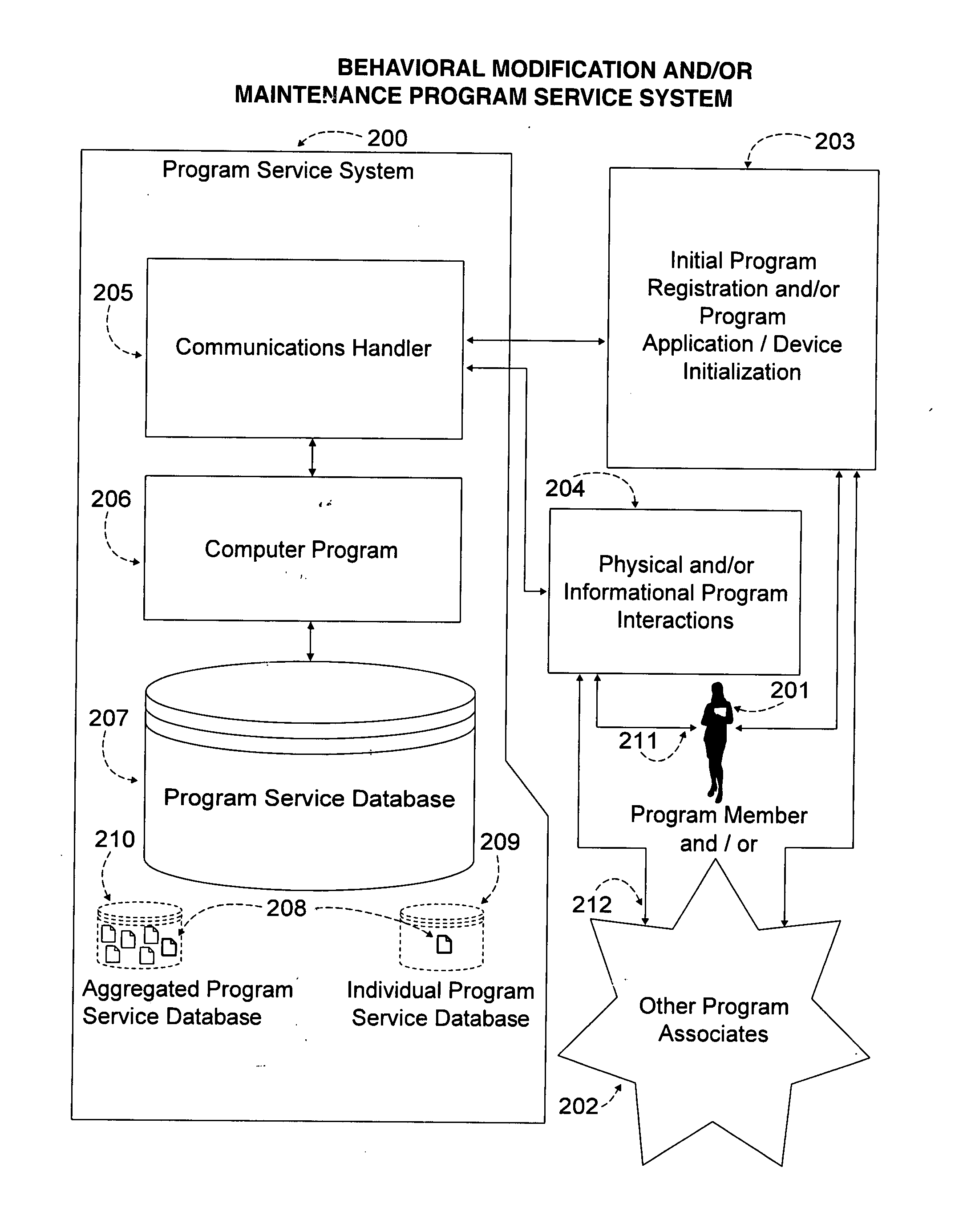
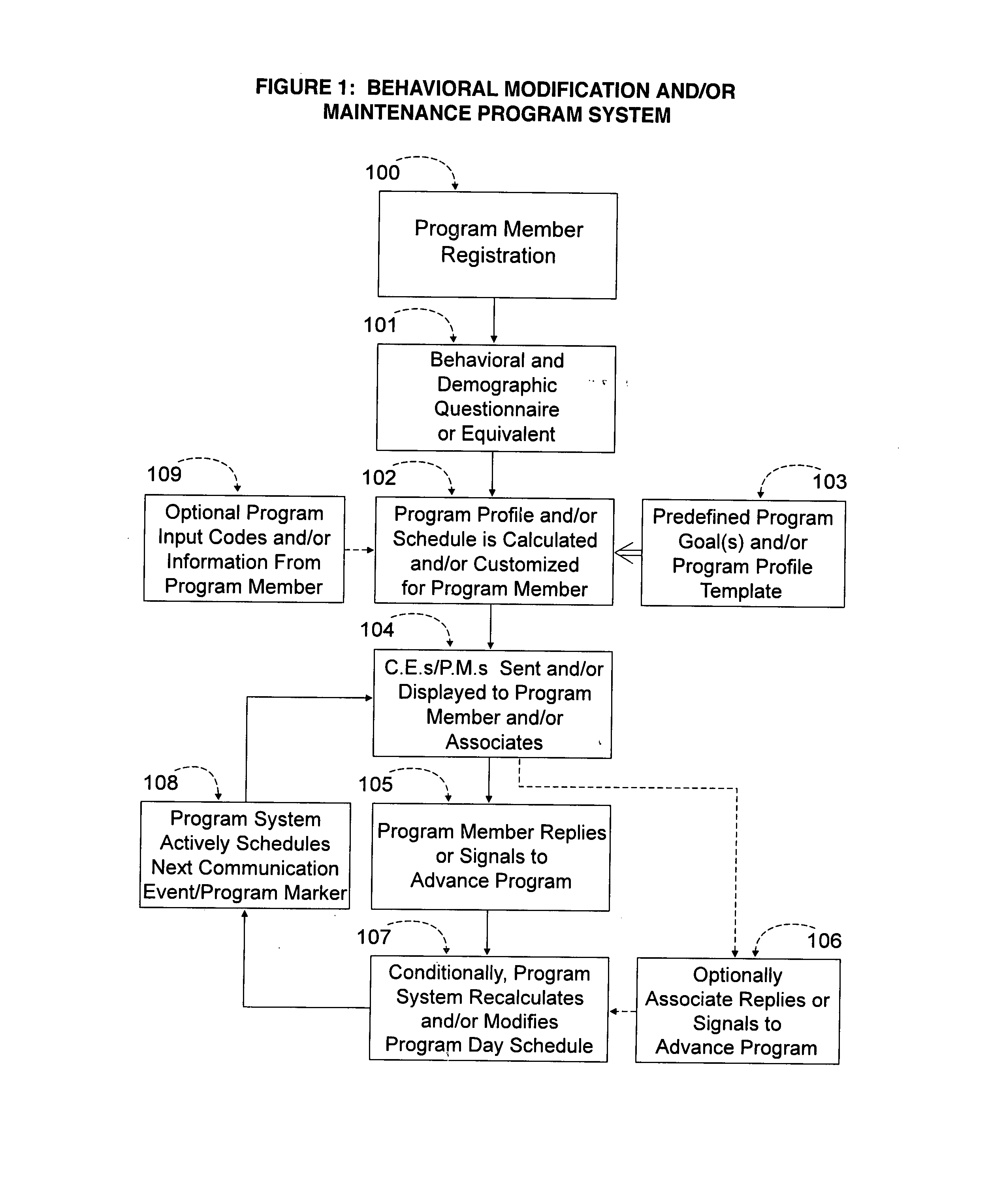
A system and methodology for human behavior modification or maintenance implemented by electronic two way communication between a host computing device with software adapted to the task, and a user. The system employs collected data regarding user identity, availability, and behavior, and generates a customized program of sequential events during identified user available time segments on a plurality of days. The events are constantly re-allotted to the available time in given daily time segments through a feedback acknowledgment from the user subsequent to communications sent to the user about an event. This results in a constantly updated program based on user responses which continually adjusts for the remaining time in the time segment on any day during the program. The program is customizable by user input requests such as exclusion of time during the daily time segments, front loading or rear loading of daily events, program day extensions or reductions, starting a program day earlier than the regularly scheduled time, inserting plateaus to repeat days in a program, and backsetting or forwardsetting within a program profile. A shaping function may be employed to further customize the program.
Owner:DOSS STEPHEN S +2
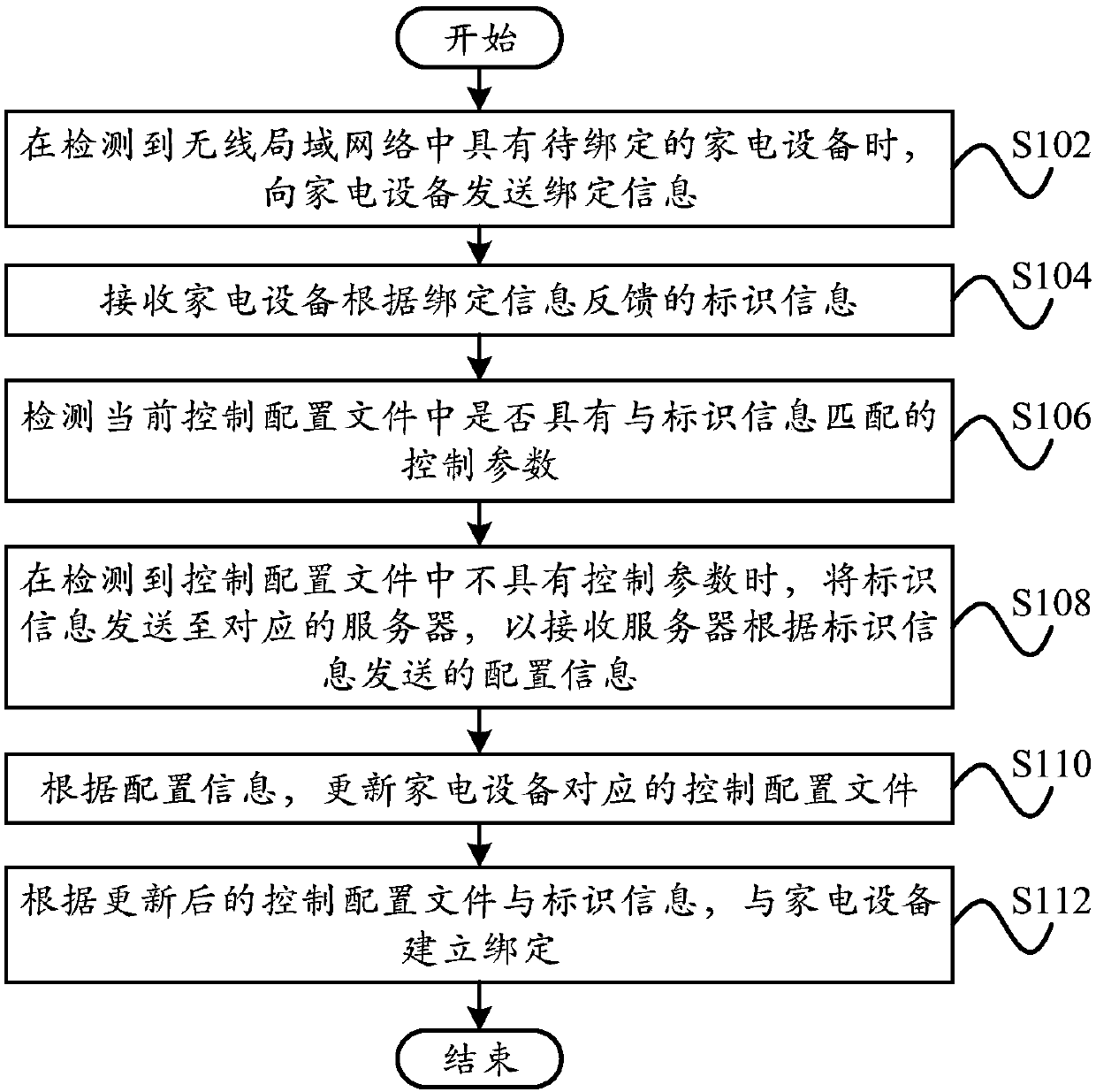
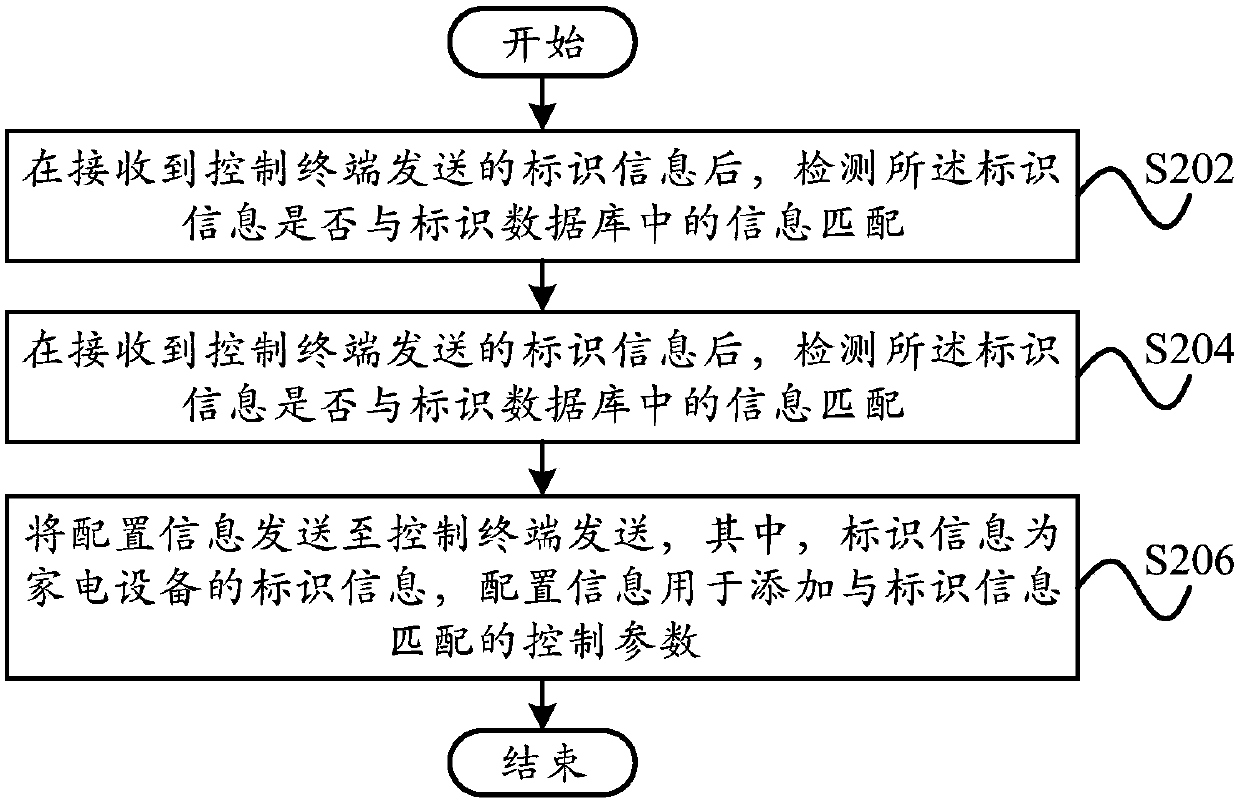
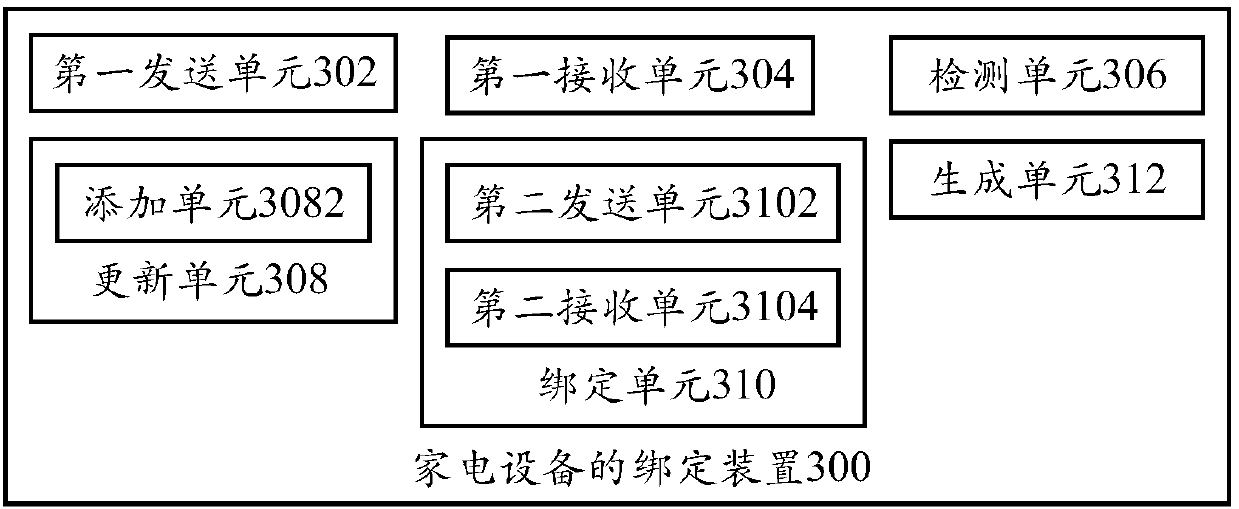
Binding method, binding device, terminal, server and readable storage medium
InactiveCN107566225AReal-time updateMake up for operational errors in timeData switching by path configurationProgram profileControl parameters
The invention provides a binding method, a binding device, a terminal, a server and a readable storage medium. The binding method comprises the steps of sending the binding information to a householdappliance when it is detected that wireless local network has the household appliance to be bound; receiving the identification information of the household appliances sent as the feedback by the binding information; detecting whether there are control parameters matched with the identification information in the current program configuration file; sending the identification information to the corresponding server when it is detected that the program configuration file does not have the control parameter, so as to receive the configuration information sent by the server based on the identification information; updating the program configuration file corresponding to the household appliance based on the configuration information; establishing binding with the household appliance based on the updated program configuration file and the identification information. The invention is advantageous in that misoperation before going out of factory can be made up in time; configuration information can be actively obtained by the terminal, and the updating of software version is not required, and reviewing time can be saved.
Owner:HEFEI MIDEA INTELLIGENT TECH CO LTD
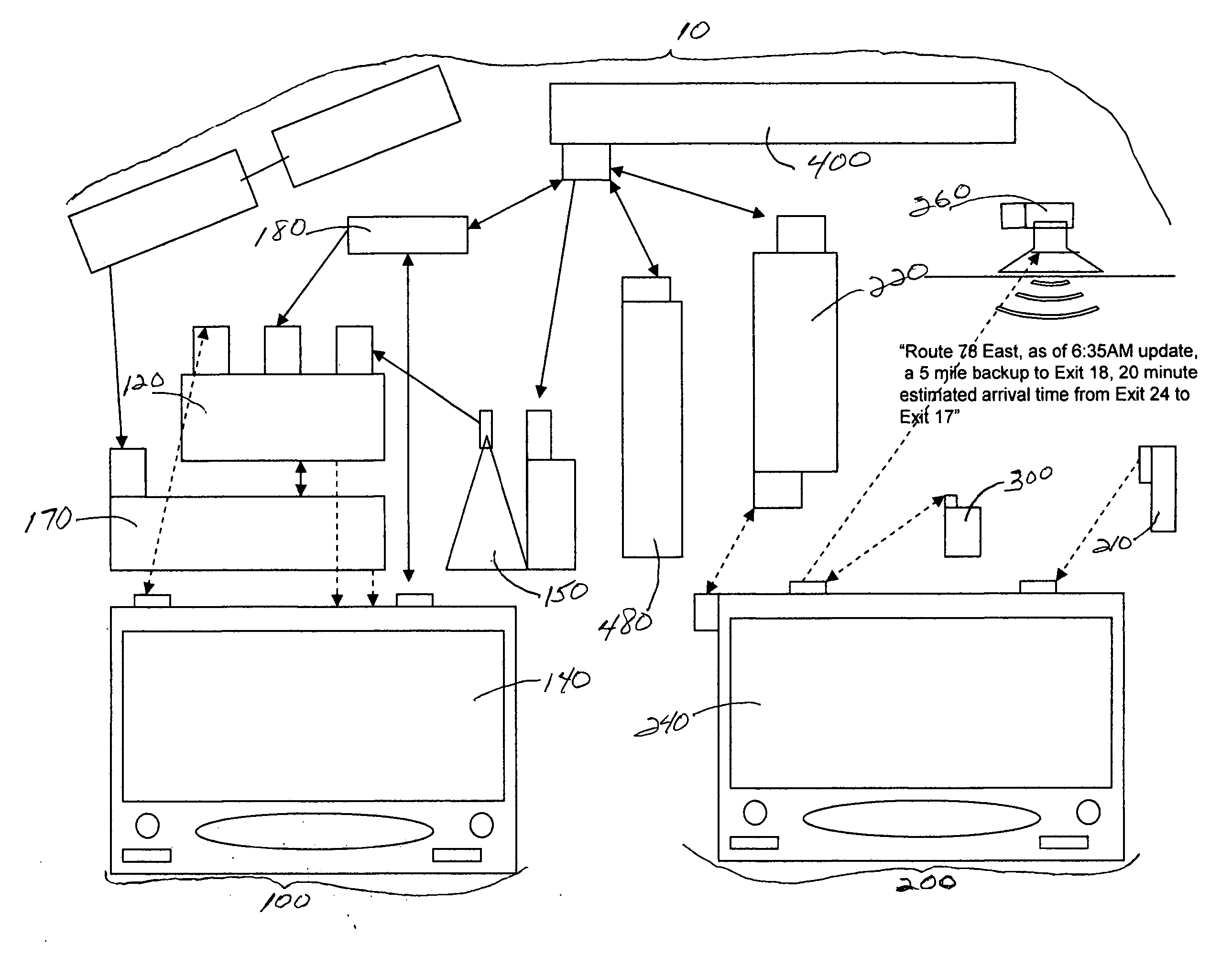
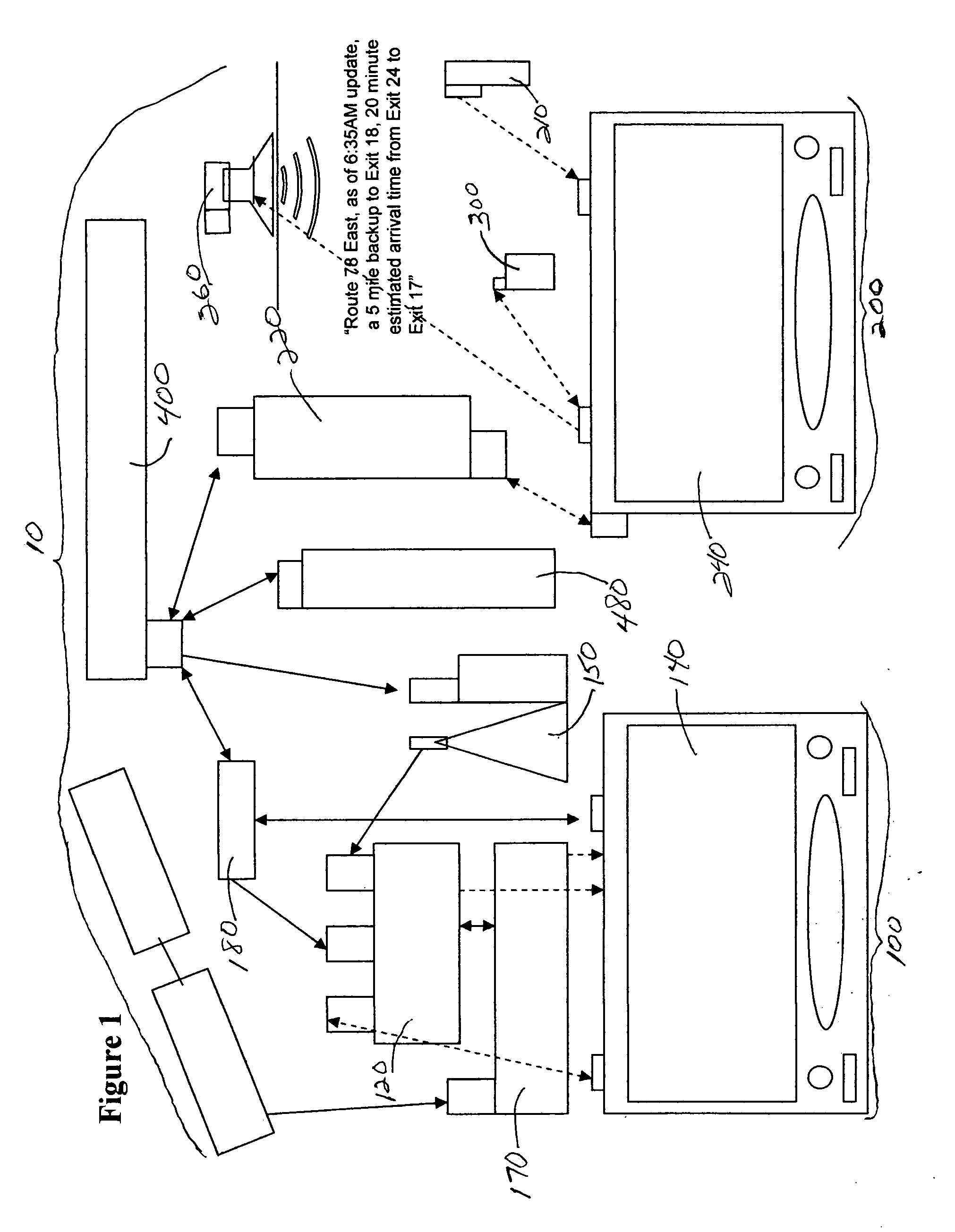
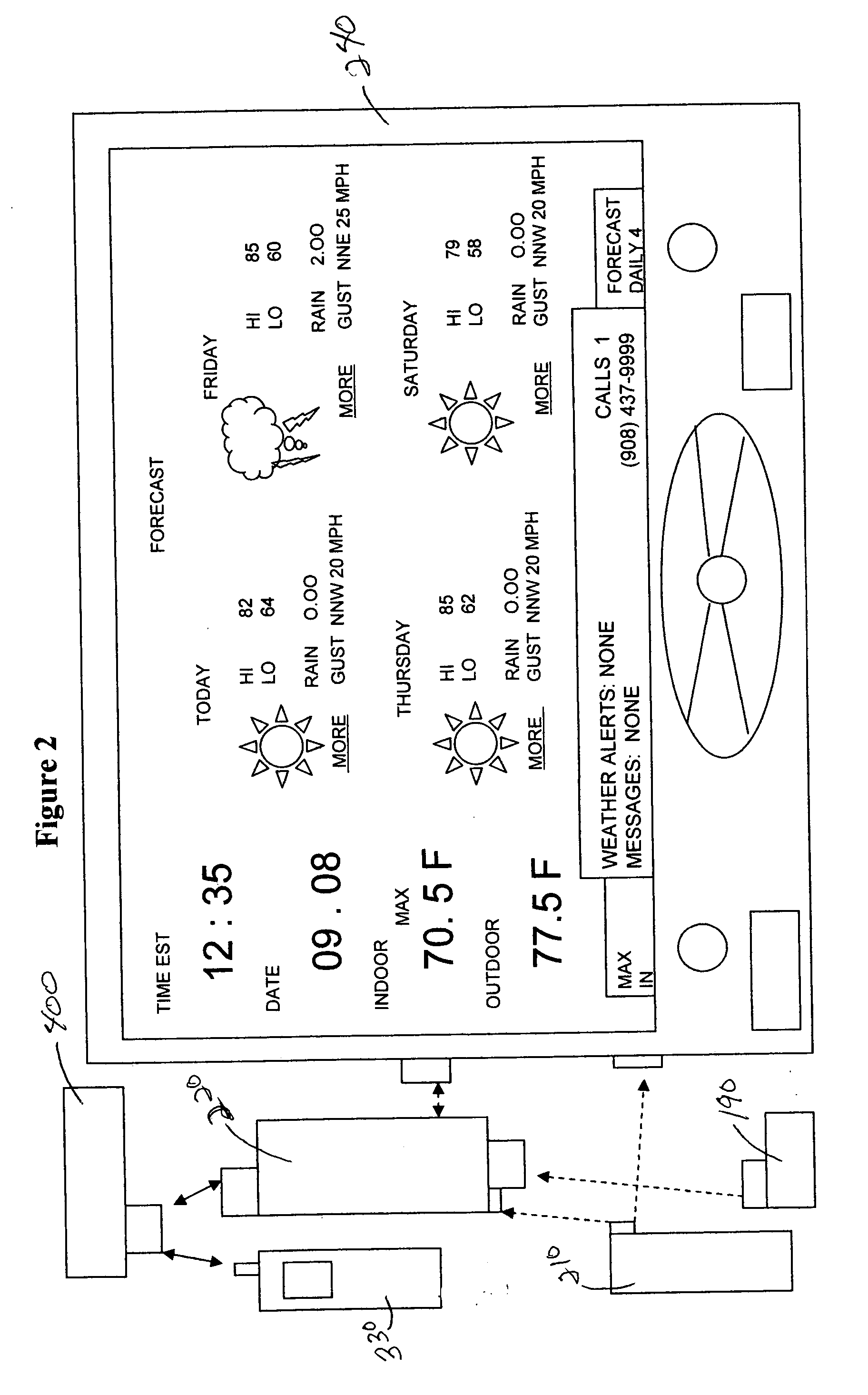
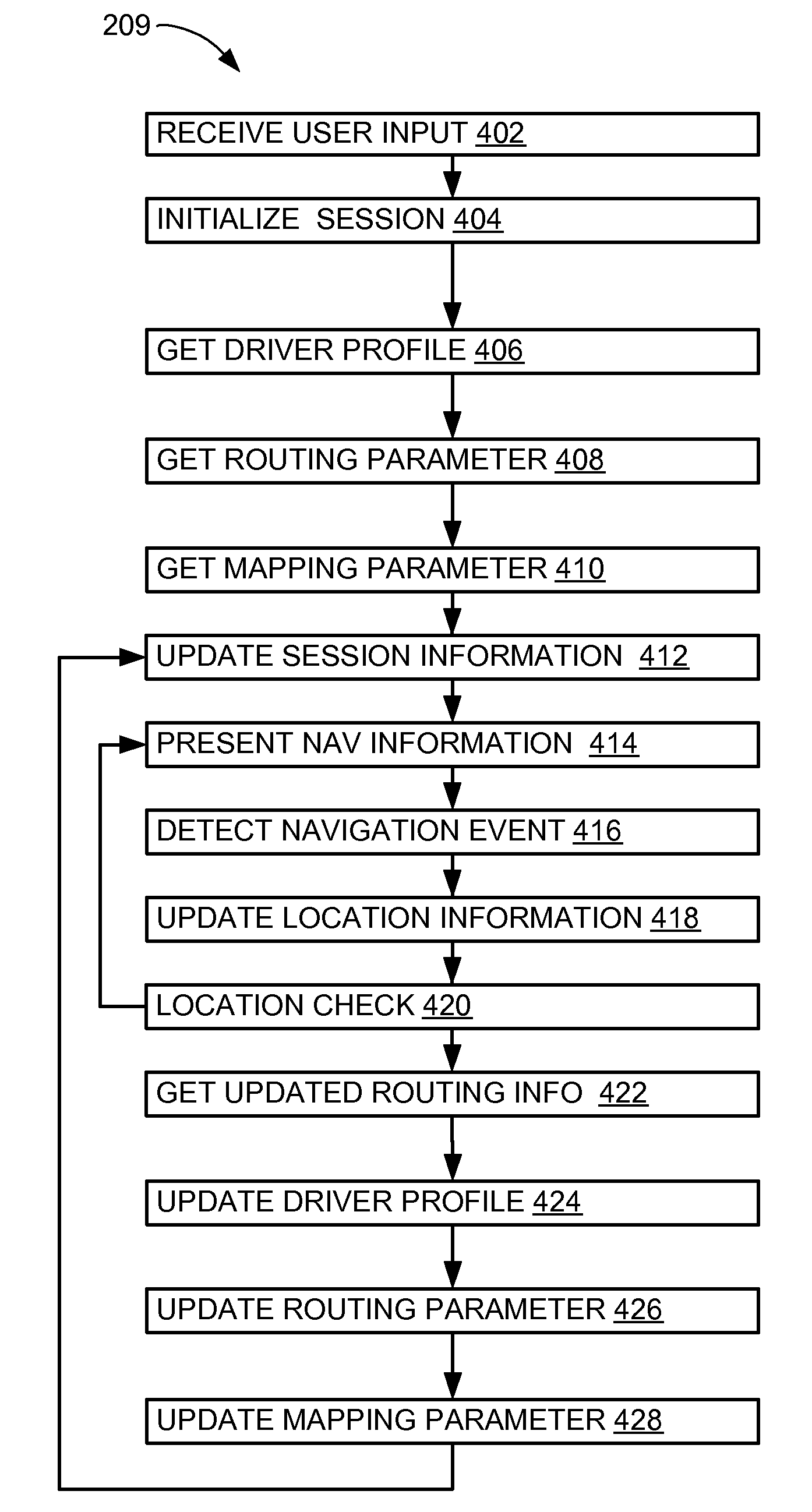
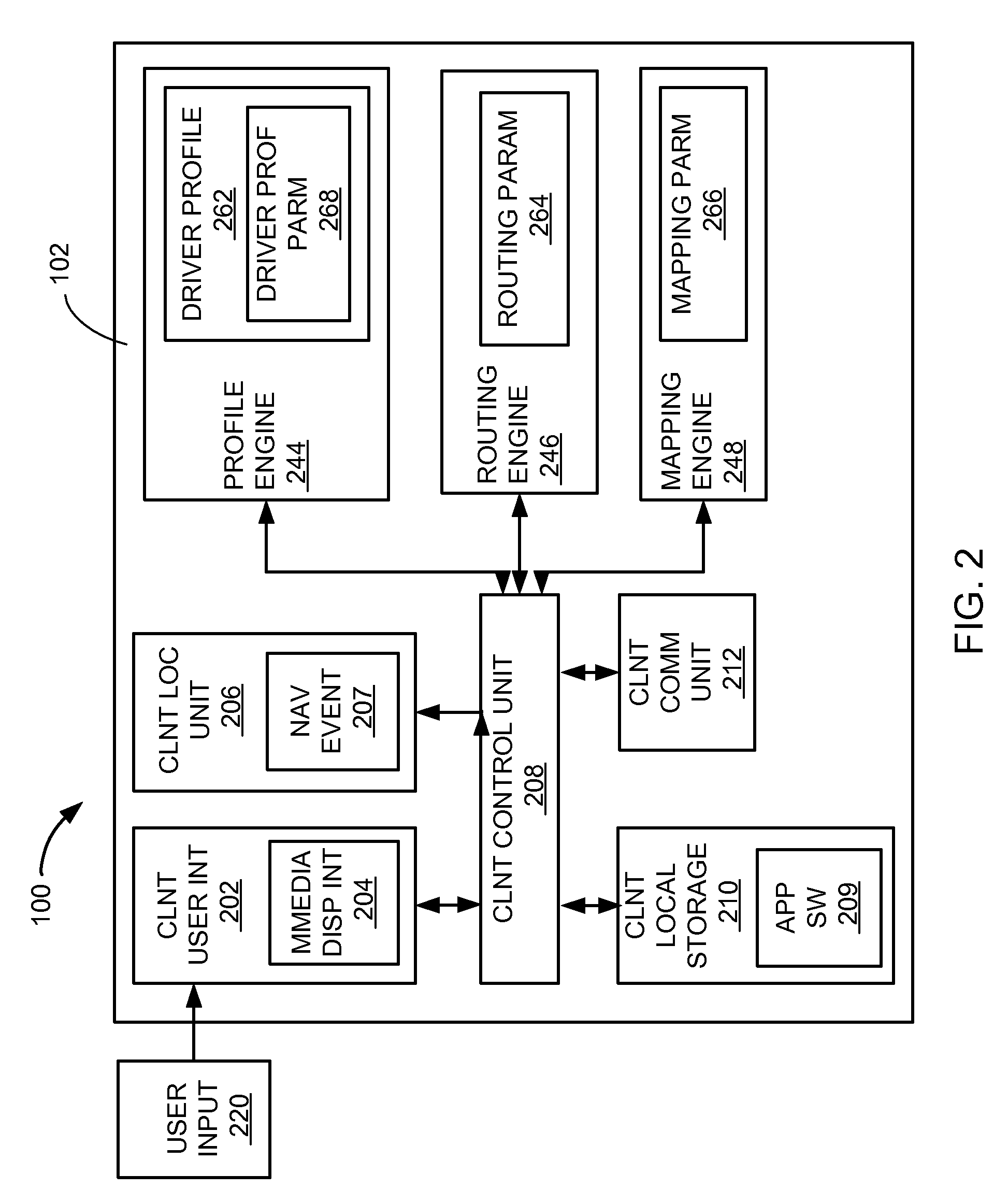
Navigation system having dynamic adaptive routing and method of operation thereof
InactiveUS20100114469A1Instruments for road network navigationRoad vehicles traffic controlProgram profileNavigation system
A method of operation of a navigation system having dynamic adaptive routing includes detecting a navigation event; updating a driver profile with the navigation event; calculating a navigation routing parameter with the driver profile; and sending the navigation routing parameter for displaying on a multimedia display interface of a device.
Owner:TELENAV
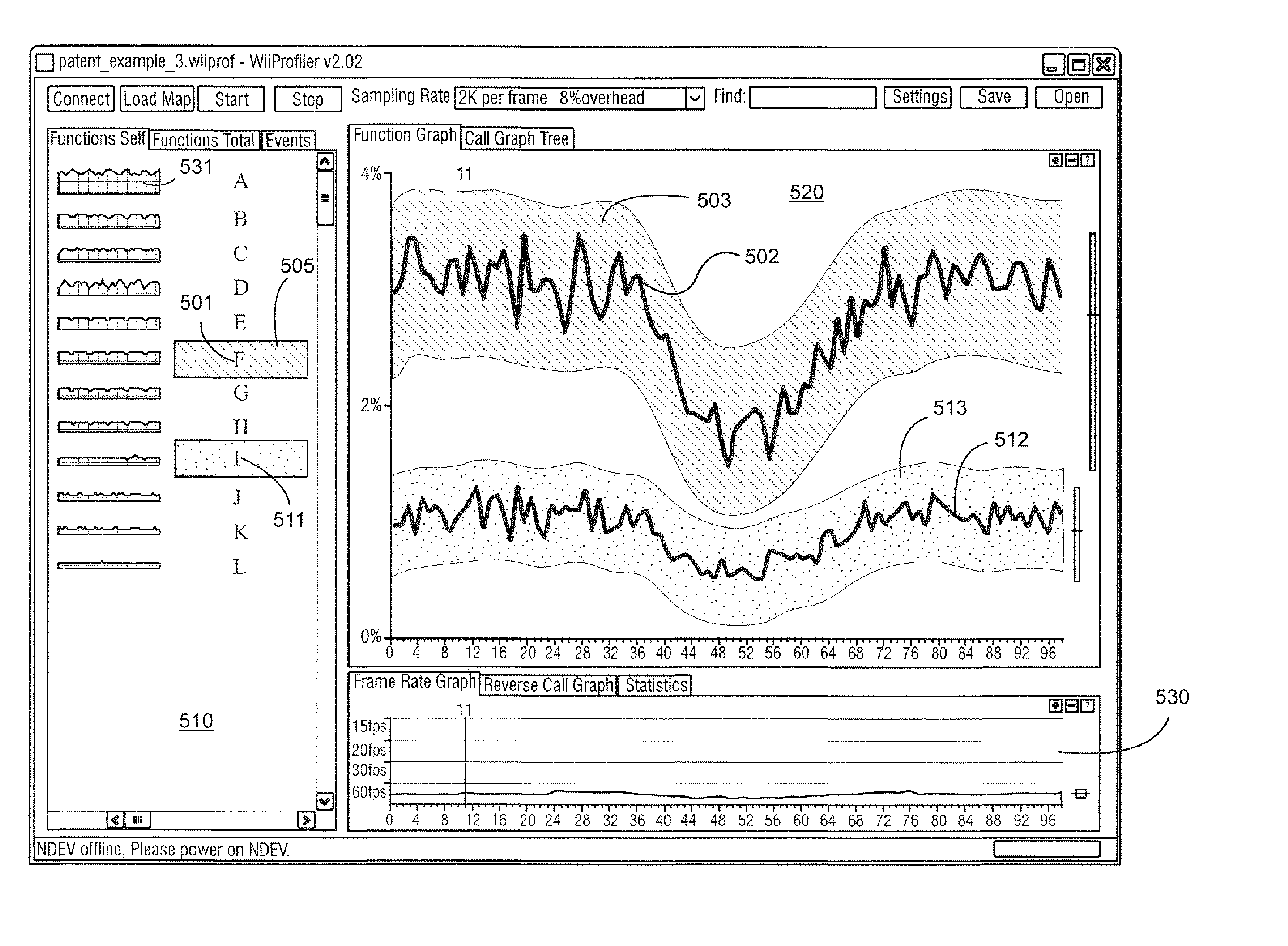
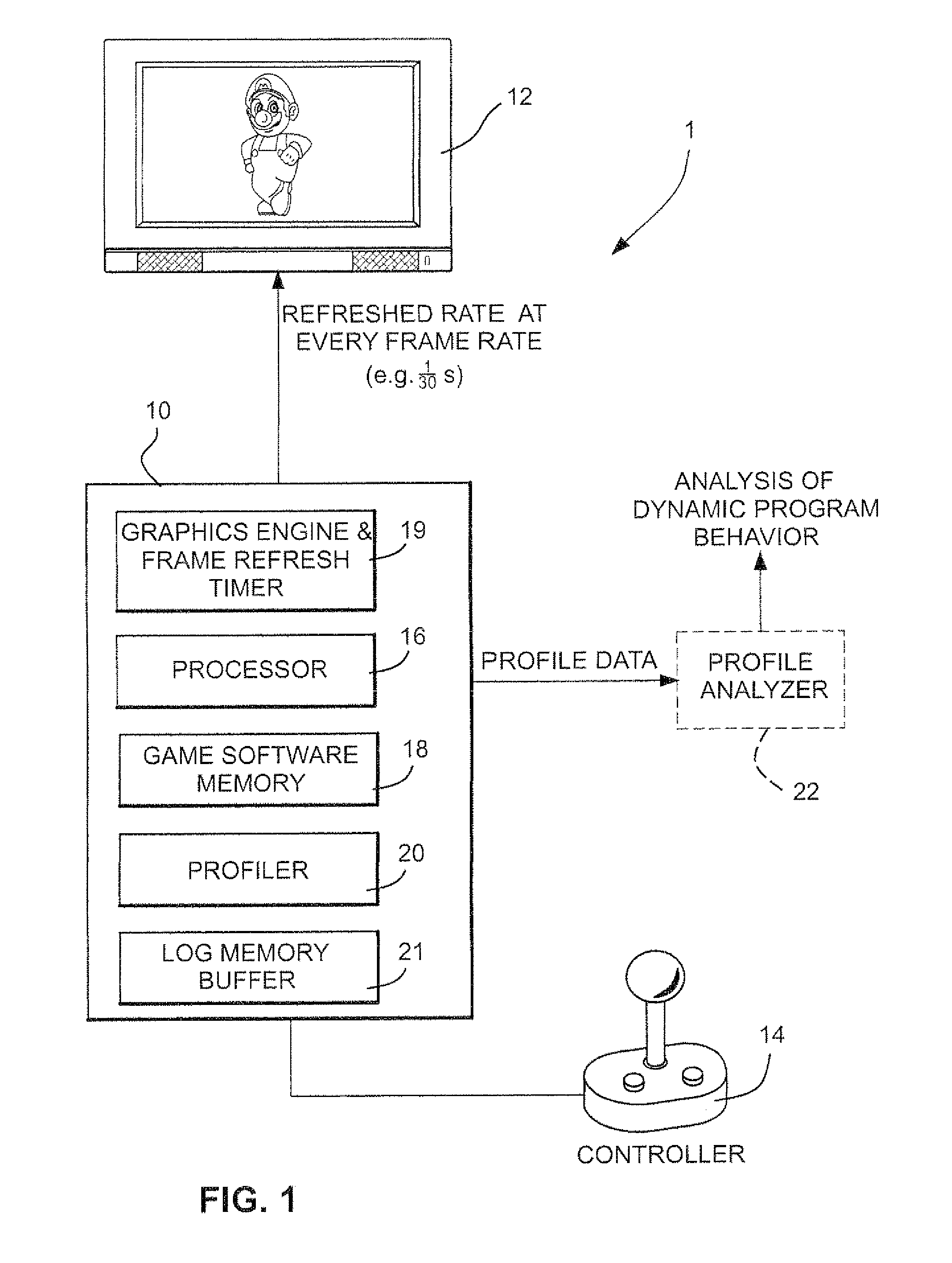
Method and apparatus for visualizing and interactively manipulating profile data
ActiveUS20100079463A1Quick fixMany pointsWindingsDrawing from basic elementsStatistical analysisProgram profile
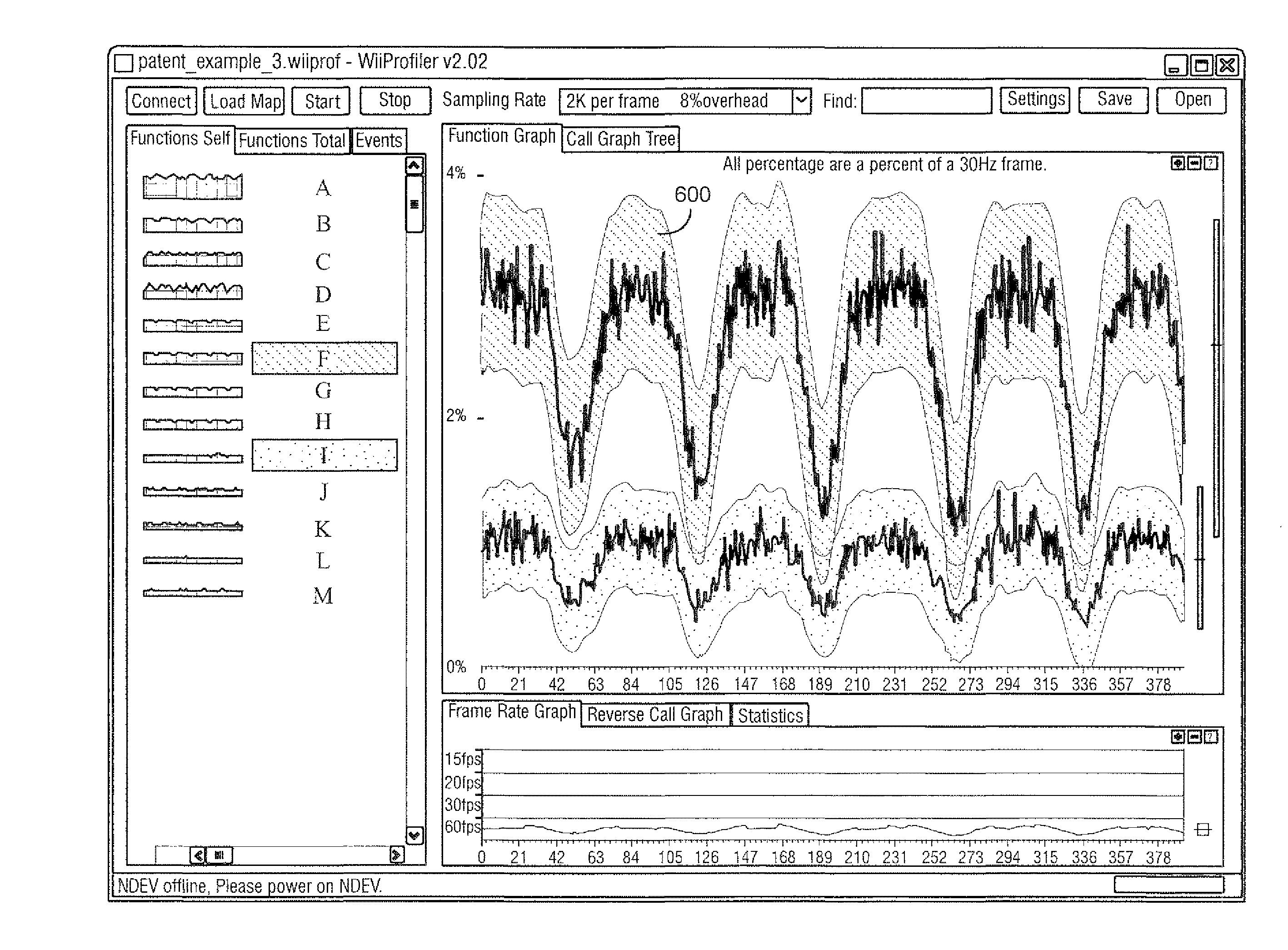
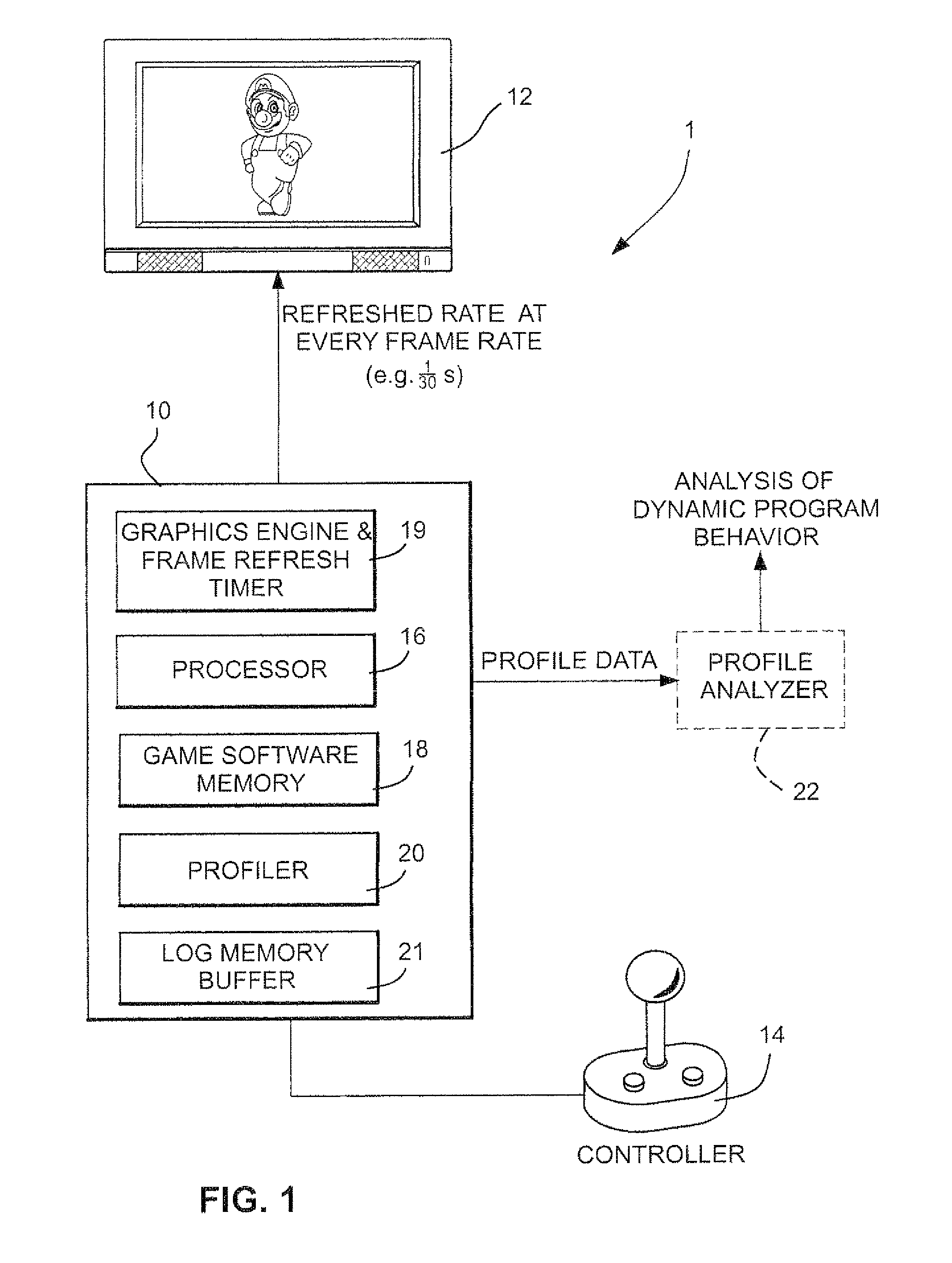
Profile data collected through sampling is transformed and visually and interactively manipulated and displayed. In one scenario, the profile data is collected through statistical profiling of a program for a video game. The game program profile data is visually and interactively manipulated and displayed to visually present a dynamic behavior of the video game that shows correlation of impacts that the functions of the program have on the video game's performance. This allows the developer to identify inefficient sections of the program for optimization.
Owner:NINTENDO CO LTD
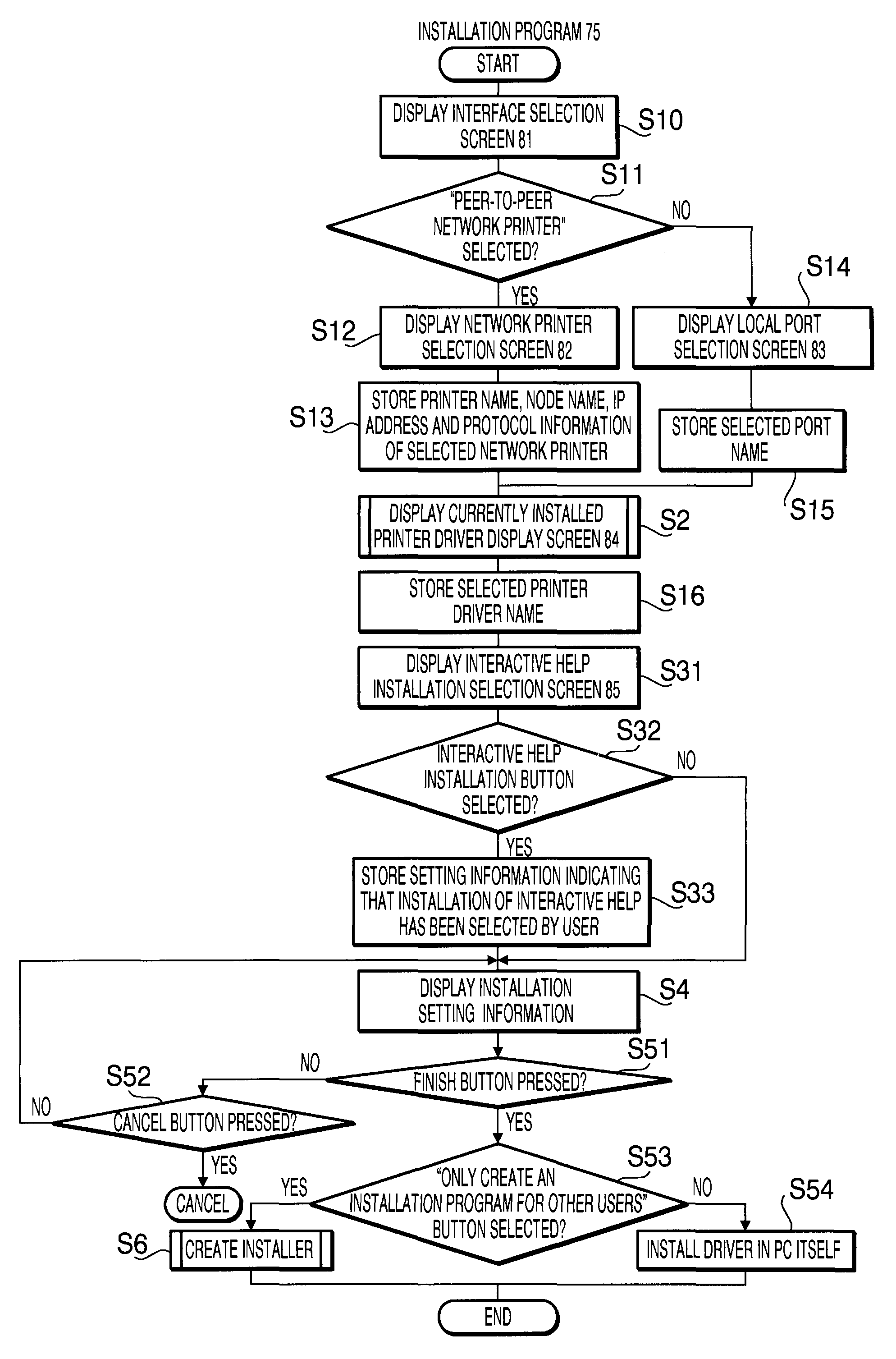
Device, Method and Program for Creating Installer
ActiveUS20070245345A1Program loading/initiatingExecution for user interfacesProgram profileControl equipment
There is provided a computer readable medium having computer readable instructions stored thereon, which, when executed by a computer, are configured to extract driver configuration files forming a device driver from the computer in which the device driver for controlling a device has been installed, to acquire an initial setting file describing control parameters that have incorporated inputs made in regard to the control parameters to be used by the device driver for controlling the device, and to create an installer which installs a device driver, including the driver configuration files and the initial setting file and controlling the device according to the control parameters described in the initial setting file, in a computer.
Owner:BROTHER KOGYO KK
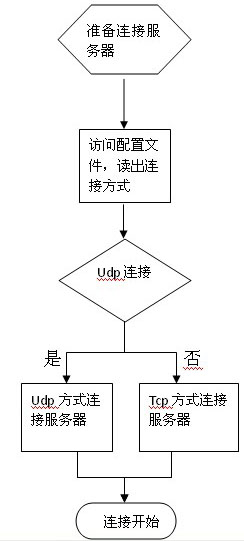
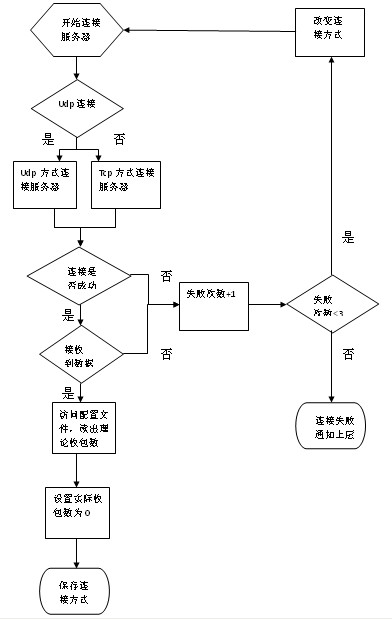
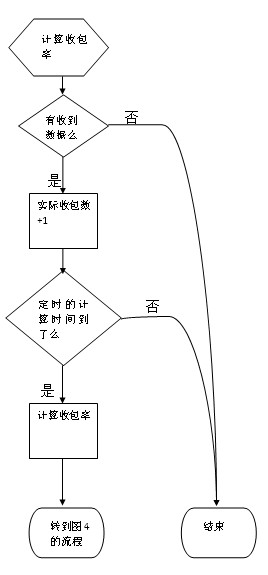
Method for ensuring stability of large data stream by tcp (Transmission Control Protocol)/udp (User Datagram Protocol) double-mode communication
The invention relates to a method for ensuring the stability of a large data stream by tcp / udp dual-mode communication. Upon a client end, the method includes the following steps of: (1) reading out items in the default communication mode in a program configuration file, and connecting with a server in the mode; (2) recording the current communication mode c1, tcp (Transmission Control Protocol) or udp (User Datagram Protocol); (3) counting a packet receiving rate a at a regular interval (N seconds); (4) disconnecting the current connection with the server when the packet receiving rate a is lower than an extent x; (5) recreating data connection with the server, and switching the communication mode; and (6) during the normal communication process, transmitting a heart packet to the server for ensuring the health of a link once the heart time heart-t is expired.
Owner:上海悠络客电子科技股份有限公司
Calculation engine achieving method, electronic device and storage medium
ActiveCN107967135AFlexible developmentStrong scalabilityProgramming languages/paradigmsProgram controlProgram profileComputer engineering
The invention provides a calculation engine achieving method. The calculation engine achieving method includes the following steps of determining, wherein all operators of which a target algorithm chain is composed are determined; judging, wherein whether all the operators of which the target algorithm chain is composed are contained in a program configuration file or not is judged, if the judgingresult is that all the operators of which the target algorithm chain is composed are not contained in the program configuration file, the configuring step is carried out, and if the judging result isthat all the operators of which the target algorithm chain is composed are contained in the program configuration file, the generating step is carried out; configuring, wherein target operators inputaccording to preset formats are received, the received target operators are configured in the program configuration file, and then the generating step is carried out; generating, wherein according toall the determined operators and the operator composition rule of the set target algorithm chain, corresponding algorithm numbers are generated; storing, wherein the algorithm numbers are stored intoa database. The invention also provides an electronic device and a computer readable storage medium. According to the calculation engine achieving method, the electronic device and the computer readable storage medium, newly-increased functions of a calculation engine can be achieved.
Owner:PING AN TECH (SHENZHEN) CO LTD
Application rewriting method and system for detecting Android privilege elevation attack
ActiveCN104102880ABlock threatsEffectivePlatform integrity maintainanceSpecific program execution arrangementsLink buildingProgram profile
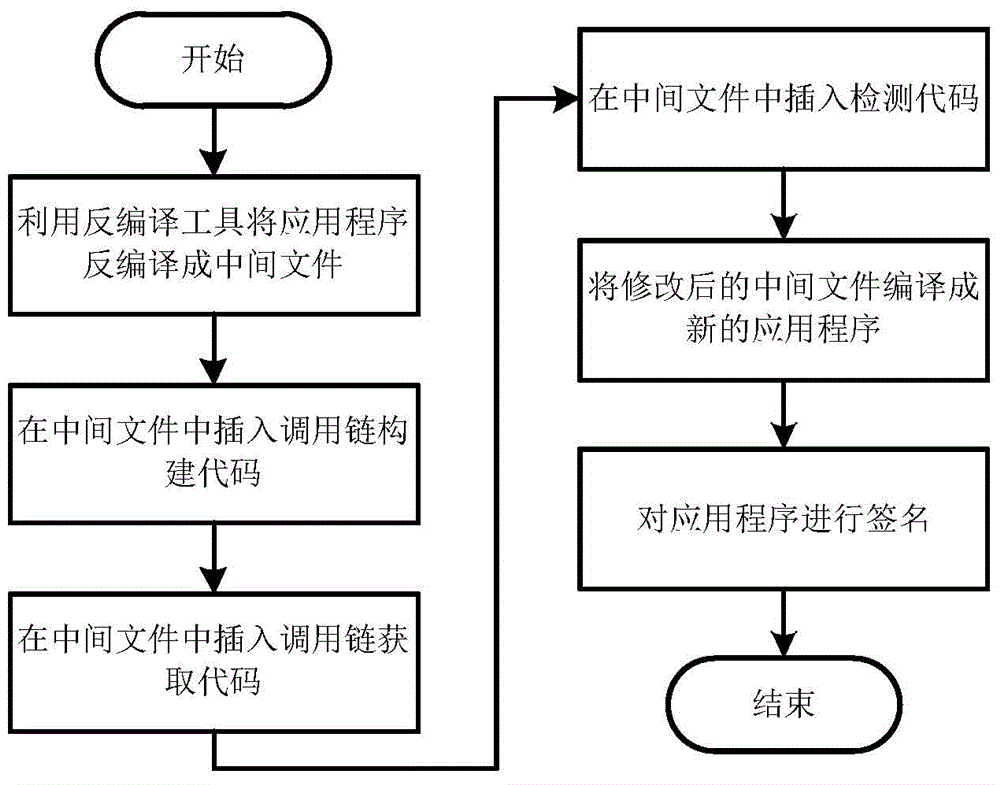
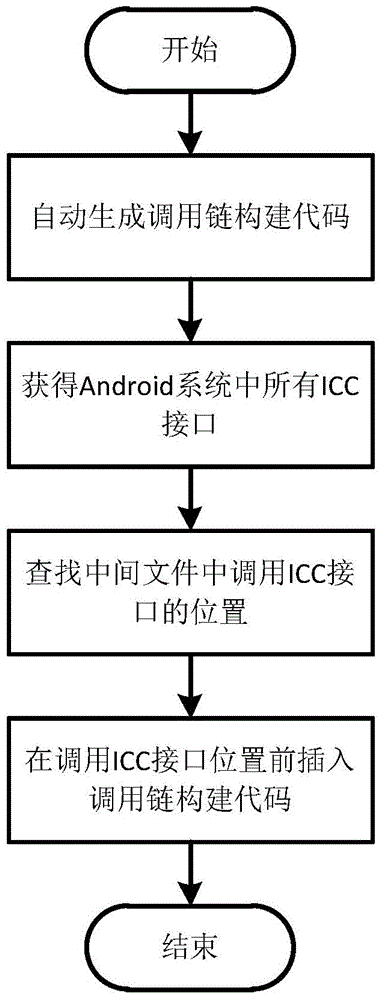
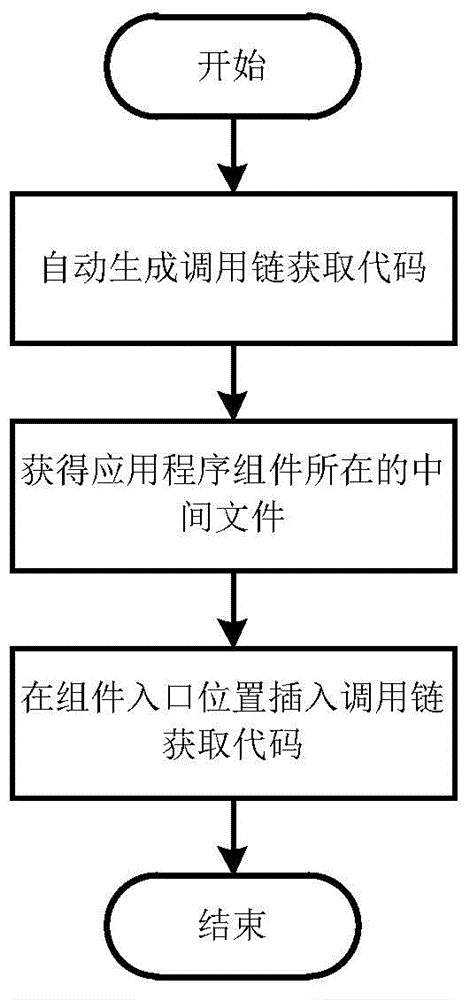
The invention discloses an application rewriting method for detecting Android privilege elevation attack. The method comprises the steps: performing decompilation on an Android application uploaded by a user to generate an intermediate file and an application configuration file; inserting a call-link building code to the generated intermediate file, so that a call link is automatically built during the running of the application; inserting a call-link acquiring code to the generated intermediate file, so that the call link sent by a calling program is automatically acquired during the running of the application; inserting a detection code to the generated intermediate file, so that whether the privilege elevation attack exists or not is automatically judged when the application accesses sensitive resources of a system; packaging the modified intermediate file and the application configuration file into a new application and signing the generated application, so that the application can be installed into mobile equipment. By adopting the application rewriting method, Android system source codes can be effectively prevented from being modified, so the method can be more easily adopted by common users.
Owner:HUAZHONG UNIV OF SCI & TECH
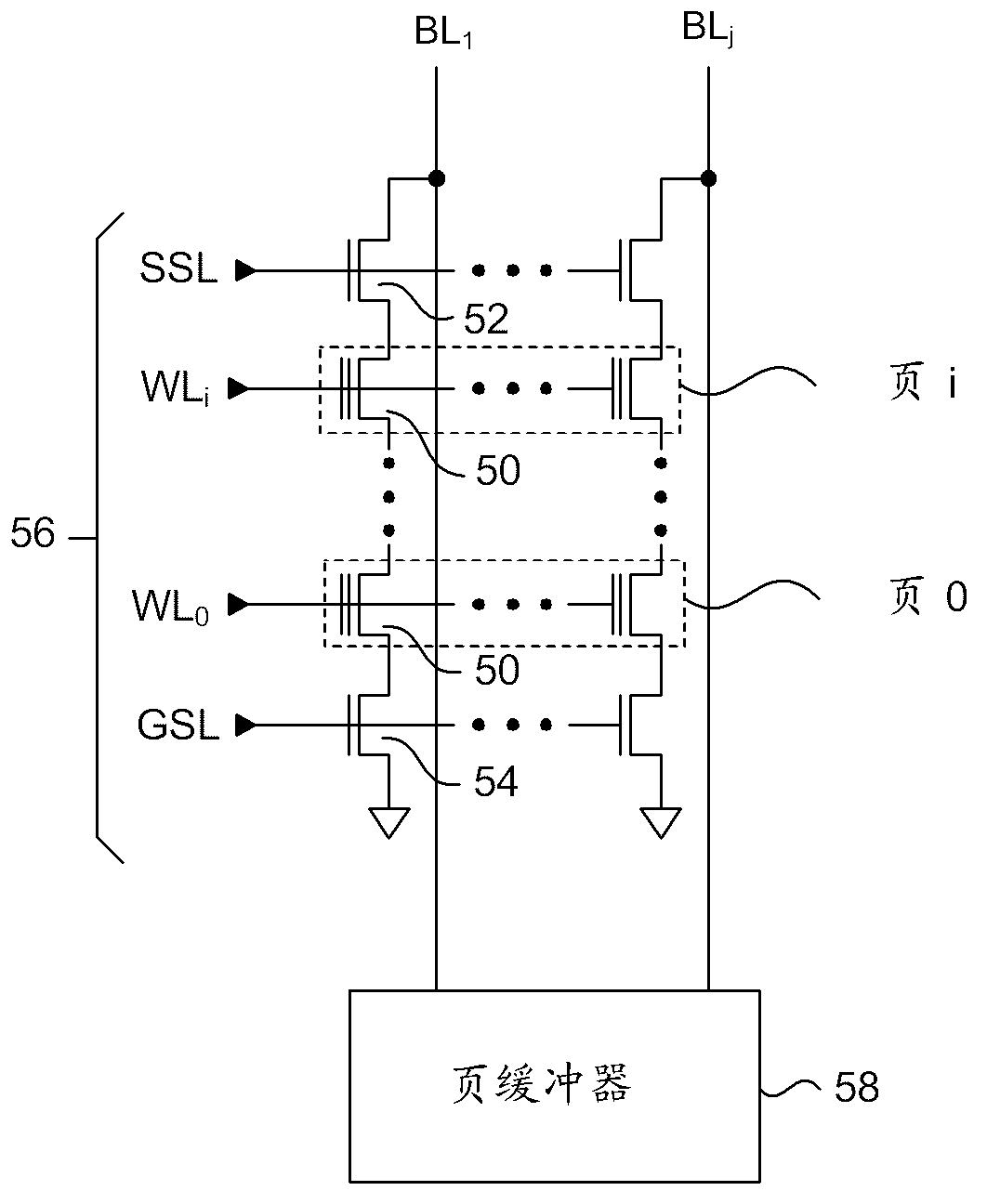
Multipage program scheme for flash memory
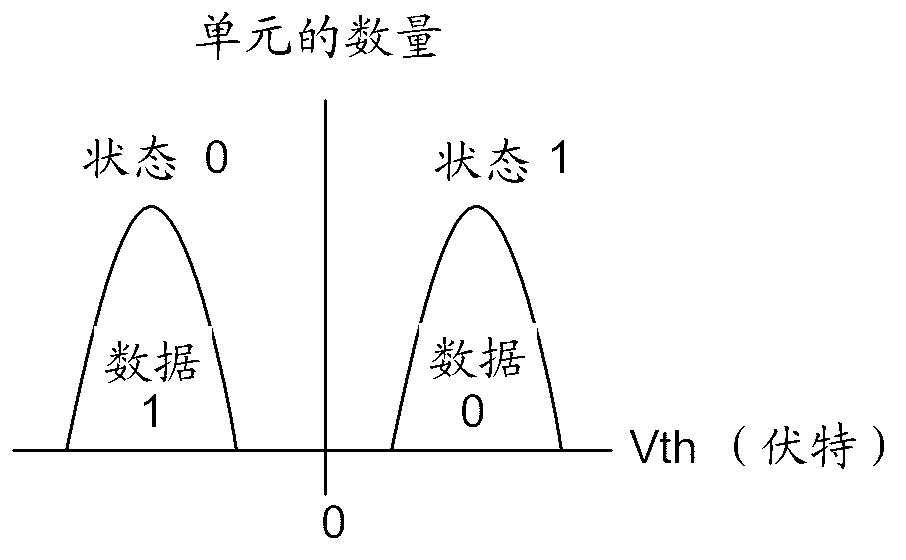
A circuit and method for programming multiple bits of data to flash memory cells in a single program operation cycle. Multiple pages of data to be programmed into one physical page of a flash memory array are stored in page buffers or other storage means on the memory device. The selected wordline connected to the cells to be programmed is driven with predetermined program profiles at different time intervals, where each predetermined program profile is configured for shifting an erase threshold voltage to a specific threshold voltage corresponding to a specific logic state. A multi-page bitline controller biases each bitline to enable or inhibit programming during each of the time intervals, in response to the combination of specific logic states of the bits belonging to each page of data that are associated with that respective bitline.
Owner:CONVERSANT INTPROP MANAGEMENT INC
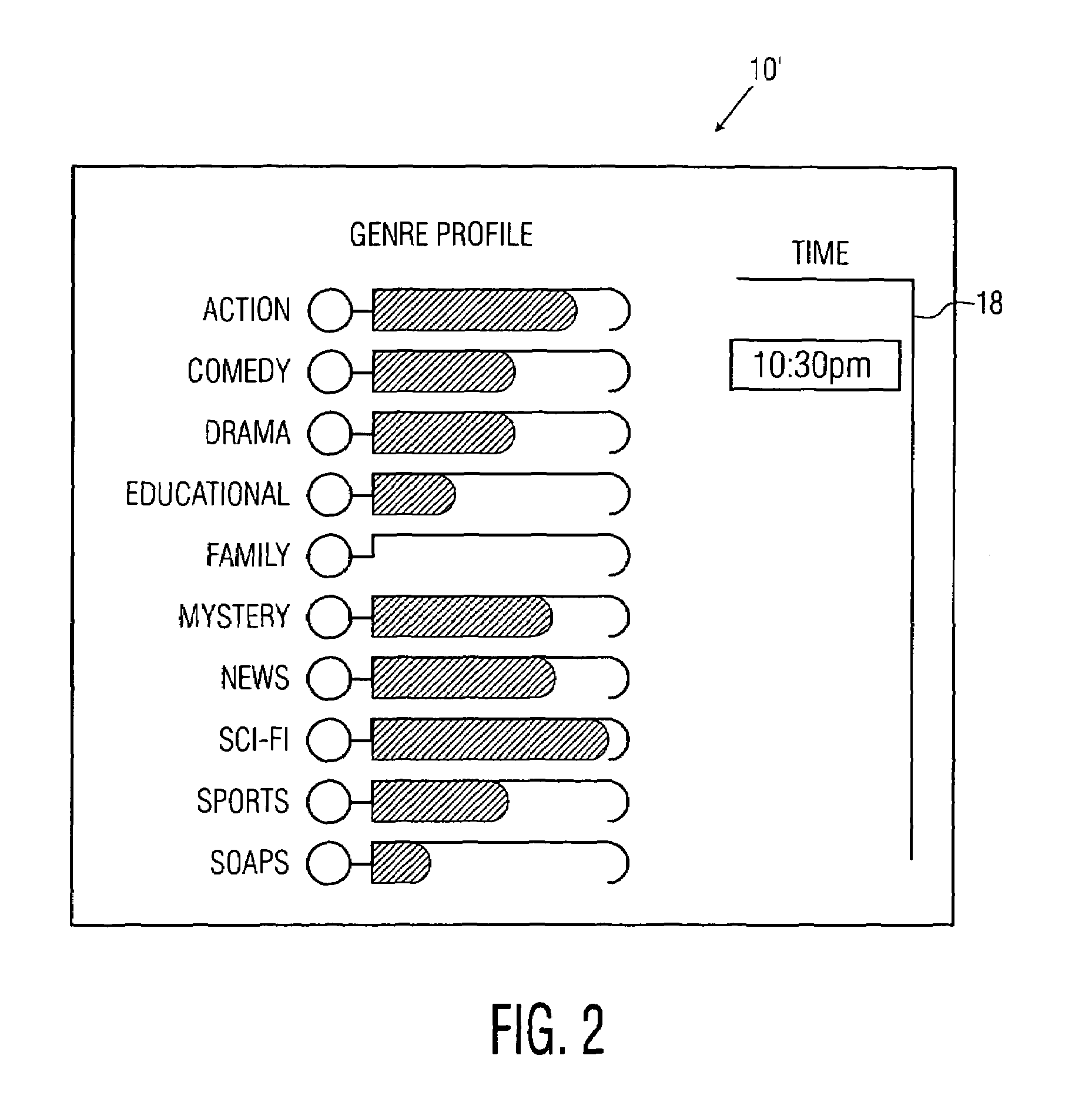
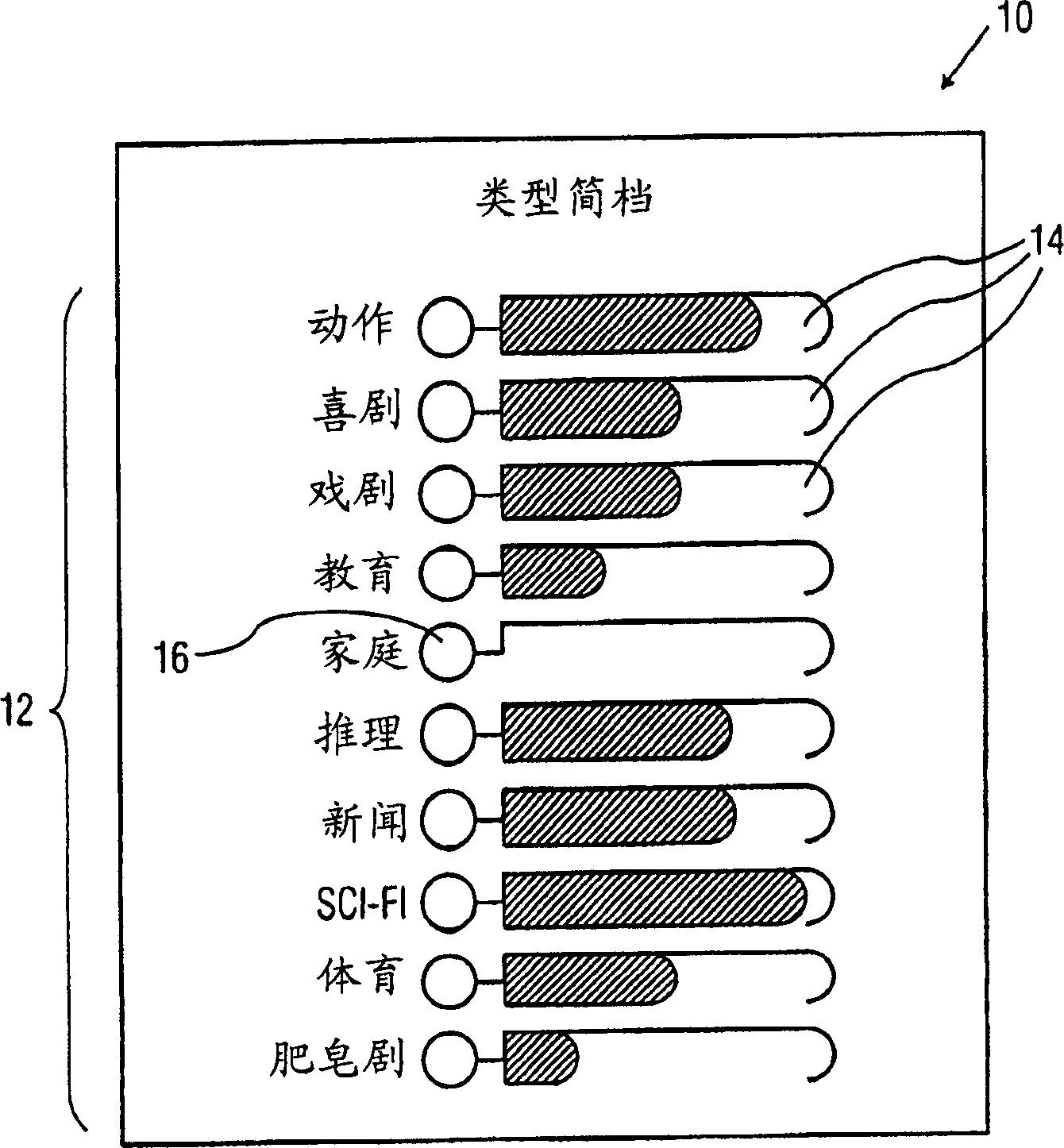
TV program profiling technique and interface
InactiveUS7451470B2Accurately reflect true likeTelevision system detailsBroadcast with distributionGraphicsProgram profile
Owner:S I SV EL SPA
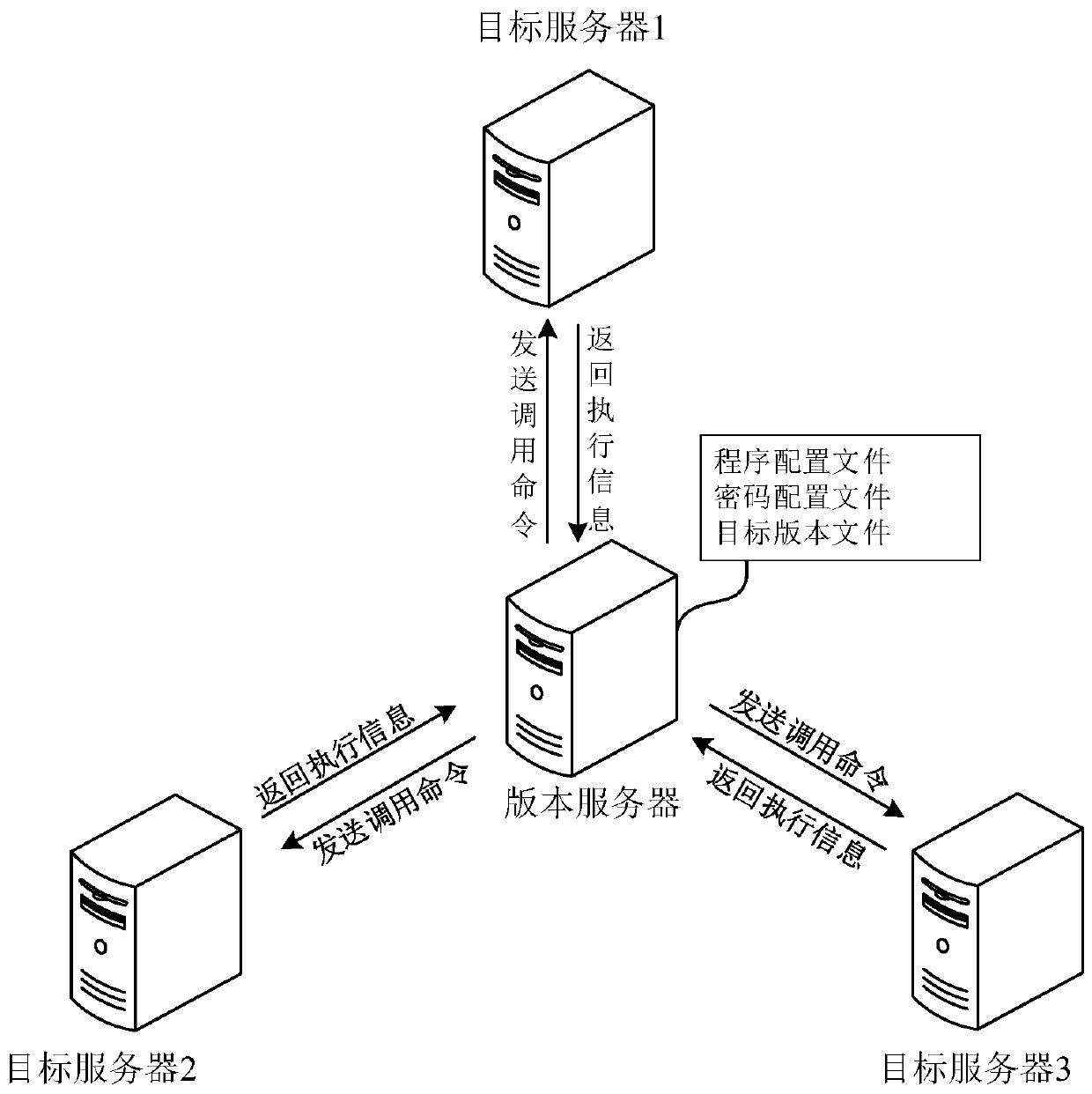
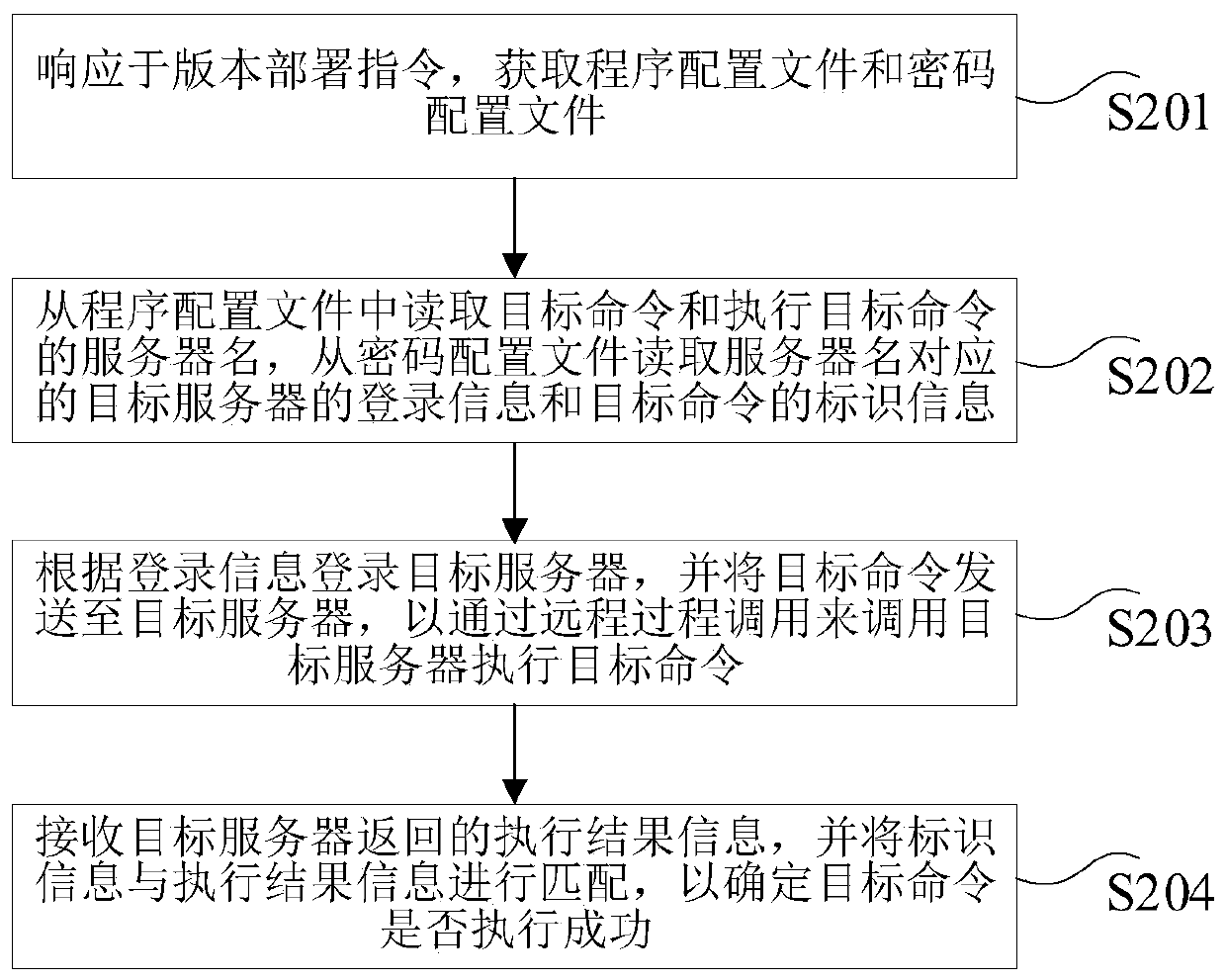
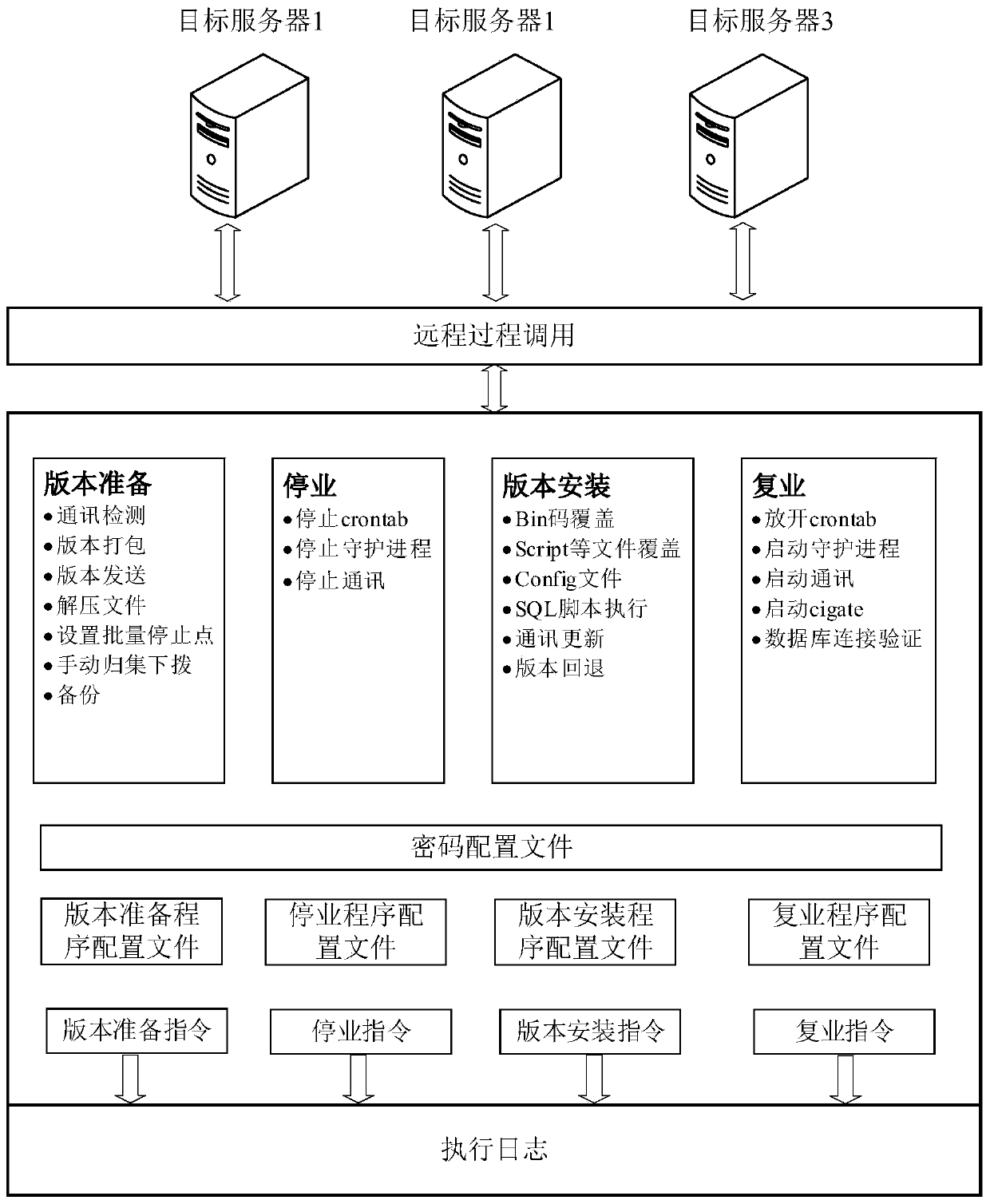
Automatic version deployment method and device, computer equipment and storage medium
InactiveCN110275872AEasy accessImplement automatic deploymentTransmissionSpecial data processing applicationsPasswordProgram profile
The invention provides an automatic version deployment method and device, computer equipment and a storage medium, and the method comprises the steps: responding to a version deployment instruction, and obtaining a program configuration file and a password configuration file; reading the target command and the server name for executing the target command from the program configuration file, and reading the login information of the target server corresponding to the server name and the identification information of the target command from the password configuration file; logging in the target server according to the login information, and sending the target command to the target server so as to call the target server to execute the target command through the remote procedure call; and receiving execution result information returned by the target server, and matching the identification information with the execution result information to determine whether the target command is successfully executed. According to the scheme, the version deployment efficiency can be effectively improved, and operation errors are reduced.
Owner:BANK OF CHINA
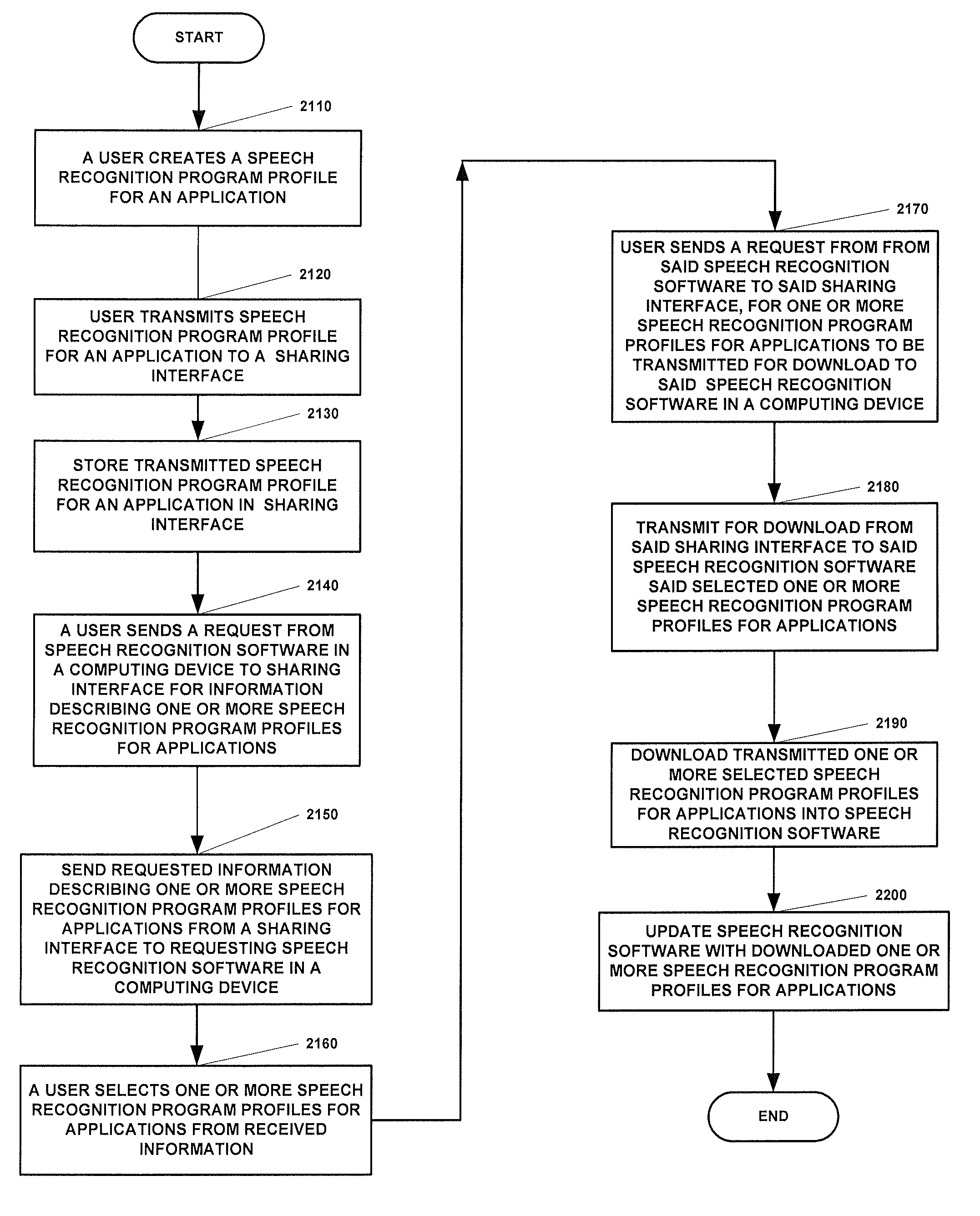
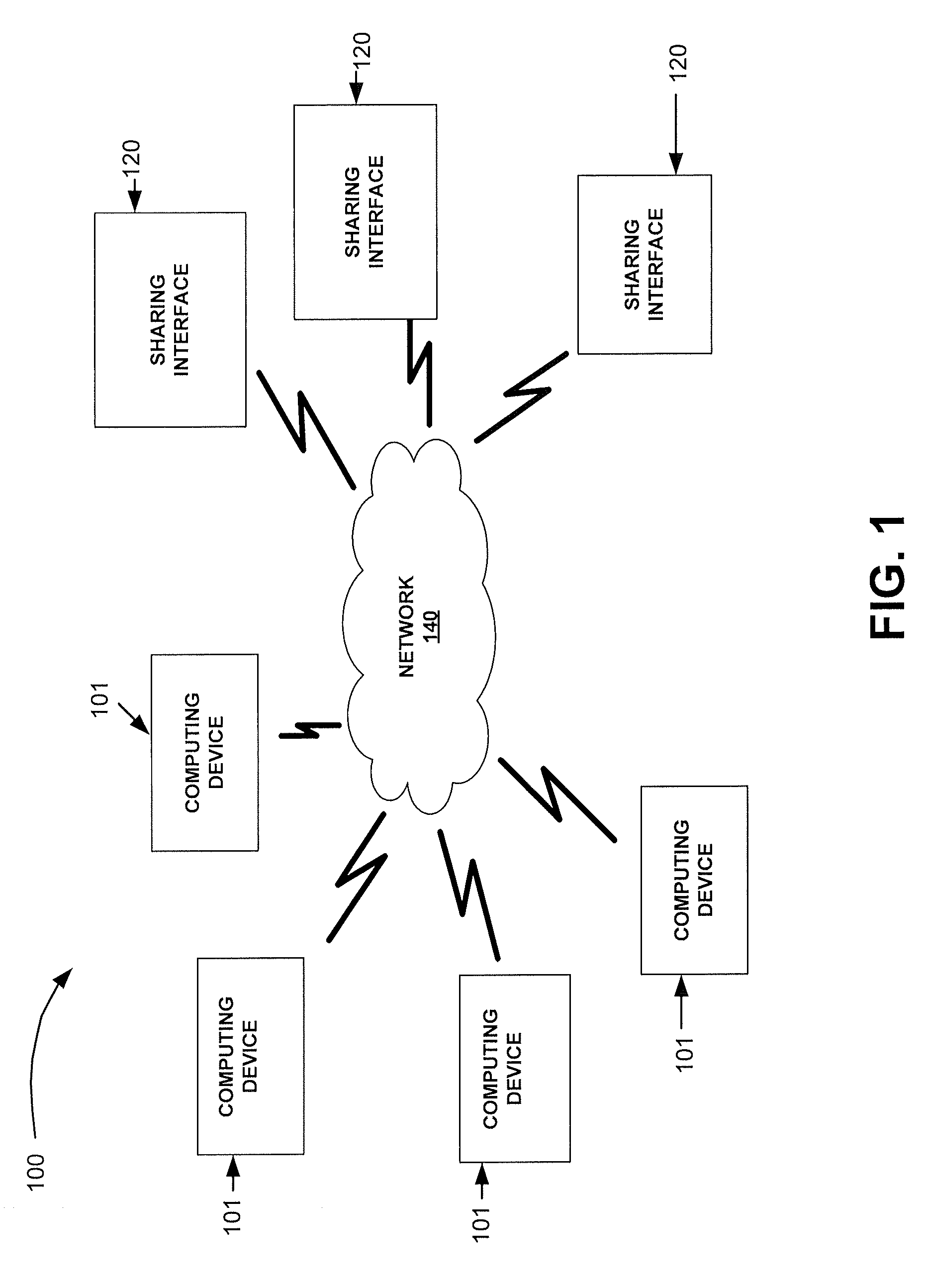
Method and system for sharing speech recognition program profiles for an application
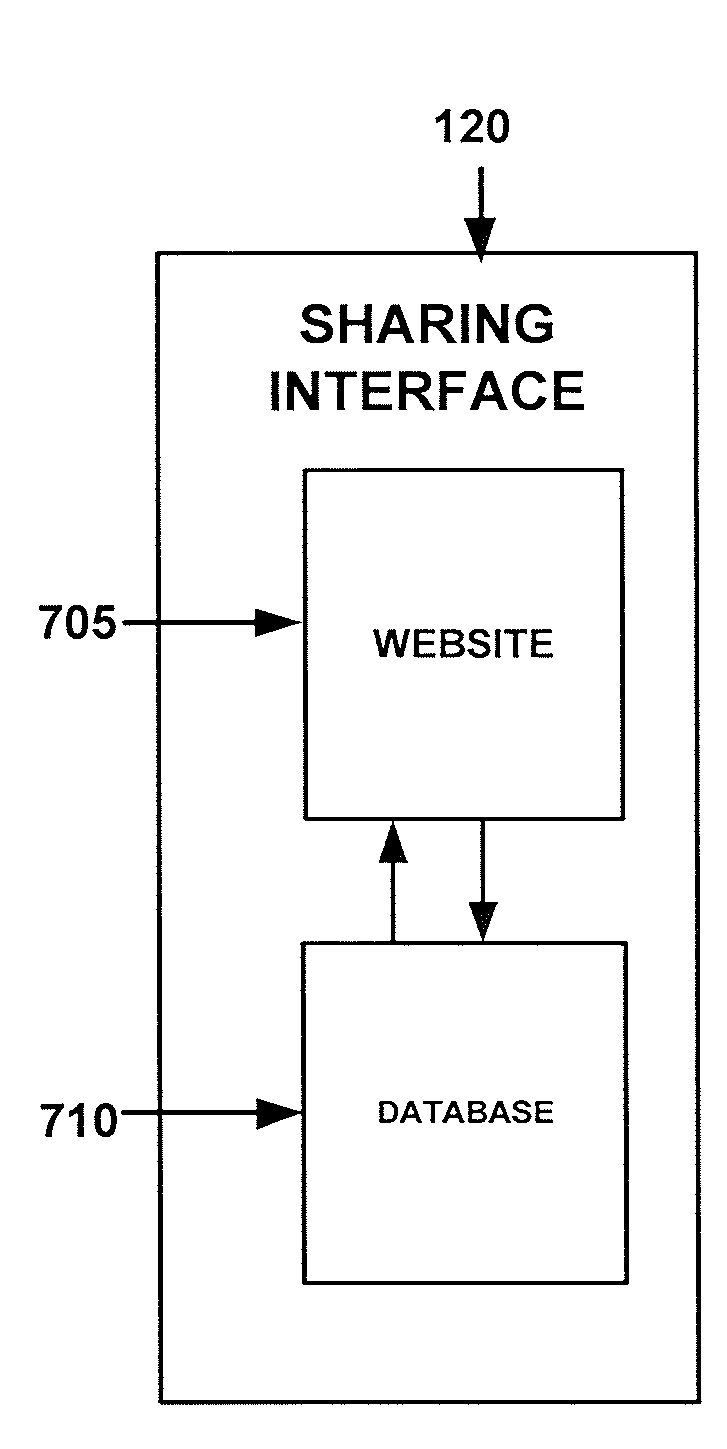
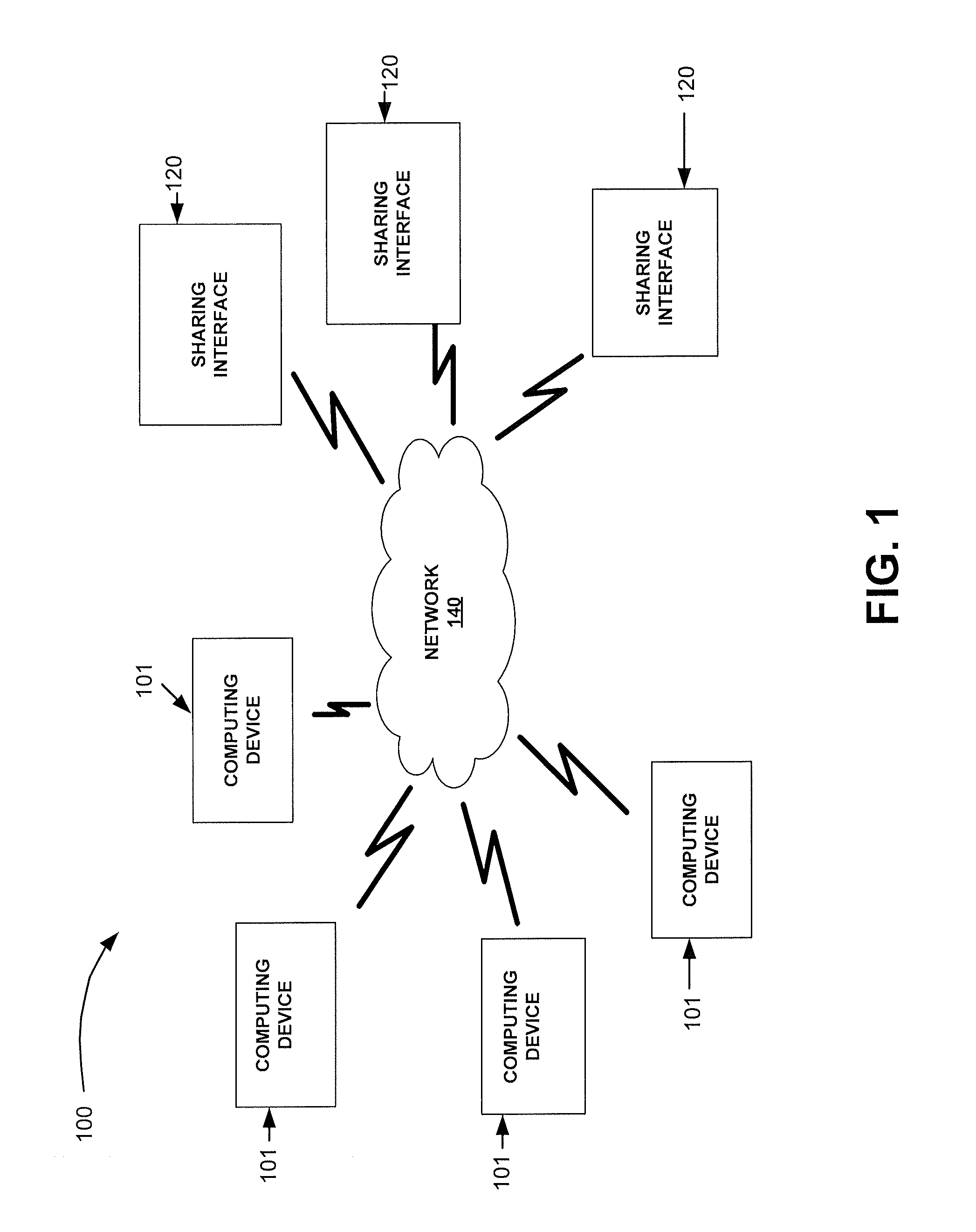
ActiveUS20120184370A1Available for useInput/output for user-computer interactionAnalogue secracy/subscription systemsTablet computerProgram profile
An embodiment provides a system and method for sharing between computing devices via a sharing interface, a speech recognition program profile for one or more applications. Another embodiment provides a system and method for sharing between computing devices via an sharing interface, a speech recognition program profile for one or more games. In an embodiment of the invention a personal computer or tablet may comprise a computing device and or a sharing interface. In an embodiment of the invention a cell phone may comprise a computing device and or a sharing interface. In an embodiment of the invention a game play device may be a computing device and or a sharing interface.
Owner:GOOGLE LLC
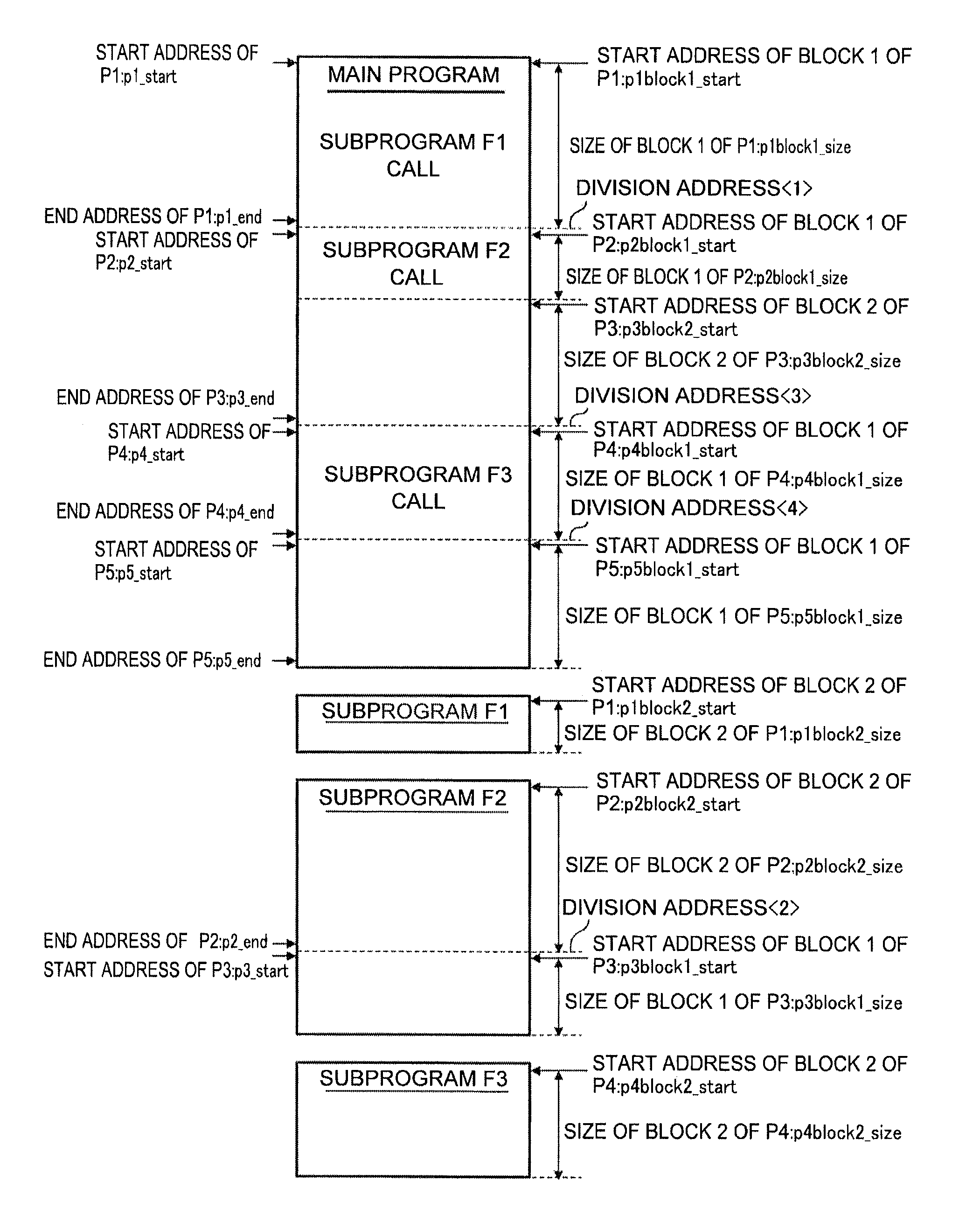
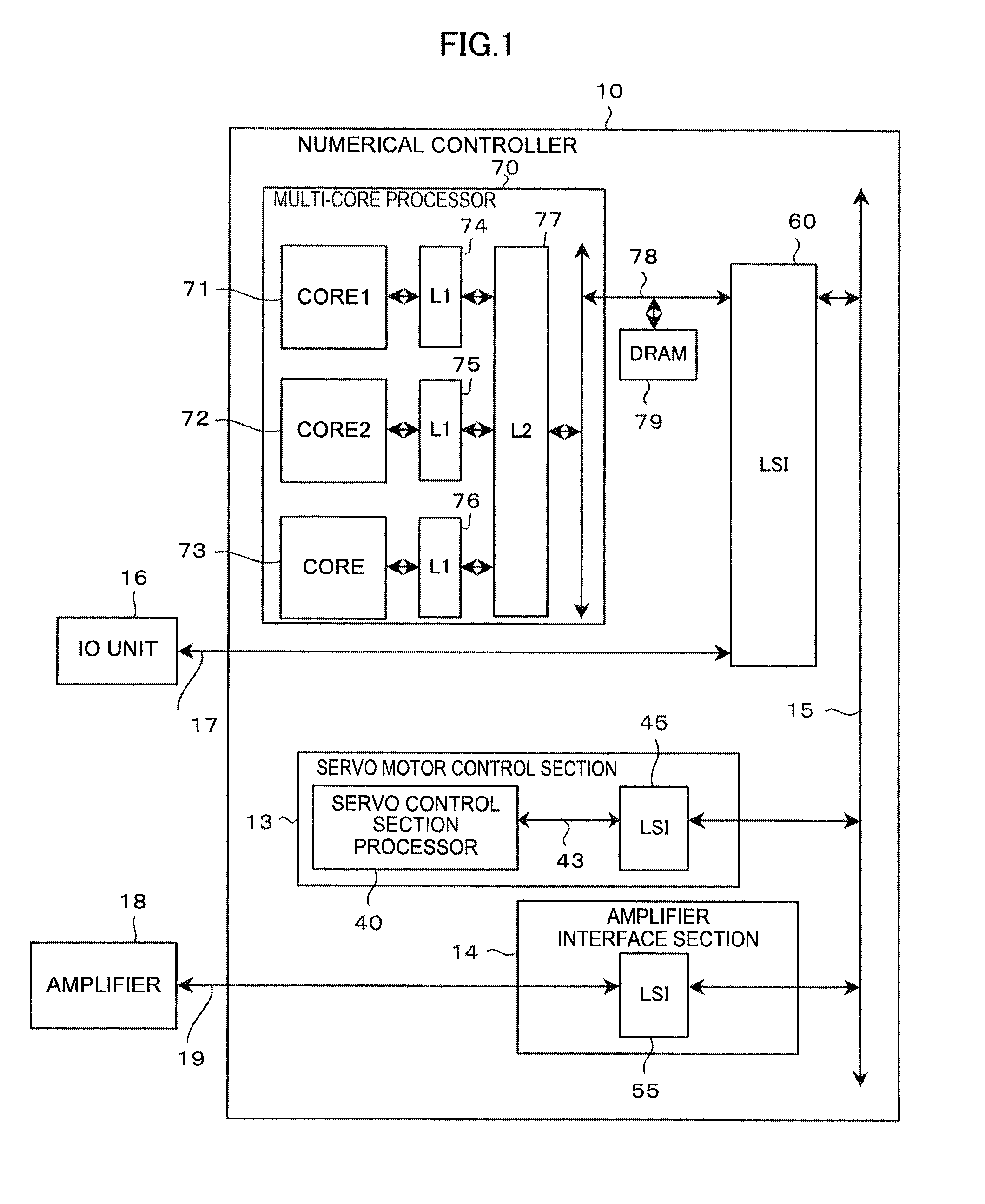
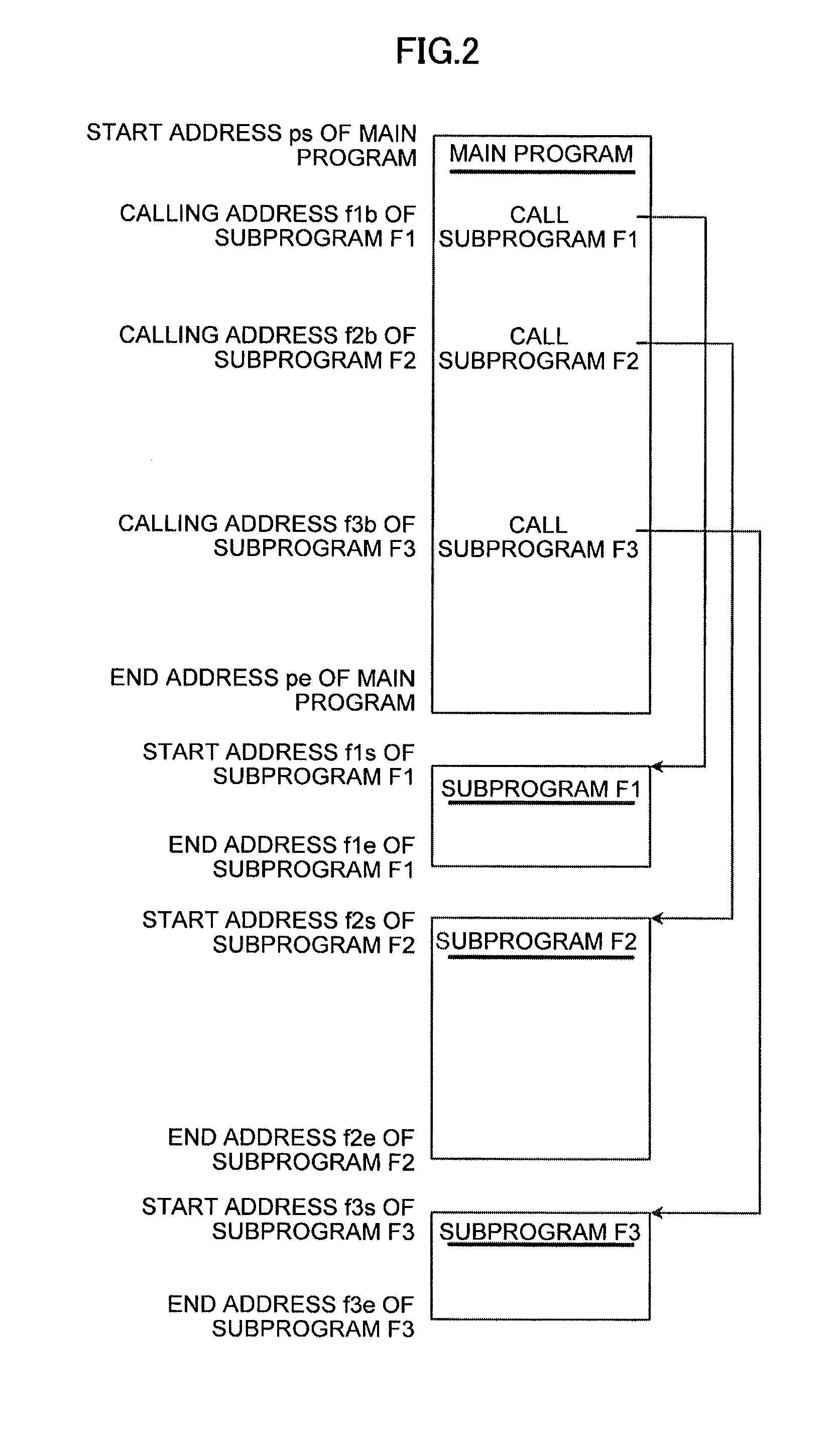
Controller executing sequential program using multi-core processor
InactiveUS20150286574A1High-speed executionMemory architecture accessing/allocationInstruction analysisProgram profileMulti-core processor
A sequential program is divided into programs each with a size fitted into a cache memory using program profile information and prepared cache memory information. Program profile information on the sequential program and information on the cache memory are acquired. Based on the acquired information, division addresses at which the sequential program is divided are determined. The IDs of the division programs, assigned core numbers, the start addresses and end addresses of the programs, and cache storage block information are stored in a memory as program execution information.
Owner:FANUC LTD
Method and apparatus for evaluating driver performance and determining driver rewards
The present invention is directed towards a method for evaluating driver performance. In exemplary embodiments, the method comprises receiving driver activity associated with a driver of a vehicle in a fleet, determining a driver score based on predetermined criteria and generating and updating a driver profile based on the driver activity and evaluating the driver score to generate rewards for the driver and updating the driver profile accordingly.
Owner:AZUGA INC
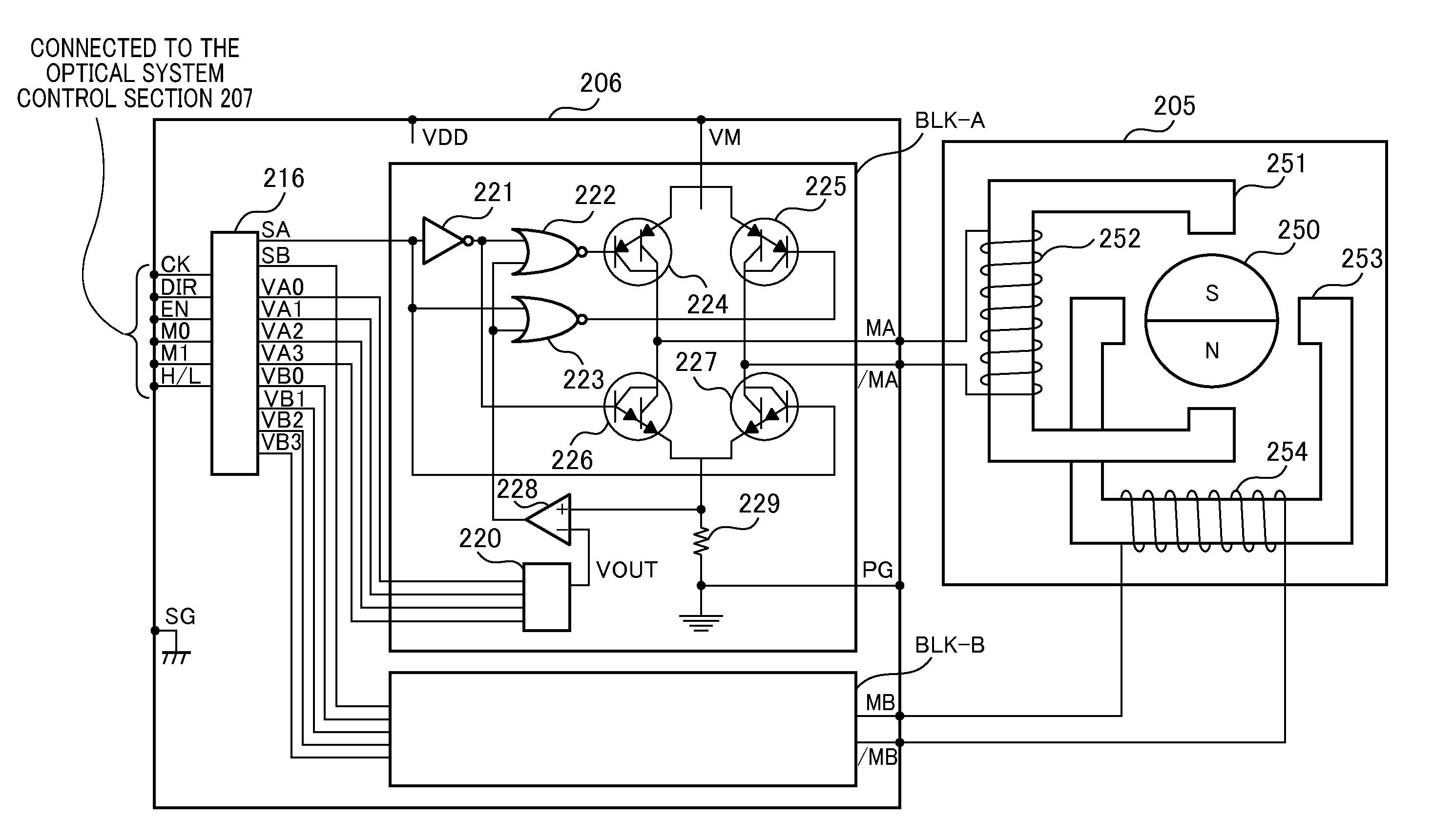
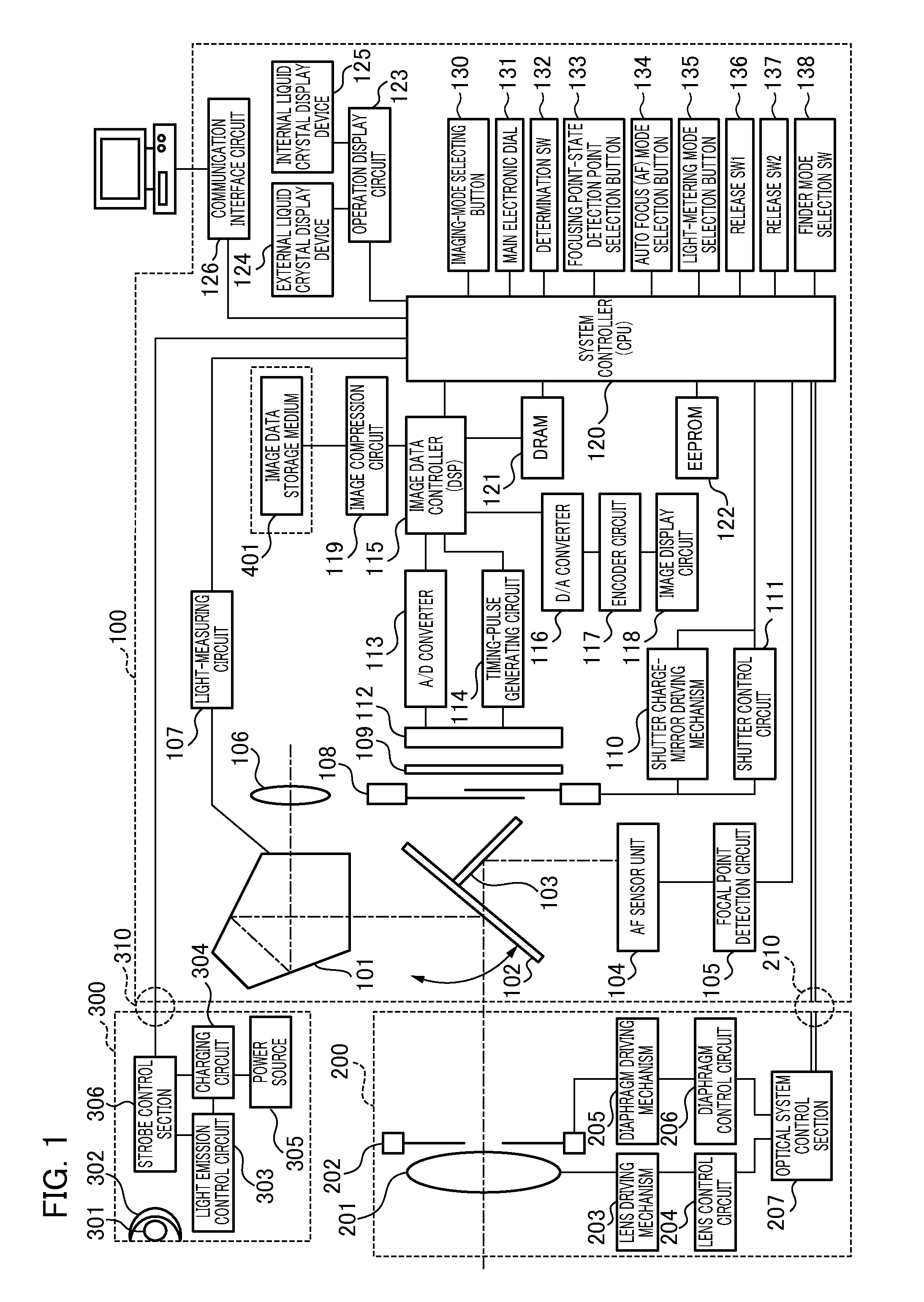
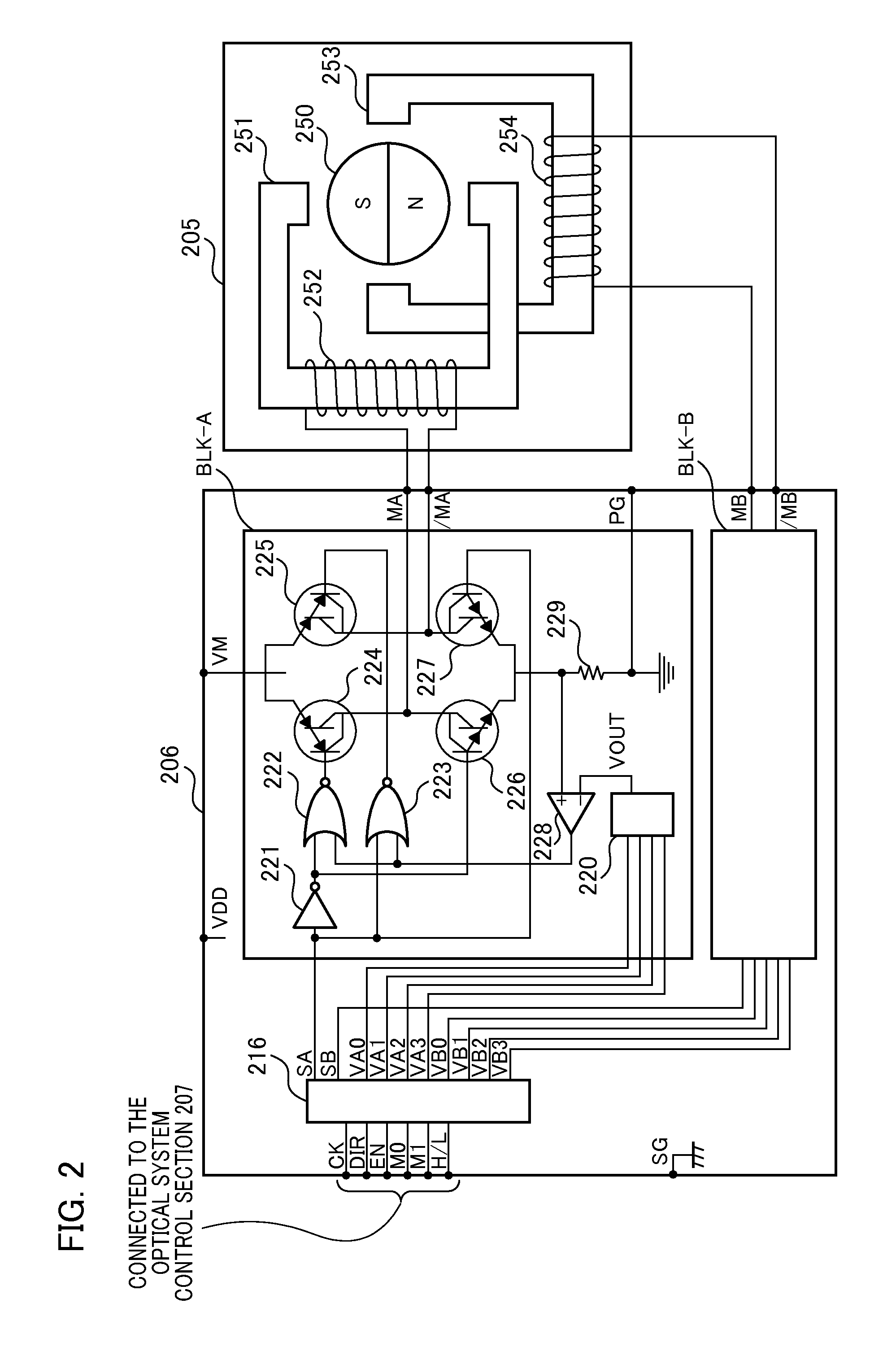
Imaging apparatus and method for controlling same
ActiveUS20110076006A1Favorable moving image exposure controlReduce electric powerTelevision system detailsColor television detailsElectric forceExposure control
In an imaging apparatus including a stepping motor that drives a diaphragm, a favorable moving image exposure control is carried out while reducing electrical power required for holding the diaphragm position. For moving image exposure control, a determination unit determines the presence or absence of the diaphragm driving. When a rotor and the magnetic poles of the stator do not face to each other in the first operation mode, the control unit of a stepping motor drives the rotor to a facing position, and shuts off the current in a coil. When the diaphragm driving does not occur in the second operation mode, the control unit of a stepping motor shuts off the current in the coil at the state where the rotor of the motor and the magnetic poles of the stator face to each other. A holding current to be supplied to the motor is shut off in the first and second operation modes, whereby the lower power consumption can be realized. The program profile of a diaphragm drive method and an exposure control is switched depending on the type of an imaging lens unit, whereby a favorable moving image exposure control can be realized.
Owner:CANON KK
Method and apparatus for visualizing and interactively manipulating profile data
ActiveUS8502822B2Quick fixMany pointsWindingsDrawing from basic elementsStatistical analysisProgram profile
Profile data collected through sampling is transformed and visually and interactively manipulated and displayed. In one scenario, the profile data is collected through statistical profiling of a program for a video game. The game program profile data is visually and interactively manipulated and displayed to visually present a dynamic behavior of the video game that shows correlation of impacts that the functions of the program have on the video game's performance. This allows the developer to identify inefficient sections of the program for optimization.
Owner:NINTENDO CO LTD
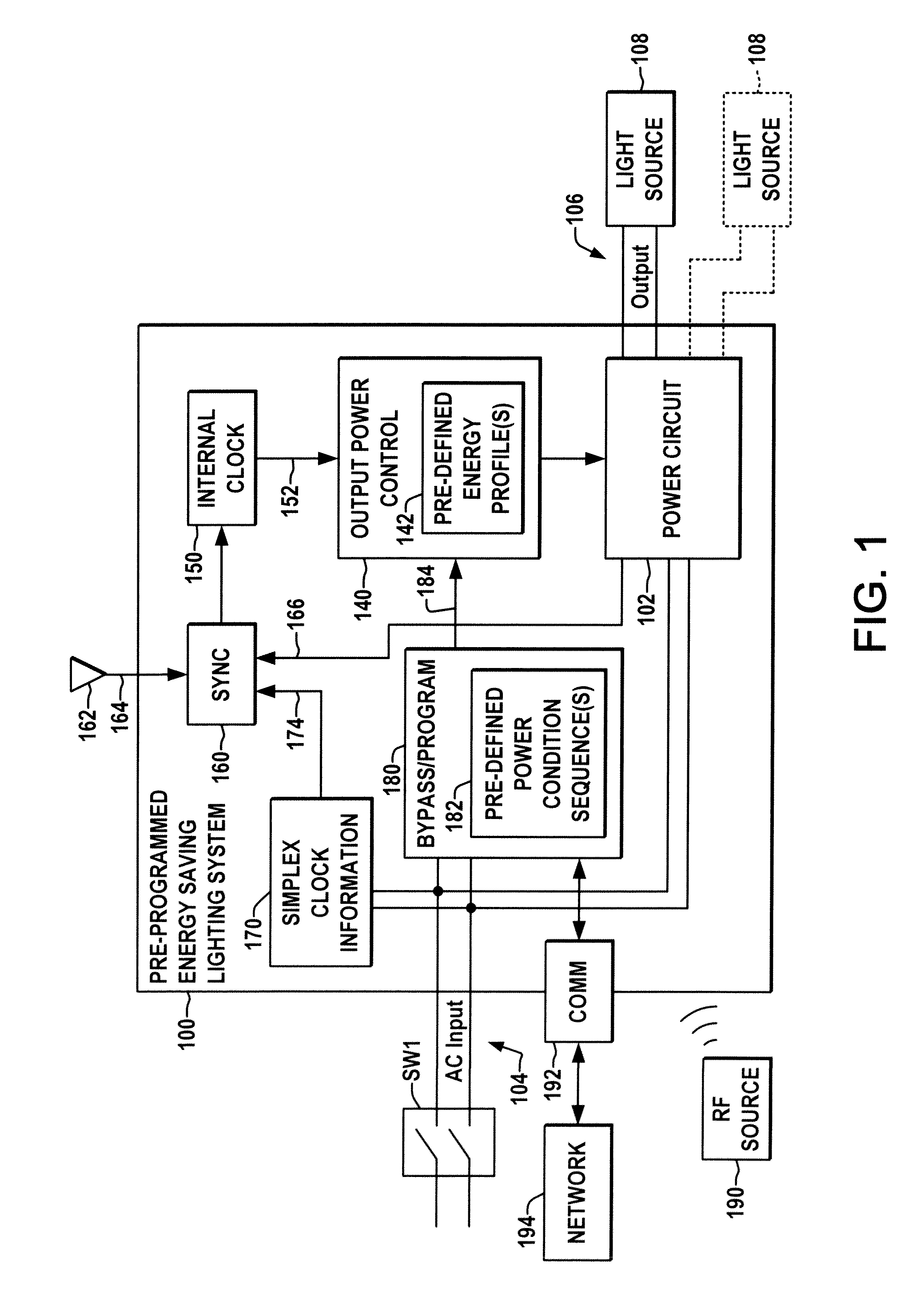
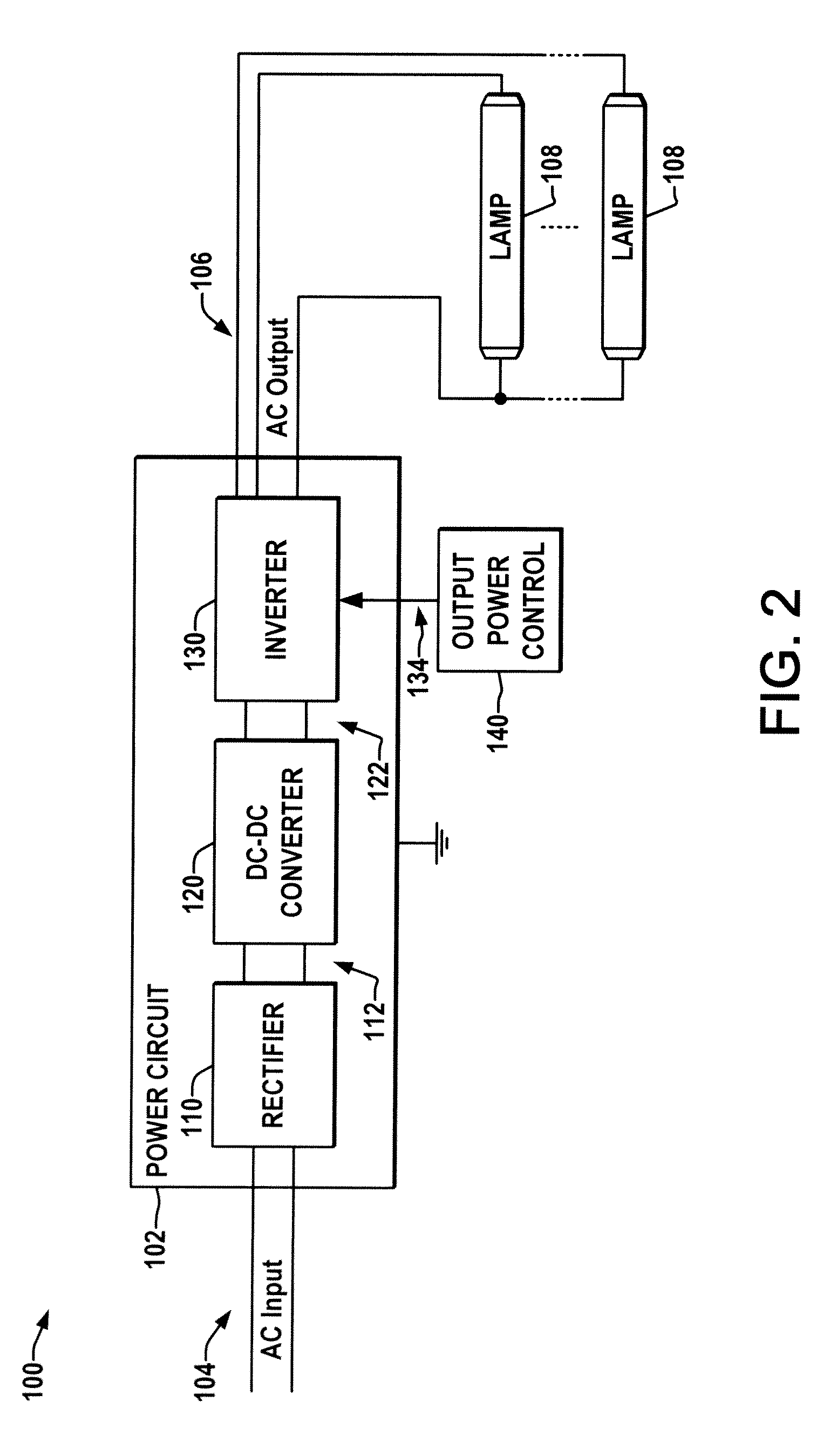
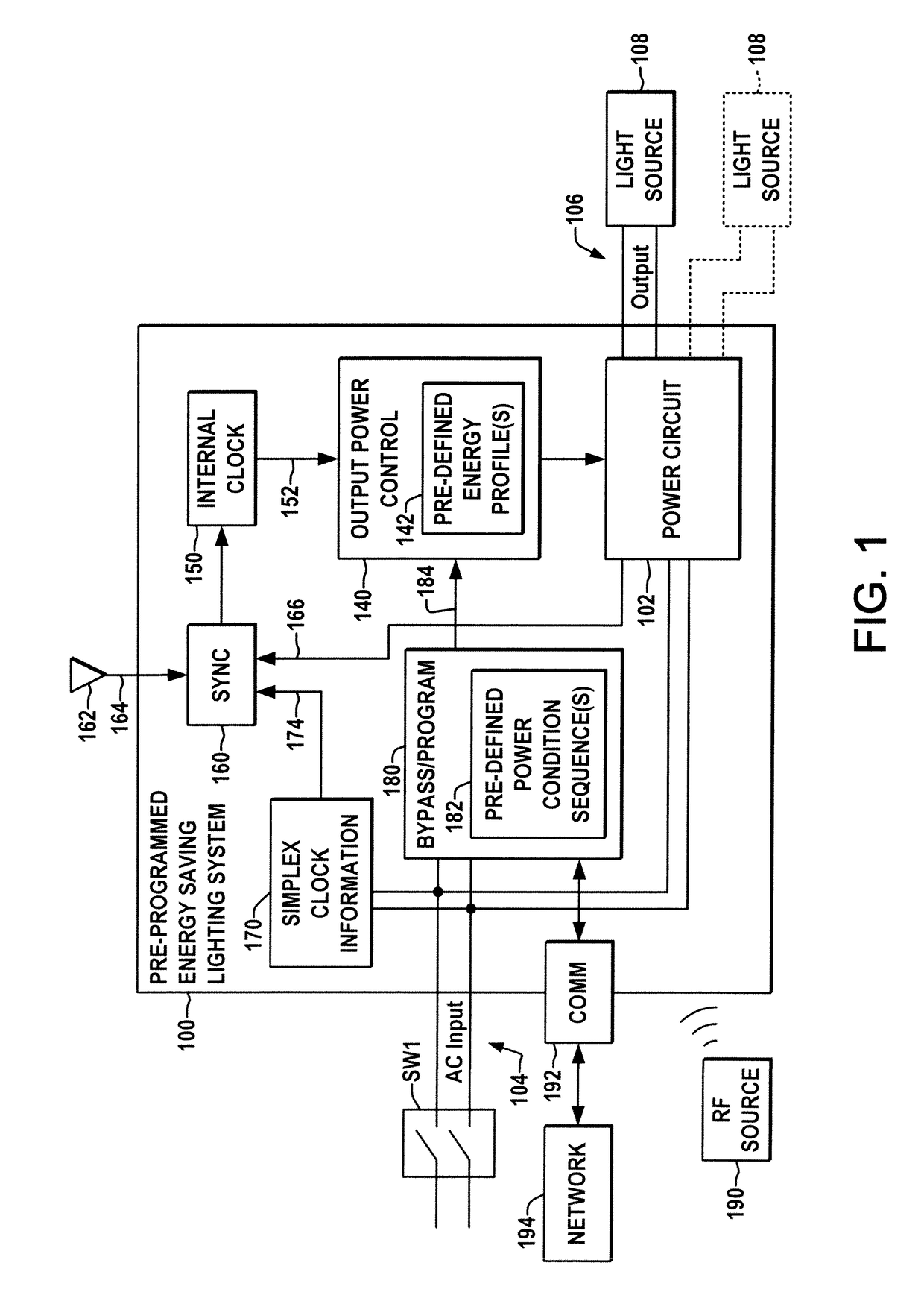
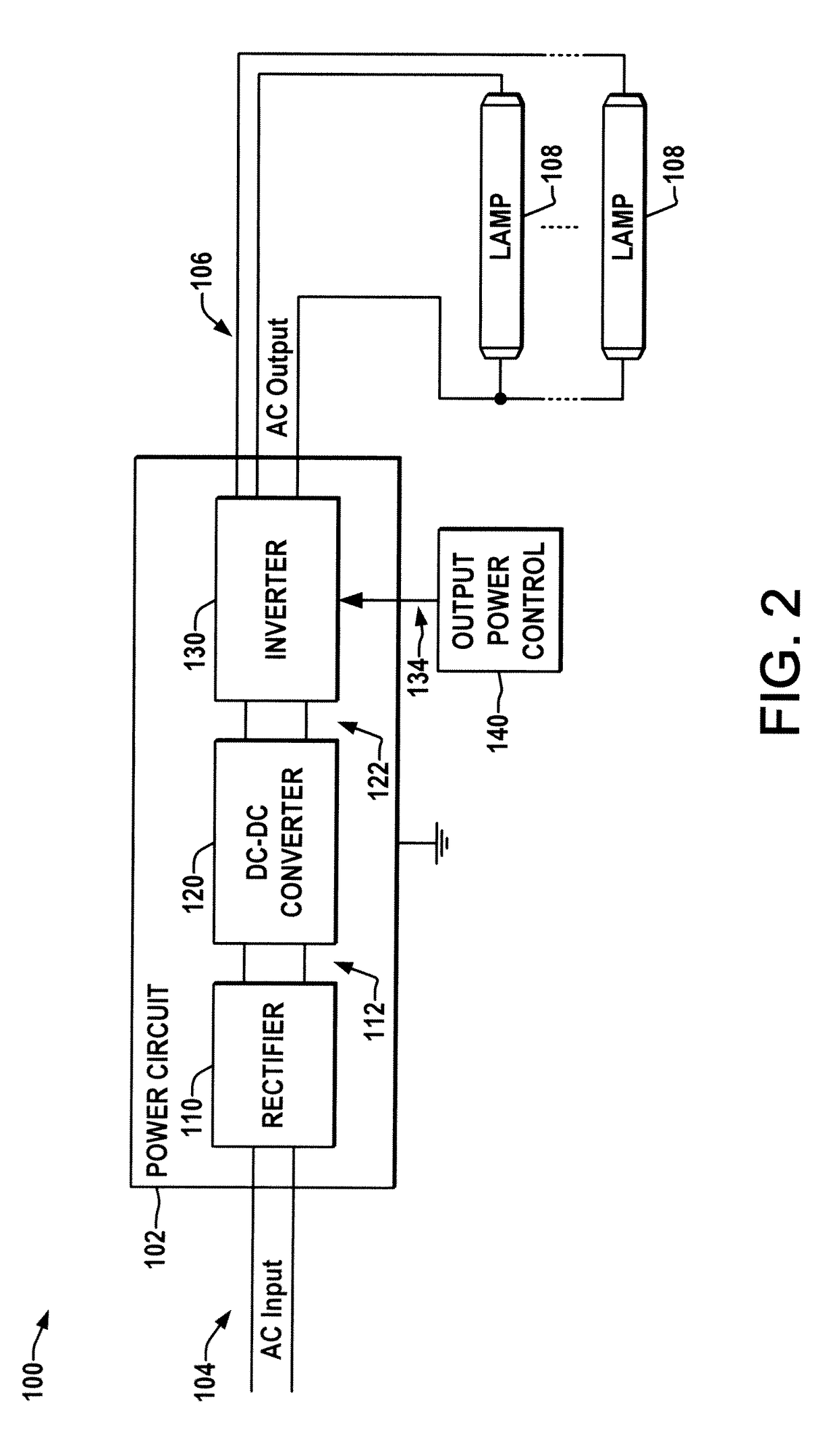
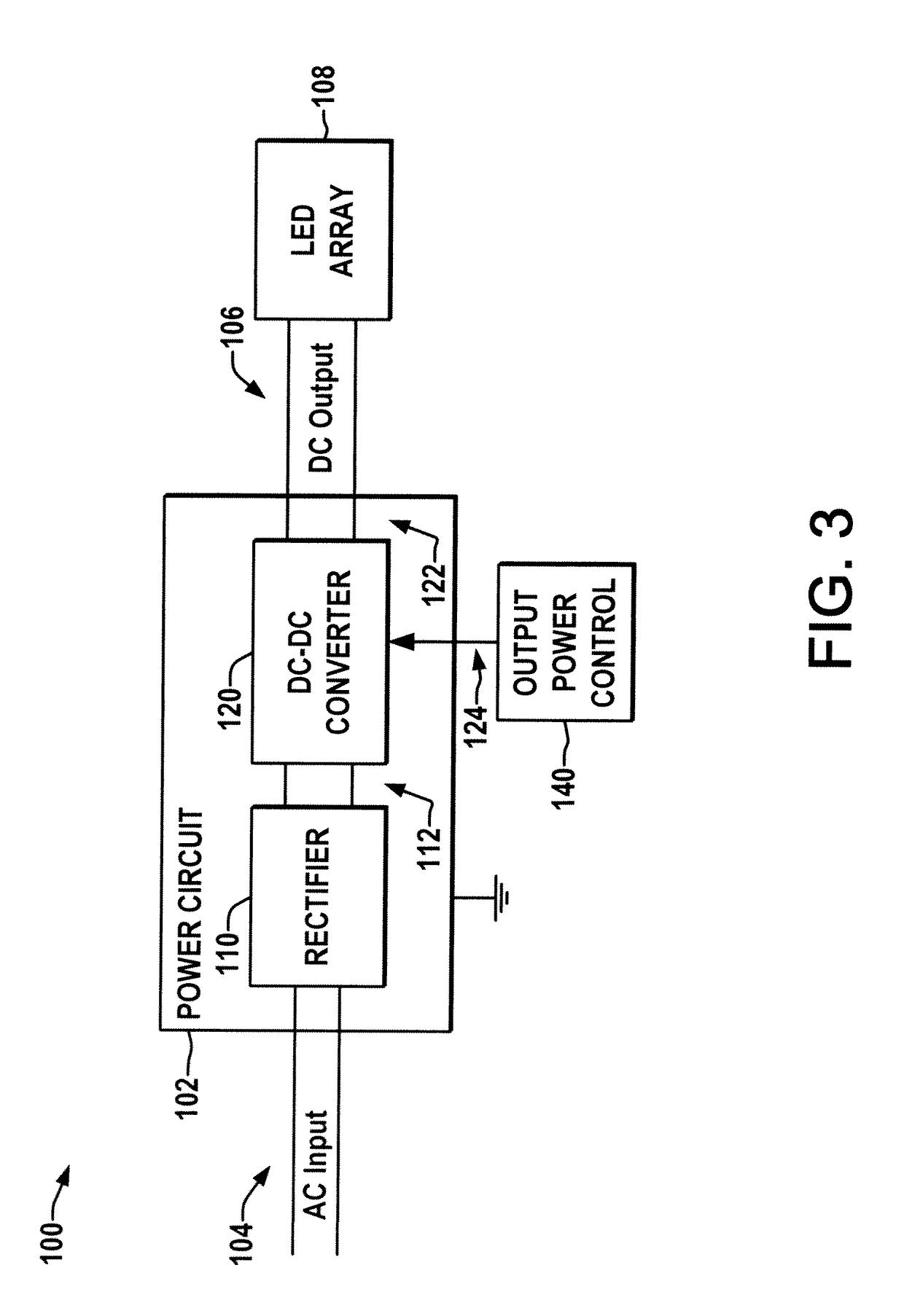
Pre-programmed energy management ballast or driver
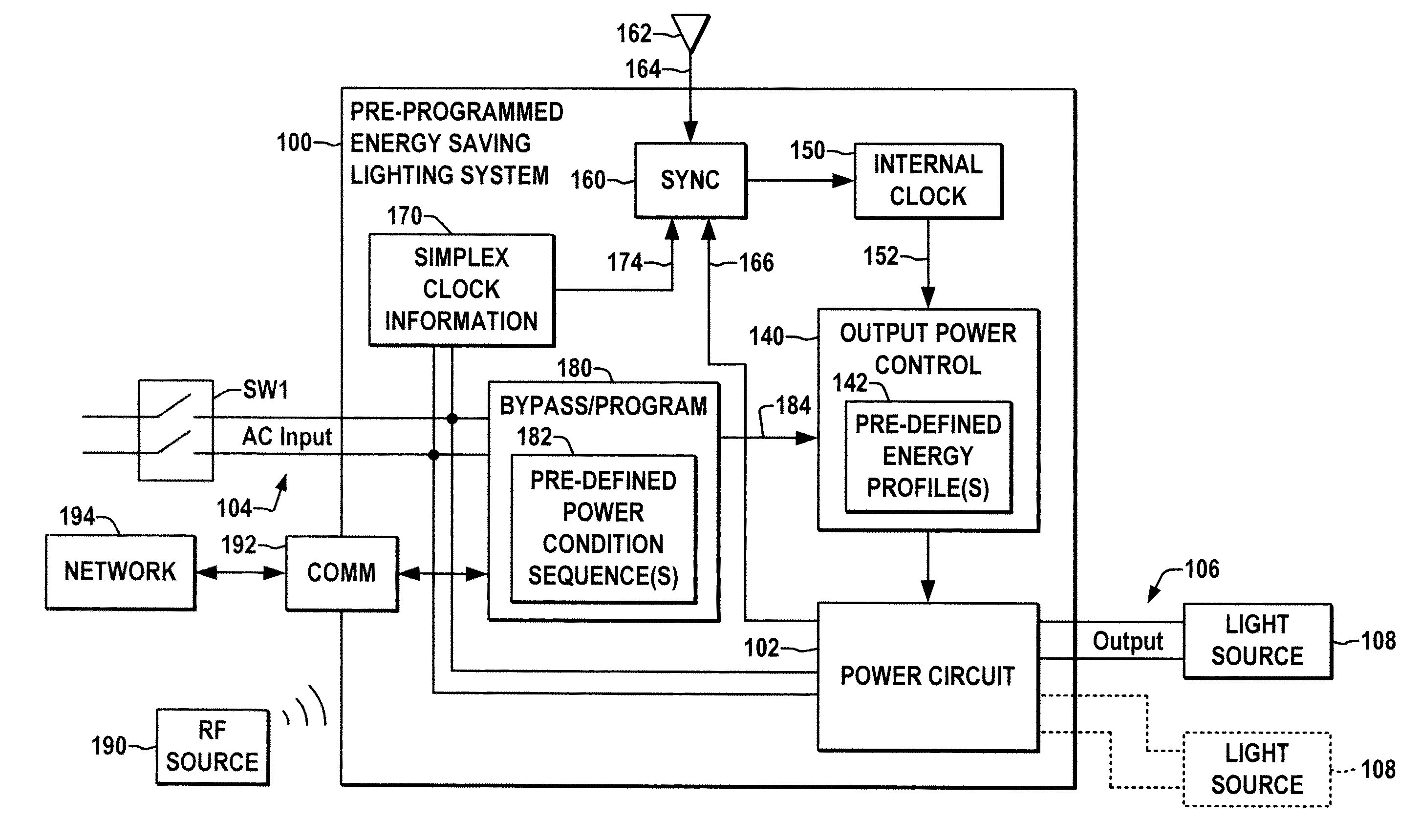
A pre-programmed energy saving ballast or driver is presented, having a pre-defined energy profile to which the output power is controlled in accordance with the current time ascertained from the input power connection via simplex clock information or from received broadcast time signals, and which allows a user to select from a number of pre-programmed profiles and / or to modify and store user-defined energy profiles.
Owner:GE LIGHTING SOLUTIONS LLC
Pre-programmed energy management ballast or driver
Owner:GE LIGHTING SOLUTIONS LLC
Method and system for scheduling jobs based on predefined, re-usable profiles
A method for scheduling execution of a work unit in a data processing system, wherein the execution of the work unit involves the execution of at least one program, the method comprising: providing a first collection of pieces of information necessary to execute the work unit, said first collection of pieces of information being arranged in at least one pre-defined, re-usable program profile corresponding to the at least one program to be executed; receiving, in a request for scheduling execution of the work unit, a second collection of pieces of information necessary to execute the work unit; determining execution information for the execution of the work unit based on the first and second collections of pieces of information, and scheduling the execution of the work unit based on the determined execution information.
Owner:INT BUSINESS MASCH CORP
Method and system for sharing speech recognition program profiles for an application
ActiveUS8562434B2Analogue secracy/subscription systemsBroadcast information monitoringTablet computerPersonal computer
An embodiment provides a system and method for sharing between computing devices via a sharing interface, a speech recognition program profile for one or more applications. Another embodiment provides a system and method for sharing between computing devices via an sharing interface, a speech recognition program profile for one or more games. In an embodiment of the invention a personal computer or tablet may comprise a computing device and or a sharing interface. In an embodiment of the invention a cell phone may comprise a computing device and or a sharing interface. In an embodiment of the invention a game play device may be a computing device and or a sharing interface.
Owner:GOOGLE LLC
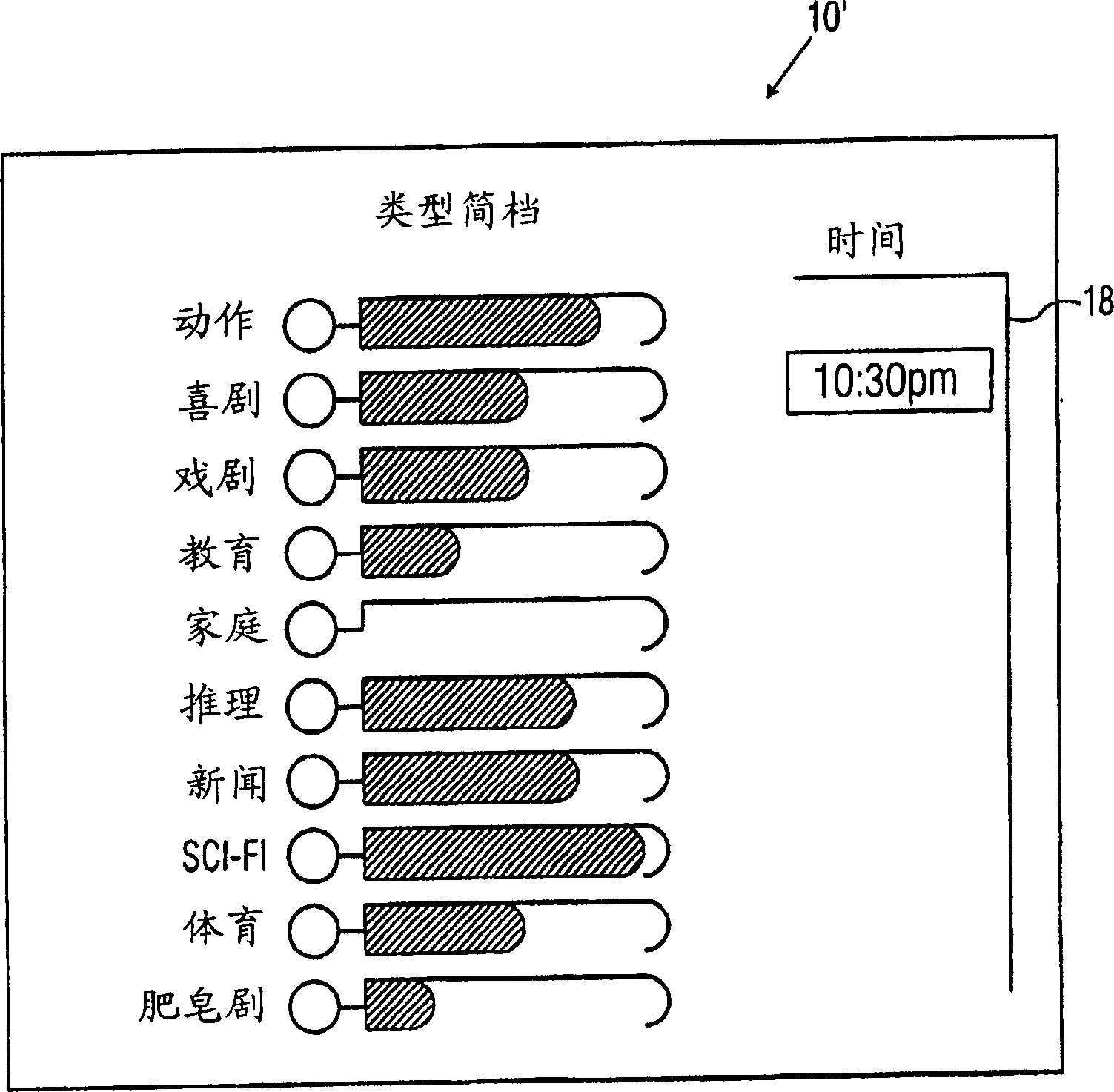
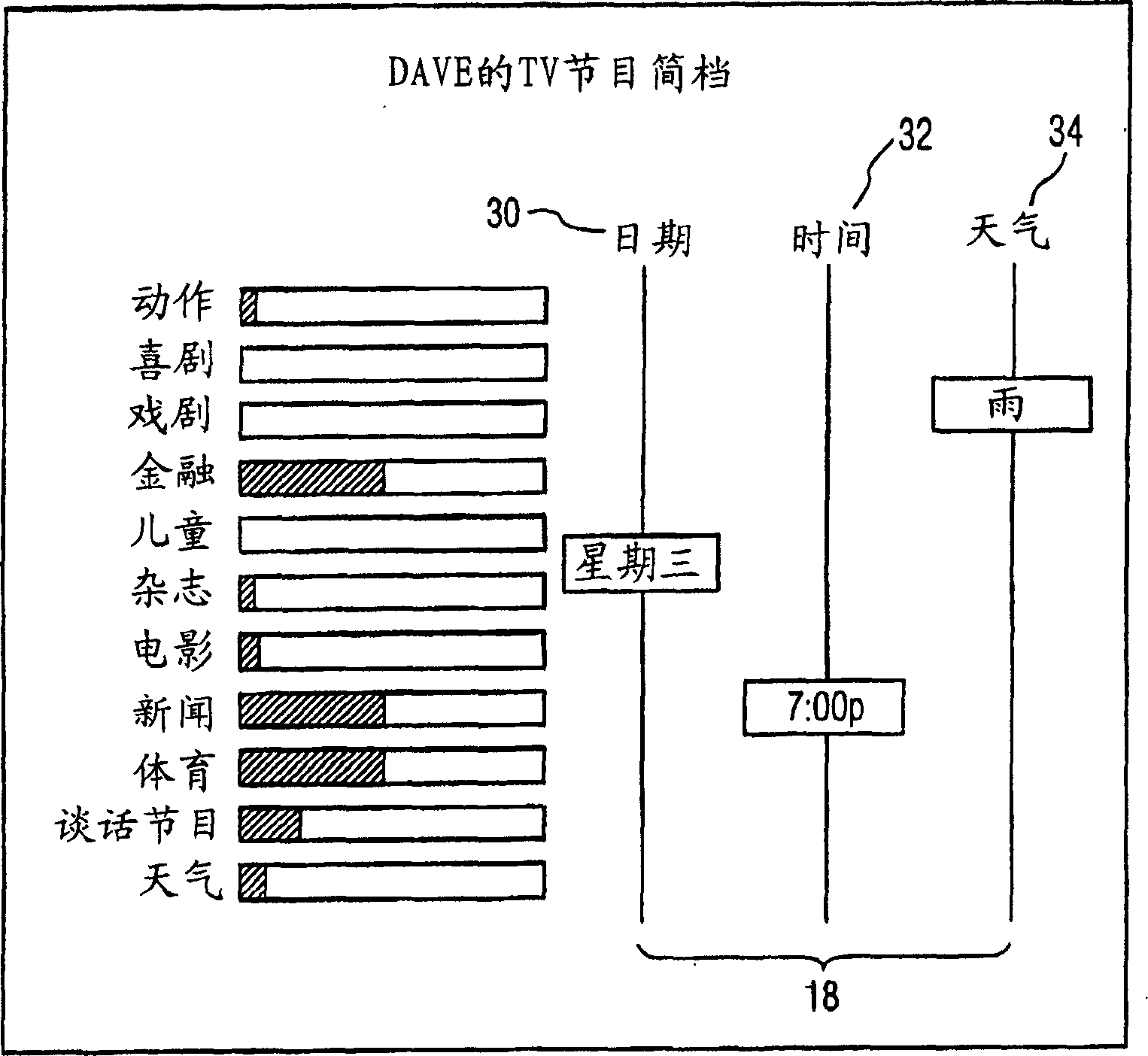
TV program profiling technique and interface
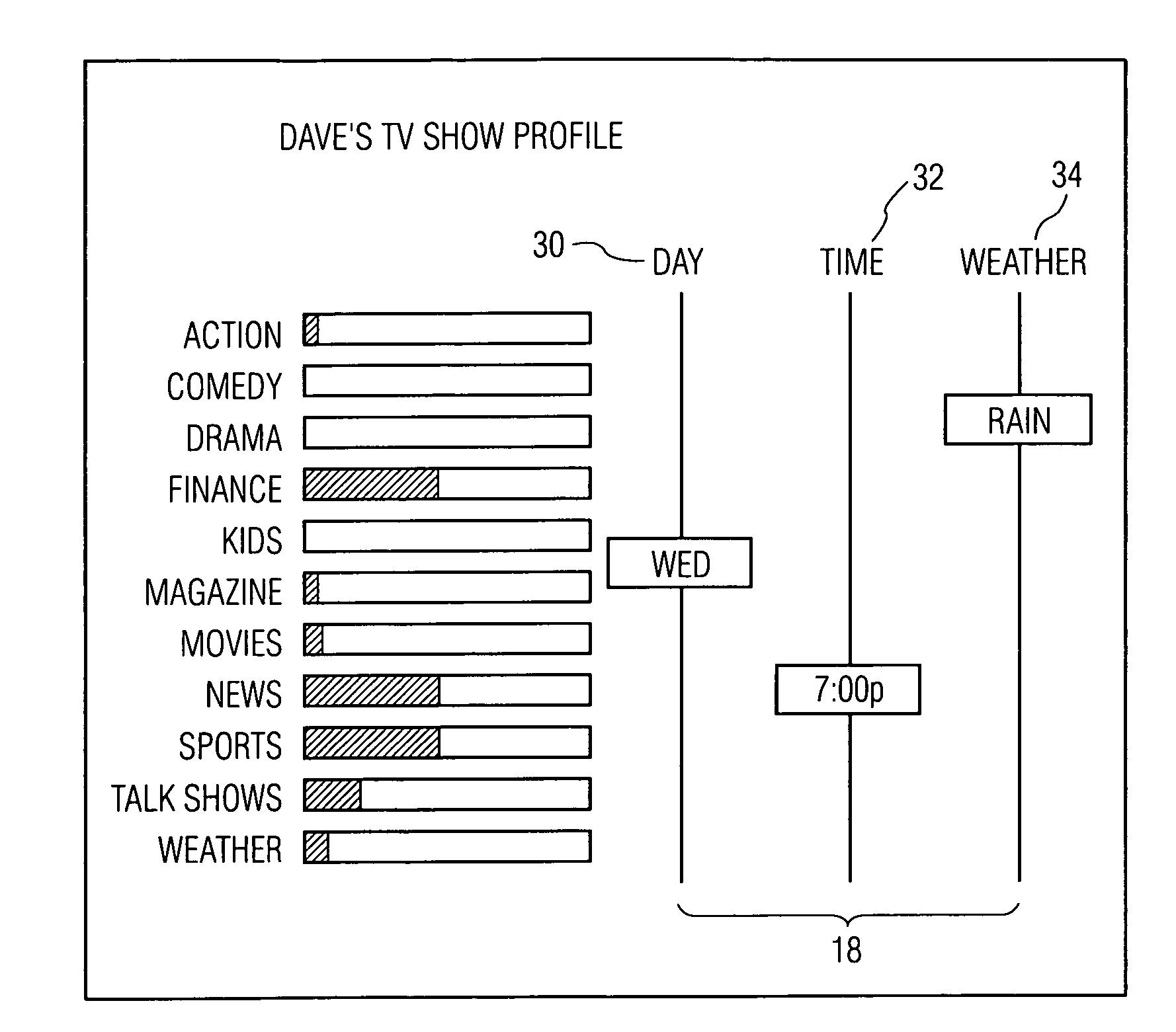
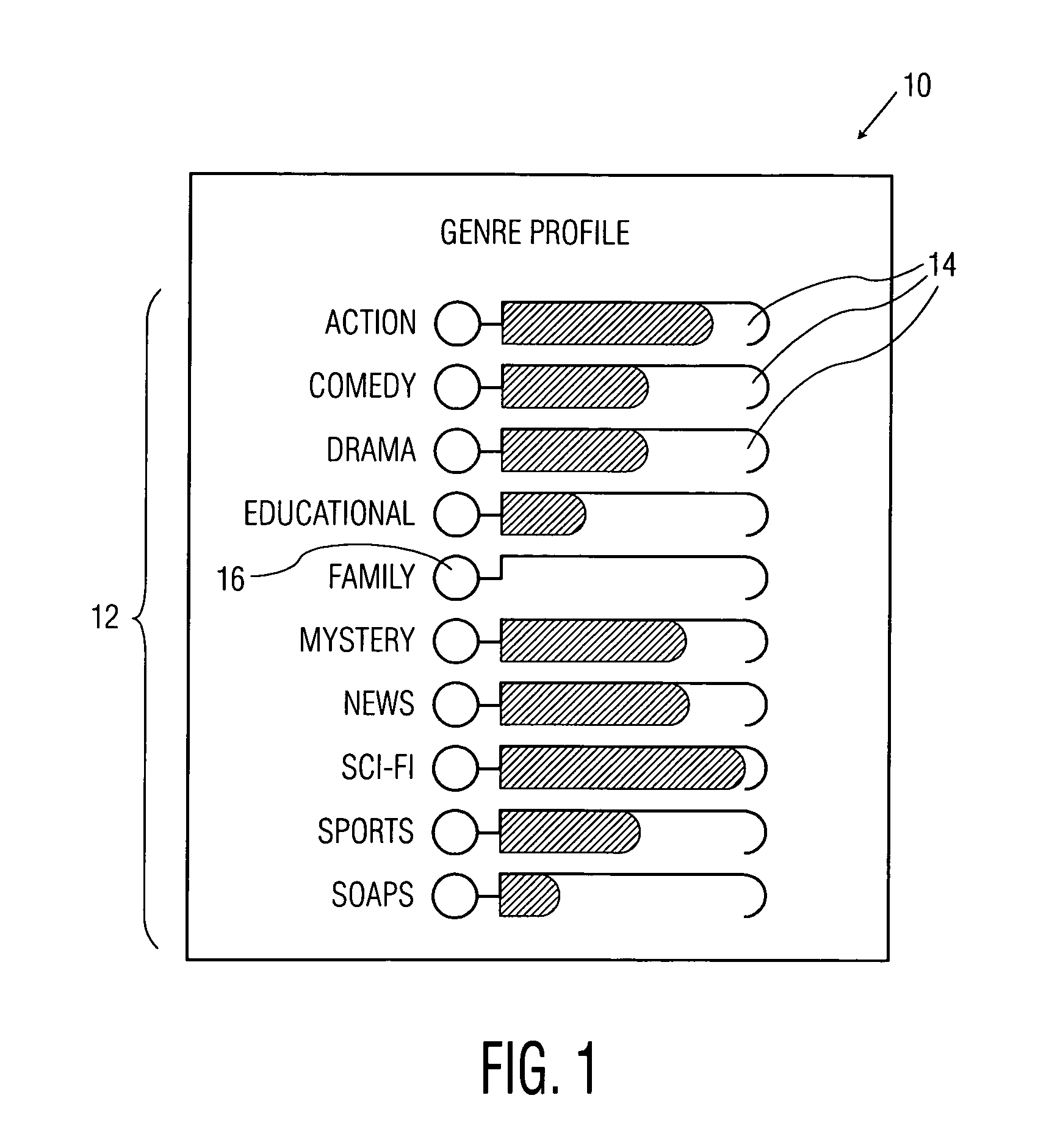
A new, interactive, television program profile interface and method are described. The interface is used to capture and display the likes and dislikes of a television viewer in multi-axis format. The weighting of the viewer's preferences proportionately changes over time. Those preferences are illustrated in bar graph format with respect to time or other axes. The viewer interacts with the graphical representations by time traversing the preferential chart, and providing necessary modifications and updates.
Owner:S I SV EL SOC ITAL PER LO SVILUPPO DELLELETTRONICA SPA
Method of Converting Personal Computers Into Thin Client Computers
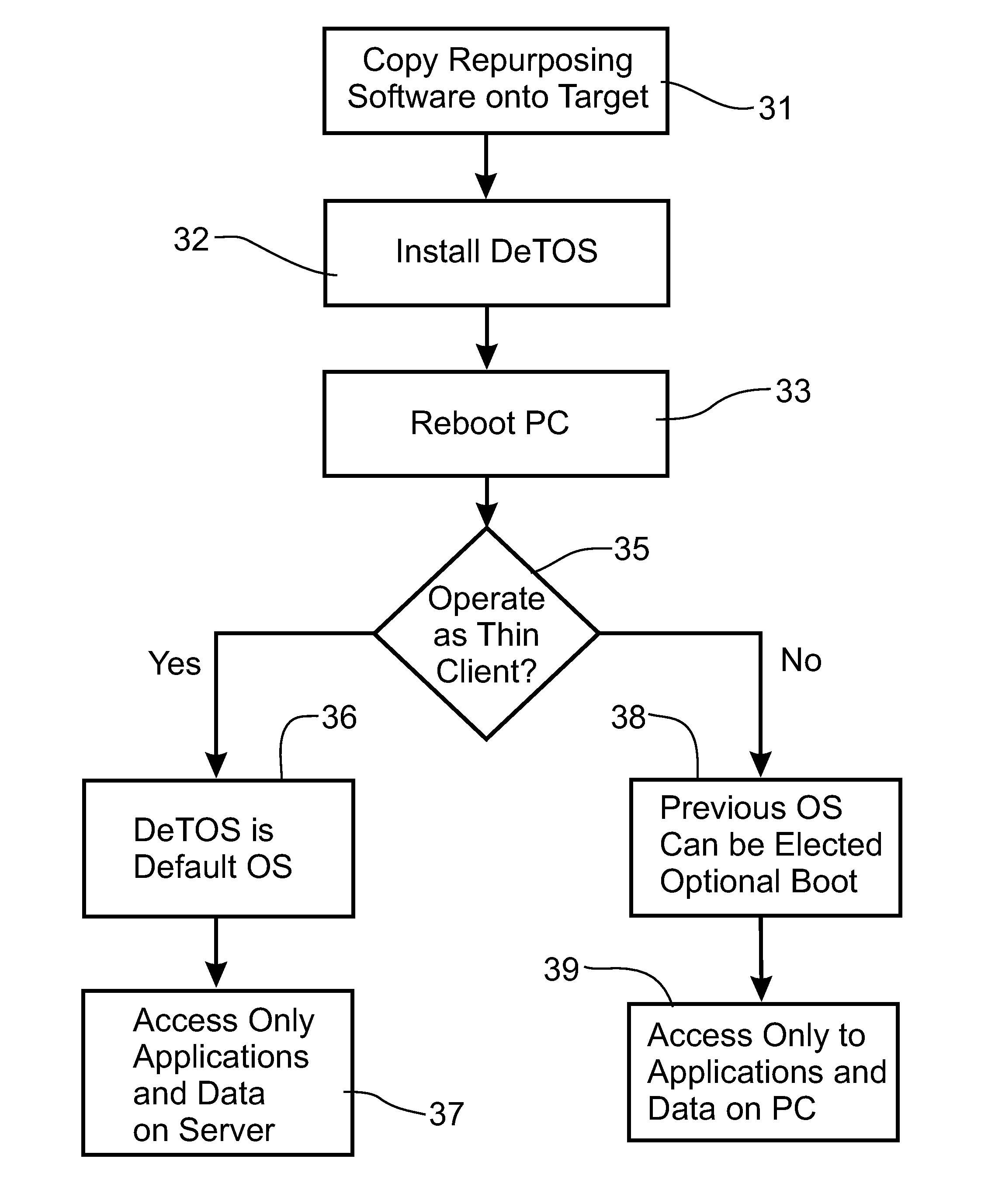
InactiveUS20110055535A1Rapid deploymentEasy to installDigital computer detailsData resettingHard disc driveProgram profile
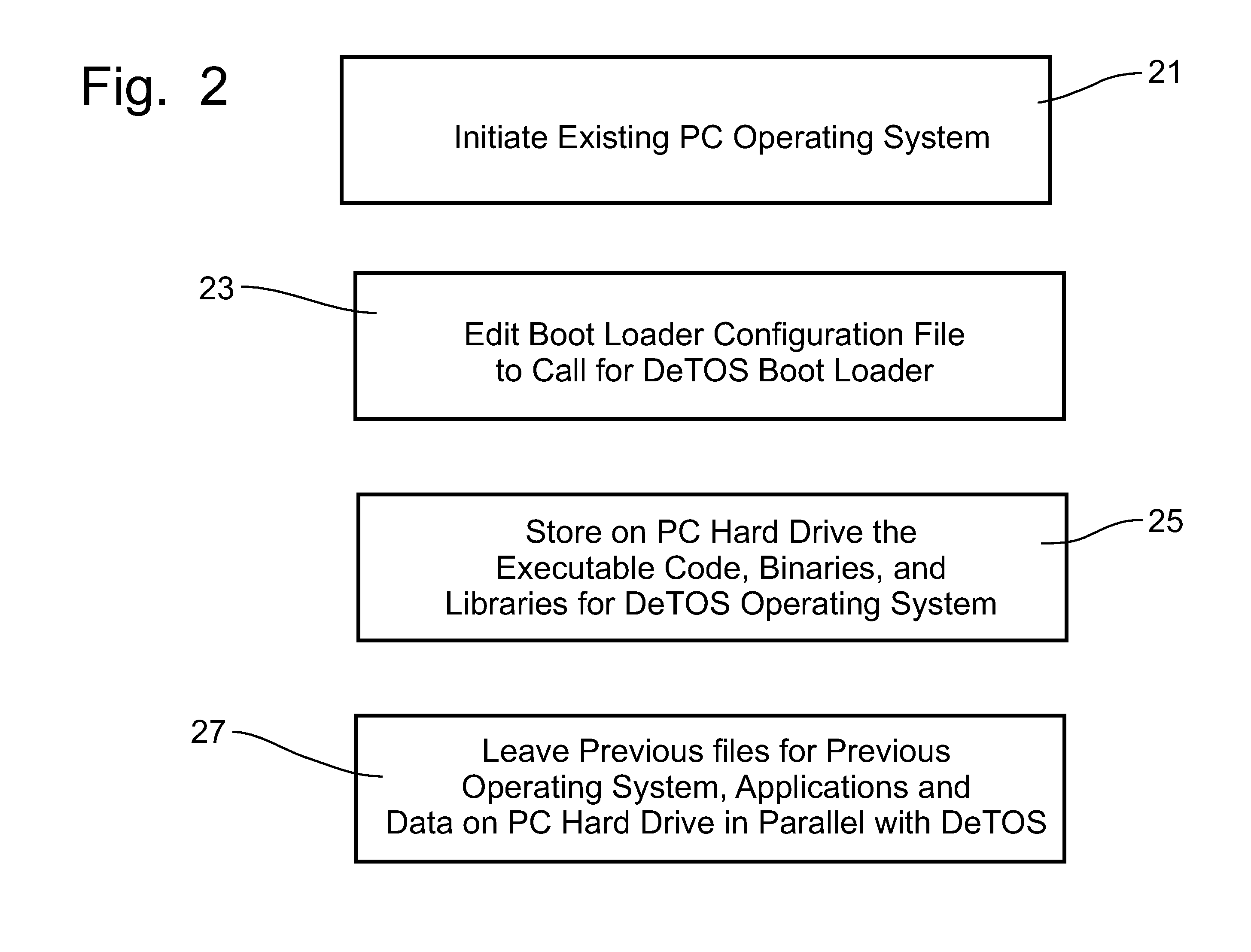
A system repurposes a personal computer operating with a conventional personal computer operating system, such as Windows® operating system, into a thin client computer system without requiring that the hard drive of the personal computer be re-formatted to remove the previous operating system. The personal computer has its boot loader configuration file edited to include a call to a thin client boot loader file to execute the thin client operating system stored on the personal computer hard drive instead of the previous operating system of the personal computer. The repurposed personal computer can be returned to the previous operating system by electing to bypass the thin client operating system. As a thin client computer, the repurposed personal computer is managed from a central server and can access applications and data on remote servers instead of using the application programs on the hard drive or the capability of storing data on the personal computer hard drive.
Owner:DEVON IT
Personalized content processing and delivery system and media
ActiveUS10417298B2Widespread user acceptanceGuaranteed maximum utilizationSpecial service for subscribersSpecial data processing applicationsPersonalizationDigital copy
A personalized content system enables a user with a communications device to convert and / or passively receive pre-selected content from multiple resources. A communications device has hardware and software to provide input and transmission to convert content from any form of media. The converted content is created by retrieving a digital copy of a digital record associated with it, and processing the digital copy for at least a web-based personalized application. Conversion is based on input of a code such as a telephone number, server program address, and a set of and / or range of characters. The transmission is communicated to at least one server that recognizes the code, the originating telephone number associated with the communications device, the device identifier associated with the communications device, and combinations thereof. The server retrieves a digital record and processes content and outputs based on user input, a user and / or program profile, and combinations thereof.
Owner:INSIGNIO TECH
Remotely located database for managing a vehicle fleet
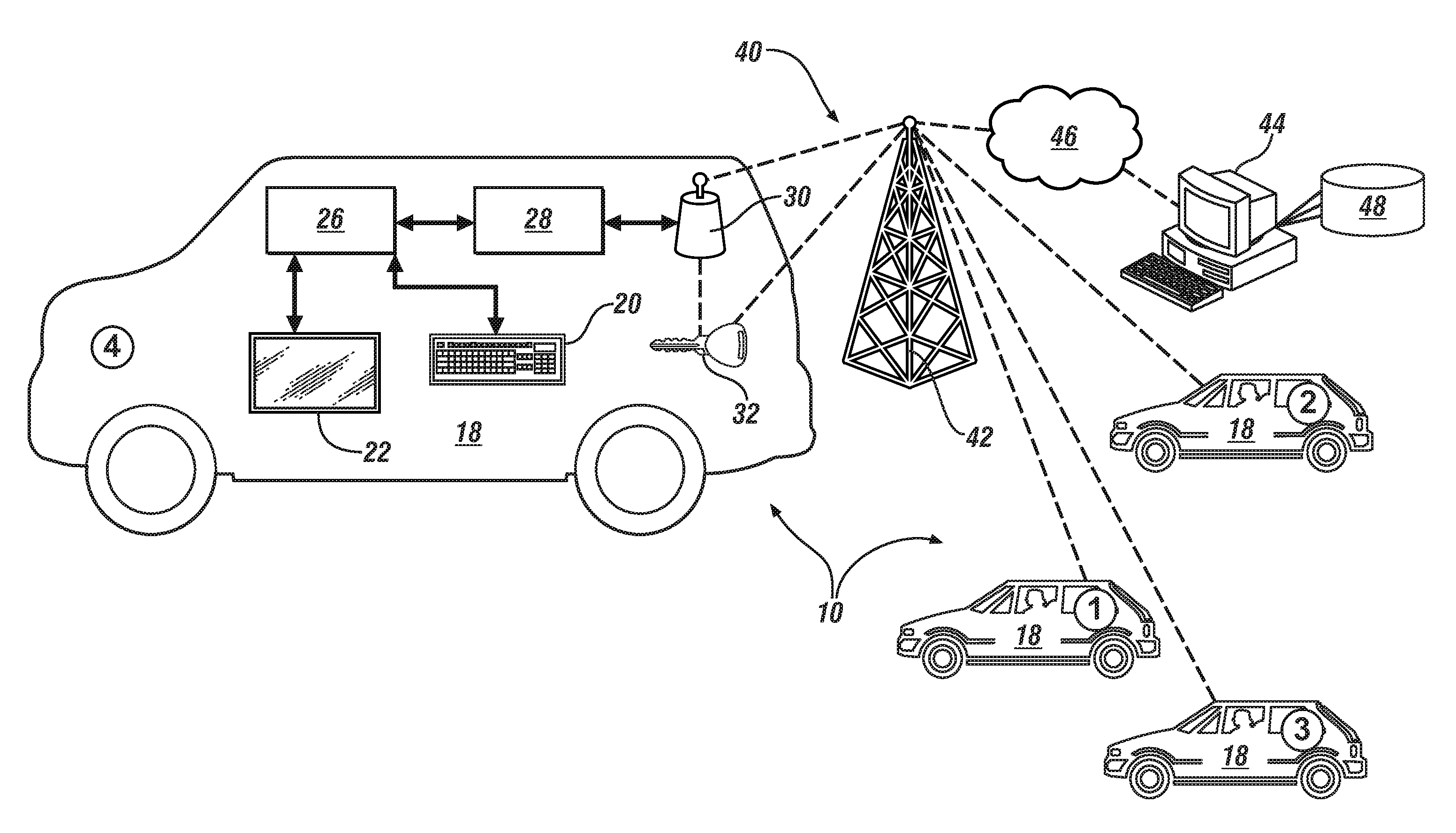
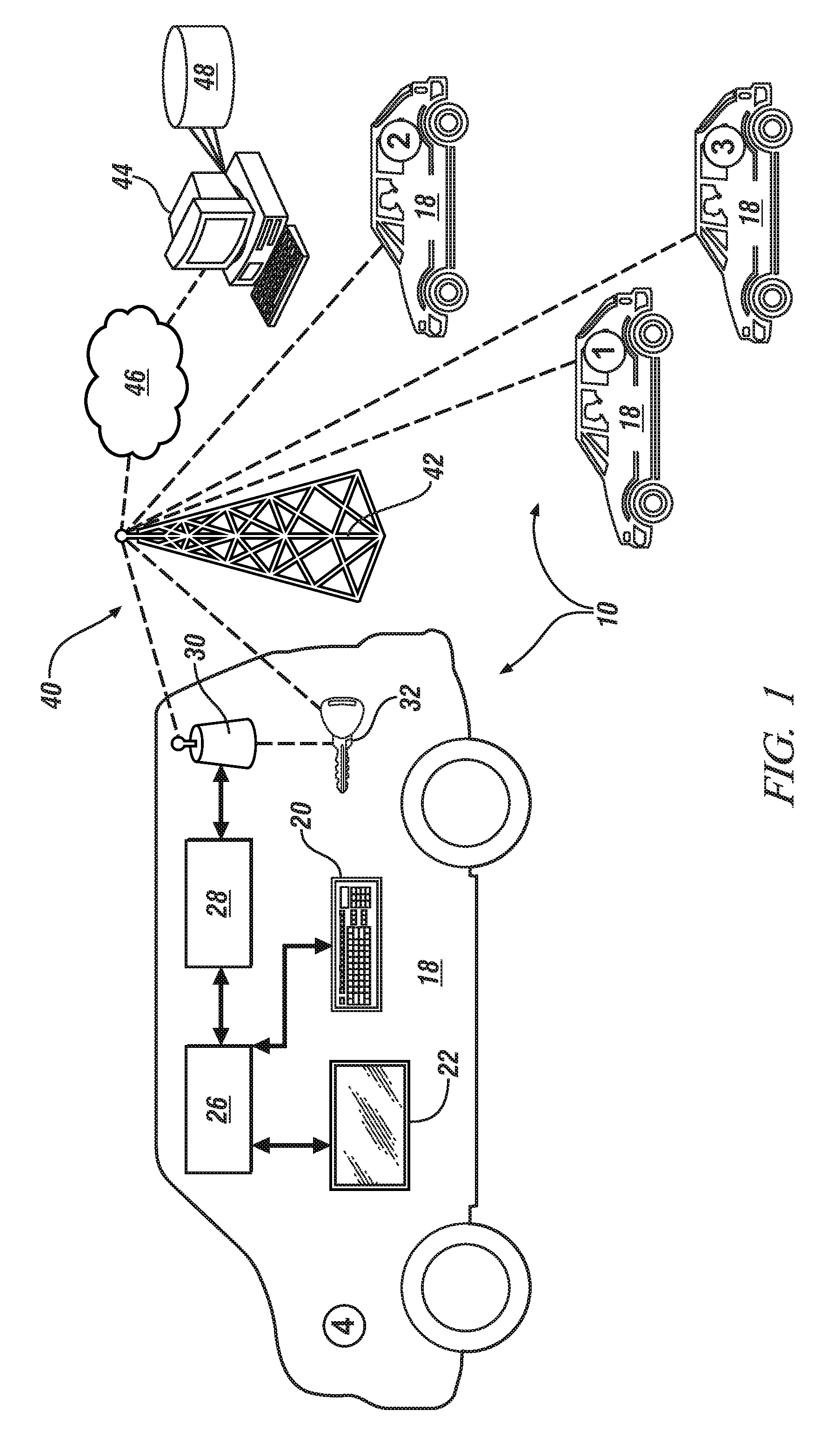
ActiveUS9165412B2Registering/indicating working of vehiclesDigital data processing detailsData signalProgram profile
Owner:GM GLOBAL TECH OPERATIONS LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com