System and method for automatic program analysis based on strategy
An automated program and analysis system technology, applied in the field of system security, can solve problems such as waste of computing resources, false negative reports of malicious behavior, inability to schedule real-time dynamic analysis modules, etc., and achieve the effect of improving analysis efficiency and accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] A method and system for automatically detecting Android malware based on policy scheduling tasks will be described in detail below with reference to the accompanying drawings, but the present invention is not limited to the following embodiments.
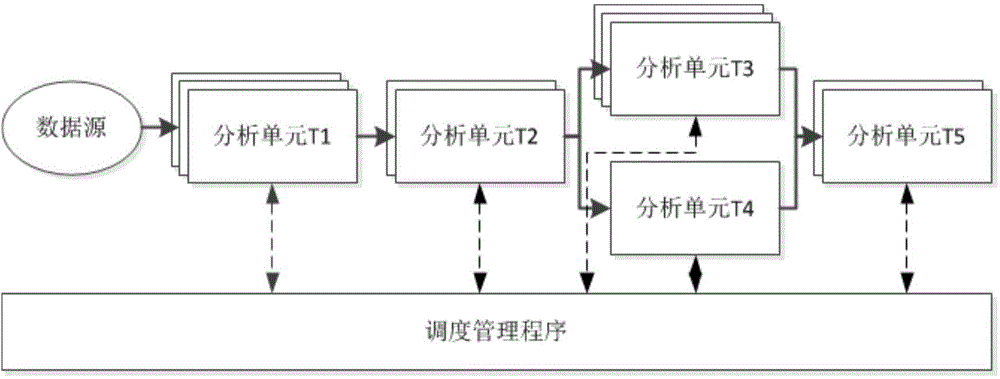
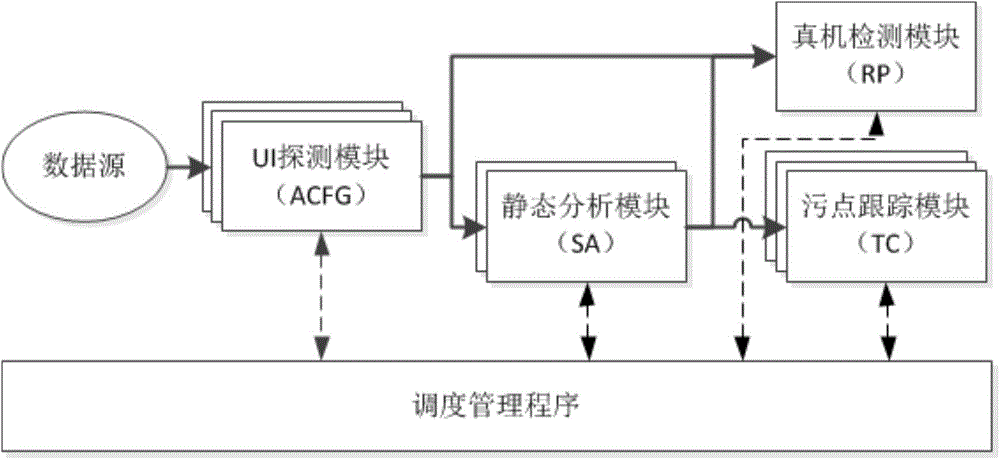
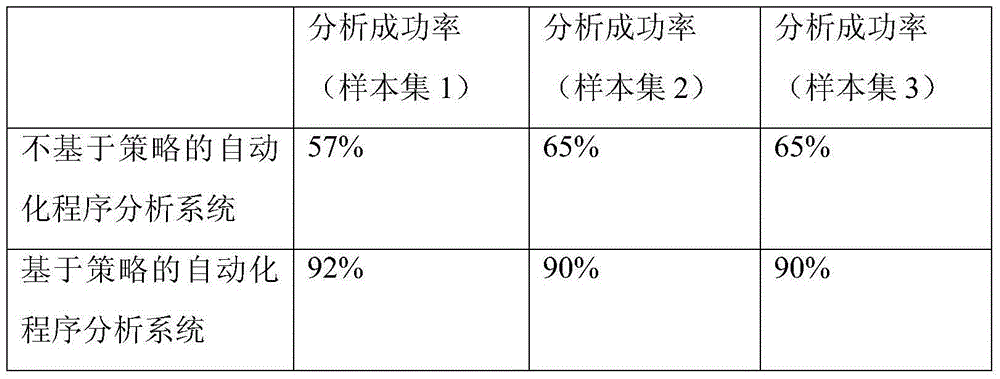
[0025] The overall structure of this embodiment is as follows figure 2 As shown, the system mainly includes three parts structurally: data source, four Android application analysis units, and scheduling management program, which includes scheduling program and configuration program. The data source is the Android software crawling module, and the Android software is output as the input task of the Android application analysis unit; the Android application analysis unit includes the following four types: dynamic UI detection module, static analysis module, dynamic stain tracking module, real machine detection module, During operation, 0 to several modules of each type can be parallelized.
[0026] In this embodiment, the XML...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com