Patents
Literature
33 results about "Static program analysis" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Static program analysis is the analysis of computer software that is performed without actually executing programs, in contrast with dynamic analysis, which is analysis performed on programs while they are executing. In most cases the analysis is performed on some version of the source code, and in the other cases, some form of the object code.
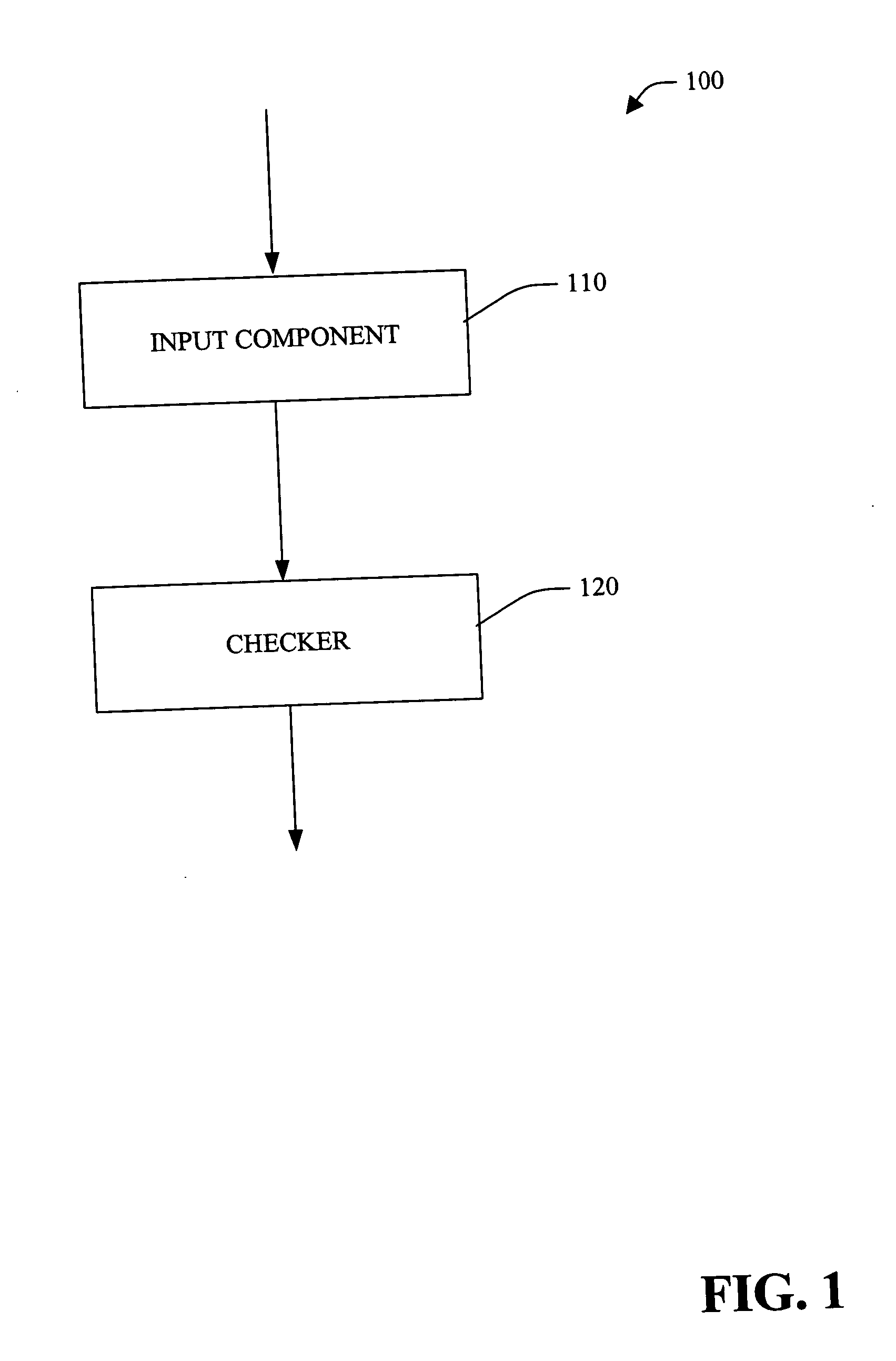
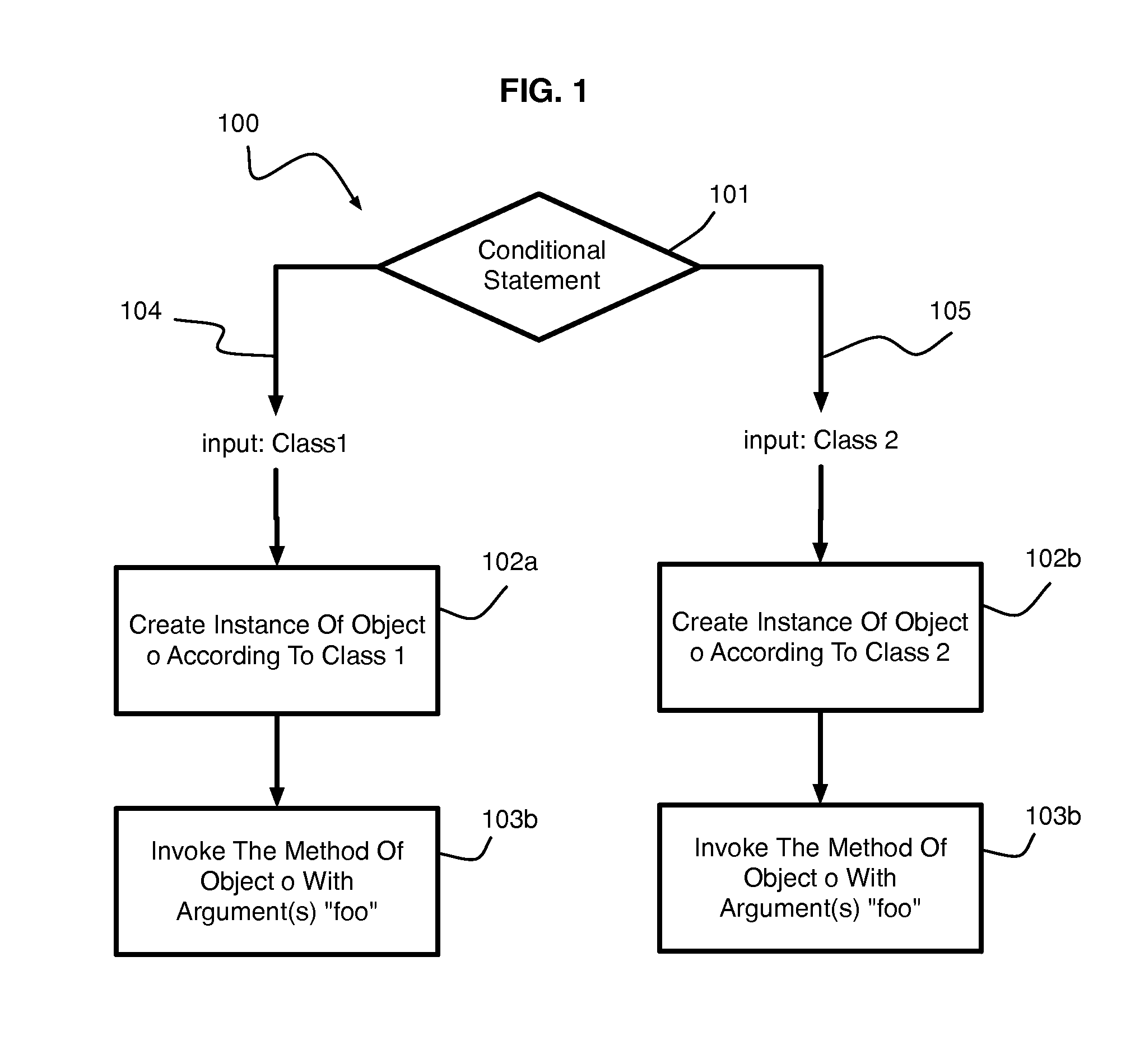
Systems and methods for performing static analysis on source code
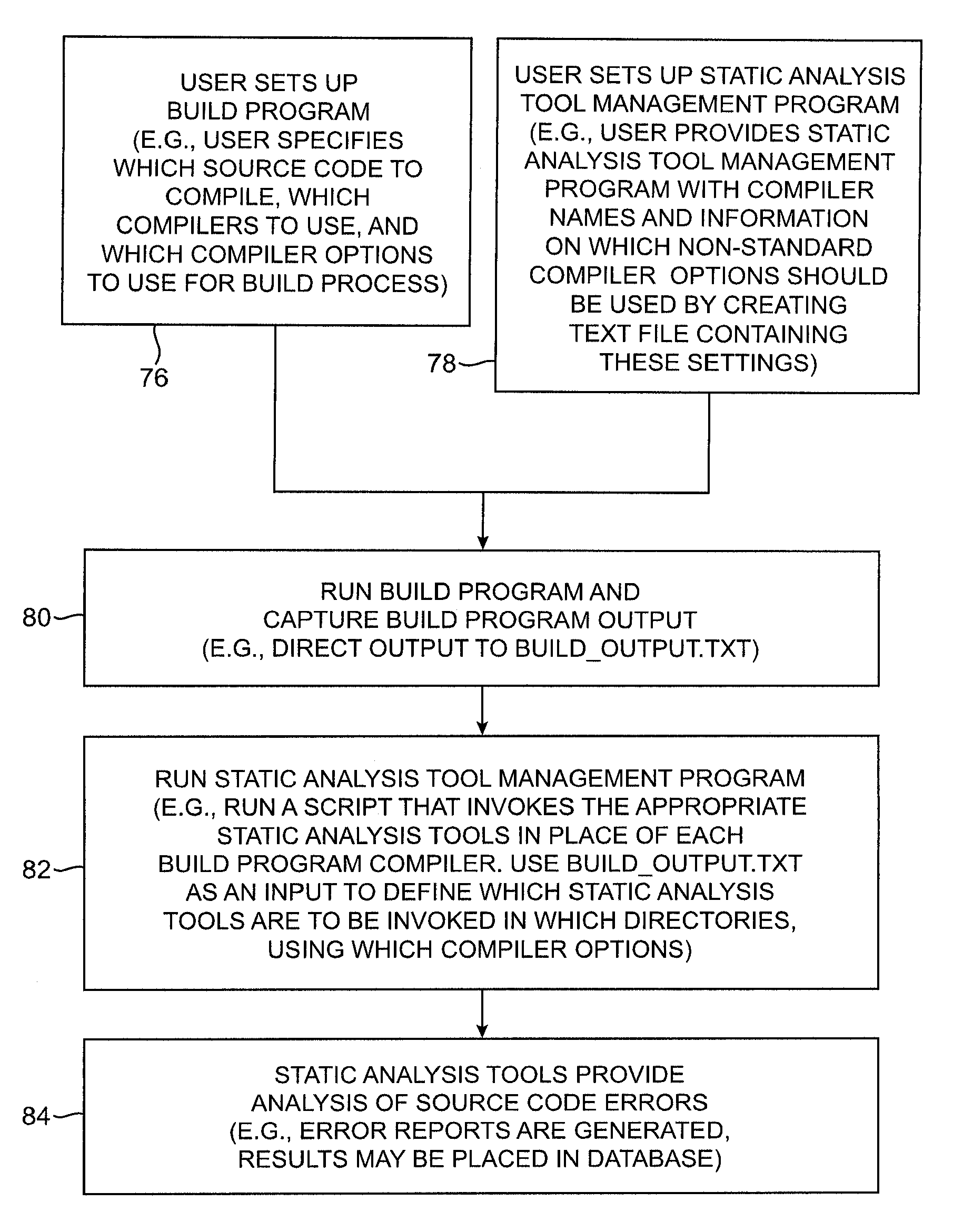
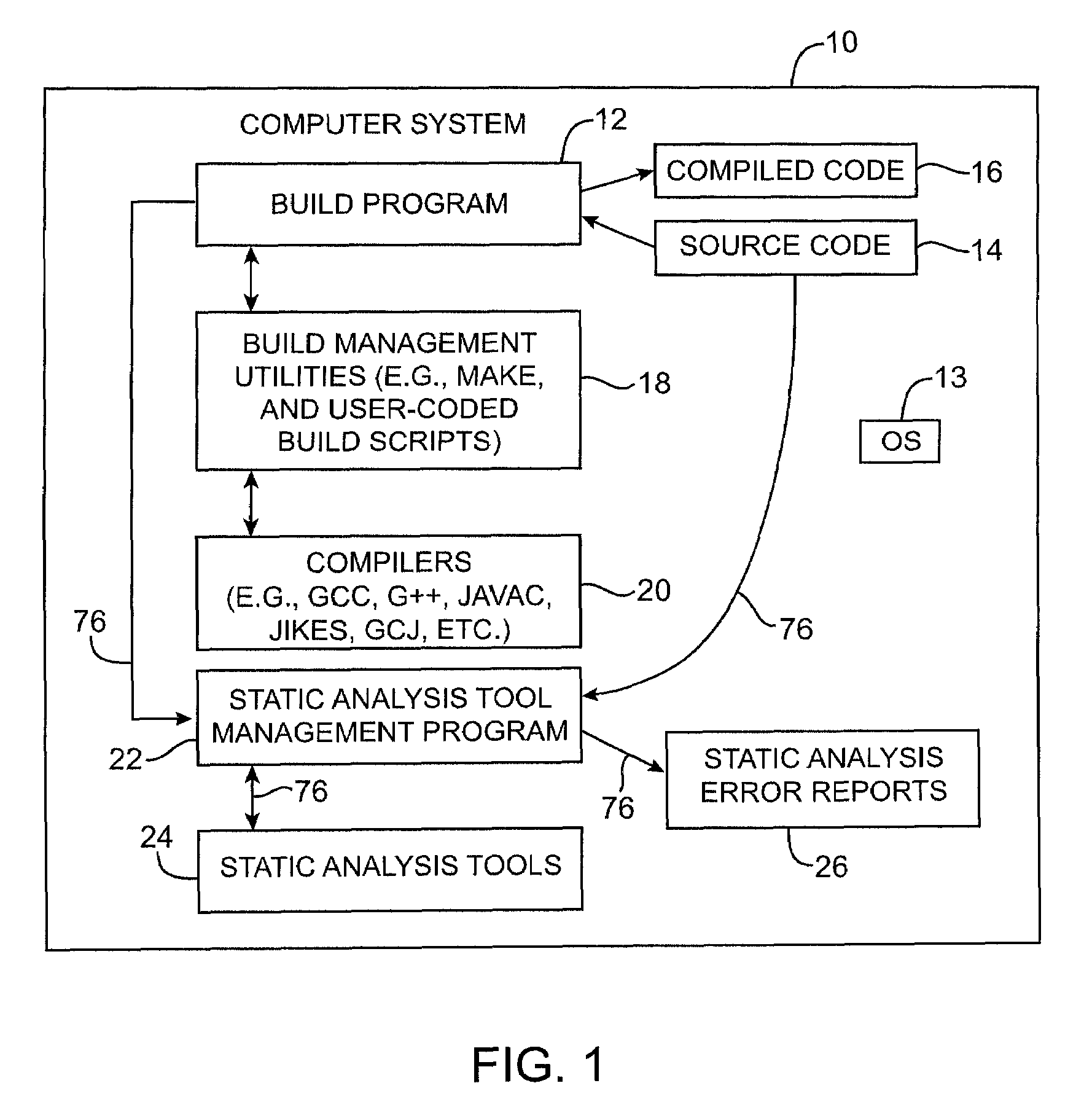
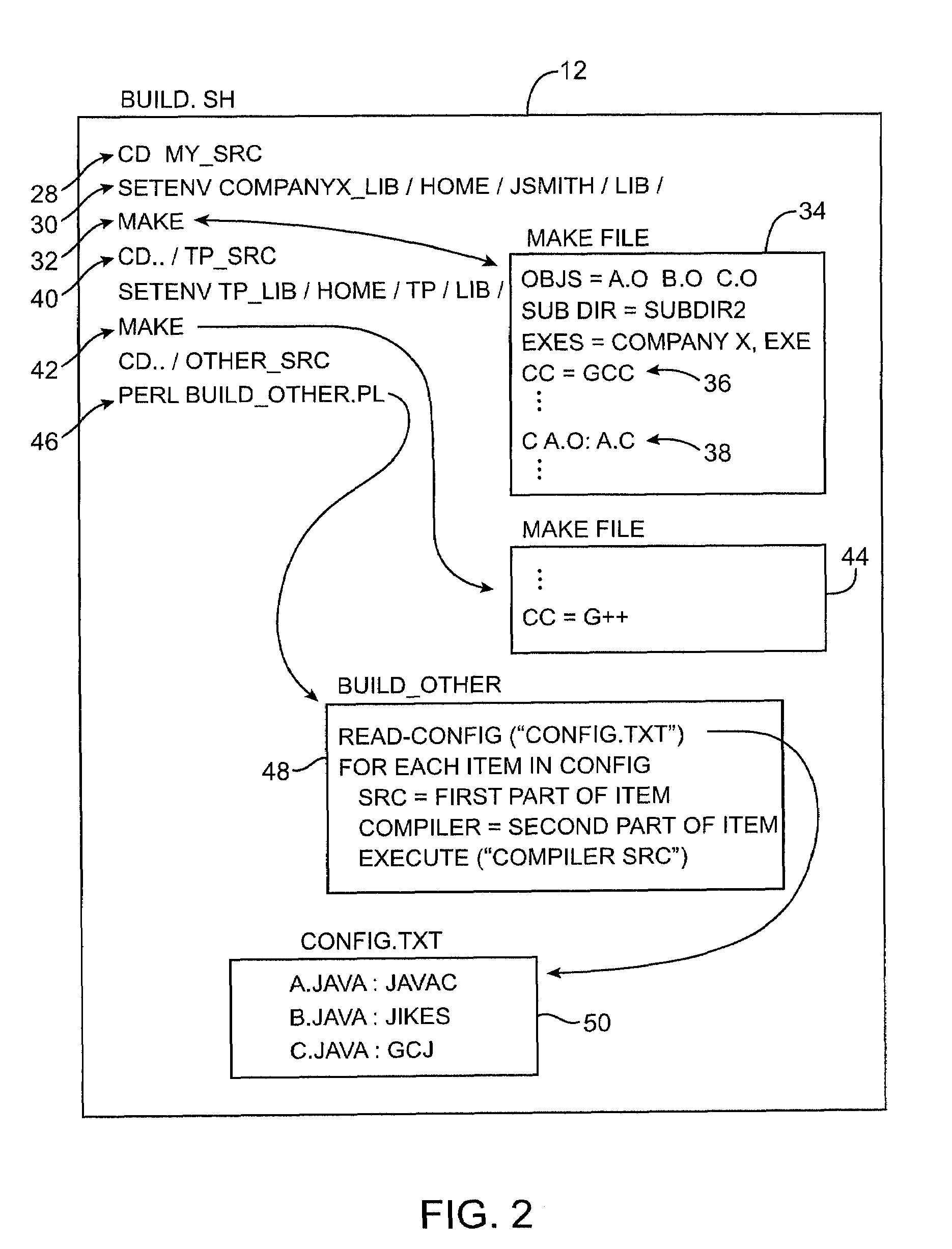
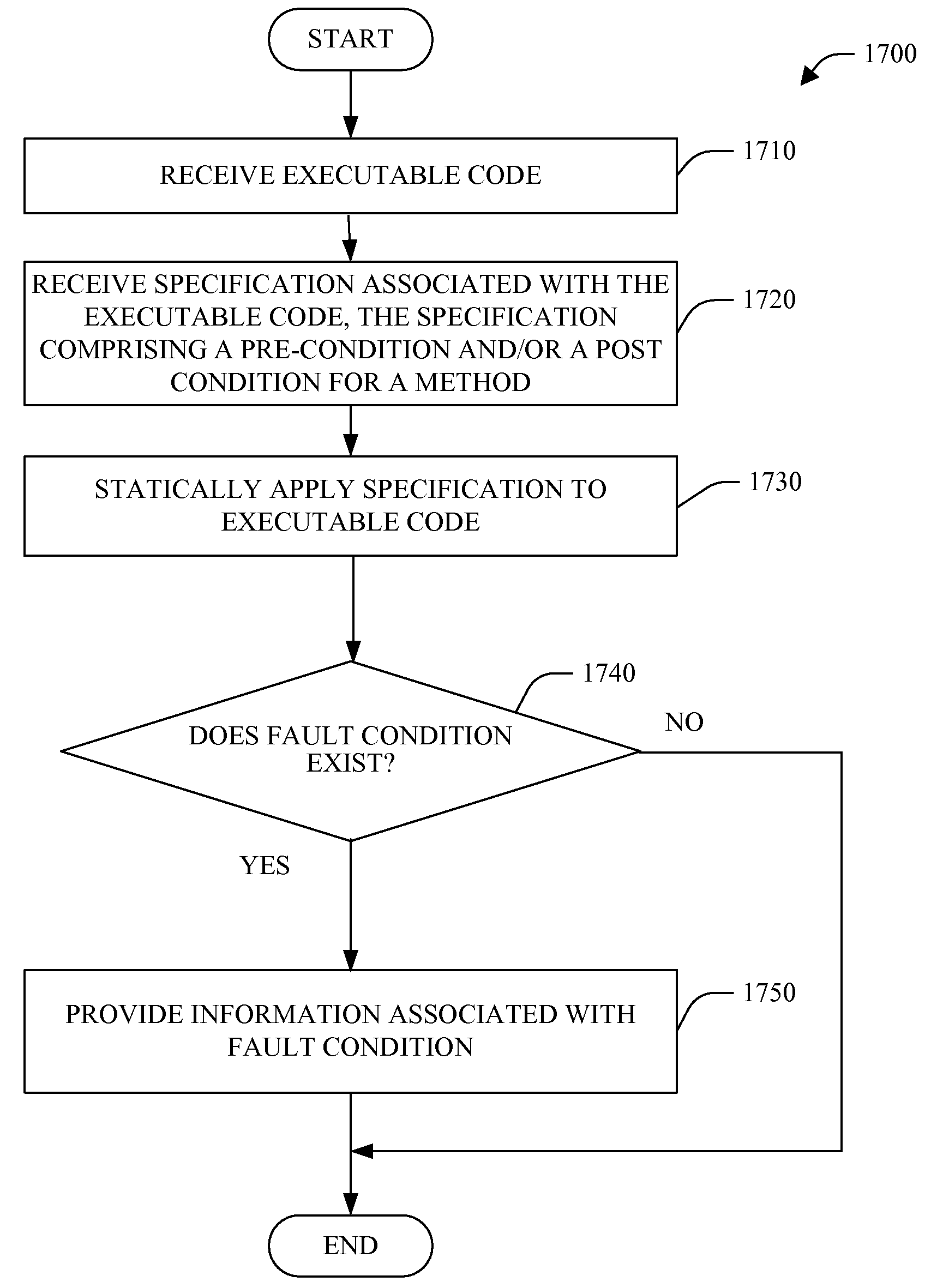
Systems and methods are provided for performing static error analysis on source code. A computer system having an operating system may contain a number of source code files. During a normal build process, a build program may be used to set various compilation options and to invoke appropriate compilers that compile the source code files into executable code. Static analysis debugging tools may be used to perform static analysis on the source code files. The appropriate static analysis tools may be invoked using a static analysis tool management program. Directory, path and name modification may be used to invoke the analysis tools. A monitoring program may be used to determine how to invoke the tools. The operating system may be modified so that the static analysis tools are invoked in place of the compilers when the build program is run.
Owner:SYNOPSYS INC
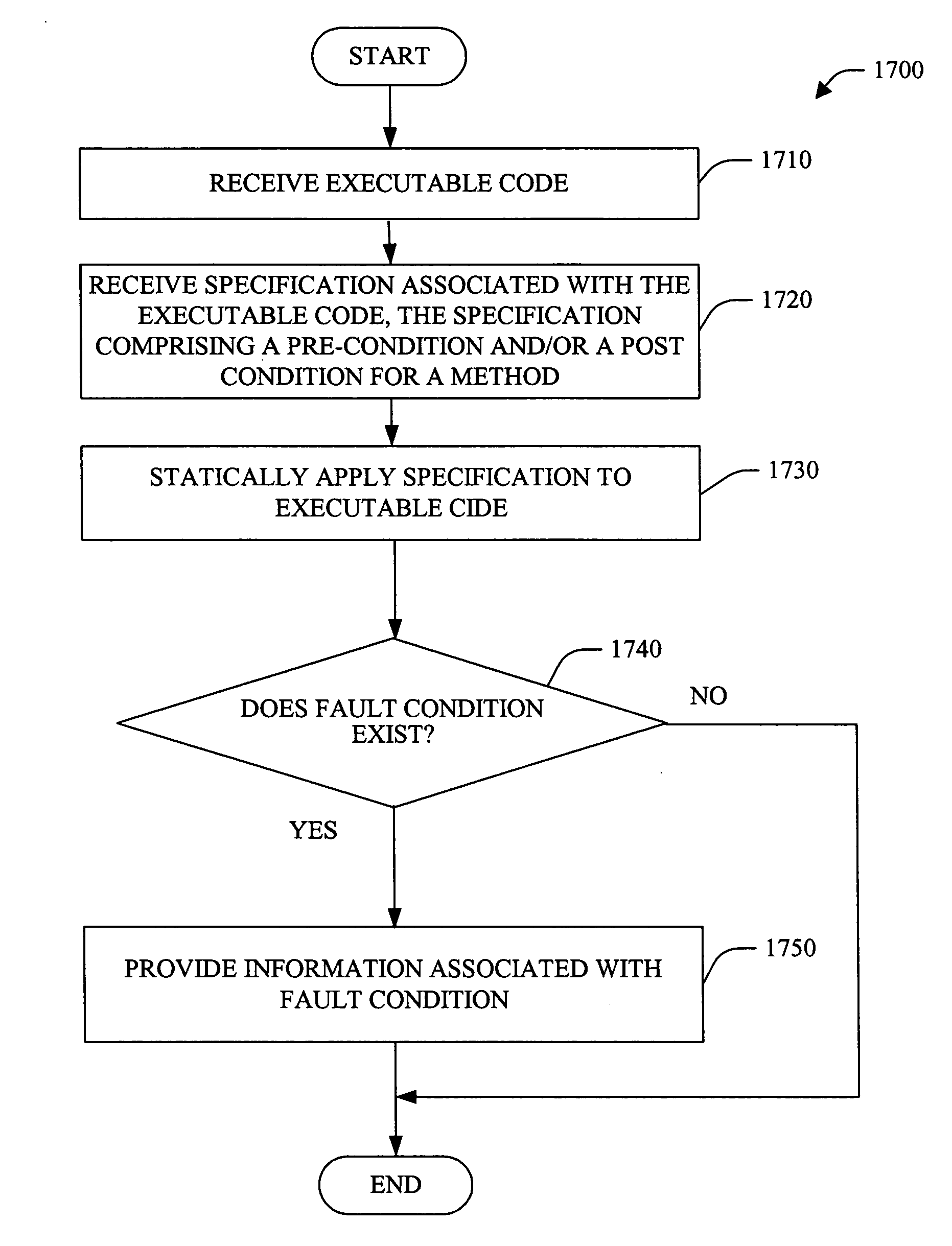
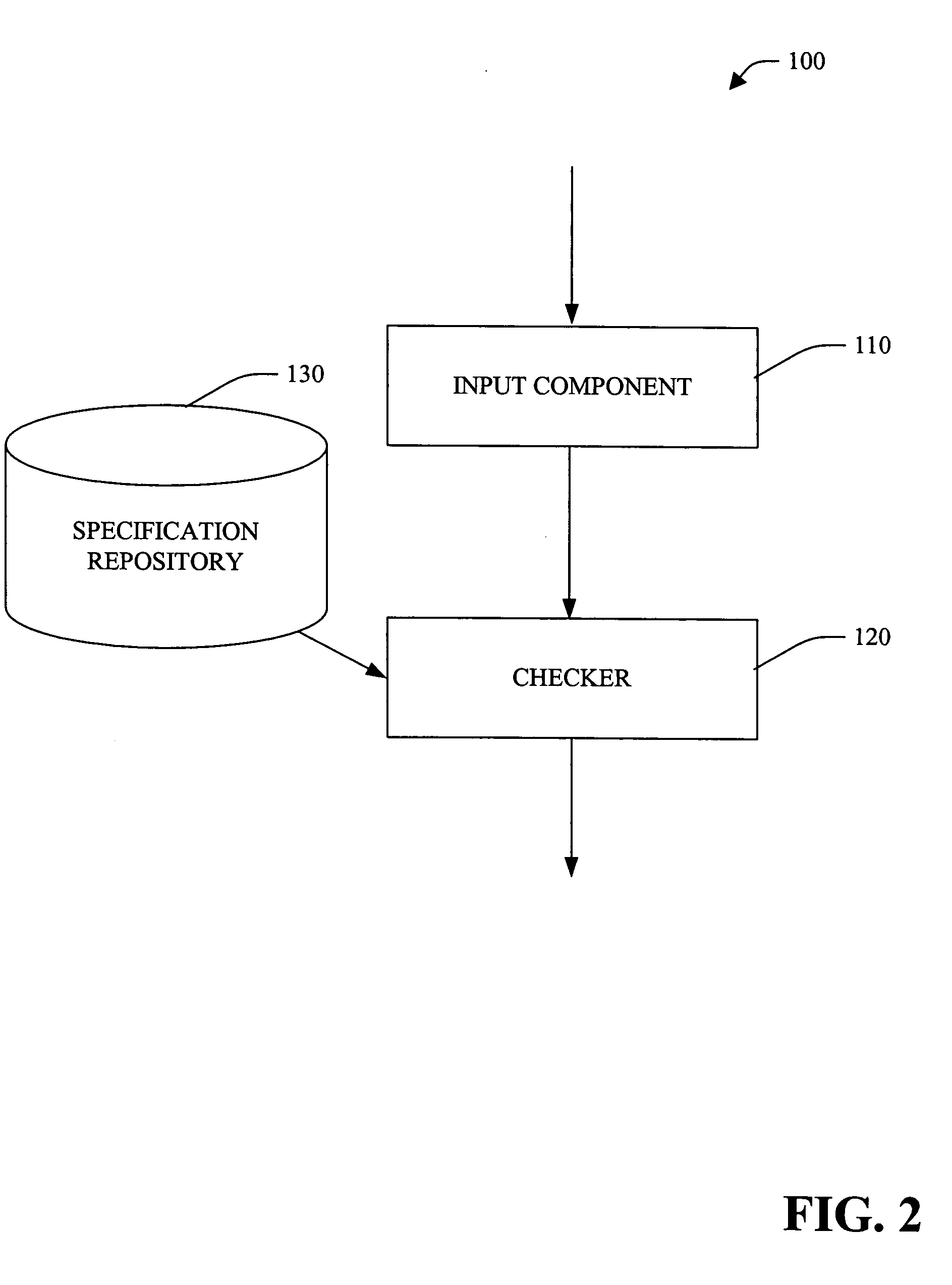
Plug-in pre-and postconditions for static program analysis
InactiveUS20050081192A1Error detection/correctionSpecific program execution arrangementsPostconditionObject code
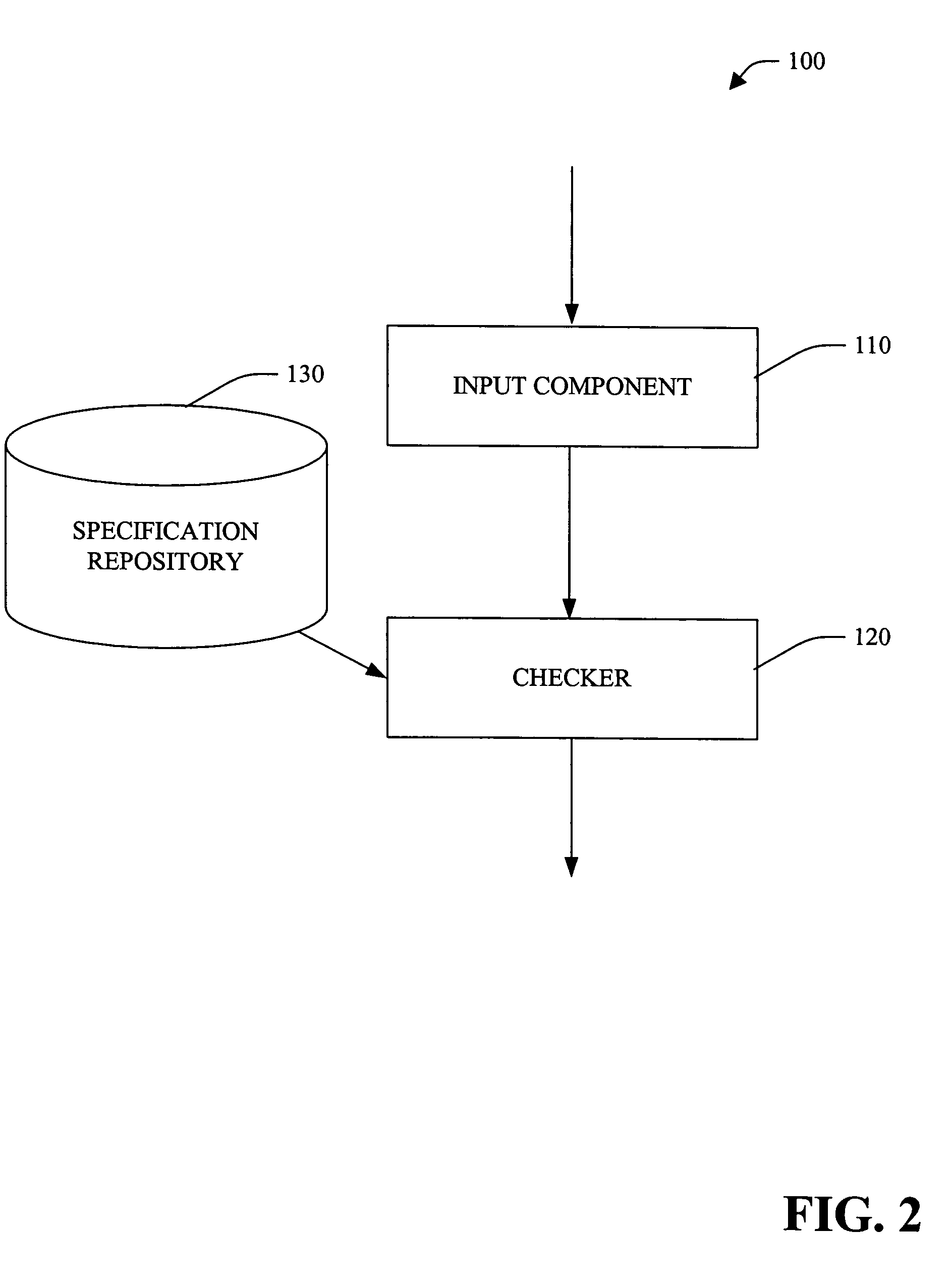
A system and method employing pre- and / or post-condition(s) specified at a source code level and persisted (e.g., in associated object code and / or a specification repository) facilitating static checking of the object code is provided. The system and method are based, at least in part, upon a framework that employs rules for using an interface to be recorded as declarative specifications in an existing language. A specifier can give a method a plug-in pre- and postcondition, which is arbitrary code that examines an object's current state and a static approximation of the method's actuals, decides whether the call is legal and returns the object's state after the call.
Owner:MICROSOFT TECH LICENSING LLC
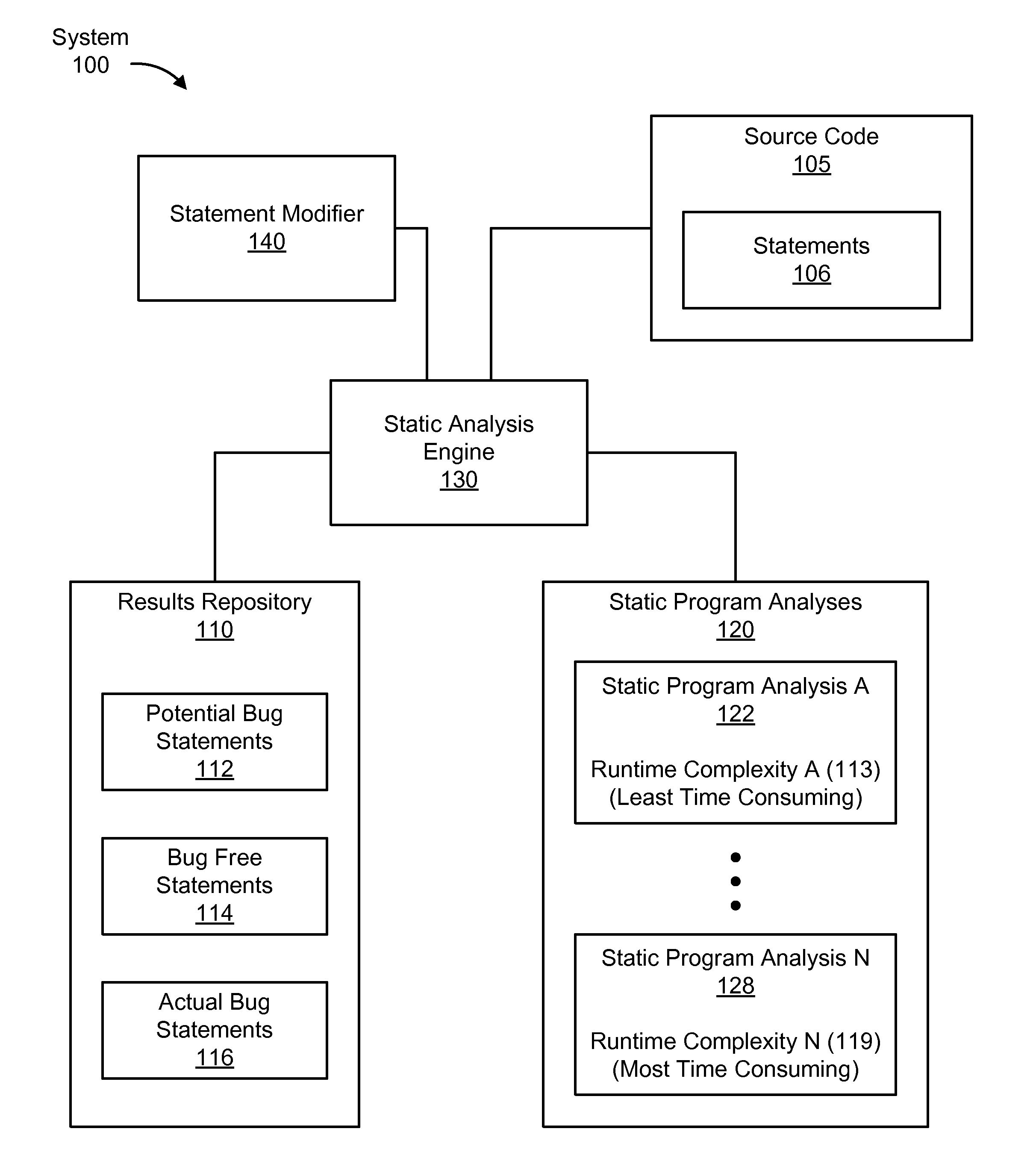
Layered static program analysis framework for software testing
ActiveUS20090259989A1Reducing pluralitySoftware testing/debuggingSpecific program execution arrangementsTheoretical computer scienceProgram analysis
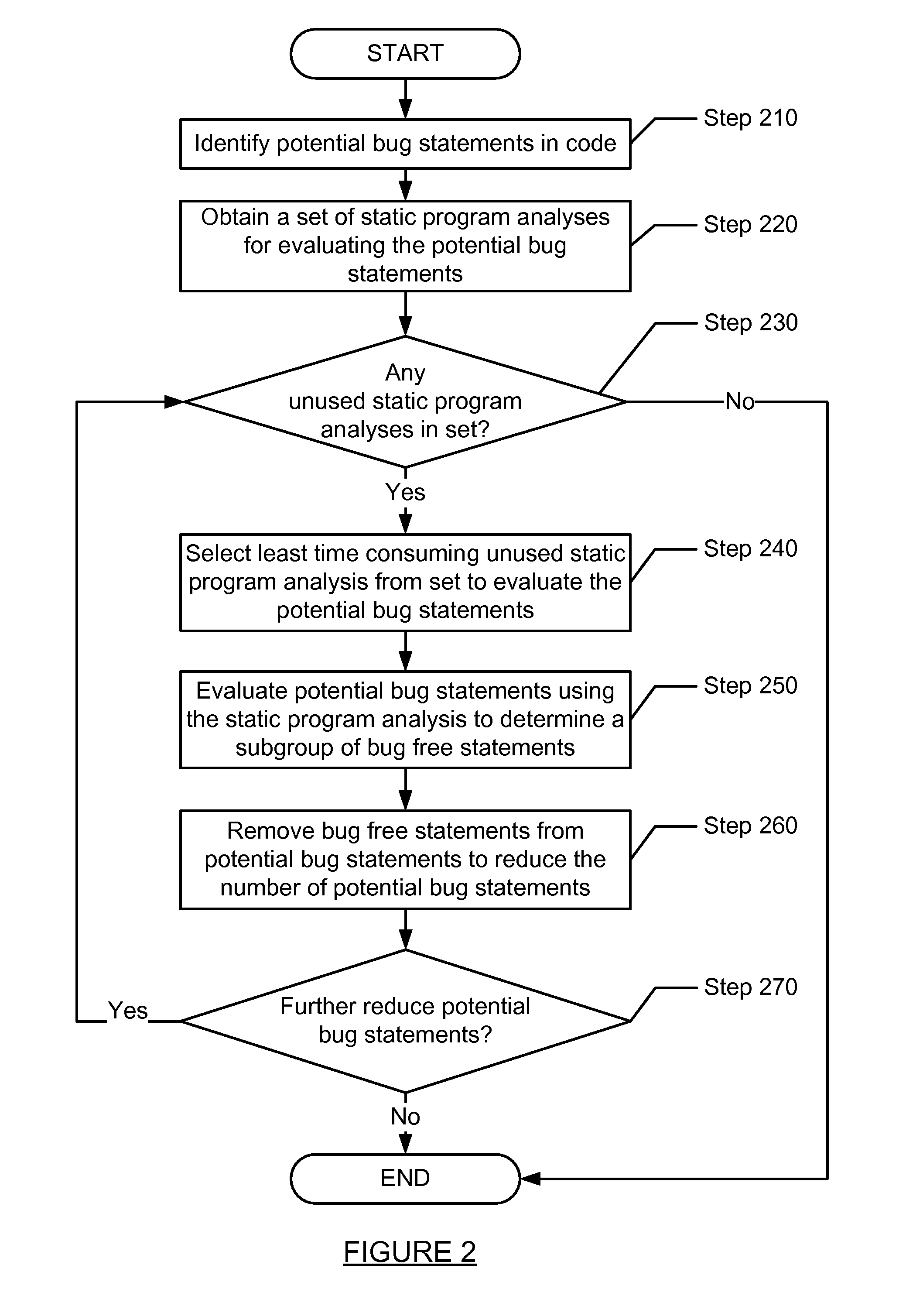
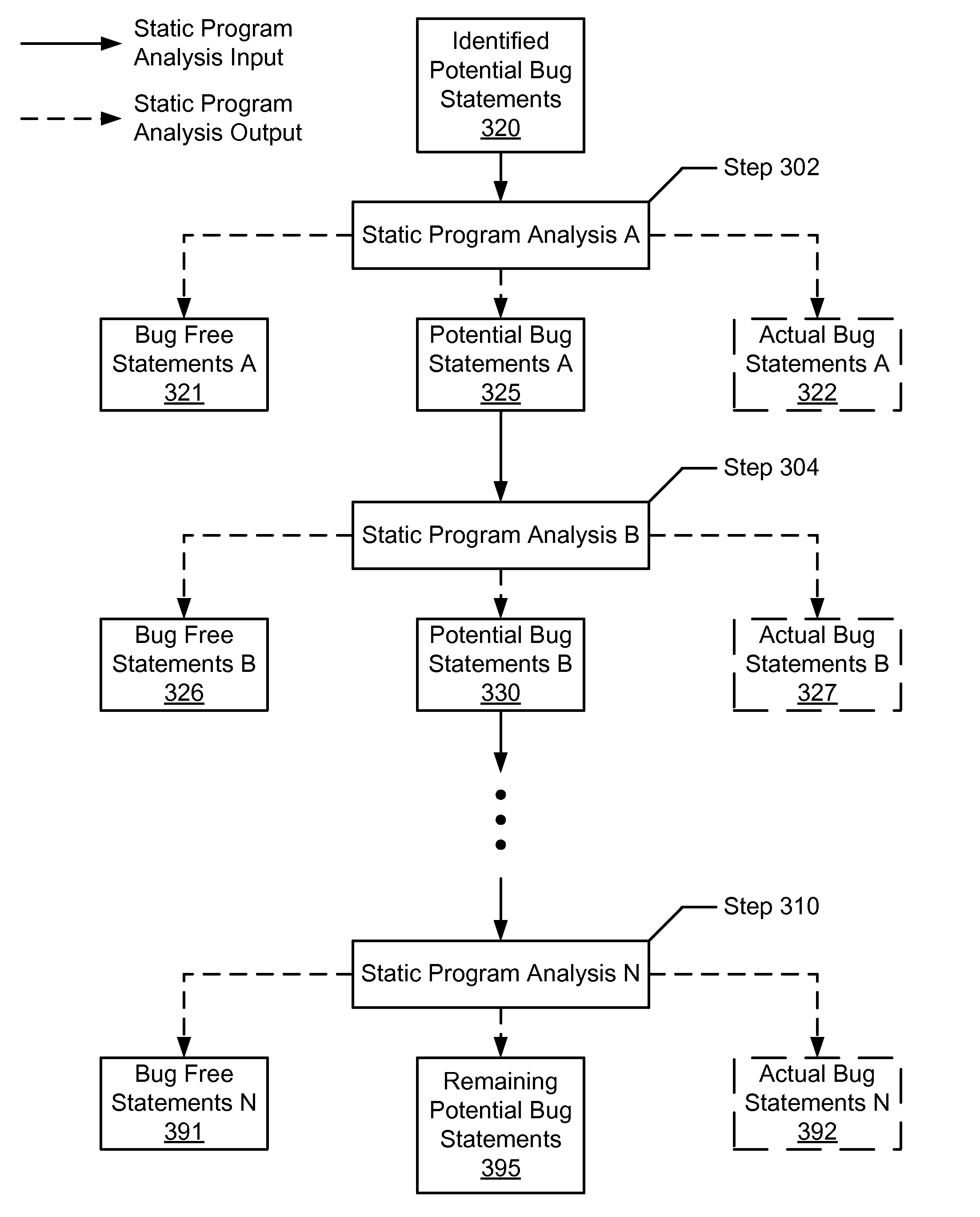
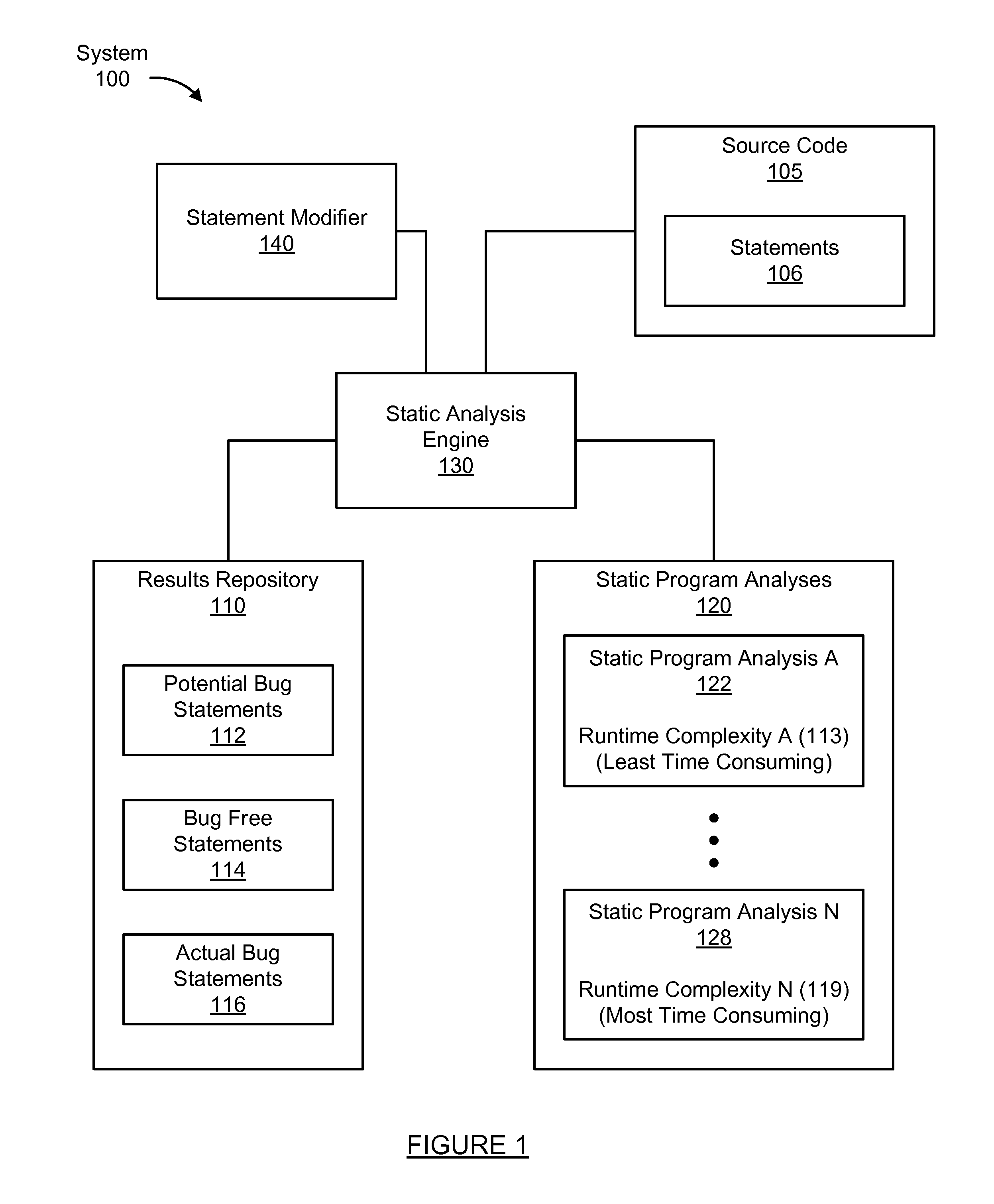
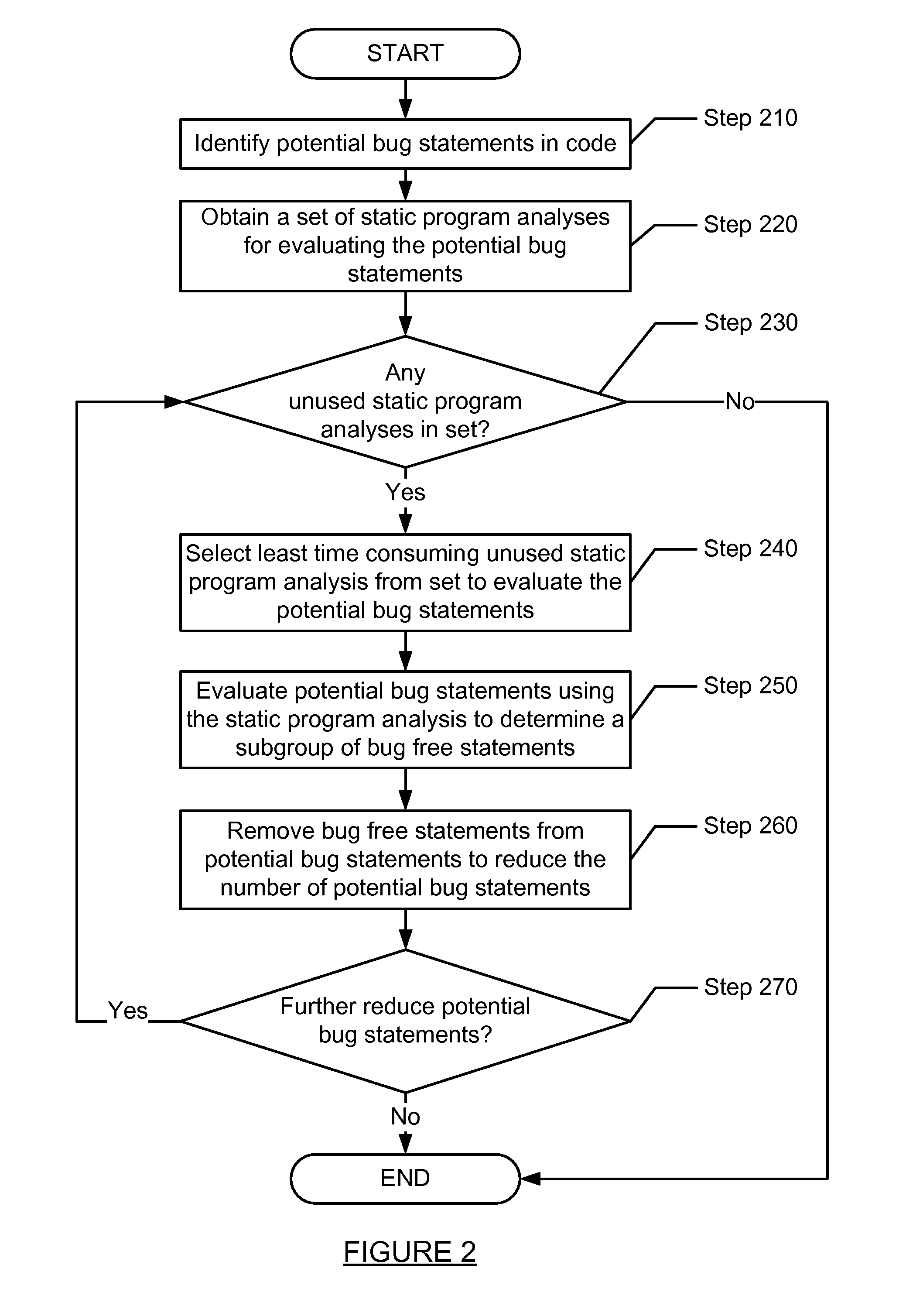
A method for analyzing a set of potential bug statements in source code. The method including obtaining a set of static program analyses; recursively reducing the set of potential bug statements in the source code by: selecting a static program analysis for each recursion from the set of static program analyses in order from least time consuming to most time consuming; evaluating the set of potential bug statements using the static program analysis of the set of static program analyses to determine a subgroup of bug free statements of the set of potential bug statements in each recursion; and removing the subgroup of the bug free statements from the set of potential bug statements to reduce the set of potential bug statements in each recursion; thereby filtering at least one subgroup of bug free statements out of the set of potential bug statements in the source code.
Owner:ORACLE INT CORP
Plug-in pre- and postconditions for static program analysis
InactiveUS7526755B2Easy to checkError detection/correctionSpecific program execution arrangementsPostconditionObject code
A system and method employing pre- and / or post-condition(s) specified at a source code level and persisted (e.g., in associated object code and / or a specification repository) facilitating static checking of the object code is provided. The system and method are based, at least in part, upon a framework that employs rules for using an interface to be recorded as declarative specifications in an existing language.A specifier can give a method a plug-in pre- and postcondition, which is arbitrary code that examines an object's current state and a static approximation of the method's actuals, decides whether the call is legal and returns the object's state after the call.
Owner:MICROSOFT TECH LICENSING LLC
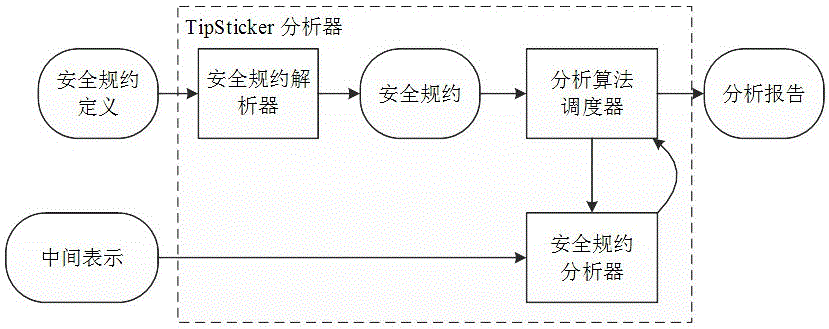
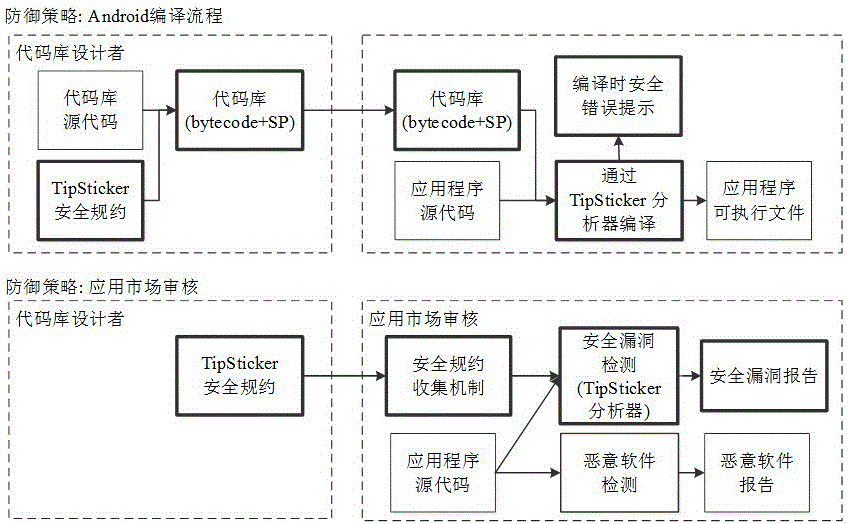
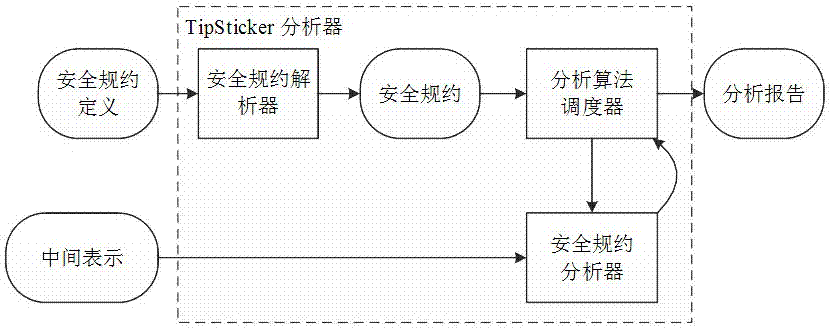
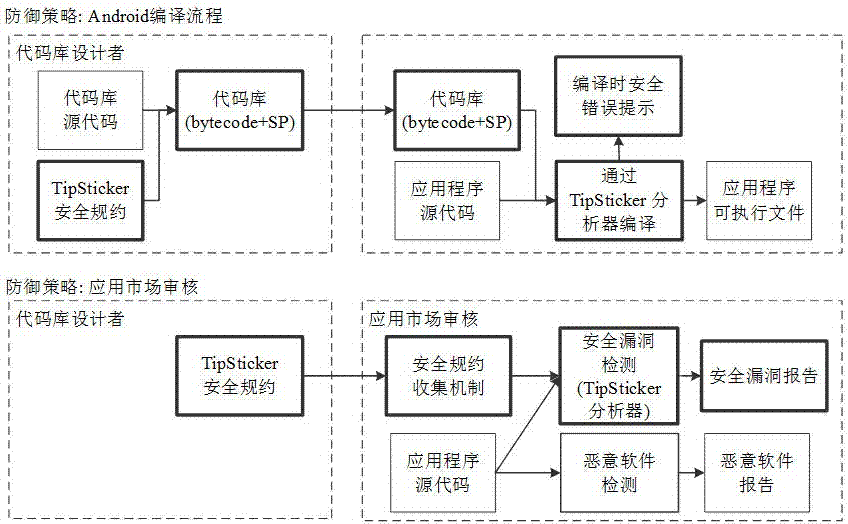
Android application used application program vulnerability detection and analysis method based on code library security specifications
ActiveCN105022958APrevent the risk of security incidentsPlatform integrity maintainanceInformation securityOperating system
The invention belongs to the technical field of program information security monitoring, and particularly relates to an Android application used application program vulnerability detection and analysis method based on code library security specifications. The method comprises the following steps: building a security specification model, i.e., describing the security specifications of the code library by using formalized rule languages; designing a static program analyzer for performing automatic verification based on the security specification model; applying the static program analyzer to two phases, i.e., compilation of application programs and examination of the application programs in an application market, and detecting security vulnerabilities. According to the detection and analysis method provided by the invention, the security risk in the program can be prevented.
Owner:FUDAN UNIV
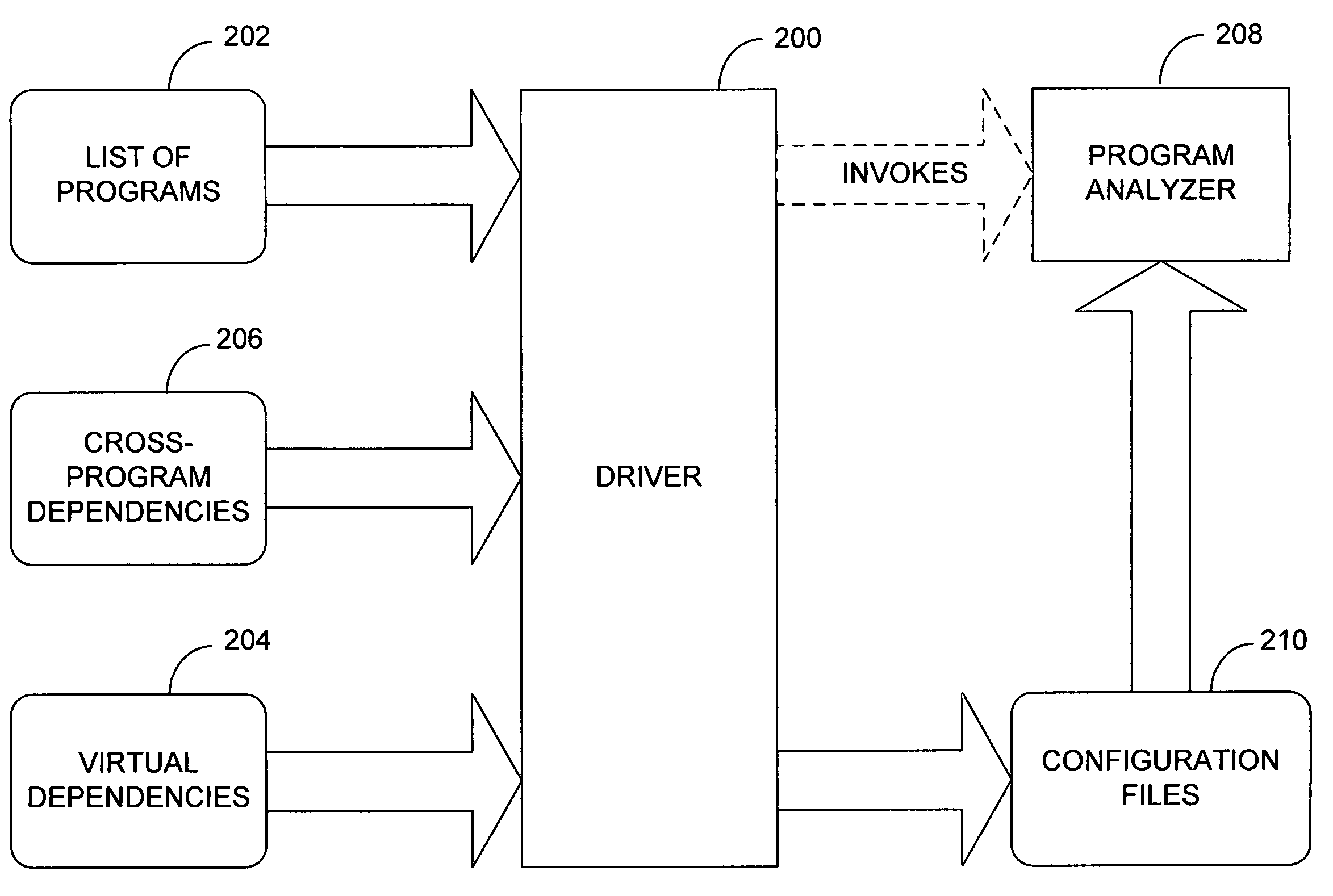
System and method for whole-system program analysis
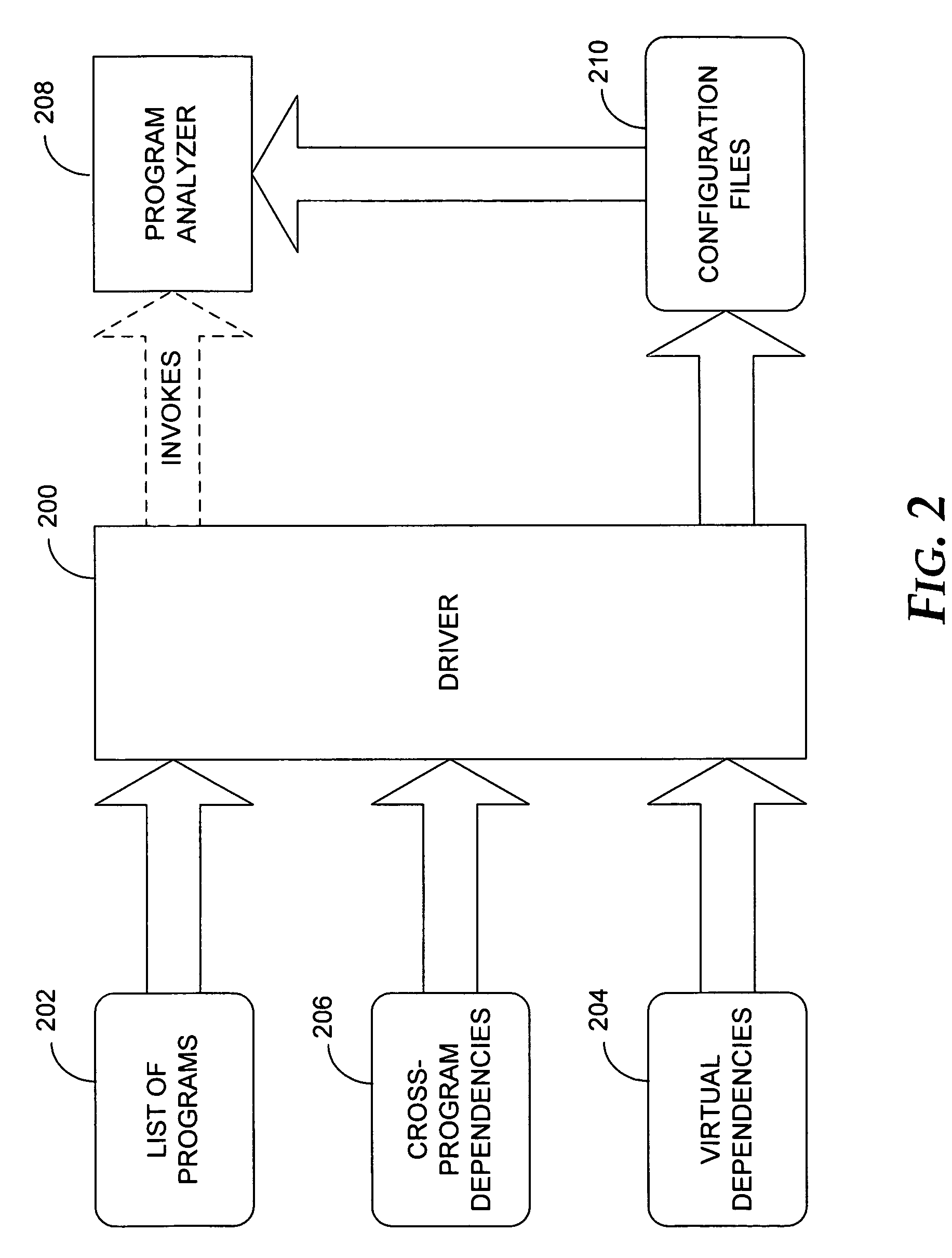
InactiveUS7406685B2Accurate representationEasy to detectGeneral purpose stored program computerSoftware testing/debuggingSoftware systemTheoretical computer science
Defect detection in a software system made of multiple computer program programs is facilitated by using information about cross-program interactions and dependency relationships between programs to analyze the individual programs in such a way that the behavior of the system as a whole is accurately represented. A list of dependency relationships is read in; these dependency relationships are used to determine an order in which the programs should be analyzed. The programs are then analyzed in that order. Information from the analysis of the programs is used to inform the analysis of subsequently-analyzed programs.
Owner:MICROSOFT TECH LICENSING LLC
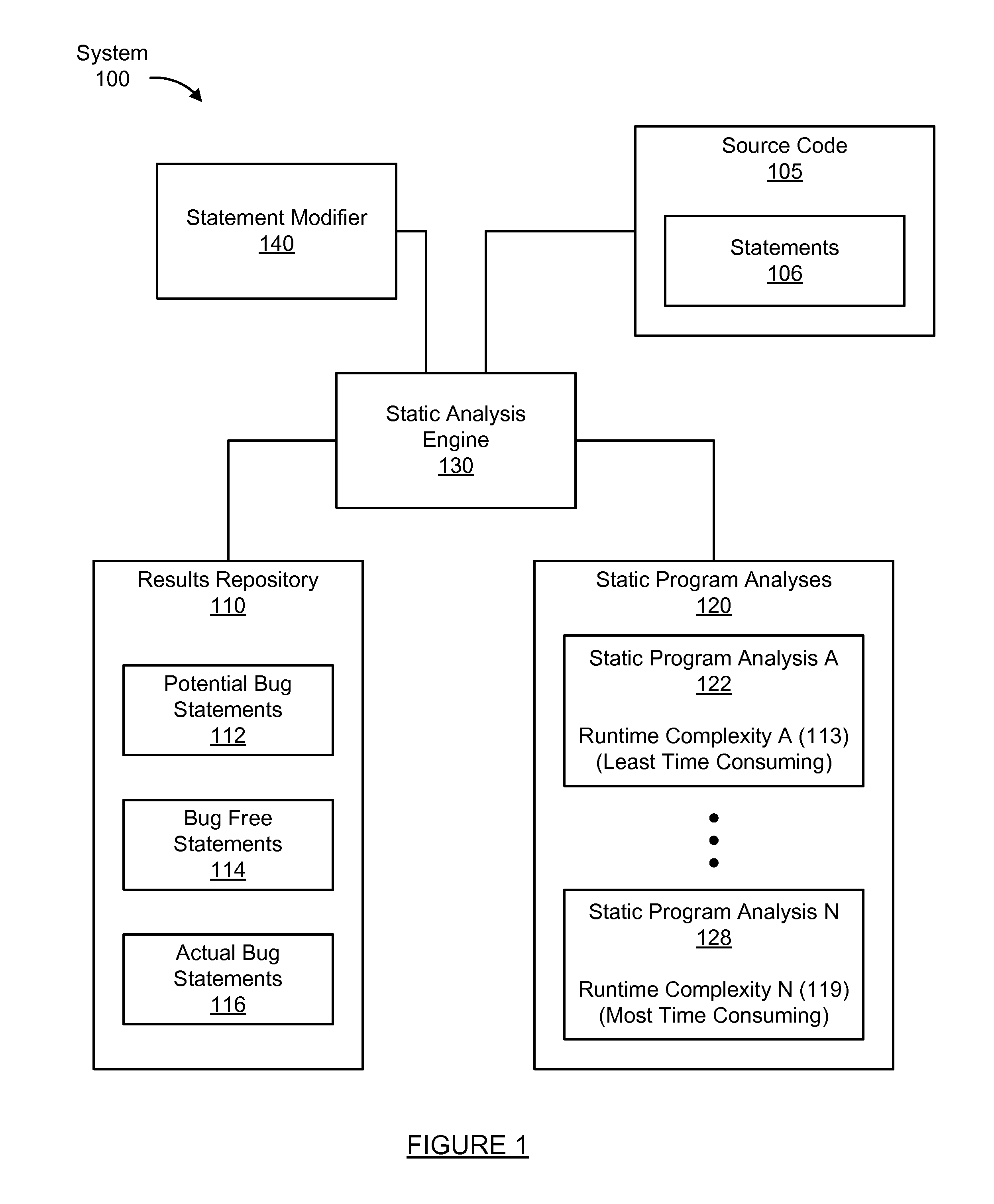
Layered static program analysis framework for software testing
ActiveUS8527965B2Reducing pluralityError detection/correctionSpecific program execution arrangementsTheoretical computer scienceProgram analysis
A method for analyzing a set of potential bug statements in source code. The method including obtaining a set of static program analyses; recursively reducing the set of potential bug statements in the source code by: selecting a static program analysis for each recursion from the set of static program analyses in order from least time consuming to most time consuming; evaluating the set of potential bug statements using the static program analysis of the set of static program analyses to determine a subgroup of bug free statements of the set of potential bug statements in each recursion; and removing the subgroup of the bug free statements from the set of potential bug statements to reduce the set of potential bug statements in each recursion; thereby filtering at least one subgroup of bug free statements out of the set of potential bug statements in the source code.
Owner:ORACLE INT CORP
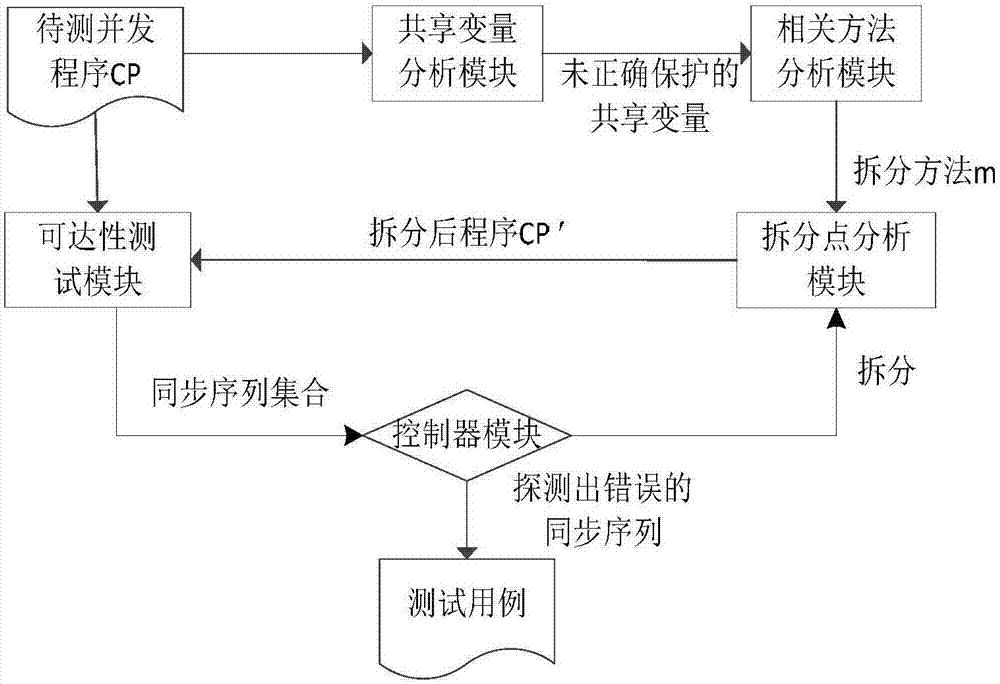
Concurrent-program test method based on lock-object splitting strategy and test system thereof
InactiveCN107391381AEfficient detectionImproved ability to detect such concurrent program errorsSoftware testing/debuggingProgram controlSoftware bugProgram testing
The invention discloses a concurrent-program test method based on the lock-object splitting strategy and a test system thereof. The concurrent-program test method includes the steps that relevant codes are analyzed with the static program analysis technology, and shared variables protected without same lock objects are determined; then abnormal access codes of the shared variables are split, the split codes are protected through the same lock objects, and the fine-grained synchronization method is generated; reachability testing (all feasible synchronization sequences are operated) is carried out, interleaved sequences between fine-grained synchronization events on different monitor objects in a raw to-be-test concurrent program are generated and carried out, and as the shared variables are protected through false lock objects, concurrent program errors such as data hazards, atomic against and deadlocking are shown. By means of the concurrent-program test method based on the lock-object splitting strategy and the test system thereof, the capacity of detecting the concurrent program errors can be effectively improved.
Owner:SOUTHEAST UNIV
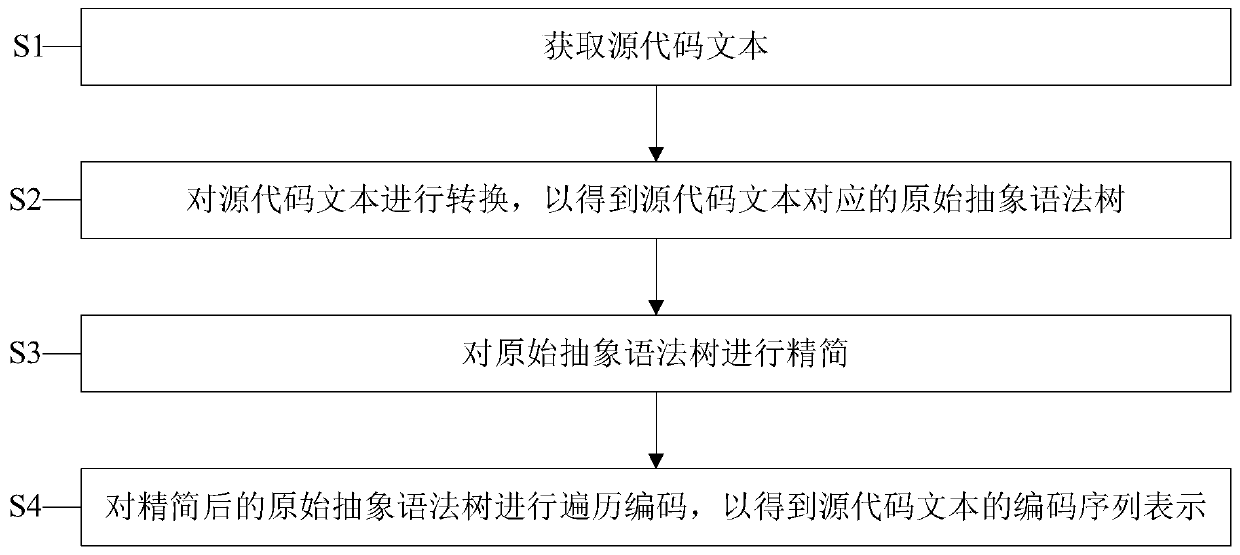
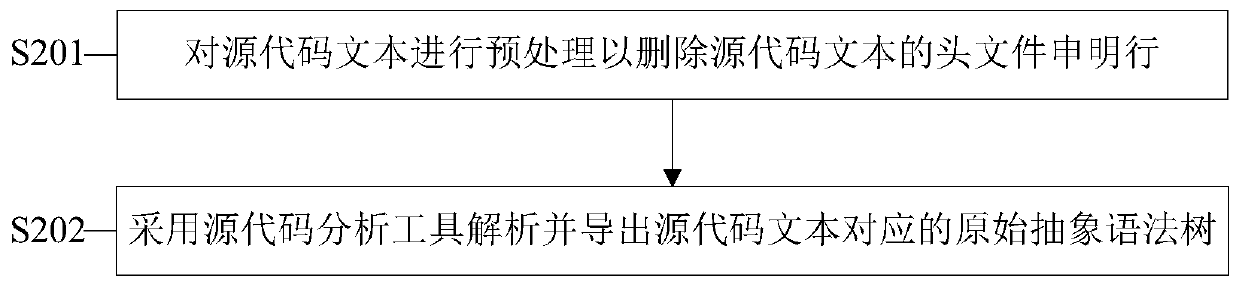
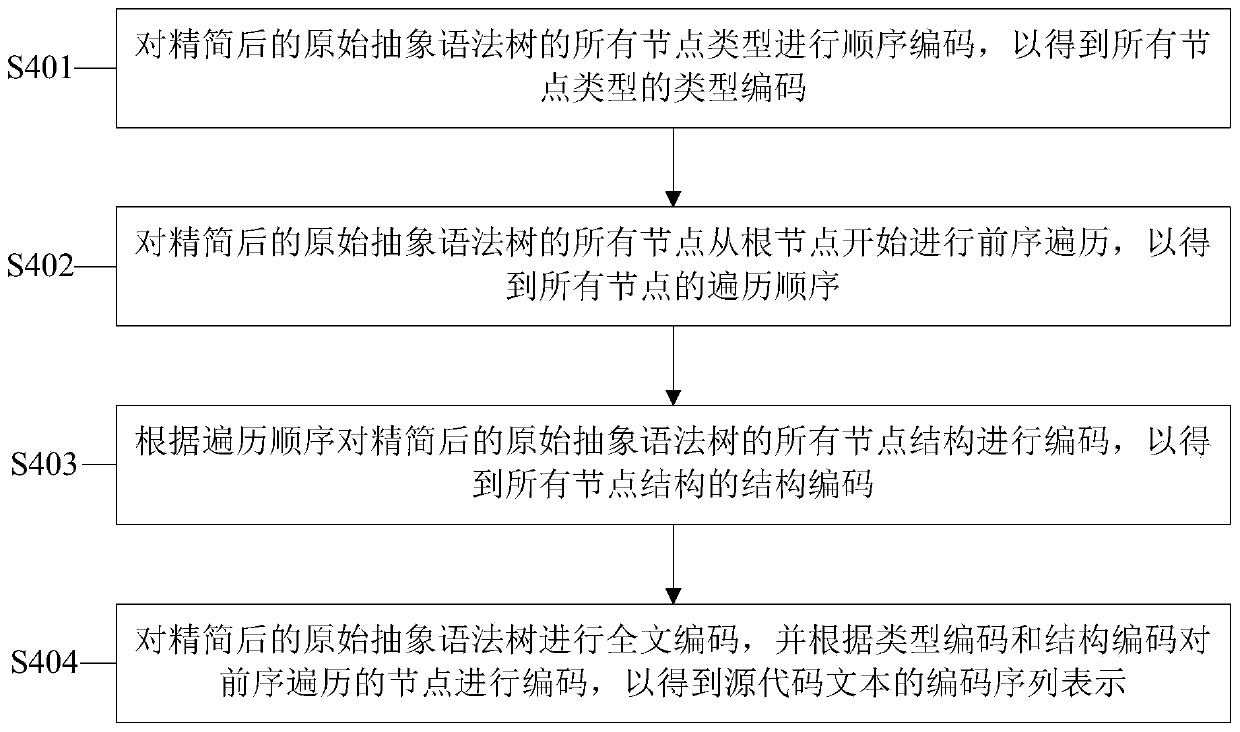
Source code coding sequence representation method based on static program analysis
ActiveCN110737466AImprove retrieval performanceImprove matchReverse engineeringSoftware reuseTheoretical computer scienceAbstract syntax tree
The invention provides a source code coding sequence representation method based on static program analysis. The source code coding sequence representation method comprises the steps of obtaining a source code text; converting the source code text to obtain an original abstract syntax tree corresponding to the source code text; simplifying the original abstract syntax tree; and performing traversal encoding on the simplified original abstract syntax tree to obtain an encoded sequence representation of the source code text. According to the method, the tree structure of the original abstract syntax tree corresponding to the source code text can be simplified, the tree structure of the original abstract syntax tree can be well converted into the coding sequence, and meanwhile it can be guaranteed that the coding sequence has good retrieval performance and matching performance.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
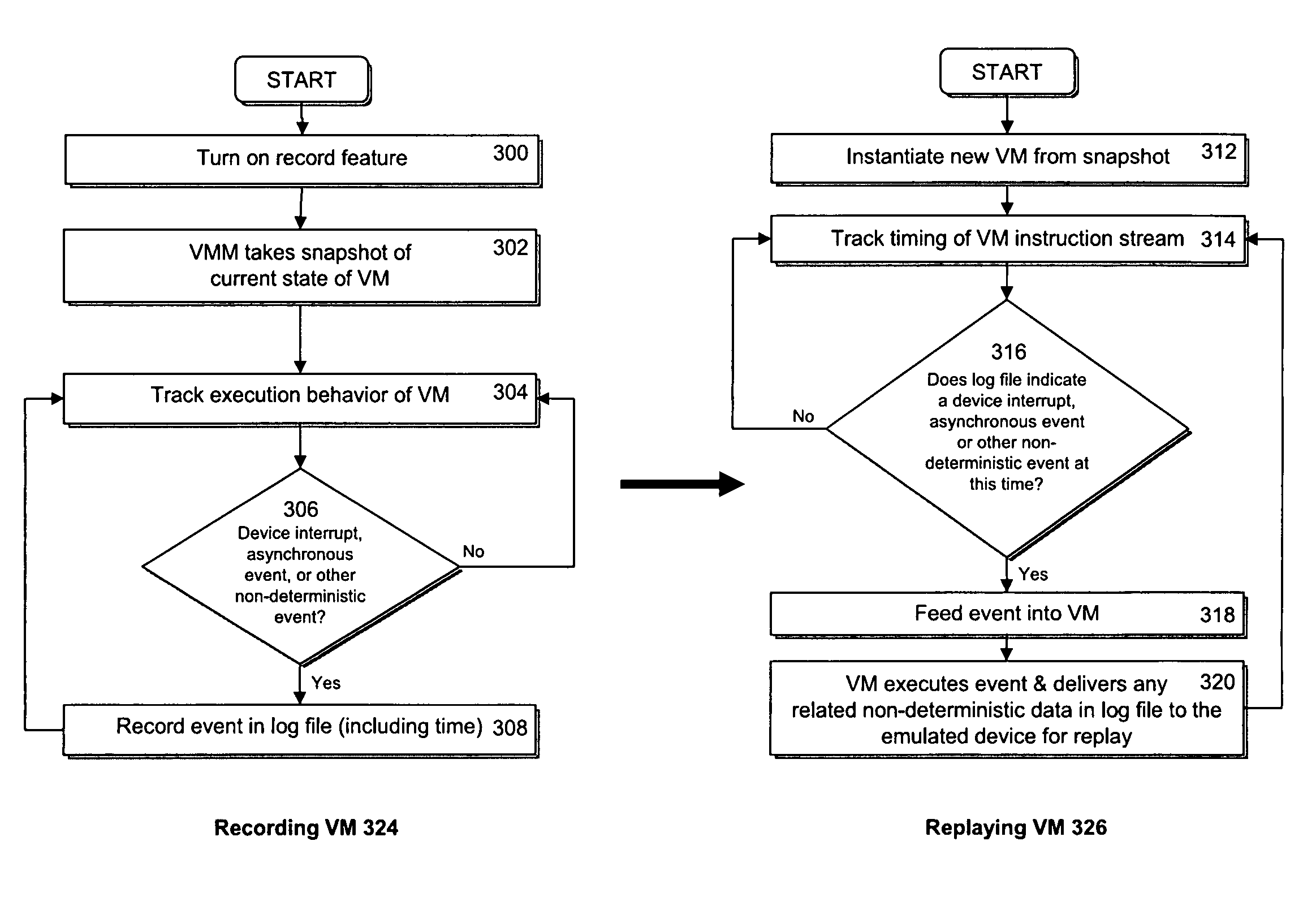
Accelerating replayed program execution to support decoupled program analysis
ActiveUS8719800B2Error detection/correctionSpecific program execution arrangementsDynamic program analysisStatic program analysis
A virtual machine system decouples dynamic program analysis from program execution. Program analysis is decoupled from program execution through the use of a virtual machine to record program execution and an analysis platform to replay and analyze the program execution. Optimization techniques are applied to prevent the analysis platform from falling too far behind the program execution platform during replay.
Owner:VMWARE LLC
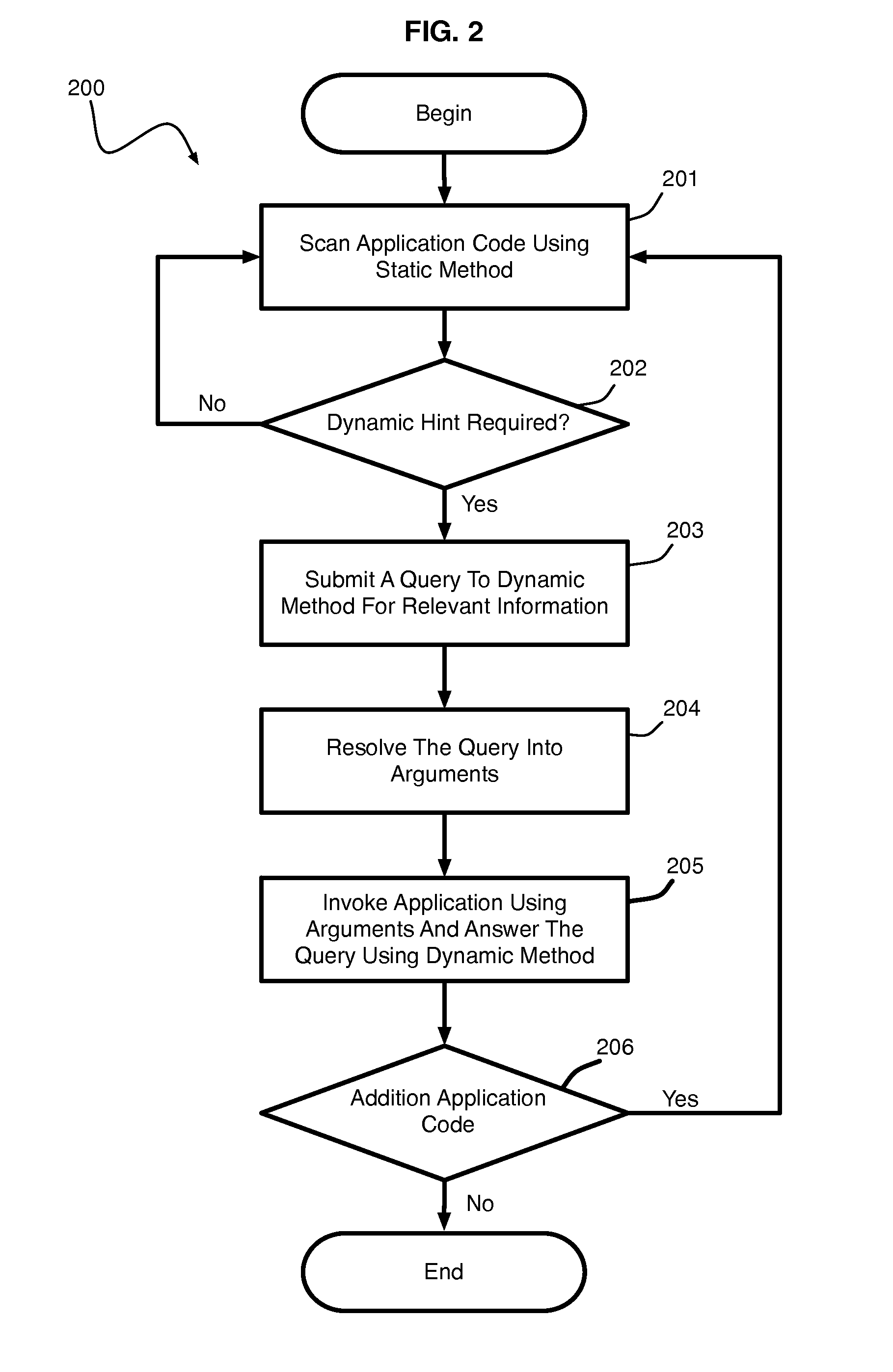
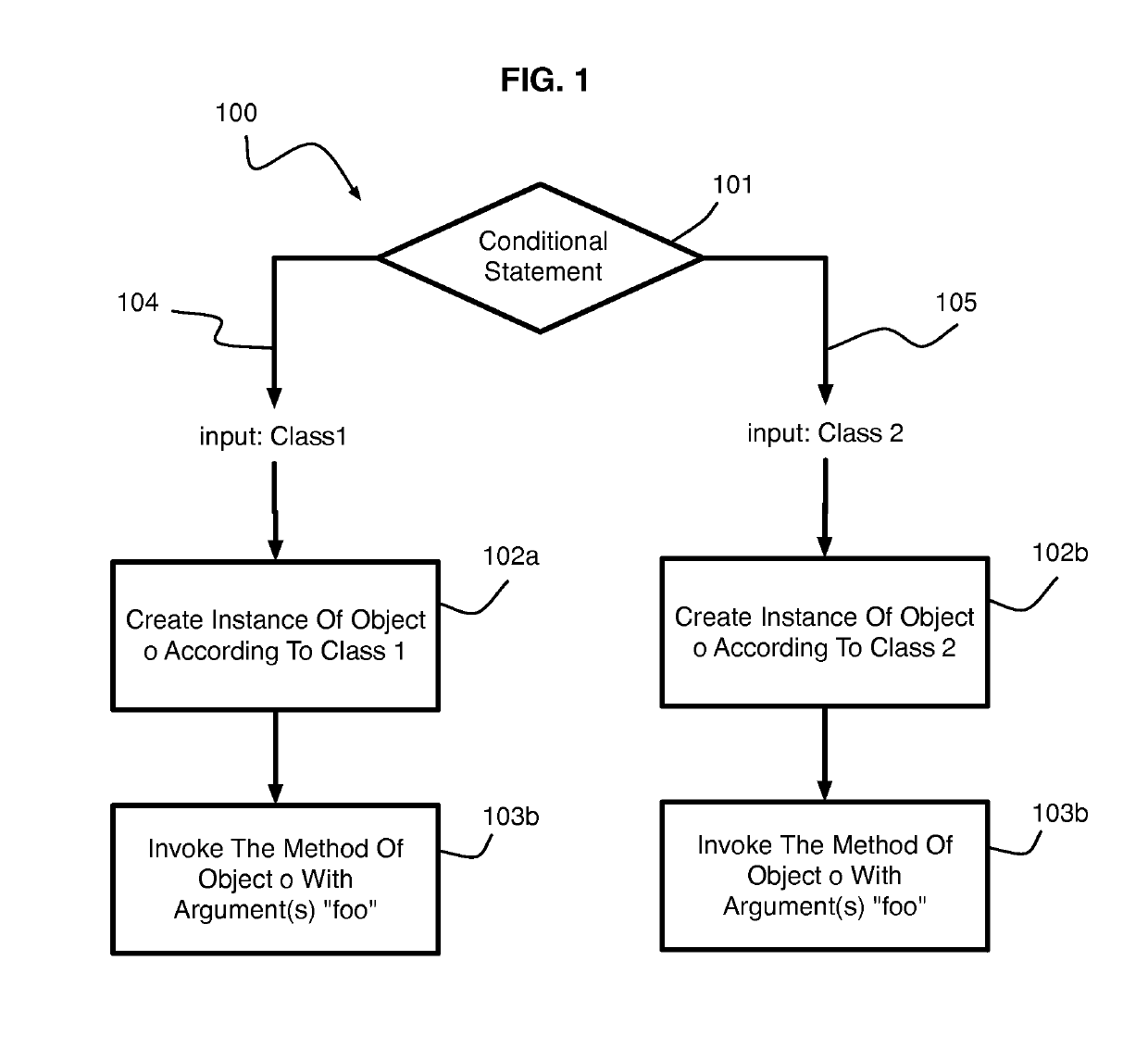
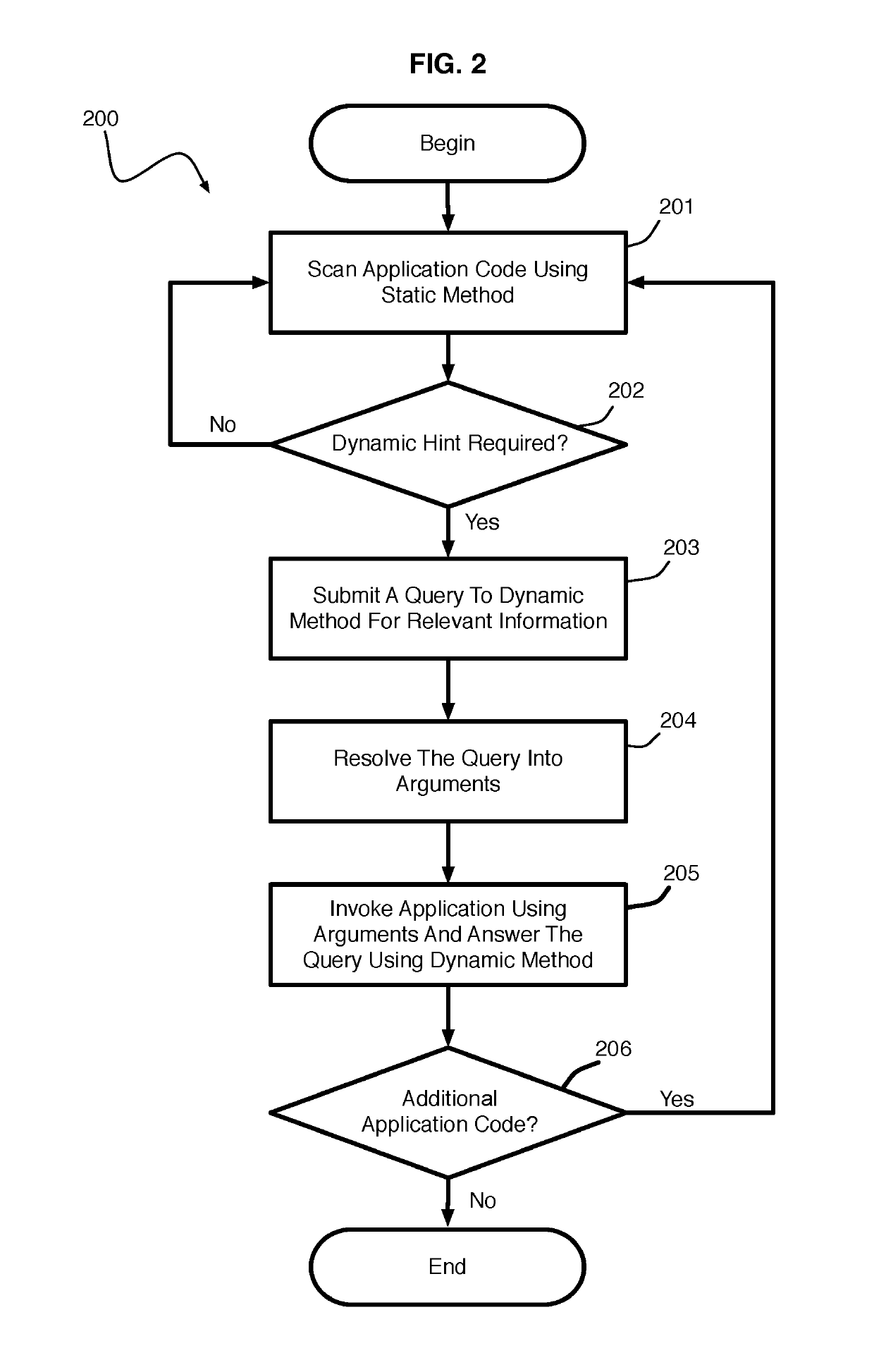
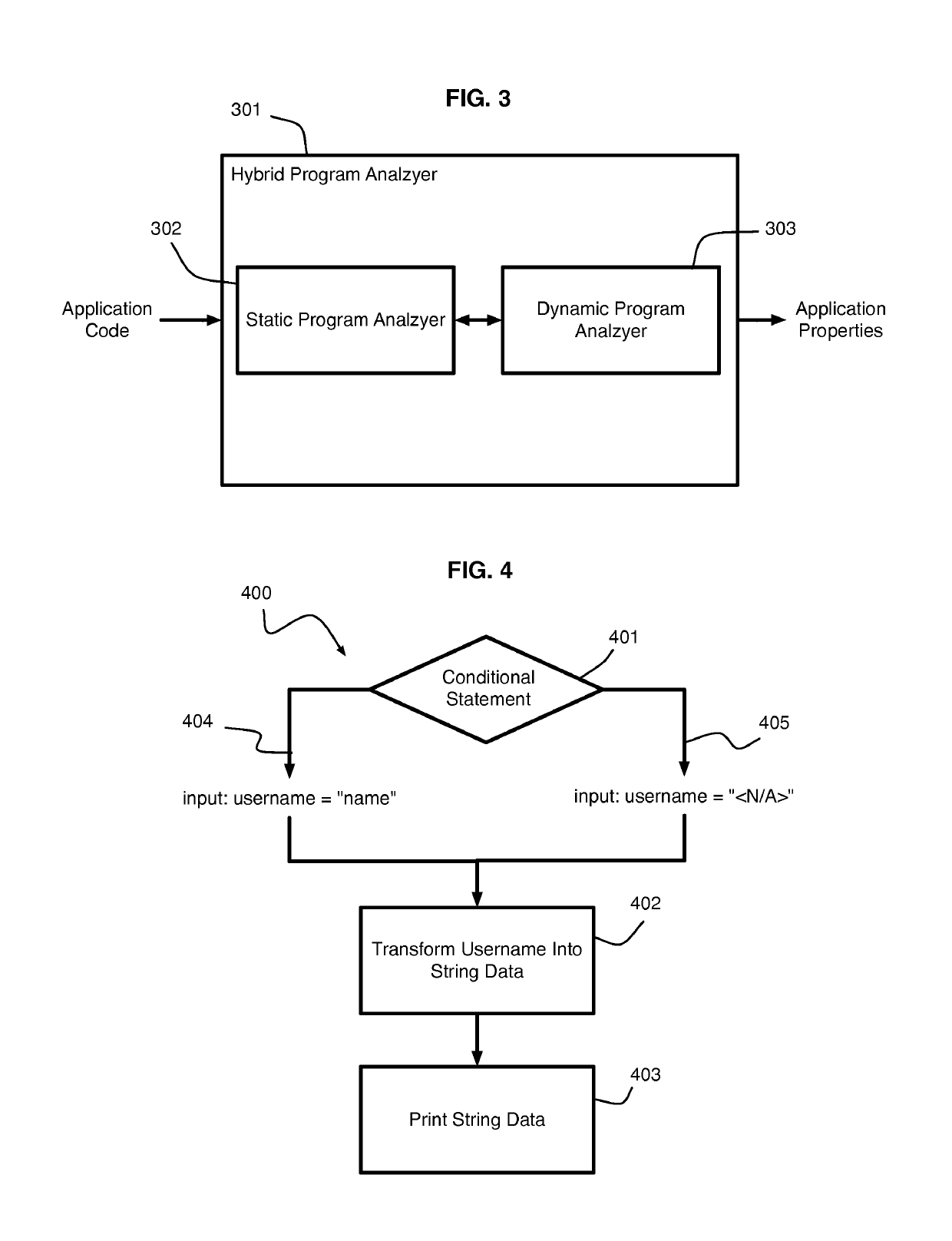
Hybrid Program Analysis
ActiveUS20140130019A1Error detection/correctionReverse engineeringDynamic program analysisApplication software
A hybrid program analysis method includes initiating a static program analysis of an application, generating, by a static program analyzer, a query to a dynamic program analyzer upon determining a code construct of the application requiring dynamic analysis, resolving, by the dynamic program analyzer, the query into a set of arguments with which to invoke the code construct of the application, generating, by the dynamic program analyzer, the set of arguments, invoking, by the dynamic program analyzer, the code construct of the application using set of arguments, answering, by the dynamic program analyzer, the query, and continuing the static program analysis of the application.
Owner:IBM CORP
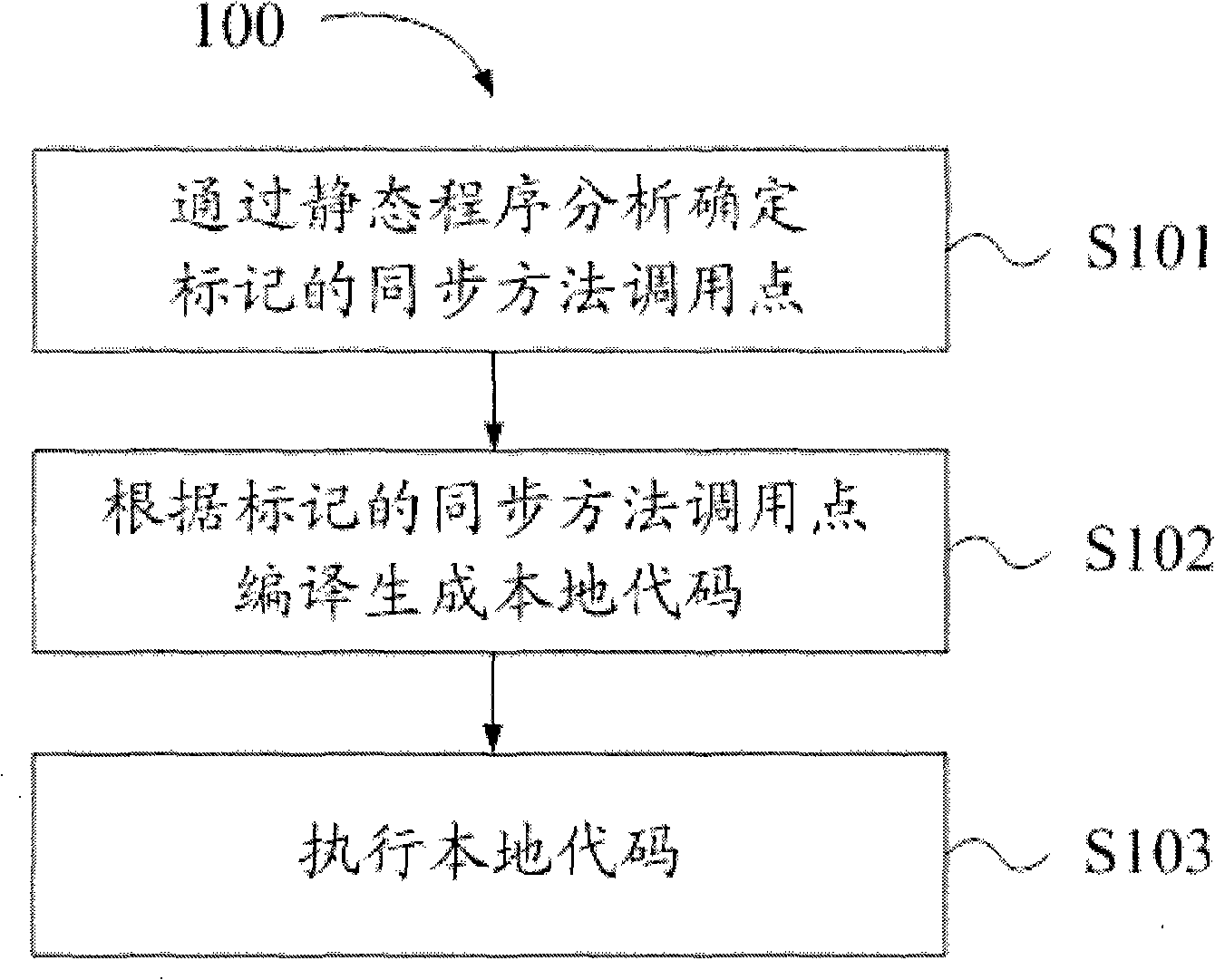
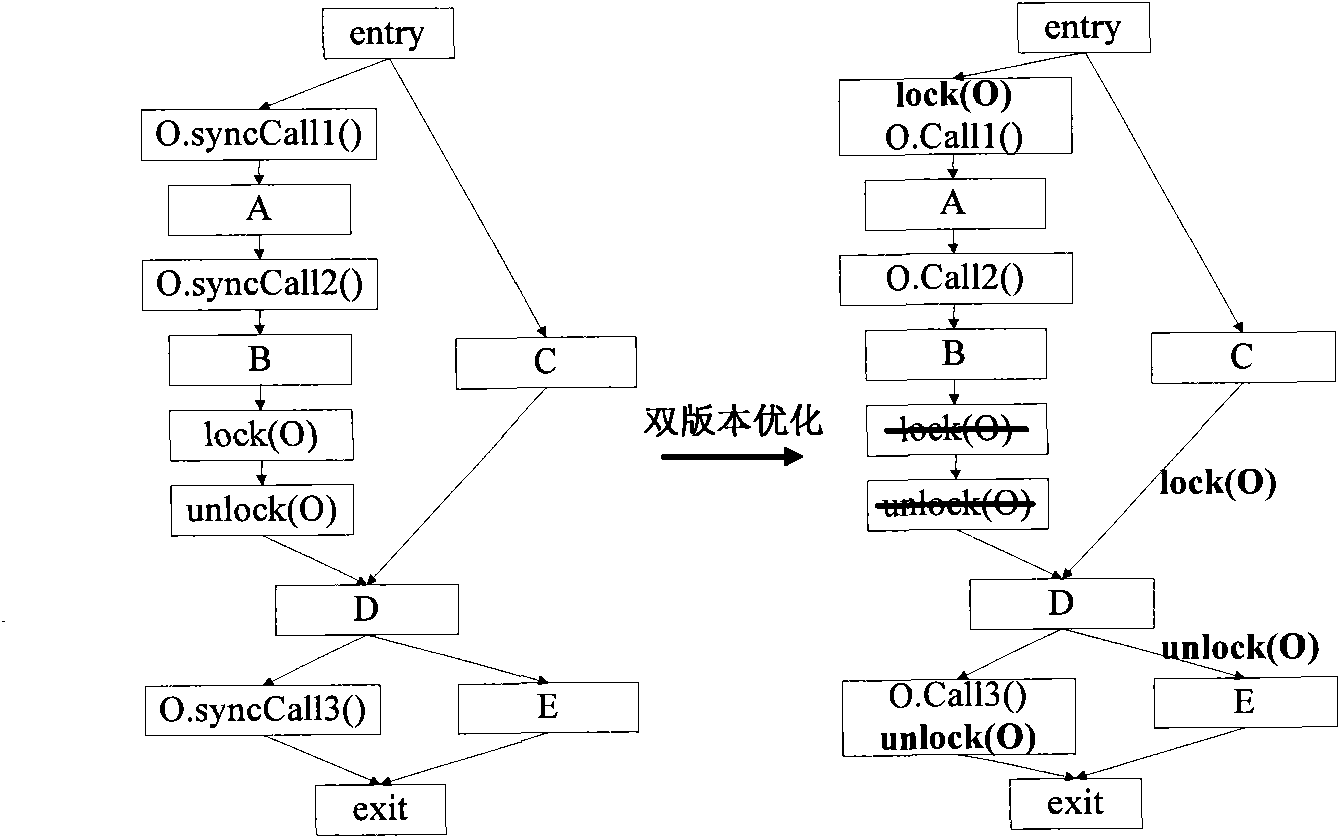
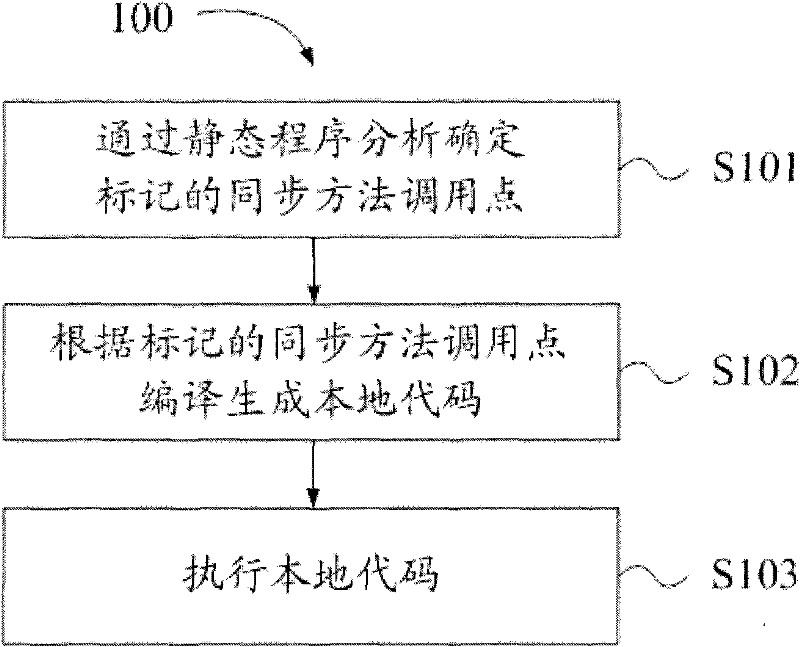
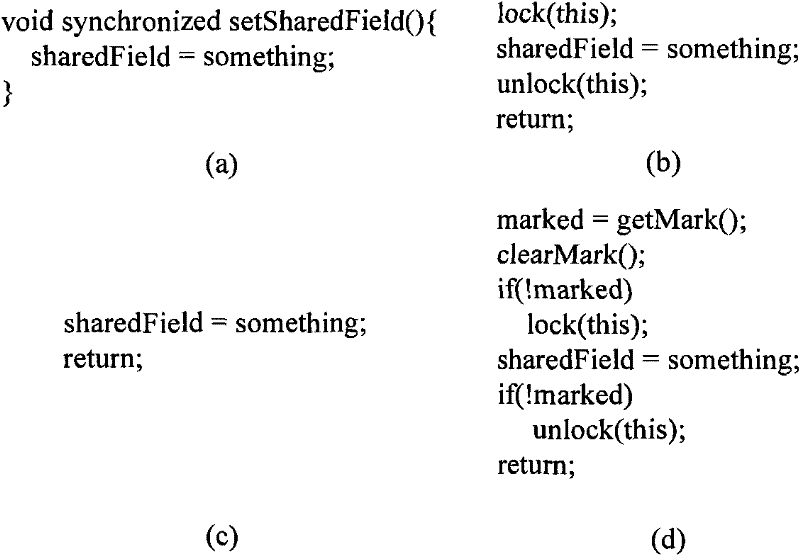
Synchronous optimization method and synchronous optimization equipment
InactiveCN101630268AIncrease flexibilityStrong scalabilityProgram controlMemory systemsParallel computingStatic program analysis
The invention provides a synchronous optimization method and synchronous optimization equipment. The method comprises the following steps: carrying out static program analysis on a compiled method, confirming a synchronous method calling point without carrying out synchronous operation on a synchronous object in the compiled method according to an analysis result and marking the synchronous method calling point; compiling the called synchronous method according to the marked synchronous method calling point to generate a local code allowing to execute the synchronous operation on the synchronous object of the synchronous method; and executing the local code according to the marked synchronous method. The synchronous optimization method and the synchronous optimization equipment have high flexibility and favorable expandability.
Owner:UNIV OF SCI & TECH OF CHINA
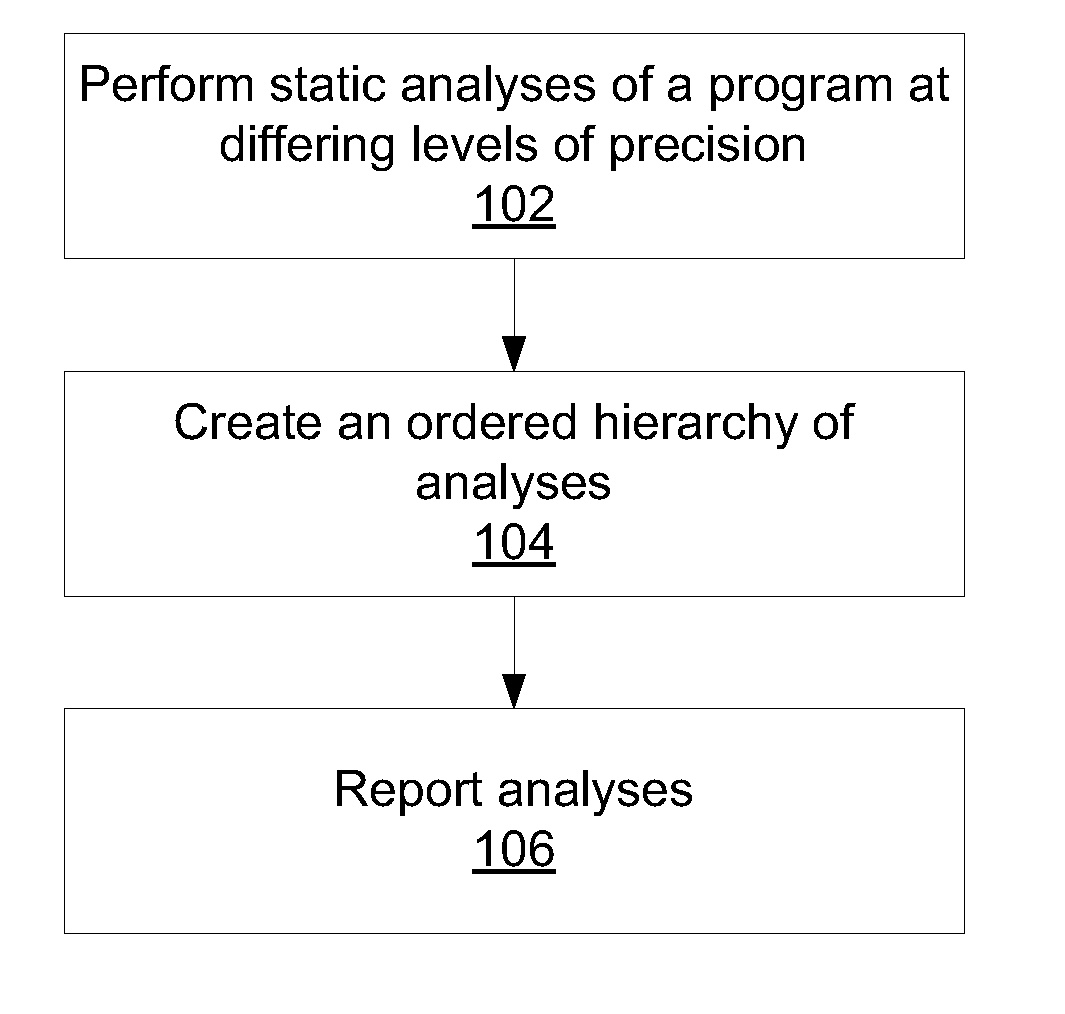
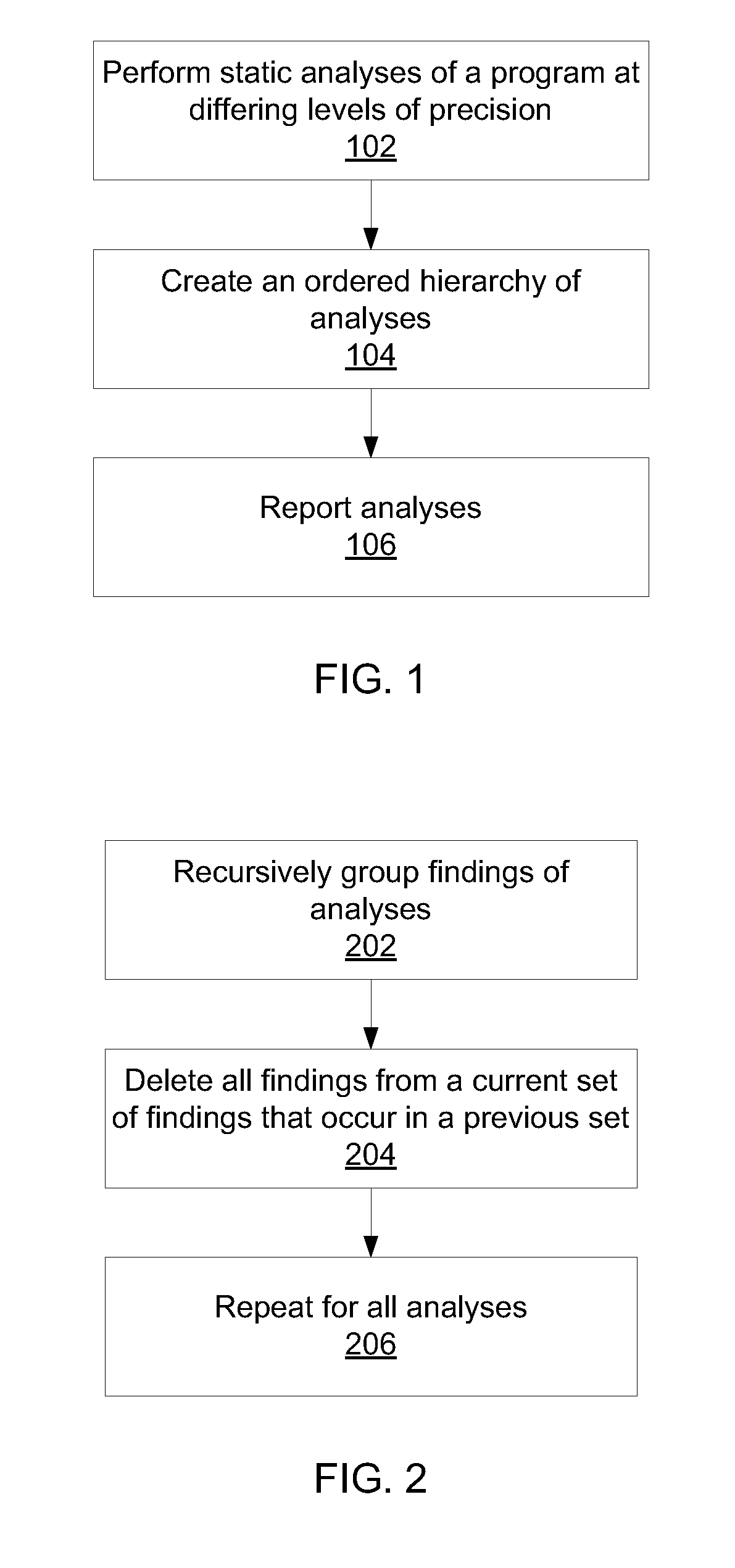
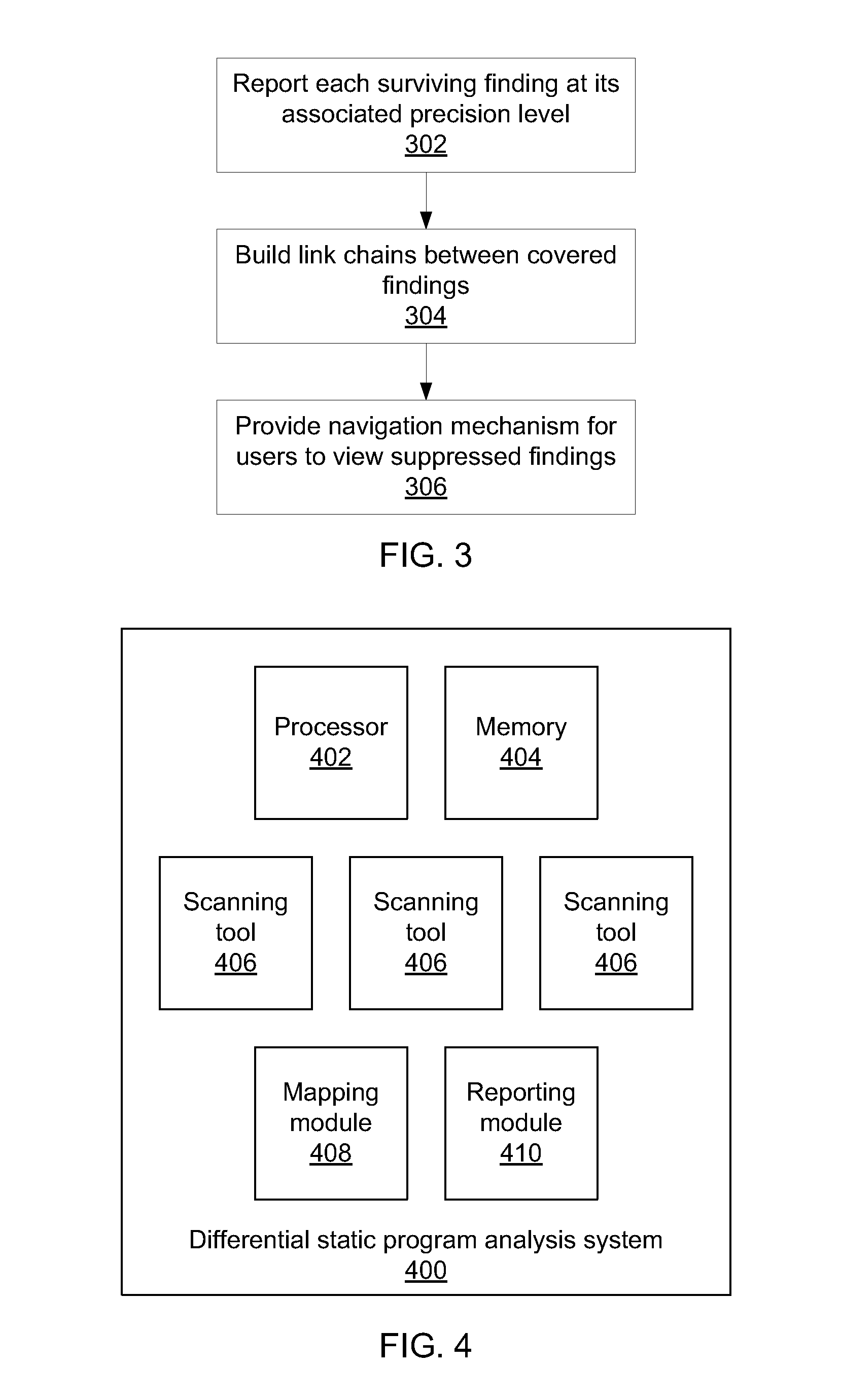
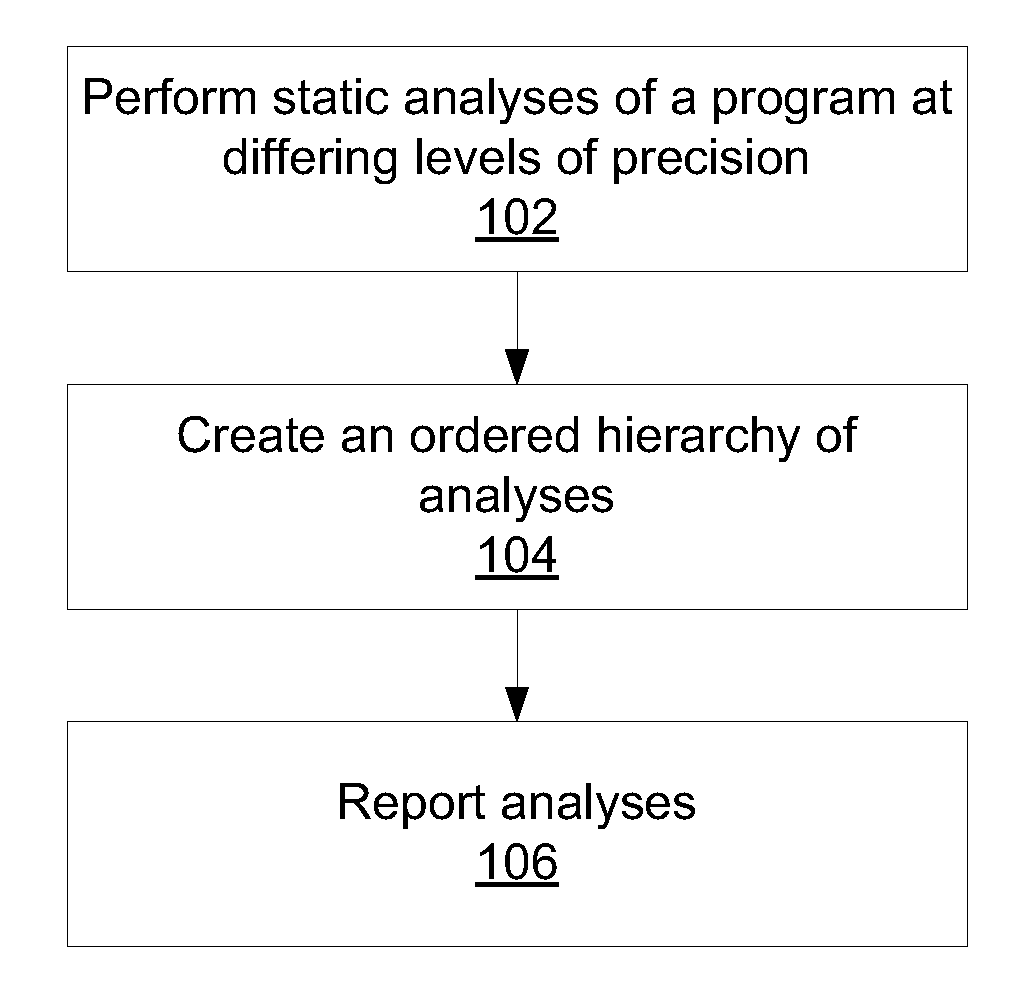
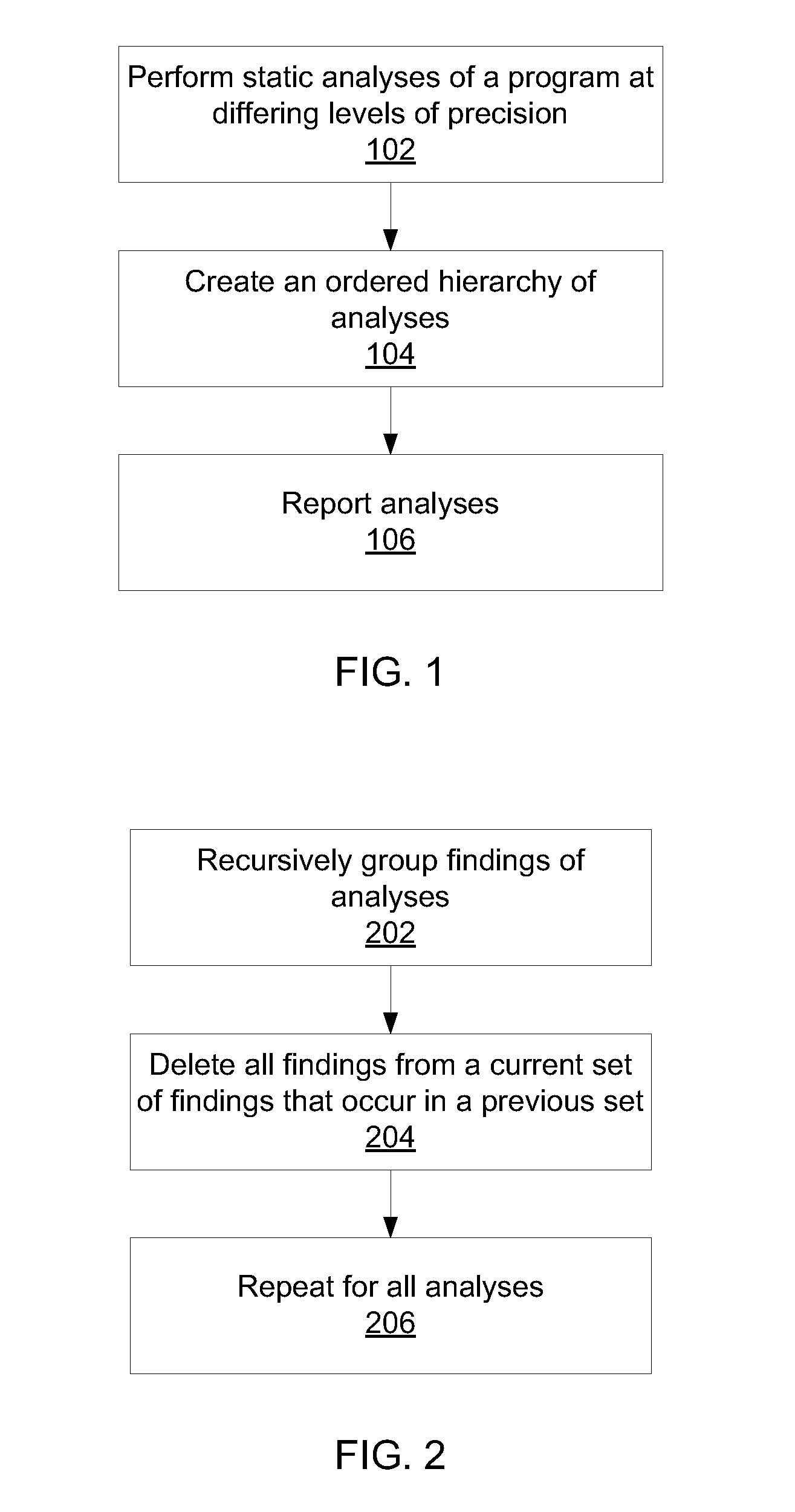
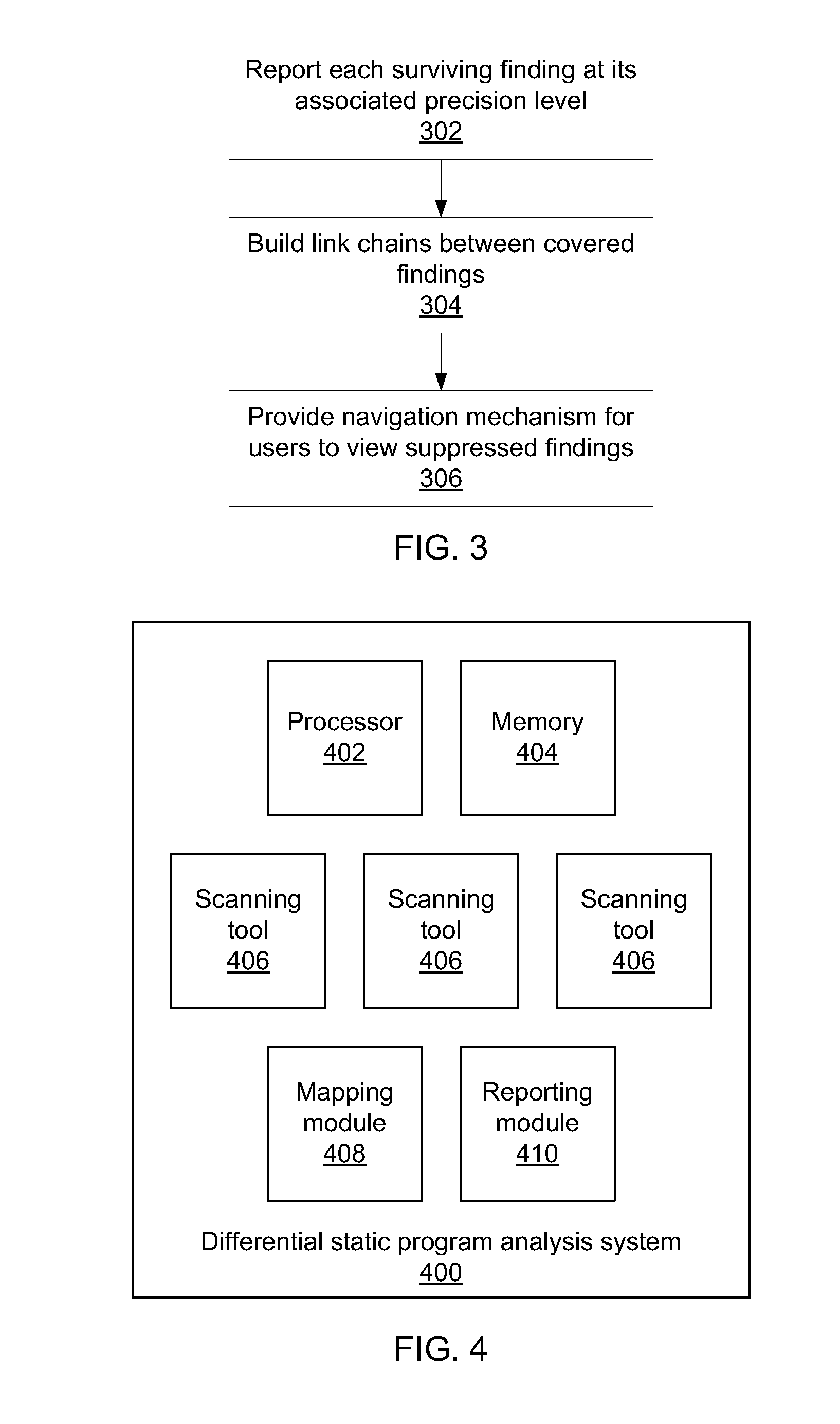
Differential static program analysis
InactiveUS20140115564A1Error detection/correctionReverse engineeringHigh level analysisProgram analysis
Methods for program analysis include performing a high-level analysis on a program using a processor to generate one or more high-level findings; performing one or more low-level analyses on the program using a processor to generate one or more low-level findings; mapping the one or more low-level findings to the high-level findings to generate a concise combination report that categorizes each finding according to the highest-level analysis that produces the finding.
Owner:IBM CORP
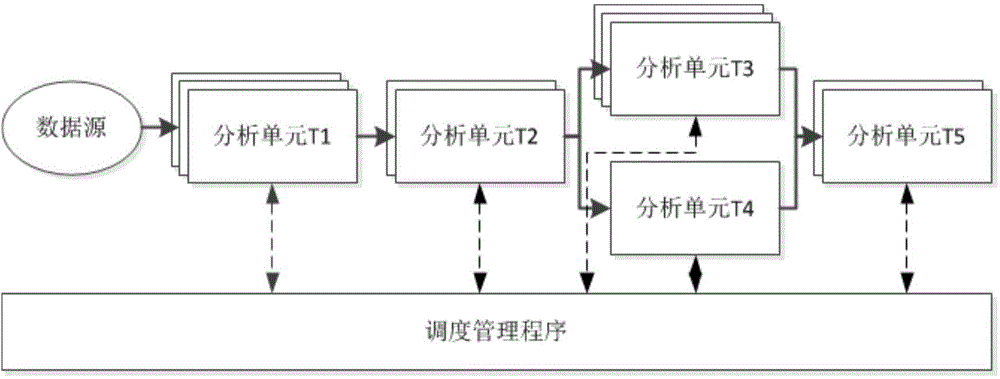
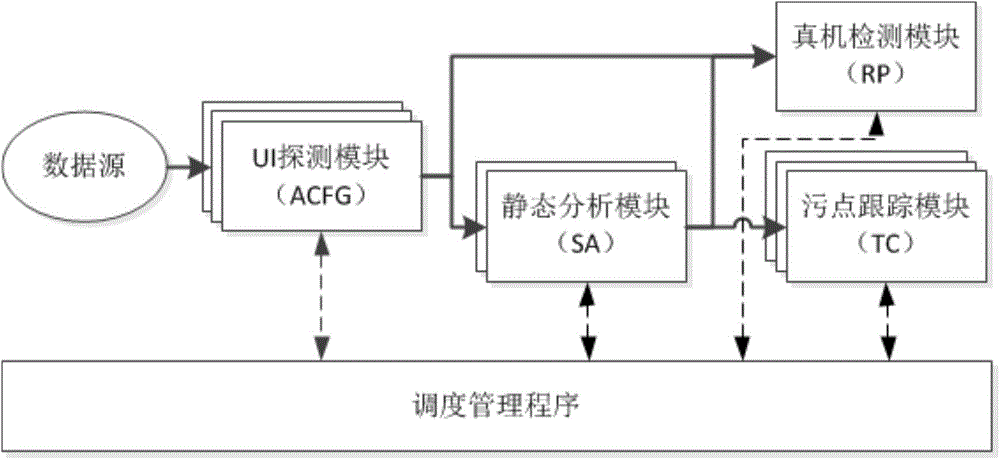
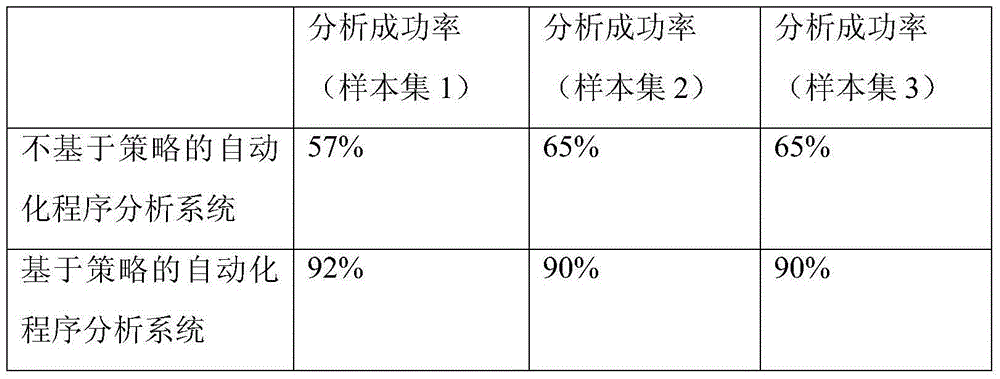
System and method for automatic program analysis based on strategy
ActiveCN106155880AImprove accuracyImplement parallel processingSoftware testing/debuggingData sourceSoftware analytics
The invention relates to a system and a method for automatic program analysis based on a strategy. The system comprises a data source, analysis units, and a dispatching management program. The data source is a set of to-be-analyzed software. The analysis unit is a packaged software analysis module, and is used to communicate with a scheduler, to complete program security analysis of a certain method or a certain stage of assigned software. The dispatching management program is used to configure an analysis strategy, and realizes dispatching and management of an analysis task through analyzing the configured analysis strategy and monitoring states of the plurality of analysis units, to form effective joining and combination of each analysis unit. Through the pre-configured strategy and global task dispatching, a plurality of analysis modules or a plurality of analysis stages are automatically joined, so as to realize a complete, efficient, and automatic analysis process of a program.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
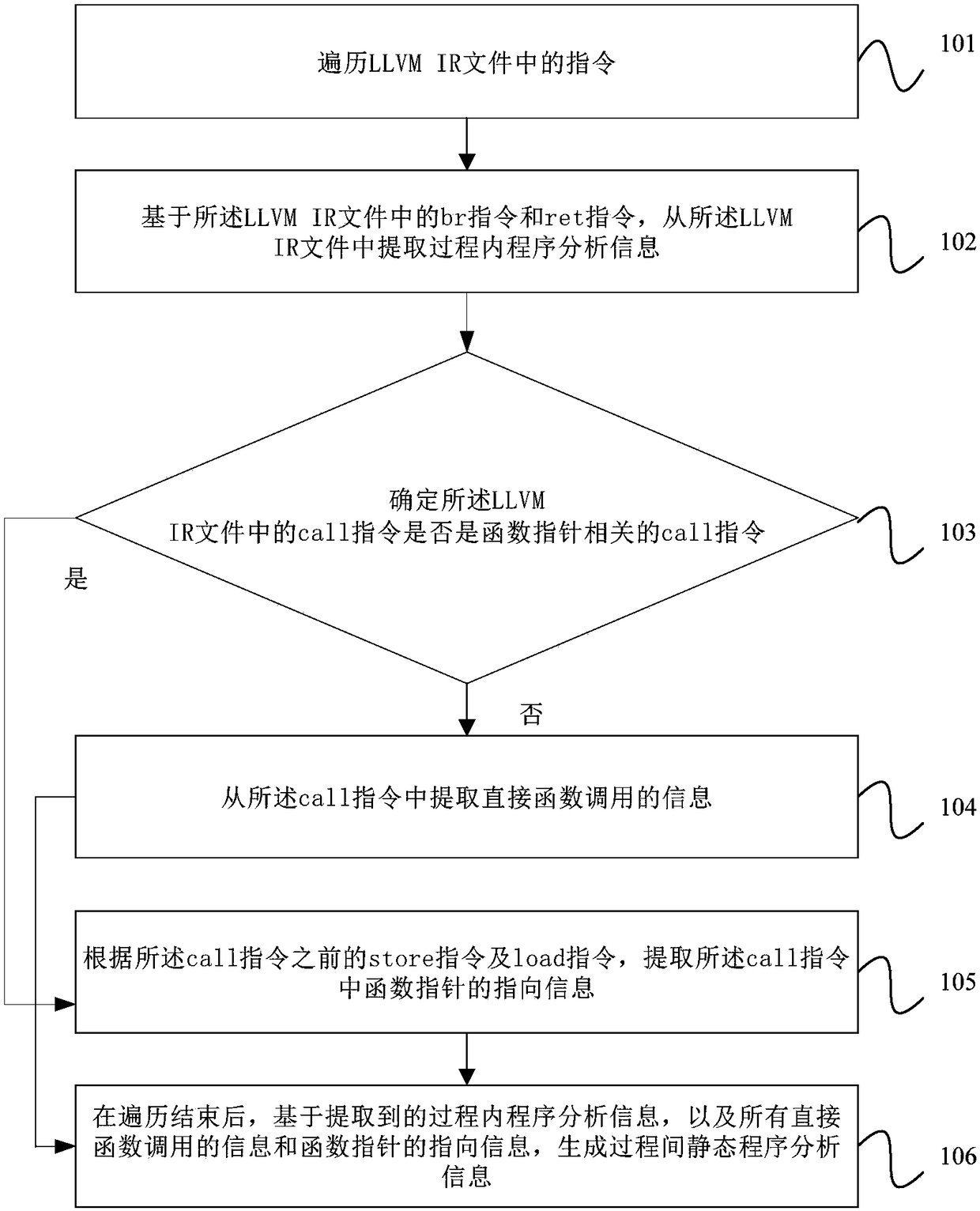
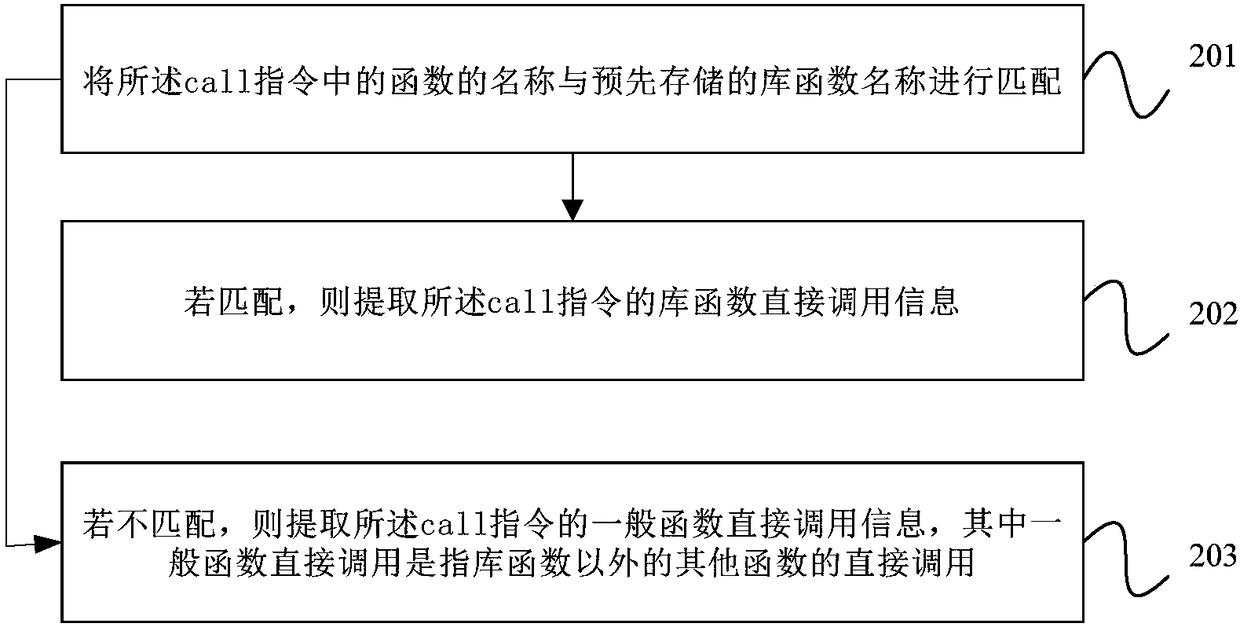
Extraction method and device for cross-process static program analysis information and equipment
ActiveCN108132799ASolve the problem of imperfect handlingReverse engineeringFunction pointerProgram analysis
The embodiment of the invention provides an extraction method and device for cross-process static program analysis information and equipment. The method comprises the steps that commands in an LLVM IRfile are traversed; based on a br command and a ret command, the cross-process program analysis information is extracted; whether or not a call command in the LLVM IR file is a call command related to a function pointer is determined; if not, information which is called by a direct function is extracted from the call command; if yes, according to a store command and a load command before the callcommand, pointing information of the function pointer in the call command is extracted; after traversing is completed, based on the extracted cross-process program analysis information, all the information which is called by the direct function and the pointing information of the function pointer, the cross-process static program analysis information is generated. Accordingly the problem is solved that the pointing information of the function pointer is inaccurately acquired in static program analysis.
Owner:CAPITAL NORMAL UNIVERSITY
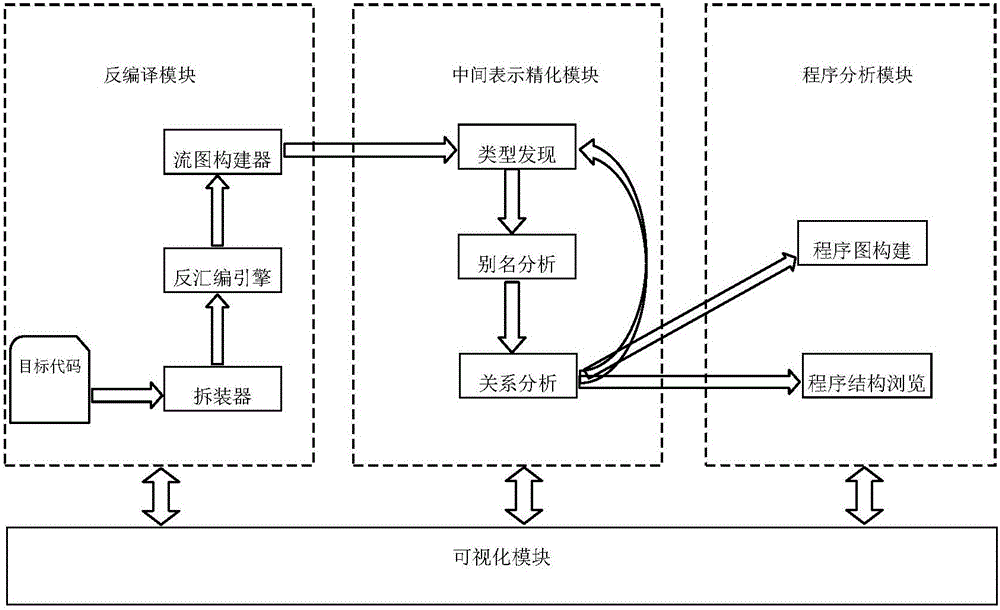
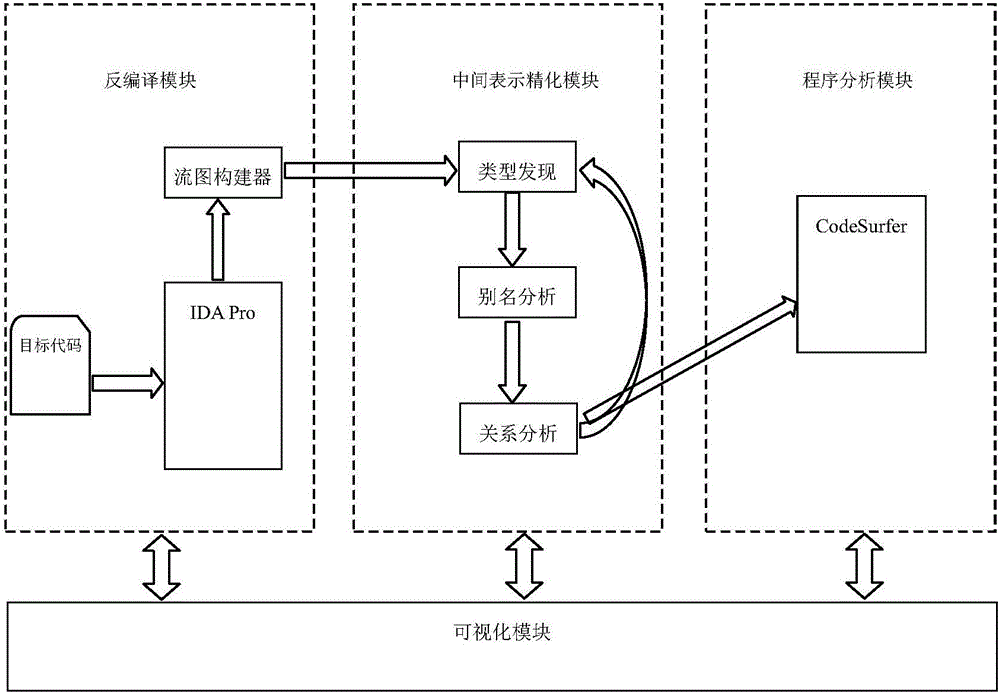
Static program analysis system for target code
InactiveCN106649095AGuaranteed correctnessThe result is accurateSoftware testing/debuggingGraphicsObject code
The invention discloses a static program analysis system for a target code. The system comprises a decompilation module, an intermediate expression refinement module, a program analysis module and a visual module. The decompilation module adopts a to-be-analyzed target code file as input, performs packaging format removal and decompilation operations on an input file, generates an assembly code, a control flowchart and process boundary and other information and adopts the same as the output of the model; the intermediate expression refinement module generates a corresponding data structure and performs a refinement operation according to the information generated by the decompilation module; the program analysis module generates several expression forms of the to-be-analyzed program according to the information output by the decompilation module and the intermediate expression refinement module; and the visual module is applied to visible display of various patterns and other information in an analysis process. The system analyzes the program behaviors according to actually executed binary codes and has higher fidelity compared with an analysis tool for source codes.
Owner:EAST CHINA NORMAL UNIV
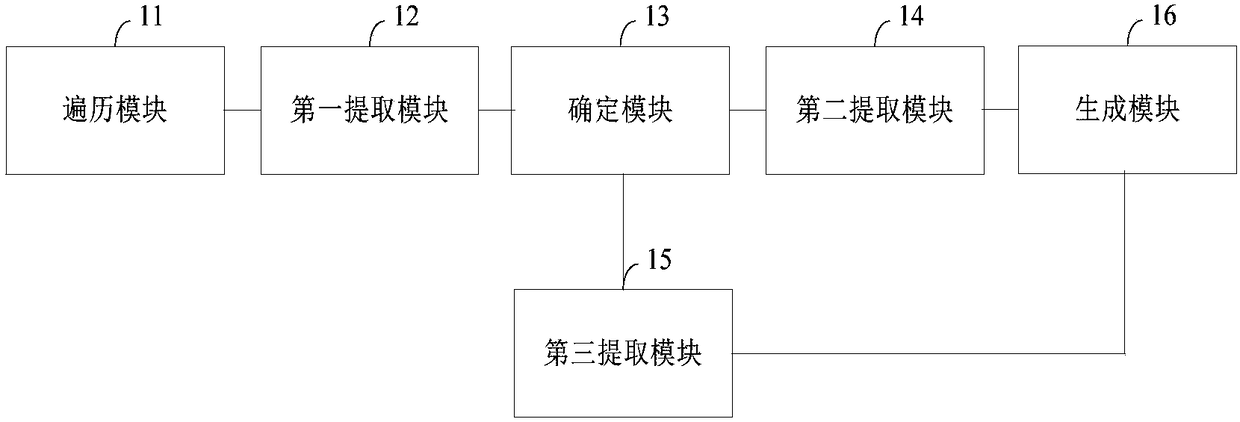
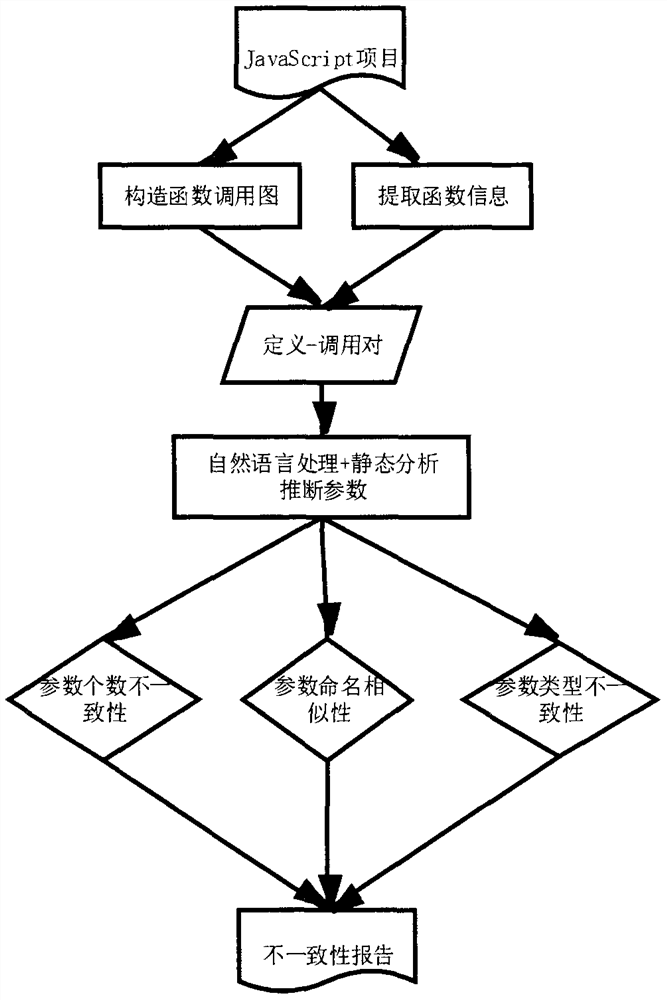
JavaScript function parameter mismatch detection method based on static program analysis
PendingCN111694570ASoftware testing/debuggingCode compilationTheoretical computer scienceAbstract syntax tree
The invention relates to a JavaScript function parameter mismatch detection method based on a static program analysis and natural language processing method. The method comprises the steps of, constructing an abstract syntax tree AST for each file in a JavaScript project, traversing the AST tree, and extracting program related information of a definition function and a construction function of thewhole project; scanning and analyzing the JavaScript file of the whole project, respectively obtaining specific positions of a definition function and a calling function, and constructing a functioncalling graph of the project; according to the extracted annotation information, deducing the type of the parameter through a natural language processing method in combination with probability; and according to the extracted information, detecting the inconsistency of the parameter number, the parameter name and the parameter type, and giving a detection report that the JavaScript function parameters in the project are not matched.
Owner:NANJING UNIV
System and method to decrease program analysis overhead
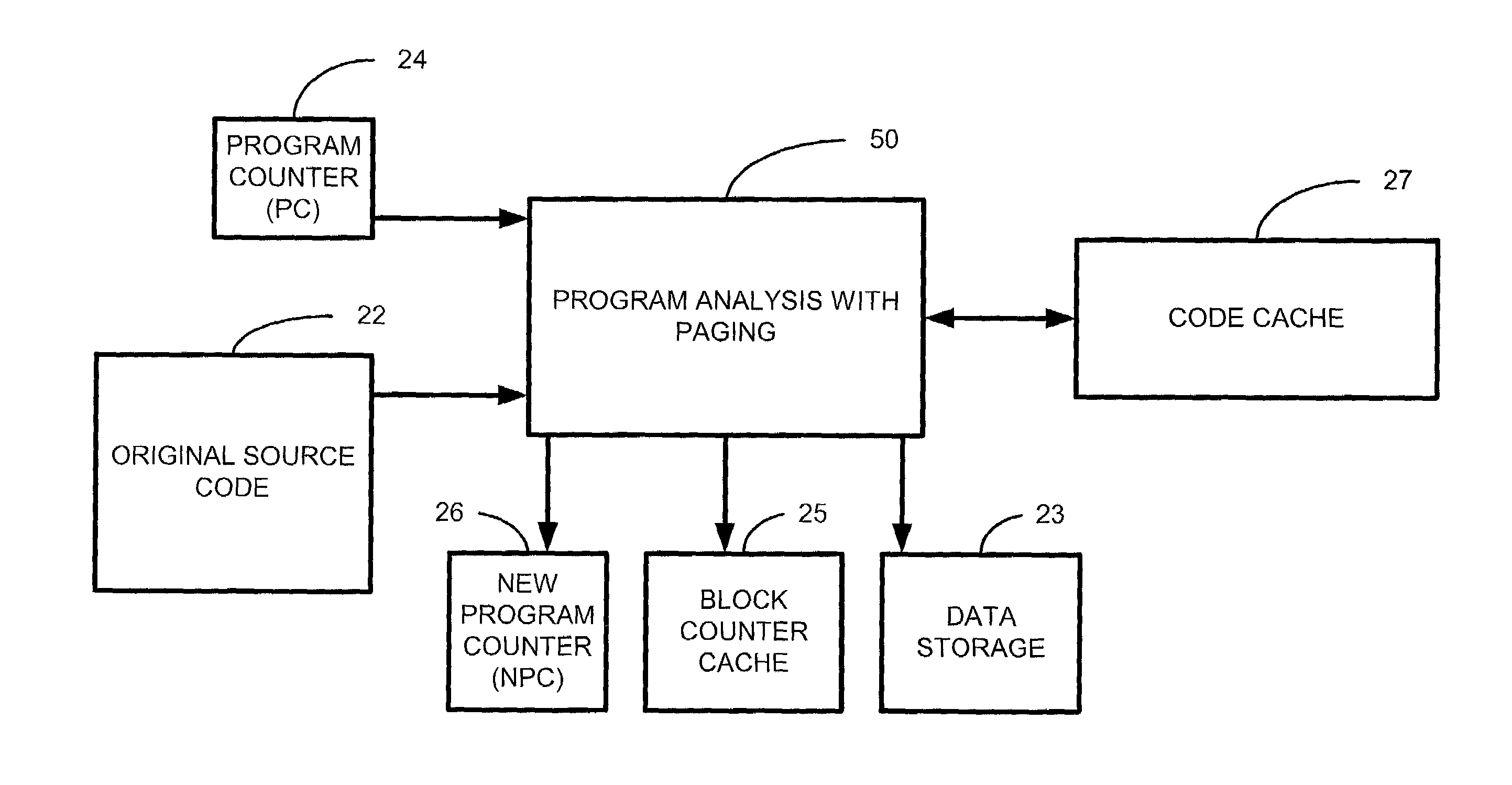
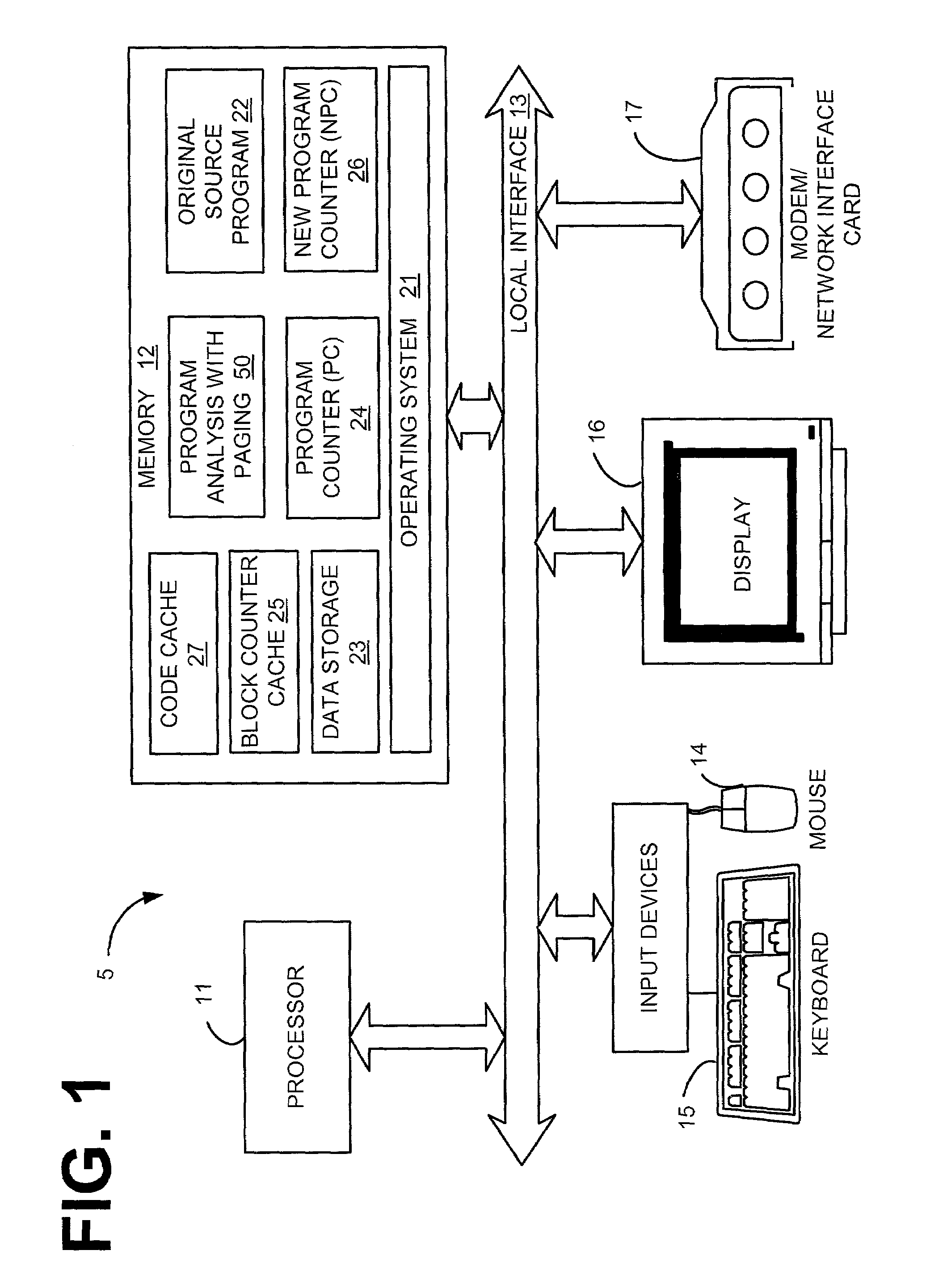
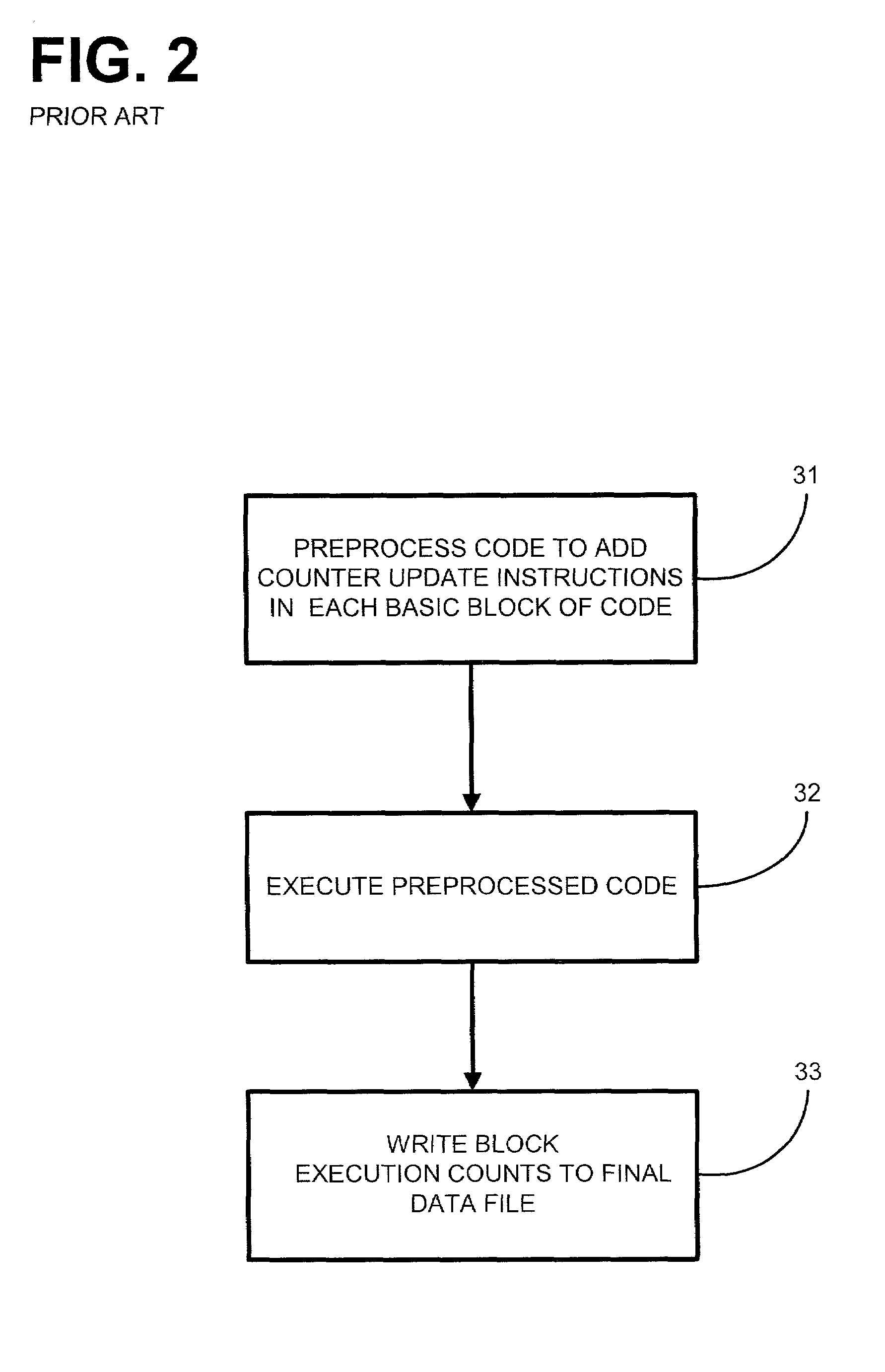
InactiveUS7243339B2Hardware monitoringSpecific program execution arrangementsParallel computingProgram analysis
System and method are described for program analysis with data caching. Briefly described, in architecture, the system can be implemented as follows. The present invention for program analysis with data caching includes a counter for tracking each time on of a plurality of blocks of code in the computer program is executed. A counter cache stores the plurality of counters of the plurality of blocks of code that are most recently executed. A storage area stores a plurality of counters of the plurality of blocks of code that are not most recently executed code.
Owner:HEWLETT PACKARD DEV CO LP
Internet of Things smart home scene safety analysis method and device
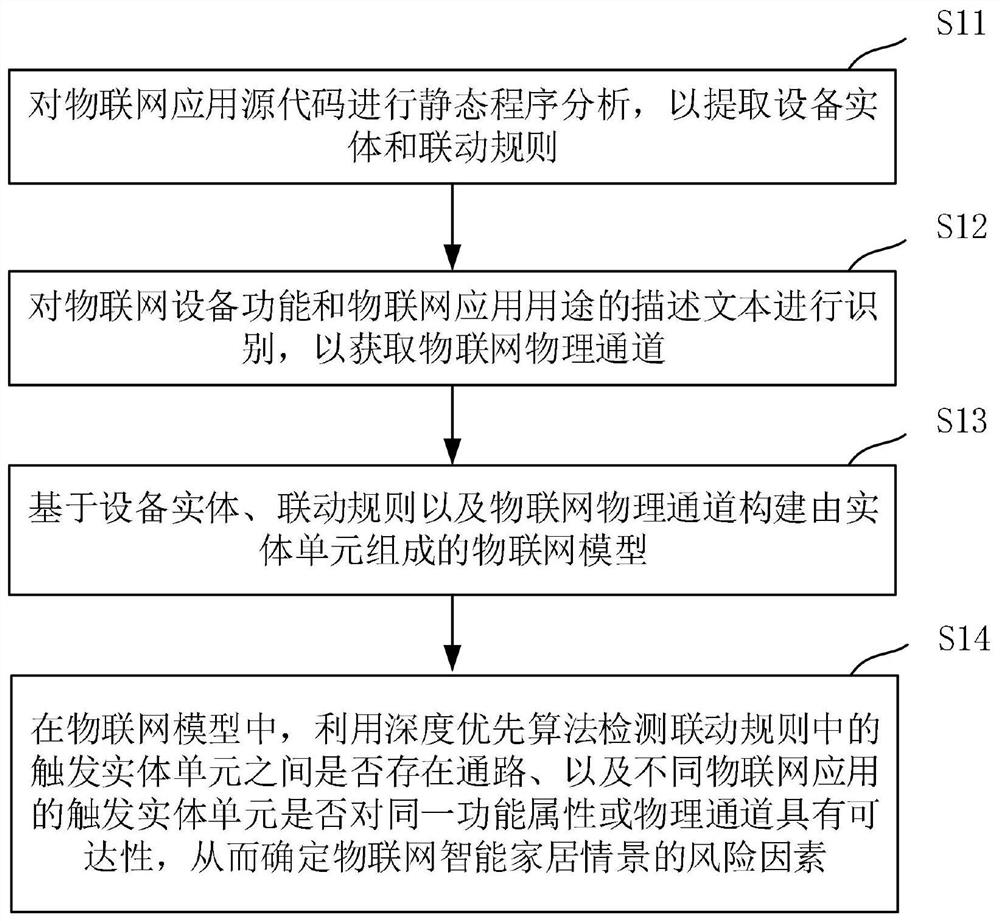
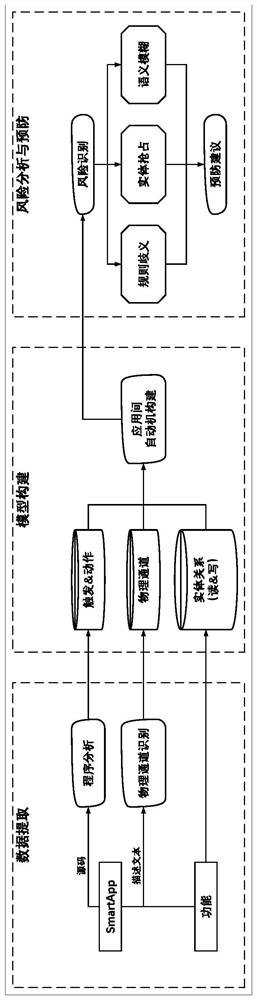
The invention discloses an Internet of Things smart home scene safety analysis method and device, and is used for solving the problems that the safety analysis of an Internet of Things platform has the limitation of a monitoring range, and the analysis is difficult when facing various Internet of Things platforms. The method comprises the following steps: performing static program analysis on an Internet of Things application source code to extract an equipment entity and a linkage rule; identifying the description text of the Internet of Things equipment function and the Internet of Things application purpose to obtain an Internet of Things physical channel; constructing an Internet of Things model composed of entity units based on the equipment entity, the linkage rule and the Internet of Things physical channel; and in the Internet of Things model, detecting whether a path exists between the trigger entity units in the linkage rule and whether the trigger entity units of different Internet of Things applications have accessibility for the same functional attribute or physical channel by using a depth-first algorithm, thereby determining risk factors of the Internet of Things smart home scene.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
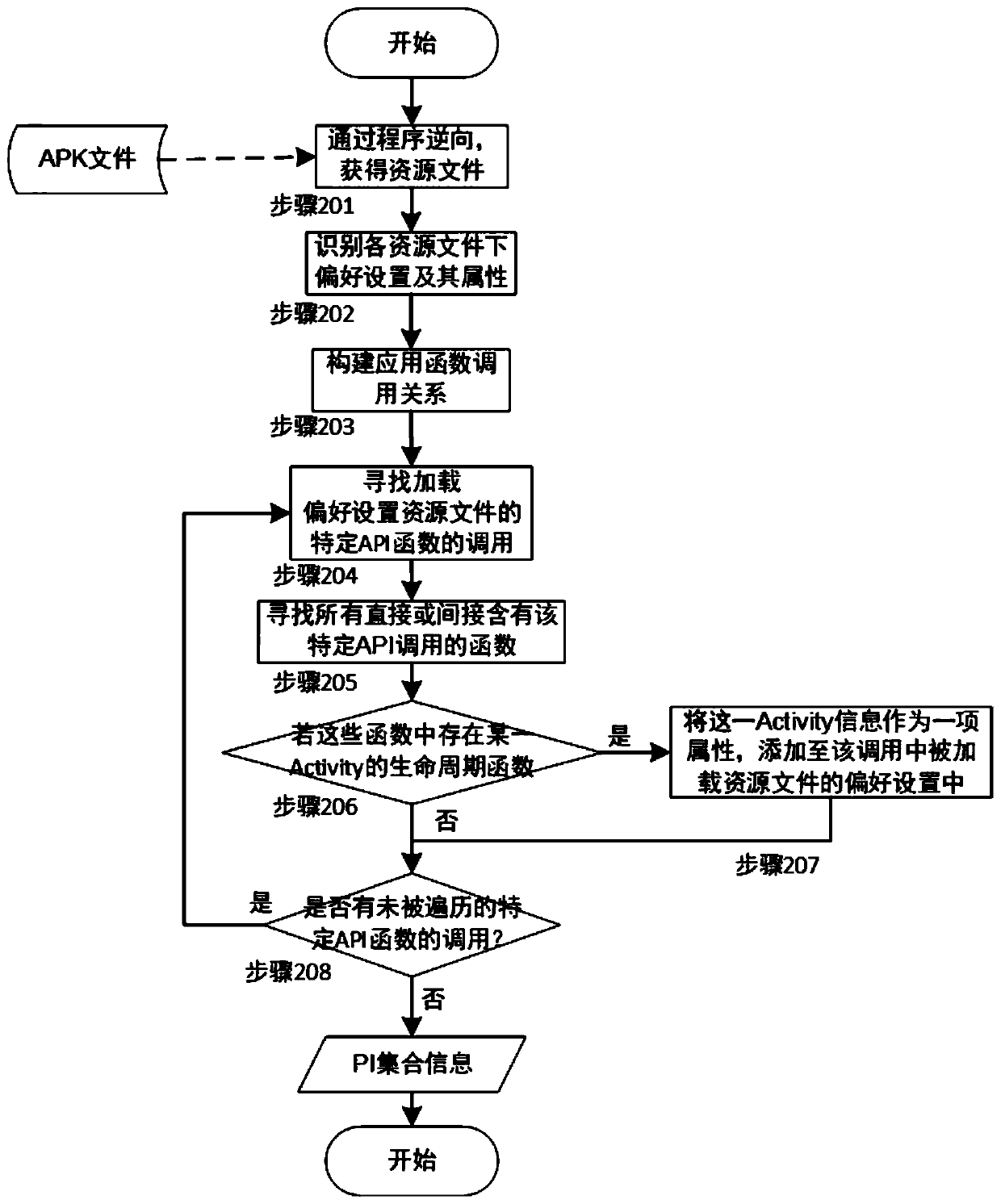
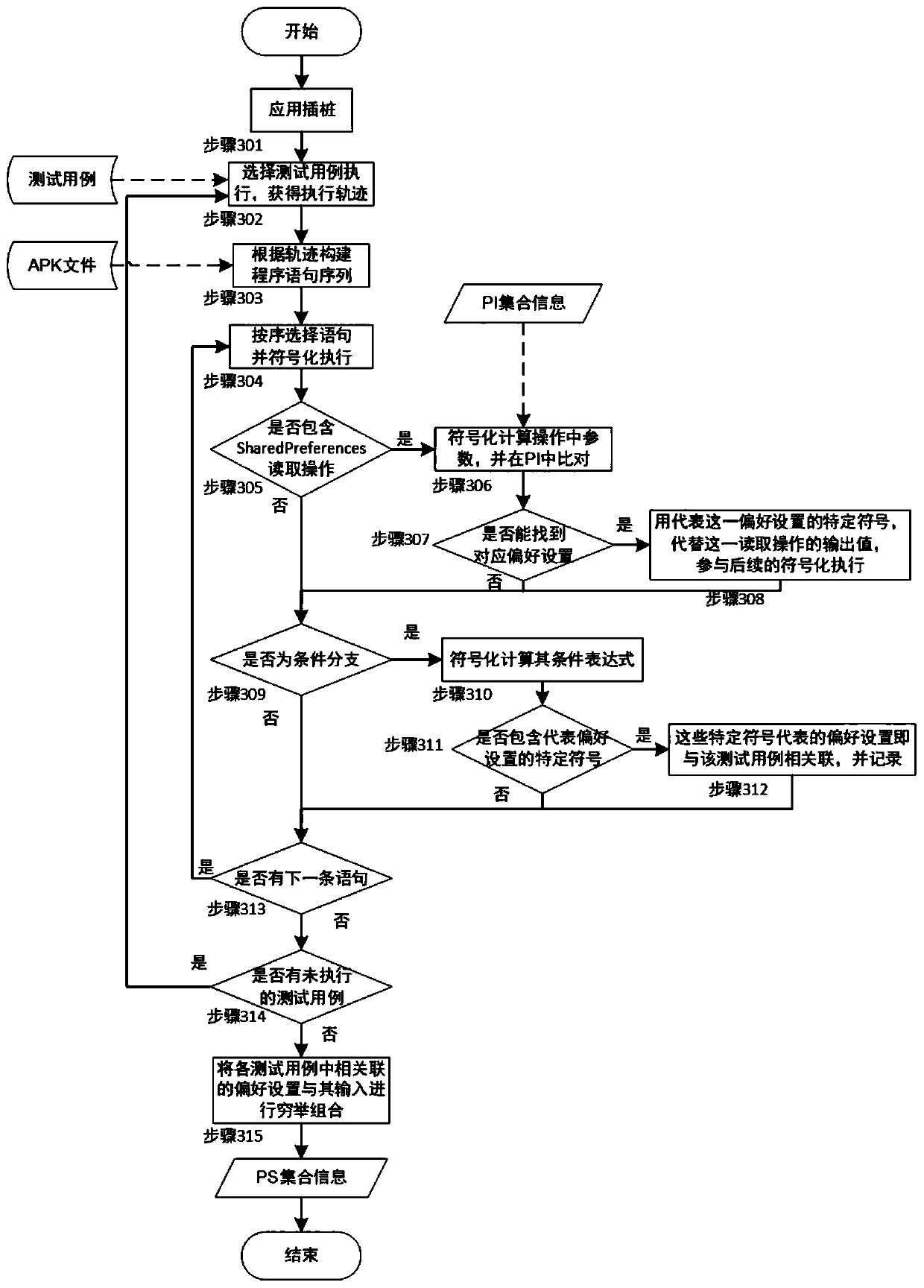
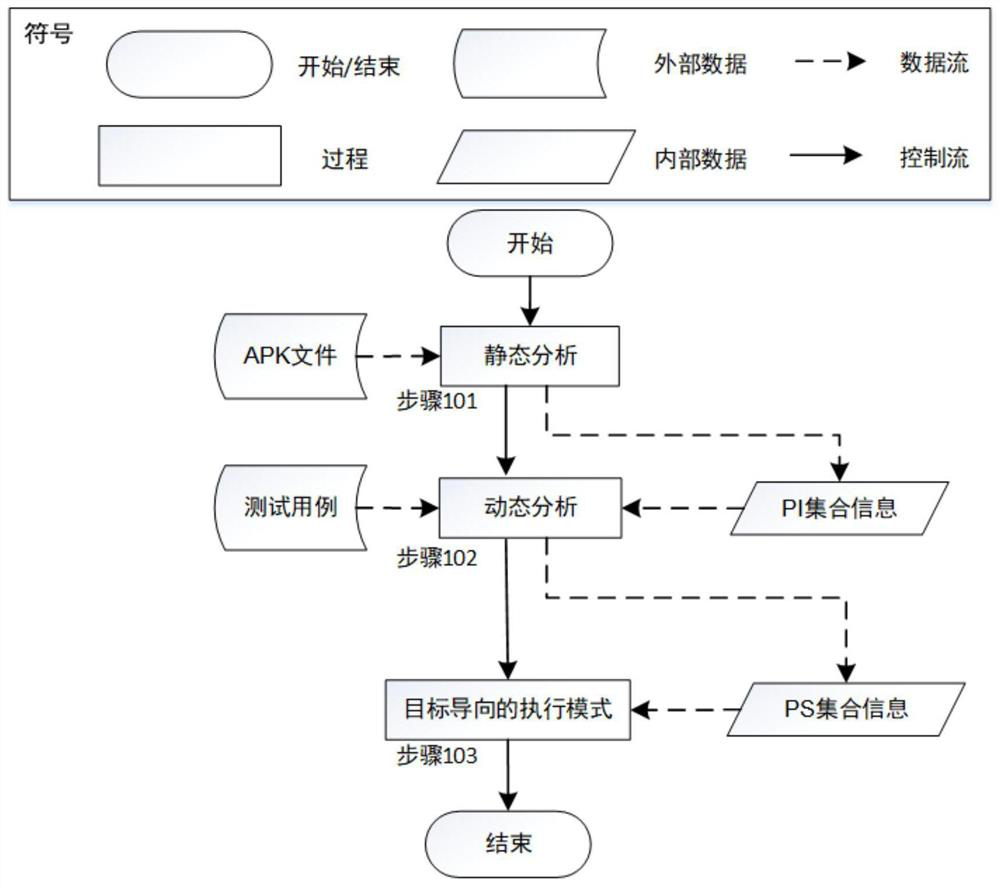
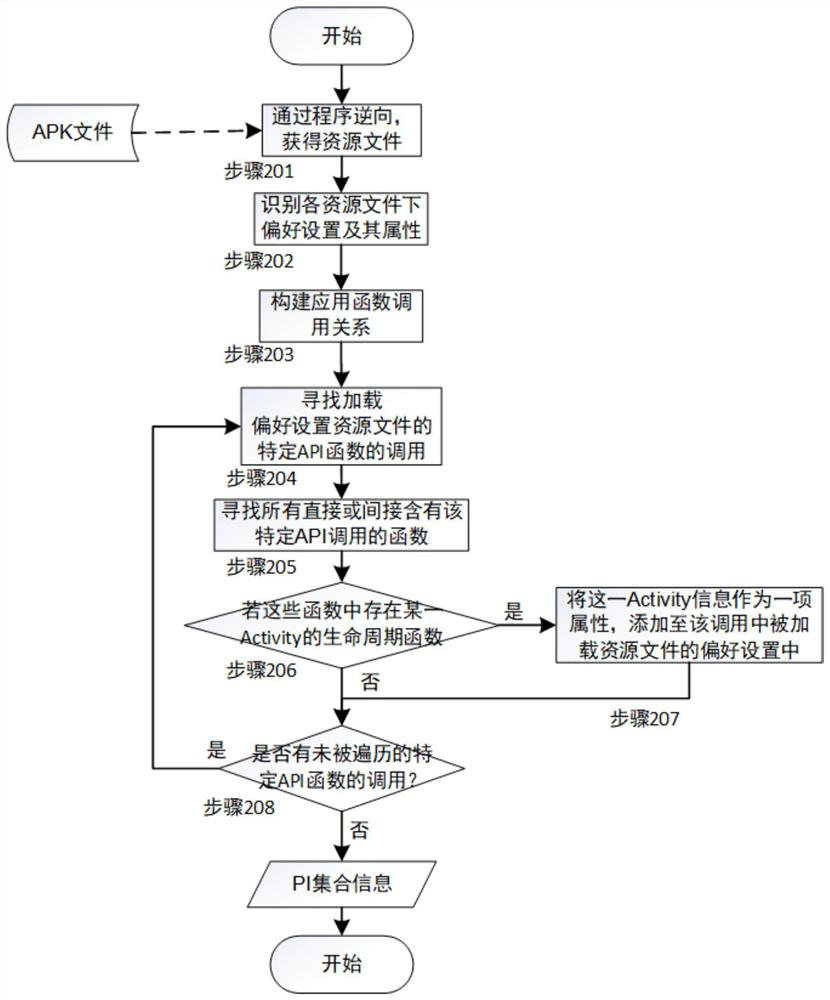
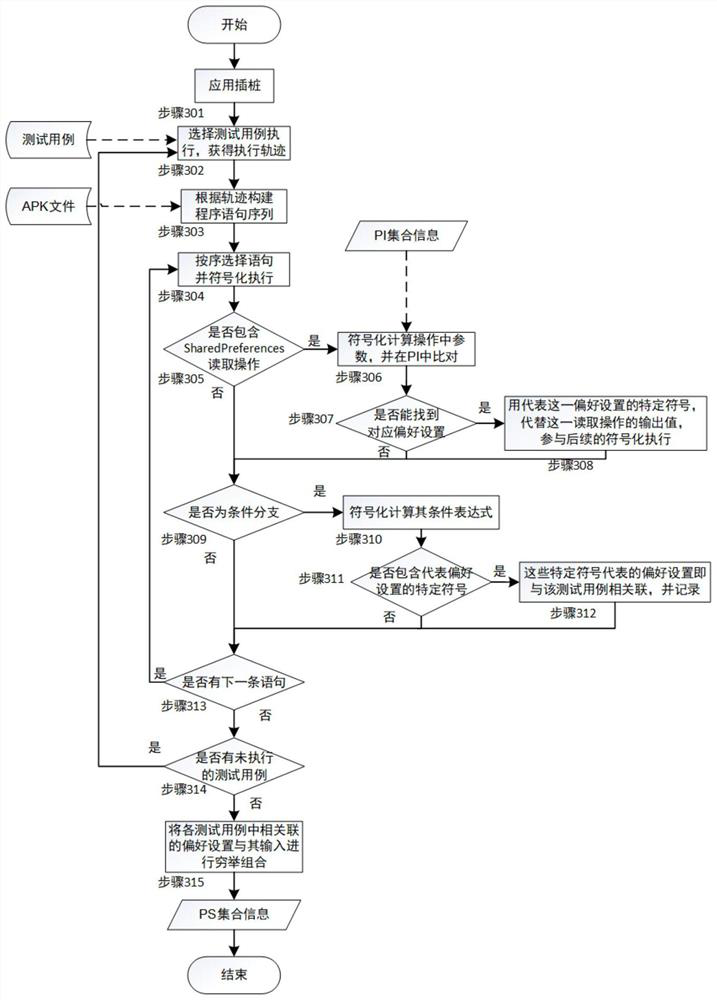
Preference setting-oriented Android application testing method
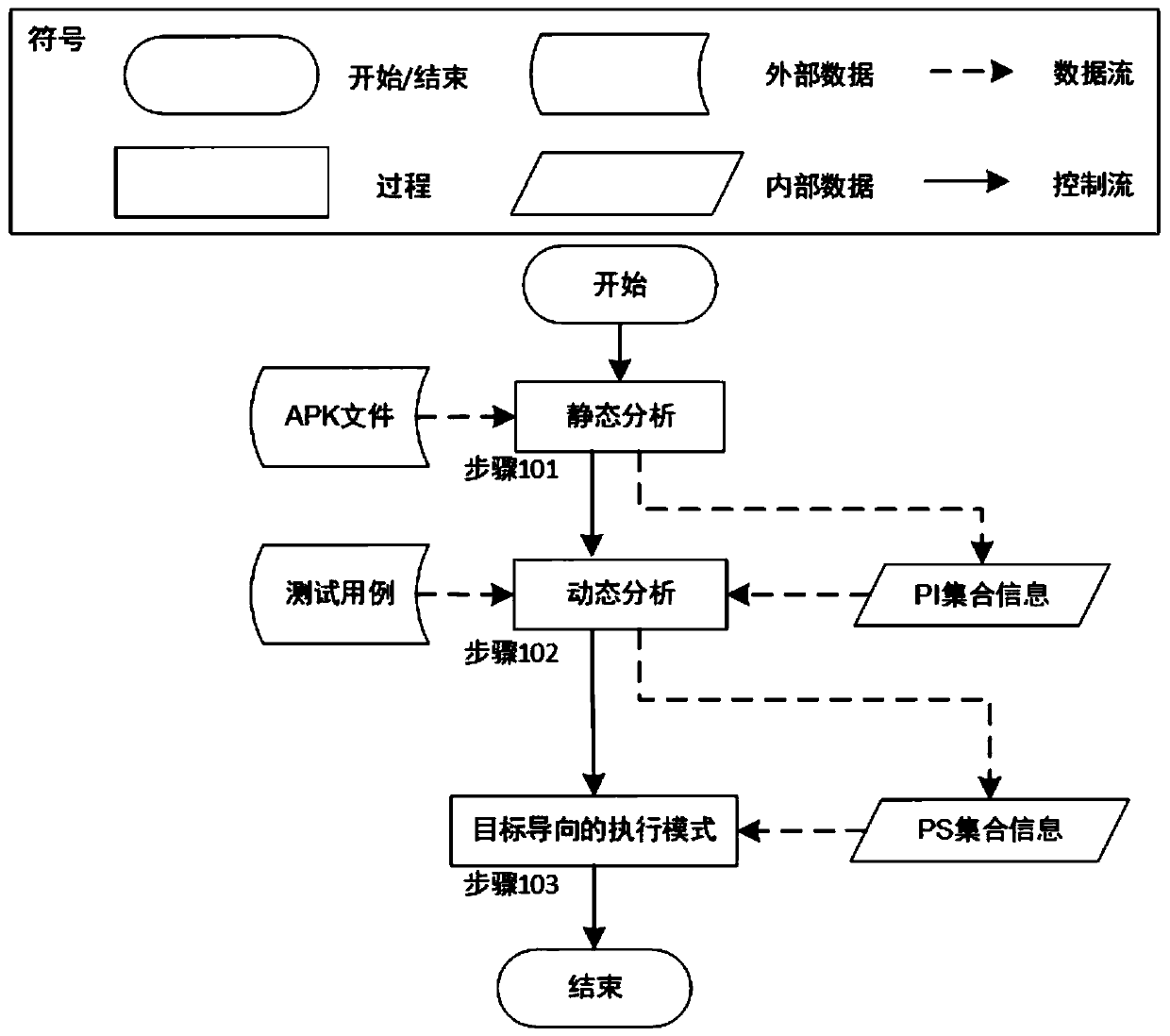
ActiveCN110209593AReduce testingReduce testing costsSoftware testing/debuggingGreedy algorithmDynamic program analysis
The invention provides a preference setting-oriented Android application testing method. The method comprises the following steps: firstly, performing static program analysis on an executable file ofan application to be tested to obtain all preference settings defined in the application and attributes thereof; and then, on the existing test cases, obtaining relevant preference settings in the test cases in a dynamic program analysis manner. For each test case, a combination of all related preference settings and its possible inputs can be tested to implement a preference setting-oriented test. Finally, in order to reduce the cost of the test, the invention provides a target-oriented execution mode, which divides the code of the test case into basic blocks, and combines the basic blocks with the input of the preference settings related thereto as the test target. According to the greedy algorithm, the combination of the test case covering the most test target and the preference settingis selected for testing, so that the repeated test of the preference setting input combination under each test case is reduced, and the test cost is greatly reduced.
Owner:NANJING UNIV
Differential static program analysis
ActiveUS8935680B2Error detection/correctionReverse engineeringHigh level analysisTheoretical computer science
Owner:INT BUSINESS MASCH CORP
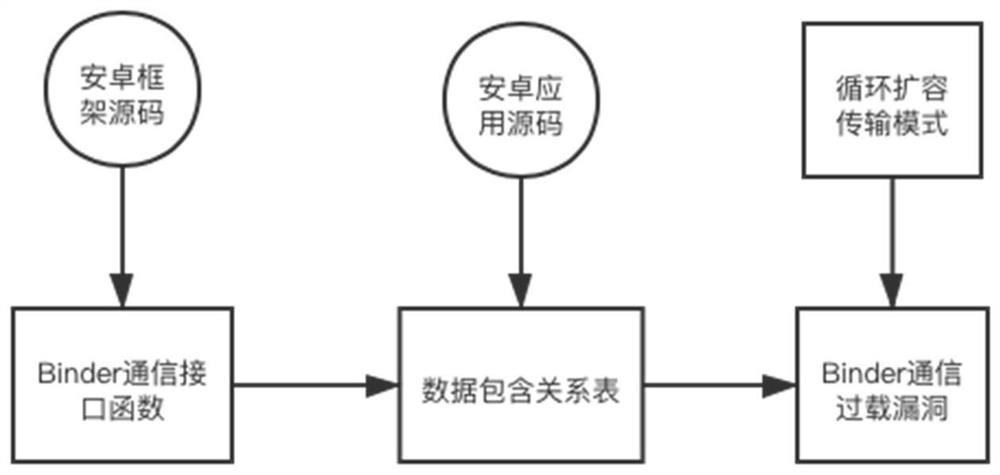
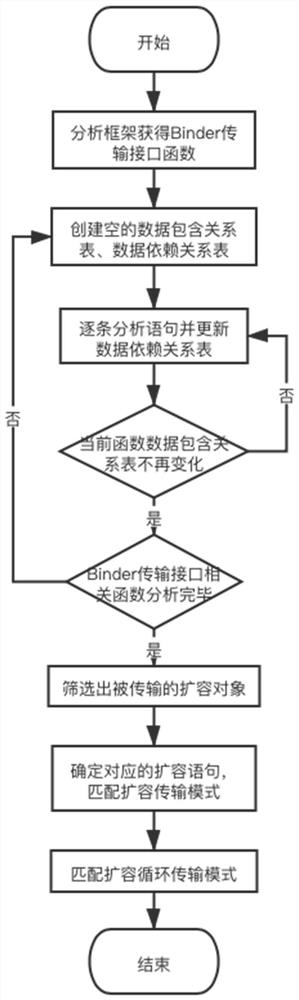
Binder communication overload vulnerability detection method based on static analysis
The invention discloses a static analysis-based Android application Binder communication overload vulnerability detection method, which comprises the following steps of: analyzing an Android framework source code to establish a function call graph, and based on transfer function transact forward analysis, determining a Binder communication interface function exposed by an Android framework; carrying out static analysis on Android application codes, and establishing a data inclusion relation table of a single function through a context-insensitive, flow-sensitive and path-insensitive inter-function data flow analysis technology; selecting functions related to a Binder communication interface function to establish an application data inclusion relation general table; based on the expansion transmission mode, searching an expansion transmission object conforming to the mode, analyzing an expansion statement of the expansion transmission object to judge whether the circulation condition is met or not, and obtaining the Binder communication overload vulnerability conforming to the circulation expansion transmission mode through detection. According to the method, a static program analysis means is adopted, the transmission object is determined by establishing the data inclusion relation of the whole application, and the technical effect of detecting the Binder communication overload vulnerability is achieved.
Owner:NANJING UNIV
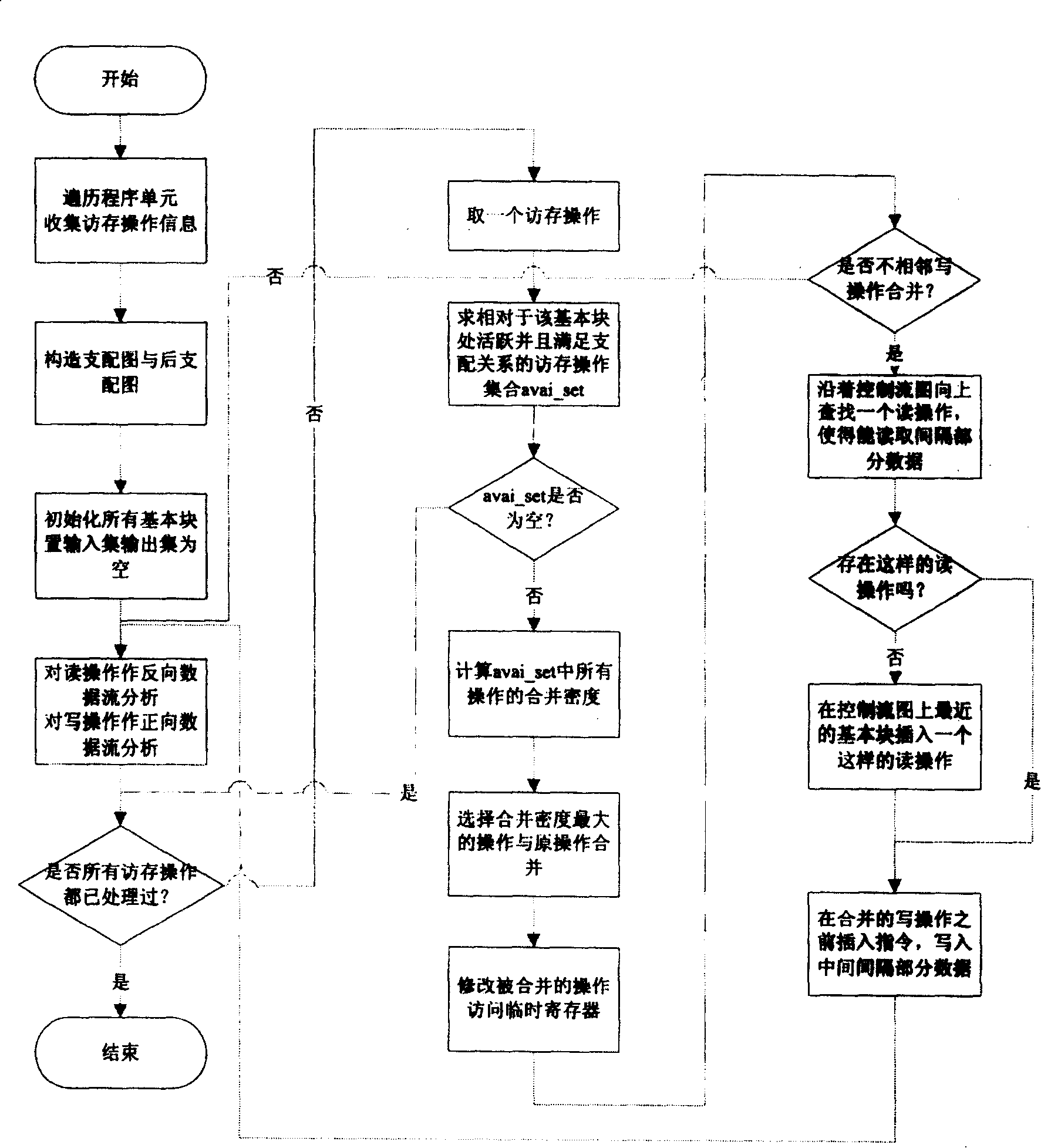
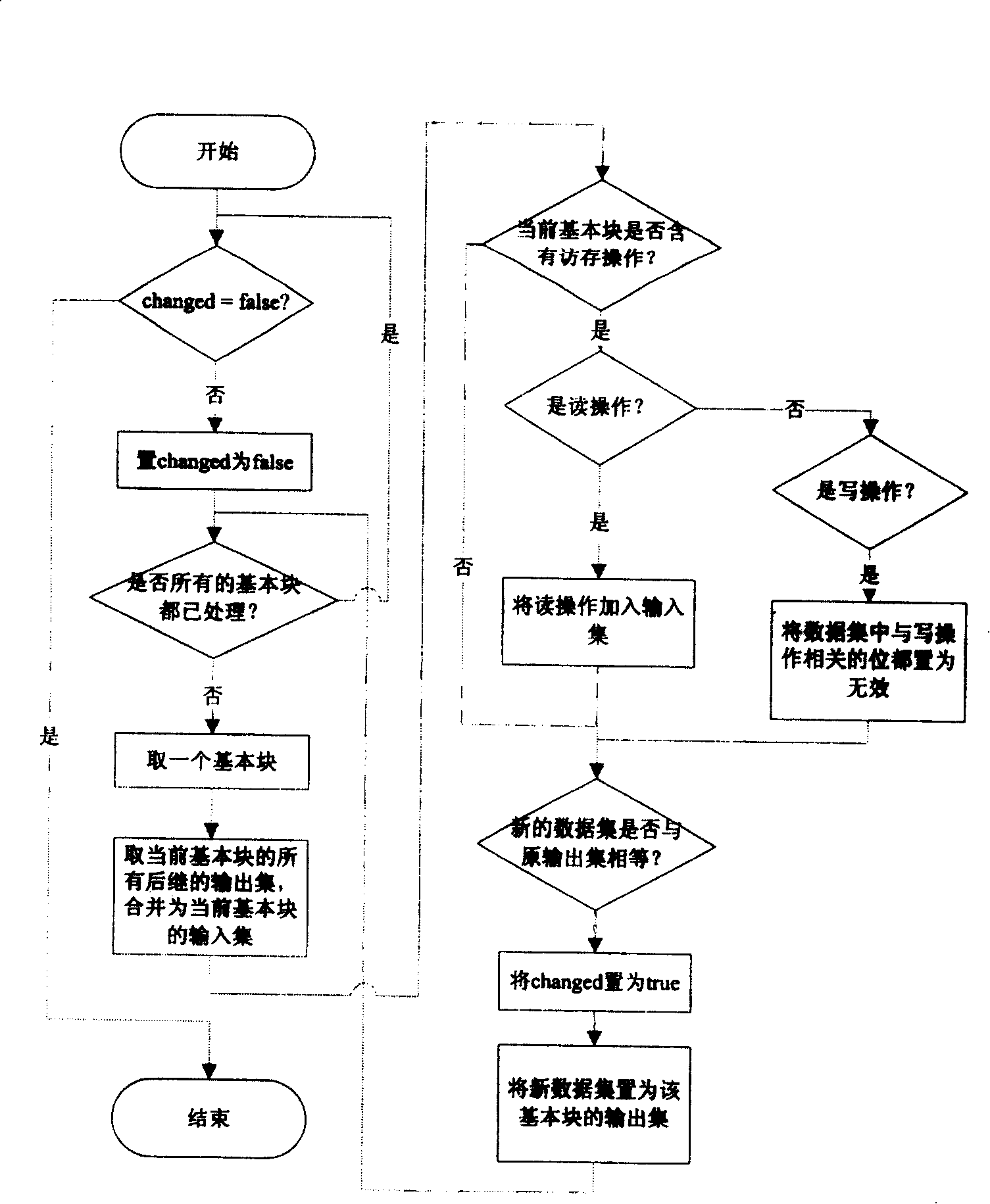
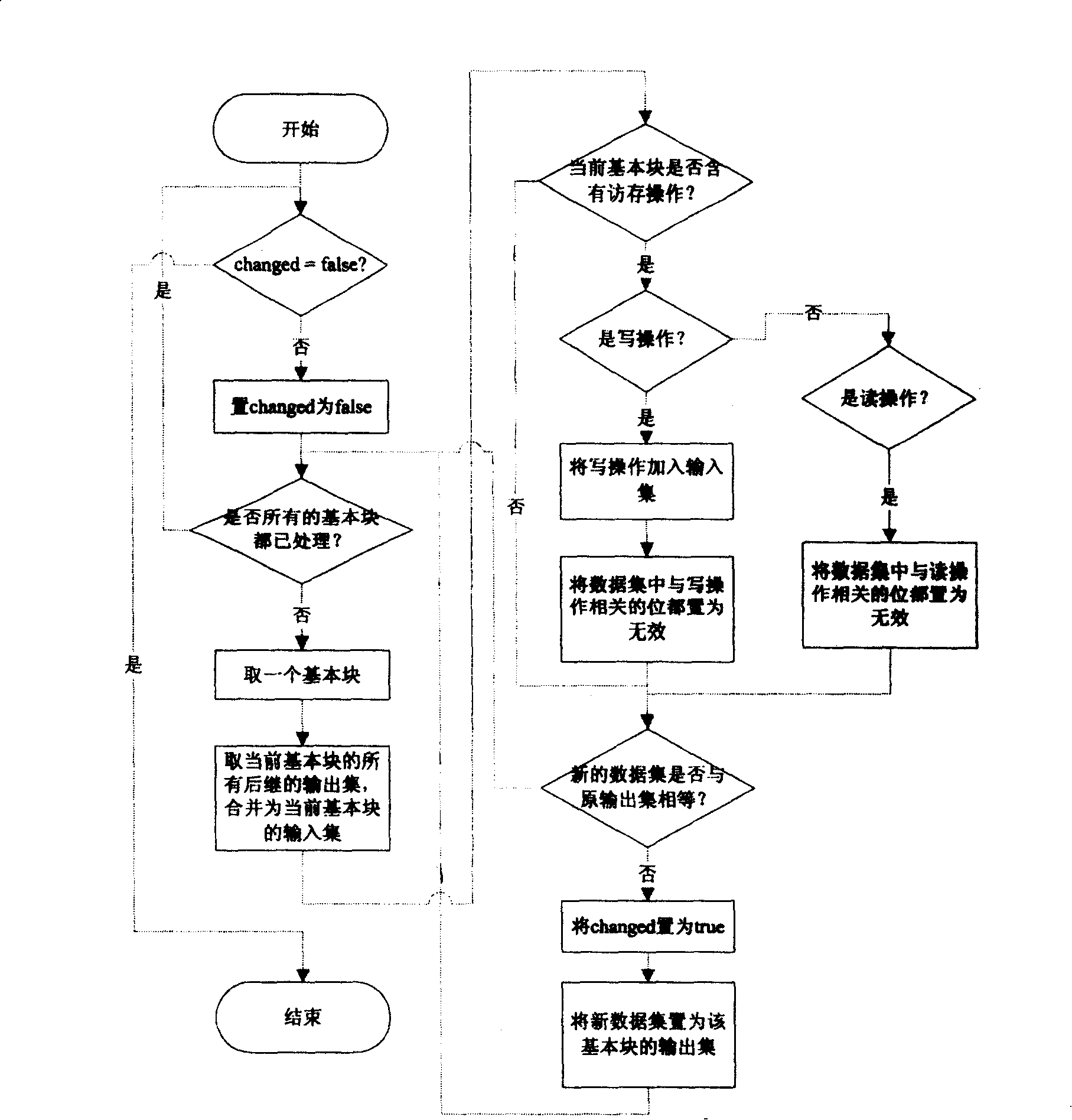
Combination and optimization methods of access and storage based on analysis of data stream
InactiveCN100390738CAccurate and effective optimizationVersatilityProgram controlMemory systemsData streamProcessor register
This invention provides one visit merge and optimization method based on data flow analysis, which merges two or more visit orders into one multi-bit visit order of adjacent address through total visit memory information for data flow analysis. The merged visit data is in register or local memory, the original visit memory order is taken place of register or local memory direct visit.
Owner:G CLOUD TECH
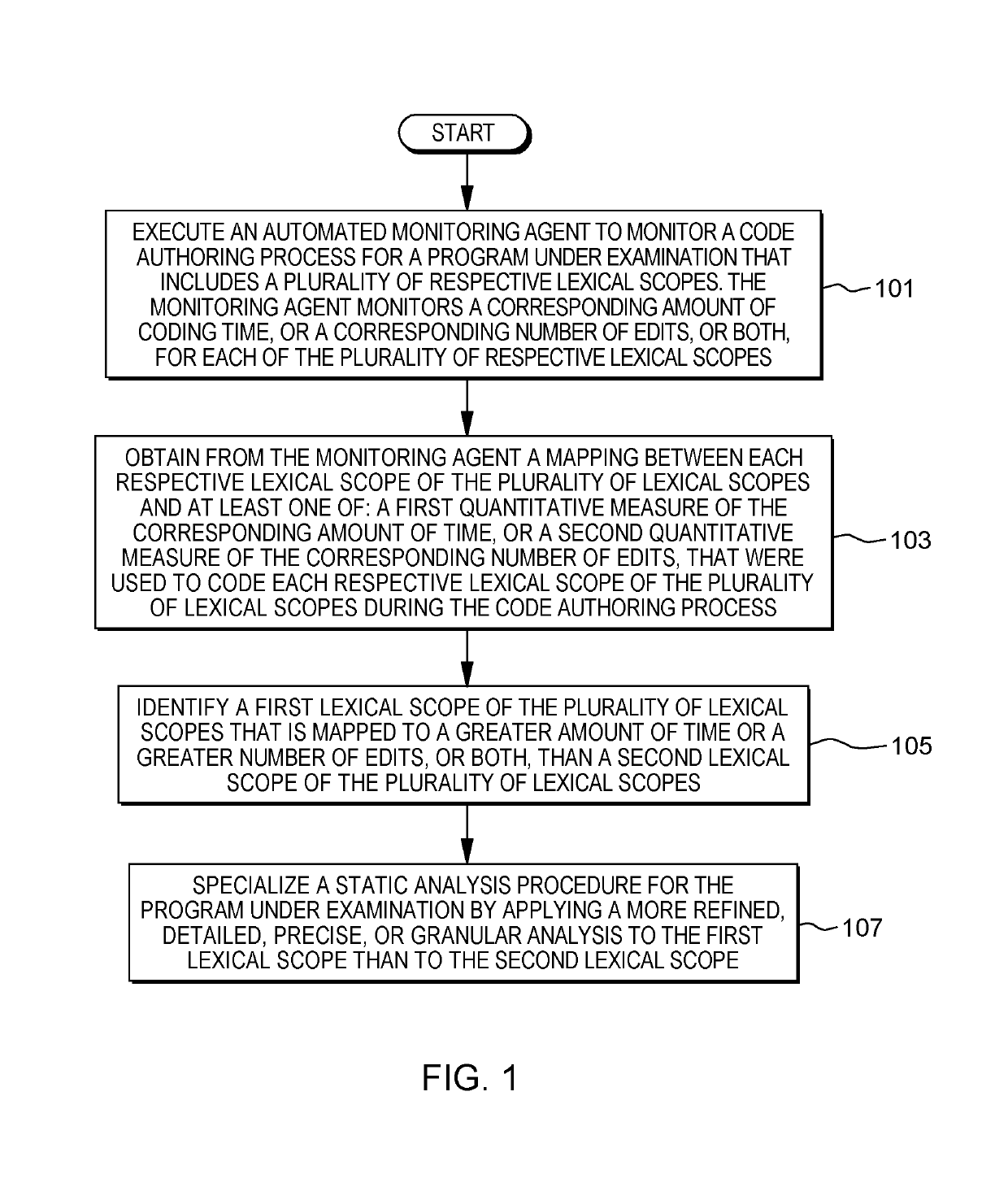
Providing specialization for static program analysis using coding hints
Providing specialization for a static program analysis procedure by executing an automated agent to monitor a code authoring process for a program under examination that includes a plurality of respective lexical scopes. The agent monitors a corresponding amount of coding time, or a corresponding number of edits, for each of the plurality of respective lexical scopes. A mapping associates each of the plurality of respective lexical scopes with a first quantitative measure of the corresponding amount of time, or a second quantitative measure of the corresponding number of edits, that were used to code each of the plurality of respective lexical scopes. The static analysis procedure is specialized by applying a more refined, detailed, precise, or granular analysis to a first lexical scope that is mapped to a greater amount of time or a greater number of edits than a second lexical scope.
Owner:IBM CORP
Hybrid program analysis
ActiveUS10275238B2Reverse engineeringSoftware testing/debuggingDynamic program analysisApplication software
A hybrid program analysis method includes initiating a static program analysis of an application, generating, by a static program analyzer, a query to a dynamic program analyzer upon determining a code construct of the application requiring dynamic analysis, resolving, by the dynamic program analyzer, the query into a set of arguments with which to invoke the code construct of the application, generating, by the dynamic program analyzer, the set of arguments, invoking, by the dynamic program analyzer, the code construct of the application using set of arguments, answering, by the dynamic program analyzer, the query, and continuing the static program analysis of the application.
Owner:INT BUSINESS MASCH CORP
An application vulnerability detection and analysis method based on code base security protocol in Android application
ActiveCN105022958BPrevent the risk of security incidentsPlatform integrity maintainanceProgramming languageSecurity specification
Owner:FUDAN UNIV
A Preference-Oriented Android Application Testing Method
ActiveCN110209593BReduce testingReduce testing costsSoftware testing/debuggingGreedy algorithmAndroid app
The invention proposes a preference-setting-oriented Android application testing method. Firstly, static program analysis is performed on the executable file of the application under test to obtain all preferences and attributes defined in the application. Then, on the existing test cases, the associated preference settings in each test case are obtained through dynamic program analysis. For each test case, all combinations of relevant preferences and their possible inputs can be tested to implement preference-oriented testing. Finally, in order to reduce the cost of this test, the present invention provides a goal-oriented execution mode, which divides the code of the test case into basic blocks, and uses the combination of basic blocks and their related preferences as the test target. According to the greedy algorithm, the present invention selects the combination of test cases and preference settings covering the most test targets for testing, thereby reducing the repeated testing of preference setting input combinations under each test case and greatly reducing the test cost.
Owner:NANJING UNIV
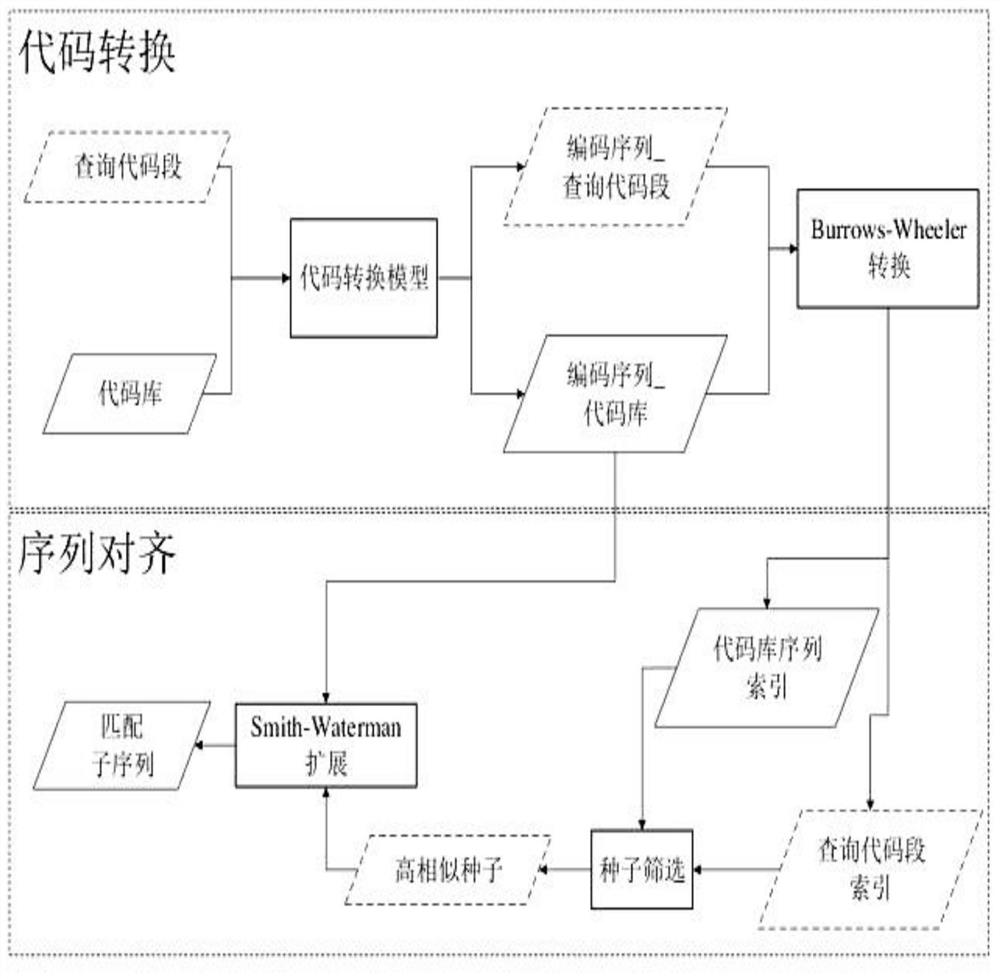
Source code fragment pairwise comparison method based on coding sequence representation
The invention discloses a source code fragment pairing comparison method based on coded sequence representation, and belongs to the technical field of computer programs. The method includes: using a coded sequence source code representation method based on static program analysis to convert a source code text into coded sequence representation; performing data processing on the coded sequence of the source code segment by using Burrows-Wheeler conversion to obtain an index of the coded sequence; through seed screening, finding out subsequence alignment seeds with high similarity from indexes of the coded sequences; using a Smith-Waterman algorithm to take the high-similarity seeds as initial positions of subsequence alignment, and expanding subsequences with a certain similarity thresholdvalue in subsequent sequences; positioning the high-similarity part between the source code fragments according to the source code line number information corresponding to the coding sequence. The technical problems that cross-granularity similarity matching cannot be supported and high-similarity fragment positioning is not accurate enough are solved, cross-granularity source code similarity comparison can be supported, and source code texts which do not need to be compared are required to have the same granularity.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
Synchronous optimization method and synchronous optimization equipment
InactiveCN101630268BIncrease flexibilityImprove scalabilityProgram controlMemory systemsParallel computingStatic program analysis
The invention provides a synchronous optimization method and synchronous optimization equipment. The method comprises the following steps: carrying out static program analysis on a compiled method, confirming a synchronous method calling point without carrying out synchronous operation on a synchronous object in the compiled method according to an analysis result and marking the synchronous method calling point; compiling the called synchronous method according to the marked synchronous method calling point to generate a local code allowing to execute the synchronous operation on the synchronous object of the synchronous method; and executing the local code according to the marked synchronous method. The synchronous optimization method and the synchronous optimization equipment have high flexibility and favorable expandability.
Owner:UNIV OF SCI & TECH OF CHINA
Program source code slice recombination-based software dynamic update hot patch synthesis method
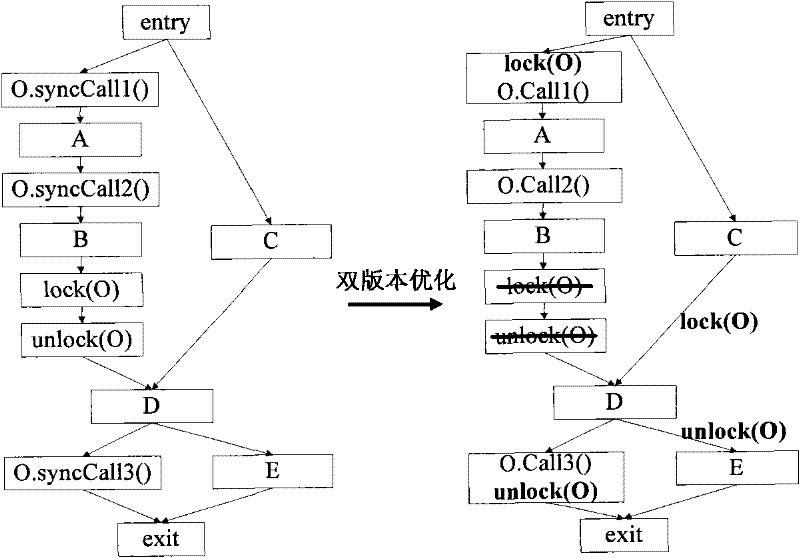
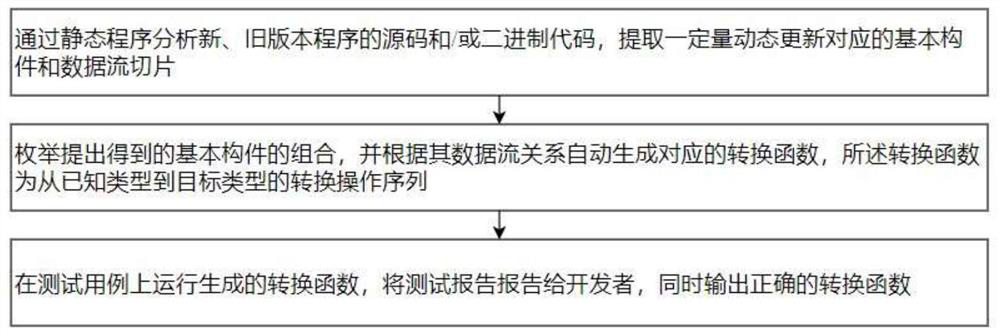
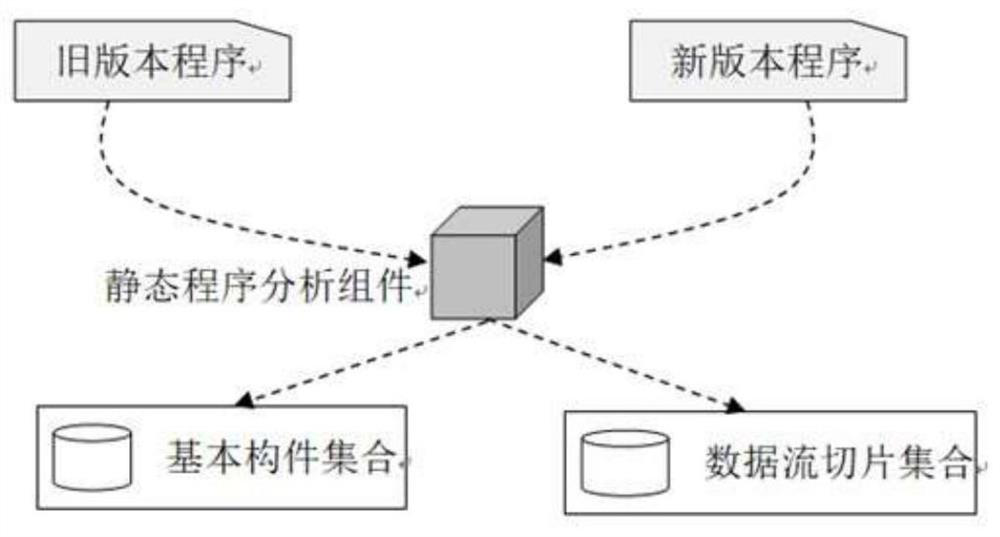
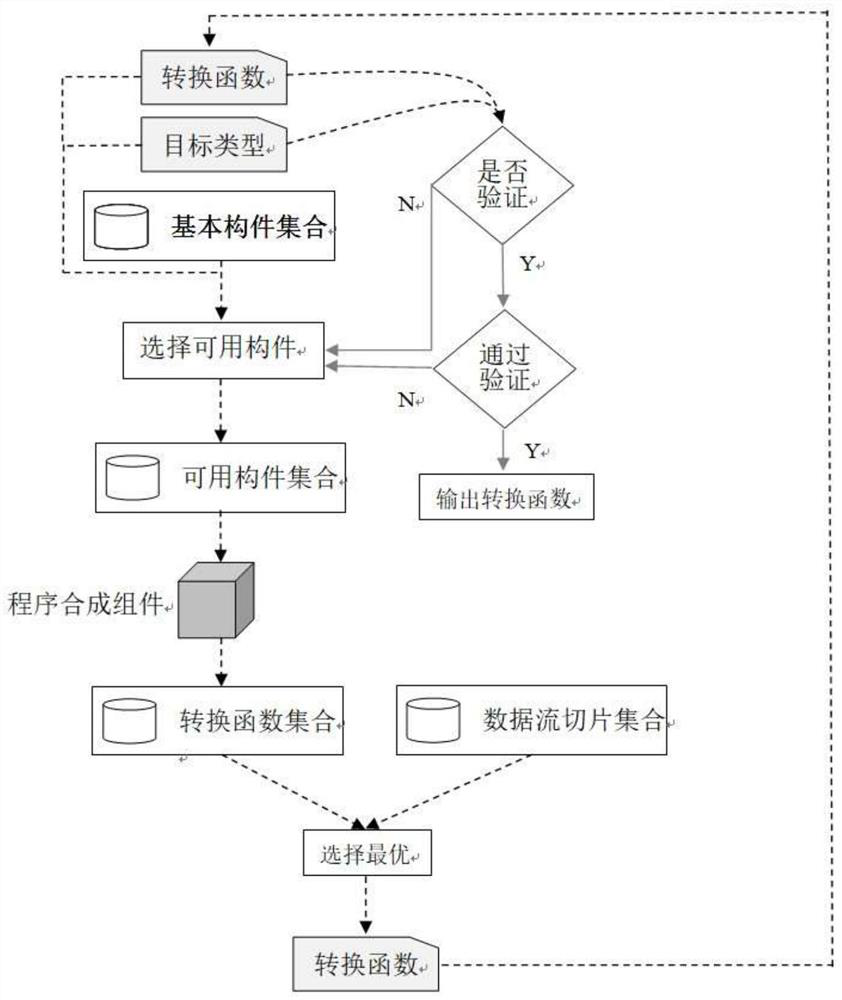
ActiveCN112764788AReduce labor burdenQuick discoveryVersion controlCode refactoringData streamAlgorithm
The invention discloses a program source code slice recombination-based software dynamic update hot patch synthesis method, which comprises the following steps of: analyzing source codes and / or binary codes of a new version program and an old version program through a static program, and extracting a certain amount of basic components and data stream slices related to dynamic update; enumerating the combination of the obtained basic components, and automatically generating a corresponding transfer function according to the data flow relationship; and running the generated transfer function on the test case, and outputting a correct transfer function. According to the method, new and old version program codes can be automatically analyzed, and basic components and data stream slices for constructing the conversion function are extracted, so that the object state conversion function is automatically synthesized by utilizing the basic components and the data stream slices, developers are helped, and the labor burden is greatly reduced.
Owner:NANJING UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com