Combination and optimization methods of access and storage based on analysis of data stream
A technology of data flow analysis and optimization method, which is applied in the field of general-purpose and embedded compiler memory access optimization, can solve the problems of lack of accurate description, etc., and achieve the effect of easy implementation, good optimization performance, and reduced bandwidth requirements
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
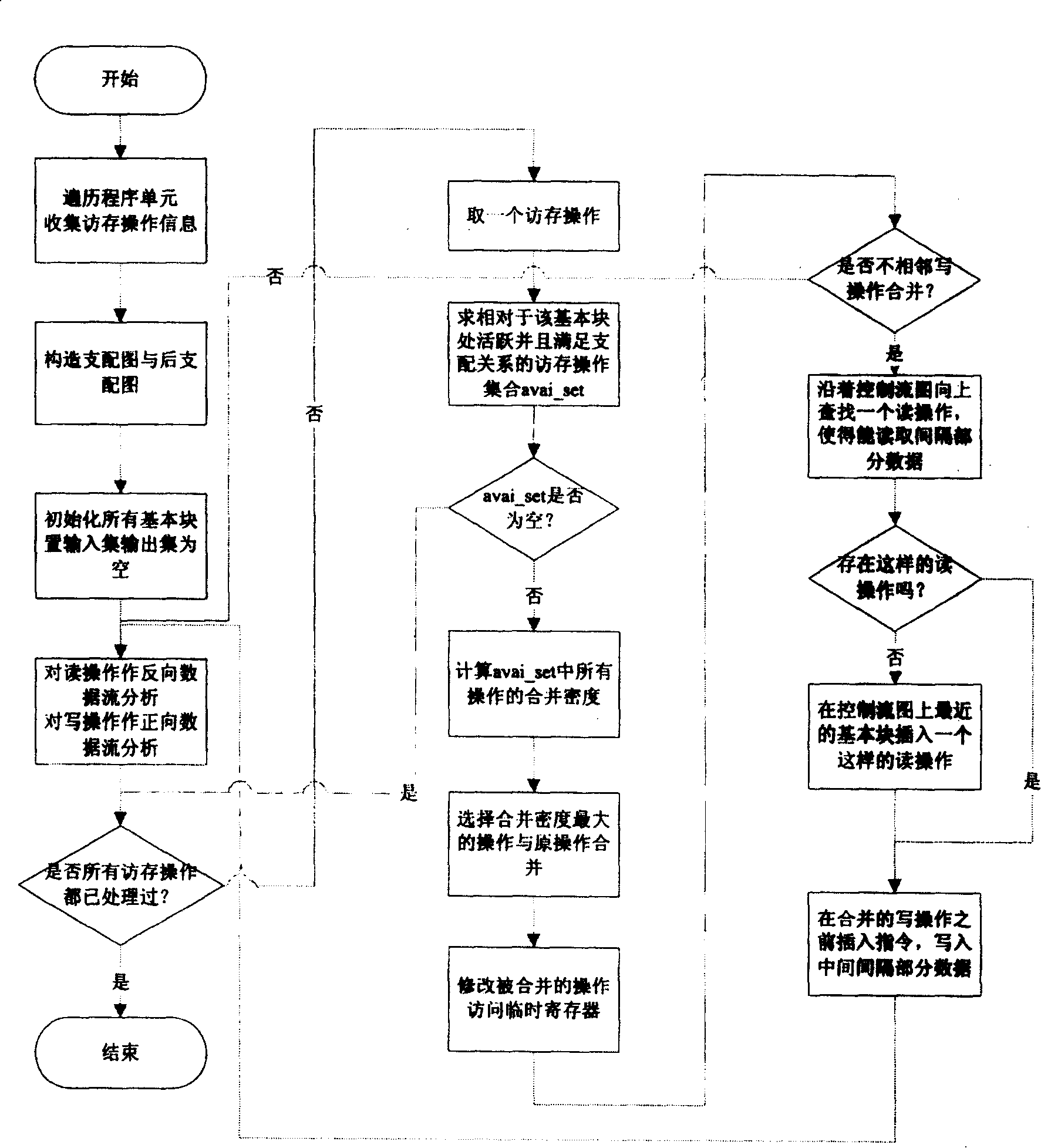
[0073] Example 1: It is assumed that each basic block contains at most one read operation or write operation, that is, there is at most one memory access operation. Let Out(x), Out(y) be the output data sets of the successor block x and the successor block y of the basic block i respectively, and In(i) be the input data set of the basic block i. There are two memory access operations in the output data set Out(x) of the successor block x, namely r(l, 20, 8) and r(m, 32, 4), and in the output data set Out(x) of the successor block y There are two memory access operations in y), namely r(l, 16, 8) and r(q, 64, 32), where r(l, 20, 8) and r(l, 16, 8) represent For the two read operations implemented in the basic block l, since the basic block l can only have one memory access operation, the two read operations must be the same read operation and the same element. Therefore, an AND operation is performed on the data areas of the two operations. In the read operation r(1, 20, 8), ...
example 2
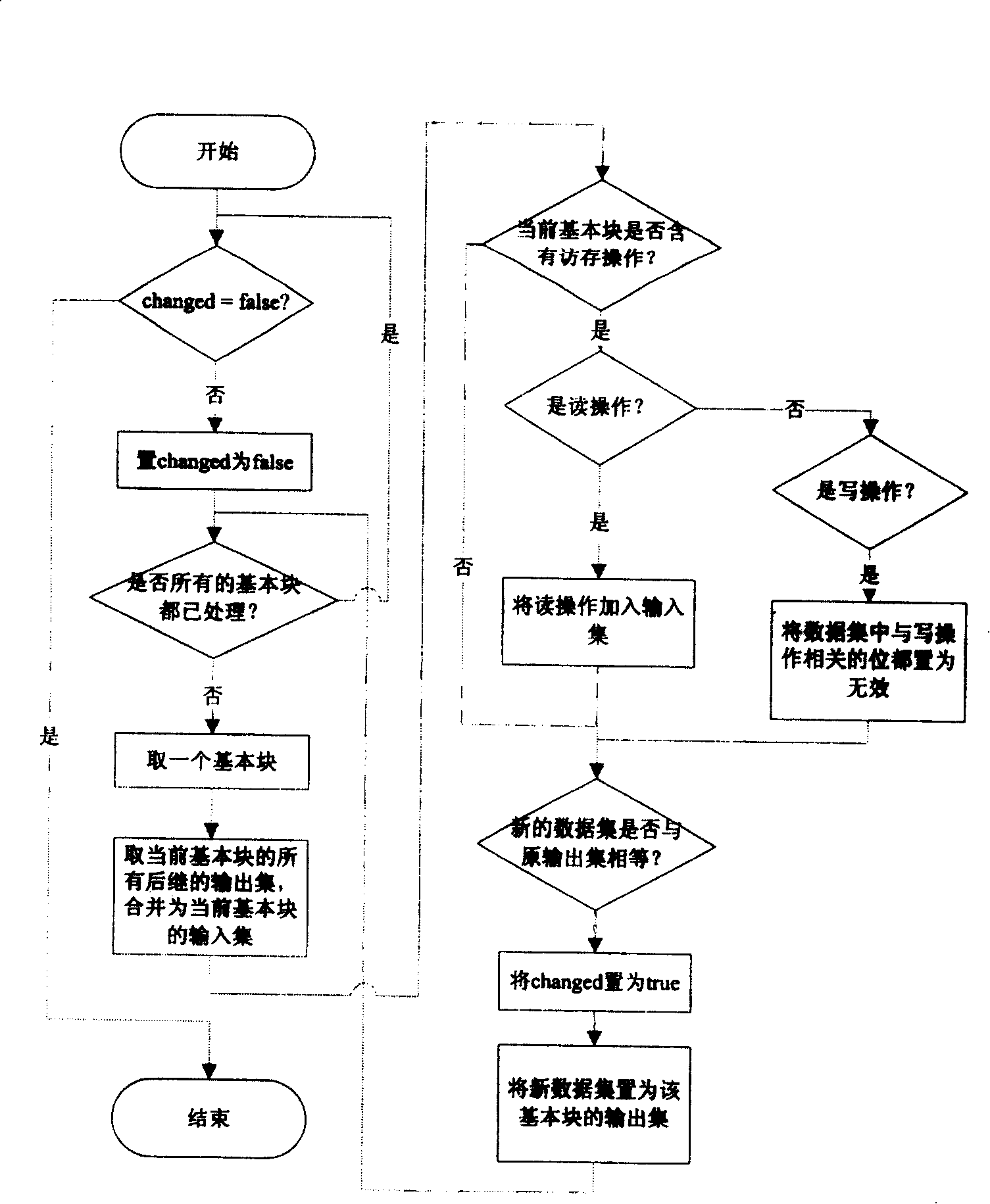
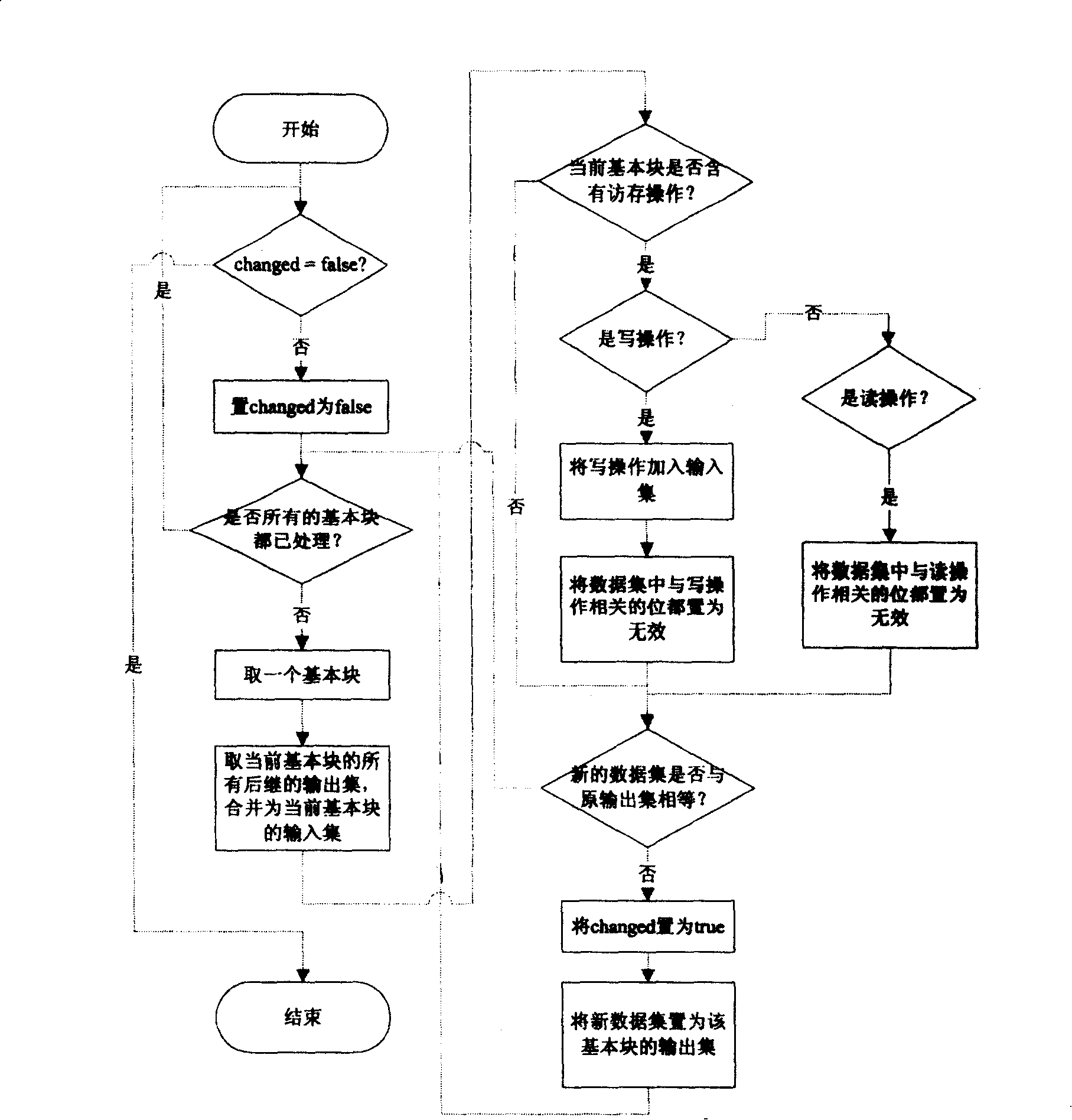
[0078]Example 2: Assuming that basic block i contains write operation w(i, 16, 8), the input data set of basic block i is {r(l, 8, 16), r(m, 20, 24)}, since the The write operation resets the data of 16 to 24 bits, so all relevant data bits in the input data set should be set as invalid. The data bits in r(l, 8, 16) are from 8 to 24 bits, and r(m , 20, 24) the data bits are from 20 to 44 bits, and the write operation resets the data of 16 to 24 bits. Therefore, the effective bits of the data in r (1, 8, 16) are from 8 to 16 bits , the effective bits of the data in r(m, 20, 24) are from 24 to 44 bits, and the changed input data set is finally {r(l, 8, 8), r(m, 24, 20)}. The specific implementation method of setting the data bits related to the write operation as invalid is to first invert the valid data bits of the write operation, and then perform an "AND" operation with the data bits of all operations in the data set, where valid data is represented by 1, and invalid The dat...
example 3
[0094] Example 3: For the read operation r(i, x, s) at the basic block i, suppose any read operation r(j, y, t) is located at the basic block j, if the input set in(i ) exists r(j, y', t') and y=y', t=t', then r(j, y, t) is active at basic block i, and it can be compared with r(i, x , s) merge. Construct a set avai_set(i), and all read operations that can be combined with r(i, x, s) are elements in the set. The same process can be done for the write operation at the basic block i.
[0095] Step 60, judging whether the set used to save the active memory access operation is empty, if it is empty, then jump to step 140, otherwise, execute the next step;
[0096] Step 70 , for all elements in the set obtained in step 50 , respectively calculate the merge density between the memory access operation corresponding to each element and the current memory access operation. The method for calculating the combined density is to add the data width of the first memory access operation to...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com