Binder communication overload vulnerability detection method based on static analysis
A static analysis and detection method technology, applied in the direction of instruments, electrical digital data processing, platform integrity maintenance, etc., can solve problems such as overload loopholes, inability to locate Binder transmission objects in advance, and no customized test cases
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
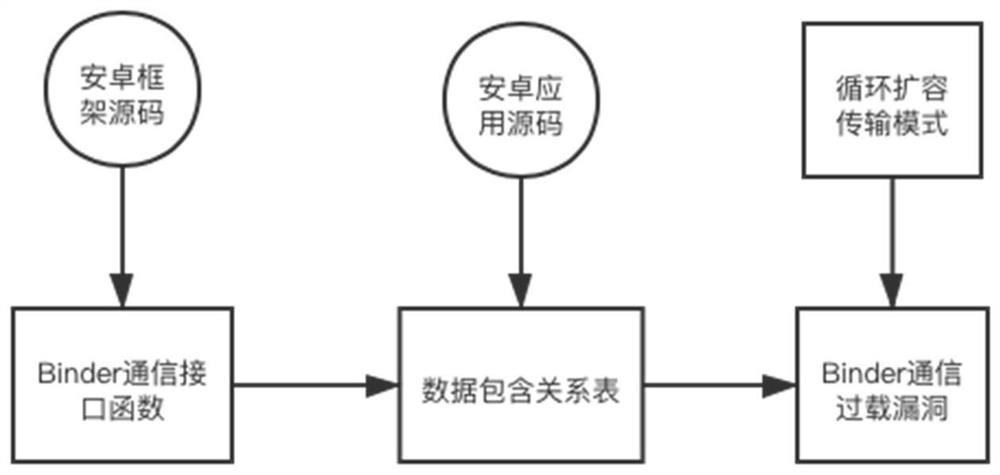
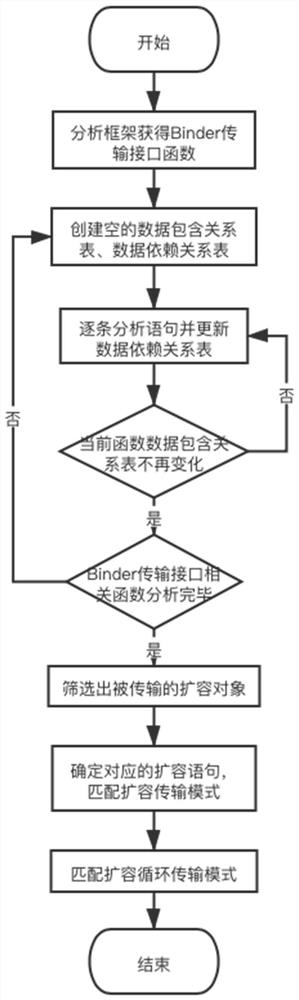
[0051] figure 1 It is a schematic diagram of the frame logic of the static analysis-based Android application Binder communication overload vulnerability detection method according to Embodiment 1 of the present invention. figure 2 It is a schematic flowchart of a method for detecting a communication overload vulnerability of an Android application Binder based on static analysis in Embodiment 1 of the present invention. This embodiment can be used to detect Binder communication overload vulnerabilities through devices such as servers. The method can be performed by a static analysis-based Android application Binder communication overload vulnerability detection device. The device can use software and / or hardware. Realized, and can be integrated in electronic equipment, such as integrated server equipment.
[0052] see figure 1 with figure 2 , the detection method specifically includes:
[0053] S1. Analyze the source code of the Android framework to establish a function...
Embodiment 2
[0068] Embodiment 2 of the present invention takes the real application LeakCanary in the application market as an example, combining figure 2 The specific algorithm flow chart of the method in Nakamoto illustrates how to use the Android application Binder communication overload vulnerability detection method based on static program analysis to detect the verified and repaired Binder communication overload vulnerability ( Github Issue 1646).
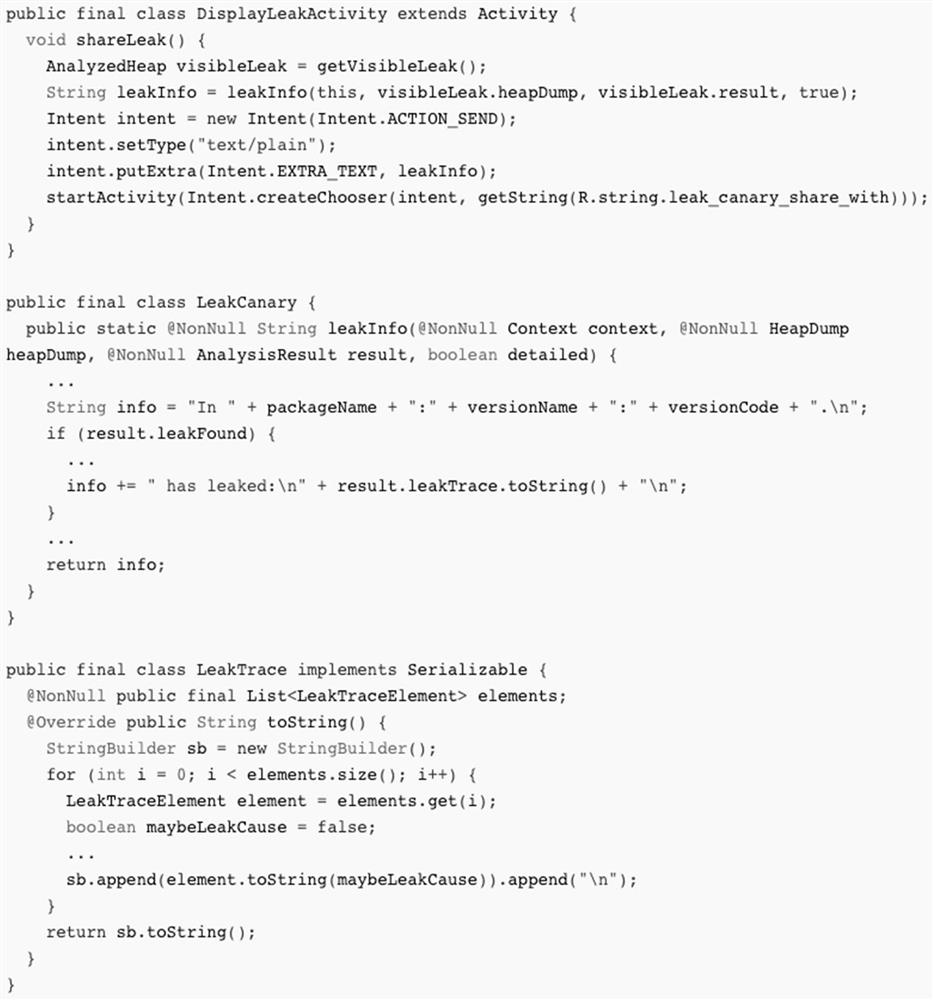
[0069] image 3 shows the source code of the program related to the Binder communication overload vulnerability in LeakCanary, mainly including three functions DisplayLeakActivity.shareLeak, LeakCanary.leakInfo and LeakTrace.toString. The following will explain how to detect this Binder communication one by one in combination with the steps in the rights specification Overload bug.
[0070] In step 1, it is necessary to determine the Binder transfer interface function provided by the Android framework. By analyzing the source code of ...
Embodiment 3
[0078] The embodiment of the present application provides a static analysis-based detection device for an Android application Binder communication overload vulnerability, the detection device comprising:
[0079] The Binder communication interface function acquisition module is used to analyze the source code of the Android framework to establish a function call graph, and determine the Binder communication interface functions exposed by the Android framework based on the forward analysis of the transfer function transact.
[0080] The ContainerMap_app building block is used to statically analyze the Android application code. Starting from the Binder communication interface function used in the Android application, through the context-insensitive, flow-sensitive, and path-insensitive inter-function data flow analysis technology, the data flow analysis The iteration termination condition is that the ContainerMap does not change anymore, and the ContainerMap is established; selec...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com