An application vulnerability detection and analysis method based on code base security protocol in Android application
A technology of security protocols and application programs, applied in computer security devices, instruments, electronic digital data processing, etc., can solve problems such as difficulty in unified management, semantic misunderstanding, and scattered security protocols, and achieve the effect of preventing security risks.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
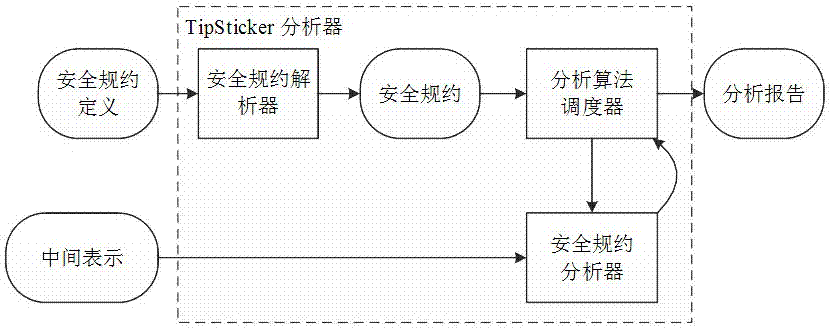
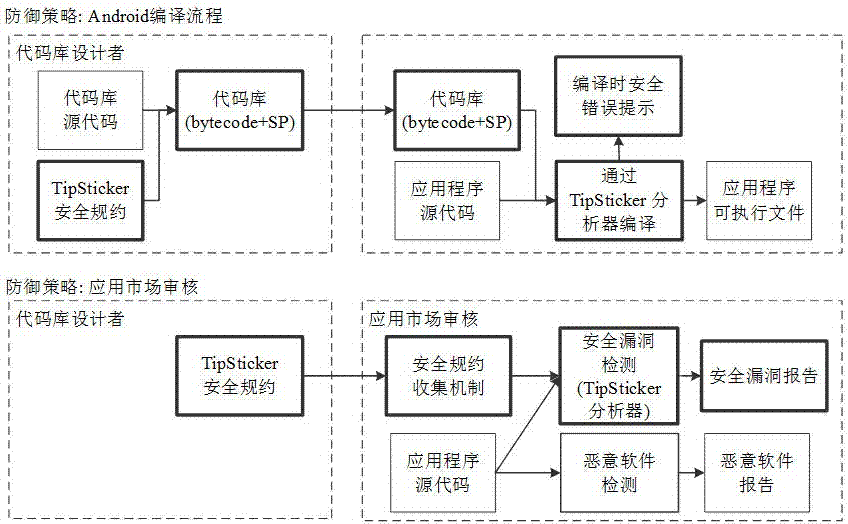
[0068] The present invention designs and implements the above-mentioned static analysis framework that can describe code base security regulations in a formalized rule language and perform automatic verification in applications. This section makes a detailed introduction to the specific implementation of the framework.
[0069] 1. Safety protocol model
[0070] The security protocol model designed by the present invention is described above. Under this model, the security specification is described in the form of a rule language, and the code base designer can directly package it into the code base. The rule language can describe the behavior that the application program should take when using the code library in a way that both the code library designer and the user can understand. Moreover, as a rule language, the static program analyzer can also understand its semantics by parsing the security regulations, so that the static program analyzer can detect the failure to compl...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com