Reconstruction attack method for biological template protection based on generative adversarial network
A biological template and network technology, applied in the field of biometrics, can solve the problem that the reconstructed image cannot meet the visual authenticity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0083] The present invention will be further described below in conjunction with specific examples, but the embodiments of the present invention are not limited thereto.
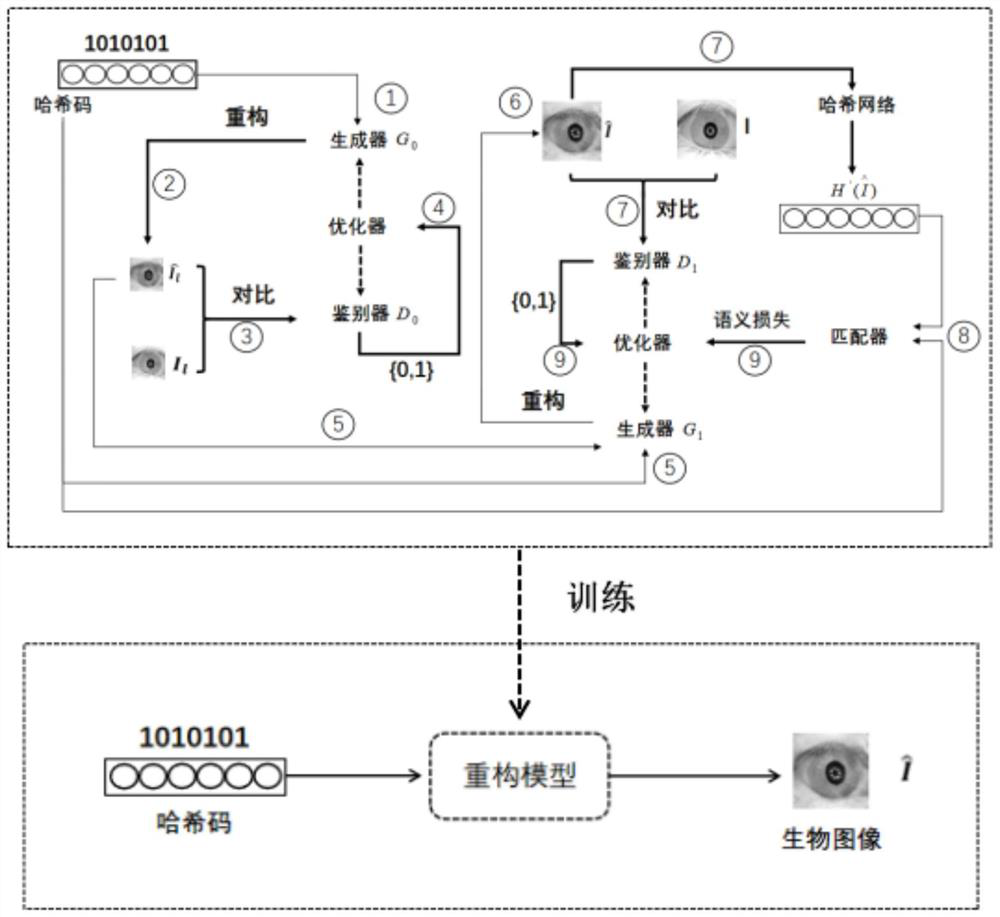
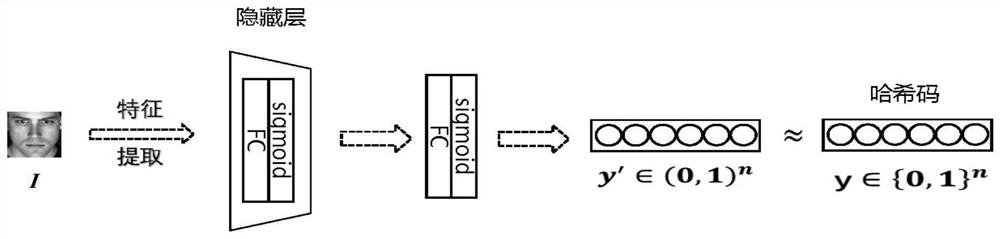
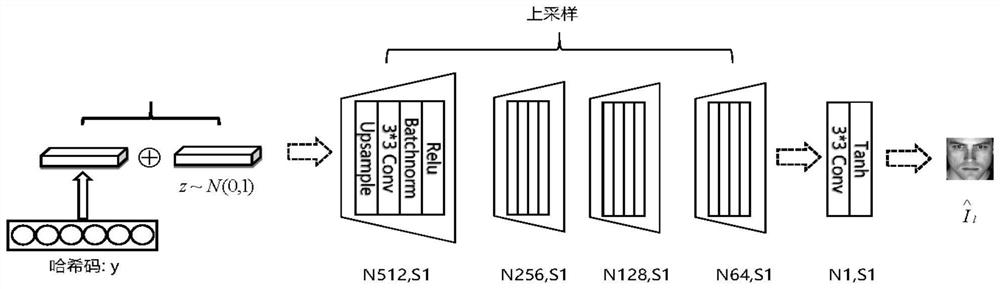
[0084] see Figure 1 to Figure 7 As shown, the reconstruction attack method for biological template protection based on generative confrontation network provided in this embodiment includes the following steps:
[0085] 1) Basic data processing, including image cropping, feature extraction, hash code generation, and training set and test set division.
[0086] Table 1 training set and test set
[0087]
[0088] The data set selected in this example is CMU PIE, which is 40,000 face images of 68 different individuals collected by researchers from the Computer Department of Carnegie Mellon University under different postures, expressions and lighting conditions. The different face images of 68 individuals below are used as the data set of this paper. Each individual contains 24 face images under different li...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com