Differential static program analysis
a static program and analysis method technology, applied in the field of static code analysis, can solve the problems of limiting the usability of commercial analysis tools, false reports, and high false reports of static analysis tools
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
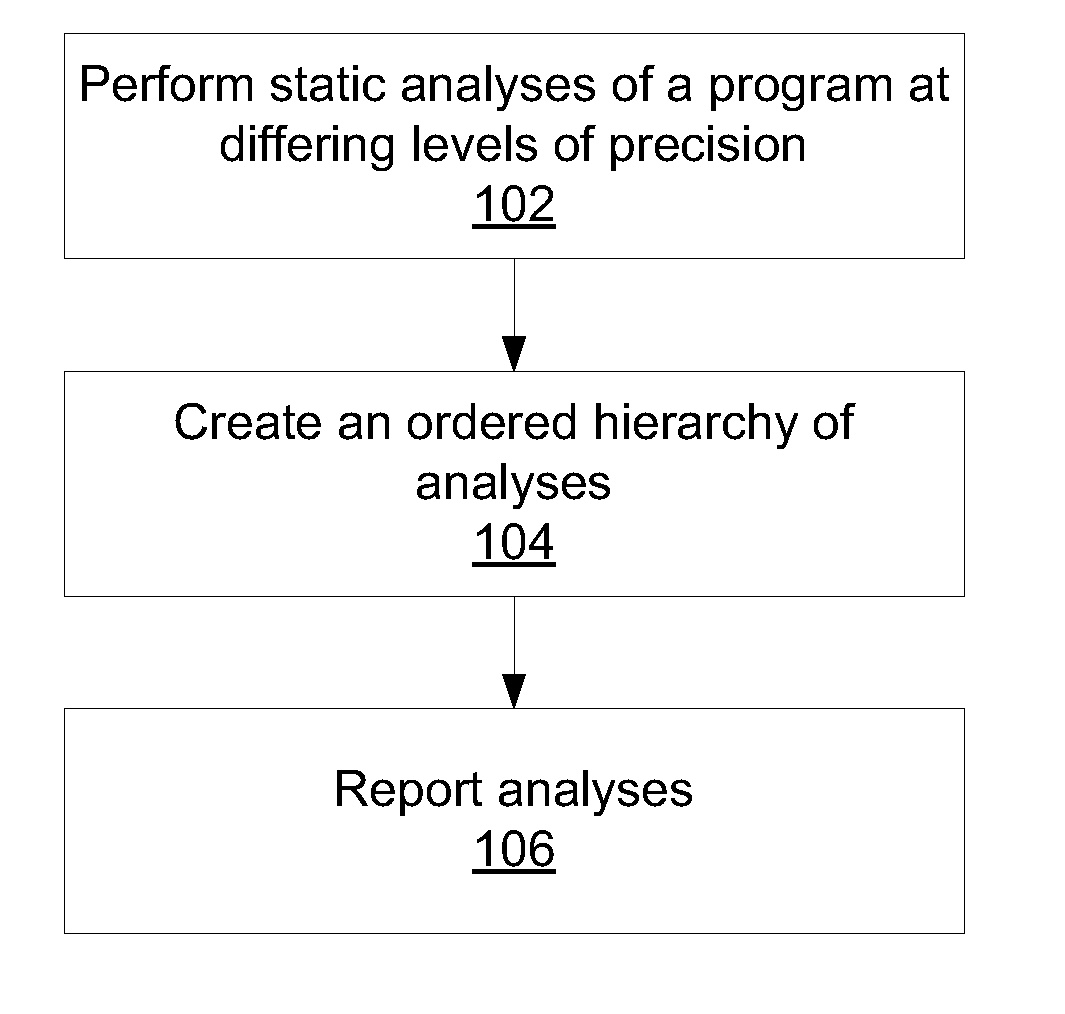
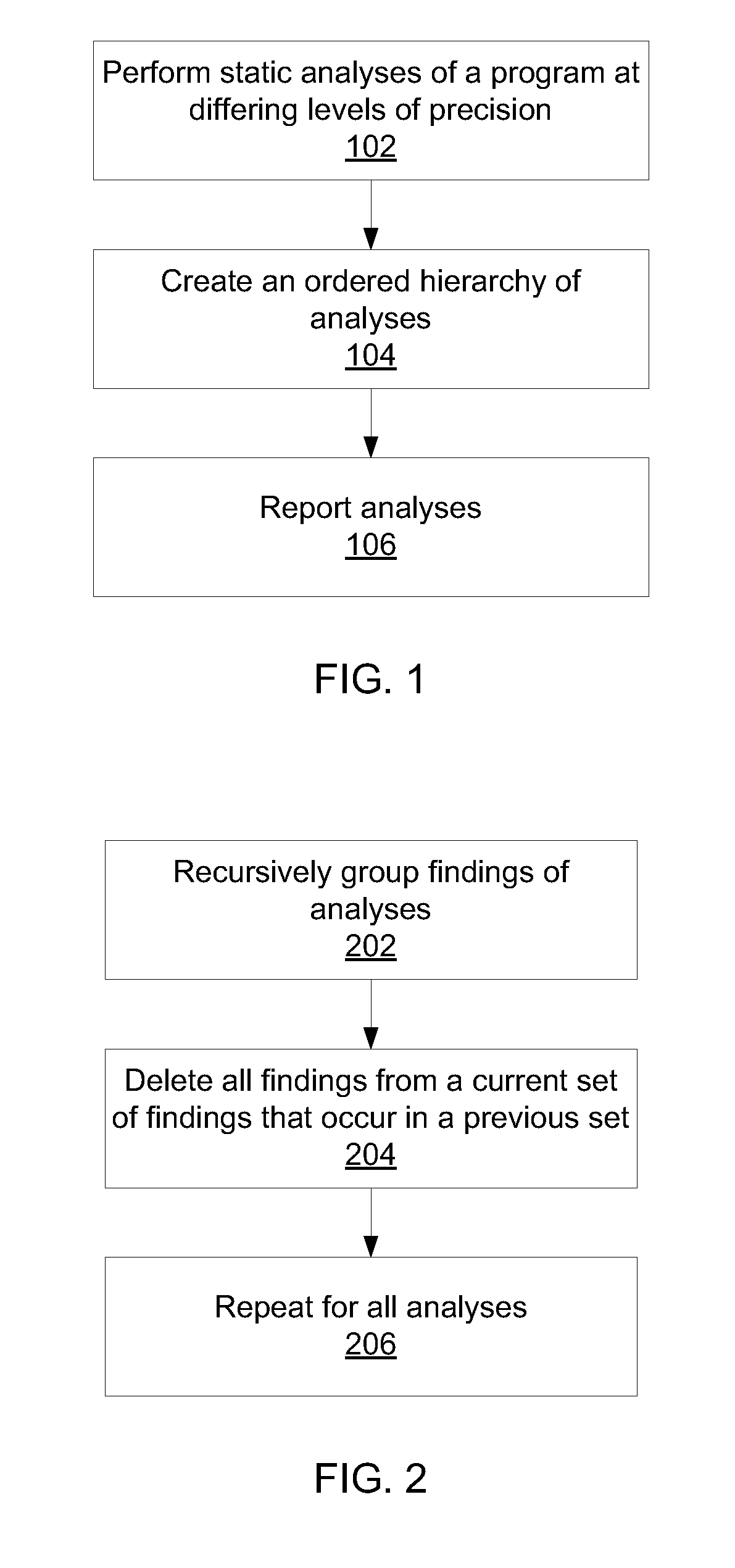
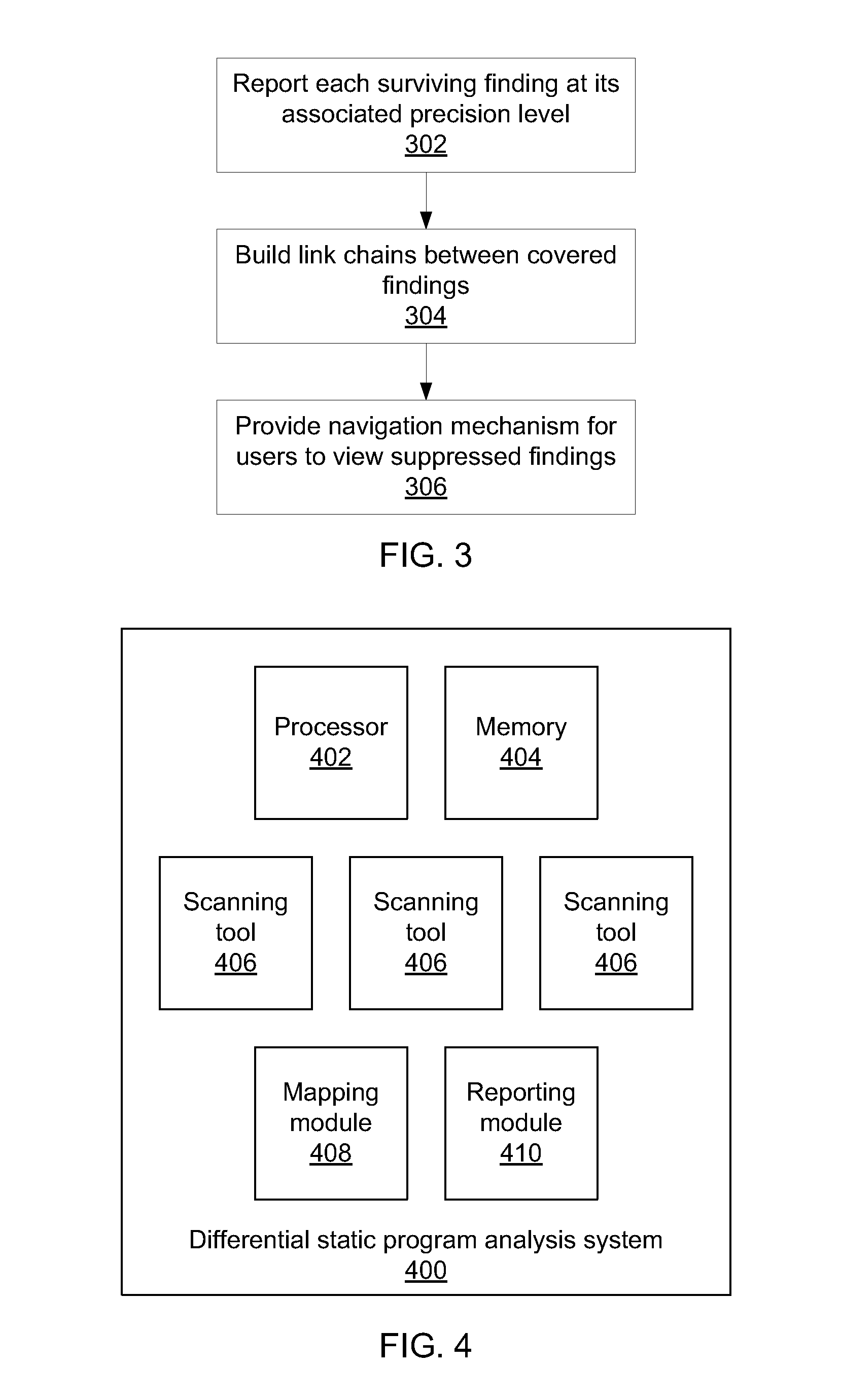
[0018]The present principles provide for a differential static analysis, where using multiple analyses of increasing granularity enables the reporting of fewer findings compared to using more fine-grained analyses. Moreover, each of the reported findings is reported at an intuitive level, making it easier for the analyst to take appropriate remediating action in response to discovered violations. By grouping together similar findings, the job of the human reviewer is made much simpler, as similar violations are listed in such a way as to make identifying root causes easier.
[0019]Static security analysis typically takes the form of taint analysis, where the analysis is parameterized by a set of security rules, each rule being a triple , where Src denotes source statements that read untrusted user inputs, San denotes downgrader statements that endorse untrusted data by validating and / or sanitizing it, and Snk denotes sink statements which perform security-sensitive operations. Given a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com