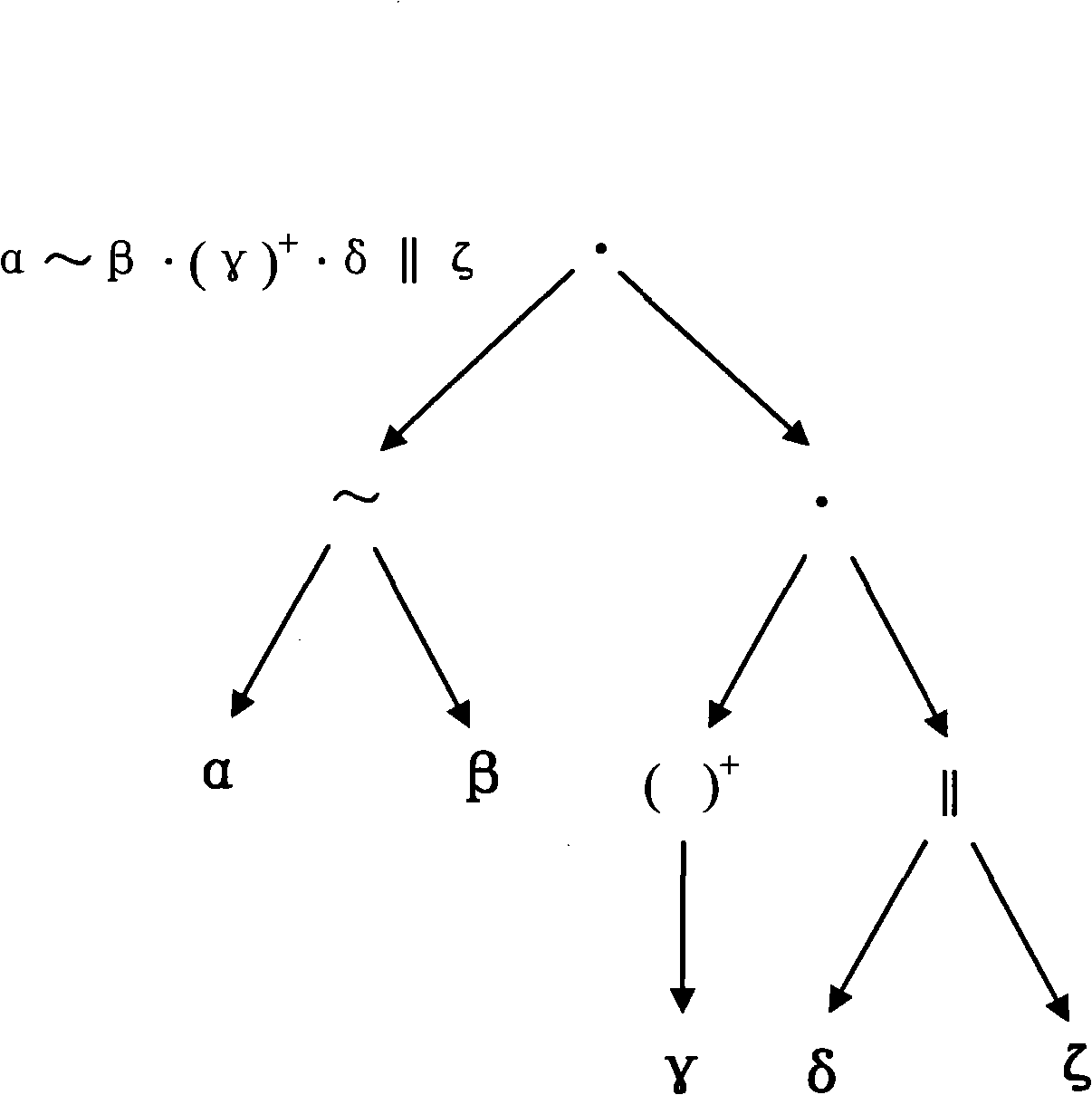
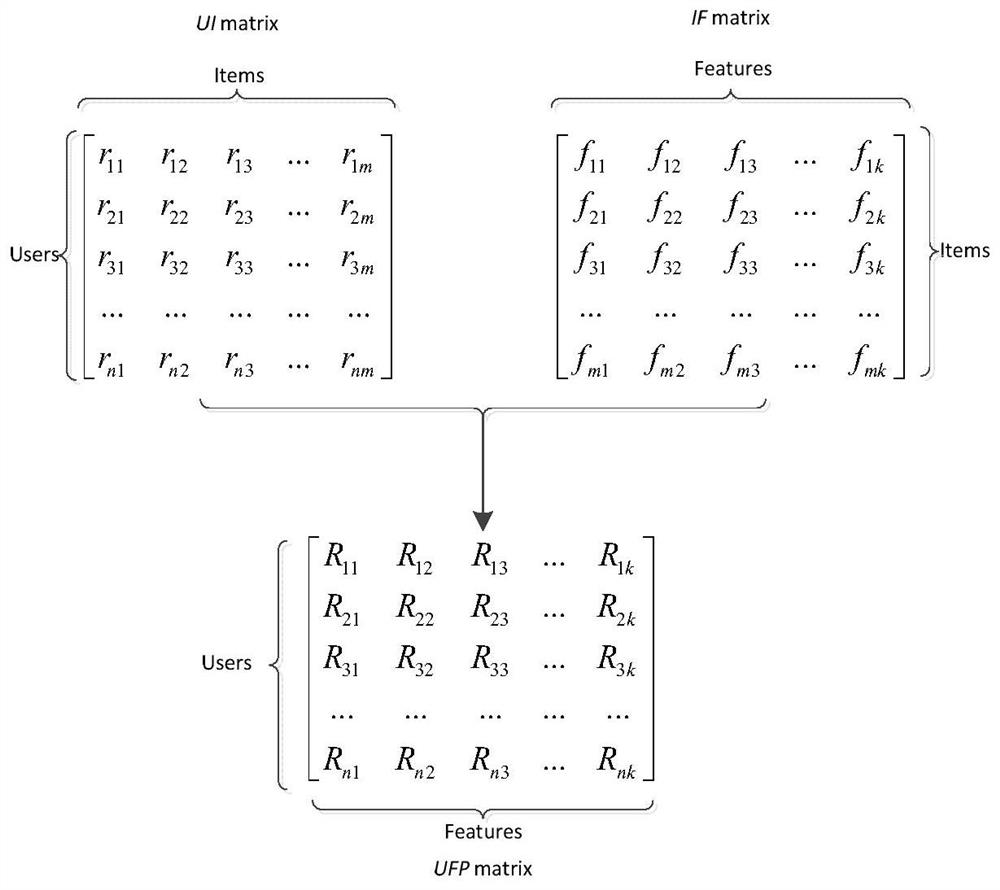
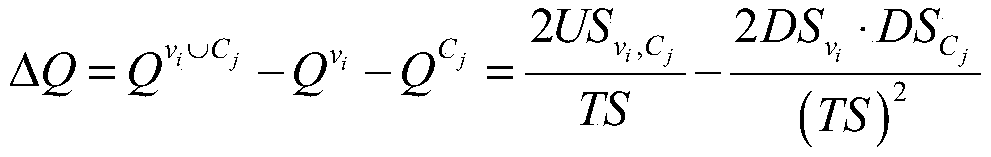Patents
Literature
76 results about "Analytical strategy" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
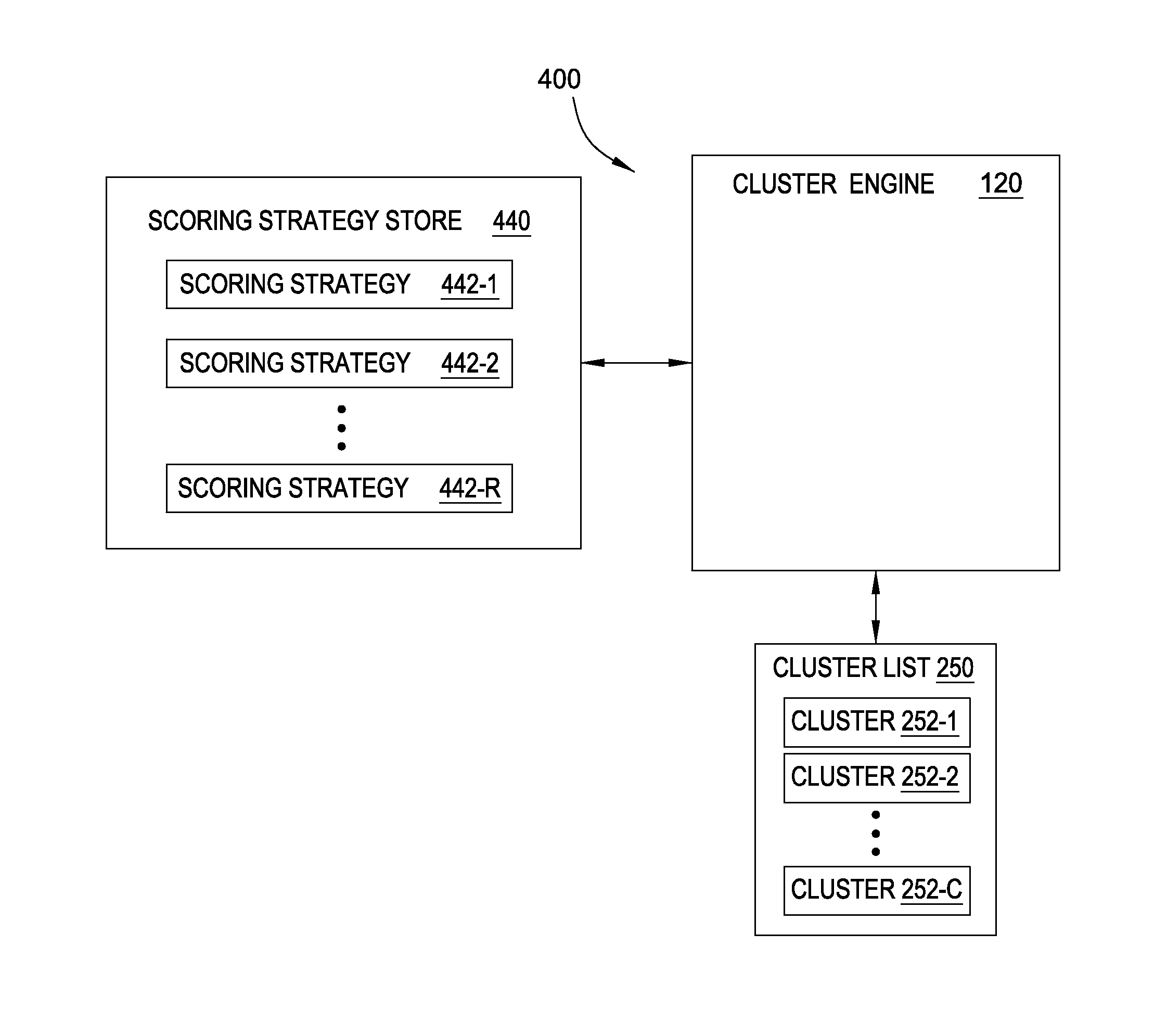
Generating data clusters with customizable analysis strategies
ActiveUS8788405B1Effective starting pointReduce the amount requiredDatabase updatingFinanceSearch protocolAnalytical strategy
Techniques are disclosed for generating a collection of clusters of related data from a seed. Doing so may generally include retrieving a seed and adding the seed to a first cluster and include retrieving a cluster strategy referencing one or more data bindings. Each data binding specifies a search protocol for retrieving data. For each of the one or more data bindings, data parameters input to the search protocol are identified, the search protocol is performed using the identified data parameters, and data returned by the search protocol is evaluated for inclusion in the first cluster.
Owner:PALANTIR TECHNOLOGIES
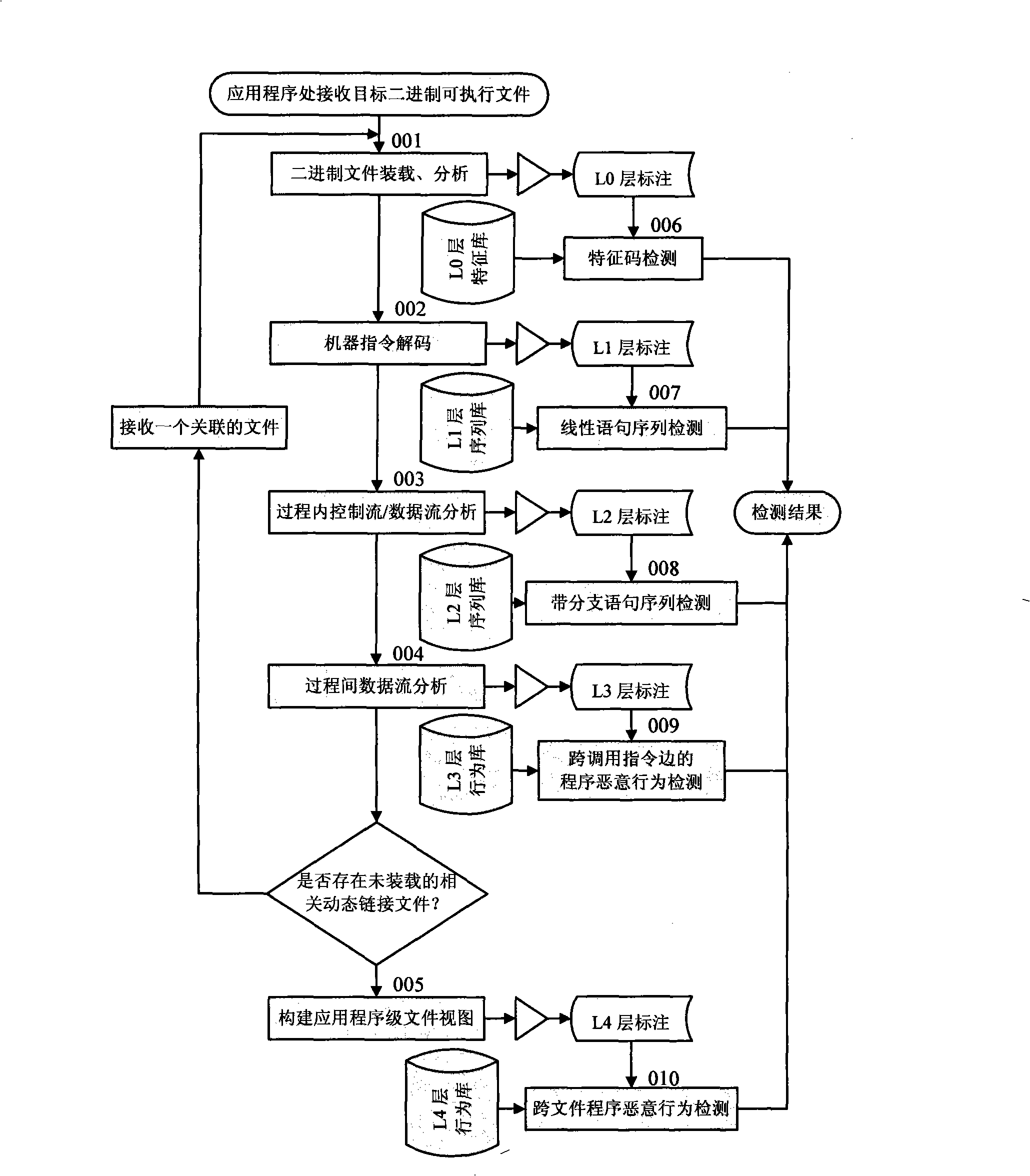
Multilayer semantic annotation and detection method against malignancy
InactiveCN101359351AEfficient decompositionAvoid inherent flawsPlatform integrity maintainanceNatural language processingControl flow
The invention relates to a method of adopting the multi-layer semantic annotation technology to analyze the intermediate result and detect the annotation information in layering mode based on the analyzed intermediate result during the malicious behavior detection. The model includes an annotation sub-module and a detection sub-module; wherein, the annotation sub-module includes a binary semantic layer, a linear instruction semantic layer, a control flow chart semantic layer, a process call chart semantic layer and an application level semantic layer. The annotation is processed towards the specified analysis target object in each layer. The detection sub-module detects the malicious behavior on the annotation information in layers based on the corresponding analysis strategy and the algorithm. The invention has the advantages of effectively decomposing the complexity of the malicious behavior detection, utilizing the advantages of different detection mechanisms, avoiding the inherent defects of different mechanisms, improving the adaptability and accuracy of the malicious behavior detection.
Owner:THE PLA INFORMATION ENG UNIV
Micro-service system-oriented call chain tracking and analyzing method
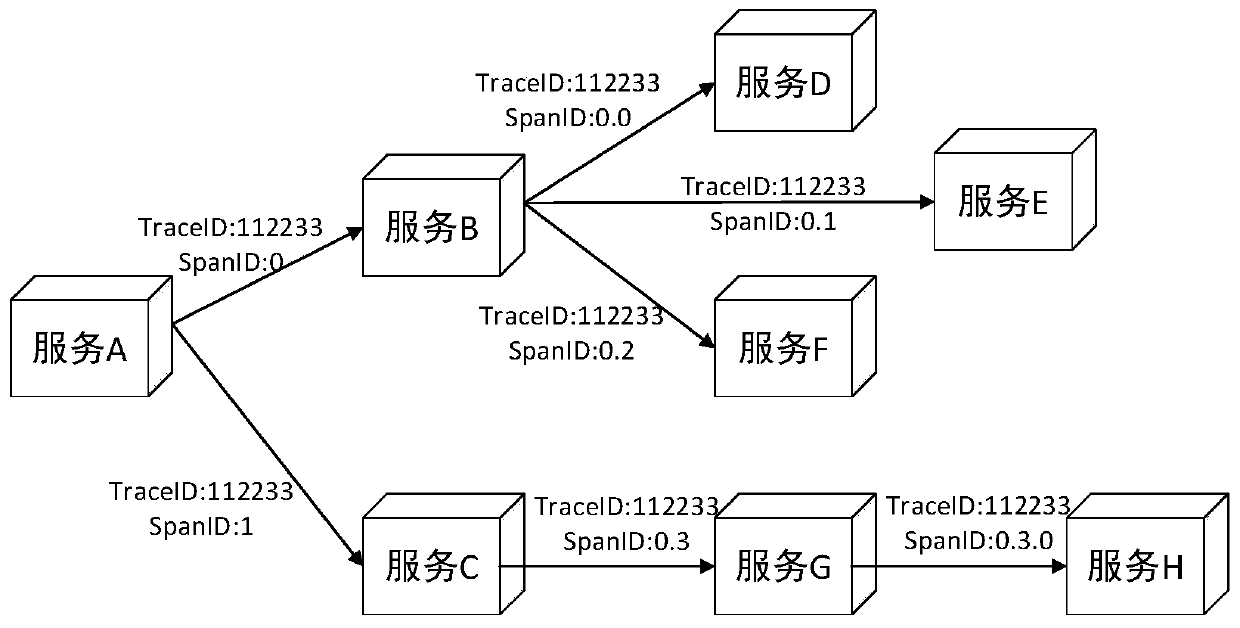
PendingCN111459766ARapid positioningPrecise positioningHardware monitoringSpecial data processing applicationsEngineeringAnalytical strategy
The invention relates to a micro-service system-oriented call chain tracking and analyzing method, which comprises the following steps of: (1) constructing a perfect call chain tracking system, namelyconstructing a tree structure of call chain tracking according to a Trace ID generated by a service request initiated by a micro-service system; then injecting the service request call chain information into system execution log information; collecting and storing log information executed by the system; and (2) carrying out aggregation analysis on the log information by using the call chain dimension: sending the log information with the same Trace ID to the same KafkaPation by using the Trace ID as a reference, and carrying out structured processing and analysis on the log information by using the call chain dimension. According to the method, aggregation analysis can be carried out on the log information through the call chain dimension, and a corresponding analysis strategy is given incombination with the actual situation, so that service abnormal fault positioning of the micro-service system is more accurate.
Owner:STATE GRID ZHEJIANG ELECTRIC POWER +2
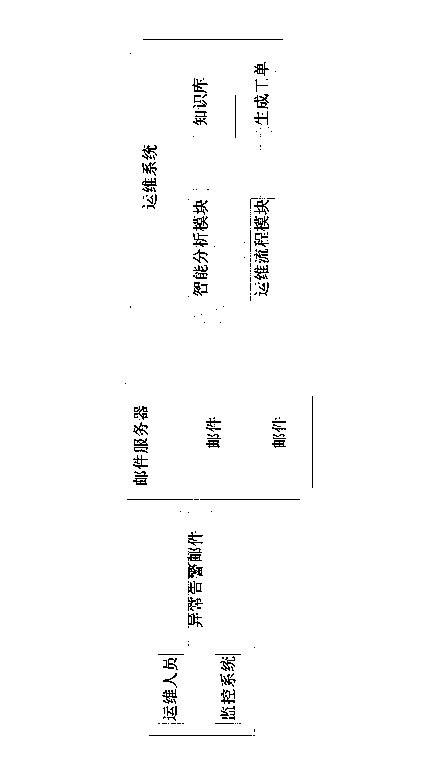
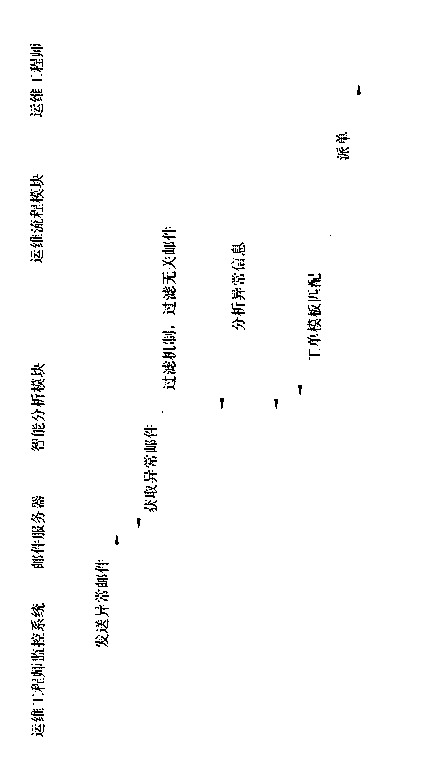
Work order generation method and device according to mail intelligent analysis
InactiveCN103186830AReduce maintenance costsTimely work orderResourcesData switching networksOrder processingComputer science
The invention discloses a work order automatic generation method and device according to a mail intelligent analysis. The main steps include: 1), a mail intelligent analysis strategy is defined in a operation and maintenance process management system; 2), when operation and maintenance work orders need to be established, mails are written and sent to a management mailbox of the operation and maintenance process management system; 3), the operation and maintenance process management system receives mails from a mail server at regular time; 4), an intelligent analyzer intelligently analyzes the received mails according to the intelligent analysis strategy; 5), the operation and maintenance process management system establishes the operation and maintenance work orders which need to be established according to an analysis result of the intelligent analyzer; and 6), the operation and maintenance process management system allocates the established work orders to appointed work order processing people according to the intelligent analysis strategy. According to the work order automatic generation method and device according to the mail intelligent analysis, maintenance cost of the operation and maintenance system is reduced, operation and maintenance efficiency is improved, and overall value of products is enhanced.
Owner:勤智数码科技股份有限公司
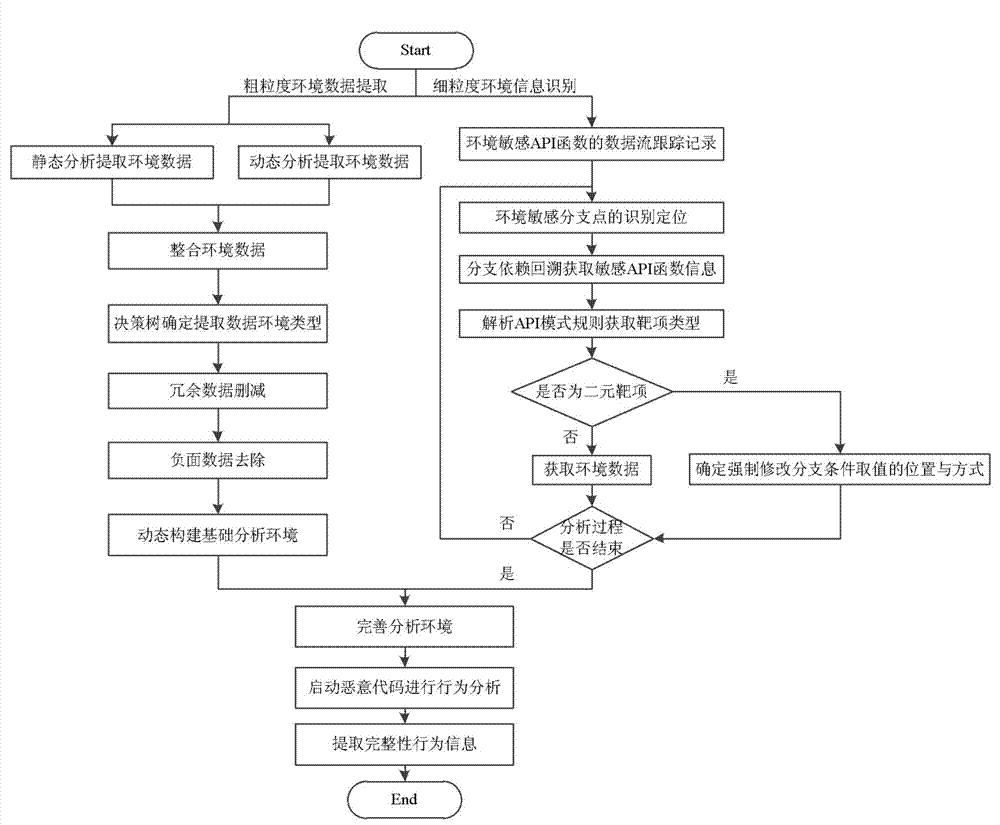
Environmental reconstruction based malicious-code integrity analysis method
ActiveCN104850786AReasonable triggerPrevent crashPlatform integrity maintainanceAnalytical strategyData mining
The invention provides an environmental reconstruction based malicious-code integrity analysis method. The method includes: extracting environmental data required during executing process in extracting malicious codes by using reasonable analytical strategies; performing dynamic reconstruction of the execution environment of the malicious codes on the basis of the environmental data; merging the malicious codes into the environment subjected to the dynamic reconstruction for analysis to acquire behavior information which is relatively integral. The problem existing in multipath analysis can be effectively solved, and analysis in integrity of the malicious codes is realized. Compared with a traditional analysis method, the integrity analysis method has the advantages that more reasonable triggering on the key paths can be realized, and accurate behavior characteristics are acquired.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
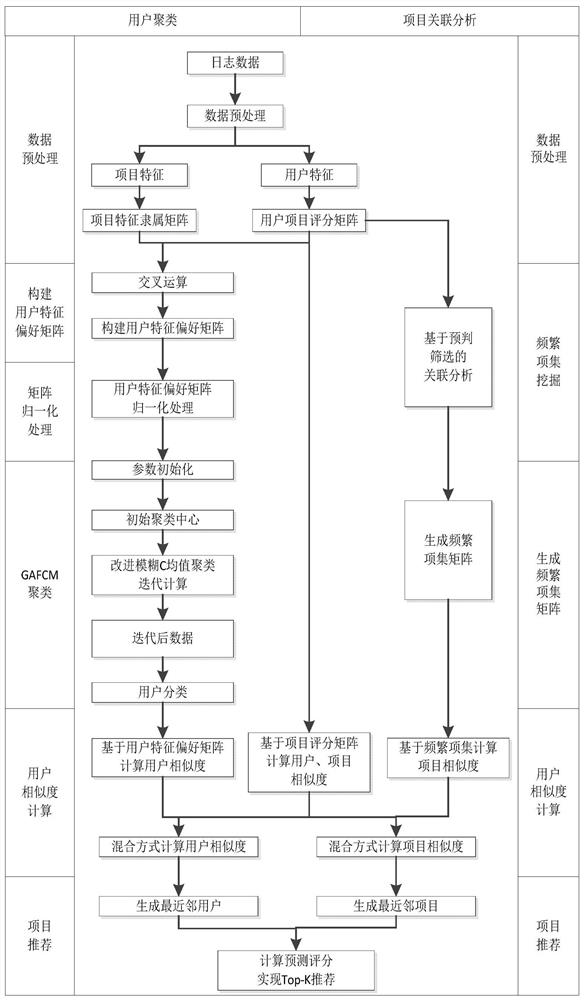
Collaborative filtering recommendation method based on user clustering and project association analysis
InactiveCN112100512AImprove recommendation qualityDigital data information retrievalCharacter and pattern recognitionCluster algorithmEngineering
The invention discloses a collaborative filtering recommendation method based on user clustering and project association analysis in order to solve the problems of cold start, data sparseness, low recommendation accuracy and the like of a traditional collaborative filtering recommendation algorithm. According to the method, an improved fuzzy C-means clustering algorithm is adopted to mine the preference degree of hidden features of a user, and an association analysis strategy based on pre-judgment screening is adopted to screen a frequent item set. On the basis, the algorithm uses a user characteristic preference matrix and a user scoring matrix to calculate the similarity between users, uses a frequent item set matrix and a user scoring matrix to calculate the similarity between items, and combines the user similarity and the item similarity to calculate the prediction score of the users for items which are not scored, thereby realizing Top-K recommendation. Compared with a traditional collaborative filtering recommendation algorithm based on a user and a collaborative filtering recommendation algorithm based on a project, the method can effectively avoid the cold start problem and the data sparsity problem, and has better recommendation quality.
Owner:NANJING UNIV OF POSTS & TELECOMM
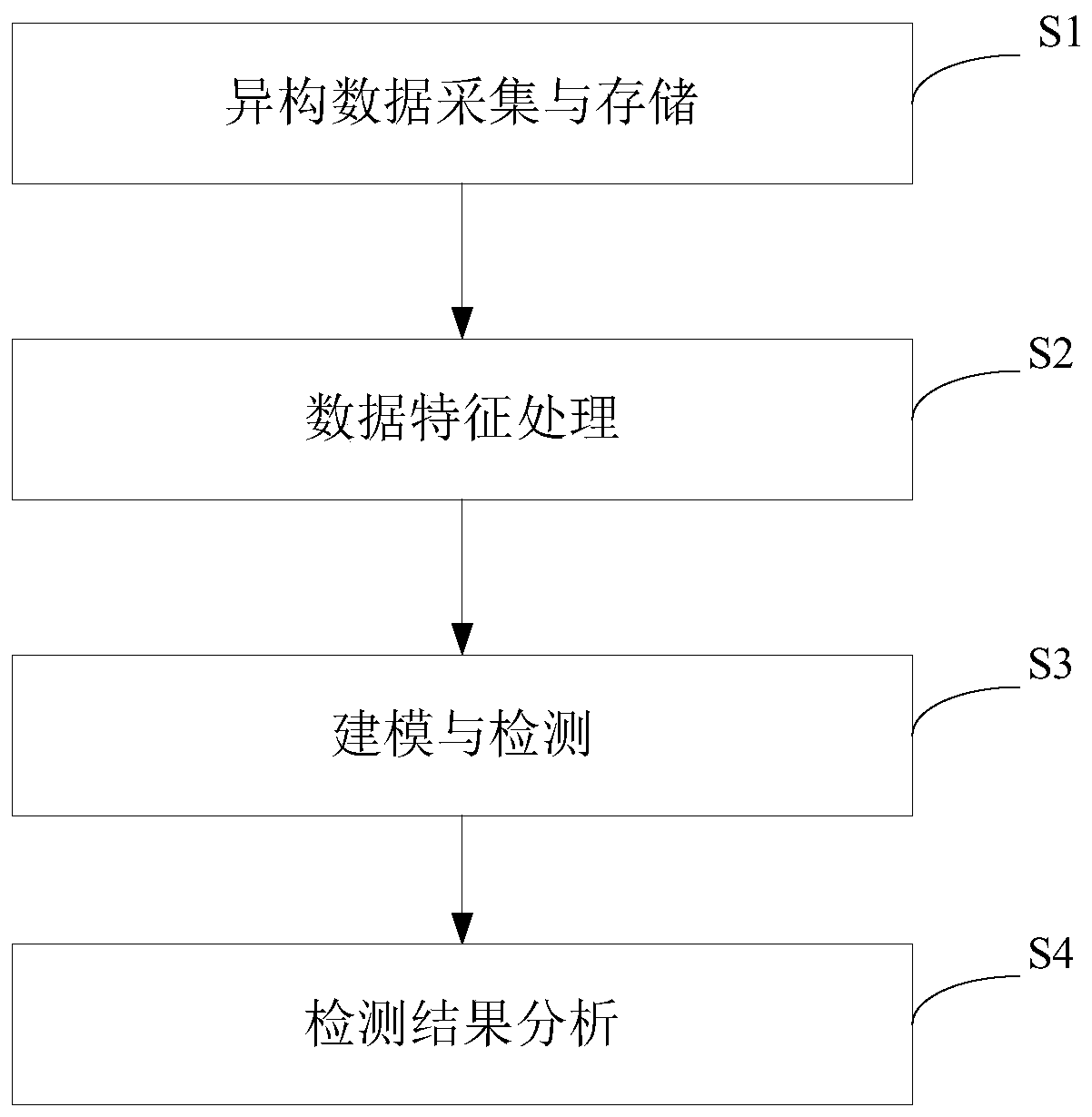
Network asset anomaly detection method and system, medium and equipment
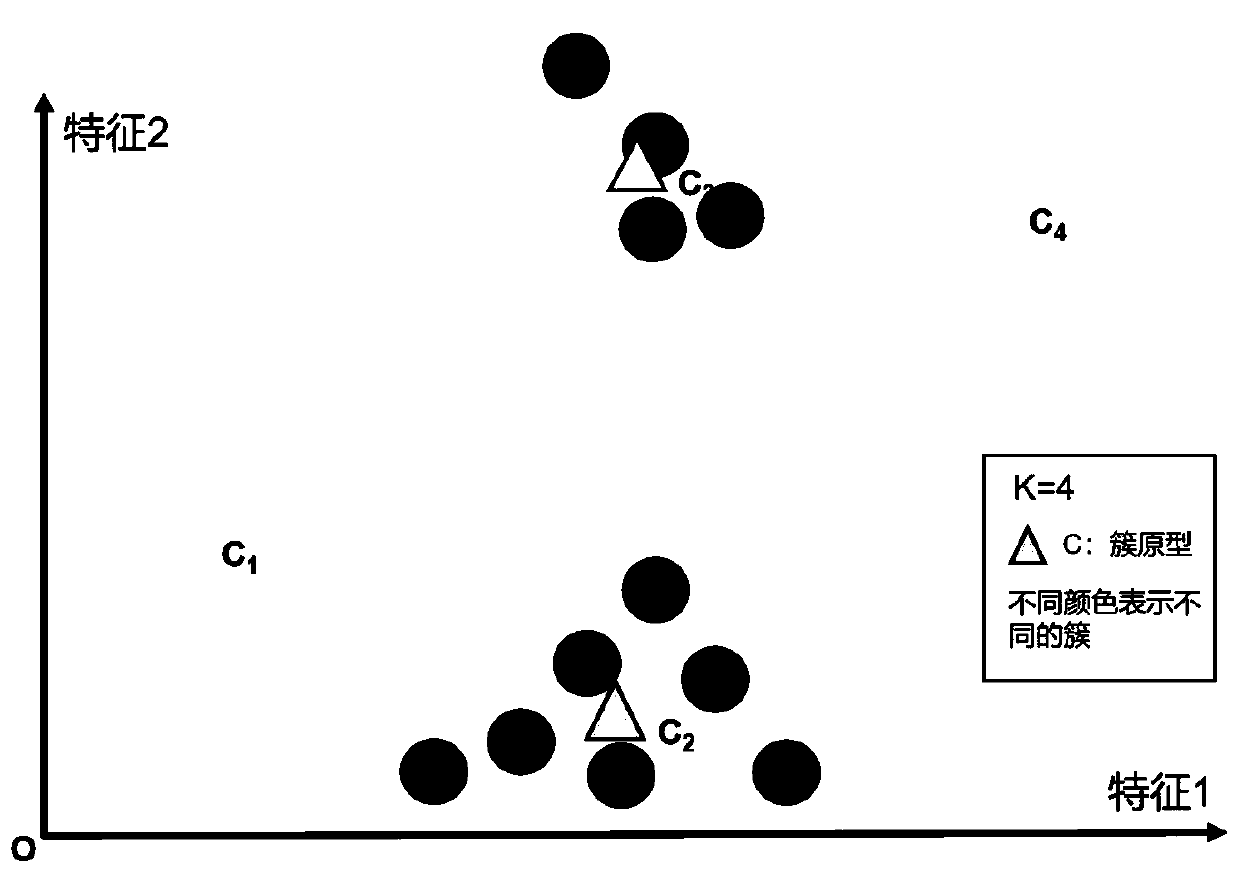
ActiveCN111339297AEasy accessFeature Field ReductionCharacter and pattern recognitionSpecial data processing applicationsCluster algorithmData set
The invention discloses a network asset anomaly detection method and system, a medium and equipment. The method comprises the following steps: acquiring and storing heterogeneous data; data feature processing: integrating multi-source original data, deriving and converting a group of probability distribution type fields into a new data feature field by using an improved Raney entropy algorithm, and standardizing the data by using a quantile-based high-robustness standardization algorithm to generate a data set required by modeling; modeling and detection: enabling a modeling unit to acquire anetwork asset data set, and establishing an optimal clustering model in groups according to asset types by adopting an automatic optimal clustering algorithm based on prototypes; and detection resultanalysis: using the optimal clustering model obtained in the modeling and detection steps to be combined with an anomaly detection result analysis strategy. According to the invention, the efficiencyand accuracy of private network asset anomaly detection are improved, and the method is a universal detection method suitable for various abnormal threat scenes.
Owner:GUANGZHOU TRUSTMO INFORMATION SYST CO LTD
BIM structure transformation increment information generation and storage system and method
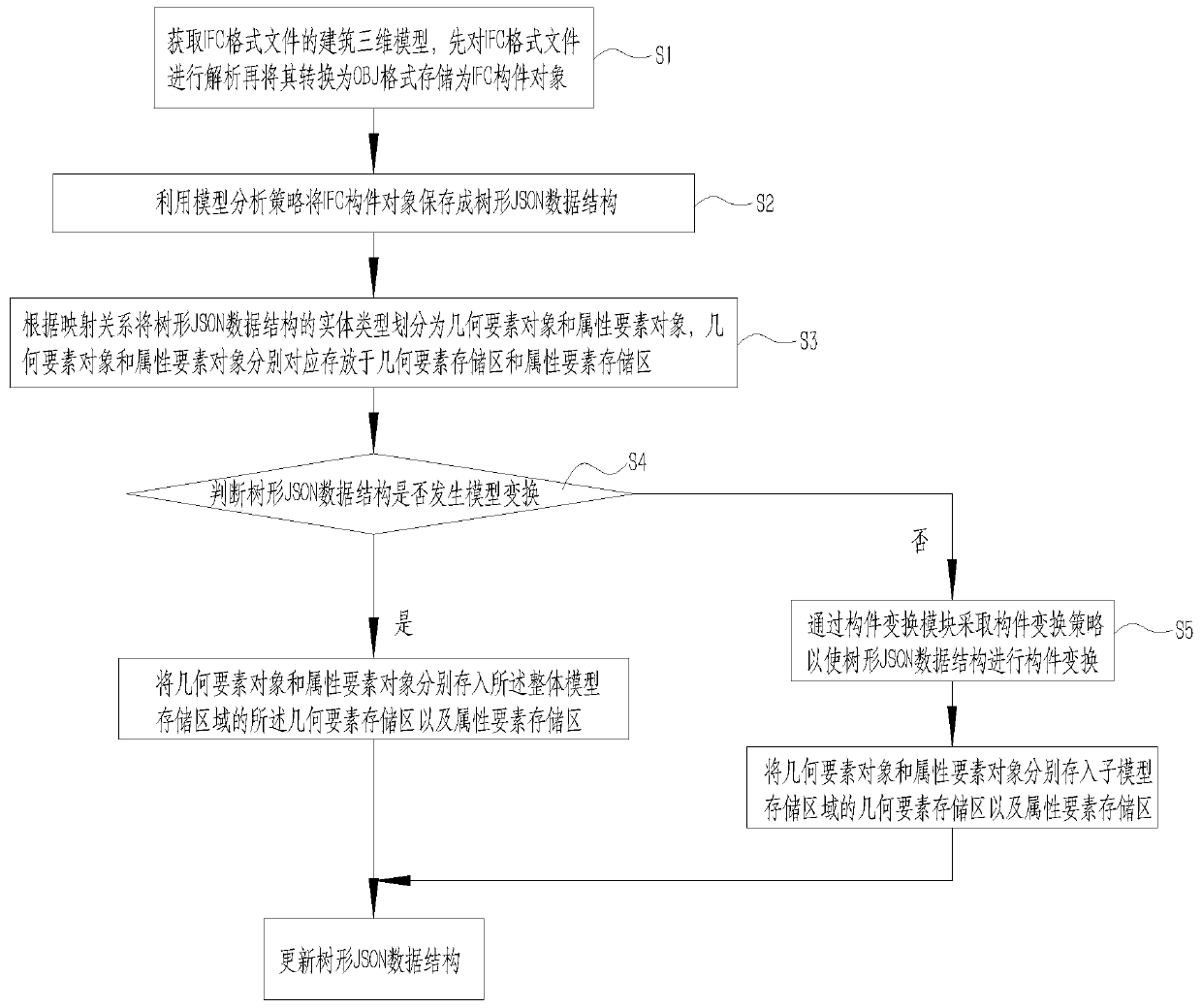
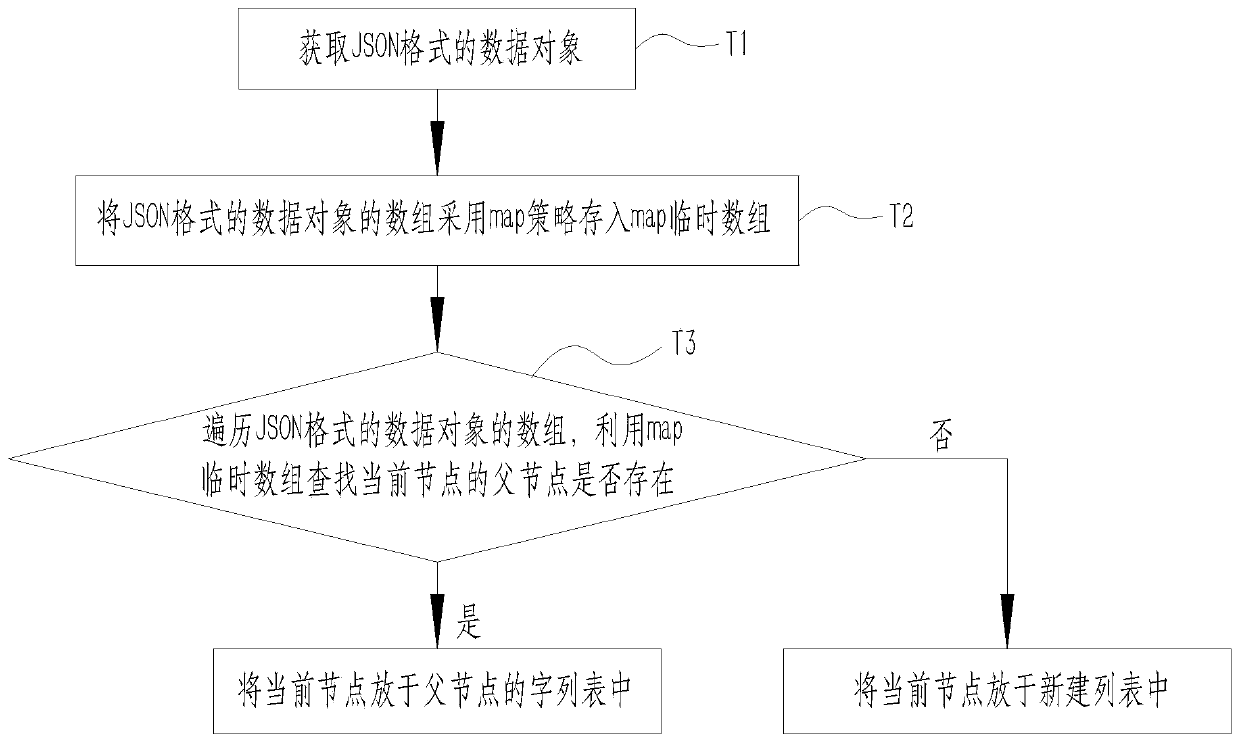
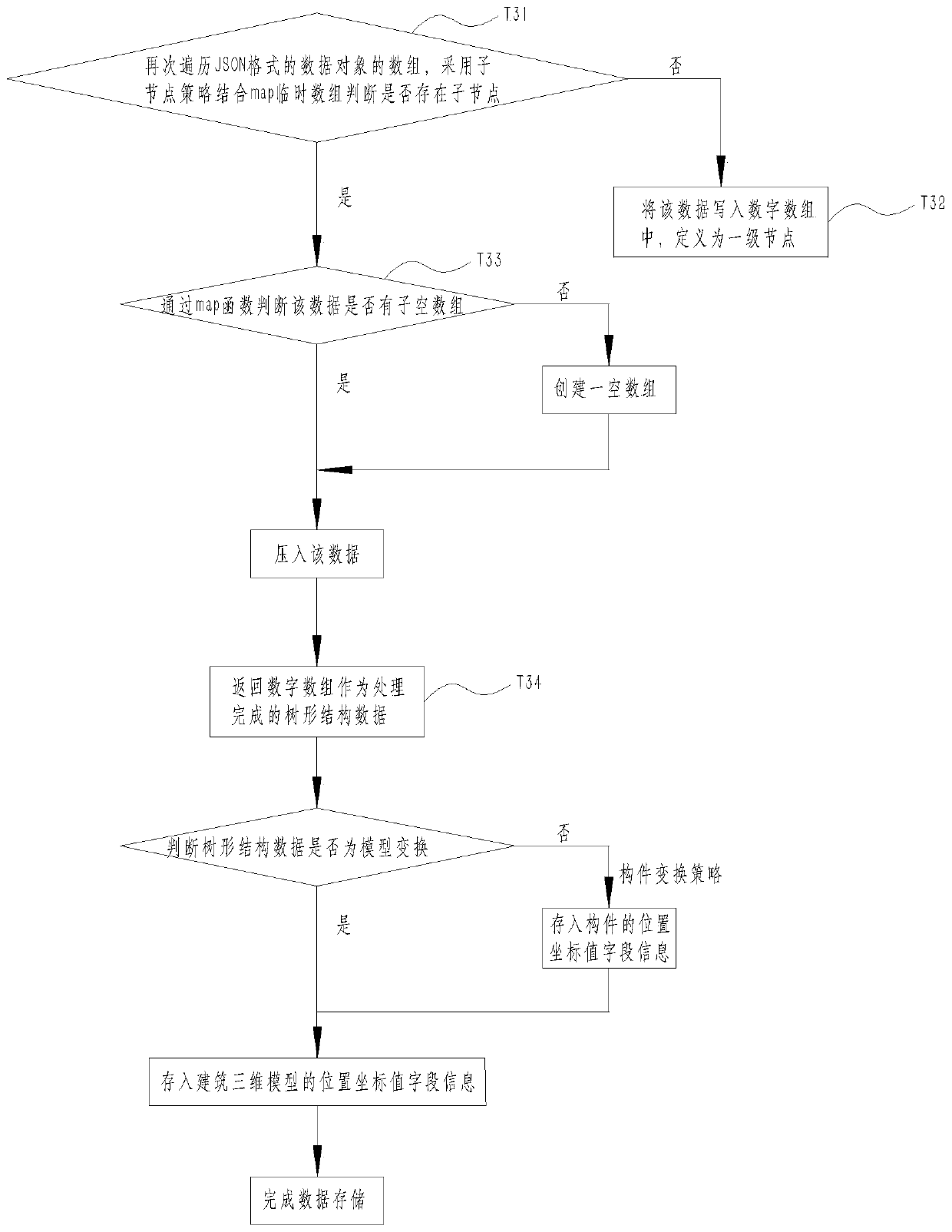
ActiveCN111506950AImprove lightweightReduce processing timeGeometric CADText processingThree dimensional modelAnalytical strategy
Owner:中筑创联建筑科技(北京)有限公司
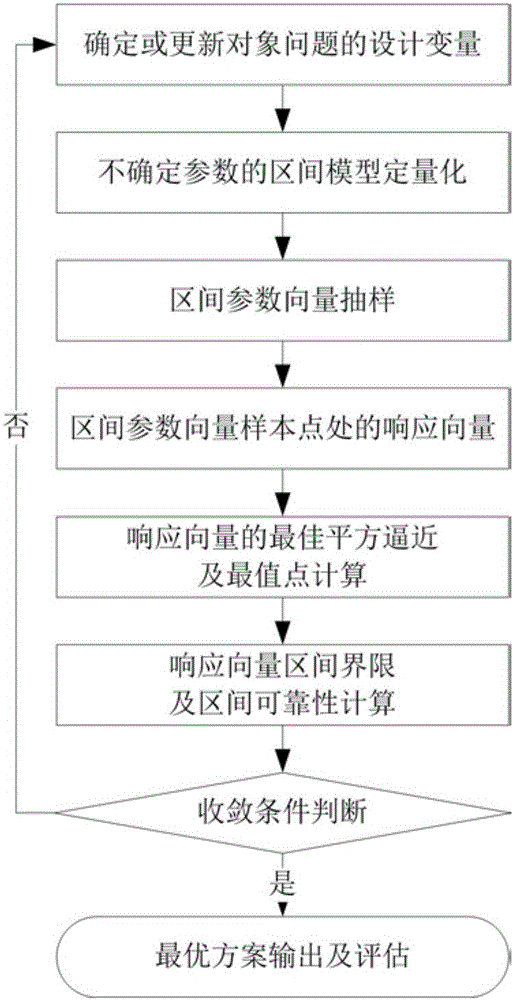
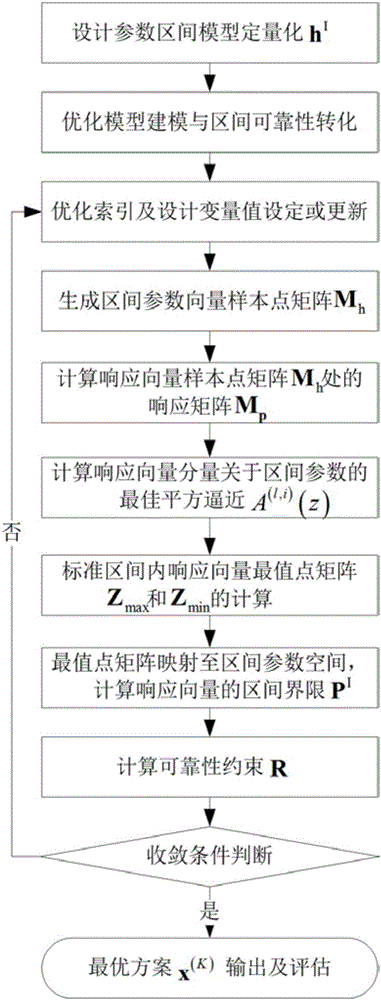
Method for optimizing reliability of structural noise based on dimension-by-dimension analysis strategy
ActiveCN105912839AWide applicabilityAvoid conservatismInformaticsSpecial data processing applicationsQuantitative modelAnalytical strategy
The invention discloses a method for optimizing reliability of structural noise based on a dimension-by-dimension analysis strategy. The method comprises following steps: firstly, establishing a structural noise optimizing model based on an interval reliability analysis model by using a quantitative structure for a model of interval value and environment and other uncertainties, determining orders and gauss integral points based on least-squares approximation responding to interval parameters by utilizing structural acoustics to response to nonlinearity degree related to interval parameters; secondly, utilizing gauss integral points and a quantitative model for interval numbers to sample parameter vectors of intervals, calculating response vector value at interval parameter sample points, establishing the best square approximation in order to determine the max-minimum point matrix such that response interval vectors can be calculated; and finally, utilizing response interval vectors and safety requirement to calculate reliability in intervals and finishing structural optimization under drive of the optimizing algorithm. The method for optimizing reliability of structural noise based on the dimension-by-dimension analysis strategy has following beneficial effects: by replacing classic safety factor with interval reliability, the method echoes the fine development trend of optimizing structural noise; conservativeness of a conventional optimizing method is effectively avoided; and the method has a broad application prospect.
Owner:BEIHANG UNIV
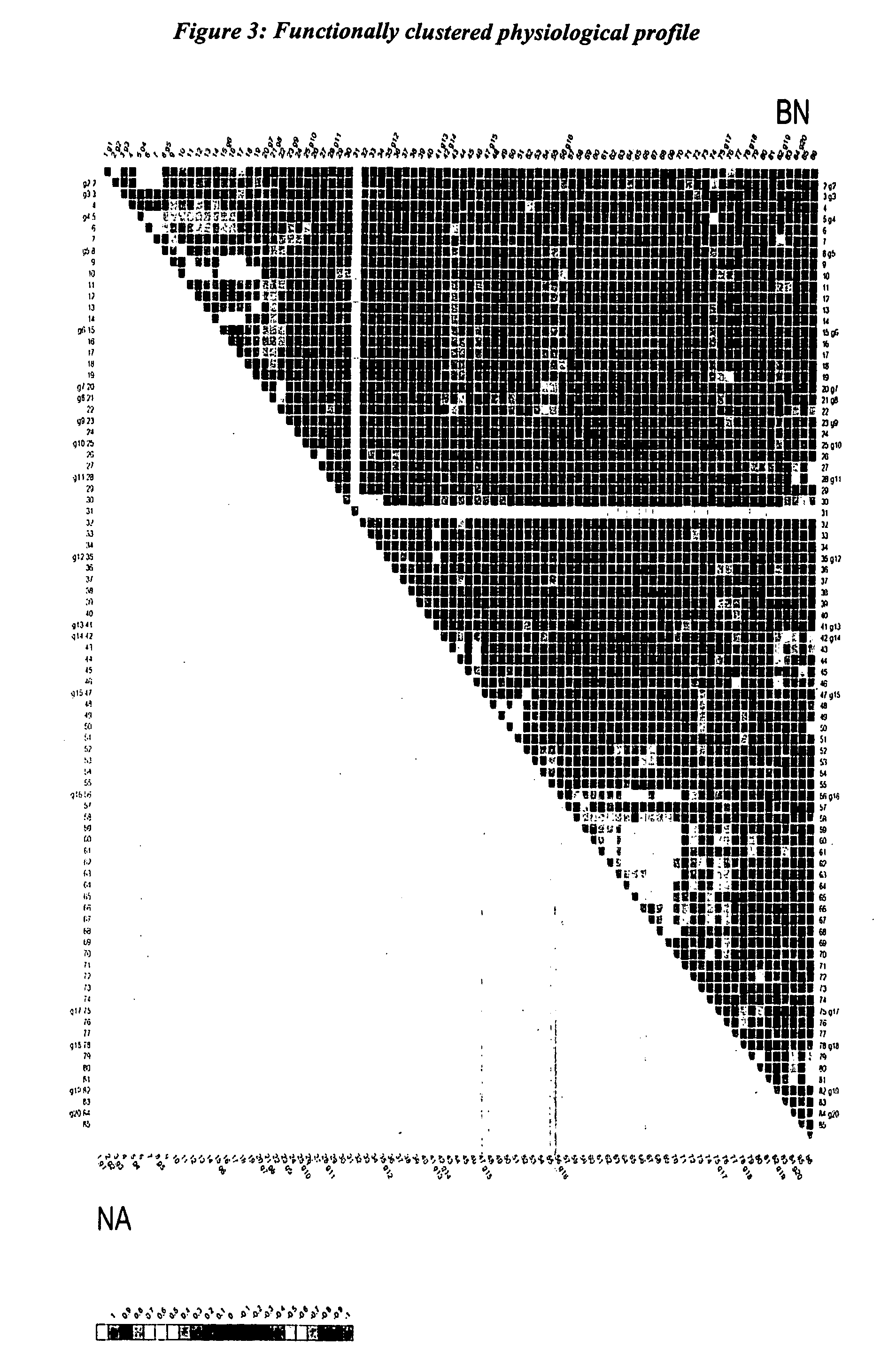
Physiological profiling
InactiveUS20050192761A1Microbiological testing/measurementData visualisationStatistical analysisGenotype
A new analytical strategy, termed physiological profiling, was developed that can capture physiological baselines and reveal relationships between particular phenotypes as a function of genotype in complex disease conditions. Physiological profiling offers a powerful strategy to visualize complex physiological processes. Combined with developing statistical analysis, this analytical tool is likely to facilitate our understanding of the biology of an organism.
Owner:JACOB HOWARD J +3
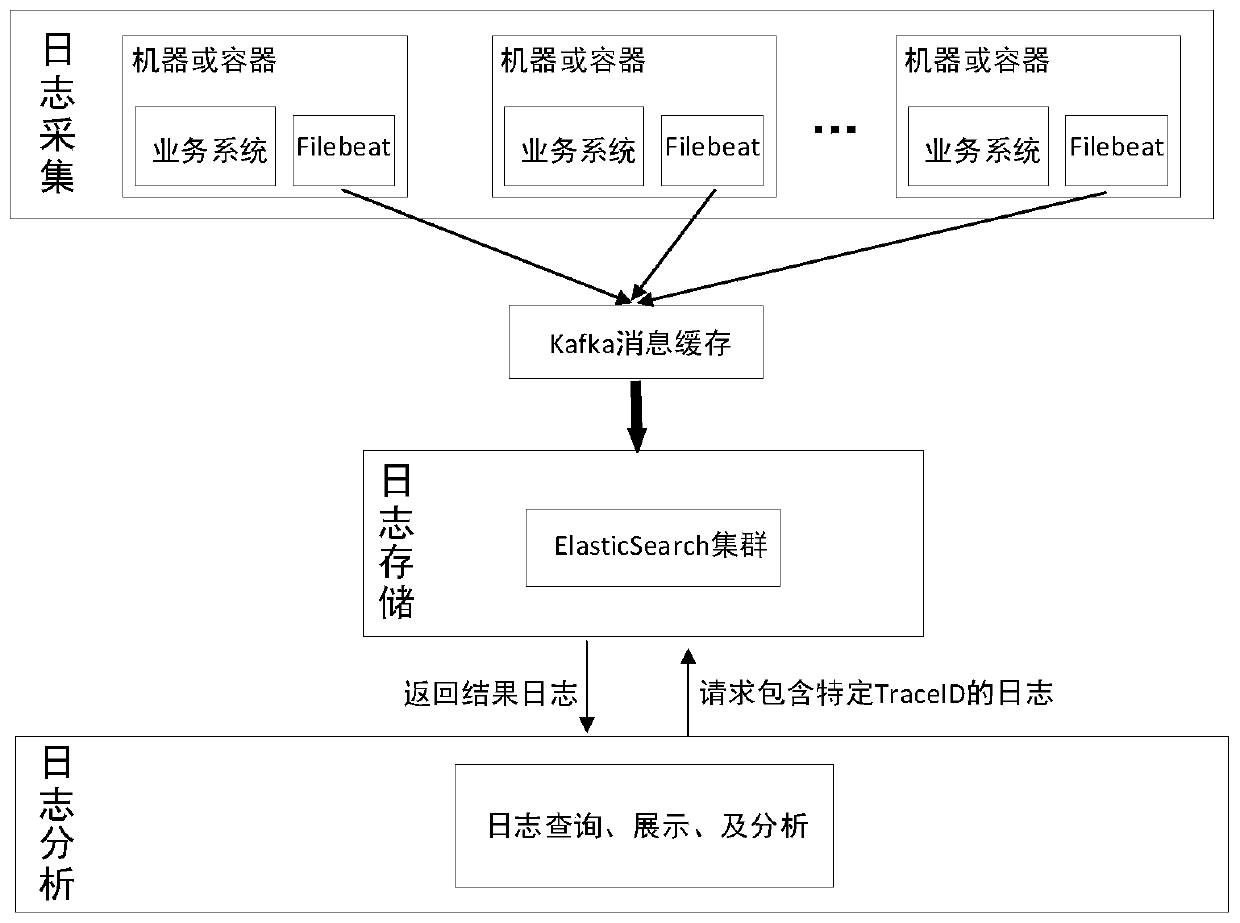
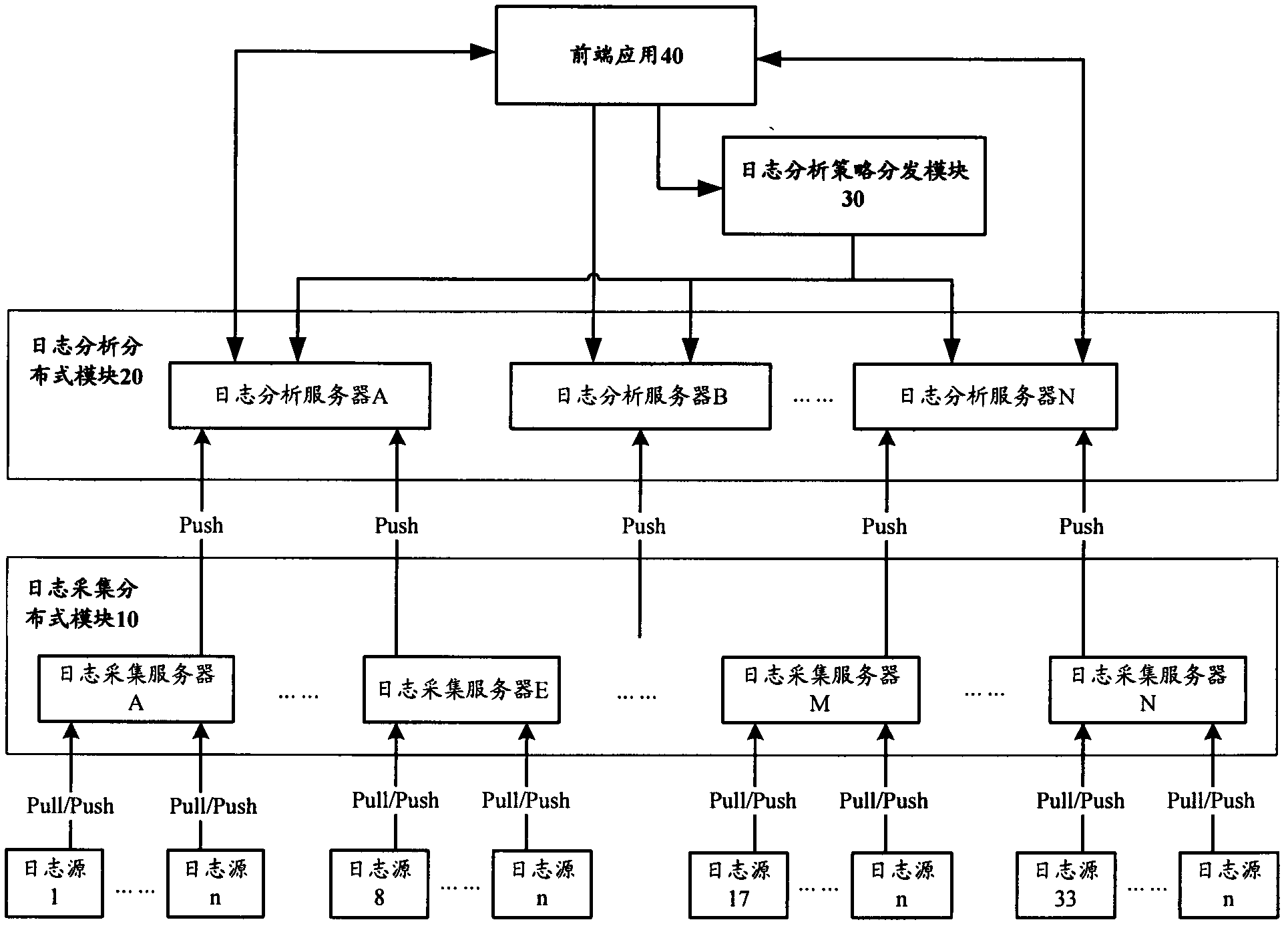
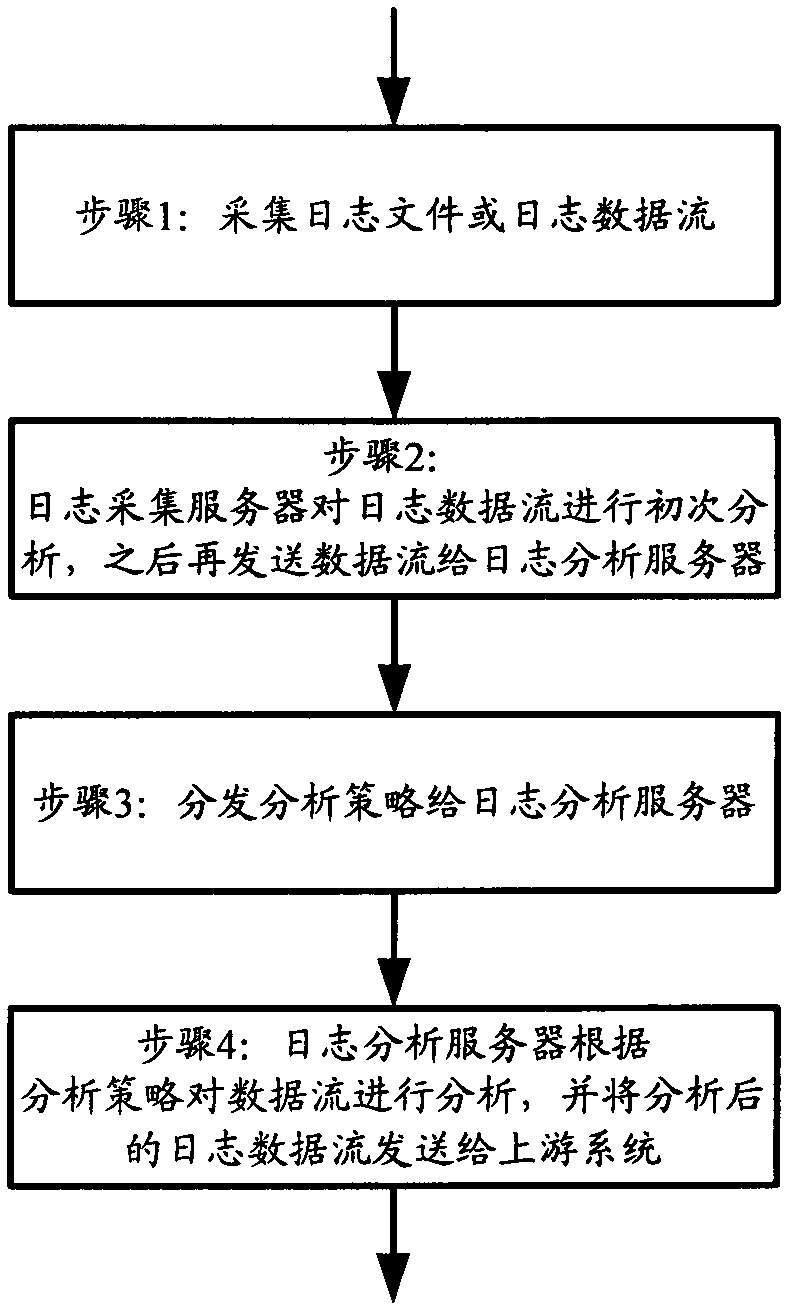
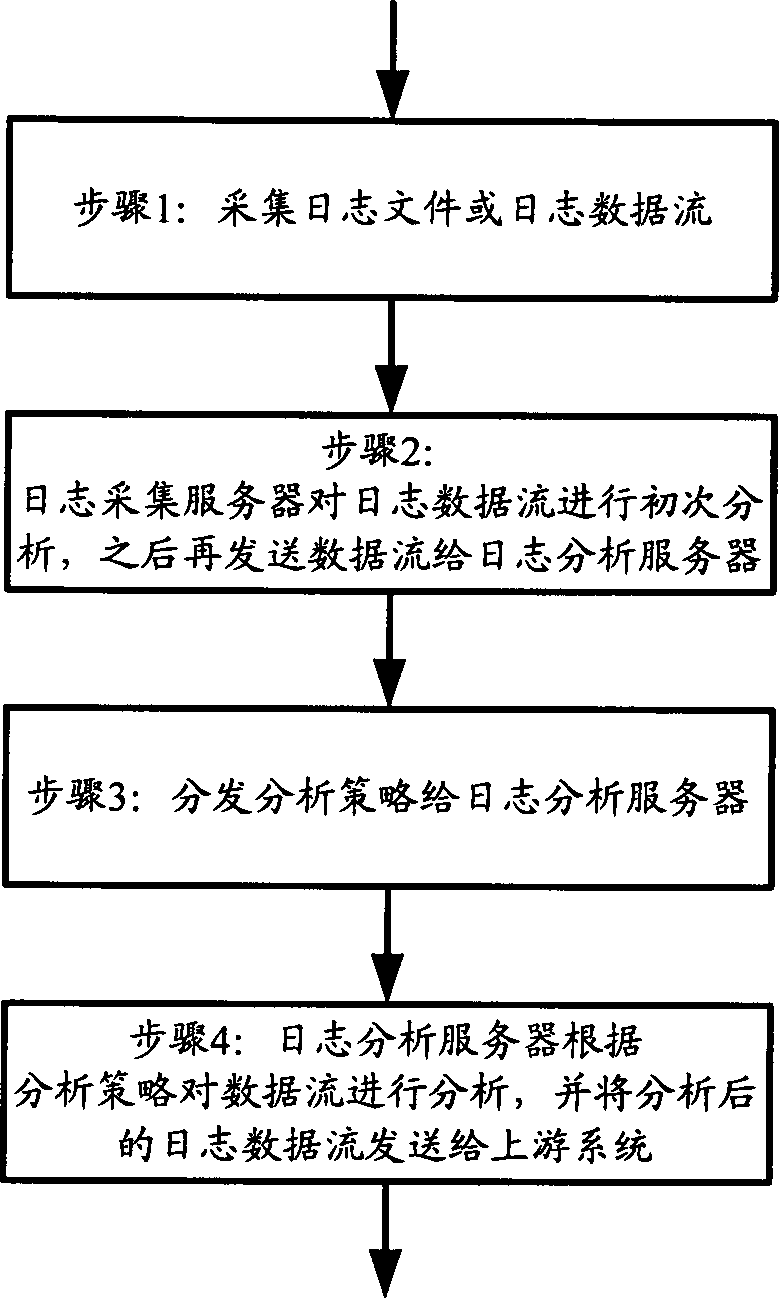
Log distribution acquisition analysis method and system thereof
InactiveCN102307111AFlexible configurationReduce the burden onData switching networksData displayData stream
The invention provide a log distribution acquisition analysis method which comprises the following steps: a log acquisition distribution module acquires log data flow; the log acquisition distribution module carries out filtering and formatting processing on the log data flow, and sends the data flow after formatting processing to a log analysis distribution module; the log analysis distribution module analyzes the data flow according to an analysis strategy, and sends the log data flow after analysis to front application. The invention also provides a log distribution acquisition analysis system. According to the log distribution acquisition analysis method and the system thereof, burden of an analysis server can be lightened when the analysis server rapidly process mass logs simultaneously, integral log acquisition analysis performance is improved, upstream front application can obtain timely and effective data display, and better experience is brought to a user.
Owner:ZICT TECH CO LTD
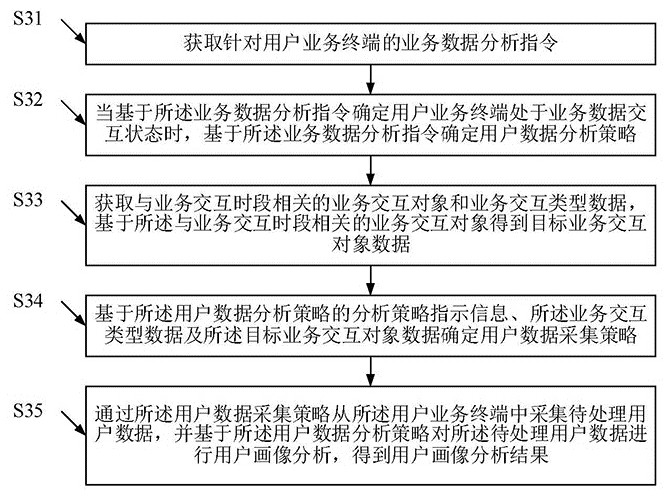
User data processing method based on big data and business analysis and big data platform
ActiveCN112463859AHigh degree of intelligenceImprove analysis rateCharacter and pattern recognitionOther databases clustering/classificationData acquisitionEngineering
The invention relates to a user data processing method based on big data and business analysis and a big data platform. The method comprises the following steps: before user portrait analysis, determining a user data analysis strategy based on a service data analysis instruction, and then determining a service interaction object and service interaction type data related to a service interaction time period, and determining the user data acquisition strategy. The big data platform can carry out targeted collection on the user data of the user service terminal based on the user data collection strategy, so that some useless data is filtered out, in this way, when user portrait analysis is carried out, the to-be-processed user data with data analysis and mining value can be directly analyzed,and the user experience is improved. The analysis rate of the user portrait can be improved, and the analysis precision of the user portrait can be improved, so that the processing efficiency of theuser data is improved. According to the method, a user data analysis strategy and a user data acquisition strategy can be combined, so that the intelligent degree of user portrait analysis is improved.
Owner:厦门蝉羽网络科技有限公司
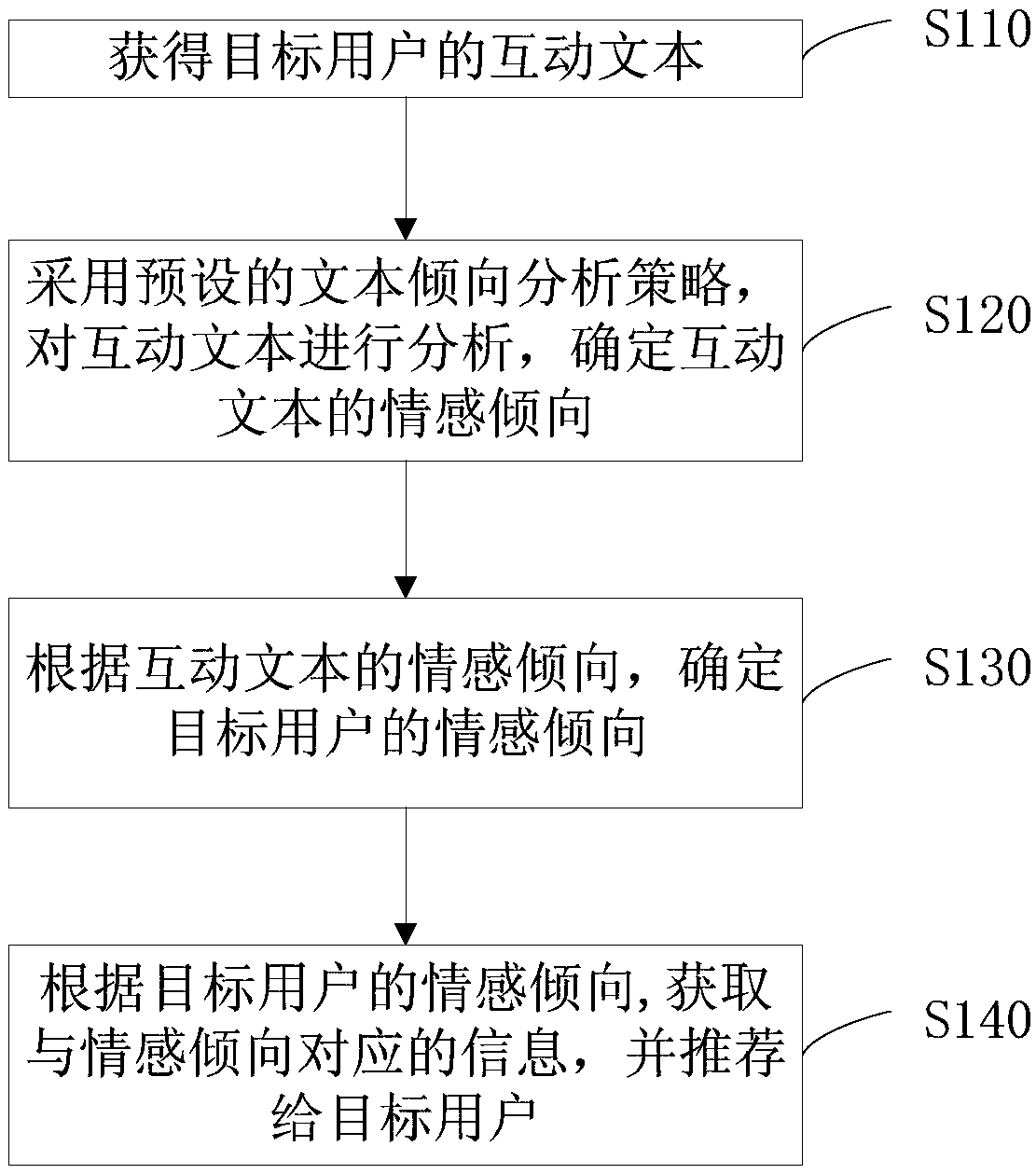
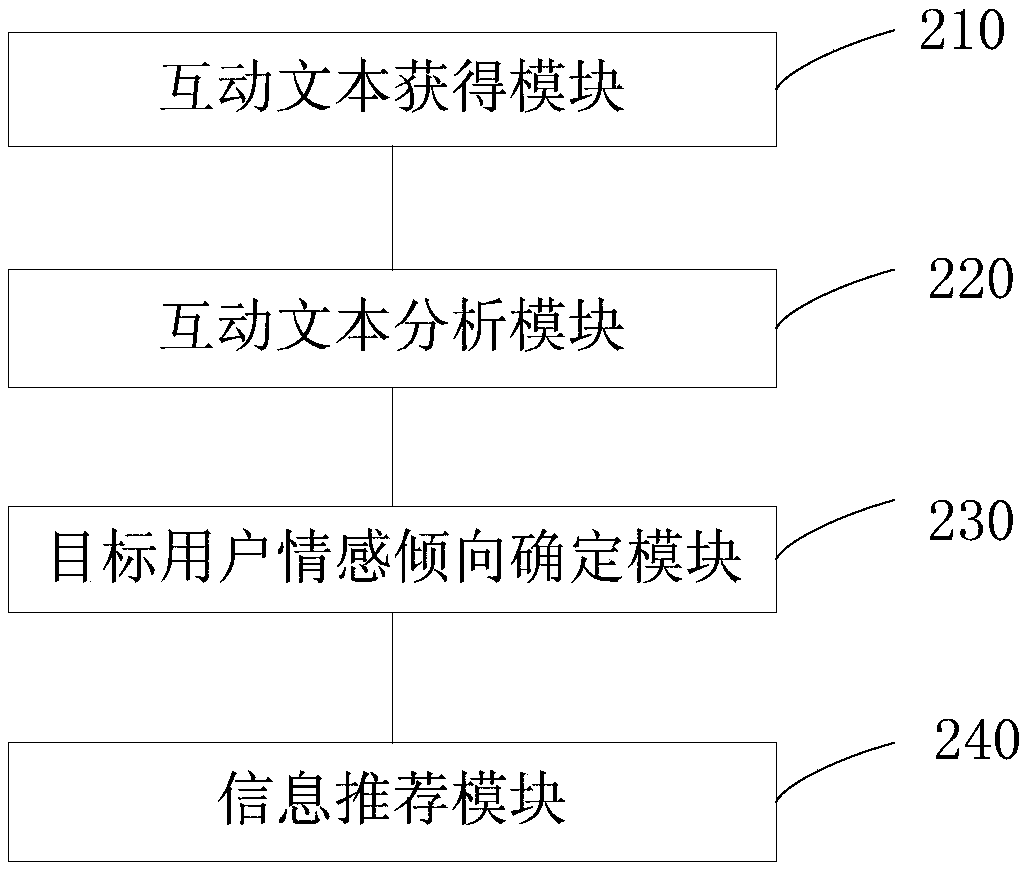
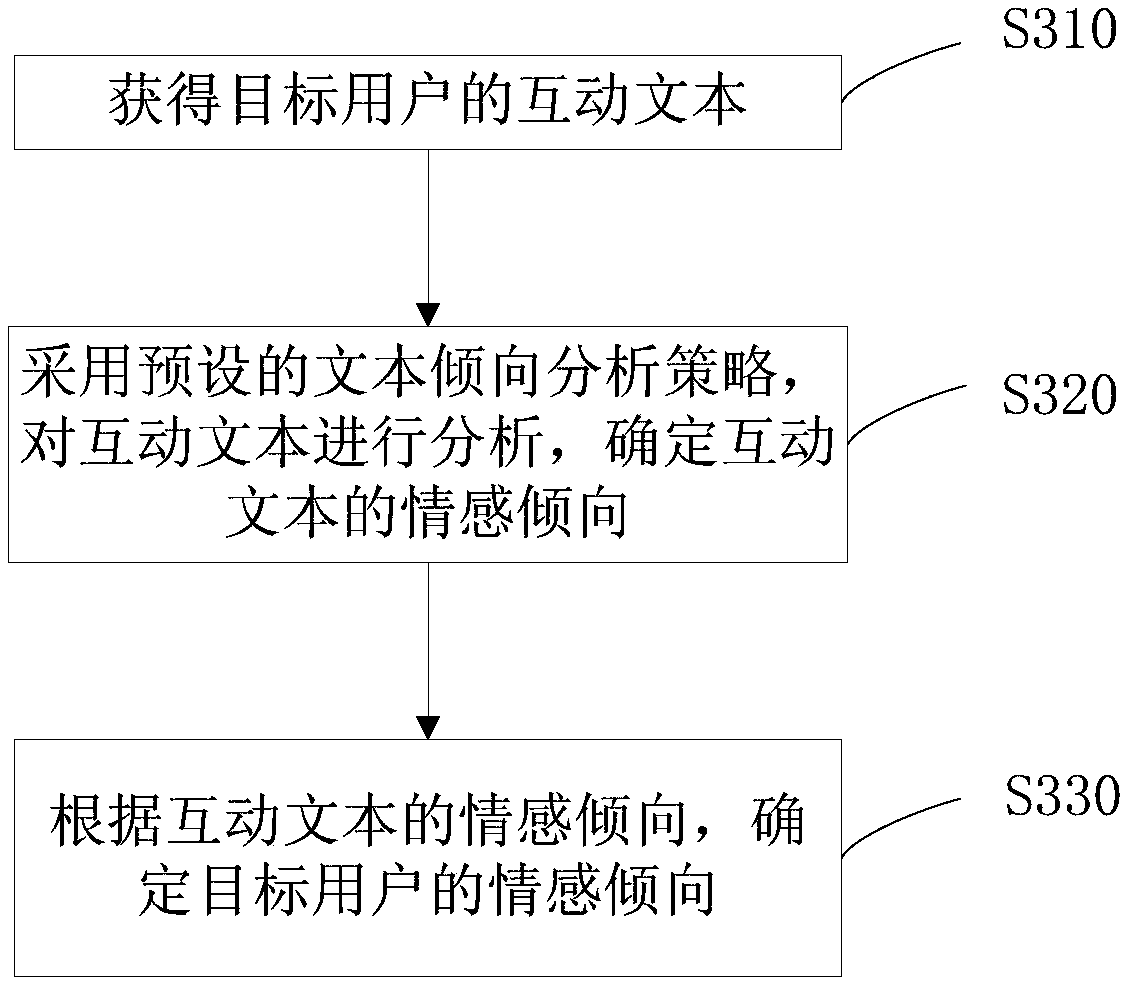
Information recommendation method, emotion tendency determination method and device and electronic device
InactiveCN109446378ADigital data information retrievalSemantic analysisComputer scienceElectronic equipment
Owner:BEIJING QIYI CENTURY SCI & TECH CO LTD
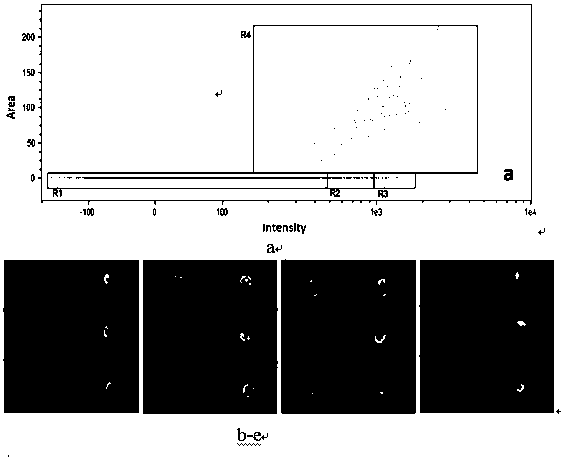
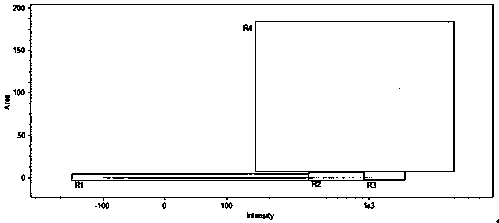
Method applicable for fish blood cell fast classification and counting and application thereof
ActiveCN107686859AGuaranteed accuracyEnsure reliabilityMicrobiological testing/measurementMaterial analysisWhite blood cellFluorescence
The invention discloses a method applicable for blood cell high-flux fast classification analysis of common fishes such as crucian and carps. By aiming at the problem of white blood cell classification and counting interference by removing-incapable nucleated red blood cells in two aspects of the quantity and the form, an automatic measurement and analysis strategy of combining the fluorochrome with the multi-channel images is utilized; the interference red blood cell sampling points are separated from the white blood cells according to the differences of particles in the cells, cell nucleus forms, positions and the like; different white blood cell class group range of lymphocyte, monocyte, particle cells and the like undertaking important immunologic functions is divided; the automatic analysis is completed. The difficulty that the nucleated red blood cells cannot be effectively removed troubles the automatic analysis of hemogram of various kinds of animals for a long time. The fluorochrome is combined with the imaging analysis; a high-flux and high-sensitivity measuring module of a multidimensional panoramic analyzer is used for accurately recognizing the red blood cell class groups; the interference is eliminated; the important technical support is provided for the focused analysis of the white blood cell class groups; wide application prospects are realized.
Owner:TIANJIN NORMAL UNIVERSITY
Development scale prediction method and system suitable for distributed energy supply system
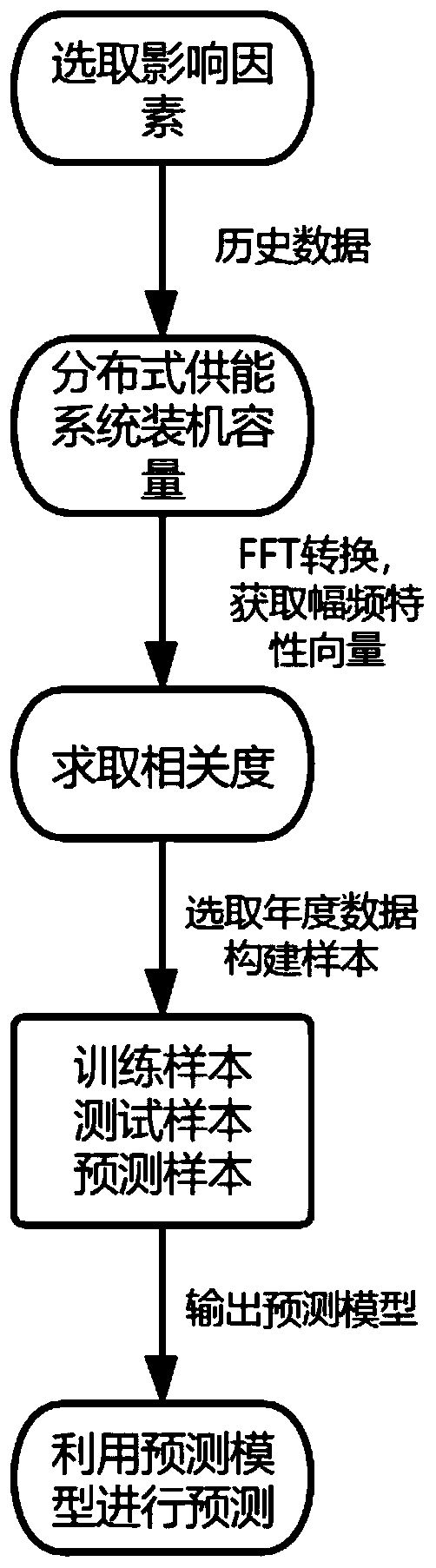
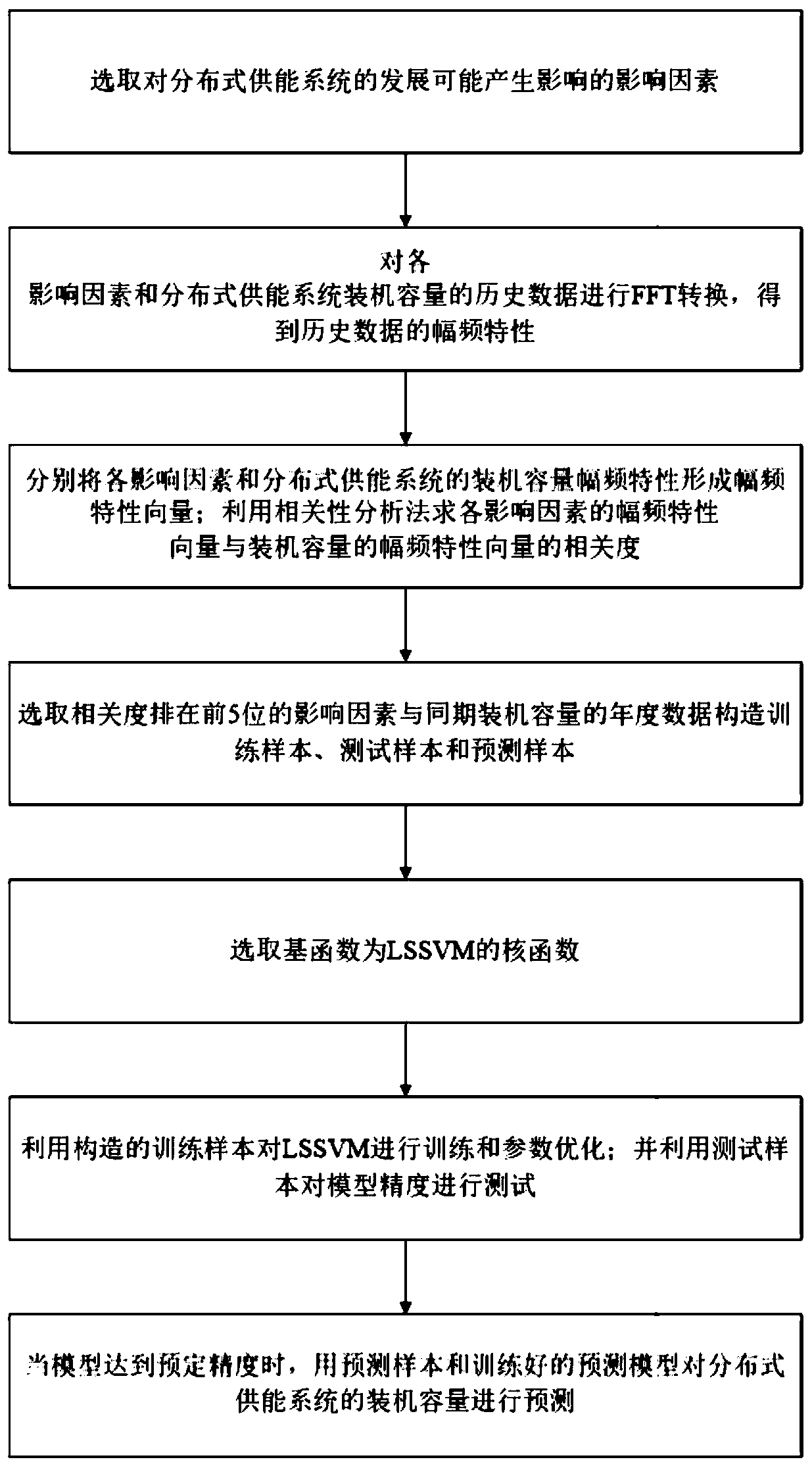
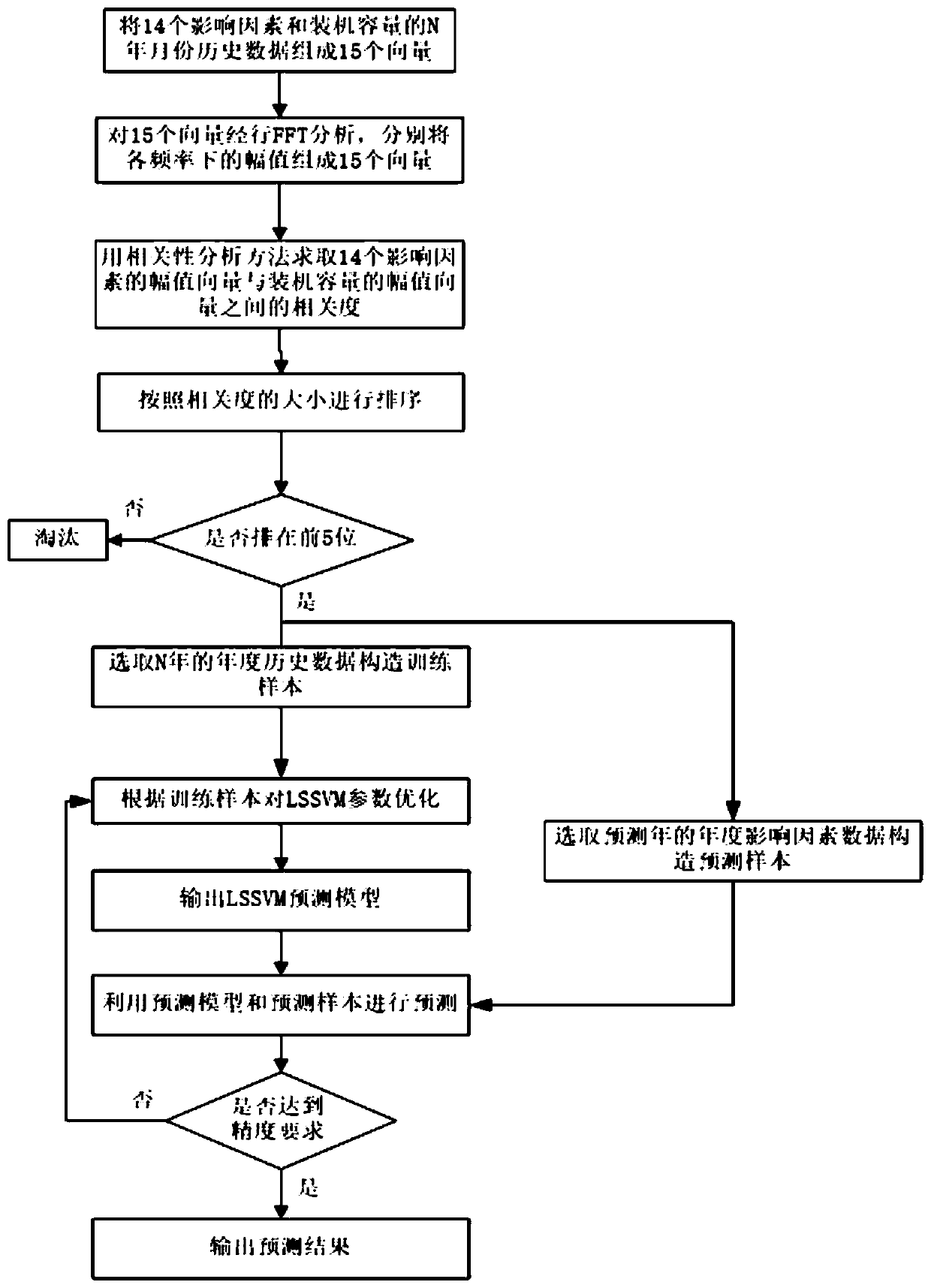
InactiveCN111461208AFully excavatedEasy to trainForecastingCharacter and pattern recognitionTest sampleSimulation
The invention discloses a development scale prediction method and system suitable for a distributed energy supply system, and the method comprises the steps: selecting impact factors which may affectthe development of the distributed energy supply system; performing FFT conversion on the impact factors and historical data of the installed capacity of the distributed energy supply system to obtainamplitude-frequency characteristics of the historical data to form an amplitude-frequency characteristic vector; utilizing a correlation analysis strategy to solve the correlation between the influence factor and the amplitude-frequency characteristic vector of the installed capacity; selecting the influence factors with the relevancy ranked in the first 5 and annual data of the installed capacity in the same period, and constructing a training sample, a test sample and a prediction sample; and performing training and parameter optimization on the LSSVM by using the training sample, outputting a prediction model after training is completed, and predicting the installed capacity of the distributed energy supply system by using the prediction model. According to the method, the installed capacity of the distributed energy supply system under the influence of multiple factors can be predicted more comprehensively.
Owner:GUIZHOU POWER GRID CO LTD
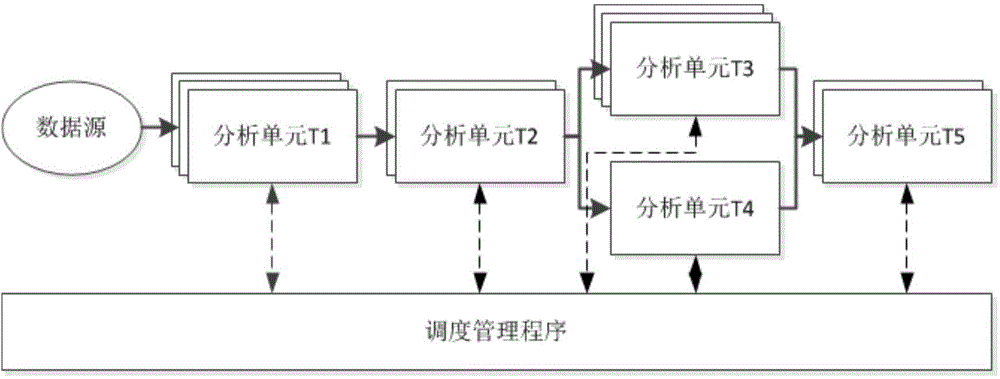
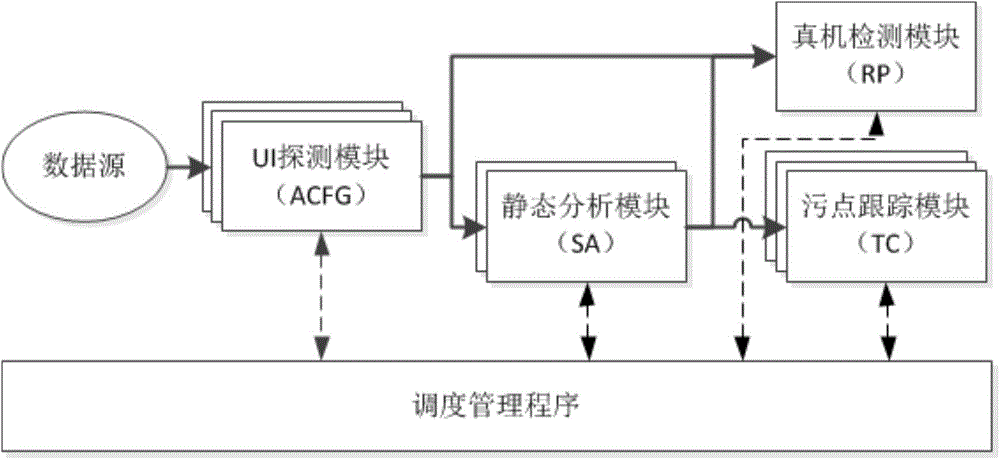
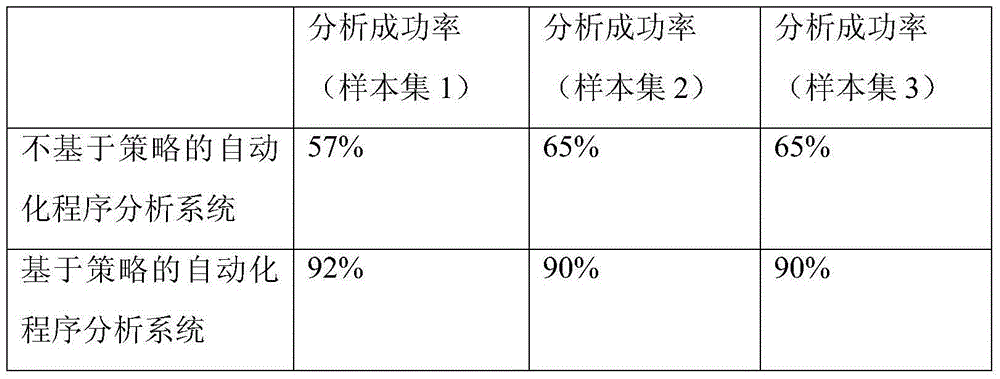
System and method for automatic program analysis based on strategy
ActiveCN106155880AImprove accuracyImplement parallel processingSoftware testing/debuggingData sourceSoftware analytics
The invention relates to a system and a method for automatic program analysis based on a strategy. The system comprises a data source, analysis units, and a dispatching management program. The data source is a set of to-be-analyzed software. The analysis unit is a packaged software analysis module, and is used to communicate with a scheduler, to complete program security analysis of a certain method or a certain stage of assigned software. The dispatching management program is used to configure an analysis strategy, and realizes dispatching and management of an analysis task through analyzing the configured analysis strategy and monitoring states of the plurality of analysis units, to form effective joining and combination of each analysis unit. Through the pre-configured strategy and global task dispatching, a plurality of analysis modules or a plurality of analysis stages are automatically joined, so as to realize a complete, efficient, and automatic analysis process of a program.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
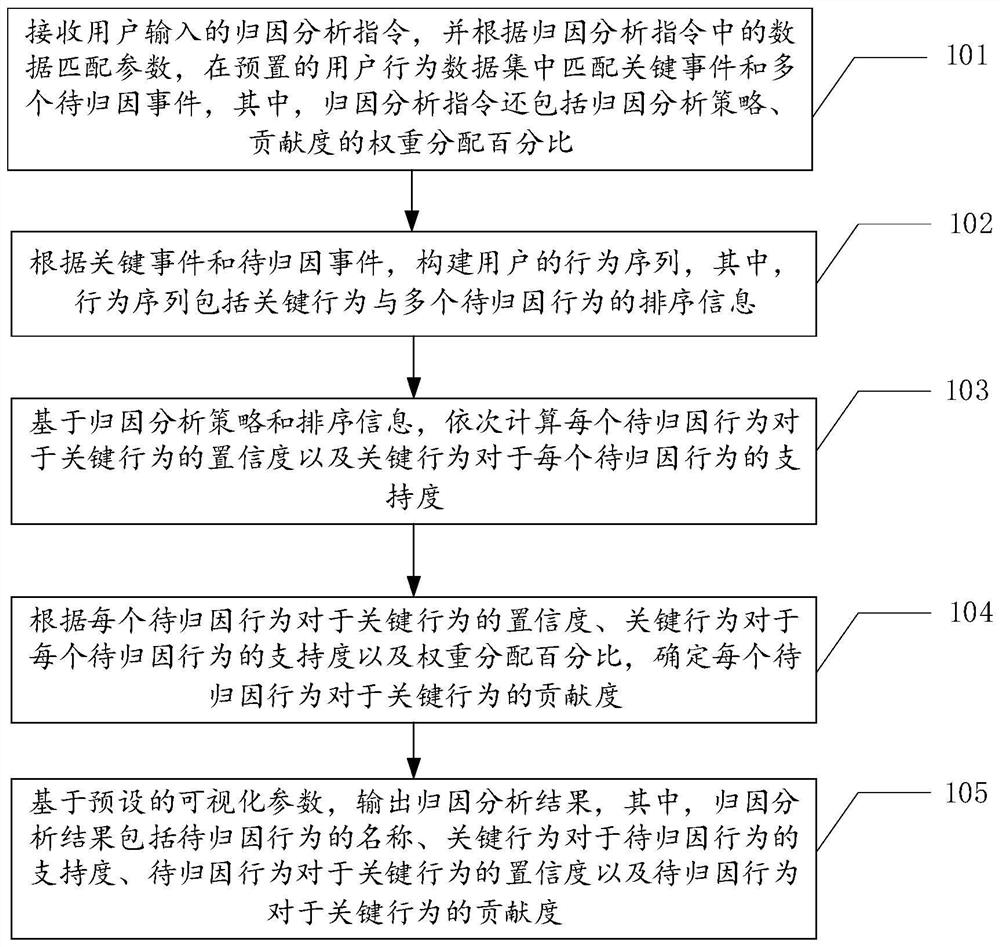
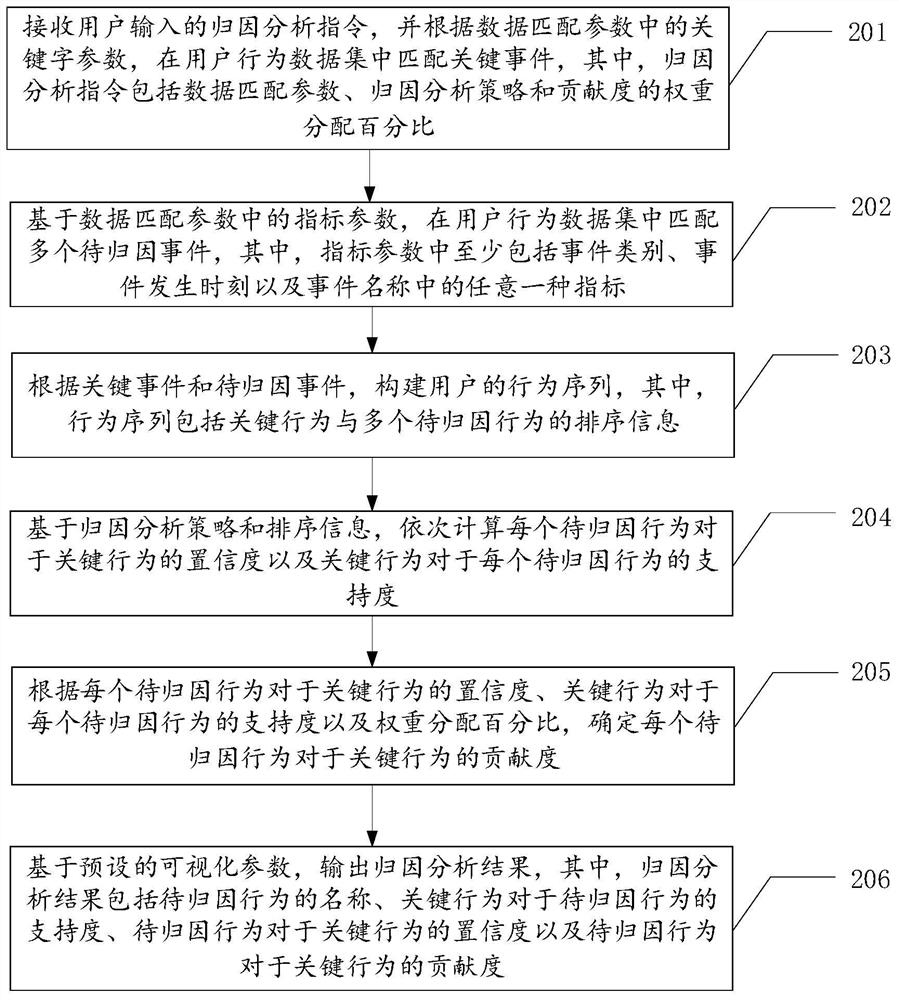
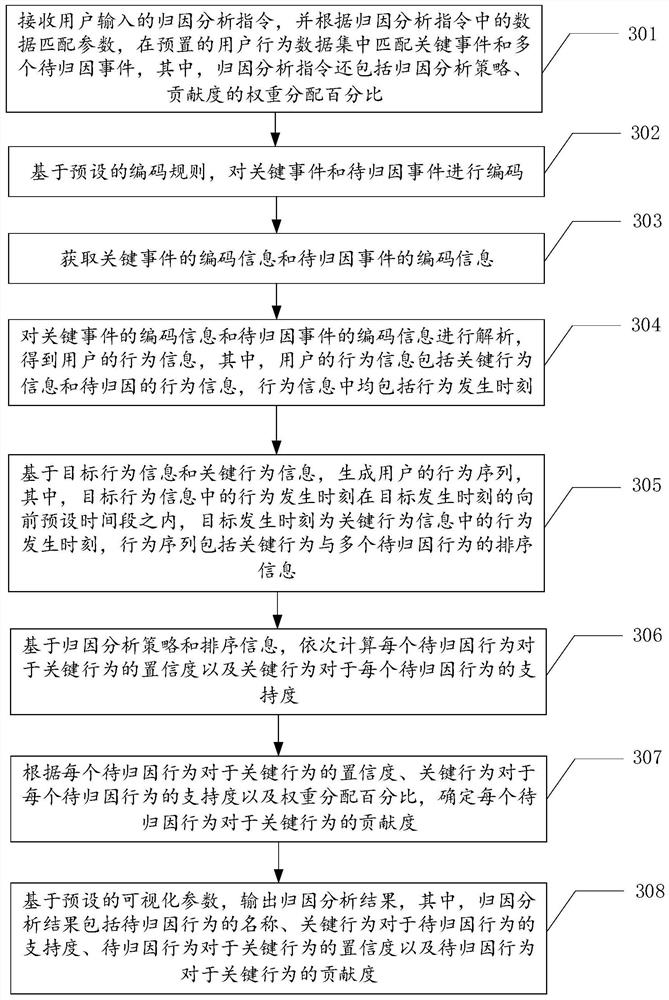
Attribution analysis method and device, equipment and storage medium
The invention relates to the field of big data, and discloses an attribution analysis method and device, equipment and a storage medium. The attribution analysis method comprises the steps of: receiving an attribution analysis instruction input by a user, and matching key events and to-be-attributed events in a user behavior data set according to data matching parameters in the attribution analysis instruction; constructing a behavior sequence of the user according to the key event and the to-be-attributed event; calculating the confidence degree of each to-be-attributed behavior to the key behavior and the support degree of the key behavior to each to-be-attributed behavior based on the attribution analysis strategy and the sorting information in the behavior sequence; according to the confidence degree, the support degree and a weight distribution percentage in an attribution analysis instruction, determining the contribution degree of each to-be-attributed behavior to the key behavior; and outputting attribution analysis result based on preset visual parameter. According to the method, the contribution degree of the behavior is determined by combining the confidence coefficient and the support degree, so that the analysis result is more accurate.
Owner:PINGAN PUHUI ENTERPRISE MANAGEMENT CO LTD
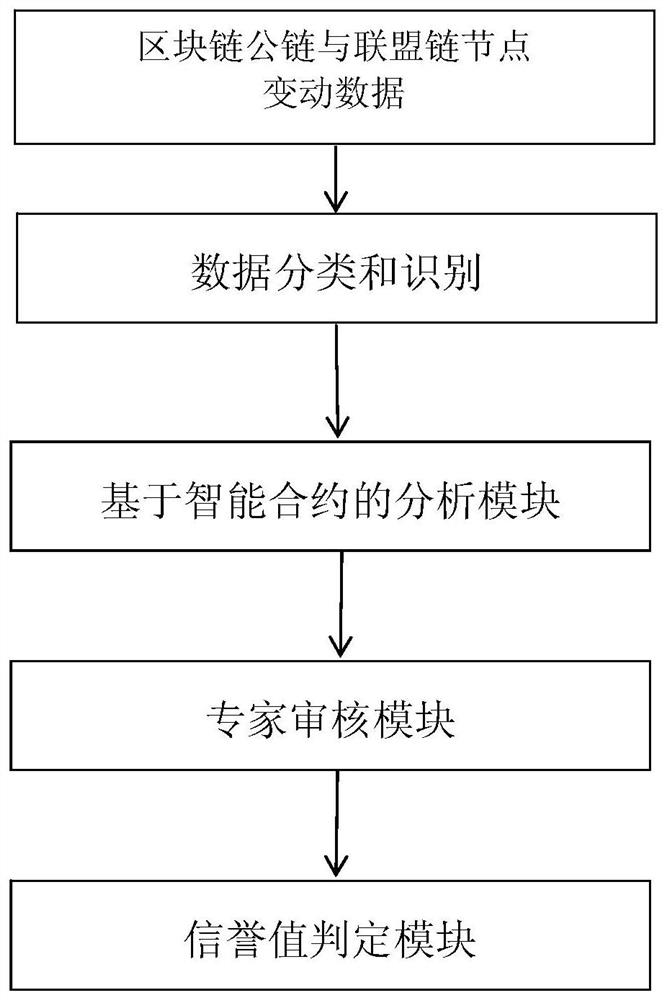
Credible threat intelligence identification method and device based on blockchain consensus mechanism
The invention discloses a credible threat intelligence identification method and device based on a blockchain consensus mechanism. The method comprises the following steps: bringing each node of an intelligence data source into a blockchain to form an intelligence data blockchain, and monitoring each node of the blockchain to obtain intelligence data; matching a corresponding analysis strategy according to a data analysis mode of the information data to obtain a corresponding analysis result; using an intelligent contract to execute processing of an analysis result of the information data andbroadcasting the analysis result to nodes of the whole network through a blockchain network, and generating a piece of unique queried data of the whole network after the whole network reaches a consensus; and endowing a reputation value by adopting the consensus mechanism, and judging whether the information is credible or threatening information according to the reputation value. In the invention, an intelligent contract and strategy directional analysis are combined, the collected block chain data are integrated and analyzed, an threat intelligence event on the block chain is ensured to be discovered at the first time, and meanwhile an advantage of accuracy of a data analysis result is possessed.
Owner:ARMY ENG UNIV OF PLA
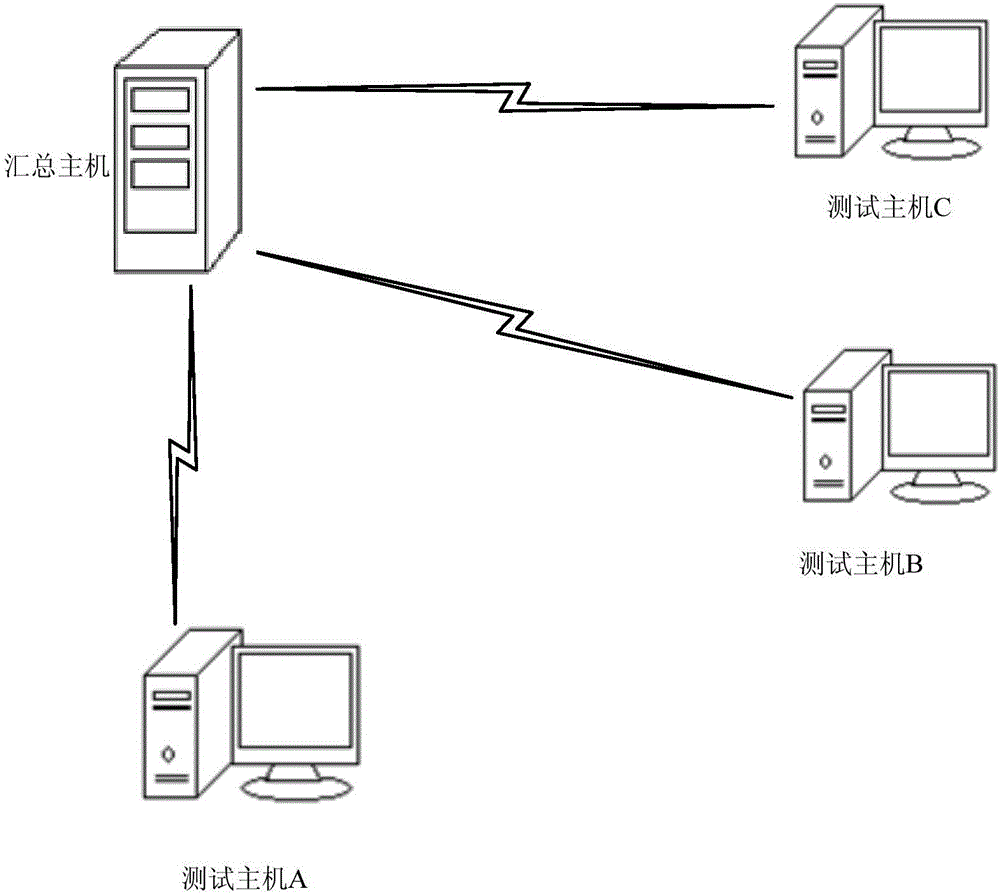
Test result analysis method and apparatus
ActiveCN106649121AAutomate analysisGuaranteed accuracySoftware testing/debuggingAnalytical strategyRepeatability
The invention provides a test result analysis method and apparatus. The test result analysis method comprises the steps of obtaining corresponding software test results from different test hosts; performing data mining and deformation on the software test results according to the dimensions of the software test results to generate test results in predetermined formats; and analyzing the test results in the predetermined formats by utilizing a pre-created analytic strategy pool to generate an analysis result, wherein the analytic strategy pool contains multiple different analytic strategies. By utilizing the method and the apparatus, automated analysis of the software test results can be realized, so that manual repeated operations are avoided and data arrangement and analysis accuracy is ensured; and differential comparison of actual software test results and expected results can be automatically realized.
Owner:CHINA UNIONPAY
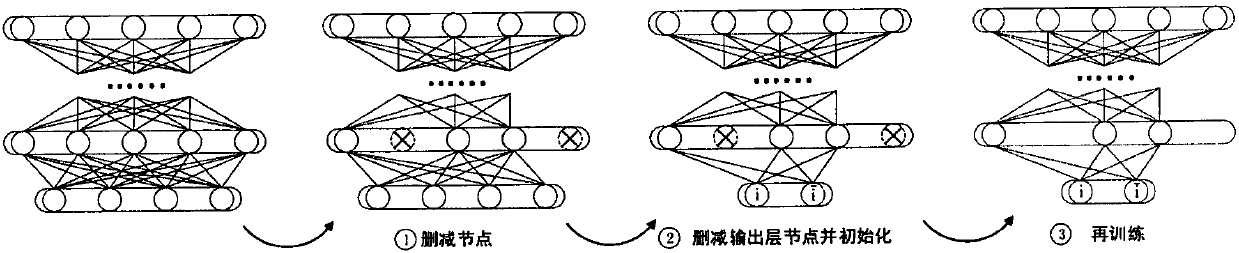
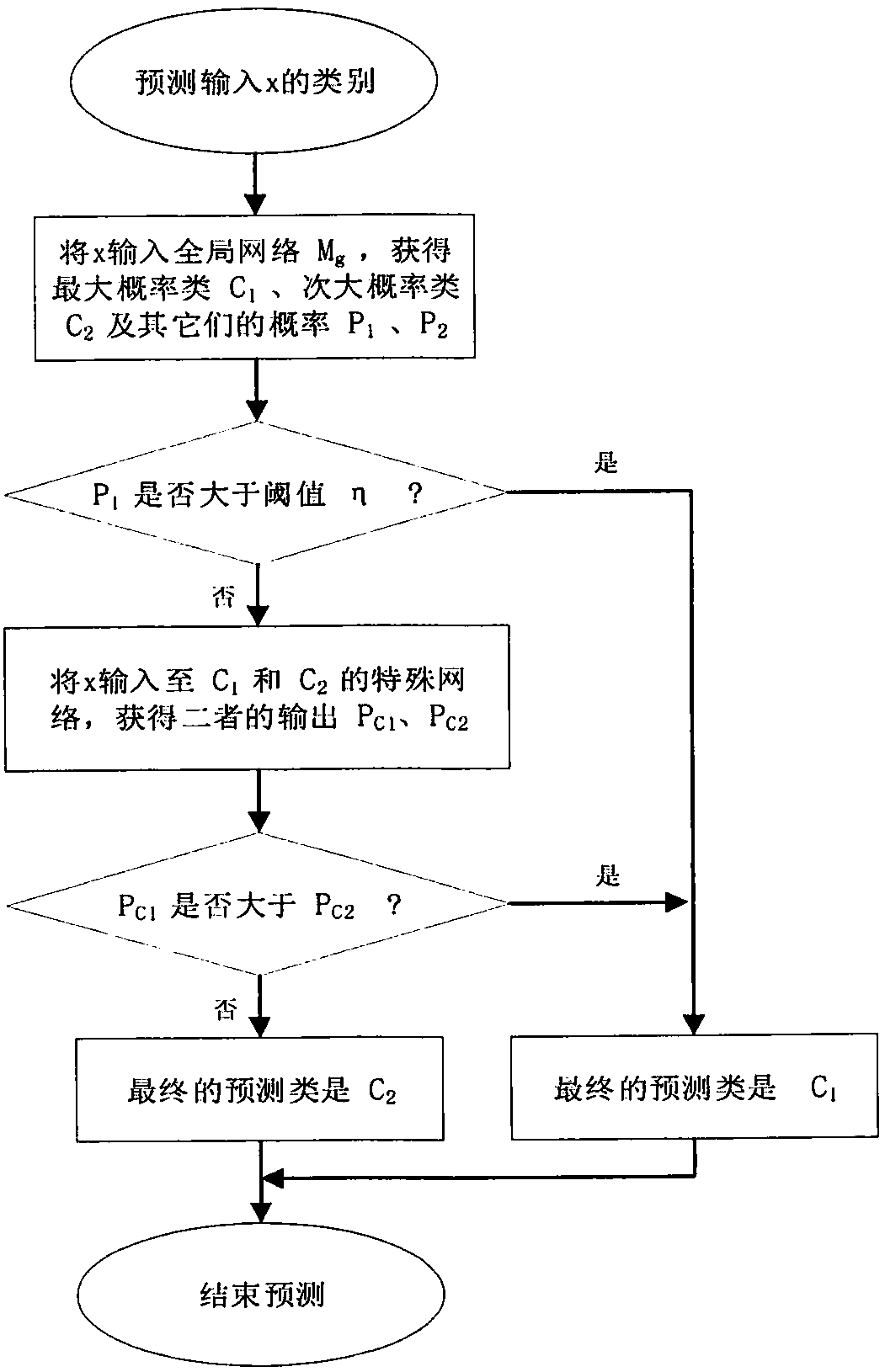
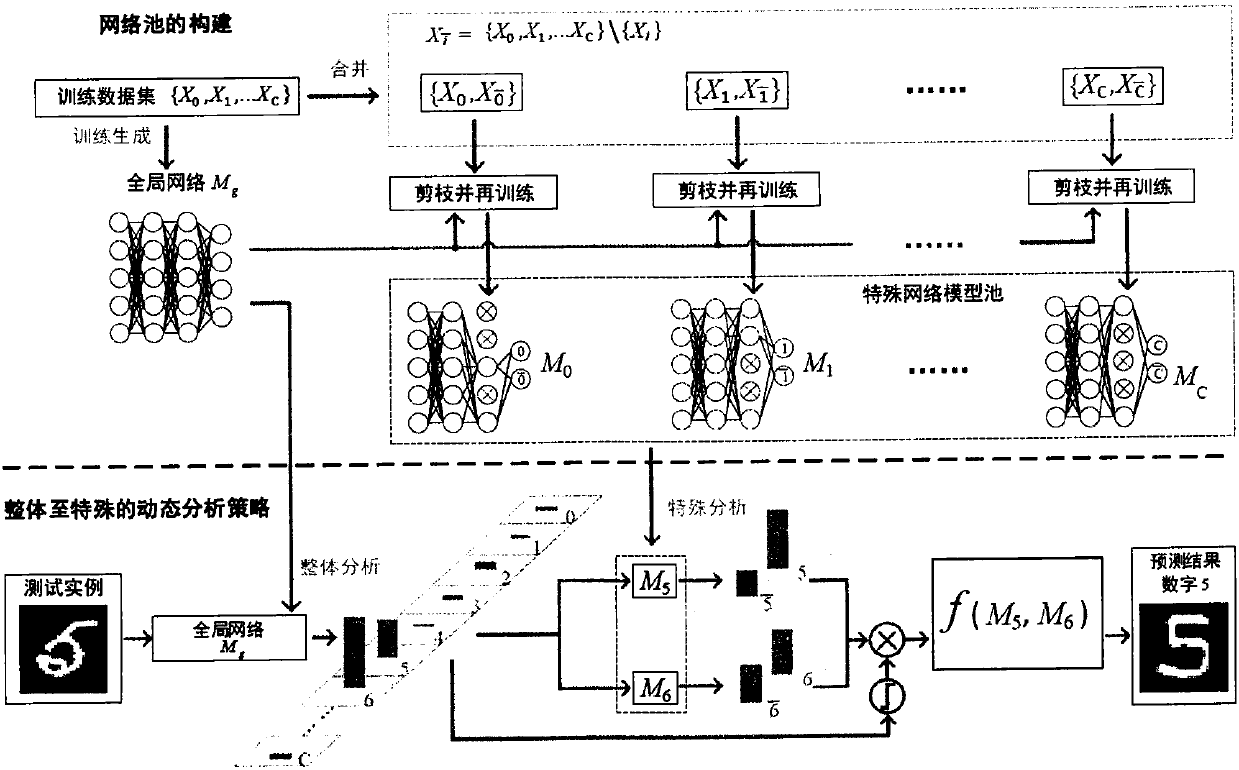
Dynamic depth confidence network analysis method
ActiveCN108446718ATargetedImprove accuracyCharacter and pattern recognitionNeural learning methodsNetwork structureAnalytical strategy
The invention relates to the field of deep learning and relates to a dynamic network structure training analysis method based on a depth confidence network. The invention aims to overcome the severaldefects of the depth confidence network, and an overall-special dynamic network structure training analysis strategy from and based on the depth confidence network is provided. According to the strategy, a fine analysis process is introduced according to an analysis strategy of the brain when the human identifies an object. According to the strategy, two networks are generated in the training stage for the classification problem and comprise a global network and a plurality of special networks for specific categories. In the prediction stage, the output results of the two networks are comprehensively considered, so that the prediction of the whole model is more targeted, and the accuracy of the classification model is improved.
Owner:TONGJI UNIV
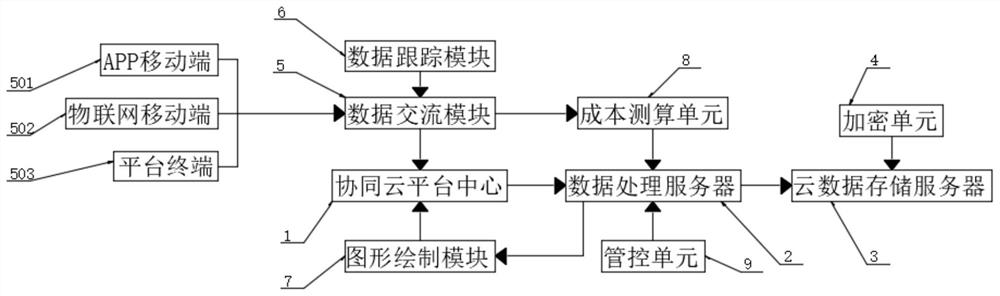
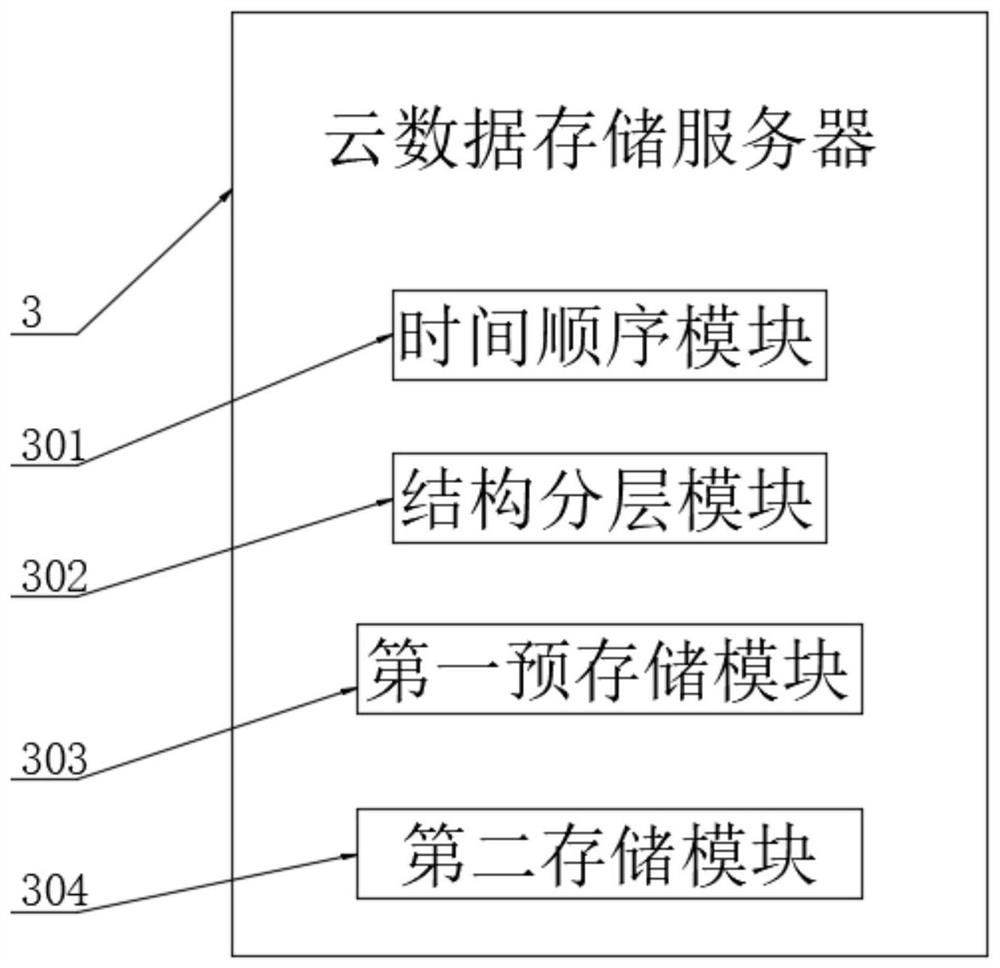
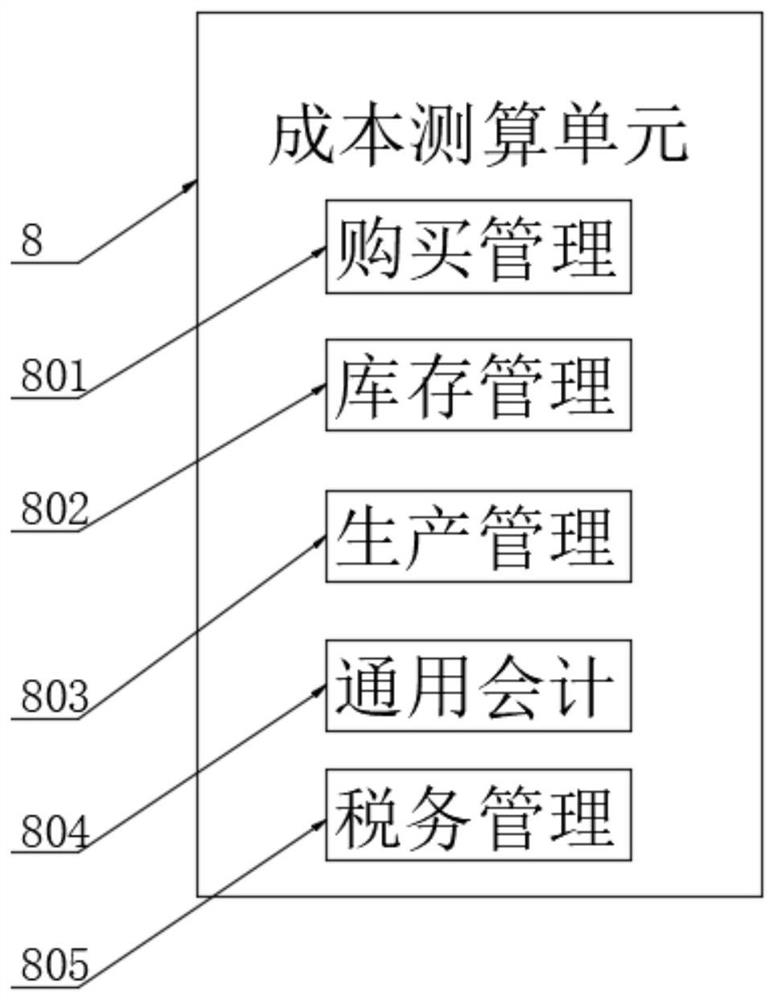
Cost management and control system based on collaborative office platform
PendingCN112633818AEnsure safetyImprove cost control abilityOffice automationPlatform integrity maintainanceGraphicsControl system
The invention discloses a cost management and control system based on a collaborative office platform, and belongs to the technical field of collaborative office. The system comprises a collaborative flat holder center, wherein the input end of the collaborative flat holder center is connected with a data communication module and a graph drawing module, and the output end of the data communication module is connected with a cost calculation unit; and the cost calculation unit is connected with a data processing server. According to the invention, the dynamic cost rate is compared through the analysis strategy provided by the analysis strategy module, and when the cost rate reaches the early warning value, the dynamic cost early warning is started, so the platform office data can be updated and traced in real time through the data communication module and the data tracking module; and the data can be gathered and stored by cooperating with the cloud platform center, so the instantaneity and security of data communication are ensured, the cost management and control capability of multi-platform office can be improved by the management and control unit and the cost measurement and calculation unit, and the overall management and control requirements are met.
Owner:易筑网络科技(苏州)有限公司
Enterprise information data processing method and system, terminal and storage medium
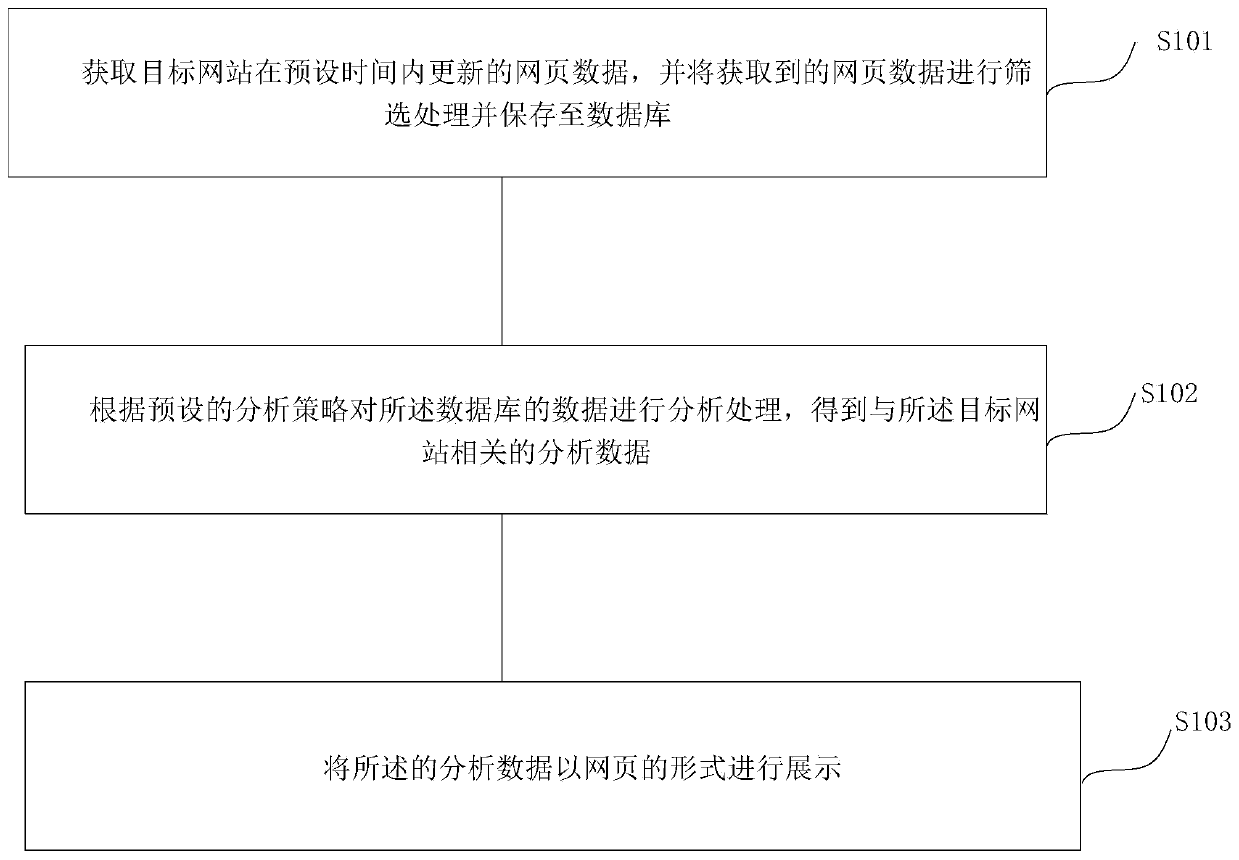
InactiveCN110837595ARealize automatic collectionAchieve preservationWebsite content managementSpecial data processing applicationsWeb siteAnalysis data
The invention provides an enterprise information data processing method and system, a terminal and a storage medium, and the method comprises the steps: obtaining webpage data updated by a target website in a preset time, carrying out the screening of the obtained webpage data, and storing the webpage data in a database; analyzing and processing the data of the database according to a preset analysis strategy to obtain analysis data related to the target website; and displaying the analysis data in the form of a webpage. The problems that in the prior art, an information information data search engine is high in search repetition rate, limited in coverage content, poor in timeliness, time-consuming in manual downloading, saving and displaying of information information data, low in efficiency and the like are solved, and automatic collection, typesetting, saving and displaying of the information data can be achieved.
Owner:BEIJING GAS GRP
Service management method and device
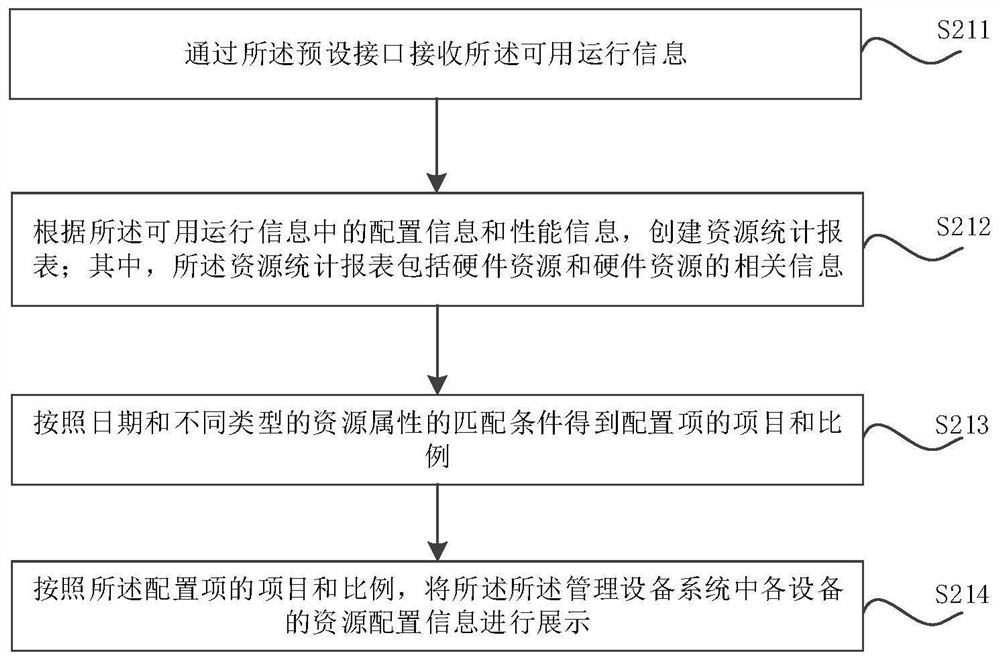
PendingCN111669295AClosed loopReduce processingData switching networksManagement efficiencyMultithreading
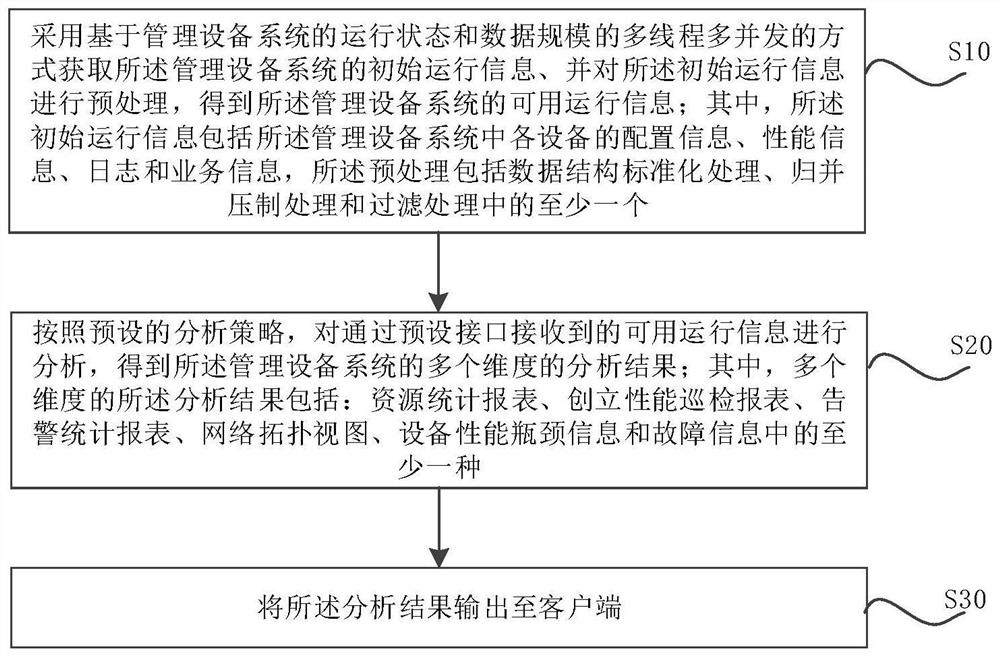
The invention relates to a service management method and device. The method comprises the following steps: acquiring initial operation information of a management equipment system by adopting a multi-thread multi-concurrency mode based on an operation state and a data scale of the management equipment system, and preprocessing the initial operation information to obtain available operation information of the management equipment system; analyzing the available operation information received through a preset interface according to a preset analysis strategy to obtain multi-dimensional analysisresults of the management equipment system, wherein the analysis results of the multiple dimensions comprise at least one of a resource statistics report, a creation performance inspection report, analarm statistics report, a network topology view, equipment performance bottleneck information and fault information; and outputting the analysis result to a client. By adopting the method, the service management efficiency can be improved.
Owner:CHINA SOUTHERN POWER GRID DIGITAL GRID RES INST CO LTD
Multi-level deep fusion mining method for multi-mode cross-boundary big data of commercial vehicles
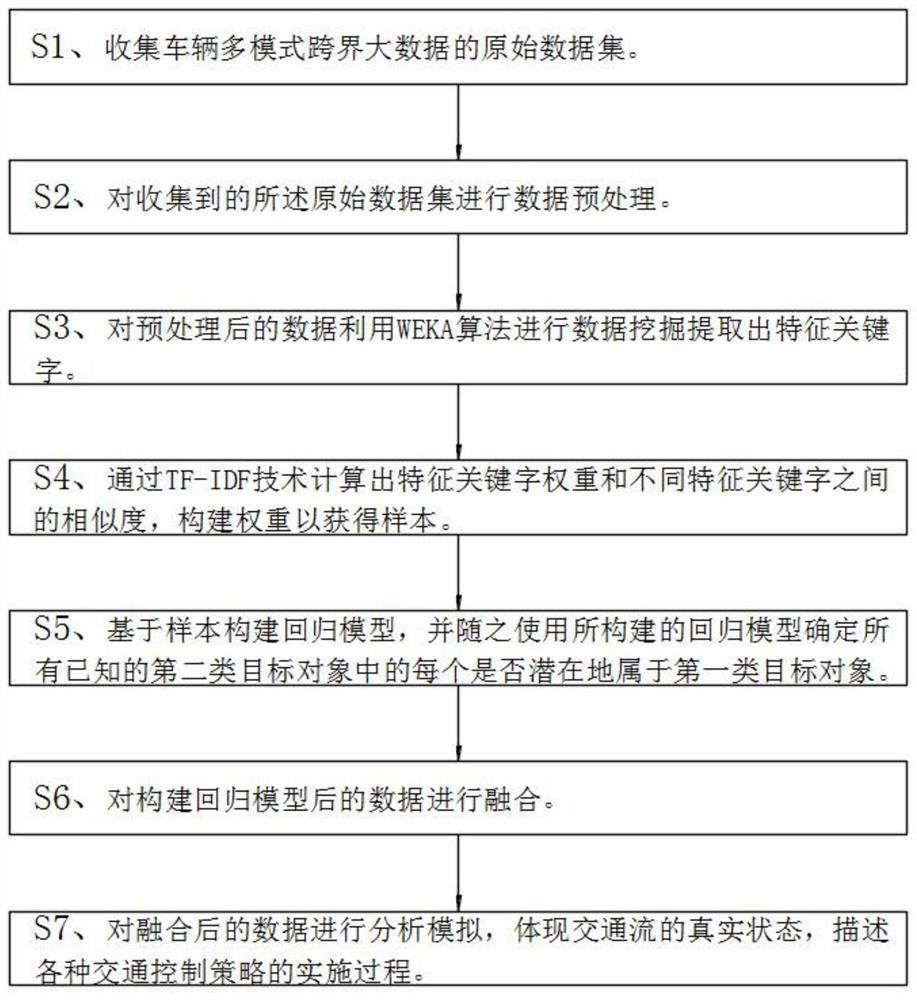
PendingCN111984707AEfficient integrationSolve efficiency problemsData processing applicationsDigital data information retrievalData classFeature extraction
The invention discloses a multi-level deep fusion mining method for multi-mode cross-boundary big data of commercial vehicles. The method comprises the following steps: S1, collecting an original dataset of multi-mode cross-boundary big data of a vehicle; s2, performing data preprocessing on the collected original data set; s3, performing data mining on the preprocessed data by using a WEKA algorithm to extract feature keywords; s4, calculating the weights of the feature keywords and the similarity between the different feature keywords through a TF-IDF technology, and constructing a weight and similarity matrix; and S5, constructing a regression model based on the sample. According to the invention, via t-SNE dimension reduction, WEKA algorithm feature extraction and a TF-IDF algorithm,an analysis strategy of dimension reduction and feature extraction in sequence is adopted for high-dimensional data, effective fusion of multi-level deep fusion mining of cross-boundary big data is achieved, and the problems that due to a high-dimensional data set with complex data types and numerous data features, the fusion efficiency is low, and the working efficiency is not remarkably improvedare solved.
Owner:重庆大数据研究院有限公司
Pretreatment method and device for fetal concentration calculation and application thereof
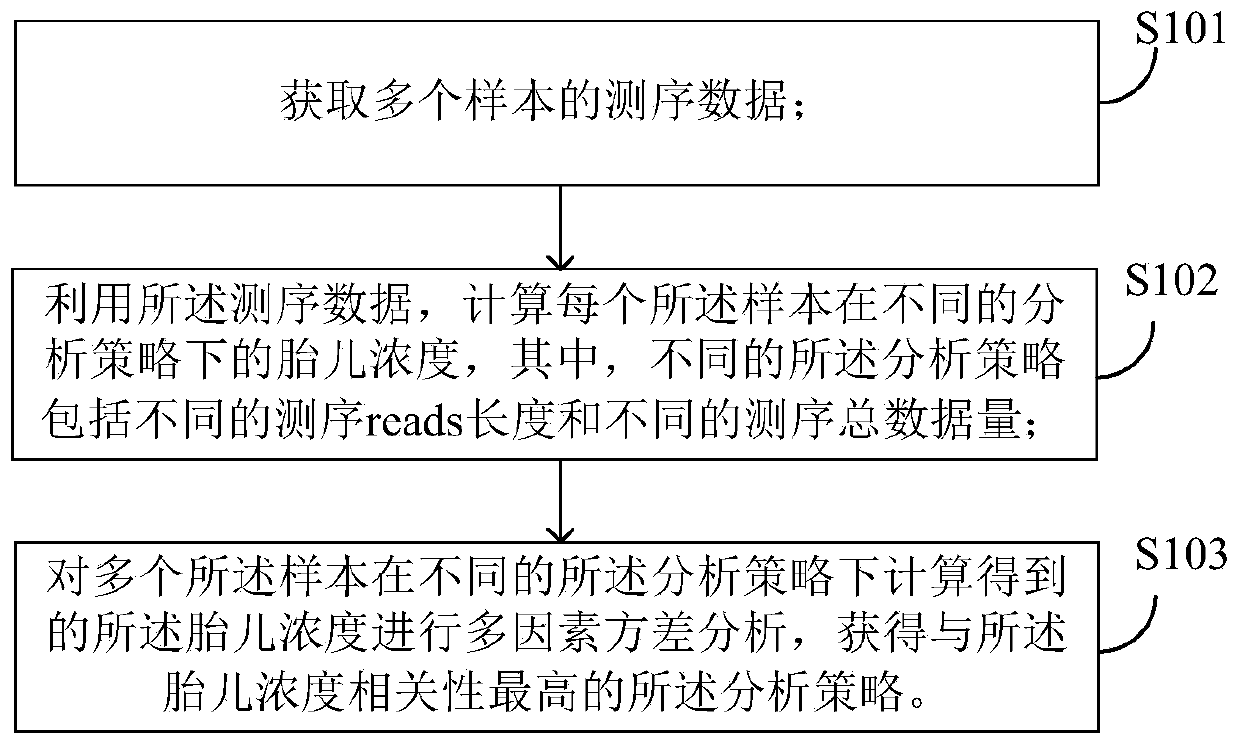
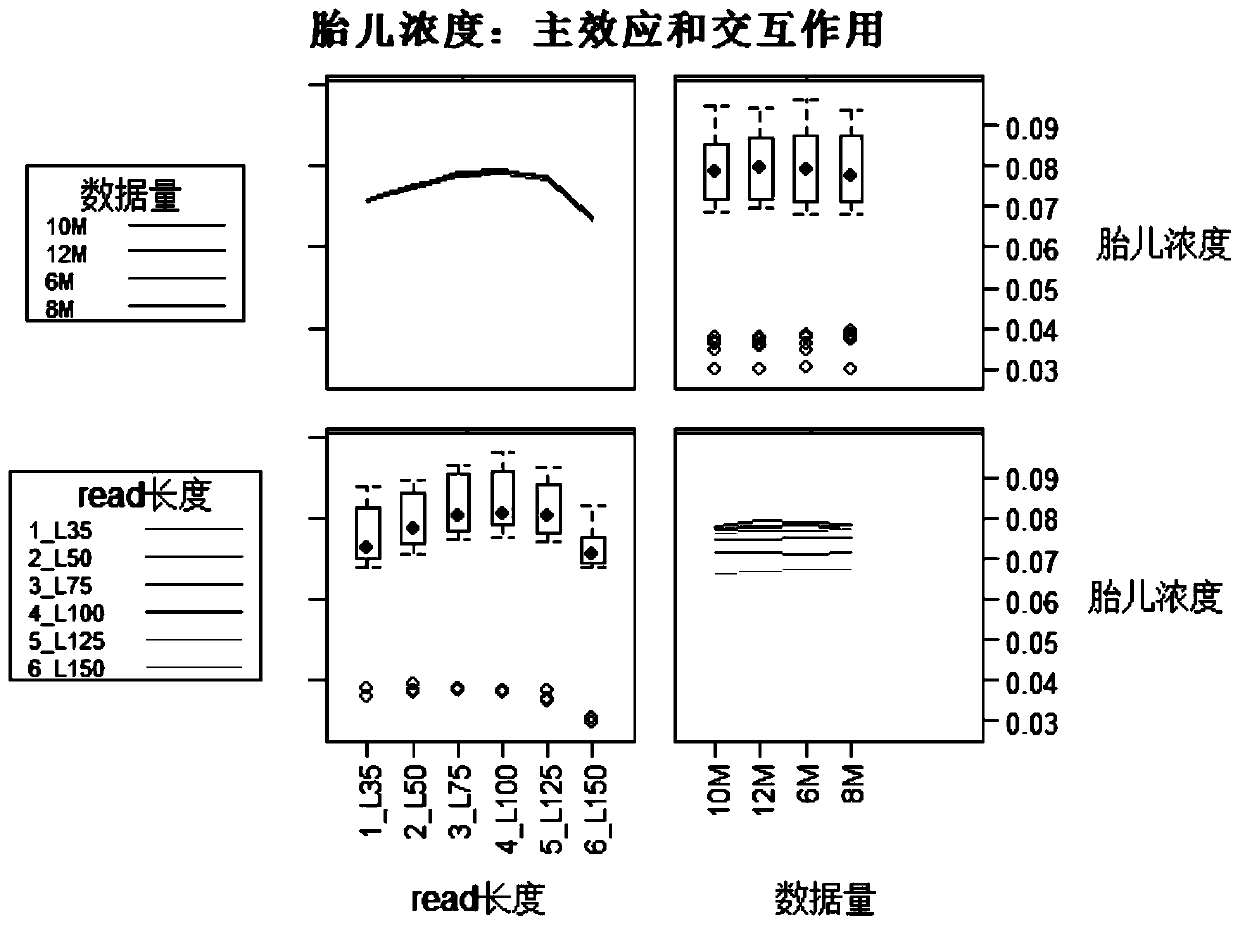
ActiveCN110970089AEasy to analyze and calculateImprove accuracySequence analysisInstrumentsPretreatment methodAnalytical strategy
The invention provides a preprocessing method and device for fetal concentration calculation and an application thereof. The preprocessing method comprises the following steps: acquiring sequencing data of a plurality of samples; calculating the fetal concentration of each sample under different analysis strategies by utilizing the sequencing data, wherein the different analysis strategies comprise different sequencing reads lengths and different sequencing total data volumes; and performing multi-factor variance analysis on the fetal concentrations obtained by calculating the plurality of samples under different analysis strategies to obtain an analysis strategy with the highest correlation with the fetal concentrations. According to the invention, through the multi-factor variance analysis on fetal concentrations obtained under different sequencing strategies, different sequencing reads lengths, different sequencing total data volumes and the correlation between the interaction of the sequencing reads lengths and the sequencing total data volumes and fetal concentration calculation are obtained, and then the analysis strategy with the highest correlation is obtained, so that theanalysis strategy with the highest correlation is conveniently adopted for analysis and calculation during subsequent fetal concentration calculation, and the calculation accuracy is improved.
Owner:BEIJING USCI MEDICAL DEVICES CO LTD
Real-time analysis method of multi-segment link network and bypass packet capturing system
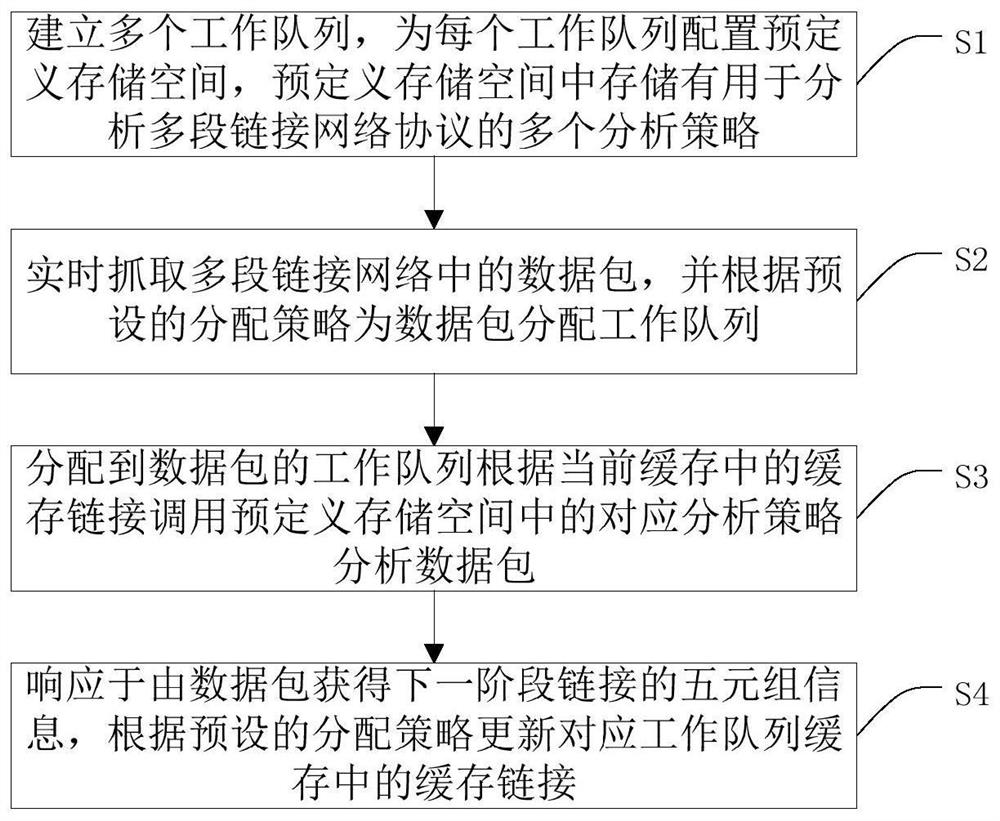
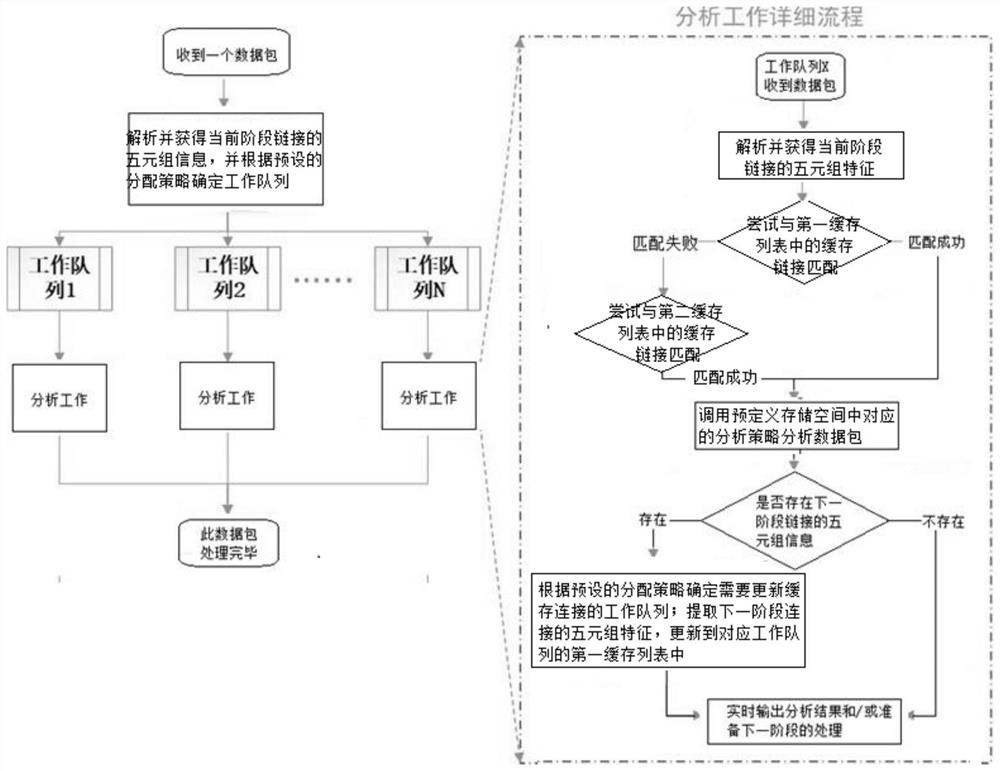
ActiveCN113098911AEnable real-time analysisImprove analytical performanceData switching networksData packReal time analysis
The invention provides a real-time analysis method of a multi-segment link network and a bypass packet capturing system. The method comprises the steps: establishing a plurality of work queues and configuring a predefined storage space for each work queue, wherein a plurality of analysis strategies used for analyzing the multi-segment link network protocol are stored in the predefined storage spaces; capturing a data packet in the multi-segment link network in real time, and distributing a working queue for the data packet according to a preset distribution strategy; calling, by the work queue distributed to the data packet, a corresponding analysis strategy in a predefined storage space to analyze the data packet according to a cache link in the current cache; and in response to the quintuple information of the next-stage link obtained by the data packet, updating the cache link in the corresponding working queue cache according to a preset allocation strategy. According to the method, the cache links in the caches of the corresponding working queues are updated in advance by configuring the plurality of working queues, so that real-time analysis of the multi-segment link network is realized, and the analysis capability and the analysis speed are improved.
Owner:神州灵云(北京)科技有限公司
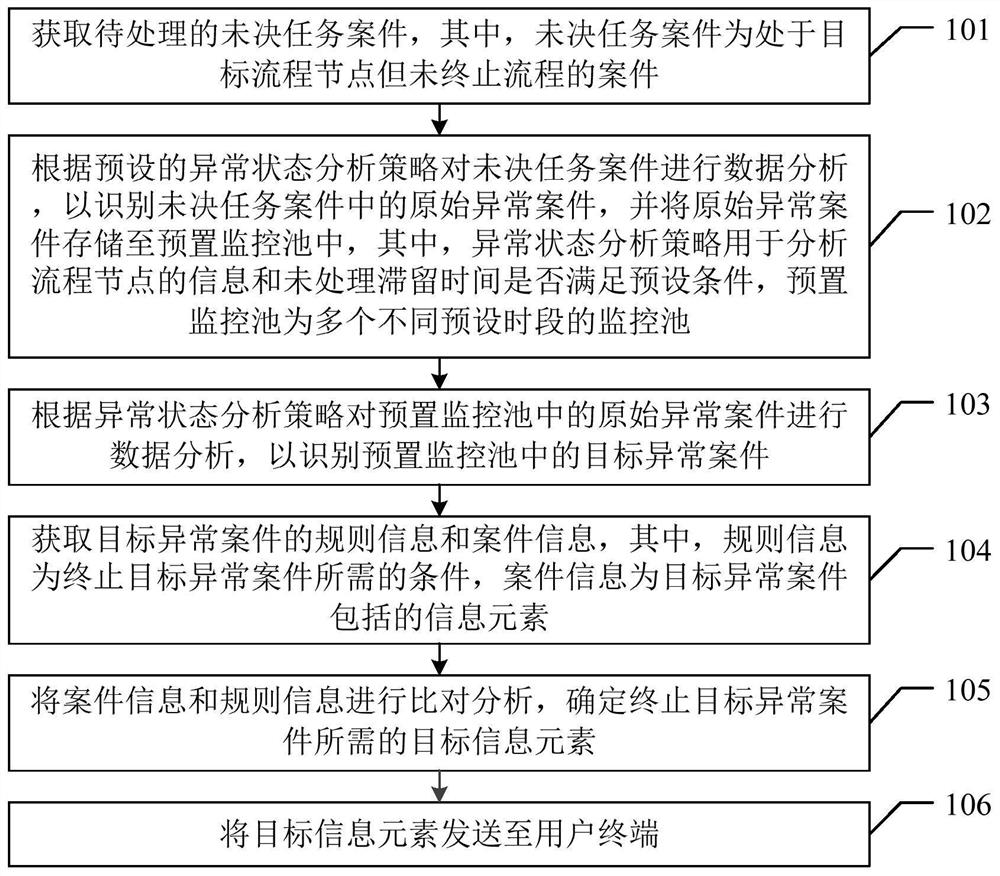
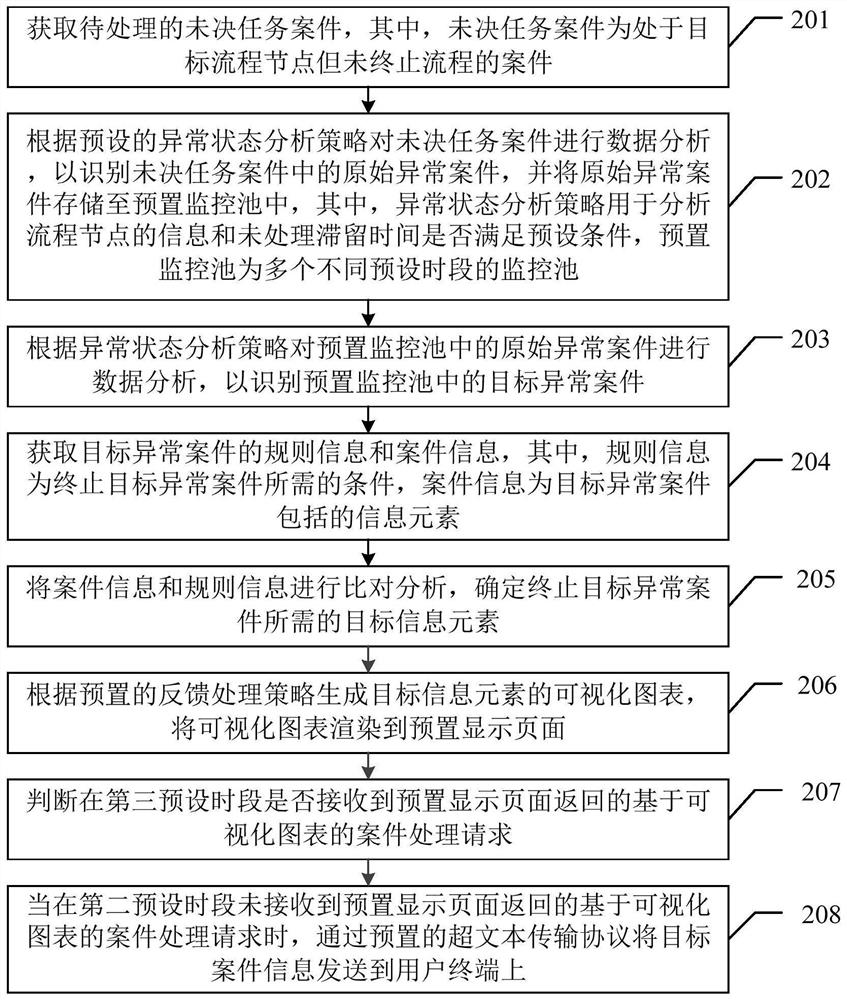
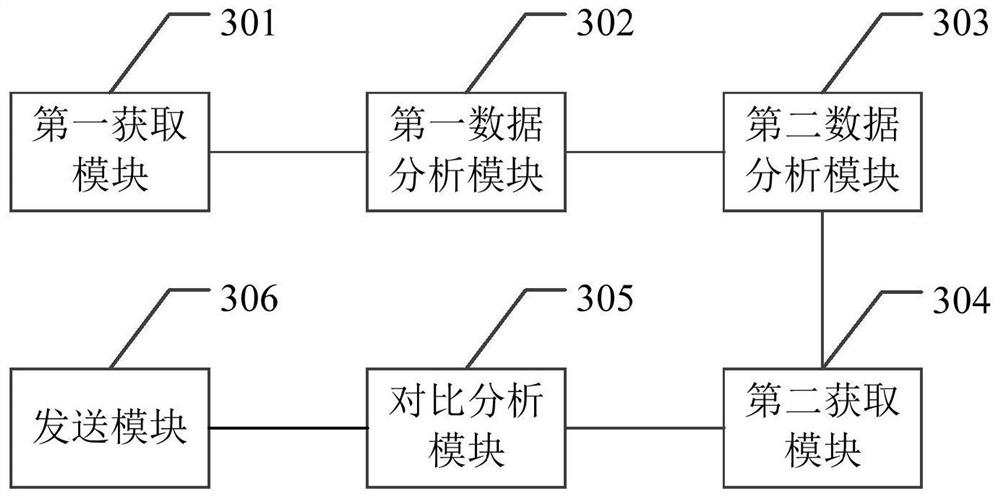
Method, device and equipment for processing pending task case and storage medium
The invention relates to the field of cloud services, discloses a pending task case processing method, device and equipment and a storage medium, and is used for improving the processing efficiency ofprocess breakpoints of pending task cases. The pending task case processing method comprises the steps of obtaining a pending task case to be processed, performing data analysis on the pending task case according to a preset abnormal state analysis strategy to identify an original abnormal case in the pending task case, and storing the original abnormal case into a preset monitoring pool; carrying out data analysis on the original abnormal case in a preset monitoring pool according to an abnormal state analysis strategy so as to identify a target abnormal case in the preset monitoring pool; obtaining rule information and case information of the target abnormal case; performing comparative analysis on the case information and the rule information, and determining a target information element required for terminating the abnormal case; and sending the target information element to the user terminal. In addition, the invention also relates to a blockchain technology, and the target information element can be stored in the blockchain node.
Owner:CHINA PING AN PROPERTY INSURANCE CO LTD
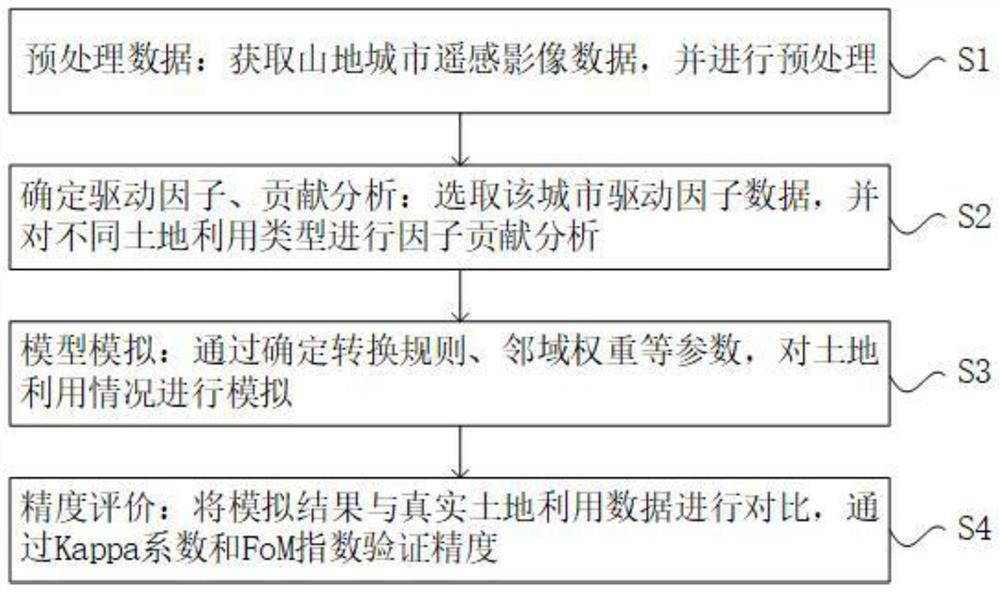
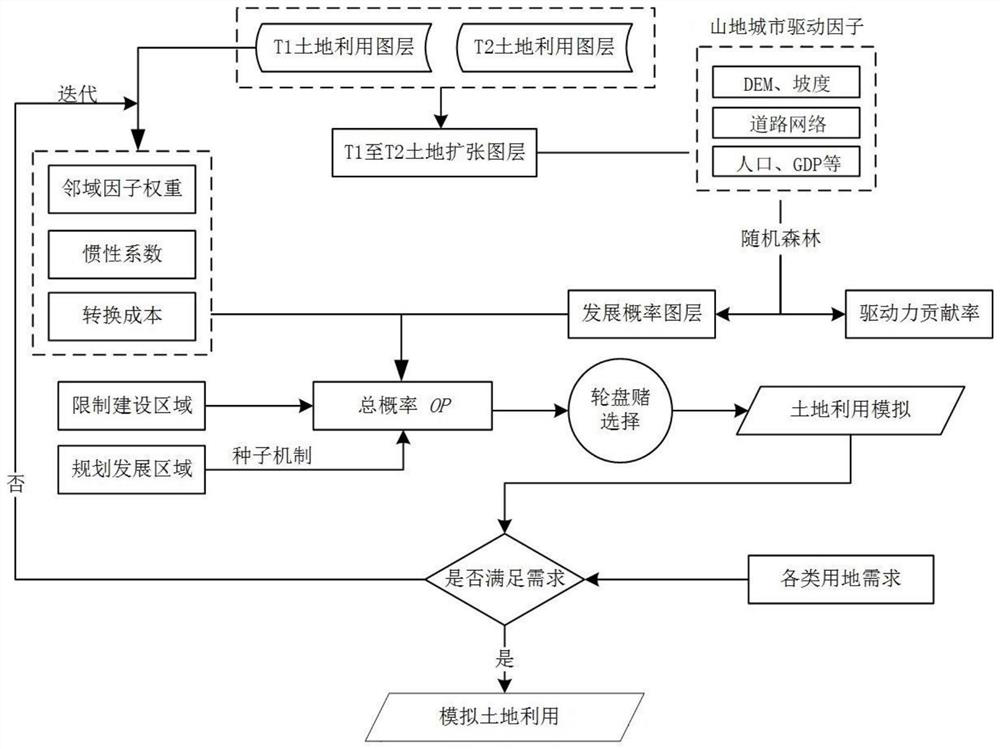
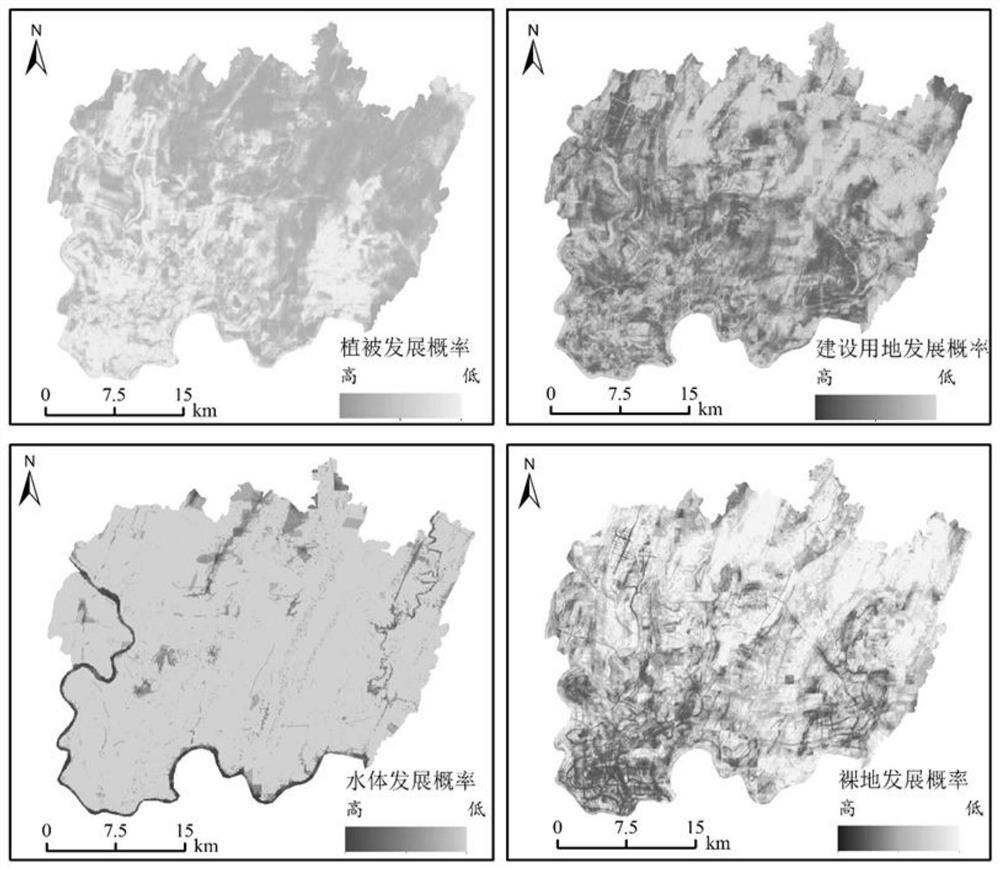
Mountain city land utilization evolution simulation method
PendingCN114417724ASimulation is accurateAccurate analysisScene recognitionDesign optimisation/simulationAlgorithmEngineering
The invention discloses a simulation method for mountain city land utilization evolution, which comprises the following specific steps: S1, data preprocessing: acquiring mountain city remote sensing image data, and preprocessing, S2, driving factor determination and contribution analysis: selecting city driving factor data, and performing factor contribution analysis on different land utilization types, s3, model simulation: simulating the land utilization condition by determining parameters such as a conversion rule and a neighborhood weight, and S4, precision evaluation: comparing a simulation result with real land utilization data, and verifying the precision through a Kappa coefficient and a FoM index. Simulation is carried out on the basis of an improved CA model-PLUS model, a new conversion rule data mining framework in the model can be used for identifying a rule of land utilization change, the advantages of a conversion analysis strategy and a pattern analysis strategy are combined, and the conversion analysis strategy and the pattern analysis strategy are combined by increasing special driving factors of a mountain city and distinguishing the contribution degree of each factor, so that the accuracy of the conversion analysis strategy is improved. The land utilization simulation precision of the mountainous city is improved, so that the driving factors of land utilization evolution of the mountainous city are accurately analyzed, and the land utilization change is accurately simulated.
Owner:HOHAI UNIV
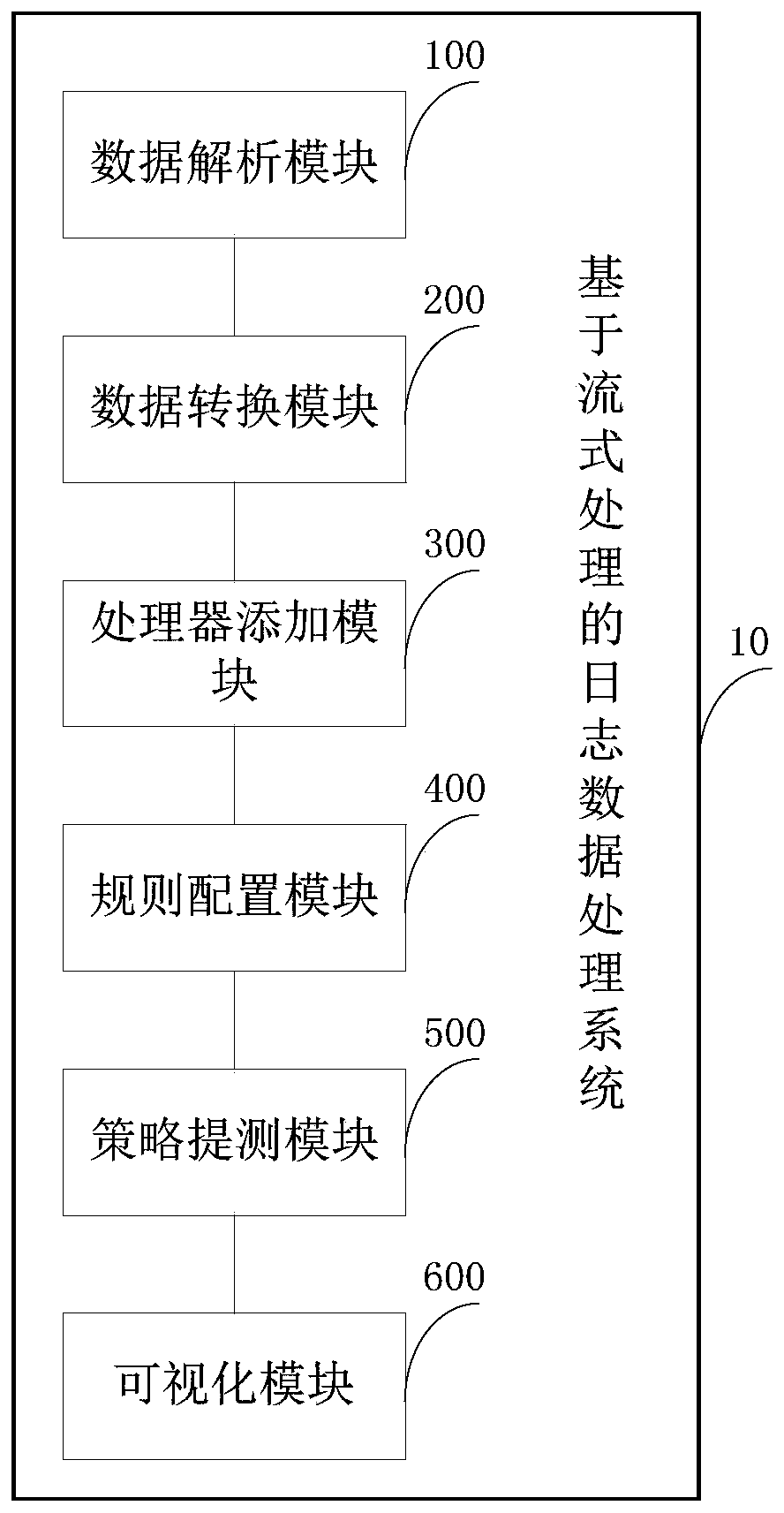
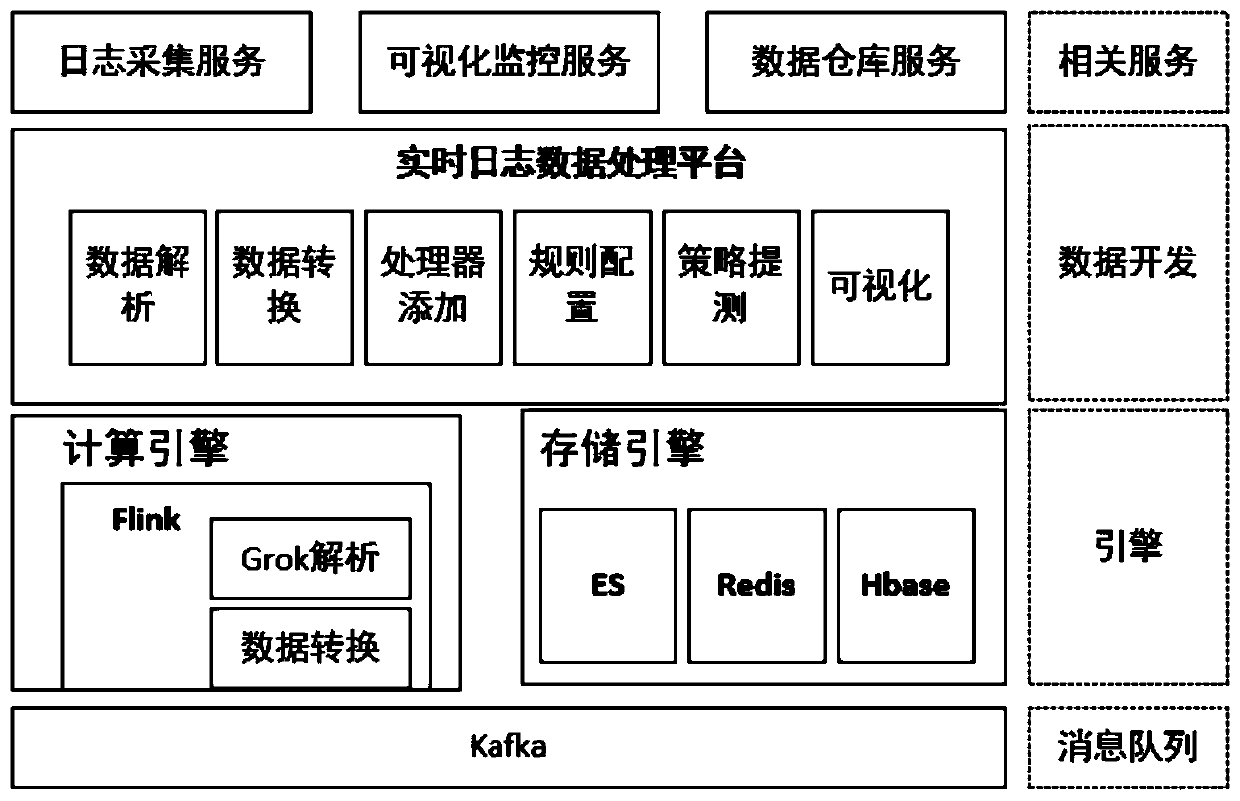
Log data processing system and method based on streaming processing
ActiveCN111459984AGuaranteed correctnessShorten the timeDigital data information retrievalSpecial data processing applicationsInteraction interfaceAnalytical strategy
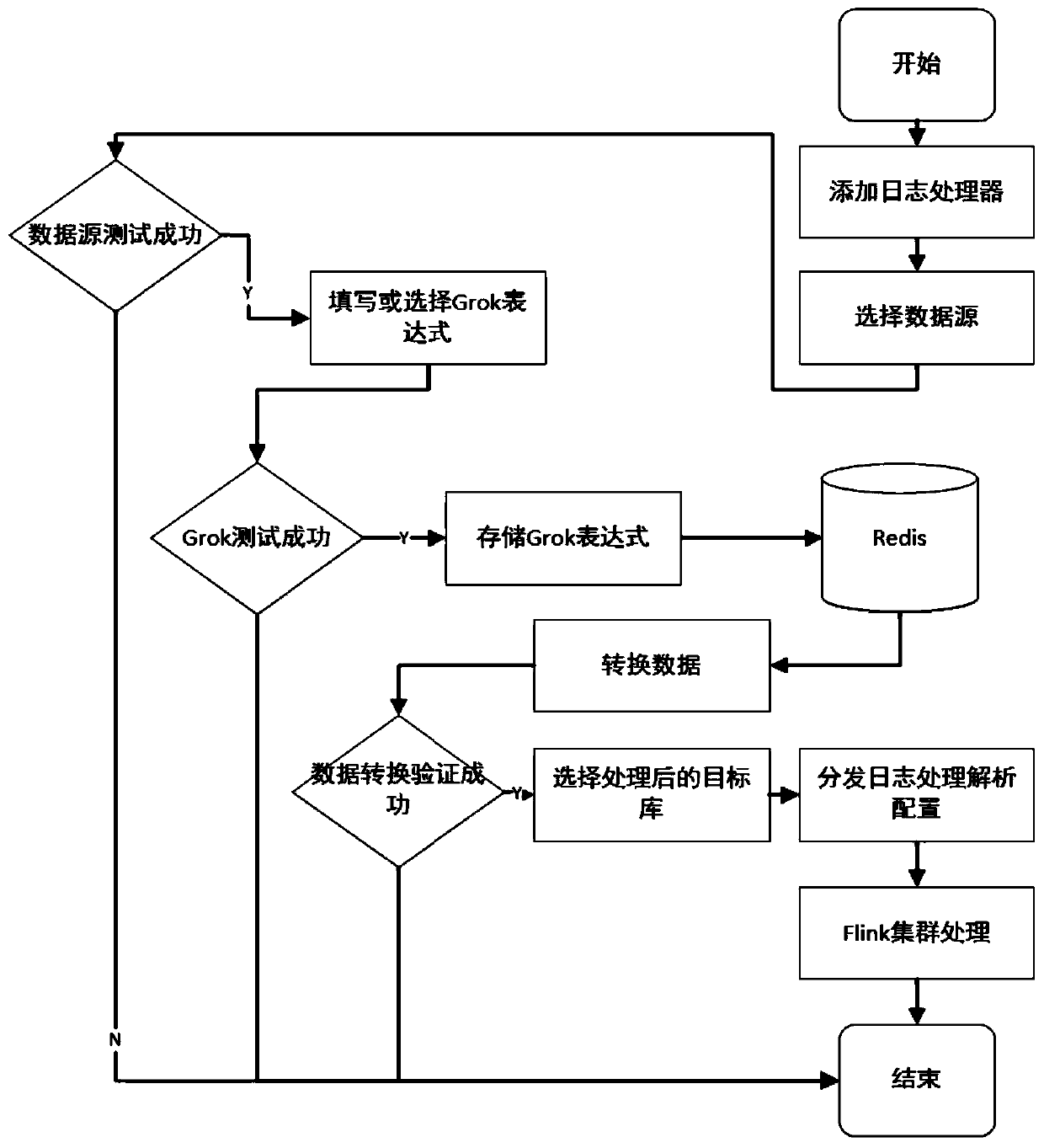
The invention discloses a log data processing system and method based on streaming processing, and the system comprises a rule configuration module which is used for configuring the processing parameters of log flow processing on an interface; a strategy testing module used for carrying out data testing on a log analysis function and a log source; a visualization module used for building a visualization interaction interface on the basis of a Vue framework; a processor adding module used for distributing log data processing tasks to the streaming processing engine cluster for execution; ae data analysis module used for officially processing and analyzing the data and converting the data from unstructured data into structured data in a Grok function analysis mode; and a data conversion module used for matching fields in the structured data and converting the data according to a configuration rule. Real-time data analysis of massive logs, word segmentation generation of an analytical expression under the condition of small and medium data volume, abnormal data processing and real-time measurement of an analytical strategy are realized.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Cheating flow identification method and system applied to API advertisements
PendingCN111311334AIncrease the difficulty of crackingImprove reliabilityAdvertisementsIp addressAnalytical strategy
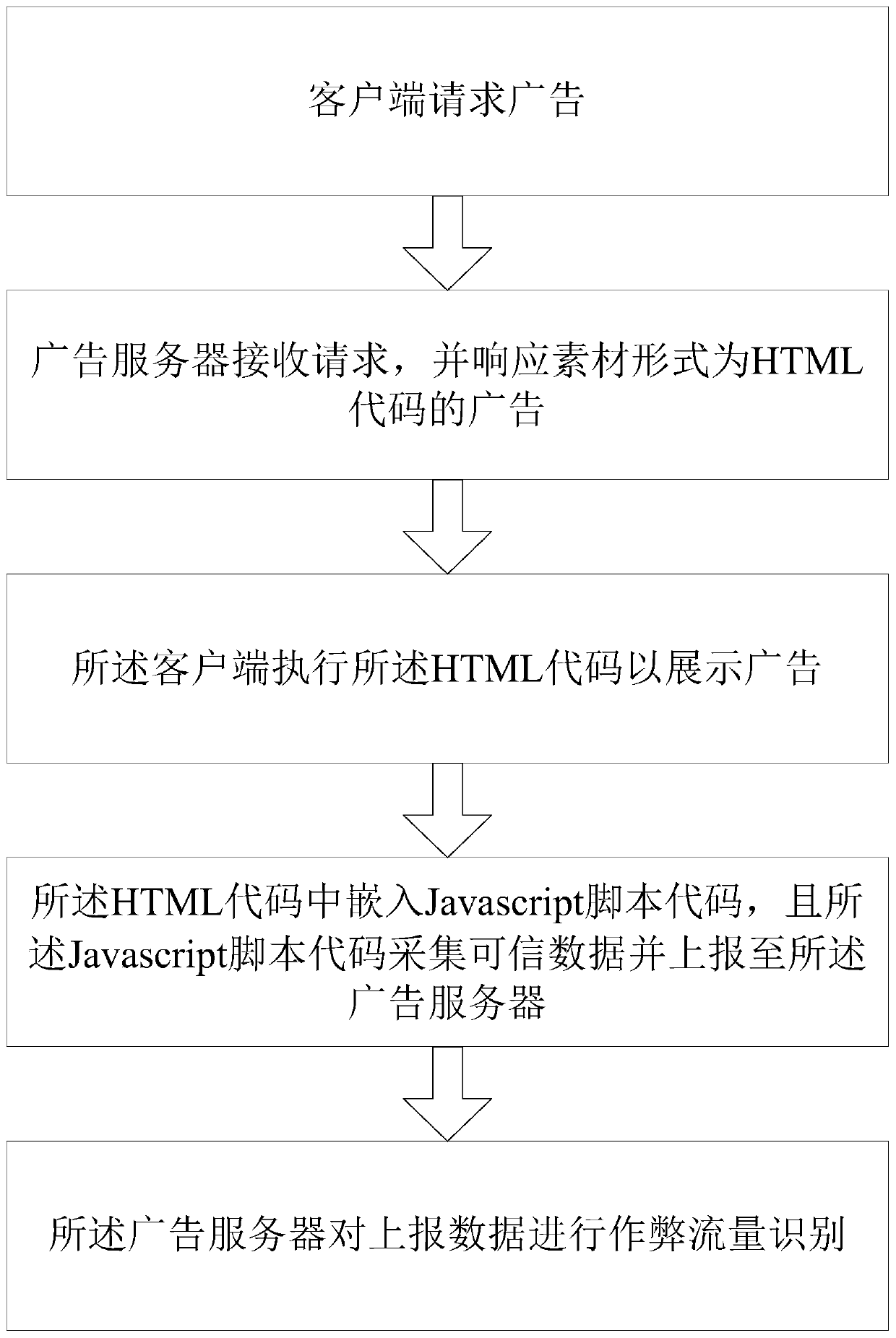
The invention provides a cheating flow identification method and system applied to API advertisements. The method comprises the following specific steps: 1the client requests an advertisement, and theadvertisement server receives the request; responding to the advertisement of which the material form is the HTML code, the client executes the HTML code to display the advertisement, and a Javascript code is embedded into the HTML code; the Javascript script code collects credible data and reports the credible data to the advertisement server; the advertisement server performs cheating flow identification on the reported data; the HTML code and the Javascript code are introduced, so that the advertisement platform can obtain more credible data for monitoring and analysis; and by using different HTML codes and Javascript codes, different collection strategies and analysis strategies are used for each advertisement, or different collection strategies and analysis strategies are used for advertisement requests of the same equipment in different time periods, so that the reliability of a cheating behavior detection result is improved. The problem that a cheating person can bypass monitoring by means of proxy IP due to traditional analysis and troubleshooting based on IP addresses is well avoided.
Owner:广州万唯邑众信息科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com