Network asset anomaly detection method and system, medium and equipment
A network asset and anomaly detection technology, applied in the field of network security, can solve problems such as the efficiency and low accuracy of private network assets, and achieve the effect of easy investigation and removal, high efficiency and easy acquisition.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
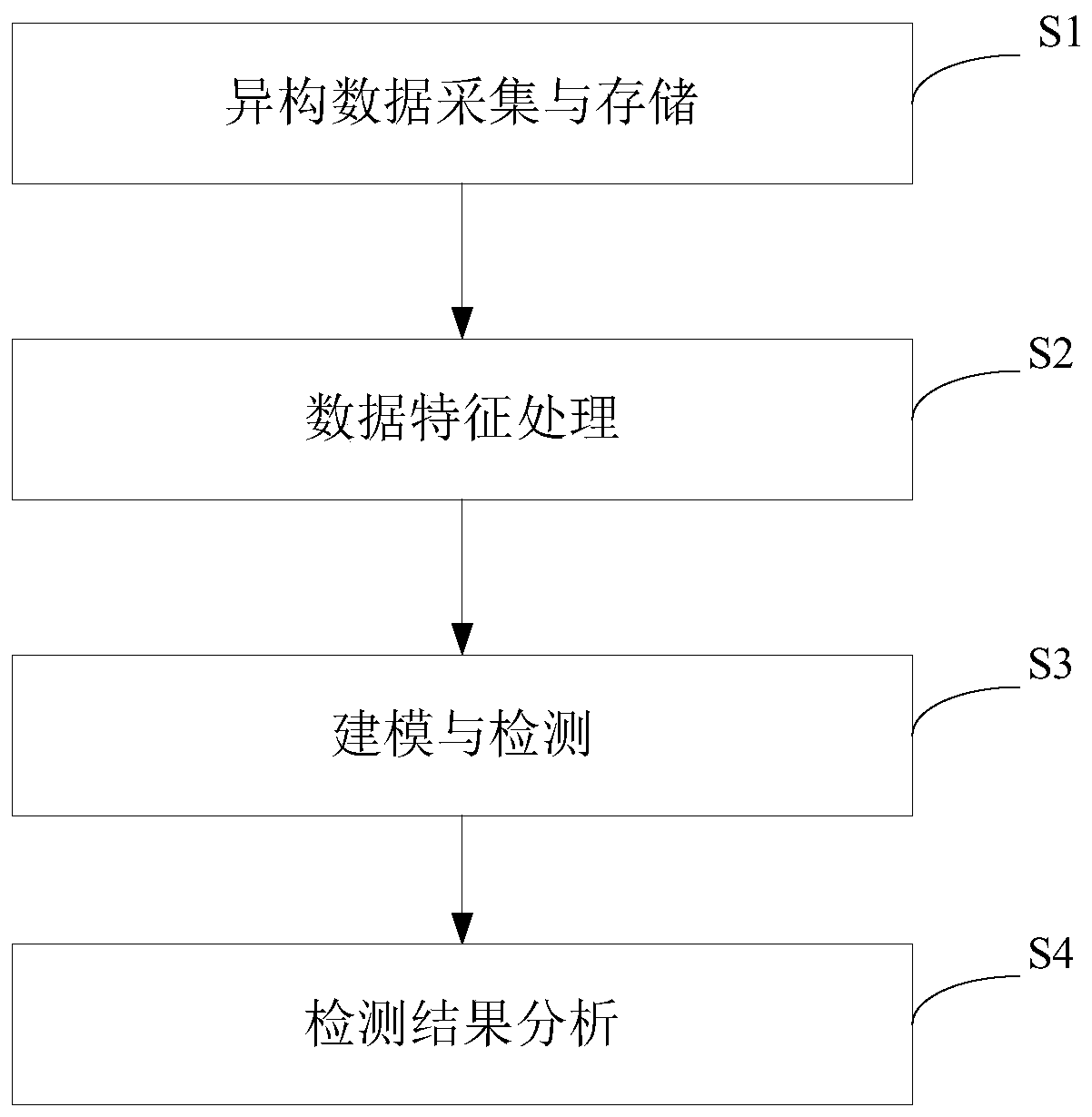
[0068] like figure 1 As shown, the abnormal detection method for network assets in this embodiment includes the following steps:
[0069] S1. Heterogeneous data collection and storage, collect traffic data, detection data and other external data of network assets from different sources, and store them in the database;
[0070] S2. Data feature processing, integrating raw data from multiple sources, using the "improved Raney entropy algorithm" to convert a set of probability distribution-type fields into a new data feature field, using "quantile-based high robustness Standardize the data and generate the data set required for modeling;
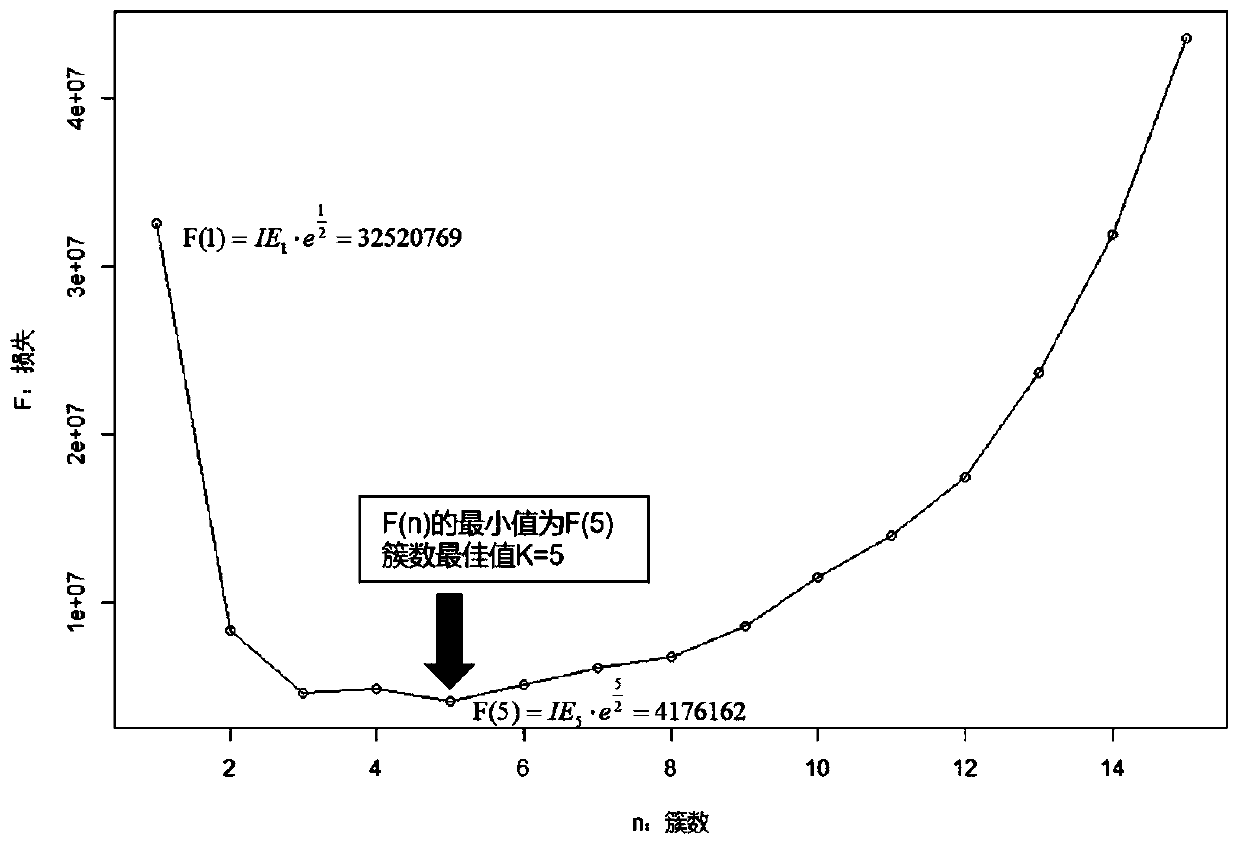
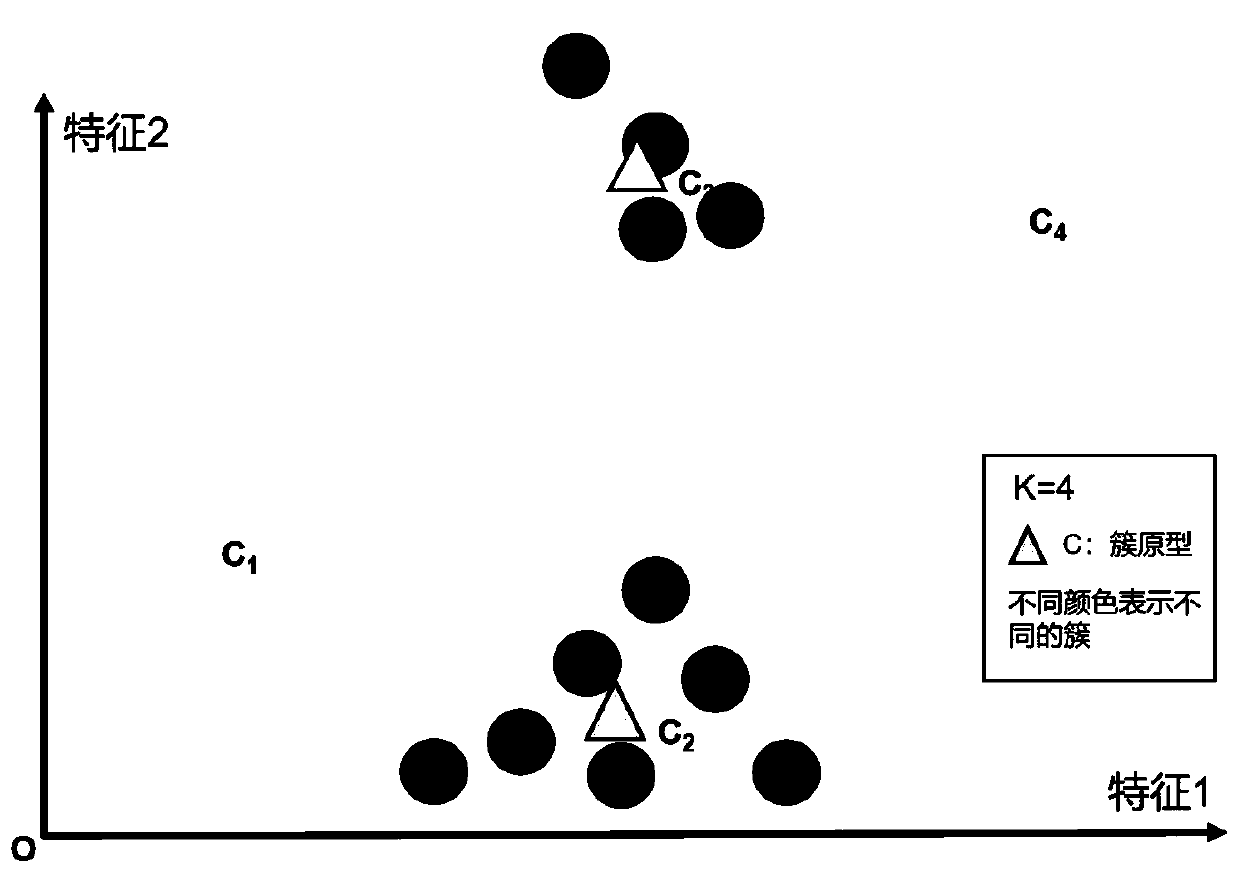
[0071] S3. Modeling and detection, the modeling unit obtains the network asset data set, adopts the "prototype-based automatic optimal clustering algorithm", and establishes the optimal clustering model according to the "asset type" grouping, and the detection unit outputs the output of the modeling unit Clustering results are processed to de...
Embodiment 2
[0171] Such as Figure 5 As shown, the present embodiment provides a network asset anomaly detection system, which includes a heterogeneous data acquisition and storage module 1, a data feature processing module 2, a modeling and detection module 3 and a detection result analysis module 4, each module The specific functions are as follows:
[0172] The heterogeneous data collection and storage module 1 is used to collect traffic data, detection data and other external data of network assets from different sources, and store them in a database;
[0173] The data feature processing module 2 is used to integrate raw data from multiple sources, use the "improved Raney entropy algorithm" to convert a set of probability distribution type fields into a new data feature field, and use the "quantile-based The highly robust standardization algorithm" standardizes the data and generates the data sets required for modeling;
[0174] The modeling and detection module 3 uses the modeling ...
Embodiment 3
[0178] This embodiment provides a storage medium, the storage medium stores one or more programs, and when the programs are executed by the processor, the network asset anomaly detection method of the above-mentioned embodiment 1 is implemented, as follows:
[0179] Heterogeneous data collection and storage, collecting traffic data, detection data and other external data of network assets from different sources, and storing them in the database;
[0180] Data feature processing, integrating raw data from multiple sources, using the "improved Raney entropy algorithm" to convert a set of probability distribution type fields into a new data feature field, using "quantile-based high robustness standardization "algorithm" to standardize the data and generate the data set required for modeling;
[0181] Modeling and detection, the modeling unit obtains the network asset data set, adopts the "prototype-based automatic optimal clustering algorithm", and establishes the optimal cluster...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com