Multilayer semantic annotation and detection method against malignancy
A detection method and semantic annotation technology, applied in the field of computer security, can solve problems such as the efficiency of unknown computer virus analysis, achieve the effects of improving adaptability and accuracy, improving protection capabilities, and improving work efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
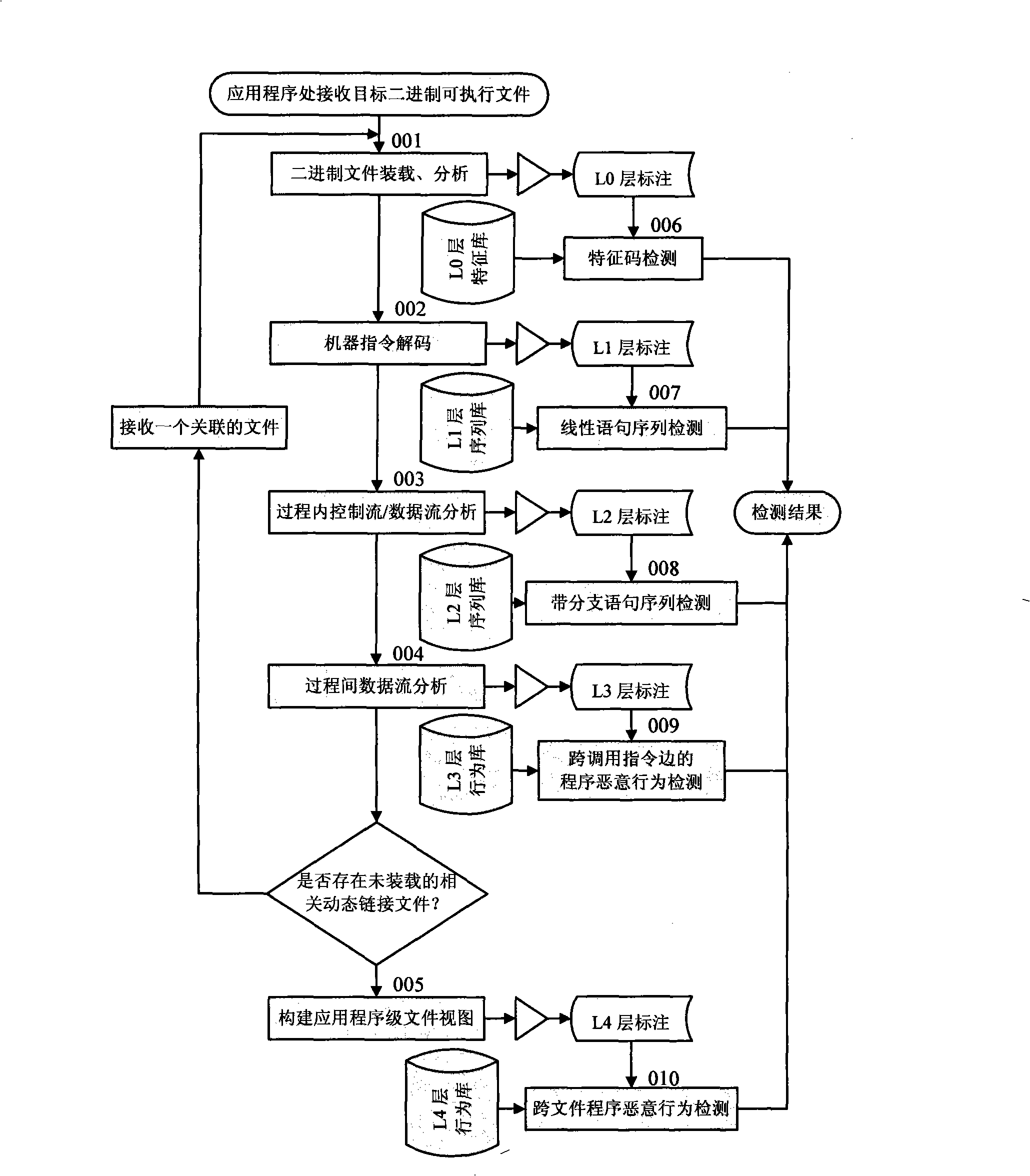
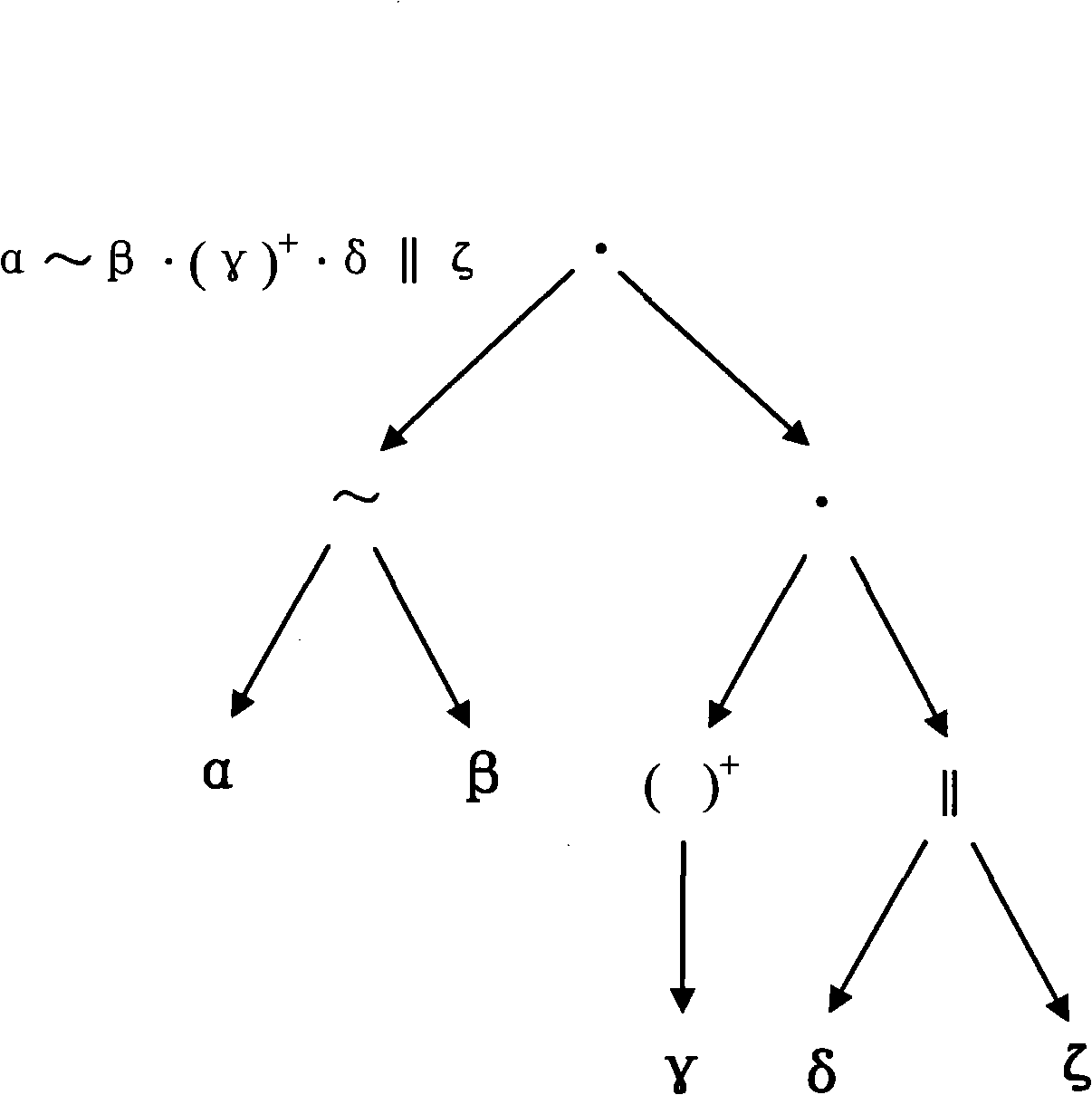
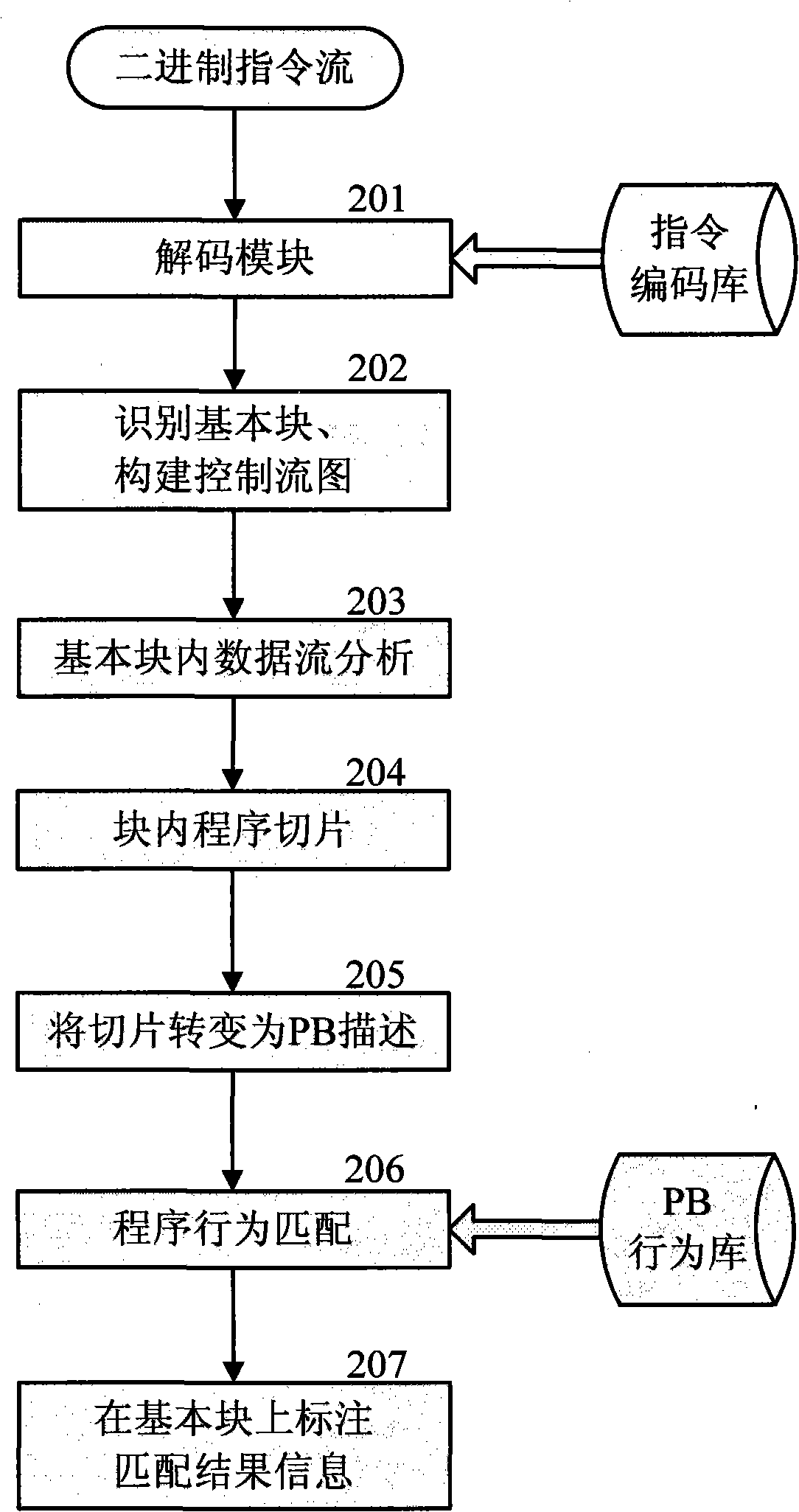
[0047] see figure 1 , figure 2 , image 3 , Figure 4 , Figure 5 , a method of recording and analyzing intermediate results using multi-layer semantic annotation technology in malicious behavior detection, and layer-by-layer detection of annotation information on this basis, that is, a multi-layer semantic annotation and detection method for malicious behavior. Including the labeling sub-module and the detection sub-module, wherein the labeling sub-module and the detection sub-module include the binary semantic layer L0, the linear instruction semantic layer L1, the control flow graph semantic layer L2, the procedure call graph semantic layer L3 and the application level semantic layer L4 labeling and detection respectively; the labeling sub-module labels specific analysis target objects at each layer; the detection sub-module detects malicious behaviors at all levels based on corresponding analysis strategies and algorithms; labeling and detection layers The intermediat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com