Credible threat intelligence identification method and device based on blockchain consensus mechanism
An identification method and identification device technology, applied to electrical components, transmission systems, etc., can solve problems such as insufficient identification accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
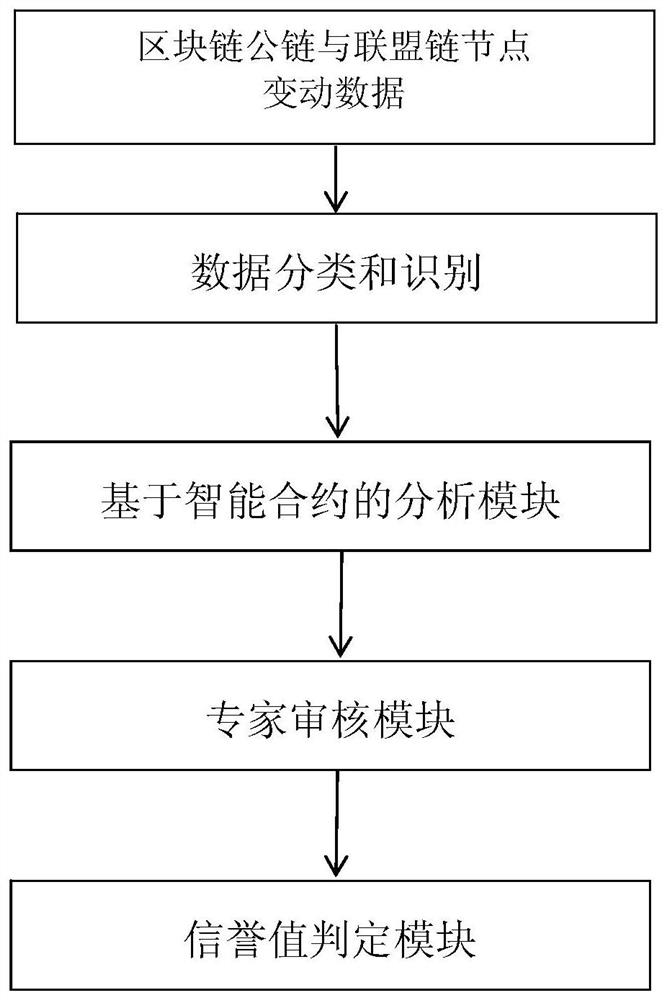
[0066] Correspondingly, the present invention also provides a trusted threat intelligence identification device based on a blockchain consensus mechanism, including an intelligence data acquisition module, an analysis mode determination module, an analysis result acquisition module, a smart contract execution module, and an intelligence identification module, wherein :
[0067] The intelligence data acquisition module is used to incorporate each node of the intelligence data source into the blockchain to form an intelligence data blockchain, and monitor each node of the blockchain to obtain intelligence data;
[0068] an analysis mode determination module, configured to determine a data analysis mode of the intelligence data;
[0069] The analysis result acquisition module is used to match the corresponding analysis strategy according to the data analysis mode of the intelligence data, and then obtain the corresponding analysis result;
[0070] The smart contract execution mo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com