Method and system for preventing remote control type Trojan viruses
A Trojan horse and remote control technology, applied in the field of network security, can solve problems such as single function, undetectable, low recognition rate, etc., to achieve the effect of preventing operation and reducing the probability of false positives and false positives
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0040] In order to enable those skilled in the art to better understand the technical solutions in the embodiments of the present invention, and to make the above-mentioned purposes, features and advantages of the present invention more obvious and easy to understand, the technical solutions in the present invention will be further detailed below in conjunction with the accompanying drawings illustrate.
[0041] The invention provides a method and system for preventing remote control Trojan horse viruses, which can effectively prevent the operation of remote control Trojan horses, block the entry and exit of malicious traffic, and protect users' computers from being damaged.
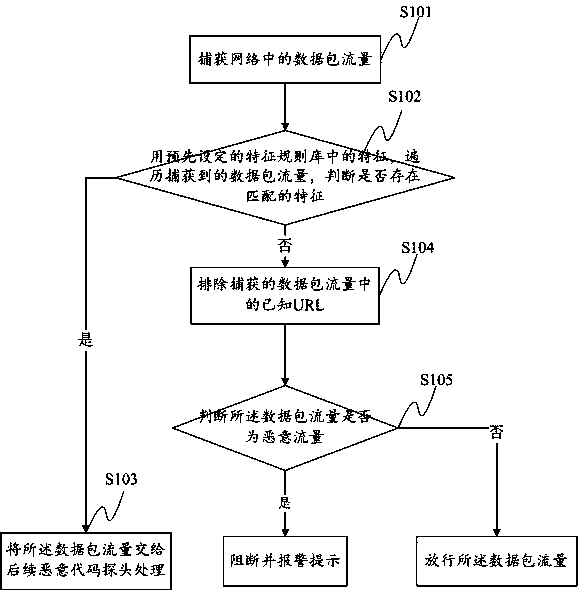
[0042] A method for guarding against remote control Trojan horse virus, such as figure 1 shown, including:
[0043] S101: Capture the data packet flow in the network; for the captured data packet flow, it can be stored in a special server device for summary, which is convenient for subsequent judgment, an...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com