Patents
Literature
45 results about "Search protocol" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
[MS-SEARCH]: Search Protocol. Specifies the Search Protocol that enables clients to make queries against an Enterprise Search service, the protocol server responding with a list of items that are relevant to the search query. This protocol also allows protocol clients to request query suggestions for a given search query.
Uniform search system and method for selectively sharing distributed access-controlled documents
InactiveUS20050055327A1Keep full controlNot allowData processing applicationsWeb data indexingRandomized algorithmPrivacy protection
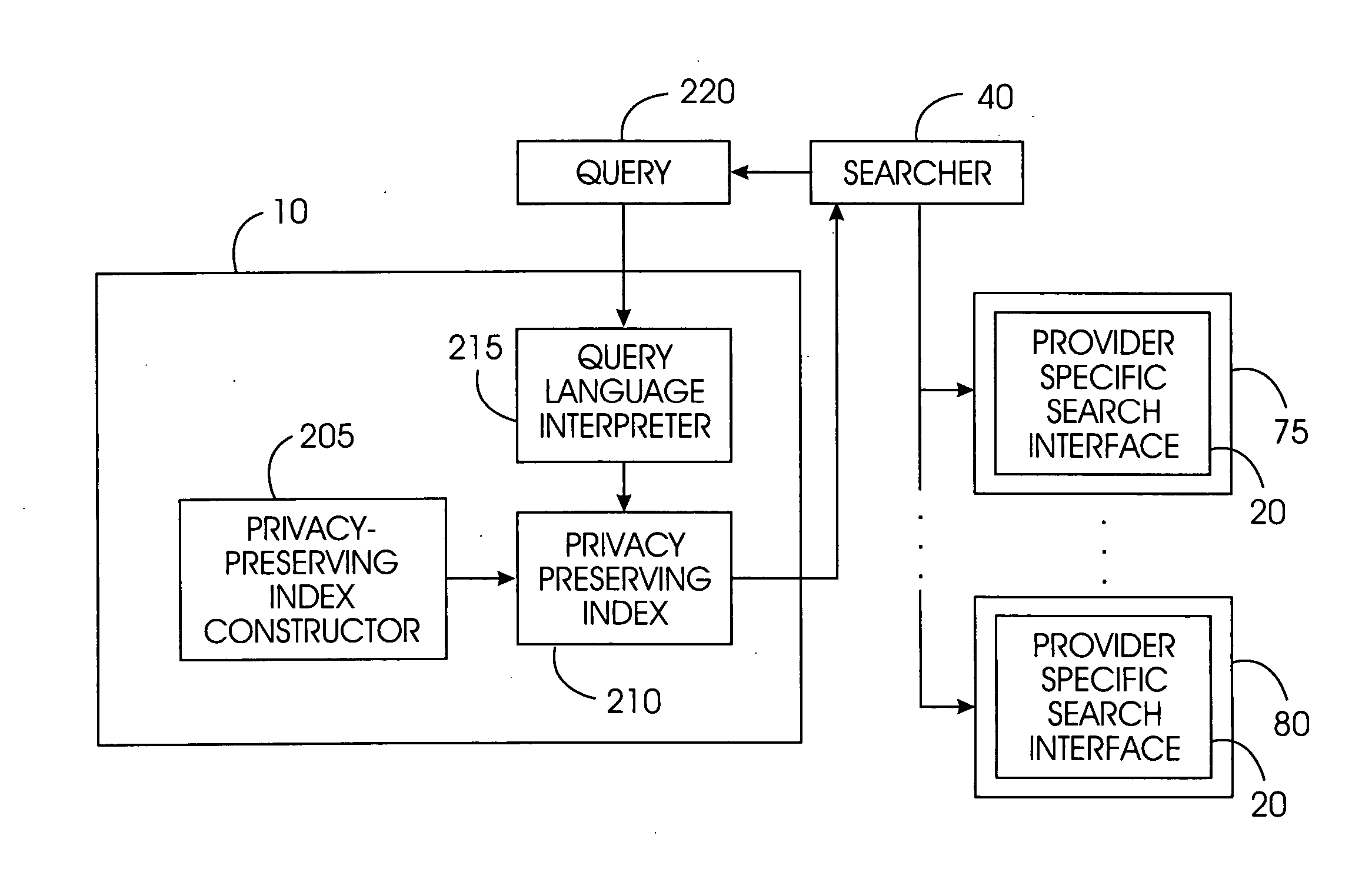
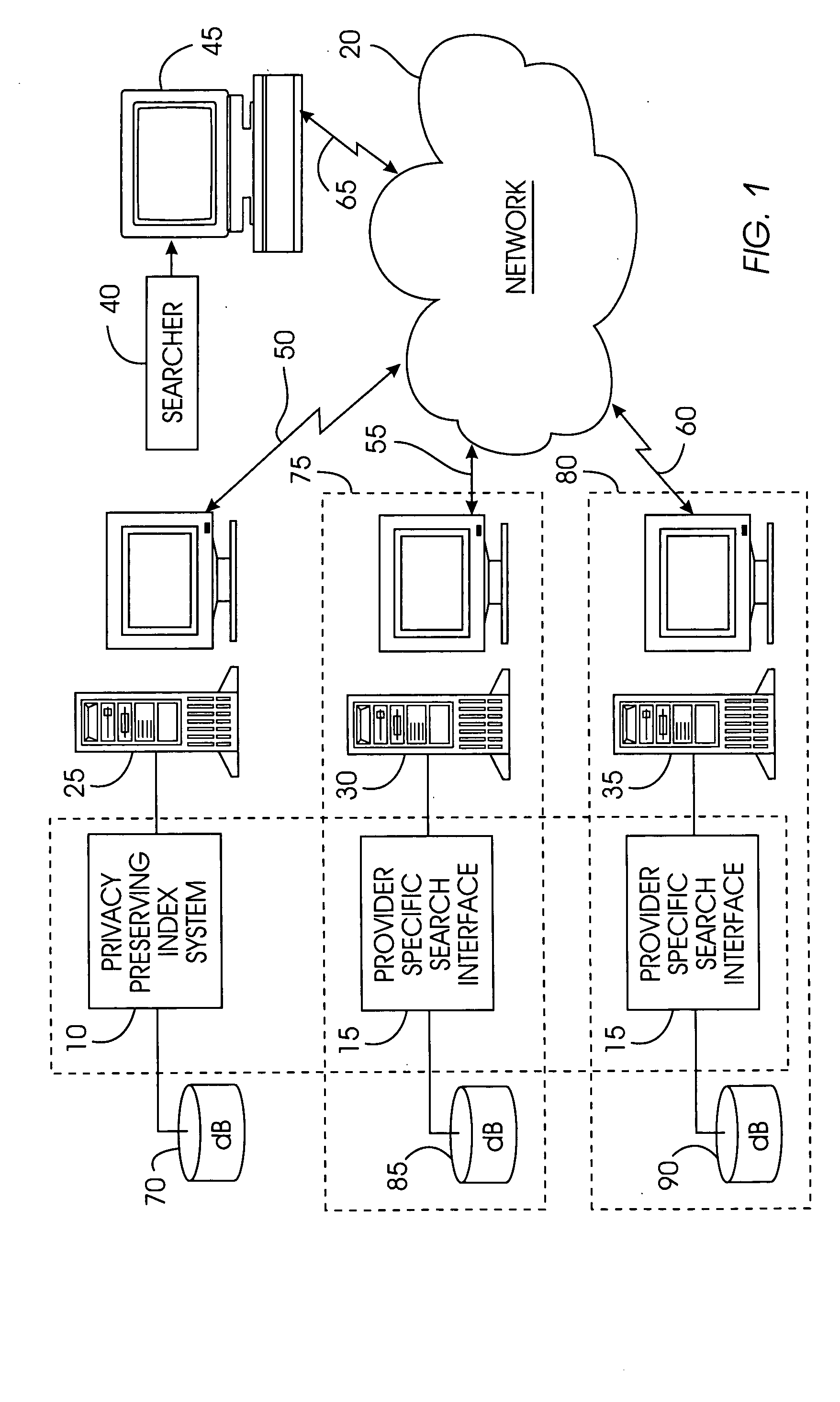
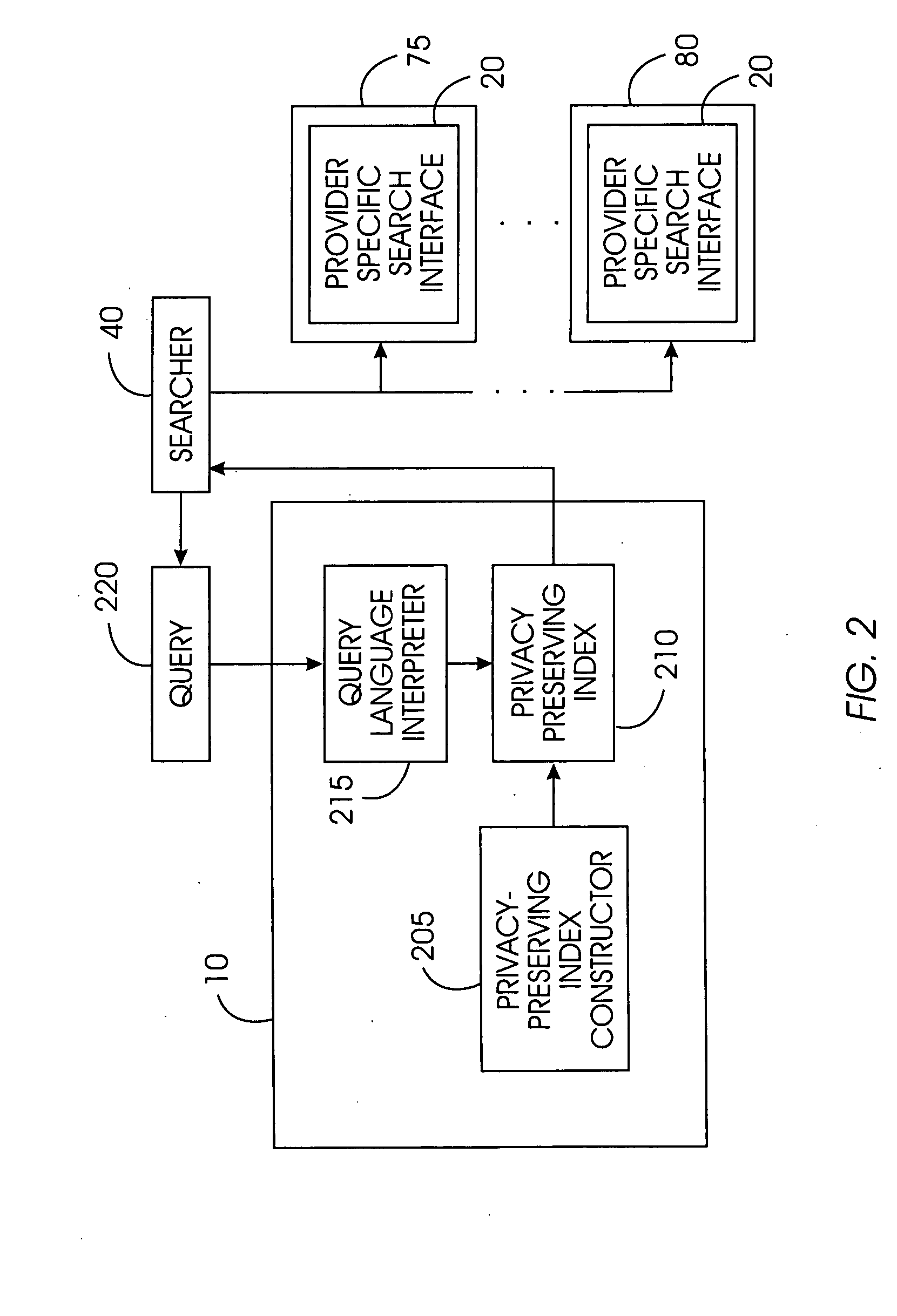
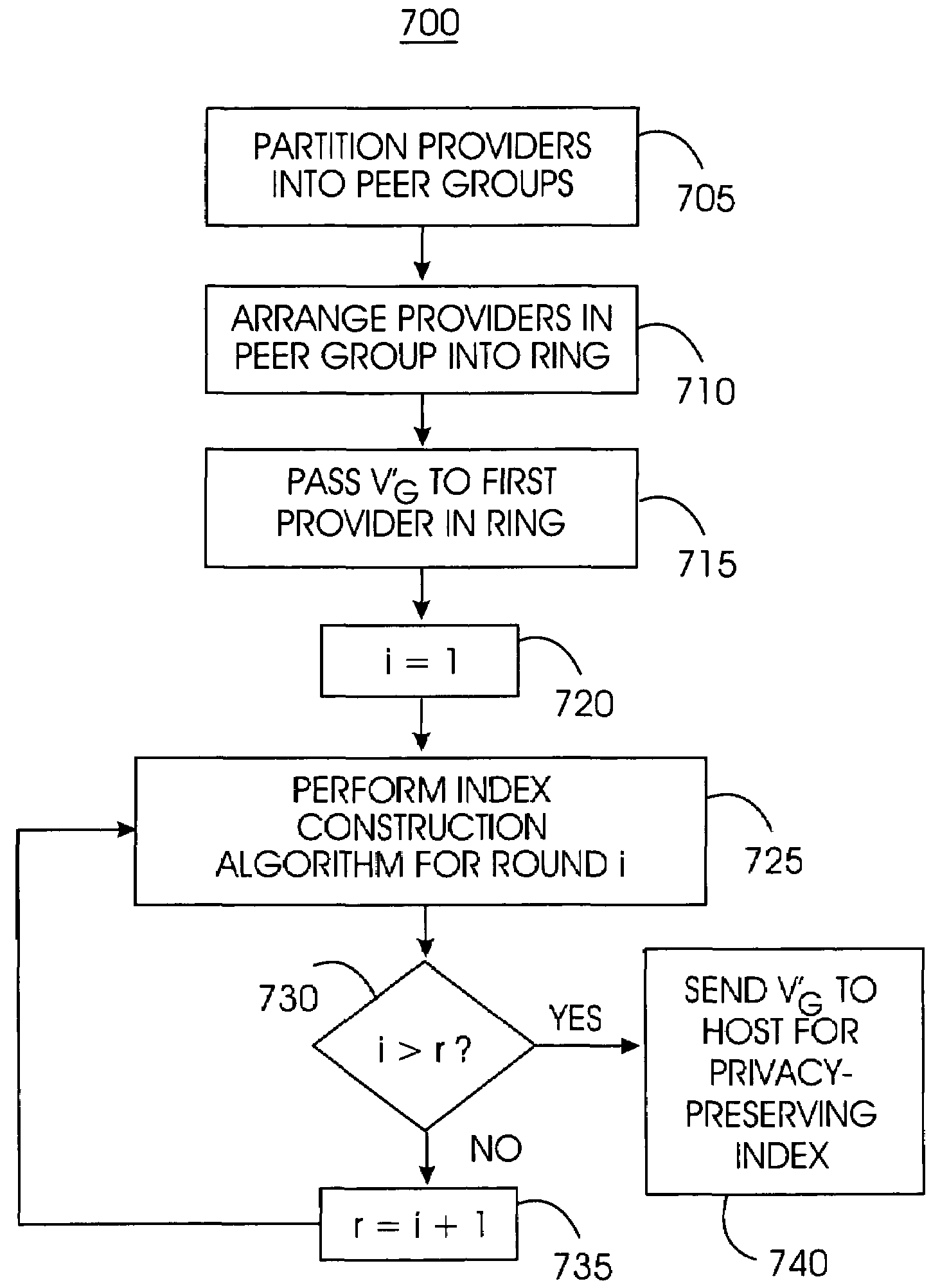
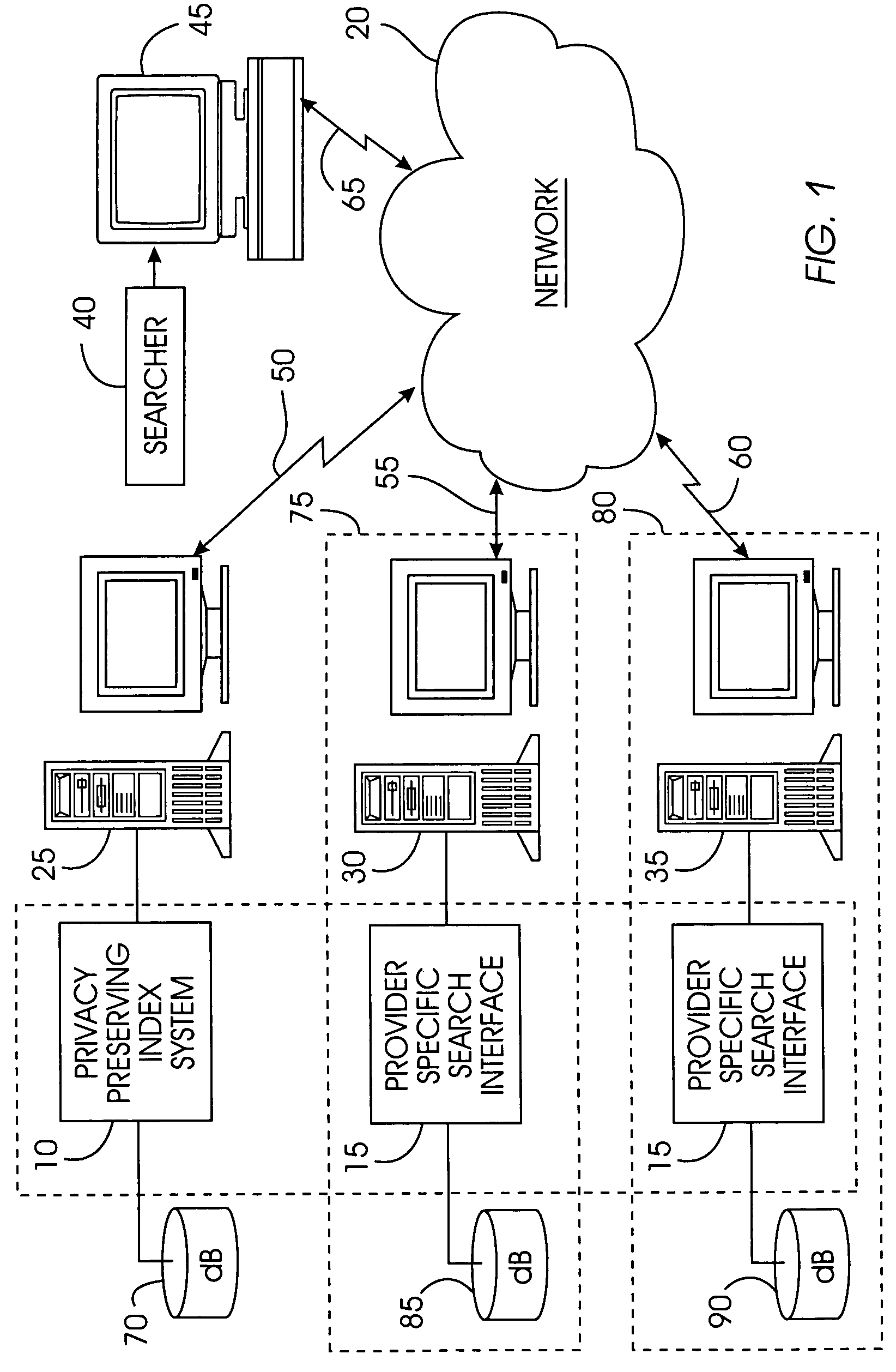
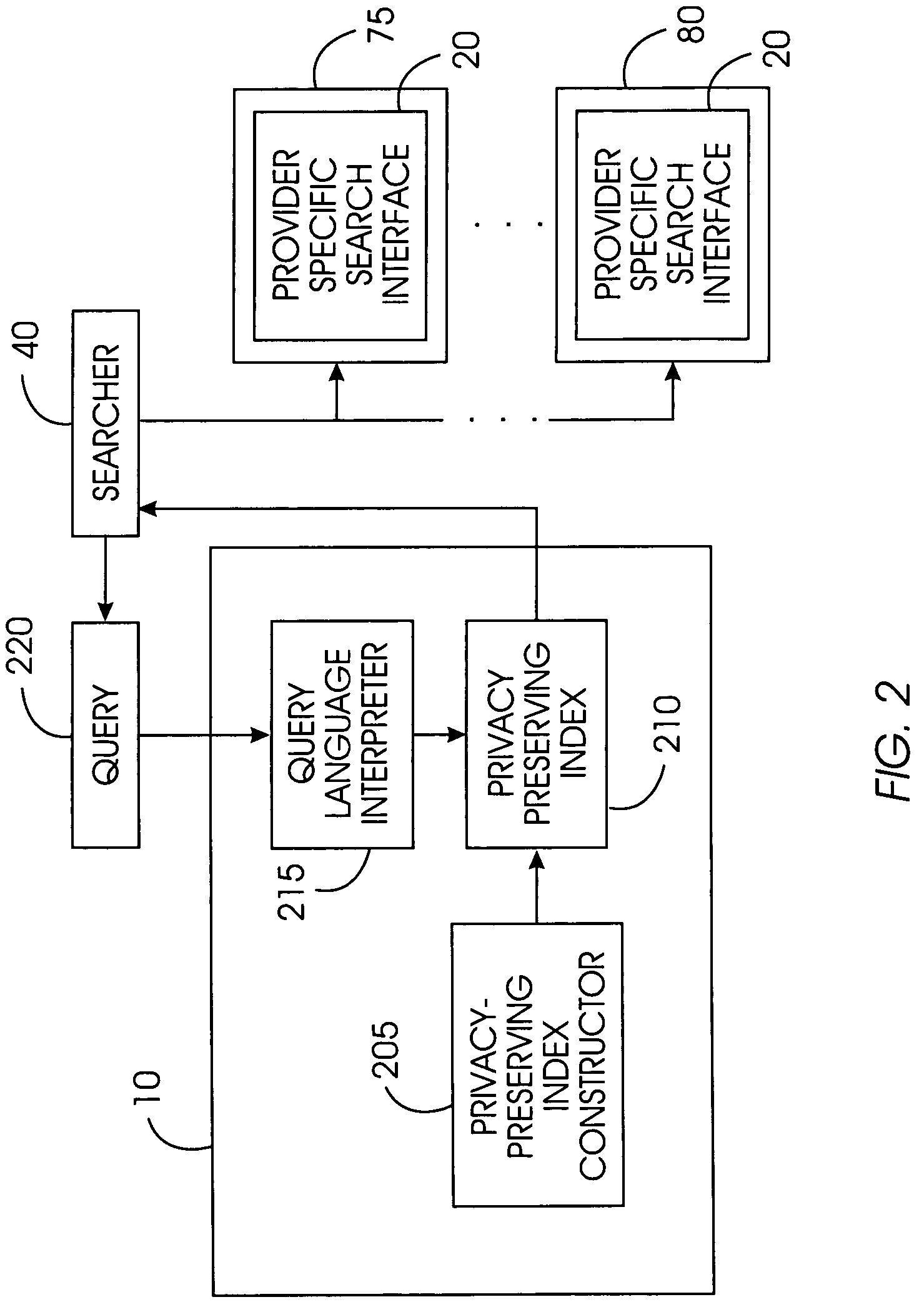
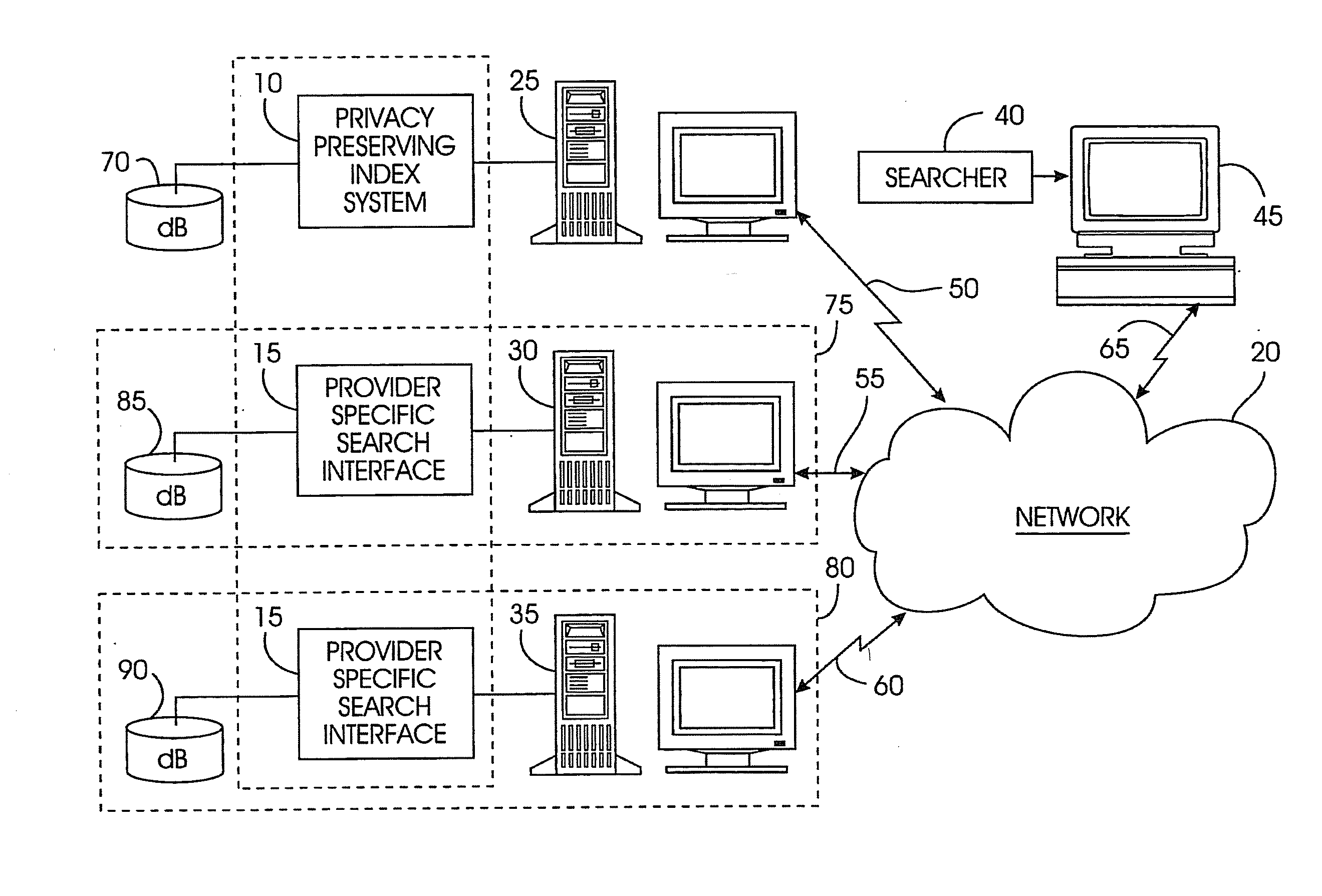
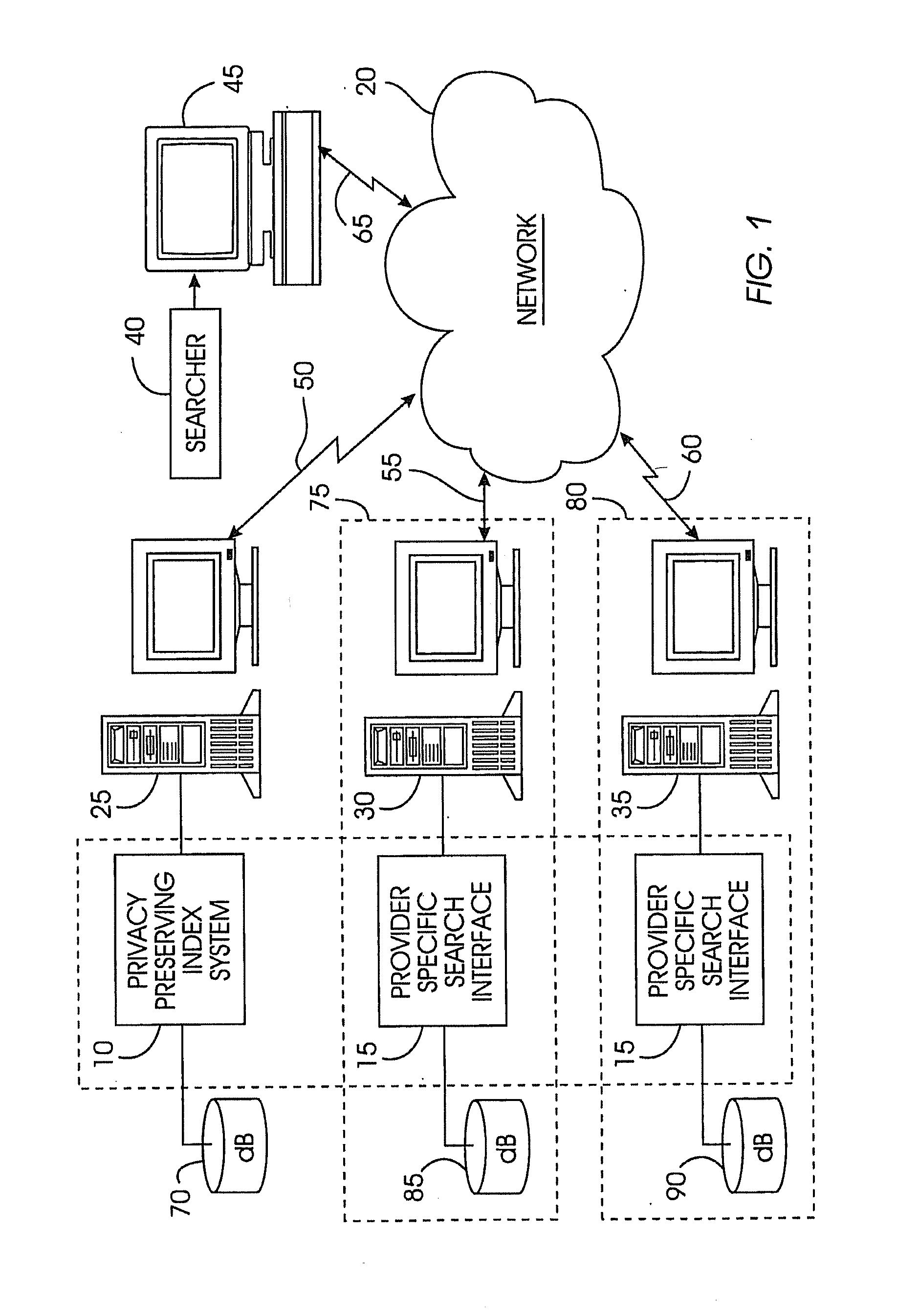
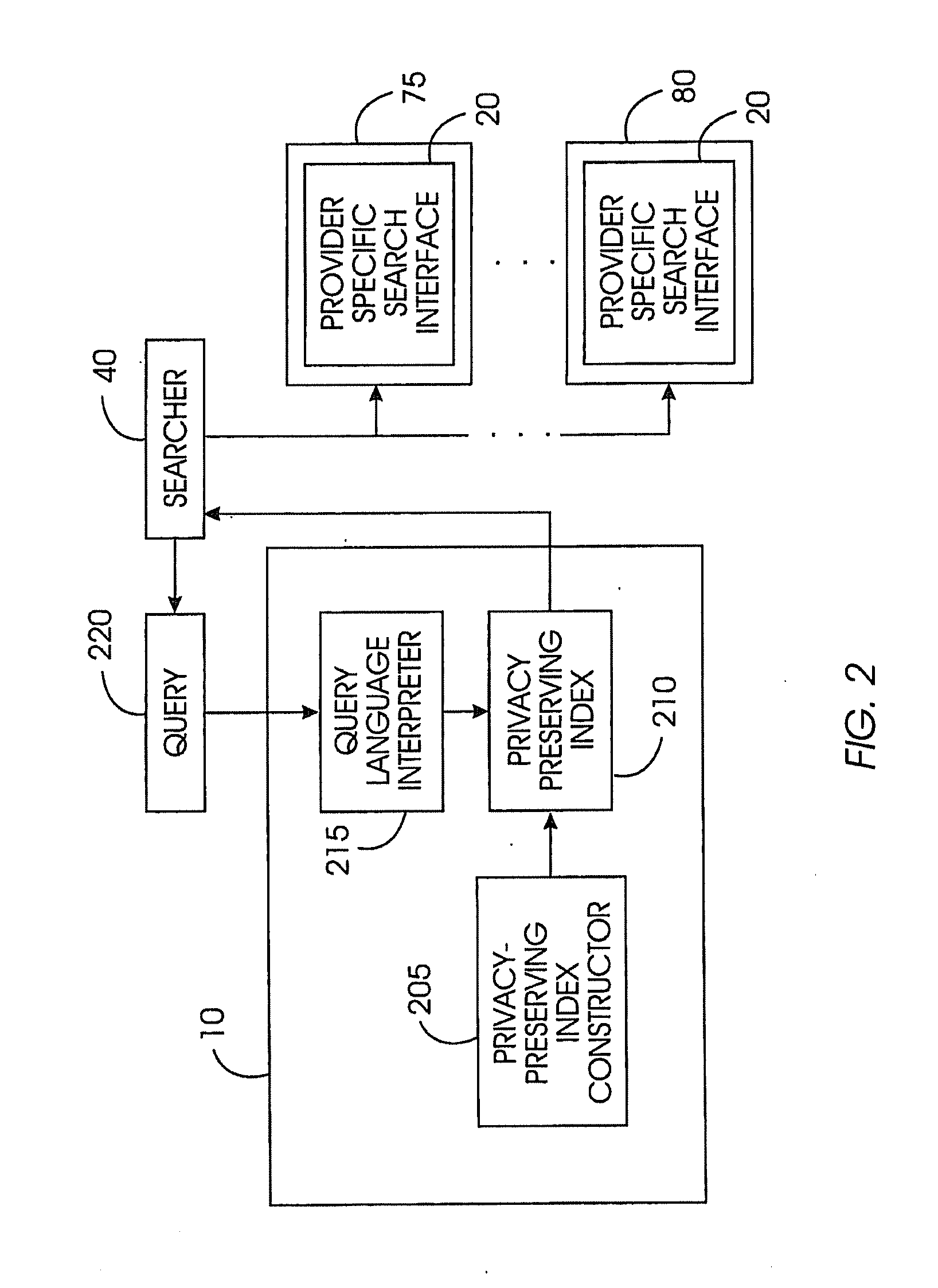
A privacy-preserving index system addresses the problem of providing a privacy-preserving search over distributed access-controlled content. Indexed documents can be readily reconstructed from inverted indexes used in the search. The privacy-preserving index system builds a centralized privacy-preserving index in conjunction with a distributed access-control enforcing search protocol. The privacy-preserving index utilizes a randomized algorithm for constructing a privacy-preserving index. The privacy-preserving index is strongly resilient to privacy breaches. The privacy-preserving index system allows content providers to maintain complete control in defining access groups and ensuring its compliance, and further allows system implementors to retain tunable knobs to balance privacy and efficiency concerns for their particular domains.
Owner:IBM CORP
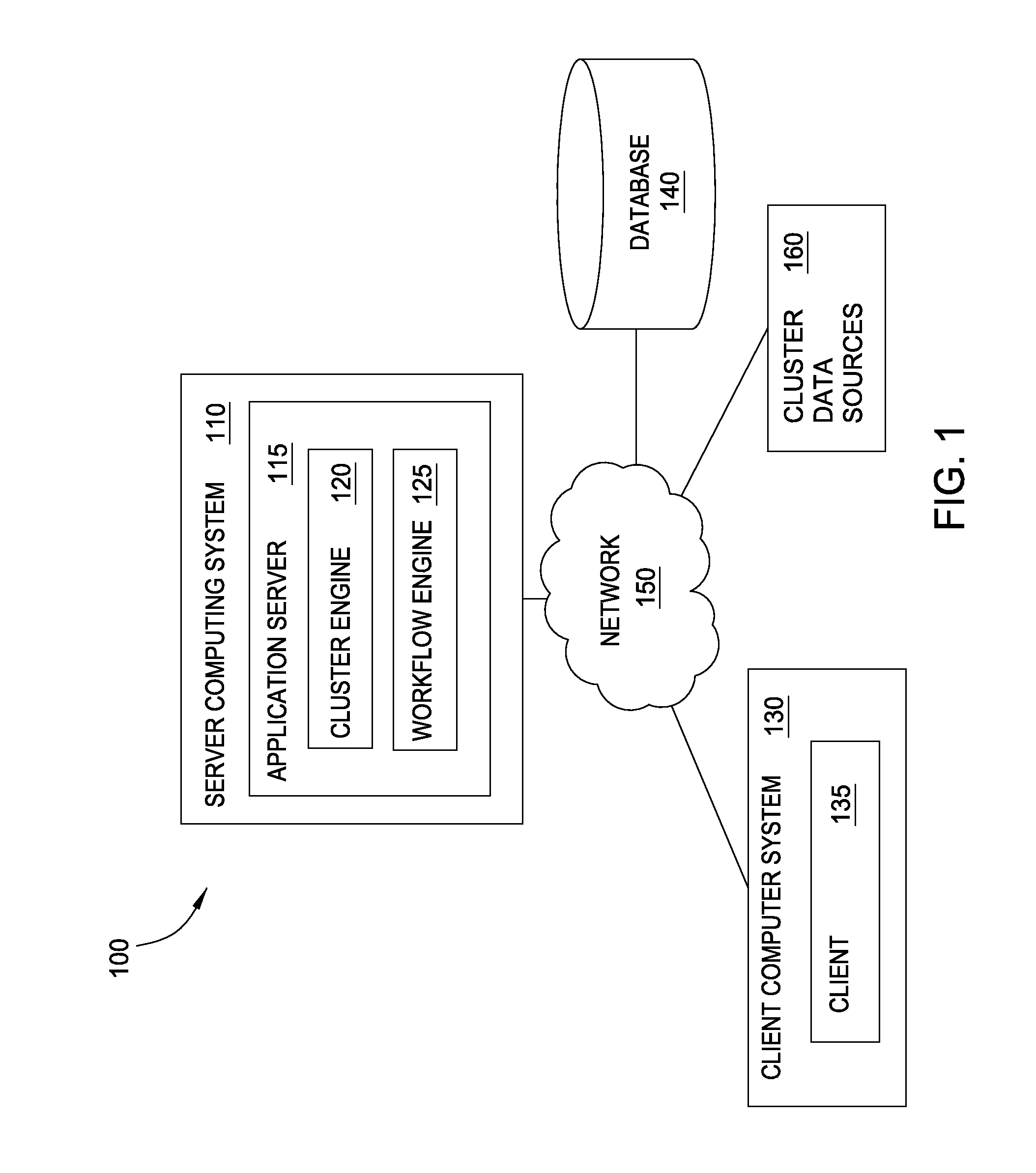
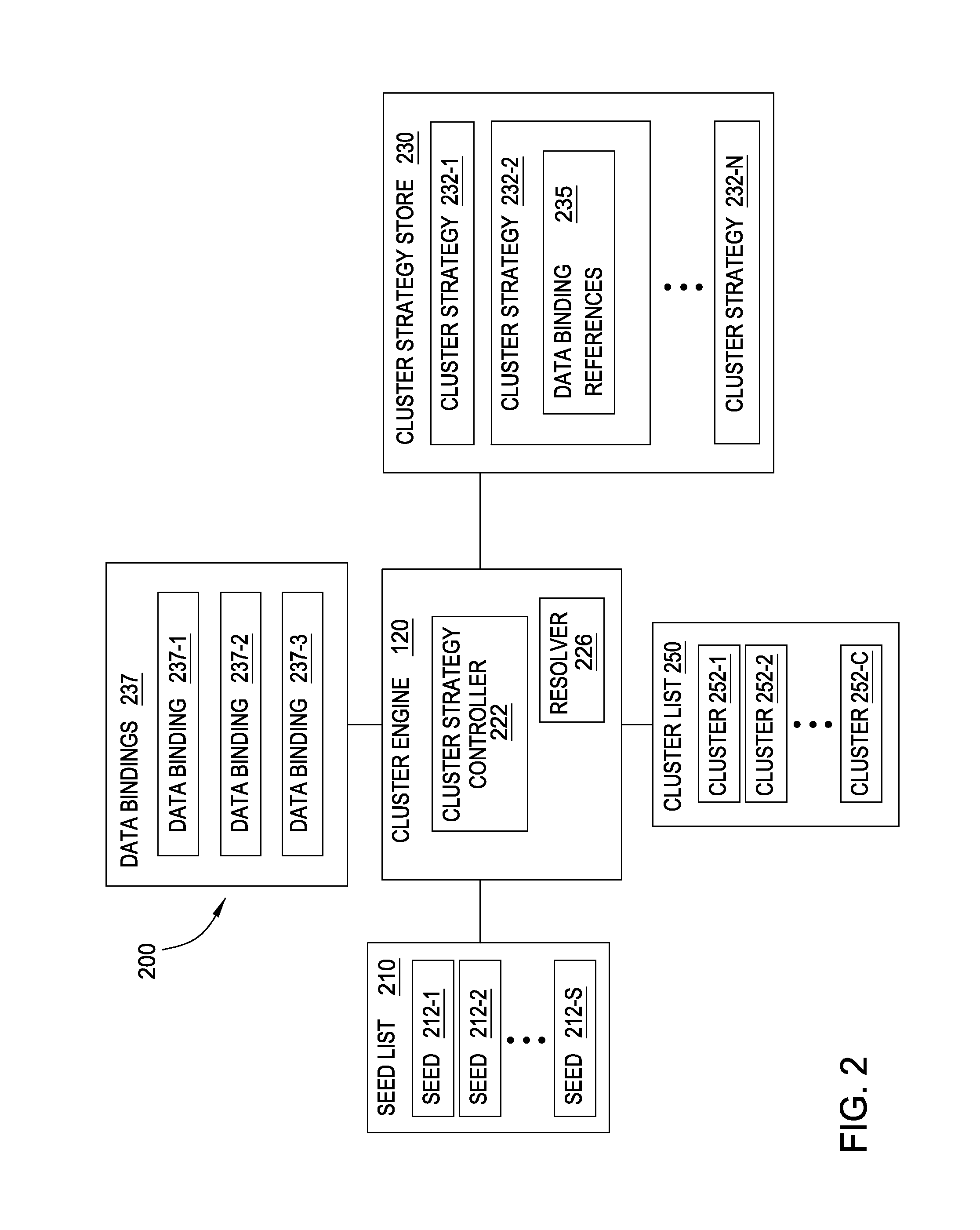
Generating data clusters with customizable analysis strategies
ActiveUS8788405B1Effective starting pointReduce the amount requiredDatabase updatingFinanceSearch protocolAnalytical strategy
Techniques are disclosed for generating a collection of clusters of related data from a seed. Doing so may generally include retrieving a seed and adding the seed to a first cluster and include retrieving a cluster strategy referencing one or more data bindings. Each data binding specifies a search protocol for retrieving data. For each of the one or more data bindings, data parameters input to the search protocol are identified, the search protocol is performed using the identified data parameters, and data returned by the search protocol is evaluated for inclusion in the first cluster.
Owner:PALANTIR TECHNOLOGIES
MAC address population protocol
InactiveUS6873603B1Reduce network bandwidth consumptionNo need to waste bandwidthTime-division multiplexNetworks interconnectionPopulation protocolEthernet lan
A new search protocol uses a message which a router periodically transmits onto the local LANs connected to its ports, and in response to the new protocol, all end stations receiving the message transmit their addresses to the router. The addresses transmitted to the router comprise the addresses and any other information needed by the router to reach the end station. For example, for an Ethernet LAN the layer 2 or MAC layer address of the end station is transmitted to the router. In the event that the protocol of the LAN uses source routing, the information transmitted to the router includes both the MAC address and the Route Information Field of the end station. In any event, the router uses the information received from the end stations to build its routing table. Then, upon receipt of the next CANUREACH message from a peer router, the desired destination end station will appear in the router's routing table, and there will be no need to waste bandwidth by transmitting search messages looking for the end station. The new protocol messages are transmitted periodically in order to keep the routing tables current is as the network changes dynamically.
Owner:CISCO TECH INC
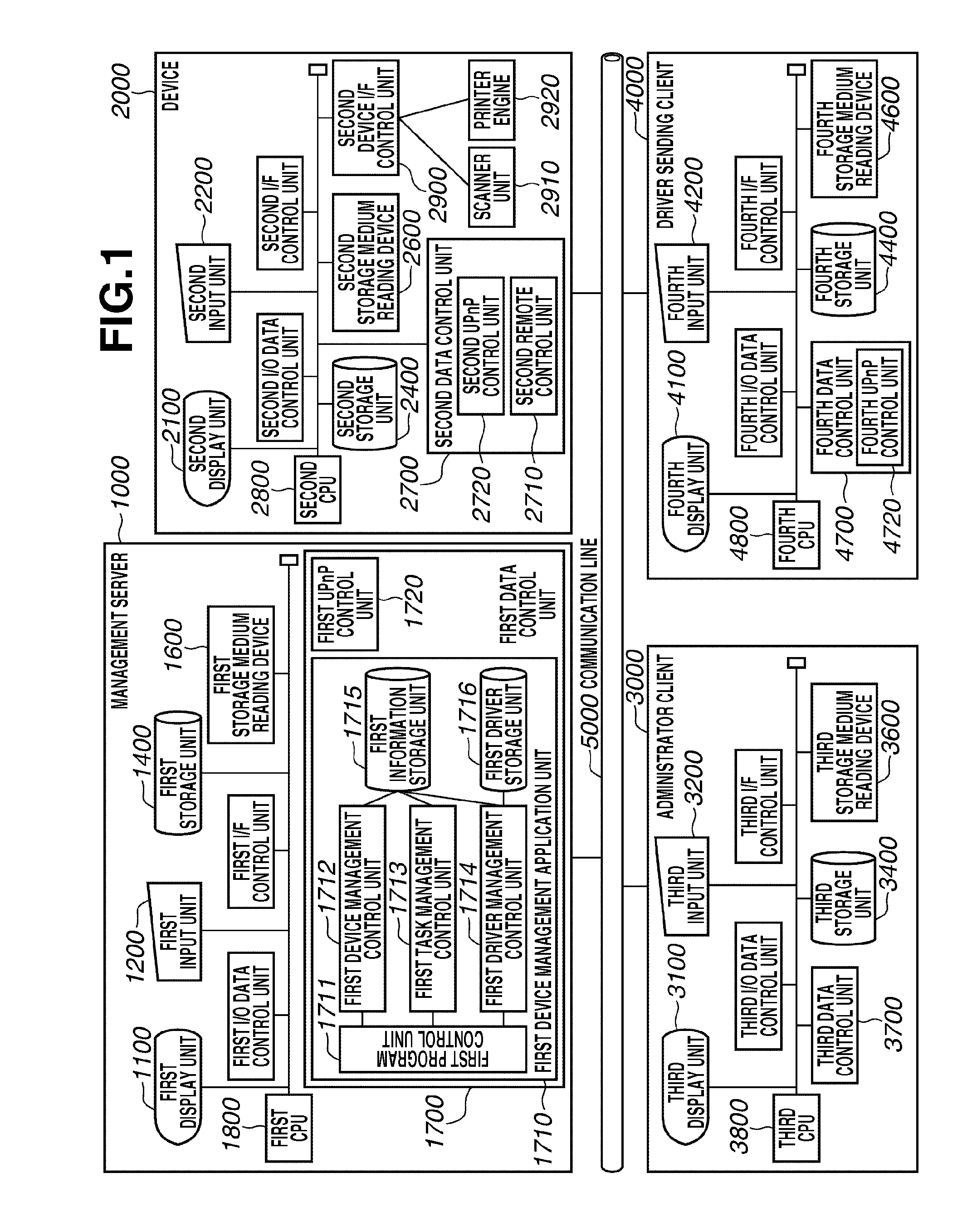
Driver management apparatus and method therefor
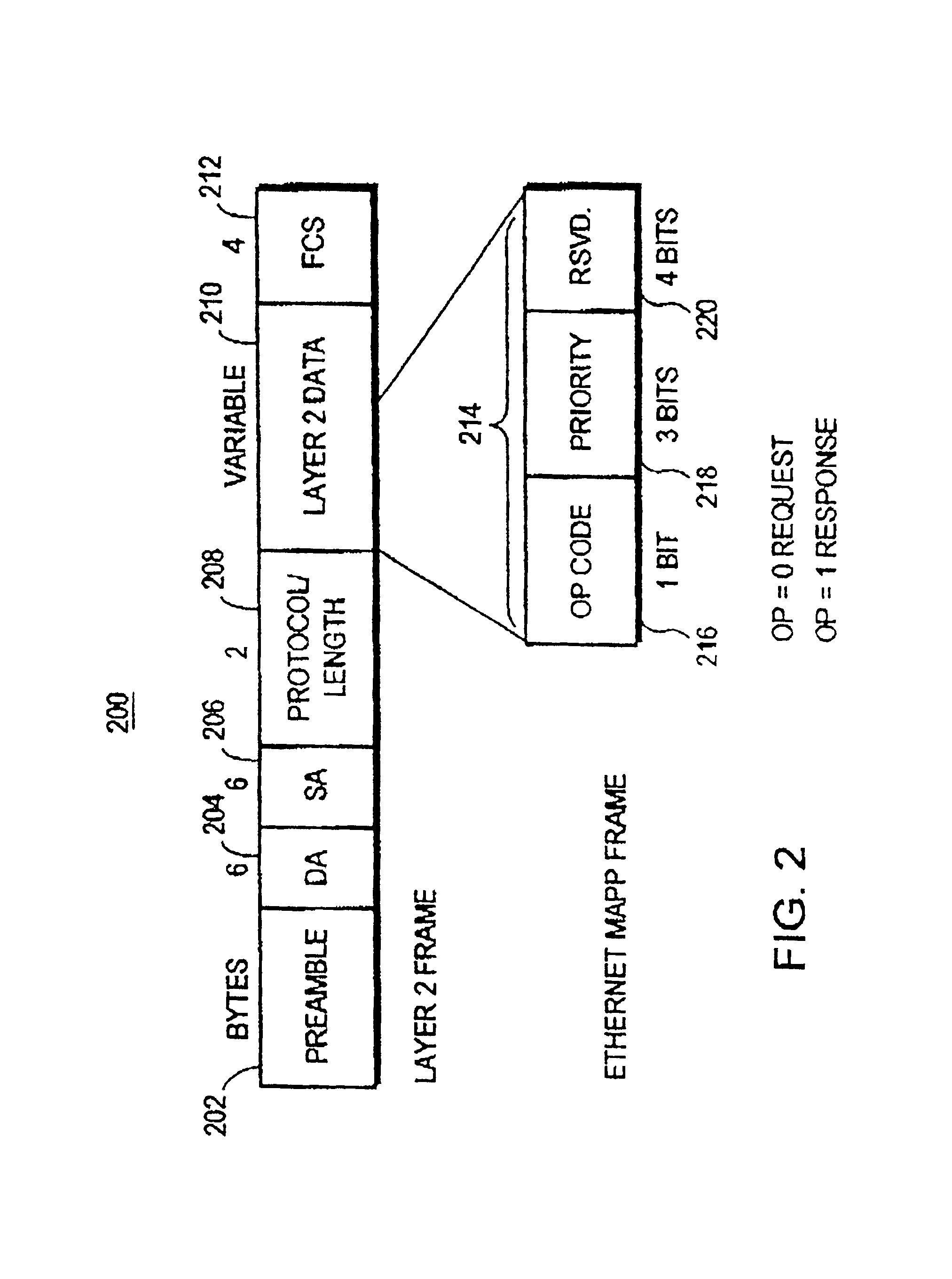
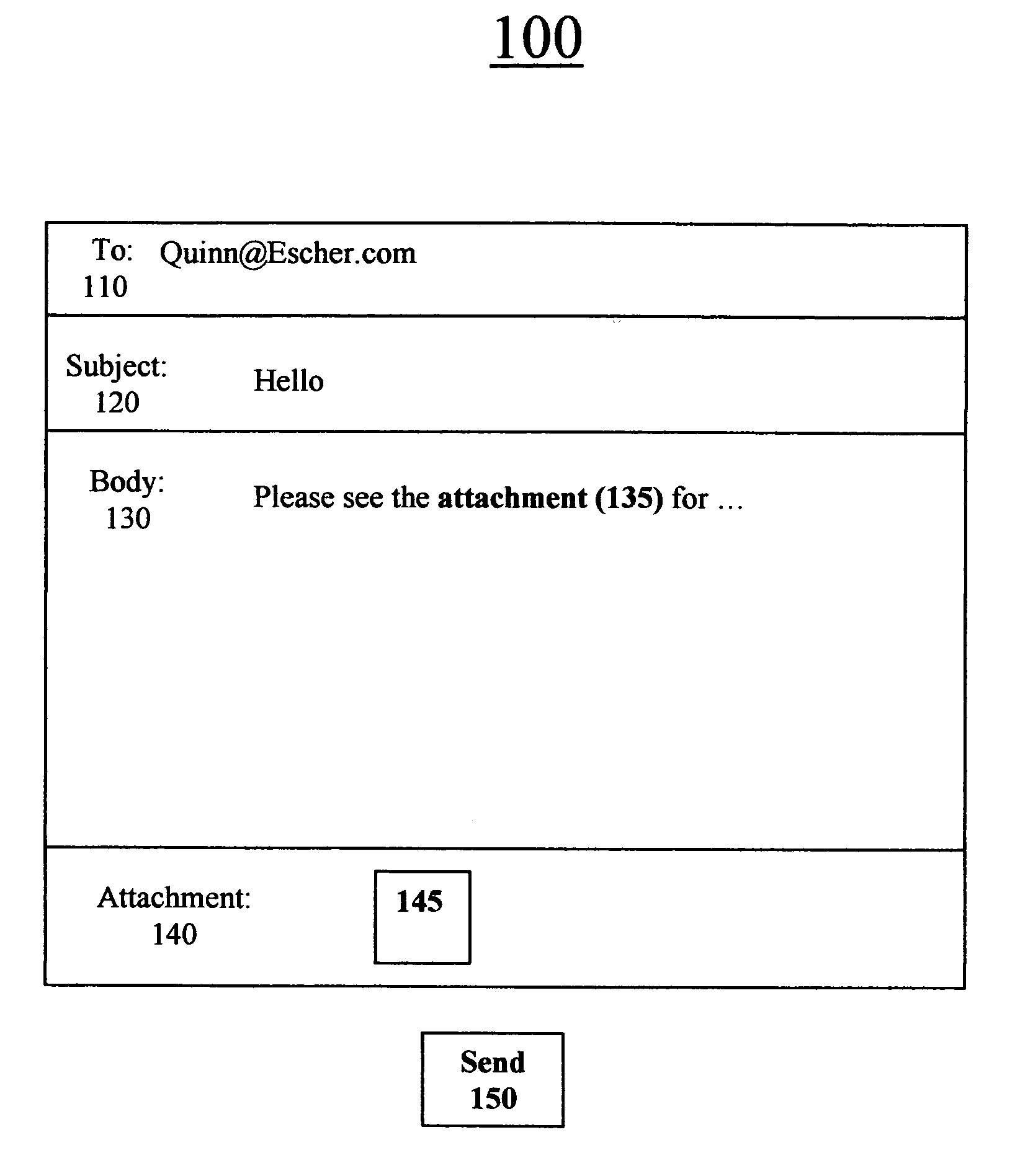
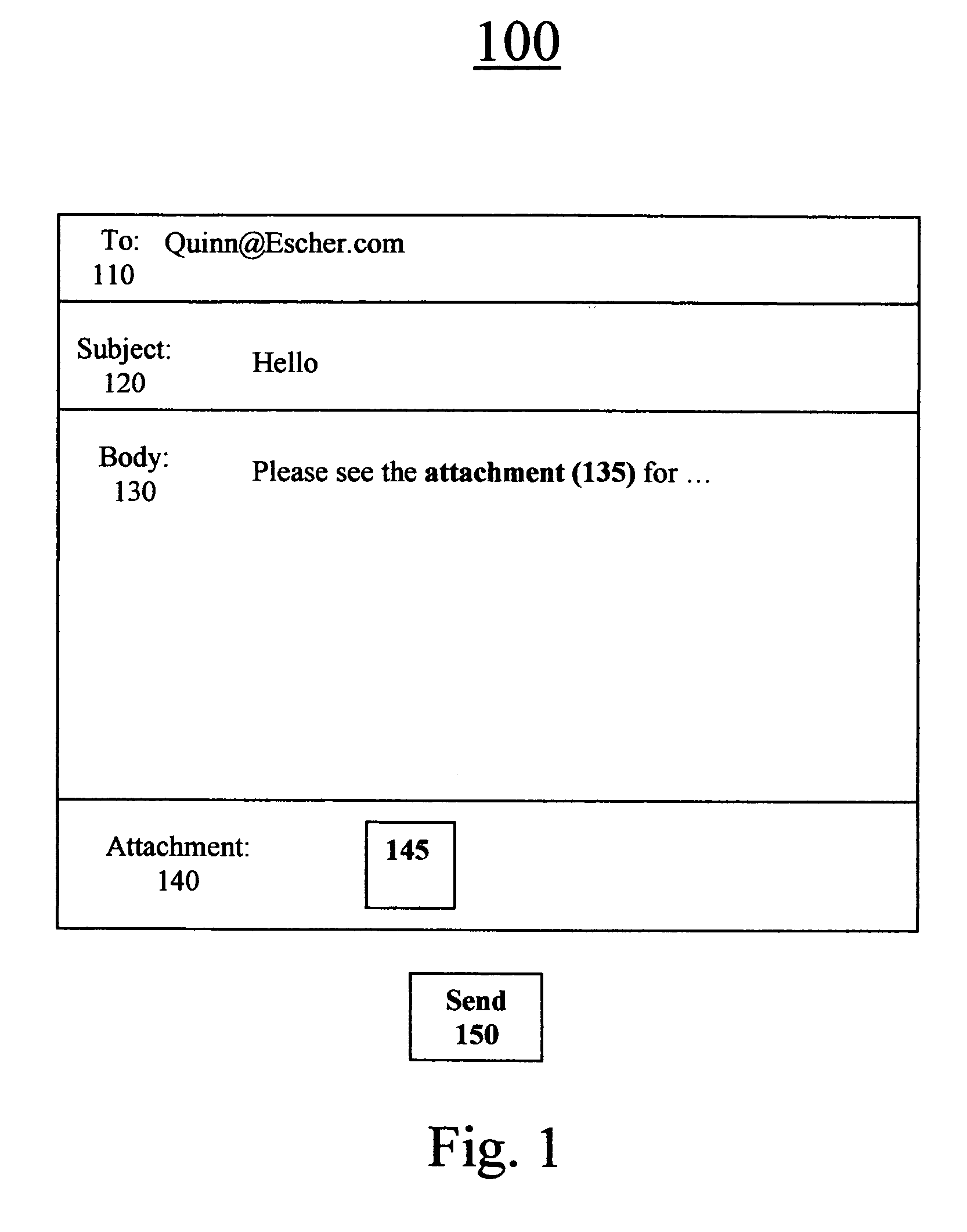
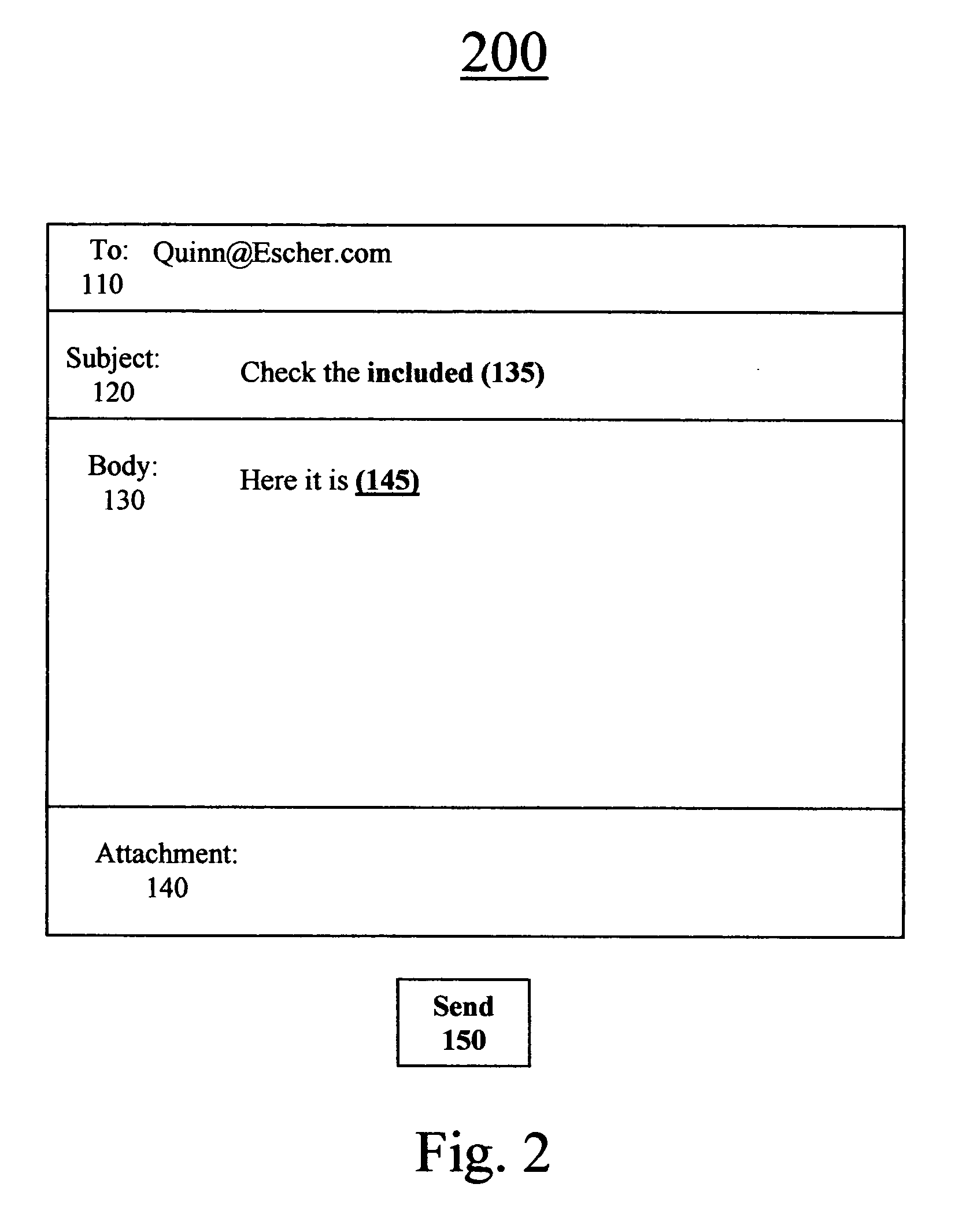
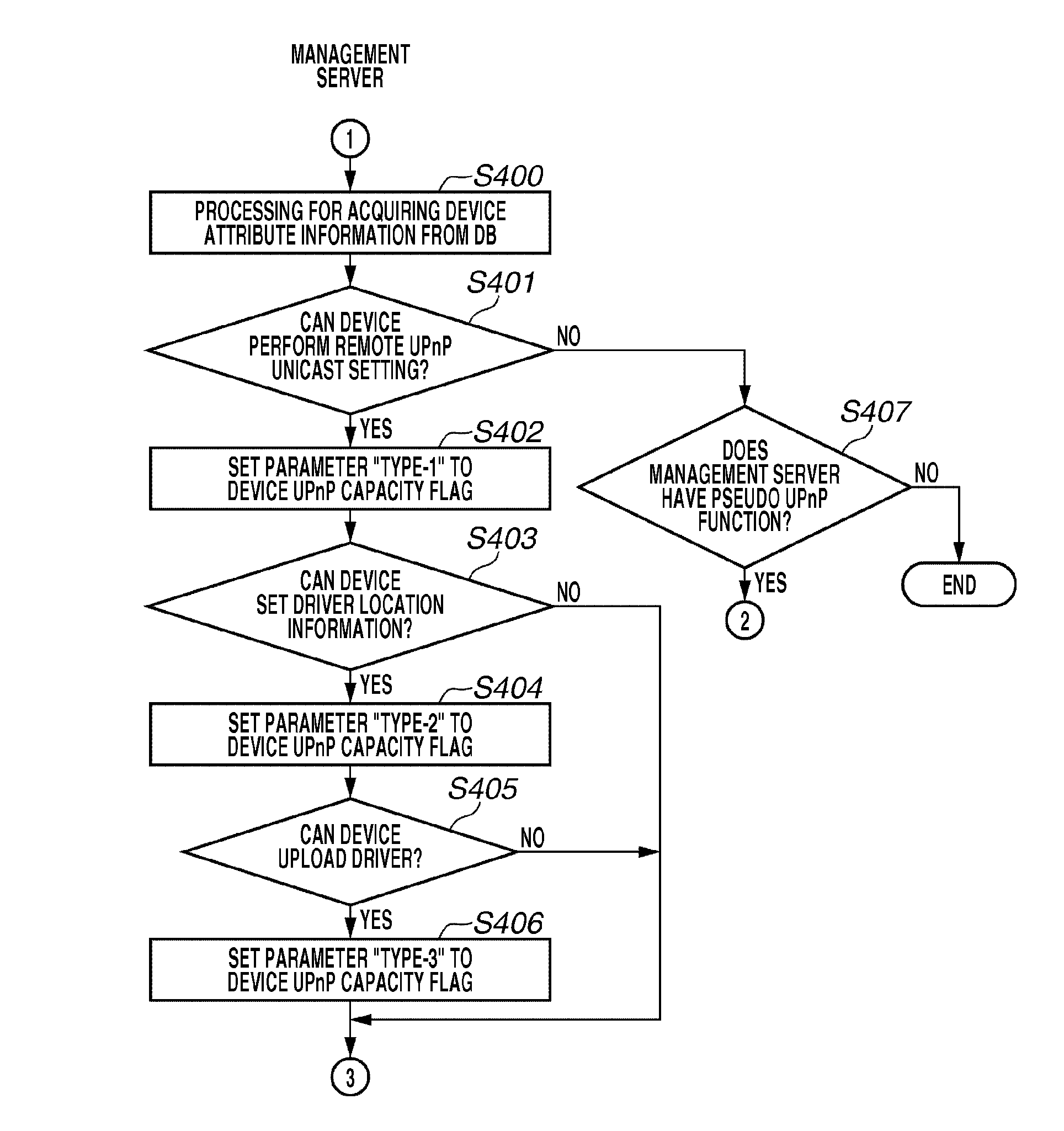
InactiveUS20090133015A1Multiple digital computer combinationsProgram loading/initiatingDriver/operatorSearch protocol
A driver management apparatus includes a receiving unit configured to receive a network entry message sent by unicast according to a search protocol for one-to-one connection from one of a plurality of devices connected to a network, a determination unit configured to determine a capacity to install a driver according to the search protocol for one-to-one connection of a device connected to the network, and a processing unit configured to perform processing for installing, on a client terminal apparatus connected to the network, a driver for operating a device that has sent the network entry message. The processing unit is configured to perform different processing operations for installing the driver for operating the device with respect to respective devices having different capacities according to the capacity determined by the determination unit.
Owner:CANON KK
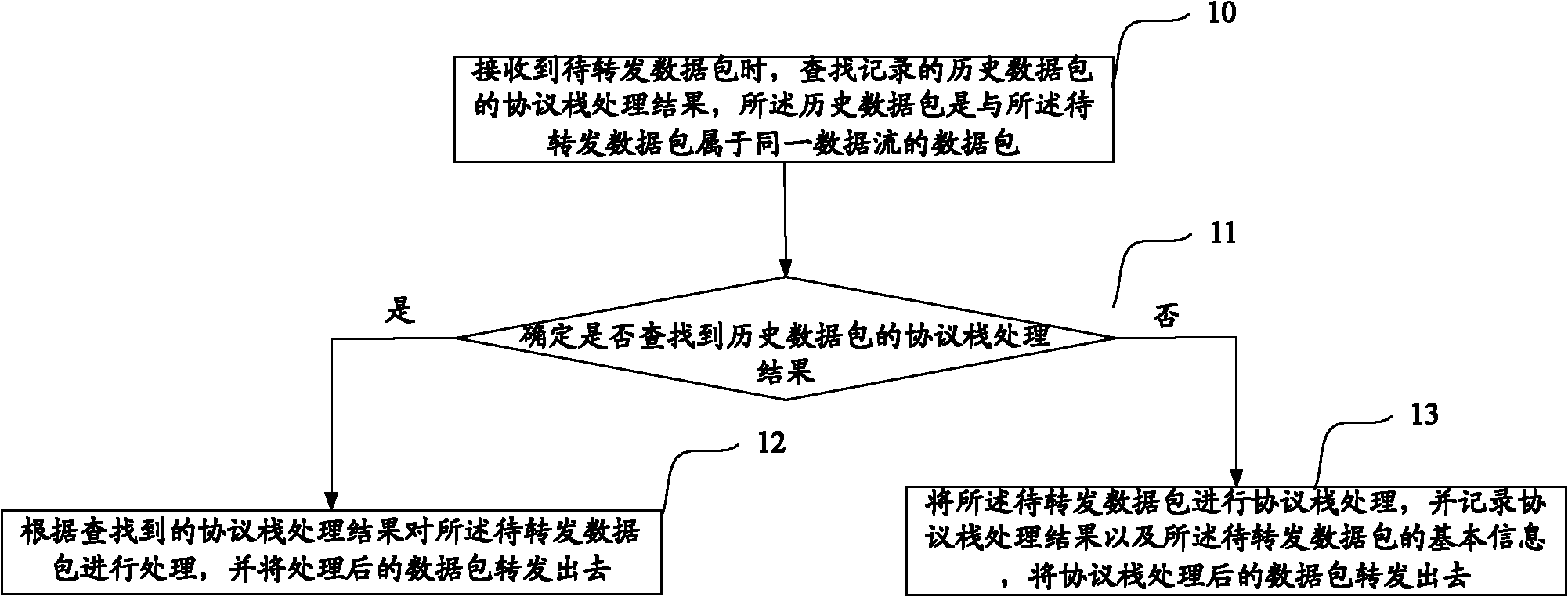
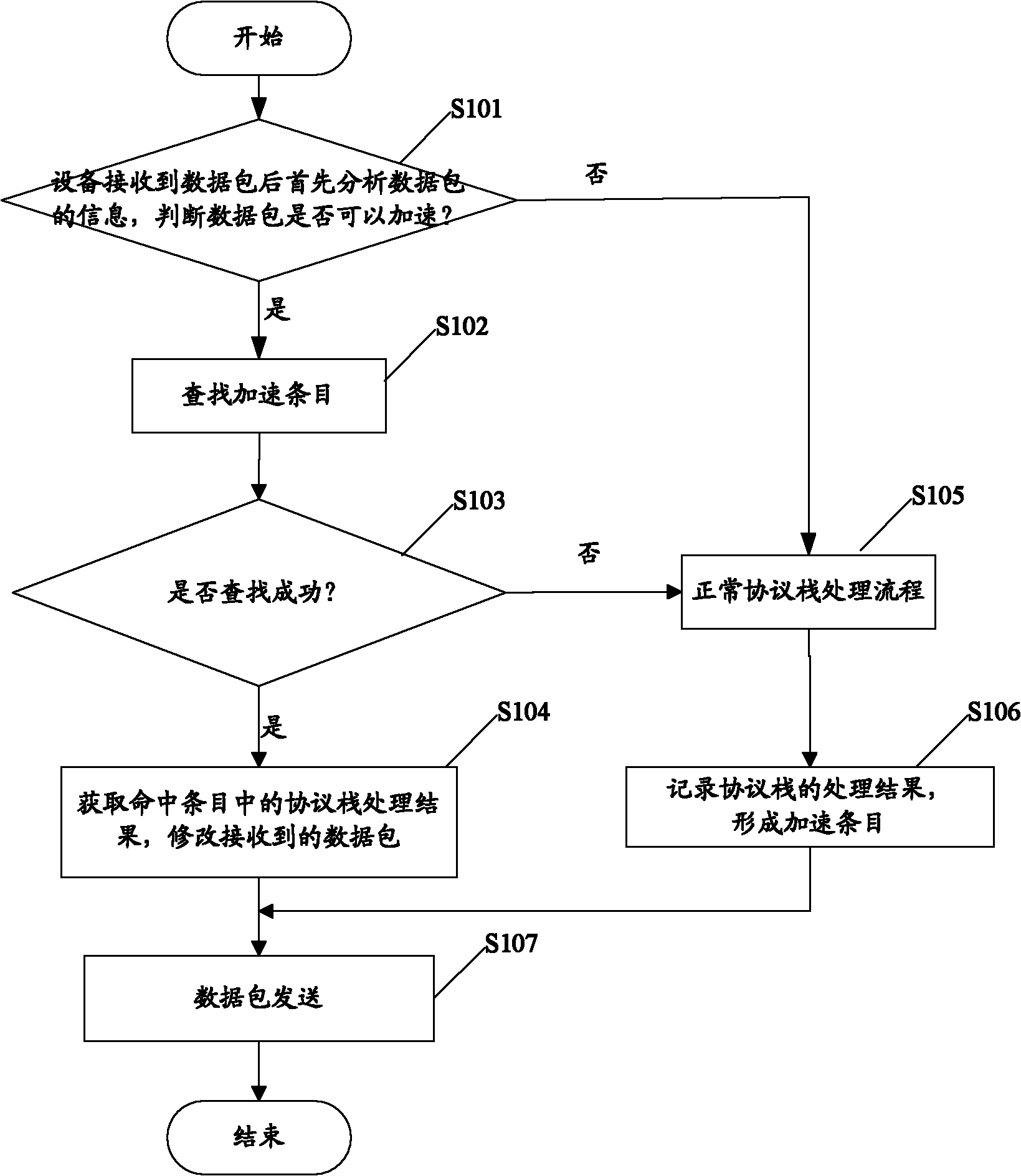
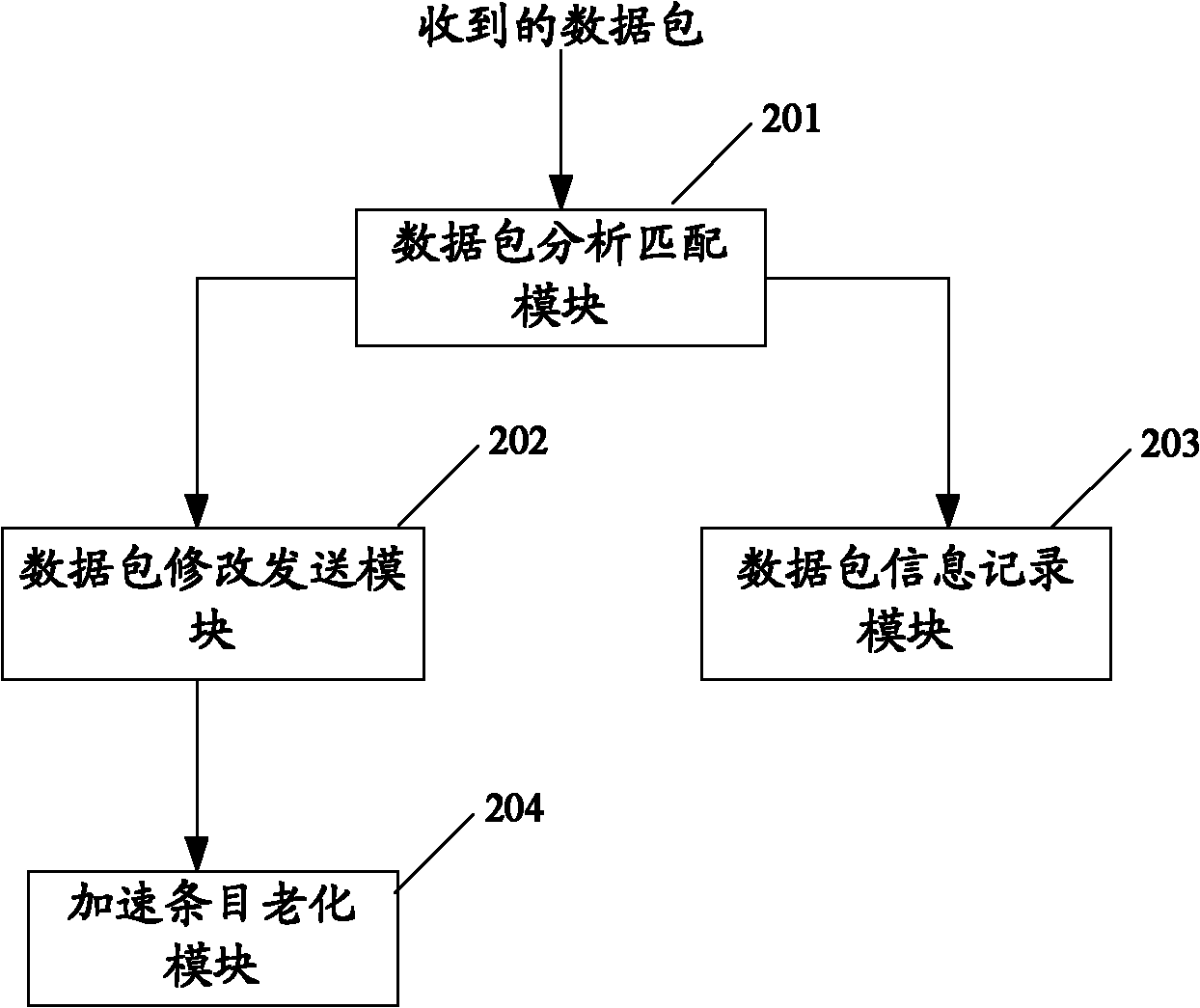
Packet forwarding method and equipment
InactiveCN102123082AReduce processing timeImprove forwarding efficiencyData switching networksComputer hardwareData stream
The embodiment of the invention discloses a packet forwarding method and equipment which relate to the field of network communication and are used for improving the packet forwarding efficiency of communication equipment. In the invention, when the packet to be forwarded is received, the communication equipment searches for the recorded protocol stack processing result of a historical packet belonging to the same data stream as the packet to be forwarded, processes the packet to be forwarded according to the searched protocol stack processing result, and forwards the processed packet. According to the invention, as the protocol stack processing is not needed for each received packet to be forwarded, and the packet to be forwarded can be processed according to the protocol stack processing result of the recorded historical packet, the processing time of the packet to be forwarded is shortened, and the packet forwarding efficiency of the communication equipment is greatly improved.
Owner:ZTE CORP
Method and apparatus for media handover in the network
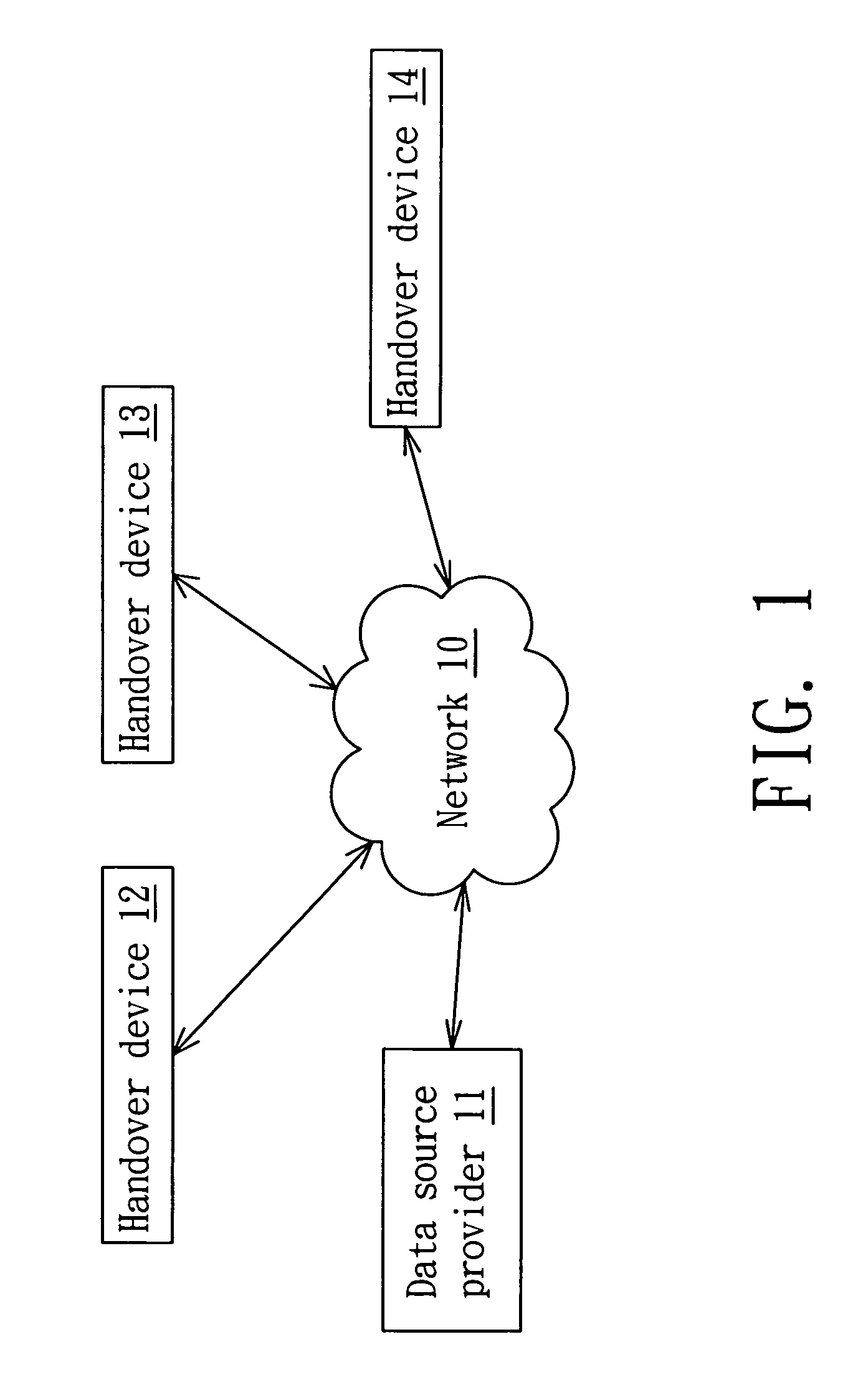
InactiveUS20070153740A1Easy to solveEasy to suspendBroadcast with distributionNetwork topologiesWired communicationData source
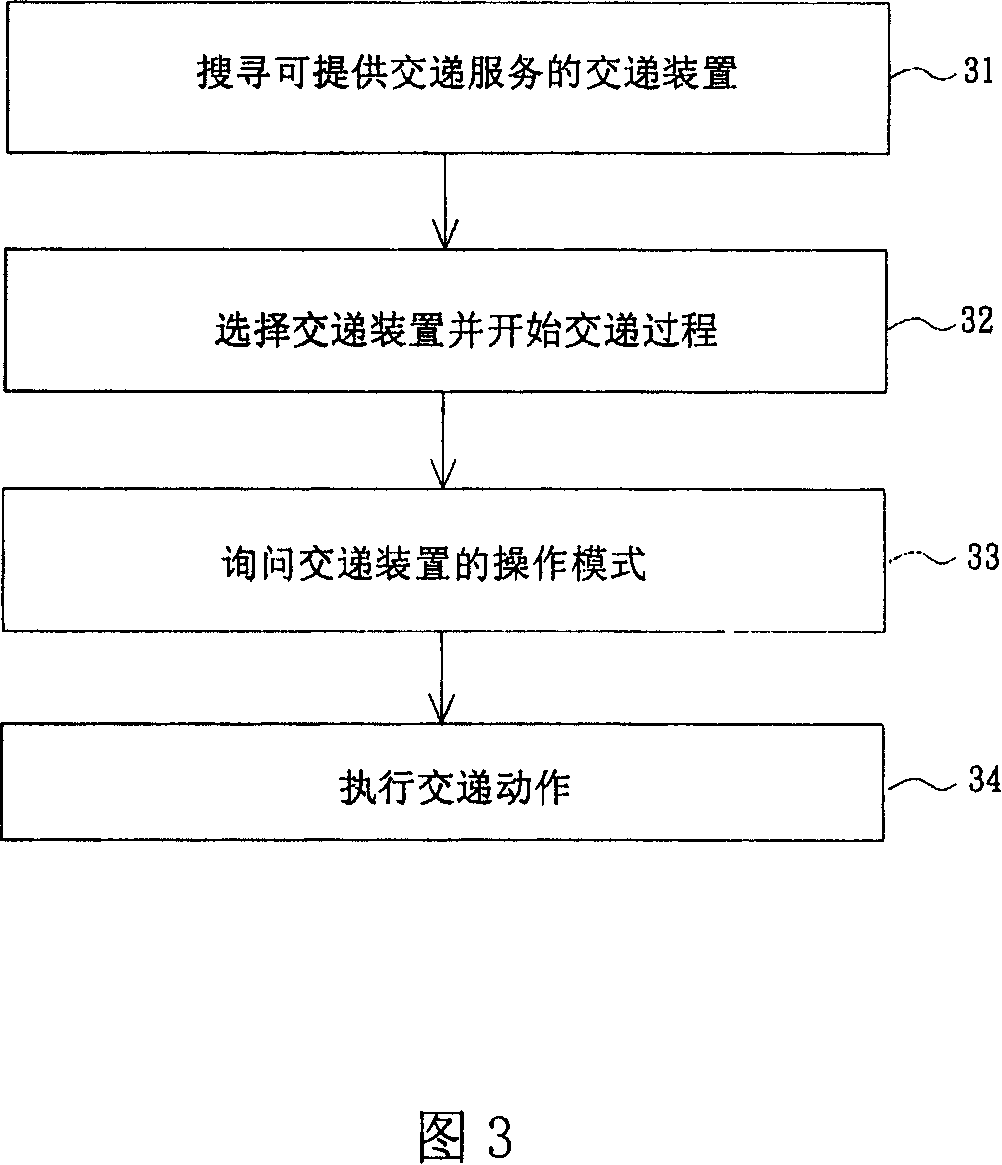
An innovative apparatus and method for media handover in the network is proposed. The apparatus comprises a communication network; a data source provider and handover devices. The handover device comprises a handover module for executing the handover execution. The handover process comprises searching for handover target devices by a searching protocol in a communication network, wherein the communication network comprises a wireless communication network or a wired communication network; selecting the target device and starting a handover process; querying the operation mode of the target device; and performing the handover process.
Owner:ARCADYAN
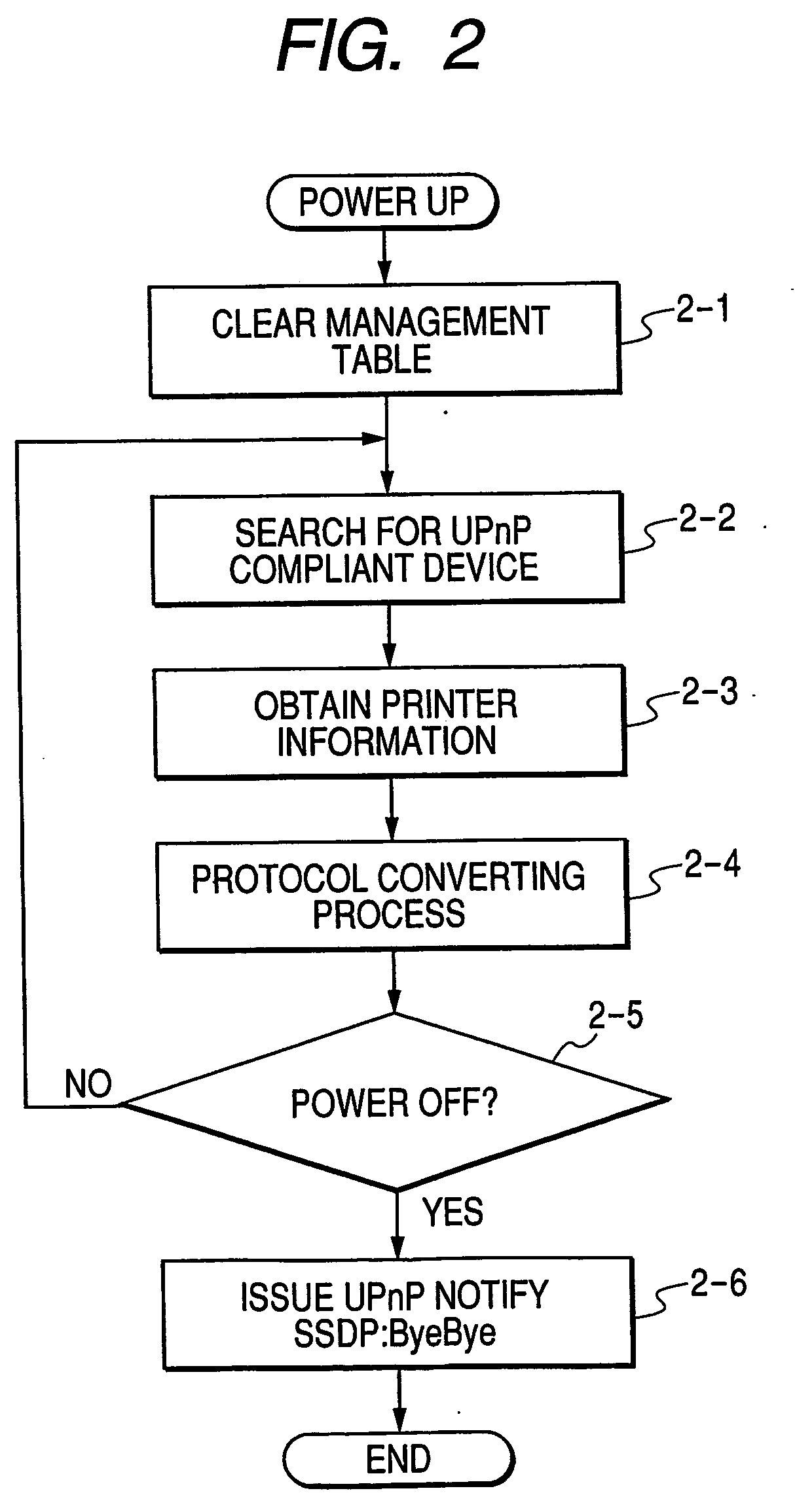
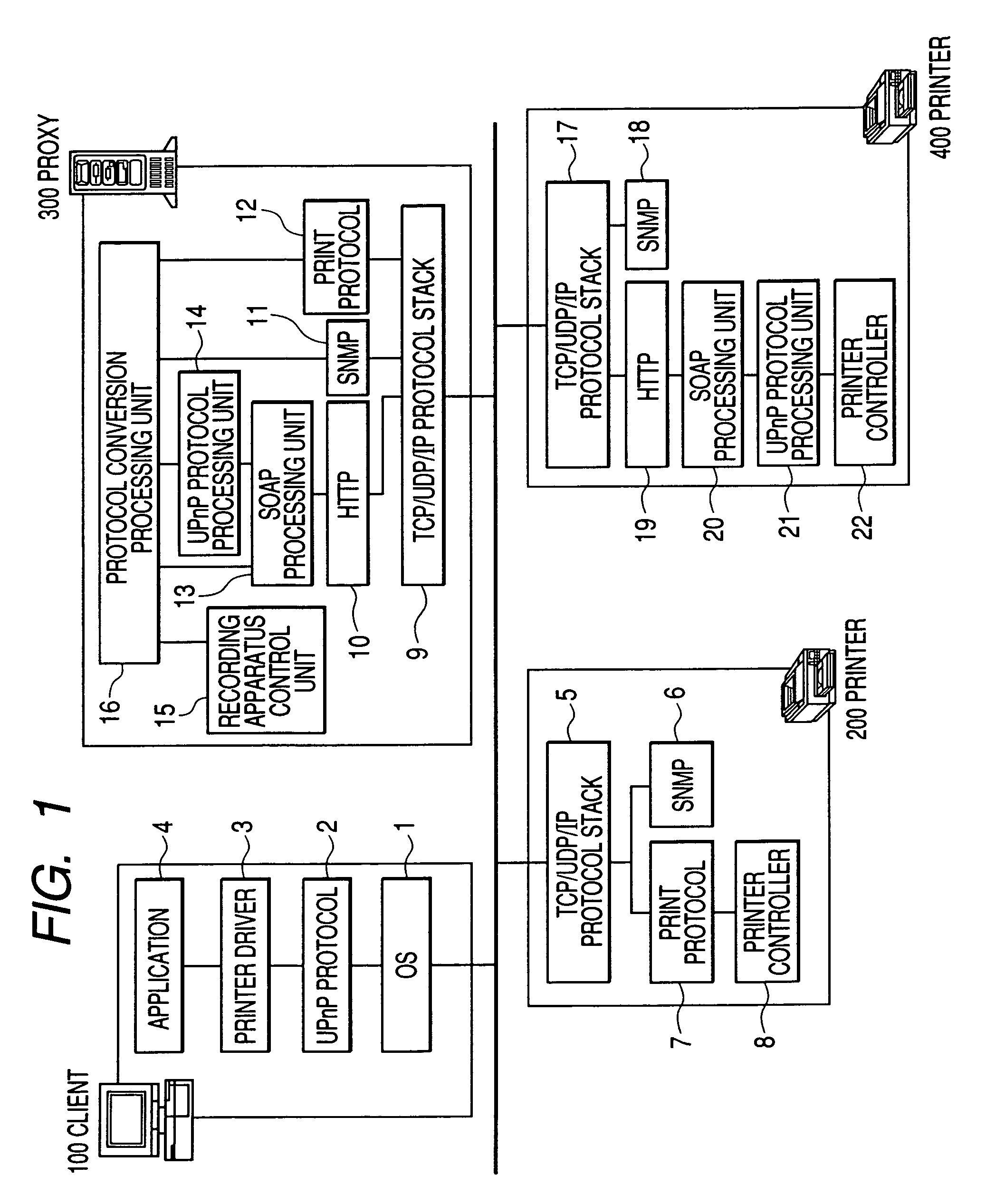
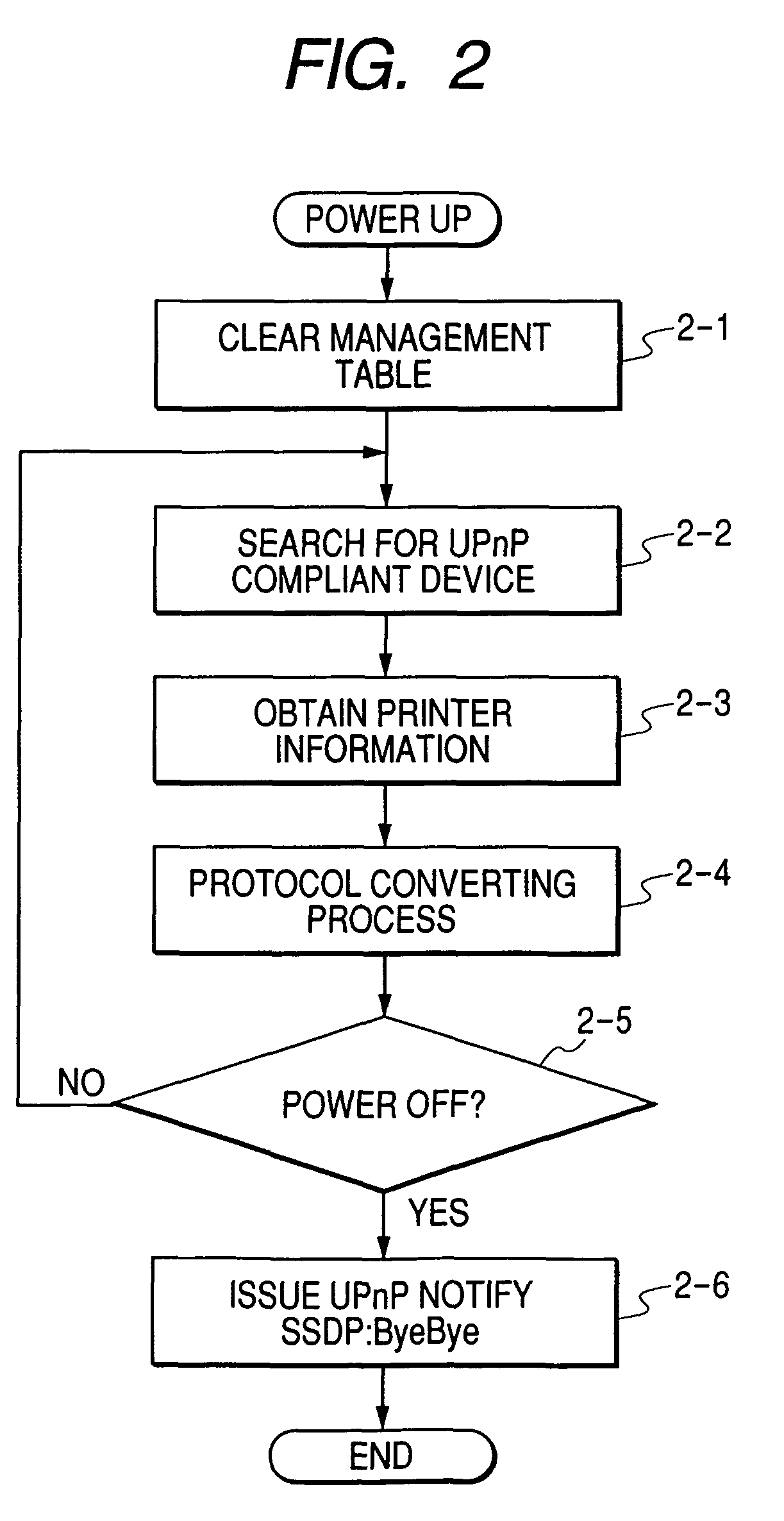
Apparatus, method, and program for executing protocol converting process
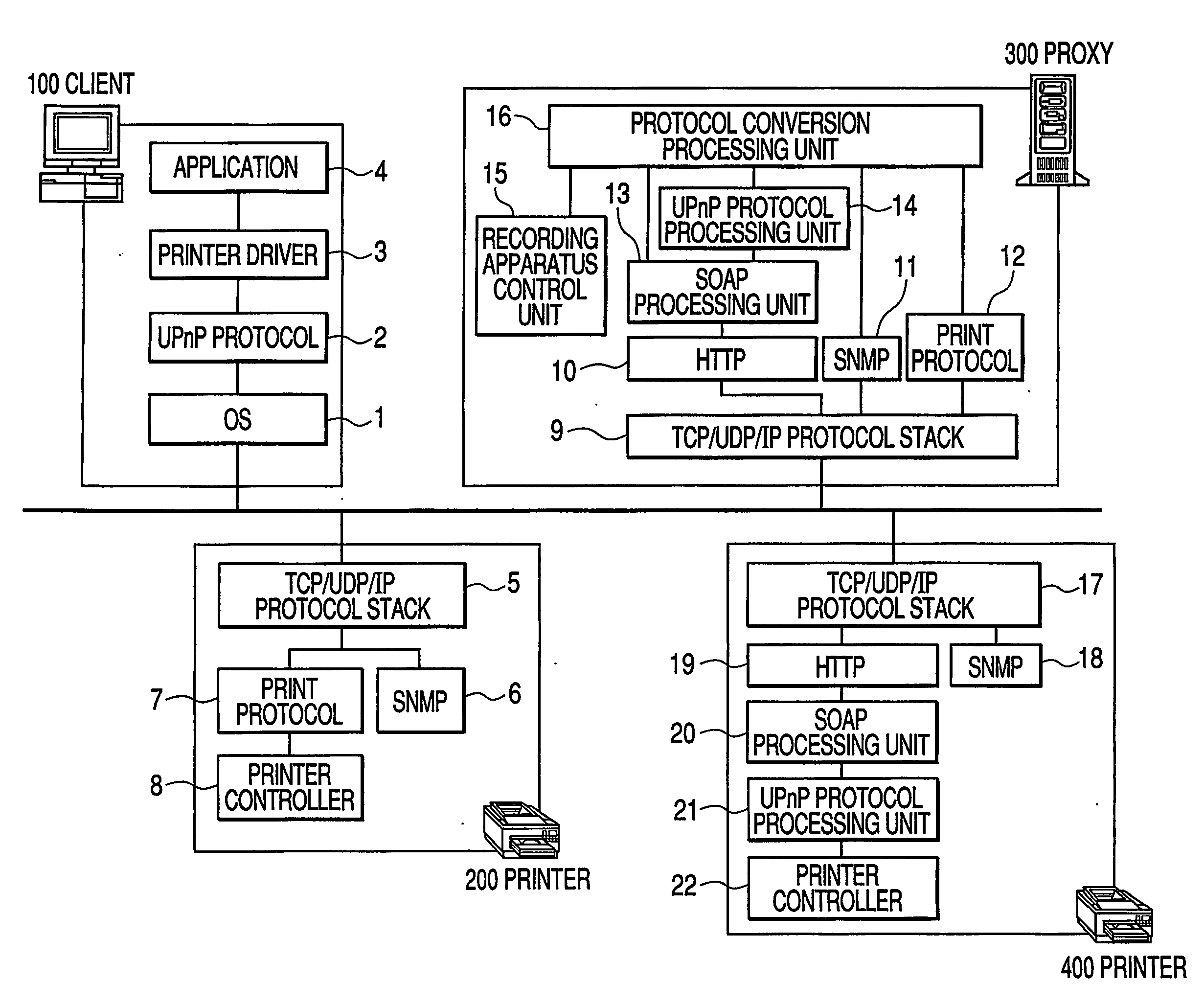
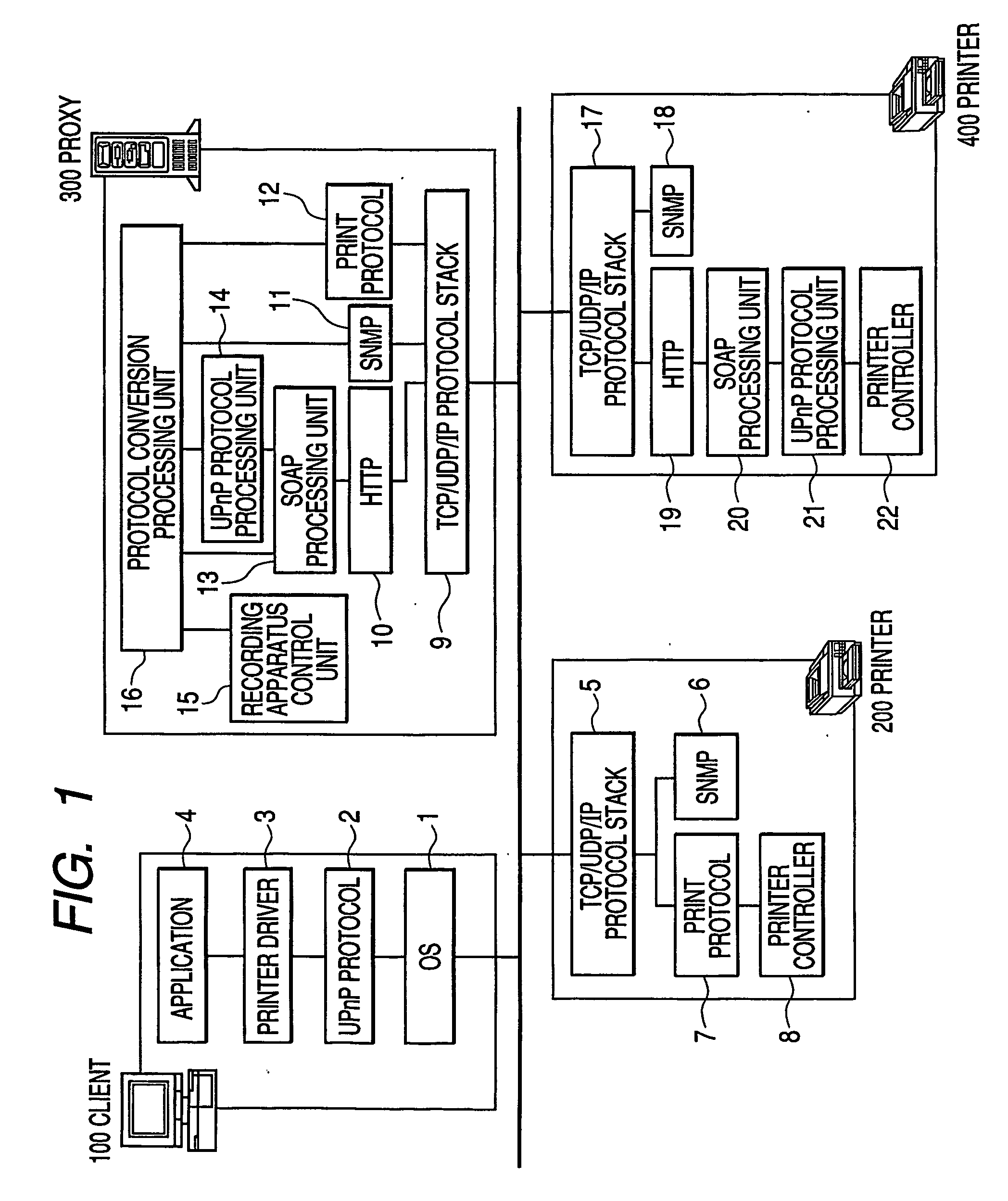
InactiveUS20060184510A1Special data processing applicationsHome automation networksNetworked systemSearch protocol
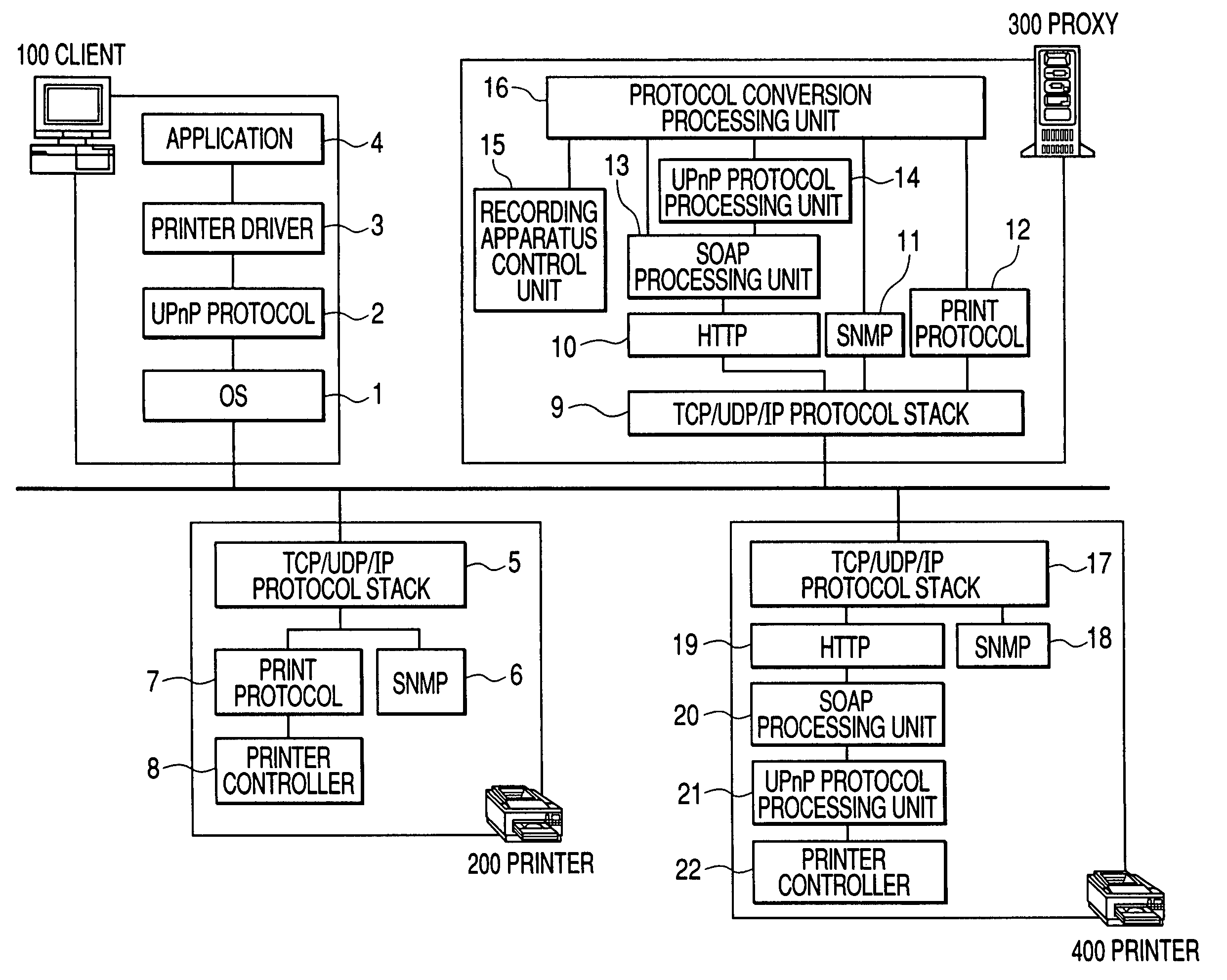
When a device searches a network, there is a case where the device is recognized as different devices as one searched by a protocol A and the other searched by a protocol B. In a proxy server 9300 for executing a protocol converting process in a network system, whether or not another protocol converting apparatus for executing a predetermined protocol converting process does not exist on the network is searched. When another protocol converting apparatus is searched on the network, whether or not the searched protocol converting apparatus has executed the protocol converting process is discriminated.
Owner:CANON KK
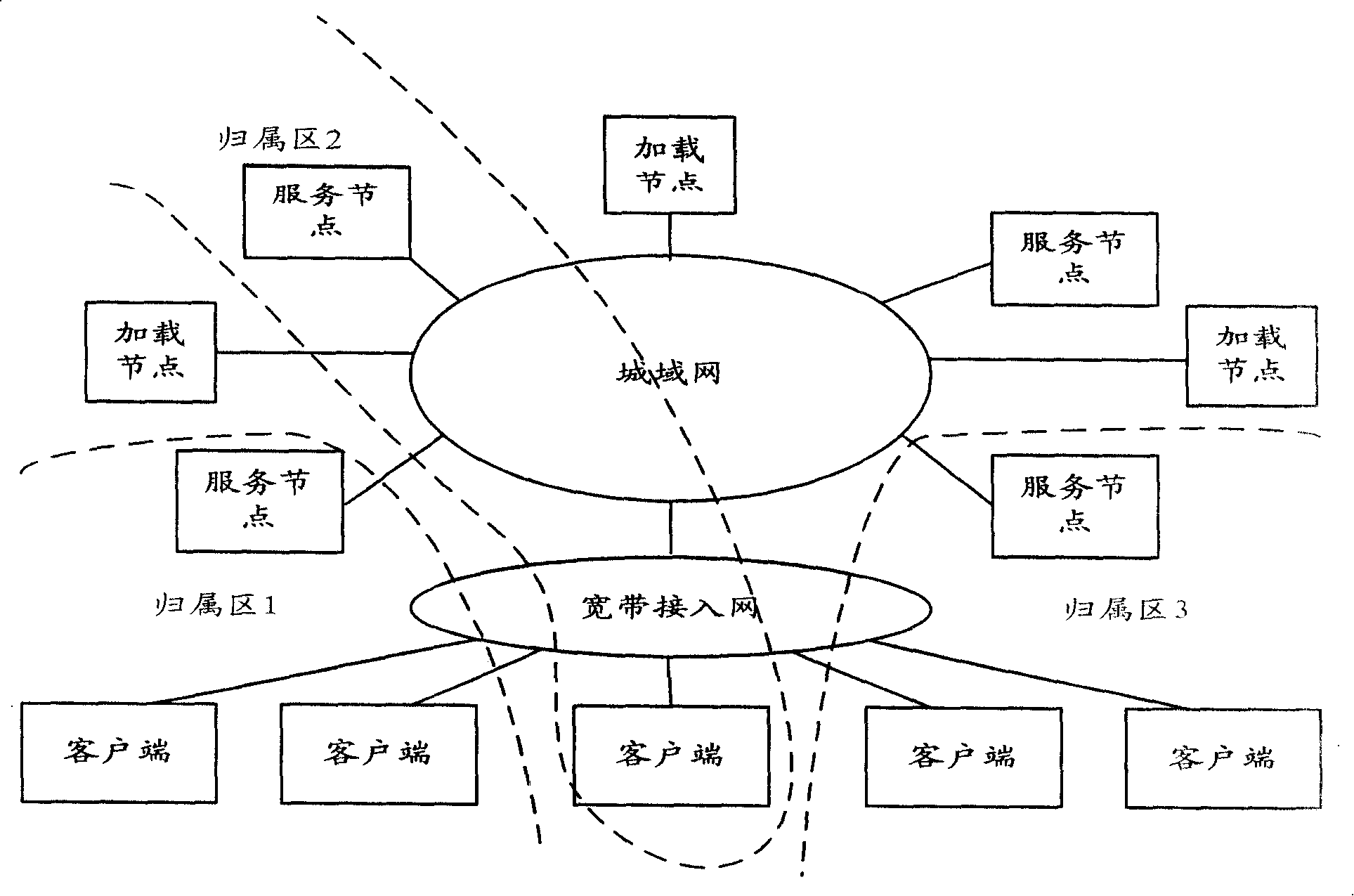
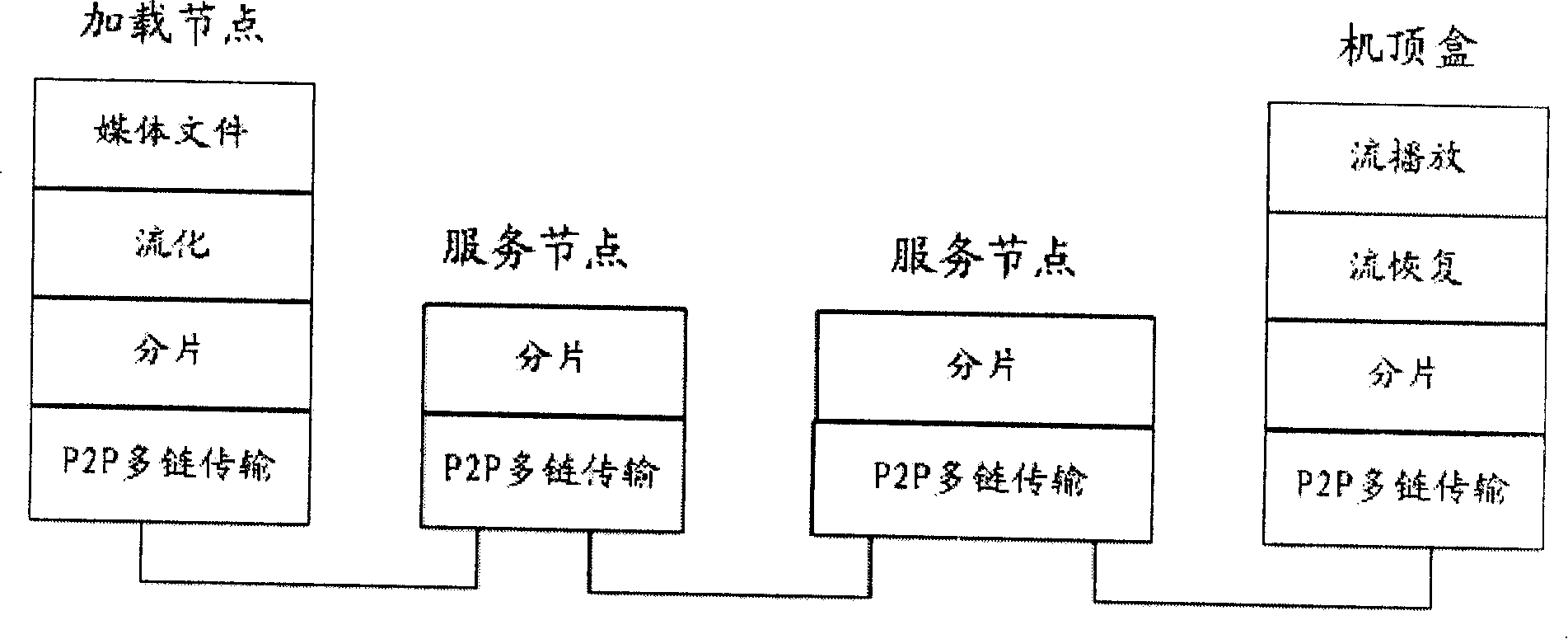
A video content service system and service method
InactiveCN101193294ASolving Scalability IssuesSolve the problem of funnel effectTwo-way working systemsSelective content distributionSystem maintenanceSearch protocol
The invention relates to a system and a method for service of video contents. A video loading node and the video service node adopt a P2P protocol to form a P2P-CDN network. The CDN network is divided into a plurality of assignment service areas; each client is allocated with an assignment CDN node; the video client is connected with an assignment CDN node through the network. When a user requests media displaying, the video client sends media search information to the assignment CDN node according to a P2P search protocol. The assignment CDN node selects a service node in the whole P2P-CDN and returns the node to the client. The client generates a media service request toward the service node and builds up a control link with control units and a plurality of data links with a plurality of media units, and media data is requested through the links. The invention solves problems such as scale expansibility of the CDN network, enhances the reliability of the system and reduces the maintenance cost of the system.
Owner:ZTE CORP
Uniform search system and method for selectively sharing distributed access-controlled documents
InactiveUS7409406B2Data processing applicationsWeb data indexingRandomized algorithmStochastic algorithms
Owner:INT BUSINESS MASCH CORP
User search method, system, server and client terminal for instant communication
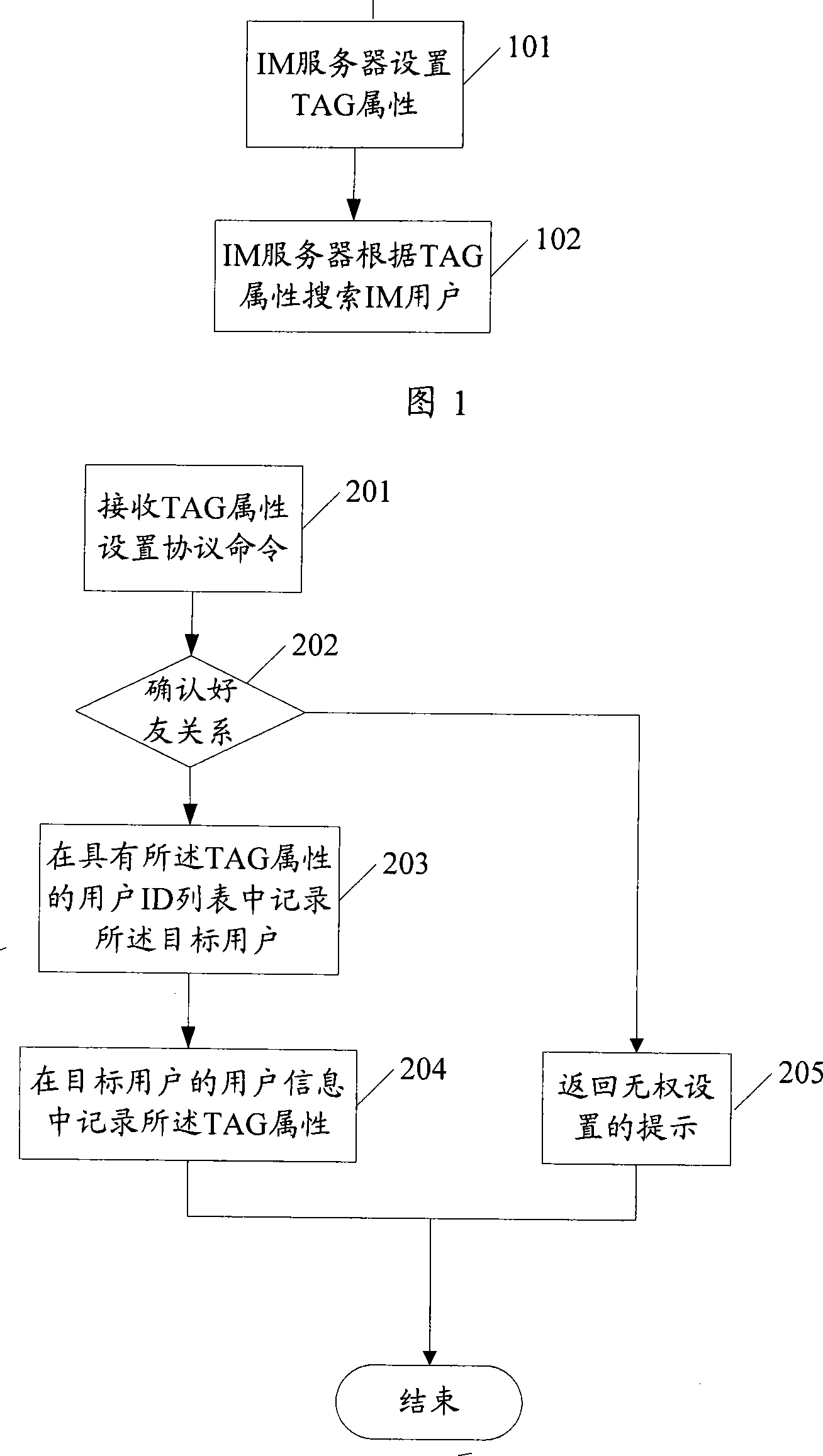
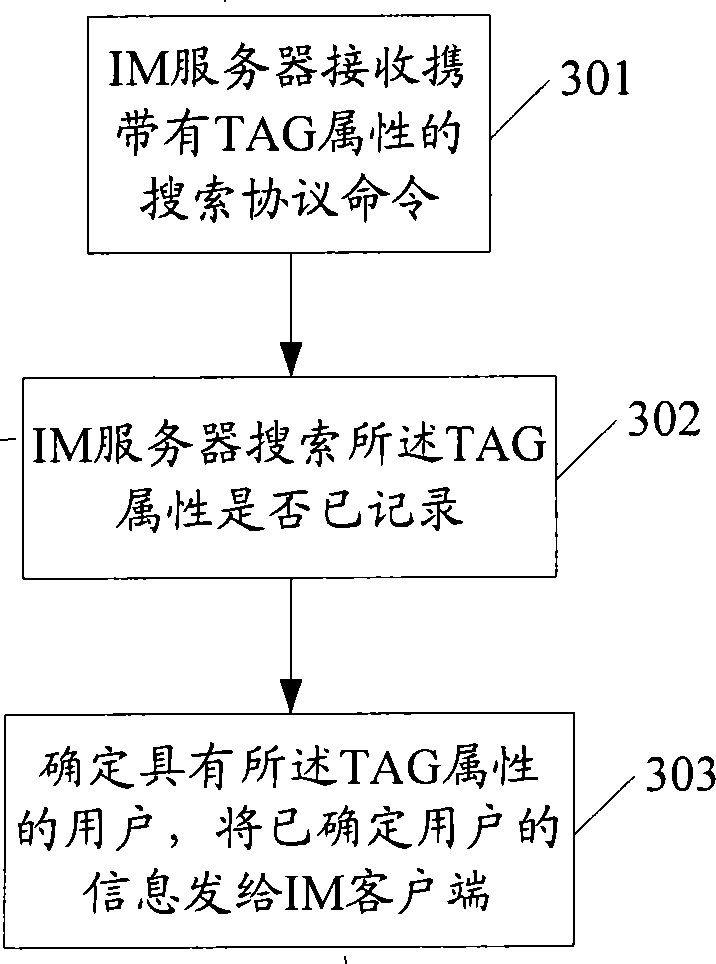
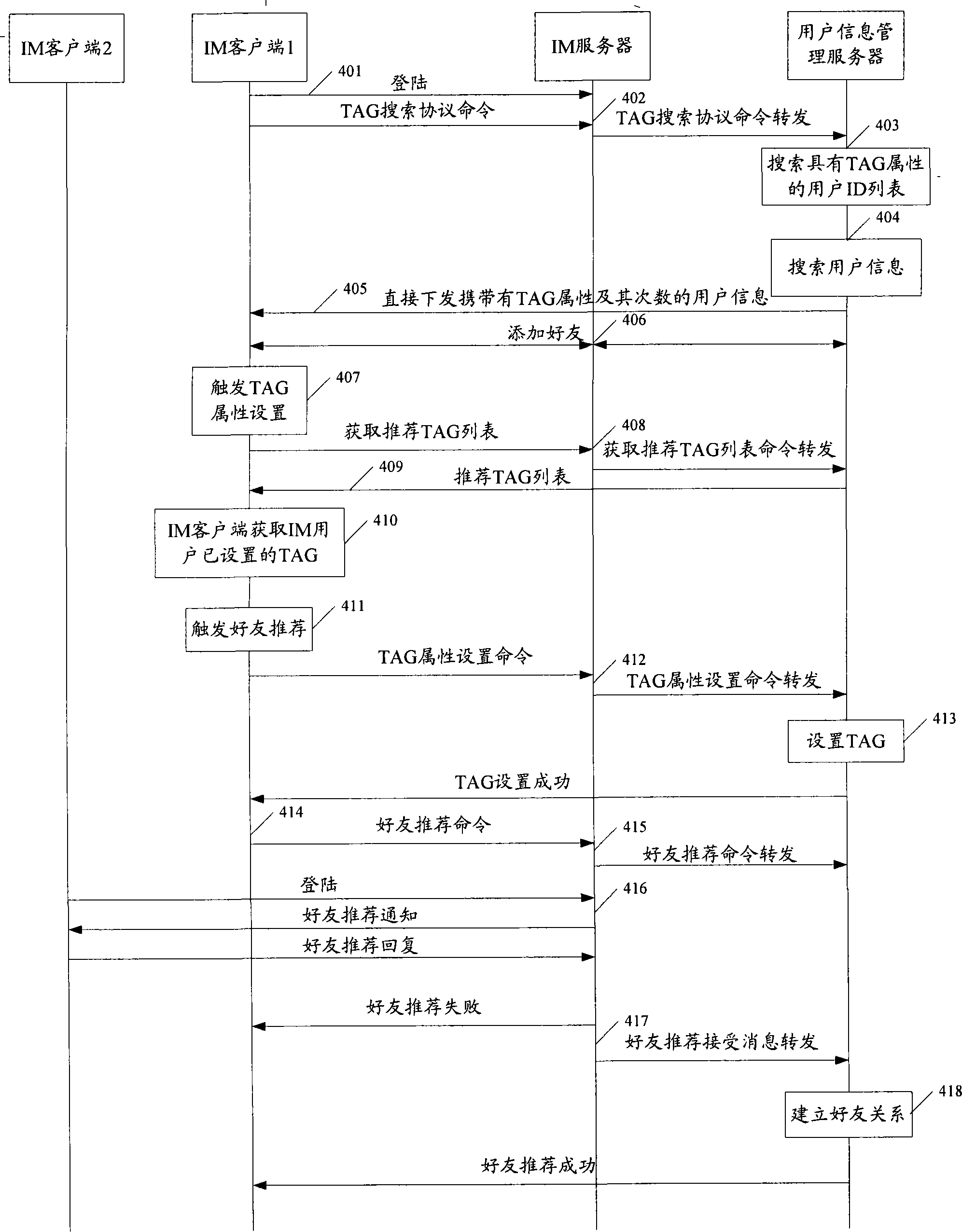
The embodiment of the invention discloses an instant communication IM user searching method, comprising the steps of: after IM server receives TAG attribute protocol instruction carrying a tag of TAG attribute and target user identity ID, if the user sending the protocol instruction is the target user, or the user has good friend relationship with the target user, recording the ID of the target user in the user ID list having the TAG attribute, and recording the TAG attribute in the user information of the target user; after IM server receives searching protocol instruction carrying the TAG attribute, if the IM server searches record of the TAG attribute, determining user having the TAG attribute, and sending information of the determined user to IM client of the searching protocol instruction. The invention also discloses an IM system, a server and a client for supporting TAG search. The embodiment of the invention can be applied to searching IM user for with user's own true situation reaction.
Owner:TENCENT TECH (SHENZHEN) CO LTD
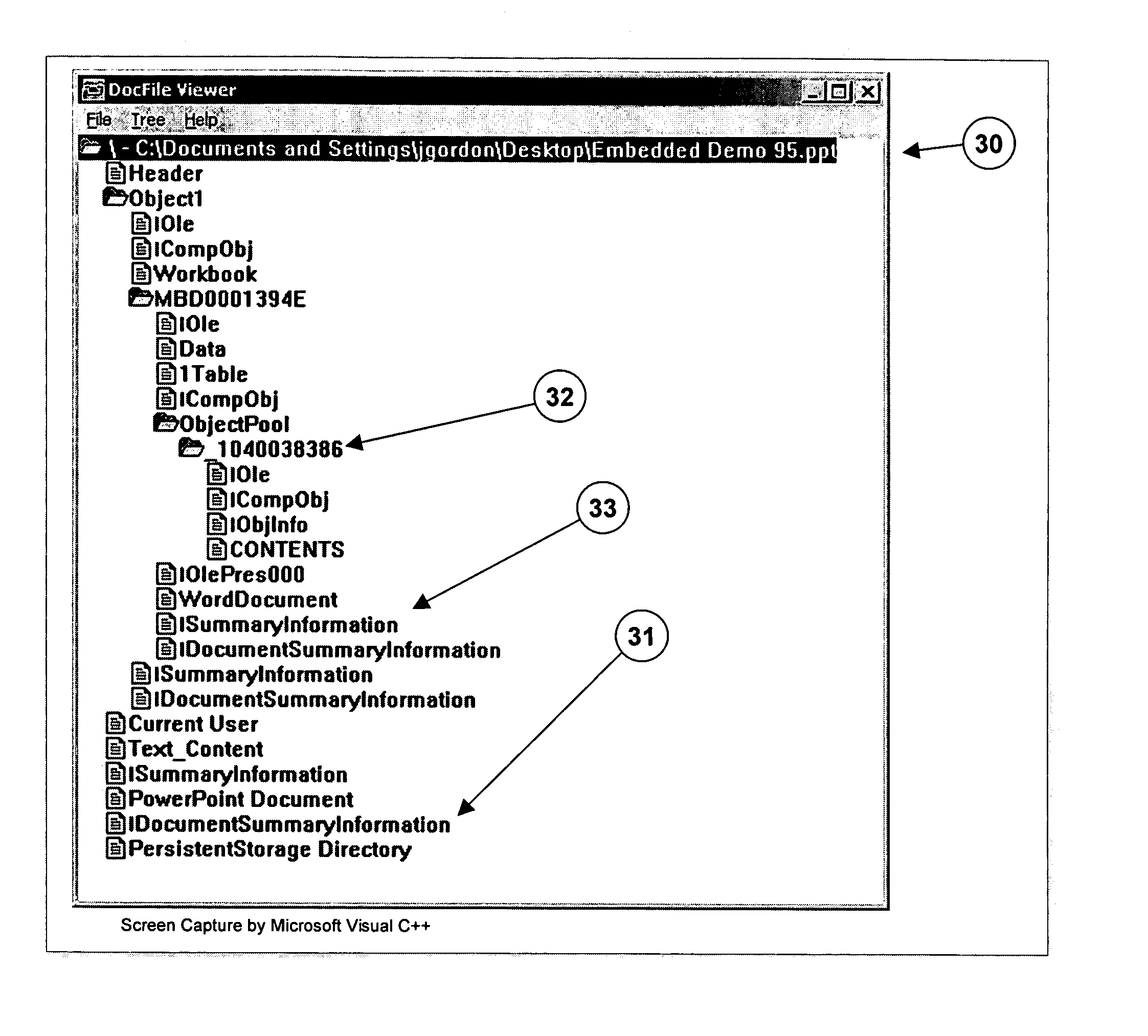
System and method for detecting, analyzing and controlling hidden data embedded in computer files
InactiveUS20060174123A1Useful for promotionEasy accessUser identity/authority verificationComputer security arrangementsHidden dataDecomposition
A system and method for detecting, analyzing, and controlling the content of computer files and information in a variety of formats, including embedded information. The system examines one or more computer files in their entirely, including any embedded files, objects, or data, looks of confidential or secret information according to an established security search protocol, which may vary from user to user. Objects in a computer file are identified and decomposed into component objects. This process can be repeated until a user-specified depth of decomposition is achieved, or until the component objects can no longer be decomposed. The component objects are then analyzed for specific content, which is displayed for review by the user. The user can then make decisions regarding removal or modification of that content before sending the file on for further processing or delivery to a recipient. A certificate file linked to the computer file documents the results of the analysis and any deletions or modifications, and can be stored in a central database. Files also may be given a risk score based on the occurrence of certain objects, data, or keywords in a file, based on type and location.
Owner:MANTECH SRS TECH
Information processing appratus, method, and storage medium
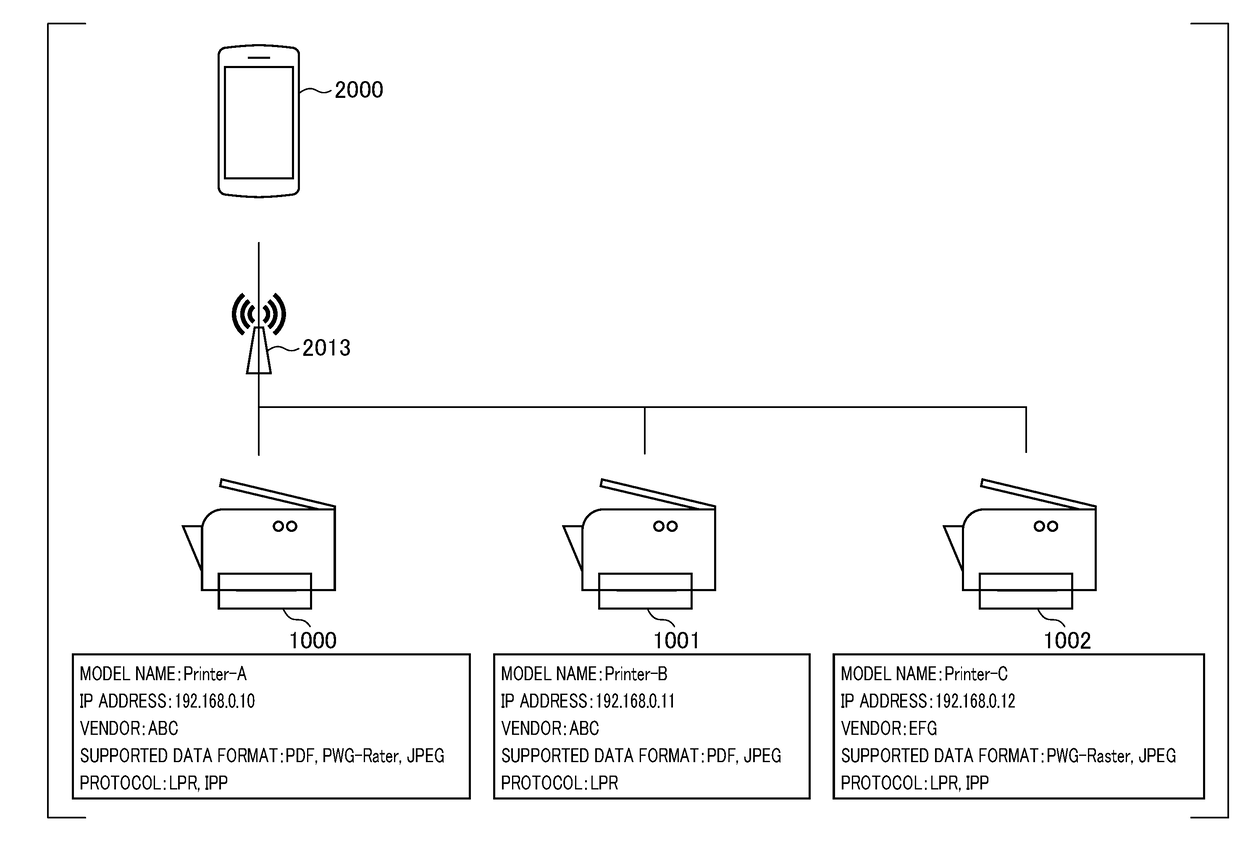
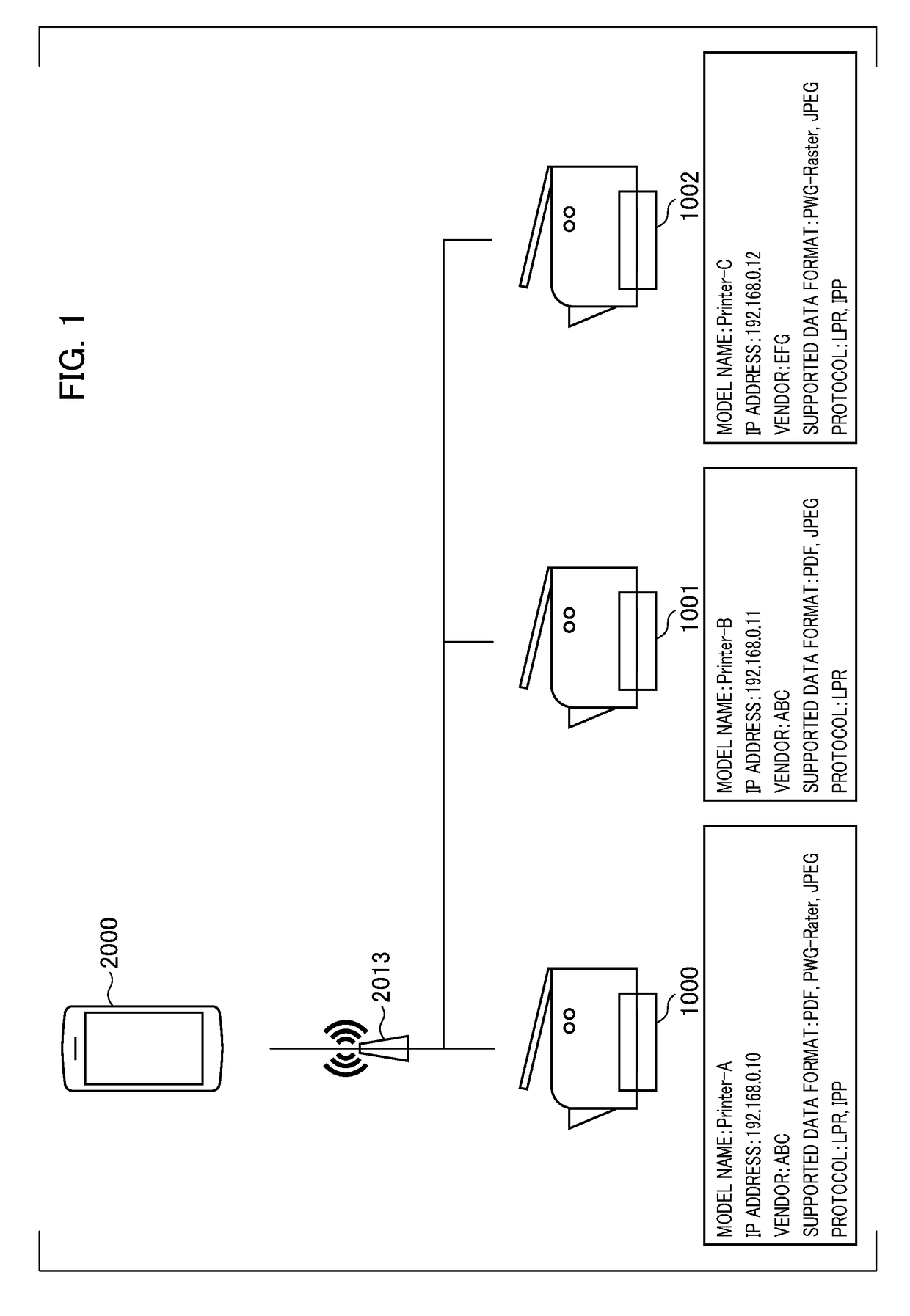
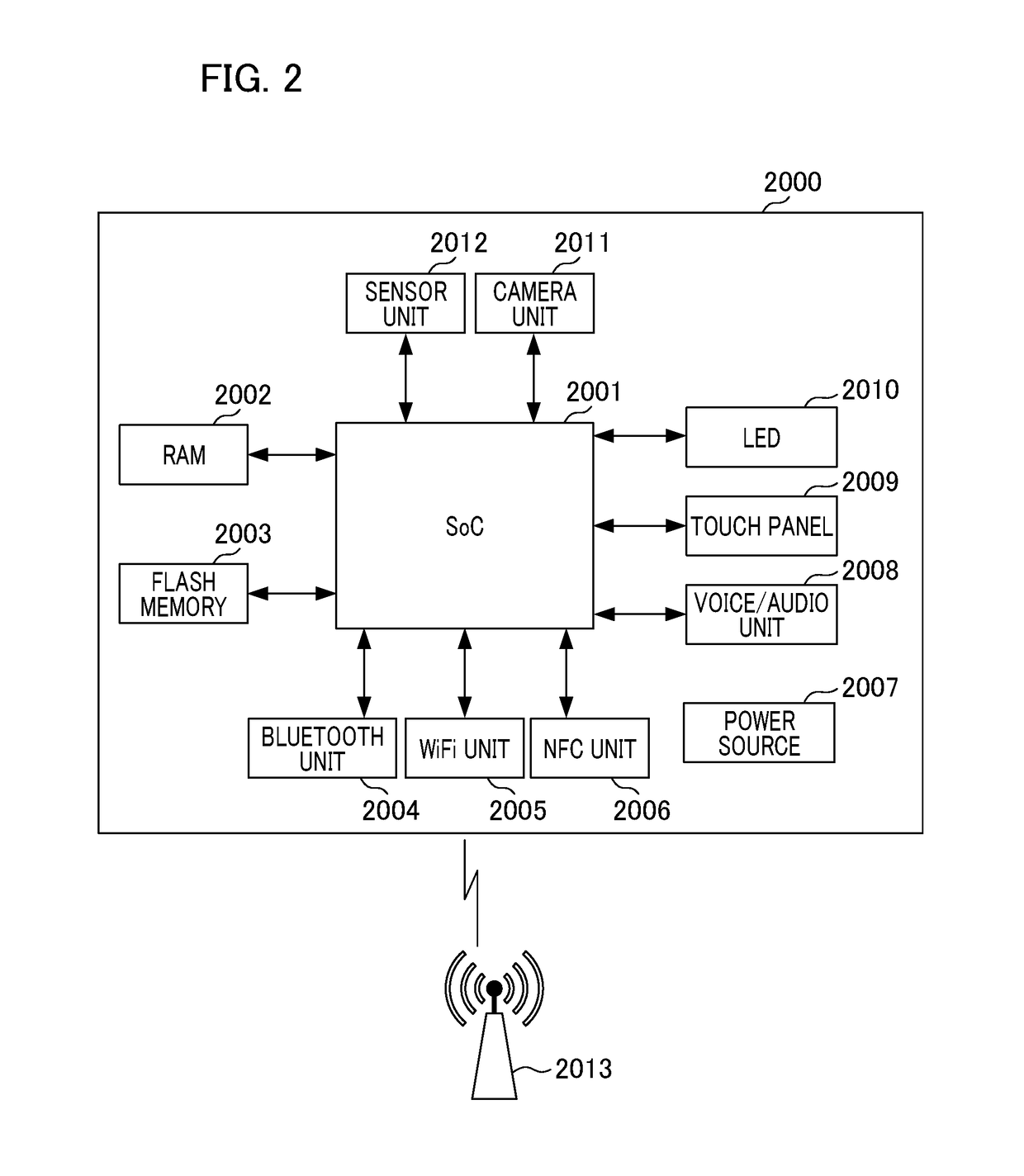
ActiveUS20180210684A1Without impairing the user's convenienceEnergy efficient computingDigital output to print unitsInformation processingComputer hardware
A mobile terminal device executes an OS including a printing system that supports a first search protocol and a printing function using a first printing method as a standard. If instructions for the use of the printing system included in the OS are provided by the user, the mobile terminal device receives a message conforming to the first search protocol from a printer that has been newly detected via the first search protocol. In a case where the detected printer has been selected, if the printer is determined not to conform to the first printing method based on the contents of the received message, the mobile terminal device activates a function for downloading a plug-in that supports the printer.
Owner:CANON KK
Uniform search system and method for selectively sharing distributed access-controlled documents
InactiveUS20080183703A1Data processing applicationsWeb data indexingStochastic algorithmsRandomized algorithm
A privacy-preserving index system addresses the problem of providing a privacy-preserving search over distributed access-controlled content. Indexed documents can be readily reconstructed from inverted indexes used in the search. The privacy-preserving index system builds a centralized privacy-preserving index in conjunction with a distributed access-control enforcing search protocol. The privacy-preserving index utilizes a randomized algorithm for constructing a privacy-preserving index. The privacy-preserving index is strongly resilient to privacy breaches. The privacy-preserving index system allows content providers to maintain complete control in defining access groups and ensuring its compliance, and further allows system implementors to retain tunable knobs to balance privacy and efficiency concerns for their particular domains.
Owner:IBM CORP
Apparatus, method, and program for executing protocol converting process
InactiveUS7895361B2Multiple digital computer combinationsElectric digital data processingNetworked systemSearch protocol
When a device searches a network, there is a case where the device is recognized as different devices as one searched by a protocol A and the other searched by a protocol B. In a proxy server 9300 for executing a protocol converting process in a network system, whether or not another protocol converting apparatus for executing a predetermined protocol converting process does not exist on the network is searched. When another protocol converting apparatus is searched on the network, whether or not the searched protocol converting apparatus has executed the protocol converting process is discriminated.
Owner:CANON KK
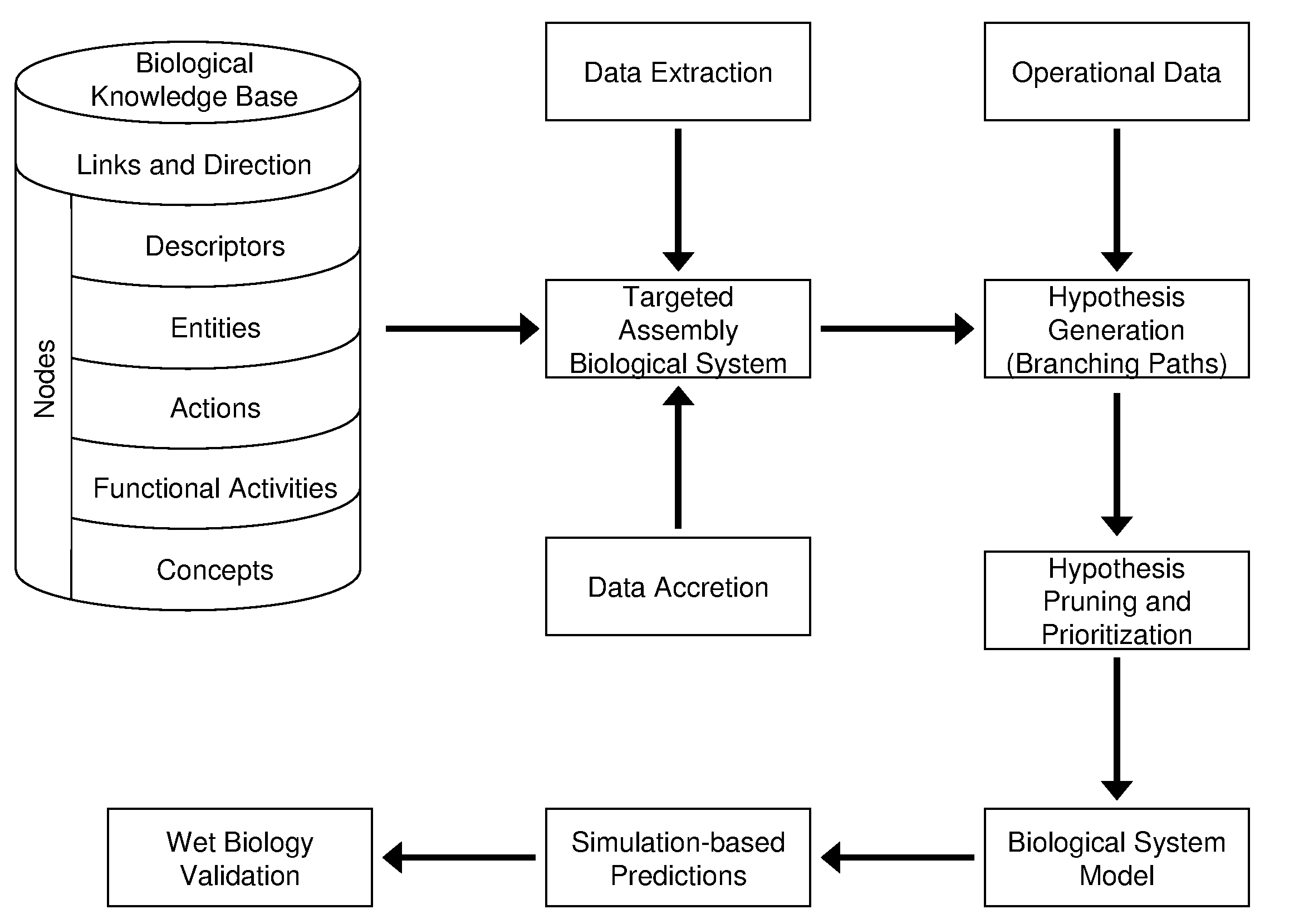
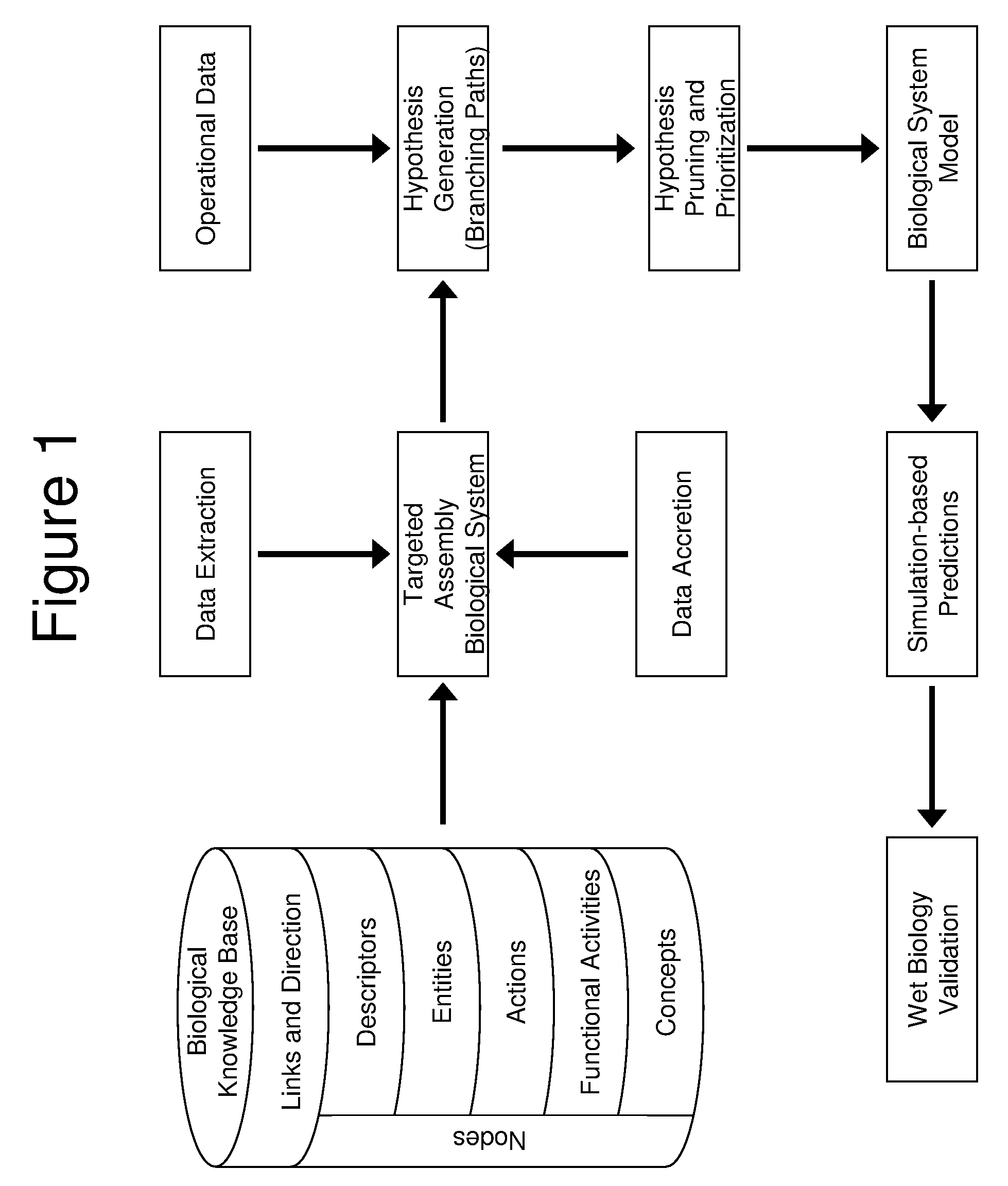
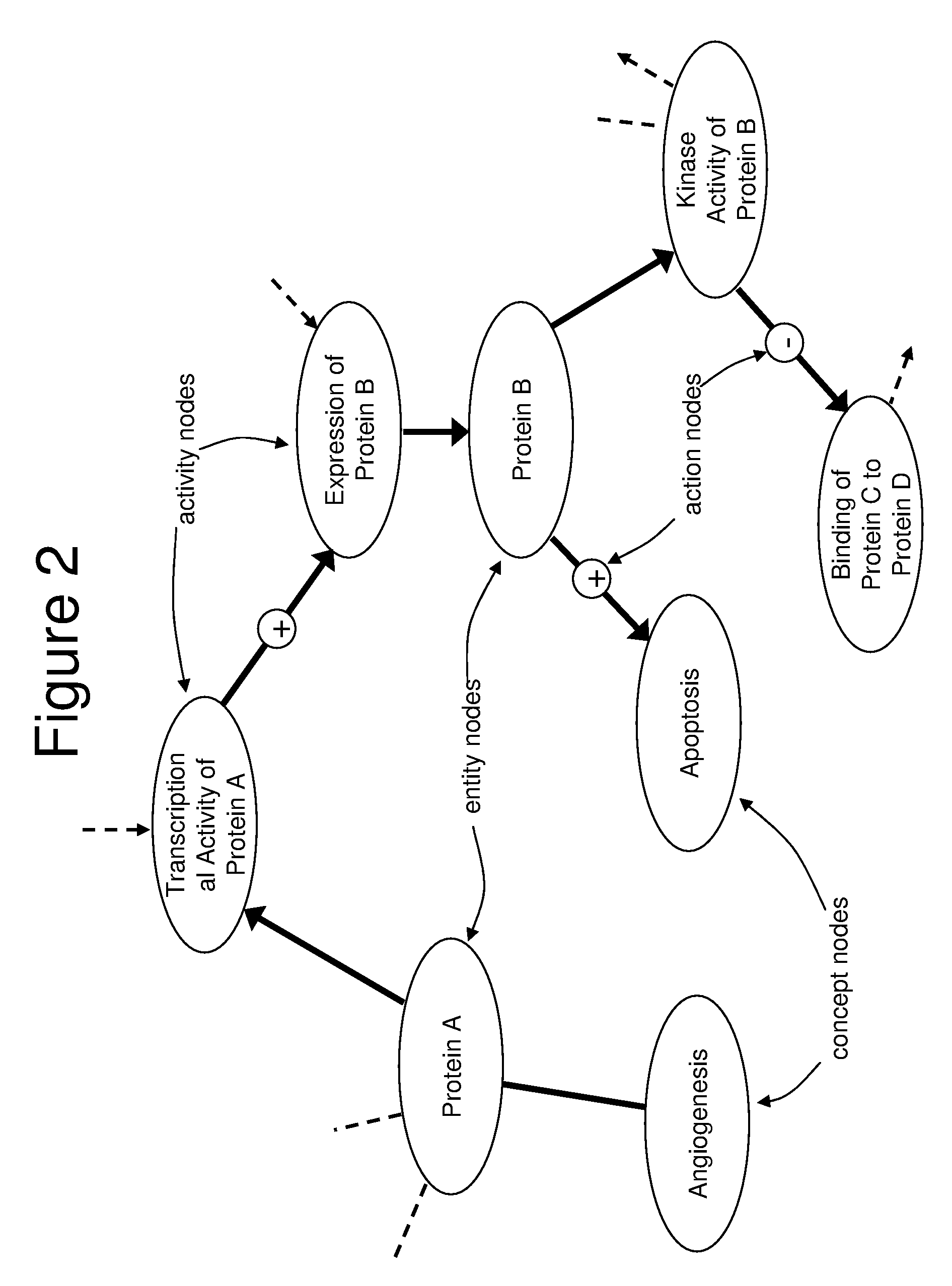
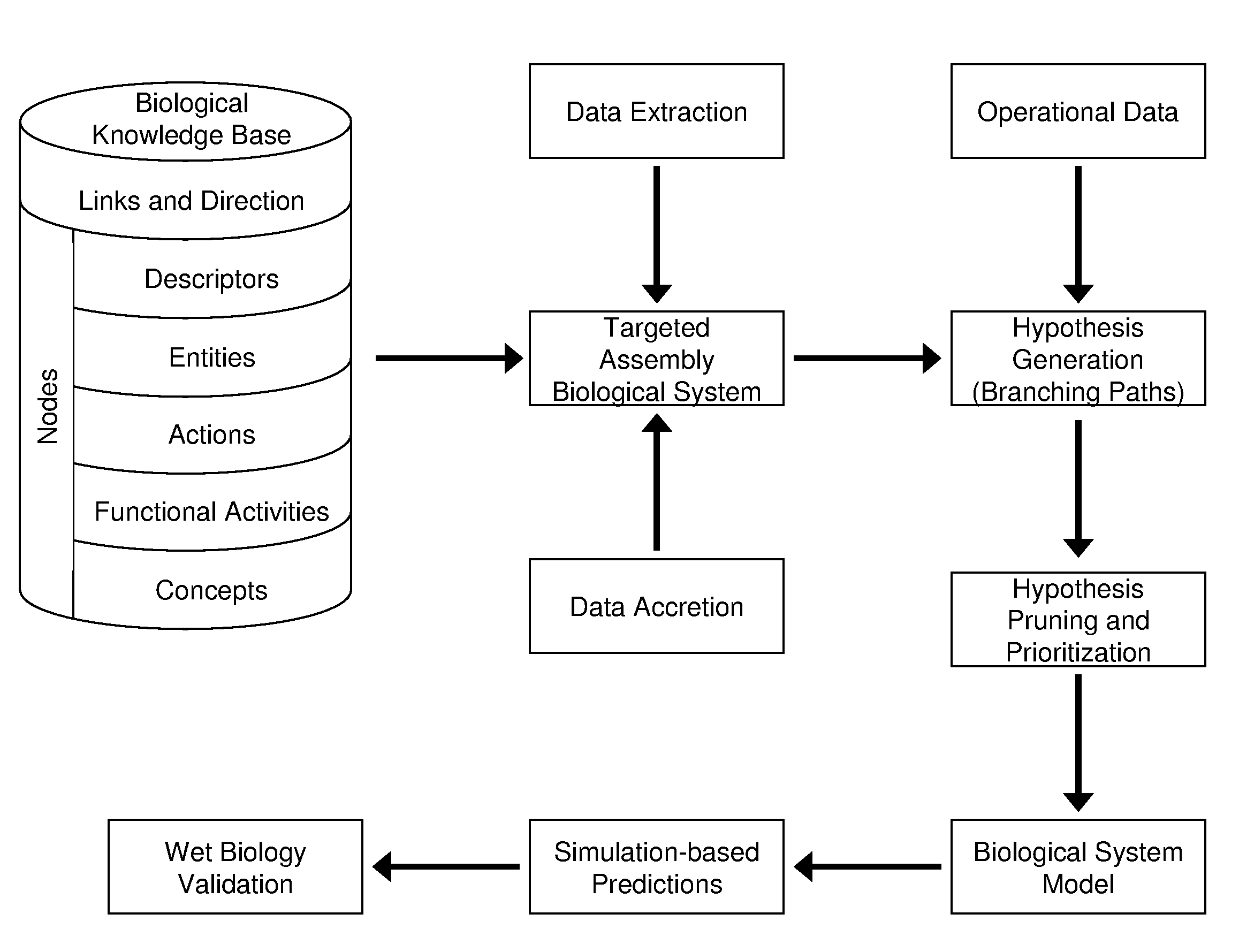
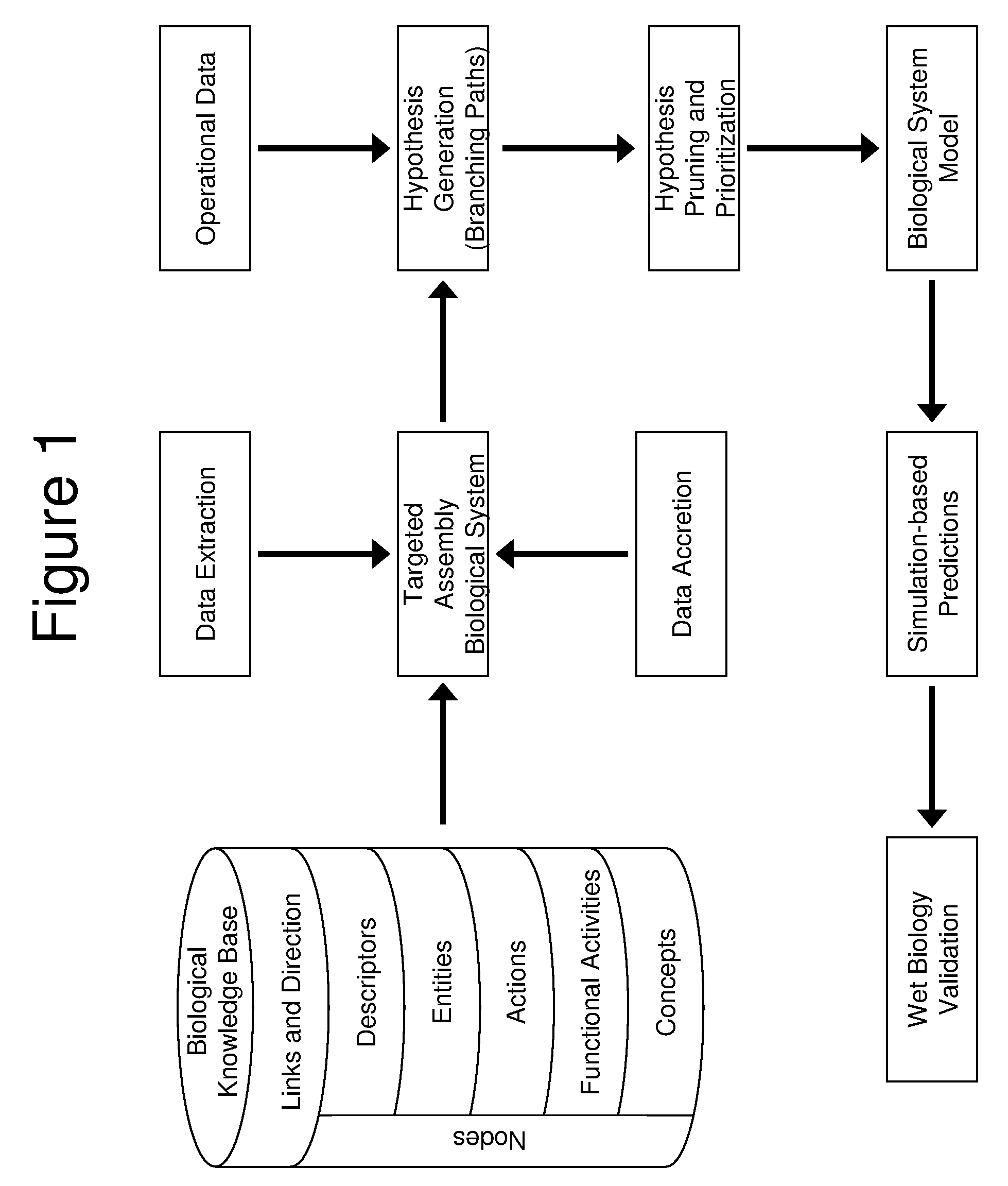
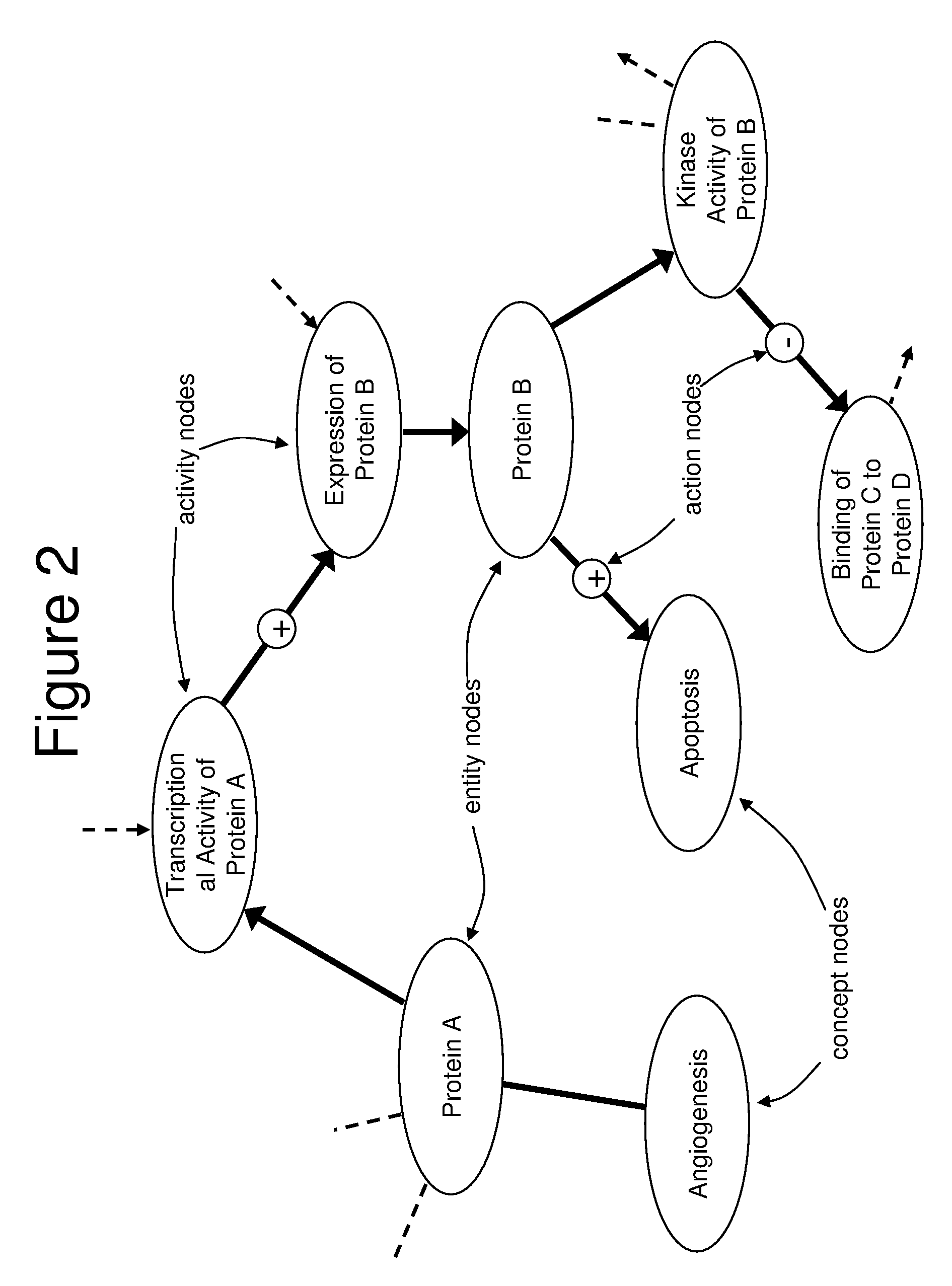
Computer-Aided Discovery of Biomarker Profiles in Complex Biological Systems
The invention relates to computational methods, systems and apparatus useful in the analysis of sets of biomolecules in an accessible body fluid or tissue sample from a patient, which biomolecules collectively or individually are candidates to serve as biomarkers, i.e., biomolecules which together or individually upon detection or change are indicative that the patient is in some biological state, such as a diseased state. The methods permit one to examine such potential biological markers to determine whether each one is indeed present as a consequence of the biological state, or as an artifact of the biomarker search protocol.
Owner:ALEXION PHARMA INC +1
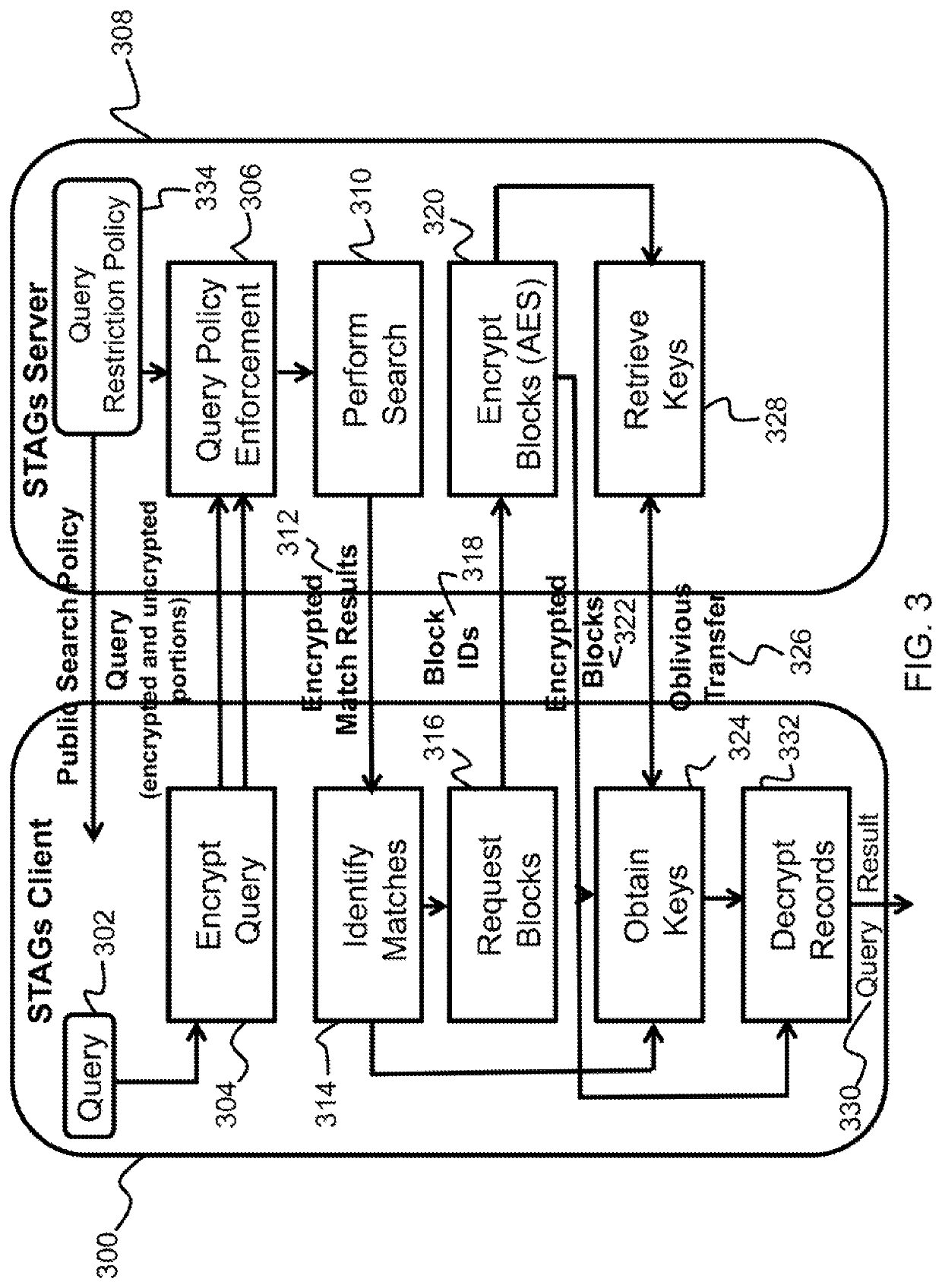
STAGS: secure, tunable, and accountable generic search in databases
ActiveUS10691754B1Digital data information retrievalDigital data protectionDatabase queryProtocol processing
Described is a system for secure database searching. The system comprises a client-server architecture which allows a client to securely search a database of records possessed by a server. A database query is generated by the client and transmitted to the server. The database query is processed by the server using a privacy-preserving search protocol. An encrypted match result is produced by the server without decrypting the database query. The encrypted match result is sent to the client, and the client decrypts the encrypted match result to obtain a set of block identifiers representing blocks of records in the database that match the database query. The client obtains a block of encrypted records containing match results using only the set of block identifiers. The match results are decrypted by the client using a key obtained from the server. The unencrypted match results to the database query are then output.
Owner:HRL LAB
Method and device for receiving and transmitting multiple protocol data of vehicle-mounting terminals on server
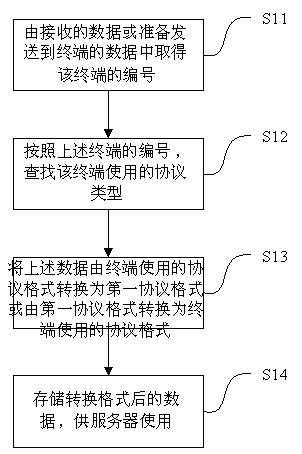
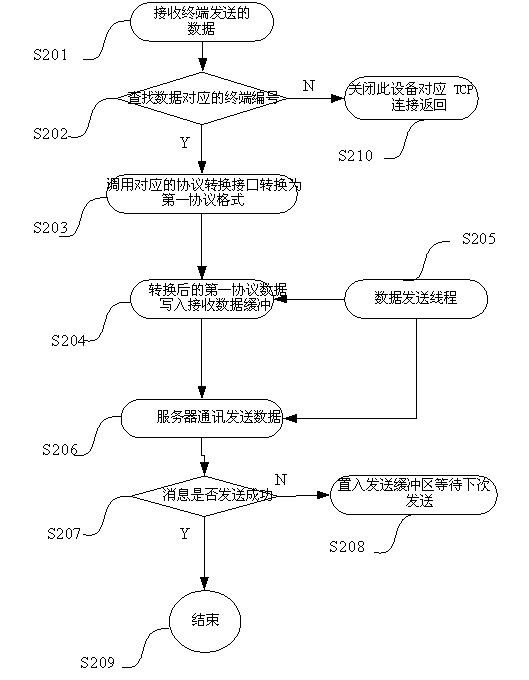
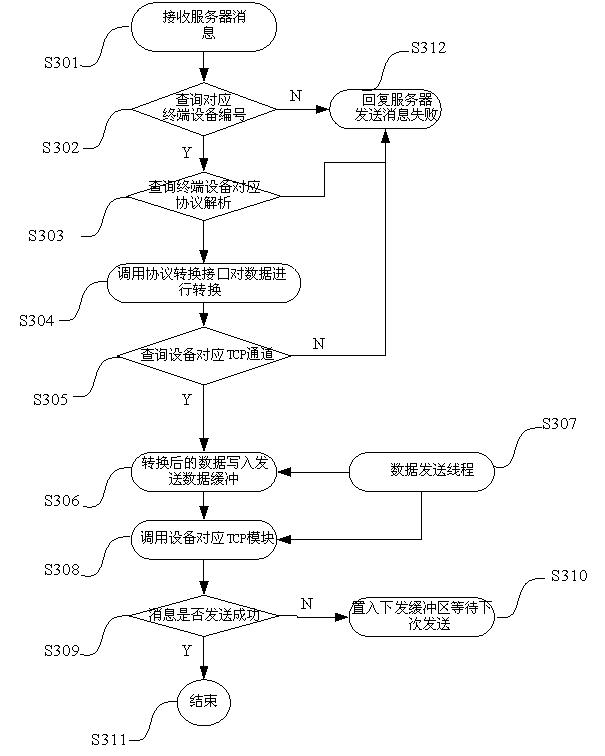
The invention relates to a method for receiving and transmitting multiple protocol data on a server. The method comprises the following steps of: receiving data transmitted by terminal equipment or detecting data which is ready to be transmitted to the terminal equipment and acquiring terminal serial number information; searching protocol information, which the terminal on the server registers in advance and use, according to the terminal serial number; according to the protocol information, converting the protocol format, which the terminal uses, of the received data into the first protocol format or converting the data transmitted to the terminal equipment from the first protocol format into the protocol format which the terminal uses; and caching the converted data for the server to use. The invention also relates to a device implementing the method. The method and the device for receiving and transmitting multiple protocol data of the vehicle-mounting terminals on the server has the following beneficial effects of low requirement on the terminals and low cost of the whole system.
Owner:深圳市长宇电器有限公司
Mobile scale-free self-organizing network model building method
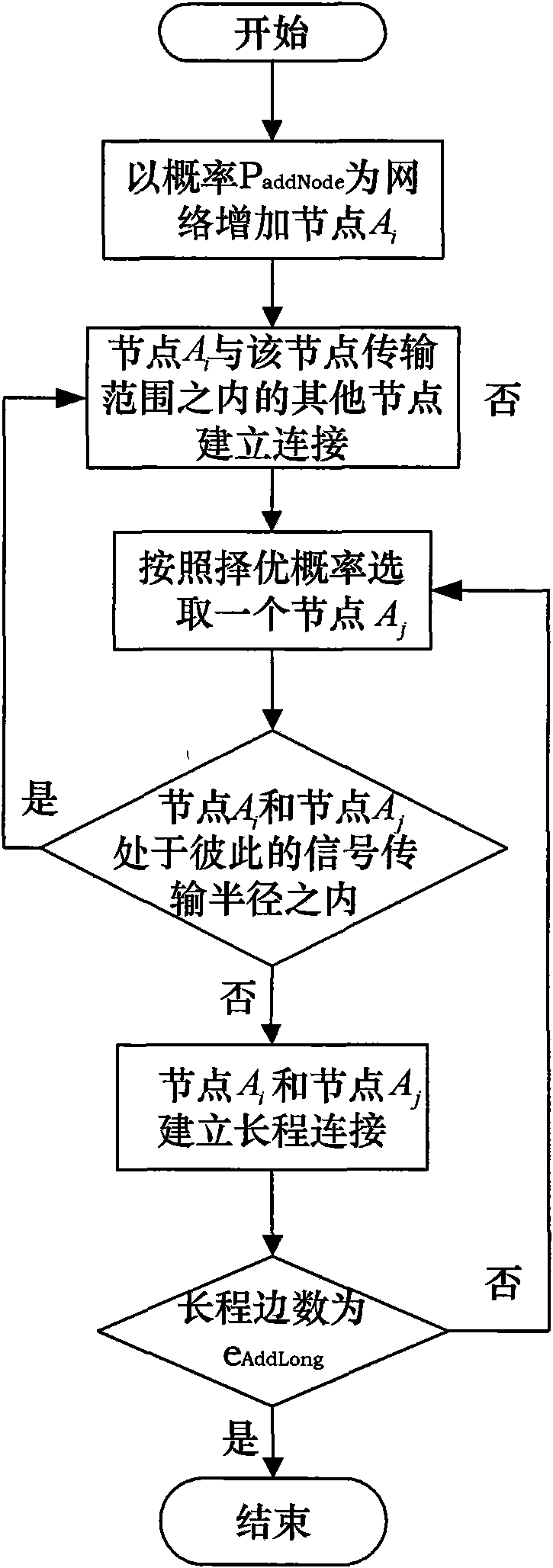
InactiveCN101572961AHas scale-free propertiesImprove connectivityEnergy efficient ICTNetwork topologiesNormal densityWireless sensor networking
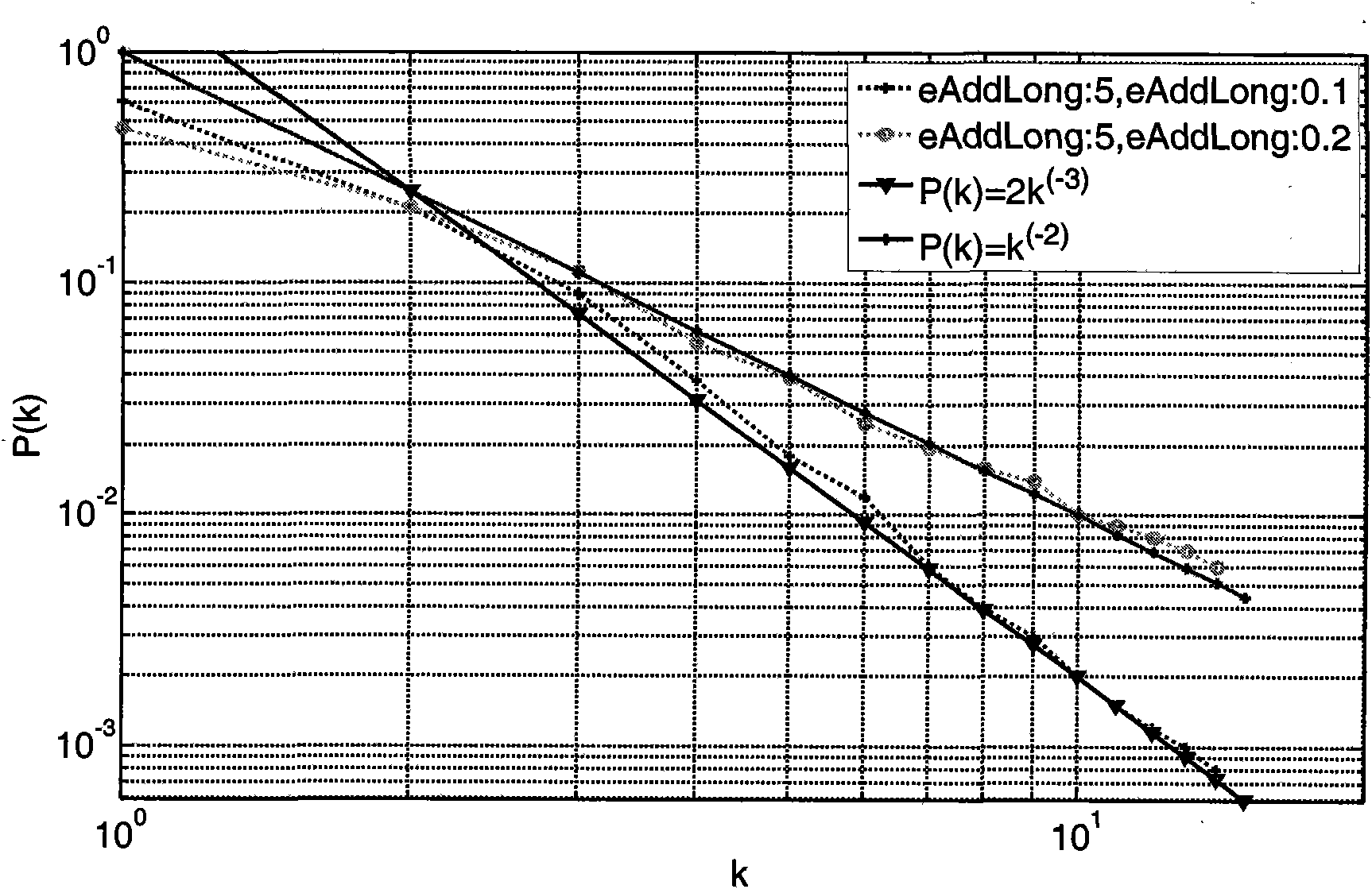
The invention discloses a mobile scale-free self-organizing network model building method. Firstly the whole simulation zone of the whole network is supposed to be [X, Y]; signal transmission radius of a node is r0; space distribution probability density function of the node is pdfUnifonn, and border effect of the node is neglected; the network is supposed to be not provided with a node or a border; the node number of the whole network is N; then the network is added with nodes under the condition that probability PAddNode is equal to 1; a connection of the node Ai in local world is built; finally the node Ai is added with eAddLong long range connections in probability PAddLong. The scale-free network topology provided by the invention is more close to the real world. The scale-free network has high robustness on random node failure, therefore the scale-free network can optimize network connectivity, prolong life period of the network, save energy, improve throughput rate and capacity of the network and make the network to be more robust and scalability and can improve network search protocol efficiency.
Owner:BEIHANG UNIV
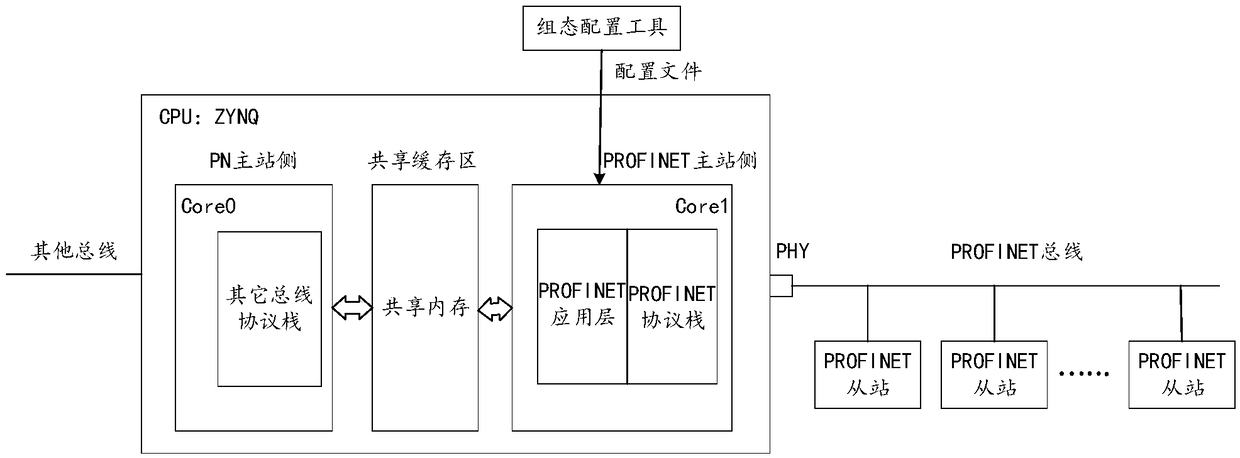
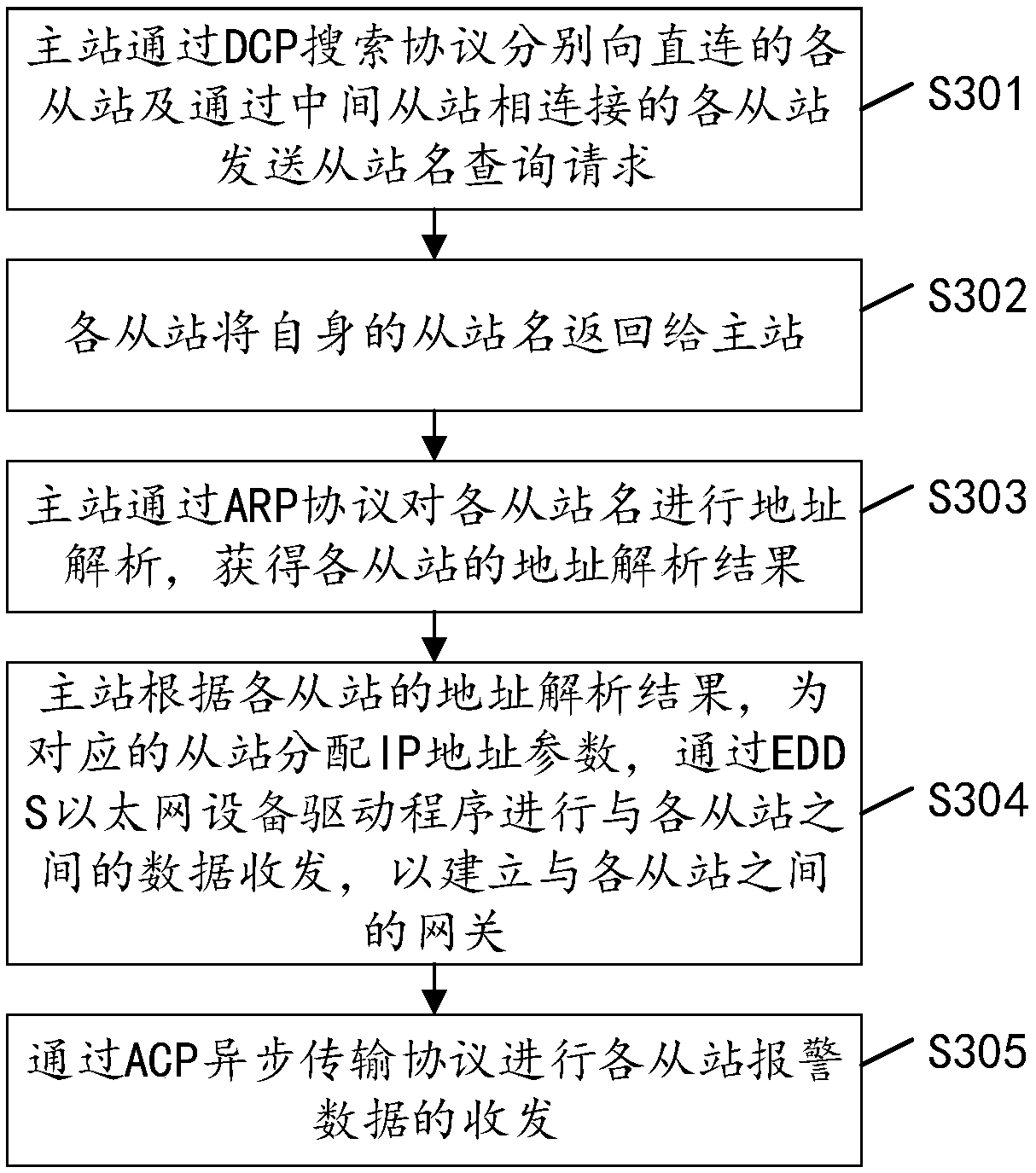
a method and a device for realizing a PROFINET industrial Ethernet gateway
ActiveCN109067644ASolve problemsSolve complexityProgramme controlComputer controlIp addressAddress resolution
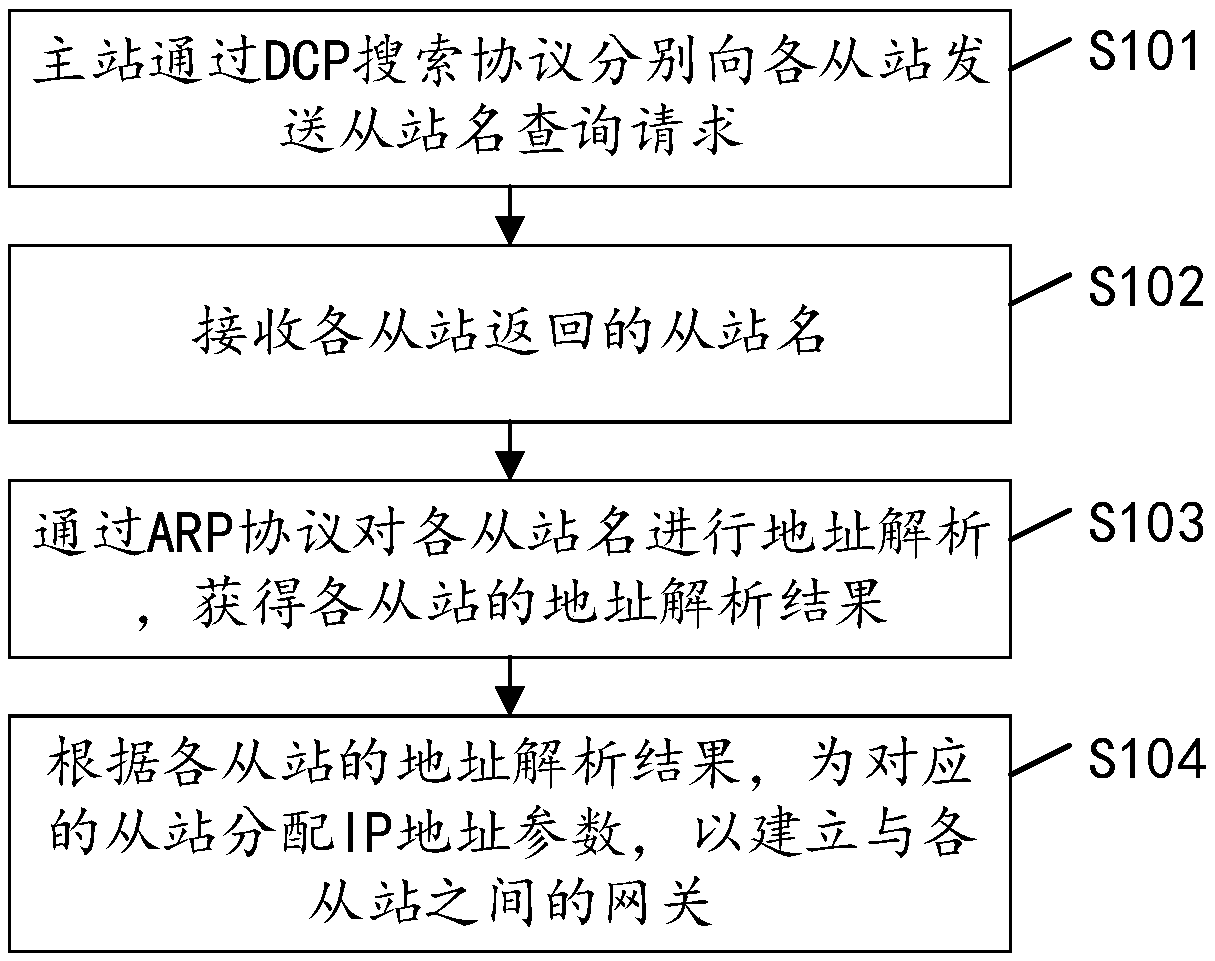
The invention discloses a method for realizing PROFINET industrial Ethernet gateway. The method comprises the following steps: a master station respectively sends a slave station name inquiry requestto each slave station through a DCP search protocol; the master station sends the slave station name inquiry request to each slave station. Receiving a master station name returned by each slave station. The address resolution of each slave station is performed by ARP protocol, and the address resolution results of each slave station are obtained. According to the address resolution result of eachslave station, IP address parameters are assigned to the corresponding slave station to establish a gateway with each slave station. The technical proposal provided by the embodiment of the inventiondoes not require an external PROFINET protocol special chip, solves the problem of complex maintenance and replacement procedures of the PROFINET protocol special chip, and reduces the cost. The invention also discloses an implementation device, a device and a storage medium of a PROFINET industrial Ethernet gateway, which have corresponding technical effects.
Owner:HANGZHOU HOLLYSYS AUTOMATION
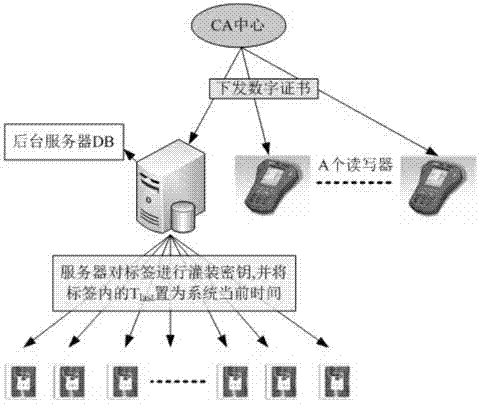
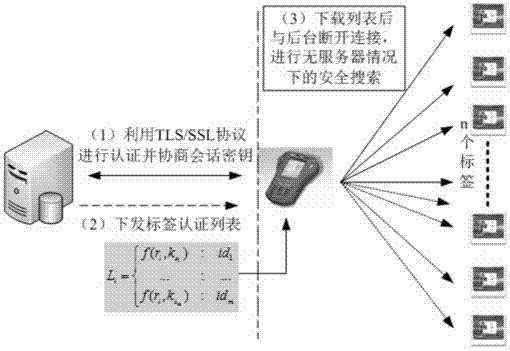
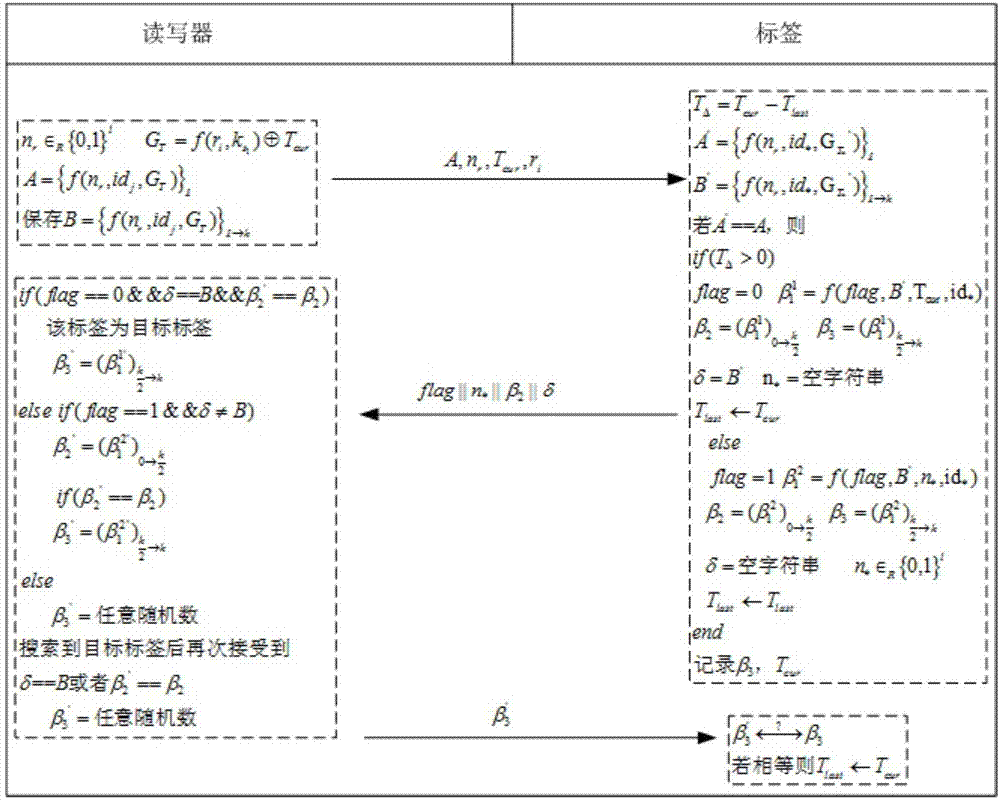
Lightweight no-service type RFID (radio frequency identification) safe search protocol
ActiveCN103581206ALow hardware resource requirementsProtection securityUser identity/authority verificationCo-operative working arrangementsHash functionTimestamp
The invention relates to a lightweight no-service type RFID (radio frequency identification) safe search protocol. The protocol uses multiple tag collision for protecting the privacy of a target tag; a loose timestamp and a one-way Hash function are used, so that the safety problem possibly occurring to a data link between an RFID reader and the tag is effectively solved; and under the condition that no background server exists, the HASH function which can be realized through a passive tag is adopted, so that safe search and bidirectional authentication to the tag are guaranteed, and excellent characteristics of fast search and safety certificate are realized. Common active and passive attacks in a wireless link can be effectively resisted. The lightweight no-service type RFID safe search protocol is ingenious in structure and wide in application environment, and has a high safety level and privacy level.
Owner:BEIJING UNIV OF POSTS & TELECOMM
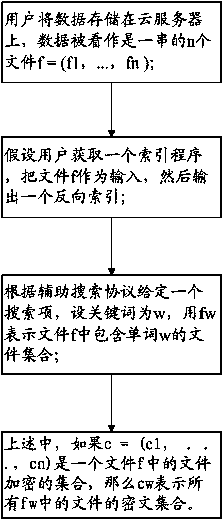
Dynamically retrievable cloud computing data encryption method
The invention discloses a dynamically retrievable cloud computing data encryption method. The method comprises the following steps: storing data on a cloud server by a user, wherein the data are considered as a string of n files, and f is equal to (f1, ellipsis, fn); supposing that the user acquires an index program, taking the file f as input and outputting a reverse index; giving a search item according to an auxiliary search protocol, setting a keyword as w, and representing a file set containing the word w in the file f by using fw, wherein if c which is equal to (c1, ellipsis, cn) is a set of encrypted files in the file f, cw represents a cipher text set of all the files in fw. By such a mode, the retrieval of encrypted data is realized, so that the privacy, the integrality and the verifiability can be guaranteed, the user can efficiently retrieve data through a search interface, and the data can also be safely added and deleted.
Owner:SUZHOU UNIV
System and method for automatically checking an electronic document for at least one attachment
InactiveUS20060123090A1Multiple digital computer combinationsAutomatic exchangesElectronic documentSearch protocol
Embodiments of the invention provide a system and method for automatically checking an electronic document for at least one attachment. In one embodiment, a search protocol is provided for automatically searching an electronic document for at least one attachment term. Furthermore, an attachment protocol is provided. The attachment protocol is configured to automatically check for at least one attachment coupled with the electronic document. In addition, a comparator protocol is also provided. The comparator protocol configured to automatically compare the results of the search protocol and the attachment protocol wherein if the search protocol finds the at least one attachment term and the attachment protocol does not find the at least one attachment, the comparator protocol providing a warning prior to allowing the electronic document to be sent.
Owner:YOUNGS JOEL DARRELL
Driver management apparatus and method therefor
A driver management apparatus includes a receiving unit configured to receive a network entry message sent by unicast according to a search protocol for one-to-one connection from one of a plurality of devices connected to a network, a determination unit configured to determine a capacity to install a driver according to the search protocol for one-to-one connection of a device connected to the network, and a processing unit configured to perform processing for installing, on a client terminal apparatus connected to the network, a driver for operating a device that has sent the network entry message. The processing unit is configured to perform different processing operations for installing the driver for operating the device with respect to respective devices having different capacities according to the capacity determined by the determination unit.
Owner:CANON KK
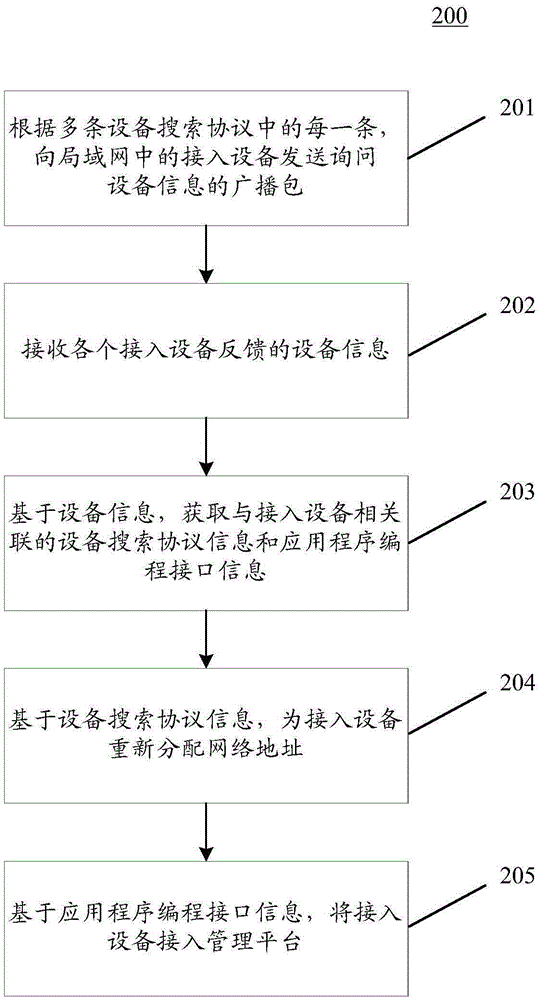
Equipment networking method and equipment networking device
ActiveCN106686694ARealize automatic adaptation to networkingImprove deployment efficiencyAssess restrictionBroadcast packetApplication programming interface
The invention discloses an equipment networking method and an equipment networking device. The equipment networking method comprises the steps of transmitting a broadcast packet for inquiring equipment information to access equipment in a local area network according to each equipment searching protocol in a plurality of equipment searching protocols; receiving equipment information which is fed back from each access equipment; based on the equipment information, acquiring equipment searching protocol information and application programming interface information which are related with the access equipment; re-allocating a network address for the access equipment based on the equipment searching protocol information; and accessing a management platform by the access equipment based on the application programming interface information. The equipment networking method and the equipment networking device realize automatic adaption networking of the equipment and furthermore improve disposition and maintenance efficiency of an equipment management system.
Owner:DATANG SOFTWARE TECH
Method for discovering and connecting digital cameras at different network segments in local area network
InactiveCN107919999AClosed circuit television systemsData switching networksData connectionVideocassette recorder
The invention provides a method for discovering and connecting digital cameras at different network segments in a local area network. The method includes the following processes: 1, monitoring and receiving an ARP message from a local area network; 2, extracting a network card IP sent by a terminal and a network segment where the network card IP is located from the ARP message, and recording the terminal IP and the network segment thereof; 3, according to the network segment where the terminal IP is located, when a user searches for a digital camera, adding an unoccupied IP address of the recorded network segment to a local network card, and reserving an original IP of the network card; 4, sending a search protocol message to the terminal by using the same network segment IP, and obtaining feedback information; and 5, the user performs data connection on the digital camera by adding the network IP where the digital camera is located. According to the method, through the mode of addingan IP on a network card of a video recorder, the camera in the local area network can be discovered through a broadcast search protocol, the camera can also be connected, and the phenomenon that theuser performs cumbersome IP allocation and configuration can be avoided.
Owner:天津英田视讯科技有限公司
Computer-aided discovery of biomarker profiles in complex biological systems
The invention relates to computational methods, systems and apparatus useful in the analysis of sets of biomolecules in an accessible body fluid or tissue sample from a patient, which biomolecules collectively or individually are candidates to serve as biomarkers, i.e., biomolecules which together or individually upon detection or change are indicative that the patient is in some biological state, such as a diseased state. The methods permit one to examine such potential biological markers to determine whether each one is indeed present as a consequence of the biological state, or as an artifact of the biomarker search protocol.
Owner:ALEXION PHARMA INC +1
Method and apparatus for media handover in the network
InactiveCN101114998ASpecial service provision for substationBroadcast with distributionData OriginWired communication
Owner:ARCADYAN
Method for creating and using registry of clinical trial participants
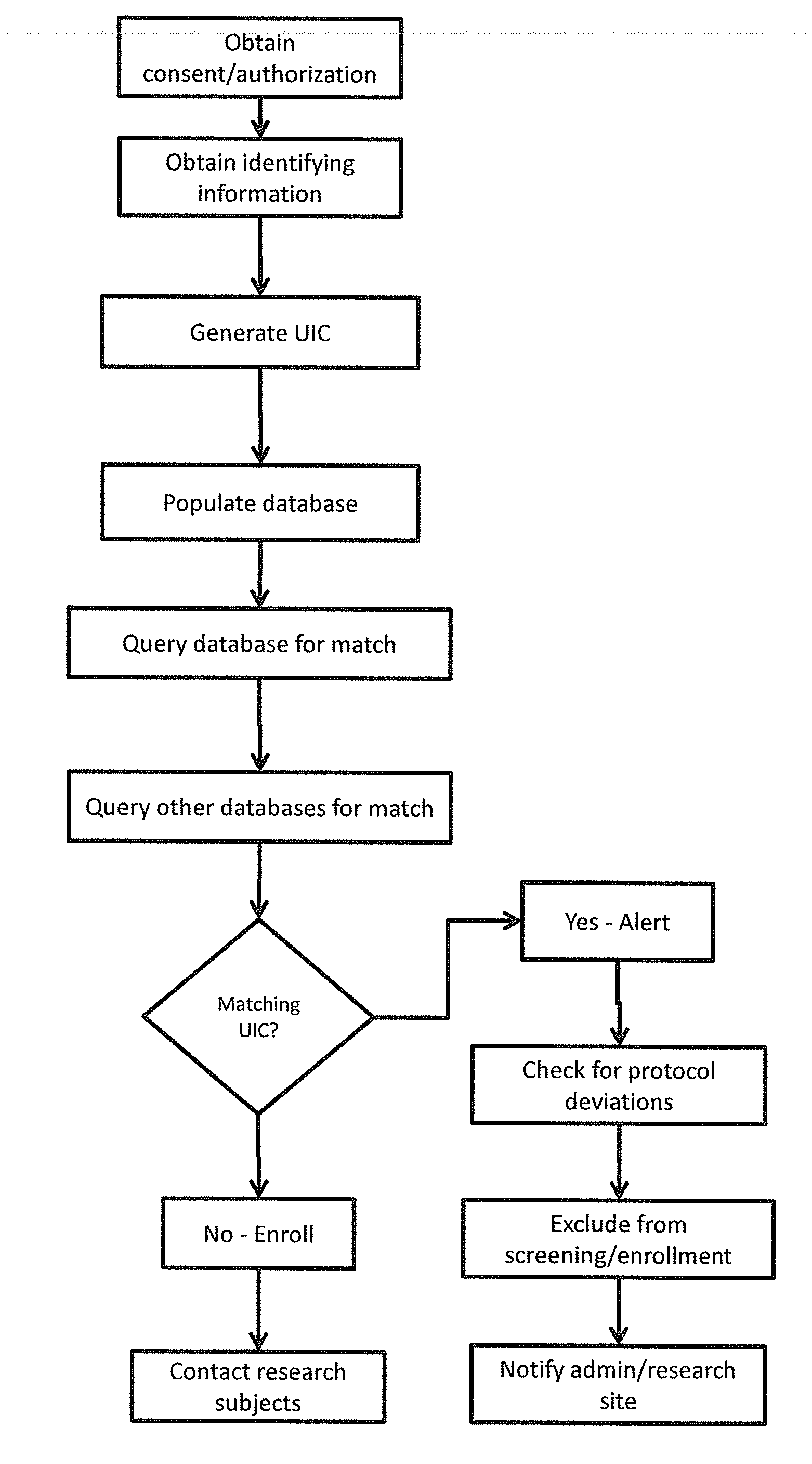
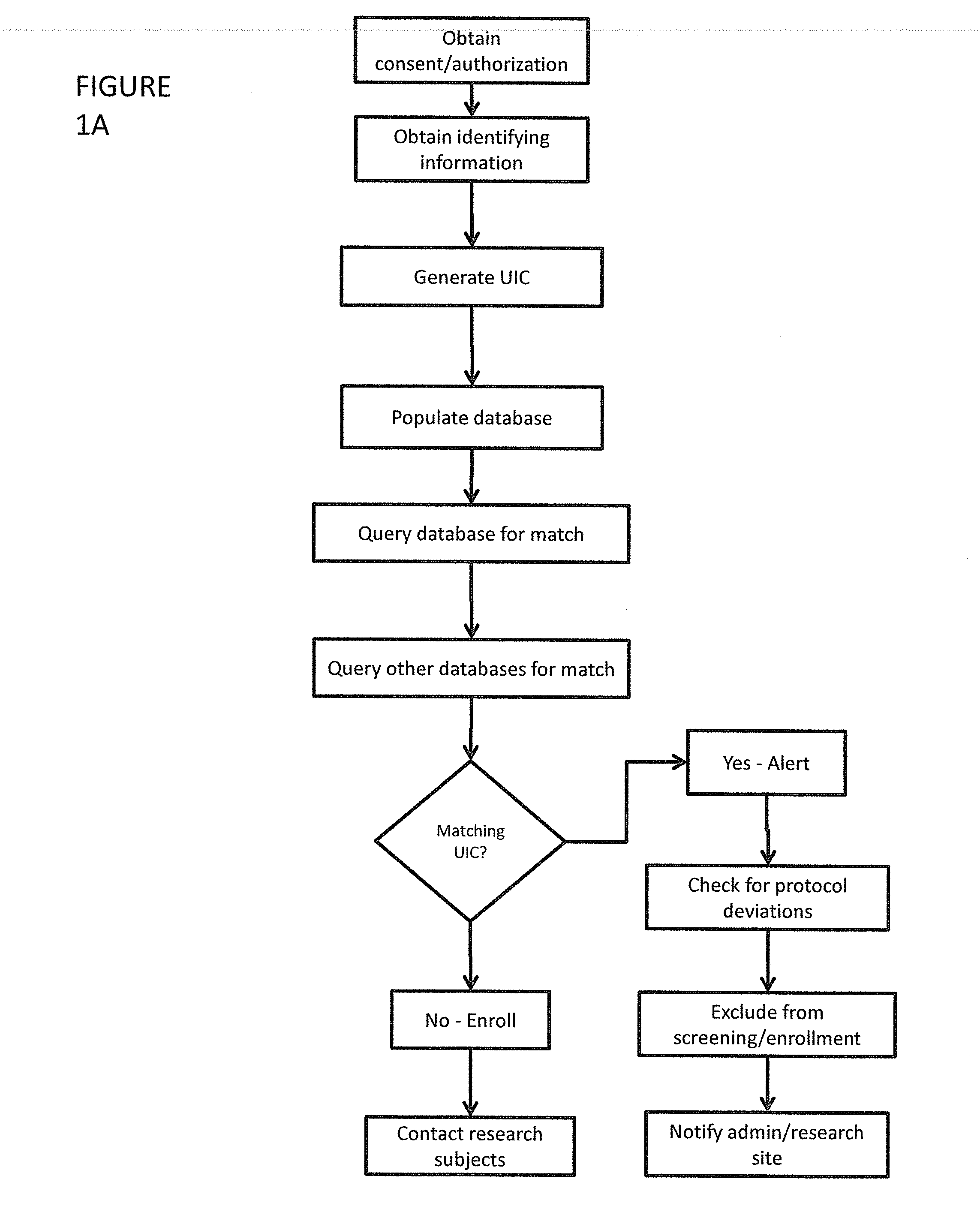
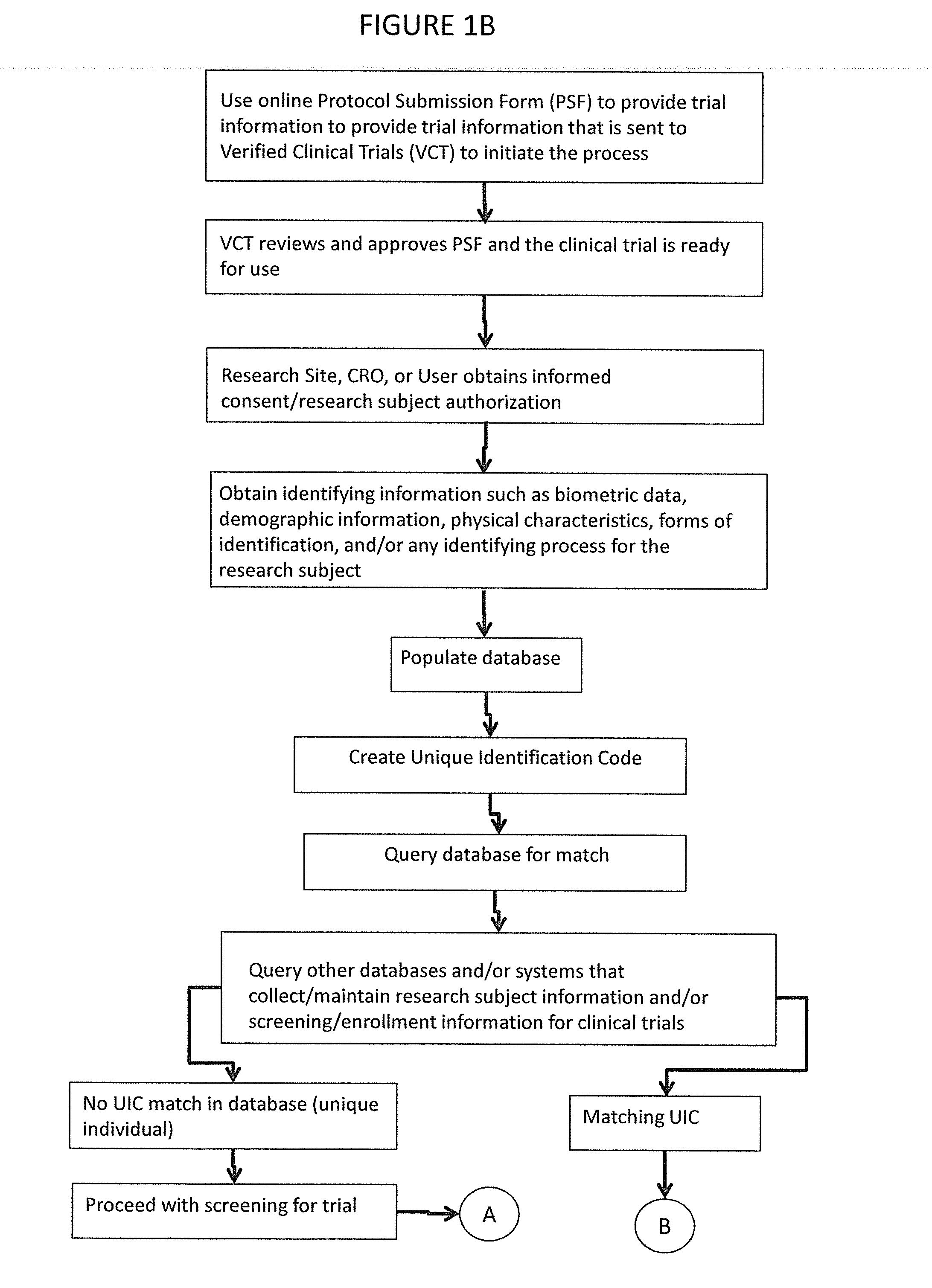
ActiveUS20160259917A1Digital data information retrievalComputer-assisted medical data acquisitionUnique identifierSearch protocol
A method of screening participants for a clinical trial by obtaining identifying information chosen from a biometric sample, personal information, physical attributes, and combinations thereof from a prospective participant, generating a unique identifier code, populating a database with the unique identifier code and participant information and storing the database on computer readable media, screening the participant for a clinical trial based on the unique identifier code and participant information and searching for a match with another participant, searching for protocol violations, and determining eligibility of the participant for the clinical trial and preventing the protocol violations. A system for screening participants for a clinical trial.
Owner:VERIFIED CLINICAL TRIALS
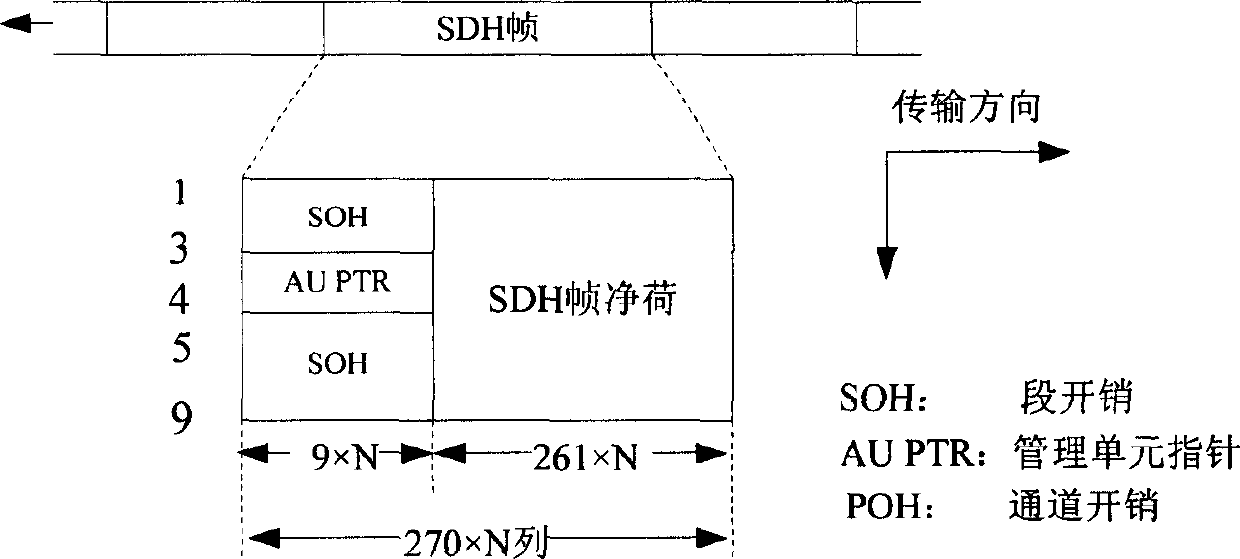
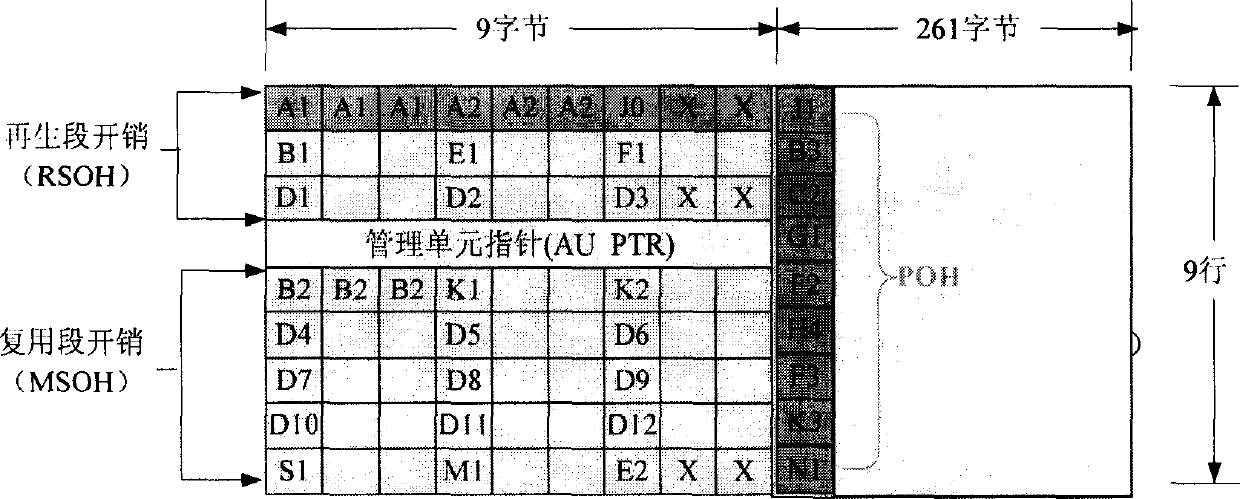
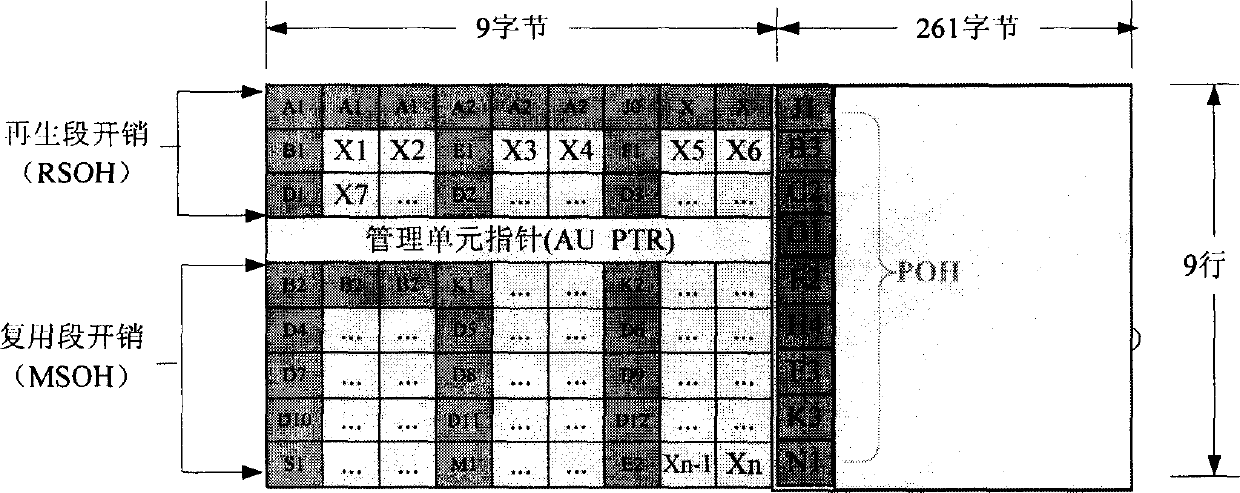
Automatic searching method for SDH frame idle overhead field
This invention discloses an automatic searching method for SDH frame idle overhead field, which applies an overhead plug technology and designs a polling idle overhead search protocol of a ciphered device to determine an available idle overhead field in a few seconds and automatically searches it again if there is any change of the network intermediate device to the idle overhead fields.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
Proxying search requests for files to a search engine
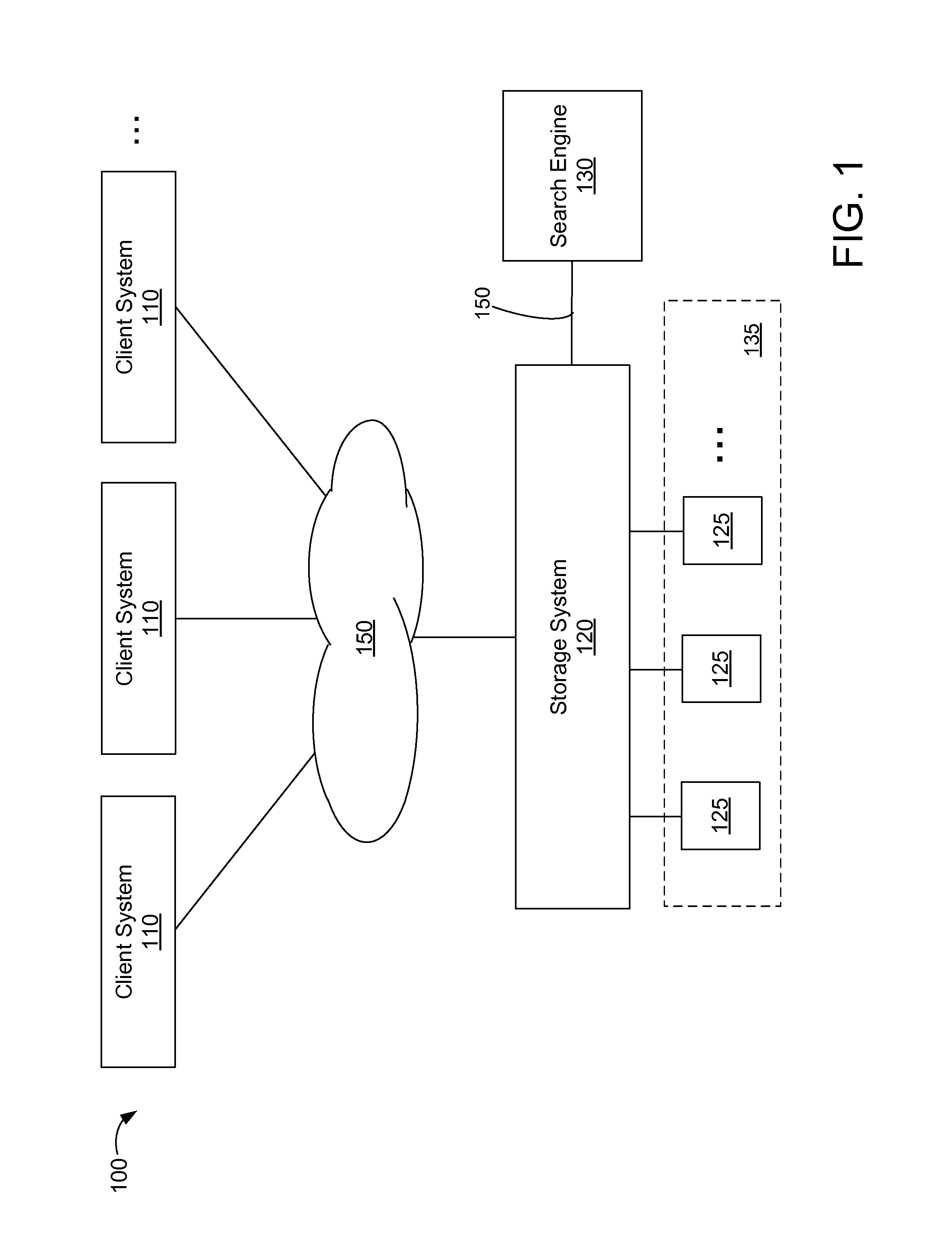
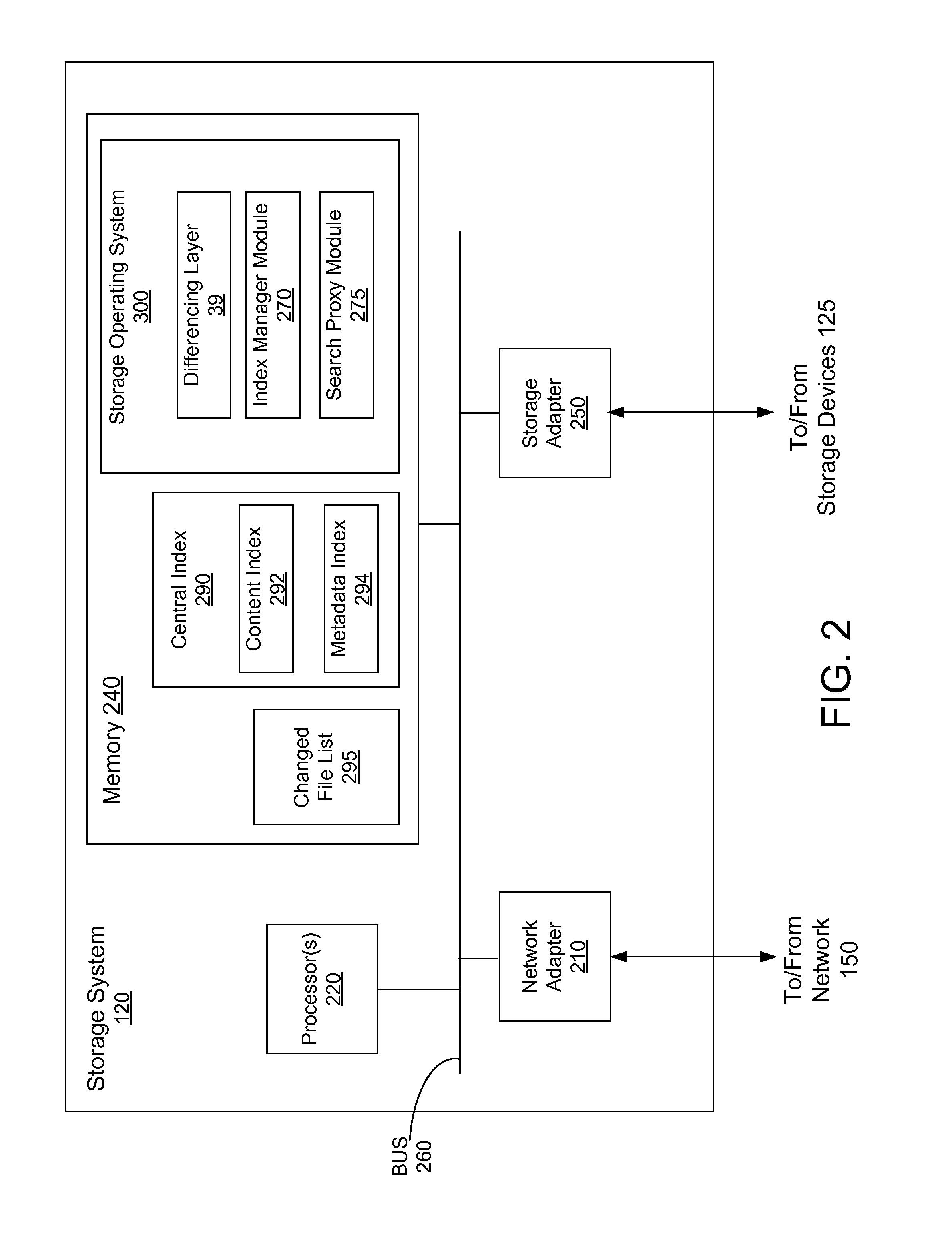
InactiveUS8782028B1Effective maintenanceLess resourcesWeb data indexingDigital data processing detailsFile systemSearch protocol
A method and apparatus for proxying search requests for a storage system and maintaining a central index for performing the search requests is described herein. An index manager on the storage system may initially produce the central index by examining each file in a file system and update the central index thereafter by examining only those files that have changed since the central index was initially produced or last updated. The index manager may receive a changed file list from a differencing layer configured for comparing snapshots of the file system at different time points to produce changed file lists. A search proxy module may receive search requests in a search protocol and proxy the search requests to a search engine by converting the search requests to another search protocol compatible with the search engine. The search engine may then use the central index for performing the search request.
Owner:NETWORK APPLIANCE INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com