Lightweight no-service type RFID (radio frequency identification) safe search protocol
A lightweight, serverless technology, applied in the field of RFID communication security, can solve the problems of inadaptability to passive tags, high energy consumption, etc., and achieve the effect of protecting channel security and tag privacy, compact structure, and low hardware resource requirements
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
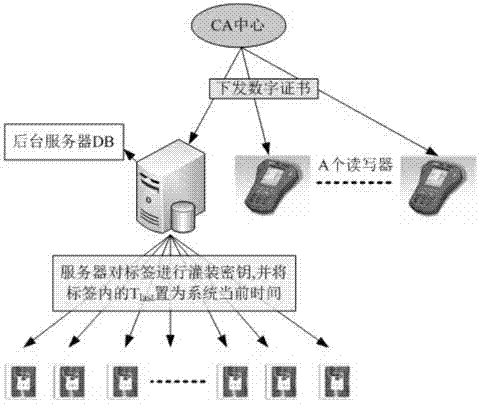
[0090] (1) System initialization
[0091] like figure 1 As shown, the CA certification center issues digital certificates to the background server and A readers, and the background server fills the label with the key and sets the label timestamp T in the application environment. last It is the current time of the background server, and correspondingly records the corresponding relationship between the unique identification code ID of the tag and the key of the tag in the background database, and then attaches the tag to the identification object.
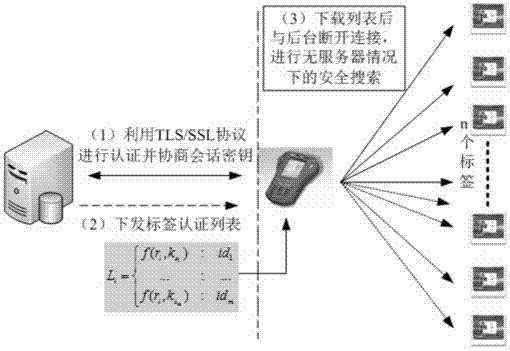
[0092] (2) System operation process
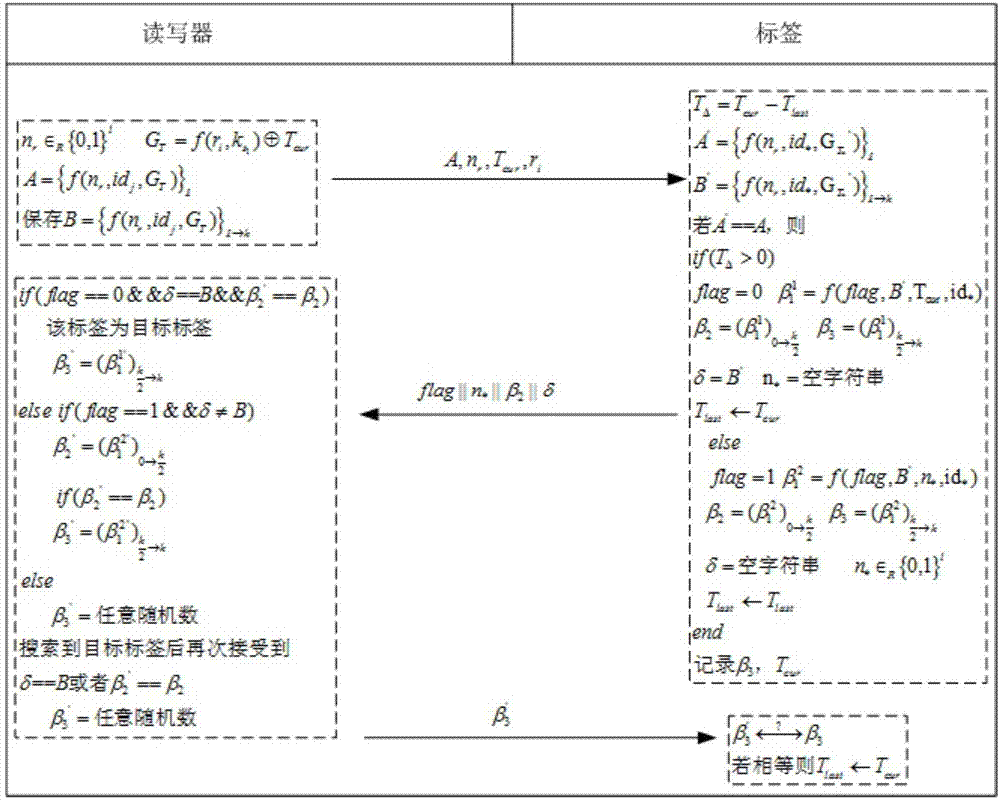
[0093] like figure 2 shown. First, the background server determines a certain reader R i for the search task reader; then, with the R i Use the TLS / SSL protocol for two-way authentication, so that both parties can confirm the legitimacy of the identity of the other party; after that, the background server sends its label to search the access list Here the key information k of the label ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com