Enciphering method for combining accidental enciphering and exhaust algorithm decipher
A random encryption and exhaustive method technology, applied in user identity/authority verification, digital transmission systems, electrical components, etc., can solve problems such as respecting people from afar, legitimate users retrieving files, and cracking encryption methods
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
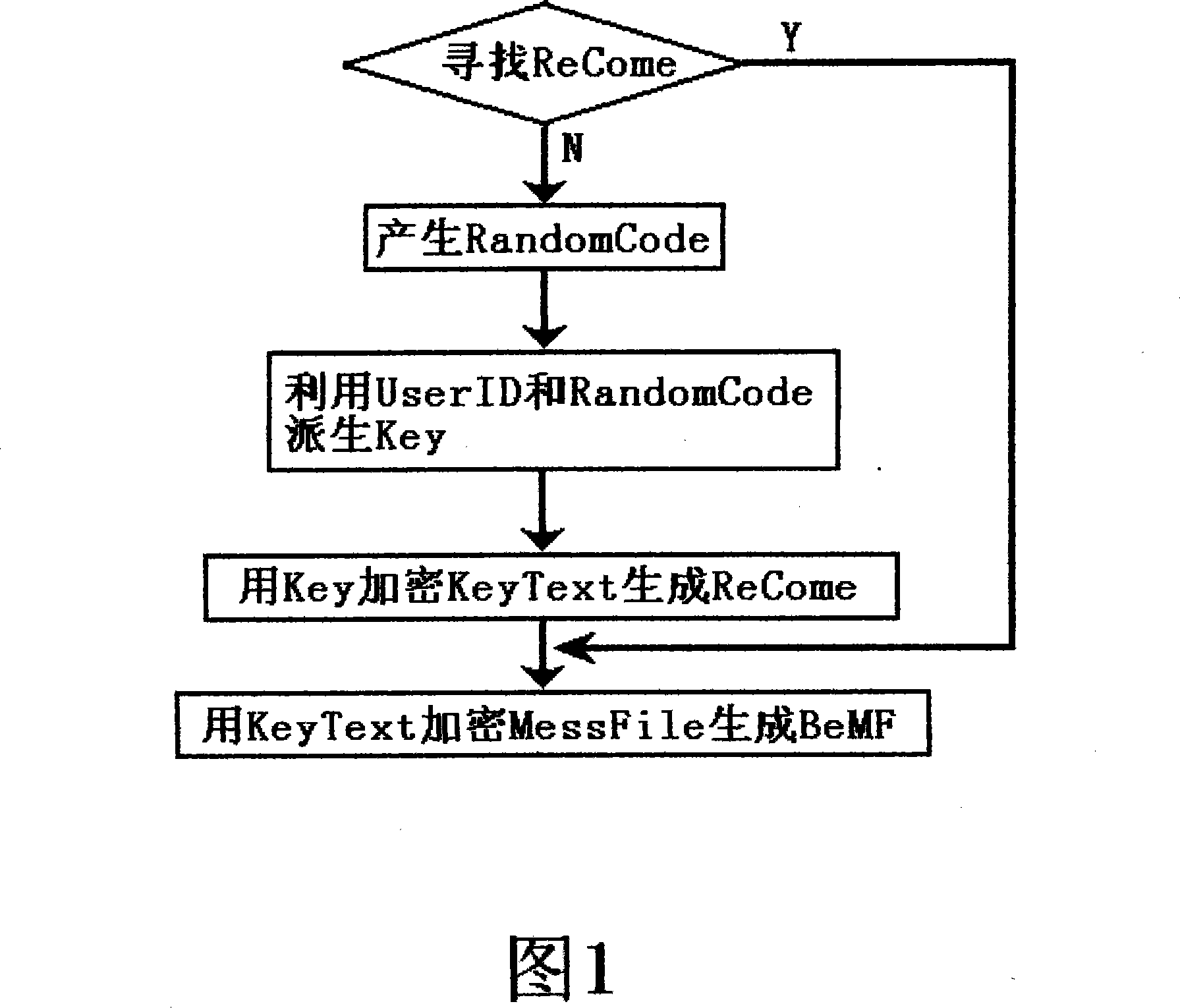
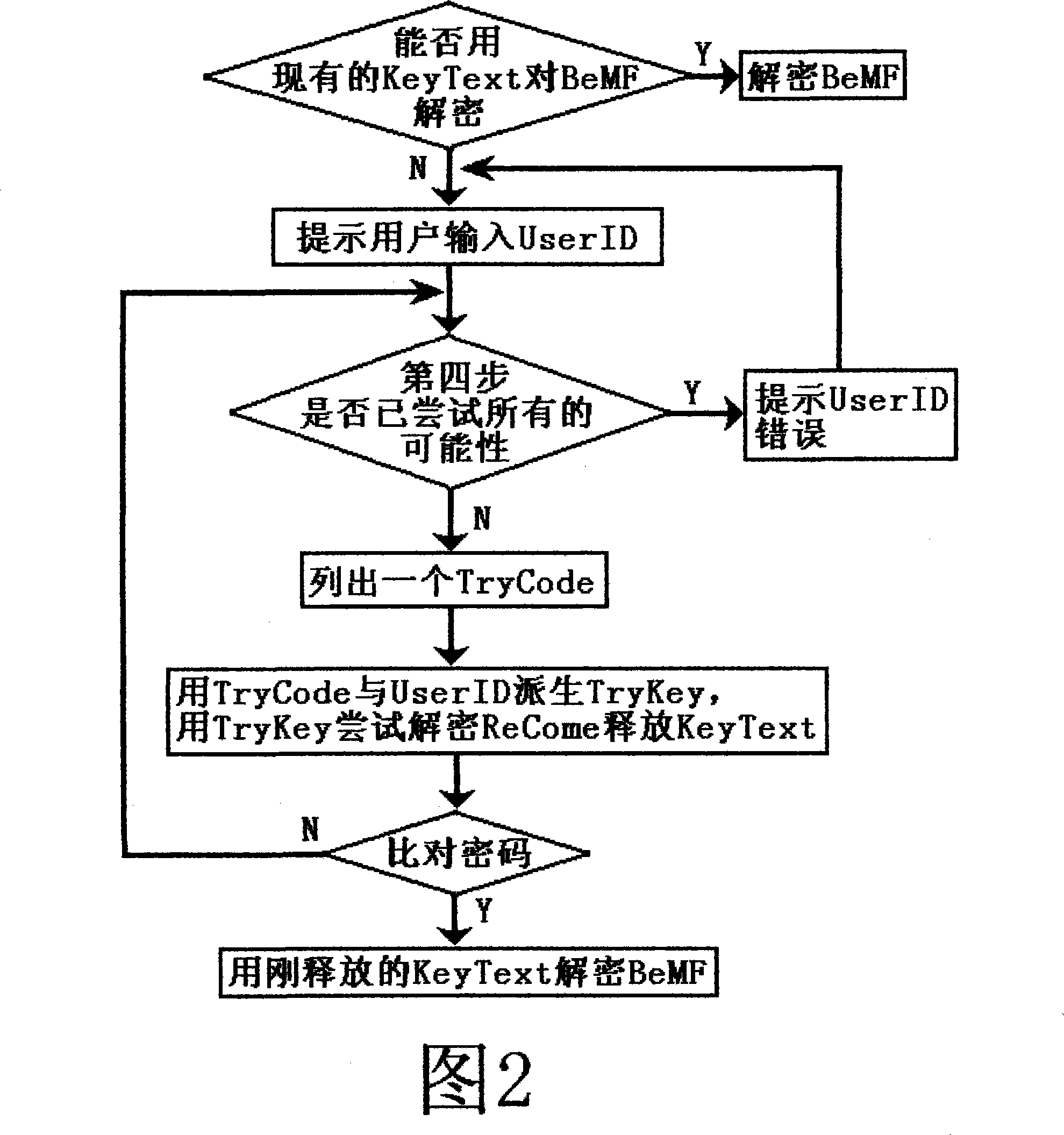
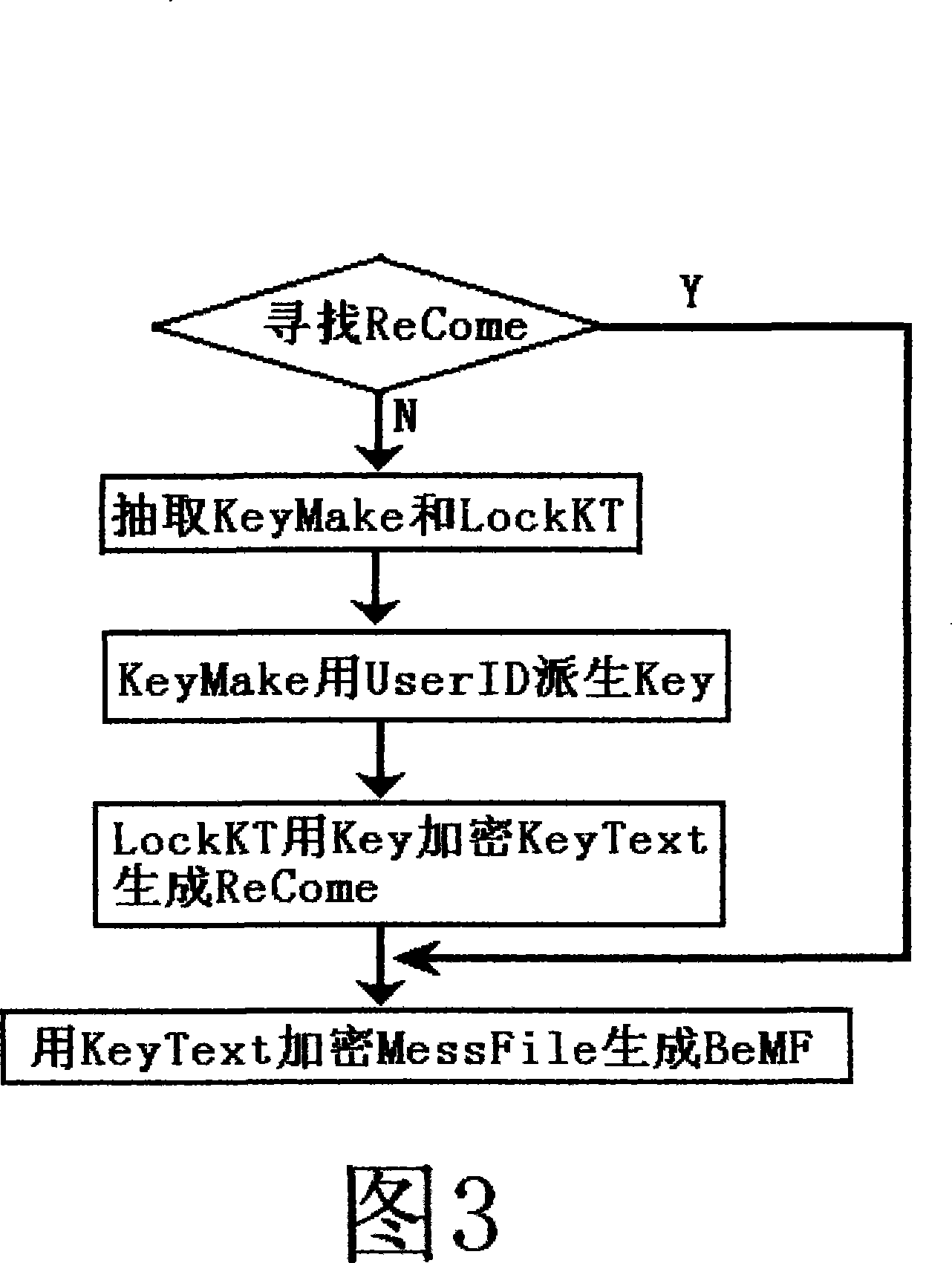
[0018] For ease of description, the file security system (comprising encryption and decryption program) that has adopted encryption method in the present invention will be abbreviated as FKSS below; The internal passwords, certificates and other important information that adopt the present invention to protect or restore will be referred to as KeyText; The backup file that generates after encrypting with encryption method among the present invention is called ReCome (after generating ReCome, still retains KeyText in FKSS); The file or information that waits for FKSS to encrypt except KeyText is called MessFile; MessFile is encrypted by FKSS The file or information generated after encryption is called BeMF. The backup file ReCome may contain a part of information that is not encrypted by the encryption method of the present invention, and this part of information is specially used for identification when FKSS decrypts, so as to quickly determine whether the existing KeyText in F...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com