File encryption and decryption method
An encryption method and file encryption technology, which is applied in the field of general file encryption and decryption, can solve problems such as complex encryption algorithms, inability to guarantee file security, and slow computing speed of mobile terminals.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0038] At first, explain the basis of the present invention:
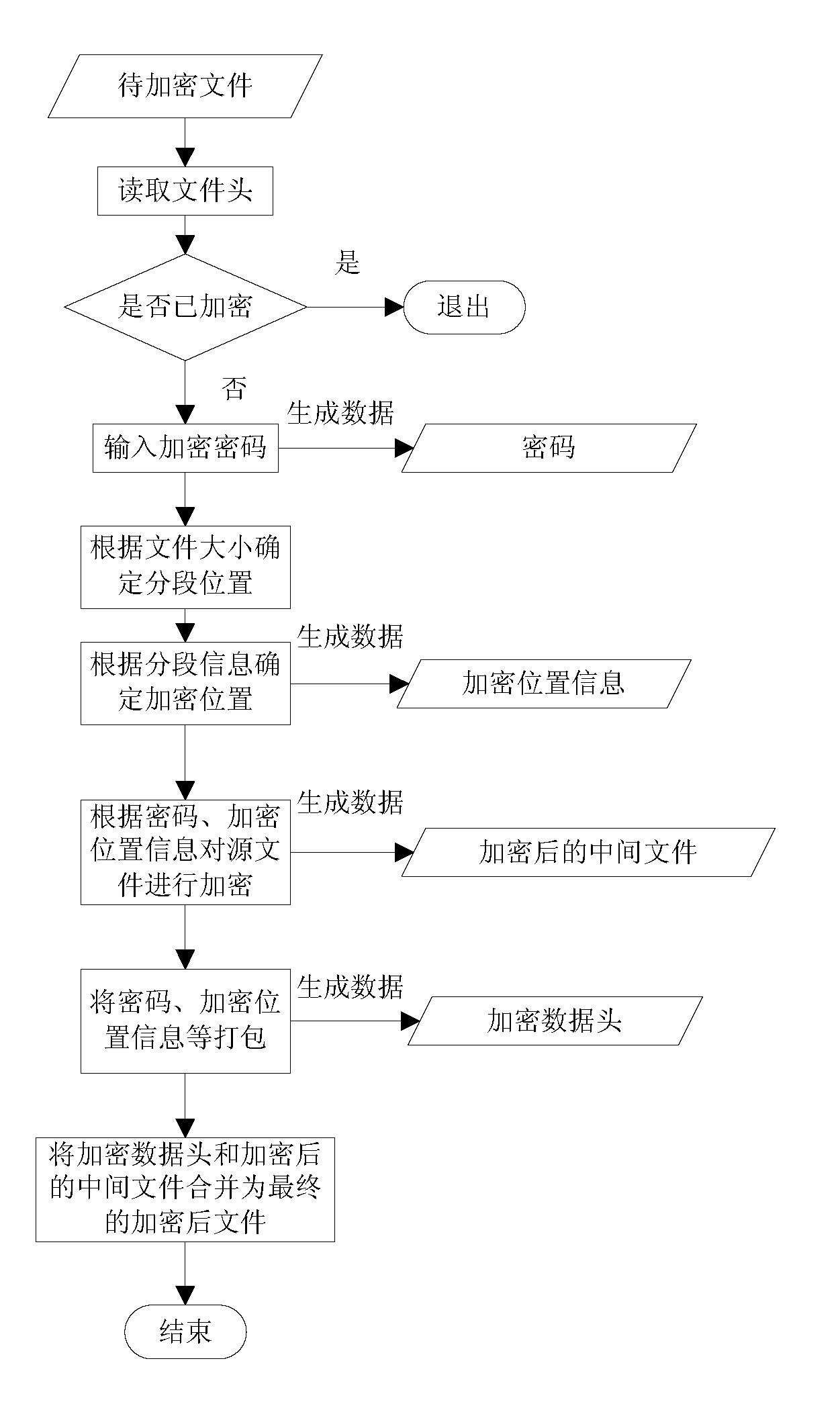
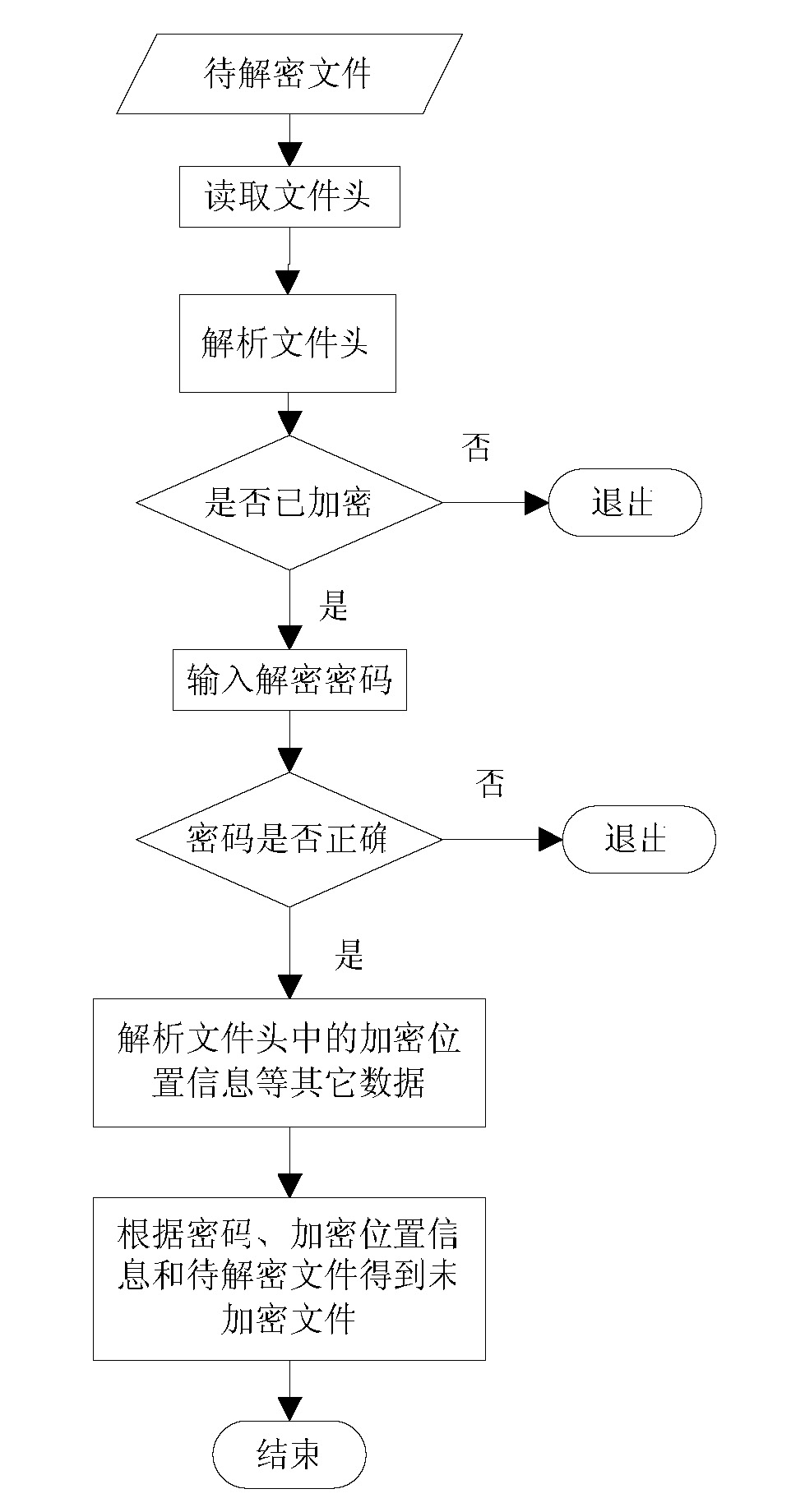
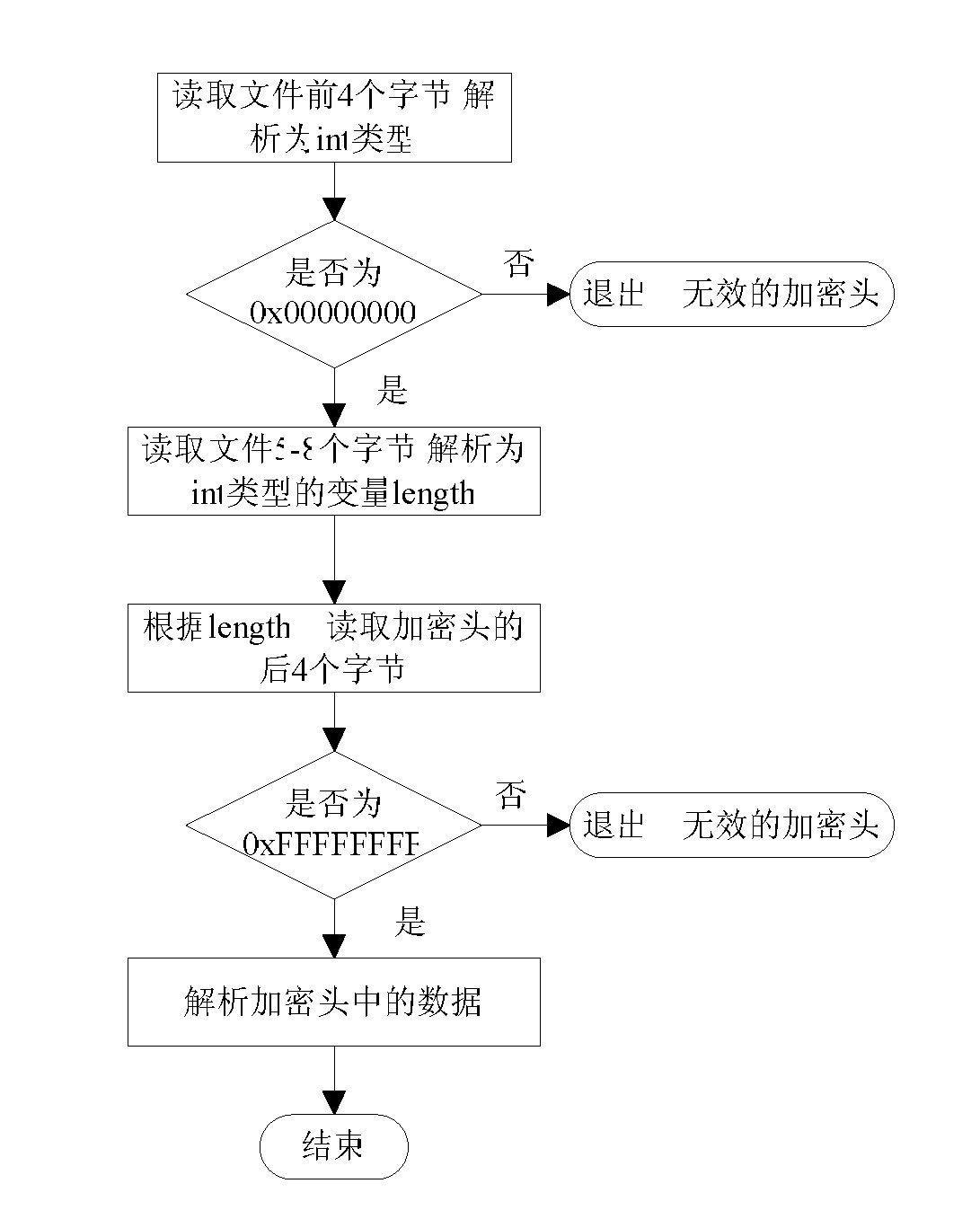
[0039] (1) The design of the whole algorithm: according to the size of the file, the file is divided into several sections, and then a certain amount of information is selected from the divided sections for encryption operation, and the required relevant information is stored in a data structure designed by oneself; The method is simple and efficient, and has good security, which is very suitable for systems and equipment that require high efficiency, making the user experience better;
[0040] (2) Design of encryption algorithm: First, use the pseudo-random number generation algorithm designed by yourself to generate a pseudo-random array for auxiliary key generation, and then use the algorithm designed by yourself to generate a non-repetitive pseudo-random array and user password. After the random sequence, the generated key and the content of the message are encrypted.
[0041] Second, the realization of specif...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com