Program analysis and variation input-based cross-site script attack detection method
A cross-site scripting attack and program analysis technology, applied in the fields of instruments, electrical digital data processing, platform integrity maintenance, etc., can solve the problems of false positives, high cost and false negatives.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
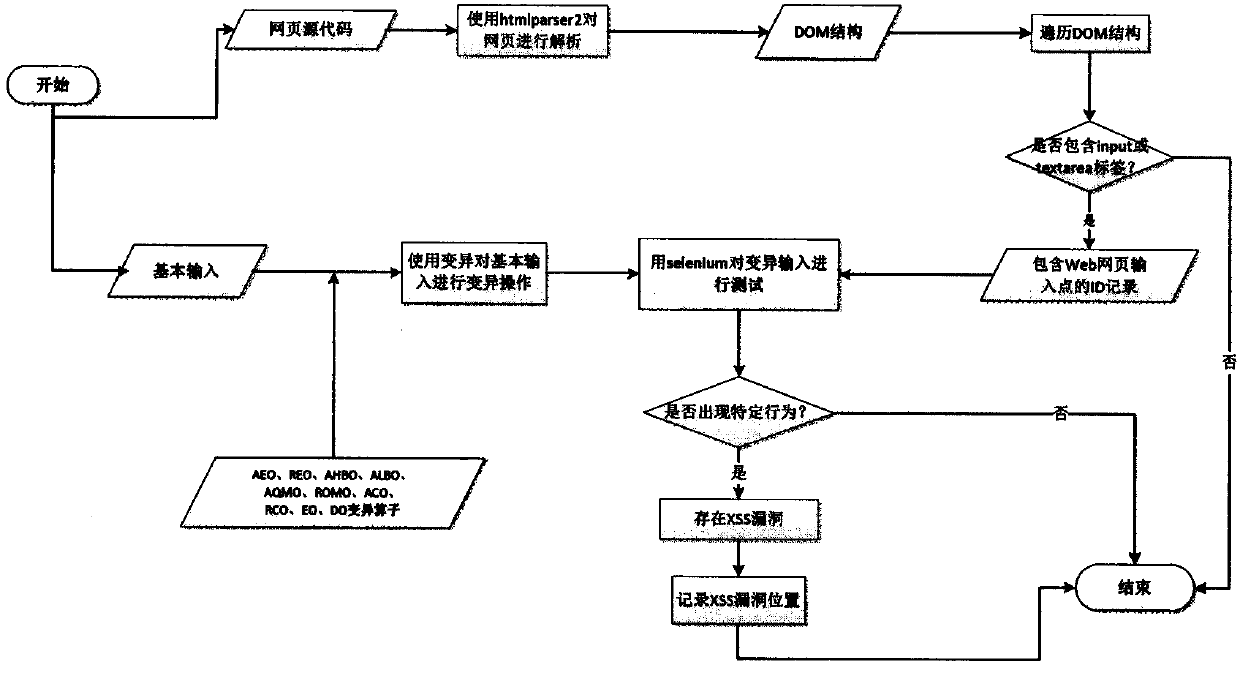
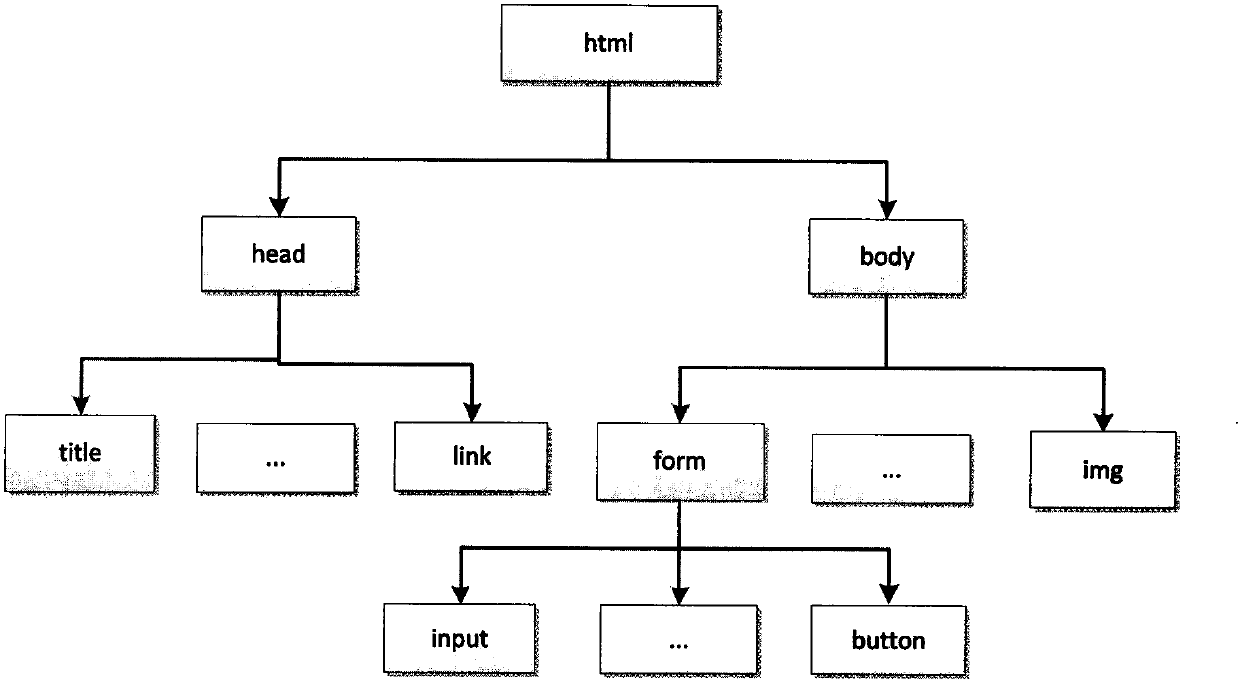
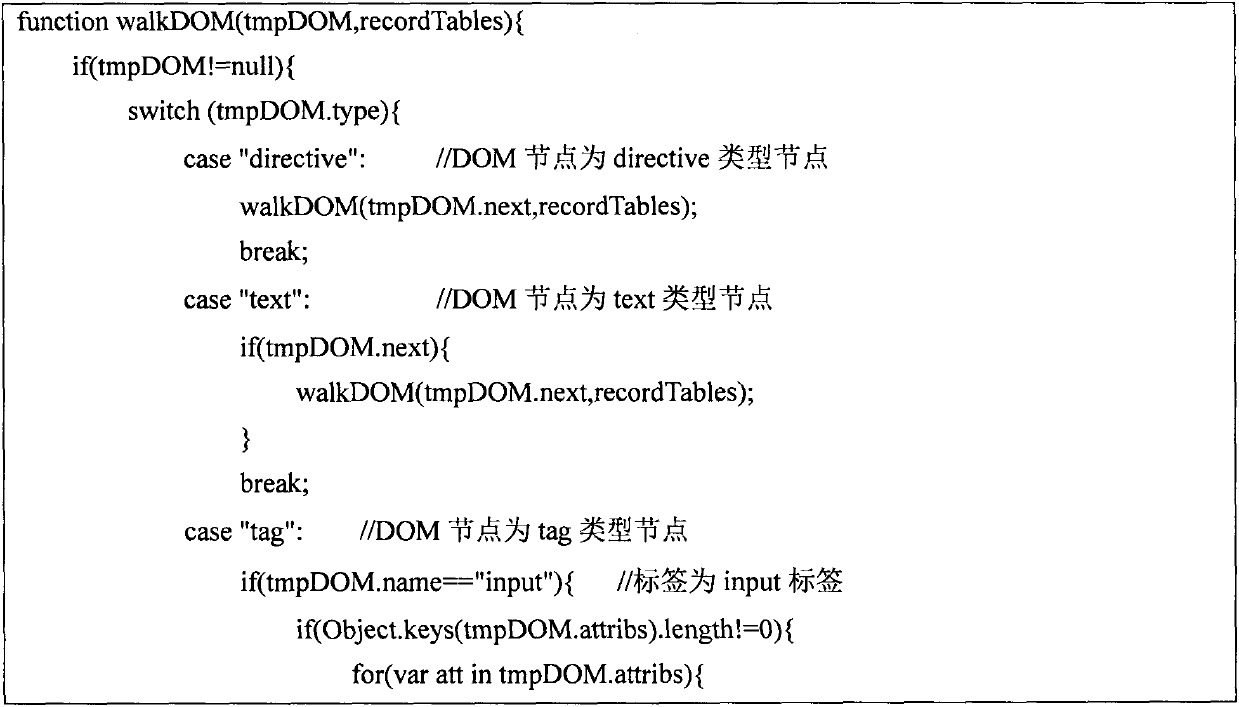
[0043] The present invention adopts the input method based on mutation to detect the XSS loophole existing in the Web application, that is: use htmlparser2 to analyze the Web page, obtain the DOM structure of the Web page; write a specific algorithm to traverse the DOM structure, and find all the input in the Web page The tags of these input points are mainly input tags and textarea tags; then the basic input is mutated according to the designed 10 kinds of mutation operators; finally, the obtained mutated input is passed to the Web page by using Selenium, an automatic test framework. Enter the test, and judge whether the Web page has an XSS vulnerability according to the running result.
[0044] Process flow of the present invention such as figure 1 As shown, it specifically includes the following four steps.
[0045] The first step: first convert the Web page into a DOM structure. The present invention uses htmlparser2 to convert Web pages into DOM structures. The resulti...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com